id
stringlengths 12
47
| title
stringlengths 0
256
⌀ | description
stringlengths 3
139k
| cpes
sequencelengths 0
5.42k
| cvss_v4_0
float64 0
10
⌀ | cvss_v3_1
float64 0
10
⌀ | cvss_v3_0
float64 0
10
⌀ | cvss_v2_0
float64 0
10
⌀ |
|---|---|---|---|---|---|---|---|
GHSA-63w9-q3qg-2wg7 | An arbitrary file upload vulnerability in the component ajax_link.php of lylme_spage v1.7.0 allows attackers to execute arbitrary code via uploading a crafted file. | [] | null | 7.8 | null | null |
|
CVE-2018-3856 | An exploitable vulnerability exists in the smart cameras RTSP configuration of the Samsung SmartThings Hub STH-ETH-250 - Firmware version 0.20.17. The device incorrectly handles spaces in the URL field, leading to an arbitrary operating system command injection. An attacker can send a series of HTTP requests to trigger this vulnerability. | [
"cpe:2.3:o:samsung:sth-eth-250_firmware:0.20.17:*:*:*:*:*:*:*",
"cpe:2.3:h:samsung:sth-eth-250:-:*:*:*:*:*:*:*"
] | null | null | 9.9 | null |
|
CVE-2025-22576 | WordPress Site PIN Plugin <= 1.3 - Reflected Cross Site Scripting (XSS) vulnerability | Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') vulnerability in Marcus Downing Site PIN allows Reflected XSS.This issue affects Site PIN: from n/a through 1.3. | [] | null | 7.1 | null | null |
GHSA-mv2c-xpfp-7pmh | IBM Lotus Notes Traveler before 8.5.1.3 allows remote attackers to cause a denial of service (sync failure) via a malformed document. | [] | null | null | null | null |
|
GHSA-c4gh-265v-f9p8 | Vulnerability in the PeopleSoft Enterprise PeopleTools product of Oracle PeopleSoft (component: Query). Supported versions that are affected are 8.56, 8.57 and 8.58. Easily exploitable vulnerability allows high privileged attacker with network access via HTTP to compromise PeopleSoft Enterprise PeopleTools. Successful attacks of this vulnerability can result in unauthorized read access to a subset of PeopleSoft Enterprise PeopleTools accessible data. CVSS 3.1 Base Score 2.7 (Confidentiality impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:L/I:N/A:N). | [] | null | null | null | null |
|
GHSA-p666-rr3r-wr28 | SQL injection vulnerability in allauctions.php in Telebid Auction Script allows remote attackers to execute arbitrary SQL commands via the aid parameter. | [] | null | null | null | null |
|
CVE-2024-0030 | In btif_to_bta_response of btif_gatt_util.cc, there is a possible out of bounds read due to an incorrect bounds check. This could lead to local information disclosure with no additional execution privileges needed. User interaction is not needed for exploitation. | [
"cpe:2.3:o:google:android:11.0:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:12.0:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:12.1:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:13.0:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:14.0:*:*:*:*:*:*:*"
] | null | 5.5 | null | null |
|
GHSA-c776-ff7g-wcxj | Foxit PDF Reader AcroForm Use-After-Free Remote Code Execution Vulnerability. This vulnerability allows remote attackers to execute arbitrary code on affected installations of Foxit PDF Reader. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file.The specific flaw exists within the handling of Doc objects in AcroForms. The issue results from the lack of validating the existence of an object prior to performing operations on the object. An attacker can leverage this vulnerability to execute code in the context of the current process. Was ZDI-CAN-22633. | [] | null | null | 7.8 | null |
|
CVE-2017-1000452 | An XML Signature Wrapping vulnerability exists in Samlify 2.2.0 and earlier, and in predecessor Express-saml2 which could allow attackers to impersonate arbitrary users. | [
"cpe:2.3:a:samlify_project:samlify:*:*:*:*:*:*:*:*"
] | null | null | 7.5 | 6 |
|
CVE-2021-37095 | There is a Integer Overflow or Wraparound vulnerability in Huawei Smartphone.Successful exploitation of this vulnerability may lead to remote denial of service and potential remote code execution. | [
"cpe:2.3:o:huawei:harmonyos:*:*:*:*:*:*:*:*"
] | null | 9.8 | null | 7.5 |
|
CVE-2018-20021 | LibVNC before commit c3115350eb8bb635d0fdb4dbbb0d0541f38ed19c contains a CWE-835: Infinite loop vulnerability in VNC client code. Vulnerability allows attacker to consume excessive amount of resources like CPU and RAM | [
"cpe:2.3:a:libvnc_project:libvncserver:*:*:*:*:*:*:*:*",
"cpe:2.3:o:canonical:ubuntu_linux:14.04:*:*:*:lts:*:*:*",
"cpe:2.3:o:canonical:ubuntu_linux:16.04:*:*:*:lts:*:*:*",
"cpe:2.3:o:canonical:ubuntu_linux:18.04:*:*:*:lts:*:*:*",
"cpe:2.3:o:canonical:ubuntu_linux:18.10:*:*:*:*:*:*:*",
"cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*"
] | null | null | 7.5 | 7.8 |
|
CVE-2024-32582 | WordPress Debug Log Manager plugin <= 2.3.1 - Cross Site Scripting (XSS) vulnerability | Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') vulnerability in Bowo Debug Log Manager allows Stored XSS.This issue affects Debug Log Manager: from n/a through 2.3.1.
