| {"title": "Google Kubernetes Engine (GKE) setup for Workbench", "url": "https://support.expel.io/hc/en-us/articles/11742313688595-Google-Kubernetes-Engine-GKE-setup-for-Workbench", "date": "2022-12-01T15:04:58Z", "contents": "The Expel Google Kubernetes Engine (GKE) offering consumes audit logs from the\nGCP platform through a log sink and pub/sub. This visibility allows Workbench\nto identify activity of interest in GKE, investigate, and notify organizations\nif action is recommended.\n\n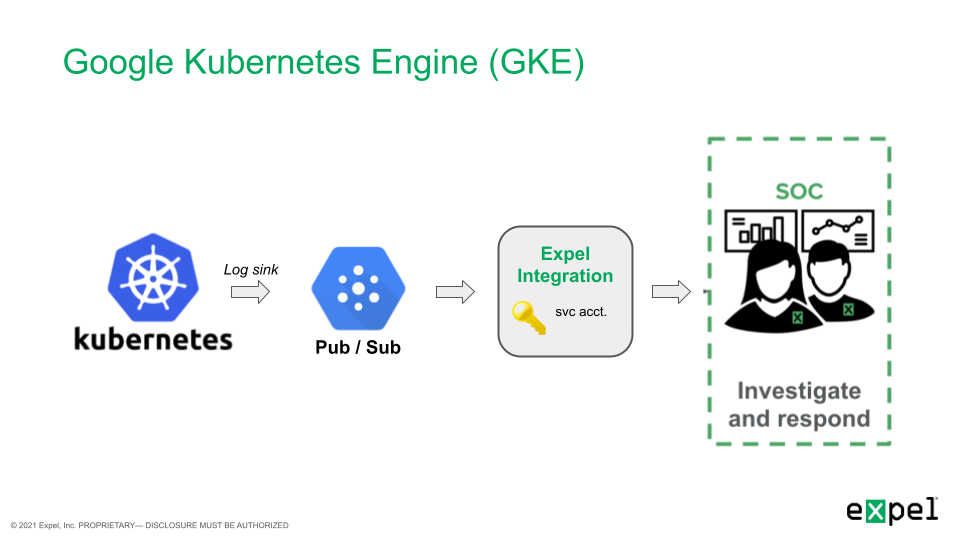\n\n#### In this article\n\n * Onboarding with terraform\n\n * Manual onboarding instructions\n\n * Before you start\n\n * Enable control plane logging for GKE clusters\n\n * Enable Cloud Resource Manager API for monitored projects\n\n * Enable data access auditing for GKE\n\n * Send GKE logs to a pub/sub topic\n\n * Step 1: Create a new pub/sub queue\n\n * Step 2: Create a log sink to route logs to pub/sub\n\n * If you are onboarding a specific project\n\n * Create IAM Role for required permissions\n\n * Create GCP service account for Workbench\n\n * Download GCP service account key\n\n * Onboarding to Expel Workbench\n\n## Onboarding with terraform\n\nExpel maintains a terraform module to help organizations easily onboard GKE\nwith Expel. Contact your engagement manager with any questions about this\nonboarding method. Otherwise, follow the manual instructions below.\n\n## Manual onboarding instructions\n\nComplete the steps below for each GCP project to be monitored by Workbench.\n\n## Before you start\n\nTo complete this procedure you need:\n\n * Administrative access to the GCP environment.\n\n * User privileges to create a service account, IAM role, log sink, a pub/sub topic, and a pub/sub subscription.\n\n## Enable control plane logging for GKE clusters\n\nAt a minimum, Workbench requires logging of the Kubernetes control plane audit\nevents for each cluster. This provides visibility into activity affecting\nresources in the cluster (the “who”, “what”, and “when” we need to detect and\nrespond). By default, GKE clusters are configured to send Kubernetes audit\nevents to Cloud Logging, so no additional configuration is required for\nclusters.