Unnamed: 0
int64 0
832k
| id
float64 2.49B
32.1B
| type
stringclasses 1
value | created_at
stringlengths 19
19
| repo
stringlengths 7
112
| repo_url
stringlengths 36
141
| action
stringclasses 3
values | title
stringlengths 1
900
| labels
stringlengths 4
522
| body
stringlengths 5
218k
| index
stringclasses 6
values | text_combine
stringlengths 96
219k
| label
stringclasses 2
values | text
stringlengths 96
102k
| binary_label
int64 0
1
|
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
1,493
| 6,122,924,471
|
IssuesEvent
|
2017-06-23 02:02:42
|
Endogix/WebFormWeaver
|
https://api.github.com/repos/Endogix/WebFormWeaver
|
opened
|
Export form structure
|
architecture business logic feature presentation logic
|
Allow the user to export the form structure when they are finished editing the form, through a button near the bottom.
Exporting will show a modal with the code - as optionally either HTML code, JSON, or XML.
There should also be the option to specify an endpoint that this script can connect to through AJAX to save to a server, with another option to specify a function to call when the connection is complete (most likely to be a redirect function).
## Acceptance criteria
User should be able to:
- [ ] Export the form as HTML code
- [ ] Export the form as a JSON string
- [ ] Export the form as an XML string
- [ ] Export the form to an endpoint through AJAX (either JSON or XML)
- [ ] Configure a function in the options to call when then connection to the endpoint is complete
|
1.0
|
Export form structure - Allow the user to export the form structure when they are finished editing the form, through a button near the bottom.
Exporting will show a modal with the code - as optionally either HTML code, JSON, or XML.
There should also be the option to specify an endpoint that this script can connect to through AJAX to save to a server, with another option to specify a function to call when the connection is complete (most likely to be a redirect function).
## Acceptance criteria
User should be able to:
- [ ] Export the form as HTML code
- [ ] Export the form as a JSON string
- [ ] Export the form as an XML string
- [ ] Export the form to an endpoint through AJAX (either JSON or XML)
- [ ] Configure a function in the options to call when then connection to the endpoint is complete
|
architecture
|
export form structure allow the user to export the form structure when they are finished editing the form through a button near the bottom exporting will show a modal with the code as optionally either html code json or xml there should also be the option to specify an endpoint that this script can connect to through ajax to save to a server with another option to specify a function to call when the connection is complete most likely to be a redirect function acceptance criteria user should be able to export the form as html code export the form as a json string export the form as an xml string export the form to an endpoint through ajax either json or xml configure a function in the options to call when then connection to the endpoint is complete
| 1
|
6,052
| 13,559,845,043
|
IssuesEvent
|
2020-09-18 00:05:01
|
QutEcoacoustics/workbench-client
|
https://api.github.com/repos/QutEcoacoustics/workbench-client
|
opened
|
Alternative E2E frameworks
|
CI architecture dependencies enhancement triage:medium
|
Protractor is extremely brittle, and currently provides limited value because of its limitations (such as being unable to intercept API requests). Look into potential alternatives which may provide stability as e2e tests failing is the most consistent breakage in the CI. Some potential alternatives:
- https://webdriver.io/
- https://codecept.io/ (built on top of protractor, might make things simpler?)
|
1.0
|
Alternative E2E frameworks - Protractor is extremely brittle, and currently provides limited value because of its limitations (such as being unable to intercept API requests). Look into potential alternatives which may provide stability as e2e tests failing is the most consistent breakage in the CI. Some potential alternatives:
- https://webdriver.io/
- https://codecept.io/ (built on top of protractor, might make things simpler?)
|
architecture
|
alternative frameworks protractor is extremely brittle and currently provides limited value because of its limitations such as being unable to intercept api requests look into potential alternatives which may provide stability as tests failing is the most consistent breakage in the ci some potential alternatives built on top of protractor might make things simpler
| 1
|
4,896
| 11,809,503,628
|
IssuesEvent
|
2020-03-19 15:03:22
|
MicrosoftDocs/architecture-center
|
https://api.github.com/repos/MicrosoftDocs/architecture-center
|
closed
|
Can you add GCP as well?
|
Pri1 architecture-center/svc assigned-to-author cloud-fundamentals/subsvc doc-idea triaged
|
Would be nice if you can add GCP as well here.
---
#### Document Details
⚠ *Do not edit this section. It is required for docs.microsoft.com ➟ GitHub issue linking.*
* ID: 30d02f16-9621-d204-4132-8ce8db79b0af
* Version Independent ID: 65b4385b-79f0-d842-d4a1-5d013615f9b1
* Content: [AWS to Azure services comparison - Azure Architecture Center](https://docs.microsoft.com/en-us/azure/architecture/aws-professional/services#feedback)
* Content Source: [docs/aws-professional/services.md](https://github.com/microsoftdocs/architecture-center/blob/master/docs/aws-professional/services.md)
* Service: **architecture-center**
* Sub-service: **cloud-fundamentals**
* GitHub Login: @JasRobe
* Microsoft Alias: **pnp**
|
1.0
|
Can you add GCP as well? - Would be nice if you can add GCP as well here.
---
#### Document Details
⚠ *Do not edit this section. It is required for docs.microsoft.com ➟ GitHub issue linking.*
* ID: 30d02f16-9621-d204-4132-8ce8db79b0af
* Version Independent ID: 65b4385b-79f0-d842-d4a1-5d013615f9b1
* Content: [AWS to Azure services comparison - Azure Architecture Center](https://docs.microsoft.com/en-us/azure/architecture/aws-professional/services#feedback)
* Content Source: [docs/aws-professional/services.md](https://github.com/microsoftdocs/architecture-center/blob/master/docs/aws-professional/services.md)
* Service: **architecture-center**
* Sub-service: **cloud-fundamentals**
* GitHub Login: @JasRobe
* Microsoft Alias: **pnp**
|
architecture
|
can you add gcp as well would be nice if you can add gcp as well here document details ⚠ do not edit this section it is required for docs microsoft com ➟ github issue linking id version independent id content content source service architecture center sub service cloud fundamentals github login jasrobe microsoft alias pnp
| 1
|
5,973
| 13,439,248,033
|
IssuesEvent
|
2020-09-07 20:29:27
|
ietf-tapswg/api-drafts
|
https://api.github.com/repos/ietf-tapswg/api-drafts
|
closed
|
In Arch.... this sentence reads like a paper, rather than an Arch spec.
|
Architecture editorial
|
OLD:
Among the Functional and Optimizing Features, some were common across all or nearly all transport protocols, while others could be seen as features that, if specified, would only be useful with a subset of protocols, but would not harm the functionality of other protocols.
Suggest NEW:
Some Functional and Optimizing Features are common across all or nearly all transport protocols. Other features might only be useful with a subset of protocols, but would not harm the functionality of other protocols.
|
1.0
|
In Arch.... this sentence reads like a paper, rather than an Arch spec. - OLD:
Among the Functional and Optimizing Features, some were common across all or nearly all transport protocols, while others could be seen as features that, if specified, would only be useful with a subset of protocols, but would not harm the functionality of other protocols.
Suggest NEW:
Some Functional and Optimizing Features are common across all or nearly all transport protocols. Other features might only be useful with a subset of protocols, but would not harm the functionality of other protocols.
|
architecture
|
in arch this sentence reads like a paper rather than an arch spec old among the functional and optimizing features some were common across all or nearly all transport protocols while others could be seen as features that if specified would only be useful with a subset of protocols but would not harm the functionality of other protocols suggest new some functional and optimizing features are common across all or nearly all transport protocols other features might only be useful with a subset of protocols but would not harm the functionality of other protocols
| 1
|
1,012
| 4,827,829,877
|
IssuesEvent
|
2016-11-07 14:46:09
|
powertac/powertac-server
|
https://api.github.com/repos/powertac/powertac-server
|
opened
|
powertac-parent pom not found when building sample broker in clean system
|
Architecture Broker Bug
|
Reported by Porag:
maven shows the following error message:
```
[ERROR] Non-resolvable parent POM: Could not find artifact org.powertac:powertac-parent:pom:1.4.0-SNAPSHOT and 'parent.relativePath' points at no local POM @ line 15, column 11
```
|
1.0
|
powertac-parent pom not found when building sample broker in clean system - Reported by Porag:
maven shows the following error message:
```
[ERROR] Non-resolvable parent POM: Could not find artifact org.powertac:powertac-parent:pom:1.4.0-SNAPSHOT and 'parent.relativePath' points at no local POM @ line 15, column 11
```
|
architecture
|
powertac parent pom not found when building sample broker in clean system reported by porag maven shows the following error message non resolvable parent pom could not find artifact org powertac powertac parent pom snapshot and parent relativepath points at no local pom line column
| 1
|
2,342
| 7,689,340,069
|
IssuesEvent
|
2018-05-17 12:27:15
|
graphhopper/graphhopper
|
https://api.github.com/repos/graphhopper/graphhopper
|
closed
|
API key usage in client-hc
|
architecture improvement
|
There was likely some misusage or heavy usage of the API key and with hiding in the travis settings this can be avoided: https://github.com/graphhopper/graphhopper/commit/50e975bd079fe22058052574fb8e82c3e83c27e9
But now the build always fails locally without this parameter
|
1.0
|
API key usage in client-hc - There was likely some misusage or heavy usage of the API key and with hiding in the travis settings this can be avoided: https://github.com/graphhopper/graphhopper/commit/50e975bd079fe22058052574fb8e82c3e83c27e9
But now the build always fails locally without this parameter
|
architecture
|
api key usage in client hc there was likely some misusage or heavy usage of the api key and with hiding in the travis settings this can be avoided but now the build always fails locally without this parameter
| 1
|
8,532
| 22,784,984,083
|
IssuesEvent
|
2022-07-09 05:11:58
|
QutEcoacoustics/workbench-client
|
https://api.github.com/repos/QutEcoacoustics/workbench-client
|
closed
|
First load failing authed resolved models
|
bug architecture triage:high
|
First load of website is resolving models using the guest details. This is because the authToken for api requests is updated after resolved model requests are made. A system to fix this would be to force angular to wait for the auth token api request to resolve, before finalizing the bootstrap process. This will likely use the `APP_INITIALIZER`
|
1.0
|
First load failing authed resolved models - First load of website is resolving models using the guest details. This is because the authToken for api requests is updated after resolved model requests are made. A system to fix this would be to force angular to wait for the auth token api request to resolve, before finalizing the bootstrap process. This will likely use the `APP_INITIALIZER`
|
architecture
|
first load failing authed resolved models first load of website is resolving models using the guest details this is because the authtoken for api requests is updated after resolved model requests are made a system to fix this would be to force angular to wait for the auth token api request to resolve before finalizing the bootstrap process this will likely use the app initializer
| 1
|
2,524
| 7,920,145,396
|
IssuesEvent
|
2018-07-04 21:29:24
|
mpostol/OPC-UA-OOI
|
https://api.github.com/repos/mpostol/OPC-UA-OOI
|
closed
|
SemanticData internal architecture is not properly layered.
|
Architecture change Bug Refactoring
|
# Describe the bug
There are circular references between some namespaces.
# To Reproduce
Create diagram
# Expected behavior
Architecture must be layered
# Screenshots
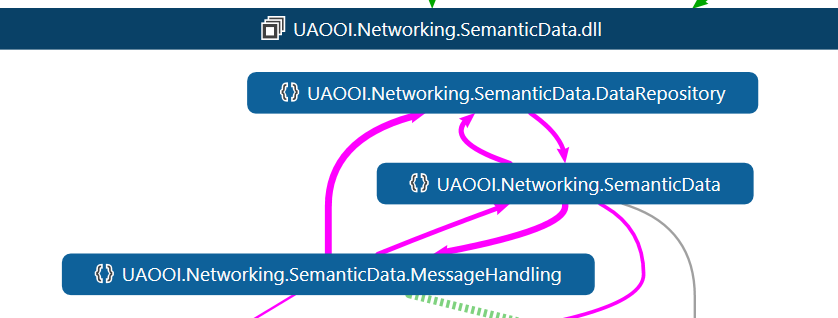
|
1.0
|
SemanticData internal architecture is not properly layered. - # Describe the bug
There are circular references between some namespaces.
# To Reproduce
Create diagram
# Expected behavior
Architecture must be layered
# Screenshots

|
architecture
|
semanticdata internal architecture is not properly layered describe the bug there are circular references between some namespaces to reproduce create diagram expected behavior architecture must be layered screenshots
| 1
|
476,875
| 13,751,608,236
|
IssuesEvent
|
2020-10-06 13:34:02
|
vandersat/vds-api-client
|
https://api.github.com/repos/vandersat/vds-api-client
|
closed
|
Add coverage percentage to api client
|
enhancement good first issue priority
|
Coverage percentage was implemented as of 2020-10-05 as an additional column on roi time series. This column contains the information on which area fraction contributed to the mean value. To request this, an additional keyword needs to be added to the time series requests: `provide_coverage=None` (default setting: `False`)
|
1.0
|
Add coverage percentage to api client - Coverage percentage was implemented as of 2020-10-05 as an additional column on roi time series. This column contains the information on which area fraction contributed to the mean value. To request this, an additional keyword needs to be added to the time series requests: `provide_coverage=None` (default setting: `False`)
|
non_architecture
|
add coverage percentage to api client coverage percentage was implemented as of as an additional column on roi time series this column contains the information on which area fraction contributed to the mean value to request this an additional keyword needs to be added to the time series requests provide coverage none default setting false
| 0
|
4,223
| 10,741,916,781
|
IssuesEvent
|
2019-10-29 21:16:38
|
Azure/azure-sdk
|
https://api.github.com/repos/Azure/azure-sdk
|
closed
|
Change Request: Error Taxonomy for General Guidelines
|
architecture
|
Java and Python error taxonomies are fairly similar. On the TypeScript side, I am willing to adopt a similar error taxonomy (while JS folks don't have much rigor around exceptions and exception hierarchies, worst case seems to be they just ignore it). Given we are so close to alignment across languages, maybe we can see if we can have a general guideline around which error classes we have.
I don't think we can agree on names necessarily, and inheritance isn't a thing in all languages, but it still seems good to align on the error classes.
|
1.0
|
Change Request: Error Taxonomy for General Guidelines - Java and Python error taxonomies are fairly similar. On the TypeScript side, I am willing to adopt a similar error taxonomy (while JS folks don't have much rigor around exceptions and exception hierarchies, worst case seems to be they just ignore it). Given we are so close to alignment across languages, maybe we can see if we can have a general guideline around which error classes we have.
I don't think we can agree on names necessarily, and inheritance isn't a thing in all languages, but it still seems good to align on the error classes.
|
architecture
|
change request error taxonomy for general guidelines java and python error taxonomies are fairly similar on the typescript side i am willing to adopt a similar error taxonomy while js folks don t have much rigor around exceptions and exception hierarchies worst case seems to be they just ignore it given we are so close to alignment across languages maybe we can see if we can have a general guideline around which error classes we have i don t think we can agree on names necessarily and inheritance isn t a thing in all languages but it still seems good to align on the error classes
| 1
|
8,941
| 23,820,221,353
|
IssuesEvent
|
2022-09-05 10:30:36
|
BetweenBooks/between-books-updates
|
https://api.github.com/repos/BetweenBooks/between-books-updates
|
closed
|
The Production of Houses
|
urban-planning philosophical architecture
|

- <https://www.goodreads.com/book/show/106725.The_Production_of_Houses>
- <https://bookshop.org/books/the-production-of-houses/9780195032239>
---
(A special holiday-edition of the book photo from sunny Italy). This is one in a long list of book written by Alexander and collaborators about building and architecture. This book is essentially a case study in his building process adopted by a community in Mexico. Ultimately I think it's fair to say the project failed; in part due to the government. The thing I liked about this book is it showed "real-world" issues with the adoption of his process; insofar as not everyone engaged in the patterns and building process as he expected.
One interesting thing it has is a discussion of how to achieve his particular kind of building in a decentralised way; and it's quite practical and interesting. I think it's fun to see this kind of discussion, which is topical now, in a work that is quite old. That said, this book is probably not for you unless you happen to be particularly obsessed with Christopher Alexander and community-focused building.
|
1.0
|
The Production of Houses - 
- <https://www.goodreads.com/book/show/106725.The_Production_of_Houses>
- <https://bookshop.org/books/the-production-of-houses/9780195032239>
---
(A special holiday-edition of the book photo from sunny Italy). This is one in a long list of book written by Alexander and collaborators about building and architecture. This book is essentially a case study in his building process adopted by a community in Mexico. Ultimately I think it's fair to say the project failed; in part due to the government. The thing I liked about this book is it showed "real-world" issues with the adoption of his process; insofar as not everyone engaged in the patterns and building process as he expected.
One interesting thing it has is a discussion of how to achieve his particular kind of building in a decentralised way; and it's quite practical and interesting. I think it's fun to see this kind of discussion, which is topical now, in a work that is quite old. That said, this book is probably not for you unless you happen to be particularly obsessed with Christopher Alexander and community-focused building.
|
architecture
|
the production of houses a special holiday edition of the book photo from sunny italy this is one in a long list of book written by alexander and collaborators about building and architecture this book is essentially a case study in his building process adopted by a community in mexico ultimately i think it s fair to say the project failed in part due to the government the thing i liked about this book is it showed real world issues with the adoption of his process insofar as not everyone engaged in the patterns and building process as he expected one interesting thing it has is a discussion of how to achieve his particular kind of building in a decentralised way and it s quite practical and interesting i think it s fun to see this kind of discussion which is topical now in a work that is quite old that said this book is probably not for you unless you happen to be particularly obsessed with christopher alexander and community focused building
| 1
|
315,712
| 27,098,818,912
|
IssuesEvent
|
2023-02-15 06:41:29
|
mumble-voip/mumble
|
https://api.github.com/repos/mumble-voip/mumble
|
closed
|
Mac os x text glitch in shortcuts setting page
|
client bug needs-ckeck-with-latest-version
|
Just a small text glitch on the shortcuts preferences page, i have a shortcut as ctrl+`, but it shows the wrong character. see screenshot.
_This ticket has been migrated from sourceforge. It is thus missing some details like original creator etc.
The original is at https://sourceforge.net/p/mumble/bugs/995/ ._
*The following attachments were added on the original item:
- https://sourceforge.net/p/mumble/bugs/995/attachment/mumble.png*
|
1.0
|
Mac os x text glitch in shortcuts setting page - Just a small text glitch on the shortcuts preferences page, i have a shortcut as ctrl+`, but it shows the wrong character. see screenshot.
_This ticket has been migrated from sourceforge. It is thus missing some details like original creator etc.
The original is at https://sourceforge.net/p/mumble/bugs/995/ ._
*The following attachments were added on the original item:
- https://sourceforge.net/p/mumble/bugs/995/attachment/mumble.png*
|
non_architecture
|
mac os x text glitch in shortcuts setting page just a small text glitch on the shortcuts preferences page i have a shortcut as ctrl but it shows the wrong character see screenshot this ticket has been migrated from sourceforge it is thus missing some details like original creator etc the original is at the following attachments were added on the original item
| 0
|
168,527
| 20,766,206,606
|
IssuesEvent
|
2022-03-15 20:52:19
|
NixOS/nixpkgs
|
https://api.github.com/repos/NixOS/nixpkgs
|
closed
|
Vulnerability roundup 111: wpa_supplicant-2.9: 2 advisories [9.8]
|
1.severity: security
|
[search](https://search.nix.gsc.io/?q=wpa_supplicant&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=wpa_supplicant+in%3Apath&type=Code)
* [ ] [CVE-2022-23303](https://nvd.nist.gov/vuln/detail/CVE-2022-23303) CVSSv3=9.8 (nixos-21.11, nixos-unstable)
* [ ] [CVE-2022-23304](https://nvd.nist.gov/vuln/detail/CVE-2022-23304) CVSSv3=9.8 (nixos-21.11, nixos-unstable)
## CVE details
### CVE-2022-23303
The implementations of SAE in hostapd before 2.10 and wpa_supplicant before 2.10 are vulnerable to side channel attacks as a result of cache access patterns. NOTE: this issue exists because of an incomplete fix for CVE-2019-9494.
### CVE-2022-23304
The implementations of EAP-pwd in hostapd before 2.10 and wpa_supplicant before 2.10 are vulnerable to side-channel attacks as a result of cache access patterns. NOTE: this issue exists because of an incomplete fix for CVE-2019-9495.
-----
Scanned versions: nixos-21.11: 2128d0aa28e; nixos-unstable: 5aaed40d22f.
Cc @ma27
Cc @marcweber
|
True
|
Vulnerability roundup 111: wpa_supplicant-2.9: 2 advisories [9.8] - [search](https://search.nix.gsc.io/?q=wpa_supplicant&i=fosho&repos=NixOS-nixpkgs), [files](https://github.com/NixOS/nixpkgs/search?utf8=%E2%9C%93&q=wpa_supplicant+in%3Apath&type=Code)
* [ ] [CVE-2022-23303](https://nvd.nist.gov/vuln/detail/CVE-2022-23303) CVSSv3=9.8 (nixos-21.11, nixos-unstable)
* [ ] [CVE-2022-23304](https://nvd.nist.gov/vuln/detail/CVE-2022-23304) CVSSv3=9.8 (nixos-21.11, nixos-unstable)
## CVE details
### CVE-2022-23303
The implementations of SAE in hostapd before 2.10 and wpa_supplicant before 2.10 are vulnerable to side channel attacks as a result of cache access patterns. NOTE: this issue exists because of an incomplete fix for CVE-2019-9494.
### CVE-2022-23304
The implementations of EAP-pwd in hostapd before 2.10 and wpa_supplicant before 2.10 are vulnerable to side-channel attacks as a result of cache access patterns. NOTE: this issue exists because of an incomplete fix for CVE-2019-9495.
-----
Scanned versions: nixos-21.11: 2128d0aa28e; nixos-unstable: 5aaed40d22f.
Cc @ma27
Cc @marcweber
|
non_architecture
|
vulnerability roundup wpa supplicant advisories nixos nixos unstable nixos nixos unstable cve details cve the implementations of sae in hostapd before and wpa supplicant before are vulnerable to side channel attacks as a result of cache access patterns note this issue exists because of an incomplete fix for cve cve the implementations of eap pwd in hostapd before and wpa supplicant before are vulnerable to side channel attacks as a result of cache access patterns note this issue exists because of an incomplete fix for cve scanned versions nixos nixos unstable cc cc marcweber
| 0
|
47,797
| 10,150,386,715
|
IssuesEvent
|
2019-08-05 17:31:44
|
joomla/joomla-cms
|
https://api.github.com/repos/joomla/joomla-cms
|
closed
|
Post-installation Messages - Open links in new tab
|
J3 Issue No Code Attached Yet a11y
|
### Steps to reproduce the issue
View the Post-Installation Messages and click some of the links which refers to other information.
Some links opens in a new tab, some links opens in the Admin itself.
Preferred: open all links to more information in a new tab.
### Expected result
Open the links to more information in a new tab.
### Actual result
Some links opens in new tab, some don't.
### System information (as much as possible)
Joomla 3.9.0-alpha2-dev, but might occur in previous versions as well.
### Additional comments
Should be fixed in the language files.
|
1.0
|
Post-installation Messages - Open links in new tab - ### Steps to reproduce the issue
View the Post-Installation Messages and click some of the links which refers to other information.
Some links opens in a new tab, some links opens in the Admin itself.
Preferred: open all links to more information in a new tab.
### Expected result
Open the links to more information in a new tab.
### Actual result
Some links opens in new tab, some don't.
### System information (as much as possible)
Joomla 3.9.0-alpha2-dev, but might occur in previous versions as well.
### Additional comments
Should be fixed in the language files.
|
non_architecture
|
post installation messages open links in new tab steps to reproduce the issue view the post installation messages and click some of the links which refers to other information some links opens in a new tab some links opens in the admin itself preferred open all links to more information in a new tab expected result open the links to more information in a new tab actual result some links opens in new tab some don t system information as much as possible joomla dev but might occur in previous versions as well additional comments should be fixed in the language files
| 0
|
738,438
| 25,559,589,069
|
IssuesEvent
|
2022-11-30 09:45:59
|
nimblehq/android-templates
|
https://api.github.com/repos/nimblehq/android-templates
|
closed
|
Update `new_project.kts` to choose between XML or Compose
|
type : feature status : essential priority : normal
|
## Why
Now the templates have been updated, let's update the script accordingly (= `new_project.kts`)
## Acceptance Criteria
- Add a new flag called `template`, the value can either be `xml` or `compose`
- Ensure a project can be generated correctly for both options
- Ensure the help message is up-to-date
- Update `verify_newproject_script.yml` so the CI still works correctly
|
1.0
|
Update `new_project.kts` to choose between XML or Compose - ## Why
Now the templates have been updated, let's update the script accordingly (= `new_project.kts`)
## Acceptance Criteria
- Add a new flag called `template`, the value can either be `xml` or `compose`
- Ensure a project can be generated correctly for both options
- Ensure the help message is up-to-date
- Update `verify_newproject_script.yml` so the CI still works correctly
|
non_architecture
|
update new project kts to choose between xml or compose why now the templates have been updated let s update the script accordingly new project kts acceptance criteria add a new flag called template the value can either be xml or compose ensure a project can be generated correctly for both options ensure the help message is up to date update verify newproject script yml so the ci still works correctly
| 0
|
250,071
| 7,967,206,102
|
IssuesEvent
|
2018-07-15 11:15:19
|
zhengqunkoo/taxibros
|
https://api.github.com/repos/zhengqunkoo/taxibros
|
reopened
|
Remove Malaysia locations.
|
Priority: Low bug
|
Remove locations obtained by grid query in Malaysia, Pulau Ubin, Pulau Tekong, Pulau Semakau, and Pulau Bukom.
|
1.0
|
Remove Malaysia locations. - Remove locations obtained by grid query in Malaysia, Pulau Ubin, Pulau Tekong, Pulau Semakau, and Pulau Bukom.
|
non_architecture
|
remove malaysia locations remove locations obtained by grid query in malaysia pulau ubin pulau tekong pulau semakau and pulau bukom
| 0
|
470
| 3,439,868,119
|
IssuesEvent
|
2015-12-14 11:48:10
|
NebulousLabs/Sia
|
https://api.github.com/repos/NebulousLabs/Sia
|
closed
|
Mining Pool - current state and TODO list
|
architecture
|
Currently the mining pool / miner do all the communicating they should ever need to do (connecting, negotiating payment channel, and submitting blocks). There are still some checks missing as far as validating block submissions and payment channels. I think that it is all decently documented, but there may be some outdated comments. Feel free to contact me with any questions/clarifications.
Here is a verbose, mostly exhaustive list of things that need to be done (in no special order):
- Only start mining pool if a flag is passed in (e.g. --miner ":9984")
- Pool should generate a new address for each miner to pay to (this is then used in the channels map to access that miner's payment channel)
- Pool (and miner) should have a persistence layer so that they can keep track of payment channels between sessions.
- Pool should subscribe to tpool and check for when miners close their channels.
- Pool should use big.Rat for PercentPayout variables.
I feel like I'm missing some thing(s), but I can't think of them now. I'll update the issue when I do.
|
1.0
|
Mining Pool - current state and TODO list - Currently the mining pool / miner do all the communicating they should ever need to do (connecting, negotiating payment channel, and submitting blocks). There are still some checks missing as far as validating block submissions and payment channels. I think that it is all decently documented, but there may be some outdated comments. Feel free to contact me with any questions/clarifications.
Here is a verbose, mostly exhaustive list of things that need to be done (in no special order):
- Only start mining pool if a flag is passed in (e.g. --miner ":9984")
- Pool should generate a new address for each miner to pay to (this is then used in the channels map to access that miner's payment channel)
- Pool (and miner) should have a persistence layer so that they can keep track of payment channels between sessions.
- Pool should subscribe to tpool and check for when miners close their channels.
- Pool should use big.Rat for PercentPayout variables.
I feel like I'm missing some thing(s), but I can't think of them now. I'll update the issue when I do.
|
architecture
|
mining pool current state and todo list currently the mining pool miner do all the communicating they should ever need to do connecting negotiating payment channel and submitting blocks there are still some checks missing as far as validating block submissions and payment channels i think that it is all decently documented but there may be some outdated comments feel free to contact me with any questions clarifications here is a verbose mostly exhaustive list of things that need to be done in no special order only start mining pool if a flag is passed in e g miner pool should generate a new address for each miner to pay to this is then used in the channels map to access that miner s payment channel pool and miner should have a persistence layer so that they can keep track of payment channels between sessions pool should subscribe to tpool and check for when miners close their channels pool should use big rat for percentpayout variables i feel like i m missing some thing s but i can t think of them now i ll update the issue when i do
| 1
|
221,771
| 17,026,807,302
|
IssuesEvent
|
2021-07-03 17:50:23
|
blockstack/docs
|
https://api.github.com/repos/blockstack/docs
|
closed
|
Adapt billboard Clarinet example into tutorial
|
documentation enhancement
|
Reed created a very nice Clarity example that is stored in the Clarinet repo that demonstrates storing text and transferring tokens. Adapt this into a tutorial, and attach Reed's Accelerator presentation to that tutorial.
|
1.0
|
Adapt billboard Clarinet example into tutorial - Reed created a very nice Clarity example that is stored in the Clarinet repo that demonstrates storing text and transferring tokens. Adapt this into a tutorial, and attach Reed's Accelerator presentation to that tutorial.
|
non_architecture
|
adapt billboard clarinet example into tutorial reed created a very nice clarity example that is stored in the clarinet repo that demonstrates storing text and transferring tokens adapt this into a tutorial and attach reed s accelerator presentation to that tutorial
| 0
|
80,577
| 15,499,500,534
|
IssuesEvent
|
2021-03-11 08:02:36
|
creativecommons/commoners
|
https://api.github.com/repos/creativecommons/commoners
|
opened
|
Malasia page on Wiki.
|
✨ goal: improvement 💻 aspect: code 🚦 status: awaiting triage 🟩 priority: low
|
## Problem
Access / Edit for the CC Malaysia Chapter.
https://wiki.creativecommons.org/wiki/malaysia
## Description
We are in the process of constituting the CC Malaysia Chapter and would like to be able to edit the Malaysia page on the wiki.
We were told to request that through this repo.
## Implementation
- [ ] Establish a mechanism to Edit the Malaysia page
https://wiki.creativecommons.org/wiki/malaysia
|
1.0
|
Malasia page on Wiki. - ## Problem
Access / Edit for the CC Malaysia Chapter.
https://wiki.creativecommons.org/wiki/malaysia
## Description
We are in the process of constituting the CC Malaysia Chapter and would like to be able to edit the Malaysia page on the wiki.
We were told to request that through this repo.
## Implementation
- [ ] Establish a mechanism to Edit the Malaysia page
https://wiki.creativecommons.org/wiki/malaysia
|
non_architecture
|
malasia page on wiki problem access edit for the cc malaysia chapter description we are in the process of constituting the cc malaysia chapter and would like to be able to edit the malaysia page on the wiki we were told to request that through this repo implementation establish a mechanism to edit the malaysia page
| 0
|
552,497
| 16,241,644,671
|
IssuesEvent
|
2021-05-07 10:13:57
|
BlueBrain/nexus
|
https://api.github.com/repos/BlueBrain/nexus
|
closed
|
/resolvers/org throw an uuid error
|
:zap: team:backend low priority 🐞 bug
|
This is due to some rejection handling mess. This type of errors were already present in 1.4.x
|
1.0
|
/resolvers/org throw an uuid error - This is due to some rejection handling mess. This type of errors were already present in 1.4.x
|
non_architecture
|
resolvers org throw an uuid error this is due to some rejection handling mess this type of errors were already present in x
| 0
|
6,026
| 13,525,068,631
|
IssuesEvent
|
2020-09-15 12:31:15
|
EightShapes/esds-site
|
https://api.github.com/repos/EightShapes/esds-site
|
closed
|
Scaffold Doc Site Build Architecture
|
Tech Architecture
|
Create a build area using 11ty, integrating esds-library and esds-doc components.
|
1.0
|
Scaffold Doc Site Build Architecture - Create a build area using 11ty, integrating esds-library and esds-doc components.
|
architecture
|
scaffold doc site build architecture create a build area using integrating esds library and esds doc components
| 1
|
181,335
| 21,658,633,559
|
IssuesEvent
|
2022-05-06 16:35:58
|
yaeljacobs67/librenms
|
https://api.github.com/repos/yaeljacobs67/librenms
|
closed
|
CVE-2019-11358 (Medium) detected in multiple libraries - autoclosed
|
security vulnerability
|
## CVE-2019-11358 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>jquery-2.1.1.min.js</b>, <b>jquery-1.10.1.min.js</b>, <b>jquery-1.10.2.min.js</b></p></summary>
<p>
<details><summary><b>jquery-2.1.1.min.js</b></p></summary>
<p>JavaScript library for DOM operations</p>
<p>Library home page: <a href="https://cdnjs.cloudflare.com/ajax/libs/jquery/2.1.1/jquery.min.js">https://cdnjs.cloudflare.com/ajax/libs/jquery/2.1.1/jquery.min.js</a></p>
<p>Path to dependency file: /librenms/lib/jQuery-Mapael/examples.html</p>
<p>Path to vulnerable library: /librenms/lib/jQuery-Mapael/examples.html</p>
<p>
Dependency Hierarchy:
- :x: **jquery-2.1.1.min.js** (Vulnerable Library)
</details>
<details><summary><b>jquery-1.10.1.min.js</b></p></summary>
<p>JavaScript library for DOM operations</p>
<p>Library home page: <a href="https://cdnjs.cloudflare.com/ajax/libs/jquery/1.10.1/jquery.min.js">https://cdnjs.cloudflare.com/ajax/libs/jquery/1.10.1/jquery.min.js</a></p>
<p>Path to dependency file: /librenms/lib/pace/docs/welcome/index.html</p>
<p>Path to vulnerable library: /librenms/lib/pace/docs/welcome/index.html</p>
<p>
Dependency Hierarchy:
- :x: **jquery-1.10.1.min.js** (Vulnerable Library)
</details>
<details><summary><b>jquery-1.10.2.min.js</b></p></summary>
<p>JavaScript library for DOM operations</p>
<p>Library home page: <a href="https://cdnjs.cloudflare.com/ajax/libs/jquery/1.10.2/jquery.min.js">https://cdnjs.cloudflare.com/ajax/libs/jquery/1.10.2/jquery.min.js</a></p>
<p>Path to vulnerable library: /librenms/html/js/jquery.min.js</p>
<p>
Dependency Hierarchy:
- :x: **jquery-1.10.2.min.js** (Vulnerable Library)
</details>
<p>Found in HEAD commit: <a href="https://api.github.com/repos/yaeljacobs67/librenms/commits/6786bd528ec13c78dcbf535eebc40667f6da79a3">6786bd528ec13c78dcbf535eebc40667f6da79a3</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
jQuery before 3.4.0, as used in Drupal, Backdrop CMS, and other products, mishandles jQuery.extend(true, {}, ...) because of Object.prototype pollution. If an unsanitized source object contained an enumerable __proto__ property, it could extend the native Object.prototype.
<p>Publish Date: 2019-04-20
<p>URL: <a href=https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-11358>CVE-2019-11358</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>6.1</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Changed
- Impact Metrics:
- Confidentiality Impact: Low
- Integrity Impact: Low
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-11358">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-11358</a></p>
<p>Release Date: 2019-04-20</p>
<p>Fix Resolution: 3.4.0</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2019-11358 (Medium) detected in multiple libraries - autoclosed - ## CVE-2019-11358 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>jquery-2.1.1.min.js</b>, <b>jquery-1.10.1.min.js</b>, <b>jquery-1.10.2.min.js</b></p></summary>
<p>
<details><summary><b>jquery-2.1.1.min.js</b></p></summary>
<p>JavaScript library for DOM operations</p>
<p>Library home page: <a href="https://cdnjs.cloudflare.com/ajax/libs/jquery/2.1.1/jquery.min.js">https://cdnjs.cloudflare.com/ajax/libs/jquery/2.1.1/jquery.min.js</a></p>
<p>Path to dependency file: /librenms/lib/jQuery-Mapael/examples.html</p>
<p>Path to vulnerable library: /librenms/lib/jQuery-Mapael/examples.html</p>
<p>
Dependency Hierarchy:
- :x: **jquery-2.1.1.min.js** (Vulnerable Library)
</details>
<details><summary><b>jquery-1.10.1.min.js</b></p></summary>
<p>JavaScript library for DOM operations</p>
<p>Library home page: <a href="https://cdnjs.cloudflare.com/ajax/libs/jquery/1.10.1/jquery.min.js">https://cdnjs.cloudflare.com/ajax/libs/jquery/1.10.1/jquery.min.js</a></p>
<p>Path to dependency file: /librenms/lib/pace/docs/welcome/index.html</p>
<p>Path to vulnerable library: /librenms/lib/pace/docs/welcome/index.html</p>
<p>
Dependency Hierarchy:
- :x: **jquery-1.10.1.min.js** (Vulnerable Library)
</details>
<details><summary><b>jquery-1.10.2.min.js</b></p></summary>
<p>JavaScript library for DOM operations</p>
<p>Library home page: <a href="https://cdnjs.cloudflare.com/ajax/libs/jquery/1.10.2/jquery.min.js">https://cdnjs.cloudflare.com/ajax/libs/jquery/1.10.2/jquery.min.js</a></p>
<p>Path to vulnerable library: /librenms/html/js/jquery.min.js</p>
<p>
Dependency Hierarchy:
- :x: **jquery-1.10.2.min.js** (Vulnerable Library)
</details>
<p>Found in HEAD commit: <a href="https://api.github.com/repos/yaeljacobs67/librenms/commits/6786bd528ec13c78dcbf535eebc40667f6da79a3">6786bd528ec13c78dcbf535eebc40667f6da79a3</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
jQuery before 3.4.0, as used in Drupal, Backdrop CMS, and other products, mishandles jQuery.extend(true, {}, ...) because of Object.prototype pollution. If an unsanitized source object contained an enumerable __proto__ property, it could extend the native Object.prototype.
<p>Publish Date: 2019-04-20
<p>URL: <a href=https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-11358>CVE-2019-11358</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>6.1</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Changed
- Impact Metrics:
- Confidentiality Impact: Low
- Integrity Impact: Low
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-11358">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-11358</a></p>
<p>Release Date: 2019-04-20</p>
<p>Fix Resolution: 3.4.0</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
non_architecture
|
cve medium detected in multiple libraries autoclosed cve medium severity vulnerability vulnerable libraries jquery min js jquery min js jquery min js jquery min js javascript library for dom operations library home page a href path to dependency file librenms lib jquery mapael examples html path to vulnerable library librenms lib jquery mapael examples html dependency hierarchy x jquery min js vulnerable library jquery min js javascript library for dom operations library home page a href path to dependency file librenms lib pace docs welcome index html path to vulnerable library librenms lib pace docs welcome index html dependency hierarchy x jquery min js vulnerable library jquery min js javascript library for dom operations library home page a href path to vulnerable library librenms html js jquery min js dependency hierarchy x jquery min js vulnerable library found in head commit a href vulnerability details jquery before as used in drupal backdrop cms and other products mishandles jquery extend true because of object prototype pollution if an unsanitized source object contained an enumerable proto property it could extend the native object prototype publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope changed impact metrics confidentiality impact low integrity impact low availability impact none for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution step up your open source security game with whitesource
| 0
|
298,069
| 9,195,552,186
|
IssuesEvent
|
2019-03-07 02:54:58
|
gw2efficiency/issues
|
https://api.github.com/repos/gw2efficiency/issues
|
closed
|
Miscalculating Deaths/hour and/or Playtime
|
1-Type: Bug 2-Priority: C 3-Complexity: Low 4-Impact: Low 5-Area: Account 9-Status: For next release 9-Status: Ready for Release
|
I have 4,142h 33m Playtime and 7,666 deaths as per the https://gw2efficiency.com/account/statistics page.
In the https://gw2efficiency.com/account/statistics/statistics.deathCountPerHour Page i have 1.85 deaths/hour which seems correct.
In the https://gw2efficiency.com/account/overview Bottom it shows:
You played a total of 4,038 hours across all characters
During that time you died a total of 7,666 times. That's 1.90 deaths per hour
This is using your account data from 4:01:42 PM.
which is also correct for the given data.
But why is there a difference in the Playtime?
Does the first include deleted characters and the other not?
But if so my deleted characters also had a few deaths, wich don't seem to count as both death values are the same.
|
1.0
|
Miscalculating Deaths/hour and/or Playtime - I have 4,142h 33m Playtime and 7,666 deaths as per the https://gw2efficiency.com/account/statistics page.
In the https://gw2efficiency.com/account/statistics/statistics.deathCountPerHour Page i have 1.85 deaths/hour which seems correct.
In the https://gw2efficiency.com/account/overview Bottom it shows:
You played a total of 4,038 hours across all characters
During that time you died a total of 7,666 times. That's 1.90 deaths per hour
This is using your account data from 4:01:42 PM.
which is also correct for the given data.