| [] | null | 7.1 | null | null |
CVE-2006-3204 | Ultimate PHP Board (UPB) 1.9.6 and earlier uses a cryptographically weak block cipher with a large key collision space, which allows remote attackers to determine a suitable decryption key given the plaintext and ciphertext by obtaining the plaintext password, which is sent when logging in, and the ciphertext, which is set in the pass_env cookie. | [
"cpe:2.3:a:ultimate_php_board:ultimate_php_board:1.8:*:*:*:*:*:*:*",
"cpe:2.3:a:ultimate_php_board:ultimate_php_board:1.8.2:*:*:*:*:*:*:*",
"cpe:2.3:a:ultimate_php_board:ultimate_php_board:1.9:*:*:*:*:*:*:*",
"cpe:2.3:a:ultimate_php_board:ultimate_php_board:1.9.6:*:*:*:*:*:*:*"
] | null | null | null | 5 |
|
CVE-2015-3885 | Integer overflow in the ljpeg_start function in dcraw 7.00 and earlier allows remote attackers to cause a denial of service (crash) via a crafted image, which triggers a buffer overflow, related to the len variable. | [
"cpe:2.3:a:dcraw_project:dcraw:*:*:*:*:*:*:*:*",
"cpe:2.3:o:fedoraproject:fedora:21:*:*:*:*:*:*:*"
] | null | null | null | 4.3 |
|
CVE-2016-9834 | An XSS vulnerability allows remote attackers to execute arbitrary client side script on vulnerable installations of Sophos Cyberoam firewall devices with firmware through 10.6.4. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file. The specific flaw exists within the handling of a request to the "LiveConnectionDetail.jsp" application. GET parameters "applicationname" and "username" are improperly sanitized allowing an attacker to inject arbitrary JavaScript into the page. This can be abused by an attacker to perform a cross-site scripting attack on the user. A vulnerable URI is /corporate/webpages/trafficdiscovery/LiveConnectionDetail.jsp. | [
"cpe:2.3:o:sophos:cyberoam_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:sophos:cyberoam:-:*:*:*:*:*:*:*"
] | null | null | 6.1 | 4.3 |
|
GHSA-9729-phqg-qhx6 | ARCserve NT agents use weak encryption (XOR) for passwords, which allows remote attackers to sniff the authentication request to port 6050 and decrypt the password. | [] | null | null | null | null |
|
CVE-2019-17103 | Get-task-allow entitlement via BDLDaemon on macOS | An Incorrect Default Permissions vulnerability in the BDLDaemon component of Bitdefender AV for Mac allows an attacker to elevate permissions to read protected directories. This issue affects: Bitdefender AV for Mac versions prior to 8.0.0. | [
"cpe:2.3:a:bitdefender:antivirus:*:*:*:*:*:macos:*:*"
] | null | 4.9 | null | null |
GHSA-mp89-pxjh-mww8 | Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') vulnerability in Automattic WooCommerce allows Stored XSS.This issue affects WooCommerce: from n/a through 9.7.0. | [] | null | 5.9 | null | null |
|
CVE-2024-43599 | Remote Desktop Client Remote Code Execution Vulnerability | Remote Desktop Client Remote Code Execution Vulnerability | [
"cpe:2.3:o:microsoft:windows_10_1507:*:*:*:*:*:*:x64:*",
"cpe:2.3:o:microsoft:windows_10_1507:*:*:*:*:*:*:x86:*",
"cpe:2.3:o:microsoft:windows_10_1607:*:*:*:*:*:*:x64:*",
"cpe:2.3:o:microsoft:windows_10_1607:*:*:*:*:*:*:x86:*",
"cpe:2.3:o:microsoft:windows_10_1809:*:*:*:*:*:*:x64:*",
"cpe:2.3:o:microsoft:windows_10_1809:*:*:*:*:*:*:x86:*",
"cpe:2.3:o:microsoft:windows_10_21h2:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_10_22h2:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_11_21h2:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_11_22h2:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_11_23h2:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_11_24h2:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2008:r2:sp1:*:*:*:*:x64:*",
"cpe:2.3:o:microsoft:windows_server_2012:-:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2012:r2:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2016:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2019:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2022:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2022_23h2:*:*:*:*:*:*:*:*"
] | null | 8.8 | null | null |
GHSA-3xhr-vwcx-8p3c | Transient DOS in WLAN Firmware when the length of received beacon is less than length of ieee802.11 beacon frame. | [] | null | 7.5 | null | null |
|
CVE-2010-0991 | Multiple heap-based buffer overflows in imlib2 1.4.3 allow context-dependent attackers to execute arbitrary code via a crafted (1) ARGB, (2) XPM, or (3) BMP file, related to the IMAGE_DIMENSIONS_OK macro in lib/image.h. | [
"cpe:2.3:a:enlightenment:imlib2:1.4.3:*:*:*:*:*:*:*"
] | null | null | null | 6.8 |
|
GHSA-3p4r-x5mr-f32g | TOTOLink outdoor CPE CP900 V6.3c.566_B20171026 is discovered to contain a command injection vulnerability in the setWebWlanIdx function via the webWlanIdx parameter. This vulnerability allows attackers to execute arbitrary commands via a crafted request. | [] | null | 9.8 | null | null |
|
GHSA-69gq-wgxm-h274 | Cross site scripting vulnerability in 188Jianzhan 2.10 allows attackers to execute arbitrary code via the username parameter to /admin/reg.php. | [] | null | 5.4 | null | null |
|
CVE-2005-4865 | Stack-based buffer overflow in call in IBM DB2 7.x and 8.1 allows remote attackers to execute arbitrary code via a long libname. | [
"cpe:2.3:a:ibm:db2_universal_database:7.0:*:aix:*:*:*:*:*",
"cpe:2.3:a:ibm:db2_universal_database:7.0:*:hp-ux:*:*:*:*:*",
"cpe:2.3:a:ibm:db2_universal_database:7.0:*:linux:*:*:*:*:*",
"cpe:2.3:a:ibm:db2_universal_database:7.0:*:solaris:*:*:*:*:*",
"cpe:2.3:a:ibm:db2_universal_database:7.1:*:aix:*:*:*:*:*",
"cpe:2.3:a:ibm:db2_universal_database:7.1:*:hp-ux:*:*:*:*:*",
"cpe:2.3:a:ibm:db2_universal_database:7.1:*:linux:*:*:*:*:*",
"cpe:2.3:a:ibm:db2_universal_database:7.1:*:solaris:*:*:*:*:*",
"cpe:2.3:a:ibm:db2_universal_database:7.1:*:windows:*:*:*:*:*",
"cpe:2.3:a:ibm:db2_universal_database:7.2:*:aix:*:*:*:*:*",
"cpe:2.3:a:ibm:db2_universal_database:7.2:*:hp-ux:*:*:*:*:*",
"cpe:2.3:a:ibm:db2_universal_database:7.2:*:linux:*:*:*:*:*",