\n\n#### Enable Cloud Resource Manager API for monitored projects\n\nFor Expel to discover GKE clusters in the environment, the Cloud Resource\nManager API needs to be enabled in monitored projects. To enable the Cloud\nResource Manager API, navigate to APIs & Services library in the Google Cloud\nconsole.\n\nFrom the library, select Cloud Resources Manager, and enable this API for all\nmonitored projects.\n\n## Enable data access auditing for GKE\n\nGoogle Kubernetes Engine (GKE) separates the Kubernetes control plane logs\ninto 2 log types in Cloud Logging: Admin Activity and Data Access logs. In\ngeneral, write operations (like get, update, or delete) are captured in the\nAdmin Activity log while read operations (like get or list) are captured in\nthe optional Data Access logs (see the documentation for more specifics).\n\nAdmin Activity logging is enabled by default, but it can be necessary to\nenable Data Access logging to increase logging visibility to include read\noperations. To do so, go to the IAM > Audit Logs page and search for\n_Kubernetes Engine API_.\n\nSelect all 3 boxes as below:\n\n\n\nThis can be done at a project, folder, or organization level.\n\n### Note\n\nEnabling additional logging can increase costs for Cloud Logging. For more\ninformation on how this is priced, see the documentation.\n\n## Send GKE logs to a pub/sub topic\n\nGKE begins routing Kubernetes logs to Cloud Logging automatically. Next, we\ncreate a pub/sub queue and a log sink to route logs to Workbench.\n\n### Step 1: Create a new pub/sub queue\n\nWorkbench collects GKE logs through a pub/sub subscription. Navigate to\nPub/Sub > Topics and create a new topic and default subscription.\n\n### Note\n\nWe don't recommend enabling retention duration because of additional cost.\nOptionally, configure a Customer-managed encryption key if needed.\n\n### Step 2: Create a log sink to route logs to pub/sub\n\nNext, we need to create a log sink to route logs to the Pub/Sub topic. To\ncreate a sink at the organization level we need to use the gcloud command line\nutility.\n\n 1. Login to GCP.\n\n`$ gcloud auth login`\n\n 2. List the organizations and take note of the org ID.