But why is there a difference in the Playtime?
Does the first include deleted characters and the other not?
But if so my deleted characters also had a few deaths, wich don't seem to count as both death values are the same.
|
non_architecture
|
miscalculating deaths hour and or playtime i have playtime and deaths as per the page in the page i have deaths hour which seems correct in the bottom it shows you played a total of hours across all characters during that time you died a total of times that s deaths per hour this is using your account data from pm which is also correct for the given data but why is there a difference in the playtime does the first include deleted characters and the other not but if so my deleted characters also had a few deaths wich don t seem to count as both death values are the same
| 0
|
33,679
| 6,228,781,712
|
IssuesEvent
|
2017-07-11 00:50:12
|
pydicom/pydicom
|
https://api.github.com/repos/pydicom/pydicom
|
closed
|
Docstring Documentation
|
Documentation
|
Pydicom docstring formatting needs an official stance for consistency and outside contributors.
Initial discussion is [here](https://groups.google.com/forum/#!topic/pydicom-dev/VGiDOFv_7pA), but should continue on this page.
The discussion seems to lean toward using [Google](https://google-styleguide.googlecode.com/svn/trunk/pyguide.html) or [Numpy](https://github.com/numpy/numpy/blob/master/doc/HOWTO_DOCUMENT.rst.txt) documentation styles. @darcymason is currently leaning towards Numpy style. This can be used as is, or can be converted back to standard reST/Sphinx with helpers like [Napoleon](http://sphinxcontrib-napoleon.readthedocs.org/en/latest/index.html).
Hopefully this will get decided and implemented (at least for public functions) for 1.0.0.
|
1.0
|
Docstring Documentation - Pydicom docstring formatting needs an official stance for consistency and outside contributors.
Initial discussion is [here](https://groups.google.com/forum/#!topic/pydicom-dev/VGiDOFv_7pA), but should continue on this page.
The discussion seems to lean toward using [Google](https://google-styleguide.googlecode.com/svn/trunk/pyguide.html) or [Numpy](https://github.com/numpy/numpy/blob/master/doc/HOWTO_DOCUMENT.rst.txt) documentation styles. @darcymason is currently leaning towards Numpy style. This can be used as is, or can be converted back to standard reST/Sphinx with helpers like [Napoleon](http://sphinxcontrib-napoleon.readthedocs.org/en/latest/index.html).
Hopefully this will get decided and implemented (at least for public functions) for 1.0.0.
|
non_architecture
|
docstring documentation pydicom docstring formatting needs an official stance for consistency and outside contributors initial discussion is but should continue on this page the discussion seems to lean toward using or documentation styles darcymason is currently leaning towards numpy style this can be used as is or can be converted back to standard rest sphinx with helpers like hopefully this will get decided and implemented at least for public functions for
| 0
|
609,986
| 18,891,508,668
|
IssuesEvent
|
2021-11-15 13:44:04
|
pulp/pulp-operator
|
https://api.github.com/repos/pulp/pulp-operator
|
opened
|
As a user, I would like to specify an external database when deploying my operator
|
Migrated from Redmine NEW Story Priority: Normal
|
Author: spredzy (spredzy)
Redmine Issue: 8207, https://pulp.plan.io/issues/8207
---
As a user, I would like to specify an external database when deploying my operator
Meaning, a way should be provided to specify the needed variables.
Ideally two ways should be provided, in order of priority:
* Deployer provides a secret that follows a template, where the informations are provided
* Deployer provides N variables with a 1:1 match for configuration that is supported (like, pg_host, pg_database, pg_user, pg_password, pg_port, ...)
|
1.0
|
As a user, I would like to specify an external database when deploying my operator - Author: spredzy (spredzy)
Redmine Issue: 8207, https://pulp.plan.io/issues/8207
---
As a user, I would like to specify an external database when deploying my operator
Meaning, a way should be provided to specify the needed variables.
Ideally two ways should be provided, in order of priority:
* Deployer provides a secret that follows a template, where the informations are provided
* Deployer provides N variables with a 1:1 match for configuration that is supported (like, pg_host, pg_database, pg_user, pg_password, pg_port, ...)
|
non_architecture
|
as a user i would like to specify an external database when deploying my operator author spredzy spredzy redmine issue as a user i would like to specify an external database when deploying my operator meaning a way should be provided to specify the needed variables ideally two ways should be provided in order of priority deployer provides a secret that follows a template where the informations are provided deployer provides n variables with a match for configuration that is supported like pg host pg database pg user pg password pg port
| 0
|
772,548
| 27,126,694,260
|
IssuesEvent
|
2023-02-16 06:11:25
|
space-wizards/space-station-14
|
https://api.github.com/repos/space-wizards/space-station-14
|
closed
|
Status effects don't show up until they are updated
|
Issue: Bug Priority: 2-Before Release Changes: UI
|
## Description
<!-- Explain your issue in detail. Issues without proper explanation are liable to be closed by maintainers. -->
**Reproduction**
<!-- Include the steps to reproduce if applicable. -->
Sometimes your status indicators don't show up
Hit yourself or get hungry
They show up
**Screenshots**
<!-- If applicable, add screenshots to help explain your problem. -->
**Additional context**
<!-- Add any other context about the problem here. Anything you think is related to the issue. -->
|
1.0
|
Status effects don't show up until they are updated - ## Description
<!-- Explain your issue in detail. Issues without proper explanation are liable to be closed by maintainers. -->
**Reproduction**
<!-- Include the steps to reproduce if applicable. -->
Sometimes your status indicators don't show up
Hit yourself or get hungry
They show up
**Screenshots**
<!-- If applicable, add screenshots to help explain your problem. -->
**Additional context**
<!-- Add any other context about the problem here. Anything you think is related to the issue. -->
|
non_architecture
|
status effects don t show up until they are updated description reproduction sometimes your status indicators don t show up hit yourself or get hungry they show up screenshots additional context
| 0
|
3,472
| 9,661,815,933
|
IssuesEvent
|
2019-05-20 19:04:28
|
Severson-Group/eMach
|
https://api.github.com/repos/Severson-Group/eMach
|
closed
|
Rewrite XFEMM tests to be formal unit tests
|
architecture
|
Refractor the PR #86 to use the Matlab unit test framework. See @npetersen2's examples.
- Move unit tests to the `tests` folder.
- Use `assert` command in Matlab
- Use naming convention: the first word of each file with an XFEMM test should be `xfemm` and the last word should be `Tests`. Example name: `xfemmRemoveExtraNodesTest.m`
- Each test should have a Word (or preferably a Markdown) file of the same name and in the same folder that documents the test.
|
1.0
|
Rewrite XFEMM tests to be formal unit tests - Refractor the PR #86 to use the Matlab unit test framework. See @npetersen2's examples.
- Move unit tests to the `tests` folder.
- Use `assert` command in Matlab
- Use naming convention: the first word of each file with an XFEMM test should be `xfemm` and the last word should be `Tests`. Example name: `xfemmRemoveExtraNodesTest.m`
- Each test should have a Word (or preferably a Markdown) file of the same name and in the same folder that documents the test.
|
architecture
|
rewrite xfemm tests to be formal unit tests refractor the pr to use the matlab unit test framework see s examples move unit tests to the tests folder use assert command in matlab use naming convention the first word of each file with an xfemm test should be xfemm and the last word should be tests example name xfemmremoveextranodestest m each test should have a word or preferably a markdown file of the same name and in the same folder that documents the test
| 1
|
6,314
| 14,175,743,585
|
IssuesEvent
|
2020-11-12 22:08:27
|
kubernetes/kubernetes
|
https://api.github.com/repos/kubernetes/kubernetes
|
closed
|
NodeProxy endpoints can not be Conformance tested in their current state
|
area/conformance needs-triage sig/architecture sig/node
|
# Conformance tests for NodeProxy
These endpoints which are tracked by [APIsnoop Conformance Progress](https://apisnoop.cncf.io/conformance-progress) and need to have conformance tests that meet the [currrent conformance requirements](https://github.com/kubernetes/community/blob/master/contributors/devel/sig-architecture/conformance-tests.md#conformance-test-requirements)
The [NodeProxy endpoints](https://kubernetes.io/docs/reference/generated/kubernetes-api/v1.19/#-strong-proxy-operations-node-v1-core-strong-) are listed below.
| endpoint | path | kind |
|---------------------------------------|-----------------------------------|------------------|
| connectCoreV1PutNodeProxyWithPath | /api/v1/nodes/{name}/proxy/{path} | NodeProxyOptions |
| connectCoreV1PutNodeProxy | /api/v1/nodes/{name}/proxy | NodeProxyOptions |
| connectCoreV1PostNodeProxyWithPath | /api/v1/nodes/{name}/proxy/{path} | NodeProxyOptions |
| connectCoreV1PostNodeProxy | /api/v1/nodes/{name}/proxy | NodeProxyOptions |
| connectCoreV1PatchNodeProxyWithPath | /api/v1/nodes/{name}/proxy/{path} | NodeProxyOptions |
| connectCoreV1PatchNodeProxy | /api/v1/nodes/{name}/proxy | NodeProxyOptions |
| connectCoreV1OptionsNodeProxyWithPath | /api/v1/nodes/{name}/proxy/{path} | NodeProxyOptions |
| connectCoreV1OptionsNodeProxy | /api/v1/nodes/{name}/proxy | NodeProxyOptions |
| connectCoreV1HeadNodeProxyWithPath | /api/v1/nodes/{name}/proxy/{path} | NodeProxyOptions |
| connectCoreV1HeadNodeProxy | /api/v1/nodes/{name}/proxy | NodeProxyOptions |
| connectCoreV1GetNodeProxy | /api/v1/nodes/{name}/proxy | NodeProxyOptions |
| connectCoreV1DeleteNodeProxyWithPath | /api/v1/nodes/{name}/proxy/{path} | NodeProxyOptions |
| connectCoreV1DeleteNodeProxy | /api/v1/nodes/{name}/proxy | NodeProxyOptions |
## Feedback request 1
Should the endpoints for **connectCoreV1*NodeProxy | /api/v1/nodes/{name}/proxy** be able to hit something valid?
- The apiserver is doing a blanket redirect for any of these at the moment.
- When testing with the *redirect* removed returns a set of 404 messages.
- What's the best action going forward for these endpoints?
- **Ticket:** Write NodeProxy Redirect Test - +7 endpoint coverage test [#94949](https://github.com/kubernetes/kubernetes/pull/94949)
## Fedback Request 2
Is there a some node api that we can use to confirm the actions of **/api/v1/nodes/{name}/proxy/{path}**? Using either 'configz' or '/metrics' is not an option as they are using kublet (which isn't allowed to be used for conformance tests)
- The test will need some way of confirming that the http method sent through the proxy hasn't beeen changed eg POST requrest must not change to a GET request.
- **Ticket:** Write NodeProxyWithPath test+promote - + 4 endpoint coverage [#95524](https://github.com/kubernetes/kubernetes/issues/95524)
## SIG Note meeting feedback
From the SIG Node meeting on 27 October 2020 it seem likely that the Node Proxy endpoints would be deprecated as it is an old feature from the beginning of K8s, likely not needed any more.
## The next steps
If there is no objections the Node Proxy endpoints would be marked as [Ineligible for Conformance](https://apisnoop.cncf.io/conformance-progress/ineligible-endpoints)
This status can be changed by either updating the endpoints as explained in the feedback requests above to support conformance testing or deprecating the endpoints.
|
1.0
|
NodeProxy endpoints can not be Conformance tested in their current state - # Conformance tests for NodeProxy
These endpoints which are tracked by [APIsnoop Conformance Progress](https://apisnoop.cncf.io/conformance-progress) and need to have conformance tests that meet the [currrent conformance requirements](https://github.com/kubernetes/community/blob/master/contributors/devel/sig-architecture/conformance-tests.md#conformance-test-requirements)
The [NodeProxy endpoints](https://kubernetes.io/docs/reference/generated/kubernetes-api/v1.19/#-strong-proxy-operations-node-v1-core-strong-) are listed below.
| endpoint | path | kind |
|---------------------------------------|-----------------------------------|------------------|
| connectCoreV1PutNodeProxyWithPath | /api/v1/nodes/{name}/proxy/{path} | NodeProxyOptions |
| connectCoreV1PutNodeProxy | /api/v1/nodes/{name}/proxy | NodeProxyOptions |
| connectCoreV1PostNodeProxyWithPath | /api/v1/nodes/{name}/proxy/{path} | NodeProxyOptions |
| connectCoreV1PostNodeProxy | /api/v1/nodes/{name}/proxy | NodeProxyOptions |
| connectCoreV1PatchNodeProxyWithPath | /api/v1/nodes/{name}/proxy/{path} | NodeProxyOptions |
| connectCoreV1PatchNodeProxy | /api/v1/nodes/{name}/proxy | NodeProxyOptions |
| connectCoreV1OptionsNodeProxyWithPath | /api/v1/nodes/{name}/proxy/{path} | NodeProxyOptions |
| connectCoreV1OptionsNodeProxy | /api/v1/nodes/{name}/proxy | NodeProxyOptions |
| connectCoreV1HeadNodeProxyWithPath | /api/v1/nodes/{name}/proxy/{path} | NodeProxyOptions |
| connectCoreV1HeadNodeProxy | /api/v1/nodes/{name}/proxy | NodeProxyOptions |
| connectCoreV1GetNodeProxy | /api/v1/nodes/{name}/proxy | NodeProxyOptions |
| connectCoreV1DeleteNodeProxyWithPath | /api/v1/nodes/{name}/proxy/{path} | NodeProxyOptions |
| connectCoreV1DeleteNodeProxy | /api/v1/nodes/{name}/proxy | NodeProxyOptions |
## Feedback request 1
Should the endpoints for **connectCoreV1*NodeProxy | /api/v1/nodes/{name}/proxy** be able to hit something valid?
- The apiserver is doing a blanket redirect for any of these at the moment.
- When testing with the *redirect* removed returns a set of 404 messages.
- What's the best action going forward for these endpoints?
- **Ticket:** Write NodeProxy Redirect Test - +7 endpoint coverage test [#94949](https://github.com/kubernetes/kubernetes/pull/94949)
## Fedback Request 2
Is there a some node api that we can use to confirm the actions of **/api/v1/nodes/{name}/proxy/{path}**? Using either 'configz' or '/metrics' is not an option as they are using kublet (which isn't allowed to be used for conformance tests)
- The test will need some way of confirming that the http method sent through the proxy hasn't beeen changed eg POST requrest must not change to a GET request.
- **Ticket:** Write NodeProxyWithPath test+promote - + 4 endpoint coverage [#95524](https://github.com/kubernetes/kubernetes/issues/95524)
## SIG Note meeting feedback
From the SIG Node meeting on 27 October 2020 it seem likely that the Node Proxy endpoints would be deprecated as it is an old feature from the beginning of K8s, likely not needed any more.
## The next steps
If there is no objections the Node Proxy endpoints would be marked as [Ineligible for Conformance](https://apisnoop.cncf.io/conformance-progress/ineligible-endpoints)
This status can be changed by either updating the endpoints as explained in the feedback requests above to support conformance testing or deprecating the endpoints.
|
architecture
|
nodeproxy endpoints can not be conformance tested in their current state conformance tests for nodeproxy these endpoints which are tracked by and need to have conformance tests that meet the the are listed below endpoint path kind api nodes name proxy path nodeproxyoptions api nodes name proxy nodeproxyoptions api nodes name proxy path nodeproxyoptions api nodes name proxy nodeproxyoptions api nodes name proxy path nodeproxyoptions api nodes name proxy nodeproxyoptions api nodes name proxy path nodeproxyoptions api nodes name proxy nodeproxyoptions api nodes name proxy path nodeproxyoptions api nodes name proxy nodeproxyoptions api nodes name proxy nodeproxyoptions api nodes name proxy path nodeproxyoptions api nodes name proxy nodeproxyoptions feedback request should the endpoints for nodeproxy api nodes name proxy be able to hit something valid the apiserver is doing a blanket redirect for any of these at the moment when testing with the redirect removed returns a set of messages what s the best action going forward for these endpoints ticket write nodeproxy redirect test endpoint coverage test fedback request is there a some node api that we can use to confirm the actions of api nodes name proxy path using either configz or metrics is not an option as they are using kublet which isn t allowed to be used for conformance tests the test will need some way of confirming that the http method sent through the proxy hasn t beeen changed eg post requrest must not change to a get request ticket write nodeproxywithpath test promote endpoint coverage sig note meeting feedback from the sig node meeting on october it seem likely that the node proxy endpoints would be deprecated as it is an old feature from the beginning of likely not needed any more the next steps if there is no objections the node proxy endpoints would be marked as this status can be changed by either updating the endpoints as explained in the feedback requests above to support conformance testing or deprecating the endpoints
| 1
|
10,146
| 26,397,927,389
|
IssuesEvent
|
2023-01-12 21:20:09
|
MicrosoftDocs/architecture-center
|
https://api.github.com/repos/MicrosoftDocs/architecture-center
|
closed
|
Mismatched image / reference arch download on page
|
doc-bug assigned-to-author triaged architecture-center/svc reference-architecture/subsvc Pri2
|
Image on the page of the Reference Arch and Visio file download do not match.


---
#### Document Details
⚠ *Do not edit this section. It is required for docs.microsoft.com ➟ GitHub issue linking.*
* ID: 84bcf722-abb3-69b8-8073-15ae4a6890de
* Version Independent ID: 7b2010c6-696d-de66-8e56-8ac5d3e54526
* Content: [Basic web application - Azure Reference Architectures](https://docs.microsoft.com/en-us/azure/architecture/reference-architectures/app-service-web-app/basic-web-app?tabs=cli)
* Content Source: [docs/reference-architectures/app-service-web-app/basic-web-app.yml](https://github.com/microsoftdocs/architecture-center/blob/master/docs/reference-architectures/app-service-web-app/basic-web-app.yml)
* Service: **architecture-center**
* Sub-service: **reference-architecture**
* GitHub Login: @EdPrice-MSFT
* Microsoft Alias: **pnp**
|
2.0
|
Mismatched image / reference arch download on page - Image on the page of the Reference Arch and Visio file download do not match.


---
#### Document Details
⚠ *Do not edit this section. It is required for docs.microsoft.com ➟ GitHub issue linking.*
* ID: 84bcf722-abb3-69b8-8073-15ae4a6890de
* Version Independent ID: 7b2010c6-696d-de66-8e56-8ac5d3e54526
* Content: [Basic web application - Azure Reference Architectures](https://docs.microsoft.com/en-us/azure/architecture/reference-architectures/app-service-web-app/basic-web-app?tabs=cli)
* Content Source: [docs/reference-architectures/app-service-web-app/basic-web-app.yml](https://github.com/microsoftdocs/architecture-center/blob/master/docs/reference-architectures/app-service-web-app/basic-web-app.yml)
* Service: **architecture-center**
* Sub-service: **reference-architecture**
* GitHub Login: @EdPrice-MSFT
* Microsoft Alias: **pnp**
|
architecture
|
mismatched image reference arch download on page image on the page of the reference arch and visio file download do not match document details ⚠ do not edit this section it is required for docs microsoft com ➟ github issue linking id version independent id content content source service architecture center sub service reference architecture github login edprice msft microsoft alias pnp
| 1
|
8,715
| 23,310,693,596
|
IssuesEvent
|
2022-08-08 07:59:39
|
toursbylocals/tblv3-api
|
https://api.github.com/repos/toursbylocals/tblv3-api
|
closed
|
feat(model) - promocodes
|
architecture backend
|
Summary:
We need the Promocodes collection to store all the promocodes info.
Check https://excalidraw.com/#room=8c349cbfd0633549d78c,GcZEPSk72FqDoi17Lsq2Pg for more details.
ACS:
- [ ] Create testing cases based on business requirements
- [ ] Create Promocodes model
- [ ] Default or require certain fields on business rules
- Campaign is required
- Code is required
- Value is required
- Rules: At least two rule are required (usage and expiration)
- History is default null
- [ ] Pass all the testings cases and reach 100% coverage
We can skip the business rules for now.
|
1.0
|
feat(model) - promocodes - Summary:
We need the Promocodes collection to store all the promocodes info.
Check https://excalidraw.com/#room=8c349cbfd0633549d78c,GcZEPSk72FqDoi17Lsq2Pg for more details.
ACS:
- [ ] Create testing cases based on business requirements
- [ ] Create Promocodes model
- [ ] Default or require certain fields on business rules
- Campaign is required
- Code is required
- Value is required
- Rules: At least two rule are required (usage and expiration)
- History is default null
- [ ] Pass all the testings cases and reach 100% coverage
We can skip the business rules for now.
|
architecture
|
feat model promocodes summary we need the promocodes collection to store all the promocodes info check for more details acs create testing cases based on business requirements create promocodes model default or require certain fields on business rules campaign is required code is required value is required rules at least two rule are required usage and expiration history is default null pass all the testings cases and reach coverage we can skip the business rules for now
| 1
|
7,908
| 19,956,773,003
|
IssuesEvent
|
2022-01-28 00:49:30
|
Azure/azure-sdk
|
https://api.github.com/repos/Azure/azure-sdk
|
opened
|
Reviewing APIView latest designs
|
architecture board-review
|
Hellooooo
Would love to book sometime with the architects (minimum of an hour) to review the design improvements of the APIView tool.
@weshaggard @praveenkuttappan @chidozieononiwu @kurtzeborn @mikekistler as additional attendants
|
1.0
|
Reviewing APIView latest designs - Hellooooo
Would love to book sometime with the architects (minimum of an hour) to review the design improvements of the APIView tool.
@weshaggard @praveenkuttappan @chidozieononiwu @kurtzeborn @mikekistler as additional attendants
|
architecture
|
reviewing apiview latest designs hellooooo would love to book sometime with the architects minimum of an hour to review the design improvements of the apiview tool weshaggard praveenkuttappan chidozieononiwu kurtzeborn mikekistler as additional attendants
| 1
|
582
| 3,699,274,932
|
IssuesEvent
|
2016-02-28 21:31:00
|
FirstLegoLeague/fllscoring
|
https://api.github.com/repos/FirstLegoLeague/fllscoring
|
opened
|
q dependency missing in npm
|
bug: medium Optimization: Internal / Architecture
|
When installing (npm install) it fails:
module.js:340
throw err;
^
Error: Cannot find module 'q'
at Function.Module._resolveFilename (module.js:338:15)
at Function.Module._load (module.js:280:25)
at Module.require (module.js:364:17)
at require (module.js:380:17)
at Object.<anonymous> (/home/fllscoring/localserver.js:4:9
at Module._compile (module.js:456:26)
at Object.Module._extensions..js (module.js:474:10)
at Module.load (module.js:356:32)
at Function.Module._load (module.js:312:12)
at Function.Module.runMain (module.js:497:10)
|
1.0
|
q dependency missing in npm - When installing (npm install) it fails:
module.js:340
throw err;
^
Error: Cannot find module 'q'
at Function.Module._resolveFilename (module.js:338:15)
at Function.Module._load (module.js:280:25)
at Module.require (module.js:364:17)
at require (module.js:380:17)
at Object.<anonymous> (/home/fllscoring/localserver.js:4:9
at Module._compile (module.js:456:26)
at Object.Module._extensions..js (module.js:474:10)
at Module.load (module.js:356:32)
at Function.Module._load (module.js:312:12)
at Function.Module.runMain (module.js:497:10)
|
architecture
|
q dependency missing in npm when installing npm install it fails module js throw err error cannot find module q at function module resolvefilename module js at function module load module js at module require module js at require module js at object home fllscoring localserver js at module compile module js at object module extensions js module js at module load module js at function module load module js at function module runmain module js
| 1
|
9,117
| 24,055,233,947
|
IssuesEvent
|
2022-09-16 16:11:17
|
MicrosoftDocs/architecture-center
|
https://api.github.com/repos/MicrosoftDocs/architecture-center
|
closed
|
Data Lake Store Reference not really clear
|
bug assigned-to-author triaged architecture-center/svc Pri2 azure-guide/subsvc
|
In the command line tools table "others", is not really clear "Copy to Data Lake Store" and "Copy from Data Lake Store" to what is referred.
AzCopy is set to "Copy from Data Lake Store" -> "NO"
what does it means? you cannot read data from where? Data Lake Store is referred to third part Data Lake Store? someone could think that has not capabilities to copy from Azure Data Lake Storage
---
#### Document Details
⚠ *Do not edit this section. It is required for docs.microsoft.com ➟ GitHub issue linking.*
* ID: 3c6e037b-a226-62cf-6e2b-2af8783b7add
* Version Independent ID: c666597e-52ae-ee51-474a-c4dd3a63941b
* Content: [Choosing a data transfer technology - Azure Architecture Center](https://docs.microsoft.com/en-us/azure/architecture/data-guide/scenarios/data-transfer#key-selection-criteria)
* Content Source: [docs/data-guide/scenarios/data-transfer.md](https://github.com/microsoftdocs/architecture-center/blob/master/docs/data-guide/scenarios/data-transfer.md)
* Service: **architecture-center**
* Sub-service: **azure-guide**
* GitHub Login: @ZoinerTejada
* Microsoft Alias: **pnp**
|
1.0
|
Data Lake Store Reference not really clear -
In the command line tools table "others", is not really clear "Copy to Data Lake Store" and "Copy from Data Lake Store" to what is referred.
AzCopy is set to "Copy from Data Lake Store" -> "NO"
what does it means? you cannot read data from where? Data Lake Store is referred to third part Data Lake Store? someone could think that has not capabilities to copy from Azure Data Lake Storage
---
#### Document Details
⚠ *Do not edit this section. It is required for docs.microsoft.com ➟ GitHub issue linking.*
* ID: 3c6e037b-a226-62cf-6e2b-2af8783b7add
* Version Independent ID: c666597e-52ae-ee51-474a-c4dd3a63941b
* Content: [Choosing a data transfer technology - Azure Architecture Center](https://docs.microsoft.com/en-us/azure/architecture/data-guide/scenarios/data-transfer#key-selection-criteria)
* Content Source: [docs/data-guide/scenarios/data-transfer.md](https://github.com/microsoftdocs/architecture-center/blob/master/docs/data-guide/scenarios/data-transfer.md)
* Service: **architecture-center**
* Sub-service: **azure-guide**
* GitHub Login: @ZoinerTejada
* Microsoft Alias: **pnp**
|
architecture
|
data lake store reference not really clear in the command line tools table others is not really clear copy to data lake store and copy from data lake store to what is referred azcopy is set to copy from data lake store no what does it means you cannot read data from where data lake store is referred to third part data lake store someone could think that has not capabilities to copy from azure data lake storage document details ⚠ do not edit this section it is required for docs microsoft com ➟ github issue linking id version independent id content content source service architecture center sub service azure guide github login zoinertejada microsoft alias pnp
| 1
|
160,644
| 13,794,470,295
|
IssuesEvent
|
2020-10-09 16:23:21
|
zrajani/iLETTERBOX_CAPSTONE_PROJECT_EMBT_F2020
|
https://api.github.com/repos/zrajani/iLETTERBOX_CAPSTONE_PROJECT_EMBT_F2020
|
closed
|
Getting the proposal approved
|
documentation
|
This issue shall be closed once the proposal is completed and the document has been uploaded to the repository
|
1.0
|
Getting the proposal approved - This issue shall be closed once the proposal is completed and the document has been uploaded to the repository
|
non_architecture
|
getting the proposal approved this issue shall be closed once the proposal is completed and the document has been uploaded to the repository
| 0
|
378,019
| 26,279,741,782
|
IssuesEvent
|
2023-01-07 06:32:45
|
jmillerv/mycroft2-skills
|
https://api.github.com/repos/jmillerv/mycroft2-skills
|
opened
|
Add Documentation Folder
|
documentation
|
As part of this ticket, move the steps for converting skills into the documentation folder and update the readme with where to find information.
|
1.0
|
Add Documentation Folder - As part of this ticket, move the steps for converting skills into the documentation folder and update the readme with where to find information.
|
non_architecture
|
add documentation folder as part of this ticket move the steps for converting skills into the documentation folder and update the readme with where to find information
| 0
|
125,187
| 10,339,223,434
|
IssuesEvent
|
2019-09-03 18:48:46
|
galaxyproject/usegalaxy-playbook
|
https://api.github.com/repos/galaxyproject/usegalaxy-playbook
|
closed
|
Prokka v 1.13 requires tbl2asn to be updated at main
|
functionality on Main impacts tutorials install on Main test/retest-pass
|
@natefoo or maybe @davebx ? Whoever can help quicker.
Multiple reports of errors due to this for a few weeks and I confirmed with our usual test case. The jobs always error out. Be good to fix this quickly now. I pinged in slack a bit over a week ago, but that probably got lost. Making a ticket so we can track this ourselves and share it with end-users.
If either of you picks this up, please lmk. I'll test right after this is updated to get it closed out.
Prior time this happened: https://github.com/galaxyproject/usegalaxy-playbook/issues/90
Updating `tbl2asn` should solve the problem again.
Test history (gtn tuto data): https://usegalaxy.org:/u/jen/h/test-tools-prokka-unicycler-quast-multiqc
Compare new errors with v 1.13 (data 139-156, failures with earlier v 1.12.0 (data 107-118, success, same input). I tested a few different output options this time to make sure not related to those (doesn't appear to be).
I reran again today just to make sure this didn't get done already. Same test history, data 157-168 + 169-187 -- used different Unicyler version outputs as input, wasn't sure if certain Prokka versions only work particular Unicycler versions or not, and seemed worth finding out -- it doesn't). Also reran prior version, failed.
**All versions of Prokka fail for the same reason -- Prokka version and `tbl2asn` version are the linked dependencies.**
The error message now is a bit more clear and consistent for this specific dep problem, which helps going forward.
```
Picked up _JAVA_OPTIONS: -Djava.io.tmpdir=/galaxy-repl/main/jobdir/024/558/24558439/_job_tmp -Xmx30g -Xms256m
[tbl2asn] This copy of tbl2asn is more than a year old. Please download the current version.
Picked up _JAVA_OPTIONS: -Djava.io.tmpdir=/galaxy-repl/main/jobdir/024/558/24558439/_job_tmp -Xmx30g -Xms256m
[12:06:21] Could not run command: tbl2asn -V b -a r10k -l paired-ends -M n -N 1 -y 'Annotated using prokka 1.13.3 from https://github.com/tseemann/prokka' -Z outdir\/prokka\.err -i outdir\/prokka\.fsa 2> /dev/null
```
|
2.0
|
Prokka v 1.13 requires tbl2asn to be updated at main - @natefoo or maybe @davebx ? Whoever can help quicker.
Multiple reports of errors due to this for a few weeks and I confirmed with our usual test case. The jobs always error out. Be good to fix this quickly now. I pinged in slack a bit over a week ago, but that probably got lost. Making a ticket so we can track this ourselves and share it with end-users.
If either of you picks this up, please lmk. I'll test right after this is updated to get it closed out.
Prior time this happened: https://github.com/galaxyproject/usegalaxy-playbook/issues/90
Updating `tbl2asn` should solve the problem again.
Test history (gtn tuto data): https://usegalaxy.org:/u/jen/h/test-tools-prokka-unicycler-quast-multiqc
Compare new errors with v 1.13 (data 139-156, failures with earlier v 1.12.0 (data 107-118, success, same input). I tested a few different output options this time to make sure not related to those (doesn't appear to be).
I reran again today just to make sure this didn't get done already. Same test history, data 157-168 + 169-187 -- used different Unicyler version outputs as input, wasn't sure if certain Prokka versions only work particular Unicycler versions or not, and seemed worth finding out -- it doesn't). Also reran prior version, failed.
**All versions of Prokka fail for the same reason -- Prokka version and `tbl2asn` version are the linked dependencies.**
The error message now is a bit more clear and consistent for this specific dep problem, which helps going forward.
```
Picked up _JAVA_OPTIONS: -Djava.io.tmpdir=/galaxy-repl/main/jobdir/024/558/24558439/_job_tmp -Xmx30g -Xms256m
[tbl2asn] This copy of tbl2asn is more than a year old. Please download the current version.
Picked up _JAVA_OPTIONS: -Djava.io.tmpdir=/galaxy-repl/main/jobdir/024/558/24558439/_job_tmp -Xmx30g -Xms256m
[12:06:21] Could not run command: tbl2asn -V b -a r10k -l paired-ends -M n -N 1 -y 'Annotated using prokka 1.13.3 from https://github.com/tseemann/prokka' -Z outdir\/prokka\.err -i outdir\/prokka\.fsa 2> /dev/null
```
|
non_architecture
|
prokka v requires to be updated at main natefoo or maybe davebx whoever can help quicker multiple reports of errors due to this for a few weeks and i confirmed with our usual test case the jobs always error out be good to fix this quickly now i pinged in slack a bit over a week ago but that probably got lost making a ticket so we can track this ourselves and share it with end users if either of you picks this up please lmk i ll test right after this is updated to get it closed out prior time this happened updating should solve the problem again test history gtn tuto data compare new errors with v data failures with earlier v data success same input i tested a few different output options this time to make sure not related to those doesn t appear to be i reran again today just to make sure this didn t get done already same test history data used different unicyler version outputs as input wasn t sure if certain prokka versions only work particular unicycler versions or not and seemed worth finding out it doesn t also reran prior version failed all versions of prokka fail for the same reason prokka version and version are the linked dependencies the error message now is a bit more clear and consistent for this specific dep problem which helps going forward picked up java options djava io tmpdir galaxy repl main jobdir job tmp this copy of is more than a year old please download the current version picked up java options djava io tmpdir galaxy repl main jobdir job tmp could not run command v b a l paired ends m n n y annotated using prokka from z outdir prokka err i outdir prokka fsa dev null
| 0
|
46,608
| 2,963,214,494
|
IssuesEvent
|
2015-07-10 08:49:54
|
handsontable/handsontable
|
https://api.github.com/repos/handsontable/handsontable
|
closed
|
datepicker locale
|
Answered Cell type: date Feature Priority: normal Released
|
hello,
i don't find a way to translate the date picker in fr , i try to use the fr.js in moment\locale,
but the date picker is always in english
i use the latest version
any helps would be appreciate.
jmarc
|
1.0
|
datepicker locale - hello,
i don't find a way to translate the date picker in fr , i try to use the fr.js in moment\locale,
but the date picker is always in english
i use the latest version
any helps would be appreciate.
jmarc
|
non_architecture
|
datepicker locale hello i don t find a way to translate the date picker in fr i try to use the fr js in moment locale but the date picker is always in english i use the latest version any helps would be appreciate jmarc
| 0
|
47,335
| 13,215,581,051
|
IssuesEvent
|
2020-08-17 00:09:10
|
benchmarkdebricked/thimble.mozilla.org
|
https://api.github.com/repos/benchmarkdebricked/thimble.mozilla.org
|
opened
|
CVE-2020-8203 (High) detected in multiple libraries
|
security vulnerability
|
## CVE-2020-8203 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>lodash-3.10.1.tgz</b>, <b>lodash-2.4.2.tgz</b>, <b>lodash-2.2.1.tgz</b>, <b>lodash-3.2.0.tgz</b>, <b>lodash-0.9.2.tgz</b></p></summary>
<p>
<details><summary><b>lodash-3.10.1.tgz</b></p></summary>
<p>The modern build of lodash modular utilities.</p>
<p>Library home page: <a href="https://registry.npmjs.org/lodash/-/lodash-3.10.1.tgz">https://registry.npmjs.org/lodash/-/lodash-3.10.1.tgz</a></p>
<p>Path to dependency file: /tmp/ws-scm/thimble.mozilla.org/services/id.webmaker.org/package.json</p>
<p>Path to vulnerable library: /tmp/ws-scm/thimble.mozilla.org/services/id.webmaker.org/node_modules/lodash/package.json</p>
<p>
Dependency Hierarchy:
- hapi-bunyan-0.6.0.tgz (Root Library)
- :x: **lodash-3.10.1.tgz** (Vulnerable Library)
</details>
<details><summary><b>lodash-2.4.2.tgz</b></p></summary>
<p>A utility library delivering consistency, customization, performance, & extras.</p>
<p>Library home page: <a href="https://registry.npmjs.org/lodash/-/lodash-2.4.2.tgz">https://registry.npmjs.org/lodash/-/lodash-2.4.2.tgz</a></p>
<p>Path to dependency file: /tmp/ws-scm/thimble.mozilla.org/services/login.webmaker.org/package.json</p>
<p>Path to vulnerable library: /tmp/ws-scm/thimble.mozilla.org/services/login.webmaker.org/node_modules/findup-sync/node_modules/lodash/package.json</p>
<p>
Dependency Hierarchy:
- grunt-0.4.5.tgz (Root Library)
- findup-sync-0.1.3.tgz
- :x: **lodash-2.4.2.tgz** (Vulnerable Library)
</details>
<details><summary><b>lodash-2.2.1.tgz</b></p></summary>
<p>A utility library delivering consistency, customization, performance, & extras.</p>
<p>Library home page: <a href="https://registry.npmjs.org/lodash/-/lodash-2.2.1.tgz">https://registry.npmjs.org/lodash/-/lodash-2.2.1.tgz</a></p>
<p>Path to dependency file: /tmp/ws-scm/thimble.mozilla.org/services/login.webmaker.org/package.json</p>
<p>Path to vulnerable library: /tmp/ws-scm/thimble.mozilla.org/services/login.webmaker.org/node_modules/webmaker-i18n/node_modules/lodash/package.json</p>
<p>
Dependency Hierarchy:
- webmaker-i18n-0.3.19.tgz (Root Library)
- :x: **lodash-2.2.1.tgz** (Vulnerable Library)
</details>
<details><summary><b>lodash-3.2.0.tgz</b></p></summary>
<p>The modern build of lodash modular utilities.</p>
<p>Library home page: <a href="https://registry.npmjs.org/lodash/-/lodash-3.2.0.tgz">https://registry.npmjs.org/lodash/-/lodash-3.2.0.tgz</a></p>
<p>Path to dependency file: /tmp/ws-scm/thimble.mozilla.org/services/login.webmaker.org/package.json</p>
<p>Path to vulnerable library: /tmp/ws-scm/thimble.mozilla.org/services/id.webmaker.org/node_modules/xmlbuilder/node_modules/lodash/package.json,/tmp/ws-scm/thimble.mozilla.org/services/id.webmaker.org/node_modules/xmlbuilder/node_modules/lodash/package.json</p>
<p>
Dependency Hierarchy:
- jscs-1.11.3.tgz (Root Library)
- xmlbuilder-2.5.2.tgz
- :x: **lodash-3.2.0.tgz** (Vulnerable Library)
</details>
<details><summary><b>lodash-0.9.2.tgz</b></p></summary>
<p>A utility library delivering consistency, customization, performance, and extras.</p>
<p>Library home page: <a href="https://registry.npmjs.org/lodash/-/lodash-0.9.2.tgz">https://registry.npmjs.org/lodash/-/lodash-0.9.2.tgz</a></p>
<p>Path to dependency file: /tmp/ws-scm/thimble.mozilla.org/services/login.webmaker.org/package.json</p>
<p>Path to vulnerable library: /tmp/ws-scm/thimble.mozilla.org/services/login.webmaker.org/node_modules/grunt/node_modules/lodash/package.json</p>
<p>
Dependency Hierarchy:
- grunt-0.4.5.tgz (Root Library)
- :x: **lodash-0.9.2.tgz** (Vulnerable Library)
</details>
<p>Found in HEAD commit: <a href="https://github.com/benchmarkdebricked/thimble.mozilla.org/commit/df4e3dcf181588072b803af80873328bf5f7f7d1">df4e3dcf181588072b803af80873328bf5f7f7d1</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Prototype pollution attack when using _.zipObjectDeep in lodash <= 4.17.15.