"cpe:2.3:a:ibm:db2_universal_database:7.2:*:solaris:*:*:*:*:*",
"cpe:2.3:a:ibm:db2_universal_database:7.2:*:windows:*:*:*:*:*",
"cpe:2.3:a:ibm:db2_universal_database:8.0:*:aix:*:*:*:*:*",
"cpe:2.3:a:ibm:db2_universal_database:8.0:*:hp-ux:*:*:*:*:*",
"cpe:2.3:a:ibm:db2_universal_database:8.0:*:linux:*:*:*:*:*",
"cpe:2.3:a:ibm:db2_universal_database:8.0:*:solaris:*:*:*:*:*",
"cpe:2.3:a:ibm:db2_universal_database:8.0:*:windows:*:*:*:*:*",
"cpe:2.3:a:ibm:db2_universal_database:8.1:*:aix:*:*:*:*:*",
"cpe:2.3:a:ibm:db2_universal_database:8.1:*:hp_ux:*:*:*:*:*",
"cpe:2.3:a:ibm:db2_universal_database:8.1:*:linux:*:*:*:*:*",
"cpe:2.3:a:ibm:db2_universal_database:8.1:*:solaris:*:*:*:*:*",
"cpe:2.3:a:ibm:db2_universal_database:8.1:*:windows:*:*:*:*:*"
] | null | null | null | 10 |
|
CVE-2023-30430 | IBM Security Verify Access information disclosure | IBM Security Verify Access 10.0.0 through 10.0.7.1 could allow a local user to obtain sensitive information from trace logs. IBM X-Force ID: 252183. | [
"cpe:2.3:a:ibm:security_verify_access:10.0.0.0:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:security_verify_access:10.0.7.1:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:security_verify_access:*:*:*:*:*:*:*:*"
] | null | 5.5 | null | null |
GHSA-pg66-fmrg-mp86 | Off-by-one error in the bmp_rle4_fread function in pngxrbmp.c in OptiPNG before 0.7.6 allows remote attackers to cause a denial of service (out-of-bounds read or write access and crash) or possibly execute arbitrary code via a crafted image file, which triggers a heap-based buffer overflow. | [] | null | null | 8.8 | null |
|
CVE-2018-6706 | McAfee Agent (MA) non-Windows versions incorrect use of temporary file vulnerability | Insecure handling of temporary files in non-Windows McAfee Agent 5.0.0 through 5.0.6, 5.5.0, and 5.5.1 allows an Unprivileged User to introduce custom paths during agent installation in Linux via unspecified vectors. | [
"cpe:2.3:a:mcafee:agent:*:*:*:*:*:*:*:*",
"cpe:2.3:a:mcafee:agent:5.5.0:*:*:*:*:*:*:*",
"cpe:2.3:a:mcafee:agent:5.5.1:*:*:*:*:*:*:*"
] | null | null | 2.3 | null |
CVE-2012-4014 | Unspecified vulnerability in McAfee Email Anti-virus (formerly WebShield SMTP) allows remote attackers to cause a denial of service via unknown vectors. | [
"cpe:2.3:a:mcafee:email_and_web_security:5.0:*:*:*:*:*:*:*",
"cpe:2.3:a:mcafee:email_and_web_security:5.5:*:*:*:*:*:*:*",
"cpe:2.3:a:mcafee:email_and_web_security:5.6:*:*:*:*:*:*:*"
] | null | null | null | 7.8 |
|
CVE-2023-31800 | Cross Site Scripting vulnerability found in Chamilo Lms v.1.11.18 allows a local attacker to execute arbitrary code via the forum title parameter. | [
"cpe:2.3:a:chamilo:chamilo_lms:1.11.18:*:*:*:*:*:*:*"
] | null | 5.4 | null | null |
|
CVE-2023-28687 | Reflected Cross-Site Scripting (XSS) vulnerability in multiple WordPress themes | Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') vulnerability in perfectwpthemes Glaze Blog Lite, themebeez Fascinate, themebeez Cream Blog, themebeez Cream Magazine allows Reflected XSS.This issue affects Glaze Blog Lite: from n/a through <= 1.1.4; Fascinate: from n/a through 1.0.8; Cream Blog: from n/a through 2.1.3; Cream Magazine: from n/a through 2.1.4.
| [] | null | 7.1 | null | null |
CVE-2020-7319 | Improper Access Control Vulnerability in ENS for Windows | Improper Access Control vulnerability in McAfee Endpoint Security (ENS) for Windows prior to 10.7.0 September 2020 Update allows local users to access files which the user otherwise would not have access to via manipulating symbolic links to redirect McAfee file operations to an unintended file. | [
"cpe:2.3:a:mcafee:endpoint_security:*:*:*:*:*:windows:*:*"
] | null | 8.8 | null | null |
GHSA-5m8h-3c7v-787m | A vulnerability in the tenant security implementation of Cisco Nexus Dashboard Orchestrator (NDO) could allow an authenticated, remote attacker to modify or delete tenant templates on an affected system.This vulnerability is due to improper access controls within tenant security. An attacker who is using a valid user account with write privileges and either a Site Manager or Tenant Manager role could exploit this vulnerability. A successful exploit could allow the attacker to modify or delete tenant templates under non-associated tenants, which could disrupt network traffic. | [] | null | 5.4 | null | null |
|
CVE-2008-0713 | Unspecified vulnerability in the FTP server for HP-UX B.11.11, B.11.23, and B.11.31 allows remote authenticated users to cause a denial of service (FTP server outage) via unknown attack vectors. | [
"cpe:2.3:o:hp:hp-ux:11.11:*:*:*:*:*:*:*",
"cpe:2.3:o:hp:hp-ux:11.23:*:*:*:*:*:*:*",
"cpe:2.3:o:hp:hp-ux:11.31:*:*:*:*:*:*:*"
] | null | null | null | 6.8 |
|
GHSA-hqxp-37pv-997r | Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') vulnerability in viktoras MorningTime Lite allows Stored XSS.This issue affects MorningTime Lite: from n/a through 1.3.2. | [] | null | 6.5 | null | null |
|
GHSA-59h2-qw44-f67r | XCOM Data Transport for Windows, Linux, and UNIX 11.6 releases contain a vulnerability due to insufficient input validation that could potentially allow remote attackers to execute arbitrary commands with elevated privileges. | [] | null | 9.8 | null | null |
|
CVE-2024-40919 | bnxt_en: Adjust logging of firmware messages in case of released token in __hwrm_send() | In the Linux kernel, the following vulnerability has been resolved:
bnxt_en: Adjust logging of firmware messages in case of released token in __hwrm_send()
In case of token is released due to token->state == BNXT_HWRM_DEFERRED,
released token (set to NULL) is used in log messages. This issue is
expected to be prevented by HWRM_ERR_CODE_PF_UNAVAILABLE error code. But
this error code is returned by recent firmware. So some firmware may not
return it. This may lead to NULL pointer dereference.
Adjust this issue by adding token pointer check.