\n\n`$ gcloud organizations list`\n\n 3. Create the pub/sub org sink. Use this command to create the sink:\n \n $ gcloud logging sinks create [name of log sink] pubsub.googleapis.com/projects/[project-id]/topics/[topic-id] --include-children --organization=[org-id] --log-filter=\"(resource.type=gke_cluster OR resource.type=k8s_cluster)\\n-proto_payload.method_name=\\\"io.k8s.core.v1.nodes.proxy.get\\\"\\n-proto_payload.method_name=\\\"io.k8s.coordination.v1.leases.update\\\"\\n-proto_payload.method_name=\\\"io.k8s.core.v1.limitranges.update\\\"\\n-proto_payload.method_name=\\\"io.k8s.autoscaling\\\"\"\n\nThis automatically creates a new service account which must be granted Pub/Sub\nPublisher permissions on the integration’s topic.\n\n 4. Grant Pub/Sub Publisher role to log sink’s writer identity.\n\nObtain the sink's writer identity—an email address—from the new sink. Go to\nthe Log Router page, and select View sink details. The writer identity appears\nin the Sink details panel.\n\nFrom the console, navigate to PubSub > Topics > [topic-id]. On the Permissions\ntab, grant the service account created above the Publisher role.\n\n### If you are onboarding a specific project\n\nNext, we need to create a log sink to route logs to the pub/sub topic.\nNavigate to Cloud Logging > Logs Router and create a new sink.\n\nType the following information:\n\n 1. A name for the sink.\n\n 2. A description for the sink.\n\n 3. Select the Cloud Pub/Sub topic we created earlier as the destination.\n\n 4. Type the filter below as an inclusion filter.\n\n**Filter**\n\n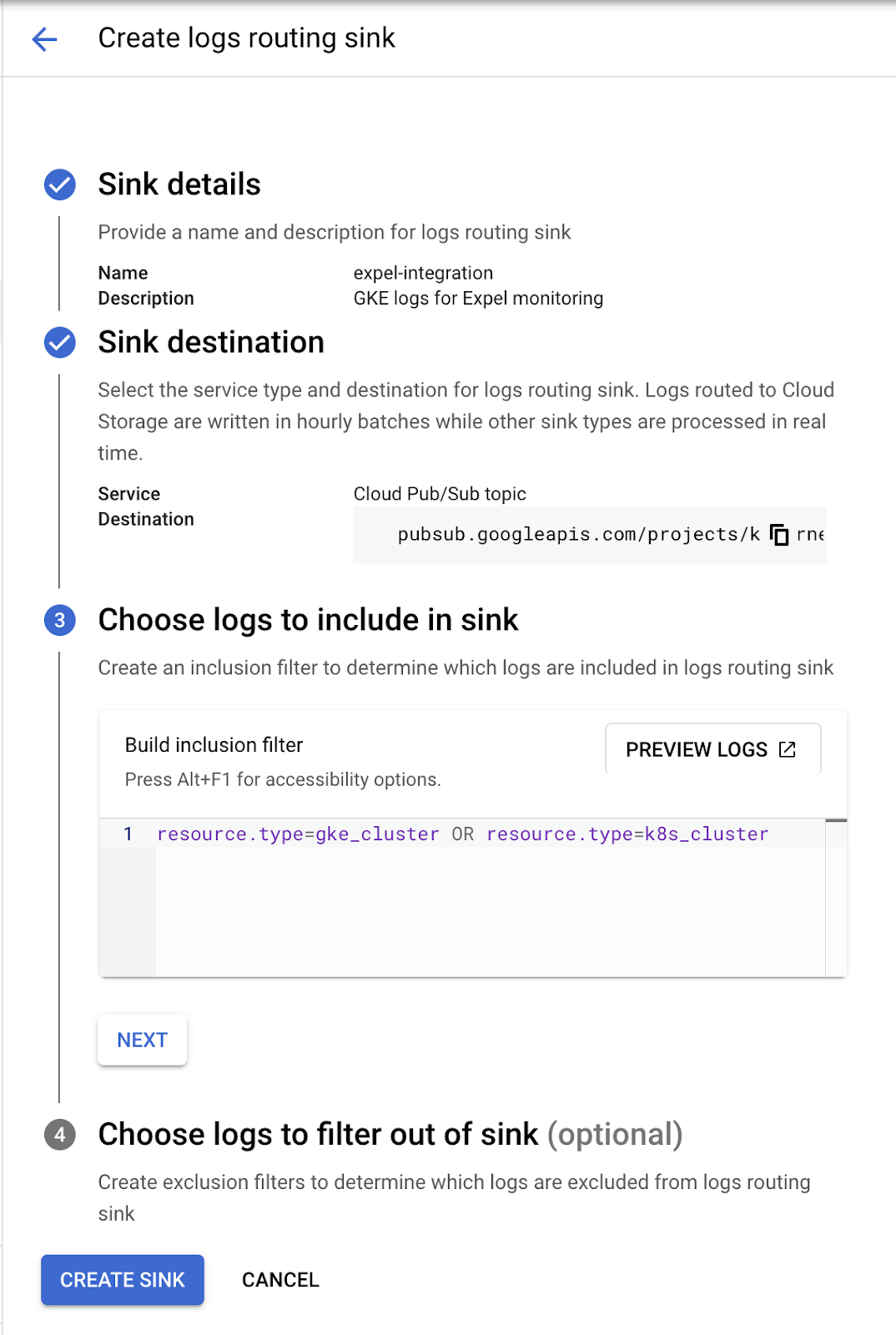\n\n### Create IAM Role for required permissions\n\nNext, we create a new custom IAM role to capture the required permissions for\nWorkbench. Navigate to IAM > Roles and create a new role.\n\nClick the ADD PERMISSIONS button and add the below permissions to this role:\n\n * compute.instanceGroupManagers.get\n\n * container.apiServices.get\n\n * container.apiServices.getStatus\n\n * container.apiServices.list\n\n * container.auditSinks.get\n\n * container.auditSinks.list\n\n * container.backendConfigs.get\n\n * container.backendConfigs.list\n\n * container.bindings.get\n\n * container.bindings.list\n\n * container.certificateSigningRequests.get\n\n * container.certificateSigningRequests.getStatus\n\n * container.certificateSigningRequests.list\n\n * container.clusterRoleBindings.get\n\n * container.clusterRoleBindings.list\n\n * container.clusterRoles.get\n\n * container.clusterRoles.list\n\n * container.clusters.get\n\n * container.clusters.list\n\n * container.componentStatuses.get\n\n * container.componentStatuses.list\n\n * container.controllerRevisions.get\n\n * container.controllerRevisions.list\n\n * container.cronJobs.get\n\n * container.cronJobs.getStatus\n\n * container.cronJobs.list\n\n * container.csiDrivers.get\n\n * container.csiDrivers.list\n\n * container.csiNodeInfos.get\n\n * container.csiNodeInfos.list\n\n * container.csiNodes.get\n\n * container.csiNodes.list\n\n * container.customResourceDefinitions.get\n\n * container.customResourceDefinitions.getStatus\n\n * container.customResourceDefinitions.list\n\n * container.daemonSets.get\n\n * container.daemonSets.getStatus\n\n * container.daemonSets.list\n\n * container.deployments.get\n\n * container.deployments.getScale\n\n * container.deployments.getStatus\n\n * container.deployments.list\n\n * container.endpointSlices.get\n\n * container.endpointSlices.list\n\n * container.endpoints.get\n\n * container.endpoints.list\n\n * container.events.get\n\n * container.events.list\n\n * container.frontendConfigs.get\n\n * container.frontendConfigs.list\n\n * container.horizontalPodAutoscalers.get\n\n * container.horizontalPodAutoscalers.getStatus\n\n * container.horizontalPodAutoscalers.list\n\n * container.ingresses.get\n\n * container.ingresses.getStatus\n\n * container.ingresses.list\n\n * container.initializerConfigurations.get\n\n * container.initializerConfigurations.list\n\n * container.jobs.get\n\n * container.jobs.getStatus\n\n * container.jobs.list\n\n * container.mutatingWebhookConfigurations.get\n\n * container.mutatingWebhookConfigurations.list\n\n * container.namespaces.get\n\n * container.namespaces.getStatus\n\n * container.namespaces.list\n\n * container.networkPolicies.get\n\n * container.networkPolicies.list\n\n * container.nodes.get\n\n * container.nodes.getStatus\n\n * container.nodes.list\n\n * container.operations.get\n\n * container.operations.list\n\n * container.persistentVolumeClaims.get\n\n * container.persistentVolumeClaims.getStatus\n\n * container.persistentVolumeClaims.list\n\n * container.persistentVolumes.get\n\n * container.persistentVolumes.getStatus\n\n * container.persistentVolumes.list\n\n * container.petSets.get\n\n * container.petSets.list\n\n * container.podDisruptionBudgets.get\n\n * container.podDisruptionBudgets.getStatus\n\n * container.podDisruptionBudgets.list\n\n * container.podPresets.get\n\n * container.podPresets.list\n\n * container.podSecurityPolicies.get\n\n * container.podSecurityPolicies.list\n\n * container.podTemplates.get\n\n * container.podTemplates.list\n\n * container.pods.get\n\n * container.pods.getStatus\n\n * container.pods.list\n\n * container.priorityClasses.get\n\n * container.priorityClasses.list\n\n * container.replicaSets.get\n\n * container.replicaSets.getScale\n\n * container.replicaSets.getStatus\n\n * container.replicaSets.list\n\n * container.replicationControllers.get\n\n * container.replicationControllers.getScale\n\n * container.replicationControllers.getStatus\n\n * container.replicationControllers.list\n\n * container.resourceQuotas.get\n\n * container.resourceQuotas.getStatus\n\n * container.resourceQuotas.list\n\n * container.roleBindings.get\n\n * container.roleBindings.list\n\n * container.roles.get\n\n * container.roles.list\n\n * container.runtimeClasses.get\n\n * container.runtimeClasses.list\n\n * container.scheduledJobs.get\n\n * container.scheduledJobs.list\n\n * container.serviceAccounts.get\n\n * container.serviceAccounts.list\n\n * container.services.get\n\n * container.services.getStatus\n\n * container.services.list\n\n * container.statefulSets.get\n\n * container.statefulSets.getScale\n\n * container.statefulSets.getStatus\n\n * container.statefulSets.list\n\n * container.storageClasses.get\n\n * container.storageClasses.list\n\n * container.storageStates.get\n\n * container.storageStates.getStatus\n\n * container.storageStates.list\n\n * container.storageVersionMigrations.get\n\n * container.storageVersionMigrations.getStatus\n\n * container.storageVersionMigrations.list\n\n * container.thirdPartyObjects.get\n\n * container.thirdPartyObjects.list\n\n * container.thirdPartyResources.get\n\n * container.thirdPartyResources.list\n\n * container.tokenReviews.create\n\n * container.updateInfos.get\n\n * container.updateInfos.list\n\n * container.validatingWebhookConfigurations.get\n\n * container.validatingWebhookConfigurations.list\n\n * container.volumeAttachments.get\n\n * container.volumeAttachments.getStatus\n\n * container.volumeAttachments.list\n\n * container.volumeSnapshotClasses.get\n\n * container.volumeSnapshotClasses.list\n\n * container.volumeSnapshotContents.get\n\n * container.volumeSnapshotContents.getStatus\n\n * container.volumeSnapshotContents.list\n\n * container.volumeSnapshots.get\n\n * container.volumeSnapshots.list\n\n### Create GCP service account for Workbench\n\nNext, we create a service account for Workbench to collect GKE logs and\nmonitor GKE clusters. Navigate to IAM > Service Accounts and create a new\nservice account.\n\nUnder service account details, type a Name, ID and Description and click\nCreate and Continue.\n\nNext, add 3 roles to the service account:\n\n 1. The “Browser” role. This allows Workbench to discover GKE clusters in the environment.\n\n 2. The custom Workbench role we created earlier.\n\n 3. The “Pub/Sub” subscriber role.\n\n### Note\n\nWe recommend adding a condition to limit this role to the pub/resource created\nearlier.\n\nFinally, for the last section, leave the blank defaults and click Done.\n\n### Download GCP service account key\n\nWorkbench requires a service account key to authenticate to your GCP\nenvironment. To generate a key, navigate to IAM > Service Accounts. Locate the\nservice account you created earlier for Workbench, and select Manage Keys from\nthe Actions menu for that account.\n\nCreate a new key, and download the key in the default JSON format. We use this\nkey later in Workbench to onboard the GKE integration.\n\n### Onboarding to Expel Workbench\n\nThe steps below outline how to finish onboarding in Workbench.\n\n 1. Log in to Workbench at https://workbench.expel.io.\n\n 2. Navigate to Settings > Security devices.\n\n 3. Click \\+ Add security device.\n\n 4. Select Google Kubernetes Engine.\n\n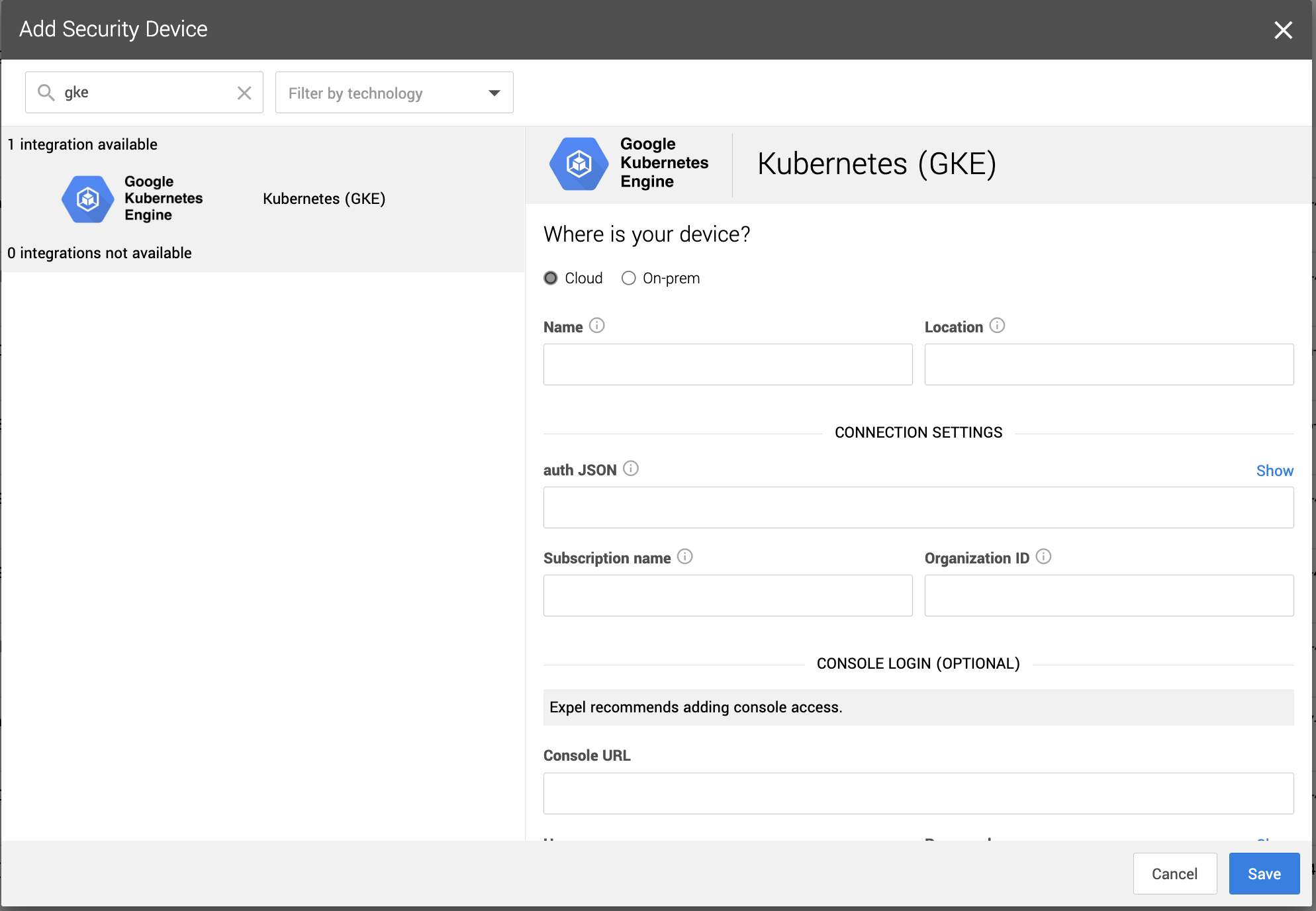\n\n 5. Name the device, provide a description, and fill in the Service Account auth JSON, and the pubsub subscription name.\n\n 6. Click Save.\n\n### Tip\n\nThis article was accurate at the time of writing, but changes happen. If you\nfind the instructions are outdated, leave a description in the comment field\nbelow and let us know!\n\n"} |