<p>Publish Date: 2020-07-15
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-8203>CVE-2020-8203</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.4</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: High
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://www.npmjs.com/advisories/1523">https://www.npmjs.com/advisories/1523</a></p>
<p>Release Date: 2020-07-23</p>
<p>Fix Resolution: lodash - 4.17.19</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2020-8203 (High) detected in multiple libraries - ## CVE-2020-8203 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>lodash-3.10.1.tgz</b>, <b>lodash-2.4.2.tgz</b>, <b>lodash-2.2.1.tgz</b>, <b>lodash-3.2.0.tgz</b>, <b>lodash-0.9.2.tgz</b></p></summary>
<p>
<details><summary><b>lodash-3.10.1.tgz</b></p></summary>
<p>The modern build of lodash modular utilities.</p>
<p>Library home page: <a href="https://registry.npmjs.org/lodash/-/lodash-3.10.1.tgz">https://registry.npmjs.org/lodash/-/lodash-3.10.1.tgz</a></p>
<p>Path to dependency file: /tmp/ws-scm/thimble.mozilla.org/services/id.webmaker.org/package.json</p>
<p>Path to vulnerable library: /tmp/ws-scm/thimble.mozilla.org/services/id.webmaker.org/node_modules/lodash/package.json</p>
<p>
Dependency Hierarchy:
- hapi-bunyan-0.6.0.tgz (Root Library)
- :x: **lodash-3.10.1.tgz** (Vulnerable Library)
</details>
<details><summary><b>lodash-2.4.2.tgz</b></p></summary>
<p>A utility library delivering consistency, customization, performance, & extras.</p>
<p>Library home page: <a href="https://registry.npmjs.org/lodash/-/lodash-2.4.2.tgz">https://registry.npmjs.org/lodash/-/lodash-2.4.2.tgz</a></p>
<p>Path to dependency file: /tmp/ws-scm/thimble.mozilla.org/services/login.webmaker.org/package.json</p>
<p>Path to vulnerable library: /tmp/ws-scm/thimble.mozilla.org/services/login.webmaker.org/node_modules/findup-sync/node_modules/lodash/package.json</p>
<p>
Dependency Hierarchy:
- grunt-0.4.5.tgz (Root Library)
- findup-sync-0.1.3.tgz
- :x: **lodash-2.4.2.tgz** (Vulnerable Library)
</details>
<details><summary><b>lodash-2.2.1.tgz</b></p></summary>
<p>A utility library delivering consistency, customization, performance, & extras.</p>
<p>Library home page: <a href="https://registry.npmjs.org/lodash/-/lodash-2.2.1.tgz">https://registry.npmjs.org/lodash/-/lodash-2.2.1.tgz</a></p>
<p>Path to dependency file: /tmp/ws-scm/thimble.mozilla.org/services/login.webmaker.org/package.json</p>
<p>Path to vulnerable library: /tmp/ws-scm/thimble.mozilla.org/services/login.webmaker.org/node_modules/webmaker-i18n/node_modules/lodash/package.json</p>
<p>
Dependency Hierarchy:
- webmaker-i18n-0.3.19.tgz (Root Library)
- :x: **lodash-2.2.1.tgz** (Vulnerable Library)
</details>
<details><summary><b>lodash-3.2.0.tgz</b></p></summary>
<p>The modern build of lodash modular utilities.</p>
<p>Library home page: <a href="https://registry.npmjs.org/lodash/-/lodash-3.2.0.tgz">https://registry.npmjs.org/lodash/-/lodash-3.2.0.tgz</a></p>
<p>Path to dependency file: /tmp/ws-scm/thimble.mozilla.org/services/login.webmaker.org/package.json</p>
<p>Path to vulnerable library: /tmp/ws-scm/thimble.mozilla.org/services/id.webmaker.org/node_modules/xmlbuilder/node_modules/lodash/package.json,/tmp/ws-scm/thimble.mozilla.org/services/id.webmaker.org/node_modules/xmlbuilder/node_modules/lodash/package.json</p>
<p>
Dependency Hierarchy:
- jscs-1.11.3.tgz (Root Library)
- xmlbuilder-2.5.2.tgz
- :x: **lodash-3.2.0.tgz** (Vulnerable Library)
</details>
<details><summary><b>lodash-0.9.2.tgz</b></p></summary>
<p>A utility library delivering consistency, customization, performance, and extras.</p>
<p>Library home page: <a href="https://registry.npmjs.org/lodash/-/lodash-0.9.2.tgz">https://registry.npmjs.org/lodash/-/lodash-0.9.2.tgz</a></p>
<p>Path to dependency file: /tmp/ws-scm/thimble.mozilla.org/services/login.webmaker.org/package.json</p>
<p>Path to vulnerable library: /tmp/ws-scm/thimble.mozilla.org/services/login.webmaker.org/node_modules/grunt/node_modules/lodash/package.json</p>
<p>
Dependency Hierarchy:
- grunt-0.4.5.tgz (Root Library)
- :x: **lodash-0.9.2.tgz** (Vulnerable Library)
</details>
<p>Found in HEAD commit: <a href="https://github.com/benchmarkdebricked/thimble.mozilla.org/commit/df4e3dcf181588072b803af80873328bf5f7f7d1">df4e3dcf181588072b803af80873328bf5f7f7d1</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Prototype pollution attack when using _.zipObjectDeep in lodash <= 4.17.15.
<p>Publish Date: 2020-07-15
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-8203>CVE-2020-8203</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.4</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: High
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://www.npmjs.com/advisories/1523">https://www.npmjs.com/advisories/1523</a></p>
<p>Release Date: 2020-07-23</p>
<p>Fix Resolution: lodash - 4.17.19</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
non_architecture
|
cve high detected in multiple libraries cve high severity vulnerability vulnerable libraries lodash tgz lodash tgz lodash tgz lodash tgz lodash tgz lodash tgz the modern build of lodash modular utilities library home page a href path to dependency file tmp ws scm thimble mozilla org services id webmaker org package json path to vulnerable library tmp ws scm thimble mozilla org services id webmaker org node modules lodash package json dependency hierarchy hapi bunyan tgz root library x lodash tgz vulnerable library lodash tgz a utility library delivering consistency customization performance extras library home page a href path to dependency file tmp ws scm thimble mozilla org services login webmaker org package json path to vulnerable library tmp ws scm thimble mozilla org services login webmaker org node modules findup sync node modules lodash package json dependency hierarchy grunt tgz root library findup sync tgz x lodash tgz vulnerable library lodash tgz a utility library delivering consistency customization performance extras library home page a href path to dependency file tmp ws scm thimble mozilla org services login webmaker org package json path to vulnerable library tmp ws scm thimble mozilla org services login webmaker org node modules webmaker node modules lodash package json dependency hierarchy webmaker tgz root library x lodash tgz vulnerable library lodash tgz the modern build of lodash modular utilities library home page a href path to dependency file tmp ws scm thimble mozilla org services login webmaker org package json path to vulnerable library tmp ws scm thimble mozilla org services id webmaker org node modules xmlbuilder node modules lodash package json tmp ws scm thimble mozilla org services id webmaker org node modules xmlbuilder node modules lodash package json dependency hierarchy jscs tgz root library xmlbuilder tgz x lodash tgz vulnerable library lodash tgz a utility library delivering consistency customization performance and extras library home page a href path to dependency file tmp ws scm thimble mozilla org services login webmaker org package json path to vulnerable library tmp ws scm thimble mozilla org services login webmaker org node modules grunt node modules lodash package json dependency hierarchy grunt tgz root library x lodash tgz vulnerable library found in head commit a href vulnerability details prototype pollution attack when using zipobjectdeep in lodash publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity high privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution lodash step up your open source security game with whitesource
| 0
|
610,985
| 18,941,682,551
|
IssuesEvent
|
2021-11-18 04:11:19
|
seannleckie/GrandstreamATAConfigurator
|
https://api.github.com/repos/seannleckie/GrandstreamATAConfigurator
|
closed
|
Network interfaces without a gateway (i.e. unmanaged switches) skipped by NetworkUtils.GetInterface()
|
bug high priority
|
Not sure why, but it looks like I added gateway detection when it was never necessary. All that we need is an interface with a local IP.
|
1.0
|
Network interfaces without a gateway (i.e. unmanaged switches) skipped by NetworkUtils.GetInterface() - Not sure why, but it looks like I added gateway detection when it was never necessary. All that we need is an interface with a local IP.
|
non_architecture
|
network interfaces without a gateway i e unmanaged switches skipped by networkutils getinterface not sure why but it looks like i added gateway detection when it was never necessary all that we need is an interface with a local ip
| 0
|
11,286
| 29,809,044,865
|
IssuesEvent
|
2023-06-16 13:48:38
|
MicrosoftDocs/architecture-center
|
https://api.github.com/repos/MicrosoftDocs/architecture-center
|
closed
|
Azure B2B should be Azure AD External Identities, Current Link Wrong
|
doc-enhancement assigned-to-author triaged architecture-center/svc cloud-fundamentals/subsvc Pri1
|
The AWS Cognito / Azure B2B entry under **"Mobile services** is no longer correct. It takes you to regular Azure AD which is not what people want. It should take you to what Microsoft now calls Azure AD External Identities:
https://azure.microsoft.com/en-us/pricing/details/active-directory/external-identities/
Also why is this under Mobile Services anyway? Shouldn't this be identity? And the Azure AD page needs to be designed better to make this feature easier to find. It was quite the chore to find basic pricing on this.
---
#### Document Details
⚠ *Do not edit this section. It is required for learn.microsoft.com ➟ GitHub issue linking.*
* ID: 30d02f16-9621-d204-4132-8ce8db79b0af
* Version Independent ID: 65b4385b-79f0-d842-d4a1-5d013615f9b1
* Content: [AWS to Azure services comparison - Azure Architecture Center](https://learn.microsoft.com/en-us/azure/architecture/aws-professional/services#security-identity-and-access)
* Content Source: [docs/aws-professional/services.md](https://github.com/microsoftdocs/architecture-center/blob/main/docs/aws-professional/services.md)
* Service: **architecture-center**
* Sub-service: **cloud-fundamentals**
* GitHub Login: @martinekuan
* Microsoft Alias: **yuanzhiqu**
|
1.0
|
Azure B2B should be Azure AD External Identities, Current Link Wrong - The AWS Cognito / Azure B2B entry under **"Mobile services** is no longer correct. It takes you to regular Azure AD which is not what people want. It should take you to what Microsoft now calls Azure AD External Identities:
https://azure.microsoft.com/en-us/pricing/details/active-directory/external-identities/
Also why is this under Mobile Services anyway? Shouldn't this be identity? And the Azure AD page needs to be designed better to make this feature easier to find. It was quite the chore to find basic pricing on this.
---
#### Document Details
⚠ *Do not edit this section. It is required for learn.microsoft.com ➟ GitHub issue linking.*
* ID: 30d02f16-9621-d204-4132-8ce8db79b0af
* Version Independent ID: 65b4385b-79f0-d842-d4a1-5d013615f9b1
* Content: [AWS to Azure services comparison - Azure Architecture Center](https://learn.microsoft.com/en-us/azure/architecture/aws-professional/services#security-identity-and-access)
* Content Source: [docs/aws-professional/services.md](https://github.com/microsoftdocs/architecture-center/blob/main/docs/aws-professional/services.md)
* Service: **architecture-center**
* Sub-service: **cloud-fundamentals**
* GitHub Login: @martinekuan
* Microsoft Alias: **yuanzhiqu**
|
architecture
|
azure should be azure ad external identities current link wrong the aws cognito azure entry under mobile services is no longer correct it takes you to regular azure ad which is not what people want it should take you to what microsoft now calls azure ad external identities also why is this under mobile services anyway shouldn t this be identity and the azure ad page needs to be designed better to make this feature easier to find it was quite the chore to find basic pricing on this document details ⚠ do not edit this section it is required for learn microsoft com ➟ github issue linking id version independent id content content source service architecture center sub service cloud fundamentals github login martinekuan microsoft alias yuanzhiqu
| 1
|
10,909
| 27,455,821,194
|
IssuesEvent
|
2023-03-02 21:15:10
|
MicrosoftDocs/architecture-center
|
https://api.github.com/repos/MicrosoftDocs/architecture-center
|
closed
|
Can sustainable coding practices or green coding also be available
|
doc-enhancement assigned-to-author triaged architecture-center/svc Pri2 guide/subsvc
|
[Enter feedback here]
Can sustainable coding practices or green coding also be available under responsible coding?
---
#### Document Details
⚠ *Do not edit this section. It is required for docs.microsoft.com ➟ GitHub issue linking.*
* ID: 33f1a7ed-041f-c313-9a25-facdc4aebea4
* Version Independent ID: 20908b14-6258-ae56-73bc-323e5c9ac75b
* Content: [Responsible Innovation toolkit - Azure Application Architecture Guide](https://docs.microsoft.com/en-us/azure/architecture/guide/responsible-innovation/)
* Content Source: [docs/guide/responsible-innovation/index.md](https://github.com/microsoftdocs/architecture-center/blob/main/docs/guide/responsible-innovation/index.md)
* Service: **architecture-center**
* Sub-service: **guide**
* GitHub Login: @dcass
* Microsoft Alias: **pnp**
|
1.0
|
Can sustainable coding practices or green coding also be available -
[Enter feedback here]
Can sustainable coding practices or green coding also be available under responsible coding?
---
#### Document Details
⚠ *Do not edit this section. It is required for docs.microsoft.com ➟ GitHub issue linking.*
* ID: 33f1a7ed-041f-c313-9a25-facdc4aebea4
* Version Independent ID: 20908b14-6258-ae56-73bc-323e5c9ac75b
* Content: [Responsible Innovation toolkit - Azure Application Architecture Guide](https://docs.microsoft.com/en-us/azure/architecture/guide/responsible-innovation/)
* Content Source: [docs/guide/responsible-innovation/index.md](https://github.com/microsoftdocs/architecture-center/blob/main/docs/guide/responsible-innovation/index.md)
* Service: **architecture-center**
* Sub-service: **guide**
* GitHub Login: @dcass
* Microsoft Alias: **pnp**
|
architecture
|
can sustainable coding practices or green coding also be available can sustainable coding practices or green coding also be available under responsible coding document details ⚠ do not edit this section it is required for docs microsoft com ➟ github issue linking id version independent id content content source service architecture center sub service guide github login dcass microsoft alias pnp
| 1
|
11,064
| 27,880,843,353
|
IssuesEvent
|
2023-03-21 19:15:53
|
MicrosoftDocs/architecture-center
|
https://api.github.com/repos/MicrosoftDocs/architecture-center
|
closed
|
Pricing Estimate link does not work
|
doc-enhancement assigned-to-author triaged architecture-center/svc example-scenario/subsvc Pri1
|
The pricing sample does not load
Looks like link to estimate no longer works.
https://azure.microsoft.com/en-us/pricing/calculator/?shared-estimate=b798fb70c53e4dd19fdeacea4db78276
---
#### Document Details
⚠ *Do not edit this section. It is required for learn.microsoft.com ➟ GitHub issue linking.*
* ID: 0e4f4c7c-f268-b75b-2486-5c4418e5b24e
* Version Independent ID: 5d28faa1-20bc-1727-05ab-0b18eba1ba7c
* Content: [Data warehousing and analytics - Azure Architecture Center](https://learn.microsoft.com/en-us/azure/architecture/example-scenario/data/data-warehouse)
* Content Source: [docs/example-scenario/data/data-warehouse.yml](https://github.com/microsoftdocs/architecture-center/blob/main/docs/example-scenario/data/data-warehouse.yml)
* Service: **architecture-center**
* Sub-service: **example-scenario**
* GitHub Login: @alexbuckgit
* Microsoft Alias: **Alex.Buck**
|
1.0
|
Pricing Estimate link does not work -
The pricing sample does not load
Looks like link to estimate no longer works.
https://azure.microsoft.com/en-us/pricing/calculator/?shared-estimate=b798fb70c53e4dd19fdeacea4db78276
---
#### Document Details
⚠ *Do not edit this section. It is required for learn.microsoft.com ➟ GitHub issue linking.*
* ID: 0e4f4c7c-f268-b75b-2486-5c4418e5b24e
* Version Independent ID: 5d28faa1-20bc-1727-05ab-0b18eba1ba7c
* Content: [Data warehousing and analytics - Azure Architecture Center](https://learn.microsoft.com/en-us/azure/architecture/example-scenario/data/data-warehouse)
* Content Source: [docs/example-scenario/data/data-warehouse.yml](https://github.com/microsoftdocs/architecture-center/blob/main/docs/example-scenario/data/data-warehouse.yml)
* Service: **architecture-center**
* Sub-service: **example-scenario**
* GitHub Login: @alexbuckgit
* Microsoft Alias: **Alex.Buck**
|
architecture
|
pricing estimate link does not work the pricing sample does not load looks like link to estimate no longer works document details ⚠ do not edit this section it is required for learn microsoft com ➟ github issue linking id version independent id content content source service architecture center sub service example scenario github login alexbuckgit microsoft alias alex buck
| 1
|
621,649
| 19,593,718,163
|
IssuesEvent
|
2022-01-05 15:35:04
|
Happy-Algorithms-League/hal-cgp
|
https://api.github.com/repos/Happy-Algorithms-League/hal-cgp
|
opened
|
Make sure caching decorator's key from numpy evaluation contains not only nan
|
bug high priority
|
Currently, two functions which return all `nan` values from the numpy evaluation are assigned identical keys without emitting any warning.
This should be fixed, e.g., by raising an exception if this is detected.
|
1.0
|
Make sure caching decorator's key from numpy evaluation contains not only nan - Currently, two functions which return all `nan` values from the numpy evaluation are assigned identical keys without emitting any warning.
This should be fixed, e.g., by raising an exception if this is detected.
|
non_architecture
|
make sure caching decorator s key from numpy evaluation contains not only nan currently two functions which return all nan values from the numpy evaluation are assigned identical keys without emitting any warning this should be fixed e g by raising an exception if this is detected
| 0
|
10,450
| 26,989,834,500
|
IssuesEvent
|
2023-02-09 18:56:32
|
MicrosoftDocs/architecture-center
|
https://api.github.com/repos/MicrosoftDocs/architecture-center
|
closed
|
What about user integrity
|
doc-enhancement assigned-to-author triaged architecture-center/svc Pri1 azure-guide/subsvc
|
I see a lot of the Zero Trust visios in the Microsoft library but I wonder about users and auth?
"verifies the trustworthiness of network packets that flow to applications"
- What about the user login?
With App Proxy and B2B, one could invite the client's guest users to log on to the App Proxy to shield the public front from 8 billion users and 8 billion bots
Why is that (pre-auth) not taken into consideration in modern ZT scetches?
---
#### Document Details
⚠ *Do not edit this section. It is required for learn.microsoft.com ➟ GitHub issue linking.*
* ID: 4f623b3a-09d7-d793-b007-85b59727c1df
* Version Independent ID: ec0506cd-cdba-784c-6832-ea59697dd39c
* Content: [Zero-trust network for web applications with Azure Firewall and Application Gateway - Azure Architecture Center](https://learn.microsoft.com/en-us/azure/architecture/example-scenario/gateway/application-gateway-before-azure-firewall)
* Content Source: [docs/example-scenario/gateway/application-gateway-before-azure-firewall.yml](https://github.com/microsoftdocs/architecture-center/blob/main/docs/example-scenario/gateway/application-gateway-before-azure-firewall.yml)
* Service: **architecture-center**
* Sub-service: **azure-guide**
* GitHub Login: @erjosito
* Microsoft Alias: **jomore**
|
1.0
|
What about user integrity - I see a lot of the Zero Trust visios in the Microsoft library but I wonder about users and auth?
"verifies the trustworthiness of network packets that flow to applications"
- What about the user login?
With App Proxy and B2B, one could invite the client's guest users to log on to the App Proxy to shield the public front from 8 billion users and 8 billion bots
Why is that (pre-auth) not taken into consideration in modern ZT scetches?
---
#### Document Details
⚠ *Do not edit this section. It is required for learn.microsoft.com ➟ GitHub issue linking.*
* ID: 4f623b3a-09d7-d793-b007-85b59727c1df
* Version Independent ID: ec0506cd-cdba-784c-6832-ea59697dd39c
* Content: [Zero-trust network for web applications with Azure Firewall and Application Gateway - Azure Architecture Center](https://learn.microsoft.com/en-us/azure/architecture/example-scenario/gateway/application-gateway-before-azure-firewall)
* Content Source: [docs/example-scenario/gateway/application-gateway-before-azure-firewall.yml](https://github.com/microsoftdocs/architecture-center/blob/main/docs/example-scenario/gateway/application-gateway-before-azure-firewall.yml)
* Service: **architecture-center**
* Sub-service: **azure-guide**
* GitHub Login: @erjosito
* Microsoft Alias: **jomore**
|
architecture
|
what about user integrity i see a lot of the zero trust visios in the microsoft library but i wonder about users and auth verifies the trustworthiness of network packets that flow to applications what about the user login with app proxy and one could invite the client s guest users to log on to the app proxy to shield the public front from billion users and billion bots why is that pre auth not taken into consideration in modern zt scetches document details ⚠ do not edit this section it is required for learn microsoft com ➟ github issue linking id version independent id cdba content content source service architecture center sub service azure guide github login erjosito microsoft alias jomore
| 1
|
10,004
| 25,989,855,879
|
IssuesEvent
|
2022-12-20 06:15:15
|
zetah11/zippy
|
https://api.github.com/repos/zetah11/zippy
|
opened
|
move to a query based system
|
enhancement architecture
|
Move to e.g. Salsa 2022 instead of the compiler pipeline model. Things might be a bit messy wrt. the cratification of the compiler, but I think this should be doable, and would open up for making an LSP as well.
|
1.0
|
move to a query based system - Move to e.g. Salsa 2022 instead of the compiler pipeline model. Things might be a bit messy wrt. the cratification of the compiler, but I think this should be doable, and would open up for making an LSP as well.
|
architecture
|
move to a query based system move to e g salsa instead of the compiler pipeline model things might be a bit messy wrt the cratification of the compiler but i think this should be doable and would open up for making an lsp as well
| 1
|
28,938
| 4,151,175,581
|
IssuesEvent
|
2016-06-15 19:44:48
|
w3c/browser-payment-api
|
https://api.github.com/repos/w3c/browser-payment-api
|
closed
|
Is it neccessary to distinguish the origin of data provided in the payment response, and how would we do it?
|
Cat: Design/Technical Doc:BrowserAPI Priority: Low question
|
Somewhat related to some of the discussion in #75 as ShippingAddress is a a good example of response data that could (in future) be provided by the payment app not the user agent.
Currently the user agent gathered data hangs directly off the response object (`response.shippingAddress`) and the data from the payment app does too (`response.details`).
If the payment app returned the shippingAddress (or some other data that the website had requested) would it sit at `response.shippingAddress` or `response.details.shippingAddress`?
|
1.0
|
Is it neccessary to distinguish the origin of data provided in the payment response, and how would we do it? - Somewhat related to some of the discussion in #75 as ShippingAddress is a a good example of response data that could (in future) be provided by the payment app not the user agent.
Currently the user agent gathered data hangs directly off the response object (`response.shippingAddress`) and the data from the payment app does too (`response.details`).
If the payment app returned the shippingAddress (or some other data that the website had requested) would it sit at `response.shippingAddress` or `response.details.shippingAddress`?
|
non_architecture
|
is it neccessary to distinguish the origin of data provided in the payment response and how would we do it somewhat related to some of the discussion in as shippingaddress is a a good example of response data that could in future be provided by the payment app not the user agent currently the user agent gathered data hangs directly off the response object response shippingaddress and the data from the payment app does too response details if the payment app returned the shippingaddress or some other data that the website had requested would it sit at response shippingaddress or response details shippingaddress
| 0
|
96,007
| 16,113,040,671
|
IssuesEvent
|
2021-04-28 01:26:12
|
Bangtrongtuyet/tudonghoa-nguonmo
|
https://api.github.com/repos/Bangtrongtuyet/tudonghoa-nguonmo
|
opened
|
CVE-2021-23337 (High) detected in multiple libraries
|
security vulnerability
|
## CVE-2021-23337 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>lodash-1.0.2.tgz</b>, <b>lodash-0.9.2.tgz</b>, <b>lodash-2.4.2.tgz</b></p></summary>
<p>
<details><summary><b>lodash-1.0.2.tgz</b></p></summary>
<p>A utility library delivering consistency, customization, performance, and extras.</p>
<p>Library home page: <a href="https://registry.npmjs.org/lodash/-/lodash-1.0.2.tgz">https://registry.npmjs.org/lodash/-/lodash-1.0.2.tgz</a></p>
<p>Path to dependency file: /tudonghoa-nguonmo/package.json</p>
<p>Path to vulnerable library: tudonghoa-nguonmo/node_modules/globule/node_modules/lodash/package.json</p>
<p>
Dependency Hierarchy:
- grunt-contrib-watch-0.6.1.tgz (Root Library)
- gaze-0.5.2.tgz
- globule-0.1.0.tgz
- :x: **lodash-1.0.2.tgz** (Vulnerable Library)
</details>
<details><summary><b>lodash-0.9.2.tgz</b></p></summary>
<p>A utility library delivering consistency, customization, performance, and extras.</p>
<p>Library home page: <a href="https://registry.npmjs.org/lodash/-/lodash-0.9.2.tgz">https://registry.npmjs.org/lodash/-/lodash-0.9.2.tgz</a></p>
<p>Path to dependency file: /tudonghoa-nguonmo/package.json</p>
<p>Path to vulnerable library: tudonghoa-nguonmo/node_modules/lodash/package.json</p>
<p>
Dependency Hierarchy:
- grunt-0.4.5.tgz (Root Library)
- :x: **lodash-0.9.2.tgz** (Vulnerable Library)
</details>
<details><summary><b>lodash-2.4.2.tgz</b></p></summary>
<p>A utility library delivering consistency, customization, performance, & extras.</p>
<p>Library home page: <a href="https://registry.npmjs.org/lodash/-/lodash-2.4.2.tgz">https://registry.npmjs.org/lodash/-/lodash-2.4.2.tgz</a></p>
<p>Path to dependency file: /tudonghoa-nguonmo/package.json</p>
<p>Path to vulnerable library: tudonghoa-nguonmo/node_modules/findup-sync/node_modules/lodash/package.json</p>
<p>
Dependency Hierarchy:
- grunt-contrib-watch-0.6.1.tgz (Root Library)
- :x: **lodash-2.4.2.tgz** (Vulnerable Library)
</details>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Lodash versions prior to 4.17.21 are vulnerable to Command Injection via the template function.
<p>Publish Date: 2021-02-15
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-23337>CVE-2021-23337</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.2</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: High
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/lodash/lodash/commit/3469357cff396a26c363f8c1b5a91dde28ba4b1c">https://github.com/lodash/lodash/commit/3469357cff396a26c363f8c1b5a91dde28ba4b1c</a></p>
<p>Release Date: 2021-02-15</p>
<p>Fix Resolution: lodash - 4.17.21</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2021-23337 (High) detected in multiple libraries - ## CVE-2021-23337 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>lodash-1.0.2.tgz</b>, <b>lodash-0.9.2.tgz</b>, <b>lodash-2.4.2.tgz</b></p></summary>
<p>
<details><summary><b>lodash-1.0.2.tgz</b></p></summary>
<p>A utility library delivering consistency, customization, performance, and extras.</p>
<p>Library home page: <a href="https://registry.npmjs.org/lodash/-/lodash-1.0.2.tgz">https://registry.npmjs.org/lodash/-/lodash-1.0.2.tgz</a></p>
<p>Path to dependency file: /tudonghoa-nguonmo/package.json</p>
<p>Path to vulnerable library: tudonghoa-nguonmo/node_modules/globule/node_modules/lodash/package.json</p>
<p>
Dependency Hierarchy:
- grunt-contrib-watch-0.6.1.tgz (Root Library)
- gaze-0.5.2.tgz
- globule-0.1.0.tgz
- :x: **lodash-1.0.2.tgz** (Vulnerable Library)
</details>
<details><summary><b>lodash-0.9.2.tgz</b></p></summary>
<p>A utility library delivering consistency, customization, performance, and extras.</p>
<p>Library home page: <a href="https://registry.npmjs.org/lodash/-/lodash-0.9.2.tgz">https://registry.npmjs.org/lodash/-/lodash-0.9.2.tgz</a></p>
<p>Path to dependency file: /tudonghoa-nguonmo/package.json</p>
<p>Path to vulnerable library: tudonghoa-nguonmo/node_modules/lodash/package.json</p>
<p>
Dependency Hierarchy:
- grunt-0.4.5.tgz (Root Library)
- :x: **lodash-0.9.2.tgz** (Vulnerable Library)
</details>
<details><summary><b>lodash-2.4.2.tgz</b></p></summary>
<p>A utility library delivering consistency, customization, performance, & extras.</p>
<p>Library home page: <a href="https://registry.npmjs.org/lodash/-/lodash-2.4.2.tgz">https://registry.npmjs.org/lodash/-/lodash-2.4.2.tgz</a></p>
<p>Path to dependency file: /tudonghoa-nguonmo/package.json</p>
<p>Path to vulnerable library: tudonghoa-nguonmo/node_modules/findup-sync/node_modules/lodash/package.json</p>
<p>
Dependency Hierarchy:
- grunt-contrib-watch-0.6.1.tgz (Root Library)
- :x: **lodash-2.4.2.tgz** (Vulnerable Library)
</details>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Lodash versions prior to 4.17.21 are vulnerable to Command Injection via the template function.
<p>Publish Date: 2021-02-15
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-23337>CVE-2021-23337</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.2</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: High
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/lodash/lodash/commit/3469357cff396a26c363f8c1b5a91dde28ba4b1c">https://github.com/lodash/lodash/commit/3469357cff396a26c363f8c1b5a91dde28ba4b1c</a></p>
<p>Release Date: 2021-02-15</p>
<p>Fix Resolution: lodash - 4.17.21</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
non_architecture
|
cve high detected in multiple libraries cve high severity vulnerability vulnerable libraries lodash tgz lodash tgz lodash tgz lodash tgz a utility library delivering consistency customization performance and extras library home page a href path to dependency file tudonghoa nguonmo package json path to vulnerable library tudonghoa nguonmo node modules globule node modules lodash package json dependency hierarchy grunt contrib watch tgz root library gaze tgz globule tgz x lodash tgz vulnerable library lodash tgz a utility library delivering consistency customization performance and extras library home page a href path to dependency file tudonghoa nguonmo package json path to vulnerable library tudonghoa nguonmo node modules lodash package json dependency hierarchy grunt tgz root library x lodash tgz vulnerable library lodash tgz a utility library delivering consistency customization performance extras library home page a href path to dependency file tudonghoa nguonmo package json path to vulnerable library tudonghoa nguonmo node modules findup sync node modules lodash package json dependency hierarchy grunt contrib watch tgz root library x lodash tgz vulnerable library vulnerability details lodash versions prior to are vulnerable to command injection via the template function publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required high user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution lodash step up your open source security game with whitesource
| 0
|
237,368
| 26,084,103,553
|
IssuesEvent
|
2022-12-25 21:25:53
|
DWG61868/dagger-browser
|
https://api.github.com/repos/DWG61868/dagger-browser
|
opened
|
CVE-2022-46175 (High) detected in json5-1.0.1.tgz, json5-2.1.1.tgz
|
security vulnerability
|
## CVE-2022-46175 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>json5-1.0.1.tgz</b>, <b>json5-2.1.1.tgz</b></p></summary>
<p>
<details><summary><b>json5-1.0.1.tgz</b></p></summary>
<p>JSON for humans.</p>
<p>Library home page: <a href="https://registry.npmjs.org/json5/-/json5-1.0.1.tgz">https://registry.npmjs.org/json5/-/json5-1.0.1.tgz</a></p>
<p>Path to dependency file: /browser/package.json</p>
<p>Path to vulnerable library: /browser/node_modules/loader-utils/node_modules/json5/package.json</p>
<p>
Dependency Hierarchy:
- react-scripts-3.2.0.tgz (Root Library)
- webpack-4.3.2.tgz
- loader-utils-1.2.3.tgz
- :x: **json5-1.0.1.tgz** (Vulnerable Library)
</details>
<details><summary><b>json5-2.1.1.tgz</b></p></summary>
<p>JSON for humans.</p>
<p>Library home page: <a href="https://registry.npmjs.org/json5/-/json5-2.1.1.tgz">https://registry.npmjs.org/json5/-/json5-2.1.1.tgz</a></p>
<p>Path to dependency file: /browser/package.json</p>
<p>Path to vulnerable library: /browser/node_modules/json5/package.json</p>
<p>
Dependency Hierarchy:
- react-scripts-3.2.0.tgz (Root Library)
- core-7.6.0.tgz
- :x: **json5-2.1.1.tgz** (Vulnerable Library)
</details>
<p>Found in base branch: <b>main</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
JSON5 is an extension to the popular JSON file format that aims to be easier to write and maintain by hand (e.g. for config files). The `parse` method of the JSON5 library before and including version `2.2.1` does not restrict parsing of keys named `__proto__`, allowing specially crafted strings to pollute the prototype of the resulting object. This vulnerability pollutes the prototype of the object returned by `JSON5.parse` and not the global Object prototype, which is the commonly understood definition of Prototype Pollution. However, polluting the prototype of a single object can have significant security impact for an application if the object is later used in trusted operations. This vulnerability could allow an attacker to set arbitrary and unexpected keys on the object returned from `JSON5.parse`. The actual impact will depend on how applications utilize the returned object and how they filter unwanted keys, but could include denial of service, cross-site scripting, elevation of privilege, and in extreme cases, remote code execution. `JSON5.parse` should restrict parsing of `__proto__` keys when parsing JSON strings to objects. As a point of reference, the `JSON.parse` method included in JavaScript ignores `__proto__` keys. Simply changing `JSON5.parse` to `JSON.parse` in the examples above mitigates this vulnerability. This vulnerability is patched in json5 version 2.2.2 and later.
<p>Publish Date: 2022-12-24
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2022-46175>CVE-2022-46175</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.1</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: High
- Privileges Required: Low
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: Low
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://www.cve.org/CVERecord?id=CVE-2022-46175">https://www.cve.org/CVERecord?id=CVE-2022-46175</a></p>
<p>Release Date: 2022-12-24</p>
<p>Fix Resolution: json5 - 2.2.2</p>
</p>
</details>
<p></p>
|
True
|
CVE-2022-46175 (High) detected in json5-1.0.1.tgz, json5-2.1.1.tgz - ## CVE-2022-46175 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>json5-1.0.1.tgz</b>, <b>json5-2.1.1.tgz</b></p></summary>
<p>
<details><summary><b>json5-1.0.1.tgz</b></p></summary>
<p>JSON for humans.</p>
<p>Library home page: <a href="https://registry.npmjs.org/json5/-/json5-1.0.1.tgz">https://registry.npmjs.org/json5/-/json5-1.0.1.tgz</a></p>
<p>Path to dependency file: /browser/package.json</p>
<p>Path to vulnerable library: /browser/node_modules/loader-utils/node_modules/json5/package.json</p>
<p>
Dependency Hierarchy:
- react-scripts-3.2.0.tgz (Root Library)
- webpack-4.3.2.tgz
- loader-utils-1.2.3.tgz
- :x: **json5-1.0.1.tgz** (Vulnerable Library)
</details>
<details><summary><b>json5-2.1.1.tgz</b></p></summary>
<p>JSON for humans.</p>
<p>Library home page: <a href="https://registry.npmjs.org/json5/-/json5-2.1.1.tgz">https://registry.npmjs.org/json5/-/json5-2.1.1.tgz</a></p>
<p>Path to dependency file: /browser/package.json</p>
<p>Path to vulnerable library: /browser/node_modules/json5/package.json</p>
<p>
Dependency Hierarchy:
- react-scripts-3.2.0.tgz (Root Library)
- core-7.6.0.tgz
- :x: **json5-2.1.1.tgz** (Vulnerable Library)
</details>
<p>Found in base branch: <b>main</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
JSON5 is an extension to the popular JSON file format that aims to be easier to write and maintain by hand (e.g. for config files). The `parse` method of the JSON5 library before and including version `2.2.1` does not restrict parsing of keys named `__proto__`, allowing specially crafted strings to pollute the prototype of the resulting object. This vulnerability pollutes the prototype of the object returned by `JSON5.parse` and not the global Object prototype, which is the commonly understood definition of Prototype Pollution. However, polluting the prototype of a single object can have significant security impact for an application if the object is later used in trusted operations. This vulnerability could allow an attacker to set arbitrary and unexpected keys on the object returned from `JSON5.parse`. The actual impact will depend on how applications utilize the returned object and how they filter unwanted keys, but could include denial of service, cross-site scripting, elevation of privilege, and in extreme cases, remote code execution. `JSON5.parse` should restrict parsing of `__proto__` keys when parsing JSON strings to objects. As a point of reference, the `JSON.parse` method included in JavaScript ignores `__proto__` keys. Simply changing `JSON5.parse` to `JSON.parse` in the examples above mitigates this vulnerability. This vulnerability is patched in json5 version 2.2.2 and later.
<p>Publish Date: 2022-12-24
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2022-46175>CVE-2022-46175</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.1</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: High
- Privileges Required: Low
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: Low
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://www.cve.org/CVERecord?id=CVE-2022-46175">https://www.cve.org/CVERecord?id=CVE-2022-46175</a></p>
<p>Release Date: 2022-12-24</p>
<p>Fix Resolution: json5 - 2.2.2</p>
</p>
</details>
<p></p>
|
non_architecture
|
cve high detected in tgz tgz cve high severity vulnerability vulnerable libraries tgz tgz tgz json for humans library home page a href path to dependency file browser package json path to vulnerable library browser node modules loader utils node modules package json dependency hierarchy react scripts tgz root library webpack tgz loader utils tgz x tgz vulnerable library tgz json for humans library home page a href path to dependency file browser package json path to vulnerable library browser node modules package json dependency hierarchy react scripts tgz root library core tgz x tgz vulnerable library found in base branch main vulnerability details is an extension to the popular json file format that aims to be easier to write and maintain by hand e g for config files the parse method of the library before and including version does not restrict parsing of keys named proto allowing specially crafted strings to pollute the prototype of the resulting object this vulnerability pollutes the prototype of the object returned by parse and not the global object prototype which is the commonly understood definition of prototype pollution however polluting the prototype of a single object can have significant security impact for an application if the object is later used in trusted operations this vulnerability could allow an attacker to set arbitrary and unexpected keys on the object returned from parse the actual impact will depend on how applications utilize the returned object and how they filter unwanted keys but could include denial of service cross site scripting elevation of privilege and in extreme cases remote code execution parse should restrict parsing of proto keys when parsing json strings to objects as a point of reference the json parse method included in javascript ignores proto keys simply changing parse to json parse in the examples above mitigates this vulnerability this vulnerability is patched in version and later publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity high privileges required low user interaction none scope unchanged impact metrics confidentiality impact high integrity impact low availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution
| 0
|
235,699
| 18,056,394,413
|
IssuesEvent
|
2021-09-20 08:48:13
|
girlscript/winter-of-contributing
|
https://api.github.com/repos/girlscript/winter-of-contributing
|
closed
|
C_CPP : To find the kth smallest element using heap (Documentation)
|
documentation GWOC21 C/CPP
|
<hr>
## Description 📜
<!-- Please describe the issue in brief. -->
I want to create documentation explaining how to find the kth smallest element using heap with code examples.
<hr>
## Domain of Contribution 📊
<!----Please delete options that are not relevant. And in order to tick the check box just but x inside them for example [x] like this----->
- [x] C/CPP
<hr>
|
1.0
|
C_CPP : To find the kth smallest element using heap (Documentation) - <hr>
## Description 📜
<!-- Please describe the issue in brief. -->
I want to create documentation explaining how to find the kth smallest element using heap with code examples.
<hr>
## Domain of Contribution 📊
<!----Please delete options that are not relevant. And in order to tick the check box just but x inside them for example [x] like this----->
- [x] C/CPP
<hr>
|
non_architecture
|
c cpp to find the kth smallest element using heap documentation description 📜 i want to create documentation explaining how to find the kth smallest element using heap with code examples domain of contribution 📊 c cpp
| 0
|
3,744
| 6,617,592,797
|
IssuesEvent
|
2017-09-21 02:43:56
|
davodey/pearson-glp-pl
|
https://api.github.com/repos/davodey/pearson-glp-pl
|
opened
|
Selects - caret in multiple browsers...
|
Browser Compatibility - Firefox Browser Compatibility - IE11 Browser Compatibility - Safari duplicate Minor
|
The select caret is not clickable in all browsers Chrome, Firefox, Safari, and IE 11. "Basic Select" option on the same page works when I tap the caret.
Also, in IE 11 there is an additional bug. Two select-components are displayed.
CHROME, 61.0.3163.91 (Official Build) (64-bit)
FIREFOX 55.0.3 (64-bit)
SAFARI 10.1.2
IE 11, Win 10
|
True
|
Selects - caret in multiple browsers... - The select caret is not clickable in all browsers Chrome, Firefox, Safari, and IE 11. "Basic Select" option on the same page works when I tap the caret.
Also, in IE 11 there is an additional bug. Two select-components are displayed.