Found by Linux Verification Center (linuxtesting.org) with SVACE. | [] | null | 5.5 | null | null |
CVE-2012-2203 | IBM Global Security Kit (aka GSKit) before 8.0.14.22, as used in IBM Rational Directory Server, IBM Tivoli Directory Server, and other products, uses the PKCS #12 file format for certificate objects without enforcing file integrity, which makes it easier for remote attackers to spoof SSL servers via vectors involving insertion of an arbitrary root Certification Authority (CA) certificate. | [
"cpe:2.3:a:ibm:global_security_kit:*:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:global_security_kit:7.0.4.28:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:global_security_kit:7.0.4.29:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:rational_directory_server:*:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:tivoli_directory_server:*:*:*:*:*:*:*:*"
] | null | null | null | 7.5 |
|
GHSA-7668-4r26-7chc | An issue has been discovered affecting GitLab versions prior to 14.4.5, between 14.5.0 and 14.5.3, and between 14.6.0 and 14.6.1. Gitlab's Slack integration is incorrectly validating user input and allows to craft malicious URLs that are sent to slack. | [] | null | 4.3 | null | null |
|
CVE-2013-4355 | Xen 4.3.x and earlier does not properly handle certain errors, which allows local HVM guests to obtain hypervisor stack memory via a (1) port or (2) memory mapped I/O write or (3) other unspecified operations related to addresses without associated memory. | [
"cpe:2.3:o:xen:xen:*:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:3.0.2:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:3.0.3:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:3.0.4:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:3.1.3:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:3.1.4:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:3.2.0:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:3.2.1:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:3.2.2:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:3.2.3:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:3.3.0:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:3.3.1:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:3.3.2:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:3.4.0:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:3.4.1:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:3.4.2:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:3.4.3:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:3.4.4:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:4.0.0:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:4.0.1:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:4.0.2:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:4.0.3:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:4.0.4:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:4.1.0:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:4.1.1:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:4.1.2:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:4.1.3:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:4.1.4:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:4.1.5:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:4.2.0:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:4.2.1:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:4.2.2:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:4.2.3:*:*:*:*:*:*:*"
] | null | null | null | 1.5 |
|
GHSA-cr48-c784-cmxh | authpam.c in courier-authdaemon for Courier Mail Server 0.37.3 through 0.52.1, when using pam_tally, does not call the pam_acct_mgmt function to verify that access should be granted, which allows attackers to authenticate to the server using accounts that have been disabled. | [] | null | null | null | null |
|
CVE-2025-26622 | sqrt doesn't define rounding behavior in Vyper | vyper is a Pythonic Smart Contract Language for the EVM. Vyper `sqrt()` builtin uses the babylonian method to calculate square roots of decimals. Unfortunately, improper handling of the oscillating final states may lead to sqrt incorrectly returning rounded up results. This issue is being addressed and a fix is expected in version 0.4.1. Users are advised to upgrade as soon as the patched release is available. There are no known workarounds for this vulnerability. | [] | 2.3 | null | null | null |
GHSA-688h-rc67-x7vx | Adobe Experience Manager versions 6.5.20 and earlier are affected by a stored Cross-Site Scripting (XSS) vulnerability that could be abused by a privileged attacker to inject malicious scripts into vulnerable form fields. Malicious JavaScript may be executed in a victim’s browser when they browse to the page containing the vulnerable field. | [] | null | 4.5 | null | null |
|
GHSA-87r9-pj76-c2hq | 3S-Smart Software Solutions GmbH CODESYS V3 OPC UA Server, all versions 3.5.11.0 to 3.5.15.0, allows an attacker to send crafted requests from a trusted OPC UA client that cause a NULL pointer dereference, which may trigger a denial-of-service condition. | [] | null | 6.5 | null | null |
|
GHSA-2wjv-2phj-464p | A malicious userspace application can cause a integer overflow and bypass security checks performed by system call handlers. The impact would depend on the underlying system call and can range from denial of service to information leak to memory corruption resulting in code execution within the kernel. See NCC-ZEP-005 This issue affects: zephyrproject-rtos zephyr version 1.14.1 and later versions. version 2.1.0 and later versions. | [] | null | null | null | null |
|
GHSA-w8w8-8hcx-qjrq | SysAid 20.3.64 b14 is affected by Blind and Stacker SQL injection via AssetManagementChart.jsp (GET computerID), AssetManagementChart.jsp (POST group1), AssetManagementList.jsp (GET computerID or group1), or AssetManagementSummary.jsp (GET group1). | [] | null | null | null | null |
|
GHSA-7w66-rrr8-g736 | An issue was discovered on D-Link DIR-816 A2 1.10 B05 devices. Within the handler function of the /goform/DDNS route, a very long password could lead to a stack-based buffer overflow and overwrite the return address. | [] | null | null | 9.8 | null |
|
GHSA-gxj3-vwm6-2f7w | The gnome-shell plugin 3.4.1 in GNOME allows remote attackers to force the download and installation of arbitrary extensions from extensions.gnome.org via a crafted web page. | [] | null | null | null | null |
|
GHSA-4jwm-69fq-5hpg | Cisco Security Monitoring, Analysis and Response System (CS-MARS) before 4.2.1 ships with an Oracle database that contains several default accounts and passwords, which allows attackers to obtain sensitive information. | [] | null | null | null | null |
|
GHSA-fx63-8q93-pfr5 | The huft_build function in inflate.c in gzip before 1.3.13 creates a hufts (aka huffman) table that is too small, which allows remote attackers to cause a denial of service (application crash or infinite loop) or possibly execute arbitrary code via a crafted archive. NOTE: this issue is caused by a CVE-2006-4334 regression. | [] | null | null | null | null |
|
