| {"title": "Cisco ASA via SIEM setup for Workbench", "url": "https://support.expel.io/hc/en-us/articles/11455992258323-Cisco-ASA-via-SIEM-setup-for-Workbench", "date": "2022-11-21T21:23:02Z", "contents": "This procedure helps you to connect your Cisco ASA via SIEM to the Expel\nWorkbench. The procedure is to port in logs by creating a new Syslog source,\nconfiguring that source in Workbench, then your Cisco ASA through SIEM device\nin Workbench.\n\n### Note\n\nSome steps in this procedure vary greatly depending upon the SIEM-based\ntechnology you use.\n\n#### In this article\n\n * Step 1: Logging Cisco ASA to a desired SIEM\n\n * Step 2: Configure the SIEM in Workbench\n\n * Step 3: Configure Cisco ASA via SIEM in Workbench\n\n## Step 1: Logging Cisco ASA to a desired SIEM\n\nRefer to your SIEM documentation or work with your SIEM representative to port\nin Cisco ASA logs. You can also refer to the following web references for\ncreating a new Syslog source:\n\n * Sumo Logic\n\n * Splunk\n\n## Step 2: Configure the SIEM in Workbench\n\nThis link opens the Expel Knowledge Base section for connecting SIEM-based\ntechnology to Workbench. Follow the applicable article to configure your SIEM-\nbased tech and confirm that Cisco ASA logs are flowing through and available.\n\n## Step 3: Configure Cisco ASA via SIEM in Workbench\n\nNow that we have the correct access configured and noted the credentials, we\ncan integrate your tech with Workbench.\n\n### Note\n\nExpel secures all login information our SOC analysts need about your devices\nin a MFA password product. Access to this login information is protected using\nour internal MFA processes. To learn more about the IP addresses all Expel\ntraffic comes from, go here.\n\n 1. In a new browser tab, go to https://workbench.expel.io/settings/security-devices?setupIntegration=cisco_asa.\n\n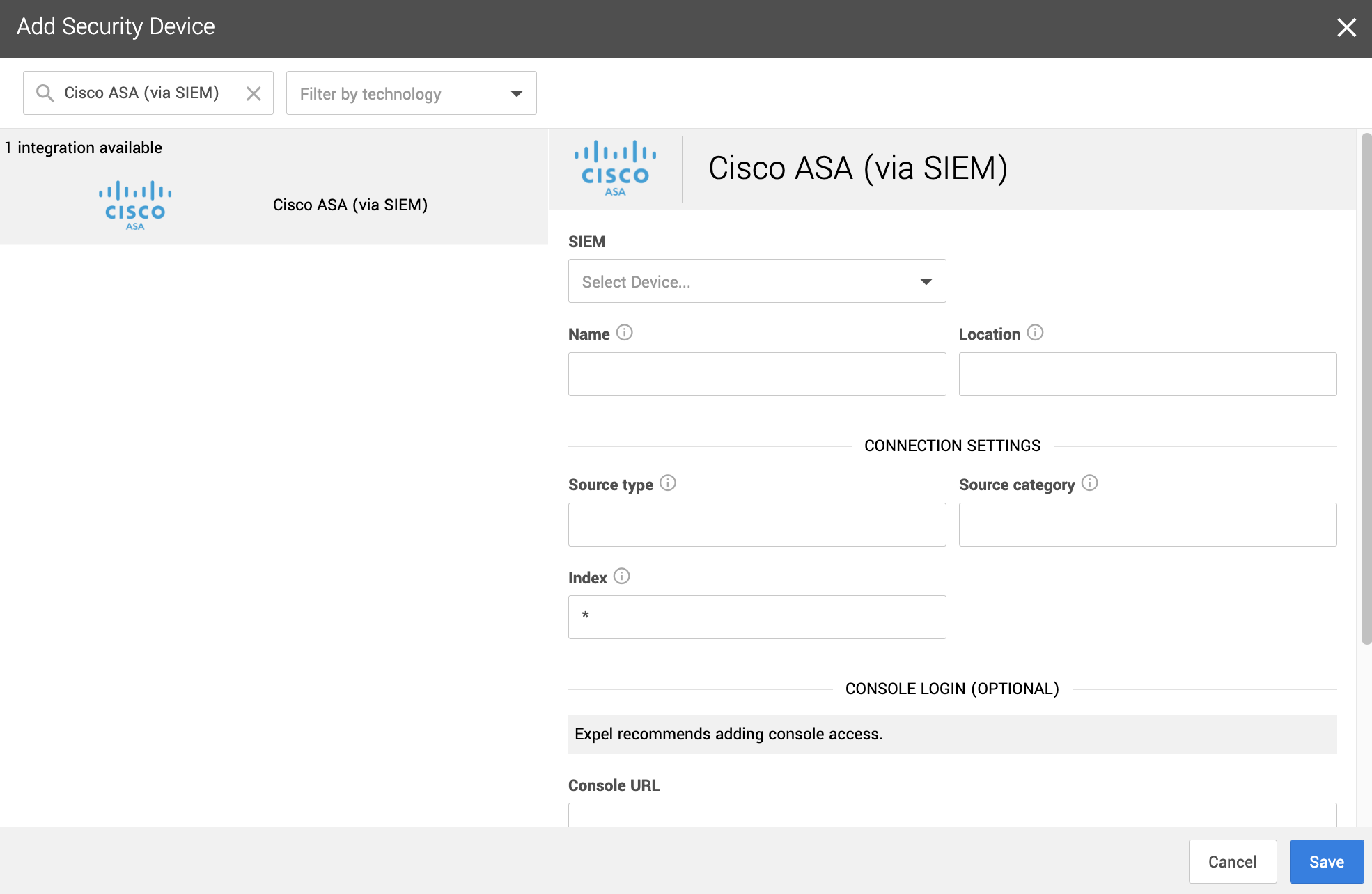\n\n 2. Fill in the device fields like this:\n\n * For SIEM, select the SIEM that was onboarded in Step 2.\n\n * For Name, type the host name of the Cisco ASA device.\n\n * For Location, type the geographic location of the device.\n\n 3. Fill in the Connection Settings fields based on the SIEM you selected:\n\n * For Source type, type the Splunk source type for this device.\n\n * For Source category, type the Sumo Logic source category for this device.\n\n * For Index, type in the Splunk index where the logs are located. By default this is filled in with a wildcard (*).\n\n 4. Click Save.\n\nYou can see if the device is healthy on the Security Devices page. It may take\na few minutes to see the device listed as healthy.\n\nTo check if alerts are coming through, navigate to the Alerts Analysis page.\nScroll to the device you want to check and click View alerts. Switch to grid\nview, then check the list for device alerts. It can take 36 to 72 hours for\nalerts to appear after setup, as we tune your device.\n\n### Tip\n\nThis article was accurate at the time of writing, but changes happen. If you\nfind the instructions are outdated, leave a description in the comment field\nbelow and let us know!\n\n"} |