CHROME, 61.0.3163.91 (Official Build) (64-bit)
FIREFOX 55.0.3 (64-bit)
SAFARI 10.1.2
IE 11, Win 10
|
non_architecture
|
selects caret in multiple browsers the select caret is not clickable in all browsers chrome firefox safari and ie basic select option on the same page works when i tap the caret also in ie there is an additional bug two select components are displayed chrome official build bit firefox bit safari ie win
| 0
|
44,123
| 11,982,391,927
|
IssuesEvent
|
2020-04-07 12:53:20
|
tschaban/AFE-Firmware
|
https://api.github.com/repos/tschaban/AFE-Firmware
|
opened
|
after removing gate 2 it should be possible to configure relay as standard one
|
Defect
|
the relay which was assigned to gate 2
|
1.0
|
after removing gate 2 it should be possible to configure relay as standard one - the relay which was assigned to gate 2
|
non_architecture
|
after removing gate it should be possible to configure relay as standard one the relay which was assigned to gate
| 0
|
5,825
| 13,201,279,467
|
IssuesEvent
|
2020-08-14 09:50:09
|
boogle-lab/ssho-issue-board
|
https://api.github.com/repos/boogle-lab/ssho-issue-board
|
opened
|
스쇼 아키텍처 v2.0
|
ARCHITECTURE
|
## 스쇼 아키텍쳐 v2.0
### 시스템 기본 구조
- 시스템 디자인
- **마이크로 서비스 아키텍쳐(MSA)**
- 공통 인터페이스를 통해 각 서비스 간의 통신을 구현
- Docker 기반의 컨테이너 가상화를 통한 서비스 별 배포
- 시스템 설계도
### 서비스 별 구성 요소 및 역할
- React Native Application 서비스
- React Native v0.62.2 / React v16.11.0
- React Native CLI 기반의 프로젝트 빌드 및 배포
- MobX 기반의 상태 관리
- Core API 서비스
- Spring Boot v2.3.2
- Spring Data JPA / Spring Data Redis
- **회원 CRUD**
- **추천 상품 캐싱 및 캐시 데이터 조회**
- 상품 API 서비스
- Spring Boot v2.3.2
- Elasticsearch Rest High Level Client
- **쇼핑몰 크롤링 및 상품 index 업데이트**
- 상품 조회
- Spring Boot Scheduler 기반 scheduled API call(크롤링 및 상품 업데이터 트랜잭션)
- 로그 API 서비스
- Spring Boot v2.3.2
- Elasticsearch Rest High Level Client
- **로그 정보(스와이프 등) index**
- 로그 정보 조회 및 기타 집계
- 태그 API 서비스
- Spring Boot v2.3.2
- Elasticsearch Rest High Level Client
- **태그 정보(실제, 노출) index**
- 태그 정보 조회 및 기타 집계
- 상품 태깅 API 서비스
- flask v1.1.2
- tensorflow v2.3.0, opencv-python
- 태깅 학습 모델을 통해 상품 API가 크롤링 데이터의 이미지 URL로 요청하면 **관련 태그를 반환**
- 추천 API 서비스
- flask v1.1.2
- MF / FM 기반 추천 방식
- Core API 서비스로 부터 **추천 상품에 대한 요청을 처리**
### 데이터 저장소
- Elasticsearch
- 상품 index
- 로그 index
- MySQL
- 회원 table
- Redis
- 추천 상품 cache
### 운영 배포
- 각 API 서비스는 Docker 이미지를 생성해서 EC2 Docker Machine 위에 개별 포트를 열어서 구동
- Elasticsearch, MySQL, Redis는 각각 AWS Elasticsearch, AWS RDS, AWS ElastiCache 서비스를 통해 호스팅
- Flask API 서비스의 배포 전략에 대해서는 논의가 필요
- 해당 API 서비스의 큰 메모리에 따른 문제점
- EC2 자원의 효율적 사용을 위해 일부 서비스를 Spring Boot에서 Express(Node.js) or Django(Python)으로 포팅하는 방식도 고려 중
|
1.0
|
스쇼 아키텍처 v2.0 - ## 스쇼 아키텍쳐 v2.0
### 시스템 기본 구조
- 시스템 디자인
- **마이크로 서비스 아키텍쳐(MSA)**
- 공통 인터페이스를 통해 각 서비스 간의 통신을 구현
- Docker 기반의 컨테이너 가상화를 통한 서비스 별 배포
- 시스템 설계도

### 서비스 별 구성 요소 및 역할
- React Native Application 서비스
- React Native v0.62.2 / React v16.11.0
- React Native CLI 기반의 프로젝트 빌드 및 배포
- MobX 기반의 상태 관리
- Core API 서비스
- Spring Boot v2.3.2
- Spring Data JPA / Spring Data Redis
- **회원 CRUD**
- **추천 상품 캐싱 및 캐시 데이터 조회**
- 상품 API 서비스
- Spring Boot v2.3.2
- Elasticsearch Rest High Level Client
- **쇼핑몰 크롤링 및 상품 index 업데이트**
- 상품 조회
- Spring Boot Scheduler 기반 scheduled API call(크롤링 및 상품 업데이터 트랜잭션)
- 로그 API 서비스
- Spring Boot v2.3.2
- Elasticsearch Rest High Level Client
- **로그 정보(스와이프 등) index**
- 로그 정보 조회 및 기타 집계
- 태그 API 서비스
- Spring Boot v2.3.2
- Elasticsearch Rest High Level Client
- **태그 정보(실제, 노출) index**
- 태그 정보 조회 및 기타 집계
- 상품 태깅 API 서비스
- flask v1.1.2
- tensorflow v2.3.0, opencv-python
- 태깅 학습 모델을 통해 상품 API가 크롤링 데이터의 이미지 URL로 요청하면 **관련 태그를 반환**
- 추천 API 서비스
- flask v1.1.2
- MF / FM 기반 추천 방식
- Core API 서비스로 부터 **추천 상품에 대한 요청을 처리**
### 데이터 저장소
- Elasticsearch
- 상품 index
- 로그 index
- MySQL
- 회원 table
- Redis
- 추천 상품 cache
### 운영 배포
- 각 API 서비스는 Docker 이미지를 생성해서 EC2 Docker Machine 위에 개별 포트를 열어서 구동
- Elasticsearch, MySQL, Redis는 각각 AWS Elasticsearch, AWS RDS, AWS ElastiCache 서비스를 통해 호스팅
- Flask API 서비스의 배포 전략에 대해서는 논의가 필요
- 해당 API 서비스의 큰 메모리에 따른 문제점
- EC2 자원의 효율적 사용을 위해 일부 서비스를 Spring Boot에서 Express(Node.js) or Django(Python)으로 포팅하는 방식도 고려 중
|
architecture
|
스쇼 아키텍처 스쇼 아키텍쳐 시스템 기본 구조 시스템 디자인 마이크로 서비스 아키텍쳐 msa 공통 인터페이스를 통해 각 서비스 간의 통신을 구현 docker 기반의 컨테이너 가상화를 통한 서비스 별 배포 시스템 설계도 서비스 별 구성 요소 및 역할 react native application 서비스 react native react react native cli 기반의 프로젝트 빌드 및 배포 mobx 기반의 상태 관리 core api 서비스 spring boot spring data jpa spring data redis 회원 crud 추천 상품 캐싱 및 캐시 데이터 조회 상품 api 서비스 spring boot elasticsearch rest high level client 쇼핑몰 크롤링 및 상품 index 업데이트 상품 조회 spring boot scheduler 기반 scheduled api call 크롤링 및 상품 업데이터 트랜잭션 로그 api 서비스 spring boot elasticsearch rest high level client 로그 정보 스와이프 등 index 로그 정보 조회 및 기타 집계 태그 api 서비스 spring boot elasticsearch rest high level client 태그 정보 실제 노출 index 태그 정보 조회 및 기타 집계 상품 태깅 api 서비스 flask tensorflow opencv python 태깅 학습 모델을 통해 상품 api가 크롤링 데이터의 이미지 url로 요청하면 관련 태그를 반환 추천 api 서비스 flask mf fm 기반 추천 방식 core api 서비스로 부터 추천 상품에 대한 요청을 처리 데이터 저장소 elasticsearch 상품 index 로그 index mysql 회원 table redis 추천 상품 cache 운영 배포 각 api 서비스는 docker 이미지를 생성해서 docker machine 위에 개별 포트를 열어서 구동 elasticsearch mysql redis는 각각 aws elasticsearch aws rds aws elasticache 서비스를 통해 호스팅 flask api 서비스의 배포 전략에 대해서는 논의가 필요 해당 api 서비스의 큰 메모리에 따른 문제점 자원의 효율적 사용을 위해 일부 서비스를 spring boot에서 express node js or django python 으로 포팅하는 방식도 고려 중
| 1
|
3,285
| 9,380,979,177
|
IssuesEvent
|
2019-04-04 18:27:04
|
NLnetLabs/gantry
|
https://api.github.com/repos/NLnetLabs/gantry
|
opened
|
Re-write CLI wrapper Bash script in Python
|
architecture
|
The `cli` Bash script has grown beyond the intended scope and is suffering from lack of proper types, e.g `get_deployment_report` returns a pipe separated string instead of an array of object, and should be test-driven/unit-tested. My suggestion would be to re-write it in Python in a test-driven manner.
|
1.0
|
Re-write CLI wrapper Bash script in Python - The `cli` Bash script has grown beyond the intended scope and is suffering from lack of proper types, e.g `get_deployment_report` returns a pipe separated string instead of an array of object, and should be test-driven/unit-tested. My suggestion would be to re-write it in Python in a test-driven manner.
|
architecture
|
re write cli wrapper bash script in python the cli bash script has grown beyond the intended scope and is suffering from lack of proper types e g get deployment report returns a pipe separated string instead of an array of object and should be test driven unit tested my suggestion would be to re write it in python in a test driven manner
| 1
|
433,062
| 12,501,152,910
|
IssuesEvent
|
2020-06-02 00:23:06
|
eclipse-ee4j/glassfish
|
https://api.github.com/repos/eclipse-ee4j/glassfish
|
closed
|
show restart activity
|
Component: admin_gui ERR: Assignee Priority: Major Stale Type: Improvement
|
I was in the Applications tab and I click on restart Hudson. Hudson take a
little time to restart.. and when it's completed.. we see a message at the top
of the page..
that's fine.. but I have few applications installed, and I know idea if I click
on the right restart link.
We should have a icon beside the Enabled check.. like a round icon telling us
that this application is restarting.. and when it's completed.. we remove the icon.
#### Environment
Operating System: All
Platform: All
#### Affected Versions
[V3]
|
1.0
|
show restart activity - I was in the Applications tab and I click on restart Hudson. Hudson take a
little time to restart.. and when it's completed.. we see a message at the top
of the page..
that's fine.. but I have few applications installed, and I know idea if I click
on the right restart link.
We should have a icon beside the Enabled check.. like a round icon telling us
that this application is restarting.. and when it's completed.. we remove the icon.
#### Environment
Operating System: All
Platform: All
#### Affected Versions
[V3]
|
non_architecture
|
show restart activity i was in the applications tab and i click on restart hudson hudson take a little time to restart and when it s completed we see a message at the top of the page that s fine but i have few applications installed and i know idea if i click on the right restart link we should have a icon beside the enabled check like a round icon telling us that this application is restarting and when it s completed we remove the icon environment operating system all platform all affected versions
| 0
|
298,191
| 22,468,925,375
|
IssuesEvent
|
2022-06-22 06:08:00
|
jOOQ/jOOQ
|
https://api.github.com/repos/jOOQ/jOOQ
|
closed
|
Feedback about manual section "codegen-database-regex-flags"
|
C: Documentation P: Medium T: Support request E: All Editions
|
when muiti team work in many feature branch, but we can't merge it, each branch have their database version in one database , so when we fresh jooq code, all code can't run , how can we configurationn a particular table to generate code ,and other table code is no change?
----
See: https://www.jooq.org/doc/latest/manual/code-generation/codegen-advanced/codegen-config-database/codegen-database-regex-flags/
|
1.0
|
Feedback about manual section "codegen-database-regex-flags" -
when muiti team work in many feature branch, but we can't merge it, each branch have their database version in one database , so when we fresh jooq code, all code can't run , how can we configurationn a particular table to generate code ,and other table code is no change?
----
See: https://www.jooq.org/doc/latest/manual/code-generation/codegen-advanced/codegen-config-database/codegen-database-regex-flags/
|
non_architecture
|
feedback about manual section codegen database regex flags when muiti team work in many feature branch but we can t merge it each branch have their database version in one database so when we fresh jooq code all code can t run how can we configurationn a particular table to generate code and other table code is no change see
| 0
|
334,716
| 29,952,146,480
|
IssuesEvent
|
2023-06-23 02:46:46
|
apache/beam
|
https://api.github.com/repos/apache/beam
|
closed
|
[Failing Test]: SpannerWriteIT is failing on master.
|
java tests bug P2 failing test awaiting triage permared
|
### What happened?
https://ci-beam.apache.org/job/beam_PreCommit_Java_GCP_IO_Direct_Phrase/188/
The test seems to be failing because it is trying to insert null values in the field `Value` of the Spanner test table `user`.
The below exception is being thrown by the test on master branch w/o any changes.
```
com.google.cloud.spanner.SpannerException: FAILED_PRECONDITION: com.google.api.gax.rpc.FailedPreconditionException: io.grpc.StatusRuntimeException: FAILED_PRECONDITION: Value must not be NULL in table users.
```
### Issue Failure
Failure: Test is continually failing
### Issue Priority
Priority: 2 (backlog / disabled test but we think the product is healthy)
### Issue Components
- [ ] Component: Python SDK
- [X] Component: Java SDK
- [ ] Component: Go SDK
- [ ] Component: Typescript SDK
- [ ] Component: IO connector
- [ ] Component: Beam examples
- [ ] Component: Beam playground
- [ ] Component: Beam katas
- [ ] Component: Website
- [ ] Component: Spark Runner
- [ ] Component: Flink Runner
- [ ] Component: Samza Runner
- [ ] Component: Twister2 Runner
- [ ] Component: Hazelcast Jet Runner
- [ ] Component: Google Cloud Dataflow Runner
|
2.0
|
[Failing Test]: SpannerWriteIT is failing on master. - ### What happened?
https://ci-beam.apache.org/job/beam_PreCommit_Java_GCP_IO_Direct_Phrase/188/
The test seems to be failing because it is trying to insert null values in the field `Value` of the Spanner test table `user`.
The below exception is being thrown by the test on master branch w/o any changes.
```
com.google.cloud.spanner.SpannerException: FAILED_PRECONDITION: com.google.api.gax.rpc.FailedPreconditionException: io.grpc.StatusRuntimeException: FAILED_PRECONDITION: Value must not be NULL in table users.
```
### Issue Failure
Failure: Test is continually failing
### Issue Priority
Priority: 2 (backlog / disabled test but we think the product is healthy)
### Issue Components
- [ ] Component: Python SDK
- [X] Component: Java SDK
- [ ] Component: Go SDK
- [ ] Component: Typescript SDK
- [ ] Component: IO connector
- [ ] Component: Beam examples
- [ ] Component: Beam playground
- [ ] Component: Beam katas
- [ ] Component: Website
- [ ] Component: Spark Runner
- [ ] Component: Flink Runner
- [ ] Component: Samza Runner
- [ ] Component: Twister2 Runner
- [ ] Component: Hazelcast Jet Runner
- [ ] Component: Google Cloud Dataflow Runner
|
non_architecture
|
spannerwriteit is failing on master what happened the test seems to be failing because it is trying to insert null values in the field value of the spanner test table user the below exception is being thrown by the test on master branch w o any changes com google cloud spanner spannerexception failed precondition com google api gax rpc failedpreconditionexception io grpc statusruntimeexception failed precondition value must not be null in table users issue failure failure test is continually failing issue priority priority backlog disabled test but we think the product is healthy issue components component python sdk component java sdk component go sdk component typescript sdk component io connector component beam examples component beam playground component beam katas component website component spark runner component flink runner component samza runner component runner component hazelcast jet runner component google cloud dataflow runner
| 0
|
3,725
| 6,586,210,977
|
IssuesEvent
|
2017-09-13 16:25:37
|
espterm/espterm-firmware
|
https://api.github.com/repos/espterm/espterm-firmware
|
opened
|
Make ⌘V use slow pasting/bracketed pasting
|
compatibility enhancement front-end [low prio]
|
iTerm2:
<img width="604" alt="iTerm2 Screenshot" src="https://user-images.githubusercontent.com/5412095/30388598-71e22f7c-98b0-11e7-8a08-88c4d4a40b65.png">
This would require doing all input through something like the soft keyboard input which supports the `paste` event (the terminal should probably have an unfocused style, too)
|
True
|
Make ⌘V use slow pasting/bracketed pasting - iTerm2:
<img width="604" alt="iTerm2 Screenshot" src="https://user-images.githubusercontent.com/5412095/30388598-71e22f7c-98b0-11e7-8a08-88c4d4a40b65.png">
This would require doing all input through something like the soft keyboard input which supports the `paste` event (the terminal should probably have an unfocused style, too)
|
non_architecture
|
make ⌘v use slow pasting bracketed pasting img width alt screenshot src this would require doing all input through something like the soft keyboard input which supports the paste event the terminal should probably have an unfocused style too
| 0
|
6,598
| 14,937,691,454
|
IssuesEvent
|
2021-01-25 14:55:51
|
dotnet/docs
|
https://api.github.com/repos/dotnet/docs
|
closed
|
Bullet points and diagram don't seem to match
|
:book: guide - Modernizing w/ Windows containers :books: Area - .NET Architecture Guide :books: Area - .NET Guide Pri2 doc-bug dotnet-ebooks/tech dotnet/prod won't fix
|
The "Microservices" bullet point suggests "Azure Web Apps for Containers" as a suitable platform for microservices. However, the diagram doesn't show a tick for using "Azure App Service" as a suitable platform for a Cloud-Native (Microservices architecture) application architecture. Is this a mistake?
---
#### Document Details
⚠ *Do not edit this section. It is required for docs.microsoft.com ➟ GitHub issue linking.*
* ID: 45be6d71-575d-5d8d-bcdc-b6885ddbb487
* Version Independent ID: 7c37b77a-63fc-4fb4-ae32-02ac9c09e1c8
* Content: [Choosing Azure compute platforms for container-based applications](https://docs.microsoft.com/en-us/dotnet/architecture/modernize-with-azure-containers/modernize-existing-apps-to-cloud-optimized/choosing-azure-compute-options-for-container-based-applications#feedback)
* Content Source: [docs/architecture/modernize-with-azure-containers/modernize-existing-apps-to-cloud-optimized/choosing-azure-compute-options-for-container-based-applications.md](https://github.com/dotnet/docs/blob/master/docs/architecture/modernize-with-azure-containers/modernize-existing-apps-to-cloud-optimized/choosing-azure-compute-options-for-container-based-applications.md)
* Product: **dotnet**
* Technology: **dotnet-ebooks**
* GitHub Login: @nishanil
* Microsoft Alias: **nanil**
|
1.0
|
Bullet points and diagram don't seem to match - The "Microservices" bullet point suggests "Azure Web Apps for Containers" as a suitable platform for microservices. However, the diagram doesn't show a tick for using "Azure App Service" as a suitable platform for a Cloud-Native (Microservices architecture) application architecture. Is this a mistake?
---
#### Document Details
⚠ *Do not edit this section. It is required for docs.microsoft.com ➟ GitHub issue linking.*
* ID: 45be6d71-575d-5d8d-bcdc-b6885ddbb487
* Version Independent ID: 7c37b77a-63fc-4fb4-ae32-02ac9c09e1c8
* Content: [Choosing Azure compute platforms for container-based applications](https://docs.microsoft.com/en-us/dotnet/architecture/modernize-with-azure-containers/modernize-existing-apps-to-cloud-optimized/choosing-azure-compute-options-for-container-based-applications#feedback)
* Content Source: [docs/architecture/modernize-with-azure-containers/modernize-existing-apps-to-cloud-optimized/choosing-azure-compute-options-for-container-based-applications.md](https://github.com/dotnet/docs/blob/master/docs/architecture/modernize-with-azure-containers/modernize-existing-apps-to-cloud-optimized/choosing-azure-compute-options-for-container-based-applications.md)
* Product: **dotnet**
* Technology: **dotnet-ebooks**
* GitHub Login: @nishanil
* Microsoft Alias: **nanil**
|
architecture
|
bullet points and diagram don t seem to match the microservices bullet point suggests azure web apps for containers as a suitable platform for microservices however the diagram doesn t show a tick for using azure app service as a suitable platform for a cloud native microservices architecture application architecture is this a mistake document details ⚠ do not edit this section it is required for docs microsoft com ➟ github issue linking id bcdc version independent id content content source product dotnet technology dotnet ebooks github login nishanil microsoft alias nanil
| 1
|
45,308
| 2,925,092,456
|
IssuesEvent
|
2015-06-26 01:28:33
|
google/guice
|
https://api.github.com/repos/google/guice
|
closed
|
Lifecycle support
|
Component-NewExtension enhancement imported Priority-Medium
|
_From [hani@formicary.net](https://code.google.com/u/103141376271880053273/) on March 14, 2007 09:22:31_
Support for JSR\-250 \(javax.annotation\) would also be very useful for all those people using init\(\)
methods and the list.
The mapping I think is:
`@`PostConstruct \-> Called right after construction
`@`Resource \-> Analogous to `@`Inject
`@`PreDestroy \-> No concept of destruction, is there?
`@`Generated \-> Doesn't apply
_Original issue: http://code.google.com/p/google-guice/issues/detail?id=62_
|
1.0
|
Lifecycle support - _From [hani@formicary.net](https://code.google.com/u/103141376271880053273/) on March 14, 2007 09:22:31_
Support for JSR\-250 \(javax.annotation\) would also be very useful for all those people using init\(\)
methods and the list.
The mapping I think is:
`@`PostConstruct \-> Called right after construction
`@`Resource \-> Analogous to `@`Inject
`@`PreDestroy \-> No concept of destruction, is there?
`@`Generated \-> Doesn't apply
_Original issue: http://code.google.com/p/google-guice/issues/detail?id=62_
|
non_architecture
|
lifecycle support from on march support for jsr javax annotation would also be very useful for all those people using init methods and the list the mapping i think is postconstruct gt called right after construction resource gt analogous to inject predestroy gt no concept of destruction is there generated gt doesn t apply original issue
| 0
|
758,408
| 26,554,366,966
|
IssuesEvent
|
2023-01-20 10:40:58
|
Warcraft-GoA-Development-Team/Warcraft-Guardians-of-Azeroth-2
|
https://api.github.com/repos/Warcraft-GoA-Development-Team/Warcraft-Guardians-of-Azeroth-2
|
opened
|
Legion Story Cycle
|
suggestion :question: priority low :grey_exclamation:
|
<!--
**DO NOT REMOVE PRE-EXISTING LINES**
------------------------------------------------------------------------------------------------------------
-->
**Describe your suggestion in full detail below:**
Very, very rough sketch for a Legion Story Cycle, will need to be fleshed out considerably. Suggestions welcomed.
- **Start**
- [ ] **Decision:** Fel-aligned character summons the Legion.
- Based on Learning / Artefact ownership / Magic traits?
- [ ] Write text, personal event for the summoner, interaction with Archimonde.
- [x] Write text, general event for everyone else describing Archimonde's arrival.
- [ ] **Event:** Archimonde arrives near Hyjall, takes Haldarr duchy, gains MaAs.
- [ ] **Story Cycle:** Archimonde begins pushing towards Hyjall.
- [ ] **Event:** If Archimonde takes Hyjall?
|
1.0
|
Legion Story Cycle - <!--
**DO NOT REMOVE PRE-EXISTING LINES**
------------------------------------------------------------------------------------------------------------
-->
**Describe your suggestion in full detail below:**
Very, very rough sketch for a Legion Story Cycle, will need to be fleshed out considerably. Suggestions welcomed.
- **Start**
- [ ] **Decision:** Fel-aligned character summons the Legion.
- Based on Learning / Artefact ownership / Magic traits?
- [ ] Write text, personal event for the summoner, interaction with Archimonde.
- [x] Write text, general event for everyone else describing Archimonde's arrival.
- [ ] **Event:** Archimonde arrives near Hyjall, takes Haldarr duchy, gains MaAs.
- [ ] **Story Cycle:** Archimonde begins pushing towards Hyjall.
- [ ] **Event:** If Archimonde takes Hyjall?
|
non_architecture
|
legion story cycle do not remove pre existing lines describe your suggestion in full detail below very very rough sketch for a legion story cycle will need to be fleshed out considerably suggestions welcomed start decision fel aligned character summons the legion based on learning artefact ownership magic traits write text personal event for the summoner interaction with archimonde write text general event for everyone else describing archimonde s arrival event archimonde arrives near hyjall takes haldarr duchy gains maas story cycle archimonde begins pushing towards hyjall event if archimonde takes hyjall
| 0
|
6,713
| 15,058,276,452
|
IssuesEvent
|
2021-02-03 23:08:33
|
kubernetes/kubernetes
|
https://api.github.com/repos/kubernetes/kubernetes
|
reopened
|
Write PodProxyWithPath & ServiceProxyWithPath test+promote - + 12 endpoint coverage
|
area/conformance needs-triage sig/architecture sig/testing
|
# Progress <code>[3/6]</code>
- [X] APISnoop org-flow : [PodProxyWithPath.org](https://github.com/cncf/apisnoop/blob/master/tickets/k8s/PodProxyWithPath.org)
- [X] test approval issue : [kubernetes/kubernetes#95500](https://github.com/kubernetes/kubernetes/issues/95500)
- [x] test pr : [kuberenetes/kubernetes#95503](https://github.com/kubernetes/kubernetes/pull/95503)
- [x] two weeks soak start date : testgrid-link
- [ ] two weeks soak end date :
- [ ] test promotion pr : kubernetes/kubernetes#?
# PodProxyWithPath
# Identifying an untested feature Using APISnoop
According to this APIsnoop query, there are still some remaining ProxyWithPath endpoints which are untested.
with this query you can filter untested endpoints by their category and eligiblity for conformance. e.g below shows a query to find all conformance eligible untested,stable,core endpoints
```sql-mode
SELECT
endpoint,
-- k8s_action,
path,
-- description,
kind
FROM testing.untested_stable_endpoint
where eligible is true
and category = 'core'
and endpoint like '%PodProxyWithPath'
order by kind, endpoint desc
limit 25;
```
```example
endpoint | path | kind
------------------------------------------------|---------------------------------------------------------|-----------------
connectCoreV1PutNamespacedPodProxyWithPath | /api/v1/namespaces/{namespace}/pods/{name}/proxy/{path} | PodProxyOptions
connectCoreV1PostNamespacedPodProxyWithPath | /api/v1/namespaces/{namespace}/pods/{name}/proxy/{path} | PodProxyOptions
connectCoreV1PatchNamespacedPodProxyWithPath | /api/v1/namespaces/{namespace}/pods/{name}/proxy/{path} | PodProxyOptions
connectCoreV1OptionsNamespacedPodProxyWithPath | /api/v1/namespaces/{namespace}/pods/{name}/proxy/{path} | PodProxyOptions
connectCoreV1HeadNamespacedPodProxyWithPath | /api/v1/namespaces/{namespace}/pods/{name}/proxy/{path} | PodProxyOptions
connectCoreV1DeleteNamespacedPodProxyWithPath | /api/v1/namespaces/{namespace}/pods/{name}/proxy/{path} | PodProxyOptions
(6 rows)
```
# API Reference and feature documentation
- [Kubernetes API Reference Docs](https://kubernetes.io/docs/reference/kubernetes-api/)
- [client-go](https://github.com/kubernetes/client-go/blob/master/kubernetes/typed/core/v1)
- [Kubernetes 1.19: Pod v1 Core: Proxy Operations](https://kubernetes.io/docs/reference/generated/kubernetes-api/v1.19/#-strong-proxy-operations-pod-v1-core-strong-)
# The mock test
## Test outline
1. Create a pod with a static label using the agnhost image
2. Confirm that the pod is in the running phase
3. Iterate through a list of http methods and check the response from the porter app
4. Confirm that each response code is 200 OK
## Test the functionality in Go
```go
package main
import (
// "encoding/json"
"context"
"flag"
"fmt"
"net/http"
"os"
"time"
v1 "k8s.io/api/core/v1"
// "k8s.io/client-go/dynamic"
// "k8s.io/apimachinery/pkg/runtime/schema"
metav1 "k8s.io/apimachinery/pkg/apis/meta/v1"
"k8s.io/apimachinery/pkg/util/wait"
"k8s.io/client-go/kubernetes"
"k8s.io/client-go/transport"
// "k8s.io/apimachinery/pkg/types"
"k8s.io/client-go/tools/clientcmd"
)
// helper function that mirrors framework.ExpectNoError
func ExpectNoError(err error, msg string) {
if err != nil {
errMsg := msg + fmt.Sprintf(" %v\n", err)
os.Stderr.WriteString(errMsg)
os.Exit(1)
}
}
// helper function that mirrors framework.ExpectEqual
func ExpectEqual(a int, b int, msg string, i interface{}) {
if a != b {
errMsg := msg + fmt.Sprintf(" %v\n", i)
os.Stderr.WriteString(errMsg)
os.Exit(1)
}
}
// helper function to inspect various interfaces
func inspect(level int, name string, i interface{}) {
fmt.Printf("Inspecting: %s\n", name)
fmt.Printf("Inspect level: %d Type: %T\n", level, i)
switch level {
case 1:
fmt.Printf("%+v\n\n", i)
case 2:
fmt.Printf("%#v\n\n", i)
default:
fmt.Printf("%v\n\n", i)
}
}
const (
podRetryPeriod = 1 * time.Second
podRetryTimeout = 1 * time.Minute
)
func main() {
// uses the current context in kubeconfig
kubeconfig := flag.String("kubeconfig", fmt.Sprintf("%v/%v/%v", os.Getenv("HOME"), ".kube", "config"), "(optional) absolute path to the kubeconfig file")
flag.Parse()
config, err := clientcmd.BuildConfigFromFlags("", *kubeconfig)
ExpectNoError(err, "Could not build config from flags")
// make our work easier to find in the audit_event queries
config.UserAgent = "live-test-writing"
// creates the clientset
ClientSet, _ := kubernetes.NewForConfig(config)
// DynamicClientSet, _ := dynamic.NewForConfig(config)
// podResource := schema.GroupVersionResource{Group: "", Version: "v1", Resource: "pods"}
// TEST BEGINS HERE
ns := "default" // f.Namespace.Name
httpVerbs := []string{"DELETE", "GET", "HEAD", "OPTIONS", "PATCH", "POST", "PUT"}
// httpVerbs := []string{"HEAD"}
// httpVerbs := []string{"OPTIONS"}
fmt.Println("Creating pod...")
_, err = ClientSet.CoreV1().Pods(ns).Create(context.TODO(), &v1.Pod{
ObjectMeta: metav1.ObjectMeta{
Name: "agnhost",
Labels: map[string]string{
"test": "response"},
},
Spec: v1.PodSpec{
Containers: []v1.Container{{
Image: "us.gcr.io/k8s-artifacts-prod/e2e-test-images/agnhost:2.21",
Name: "agnhost",
Command: []string{"/agnhost", "porter"},
Env: []v1.EnvVar{{
Name: "SERVE_PORT_80",
Value: "foo",
}},
}},
RestartPolicy: v1.RestartPolicyNever,
}}, metav1.CreateOptions{})
ExpectNoError(err, "failed to create pod")
err = wait.PollImmediate(podRetryPeriod, podRetryTimeout, checkPodStatus(ClientSet, "test=response"))
ExpectNoError(err, "Pod didn't start within time out period")
transportCfg, err := config.TransportConfig()
ExpectNoError(err, "Error creating transportCfg")
restTransport, err := transport.New(transportCfg)
ExpectNoError(err, "Error creating restTransport")
client := &http.Client{
CheckRedirect: func(req *http.Request, via []*http.Request) error {
return http.ErrUseLastResponse
},
Transport: restTransport,
}
for _, httpVerb := range httpVerbs {
urlString := config.Host + "/api/v1/namespaces/" + ns + "/pods/agnhost/proxy/some/path/with/" + httpVerb
fmt.Printf("Starting http.Client for %s\n", urlString)
request, err := http.NewRequest(httpVerb, urlString, nil)
ExpectNoError(err, "processing request")
resp, err := client.Do(request)
ExpectNoError(err, "processing response")
defer resp.Body.Close()
fmt.Printf("http.Client request:%s StatusCode:%d\n", httpVerb, resp.StatusCode)
ExpectEqual(resp.StatusCode, 200, "The resp.StatusCode returned: %d", resp.StatusCode)
}
// TEST ENDS HERE
fmt.Println("[status] complete")
}
func checkPodStatus(cs *kubernetes.Clientset, label string) func() (bool, error) {
return func() (bool, error) {
var err error
list, err := cs.CoreV1().Pods("default").List(context.TODO(), metav1.ListOptions{
LabelSelector: label})
if err != nil {
return false, err
}
if list.Items[0].Status.Phase != "Running" {
fmt.Printf("Pod Quantity: %d Status: %s\n", len(list.Items), list.Items[0].Status.Phase)
return false, err
}
fmt.Printf("Pod Status: %v\n", list.Items[0].Status.Phase)
return true, nil
}
}
```
# Verifying increase in coverage with APISnoop
## Reset stats
```sql-mode
delete from testing.audit_event;
```
```example
DELETE 977385
```
## Discover useragents:
```sql-mode
select distinct useragent
from testing.audit_event
where useragent like 'live%';
```
```example
useragent
-------------------
live-test-writing
(1 row)
```
## List endpoints hit by the test:
```sql-mode
select * from testing.endpoint_hit_by_new_test ORDER BY hit_by_ete;
```
```example
useragent | endpoint | hit_by_ete | hit_by_new_test
-------------------|-----------------------------------------------|------------|-----------------
live-test-writing | connectCoreV1PostNamespacedPodProxyWithPath | f | 9
live-test-writing | connectCoreV1PatchNamespacedPodProxyWithPath | f | 9
live-test-writing | connectCoreV1DeleteNamespacedPodProxyWithPath | f | 9
live-test-writing | connectCoreV1PutNamespacedPodProxyWithPath | f | 9
live-test-writing | connectCoreV1GetNamespacedPodProxyWithPath | t | 18
live-test-writing | listCoreV1NamespacedPod | t | 42
live-test-writing | createCoreV1NamespacedPod | t | 6
(7 rows)
```
## Display endpoint coverage change:
```sql-mode
select * from testing.projected_change_in_coverage;
```
```example
category | total_endpoints | old_coverage | new_coverage | change_in_number
---------------|-----------------|--------------|--------------|------------------
test_coverage | 831 | 306 | 310 | 4
(1 row)
```
# Final notes
If a test with these calls gets merged, **test coverage will go up by 4 points**
This test is also created with the goal of conformance promotion.
---
/sig testing
/sig architecture
/area conformance
# Exploring / Questions about missing endpoints
Where/How does PATCH/HEAD/OPTIONS requests for the following endpoints line up with the API reference?
- connectCoreV1PatchNamespacedPodProxyWithPath
- connectCoreV1HeadNamespacedPodProxyWithPath
- connectCoreV1OptionsNamespacedPodProxyWithPath
**Pod v1 core: Proxy Operations**
<https://kubernetes.io/docs/reference/generated/kubernetes-api/v1.19/#-strong-proxy-operations-pod-v1-core-strong>-
| httpVerb | Endpoint |
|-------- |-------------------------- |
| POST | Create Connect Proxy |
| | Create Connect Proxy Path |
| DELETE | Delete Connect Proxy |
| | Delete Connect Proxy Path |
| GET | Get Connect Proxy |
| | Get Connect Proxy Path |
| HEAD | Head Connect Proxy |
| | Head Connect Proxy Path |
| PUT | Replace Connect Proxy |
| | Replace Connect Proxy Path |
# Locate why 2 endpoints are missing
<https://apisnoop.cncf.io/conformance-progress/endpoints/1.9.0?filter=promotedWithoutTests&filter=untested> shows the following endpoints are listed as valid endpoints;
- connectCoreV1HeadNamespacedPodProxyWithPath
- connectCoreV1OptionsNamespacedPodProxyWithPath
## Missing HEAD requests
These requests are getting logged as a `get` verb.
Line 24520: api/openapi-spec
```json
"head": {
"consumes": [
"*/*"
],
"description": "connect HEAD requests to proxy of Pod",
"operationId": "connectCoreV1HeadNamespacedPodProxyWithPath",
"produces": [
"*/*"
],
"responses": {
"200": {
"description": "OK",
"schema": {
"type": "string"
}
},
"401": {
"description": "Unauthorized"
}
},
"schemes": [
"https"
],
"tags": [
"core_v1"
],
"x-kubernetes-action": "connect",
"x-kubernetes-group-version-kind": {
"group": "",
"kind": "PodProxyOptions",
"version": "v1"
}
```
## Missing OPTIONS requests
Line 24553: api/openapi-spec
```json
"options": {
"consumes": [
"*/*"
],
"description": "connect OPTIONS requests to proxy of Pod",
"operationId": "connectCoreV1OptionsNamespacedPodProxyWithPath",
"produces": [
"*/*"
],
"responses": {
"200": {
"description": "OK",
"schema": {
"type": "string"
}
},
"401": {
"description": "Unauthorized"
}
},
"schemes": [
"https"
],
"tags": [
"core_v1"
],
"x-kubernetes-action": "connect",
"x-kubernetes-group-version-kind": {
"group": "",
"kind": "PodProxyOptions",
"version": "v1"
}
```
## Verbs missing
Looking at snoopUtils.py there doesn't look to be a mapping for the above methods.
```python
VERB_TO_METHOD={
'get': 'get',
'list': 'get',
'proxy': 'proxy',
'create': 'post',
'post':'post',
'put':'post',
'update':'put',
'patch':'patch',
'connect':'connect',
'delete':'delete',
'deletecollection':'delete',
'watch':'get'
}
```
# ServiceProxyWithPath
- [X] APISnoop org-flow : [ServiceProxyWithPath.org](https://github.com/cncf/apisnoop/blob/master/tickets/k8s/ServiceProxyWithPath.org)
# Identifying an untested feature Using APISnoop
According to this APIsnoop query, there are still some remaining ProxyWithPath endpoints which are untested.
with this query you can filter untested endpoints by their category and eligiblity for conformance. e.g below shows a query to find all conformance eligible untested,stable,core endpoints
```sql-mode
SELECT
endpoint,
-- k8s_action,
path,
-- description,
kind
FROM testing.untested_stable_endpoint
where eligible is true
and category = 'core'
and endpoint like '%ServiceProxyWithPath'
order by kind, endpoint desc
limit 25;
```
```example
endpoint | path | kind
----------------------------------------------------|-------------------------------------------------------------|---------------------
connectCoreV1PutNamespacedServiceProxyWithPath | /api/v1/namespaces/{namespace}/services/{name}/proxy/{path} | ServiceProxyOptions
connectCoreV1PostNamespacedServiceProxyWithPath | /api/v1/namespaces/{namespace}/services/{name}/proxy/{path} | ServiceProxyOptions
connectCoreV1PatchNamespacedServiceProxyWithPath | /api/v1/namespaces/{namespace}/services/{name}/proxy/{path} | ServiceProxyOptions
connectCoreV1OptionsNamespacedServiceProxyWithPath | /api/v1/namespaces/{namespace}/services/{name}/proxy/{path} | ServiceProxyOptions
connectCoreV1HeadNamespacedServiceProxyWithPath | /api/v1/namespaces/{namespace}/services/{name}/proxy/{path} | ServiceProxyOptions
connectCoreV1DeleteNamespacedServiceProxyWithPath | /api/v1/namespaces/{namespace}/services/{name}/proxy/{path} | ServiceProxyOptions
(6 rows)
```
# API Reference and feature documentation
- [Kubernetes API Reference Docs](https://kubernetes.io/docs/reference/kubernetes-api/)
- [client-go](https://github.com/kubernetes/client-go/blob/master/kubernetes/typed/core/v1)
- [Kubernetes 1.19: Service v1 Core: Proxy Operations](https://kubernetes.io/docs/reference/generated/kubernetes-api/v1.19/#-strong-proxy-operations-service-v1-core-strong-)
# The mock test
## Test outline
1. Create a pod with a static label using the agnhost image
2. Confirm that the pod is in the running phase
3. Create a service and link it to the pod
4. Iterate through a list of http methods and check the response from the porter app
5. Confirm that each response code is 200 OK
## Test the functionality in Go
```go
package main
import (
// "encoding/json"
"context"
"flag"
"fmt"
"net/http"
"os"
"time"
v1 "k8s.io/api/core/v1"
// "k8s.io/client-go/dynamic"
// "k8s.io/apimachinery/pkg/runtime/schema"
metav1 "k8s.io/apimachinery/pkg/apis/meta/v1"
"k8s.io/apimachinery/pkg/util/wait"
"k8s.io/client-go/kubernetes"
"k8s.io/client-go/transport"
// "k8s.io/apimachinery/pkg/types"
"k8s.io/client-go/tools/clientcmd"
"k8s.io/apimachinery/pkg/util/intstr"
)
// helper function that mirrors framework.ExpectNoError
func ExpectNoError(err error, msg string) {
if err != nil {
errMsg := msg + fmt.Sprintf(" %v\n", err)
os.Stderr.WriteString(errMsg)
os.Exit(1)
}
}
// helper function that mirrors framework.ExpectEqual
func ExpectEqual(a int, b int, msg string, i interface{}) {
if a != b {
errMsg := msg + fmt.Sprintf(" %v\n", i)
os.Stderr.WriteString(errMsg)
os.Exit(1)
}
}
// helper function to inspect various interfaces
func inspect(level int, name string, i interface{}) {
fmt.Printf("Inspecting: %s\n", name)
fmt.Printf("Inspect level: %d Type: %T\n", level, i)
switch level {
case 1:
fmt.Printf("%+v\n\n", i)
case 2:
fmt.Printf("%#v\n\n", i)
default:
fmt.Printf("%v\n\n", i)
}
}
const (
podRetryPeriod = 1 * time.Second
podRetryTimeout = 1 * time.Minute
)
func main() {
// uses the current context in kubeconfig
kubeconfig := flag.String("kubeconfig", fmt.Sprintf("%v/%v/%v", os.Getenv("HOME"), ".kube", "config"), "(optional) absolute path to the kubeconfig file")
flag.Parse()
config, err := clientcmd.BuildConfigFromFlags("", *kubeconfig)
ExpectNoError(err, "Could not build config from flags")
// make our work easier to find in the audit_event queries
config.UserAgent = "live-test-writing"
// creates the clientset
ClientSet, _ := kubernetes.NewForConfig(config)
// DynamicClientSet, _ := dynamic.NewForConfig(config)
// podResource := schema.GroupVersionResource{Group: "", Version: "v1", Resource: "pods"}
// TEST BEGINS HERE
ns := "default" // f.Namespace.Name
fmt.Println("Creating pod...")