GHSA-2rr3-vw22-qpv2 | In the web management interface in Foscam C1 Indoor HD Camera running application firmware 2.52.2.37, a specially crafted HTTP request can allow for a user to inject arbitrary data in the "msmtprc" configuration file resulting in command execution. An attacker can simply send an HTTP request to the device to trigger this vulnerability. | [] | null | null | 8.8 | null |
|
GHSA-v6wq-m5xf-2r3c | hydrogen.cc in Google V8, as used Google Chrome before 40.0.2214.91, does not properly handle arrays with holes, which allows remote attackers to cause a denial of service (memory corruption) or possibly have unspecified other impact via crafted JavaScript code that triggers an array copy. | [] | null | null | null | null |
|
GHSA-vm3v-rp2c-5h56 | A memory corruption issue was addressed with improved input validation. This issue is fixed in iOS 12.2, macOS Mojave 10.14.4. An application may be able to execute arbitrary code with kernel privileges. | [] | null | null | null | null |
|
CVE-2024-8121 | The Ultimate WordPress Toolkit – WP Extended <= 3.0.8 - Missing Authorization to Admin Username Change | The The Ultimate WordPress Toolkit – WP Extended plugin for WordPress is vulnerable to unauthorized modification of user names due to a missing capability check on the wpext_change_admin_name() function in all versions up to, and including, 3.0.8. This makes it possible for authenticated attackers, with Subscriber-level access and above, to change an admin's username to a username of their liking as long as the default 'admin' was used. | [
"cpe:2.3:a:wpextended:wp_extended:*:*:*:*:*:wordpress:*:*"
] | null | 5.4 | null | null |
CVE-2002-1224 | Directory traversal vulnerability in kpf for KDE 3.0.1 through KDE 3.0.3a allows remote attackers to read arbitrary files as the kpf user via a URL with a modified icon parameter. | [
"cpe:2.3:o:kde:kde:3.0.1:*:*:*:*:*:*:*",
"cpe:2.3:o:kde:kde:3.0.2:*:*:*:*:*:*:*",
"cpe:2.3:o:kde:kde:3.0.3:*:*:*:*:*:*:*",
"cpe:2.3:o:kde:kde:3.0.3a:*:*:*:*:*:*:*"
] | null | null | null | 5 |
|
CVE-2005-2812 | man2web allows remote attackers to execute arbitrary commands via -P arguments. | [
"cpe:2.3:a:man2web:man2web:0.87:*:*:*:*:*:*:*",
"cpe:2.3:a:man2web:man2web:0.88:*:*:*:*:*:*:*"
] | null | null | null | 7.5 |
|
CVE-2024-51871 | WordPress Luzuk Team plugin <= 0.1.0 - Cross Site Scripting (XSS) vulnerability | Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') vulnerability in Luzuk Luzuk Team allows Stored XSS.This issue affects Luzuk Team: from n/a through 0.1.0. | [] | null | 6.5 | null | null |
GHSA-x4qm-mcjq-v2gf | Overflow in prost-types | Affected versions of this crate contained a bug in which untrusted input could cause an overflow and panic when converting a Timestamp to SystemTime. It is recommended to upgrade to prost-types v0.8 and switch the usage of From<Timestamp> for SystemTime to TryFrom<Timestamp> for SystemTime. | [] | null | 7.5 | null | null |
CVE-2024-56184 | In static long dev_send of tipc_dev_ql, there is a possible out of bounds read due to an incorrect bounds check. This could lead to local information disclosure with no additional execution privileges needed. User interaction is not needed for exploitation. | [] | null | 5.1 | null | null |
|
CVE-2021-1718 | Microsoft SharePoint Server Tampering Vulnerability | Microsoft SharePoint Server Tampering Vulnerability | [
"cpe:2.3:a:microsoft:sharepoint_server:2010:sp2:*:*:foundation:*:*:*",
"cpe:2.3:a:microsoft:sharepoint_foundation:2010:sp2:*:*:*:*:*:*"
] | null | 8 | null | null |
RHSA-2020:2547 | Red Hat Security Advisory: flash-plugin security update | flash-plugin: Arbitrary Code Execution vulnerability (APSB20-30) | [
"cpe:/a:redhat:rhel_extras:6"
] | null | 9.8 | null | null |
CVE-2019-16573 | A cross-site request forgery vulnerability in Jenkins Alauda DevOps Pipeline Plugin 2.3.2 and earlier allows attackers to connect to an attacker-specified URL using attacker-specified credentials IDs obtained through another method, capturing credentials stored in Jenkins. | [
"cpe:2.3:a:jenkins:alauda_devops_pipeline:*:*:*:*:*:jenkins:*:*"
] | null | 8.8 | null | 6.8 |
|
CVE-2023-45106 | WordPress Urvanov Syntax Highlighter Plugin <= 2.8.33 is vulnerable to Cross Site Request Forgery (CSRF) | Cross-Site Request Forgery (CSRF) vulnerability in Fedor Urvanov, Aram Kocharyan Urvanov Syntax Highlighter plugin <= 2.8.33 versions. | [
"cpe:2.3:a:urvanov:urvanov_syntax_highlighter:*:*:*:*:*:wordpress:*:*"
] | null | 4.3 | null | null |
GHSA-mfqr-wp5f-9gj8 | Possible Insertion of Sensitive Information into Log File Vulnerabilityin eDirectory has been discovered in
OpenText™ eDirectory 9.2.4.0000. | [] | null | 6.5 | null | null |
|
RHSA-2019:1591 | Red Hat Security Advisory: OpenShift Container Platform 4.1 image security update | openshift: OAuth access tokens written in plaintext to API server audit logs | [
"cpe:/a:redhat:openshift:4.1::el7"
] | null | null | 2.3 | null |
GHSA-gr6m-w52c-x634 | In versions of NGINX Controller prior to 3.2.0, communication between NGINX Controller and NGINX Plus instances skip TLS verification by default. | [] | null | null | null | null |
|
CVE-2018-0872 | ChakraCore and Microsoft Edge in Microsoft Windows 10 Gold, 1511, 1607, 1703, 1709, and Windows Server 2016 allows remote code execution, due to how the Chakra scripting engine handles objects in memory, aka "Chakra Scripting Engine Memory Corruption Vulnerability". This CVE ID is unique from CVE-2018-0873, CVE-2018-0874, CVE-2018-0930, CVE-2018-0931, CVE-2018-0933, CVE-2018-0934, CVE-2018-0936, and CVE-2018-0937. | [
"cpe:2.3:a:microsoft:edge:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_10:-:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_10:1511:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_10:1607:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_10:1703:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_10:1709:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2016:*:*:*:*:*:*:*:*"
] | null | null | 7.5 | 7.6 |
|
GHSA-ghv2-6cx6-8wrg | FrogCMS v0.9.5 was discovered to contain a Cross-Site Request Forgery (CSRF) vulnerability via /admin/?/snippet/delete/3. | [] | null | 8.8 | null | null |
|
GHSA-m7rm-rgh4-mhj4 | Directory traversal vulnerability in the WebLaunch.WeblaunchCtl.1 (aka CWebLaunchCtl) ActiveX control in weblaunch.ocx 1.0.0.1 in Gateway Weblaunch allows remote attackers to execute arbitrary programs via a ..\ (dot dot backslash) in the second argument to the DoWebLaunch method. NOTE: some of these details are obtained from third party information. | [] | null | null | null | null |
|
CVE-2024-28167 | Missing Authorization check in SAP Group Reporting Data Collection (Enter Package Data) | SAP Group Reporting Data Collection does not perform necessary authorization checks for an authenticated user, resulting in escalation of privileges. On successful exploitation, specific data can be changed via the Enter Package Data app although the user does not have sufficient authorization causing high impact on Integrity of the appliction.