_, err = ClientSet.CoreV1().Pods(ns).Create(context.TODO(), &v1.Pod{
ObjectMeta: metav1.ObjectMeta{
Name: "agnhost",
Labels: map[string]string{
"test": "response"},
},
Spec: v1.PodSpec{
Containers: []v1.Container{{
Image: "us.gcr.io/k8s-artifacts-prod/e2e-test-images/agnhost:2.21",
Name: "agnhost",
Command: []string{"/agnhost", "porter"},
Env: []v1.EnvVar{{
Name: "SERVE_PORT_80",
Value: "foo",
}},
}},
RestartPolicy: v1.RestartPolicyNever,
}}, metav1.CreateOptions{})
ExpectNoError(err, "failed to create pod")
err = wait.PollImmediate(podRetryPeriod, podRetryTimeout, checkPodStatus(ClientSet, "test=response"))
ExpectNoError(err, "Pod didn't start within time out period")
_, err = ClientSet.CoreV1().Services(ns).Create(context.TODO(), &v1.Service{
ObjectMeta: metav1.ObjectMeta{
Name: "test-service",
Namespace: ns,
Labels: map[string]string{
"test": "response",
},
},
Spec: v1.ServiceSpec{
Ports: []v1.ServicePort{{
Port: 80,
TargetPort: intstr.FromInt(80),
Protocol: v1.ProtocolTCP,
}},
Selector: map[string]string{
"test": "response",
},
}}, metav1.CreateOptions{})
ExpectNoError(err, "Failed to create the service")
fmt.Println("Service created")
transportCfg, err := config.TransportConfig()
ExpectNoError(err, "Error creating transportCfg")
restTransport, err := transport.New(transportCfg)
ExpectNoError(err, "Error creating restTransport")
client := &http.Client{
CheckRedirect: func(req *http.Request, via []*http.Request) error {
return http.ErrUseLastResponse
},
Transport: restTransport,
}
time.Sleep(1 * time.Second) // not required in e2e test
httpVerbs := []string{"DELETE", "GET", "HEAD", "OPTIONS", "PATCH", "POST", "PUT"}
for _, httpVerb := range httpVerbs {
urlString := config.Host + "/api/v1/namespaces/" + ns + "/services/test-service/proxy/some/path/with/" + httpVerb
fmt.Printf("Starting http.Client for %s\n", urlString)
request, err := http.NewRequest(httpVerb, urlString, nil)
ExpectNoError(err, "processing request")
resp, err := client.Do(request)
ExpectNoError(err, "processing response")
defer resp.Body.Close()
fmt.Printf("http.Client request:%s StatusCode:%d\n", httpVerb, resp.StatusCode)
ExpectEqual(resp.StatusCode, 200, "The resp.StatusCode returned: %d", resp.StatusCode)
}
// TEST ENDS HERE
fmt.Println("[status] complete")
}
func checkPodStatus(cs *kubernetes.Clientset, label string) func() (bool, error) {
return func() (bool, error) {
var err error
list, err := cs.CoreV1().Pods("default").List(context.TODO(), metav1.ListOptions{
LabelSelector: label})
if err != nil {
return false, err
}
if list.Items[0].Status.Phase != "Running" {
fmt.Printf("Pod Quantity: %d Status: %s\n", len(list.Items), list.Items[0].Status.Phase)
return false, err
}
fmt.Printf("Pod Status: %v\n", list.Items[0].Status.Phase)
return true, nil
}
}
```
# Verifying increase in coverage with APISnoop
## Reset stats
```sql-mode
delete from testing.audit_event;
```
```example
DELETE 89563
```
## Discover useragents:
```sql-mode
select distinct useragent
from testing.audit_event
where useragent like 'live%';
```
```example
useragent
-------------------
live-test-writing
(1 row)
```
## List endpoints hit by the test:
```sql-mode
select * from testing.endpoint_hit_by_new_test ORDER BY hit_by_ete;
```
```example
useragent | endpoint | hit_by_ete | hit_by_new_test
-------------------|---------------------------------------------------|------------|-----------------
live-test-writing | connectCoreV1DeleteNamespacedServiceProxyWithPath | f | 12
live-test-writing | connectCoreV1PatchNamespacedServiceProxyWithPath | f | 12
live-test-writing | connectCoreV1PostNamespacedServiceProxyWithPath | f | 12
live-test-writing | connectCoreV1PutNamespacedServiceProxyWithPath | f | 12
live-test-writing | listCoreV1NamespacedPod | t | 24
live-test-writing | connectCoreV1GetNamespacedServiceProxyWithPath | t | 24
live-test-writing | createCoreV1NamespacedPod | t | 8
live-test-writing | createCoreV1NamespacedService | t | 8
(8 rows)
```
## Display endpoint coverage change:
```sql-mode
select * from testing.projected_change_in_coverage;
```
```example
category | total_endpoints | old_coverage | new_coverage | change_in_number
---------------|-----------------|--------------|--------------|------------------
test_coverage | 831 | 306 | 310 | 4
(1 row)
```
# Final notes
If a test with these calls gets merged, **test coverage will go up by 4 points**
This test is also created with the goal of conformance promotion.
---
|
1.0
|
Write PodProxyWithPath & ServiceProxyWithPath test+promote - + 12 endpoint coverage - # Progress <code>[3/6]</code>
- [X] APISnoop org-flow : [PodProxyWithPath.org](https://github.com/cncf/apisnoop/blob/master/tickets/k8s/PodProxyWithPath.org)
- [X] test approval issue : [kubernetes/kubernetes#95500](https://github.com/kubernetes/kubernetes/issues/95500)
- [x] test pr : [kuberenetes/kubernetes#95503](https://github.com/kubernetes/kubernetes/pull/95503)
- [x] two weeks soak start date : testgrid-link
- [ ] two weeks soak end date :
- [ ] test promotion pr : kubernetes/kubernetes#?
# PodProxyWithPath
# Identifying an untested feature Using APISnoop
According to this APIsnoop query, there are still some remaining ProxyWithPath endpoints which are untested.
with this query you can filter untested endpoints by their category and eligiblity for conformance. e.g below shows a query to find all conformance eligible untested,stable,core endpoints
```sql-mode
SELECT
endpoint,
-- k8s_action,
path,
-- description,
kind
FROM testing.untested_stable_endpoint
where eligible is true
and category = 'core'
and endpoint like '%PodProxyWithPath'
order by kind, endpoint desc
limit 25;
```
```example
endpoint | path | kind
------------------------------------------------|---------------------------------------------------------|-----------------
connectCoreV1PutNamespacedPodProxyWithPath | /api/v1/namespaces/{namespace}/pods/{name}/proxy/{path} | PodProxyOptions
connectCoreV1PostNamespacedPodProxyWithPath | /api/v1/namespaces/{namespace}/pods/{name}/proxy/{path} | PodProxyOptions
connectCoreV1PatchNamespacedPodProxyWithPath | /api/v1/namespaces/{namespace}/pods/{name}/proxy/{path} | PodProxyOptions
connectCoreV1OptionsNamespacedPodProxyWithPath | /api/v1/namespaces/{namespace}/pods/{name}/proxy/{path} | PodProxyOptions
connectCoreV1HeadNamespacedPodProxyWithPath | /api/v1/namespaces/{namespace}/pods/{name}/proxy/{path} | PodProxyOptions
connectCoreV1DeleteNamespacedPodProxyWithPath | /api/v1/namespaces/{namespace}/pods/{name}/proxy/{path} | PodProxyOptions
(6 rows)
```
# API Reference and feature documentation
- [Kubernetes API Reference Docs](https://kubernetes.io/docs/reference/kubernetes-api/)
- [client-go](https://github.com/kubernetes/client-go/blob/master/kubernetes/typed/core/v1)
- [Kubernetes 1.19: Pod v1 Core: Proxy Operations](https://kubernetes.io/docs/reference/generated/kubernetes-api/v1.19/#-strong-proxy-operations-pod-v1-core-strong-)
# The mock test
## Test outline
1. Create a pod with a static label using the agnhost image
2. Confirm that the pod is in the running phase
3. Iterate through a list of http methods and check the response from the porter app
4. Confirm that each response code is 200 OK
## Test the functionality in Go
```go
package main
import (
// "encoding/json"
"context"
"flag"
"fmt"
"net/http"
"os"
"time"
v1 "k8s.io/api/core/v1"
// "k8s.io/client-go/dynamic"
// "k8s.io/apimachinery/pkg/runtime/schema"
metav1 "k8s.io/apimachinery/pkg/apis/meta/v1"
"k8s.io/apimachinery/pkg/util/wait"
"k8s.io/client-go/kubernetes"
"k8s.io/client-go/transport"
// "k8s.io/apimachinery/pkg/types"
"k8s.io/client-go/tools/clientcmd"
)
// helper function that mirrors framework.ExpectNoError
func ExpectNoError(err error, msg string) {
if err != nil {
errMsg := msg + fmt.Sprintf(" %v\n", err)
os.Stderr.WriteString(errMsg)
os.Exit(1)
}
}
// helper function that mirrors framework.ExpectEqual
func ExpectEqual(a int, b int, msg string, i interface{}) {
if a != b {
errMsg := msg + fmt.Sprintf(" %v\n", i)
os.Stderr.WriteString(errMsg)
os.Exit(1)
}
}
// helper function to inspect various interfaces
func inspect(level int, name string, i interface{}) {
fmt.Printf("Inspecting: %s\n", name)
fmt.Printf("Inspect level: %d Type: %T\n", level, i)
switch level {
case 1:
fmt.Printf("%+v\n\n", i)
case 2:
fmt.Printf("%#v\n\n", i)
default:
fmt.Printf("%v\n\n", i)
}
}
const (
podRetryPeriod = 1 * time.Second
podRetryTimeout = 1 * time.Minute
)
func main() {
// uses the current context in kubeconfig
kubeconfig := flag.String("kubeconfig", fmt.Sprintf("%v/%v/%v", os.Getenv("HOME"), ".kube", "config"), "(optional) absolute path to the kubeconfig file")
flag.Parse()
config, err := clientcmd.BuildConfigFromFlags("", *kubeconfig)
ExpectNoError(err, "Could not build config from flags")
// make our work easier to find in the audit_event queries
config.UserAgent = "live-test-writing"
// creates the clientset
ClientSet, _ := kubernetes.NewForConfig(config)
// DynamicClientSet, _ := dynamic.NewForConfig(config)
// podResource := schema.GroupVersionResource{Group: "", Version: "v1", Resource: "pods"}
// TEST BEGINS HERE
ns := "default" // f.Namespace.Name
httpVerbs := []string{"DELETE", "GET", "HEAD", "OPTIONS", "PATCH", "POST", "PUT"}
// httpVerbs := []string{"HEAD"}
// httpVerbs := []string{"OPTIONS"}
fmt.Println("Creating pod...")
_, err = ClientSet.CoreV1().Pods(ns).Create(context.TODO(), &v1.Pod{
ObjectMeta: metav1.ObjectMeta{
Name: "agnhost",
Labels: map[string]string{
"test": "response"},
},
Spec: v1.PodSpec{
Containers: []v1.Container{{
Image: "us.gcr.io/k8s-artifacts-prod/e2e-test-images/agnhost:2.21",
Name: "agnhost",
Command: []string{"/agnhost", "porter"},
Env: []v1.EnvVar{{
Name: "SERVE_PORT_80",
Value: "foo",
}},
}},
RestartPolicy: v1.RestartPolicyNever,
}}, metav1.CreateOptions{})
ExpectNoError(err, "failed to create pod")
err = wait.PollImmediate(podRetryPeriod, podRetryTimeout, checkPodStatus(ClientSet, "test=response"))
ExpectNoError(err, "Pod didn't start within time out period")
transportCfg, err := config.TransportConfig()
ExpectNoError(err, "Error creating transportCfg")
restTransport, err := transport.New(transportCfg)
ExpectNoError(err, "Error creating restTransport")
client := &http.Client{
CheckRedirect: func(req *http.Request, via []*http.Request) error {
return http.ErrUseLastResponse
},
Transport: restTransport,
}
for _, httpVerb := range httpVerbs {
urlString := config.Host + "/api/v1/namespaces/" + ns + "/pods/agnhost/proxy/some/path/with/" + httpVerb
fmt.Printf("Starting http.Client for %s\n", urlString)
request, err := http.NewRequest(httpVerb, urlString, nil)
ExpectNoError(err, "processing request")
resp, err := client.Do(request)
ExpectNoError(err, "processing response")
defer resp.Body.Close()
fmt.Printf("http.Client request:%s StatusCode:%d\n", httpVerb, resp.StatusCode)
ExpectEqual(resp.StatusCode, 200, "The resp.StatusCode returned: %d", resp.StatusCode)
}
// TEST ENDS HERE
fmt.Println("[status] complete")
}
func checkPodStatus(cs *kubernetes.Clientset, label string) func() (bool, error) {
return func() (bool, error) {
var err error
list, err := cs.CoreV1().Pods("default").List(context.TODO(), metav1.ListOptions{
LabelSelector: label})
if err != nil {
return false, err
}
if list.Items[0].Status.Phase != "Running" {
fmt.Printf("Pod Quantity: %d Status: %s\n", len(list.Items), list.Items[0].Status.Phase)
return false, err
}
fmt.Printf("Pod Status: %v\n", list.Items[0].Status.Phase)
return true, nil
}
}
```
# Verifying increase in coverage with APISnoop
## Reset stats
```sql-mode
delete from testing.audit_event;
```
```example
DELETE 977385
```
## Discover useragents:
```sql-mode
select distinct useragent
from testing.audit_event
where useragent like 'live%';
```
```example
useragent
-------------------
live-test-writing
(1 row)
```
## List endpoints hit by the test:
```sql-mode
select * from testing.endpoint_hit_by_new_test ORDER BY hit_by_ete;
```
```example
useragent | endpoint | hit_by_ete | hit_by_new_test
-------------------|-----------------------------------------------|------------|-----------------
live-test-writing | connectCoreV1PostNamespacedPodProxyWithPath | f | 9
live-test-writing | connectCoreV1PatchNamespacedPodProxyWithPath | f | 9
live-test-writing | connectCoreV1DeleteNamespacedPodProxyWithPath | f | 9
live-test-writing | connectCoreV1PutNamespacedPodProxyWithPath | f | 9
live-test-writing | connectCoreV1GetNamespacedPodProxyWithPath | t | 18
live-test-writing | listCoreV1NamespacedPod | t | 42
live-test-writing | createCoreV1NamespacedPod | t | 6
(7 rows)
```
## Display endpoint coverage change:
```sql-mode
select * from testing.projected_change_in_coverage;
```
```example
category | total_endpoints | old_coverage | new_coverage | change_in_number
---------------|-----------------|--------------|--------------|------------------
test_coverage | 831 | 306 | 310 | 4
(1 row)
```
# Final notes
If a test with these calls gets merged, **test coverage will go up by 4 points**
This test is also created with the goal of conformance promotion.
---
/sig testing
/sig architecture
/area conformance
# Exploring / Questions about missing endpoints
Where/How does PATCH/HEAD/OPTIONS requests for the following endpoints line up with the API reference?
- connectCoreV1PatchNamespacedPodProxyWithPath
- connectCoreV1HeadNamespacedPodProxyWithPath
- connectCoreV1OptionsNamespacedPodProxyWithPath
**Pod v1 core: Proxy Operations**
<https://kubernetes.io/docs/reference/generated/kubernetes-api/v1.19/#-strong-proxy-operations-pod-v1-core-strong>-
| httpVerb | Endpoint |
|-------- |-------------------------- |
| POST | Create Connect Proxy |
| | Create Connect Proxy Path |
| DELETE | Delete Connect Proxy |
| | Delete Connect Proxy Path |
| GET | Get Connect Proxy |
| | Get Connect Proxy Path |
| HEAD | Head Connect Proxy |
| | Head Connect Proxy Path |
| PUT | Replace Connect Proxy |
| | Replace Connect Proxy Path |
# Locate why 2 endpoints are missing
<https://apisnoop.cncf.io/conformance-progress/endpoints/1.9.0?filter=promotedWithoutTests&filter=untested> shows the following endpoints are listed as valid endpoints;
- connectCoreV1HeadNamespacedPodProxyWithPath
- connectCoreV1OptionsNamespacedPodProxyWithPath
## Missing HEAD requests
These requests are getting logged as a `get` verb.
Line 24520: api/openapi-spec
```json
"head": {
"consumes": [
"*/*"
],
"description": "connect HEAD requests to proxy of Pod",
"operationId": "connectCoreV1HeadNamespacedPodProxyWithPath",
"produces": [
"*/*"
],
"responses": {
"200": {
"description": "OK",
"schema": {
"type": "string"
}
},
"401": {
"description": "Unauthorized"
}
},
"schemes": [
"https"
],
"tags": [
"core_v1"
],
"x-kubernetes-action": "connect",
"x-kubernetes-group-version-kind": {
"group": "",
"kind": "PodProxyOptions",
"version": "v1"
}
```
## Missing OPTIONS requests
Line 24553: api/openapi-spec
```json
"options": {
"consumes": [
"*/*"
],
"description": "connect OPTIONS requests to proxy of Pod",
"operationId": "connectCoreV1OptionsNamespacedPodProxyWithPath",
"produces": [
"*/*"
],
"responses": {
"200": {
"description": "OK",
"schema": {
"type": "string"
}
},
"401": {
"description": "Unauthorized"
}
},
"schemes": [
"https"
],
"tags": [
"core_v1"
],
"x-kubernetes-action": "connect",
"x-kubernetes-group-version-kind": {
"group": "",
"kind": "PodProxyOptions",
"version": "v1"
}
```
## Verbs missing
Looking at snoopUtils.py there doesn't look to be a mapping for the above methods.
```python
VERB_TO_METHOD={
'get': 'get',
'list': 'get',
'proxy': 'proxy',
'create': 'post',
'post':'post',
'put':'post',
'update':'put',
'patch':'patch',
'connect':'connect',
'delete':'delete',
'deletecollection':'delete',
'watch':'get'
}
```
# ServiceProxyWithPath
- [X] APISnoop org-flow : [ServiceProxyWithPath.org](https://github.com/cncf/apisnoop/blob/master/tickets/k8s/ServiceProxyWithPath.org)
# Identifying an untested feature Using APISnoop
According to this APIsnoop query, there are still some remaining ProxyWithPath endpoints which are untested.
with this query you can filter untested endpoints by their category and eligiblity for conformance. e.g below shows a query to find all conformance eligible untested,stable,core endpoints
```sql-mode
SELECT
endpoint,
-- k8s_action,
path,
-- description,
kind
FROM testing.untested_stable_endpoint
where eligible is true
and category = 'core'
and endpoint like '%ServiceProxyWithPath'
order by kind, endpoint desc
limit 25;
```
```example
endpoint | path | kind
----------------------------------------------------|-------------------------------------------------------------|---------------------
connectCoreV1PutNamespacedServiceProxyWithPath | /api/v1/namespaces/{namespace}/services/{name}/proxy/{path} | ServiceProxyOptions
connectCoreV1PostNamespacedServiceProxyWithPath | /api/v1/namespaces/{namespace}/services/{name}/proxy/{path} | ServiceProxyOptions
connectCoreV1PatchNamespacedServiceProxyWithPath | /api/v1/namespaces/{namespace}/services/{name}/proxy/{path} | ServiceProxyOptions
connectCoreV1OptionsNamespacedServiceProxyWithPath | /api/v1/namespaces/{namespace}/services/{name}/proxy/{path} | ServiceProxyOptions
connectCoreV1HeadNamespacedServiceProxyWithPath | /api/v1/namespaces/{namespace}/services/{name}/proxy/{path} | ServiceProxyOptions
connectCoreV1DeleteNamespacedServiceProxyWithPath | /api/v1/namespaces/{namespace}/services/{name}/proxy/{path} | ServiceProxyOptions
(6 rows)
```
# API Reference and feature documentation
- [Kubernetes API Reference Docs](https://kubernetes.io/docs/reference/kubernetes-api/)
- [client-go](https://github.com/kubernetes/client-go/blob/master/kubernetes/typed/core/v1)
- [Kubernetes 1.19: Service v1 Core: Proxy Operations](https://kubernetes.io/docs/reference/generated/kubernetes-api/v1.19/#-strong-proxy-operations-service-v1-core-strong-)
# The mock test
## Test outline
1. Create a pod with a static label using the agnhost image
2. Confirm that the pod is in the running phase
3. Create a service and link it to the pod
4. Iterate through a list of http methods and check the response from the porter app
5. Confirm that each response code is 200 OK
## Test the functionality in Go
```go
package main
import (
// "encoding/json"
"context"
"flag"
"fmt"
"net/http"
"os"
"time"
v1 "k8s.io/api/core/v1"
// "k8s.io/client-go/dynamic"
// "k8s.io/apimachinery/pkg/runtime/schema"
metav1 "k8s.io/apimachinery/pkg/apis/meta/v1"
"k8s.io/apimachinery/pkg/util/wait"
"k8s.io/client-go/kubernetes"
"k8s.io/client-go/transport"
// "k8s.io/apimachinery/pkg/types"
"k8s.io/client-go/tools/clientcmd"
"k8s.io/apimachinery/pkg/util/intstr"
)
// helper function that mirrors framework.ExpectNoError
func ExpectNoError(err error, msg string) {
if err != nil {
errMsg := msg + fmt.Sprintf(" %v\n", err)
os.Stderr.WriteString(errMsg)
os.Exit(1)
}
}
// helper function that mirrors framework.ExpectEqual
func ExpectEqual(a int, b int, msg string, i interface{}) {
if a != b {
errMsg := msg + fmt.Sprintf(" %v\n", i)
os.Stderr.WriteString(errMsg)
os.Exit(1)
}
}
// helper function to inspect various interfaces
func inspect(level int, name string, i interface{}) {
fmt.Printf("Inspecting: %s\n", name)
fmt.Printf("Inspect level: %d Type: %T\n", level, i)
switch level {
case 1:
fmt.Printf("%+v\n\n", i)
case 2:
fmt.Printf("%#v\n\n", i)
default:
fmt.Printf("%v\n\n", i)
}
}
const (
podRetryPeriod = 1 * time.Second
podRetryTimeout = 1 * time.Minute
)
func main() {
// uses the current context in kubeconfig
kubeconfig := flag.String("kubeconfig", fmt.Sprintf("%v/%v/%v", os.Getenv("HOME"), ".kube", "config"), "(optional) absolute path to the kubeconfig file")
flag.Parse()
config, err := clientcmd.BuildConfigFromFlags("", *kubeconfig)
ExpectNoError(err, "Could not build config from flags")
// make our work easier to find in the audit_event queries
config.UserAgent = "live-test-writing"
// creates the clientset
ClientSet, _ := kubernetes.NewForConfig(config)
// DynamicClientSet, _ := dynamic.NewForConfig(config)
// podResource := schema.GroupVersionResource{Group: "", Version: "v1", Resource: "pods"}
// TEST BEGINS HERE
ns := "default" // f.Namespace.Name
fmt.Println("Creating pod...")
_, err = ClientSet.CoreV1().Pods(ns).Create(context.TODO(), &v1.Pod{
ObjectMeta: metav1.ObjectMeta{
Name: "agnhost",
Labels: map[string]string{
"test": "response"},
},
Spec: v1.PodSpec{
Containers: []v1.Container{{
Image: "us.gcr.io/k8s-artifacts-prod/e2e-test-images/agnhost:2.21",
Name: "agnhost",
Command: []string{"/agnhost", "porter"},
Env: []v1.EnvVar{{
Name: "SERVE_PORT_80",
Value: "foo",
}},
}},
RestartPolicy: v1.RestartPolicyNever,
}}, metav1.CreateOptions{})
ExpectNoError(err, "failed to create pod")
err = wait.PollImmediate(podRetryPeriod, podRetryTimeout, checkPodStatus(ClientSet, "test=response"))
ExpectNoError(err, "Pod didn't start within time out period")
_, err = ClientSet.CoreV1().Services(ns).Create(context.TODO(), &v1.Service{
ObjectMeta: metav1.ObjectMeta{
Name: "test-service",
Namespace: ns,
Labels: map[string]string{
"test": "response",
},
},
Spec: v1.ServiceSpec{
Ports: []v1.ServicePort{{
Port: 80,
TargetPort: intstr.FromInt(80),
Protocol: v1.ProtocolTCP,
}},
Selector: map[string]string{
"test": "response",
},
}}, metav1.CreateOptions{})
ExpectNoError(err, "Failed to create the service")
fmt.Println("Service created")
transportCfg, err := config.TransportConfig()
ExpectNoError(err, "Error creating transportCfg")
restTransport, err := transport.New(transportCfg)
ExpectNoError(err, "Error creating restTransport")
client := &http.Client{
CheckRedirect: func(req *http.Request, via []*http.Request) error {
return http.ErrUseLastResponse
},
Transport: restTransport,
}
time.Sleep(1 * time.Second) // not required in e2e test
httpVerbs := []string{"DELETE", "GET", "HEAD", "OPTIONS", "PATCH", "POST", "PUT"}
for _, httpVerb := range httpVerbs {
urlString := config.Host + "/api/v1/namespaces/" + ns + "/services/test-service/proxy/some/path/with/" + httpVerb
fmt.Printf("Starting http.Client for %s\n", urlString)
request, err := http.NewRequest(httpVerb, urlString, nil)
ExpectNoError(err, "processing request")
resp, err := client.Do(request)
ExpectNoError(err, "processing response")
defer resp.Body.Close()
fmt.Printf("http.Client request:%s StatusCode:%d\n", httpVerb, resp.StatusCode)
ExpectEqual(resp.StatusCode, 200, "The resp.StatusCode returned: %d", resp.StatusCode)
}
// TEST ENDS HERE
fmt.Println("[status] complete")
}
func checkPodStatus(cs *kubernetes.Clientset, label string) func() (bool, error) {
return func() (bool, error) {
var err error
list, err := cs.CoreV1().Pods("default").List(context.TODO(), metav1.ListOptions{
LabelSelector: label})
if err != nil {
return false, err
}
if list.Items[0].Status.Phase != "Running" {
fmt.Printf("Pod Quantity: %d Status: %s\n", len(list.Items), list.Items[0].Status.Phase)
return false, err
}
fmt.Printf("Pod Status: %v\n", list.Items[0].Status.Phase)
return true, nil
}
}
```
# Verifying increase in coverage with APISnoop
## Reset stats
```sql-mode
delete from testing.audit_event;
```
```example
DELETE 89563
```
## Discover useragents:
```sql-mode
select distinct useragent
from testing.audit_event
where useragent like 'live%';
```
```example
useragent
-------------------
live-test-writing
(1 row)
```
## List endpoints hit by the test:
```sql-mode
select * from testing.endpoint_hit_by_new_test ORDER BY hit_by_ete;
```
```example
useragent | endpoint | hit_by_ete | hit_by_new_test
-------------------|---------------------------------------------------|------------|-----------------
live-test-writing | connectCoreV1DeleteNamespacedServiceProxyWithPath | f | 12
live-test-writing | connectCoreV1PatchNamespacedServiceProxyWithPath | f | 12
live-test-writing | connectCoreV1PostNamespacedServiceProxyWithPath | f | 12
live-test-writing | connectCoreV1PutNamespacedServiceProxyWithPath | f | 12
live-test-writing | listCoreV1NamespacedPod | t | 24
live-test-writing | connectCoreV1GetNamespacedServiceProxyWithPath | t | 24
live-test-writing | createCoreV1NamespacedPod | t | 8
live-test-writing | createCoreV1NamespacedService | t | 8
(8 rows)
```
## Display endpoint coverage change:
```sql-mode
select * from testing.projected_change_in_coverage;
```
```example
category | total_endpoints | old_coverage | new_coverage | change_in_number
---------------|-----------------|--------------|--------------|------------------
test_coverage | 831 | 306 | 310 | 4
(1 row)
```
# Final notes
If a test with these calls gets merged, **test coverage will go up by 4 points**
This test is also created with the goal of conformance promotion.
---
|
architecture
|
write podproxywithpath serviceproxywithpath test promote endpoint coverage progress apisnoop org flow test approval issue test pr two weeks soak start date testgrid link two weeks soak end date test promotion pr kubernetes kubernetes podproxywithpath identifying an untested feature using apisnoop according to this apisnoop query there are still some remaining proxywithpath endpoints which are untested with this query you can filter untested endpoints by their category and eligiblity for conformance e g below shows a query to find all conformance eligible untested stable core endpoints sql mode select endpoint action path description kind from testing untested stable endpoint where eligible is true and category core and endpoint like podproxywithpath order by kind endpoint desc limit example endpoint path kind api namespaces namespace pods name proxy path podproxyoptions api namespaces namespace pods name proxy path podproxyoptions api namespaces namespace pods name proxy path podproxyoptions api namespaces namespace pods name proxy path podproxyoptions api namespaces namespace pods name proxy path podproxyoptions api namespaces namespace pods name proxy path podproxyoptions rows api reference and feature documentation the mock test test outline create a pod with a static label using the agnhost image confirm that the pod is in the running phase iterate through a list of http methods and check the response from the porter app confirm that each response code is ok test the functionality in go go package main import encoding json context flag fmt net http os time io api core io client go dynamic io apimachinery pkg runtime schema io apimachinery pkg apis meta io apimachinery pkg util wait io client go kubernetes io client go transport io apimachinery pkg types io client go tools clientcmd helper function that mirrors framework expectnoerror func expectnoerror err error msg string if err nil errmsg msg fmt sprintf v n err os stderr writestring errmsg os exit helper function that mirrors framework expectequal func expectequal a int b int msg string i interface if a b errmsg msg fmt sprintf v n i os stderr writestring errmsg os exit helper function to inspect various interfaces func inspect level int name string i interface fmt printf inspecting s n name fmt printf inspect level d type t n level i switch level case fmt printf v n n i case fmt printf v n n i default fmt printf v n n i const podretryperiod time second podretrytimeout time minute func main uses the current context in kubeconfig kubeconfig flag string kubeconfig fmt sprintf v v v os getenv home kube config optional absolute path to the kubeconfig file flag parse config err clientcmd buildconfigfromflags kubeconfig expectnoerror err could not build config from flags make our work easier to find in the audit event queries config useragent live test writing creates the clientset clientset kubernetes newforconfig config dynamicclientset dynamic newforconfig config podresource schema groupversionresource group version resource pods test begins here ns default f namespace name httpverbs string delete get head options patch post put httpverbs string head httpverbs string options fmt println creating pod err clientset pods ns create context todo pod objectmeta objectmeta name agnhost labels map string test response spec podspec containers container image us gcr io artifacts prod test images agnhost name agnhost command string agnhost porter env envvar name serve port value foo restartpolicy restartpolicynever createoptions expectnoerror err failed to create pod err wait pollimmediate podretryperiod podretrytimeout checkpodstatus clientset test response expectnoerror err pod didn t start within time out period transportcfg err config transportconfig expectnoerror err error creating transportcfg resttransport err transport new transportcfg expectnoerror err error creating resttransport client http client checkredirect func req http request via http request error return http erruselastresponse transport resttransport for httpverb range httpverbs urlstring config host api namespaces ns pods agnhost proxy some path with httpverb fmt printf starting http client for s n urlstring request err http newrequest httpverb urlstring nil expectnoerror err processing request resp err client do request expectnoerror err processing response defer resp body close fmt printf http client request s statuscode d n httpverb resp statuscode expectequal resp statuscode the resp statuscode returned d resp statuscode test ends here fmt println complete func checkpodstatus cs kubernetes clientset label string func bool error return func bool error var err error list err cs pods default list context todo listoptions labelselector label if err nil return false err if list items status phase running fmt printf pod quantity d status s n len list items list items status phase return false err fmt printf pod status v n list items status phase return true nil verifying increase in coverage with apisnoop reset stats sql mode delete from testing audit event example delete discover useragents sql mode select distinct useragent from testing audit event where useragent like live example useragent live test writing row list endpoints hit by the test sql mode select from testing endpoint hit by new test order by hit by ete example useragent endpoint hit by ete hit by new test live test writing f live test writing f live test writing f live test writing f live test writing t live test writing t live test writing t rows display endpoint coverage change sql mode select from testing projected change in coverage example category total endpoints old coverage new coverage change in number test coverage row final notes if a test with these calls gets merged test coverage will go up by points this test is also created with the goal of conformance promotion sig testing sig architecture area conformance exploring questions about missing endpoints where how does patch head options requests for the following endpoints line up with the api reference pod core proxy operations httpverb endpoint post create connect proxy create connect proxy path delete delete connect proxy delete connect proxy path get get connect proxy get connect proxy path head head connect proxy head connect proxy path put replace connect proxy replace connect proxy path locate why endpoints are missing shows the following endpoints are listed as valid endpoints missing head requests these requests are getting logged as a get verb line api openapi spec json head consumes description connect head requests to proxy of pod operationid produces responses description ok schema type string description unauthorized schemes https tags core x kubernetes action connect x kubernetes group version kind group kind podproxyoptions version missing options requests line api openapi spec json options consumes description connect options requests to proxy of pod operationid produces responses description ok schema type string description unauthorized schemes https tags core x kubernetes action connect x kubernetes group version kind group kind podproxyoptions version verbs missing looking at snooputils py there doesn t look to be a mapping for the above methods python verb to method get get list get proxy proxy create post post post put post update put patch patch connect connect delete delete deletecollection delete watch get serviceproxywithpath apisnoop org flow identifying an untested feature using apisnoop according to this apisnoop query there are still some remaining proxywithpath endpoints which are untested with this query you can filter untested endpoints by their category and eligiblity for conformance e g below shows a query to find all conformance eligible untested stable core endpoints sql mode select endpoint action path description kind from testing untested stable endpoint where eligible is true and category core and endpoint like serviceproxywithpath order by kind endpoint desc limit example endpoint path kind api namespaces namespace services name proxy path serviceproxyoptions api namespaces namespace services name proxy path serviceproxyoptions api namespaces namespace services name proxy path serviceproxyoptions api namespaces namespace services name proxy path serviceproxyoptions api namespaces namespace services name proxy path serviceproxyoptions api namespaces namespace services name proxy path serviceproxyoptions rows api reference and feature documentation the mock test test outline create a pod with a static label using the agnhost image confirm that the pod is in the running phase create a service and link it to the pod iterate through a list of http methods and check the response from the porter app confirm that each response code is ok test the functionality in go go package main import encoding json context flag fmt net http os time io api core io client go dynamic io apimachinery pkg runtime schema io apimachinery pkg apis meta io apimachinery pkg util wait io client go kubernetes io client go transport io apimachinery pkg types io client go tools clientcmd io apimachinery pkg util intstr helper function that mirrors framework expectnoerror func expectnoerror err error msg string if err nil errmsg msg fmt sprintf v n err os stderr writestring errmsg os exit helper function that mirrors framework expectequal func expectequal a int b int msg string i interface if a b errmsg msg fmt sprintf v n i os stderr writestring errmsg os exit helper function to inspect various interfaces func inspect level int name string i interface fmt printf inspecting s n name fmt printf inspect level d type t n level i switch level case fmt printf v n n i case fmt printf v n n i default fmt printf v n n i const podretryperiod time second podretrytimeout time minute func main uses the current context in kubeconfig kubeconfig flag string kubeconfig fmt sprintf v v v os getenv home kube config optional absolute path to the kubeconfig file flag parse config err clientcmd buildconfigfromflags kubeconfig expectnoerror err could not build config from flags make our work easier to find in the audit event queries config useragent live test writing creates the clientset clientset kubernetes newforconfig config dynamicclientset dynamic newforconfig config podresource schema groupversionresource group version resource pods test begins here ns default f namespace name fmt println creating pod err clientset pods ns create context todo pod objectmeta objectmeta name agnhost labels map string test response spec podspec containers container image us gcr io artifacts prod test images agnhost name agnhost command string agnhost porter env envvar name serve port value foo restartpolicy restartpolicynever createoptions expectnoerror err failed to create pod err wait pollimmediate podretryperiod podretrytimeout checkpodstatus clientset test response expectnoerror err pod didn t start within time out period err clientset services ns create context todo service objectmeta objectmeta name test service namespace ns labels map string test response spec servicespec ports serviceport port targetport intstr fromint protocol protocoltcp selector map string test response createoptions expectnoerror err failed to create the service fmt println service created transportcfg err config transportconfig expectnoerror err error creating transportcfg resttransport err transport new transportcfg expectnoerror err error creating resttransport client http client checkredirect func req http request via http request error return http erruselastresponse transport resttransport time sleep time second not required in test httpverbs string delete get head options patch post put for httpverb range httpverbs urlstring config host api namespaces ns services test service proxy some path with httpverb fmt printf starting http client for s n urlstring request err http newrequest httpverb urlstring nil expectnoerror err processing request resp err client do request expectnoerror err processing response defer resp body close fmt printf http client request s statuscode d n httpverb resp statuscode expectequal resp statuscode the resp statuscode returned d resp statuscode test ends here fmt println complete func checkpodstatus cs kubernetes clientset label string func bool error return func bool error var err error list err cs pods default list context todo listoptions labelselector label if err nil return false err if list items status phase running fmt printf pod quantity d status s n len list items list items status phase return false err fmt printf pod status v n list items status phase return true nil verifying increase in coverage with apisnoop reset stats sql mode delete from testing audit event example delete discover useragents sql mode select distinct useragent from testing audit event where useragent like live example useragent live test writing row list endpoints hit by the test sql mode select from testing endpoint hit by new test order by hit by ete example useragent endpoint hit by ete hit by new test live test writing f live test writing f live test writing f live test writing f live test writing t live test writing t live test writing t live test writing t rows display endpoint coverage change sql mode select from testing projected change in coverage example category total endpoints old coverage new coverage change in number test coverage row final notes if a test with these calls gets merged test coverage will go up by points this test is also created with the goal of conformance promotion
| 1
|
37,378
| 18,294,365,560
|
IssuesEvent
|
2021-10-05 18:48:36
|
tournesol-app/tournesol
|
https://api.github.com/repos/tournesol-app/tournesol
|
closed
|
Reduce the size of main.js
|
part:frontend prio:important cat:performance
|
The file is too big: https://tournesol.app/static/frontend/main.js (2MB compressed by Apache, 6.4M uncompressed)
- Remove extra dependencies
- Remove unused icons
- Look into alternative compression options
|
True
|
Reduce the size of main.js - The file is too big: https://tournesol.app/static/frontend/main.js (2MB compressed by Apache, 6.4M uncompressed)
- Remove extra dependencies
- Remove unused icons
- Look into alternative compression options
|
non_architecture
|
reduce the size of main js the file is too big compressed by apache uncompressed remove extra dependencies remove unused icons look into alternative compression options
| 0
|
417,192
| 12,156,786,490
|
IssuesEvent
|
2020-04-25 18:51:19
|
Cloud-CV/EvalAI
|
https://api.github.com/repos/Cloud-CV/EvalAI
|
opened
|
Add functionality to send slack notifications from worker
|
GSoC-2020 backend easy_to_fix enhancement new-feature priority-high
|
**Description:**
Some of the challenge hosts are curious so to when the submissions to their challenge are coming, hence they want the worker to post on the slack channel whenever a new submission comes in.
**Deliverables:**
- [ ] Add a nullable with blank=True field in the Challenge model with the name `slack_webhook_url`.
- [ ] Add a migrations file for the same.
- [ ] Create a function in jobs/utils which will take in slack webhook URL as a parameter and post a message on that URL, raise an exception if the request doesn't go through.
- [ ] In the function `publish_submission_message` in `jobs/sender.py`, if there is a `slack_webhook_url` in the challenge model, then call the function in the above step with this URL after sending the message in the queue.
|
1.0
|
Add functionality to send slack notifications from worker - **Description:**
Some of the challenge hosts are curious so to when the submissions to their challenge are coming, hence they want the worker to post on the slack channel whenever a new submission comes in.
**Deliverables:**
- [ ] Add a nullable with blank=True field in the Challenge model with the name `slack_webhook_url`.
- [ ] Add a migrations file for the same.
- [ ] Create a function in jobs/utils which will take in slack webhook URL as a parameter and post a message on that URL, raise an exception if the request doesn't go through.
- [ ] In the function `publish_submission_message` in `jobs/sender.py`, if there is a `slack_webhook_url` in the challenge model, then call the function in the above step with this URL after sending the message in the queue.
|
non_architecture
|
add functionality to send slack notifications from worker description some of the challenge hosts are curious so to when the submissions to their challenge are coming hence they want the worker to post on the slack channel whenever a new submission comes in deliverables add a nullable with blank true field in the challenge model with the name slack webhook url add a migrations file for the same create a function in jobs utils which will take in slack webhook url as a parameter and post a message on that url raise an exception if the request doesn t go through in the function publish submission message in jobs sender py if there is a slack webhook url in the challenge model then call the function in the above step with this url after sending the message in the queue
| 0
|
8,468
| 22,593,789,494
|
IssuesEvent
|
2022-06-28 23:05:15
|
MaterializeInc/materialize
|
https://api.github.com/repos/MaterializeInc/materialize
|
closed
|
docs: show command prompt in shell commands
|
C-feature A-docs T-docs-architecture
|
Currently, we do not show the shell prompt when a user requires to run an OS command. As a result, some of the steps fail when run as a non-privileged user - example below from https://materialize.io/docs/install/
The part where we need to run curl and other commands as well - missing the user prompt as $ or #
`[mz@compute1vm2 ~]$ curl -L https://downloads.mtrlz.dev/materialized-v0.4.3-x86_64-unknown-linux-gnu.tar.gz \
> | tar -xzC /usr/local --strip-components=1
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 63.0M 100 63.0M 0 0 6720k 0 0:00:09 0:00:09 --:--:-- 6928k
tar: bin/materialized: Cannot open: Permission denied
tar: bin: Cannot utime: Operation not permitted
tar: etc/materialized: Cannot mkdir: Permission denied
tar: Exiting with failure status due to previous errors
`
General industry practice is to show the user running the commands as below - https://docs.aws.amazon.com/cli/latest/userguide/cli-chap-install.html
The command here is run by a normal user.
In order to run as root, either we use sudo or show the root prompt. The example below - AWS is showing sudo.
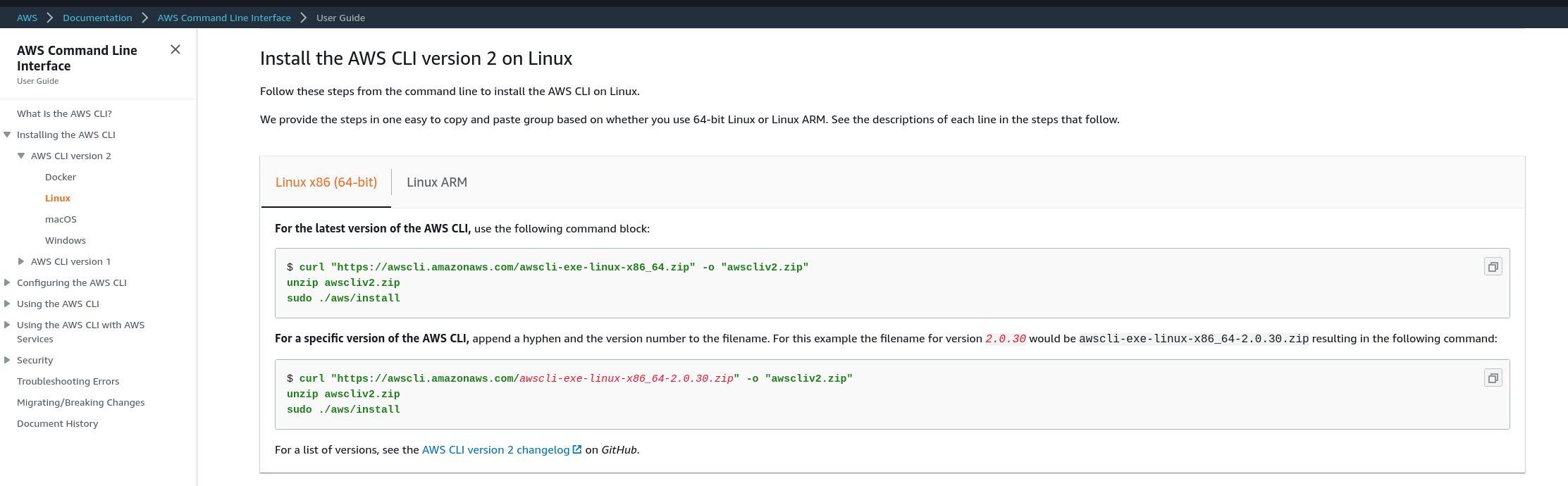
The docs can use sudo wherever root privileges are needed and follow the convention for showing users are non-privileged. This would make it obvious and also standardize the process.
|
1.0
|
docs: show command prompt in shell commands - Currently, we do not show the shell prompt when a user requires to run an OS command. As a result, some of the steps fail when run as a non-privileged user - example below from https://materialize.io/docs/install/
The part where we need to run curl and other commands as well - missing the user prompt as $ or #
`[mz@compute1vm2 ~]$ curl -L https://downloads.mtrlz.dev/materialized-v0.4.3-x86_64-unknown-linux-gnu.tar.gz \
> | tar -xzC /usr/local --strip-components=1
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 63.0M 100 63.0M 0 0 6720k 0 0:00:09 0:00:09 --:--:-- 6928k
tar: bin/materialized: Cannot open: Permission denied
tar: bin: Cannot utime: Operation not permitted
tar: etc/materialized: Cannot mkdir: Permission denied
tar: Exiting with failure status due to previous errors
`
General industry practice is to show the user running the commands as below - https://docs.aws.amazon.com/cli/latest/userguide/cli-chap-install.html

The command here is run by a normal user.
In order to run as root, either we use sudo or show the root prompt. The example below - AWS is showing sudo.

The docs can use sudo wherever root privileges are needed and follow the convention for showing users are non-privileged. This would make it obvious and also standardize the process.
|
architecture
|
docs show command prompt in shell commands currently we do not show the shell prompt when a user requires to run an os command as a result some of the steps fail when run as a non privileged user example below from the part where we need to run curl and other commands as well missing the user prompt as or curl l tar xzc usr local strip components total received xferd average speed time time time current dload upload total spent left speed tar bin materialized cannot open permission denied tar bin cannot utime operation not permitted tar etc materialized cannot mkdir permission denied tar exiting with failure status due to previous errors general industry practice is to show the user running the commands as below the command here is run by a normal user in order to run as root either we use sudo or show the root prompt the example below aws is showing sudo the docs can use sudo wherever root privileges are needed and follow the convention for showing users are non privileged this would make it obvious and also standardize the process
| 1
|
10,960
| 27,594,816,227
|
IssuesEvent
|
2023-03-09 05:03:11
|
IQSS/dataverse
|
https://api.github.com/repos/IQSS/dataverse
|
closed
|
Containerize Dataverse service dependencies for development
|
Feature: Code Infrastructure Feature: Developer Guide Containers & Cloud NIH OTA: 1.7.1 (reArchitecture) Size: 33
|
## Overview of the Feature Request
This issue is created within the scope of IQSS/dataverse#9423, and separated from it since the containerization of the Dataverse dependencies (Postgres, Solr and smtp server) is itself an enhancement to the development environment setup.
In this way, although we still need the install.py script for installing the Dataverse application, we offer a different and more automated way to install its dependencies (through Docker containers).
In addition to creating the necessary configurations to run the containers, it will be necessary to update the documentation related to the development environment setup to offer this alternative.
## What kind of user is the feature intended for?
Developers
## What inspired the request?
- Working on IQSS/dataverse#9423
- Standup discussions
## What existing behavior do you want changed?
Dataverse development environment setup
## Any brand new behavior do you want to add to Dataverse?
No, should be the same.
## Any related open or closed issues to this feature request?
- IQSS/dataverse#9423
|
1.0
|
Containerize Dataverse service dependencies for development - ## Overview of the Feature Request
This issue is created within the scope of IQSS/dataverse#9423, and separated from it since the containerization of the Dataverse dependencies (Postgres, Solr and smtp server) is itself an enhancement to the development environment setup.
In this way, although we still need the install.py script for installing the Dataverse application, we offer a different and more automated way to install its dependencies (through Docker containers).
In addition to creating the necessary configurations to run the containers, it will be necessary to update the documentation related to the development environment setup to offer this alternative.
## What kind of user is the feature intended for?
Developers
## What inspired the request?
- Working on IQSS/dataverse#9423
- Standup discussions
## What existing behavior do you want changed?
Dataverse development environment setup
## Any brand new behavior do you want to add to Dataverse?
No, should be the same.
## Any related open or closed issues to this feature request?
- IQSS/dataverse#9423
|
architecture
|
containerize dataverse service dependencies for development overview of the feature request this issue is created within the scope of iqss dataverse and separated from it since the containerization of the dataverse dependencies postgres solr and smtp server is itself an enhancement to the development environment setup in this way although we still need the install py script for installing the dataverse application we offer a different and more automated way to install its dependencies through docker containers in addition to creating the necessary configurations to run the containers it will be necessary to update the documentation related to the development environment setup to offer this alternative what kind of user is the feature intended for developers what inspired the request working on iqss dataverse standup discussions what existing behavior do you want changed dataverse development environment setup any brand new behavior do you want to add to dataverse no should be the same any related open or closed issues to this feature request iqss dataverse
| 1
|
217,659
| 24,348,831,122
|
IssuesEvent
|
2022-10-02 17:32:21
|
sast-automation-dev/GO-Vulnerable-29
|
https://api.github.com/repos/sast-automation-dev/GO-Vulnerable-29
|
opened
|
jquery-3.2.1.min.js: 3 vulnerabilities (highest severity is: 6.1)
|
security vulnerability
|
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>jquery-3.2.1.min.js</b></p></summary>
<p>JavaScript library for DOM operations</p>
<p>Library home page: <a href="https://cdnjs.cloudflare.com/ajax/libs/jquery/3.2.1/jquery.min.js">https://cdnjs.cloudflare.com/ajax/libs/jquery/3.2.1/jquery.min.js</a></p>
<p>Path to dependency file: /templates/template.login.html</p>
<p>Path to vulnerable library: /templates/template.login.html,/public/js/jquery-3.2.1-min.js</p>
<p>
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/GO-Vulnerable-29/commit/b737a1dd23787b201f9162a2af1d1c93f81381be">b737a1dd23787b201f9162a2af1d1c93f81381be</a></p></details>
## Vulnerabilities
| CVE | Severity | <img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS | Dependency | Type | Fixed in (jquery version) | Remediation Available |
| ------------- | ------------- | ----- | ----- | ----- | ------------- | --- |
| [CVE-2020-11023](https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-11023) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 6.1 | jquery-3.2.1.min.js | Direct | jquery - 3.5.0 | ❌ |
| [CVE-2020-11022](https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-11022) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 6.1 | jquery-3.2.1.min.js | Direct | jQuery - 3.5.0 | ❌ |
| [CVE-2019-11358](https://vuln.whitesourcesoftware.com/vulnerability/CVE-2019-11358) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 6.1 | jquery-3.2.1.min.js | Direct | 3.4.0 | ❌ |
## Details
<details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> CVE-2020-11023</summary>
### Vulnerable Library - <b>jquery-3.2.1.min.js</b></p>
<p>JavaScript library for DOM operations</p>
<p>Library home page: <a href="https://cdnjs.cloudflare.com/ajax/libs/jquery/3.2.1/jquery.min.js">https://cdnjs.cloudflare.com/ajax/libs/jquery/3.2.1/jquery.min.js</a></p>
<p>Path to dependency file: /templates/template.login.html</p>
<p>Path to vulnerable library: /templates/template.login.html,/public/js/jquery-3.2.1-min.js</p>
<p>
Dependency Hierarchy:
- :x: **jquery-3.2.1.min.js** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/GO-Vulnerable-29/commit/b737a1dd23787b201f9162a2af1d1c93f81381be">b737a1dd23787b201f9162a2af1d1c93f81381be</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
In jQuery versions greater than or equal to 1.0.3 and before 3.5.0, passing HTML containing <option> elements from untrusted sources - even after sanitizing it - to one of jQuery's DOM manipulation methods (i.e. .html(), .append(), and others) may execute untrusted code. This problem is patched in jQuery 3.5.0.
<p>Publish Date: 2020-04-29
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-11023>CVE-2020-11023</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>6.1</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Changed
- Impact Metrics:
- Confidentiality Impact: Low
- Integrity Impact: Low
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11023">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11023</a></p>
<p>Release Date: 2020-04-29</p>
<p>Fix Resolution: jquery - 3.5.0</p>
</p>
<p></p>
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> CVE-2020-11022</summary>
### Vulnerable Library - <b>jquery-3.2.1.min.js</b></p>
<p>JavaScript library for DOM operations</p>
<p>Library home page: <a href="https://cdnjs.cloudflare.com/ajax/libs/jquery/3.2.1/jquery.min.js">https://cdnjs.cloudflare.com/ajax/libs/jquery/3.2.1/jquery.min.js</a></p>
<p>Path to dependency file: /templates/template.login.html</p>
<p>Path to vulnerable library: /templates/template.login.html,/public/js/jquery-3.2.1-min.js</p>
<p>
Dependency Hierarchy:
- :x: **jquery-3.2.1.min.js** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/GO-Vulnerable-29/commit/b737a1dd23787b201f9162a2af1d1c93f81381be">b737a1dd23787b201f9162a2af1d1c93f81381be</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
In jQuery versions greater than or equal to 1.2 and before 3.5.0, passing HTML from untrusted sources - even after sanitizing it - to one of jQuery's DOM manipulation methods (i.e. .html(), .append(), and others) may execute untrusted code. This problem is patched in jQuery 3.5.0.
<p>Publish Date: 2020-04-29
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-11022>CVE-2020-11022</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>6.1</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Changed
- Impact Metrics:
- Confidentiality Impact: Low
- Integrity Impact: Low
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://blog.jquery.com/2020/04/10/jquery-3-5-0-released/">https://blog.jquery.com/2020/04/10/jquery-3-5-0-released/</a></p>
<p>Release Date: 2020-04-29</p>
<p>Fix Resolution: jQuery - 3.5.0</p>
</p>
<p></p>
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> CVE-2019-11358</summary>
### Vulnerable Library - <b>jquery-3.2.1.min.js</b></p>
<p>JavaScript library for DOM operations</p>
<p>Library home page: <a href="https://cdnjs.cloudflare.com/ajax/libs/jquery/3.2.1/jquery.min.js">https://cdnjs.cloudflare.com/ajax/libs/jquery/3.2.1/jquery.min.js</a></p>
<p>Path to dependency file: /templates/template.login.html</p>
<p>Path to vulnerable library: /templates/template.login.html,/public/js/jquery-3.2.1-min.js</p>
<p>
Dependency Hierarchy:
- :x: **jquery-3.2.1.min.js** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/GO-Vulnerable-29/commit/b737a1dd23787b201f9162a2af1d1c93f81381be">b737a1dd23787b201f9162a2af1d1c93f81381be</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
jQuery before 3.4.0, as used in Drupal, Backdrop CMS, and other products, mishandles jQuery.extend(true, {}, ...) because of Object.prototype pollution. If an unsanitized source object contained an enumerable __proto__ property, it could extend the native Object.prototype.
<p>Publish Date: 2019-04-20
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2019-11358>CVE-2019-11358</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>6.1</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Changed
- Impact Metrics:
- Confidentiality Impact: Low
- Integrity Impact: Low
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-11358">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-11358</a></p>
<p>Release Date: 2019-04-20</p>
<p>Fix Resolution: 3.4.0</p>
</p>
<p></p>
</details>
|
True
|
jquery-3.2.1.min.js: 3 vulnerabilities (highest severity is: 6.1) - <details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>jquery-3.2.1.min.js</b></p></summary>
<p>JavaScript library for DOM operations</p>
<p>Library home page: <a href="https://cdnjs.cloudflare.com/ajax/libs/jquery/3.2.1/jquery.min.js">https://cdnjs.cloudflare.com/ajax/libs/jquery/3.2.1/jquery.min.js</a></p>
<p>Path to dependency file: /templates/template.login.html</p>
<p>Path to vulnerable library: /templates/template.login.html,/public/js/jquery-3.2.1-min.js</p>
<p>
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/GO-Vulnerable-29/commit/b737a1dd23787b201f9162a2af1d1c93f81381be">b737a1dd23787b201f9162a2af1d1c93f81381be</a></p></details>
## Vulnerabilities
| CVE | Severity | <img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS | Dependency | Type | Fixed in (jquery version) | Remediation Available |
| ------------- | ------------- | ----- | ----- | ----- | ------------- | --- |
| [CVE-2020-11023](https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-11023) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 6.1 | jquery-3.2.1.min.js | Direct | jquery - 3.5.0 | ❌ |
| [CVE-2020-11022](https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-11022) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 6.1 | jquery-3.2.1.min.js | Direct | jQuery - 3.5.0 | ❌ |
| [CVE-2019-11358](https://vuln.whitesourcesoftware.com/vulnerability/CVE-2019-11358) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 6.1 | jquery-3.2.1.min.js | Direct | 3.4.0 | ❌ |
## Details
<details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> CVE-2020-11023</summary>
### Vulnerable Library - <b>jquery-3.2.1.min.js</b></p>
<p>JavaScript library for DOM operations</p>
<p>Library home page: <a href="https://cdnjs.cloudflare.com/ajax/libs/jquery/3.2.1/jquery.min.js">https://cdnjs.cloudflare.com/ajax/libs/jquery/3.2.1/jquery.min.js</a></p>
<p>Path to dependency file: /templates/template.login.html</p>
<p>Path to vulnerable library: /templates/template.login.html,/public/js/jquery-3.2.1-min.js</p>
<p>
Dependency Hierarchy:
- :x: **jquery-3.2.1.min.js** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/GO-Vulnerable-29/commit/b737a1dd23787b201f9162a2af1d1c93f81381be">b737a1dd23787b201f9162a2af1d1c93f81381be</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
In jQuery versions greater than or equal to 1.0.3 and before 3.5.0, passing HTML containing <option> elements from untrusted sources - even after sanitizing it - to one of jQuery's DOM manipulation methods (i.e. .html(), .append(), and others) may execute untrusted code. This problem is patched in jQuery 3.5.0.
<p>Publish Date: 2020-04-29
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-11023>CVE-2020-11023</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>6.1</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Changed
- Impact Metrics:
- Confidentiality Impact: Low
- Integrity Impact: Low
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11023">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11023</a></p>
<p>Release Date: 2020-04-29</p>
<p>Fix Resolution: jquery - 3.5.0</p>
</p>
<p></p>
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> CVE-2020-11022</summary>
### Vulnerable Library - <b>jquery-3.2.1.min.js</b></p>
<p>JavaScript library for DOM operations</p>
<p>Library home page: <a href="https://cdnjs.cloudflare.com/ajax/libs/jquery/3.2.1/jquery.min.js">https://cdnjs.cloudflare.com/ajax/libs/jquery/3.2.1/jquery.min.js</a></p>
<p>Path to dependency file: /templates/template.login.html</p>
<p>Path to vulnerable library: /templates/template.login.html,/public/js/jquery-3.2.1-min.js</p>
<p>
Dependency Hierarchy:
- :x: **jquery-3.2.1.min.js** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/GO-Vulnerable-29/commit/b737a1dd23787b201f9162a2af1d1c93f81381be">b737a1dd23787b201f9162a2af1d1c93f81381be</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
In jQuery versions greater than or equal to 1.2 and before 3.5.0, passing HTML from untrusted sources - even after sanitizing it - to one of jQuery's DOM manipulation methods (i.e. .html(), .append(), and others) may execute untrusted code. This problem is patched in jQuery 3.5.0.
<p>Publish Date: 2020-04-29
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-11022>CVE-2020-11022</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>6.1</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Changed
- Impact Metrics:
- Confidentiality Impact: Low
- Integrity Impact: Low
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://blog.jquery.com/2020/04/10/jquery-3-5-0-released/">https://blog.jquery.com/2020/04/10/jquery-3-5-0-released/</a></p>
<p>Release Date: 2020-04-29</p>
<p>Fix Resolution: jQuery - 3.5.0</p>
</p>
<p></p>
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> CVE-2019-11358</summary>
### Vulnerable Library - <b>jquery-3.2.1.min.js</b></p>
<p>JavaScript library for DOM operations</p>
<p>Library home page: <a href="https://cdnjs.cloudflare.com/ajax/libs/jquery/3.2.1/jquery.min.js">https://cdnjs.cloudflare.com/ajax/libs/jquery/3.2.1/jquery.min.js</a></p>
<p>Path to dependency file: /templates/template.login.html</p>
<p>Path to vulnerable library: /templates/template.login.html,/public/js/jquery-3.2.1-min.js</p>
<p>
Dependency Hierarchy:
- :x: **jquery-3.2.1.min.js** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/GO-Vulnerable-29/commit/b737a1dd23787b201f9162a2af1d1c93f81381be">b737a1dd23787b201f9162a2af1d1c93f81381be</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
jQuery before 3.4.0, as used in Drupal, Backdrop CMS, and other products, mishandles jQuery.extend(true, {}, ...) because of Object.prototype pollution. If an unsanitized source object contained an enumerable __proto__ property, it could extend the native Object.prototype.
<p>Publish Date: 2019-04-20
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2019-11358>CVE-2019-11358</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>6.1</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Changed
- Impact Metrics:
- Confidentiality Impact: Low
- Integrity Impact: Low
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-11358">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-11358</a></p>
<p>Release Date: 2019-04-20</p>
<p>Fix Resolution: 3.4.0</p>
</p>
<p></p>
</details>
|
non_architecture
|
jquery min js vulnerabilities highest severity is vulnerable library jquery min js javascript library for dom operations library home page a href path to dependency file templates template login html path to vulnerable library templates template login html public js jquery min js found in head commit a href vulnerabilities cve severity cvss dependency type fixed in jquery version remediation available medium jquery min js direct jquery medium jquery min js direct jquery medium jquery min js direct details cve vulnerable library jquery min js javascript library for dom operations library home page a href path to dependency file templates template login html path to vulnerable library templates template login html public js jquery min js dependency hierarchy x jquery min js vulnerable library found in head commit a href found in base branch master vulnerability details in jquery versions greater than or equal to and before passing html containing elements from untrusted sources even after sanitizing it to one of jquery s dom manipulation methods i e html append and others may execute untrusted code this problem is patched in jquery publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope changed impact metrics confidentiality impact low integrity impact low availability impact none for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution jquery cve vulnerable library jquery min js javascript library for dom operations library home page a href path to dependency file templates template login html path to vulnerable library templates template login html public js jquery min js dependency hierarchy x jquery min js vulnerable library found in head commit a href found in base branch master vulnerability details in jquery versions greater than or equal to and before passing html from untrusted sources even after sanitizing it to one of jquery s dom manipulation methods i e html append and others may execute untrusted code this problem is patched in jquery publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope changed impact metrics confidentiality impact low integrity impact low availability impact none for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution jquery cve vulnerable library jquery min js javascript library for dom operations library home page a href path to dependency file templates template login html path to vulnerable library templates template login html public js jquery min js dependency hierarchy x jquery min js vulnerable library found in head commit a href found in base branch master vulnerability details jquery before as used in drupal backdrop cms and other products mishandles jquery extend true because of object prototype pollution if an unsanitized source object contained an enumerable proto property it could extend the native object prototype publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope changed impact metrics confidentiality impact low integrity impact low availability impact none for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution
| 0
|
8,626
| 23,147,455,540
|
IssuesEvent
|
2022-07-29 03:32:25
|
QutEcoacoustics/workbench-client
|
https://api.github.com/repos/QutEcoacoustics/workbench-client
|
opened
|
Association decorators should not show error notifications
|
bug architecture
|
Currently, when guest users access pages which use the association decorators to load data, error notifications are shown to them. This is an issue when they view the permissions widgets which retrieve the current user, but fail with a 401. These requests should not produce any warning messages.
This may need to be solved by either identifying association decorator requests, and handling them differently (this may help us with handling caching as well), or changing how notifications are handled.
|
1.0
|
Association decorators should not show error notifications - Currently, when guest users access pages which use the association decorators to load data, error notifications are shown to them. This is an issue when they view the permissions widgets which retrieve the current user, but fail with a 401. These requests should not produce any warning messages.
This may need to be solved by either identifying association decorator requests, and handling them differently (this may help us with handling caching as well), or changing how notifications are handled.
|
architecture
|
association decorators should not show error notifications currently when guest users access pages which use the association decorators to load data error notifications are shown to them this is an issue when they view the permissions widgets which retrieve the current user but fail with a these requests should not produce any warning messages this may need to be solved by either identifying association decorator requests and handling them differently this may help us with handling caching as well or changing how notifications are handled
| 1
|
324,201
| 23,988,375,232
|
IssuesEvent
|
2022-09-13 21:24:33
|
microsoft/STL
|
https://api.github.com/repos/microsoft/STL
|
closed
|
`<yvals_core.h>`: Update the reference to P2549 to P2549R1
|
documentation duplicate good first issue
|
The adopted revision of WG21-P2549 is [P2549R1](https://wg21.link/p2549r1), which only differs from R0 in some editorial changes.
We should just update the reference to it in `<yvals_core.h>`.
Code:
https://github.com/microsoft/STL/blob/ef62d3fa0b8e4e2406b9bb74e916e1ca8a1df802/stl/inc/yvals_core.h#L318
This issue is intended for a new contributor (especially one new to GitHub) to get started with the simplest possible change.
Please feel free to submit a pull request if there isn't one already linked here - no need to ask for permission! 😸
You can (and should) link your pull request to this issue using [GitHub's close/fix/resolve syntax](https://docs.github.com/en/issues/tracking-your-work-with-issues/linking-a-pull-request-to-an-issue#linking-a-pull-request-to-an-issue-using-a-keyword).
(in the PR description not the commit message)
|
1.0
|
`<yvals_core.h>`: Update the reference to P2549 to P2549R1 - The adopted revision of WG21-P2549 is [P2549R1](https://wg21.link/p2549r1), which only differs from R0 in some editorial changes.
We should just update the reference to it in `<yvals_core.h>`.
Code:
https://github.com/microsoft/STL/blob/ef62d3fa0b8e4e2406b9bb74e916e1ca8a1df802/stl/inc/yvals_core.h#L318
This issue is intended for a new contributor (especially one new to GitHub) to get started with the simplest possible change.
Please feel free to submit a pull request if there isn't one already linked here - no need to ask for permission! 😸
You can (and should) link your pull request to this issue using [GitHub's close/fix/resolve syntax](https://docs.github.com/en/issues/tracking-your-work-with-issues/linking-a-pull-request-to-an-issue#linking-a-pull-request-to-an-issue-using-a-keyword).
(in the PR description not the commit message)
|
non_architecture
|
update the reference to to the adopted revision of is which only differs from in some editorial changes we should just update the reference to it in code this issue is intended for a new contributor especially one new to github to get started with the simplest possible change please feel free to submit a pull request if there isn t one already linked here no need to ask for permission 😸 you can and should link your pull request to this issue using in the pr description not the commit message
| 0
|
2,929
| 8,557,259,882
|
IssuesEvent
|
2018-11-08 15:18:54
|
rydavidson/SustainingDevTools
|
https://api.github.com/repos/rydavidson/SustainingDevTools
|
opened
|
Add a caching system
|
architecture
|
Add some kind of caching mechanism I can use for global caching and state management. Should be a singleton so it's somewhat thread safe.
|
1.0
|
Add a caching system - Add some kind of caching mechanism I can use for global caching and state management. Should be a singleton so it's somewhat thread safe.
|
architecture
|
add a caching system add some kind of caching mechanism i can use for global caching and state management should be a singleton so it s somewhat thread safe
| 1
|
171,478
| 20,964,125,292
|
IssuesEvent
|
2022-03-28 03:46:55
|
nvenkatesh1/SCA_test_JS
|
https://api.github.com/repos/nvenkatesh1/SCA_test_JS
|
reopened
|
url-loader-0.5.7.tgz: 1 vulnerabilities (highest severity is: 7.5)
|
security vulnerability
|
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>url-loader-0.5.7.tgz</b></p></summary>
<p></p>
<p>Path to dependency file: /app/compilers/react-compiler/package.json</p>
<p>Path to vulnerable library: /app/compilers/react-compiler/node_modules/url-loader/node_modules/mime/package.json</p>
<p>
<p>Found in HEAD commit: <a href="https://github.com/nvenkatesh1/SCA_test_JS/commit/eb47eeefc02a252a76628fec10a3c26aacb34024">eb47eeefc02a252a76628fec10a3c26aacb34024</a></p></details>
## Vulnerabilities
| CVE | Severity | <img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS | Dependency | Type | Fixed in | Remediation Available |
| ------------- | ------------- | ----- | ----- | ----- | --- | --- |
| [CVE-2017-16138](https://vuln.whitesourcesoftware.com/vulnerability/CVE-2017-16138) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | mime-1.2.11.tgz | Transitive | 0.6.0 | ✅ |
## Details
<details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2017-16138</summary>
### Vulnerable Library - <b>mime-1.2.11.tgz</b></p>
<p>A comprehensive library for mime-type mapping</p>
<p>Library home page: <a href="https://registry.npmjs.org/mime/-/mime-1.2.11.tgz">https://registry.npmjs.org/mime/-/mime-1.2.11.tgz</a></p>
<p>Path to dependency file: /app/compilers/react-compiler/package.json</p>
<p>Path to vulnerable library: /app/compilers/react-compiler/node_modules/url-loader/node_modules/mime/package.json</p>
<p>
Dependency Hierarchy:
- url-loader-0.5.7.tgz (Root Library)
- :x: **mime-1.2.11.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/nvenkatesh1/SCA_test_JS/commit/eb47eeefc02a252a76628fec10a3c26aacb34024">eb47eeefc02a252a76628fec10a3c26aacb34024</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
The mime module < 1.4.1, 2.0.1, 2.0.2 is vulnerable to regular expression denial of service when a mime lookup is performed on untrusted user input.
<p>Publish Date: 2018-06-07
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2017-16138>CVE-2017-16138</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>7.5</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-16138">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-16138</a></p>
<p>Release Date: 2018-06-07</p>
<p>Fix Resolution (mime): 1.4.1</p>
<p>Direct dependency fix Resolution (url-loader): 0.6.0</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details>
***
<p>:rescue_worker_helmet: Automatic Remediation is available for this issue.</p>
<!-- <REMEDIATE>[{"isOpenPROnVulnerability":true,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"javascript/Node.js","packageName":"url-loader","packageVersion":"0.5.7","packageFilePaths":["/app/compilers/react-compiler/package.json"],"isTransitiveDependency":false,"dependencyTree":"url-loader:0.5.7","isMinimumFixVersionAvailable":true,"minimumFixVersion":"0.6.0","isBinary":false}],"baseBranches":["master"],"vulnerabilityIdentifier":"CVE-2017-16138","vulnerabilityDetails":"The mime module \u003c 1.4.1, 2.0.1, 2.0.2 is vulnerable to regular expression denial of service when a mime lookup is performed on untrusted user input.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2017-16138","cvss3Severity":"high","cvss3Score":"7.5","cvss3Metrics":{"A":"High","AC":"Low","PR":"None","S":"Unchanged","C":"None","UI":"None","AV":"Network","I":"None"},"extraData":{}}]</REMEDIATE> -->
|
True
|
url-loader-0.5.7.tgz: 1 vulnerabilities (highest severity is: 7.5) - <details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>url-loader-0.5.7.tgz</b></p></summary>
<p></p>
<p>Path to dependency file: /app/compilers/react-compiler/package.json</p>
<p>Path to vulnerable library: /app/compilers/react-compiler/node_modules/url-loader/node_modules/mime/package.json</p>
<p>
<p>Found in HEAD commit: <a href="https://github.com/nvenkatesh1/SCA_test_JS/commit/eb47eeefc02a252a76628fec10a3c26aacb34024">eb47eeefc02a252a76628fec10a3c26aacb34024</a></p></details>
## Vulnerabilities
| CVE | Severity | <img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS | Dependency | Type | Fixed in | Remediation Available |
| ------------- | ------------- | ----- | ----- | ----- | --- | --- |
| [CVE-2017-16138](https://vuln.whitesourcesoftware.com/vulnerability/CVE-2017-16138) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | mime-1.2.11.tgz | Transitive | 0.6.0 | ✅ |
## Details
<details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2017-16138</summary>
### Vulnerable Library - <b>mime-1.2.11.tgz</b></p>
<p>A comprehensive library for mime-type mapping</p>
<p>Library home page: <a href="https://registry.npmjs.org/mime/-/mime-1.2.11.tgz">https://registry.npmjs.org/mime/-/mime-1.2.11.tgz</a></p>
<p>Path to dependency file: /app/compilers/react-compiler/package.json</p>
<p>Path to vulnerable library: /app/compilers/react-compiler/node_modules/url-loader/node_modules/mime/package.json</p>
<p>
Dependency Hierarchy:
- url-loader-0.5.7.tgz (Root Library)
- :x: **mime-1.2.11.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/nvenkatesh1/SCA_test_JS/commit/eb47eeefc02a252a76628fec10a3c26aacb34024">eb47eeefc02a252a76628fec10a3c26aacb34024</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
The mime module < 1.4.1, 2.0.1, 2.0.2 is vulnerable to regular expression denial of service when a mime lookup is performed on untrusted user input.
<p>Publish Date: 2018-06-07
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2017-16138>CVE-2017-16138</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>7.5</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-16138">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-16138</a></p>
<p>Release Date: 2018-06-07</p>
<p>Fix Resolution (mime): 1.4.1</p>
<p>Direct dependency fix Resolution (url-loader): 0.6.0</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details>
***
<p>:rescue_worker_helmet: Automatic Remediation is available for this issue.</p>
<!-- <REMEDIATE>[{"isOpenPROnVulnerability":true,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"javascript/Node.js","packageName":"url-loader","packageVersion":"0.5.7","packageFilePaths":["/app/compilers/react-compiler/package.json"],"isTransitiveDependency":false,"dependencyTree":"url-loader:0.5.7","isMinimumFixVersionAvailable":true,"minimumFixVersion":"0.6.0","isBinary":false}],"baseBranches":["master"],"vulnerabilityIdentifier":"CVE-2017-16138","vulnerabilityDetails":"The mime module \u003c 1.4.1, 2.0.1, 2.0.2 is vulnerable to regular expression denial of service when a mime lookup is performed on untrusted user input.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2017-16138","cvss3Severity":"high","cvss3Score":"7.5","cvss3Metrics":{"A":"High","AC":"Low","PR":"None","S":"Unchanged","C":"None","UI":"None","AV":"Network","I":"None"},"extraData":{}}]</REMEDIATE> -->
|
non_architecture
|
url loader tgz vulnerabilities highest severity is vulnerable library url loader tgz path to dependency file app compilers react compiler package json path to vulnerable library app compilers react compiler node modules url loader node modules mime package json found in head commit a href vulnerabilities cve severity cvss dependency type fixed in remediation available high mime tgz transitive details cve vulnerable library mime tgz a comprehensive library for mime type mapping library home page a href path to dependency file app compilers react compiler package json path to vulnerable library app compilers react compiler node modules url loader node modules mime package json dependency hierarchy url loader tgz root library x mime tgz vulnerable library found in head commit a href found in base branch master vulnerability details the mime module is vulnerable to regular expression denial of service when a mime lookup is performed on untrusted user input publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution mime direct dependency fix resolution url loader rescue worker helmet automatic remediation is available for this issue rescue worker helmet automatic remediation is available for this issue istransitivedependency false dependencytree url loader isminimumfixversionavailable true minimumfixversion isbinary false basebranches vulnerabilityidentifier cve vulnerabilitydetails the mime module is vulnerable to regular expression denial of service when a mime lookup is performed on untrusted user input vulnerabilityurl
| 0
|
63,694
| 17,860,888,677
|
IssuesEvent
|
2021-09-05 23:40:27
|
vector-im/element-ios
|
https://api.github.com/repos/vector-im/element-ios
|
opened
|
Latest version of element in app store can't login get M_UNRECOGNIZED error
|
T-Defect
|
### Steps to reproduce
Around a week ago logins started to fail, presumably with an auto update. After being asked to re-login again it opens a webview popup which connects to our home server and then shows this error:
```
{"errcode": "M_UNRECOGNIZED", "error": "Unrecognized request"}
```
At first we thought it was something with our homeserver or our SSO but when attempting to connect to matrix.org we get the same error. It seems everyone in our organisation is getting the same error.
We have trialed using the Syphon iphone mobile app which does correctly connect (but the app seem beta quality) so it isn't an issue with out server or SSO.
### What happened?
### What did you expect?
Be prompted with the normal SSO login for our home server
### What happened?
```
{"errcode": "M_UNRECOGNIZED", "error": "Unrecognized request"}
```
### Your phone model
iPhone 11
### Operating system version
ios 14.71
### Application version
_No response_
### Homeserver
chat.catalyst-au.net
### Have you submitted a rageshake?
No
|
1.0
|
Latest version of element in app store can't login get M_UNRECOGNIZED error - ### Steps to reproduce
Around a week ago logins started to fail, presumably with an auto update. After being asked to re-login again it opens a webview popup which connects to our home server and then shows this error:
```
{"errcode": "M_UNRECOGNIZED", "error": "Unrecognized request"}
```
At first we thought it was something with our homeserver or our SSO but when attempting to connect to matrix.org we get the same error. It seems everyone in our organisation is getting the same error.
We have trialed using the Syphon iphone mobile app which does correctly connect (but the app seem beta quality) so it isn't an issue with out server or SSO.
### What happened?
### What did you expect?
Be prompted with the normal SSO login for our home server
### What happened?
```
{"errcode": "M_UNRECOGNIZED", "error": "Unrecognized request"}
```
### Your phone model
iPhone 11
### Operating system version
ios 14.71
### Application version
_No response_
### Homeserver
chat.catalyst-au.net
### Have you submitted a rageshake?
No
|
non_architecture
|
latest version of element in app store can t login get m unrecognized error steps to reproduce around a week ago logins started to fail presumably with an auto update after being asked to re login again it opens a webview popup which connects to our home server and then shows this error errcode m unrecognized error unrecognized request at first we thought it was something with our homeserver or our sso but when attempting to connect to matrix org we get the same error it seems everyone in our organisation is getting the same error we have trialed using the syphon iphone mobile app which does correctly connect but the app seem beta quality so it isn t an issue with out server or sso what happened what did you expect be prompted with the normal sso login for our home server what happened errcode m unrecognized error unrecognized request your phone model iphone operating system version ios application version no response homeserver chat catalyst au net have you submitted a rageshake no
| 0
|
102,573
| 12,809,182,150
|
IssuesEvent
|
2020-07-03 15:05:33
|
department-of-veterans-affairs/va.gov-team
|
https://api.github.com/repos/department-of-veterans-affairs/va.gov-team
|
closed
|
[Design] Claims Status: Usability Study #1
|
design discovery vsa-benefits
|
## Issue Description
_What details are necessary for understanding the specific work or request tracked by this issue?_
_Plan Research_
_Recruit 8-10 participants_
_Execute research_
_Synthesize and summarize research_
---
## Tasks
- [x] _Finish Research Plan_
- [x] _Finish Conversation Guide_
- [x] _Finish Mural board for Co-design session_
- [x] _Finish Invision Prototype of current Claim Status Tool_
## Acceptance Criteria
- [x] _What will be created or happen as a result of this story?_
- [x] _Research planning is completed_
- [x] _Recruiting is completed_
- [x] _Research is completed_
All documents are here:
https://github.com/department-of-veterans-affairs/va.gov-team/tree/master/products/claim-appeal-status/research/co-design-usability-June
---
## How to configure this issue
- [ ] **Attached to a Milestone** (when will this be completed?)
- [ ] **Attached to an Epic** (what body of work is this a part of?)
- [ ] **Labeled with Team** (`product support`, `analytics-insights`, `operations`, `service-design`, `tools-be`, `tools-fe`)
- [ ] **Labeled with Practice Area** (`backend`, `frontend`, `devops`, `design`, `research`, `product`, `ia`, `qa`, `analytics`, `contact center`, `research`, `accessibility`, `content`)
- [ ] **Labeled with Type** (`bug`, `request`, `discovery`, `documentation`, etc.)
https://github.com/department-of-veterans-affairs/va.gov-team/tree/master/products/claim-appeal-status/research/co-design-usability-June
|
1.0
|
[Design] Claims Status: Usability Study #1 - ## Issue Description
_What details are necessary for understanding the specific work or request tracked by this issue?_
_Plan Research_
_Recruit 8-10 participants_
_Execute research_
_Synthesize and summarize research_
---
## Tasks
- [x] _Finish Research Plan_
- [x] _Finish Conversation Guide_
- [x] _Finish Mural board for Co-design session_
- [x] _Finish Invision Prototype of current Claim Status Tool_
## Acceptance Criteria
- [x] _What will be created or happen as a result of this story?_
- [x] _Research planning is completed_
- [x] _Recruiting is completed_
- [x] _Research is completed_
All documents are here:
https://github.com/department-of-veterans-affairs/va.gov-team/tree/master/products/claim-appeal-status/research/co-design-usability-June
---
## How to configure this issue
- [ ] **Attached to a Milestone** (when will this be completed?)