| [
"cpe:2.3:a:sap_se:sap_group_reporting_data_collection:*:*:*:*:*:*:*:*"
] | null | 6.5 | null | null |
CVE-2022-3287 | When creating an OPERATOR user account on the BMC, the redfish plugin saved the auto-generated password to /etc/fwupd/redfish.conf without proper restriction, allowing any user on the system to read the same configuration file. | [
"cpe:2.3:a:fwupd:fwupd:*:*:*:*:*:*:*:*"
] | null | 6.5 | null | null |
|
CVE-2023-35047 | WordPress All Bootstrap Blocks Plugin <= 1.3.6 is vulnerable to Cross Site Request Forgery (CSRF) | Cross-Site Request Forgery (CSRF) vulnerability in AREOI All Bootstrap Blocks plugin <= 1.3.6 versions. | [
"cpe:2.3:a:areoi:all_bootstrap_blocks:*:*:*:*:*:wordpress:*:*"
] | null | 4.3 | null | null |
CVE-2022-39912 | Improper handling of insufficient permissions vulnerability in setSecureFolderPolicy in PersonaManagerService prior to Android T(13) allows local attackers to set some setting value in Secure folder. | [
"cpe:2.3:o:google:android:*:*:*:*:*:*:*:*"
] | null | 6.2 | null | null |
|
GHSA-x76w-6vjr-8xgj | Possible ReDoS vulnerability in query parameter filtering in Action Dispatch | There is a possible ReDoS vulnerability in the query parameter filtering routines of Action Dispatch. This vulnerability has been assigned the CVE identifier CVE-2024-41128.ImpactCarefully crafted query parameters can cause query parameter filtering to take an unexpected amount of time, possibly resulting in a DoS vulnerability. All users running an affected release should either upgrade or apply the relevant patch immediately.Ruby 3.2 has mitigations for this problem, so Rails applications using Ruby 3.2 or newer are unaffected. Rails 8.0.0.beta1 depends on Ruby 3.2 or greater so is unaffected.ReleasesThe fixed releases are available at the normal locations.WorkaroundsUsers on Ruby 3.2 are unaffected by this issue.CreditsThanks to [scyoon](https://hackerone.com/scyoon) for the report and patches! | [] | 6.6 | null | null | null |
CVE-2016-10884 | The simple-membership plugin before 3.3.3 for WordPress has multiple CSRF issues. | [
"cpe:2.3:a:simple-membership-plugin:simple_membership:*:*:*:*:*:wordpress:*:*"
] | null | 8.8 | null | 6.8 |
|
RHSA-2022:5053 | Red Hat Security Advisory: log4j security update | log4j: deserialization of untrusted data in SocketServer | [
"cpe:/o:redhat:rhel_els:6"
] | null | 9.8 | null | null |
GHSA-w2px-wm37-g99g | A memory corruption issue was addressed with improved lock state checking. This issue is fixed in iOS 12.1.3, macOS Mojave 10.14.3, tvOS 12.1.2. A malicious application may cause unexpected changes in memory shared between processes. | [] | null | null | 7.8 | null |
|
GHSA-4gqh-r946-jvgc | A vulnerability, which was classified as critical, has been found in zhijiantianya ruoyi-vue-pro 2.4.1. Affected by this issue is some unknown functionality of the file /app-api/infra/file/upload of the component Front-End Store Interface. The manipulation of the argument path leads to path traversal. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. The vendor was contacted early about this disclosure but did not respond in any way. | [] | 5.3 | 5.4 | null | null |
|
CVE-2024-49319 | WordPress Awesome Contact Form7 for Elementor plugin <= 3.0 - Cross Site Scripting (XSS) vulnerability | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in B.M. Rafiul Alam Awesome Contact Form7 for Elementor allows Stored XSS.This issue affects Awesome Contact Form7 for Elementor: from n/a through 3.0. | [] | null | 6.5 | null | null |
GHSA-494p-v8gw-x4mq | IBM Security Privileged Identity Manager Virtual Appliance could allow a remote attacker to obtain sensitive information, caused by the failure to properly enable HTTP Strict Transport Security. An attacker could exploit this vulnerability to obtain sensitive information using man in the middle techniques. | [] | null | null | 5.9 | null |
|
GHSA-c2c3-pqw5-5p7c | Go-Guerrilla SMTP Daemon allows the PROXY command to be sent multiple times | SummaryThe PROXY command is accepted multiple times, allowing a client to spoof its IP address when the proxy protocol is being used.DetailsWhen ProxyOn is enabled, [it looks like the PROXY command will be accepted multiple times](https://github.com/phires/go-guerrilla/blob/fca3b2d8957a746997c7e71fca39004f5c96e91f/server.go#L495), with later invocations overriding earlier ones. The proxy protocol only supports one initial PROXY header; anything after that is considered part of the exchange between client and server, so the client is free to send further PROXY commands with whatever data it pleases. go-guerrilla will treat these as coming from the reverse proxy, allowing a client to spoof its IP address.Note that the format of the PROXY header is [well-defined](https://www.haproxy.org/download/1.8/doc/proxy-protocol.txt). It probably shouldn't be treated as an SMTP command; parsing it the same way is likely to result in odd behavior and could lead to other vulnerabilities.PoCI'm working on writing a PR to fix this vulnerability. It'll include a unit test that will serve as a PoC on the current version.ImpactAny instance with `ProxyOn` enabled (`proxyon` in the JSON config) is affected.As far as I'm able to tell, the impact is limited to spoofing the `RemoteIP` field. This isn't ideal, but it probably has less practical impact on an MTA than, say, a web server. | [] | null | 5.3 | null | null |
GHSA-q7jx-m6qw-6j3q | SQL injection vulnerability in index.php in Quick.Cms.Lite 0.5 allows remote attackers to execute arbitrary SQL commands via the id parameter. | [] | null | null | null | null |
|
RHSA-2019:0431 | Red Hat Security Advisory: ansible security and bug fix update | Ansible: path traversal in the fetch module | [
"cpe:/a:redhat:ansible_engine:2.7::el7"
] | null | null | 4.2 | null |