- [ ] **Attached to an Epic** (what body of work is this a part of?)
- [ ] **Labeled with Team** (`product support`, `analytics-insights`, `operations`, `service-design`, `tools-be`, `tools-fe`)
- [ ] **Labeled with Practice Area** (`backend`, `frontend`, `devops`, `design`, `research`, `product`, `ia`, `qa`, `analytics`, `contact center`, `research`, `accessibility`, `content`)
- [ ] **Labeled with Type** (`bug`, `request`, `discovery`, `documentation`, etc.)
https://github.com/department-of-veterans-affairs/va.gov-team/tree/master/products/claim-appeal-status/research/co-design-usability-June
|
non_architecture
|
claims status usability study issue description what details are necessary for understanding the specific work or request tracked by this issue plan research recruit participants execute research synthesize and summarize research tasks finish research plan finish conversation guide finish mural board for co design session finish invision prototype of current claim status tool acceptance criteria what will be created or happen as a result of this story research planning is completed recruiting is completed research is completed all documents are here how to configure this issue attached to a milestone when will this be completed attached to an epic what body of work is this a part of labeled with team product support analytics insights operations service design tools be tools fe labeled with practice area backend frontend devops design research product ia qa analytics contact center research accessibility content labeled with type bug request discovery documentation etc
| 0
|
9,421
| 24,562,199,226
|
IssuesEvent
|
2022-10-12 21:28:06
|
R-Type-Epitech-Nantes/R-Type
|
https://api.github.com/repos/R-Type-Epitech-Nantes/R-Type
|
closed
|
GameClock
|
Documentation Architecture ECS Game Shared Resources
|
This issue is to create the GameClock Shared Resource.
The Timer is use to regulate all modifications done by Systems (is to avoid any problem with the display like the BM:GO)
Please Change the Movement system to work with this Shared Resource
|
1.0
|
GameClock - This issue is to create the GameClock Shared Resource.
The Timer is use to regulate all modifications done by Systems (is to avoid any problem with the display like the BM:GO)
Please Change the Movement system to work with this Shared Resource
|
architecture
|
gameclock this issue is to create the gameclock shared resource the timer is use to regulate all modifications done by systems is to avoid any problem with the display like the bm go please change the movement system to work with this shared resource
| 1
|
2,742
| 8,248,466,732
|
IssuesEvent
|
2018-09-11 18:31:46
|
fga-eps-mds/2018.2-GamesBI
|
https://api.github.com/repos/fga-eps-mds/2018.2-GamesBI
|
reopened
|
Atualizar MER microservicos
|
architecture data science documentation important
|
## Description
Novos dados listados e o MER precisa ser atualizado e adicionado no doc de arquitetura
## Tasks
- [ ] Listar atributos das APIs fontes de dados
- [ ] Desenhar MER
- [ ] Adicionar no doc de arquitetura
## Acceptance criteria
Apenas dados relevantes
## How this will benefit the project?
Guiar o time de desenvolvimento
|
1.0
|
Atualizar MER microservicos - ## Description
Novos dados listados e o MER precisa ser atualizado e adicionado no doc de arquitetura
## Tasks
- [ ] Listar atributos das APIs fontes de dados
- [ ] Desenhar MER
- [ ] Adicionar no doc de arquitetura
## Acceptance criteria
Apenas dados relevantes
## How this will benefit the project?
Guiar o time de desenvolvimento
|
architecture
|
atualizar mer microservicos description novos dados listados e o mer precisa ser atualizado e adicionado no doc de arquitetura tasks listar atributos das apis fontes de dados desenhar mer adicionar no doc de arquitetura acceptance criteria apenas dados relevantes how this will benefit the project guiar o time de desenvolvimento
| 1
|
3,027
| 8,722,098,843
|
IssuesEvent
|
2018-12-09 08:32:29
|
laredoza/.NetScaffolder
|
https://api.github.com/repos/laredoza/.NetScaffolder
|
closed
|
Implement caching on queries.
|
Architecture Generation enhancement
|
The driver type's caching still needs to be selected but repository methods will also have a cache parameter which will specify if caching needs to be used.
At the moment memory & redis caching is implemented.
|
1.0
|
Implement caching on queries. - The driver type's caching still needs to be selected but repository methods will also have a cache parameter which will specify if caching needs to be used.
At the moment memory & redis caching is implemented.
|
architecture
|
implement caching on queries the driver type s caching still needs to be selected but repository methods will also have a cache parameter which will specify if caching needs to be used at the moment memory redis caching is implemented
| 1
|
10,560
| 27,119,655,386
|
IssuesEvent
|
2023-02-15 21:37:38
|
Azure/azure-sdk
|
https://api.github.com/repos/Azure/azure-sdk
|
closed
|
Board Review: Azure Communication Services (SPOOL) Navigation Bar - UI Library [iOS, Android]
|
architecture board-review
|
Title composition:
[Team] - ACS Mobile UI Android
[Release Type] - Public Preview
[Feature to be reviewed] - NavigationBarViewData
[DevEx Internal / ARB] - DevEx
Service name:
Key contact for this review:
Link to previous API version:
-Android[azure-communication-ui-calling (version 1.1.0) - apiview.dev](https://apiview.dev/Assemblies/Review/6c99f6dc8e134efa8e163d7d941519c7?revisionId=88de2ff2613c4ce1b197923f8f3b50cf&doc=False)
-iOS https://apiview.dev/Assemblies/Review/1ce5513aaca54e5c8e86f9c982ca3f78?diffRevisionId=9ff82842d8b24a8fb14bebc34160dabb&doc=False&diffOnly=False&revisionId=997b226003c84fa0979d6adb00730799
Description of the material to be reviewed/changed: Call Title and Sub Title to be configured
Champion scenarios that briefly explain how developers will use your API:
Contoso developer is able to set Call Title and Sub Title using public API
Languages for this review: Java
Artifacts per language.
JAVA: [azure-communication-ui-calling (version 1.1.0-beta.1) - apiview.dev](https://apiview.dev/Assemblies/Review/6c99f6dc8e134efa8e163d7d941519c7?revisionId=392175286f874666a92744a8ee1298f9).
We encourage you to add the meeting notes over the story discussion to track visibility and status of the review. Please keep updated the story.
|
1.0
|
Board Review: Azure Communication Services (SPOOL) Navigation Bar - UI Library [iOS, Android] - Title composition:
[Team] - ACS Mobile UI Android
[Release Type] - Public Preview
[Feature to be reviewed] - NavigationBarViewData
[DevEx Internal / ARB] - DevEx
Service name:
Key contact for this review:
Link to previous API version:
-Android[azure-communication-ui-calling (version 1.1.0) - apiview.dev](https://apiview.dev/Assemblies/Review/6c99f6dc8e134efa8e163d7d941519c7?revisionId=88de2ff2613c4ce1b197923f8f3b50cf&doc=False)
-iOS https://apiview.dev/Assemblies/Review/1ce5513aaca54e5c8e86f9c982ca3f78?diffRevisionId=9ff82842d8b24a8fb14bebc34160dabb&doc=False&diffOnly=False&revisionId=997b226003c84fa0979d6adb00730799
Description of the material to be reviewed/changed: Call Title and Sub Title to be configured
Champion scenarios that briefly explain how developers will use your API:
Contoso developer is able to set Call Title and Sub Title using public API
Languages for this review: Java
Artifacts per language.
JAVA: [azure-communication-ui-calling (version 1.1.0-beta.1) - apiview.dev](https://apiview.dev/Assemblies/Review/6c99f6dc8e134efa8e163d7d941519c7?revisionId=392175286f874666a92744a8ee1298f9).
We encourage you to add the meeting notes over the story discussion to track visibility and status of the review. Please keep updated the story.
|
architecture
|
board review azure communication services spool navigation bar ui library title composition acs mobile ui android public preview navigationbarviewdata devex service name key contact for this review link to previous api version android ios description of the material to be reviewed changed call title and sub title to be configured champion scenarios that briefly explain how developers will use your api contoso developer is able to set call title and sub title using public api languages for this review java artifacts per language java we encourage you to add the meeting notes over the story discussion to track visibility and status of the review please keep updated the story
| 1
|
37,750
| 12,489,943,285
|
IssuesEvent
|
2020-05-31 21:18:09
|
the-benchmarker/web-frameworks
|
https://api.github.com/repos/the-benchmarker/web-frameworks
|
closed
|
CVE-2017-17485 (High) detected in jackson-databind-2.8.5.jar
|
security vulnerability
|
## CVE-2017-17485 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>jackson-databind-2.8.5.jar</b></p></summary>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /tmp/ws-scm/web-frameworks/java/rapidoid/pom.xml</p>
<p>Path to vulnerable library: /root/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.8.5/jackson-databind-2.8.5.jar</p>
<p>
Dependency Hierarchy:
- rapidoid-web-5.5.5.jar (Root Library)
- rapidoid-sql-5.5.5.jar
- rapidoid-commons-5.5.5.jar
- :x: **jackson-databind-2.8.5.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/the-benchmarker/web-frameworks/commit/ab64b8404e01abede0aa4aa810306b3705409b30">ab64b8404e01abede0aa4aa810306b3705409b30</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
FasterXML jackson-databind through 2.8.10 and 2.9.x through 2.9.3 allows unauthenticated remote code execution because of an incomplete fix for the CVE-2017-7525 deserialization flaw. This is exploitable by sending maliciously crafted JSON input to the readValue method of the ObjectMapper, bypassing a blacklist that is ineffective if the Spring libraries are available in the classpath.
<p>Publish Date: 2018-01-10
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2017-17485>CVE-2017-17485</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>9.8</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17485">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17485</a></p>
<p>Release Date: 2018-01-10</p>
<p>Fix Resolution: 2.9.4</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2017-17485 (High) detected in jackson-databind-2.8.5.jar - ## CVE-2017-17485 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>jackson-databind-2.8.5.jar</b></p></summary>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /tmp/ws-scm/web-frameworks/java/rapidoid/pom.xml</p>
<p>Path to vulnerable library: /root/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.8.5/jackson-databind-2.8.5.jar</p>
<p>
Dependency Hierarchy:
- rapidoid-web-5.5.5.jar (Root Library)
- rapidoid-sql-5.5.5.jar
- rapidoid-commons-5.5.5.jar
- :x: **jackson-databind-2.8.5.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/the-benchmarker/web-frameworks/commit/ab64b8404e01abede0aa4aa810306b3705409b30">ab64b8404e01abede0aa4aa810306b3705409b30</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
FasterXML jackson-databind through 2.8.10 and 2.9.x through 2.9.3 allows unauthenticated remote code execution because of an incomplete fix for the CVE-2017-7525 deserialization flaw. This is exploitable by sending maliciously crafted JSON input to the readValue method of the ObjectMapper, bypassing a blacklist that is ineffective if the Spring libraries are available in the classpath.
<p>Publish Date: 2018-01-10
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2017-17485>CVE-2017-17485</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>9.8</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17485">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17485</a></p>
<p>Release Date: 2018-01-10</p>
<p>Fix Resolution: 2.9.4</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
non_architecture
|
cve high detected in jackson databind jar cve high severity vulnerability vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file tmp ws scm web frameworks java rapidoid pom xml path to vulnerable library root repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy rapidoid web jar root library rapidoid sql jar rapidoid commons jar x jackson databind jar vulnerable library found in head commit a href vulnerability details fasterxml jackson databind through and x through allows unauthenticated remote code execution because of an incomplete fix for the cve deserialization flaw this is exploitable by sending maliciously crafted json input to the readvalue method of the objectmapper bypassing a blacklist that is ineffective if the spring libraries are available in the classpath publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution step up your open source security game with whitesource
| 0
|
34,522
| 2,782,042,881
|
IssuesEvent
|
2015-05-06 16:10:59
|
GoogleCloudPlatform/kubernetes
|
https://api.github.com/repos/GoogleCloudPlatform/kubernetes
|
closed
|
Consider removing Rackspace support
|
cluster/platform/rackspace kind/cleanup priority/P3 team/cluster-lifecycle
|
Rackspace support has not ben updated in a few months.
cluster/rackspace/cloud-config/minion-cloud-config.yaml is using etcd_servers for kubelet and kube-proxy, but support for them has been removed since v0.9, I think.
I'll remove it in a few days if no-one makes a counter-offer to get the config working with latest release.
|
1.0
|
Consider removing Rackspace support - Rackspace support has not ben updated in a few months.
cluster/rackspace/cloud-config/minion-cloud-config.yaml is using etcd_servers for kubelet and kube-proxy, but support for them has been removed since v0.9, I think.
I'll remove it in a few days if no-one makes a counter-offer to get the config working with latest release.
|
non_architecture
|
consider removing rackspace support rackspace support has not ben updated in a few months cluster rackspace cloud config minion cloud config yaml is using etcd servers for kubelet and kube proxy but support for them has been removed since i think i ll remove it in a few days if no one makes a counter offer to get the config working with latest release
| 0
|
46,136
| 13,150,684,800
|
IssuesEvent
|
2020-08-09 12:57:39
|
shaundmorris/ddf
|
https://api.github.com/repos/shaundmorris/ddf
|
closed
|
WS-2017-0120 High Severity Vulnerability detected by WhiteSource
|
security vulnerability wontfix
|
## WS-2017-0120 - High Severity Vulnerability
<details><summary><img src='https://www.whitesourcesoftware.com/wp-content/uploads/2018/10/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>angular-1.3.8.min.js</b>, <b>angular-1.3.8.js</b></p></summary>
<p>
<details><summary><b>angular-1.3.8.min.js</b></p></summary>
<p>AngularJS is an MVC framework for building web applications. The core features include HTML enhanced with custom component and data-binding capabilities, dependency injection and strong focus on simplicity, testability, maintainability and boiler-plate reduction.</p>
<p>path: /ddf/distribution/solr-distro/target/solr-7.4.0/server/solr-webapp/webapp/libs/angular.min.js,/ddf/distribution/kernel/target/dependencies/solr/server/solr-webapp/webapp/libs/angular.min.js,/ddf/distribution/ddf/target/dependencies/solr/server/solr-webapp/webapp/libs/angular.min.js</p>
<p>
<p>Library home page: <a href=https://cdnjs.cloudflare.com/ajax/libs/angular.js/1.3.8/angular.min.js>https://cdnjs.cloudflare.com/ajax/libs/angular.js/1.3.8/angular.min.js</a></p>
Dependency Hierarchy:
- :x: **angular-1.3.8.min.js** (Vulnerable Library)
</details>
<details><summary><b>angular-1.3.8.js</b></p></summary>
<p>AngularJS is an MVC framework for building web applications. The core features include HTML enhanced with custom component and data-binding capabilities, dependency injection and strong focus on simplicity, testability, maintainability and boiler-plate reduction.</p>
<p>path: /ddf/distribution/solr-distro/target/solr-7.4.0/server/solr-webapp/webapp/libs/angular.js,/ddf/distribution/kernel/target/dependencies/solr/server/solr-webapp/webapp/libs/angular.js,/ddf/distribution/ddf/target/dependencies/solr/server/solr-webapp/webapp/libs/angular.js</p>
<p>
<p>Library home page: <a href=https://cdnjs.cloudflare.com/ajax/libs/angular.js/1.3.8/angular.js>https://cdnjs.cloudflare.com/ajax/libs/angular.js/1.3.8/angular.js</a></p>
Dependency Hierarchy:
- :x: **angular-1.3.8.js** (Vulnerable Library)
</details>
<p>Found in HEAD commit: <a href="https://github.com/shaundmorris/ddf/commit/ea35fc52f05b85ef437e9a9e39a887ad51692ff0">ea35fc52f05b85ef437e9a9e39a887ad51692ff0</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://www.whitesourcesoftware.com/wp-content/uploads/2018/10/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
No proper sanitize of xlink:href attribute interoplation, thus vulnerable to Cross-site Scripting (XSS).
<p>Publish Date: 2017-01-20
<p>URL: <a href=https://github.com/angular/angular.js/commit/f33ce173c90736e349cf594df717ae3ee41e0f7a>WS-2017-0120</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://www.whitesourcesoftware.com/wp-content/uploads/2018/10/cvss3.png' width=19 height=20> CVSS 2 Score Details (<b>7.8</b>)</summary>
<p>
Base Score Metrics not available</p>
</p>
</details>
<p></p>
<details><summary><img src='https://www.whitesourcesoftware.com/wp-content/uploads/2018/10/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Change files</p>
<p>Origin: <a href="https://github.com/angular/angular.js/commit/f33ce173c90736e349cf594df717ae3ee41e0f7a">https://github.com/angular/angular.js/commit/f33ce173c90736e349cf594df717ae3ee41e0f7a</a></p>
<p>Release Date: 2015-09-18</p>
<p>Fix Resolution: Replace or update the following files: compileSpec.js, compile.js</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
WS-2017-0120 High Severity Vulnerability detected by WhiteSource - ## WS-2017-0120 - High Severity Vulnerability
<details><summary><img src='https://www.whitesourcesoftware.com/wp-content/uploads/2018/10/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>angular-1.3.8.min.js</b>, <b>angular-1.3.8.js</b></p></summary>
<p>
<details><summary><b>angular-1.3.8.min.js</b></p></summary>
<p>AngularJS is an MVC framework for building web applications. The core features include HTML enhanced with custom component and data-binding capabilities, dependency injection and strong focus on simplicity, testability, maintainability and boiler-plate reduction.</p>
<p>path: /ddf/distribution/solr-distro/target/solr-7.4.0/server/solr-webapp/webapp/libs/angular.min.js,/ddf/distribution/kernel/target/dependencies/solr/server/solr-webapp/webapp/libs/angular.min.js,/ddf/distribution/ddf/target/dependencies/solr/server/solr-webapp/webapp/libs/angular.min.js</p>
<p>
<p>Library home page: <a href=https://cdnjs.cloudflare.com/ajax/libs/angular.js/1.3.8/angular.min.js>https://cdnjs.cloudflare.com/ajax/libs/angular.js/1.3.8/angular.min.js</a></p>
Dependency Hierarchy:
- :x: **angular-1.3.8.min.js** (Vulnerable Library)
</details>
<details><summary><b>angular-1.3.8.js</b></p></summary>
<p>AngularJS is an MVC framework for building web applications. The core features include HTML enhanced with custom component and data-binding capabilities, dependency injection and strong focus on simplicity, testability, maintainability and boiler-plate reduction.</p>
<p>path: /ddf/distribution/solr-distro/target/solr-7.4.0/server/solr-webapp/webapp/libs/angular.js,/ddf/distribution/kernel/target/dependencies/solr/server/solr-webapp/webapp/libs/angular.js,/ddf/distribution/ddf/target/dependencies/solr/server/solr-webapp/webapp/libs/angular.js</p>
<p>
<p>Library home page: <a href=https://cdnjs.cloudflare.com/ajax/libs/angular.js/1.3.8/angular.js>https://cdnjs.cloudflare.com/ajax/libs/angular.js/1.3.8/angular.js</a></p>
Dependency Hierarchy:
- :x: **angular-1.3.8.js** (Vulnerable Library)
</details>
<p>Found in HEAD commit: <a href="https://github.com/shaundmorris/ddf/commit/ea35fc52f05b85ef437e9a9e39a887ad51692ff0">ea35fc52f05b85ef437e9a9e39a887ad51692ff0</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://www.whitesourcesoftware.com/wp-content/uploads/2018/10/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
No proper sanitize of xlink:href attribute interoplation, thus vulnerable to Cross-site Scripting (XSS).
<p>Publish Date: 2017-01-20
<p>URL: <a href=https://github.com/angular/angular.js/commit/f33ce173c90736e349cf594df717ae3ee41e0f7a>WS-2017-0120</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://www.whitesourcesoftware.com/wp-content/uploads/2018/10/cvss3.png' width=19 height=20> CVSS 2 Score Details (<b>7.8</b>)</summary>
<p>
Base Score Metrics not available</p>
</p>
</details>
<p></p>
<details><summary><img src='https://www.whitesourcesoftware.com/wp-content/uploads/2018/10/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Change files</p>
<p>Origin: <a href="https://github.com/angular/angular.js/commit/f33ce173c90736e349cf594df717ae3ee41e0f7a">https://github.com/angular/angular.js/commit/f33ce173c90736e349cf594df717ae3ee41e0f7a</a></p>
<p>Release Date: 2015-09-18</p>
<p>Fix Resolution: Replace or update the following files: compileSpec.js, compile.js</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
non_architecture
|
ws high severity vulnerability detected by whitesource ws high severity vulnerability vulnerable libraries angular min js angular js angular min js angularjs is an mvc framework for building web applications the core features include html enhanced with custom component and data binding capabilities dependency injection and strong focus on simplicity testability maintainability and boiler plate reduction path ddf distribution solr distro target solr server solr webapp webapp libs angular min js ddf distribution kernel target dependencies solr server solr webapp webapp libs angular min js ddf distribution ddf target dependencies solr server solr webapp webapp libs angular min js library home page a href dependency hierarchy x angular min js vulnerable library angular js angularjs is an mvc framework for building web applications the core features include html enhanced with custom component and data binding capabilities dependency injection and strong focus on simplicity testability maintainability and boiler plate reduction path ddf distribution solr distro target solr server solr webapp webapp libs angular js ddf distribution kernel target dependencies solr server solr webapp webapp libs angular js ddf distribution ddf target dependencies solr server solr webapp webapp libs angular js library home page a href dependency hierarchy x angular js vulnerable library found in head commit a href vulnerability details no proper sanitize of xlink href attribute interoplation thus vulnerable to cross site scripting xss publish date url a href cvss score details base score metrics not available suggested fix type change files origin a href release date fix resolution replace or update the following files compilespec js compile js step up your open source security game with whitesource
| 0
|
67,892
| 21,301,327,405
|
IssuesEvent
|
2022-04-15 03:49:38
|
klubcoin/lcn-mobile
|
https://api.github.com/repos/klubcoin/lcn-mobile
|
opened
|
[Account Maintenance][General][Language] Fix must be able to process send KLUB after changing language setting.
|
Defect Should Have Minor Account Maintenance Services
|
### **Description:**
Must be able to process send KLUB after changing language setting.
**Build Environment:** Prod Candidate Environment
**Affects Version:** 1.0.0.prod.3
**Device Platform:** Android
**Device OS:** 11
**Test Device:** OnePlus 7T Pro
### **Pre-condition:**
1. User successfully installed Klubcoin App
2. User already has an existing Wallet Account
3. User is currently at Klubcoin Dashboard
### **Steps to Reproduce:**
1. Tap Hamburger Button
2. Tap Settings
3. Tap General
4. Tap Language
5. Select any language
6. Tap Hamburger Button
7. Tap Send Button
8. Select Receiver
9. Enter Amount
10. Tap Next
11. Tap Send Button
### **Expected Result:**
1. Send button is disabled
2. Redirect to Wallet Screen
### **Actual Result:**
Displaying loading send button then staying at send token confirmation screen instead of redirecting to wallet screen that lets user to spam send button
### **Attachment/s:**
|
1.0
|
[Account Maintenance][General][Language] Fix must be able to process send KLUB after changing language setting. - ### **Description:**
Must be able to process send KLUB after changing language setting.
**Build Environment:** Prod Candidate Environment
**Affects Version:** 1.0.0.prod.3
**Device Platform:** Android
**Device OS:** 11
**Test Device:** OnePlus 7T Pro
### **Pre-condition:**
1. User successfully installed Klubcoin App
2. User already has an existing Wallet Account
3. User is currently at Klubcoin Dashboard
### **Steps to Reproduce:**
1. Tap Hamburger Button
2. Tap Settings
3. Tap General
4. Tap Language
5. Select any language
6. Tap Hamburger Button
7. Tap Send Button
8. Select Receiver
9. Enter Amount
10. Tap Next
11. Tap Send Button
### **Expected Result:**
1. Send button is disabled
2. Redirect to Wallet Screen
### **Actual Result:**
Displaying loading send button then staying at send token confirmation screen instead of redirecting to wallet screen that lets user to spam send button
### **Attachment/s:**
|
non_architecture
|
fix must be able to process send klub after changing language setting description must be able to process send klub after changing language setting build environment prod candidate environment affects version prod device platform android device os test device oneplus pro pre condition user successfully installed klubcoin app user already has an existing wallet account user is currently at klubcoin dashboard steps to reproduce tap hamburger button tap settings tap general tap language select any language tap hamburger button tap send button select receiver enter amount tap next tap send button expected result send button is disabled redirect to wallet screen actual result displaying loading send button then staying at send token confirmation screen instead of redirecting to wallet screen that lets user to spam send button attachment s
| 0
|
3,346
| 9,531,166,289
|
IssuesEvent
|
2019-04-29 15:24:17
|
littlevgl/lvgl
|
https://api.github.com/repos/littlevgl/lvgl
|
closed
|
Close/OK keyboard buttons shouldn't fire PRESSED events
|
architecture
|
_`LV_SYMBOL_CLOSE`/`LV_SYMBOL_OK` keyboard buttons should fire `LV_EVENT_CANCEL`/`LV_EVENT_APPLY` on `LV_EVENT_CLICKED` events, not `LV_EVENT_PRESSED`_.
All of the keyboard buttons currently respond to the `LV_EVENT_PRESSED` and `LV_EVENT_LONG_PRESSED_REPEAT` events exclusively. This makes sense for the regular keyboard keys and is normal keyboard behaviour, but it's a problem for the apply/cancel buttons, which trigger the `LV_EVENT_CANCEL` / `LV_EVENT_APPLY` events and in most apps will close the keyboard.
These buttons should respond as normal buttons do, to click events.
The problem (aside from the non-standard UI pattern) is that the the `LV_EVENT_CANCEL` / `LV_EVENT_APPLY` events will typically hide/destroy the keyboard and replace it with something else. With the current approach, the area formerly occupied by the apply/cancel button is still being pressed and results in `LV_EVENT_PRESSED` events being sent to the new content, as well as a `LV_EVENT_CLICKED` event when the button/touch is released.
Separate from this (but included here for discussion since it's the same code location), the current CANCEL/APPLY control flow looks quite strange. From `lv_kb_def_event_cb`:
```
} else if(strcmp(txt, LV_SYMBOL_CLOSE) == 0) {
if(kb->event_cb) {
lv_event_send(kb, LV_EVENT_CANCEL, NULL);
} else {
lv_kb_set_ta(kb, NULL); /*De-assign the text area to hide it cursor if needed*/
lv_obj_del(kb);
}
return;
} else if(strcmp(txt, LV_SYMBOL_OK) == 0) {
if(kb->event_cb)
lv_event_send(kb, LV_EVENT_APPLY, NULL);
else
lv_kb_set_ta(kb, NULL); /*De-assign the text area to hide it cursor if needed*/
return;
}
```
My guess is that the `if(kb->event_cb)` conditional is supposed to check if a custom event_cb has been assigned, if so, call it, otherwise handle the object cleanup (`lv_kb_set_ta`, `lv_obj_del`) here.
But even if no custom handler has been assigned, kb->event_cb will point to `lv_kb_def_event_cb` (i.e. this function), and if it didn't, then this function wouldn't be executing. So I can't see when the `else` clause would ever be called. Perhaps the conditional was supposed to be `if(kb->event_cb != lv_kb_def_event_cb)`? The `else` clauses also differ, with `LV_SYMBOL_CLOSE` deleting the keyboard, but `LV_SYMBOL_OK` leaving it.
Perhaps an alternative solution would be to send the `LV_EVENT_CANCEL`/`LV_EVENT_CANCEL` events regardless and handle them as first class events rather than conditionals on pressed/clicked events.
|
1.0
|
Close/OK keyboard buttons shouldn't fire PRESSED events - _`LV_SYMBOL_CLOSE`/`LV_SYMBOL_OK` keyboard buttons should fire `LV_EVENT_CANCEL`/`LV_EVENT_APPLY` on `LV_EVENT_CLICKED` events, not `LV_EVENT_PRESSED`_.
All of the keyboard buttons currently respond to the `LV_EVENT_PRESSED` and `LV_EVENT_LONG_PRESSED_REPEAT` events exclusively. This makes sense for the regular keyboard keys and is normal keyboard behaviour, but it's a problem for the apply/cancel buttons, which trigger the `LV_EVENT_CANCEL` / `LV_EVENT_APPLY` events and in most apps will close the keyboard.
These buttons should respond as normal buttons do, to click events.
The problem (aside from the non-standard UI pattern) is that the the `LV_EVENT_CANCEL` / `LV_EVENT_APPLY` events will typically hide/destroy the keyboard and replace it with something else. With the current approach, the area formerly occupied by the apply/cancel button is still being pressed and results in `LV_EVENT_PRESSED` events being sent to the new content, as well as a `LV_EVENT_CLICKED` event when the button/touch is released.
Separate from this (but included here for discussion since it's the same code location), the current CANCEL/APPLY control flow looks quite strange. From `lv_kb_def_event_cb`:
```
} else if(strcmp(txt, LV_SYMBOL_CLOSE) == 0) {
if(kb->event_cb) {
lv_event_send(kb, LV_EVENT_CANCEL, NULL);
} else {
lv_kb_set_ta(kb, NULL); /*De-assign the text area to hide it cursor if needed*/
lv_obj_del(kb);
}
return;
} else if(strcmp(txt, LV_SYMBOL_OK) == 0) {
if(kb->event_cb)
lv_event_send(kb, LV_EVENT_APPLY, NULL);
else
lv_kb_set_ta(kb, NULL); /*De-assign the text area to hide it cursor if needed*/
return;
}
```
My guess is that the `if(kb->event_cb)` conditional is supposed to check if a custom event_cb has been assigned, if so, call it, otherwise handle the object cleanup (`lv_kb_set_ta`, `lv_obj_del`) here.
But even if no custom handler has been assigned, kb->event_cb will point to `lv_kb_def_event_cb` (i.e. this function), and if it didn't, then this function wouldn't be executing. So I can't see when the `else` clause would ever be called. Perhaps the conditional was supposed to be `if(kb->event_cb != lv_kb_def_event_cb)`? The `else` clauses also differ, with `LV_SYMBOL_CLOSE` deleting the keyboard, but `LV_SYMBOL_OK` leaving it.
Perhaps an alternative solution would be to send the `LV_EVENT_CANCEL`/`LV_EVENT_CANCEL` events regardless and handle them as first class events rather than conditionals on pressed/clicked events.
|
architecture
|
close ok keyboard buttons shouldn t fire pressed events lv symbol close lv symbol ok keyboard buttons should fire lv event cancel lv event apply on lv event clicked events not lv event pressed all of the keyboard buttons currently respond to the lv event pressed and lv event long pressed repeat events exclusively this makes sense for the regular keyboard keys and is normal keyboard behaviour but it s a problem for the apply cancel buttons which trigger the lv event cancel lv event apply events and in most apps will close the keyboard these buttons should respond as normal buttons do to click events the problem aside from the non standard ui pattern is that the the lv event cancel lv event apply events will typically hide destroy the keyboard and replace it with something else with the current approach the area formerly occupied by the apply cancel button is still being pressed and results in lv event pressed events being sent to the new content as well as a lv event clicked event when the button touch is released separate from this but included here for discussion since it s the same code location the current cancel apply control flow looks quite strange from lv kb def event cb else if strcmp txt lv symbol close if kb event cb lv event send kb lv event cancel null else lv kb set ta kb null de assign the text area to hide it cursor if needed lv obj del kb return else if strcmp txt lv symbol ok if kb event cb lv event send kb lv event apply null else lv kb set ta kb null de assign the text area to hide it cursor if needed return my guess is that the if kb event cb conditional is supposed to check if a custom event cb has been assigned if so call it otherwise handle the object cleanup lv kb set ta lv obj del here but even if no custom handler has been assigned kb event cb will point to lv kb def event cb i e this function and if it didn t then this function wouldn t be executing so i can t see when the else clause would ever be called perhaps the conditional was supposed to be if kb event cb lv kb def event cb the else clauses also differ with lv symbol close deleting the keyboard but lv symbol ok leaving it perhaps an alternative solution would be to send the lv event cancel lv event cancel events regardless and handle them as first class events rather than conditionals on pressed clicked events
| 1
|
7,885
| 19,806,165,228
|
IssuesEvent
|
2022-01-19 07:03:54
|
qtsky89/tblog
|
https://api.github.com/repos/qtsky89/tblog
|
opened
|
Architecture
|
architecture
|
## Requirement
* Want to make Tech blog.
* Overall design should feel like [brunch](https://brunch.co.kr) or [medium](https://medium.com)
* Document should exist only in markdown format.
* Doc editing should be available in real time. (preview needed)
* Post CRUD, Comment CRUD should be available.
## Tech Stack
* Front: Vue.js 3
* Backend: Django 3 with drf (django rest framework)
* Cloud: AWS lightsail
## Mock up
* TBD
|
1.0
|
Architecture - ## Requirement
* Want to make Tech blog.
* Overall design should feel like [brunch](https://brunch.co.kr) or [medium](https://medium.com)
* Document should exist only in markdown format.
* Doc editing should be available in real time. (preview needed)
* Post CRUD, Comment CRUD should be available.
## Tech Stack
* Front: Vue.js 3
* Backend: Django 3 with drf (django rest framework)
* Cloud: AWS lightsail
## Mock up
* TBD
|
architecture
|
architecture requirement want to make tech blog overall design should feel like or document should exist only in markdown format doc editing should be available in real time preview needed post crud comment crud should be available tech stack front vue js backend django with drf django rest framework cloud aws lightsail mock up tbd
| 1
|
2,471
| 7,849,216,640
|
IssuesEvent
|
2018-06-20 02:11:20
|
kubernetes/kubernetes
|
https://api.github.com/repos/kubernetes/kubernetes
|
closed
|
Schedule DaemonSet Pods by default scheduler
|
kind/feature milestone/removed priority/important-soon sig/apps sig/architecture sig/scheduling status/approved-for-milestone status/in-progress
|
**Is this a BUG REPORT or FEATURE REQUEST?**:
/kind feature
**Description**:
After [discussion](https://docs.google.com/document/d/1v7hsusMaeImQrOagktQb40ePbK6Jxp1hzgFB9OZa_ew/edit#), we agree to let kube-scheduler to schedule DaemonSet Pods instead of DaemonSet controller. This issue is used to trace all related sub-tasks.
Design Doc: https://github.com/kubernetes/community/pull/1714
Features: https://github.com/kubernetes/features/issues/548
Tasks:
- [x] Added Alpha flag for NoDaemonSetScheduler feature. (#59630)
- [x] Schedule DaemonSet Pods by default scheduler. (#59862)
- [x] Added MatchFields to NodeSelectorTerm. (#62002)
- [x] Supported nodeSelector.matchFields in scheduler. (#62453)
- [x] ~~Got target node name of pending DaemonSet pod. (#61387)~~
- [x] Schedule DaemonSet Pods in scheduler. (#63223)
- [x] Release notes and doc (https://github.com/kubernetes/website/pull/8842)
/cc @bsalamat
|
1.0
|
Schedule DaemonSet Pods by default scheduler - **Is this a BUG REPORT or FEATURE REQUEST?**:
/kind feature
**Description**:
After [discussion](https://docs.google.com/document/d/1v7hsusMaeImQrOagktQb40ePbK6Jxp1hzgFB9OZa_ew/edit#), we agree to let kube-scheduler to schedule DaemonSet Pods instead of DaemonSet controller. This issue is used to trace all related sub-tasks.
Design Doc: https://github.com/kubernetes/community/pull/1714
Features: https://github.com/kubernetes/features/issues/548
Tasks:
- [x] Added Alpha flag for NoDaemonSetScheduler feature. (#59630)
- [x] Schedule DaemonSet Pods by default scheduler. (#59862)
- [x] Added MatchFields to NodeSelectorTerm. (#62002)
- [x] Supported nodeSelector.matchFields in scheduler. (#62453)
- [x] ~~Got target node name of pending DaemonSet pod. (#61387)~~
- [x] Schedule DaemonSet Pods in scheduler. (#63223)
- [x] Release notes and doc (https://github.com/kubernetes/website/pull/8842)
/cc @bsalamat
|
architecture
|
schedule daemonset pods by default scheduler is this a bug report or feature request kind feature description after we agree to let kube scheduler to schedule daemonset pods instead of daemonset controller this issue is used to trace all related sub tasks design doc features tasks added alpha flag for nodaemonsetscheduler feature schedule daemonset pods by default scheduler added matchfields to nodeselectorterm supported nodeselector matchfields in scheduler got target node name of pending daemonset pod schedule daemonset pods in scheduler release notes and doc cc bsalamat
| 1
|
3,288
| 9,393,107,606
|
IssuesEvent
|
2019-04-07 08:34:05
|
jimkyndemeyer/js-graphql-intellij-plugin
|
https://api.github.com/repos/jimkyndemeyer/js-graphql-intellij-plugin
|
closed
|
Add "Navigate to Declaration" across files
|
enhancement v2-alpha v2-architecture
|
First off thanks for putting this plugin together. It's absolutely amazing and have most likely saved me hours of work already.
I do have one feature request though. It's amazing that you support "Navigate to Declaration" (CMD+Click) in GQL. However we have our schema split up into multiple files to make it easier to navigate. It would be amazing if the plugin could search across all .graphqls files in the project and not just the current file.
Don't have any experience with Intellij Plugins but might have a look around the code base to see if it's an easy fix. But would love to hear from you either way.
Thanks again,
Andreas
|
1.0
|
Add "Navigate to Declaration" across files - First off thanks for putting this plugin together. It's absolutely amazing and have most likely saved me hours of work already.
I do have one feature request though. It's amazing that you support "Navigate to Declaration" (CMD+Click) in GQL. However we have our schema split up into multiple files to make it easier to navigate. It would be amazing if the plugin could search across all .graphqls files in the project and not just the current file.
Don't have any experience with Intellij Plugins but might have a look around the code base to see if it's an easy fix. But would love to hear from you either way.
Thanks again,
Andreas
|
architecture
|
add navigate to declaration across files first off thanks for putting this plugin together it s absolutely amazing and have most likely saved me hours of work already i do have one feature request though it s amazing that you support navigate to declaration cmd click in gql however we have our schema split up into multiple files to make it easier to navigate it would be amazing if the plugin could search across all graphqls files in the project and not just the current file don t have any experience with intellij plugins but might have a look around the code base to see if it s an easy fix but would love to hear from you either way thanks again andreas
| 1
|
1,503
| 6,146,041,079
|
IssuesEvent
|
2017-06-27 13:03:44
|
hyperledger/composer
|
https://api.github.com/repos/hyperledger/composer
|
closed
|
As a user, I need to add non-optional fields to asset definitions for which existing assets already exist
|
architecture design model playground user story
|
## Steps to Reproduce
<!--- Provide a link to a live example, or an unambiguous set of steps to -->
<!--- reproduce this bug include code to reproduce, if relevant -->
1. Open a clean playground (with default model)
2. Switch to Test tab
3. Create a new participant
4. Switch to Define tab
5. Add `o String email` to `Participant` definition
6. Click `Update` button to deploy BN.
7. Switch to Test tab.
Observe error:

## Existing issues
<!-- Have you searched for any existing issues or are their any similar issues that you've found? -->
- [ ] [StackOverflow issues](http://stackoverflow.com/tags/fabric-composer)
- [ ] [GitHub Issues](https://github.com/fabric-composer/fabric-composer/issues)
- [ ] [Rocket Chat history](https://chat.hyperledger.org/channel/fabric-composer)
<!-- please include any links to issues here -->
## Context
<!--- How has this bug affected you? What were you trying to accomplish? -->
Just trying to update an existing model
## Your Environment
<!--- Include as many relevant details about the environment you experienced the bug in -->
* Version used: 0.5.5
* Environment name and version (e.g. Chrome 39, node.js 5.4): Chrome/FF
* Operating System and version (desktop or mobile): Mac desktop Sierra
* Link to your project:
|
1.0
|
As a user, I need to add non-optional fields to asset definitions for which existing assets already exist -
## Steps to Reproduce
<!--- Provide a link to a live example, or an unambiguous set of steps to -->
<!--- reproduce this bug include code to reproduce, if relevant -->
1. Open a clean playground (with default model)
2. Switch to Test tab
3. Create a new participant
4. Switch to Define tab
5. Add `o String email` to `Participant` definition
6. Click `Update` button to deploy BN.
7. Switch to Test tab.
Observe error:

## Existing issues
<!-- Have you searched for any existing issues or are their any similar issues that you've found? -->
- [ ] [StackOverflow issues](http://stackoverflow.com/tags/fabric-composer)
- [ ] [GitHub Issues](https://github.com/fabric-composer/fabric-composer/issues)
- [ ] [Rocket Chat history](https://chat.hyperledger.org/channel/fabric-composer)
<!-- please include any links to issues here -->
## Context
<!--- How has this bug affected you? What were you trying to accomplish? -->
Just trying to update an existing model
## Your Environment
<!--- Include as many relevant details about the environment you experienced the bug in -->
* Version used: 0.5.5
* Environment name and version (e.g. Chrome 39, node.js 5.4): Chrome/FF
* Operating System and version (desktop or mobile): Mac desktop Sierra
* Link to your project:
|
architecture
|
as a user i need to add non optional fields to asset definitions for which existing assets already exist steps to reproduce open a clean playground with default model switch to test tab create a new participant switch to define tab add o string email to participant definition click update button to deploy bn switch to test tab observe error existing issues context just trying to update an existing model your environment version used environment name and version e g chrome node js chrome ff operating system and version desktop or mobile mac desktop sierra link to your project
| 1
|
417,089
| 12,155,756,613
|
IssuesEvent
|
2020-04-25 14:31:47
|
iamdefinitelyahuman/brownie
|
https://api.github.com/repos/iamdefinitelyahuman/brownie
|
closed
|
Update dependencies for coverage / coveralls
|
priority
|
`coveralls` now supports `coverage>=5` ([coveralls-python#214](https://github.com/coveralls-clients/coveralls-python/pull/214))
Currently brownie is fixed to `coverage==v4.5.4`, probably time to bump both of these dependencies.
|
1.0
|
Update dependencies for coverage / coveralls - `coveralls` now supports `coverage>=5` ([coveralls-python#214](https://github.com/coveralls-clients/coveralls-python/pull/214))
Currently brownie is fixed to `coverage==v4.5.4`, probably time to bump both of these dependencies.
|
non_architecture
|
update dependencies for coverage coveralls coveralls now supports coverage currently brownie is fixed to coverage probably time to bump both of these dependencies
| 0
|
11,078
| 27,966,700,746
|
IssuesEvent
|
2023-03-24 20:15:30
|
bcgov/ols-geocoder
|
https://api.github.com/repos/bcgov/ols-geocoder
|
closed
|
Deploy a second batch geocoder to support continuous availability
|
cloud ready architecture medium priority task continuous availability
|
By deploying a second batch geocoder on its own CPF, we get continuous availability.
|
1.0
|
Deploy a second batch geocoder to support continuous availability - By deploying a second batch geocoder on its own CPF, we get continuous availability.
|
architecture
|
deploy a second batch geocoder to support continuous availability by deploying a second batch geocoder on its own cpf we get continuous availability
| 1
|
5,164
| 12,166,725,154
|
IssuesEvent
|
2020-04-27 09:42:39
|
jhviggo/capex-SG
|
https://api.github.com/repos/jhviggo/capex-SG
|
closed
|
Architecture MVC setup (1)
|
Architecture
|
Should contain following structure:
- src
- assets
- images
- css
- styles.css
- views
- includes
- header.pug
- models
- developer.js
- project.js
- controllers
- controller.js
- routes
- project_overview.js
- app.js
- config.js
- test
|
1.0
|
Architecture MVC setup (1) - Should contain following structure:
- src
- assets
- images
- css
- styles.css
- views
- includes
- header.pug
- models
- developer.js
- project.js
- controllers
- controller.js
- routes
- project_overview.js
- app.js
- config.js
- test
|
architecture
|
architecture mvc setup should contain following structure src assets images css styles css views includes header pug models developer js project js controllers controller js routes project overview js app js config js test
| 1
|
10,064
| 26,174,014,064
|
IssuesEvent
|
2023-01-02 06:58:40
|
rubygems/bundler-site
|
https://api.github.com/repos/rubygems/bundler-site
|
closed
|
Integrate bundle_help with man from rubygems/rubygems/bundler
|
content/missing architecture/cleanup
|
We do not have bundle-help.1.ronn at https://github.com/rubygems/rubygems/tree/master/bundler/lib/bundler/man yet
- [x] https://github.com/rubygems/rubygems/pull/5886 Create `bundle-help.1.ronn` in https://github.com/rubygems/rubygems/tree/master/bundler/lib/bundler/man
- https://github.com/rubygems/bundler-site/blob/cdaa5689c3e281b9ad32b2ca5ade30659b554868/source/v2.3/bundle_help.html.haml might be little helpful
- [x] Replace `source/v:ver/bundle_help.html.haml` with `bundle-help.1.ronn`
|
1.0
|
Integrate bundle_help with man from rubygems/rubygems/bundler - We do not have bundle-help.1.ronn at https://github.com/rubygems/rubygems/tree/master/bundler/lib/bundler/man yet
- [x] https://github.com/rubygems/rubygems/pull/5886 Create `bundle-help.1.ronn` in https://github.com/rubygems/rubygems/tree/master/bundler/lib/bundler/man
- https://github.com/rubygems/bundler-site/blob/cdaa5689c3e281b9ad32b2ca5ade30659b554868/source/v2.3/bundle_help.html.haml might be little helpful
- [x] Replace `source/v:ver/bundle_help.html.haml` with `bundle-help.1.ronn`
|
architecture
|
integrate bundle help with man from rubygems rubygems bundler we do not have bundle help ronn at yet create bundle help ronn in might be little helpful replace source v ver bundle help html haml with bundle help ronn
| 1
|
193,225
| 15,371,208,899
|
IssuesEvent
|
2021-03-02 09:44:51
|
AbbyXSu/Financial_report_generator
|
https://api.github.com/repos/AbbyXSu/Financial_report_generator
|
closed
|
[Story] service 4 - report aggregate service
|
User Story documentation
|
the report aggregate service will receive POST request from report engine, which has passed down the JSON object from revenue and expense service via http get request; and process the revenue and expense to calculate the income. profit/loss, and efficiency ratio. and return back to report_engine as JSON object .
|
1.0
|
[Story] service 4 - report aggregate service - the report aggregate service will receive POST request from report engine, which has passed down the JSON object from revenue and expense service via http get request; and process the revenue and expense to calculate the income. profit/loss, and efficiency ratio. and return back to report_engine as JSON object .
|
non_architecture
|
service report aggregate service the report aggregate service will receive post request from report engine which has passed down the json object from revenue and expense service via http get request and process the revenue and expense to calculate the income profit loss and efficiency ratio and return back to report engine as json object
| 0
|
7,536
| 18,162,180,833
|
IssuesEvent
|
2021-09-27 10:54:41
|
verida/verida-js
|
https://api.github.com/repos/verida/verida-js
|
closed
|
Migrate to pbkdf2
|
bug architecture
|
Need to update dependencies to use `pbkdf2` password hashing algorithm as it works across nodeJs, browser and react-native environments.
After a lot of investgation, there is no easy cross-environment solution exists for `argon2id` or `scrypt`.
|
1.0
|
Migrate to pbkdf2 - Need to update dependencies to use `pbkdf2` password hashing algorithm as it works across nodeJs, browser and react-native environments.
After a lot of investgation, there is no easy cross-environment solution exists for `argon2id` or `scrypt`.
|
architecture
|
migrate to need to update dependencies to use password hashing algorithm as it works across nodejs browser and react native environments after a lot of investgation there is no easy cross environment solution exists for or scrypt
| 1
|
8,955
| 23,852,405,192
|
IssuesEvent
|
2022-09-06 19:16:23
|
FusionAuth/fusionauth-issues
|
https://api.github.com/repos/FusionAuth/fusionauth-issues
|
closed
|
User Self Service Account Management "Keep Me
|
enhancement working as designed architecture
|
## Self Service Account Management Login Bug - Unchecking "Keep me signed in" prevents user access
### Description
I created an application in a tenant for a user to log into to edit their profile using FusionAuth's Self Service Account Management tool.
My relevant OAuth configuration for the application is as follows:
client_id: \<application id\>
client_secret: \<obscured\>
Client Authentication: "Not required when using PCKE"
PKCE: "Not required when using client authentication"
I created a user and assigned the user to my application within my tenant. I then used the Account URL (found when inspecting the application that takes the form of \<subdomain\>.fusionauth.io/account/?client_id=\<application id\>) to attempt to log in, unchecking "Keep me signed in". FusionAuth reported a successful log in on the user's page in the console, but a network trace shows that I was routed back to the log in page, which appears to the user that they did not successfully log in.
However, when I leave the "Keep me signed in" checkbox checked, and log in, I am authenticated properly and can view my user edit page.
### Affects versions
1.30.2
### Steps to reproduce
Steps to reproduce the behavior:
1. Create a tenant in the FusionAuth Web Console
2. Create an application within the newly created tenant
3. Create a user, setup user password, and assign them to the newly created application
4. Visit application page in web console, inspect application, and copy Account URL
5. Visit Account URL, enter username and password, and uncheck "Keep me signed in"
6. Will get redirected to log in page
7. Verify that log in succeeded by visiting user page in FusionAuth web console -\> Recent Logins
### Expected behavior
Access the self service account management page (the ability to edit and change my user's profile with the appropriate permissions setup).
### Screenshots
If applicable, add screenshots to help explain your problem.
Login where "Keep me signed in" unchecked:
<img width="960" alt="debug1" src="https://user-images.githubusercontent.com/34141612/148833289-6eec2c6c-f455-463a-a1a8-51081038232d.png">
<img width="958" alt="debug2" src="https://user-images.githubusercontent.com/34141612/148833299-5ff5bd6c-cfb1-4cc3-b78f-08c1349aad75.png">
Login where "Keep me signed in" checked:
<img width="957" alt="debug4" src="https://user-images.githubusercontent.com/34141612/148833348-2ffb3de8-1546-461a-90d4-1aed17fdd2d7.png">
<img width="961" alt="debug3" src="https://user-images.githubusercontent.com/34141612/148833356-488efca8-477c-4e8a-9b99-5e5abf037207.png">
### Platform
(Please complete the following information)
- Device: Desktop
- OS: Windows 10
- Browser + version: Chrome 97.0.4692.71 | Edge 97.0.1072.55
### Community guidelines
N/A
### Related
- https://github.com/FusionAuth/fusionauth-issues/issues/1860
### Additional context
Additionally, when attempting to log into the Self Service Account Management portal, if one uses a browser that does not save cookies (like incognito mode), the portal redirects the user to the login page as well. This issue may be related to what I've described above.
|
1.0
|
User Self Service Account Management "Keep Me - ## Self Service Account Management Login Bug - Unchecking "Keep me signed in" prevents user access
### Description
I created an application in a tenant for a user to log into to edit their profile using FusionAuth's Self Service Account Management tool.
My relevant OAuth configuration for the application is as follows:
client_id: \<application id\>
client_secret: \<obscured\>
Client Authentication: "Not required when using PCKE"
PKCE: "Not required when using client authentication"
I created a user and assigned the user to my application within my tenant. I then used the Account URL (found when inspecting the application that takes the form of \<subdomain\>.fusionauth.io/account/?client_id=\<application id\>) to attempt to log in, unchecking "Keep me signed in". FusionAuth reported a successful log in on the user's page in the console, but a network trace shows that I was routed back to the log in page, which appears to the user that they did not successfully log in.
However, when I leave the "Keep me signed in" checkbox checked, and log in, I am authenticated properly and can view my user edit page.
### Affects versions
1.30.2
### Steps to reproduce
Steps to reproduce the behavior:
1. Create a tenant in the FusionAuth Web Console
2. Create an application within the newly created tenant
3. Create a user, setup user password, and assign them to the newly created application
4. Visit application page in web console, inspect application, and copy Account URL
5. Visit Account URL, enter username and password, and uncheck "Keep me signed in"
6. Will get redirected to log in page
7. Verify that log in succeeded by visiting user page in FusionAuth web console -\> Recent Logins
### Expected behavior
Access the self service account management page (the ability to edit and change my user's profile with the appropriate permissions setup).
### Screenshots
If applicable, add screenshots to help explain your problem.
Login where "Keep me signed in" unchecked:
<img width="960" alt="debug1" src="https://user-images.githubusercontent.com/34141612/148833289-6eec2c6c-f455-463a-a1a8-51081038232d.png">
<img width="958" alt="debug2" src="https://user-images.githubusercontent.com/34141612/148833299-5ff5bd6c-cfb1-4cc3-b78f-08c1349aad75.png">
Login where "Keep me signed in" checked:
<img width="957" alt="debug4" src="https://user-images.githubusercontent.com/34141612/148833348-2ffb3de8-1546-461a-90d4-1aed17fdd2d7.png">
<img width="961" alt="debug3" src="https://user-images.githubusercontent.com/34141612/148833356-488efca8-477c-4e8a-9b99-5e5abf037207.png">
### Platform
(Please complete the following information)
- Device: Desktop
- OS: Windows 10
- Browser + version: Chrome 97.0.4692.71 | Edge 97.0.1072.55
### Community guidelines
N/A
### Related
- https://github.com/FusionAuth/fusionauth-issues/issues/1860
### Additional context
Additionally, when attempting to log into the Self Service Account Management portal, if one uses a browser that does not save cookies (like incognito mode), the portal redirects the user to the login page as well. This issue may be related to what I've described above.
|
architecture
|
user self service account management keep me self service account management login bug unchecking keep me signed in prevents user access description i created an application in a tenant for a user to log into to edit their profile using fusionauth s self service account management tool my relevant oauth configuration for the application is as follows client id client secret client authentication not required when using pcke pkce not required when using client authentication i created a user and assigned the user to my application within my tenant i then used the account url found when inspecting the application that takes the form of fusionauth io account client id to attempt to log in unchecking keep me signed in fusionauth reported a successful log in on the user s page in the console but a network trace shows that i was routed back to the log in page which appears to the user that they did not successfully log in however when i leave the keep me signed in checkbox checked and log in i am authenticated properly and can view my user edit page affects versions steps to reproduce steps to reproduce the behavior create a tenant in the fusionauth web console create an application within the newly created tenant create a user setup user password and assign them to the newly created application visit application page in web console inspect application and copy account url visit account url enter username and password and uncheck keep me signed in will get redirected to log in page verify that log in succeeded by visiting user page in fusionauth web console recent logins expected behavior access the self service account management page the ability to edit and change my user s profile with the appropriate permissions setup screenshots if applicable add screenshots to help explain your problem login where keep me signed in unchecked img width alt src img width alt src login where keep me signed in checked img width alt src img width alt src platform please complete the following information device desktop os windows browser version chrome edge community guidelines n a related additional context additionally when attempting to log into the self service account management portal if one uses a browser that does not save cookies like incognito mode the portal redirects the user to the login page as well this issue may be related to what i ve described above
| 1
|
62,775
| 12,240,574,544
|
IssuesEvent
|
2020-05-05 00:48:21
|
chshsmit/WeBoredGames
|
https://api.github.com/repos/chshsmit/WeBoredGames
|
closed
|
Button Wording in Codenames
|
client codenames good first issue
|
When the game ends, there are two buttons for the room leader to select.
- Back Home:
- Change this wording to be: `Return to Lobby`
- Restart:
- Change this wording to be: `Restart Game`
|
1.0
|
Button Wording in Codenames - When the game ends, there are two buttons for the room leader to select.
- Back Home:
- Change this wording to be: `Return to Lobby`
- Restart:
- Change this wording to be: `Restart Game`
|
non_architecture
|
button wording in codenames when the game ends there are two buttons for the room leader to select back home change this wording to be return to lobby restart change this wording to be restart game
| 0
|
108,948
| 23,684,520,348
|
IssuesEvent
|
2022-08-29 04:13:19
|
sast-automation-dev/JavaVulnerableLab-18
|
https://api.github.com/repos/sast-automation-dev/JavaVulnerableLab-18
|
opened
|
Code Security Report: 111 high severity findings, 177 total findings
|
code security findings
|
# Code Security Report
**Latest Scan:** 2022-08-29 04:12am
**Total Findings:** 177
**Tested Project Files:** 105
**Detected Programming Languages:** 2
<!-- SAST-MANUAL-SCAN-START -->
- [ ] Check this box to manually trigger a scan
<!-- SAST-MANUAL-SCAN-END -->
## Language: Java
| Severity | CWE | Vulnerability Type | Count |
|-|-|-|-|
|<img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High|[CWE-89](https://cwe.mitre.org/data/definitions/89.html)|SQL Injection|38|
|<img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High|[CWE-643](https://cwe.mitre.org/data/definitions/643.html)|XPath Injection|2|
|<img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High|[CWE-94](https://cwe.mitre.org/data/definitions/94.html)|Code Injection|2|
|<img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High|[CWE-22](https://cwe.mitre.org/data/definitions/22.html)|Path/Directory Traversal|11|
|<img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High|[CWE-73](https://cwe.mitre.org/data/definitions/73.html)|File Manipulation|1|
|<img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High|[CWE-79](https://cwe.mitre.org/data/definitions/79.html)|Cross-Site Scripting|57|
|<img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium|[CWE-798](https://cwe.mitre.org/data/definitions/798.html)|Hardcoded Password/Credentials|1|
|<img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium|[CWE-338](https://cwe.mitre.org/data/definitions/338.html)|Weak Pseudo-Random|1|
|<img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium|[CWE-244](https://cwe.mitre.org/data/definitions/244.html)|Heap Inspection|13|
|<img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium|[CWE-501](https://cwe.mitre.org/data/definitions/501.html)|Trust Boundary Violation|11|
|<img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium|[CWE-209](https://cwe.mitre.org/data/definitions/209.html)|Error Messages Information Exposure|3|
|<img src='https://whitesource-resources.whitesourcesoftware.com/low_vul.png' width=19 height=20> Low|[CWE-601](https://cwe.mitre.org/data/definitions/601.html)|Unvalidated/Open Redirect|1|
|<img src='https://whitesource-resources.whitesourcesoftware.com/low_vul.png' width=19 height=20> Low|[CWE-916](https://cwe.mitre.org/data/definitions/916.html)|Weak Hash Strength|1|
|<img src='https://whitesource-resources.whitesourcesoftware.com/low_vul.png' width=19 height=20> Low|[CWE-113](https://cwe.mitre.org/data/definitions/113.html)|HTTP Header Injection|3|
|<img src='https://whitesource-resources.whitesourcesoftware.com/low_vul.png' width=19 height=20> Low|[CWE-20](https://cwe.mitre.org/data/definitions/20.html)|Cookie Injection|4|
|<img src='https://whitesource-resources.whitesourcesoftware.com/low_vul.png' width=19 height=20> Low|[CWE-20](https://cwe.mitre.org/data/definitions/20.html)|Session Poisoning|11|
|<img src='https://whitesource-resources.whitesourcesoftware.com/low_vul.png' width=19 height=20> Low|[CWE-941](https://cwe.mitre.org/data/definitions/941.html)|Arbitrary Server Connection|14|
### Details
> The below list presents the 20 most relevant findings that need your attention. To view information on the remaining findings, navigate to the [Mend SAST Application](https://dev.whitesourcesoftware.com/sast/#/scans/e12538bf-5dc6-4028-8a9a-7a4df78123e6/details).
<details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20>SQL Injection (CWE-89) : 20</summary>
#### Findings
<details>
<summary>vulnerability/Messages.jsp:14</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/Messages.jsp#L9-L14
</details>
<details>
<summary>vulnerability/UserDetails.jsp:13</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/UserDetails.jsp#L8-L13
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/UserDetails.jsp#L8
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/UserDetails.jsp#L13
</details>
</details>
<details>
<summary>controller/Register.java:58</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Register.java#L53-L58
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Register.java#L46
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Register.java#L58
</details>
</details>
<details>
<summary>controller/Register.java:58</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Register.java#L53-L58
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Register.java#L45
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Register.java#L58
</details>
</details>
<details>
<summary>controller/Register.java:58</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Register.java#L53-L58
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Register.java#L44
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Register.java#L58
</details>
</details>
<details>
<summary>controller/Register.java:58</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Register.java#L53-L58
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Register.java#L43
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Register.java#L58
</details>
</details>
<details>
<summary>controller/Install.java:119</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Install.java#L114-L119
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Install.java#L58
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Install.java#L119
</details>
</details>
<details>
<summary>vulnerability/forum.jsp:48</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/forum.jsp#L43-L48
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/forum.jsp#L43
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/forum.jsp#L48
</details>
</details>
<details>
<summary>vulnerability/forum.jsp:48</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/forum.jsp#L43-L48
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/forum.jsp#L42
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/forum.jsp#L48
</details>
</details>
<details>
<summary>controller/Install.java:127</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Install.java#L122-L127
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Install.java#L60
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Install.java#L127
</details>
</details>
<details>
<summary>csrf/change-info.jsp:31</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/csrf/change-info.jsp#L26-L31
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/csrf/change-info.jsp#L26
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/csrf/change-info.jsp#L31
</details>
</details>
<details>
<summary>controller/Install.java:127</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Install.java#L122-L127
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Install.java#L61
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Install.java#L127
</details>
</details>
<details>
<summary>webapp/changeCardDetails.jsp:43</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/changeCardDetails.jsp#L38-L43
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/changeCardDetails.jsp#L37
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/changeCardDetails.jsp#L43
</details>
</details>
<details>
<summary>webapp/changeCardDetails.jsp:43</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/changeCardDetails.jsp#L38-L43
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/changeCardDetails.jsp#L38
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/changeCardDetails.jsp#L43
</details>
</details>
<details>
<summary>controller/Register.java:59</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Register.java#L54-L59
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Register.java#L43
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Register.java#L59
</details>
</details>
<details>
<summary>controller/Install.java:117</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Install.java#L112-L117
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Install.java#L58
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Install.java#L117
</details>
</details>
<details>
<summary>controller/UsernameCheck.java:48</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/UsernameCheck.java#L43-L48
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/UsernameCheck.java#L42
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/UsernameCheck.java#L48
</details>
</details>
<details>
<summary>idor/change-email.jsp:32</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/idor/change-email.jsp#L27-L32
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/idor/change-email.jsp#L28
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/idor/change-email.jsp#L32
</details>
</details>
<details>
<summary>idor/change-email.jsp:32</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/idor/change-email.jsp#L27-L32
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/idor/change-email.jsp#L27
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/idor/change-email.jsp#L32
</details>
</details>
<details>
<summary>webapp/changeCardDetails.jsp:43</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/changeCardDetails.jsp#L38-L43
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/changeCardDetails.jsp#L39
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/changeCardDetails.jsp#L43
</details>
</details>
</details>
## Language: JavaScript / Node.js
| Severity | CWE | Vulnerability Type | Count |
|-|-|-|-|
|<img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium|[CWE-798](https://cwe.mitre.org/data/definitions/798.html)|Hardcoded Password/Credentials|3|
### Details
> No high vulnerability findings detected. To view information on the remaining findings, navigate to the [Mend SAST Application](https://dev.whitesourcesoftware.com/sast/#/scans/e12538bf-5dc6-4028-8a9a-7a4df78123e6/details).
|
1.0
|
Code Security Report: 111 high severity findings, 177 total findings - # Code Security Report
**Latest Scan:** 2022-08-29 04:12am
**Total Findings:** 177
**Tested Project Files:** 105
**Detected Programming Languages:** 2
<!-- SAST-MANUAL-SCAN-START -->
- [ ] Check this box to manually trigger a scan
<!-- SAST-MANUAL-SCAN-END -->
## Language: Java
| Severity | CWE | Vulnerability Type | Count |
|-|-|-|-|
|<img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High|[CWE-89](https://cwe.mitre.org/data/definitions/89.html)|SQL Injection|38|
|<img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High|[CWE-643](https://cwe.mitre.org/data/definitions/643.html)|XPath Injection|2|
|<img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High|[CWE-94](https://cwe.mitre.org/data/definitions/94.html)|Code Injection|2|
|<img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High|[CWE-22](https://cwe.mitre.org/data/definitions/22.html)|Path/Directory Traversal|11|
|<img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High|[CWE-73](https://cwe.mitre.org/data/definitions/73.html)|File Manipulation|1|
|<img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High|[CWE-79](https://cwe.mitre.org/data/definitions/79.html)|Cross-Site Scripting|57|
|<img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium|[CWE-798](https://cwe.mitre.org/data/definitions/798.html)|Hardcoded Password/Credentials|1|
|<img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium|[CWE-338](https://cwe.mitre.org/data/definitions/338.html)|Weak Pseudo-Random|1|
|<img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium|[CWE-244](https://cwe.mitre.org/data/definitions/244.html)|Heap Inspection|13|
|<img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium|[CWE-501](https://cwe.mitre.org/data/definitions/501.html)|Trust Boundary Violation|11|
|<img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium|[CWE-209](https://cwe.mitre.org/data/definitions/209.html)|Error Messages Information Exposure|3|
|<img src='https://whitesource-resources.whitesourcesoftware.com/low_vul.png' width=19 height=20> Low|[CWE-601](https://cwe.mitre.org/data/definitions/601.html)|Unvalidated/Open Redirect|1|
|<img src='https://whitesource-resources.whitesourcesoftware.com/low_vul.png' width=19 height=20> Low|[CWE-916](https://cwe.mitre.org/data/definitions/916.html)|Weak Hash Strength|1|
|<img src='https://whitesource-resources.whitesourcesoftware.com/low_vul.png' width=19 height=20> Low|[CWE-113](https://cwe.mitre.org/data/definitions/113.html)|HTTP Header Injection|3|
|<img src='https://whitesource-resources.whitesourcesoftware.com/low_vul.png' width=19 height=20> Low|[CWE-20](https://cwe.mitre.org/data/definitions/20.html)|Cookie Injection|4|
|<img src='https://whitesource-resources.whitesourcesoftware.com/low_vul.png' width=19 height=20> Low|[CWE-20](https://cwe.mitre.org/data/definitions/20.html)|Session Poisoning|11|
|<img src='https://whitesource-resources.whitesourcesoftware.com/low_vul.png' width=19 height=20> Low|[CWE-941](https://cwe.mitre.org/data/definitions/941.html)|Arbitrary Server Connection|14|
### Details
> The below list presents the 20 most relevant findings that need your attention. To view information on the remaining findings, navigate to the [Mend SAST Application](https://dev.whitesourcesoftware.com/sast/#/scans/e12538bf-5dc6-4028-8a9a-7a4df78123e6/details).
<details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20>SQL Injection (CWE-89) : 20</summary>
#### Findings
<details>
<summary>vulnerability/Messages.jsp:14</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/Messages.jsp#L9-L14
</details>
<details>
<summary>vulnerability/UserDetails.jsp:13</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/UserDetails.jsp#L8-L13
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/UserDetails.jsp#L8
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/UserDetails.jsp#L13
</details>
</details>
<details>
<summary>controller/Register.java:58</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Register.java#L53-L58
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Register.java#L46
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Register.java#L58
</details>
</details>
<details>
<summary>controller/Register.java:58</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Register.java#L53-L58
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Register.java#L45
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Register.java#L58
</details>
</details>
<details>
<summary>controller/Register.java:58</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Register.java#L53-L58
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Register.java#L44
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Register.java#L58
</details>
</details>
<details>
<summary>controller/Register.java:58</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Register.java#L53-L58
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Register.java#L43
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Register.java#L58
</details>
</details>
<details>
<summary>controller/Install.java:119</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Install.java#L114-L119
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Install.java#L58
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Install.java#L119
</details>
</details>
<details>
<summary>vulnerability/forum.jsp:48</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/forum.jsp#L43-L48
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/forum.jsp#L43
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/forum.jsp#L48
</details>
</details>
<details>
<summary>vulnerability/forum.jsp:48</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/forum.jsp#L43-L48
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/forum.jsp#L42
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/forum.jsp#L48
</details>
</details>
<details>
<summary>controller/Install.java:127</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Install.java#L122-L127
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Install.java#L60
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Install.java#L127
</details>
</details>
<details>
<summary>csrf/change-info.jsp:31</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/csrf/change-info.jsp#L26-L31
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/csrf/change-info.jsp#L26
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/csrf/change-info.jsp#L31
</details>
</details>
<details>
<summary>controller/Install.java:127</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Install.java#L122-L127
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Install.java#L61
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Install.java#L127
</details>
</details>
<details>
<summary>webapp/changeCardDetails.jsp:43</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/changeCardDetails.jsp#L38-L43
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/changeCardDetails.jsp#L37
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/changeCardDetails.jsp#L43
</details>
</details>
<details>
<summary>webapp/changeCardDetails.jsp:43</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/changeCardDetails.jsp#L38-L43
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/changeCardDetails.jsp#L38
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/changeCardDetails.jsp#L43
</details>
</details>
<details>
<summary>controller/Register.java:59</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Register.java#L54-L59
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Register.java#L43
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Register.java#L59
</details>
</details>
<details>
<summary>controller/Install.java:117</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Install.java#L112-L117
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Install.java#L58
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/Install.java#L117
</details>
</details>
<details>
<summary>controller/UsernameCheck.java:48</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/UsernameCheck.java#L43-L48
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/UsernameCheck.java#L42
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/java/org/cysecurity/cspf/jvl/controller/UsernameCheck.java#L48
</details>
</details>
<details>
<summary>idor/change-email.jsp:32</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/idor/change-email.jsp#L27-L32
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/idor/change-email.jsp#L28
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/idor/change-email.jsp#L32
</details>
</details>
<details>
<summary>idor/change-email.jsp:32</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/idor/change-email.jsp#L27-L32
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/idor/change-email.jsp#L27
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/vulnerability/idor/change-email.jsp#L32
</details>
</details>
<details>
<summary>webapp/changeCardDetails.jsp:43</summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/changeCardDetails.jsp#L38-L43
<details>
<summary> Trace </summary>
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/changeCardDetails.jsp#L39
https://github.com/sast-automation-dev/JavaVulnerableLab-18/blob/b41a8c24690dcdf3b0a5bbe9c6cc1d38a1590055/JavaVulnerableLab-18/src/main/webapp/changeCardDetails.jsp#L43
</details>
</details>
</details>
## Language: JavaScript / Node.js
| Severity | CWE | Vulnerability Type | Count |
|-|-|-|-|
|<img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium|[CWE-798](https://cwe.mitre.org/data/definitions/798.html)|Hardcoded Password/Credentials|3|
### Details
> No high vulnerability findings detected. To view information on the remaining findings, navigate to the [Mend SAST Application](https://dev.whitesourcesoftware.com/sast/#/scans/e12538bf-5dc6-4028-8a9a-7a4df78123e6/details).
|
non_architecture
|
code security report high severity findings total findings code security report latest scan total findings tested project files detected programming languages check this box to manually trigger a scan language java severity cwe vulnerability type count high injection high injection high injection high traversal high manipulation high scripting medium password credentials medium pseudo random medium inspection medium boundary violation medium messages information exposure low redirect low hash strength low header injection low injection low poisoning low server connection details the below list presents the most relevant findings that need your attention to view information on the remaining findings navigate to the sql injection cwe findings vulnerability messages jsp vulnerability userdetails jsp trace controller register java trace controller register java trace controller register java trace controller register java trace controller install java trace vulnerability forum jsp trace vulnerability forum jsp trace controller install java trace csrf change info jsp trace controller install java trace webapp changecarddetails jsp trace webapp changecarddetails jsp trace controller register java trace controller install java trace controller usernamecheck java trace idor change email jsp trace idor change email jsp trace webapp changecarddetails jsp trace language javascript node js severity cwe vulnerability type count medium password credentials details no high vulnerability findings detected to view information on the remaining findings navigate to the
| 0
|
11,227
| 28,499,558,925
|
IssuesEvent
|
2023-04-18 16:18:04
|
open-mmlab/mmcv
|
https://api.github.com/repos/open-mmlab/mmcv
|
closed
|
from mmcv.runner import load_checkpoint ModuleNotFoundError: No module named 'mmcv.runner'
|
new architecture
|
Hi,
I met the error when I run the code
from mmcv.runner import load_checkpoint
ModuleNotFoundError: No module named 'mmcv.runner'
|
1.0
|
from mmcv.runner import load_checkpoint ModuleNotFoundError: No module named 'mmcv.runner' - Hi,
I met the error when I run the code
from mmcv.runner import load_checkpoint
ModuleNotFoundError: No module named 'mmcv.runner'
|
architecture
|
from mmcv runner import load checkpoint modulenotfounderror no module named mmcv runner hi i met the error when i run the code from mmcv runner import load checkpoint modulenotfounderror no module named mmcv runner
| 1
|
8,582
| 7,495,027,184
|
IssuesEvent
|
2018-04-07 16:25:21
|
kaitai-io/kaitai_struct
|
https://api.github.com/repos/kaitai-io/kaitai_struct
|
closed
|
Documentation updates remain uncommited
|
infrastructure
|
There are 2 open PRs with plenty of documentation text, and we should sort it out before shipping 0.8. I am opening this Issue so that it doesnt get forgotten.
- [ ] https://github.com/kaitai-io/kaitai_struct_doc/pull/7
- [ ] https://github.com/kaitai-io/kaitai_struct_doc/pull/5
I am asssigning @GreyCat because he seems to be the ultimate authority here and noone else will merge it on his own.
|
1.0
|
Documentation updates remain uncommited - There are 2 open PRs with plenty of documentation text, and we should sort it out before shipping 0.8. I am opening this Issue so that it doesnt get forgotten.
- [ ] https://github.com/kaitai-io/kaitai_struct_doc/pull/7
- [ ] https://github.com/kaitai-io/kaitai_struct_doc/pull/5
I am asssigning @GreyCat because he seems to be the ultimate authority here and noone else will merge it on his own.
|
non_architecture
|
documentation updates remain uncommited there are open prs with plenty of documentation text and we should sort it out before shipping i am opening this issue so that it doesnt get forgotten i am asssigning greycat because he seems to be the ultimate authority here and noone else will merge it on his own
| 0
|
382,626
| 26,507,831,711
|
IssuesEvent
|
2023-01-18 15:02:41
|
GAIGResearch/TabletopGames
|
https://api.github.com/repos/GAIGResearch/TabletopGames
|
closed
|
Website
|
documentation
|
Create a website for the project, with general info, competition info (when decided), documentation
|
1.0
|
Website - Create a website for the project, with general info, competition info (when decided), documentation
|
non_architecture
|
website create a website for the project with general info competition info when decided documentation
| 0
|
9,598
| 24,877,644,059
|
IssuesEvent
|
2022-10-27 20:40:34
|
MicrosoftDocs/architecture-center
|
https://api.github.com/repos/MicrosoftDocs/architecture-center
|
closed
|
What about Azure Container Apps?
|
doc-enhancement assigned-to-author triaged architecture-center/svc Pri2 azure-guide/subsvc
|
This decision chart is great to summarize all the choices available for Compute.
However with Azure Container Apps in GA, it will interesting to see in which category it will be placed.
Would be great if it can be added here.
https://techcommunity.microsoft.com/t5/apps-on-azure-blog/introducing-azure-container-apps-a-serverless-container-service/ba-p/2867265#:~:text=%20Introducing%20Azure%20Container%20Apps%3A%20a%20serverless%20container,management.%20Azure%20Container%20Apps%20streamlines%20the...%20More%20
---
#### Document Details
⚠ *Do not edit this section. It is required for docs.microsoft.com ➟ GitHub issue linking.*
* ID: 510808e8-db5d-6b07-9a04-6edb743a2dfc
* Version Independent ID: 20d098aa-ef31-cb26-d677-765cfc9a7164
* Content: [Choose an Azure compute service - Azure Architecture Center](https://docs.microsoft.com/en-us/azure/architecture/guide/technology-choices/compute-decision-tree)
* Content Source: [docs/guide/technology-choices/compute-decision-tree.md](https://github.com/microsoftdocs/architecture-center/blob/main/docs/guide/technology-choices/compute-decision-tree.md)
* Service: **architecture-center**
* Sub-service: **azure-guide**
* GitHub Login: @EdPrice-MSFT
* Microsoft Alias: **pnp**
|
1.0
|
What about Azure Container Apps? -
This decision chart is great to summarize all the choices available for Compute.
However with Azure Container Apps in GA, it will interesting to see in which category it will be placed.
Would be great if it can be added here.
https://techcommunity.microsoft.com/t5/apps-on-azure-blog/introducing-azure-container-apps-a-serverless-container-service/ba-p/2867265#:~:text=%20Introducing%20Azure%20Container%20Apps%3A%20a%20serverless%20container,management.%20Azure%20Container%20Apps%20streamlines%20the...%20More%20
---
#### Document Details
⚠ *Do not edit this section. It is required for docs.microsoft.com ➟ GitHub issue linking.*
* ID: 510808e8-db5d-6b07-9a04-6edb743a2dfc
* Version Independent ID: 20d098aa-ef31-cb26-d677-765cfc9a7164
* Content: [Choose an Azure compute service - Azure Architecture Center](https://docs.microsoft.com/en-us/azure/architecture/guide/technology-choices/compute-decision-tree)
* Content Source: [docs/guide/technology-choices/compute-decision-tree.md](https://github.com/microsoftdocs/architecture-center/blob/main/docs/guide/technology-choices/compute-decision-tree.md)
* Service: **architecture-center**
* Sub-service: **azure-guide**
* GitHub Login: @EdPrice-MSFT
* Microsoft Alias: **pnp**
|
architecture
|
what about azure container apps this decision chart is great to summarize all the choices available for compute however with azure container apps in ga it will interesting to see in which category it will be placed would be great if it can be added here document details ⚠ do not edit this section it is required for docs microsoft com ➟ github issue linking id version independent id content content source service architecture center sub service azure guide github login edprice msft microsoft alias pnp
| 1
|
755,153
| 26,419,211,718
|
IssuesEvent
|
2023-01-13 18:40:08
|
bcgov/foi-flow
|
https://api.github.com/repos/bcgov/foi-flow
|
closed
|
Divisional Tracking Update - TRA
|
Task high priority onboarding
|
Title of ticket:
#### Description
This is related to ticket #3191
Although closed and deployed to production - it was not technically done as required. Ministry requested a specific order, and not the default alphabetical order.
In addition - some new divisions that were previously missed by the client have been added.
#### DOD
Add and update the division so the **order is exactly as presented**
- [x] Deputy Minister’s Office
- [x] Minister's Office
- [x] Minister of State
- [x] Corporate Writing Services
- [x] Finance & Risk Management Division
- [x] Highways & Regional Services Division
- [x] Headquarters
- [x] Northern Region
- [x] South Coast Region
- [x] Southern Interior Region
- [x] Commercial Vehicle Safety & Enforcement
- [x] Passenger Transportation Branch
- [x] Integrated Transportation & Infrastructure Services Division
- [x] Policy, Programs, & Partnerships Division
- [x] Strategic & Corporate Priorities Division
- [x] BC Railway Company
- [x] BC Transit
- [x] BC Transportation Finance Authority
- [x] Transportation Investment Company
|
1.0
|
Divisional Tracking Update - TRA - Title of ticket:
#### Description
This is related to ticket #3191
Although closed and deployed to production - it was not technically done as required. Ministry requested a specific order, and not the default alphabetical order.
In addition - some new divisions that were previously missed by the client have been added.
#### DOD
Add and update the division so the **order is exactly as presented**
- [x] Deputy Minister’s Office
- [x] Minister's Office
- [x] Minister of State
- [x] Corporate Writing Services
- [x] Finance & Risk Management Division
- [x] Highways & Regional Services Division
- [x] Headquarters
- [x] Northern Region
- [x] South Coast Region
- [x] Southern Interior Region
- [x] Commercial Vehicle Safety & Enforcement
- [x] Passenger Transportation Branch
- [x] Integrated Transportation & Infrastructure Services Division
- [x] Policy, Programs, & Partnerships Division
- [x] Strategic & Corporate Priorities Division
- [x] BC Railway Company
- [x] BC Transit
- [x] BC Transportation Finance Authority
- [x] Transportation Investment Company
|
non_architecture
|
divisional tracking update tra title of ticket description this is related to ticket although closed and deployed to production it was not technically done as required ministry requested a specific order and not the default alphabetical order in addition some new divisions that were previously missed by the client have been added dod add and update the division so the order is exactly as presented deputy minister’s office minister s office minister of state corporate writing services finance risk management division highways regional services division headquarters northern region south coast region southern interior region commercial vehicle safety enforcement passenger transportation branch integrated transportation infrastructure services division policy programs partnerships division strategic corporate priorities division bc railway company bc transit bc transportation finance authority transportation investment company
| 0
|
417,946
| 12,190,560,270
|
IssuesEvent
|
2020-04-29 09:31:55
|
cilium/cilium
|
https://api.github.com/repos/cilium/cilium
|
opened
|
Revisit NO_REDIRECT in datapath
|
area/kube-proxy-free kind/feature priority/release-blocker
|
We should be able to get rid of `NO_REDIRECT` which was introduced by https://github.com/cilium/cilium/pull/8639. This is because in bpf_lxc we do a tail call to `CILIUM_CALL_IPV{4,6}_NODEPORT_REVNAT` which does ctx_redirect bypassing the stack and thus the troublesome iptables rule.
|
1.0
|
Revisit NO_REDIRECT in datapath - We should be able to get rid of `NO_REDIRECT` which was introduced by https://github.com/cilium/cilium/pull/8639. This is because in bpf_lxc we do a tail call to `CILIUM_CALL_IPV{4,6}_NODEPORT_REVNAT` which does ctx_redirect bypassing the stack and thus the troublesome iptables rule.
|
non_architecture
|
revisit no redirect in datapath we should be able to get rid of no redirect which was introduced by this is because in bpf lxc we do a tail call to cilium call ipv nodeport revnat which does ctx redirect bypassing the stack and thus the troublesome iptables rule
| 0
|
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.