CVE-2020-26101 | In cPanel before 88.0.3, insecure RNDC credentials are used for BIND on a templated VM (SEC-549). | [
"cpe:2.3:a:cpanel:cpanel:*:*:*:*:*:*:*:*"
] | null | 9.8 | null | 5 |
|
CVE-2020-1289 | A spoofing vulnerability exists when Microsoft SharePoint Server does not properly sanitize a specially crafted web request to an affected SharePoint server, aka 'Microsoft SharePoint Spoofing Vulnerability'. This CVE ID is unique from CVE-2020-1148. | [
"cpe:2.3:a:microsoft:sharepoint_foundation:2010:sp2:*:*:*:*:*:*"
] | null | 5.4 | null | 3.5 |
|
CVE-2023-1739 | SourceCodester Simple and Beautiful Shopping Cart System upload.php unrestricted upload | A vulnerability was found in SourceCodester Simple and Beautiful Shopping Cart System 1.0 and classified as critical. This issue affects some unknown processing of the file upload.php. The manipulation leads to unrestricted upload. The attack may be initiated remotely. The exploit has been disclosed to the public and may be used. The associated identifier of this vulnerability is VDB-224627. | [
"cpe:2.3:a:simple_and_beautiful_shopping_cart_system_project:simple_and_beautiful_shopping_cart_system:1.0:*:*:*:*:*:*:*"
] | null | 6.3 | 6.3 | 6.5 |
GHSA-f3v8-7jfc-xgvg | The register method in the UsersModelRegistration class in controllers/user.php in the Users component in Joomla! before 3.6.4, when registration has been disabled, allows remote attackers to create user accounts by leveraging failure to check the Allow User Registration configuration setting. | [] | null | null | 8.1 | null |
|
CVE-2015-1094 | IOAcceleratorFamily in Apple iOS before 8.3 and Apple TV before 7.2 allows attackers to obtain sensitive information about kernel memory via a crafted app. | [
"cpe:2.3:o:apple:tvos:*:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:iphone_os:*:*:*:*:*:*:*:*"
] | null | null | null | 1.9 |
|
GHSA-qmvm-6g77-jj45 | Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Compiling). Supported versions that are affected are 5.7.36 and prior and 8.0.27 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server as well as unauthorized update, insert or delete access to some of MySQL Server accessible data. CVSS 3.1 Base Score 5.5 (Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:L/A:H). | [] | null | null | null | null |
|
GHSA-h9rg-c998-4hw4 | Cross-site scripting (XSS) vulnerability in BusinessFlow/login in AlgoSec Firewall Analyzer 6.4 allows remote attackers to inject arbitrary web script or HTML via the message parameter. | [] | null | null | null | null |
|
CVE-2022-30579 | TIBCO Spotfire Server Blind SSRF vulnerability | The Web Player component of TIBCO Software Inc.'s TIBCO Spotfire Analytics Platform for AWS Marketplace and TIBCO Spotfire Server contains a difficult to exploit vulnerability that allows a low privileged attacker with network access to execute blind Server Side Request Forgery (SSRF) on the affected system. Affected releases are TIBCO Software Inc.'s TIBCO Spotfire Analytics Platform for AWS Marketplace: version 12.0.0 and TIBCO Spotfire Server: version 12.0.0. | [
"cpe:2.3:a:tibco:spotfire_analytics_platform:12.0.0:*:*:*:*:aws_marketplace:*:*",
"cpe:2.3:a:tibco:spotfire_server:12.0.0:*:*:*:*:*:*:*"
] | null | 7.1 | null | null |
CVE-2016-0839 | post_proc/volume_listener.c in mediaserver in Android 6.x before 2016-04-01 mishandles deleted effect context, which allows remote attackers to execute arbitrary code or cause a denial of service (memory corruption) via a crafted media file, aka internal bug 25753245. | [
"cpe:2.3:o:google:android:6.0:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:6.0.1:*:*:*:*:*:*:*"
] | null | null | 9.8 | 10 |
|
CVE-2025-21714 | RDMA/mlx5: Fix implicit ODP use after free | In the Linux kernel, the following vulnerability has been resolved:
RDMA/mlx5: Fix implicit ODP use after free
Prevent double queueing of implicit ODP mr destroy work by using
__xa_cmpxchg() to make sure this is the only time we are destroying this
specific mr.
Without this change, we could try to invalidate this mr twice, which in
turn could result in queuing a MR work destroy twice, and eventually the
second work could execute after the MR was freed due to the first work,
causing a user after free and trace below.
refcount_t: underflow; use-after-free.
WARNING: CPU: 2 PID: 12178 at lib/refcount.c:28 refcount_warn_saturate+0x12b/0x130
Modules linked in: bonding ib_ipoib vfio_pci ip_gre geneve nf_tables ip6_gre gre ip6_tunnel tunnel6 ipip tunnel4 ib_umad rdma_ucm mlx5_vfio_pci vfio_pci_core vfio_iommu_type1 mlx5_ib vfio ib_uverbs mlx5_core iptable_raw openvswitch nsh rpcrdma ib_iser libiscsi scsi_transport_iscsi rdma_cm iw_cm ib_cm ib_core xt_conntrack xt_MASQUERADE nf_conntrack_netlink nfnetlink xt_addrtype iptable_nat nf_nat br_netfilter rpcsec_gss_krb5 auth_rpcgss oid_registry overlay zram zsmalloc fuse [last unloaded: ib_uverbs]
CPU: 2 PID: 12178 Comm: kworker/u20:5 Not tainted 6.5.0-rc1_net_next_mlx5_58c644e #1
Hardware name: QEMU Standard PC (Q35 + ICH9, 2009), BIOS rel-1.13.0-0-gf21b5a4aeb02-prebuilt.qemu.org 04/01/2014
Workqueue: events_unbound free_implicit_child_mr_work [mlx5_ib]
RIP: 0010:refcount_warn_saturate+0x12b/0x130
Code: 48 c7 c7 38 95 2a 82 c6 05 bc c6 fe 00 01 e8 0c 66 aa ff 0f 0b 5b c3 48 c7 c7 e0 94 2a 82 c6 05 a7 c6 fe 00 01 e8 f5 65 aa ff <0f> 0b 5b c3 90 8b 07 3d 00 00 00 c0 74 12 83 f8 01 74 13 8d 50 ff
RSP: 0018:ffff8881008e3e40 EFLAGS: 00010286
RAX: 0000000000000000 RBX: 0000000000000000 RCX: 0000000000000027
RDX: ffff88852c91b5c8 RSI: 0000000000000001 RDI: ffff88852c91b5c0
RBP: ffff8881dacd4e00 R08: 00000000ffffffff R09: 0000000000000019
R10: 000000000000072e R11: 0000000063666572 R12: ffff88812bfd9e00
R13: ffff8881c792d200 R14: ffff88810011c005 R15: ffff8881002099c0
FS: 0000000000000000(0000) GS:ffff88852c900000(0000) knlGS:0000000000000000
CS: 0010 DS: 0000 ES: 0000 CR0: 0000000080050033
CR2: 00007f5694b5e000 CR3: 00000001153f6003 CR4: 0000000000370ea0
DR0: 0000000000000000 DR1: 0000000000000000 DR2: 0000000000000000
DR3: 0000000000000000 DR6: 00000000fffe0ff0 DR7: 0000000000000400
Call Trace:
<TASK>
? refcount_warn_saturate+0x12b/0x130
free_implicit_child_mr_work+0x180/0x1b0 [mlx5_ib]
process_one_work+0x1cc/0x3c0
worker_thread+0x218/0x3c0
kthread+0xc6/0xf0
ret_from_fork+0x1f/0x30
</TASK> | [] | null | 7.8 | null | null |
CVE-2014-9520 | SQL injection vulnerability in execute.php in InfiniteWP Admin Panel before 2.4.4 allows remote attackers to execute arbitrary SQL commands via the historyID parameter. | [
"cpe:2.3:a:infinitewp:infinitewp:*:*:*:*:*:*:*:*"
] | null | null | null | 7.5 |
|
GHSA-fq84-chpx-fm5f | Viewing restrictions bypass vulnerability in Portal of Cybozu Garoon 4.0.0 to 5.0.2 allows a remote authenticated attacker to obtain the data of Portal without the viewing privilege. | [] | null | 4.3 | null | null |
|
GHSA-58h4-9j5q-gmvr | A vulnerability in the Cisco Network Plug and Play application of Cisco IOS 12.4 through 15.6 and Cisco IOS XE 3.3 through 16.4 could allow an unauthenticated, remote attacker to gain unauthorized access to sensitive data by using an invalid certificate. The vulnerability is due to insufficient certificate validation by the affected software. An attacker could exploit this vulnerability by supplying a crafted certificate to an affected device. A successful exploit could allow the attacker to conduct man-in-the-middle attacks to decrypt confidential information on user connections to the affected software. Cisco Bug IDs: CSCvc33171. | [] | null | null | 5.9 | null |
|
GHSA-7pf2-qwx3-5fmv | Multiple cross-site scripting (XSS) vulnerabilities in MyBB (aka MyBulletinBoard) 1.8.x before 1.8.2 allow remote attackers to inject arbitrary web script or HTML via the (1) type parameter to report.php, (2) signature parameter in a do_editsig action to usercp.php, or (3) title parameter in the style-templates module in an edit_template action or (4) file parameter in the config-languages module in an edit action to admin/index.php. | [] | null | null | null | null |
|
GHSA-x49m-3cw7-gq5q | jcvi vulnerable to Configuration Injection due to unsanitized user input | SummaryA configuration injection happens when user input is considered by the application in an unsanitized format and can reach the configuration file. A malicious user may craft a special payload that may lead to a command injection.PoCThe vulnerable code snippet is [/jcvi/apps/base.py#LL2227C1-L2228C41](https://github.com/tanghaibao/jcvi/blob/cede6c65c8e7603cb266bc3395ac8f915ea9eac7/jcvi/apps/base.py#LL2227C1-L2228C41). Under some circumstances a user input is retrieved and stored within the `fullpath` variable which reaches the configuration file `~/.jcvirc`.I ripped a part of the codebase into a runnable PoC as follows. All the PoC does is call the `getpath()` function under some circumstances.To run the PoC, you need to remove the config file `~/.jcvirc` to emulate the first run,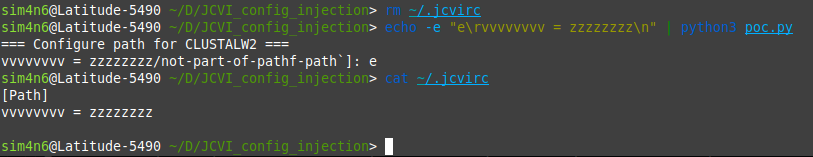You can notice the random key/value characters `vvvvvvvv = zzzzzzzz` were successfully injected.ImpactThe impact of a configuration injection may vary. Under some conditions, it may lead to command injection if there is for instance shell code execution from the configuration file values. | [] | null | 7.1 | null | null |
GHSA-cggq-qh98-22f3 | Vulnerability in the Core RDBMS component of Oracle Database Server. Supported versions that are affected are 12.2.0.1, 18c and 19c. Easily exploitable vulnerability allows low privileged attacker having Create Session, Execute on DBMS_ADVISOR privilege with network access via OracleNet to compromise Core RDBMS. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of Core RDBMS accessible data. CVSS 3.0 Base Score 4.3 (Integrity impacts). CVSS Vector: (CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:L/A:N). | [] | null | 4.3 | null | null |
|
CVE-2022-20850 | Cisco SD-WAN Arbitrary File Deletion Vulnerability | A vulnerability in the CLI of stand-alone Cisco IOS XE SD-WAN Software and Cisco SD-WAN Software could allow an authenticated, local attacker to delete arbitrary files from the file system of an affected device. This vulnerability is due to insufficient input validation. An attacker could exploit this vulnerability by injecting arbitrary file path information when using commands in the CLI of an affected device. A successful exploit could allow the attacker to delete arbitrary files from the file system of the affected device. | [
"cpe:2.3:a:cisco:sd-wan_vbond_orchestrator:*:*:*:*:*:*:*:*",
"cpe:2.3:a:cisco:sd-wan_vmanage:*:*:*:*:*:*:*:*",
"cpe:2.3:a:cisco:sd-wan_vsmart_controller:*:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe_sd-wan:*:*:*:*:*:*:*:*",
"cpe:2.3:a:cisco:sd-wan:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:1100-4g_integrated_services_router:-:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:1100-6g_integrated_services_router:-:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:1100_integrated_services_router:-:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:vedge_100:-:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:vedge_1000:-:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:vedge_100b:-:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:vedge_100m:-:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:vedge_2000:-:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:vedge_5000:-:*:*:*:*:*:*:*"
] | null | 5.5 | null | null |
GHSA-7pqf-c737-ccf9 | Little Snitch version 4.5.1 and older changed ownership of a directory path controlled by the user. This allowed the user to escalate to root by linking the path to a directory containing code executed by root. | [] | null | null | null | null |